Skip Lists S 3 S 2 S 1. Skip Lists Goodrich, Tamassia
|
|
|
- Clement Watson
- 6 years ago
- Views:
Transcription
1 Skip Lists S Skip Lists 1
2 What is a Skip List A skip list for a set S of distinct (key, element) items is a series of lists,,, S h such that Each list S i contains the special keys and List contains the keys of S in nondecreasing order Each list is a subsequence of the previous one, i.e., S h List S h contains only the two special keys We show how to use a skip list to implement the dictionary ADT S Skip Lists 2
3 Search We search for a key x in a a skip list as follows: We start at the first position of the top list At the current position p, we compare x with y key(next(p)) x = y: we return element(next(p)) x > y: we scan forward x < y: we drop down If we try to drop down past the bottom list, we return null Example: search for 78 S Skip Lists 3
4 Randomized Algorithms A randomized algorithm performs coin tosses (i.e., uses random bits) to control its execution It contains statements of the type b random() if b = 0 do A else { b = 1} do B Its running time depends on the outcomes of the coin tosses We analyze the expected running time of a randomized algorithm under the following assumptions the coins are unbiased, and the coin tosses are independent The worst-case running time of a randomized algorithm is often large but has very low probability (e.g., it occurs when all the coin tosses give heads ) We use a randomized algorithm to insert items into a skip list Skip Lists 4
5 Insertion To insert an entry (x, o) into a skip list, we use a randomized algorithm: We repeatedly toss a coin until we get tails, and we denote with i the number of times the coin came up heads If i h, we add to the skip list new lists S h+1,, S i +1, each containing only the two special keys We search for x in the skip list and find the positions p 0, p 1,, p i of the items with largest key less than x in each list,,, S i For j 0,, i, we insert item (x, o) into list S j after position p j Example: insert key 15, with i = 2 p 2 p 1 p S Skip Lists 5
6 Deletion To remove an entry with key x from a skip list, we proceed as follows: We search for x in the skip list and find the positions p 0, p 1,, p i of the items with key x, where position p j is in list S j We remove positions p 0, p 1,, p i from the lists,,, S i We remove all but one list containing only the two special keys Example: remove key 34 S 3 p 2 34 p p Skip Lists 6
7 Implementation We can implement a skip list with quad-nodes A quad-node stores: entry link to the node prev link to the node next link to the node below link to the node above Also, we define special keys PLUS_INF and MINUS_INF, and we modify the key comparator to handle them quad-node x Skip Lists 7
8 Space Usage The space used by a skip list depends on the random bits used by each invocation of the insertion algorithm We use the following two basic probabilistic facts: Fact 1: The probability of getting i consecutive heads when flipping a coin is 1/2 i Fact 2: If each of n entries is present in a set with probability p, the expected size of the set is np Consider a skip list with n entries By Fact 1, we insert an entry in list S i with probability 1/2 i By Fact 2, the expected size of list S i is n/2 i The expected number of nodes used by the skip list is h i= 0 h n 1 = n 2n i < i 2 2 i= 0 Thus, the expected space usage of a skip list with n items is O(n) Skip Lists 8
9 Height The running time of the search an insertion algorithms is affected by the height h of the skip list We show that with high probability, a skip list with n items has height O(log n) We use the following additional probabilistic fact: Fact 3: If each of n events has probability p, the probability that at least one event occurs is at most np Consider a skip list with n entires By Fact 1, we insert an entry in list S i with probability 1/2 i By Fact 3, the probability that list S i has at least one item is at most n/2 i By picking i = 3log n, we have that the probability that S 3log n has at least one entry is at most n/2 3log n = n/n 3 = 1/n 2 Thus a skip list with n entries has height at most 3log n with probability at least 1 1/n 2 Skip Lists 9
10 Search and Update Times The search time in a skip list is proportional to the number of drop-down steps, plus the number of scan-forward steps The drop-down steps are bounded by the height of the skip list and thus are O(log n) with high probability To analyze the scan-forward steps, we use yet another probabilistic fact: Fact 4: The expected number of coin tosses required in order to get tails is 2 When we scan forward in a list, the destination key does not belong to a higher list A scan-forward step is associated with a former coin toss that gave tails By Fact 4, in each list the expected number of scanforward steps is 2 Thus, the expected number of scan-forward steps is O(log n) We conclude that a search in a skip list takes O(log n) expected time The analysis of insertion and deletion gives similar results Skip Lists 10
11 Summary A skip list is a data structure for dictionaries that uses a randomized insertion algorithm In a skip list with n entries The expected space used is O(n) The expected search, insertion and deletion time is O(log n) Using a more complex probabilistic analysis, one can show that these performance bounds also hold with high probability Skip lists are fast and simple to implement in practice Skip Lists 11
CSED233: Data Structures (2017F) Lecture10:Hash Tables, Maps, and Skip Lists
 (2017F) Lecture10:Hash Tables, Maps, and Skip Lists Daijin Kim CSE, POSTECH dkim@postech.ac.kr Maps A map models a searchable collection of key-value entries The main operations of a map are for searching,
(2017F) Lecture10:Hash Tables, Maps, and Skip Lists Daijin Kim CSE, POSTECH dkim@postech.ac.kr Maps A map models a searchable collection of key-value entries The main operations of a map are for searching,
CHAPTER 9 HASH TABLES, MAPS, AND SKIP LISTS
 0 1 2 025-612-0001 981-101-0002 3 4 451-229-0004 CHAPTER 9 HASH TABLES, MAPS, AND SKIP LISTS ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH,
0 1 2 025-612-0001 981-101-0002 3 4 451-229-0004 CHAPTER 9 HASH TABLES, MAPS, AND SKIP LISTS ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH,
Linear Lists. Advanced Algorithmics (4AP) Linear structures: Abstract Data Type (ADT) Lists: Array ADT
 Linear Lists Advanced Algorithmics (4AP) Linear structures: Lists, Queues, Stacks, sorting, Jaak Vilo 2009 Spring Operations which one may want to perform on a linear list of n elements include: gain access
Linear Lists Advanced Algorithmics (4AP) Linear structures: Lists, Queues, Stacks, sorting, Jaak Vilo 2009 Spring Operations which one may want to perform on a linear list of n elements include: gain access
9.4.1 Search and Update Operations in a Skip List
 400 Chapter 9. Maps and Dictionaries 9.4.1 Search and Update Operations in a Skip List The skip list structure allows for simple dictionary search and update algorithms. In fact, all of the skip list search
400 Chapter 9. Maps and Dictionaries 9.4.1 Search and Update Operations in a Skip List The skip list structure allows for simple dictionary search and update algorithms. In fact, all of the skip list search
Data Structure - Skip List etc. -
 Data Structure - Skip List etc. - Hanyang University Jong-Il Park SKIP LIST Introduction to Skip Lists An interesting generalization of linked lists for dictionary ADT. Keep the simplicity of linked lists
Data Structure - Skip List etc. - Hanyang University Jong-Il Park SKIP LIST Introduction to Skip Lists An interesting generalization of linked lists for dictionary ADT. Keep the simplicity of linked lists
Using Randomization in the Teaching of Data Structures and Algorithms
 Using Randomization in the Teaching of Data Structures and Algorithms Michael T. Goodrich* Dept. of Computer Science Johns Hopkins University Baltimore, MD 21218 goodrichqcs.jhu.edu Roberto Tamassiat Dept.
Using Randomization in the Teaching of Data Structures and Algorithms Michael T. Goodrich* Dept. of Computer Science Johns Hopkins University Baltimore, MD 21218 goodrichqcs.jhu.edu Roberto Tamassiat Dept.
CS 261: Data Structures. Skip Lists
 CS 261: Data Structures Skip Lists 1 Complexity Lists and Arrays OPERATIONS ORDINARY LISTS AND ARRAYS SORTED ARRAYS SORTED LISTS Add O(1) O(n) O(n) Remove O(n) O(n) O(n) Contains O(n) O(log n) O(n) 2 Sorted
CS 261: Data Structures Skip Lists 1 Complexity Lists and Arrays OPERATIONS ORDINARY LISTS AND ARRAYS SORTED ARRAYS SORTED LISTS Add O(1) O(n) O(n) Remove O(n) O(n) O(n) Contains O(n) O(log n) O(n) 2 Sorted
Solution: It may be helpful to list out exactly what is in each of these events:
 MATH 5010(002) Fall 2017 Homework 1 Solutions Please inform your instructor if you find any errors in the solutions. 1. You ask a friend to choose an integer N between 0 and 9. Let A = {N 5}, B = {3 N
MATH 5010(002) Fall 2017 Homework 1 Solutions Please inform your instructor if you find any errors in the solutions. 1. You ask a friend to choose an integer N between 0 and 9. Let A = {N 5}, B = {3 N
Quick-Sort. Quick-Sort 1
 Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 Quick-Sort 1 Outline and Reading Quick-sort ( 4.3) Algorithm Partition step Quick-sort tree Execution example Analysis of quick-sort (4.3.1) In-place
Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 Quick-Sort 1 Outline and Reading Quick-sort ( 4.3) Algorithm Partition step Quick-sort tree Execution example Analysis of quick-sort (4.3.1) In-place
Lists: Array. Advanced Algorithmics (6EAP) MTAT searching, etc. Linear Lists
 Advanced Algorithmics (6EAP) http://courses.cs.ut.ee/2010/algorithmics/ MTAT.03.238 Linear structures, sorting, searching, etc Jaak Vilo 2010 Spring Lists: Array 0 1 size MAX_SIZE-1 3 6 7 5 2 L = int[max_size]
Advanced Algorithmics (6EAP) http://courses.cs.ut.ee/2010/algorithmics/ MTAT.03.238 Linear structures, sorting, searching, etc Jaak Vilo 2010 Spring Lists: Array 0 1 size MAX_SIZE-1 3 6 7 5 2 L = int[max_size]
COSC 2011 Section N Data structure for efficient Thursday, April
 Skip Lists - Description: (1) COSC 2011 Data structure for efficient Thursday, April 26 2001 Overview Skip Lists Description, Definition ADT Searching Insertion Removal realization of the Ordered Dictionary.
Skip Lists - Description: (1) COSC 2011 Data structure for efficient Thursday, April 26 2001 Overview Skip Lists Description, Definition ADT Searching Insertion Removal realization of the Ordered Dictionary.
Recitation 11. Graph Contraction and MSTs Announcements. SegmentLab has been released, and is due Friday, April 14. It s worth 135 points.
 Recitation Graph Contraction and MSTs. Announcements SegmentLab has been released, and is due Friday, April. It s worth 5 points. Midterm is on Friday, April. 5 RECITATION. GRAPH CONTRACTION AND MSTS.
Recitation Graph Contraction and MSTs. Announcements SegmentLab has been released, and is due Friday, April. It s worth 5 points. Midterm is on Friday, April. 5 RECITATION. GRAPH CONTRACTION AND MSTS.
Quick-Sort. Quick-sort is a randomized sorting algorithm based on the divide-and-conquer paradigm:
 Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 2014 Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9
Presentation for use with the textbook Data Structures and Algorithms in Java, 6 th edition, by M. T. Goodrich, R. Tamassia, and M. H. Goldwasser, Wiley, 2014 Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9
Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015
 Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 2015 Goodrich and Tamassia
Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 Quick-Sort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 2015 Goodrich and Tamassia
Chapter 4: Sorting. Spring 2014 Sorting Fun 1
 Chapter 4: Sorting 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 Spring 2014 Sorting Fun 1 What We ll Do! Quick Sort! Lower bound on runtimes for comparison based sort! Radix and Bucket sort Spring 2014
Chapter 4: Sorting 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 Spring 2014 Sorting Fun 1 What We ll Do! Quick Sort! Lower bound on runtimes for comparison based sort! Radix and Bucket sort Spring 2014
Sorting Goodrich, Tamassia Sorting 1
 Sorting Put array A of n numbers in increasing order. A core algorithm with many applications. Simple algorithms are O(n 2 ). Optimal algorithms are O(n log n). We will see O(n) for restricted input in
Sorting Put array A of n numbers in increasing order. A core algorithm with many applications. Simple algorithms are O(n 2 ). Optimal algorithms are O(n log n). We will see O(n) for restricted input in
Quick-Sort fi fi fi 7 9. Quick-Sort Goodrich, Tamassia
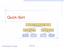 Quick-Sort 7 4 9 6 2 fi 2 4 6 7 9 4 2 fi 2 4 7 9 fi 7 9 2 fi 2 9 fi 9 Quick-Sort 1 Quick-Sort ( 10.2 text book) Quick-sort is a randomized sorting algorithm based on the divide-and-conquer paradigm: x
Quick-Sort 7 4 9 6 2 fi 2 4 6 7 9 4 2 fi 2 4 7 9 fi 7 9 2 fi 2 9 fi 9 Quick-Sort 1 Quick-Sort ( 10.2 text book) Quick-sort is a randomized sorting algorithm based on the divide-and-conquer paradigm: x
CS 561, Lecture 2 : Randomization in Data Structures. Jared Saia University of New Mexico
 CS 561, Lecture 2 : Randomization in Data Structures Jared Saia University of New Mexico Outline Hash Tables Bloom Filters Skip Lists 1 Dictionary ADT A dictionary ADT implements the following operations
CS 561, Lecture 2 : Randomization in Data Structures Jared Saia University of New Mexico Outline Hash Tables Bloom Filters Skip Lists 1 Dictionary ADT A dictionary ADT implements the following operations
The Probabilistic Method
 The Probabilistic Method Po-Shen Loh June 2010 1 Warm-up 1. (Russia 1996/4 In the Duma there are 1600 delegates, who have formed 16000 committees of 80 persons each. Prove that one can find two committees
The Probabilistic Method Po-Shen Loh June 2010 1 Warm-up 1. (Russia 1996/4 In the Duma there are 1600 delegates, who have formed 16000 committees of 80 persons each. Prove that one can find two committees
Recursion: The Beginning
 Department of Computer Science and Engineering Chinese University of Hong Kong This lecture will introduce a useful technique called recursion. If used judiciously, this technique often leads to elegant
Department of Computer Science and Engineering Chinese University of Hong Kong This lecture will introduce a useful technique called recursion. If used judiciously, this technique often leads to elegant
L10: Dictionary & Skip List
 Indian Institute of Science Bangalore, India भ रत य व ज ञ न स स थ न ब गल र, भ रत Department of Computational and Data Sciences DS286 2016-09-14 L10: Dictionary & Skip List Yogesh Simmhan s i m m h a n
Indian Institute of Science Bangalore, India भ रत य व ज ञ न स स थ न ब गल र, भ रत Department of Computational and Data Sciences DS286 2016-09-14 L10: Dictionary & Skip List Yogesh Simmhan s i m m h a n
Skip Lists in Julia. Drew Minnear. Massachusetts Institute of Technology. December 8, 2013
 in Julia Drew Minnear Massachusetts Institute of Technology December 8, 2013 Drew Minnear (MIT) in Julia December 8, 2013 1 / 14 What are? Introduction Randomized data structure invented by William Pugh
in Julia Drew Minnear Massachusetts Institute of Technology December 8, 2013 Drew Minnear (MIT) in Julia December 8, 2013 1 / 14 What are? Introduction Randomized data structure invented by William Pugh
Recursion: The Beginning
 Yufei Tao ITEE University of Queensland This lecture is the inception of a powerful technique called recursion. If used judiciously, this technique can simplify the design of an algorithm significantly,
Yufei Tao ITEE University of Queensland This lecture is the inception of a powerful technique called recursion. If used judiciously, this technique can simplify the design of an algorithm significantly,
CS 350 : Data Structures Skip Lists
 CS 350 : Data Structures Skip Lists David Babcock (courtesy of James Moscola) Department of Physical Sciences York College of Pennsylvania James Moscola Skip List Introduction A data structure used for
CS 350 : Data Structures Skip Lists David Babcock (courtesy of James Moscola) Department of Physical Sciences York College of Pennsylvania James Moscola Skip List Introduction A data structure used for
1 Probability Review. CS 124 Section #8 Hashing, Skip Lists 3/20/17. Expectation (weighted average): the expectation of a random quantity X is:
 CS 124 Section #8 Hashing, Skip Lists 3/20/17 1 Probability Review Expectation (weighted average): the expectation of a random quantity X is: x= x P (X = x) For each value x that X can take on, we look
CS 124 Section #8 Hashing, Skip Lists 3/20/17 1 Probability Review Expectation (weighted average): the expectation of a random quantity X is: x= x P (X = x) For each value x that X can take on, we look
DIVIDE AND CONQUER ALGORITHMS ANALYSIS WITH RECURRENCE EQUATIONS
 CHAPTER 11 SORTING ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY M. AMATO AND
CHAPTER 11 SORTING ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM NANCY M. AMATO AND
Lecture 7. SchemeList, finish up; Universal Hashing introduction
 Lecture 7. SchemeList, finish up; Universal Hashing introduction CS 16 February 24, 2010 1 / 15 foldleft #!/usr/bin/python def foldleft(func, slist, init): foldleft: ( * -> ) * ( SchemeList)
Lecture 7. SchemeList, finish up; Universal Hashing introduction CS 16 February 24, 2010 1 / 15 foldleft #!/usr/bin/python def foldleft(func, slist, init): foldleft: ( * -> ) * ( SchemeList)
Disk Accesses. CS 361, Lecture 25. B-Tree Properties. Outline
 Disk Accesses CS 361, Lecture 25 Jared Saia University of New Mexico Consider any search tree The number of disk accesses per search will dominate the run time Unless the entire tree is in memory, there
Disk Accesses CS 361, Lecture 25 Jared Saia University of New Mexico Consider any search tree The number of disk accesses per search will dominate the run time Unless the entire tree is in memory, there
SORTING, SETS, AND SELECTION
 CHAPTER 11 SORTING, SETS, AND SELECTION ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM
CHAPTER 11 SORTING, SETS, AND SELECTION ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN C++, GOODRICH, TAMASSIA AND MOUNT (WILEY 2004) AND SLIDES FROM
Treaps. 1 Binary Search Trees (BSTs) CSE341T/CSE549T 11/05/2014. Lecture 19
 CSE34T/CSE549T /05/04 Lecture 9 Treaps Binary Search Trees (BSTs) Search trees are tree-based data structures that can be used to store and search for items that satisfy a total order. There are many types
CSE34T/CSE549T /05/04 Lecture 9 Treaps Binary Search Trees (BSTs) Search trees are tree-based data structures that can be used to store and search for items that satisfy a total order. There are many types
Compliments and Disjoint Events
 Compliments and Disjoint Events p. 1/ Compliments and Disjoint Events Gene Quinn Compliments and Disjoint Events p. 2/ Suppose E is an event. Then "E does not occur" is also an event. Compliments and Disjoint
Compliments and Disjoint Events p. 1/ Compliments and Disjoint Events Gene Quinn Compliments and Disjoint Events p. 2/ Suppose E is an event. Then "E does not occur" is also an event. Compliments and Disjoint
Randomized algorithms have several advantages over deterministic ones. We discuss them here:
 CS787: Advanced Algorithms Lecture 6: Randomized Algorithms In this lecture we introduce randomized algorithms. We will begin by motivating the use of randomized algorithms through a few examples. Then
CS787: Advanced Algorithms Lecture 6: Randomized Algorithms In this lecture we introduce randomized algorithms. We will begin by motivating the use of randomized algorithms through a few examples. Then
Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, Merge Sort & Quick Sort
 Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 Merge Sort & Quick Sort 1 Divide-and-Conquer Divide-and conquer is a general algorithm
Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015 Merge Sort & Quick Sort 1 Divide-and-Conquer Divide-and conquer is a general algorithm
COT 3100 Spring 2010 Midterm 2
 COT 3100 Spring 2010 Midterm 2 For the first two questions #1 and #2, do ONLY ONE of them. If you do both, only question #1 will be graded. 1. (20 pts) Give iterative and recursive algorithms for finding
COT 3100 Spring 2010 Midterm 2 For the first two questions #1 and #2, do ONLY ONE of them. If you do both, only question #1 will be graded. 1. (20 pts) Give iterative and recursive algorithms for finding
8. Binary Search Tree
 8 Binary Search Tree Searching Basic Search Sequential Search : Unordered Lists Binary Search : Ordered Lists Tree Search Binary Search Tree Balanced Search Trees (Skipped) Sequential Search int Seq-Search
8 Binary Search Tree Searching Basic Search Sequential Search : Unordered Lists Binary Search : Ordered Lists Tree Search Binary Search Tree Balanced Search Trees (Skipped) Sequential Search int Seq-Search
ECE 122. Engineering Problem Solving Using Java
 ECE 122 Engineering Problem Solving Using Java Lecture 27 Linear and Binary Search Overview Problem: How can I efficiently locate data within a data structure Searching for data is a fundamental function
ECE 122 Engineering Problem Solving Using Java Lecture 27 Linear and Binary Search Overview Problem: How can I efficiently locate data within a data structure Searching for data is a fundamental function
SORTING AND SELECTION
 2 < > 1 4 8 6 = 9 CHAPTER 12 SORTING AND SELECTION ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN JAVA, GOODRICH, TAMASSIA AND GOLDWASSER (WILEY 2016)
2 < > 1 4 8 6 = 9 CHAPTER 12 SORTING AND SELECTION ACKNOWLEDGEMENT: THESE SLIDES ARE ADAPTED FROM SLIDES PROVIDED WITH DATA STRUCTURES AND ALGORITHMS IN JAVA, GOODRICH, TAMASSIA AND GOLDWASSER (WILEY 2016)
Introduction to Randomized Algorithms
 Introduction to Randomized Algorithms Gopinath Mishra Advanced Computing and Microelectronics Unit Indian Statistical Institute Kolkata 700108, India. Organization 1 Introduction 2 Some basic ideas from
Introduction to Randomized Algorithms Gopinath Mishra Advanced Computing and Microelectronics Unit Indian Statistical Institute Kolkata 700108, India. Organization 1 Introduction 2 Some basic ideas from
Randomized Algorithms, Quicksort and Randomized Selection
 CMPS 2200 Fall 2017 Randomized Algorithms, Quicksort and Randomized Selection Carola Wenk Slides by Carola Wenk and Charles Leiserson CMPS 2200 Intro. to Algorithms 1 Deterministic Algorithms Runtime for
CMPS 2200 Fall 2017 Randomized Algorithms, Quicksort and Randomized Selection Carola Wenk Slides by Carola Wenk and Charles Leiserson CMPS 2200 Intro. to Algorithms 1 Deterministic Algorithms Runtime for
Problem Set 4 Solutions
 Design and Analysis of Algorithms March 5, 205 Massachusetts Institute of Technology 6.046J/8.40J Profs. Erik Demaine, Srini Devadas, and Nancy Lynch Problem Set 4 Solutions Problem Set 4 Solutions This
Design and Analysis of Algorithms March 5, 205 Massachusetts Institute of Technology 6.046J/8.40J Profs. Erik Demaine, Srini Devadas, and Nancy Lynch Problem Set 4 Solutions Problem Set 4 Solutions This
COMP 250 Midterm #2 March 11 th 2013
 NAME: STUDENT ID: COMP 250 Midterm #2 March 11 th 2013 - This exam has 6 pages - This is an open book and open notes exam. No electronic equipment is allowed. 1) Questions with short answers (28 points;
NAME: STUDENT ID: COMP 250 Midterm #2 March 11 th 2013 - This exam has 6 pages - This is an open book and open notes exam. No electronic equipment is allowed. 1) Questions with short answers (28 points;
1 Probabilistic analysis and randomized algorithms
 1 Probabilistic analysis and randomized algorithms Consider the problem of hiring an office assistant. We interview candidates on a rolling basis, and at any given point we want to hire the best candidate
1 Probabilistic analysis and randomized algorithms Consider the problem of hiring an office assistant. We interview candidates on a rolling basis, and at any given point we want to hire the best candidate
Dictionaries. 2/17/2006 Dictionaries 1
 Dictionaries < 6 > 1 4 = 8 9 /17/006 Dictionaries 1 Outline and Reading Dictionary ADT ( 9.3) Log file ( 9.3.1) Binary search ( 9.3.3) Lookup table ( 9.3.3) Binary search tree ( 10.1) Search ( 10.1.1)
Dictionaries < 6 > 1 4 = 8 9 /17/006 Dictionaries 1 Outline and Reading Dictionary ADT ( 9.3) Log file ( 9.3.1) Binary search ( 9.3.3) Lookup table ( 9.3.3) Binary search tree ( 10.1) Search ( 10.1.1)
Graph Contraction. Graph Contraction CSE341T/CSE549T 10/20/2014. Lecture 14
 CSE341T/CSE549T 10/20/2014 Lecture 14 Graph Contraction Graph Contraction So far we have mostly talking about standard techniques for solving problems on graphs that were developed in the context of sequential
CSE341T/CSE549T 10/20/2014 Lecture 14 Graph Contraction Graph Contraction So far we have mostly talking about standard techniques for solving problems on graphs that were developed in the context of sequential
: Fundamental Data Structures and Algorithms. June 06, 2011 SOLUTIONS
 15-211 Midterm Exam Summer 2011 Page 1 of 10 15-211 : Fundamental Data Structures and Algorithms June 06, 2011 SOLUIONS 15-211 Midterm Exam Summer 2011 Page 2 of 10 (10) 1. rue/false questions. Clearly
15-211 Midterm Exam Summer 2011 Page 1 of 10 15-211 : Fundamental Data Structures and Algorithms June 06, 2011 SOLUIONS 15-211 Midterm Exam Summer 2011 Page 2 of 10 (10) 1. rue/false questions. Clearly
Minimum-Spanning-Tree problem. Minimum Spanning Trees (Forests) Minimum-Spanning-Tree problem
 Minimum Spanning Trees (Forests) Given an undirected graph G=(V,E) with each edge e having a weight w(e) : Find a subgraph T of G of minimum total weight s.t. every pair of vertices connected in G are
Minimum Spanning Trees (Forests) Given an undirected graph G=(V,E) with each edge e having a weight w(e) : Find a subgraph T of G of minimum total weight s.t. every pair of vertices connected in G are
CSE 100 Disjoint Set, Union Find
 CSE 100 Disjoint Set, Union Find Union-find using up-trees The union-find data structure 1 0 2 6 7 4 3 5 8 Perform these operations: Find(4) =! Find(3) =! Union(1,0)=! Find(4)=! 2 Array representation
CSE 100 Disjoint Set, Union Find Union-find using up-trees The union-find data structure 1 0 2 6 7 4 3 5 8 Perform these operations: Find(4) =! Find(3) =! Union(1,0)=! Find(4)=! 2 Array representation
COMP3121/3821/9101/ s1 Assignment 1
 Sample solutions to assignment 1 1. (a) Describe an O(n log n) algorithm (in the sense of the worst case performance) that, given an array S of n integers and another integer x, determines whether or not
Sample solutions to assignment 1 1. (a) Describe an O(n log n) algorithm (in the sense of the worst case performance) that, given an array S of n integers and another integer x, determines whether or not
Hashing. Yufei Tao. Department of Computer Science and Engineering Chinese University of Hong Kong
 Department of Computer Science and Engineering Chinese University of Hong Kong In this lecture, we will revisit the dictionary search problem, where we want to locate an integer v in a set of size n or
Department of Computer Science and Engineering Chinese University of Hong Kong In this lecture, we will revisit the dictionary search problem, where we want to locate an integer v in a set of size n or
Complexity of Prim s Algorithm
 The main loop is: Complexity of Prim s Algorithm while ( not ISEMPTY(Q) ): u = EXTRACT-MIN(Q) if p[u]!= NIL: A = A U {(p[u],u)} for v in adjacency-list[u]: if v in Q and w(u,v) < priority[v] : DECREASE-PRIORITY(v,
The main loop is: Complexity of Prim s Algorithm while ( not ISEMPTY(Q) ): u = EXTRACT-MIN(Q) if p[u]!= NIL: A = A U {(p[u],u)} for v in adjacency-list[u]: if v in Q and w(u,v) < priority[v] : DECREASE-PRIORITY(v,
CS 561, Lecture 2 : Hash Tables, Skip Lists, Bloom Filters, Count-Min sketch. Jared Saia University of New Mexico
 CS 561, Lecture 2 : Hash Tables, Skip Lists, Bloom Filters, Count-Min sketch Jared Saia University of New Mexico Outline Hash Tables Skip Lists Count-Min Sketch 1 Dictionary ADT A dictionary ADT implements
CS 561, Lecture 2 : Hash Tables, Skip Lists, Bloom Filters, Count-Min sketch Jared Saia University of New Mexico Outline Hash Tables Skip Lists Count-Min Sketch 1 Dictionary ADT A dictionary ADT implements
SORTING LOWER BOUND & BUCKET-SORT AND RADIX-SORT
 Bucket-Sort and Radix-Sort SORTING LOWER BOUND & BUCKET-SORT AND RADIX-SORT 1, c 3, a 3, b 7, d 7, g 7, e B 0 1 2 3 4 5 6 7 8 9 Presentation for use with the textbook Data Structures and Algorithms in
Bucket-Sort and Radix-Sort SORTING LOWER BOUND & BUCKET-SORT AND RADIX-SORT 1, c 3, a 3, b 7, d 7, g 7, e B 0 1 2 3 4 5 6 7 8 9 Presentation for use with the textbook Data Structures and Algorithms in
On Biased Reservoir Sampling in the Presence of Stream Evolution
 Charu C. Aggarwal T J Watson Research Center IBM Corporation Hawthorne, NY USA On Biased Reservoir Sampling in the Presence of Stream Evolution VLDB Conference, Seoul, South Korea, 2006 Synopsis Construction
Charu C. Aggarwal T J Watson Research Center IBM Corporation Hawthorne, NY USA On Biased Reservoir Sampling in the Presence of Stream Evolution VLDB Conference, Seoul, South Korea, 2006 Synopsis Construction
Chapter 2: Basic Data Structures
 Chapter 2: Basic Data Structures Basic Data Structures Stacks Queues Vectors, Linked Lists Trees (Including Balanced Trees) Priority Queues and Heaps Dictionaries and Hash Tables Spring 2014 CS 315 2 Two
Chapter 2: Basic Data Structures Basic Data Structures Stacks Queues Vectors, Linked Lists Trees (Including Balanced Trees) Priority Queues and Heaps Dictionaries and Hash Tables Spring 2014 CS 315 2 Two
Approximation Algorithms
 Approximation Algorithms Frédéric Giroire FG Simplex 1/11 Motivation Goal: Find good solutions for difficult problems (NP-hard). Be able to quantify the goodness of the given solution. Presentation of
Approximation Algorithms Frédéric Giroire FG Simplex 1/11 Motivation Goal: Find good solutions for difficult problems (NP-hard). Be able to quantify the goodness of the given solution. Presentation of
CSE373 Fall 2013, Midterm Examination October 18, 2013
 CSE373 Fall 2013, Midterm Examination October 18, 2013 Please do not turn the page until the bell rings. Rules: The exam is closed-book, closed-note, closed calculator, closed electronics. Please stop
CSE373 Fall 2013, Midterm Examination October 18, 2013 Please do not turn the page until the bell rings. Rules: The exam is closed-book, closed-note, closed calculator, closed electronics. Please stop
Sorting. Outline. Sorting with a priority queue Selection-sort Insertion-sort Heap Sort Quick Sort
 Sorting Hiroaki Kobayashi 1 Outline Sorting with a priority queue Selection-sort Insertion-sort Heap Sort Quick Sort Merge Sort Lower Bound on Comparison-Based Sorting Bucket Sort and Radix Sort Hiroaki
Sorting Hiroaki Kobayashi 1 Outline Sorting with a priority queue Selection-sort Insertion-sort Heap Sort Quick Sort Merge Sort Lower Bound on Comparison-Based Sorting Bucket Sort and Radix Sort Hiroaki
9.2 Hash Tables. When implementing a map with a hash table, the goal is to store item (k, e) at index i = h(k)
 9.2 Hash Tables A hash function h() maps keys of a given type to integers in a fixed interval [0, N - 1] Example: h(x) = x mod N is a hash function for integer keys The integer h(x) is called the hash
9.2 Hash Tables A hash function h() maps keys of a given type to integers in a fixed interval [0, N - 1] Example: h(x) = x mod N is a hash function for integer keys The integer h(x) is called the hash
Data Structures. Department of Computer Science. Brown University. 115 Waterman Street. Providence, RI 02912{1910.
 Data Structures Roberto Tamassia Bryan Cantrill Department of Computer Science Brown University 115 Waterman Street Providence, RI 02912{1910 frt,bmcg@cs.brown.edu January 27, 1996 Revised version for
Data Structures Roberto Tamassia Bryan Cantrill Department of Computer Science Brown University 115 Waterman Street Providence, RI 02912{1910 frt,bmcg@cs.brown.edu January 27, 1996 Revised version for
CS 234. Module 8. November 15, CS 234 Module 8 ADT Priority Queue 1 / 22
 CS 234 Module 8 November 15, 2018 CS 234 Module 8 ADT Priority Queue 1 / 22 ADT Priority Queue Data: (key, element pairs) where keys are orderable but not necessarily distinct, and elements are any data.
CS 234 Module 8 November 15, 2018 CS 234 Module 8 ADT Priority Queue 1 / 22 ADT Priority Queue Data: (key, element pairs) where keys are orderable but not necessarily distinct, and elements are any data.
Binary Search Trees > = 2014 Goodrich, Tamassia, Goldwasser. Binary Search Trees 1
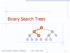 Binary Search Trees < > = Binary Search Trees 1 Ordered Dictionary (Map) ADT get (k): record with key k put (k,data): add record (k,data) remove (k): delete record with key k smallest(): record with smallest
Binary Search Trees < > = Binary Search Trees 1 Ordered Dictionary (Map) ADT get (k): record with key k put (k,data): add record (k,data) remove (k): delete record with key k smallest(): record with smallest
Problem Set 5 Solutions
 Design and Analysis of Algorithms?? Massachusetts Institute of Technology 6.046J/18.410J Profs. Erik Demaine, Srini Devadas, and Nancy Lynch Problem Set 5 Solutions Problem Set 5 Solutions This problem
Design and Analysis of Algorithms?? Massachusetts Institute of Technology 6.046J/18.410J Profs. Erik Demaine, Srini Devadas, and Nancy Lynch Problem Set 5 Solutions Problem Set 5 Solutions This problem
Figure 1: An example of a hypercube 1: Given that the source and destination addresses are n-bit vectors, consider the following simple choice of rout
 Tail Inequalities Wafi AlBalawi and Ashraf Osman Department of Computer Science and Electrical Engineering, West Virginia University, Morgantown, WV fwafi,osman@csee.wvu.edug 1 Routing in a Parallel Computer
Tail Inequalities Wafi AlBalawi and Ashraf Osman Department of Computer Science and Electrical Engineering, West Virginia University, Morgantown, WV fwafi,osman@csee.wvu.edug 1 Routing in a Parallel Computer
CS 151 Complexity Theory Spring Final Solutions. L i NL i NC 2i P.
 CS 151 Complexity Theory Spring 2017 Posted: June 9 Final Solutions Chris Umans 1. (a) The procedure that traverses a fan-in 2 depth O(log i n) circuit and outputs a formula runs in L i this can be done
CS 151 Complexity Theory Spring 2017 Posted: June 9 Final Solutions Chris Umans 1. (a) The procedure that traverses a fan-in 2 depth O(log i n) circuit and outputs a formula runs in L i this can be done
1 Unweighted Set Cover
 Comp 60: Advanced Algorithms Tufts University, Spring 018 Prof. Lenore Cowen Scribe: Yuelin Liu Lecture 7: Approximation Algorithms: Set Cover and Max Cut 1 Unweighted Set Cover 1.1 Formulations There
Comp 60: Advanced Algorithms Tufts University, Spring 018 Prof. Lenore Cowen Scribe: Yuelin Liu Lecture 7: Approximation Algorithms: Set Cover and Max Cut 1 Unweighted Set Cover 1.1 Formulations There
CSE 131S Introduction to Computer Science Summer SON Exam III
 CSE 131S Introduction to Computer Science Summer SON 2014 Given: 6 August 2014 Exam III Due: 90 minutes after starting This exam is closed-book, closed-notes, no electronic devices allowed except for downloading
CSE 131S Introduction to Computer Science Summer SON 2014 Given: 6 August 2014 Exam III Due: 90 minutes after starting This exam is closed-book, closed-notes, no electronic devices allowed except for downloading
Sorting. Data structures and Algorithms
 Sorting Data structures and Algorithms Acknowledgement: These slides are adapted from slides provided with Data Structures and Algorithms in C++ Goodrich, Tamassia and Mount (Wiley, 2004) Outline Bubble
Sorting Data structures and Algorithms Acknowledgement: These slides are adapted from slides provided with Data Structures and Algorithms in C++ Goodrich, Tamassia and Mount (Wiley, 2004) Outline Bubble
Dr. Amotz Bar-Noy s Compendium of Algorithms Problems. Problems, Hints, and Solutions
 Dr. Amotz Bar-Noy s Compendium of Algorithms Problems Problems, Hints, and Solutions Chapter 1 Searching and Sorting Problems 1 1.1 Array with One Missing 1.1.1 Problem Let A = A[1],..., A[n] be an array
Dr. Amotz Bar-Noy s Compendium of Algorithms Problems Problems, Hints, and Solutions Chapter 1 Searching and Sorting Problems 1 1.1 Array with One Missing 1.1.1 Problem Let A = A[1],..., A[n] be an array
Geometric Algorithms and Data Structures. Part II: Scan-Line Algorithms and Planar Decompositions. Jim Fix
 Geometric Algorithms and Data Structures Part II: Scan-Line Algorithms and Planar Decompositions Jim Fix Intersecting segments Input: Set of n line segments S = {s 0,... s n 1 } in R 2. Output: Set of
Geometric Algorithms and Data Structures Part II: Scan-Line Algorithms and Planar Decompositions Jim Fix Intersecting segments Input: Set of n line segments S = {s 0,... s n 1 } in R 2. Output: Set of
Operations on Heap Tree The major operations required to be performed on a heap tree are Insertion, Deletion, and Merging.
 Priority Queue, Heap and Heap Sort In this time, we will study Priority queue, heap and heap sort. Heap is a data structure, which permits one to insert elements into a set and also to find the largest
Priority Queue, Heap and Heap Sort In this time, we will study Priority queue, heap and heap sort. Heap is a data structure, which permits one to insert elements into a set and also to find the largest
CS 315 Data Structures mid-term 2
 CS 315 Data Structures mid-term 2 1) Shown below is an AVL tree T. Nov 14, 2012 Solutions to OPEN BOOK section. (a) Suggest a key whose insertion does not require any rotation. 18 (b) Suggest a key, if
CS 315 Data Structures mid-term 2 1) Shown below is an AVL tree T. Nov 14, 2012 Solutions to OPEN BOOK section. (a) Suggest a key whose insertion does not require any rotation. 18 (b) Suggest a key, if
Lec 17 April 8. Topics: binary Trees expression trees. (Chapter 5 of text)
 Lec 17 April 8 Topics: binary Trees expression trees Binary Search Trees (Chapter 5 of text) Trees Linear access time of linked lists is prohibitive Heap can t support search in O(log N) time. (takes O(N)
Lec 17 April 8 Topics: binary Trees expression trees Binary Search Trees (Chapter 5 of text) Trees Linear access time of linked lists is prohibitive Heap can t support search in O(log N) time. (takes O(N)
Fast Sorting and Selection. A Lower Bound for Worst Case
 Lists and Iterators 0//06 Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 0 Fast Sorting and Selection USGS NEIC. Public domain government
Lists and Iterators 0//06 Presentation for use with the textbook, Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 0 Fast Sorting and Selection USGS NEIC. Public domain government
Analyze the work and depth of this algorithm. These should both be given with high probability bounds.
 CME 323: Distributed Algorithms and Optimization Instructor: Reza Zadeh (rezab@stanford.edu) TA: Yokila Arora (yarora@stanford.edu) HW#2 Solution 1. List Prefix Sums As described in class, List Prefix
CME 323: Distributed Algorithms and Optimization Instructor: Reza Zadeh (rezab@stanford.edu) TA: Yokila Arora (yarora@stanford.edu) HW#2 Solution 1. List Prefix Sums As described in class, List Prefix
Fractional Cascading
 C.S. 252 Prof. Roberto Tamassia Computational Geometry Sem. II, 1992 1993 Lecture 11 Scribe: Darren Erik Vengroff Date: March 15, 1993 Fractional Cascading 1 Introduction Fractional cascading is a data
C.S. 252 Prof. Roberto Tamassia Computational Geometry Sem. II, 1992 1993 Lecture 11 Scribe: Darren Erik Vengroff Date: March 15, 1993 Fractional Cascading 1 Introduction Fractional cascading is a data
Binary Search Trees (10.1) Dictionary ADT (9.5.1)
 Binary Search Trees (10.1) CSE 011 Winter 011 4 March 011 1 Dictionary ADT (..1) The dictionary ADT models a searchable collection of keyelement items The main operations of a dictionary are searching,
Binary Search Trees (10.1) CSE 011 Winter 011 4 March 011 1 Dictionary ADT (..1) The dictionary ADT models a searchable collection of keyelement items The main operations of a dictionary are searching,
CSE638: Advanced Algorithms, Spring 2013 Date: March 26. Homework #2. ( Due: April 16 )
 CSE638: Advanced Algorithms, Spring 2013 Date: March 26 Homework #2 ( Due: April 16 ) Task 1. [ 40 Points ] Parallel BFS with Cilk s Work Stealing. (a) [ 20 Points ] In homework 1 we analyzed and implemented
CSE638: Advanced Algorithms, Spring 2013 Date: March 26 Homework #2 ( Due: April 16 ) Task 1. [ 40 Points ] Parallel BFS with Cilk s Work Stealing. (a) [ 20 Points ] In homework 1 we analyzed and implemented
(2,4) Trees. 2/22/2006 (2,4) Trees 1
 (2,4) Trees 9 2 5 7 10 14 2/22/2006 (2,4) Trees 1 Outline and Reading Multi-way search tree ( 10.4.1) Definition Search (2,4) tree ( 10.4.2) Definition Search Insertion Deletion Comparison of dictionary
(2,4) Trees 9 2 5 7 10 14 2/22/2006 (2,4) Trees 1 Outline and Reading Multi-way search tree ( 10.4.1) Definition Search (2,4) tree ( 10.4.2) Definition Search Insertion Deletion Comparison of dictionary
Search Trees (Ch. 9) > = Binary Search Trees 1
 Search Trees (Ch. 9) < 6 > = 1 4 8 9 Binary Search Trees 1 Ordered Dictionaries Keys are assumed to come from a total order. New operations: closestbefore(k) closestafter(k) Binary Search Trees Binary
Search Trees (Ch. 9) < 6 > = 1 4 8 9 Binary Search Trees 1 Ordered Dictionaries Keys are assumed to come from a total order. New operations: closestbefore(k) closestafter(k) Binary Search Trees Binary
Predictive Analysis: Evaluation and Experimentation. Heejun Kim
 Predictive Analysis: Evaluation and Experimentation Heejun Kim June 19, 2018 Evaluation and Experimentation Evaluation Metrics Cross-Validation Significance Tests Evaluation Predictive analysis: training
Predictive Analysis: Evaluation and Experimentation Heejun Kim June 19, 2018 Evaluation and Experimentation Evaluation Metrics Cross-Validation Significance Tests Evaluation Predictive analysis: training
1. The Sets ADT. 1. The Sets ADT. 1. The Sets ADT 11/22/2011. Class Assignment Set in STL
 1. Sets 2. Sorting 1. The Sets ADT A set is a container of distinct objects. no duplicate no notation of key, or order. The operation of the set ADT: union: A B = {x:x A or x B} intersection: A B = {x:x
1. Sets 2. Sorting 1. The Sets ADT A set is a container of distinct objects. no duplicate no notation of key, or order. The operation of the set ADT: union: A B = {x:x A or x B} intersection: A B = {x:x
CSE 100: GRAPH ALGORITHMS
 CSE 100: GRAPH ALGORITHMS Dijkstra s Algorithm: Questions Initialize the graph: Give all vertices a dist of INFINITY, set all done flags to false Start at s; give s dist = 0 and set prev field to -1 Enqueue
CSE 100: GRAPH ALGORITHMS Dijkstra s Algorithm: Questions Initialize the graph: Give all vertices a dist of INFINITY, set all done flags to false Start at s; give s dist = 0 and set prev field to -1 Enqueue
CSE 613: Parallel Programming. Lecture 6 ( Basic Parallel Algorithmic Techniques )
 CSE 613: Parallel Programming Lecture 6 ( Basic Parallel Algorithmic Techniques ) Rezaul A. Chowdhury Department of Computer Science SUNY Stony Brook Spring 2017 Some Basic Techniques 1. Divide-and-Conquer
CSE 613: Parallel Programming Lecture 6 ( Basic Parallel Algorithmic Techniques ) Rezaul A. Chowdhury Department of Computer Science SUNY Stony Brook Spring 2017 Some Basic Techniques 1. Divide-and-Conquer
Sorting. Divide-and-Conquer 1
 Sorting Divide-and-Conquer 1 Divide-and-Conquer 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9 7 7 2 2 9 9 4 4 Divide-and-Conquer 2 Divide-and-Conquer Divide-and conquer is a general algorithm design paradigm: Divide:
Sorting Divide-and-Conquer 1 Divide-and-Conquer 7 2 9 4 2 4 7 9 7 2 2 7 9 4 4 9 7 7 2 2 9 9 4 4 Divide-and-Conquer 2 Divide-and-Conquer Divide-and conquer is a general algorithm design paradigm: Divide:
CSE 638: Advanced Algorithms. Lectures 10 & 11 ( Parallel Connected Components )
 CSE 6: Advanced Algorithms Lectures & ( Parallel Connected Components ) Rezaul A. Chowdhury Department of Computer Science SUNY Stony Brook Spring 01 Symmetry Breaking: List Ranking break symmetry: t h
CSE 6: Advanced Algorithms Lectures & ( Parallel Connected Components ) Rezaul A. Chowdhury Department of Computer Science SUNY Stony Brook Spring 01 Symmetry Breaking: List Ranking break symmetry: t h
Comp2402: Review Questions
 Comp2402: Review Questions 1: JCF & Big-Oh 1.1 Big-Oh Notation 1. What is O(n)? What kind of object is it? 2. What does the statement 2n + 3 = O(n 2 ) mean? 3. Recall the basic big-o hierarchy: for any
Comp2402: Review Questions 1: JCF & Big-Oh 1.1 Big-Oh Notation 1. What is O(n)? What kind of object is it? 2. What does the statement 2n + 3 = O(n 2 ) mean? 3. Recall the basic big-o hierarchy: for any
Binary Search Trees Treesort
 Treesort CS 311 Data Structures and Algorithms Lecture Slides Friday, November 13, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks CHAPPELLG@member.ams.org 2005 2009
Treesort CS 311 Data Structures and Algorithms Lecture Slides Friday, November 13, 2009 Glenn G. Chappell Department of Computer Science University of Alaska Fairbanks CHAPPELLG@member.ams.org 2005 2009
SEARCHING, SORTING, AND ASYMPTOTIC COMPLEXITY. Lecture 11 CS2110 Spring 2016
 1 SEARCHING, SORTING, AND ASYMPTOTIC COMPLEXITY Lecture 11 CS2110 Spring 2016 Time spent on A2 2 Histogram: [inclusive:exclusive) [0:1): 0 [1:2): 24 ***** [2:3): 84 ***************** [3:4): 123 *************************
1 SEARCHING, SORTING, AND ASYMPTOTIC COMPLEXITY Lecture 11 CS2110 Spring 2016 Time spent on A2 2 Histogram: [inclusive:exclusive) [0:1): 0 [1:2): 24 ***** [2:3): 84 ***************** [3:4): 123 *************************
CPSC 536N: Randomized Algorithms Term 2. Lecture 4
 CPSC 536N: Randomized Algorithms 2011-12 Term 2 Prof. Nick Harvey Lecture 4 University of British Columbia In today s lecture we will see two applications of negative binomially distributed random variables.
CPSC 536N: Randomized Algorithms 2011-12 Term 2 Prof. Nick Harvey Lecture 4 University of British Columbia In today s lecture we will see two applications of negative binomially distributed random variables.
QuickSort
 QuickSort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 1 QuickSort QuickSort on an input sequence S with n elements consists of three steps: n n n Divide: partition S into two sequences S 1 and S 2 of about
QuickSort 7 4 9 6 2 2 4 6 7 9 4 2 2 4 7 9 7 9 2 2 9 9 1 QuickSort QuickSort on an input sequence S with n elements consists of three steps: n n n Divide: partition S into two sequences S 1 and S 2 of about
Comparison Sorts. Chapter 9.4, 12.1, 12.2
 Comparison Sorts Chapter 9.4, 12.1, 12.2 Sorting We have seen the advantage of sorted data representations for a number of applications Sparse vectors Maps Dictionaries Here we consider the problem of
Comparison Sorts Chapter 9.4, 12.1, 12.2 Sorting We have seen the advantage of sorted data representations for a number of applications Sparse vectors Maps Dictionaries Here we consider the problem of
Chapter 10: Search Trees
 < 6 > 1 4 = 8 9 Chapter 10: Search Trees Nancy Amato Parasol Lab, Dept. CSE, Texas A&M University Acknowledgement: These slides are adapted from slides provided with Data Structures and Algorithms in C++,
< 6 > 1 4 = 8 9 Chapter 10: Search Trees Nancy Amato Parasol Lab, Dept. CSE, Texas A&M University Acknowledgement: These slides are adapted from slides provided with Data Structures and Algorithms in C++,
Heap-on-Top Priority Queues. March Abstract. We introduce the heap-on-top (hot) priority queue data structure that combines the
 Heap-on-Top Priority Queues Boris V. Cherkassky Central Economics and Mathematics Institute Krasikova St. 32 117418, Moscow, Russia cher@cemi.msk.su Andrew V. Goldberg NEC Research Institute 4 Independence
Heap-on-Top Priority Queues Boris V. Cherkassky Central Economics and Mathematics Institute Krasikova St. 32 117418, Moscow, Russia cher@cemi.msk.su Andrew V. Goldberg NEC Research Institute 4 Independence
CSE373: Data Structures & Algorithms Lecture 11: Implementing Union-Find. Lauren Milne Spring 2015
 CSE: Data Structures & Algorithms Lecture : Implementing Union-Find Lauren Milne Spring 05 Announcements Homework due in ONE week Wednesday April 9 th! TA sessions Catie will be back on Monday. The plan
CSE: Data Structures & Algorithms Lecture : Implementing Union-Find Lauren Milne Spring 05 Announcements Homework due in ONE week Wednesday April 9 th! TA sessions Catie will be back on Monday. The plan
Insertion Sort: an algorithm for sorting an array
 Insertion Sort: an algorithm for sorting an array Let s use arrays to solve a problem that comes up often in programming, namely sorting. Suppose we have an array of objects that is in no particular order
Insertion Sort: an algorithm for sorting an array Let s use arrays to solve a problem that comes up often in programming, namely sorting. Suppose we have an array of objects that is in no particular order
Question And Answer.
 Q.1 What is the number of swaps required to sort n elements using selection sort, in the worst case? A. Θ(n) B. Θ(n log n) C. Θ(n2) D. Θ(n2 log n) ANSWER : Option A Θ(n) Note that we
Q.1 What is the number of swaps required to sort n elements using selection sort, in the worst case? A. Θ(n) B. Θ(n log n) C. Θ(n2) D. Θ(n2 log n) ANSWER : Option A Θ(n) Note that we
Today s outline: pp
 Chapter 3 sections We will SKIP a number of sections Random variables and discrete distributions Continuous distributions The cumulative distribution function Bivariate distributions Marginal distributions
Chapter 3 sections We will SKIP a number of sections Random variables and discrete distributions Continuous distributions The cumulative distribution function Bivariate distributions Marginal distributions
Lecture 7. Random number generation More randomized data structures Skip lists: ideas and implementation Skip list time costs
 Lecture 7 Random number generation More randomized data structures Skip lists: ideas and implementation Skip list time costs Reading: Skip Lists: A Probabilistic Alternative to Balanced Trees paper (Pugh);
Lecture 7 Random number generation More randomized data structures Skip lists: ideas and implementation Skip list time costs Reading: Skip Lists: A Probabilistic Alternative to Balanced Trees paper (Pugh);
COMP Data Structures
 COMP 2140 - Data Structures Shahin Kamali Topic 5 - Sorting University of Manitoba Based on notes by S. Durocher. COMP 2140 - Data Structures 1 / 55 Overview Review: Insertion Sort Merge Sort Quicksort
COMP 2140 - Data Structures Shahin Kamali Topic 5 - Sorting University of Manitoba Based on notes by S. Durocher. COMP 2140 - Data Structures 1 / 55 Overview Review: Insertion Sort Merge Sort Quicksort
Chapter 9: Maps, Dictionaries, Hashing
 Chapter 9: 0 1 025-612-0001 2 981-101-0002 3 4 451-229-0004 Maps, Dictionaries, Hashing Nancy Amato Parasol Lab, Dept. CSE, Texas A&M University Acknowledgement: These slides are adapted from slides provided
Chapter 9: 0 1 025-612-0001 2 981-101-0002 3 4 451-229-0004 Maps, Dictionaries, Hashing Nancy Amato Parasol Lab, Dept. CSE, Texas A&M University Acknowledgement: These slides are adapted from slides provided
