FORMULATION OF INFORMATION SYSTEMS (IS) STRATEGY
|
|
|
- Erika Clark
- 6 years ago
- Views:
Transcription
1 FORMULATION OF INFORMATION SYSTEMS (IS) STRATEGY 1
2 IS Dev t Strategy Formulation Generate & direct resources to develop ISs that serve the shared goals of the organization Tells where you are going in IS development and how to get there
3 What is an Information System a collection of procedures, activities, people and technology, set up for the collection and storage of data and its processing to produce information for communication to people who need to act upon it. 2/18/14 3
4 System Model FEEDBACK /CONTROL INPUT OUTPUT PROCESS 2/18/14 4
5 Why We Need Information to effectively & efficiently perform one s job to assist decision-making activities to know options available to us. 2/18/14 5
6 Types of Information System Office Automation Systems (OAS) - support clerical and other common office tasks v Word Processing v Electronic Spreadsheet v Desktop Publishing v Presentation v 2/18/14 6
7 Types of Information System Mission-Critical Information Systems - support client-driven transactions or operations for the delivery of MFOs v Philippine Business Registry v Philippine Health Information Exchange v e-filing and Payment System 2/18/14 7
8 Types of Information System Support to Operations (STO) Systems - support planning, policy development, monitoring, coordination and secretarial tasks v Performance Monitoring System v Project Monitoring System v Planning Information System 2/18/14 8
9 Types of Information System General Admin and Support Services (GASS) Systems - support tasks related to finance, assets, personnel, legal, procurement v Document Tracking System v Financial Management Info System v Records Management System v Inventory System 2/18/14 9
10 Purpose of IS Strategy Identify the ISs Set IS priorities Describe the IS and their linkages (Conceptual Framework) Map out the approach to IS development. 2/18/14 10
11 Steps in IS Strategy Formulation 1. Identify and Rank the ISs 4. Describe the IS Dev t Strategy 2. Design the Conceptual Framework 5. Present the Computing Scheme 3. Describe the ISs and their Status 6. Describe the Linkages
12 1. Identification of IS ü Identify KEY PROCESSES in the Strategic Concerns for ICT Use (Part I.E p.6) ü Identify ACTIVITIES linked with or supporting key processes (Subsystems) ü Look for the possibility of merging processes/ activities dealing with similar data (Data-based IS) ü Provide a descriptive name for the IS 2/18/14 12
13 Identification of IS HR MGMT & DEVT Selection, Hiring, Training, Payroll, etc. FINANCIAL MGMT Budgeting, Accounting, etc. SUPPLIES & PROPERTY MGMT Canvassing, Procurement, Disposal, etc RESOURCE MANAGEMENT INFORMATION SYSTEM
14 Identification of IS HR MGMT & DEVT Selection, Hiring, Training, etc. FINANCIAL MGMT Budgeting, Accounting, etc. SUPPLIES & PROPERTY MGMT Canvassing, Procurement, Disposal, etc ADMIN SERVICES Maintenance, Security & Janitorial Services, Records Mgmt.
15 Identification of IS HR MGMT & DEVT Selection, Hiring, Training, etc. FINANCIAL MGMT Budgeting, Accounting, etc. SUPPLIES & PROPERTY MGMT Canvassing, Procurement, Disposal, etc ADMIN SERVICES Maintenance, Security & Janitorial Services, Records Mgmt. GENERAL ADMINISTRATIVE & SUPPPORT SERVICES INFORMATION SYSTEM
16 2. Design the Conceptual Framework ü Present the general design of the ISs showing subsystems if any sources and recipient of data databases to be used linkages ü use symbols to represent the ff: ISs and sub-systems - circle or rounded-edge square data sources and recipients databases - cylinder linkages arrows 2/18/14 16
17 3. Description and Status of ISs ü Describe each ISs in terms of: v performance indicator/s in relation to relevant MFOs v salient features v major information generated ü State status of proposed ISs if: v for development v for enhancement 2/18/14 17
18 4. IS Development Strategy ü Describe how each IS is developed: v in-house v outsourcing/contracting v combination of in-house & outsourcing v purchase of off-the-shelf packages v grant/donations from other organizations 2/18/14 18
19 5. Computing Scheme Two big classifications of computing scheme: v Stand-alone or independent systems v Networked systems. 2/18/14 19
20 Stand-alone/Independent Systems a computer system, by itself, operates or process an application system or IS operating system, application program and database are resident in the same computer.
21 Illustration of stand-alone system
22 Networked Systems the linking of computers, printers and other devices so that users can exchange and share information and resources.
23 Networked Systems Two types : Local Area Networking (LAN) - confined to moderate sized geographic areas such as one office, building, warehouse or campus. Wide Area Networking (WAN) - usually consisting of a series of complex packet switches interconnected by communication lines.
24 Network Computing Schemes Network computing can be : Centralized Distributed Centralized-Distributed
25 Centralized ü one site supplying all information processing ü information is integrated at one location ü resources and control are integrated at one location.
26 Centralized LAN Workstation Printer Servers Workstation Department A Department B Department C
27 Distributed System ü more than one site supplying information processing ü different information are integrated at different locations ü resources and control are integrated at different locations. ü a popular example is cloud computing, which allows a large number of computing devices to run a program or application through a real time network such as the Internet
28 Distributed System Workstation Printer Server Server Workstation Department A Department B Department C
29 Centralized-Distributed ü more than one site supplying information processing, but connected in a single server ü different network information are integrated at one location.
30 Centralized-Distributed Workstation Server Printer Server Workstation Department A Department B Department C
31 6. IS Inter-linkages ü Describe each IS in terms of : v system owner v users, both internal and external 2/18/14 31
32 What is a Database? ü Organized collection of data for storing, managing and retrieving information. ü Supports processes requiring information as output 2/18/14 32
33 Material/s needed: EXERCISE ü Accomplished Part I.E Strategic Concerns for ICT Use ü Diagram of Existing ISs Interface ü Annex A-2 ü Annex A-5 ICT Inventory ü Annex A-4 ü Diagram of Existing Network Layout ü Problem ID Facilitative worksheet 2/18/14 33
34 EXERCISE ü Instruction for Identification of IS: ü For each MFO/business process or critical business systems in column 1 and column 2 respectively, of your Part I.E, is there an existing information system that facilitates the delivery of that MFO or business activity? ü If yes, did the user complain of problems? Will it be solved by enhancing the existing system/s? ü If no IS exist, what information system would you propose? ü The name of the IS should be descriptive of the functional area or service for which it is intended. 2/18/14 34
35 EXERCISE Instruction for PART II.C DATABASES REQUIRED : ü ü ü ü ü ü Based on PART II.B, for each identified ISs where you have stated the major information to be generated, will there be data needed to generate said major information? If yes, what are the data needed? Write them under the General Contents/Description of table in Part II.C If there are data that have been repeatedly identified by several ISs, then a single database can serve them. STATUS If none yet exists, then write to be built-up. If there is an existing database but you plan to convert it then write for conversion. However, if you plan to migrate to another platform, then write for migration. INFORMATION SYSTEMS SERVED What is/are the ISs that will make use of the database? DATA ARCHIVING STRATEGY How will you store the data for processing? 2/18/14 35
36 EXERCISE Instruction for PART II.D NETWORK LAYOUT: ü Based on Facilitative worksheet, PART II.A to PART II.C, you can now assess the existing network layout to see if the additional requirements can be absorbed by the current network resources. If not, draw the logical layout that will support your proposed ISs, databases, computing scheme. See Annex A-4. However, for capacity requirements and HW needed including configuration, it will be defined in Part IV. Resource Requirements. You can then refine your network diagram. 2/18/14 36
Federal Data Center Consolidation Initiative (FDCCI) Workshop I: Initial Data Center Consolidation Plan
 Federal Data Center Consolidation Initiative (FDCCI) Workshop I: Initial Data Center Consolidation Plan June 04, 2010 FDCCI Workshop I Agenda for June 4, 2010 1. Welcome Katie Lewin GSA Director Cloud
Federal Data Center Consolidation Initiative (FDCCI) Workshop I: Initial Data Center Consolidation Plan June 04, 2010 FDCCI Workshop I Agenda for June 4, 2010 1. Welcome Katie Lewin GSA Director Cloud
Federal Data Center Consolidation Initiative (FDCCI) Workshop III: Final Data Center Consolidation Plan
 Federal Data Center Consolidation Initiative (FDCCI) Workshop III: Final Data Center Consolidation Plan August 10, 2010 FDCCI Agenda August 10 th, 2010 1. Welcome Katie Lewin GSA Director Cloud Computing
Federal Data Center Consolidation Initiative (FDCCI) Workshop III: Final Data Center Consolidation Plan August 10, 2010 FDCCI Agenda August 10 th, 2010 1. Welcome Katie Lewin GSA Director Cloud Computing
Geog 469 GIS Workshop. System Requirements - Data
 Geog 469 GIS Workshop System Requirements - Data Outline 1. What are some principles of project management? 2. What are some fundamental issues associated with system requirements? 3. What are some issues
Geog 469 GIS Workshop System Requirements - Data Outline 1. What are some principles of project management? 2. What are some fundamental issues associated with system requirements? 3. What are some issues
SOFTWARE ENGINEERING : A MCQ BOOK CODE : RBMCQ0602. Second Edition
 SOFTWARE ENGINEERING : A MCQ BOOK CODE : RBMCQ0602 Second Edition S/W Engg. Fundamental 1) Which phase of the SDLC are information needs identified? A. preliminary investigation B. system analysis C. system
SOFTWARE ENGINEERING : A MCQ BOOK CODE : RBMCQ0602 Second Edition S/W Engg. Fundamental 1) Which phase of the SDLC are information needs identified? A. preliminary investigation B. system analysis C. system
STUDENT GUIDE Risk Management Framework Step 1: Categorization of the Information System
 Slide 1 RMF Overview RMF Module 1 RMF takes into account the organization as a whole, including strategic goals and objectives and relationships between mission/business processes, the supporting information
Slide 1 RMF Overview RMF Module 1 RMF takes into account the organization as a whole, including strategic goals and objectives and relationships between mission/business processes, the supporting information
E-DISCOVERY PRESENTATION E-DISCOVERY 101: BASICS
 E-DISCOVERY PRESENTATION E-DISCOVERY 101: BASICS Agenda E-discovery Legal Issues Elements of a Litigation Hold Identification and Data Mapping of ESI Preservation and Collection Early Case Assessment Processing
E-DISCOVERY PRESENTATION E-DISCOVERY 101: BASICS Agenda E-discovery Legal Issues Elements of a Litigation Hold Identification and Data Mapping of ESI Preservation and Collection Early Case Assessment Processing
ROLE DESCRIPTION IT SPECIALIST
 ROLE DESCRIPTION IT SPECIALIST JOB IDENTIFICATION Job Title: Job Grade: Department: Location Reporting Line (This structure reports to?) Full-time/Part-time/Contract: IT Specialist D1 Finance INSETA Head
ROLE DESCRIPTION IT SPECIALIST JOB IDENTIFICATION Job Title: Job Grade: Department: Location Reporting Line (This structure reports to?) Full-time/Part-time/Contract: IT Specialist D1 Finance INSETA Head
WELCOME TO MUNIS 11.2
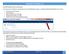 The MUNIS dashboard opens as a blank page. Your Munis User ID will appear in the right hand corner of the dashboard home page. To change the dashboard identification to your name: Click the arrow next
The MUNIS dashboard opens as a blank page. Your Munis User ID will appear in the right hand corner of the dashboard home page. To change the dashboard identification to your name: Click the arrow next
Mid-Kent ICT Services Technology Strategy. Author: Tony Bullock Date: September 2013 Version: 019
 Mid-Kent ICT Services Technology Strategy Author: Tony Bullock Date: September 2013 Version: 019 Contents Background and purpose... 2 Key deliverables... 3 Benefits... 3 Principles... 3 Work anywhere,
Mid-Kent ICT Services Technology Strategy Author: Tony Bullock Date: September 2013 Version: 019 Contents Background and purpose... 2 Key deliverables... 3 Benefits... 3 Principles... 3 Work anywhere,
User Guide Version 2.1 August 8, IMAPP, Inc. Technical Support: Monday Friday 8:00 AM 5:00 PM Phone: (888) IMAPP.
 User Guide Version 2.1 August 8, 2008 IMAPP, Inc. Technical Support: Monday Friday 8:00 AM 5:00 PM Phone: (888) 462-7701 Email: support@ IMAPP.com www.imapp.com Index Accessing IMAPP... 3 Log in to IMAPP...
User Guide Version 2.1 August 8, 2008 IMAPP, Inc. Technical Support: Monday Friday 8:00 AM 5:00 PM Phone: (888) 462-7701 Email: support@ IMAPP.com www.imapp.com Index Accessing IMAPP... 3 Log in to IMAPP...
Jenzabar EX 4.5. Getting Started Guide for Administrators and Users
 Getting Started Guide for Administrators and Users October 24, 2012 2012, Jenzabar, Inc. 101 Huntington Avenue Suite 2205 Boston, MA 02199 1.877.535.0222 www.jenzabar.net This document is confidential
Getting Started Guide for Administrators and Users October 24, 2012 2012, Jenzabar, Inc. 101 Huntington Avenue Suite 2205 Boston, MA 02199 1.877.535.0222 www.jenzabar.net This document is confidential
Data Center Management and Automation Strategic Briefing
 Data Center and Automation Strategic Briefing Contents Why is Data Center and Automation (DCMA) so important? 2 The Solution Pathway: Data Center and Automation 2 Identifying and Addressing the Challenges
Data Center and Automation Strategic Briefing Contents Why is Data Center and Automation (DCMA) so important? 2 The Solution Pathway: Data Center and Automation 2 Identifying and Addressing the Challenges
Institute of Technology, Sligo. Information Security Policy. Version 0.2
 Institute of Technology, Sligo Information Security Policy Version 0.2 1 Document Location The document is held on the Institute s Staff Portal here. Revision History Date of this revision: 28.03.16 Date
Institute of Technology, Sligo Information Security Policy Version 0.2 1 Document Location The document is held on the Institute s Staff Portal here. Revision History Date of this revision: 28.03.16 Date
Set 2 MCQ
 1. ETCS means A) Enable Tax Collected at Source B) Electronic Tax Collected at Source C) Electric Tax Collected at Source D) None of these 2. To get Payroll Reports choose A) Gateway of Tally > Display
1. ETCS means A) Enable Tax Collected at Source B) Electronic Tax Collected at Source C) Electric Tax Collected at Source D) None of these 2. To get Payroll Reports choose A) Gateway of Tally > Display
Assessment: Program Four Column
 Assessment: Program Four Column Program - MBA Mission Statement: Through small, interactive, hybrid, and online courses, students develop managerial skills for dynamic environments emphasizing applied
Assessment: Program Four Column Program - MBA Mission Statement: Through small, interactive, hybrid, and online courses, students develop managerial skills for dynamic environments emphasizing applied
Thailand Digital Government Development Plan Digital Government Development Agency (Public Organization) (DGA)
 ขอแค ประมาณ ร ปน นะโม Thailand Digital Government Development Plan Digital Government Development Agency (Public Organization) (DGA) 1 Government agencies need to develop the Digital Government Master
ขอแค ประมาณ ร ปน นะโม Thailand Digital Government Development Plan Digital Government Development Agency (Public Organization) (DGA) 1 Government agencies need to develop the Digital Government Master
ISO & ISO & ISO Cloud Documentation Toolkit
 ISO & ISO 27017 & ISO 27018 Cloud ation Toolkit Note: The documentation should preferably be implemented order in which it is listed here. The order of implementation of documentation related to Annex
ISO & ISO 27017 & ISO 27018 Cloud ation Toolkit Note: The documentation should preferably be implemented order in which it is listed here. The order of implementation of documentation related to Annex
Chapter 3: AIS Enhancements Through Information Technology and Networks
 Accounting Information Systems: Essential Concepts and Applications Fourth Edition by Wilkinson, Cerullo, Raval, and Wong-On-Wing Chapter 3: AIS Enhancements Through Information Technology and Networks
Accounting Information Systems: Essential Concepts and Applications Fourth Edition by Wilkinson, Cerullo, Raval, and Wong-On-Wing Chapter 3: AIS Enhancements Through Information Technology and Networks
Administration & Finance. Capital Projects and Other Major Initiatives
 Administration & Finance Capital Projects and Other Major Initiatives, October 11, 2011 Administration and Finance -Mission Statement- Administration and Finance exists to support the strategic mission
Administration & Finance Capital Projects and Other Major Initiatives, October 11, 2011 Administration and Finance -Mission Statement- Administration and Finance exists to support the strategic mission
On-site Time and Material Rates for Equipment Not Covered under an HP Service Contract
 HPE Per Event U.S. On-Site Services Rate Schedule On-site Time and Material Rates for Equipment Not Covered under an HP Service Contract Equipment Type Enterprise Servers, Associated Storage, Network,
HPE Per Event U.S. On-Site Services Rate Schedule On-site Time and Material Rates for Equipment Not Covered under an HP Service Contract Equipment Type Enterprise Servers, Associated Storage, Network,
KENYA SCHOOL OF GOVERNMENT EMPLOYMENT OPORTUNITY (EXTERNAL ADVERTISEMENT)
 KENYA SCHOOL OF GOVERNMENT EMPLOYMENT OPORTUNITY (EXTERNAL ADVERTISEMENT) 1. DIRECTOR, LEARNING & DEVELOPMENT - LOWER KABETE Reporting to the Director General, Campus Directors will be responsible for
KENYA SCHOOL OF GOVERNMENT EMPLOYMENT OPORTUNITY (EXTERNAL ADVERTISEMENT) 1. DIRECTOR, LEARNING & DEVELOPMENT - LOWER KABETE Reporting to the Director General, Campus Directors will be responsible for
Data Protection. Practical Strategies for Getting it Right. Jamie Ross Data Security Day June 8, 2016
 Data Protection Practical Strategies for Getting it Right Jamie Ross Data Security Day June 8, 2016 Agenda 1) Data protection key drivers and the need for an integrated approach 2) Common challenges data
Data Protection Practical Strategies for Getting it Right Jamie Ross Data Security Day June 8, 2016 Agenda 1) Data protection key drivers and the need for an integrated approach 2) Common challenges data
Information Technology Security Plan Policies, Controls, and Procedures Protect: Identity Management and Access Control PR.AC
 Information Technology Security Plan Policies, Controls, and Procedures Protect: Identity Management and Access Control PR.AC Location: https://www.pdsimplified.com/ndcbf_pdframework/nist_csf_prc/documents/protect/ndcbf_
Information Technology Security Plan Policies, Controls, and Procedures Protect: Identity Management and Access Control PR.AC Location: https://www.pdsimplified.com/ndcbf_pdframework/nist_csf_prc/documents/protect/ndcbf_
AUDIT UNITED NATIONS VOLUNTEERS PROGRAMME INFORMATION AND COMMUNICATION TECHNOLOGY. Report No Issue Date: 8 January 2014
 UNITED NATIONS DEVELOPMENT PROGRAMME AUDIT OF UNITED NATIONS VOLUNTEERS PROGRAMME INFORMATION AND COMMUNICATION TECHNOLOGY Report No. 1173 Issue Date: 8 January 2014 Table of Contents Executive Summary
UNITED NATIONS DEVELOPMENT PROGRAMME AUDIT OF UNITED NATIONS VOLUNTEERS PROGRAMME INFORMATION AND COMMUNICATION TECHNOLOGY Report No. 1173 Issue Date: 8 January 2014 Table of Contents Executive Summary
Managing Born- Digital Documents.
 Managing Born- Digital Documents www.archives.nysed.gov Objectives Review the challenges of managing born-digital records Provide Practical strategies to ensure born-digital records are well managed Understand
Managing Born- Digital Documents www.archives.nysed.gov Objectives Review the challenges of managing born-digital records Provide Practical strategies to ensure born-digital records are well managed Understand
AADMER Work Programme
 The ASEAN Secretariat AADMER Work Programme Overview and Update Presentation Outline 1. ASEAN Agreement on Disaster Management and Emergency Response (AADMER) 2. AADMER Work Programme 3. Flagship Projects
The ASEAN Secretariat AADMER Work Programme Overview and Update Presentation Outline 1. ASEAN Agreement on Disaster Management and Emergency Response (AADMER) 2. AADMER Work Programme 3. Flagship Projects
QM Chapter 1 Database Fundamentals Version 10 th Ed. Prepared by Dr Kamel Rouibah / Dept QM & IS
 QM 433 - Chapter 1 Database Fundamentals Version 10 th Ed Prepared by Dr Kamel Rouibah / Dept QM & IS www.cba.edu.kw/krouibah Dr K. Rouibah / dept QM & IS Chapter 1 (433) Database fundamentals 1 Objectives
QM 433 - Chapter 1 Database Fundamentals Version 10 th Ed Prepared by Dr Kamel Rouibah / Dept QM & IS www.cba.edu.kw/krouibah Dr K. Rouibah / dept QM & IS Chapter 1 (433) Database fundamentals 1 Objectives
University of Richmond Chief Operating Officer Organization Chart August 2017
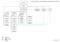 & Chief Operating Officer for University Communications & General Counsel & Provost, Advancement of Athletics () & Chief Information Officer Asst, Advancement Deputy Asst, Systems & Networks Sr Assoc,
& Chief Operating Officer for University Communications & General Counsel & Provost, Advancement of Athletics () & Chief Information Officer Asst, Advancement Deputy Asst, Systems & Networks Sr Assoc,
INSTRUCTIONS for PLANNING RECOMMENDATIONS in TracDat Unit Level
 INSTRUCTIONS for PLANNING RECOMMENDATIONS in TracDat Unit Level Table of Contents Introduction to TracDat... 2 Background... 2 Logging into TracDat... 2 Definitions... 2 Recommendations... 3 TracDat Menu...
INSTRUCTIONS for PLANNING RECOMMENDATIONS in TracDat Unit Level Table of Contents Introduction to TracDat... 2 Background... 2 Logging into TracDat... 2 Definitions... 2 Recommendations... 3 TracDat Menu...
Data Inventory and Classification, Physical Devices and Systems ID.AM-1, Software Platforms and Applications ID.AM-2 Inventory
 Audience: NDCBF IT Security Team Last Reviewed/Updated: March 2018 Contact: Henry Draughon hdraughon@processdeliveysystems.com Overview... 2 Sensitive Data Inventory and Classification... 3 Applicable
Audience: NDCBF IT Security Team Last Reviewed/Updated: March 2018 Contact: Henry Draughon hdraughon@processdeliveysystems.com Overview... 2 Sensitive Data Inventory and Classification... 3 Applicable
MANAGING STATISTICAL DEVELOPMENT AND INFORMATION TECHNOLOGY IN THE STATISTICAL SYSTEM OF MALAYSIA
 SIXTH MANAGEMENT SEMINAR FOR HEADS OF NATIONAL STATISTICAL OFFICES IN ASIA AND THE PACIFIC. 28 30 MAY 2007, HONG KONG, CHINA 1. Introduction MANAGING STATISTICAL DEVELOPMENT AND INFORMATION TECHNOLOGY
SIXTH MANAGEMENT SEMINAR FOR HEADS OF NATIONAL STATISTICAL OFFICES IN ASIA AND THE PACIFIC. 28 30 MAY 2007, HONG KONG, CHINA 1. Introduction MANAGING STATISTICAL DEVELOPMENT AND INFORMATION TECHNOLOGY
Network+ Guide to Networks 5 th Edition. Chapter 1 An Introduction to Networking
 Network+ Guide to Networks 5 th Edition Chapter 1 An Introduction to Networking Goals of This Chapter List the advantages of networked computing relative to standalone computing Distinguish between client/server
Network+ Guide to Networks 5 th Edition Chapter 1 An Introduction to Networking Goals of This Chapter List the advantages of networked computing relative to standalone computing Distinguish between client/server
Top-Down Network Design
 Top-Down Network Design Chapter One Analyzing Business Goals and Constraints Original slides by Cisco Press & Priscilla Oppenheimer Top-Down Network Design Network design should be a complete and iterative
Top-Down Network Design Chapter One Analyzing Business Goals and Constraints Original slides by Cisco Press & Priscilla Oppenheimer Top-Down Network Design Network design should be a complete and iterative
Project Name System Critical Design Review
 Insert project logo Project Name System Critical Design Review Class Number Title Date Location This Critical Design Review assumes that the design team will be following a formalized design process. This
Insert project logo Project Name System Critical Design Review Class Number Title Date Location This Critical Design Review assumes that the design team will be following a formalized design process. This
Vocational Arts Montana State Standards For Technology
 Vocational Arts Montana State Standards For Technology Technology Content Standard 1 (CS1) Students demonstrate an understanding of the basic operations of technologies. Technology Content Standard 2 (CS2)
Vocational Arts Montana State Standards For Technology Technology Content Standard 1 (CS1) Students demonstrate an understanding of the basic operations of technologies. Technology Content Standard 2 (CS2)
Chapter 2 Introduction to Transaction Processing
 Chapter 2 Introduction to Transaction Processing TRUE/FALSE 1. Processing more transactions at a lower unit cost makes batch processing more efficient than real-time systems. T 2. The process of acquiring
Chapter 2 Introduction to Transaction Processing TRUE/FALSE 1. Processing more transactions at a lower unit cost makes batch processing more efficient than real-time systems. T 2. The process of acquiring
Kentucky IT Consolidation
 2007 NASCIO Recognition Awards Nomination Category: Enterprise IT Management Initiatives Kentucky IT Consolidation Commonwealth Office of Technology The Commonwealth of Kentucky is nearing completion of
2007 NASCIO Recognition Awards Nomination Category: Enterprise IT Management Initiatives Kentucky IT Consolidation Commonwealth Office of Technology The Commonwealth of Kentucky is nearing completion of
Powered by TCPDF (
 Powered by TCPDF (www.tcpdf.org) 1 FINANCE AND ACCOUNTING FOR NON-FINANCIAL PROFESSIONALS 28th Feb - 3rd Mar, 2017 1st - 4th Aug, 2017 2 MODERN APPROACHES TO CORPORATE AND INDIVIDUAL TAX COMPLIANCE 28th
Powered by TCPDF (www.tcpdf.org) 1 FINANCE AND ACCOUNTING FOR NON-FINANCIAL PROFESSIONALS 28th Feb - 3rd Mar, 2017 1st - 4th Aug, 2017 2 MODERN APPROACHES TO CORPORATE AND INDIVIDUAL TAX COMPLIANCE 28th
Metropolitan Washington Airports Authority PROCUREMENT AND CONTRACTS DEPT. AMENDMENT OF SOLICITATION
 Metropolitan Washington Airports Authority PROCUREMENT AND CONTRACTS DEPT. AMENDMENT OF SOLICITATION Metropolitan Washington Airports Authority Procurement and Contracts Dept., MA-29 2733 Crystal Drive
Metropolitan Washington Airports Authority PROCUREMENT AND CONTRACTS DEPT. AMENDMENT OF SOLICITATION Metropolitan Washington Airports Authority Procurement and Contracts Dept., MA-29 2733 Crystal Drive
University of Richmond August 2018 Business Affairs Organization Chart
 & Chief Operating Officer for University Communications & General Counsel, Advancement & of & Chief Information Officer Asst, Advancement Deputy Asst, Systems & Networks Sr Assoc, Finance & Administration
& Chief Operating Officer for University Communications & General Counsel, Advancement & of & Chief Information Officer Asst, Advancement Deputy Asst, Systems & Networks Sr Assoc, Finance & Administration
SYMBIOSIS CENTRE FOR DISTANCE LEARNING (SCDL) Subject: Management Information Systems
 Sample Questions: Section I: Subjective Questions 1. Which factors are considered critical for the success/failure of the Decision Support System? 2. List the categories of data warehousing tools. 3. "MIS
Sample Questions: Section I: Subjective Questions 1. Which factors are considered critical for the success/failure of the Decision Support System? 2. List the categories of data warehousing tools. 3. "MIS
CALL FOR EXPRESSION OF INTEREST (EOI N PTD/15/101) Enterprise Content Management (ECM) Implementation. Annex II BACKGROUND INFORMATION
 CALL FOR EXPRESSION OF INTEREST (EOI N PTD/15/101) Enterprise Content Management (ECM) Implementation Annex II BACKGROUND INFORMATION EOI N PTD/15/101 (ECM Implementation) Background Information 1 7 1.
CALL FOR EXPRESSION OF INTEREST (EOI N PTD/15/101) Enterprise Content Management (ECM) Implementation Annex II BACKGROUND INFORMATION EOI N PTD/15/101 (ECM Implementation) Background Information 1 7 1.
WELCOME ISO/IEC 27001:2017 Information Briefing
 WELCOME ISO/IEC 27001:2017 Information Briefing Denis Ryan C.I.S.S.P NSAI Lead Auditor Running Order 1. Market survey 2. Why ISO 27001 3. Requirements of ISO 27001 4. Annex A 5. Registration process 6.
WELCOME ISO/IEC 27001:2017 Information Briefing Denis Ryan C.I.S.S.P NSAI Lead Auditor Running Order 1. Market survey 2. Why ISO 27001 3. Requirements of ISO 27001 4. Annex A 5. Registration process 6.
ACCT ACCOUNTING. ACCT Accounting 1. ACCT 214 Integrated Accounting Systems
 ACCT Accounting 1 ACCT ACCOUNTING ACCT 100 Introduction to Accounting and Computerized Accounting Applications This is a basic financial accounting course in which students explore the introductory principles,
ACCT Accounting 1 ACCT ACCOUNTING ACCT 100 Introduction to Accounting and Computerized Accounting Applications This is a basic financial accounting course in which students explore the introductory principles,
BUSINESS CONTINUITY. Topics covered in this checklist include: General Planning
 BUSINESS CONTINUITY Natural and manmade disasters are happening with alarming regularity. If your organization doesn t have a great business continuity plan the repercussions will range from guaranteed
BUSINESS CONTINUITY Natural and manmade disasters are happening with alarming regularity. If your organization doesn t have a great business continuity plan the repercussions will range from guaranteed
Information. Technology. Annual Report
 Information 2016 Technology Annual Report Information Technology Table of Contents Division Personnel 2 Mission Statement & Core Values 2 Technical Support 3 System Integration 4 Infrastructure 4-6 WARCOG
Information 2016 Technology Annual Report Information Technology Table of Contents Division Personnel 2 Mission Statement & Core Values 2 Technical Support 3 System Integration 4 Infrastructure 4-6 WARCOG
Sage What s New. March 2019
 Sage 100 2019 What s New March 2019 2019 The Sage Group plc or its licensors. All rights reserved. Sage, Sage logos, and Sage product and service names mentioned herein are the trademarks of The Sage Group
Sage 100 2019 What s New March 2019 2019 The Sage Group plc or its licensors. All rights reserved. Sage, Sage logos, and Sage product and service names mentioned herein are the trademarks of The Sage Group
Certified Information Security Manager (CISM) Course Overview
 Certified Information Security Manager (CISM) Course Overview This course teaches students about information security governance, information risk management, information security program development,
Certified Information Security Manager (CISM) Course Overview This course teaches students about information security governance, information risk management, information security program development,
DATA Act Information Model Schema (DAIMS) Architecture. U.S. Department of the Treasury
 DATA Act Information Model Schema (DAIMS) Architecture U.S. Department of the Treasury September 22, 2017 Table of Contents 1. Introduction... 1 2. Conceptual Information Model... 2 3. Metadata... 4 4.
DATA Act Information Model Schema (DAIMS) Architecture U.S. Department of the Treasury September 22, 2017 Table of Contents 1. Introduction... 1 2. Conceptual Information Model... 2 3. Metadata... 4 4.
MainOpsStaff-2ed Training Manual Updated 6/26/2018
 MainOpsStaff-2ed Training Manual Updated 6/26/2018 (Recommend you print this file) (Open latest version of this document from website) Table of Contents MainOpsStaff-2ed Training Manual Updated 6/26/2018...
MainOpsStaff-2ed Training Manual Updated 6/26/2018 (Recommend you print this file) (Open latest version of this document from website) Table of Contents MainOpsStaff-2ed Training Manual Updated 6/26/2018...
Lab #1 Creating an IT Infrastructure Asset List and. Identifying Where Privacy Data Resides
 Lab #1 Creating an IT Infrastructure Asset List and Identifying Where Privacy Data Resides Introduction Privacy is of growing concern, especially that of individual personal information. Between businesses
Lab #1 Creating an IT Infrastructure Asset List and Identifying Where Privacy Data Resides Introduction Privacy is of growing concern, especially that of individual personal information. Between businesses
Technical and Advisory Support Facility (TASF) Development of E-Government & ICT in the Public Sector: Government of Grenada. June 21 st - 22 nd, 2006
 T@SF Caribbean Technical and Advisory Support Facility (TASF) on egovernment UNDESA/ CARICAD MISSION REPORT Technical and Advisory Support Facility (TASF) Development of E-Government & ICT in the Public
T@SF Caribbean Technical and Advisory Support Facility (TASF) on egovernment UNDESA/ CARICAD MISSION REPORT Technical and Advisory Support Facility (TASF) Development of E-Government & ICT in the Public
COLUMBUS. Business Solutions. Cloud Unified Communications & Interoperability. Javier Pereira Director of Product Development November 2011
 COLUMBUS Business Solutions Cloud Unified Communications & Interoperability Javier Pereira Director of Product Development November 2011 Industry Tendencies Gartner Reported that the second priority for
COLUMBUS Business Solutions Cloud Unified Communications & Interoperability Javier Pereira Director of Product Development November 2011 Industry Tendencies Gartner Reported that the second priority for
MOTHER TERESA SR. SEC. CO-ED SCHOOL. CLASS VIII (Comp Sc.) CHAPTER-1 : ABOUT NETWORKING
 Q1. Multiple Choice Questions MOTHER TERESA SR. SEC. CO-ED SCHOOL 1) WLAN stands for : CLASS VIII (Comp Sc.) 2017-18 CHAPTER-1 : ABOUT NETWORKING a) Wide Local Area Network b) World Local Area Network
Q1. Multiple Choice Questions MOTHER TERESA SR. SEC. CO-ED SCHOOL 1) WLAN stands for : CLASS VIII (Comp Sc.) 2017-18 CHAPTER-1 : ABOUT NETWORKING a) Wide Local Area Network b) World Local Area Network
PAF Chapter Junior Section Name : Class: 5 Sec: Date: SECTION - A
 ICT CLASS-5 COMPREHENSIVE WORKSHEET Mid Term Session 2015-16 The City School PAF Chapter Junior Section Name : Class: 5 Sec: Date: Q1. Encircle any one correct option. i.) SECTION - A is an electronic
ICT CLASS-5 COMPREHENSIVE WORKSHEET Mid Term Session 2015-16 The City School PAF Chapter Junior Section Name : Class: 5 Sec: Date: Q1. Encircle any one correct option. i.) SECTION - A is an electronic
MAIL MERGE MARKETING WITH CARDEX
 This procedure contains several steps to accomplish exporting the Cardex records to a text file and merging the exported Cardex data to Microsoft Word for address labels. Exporting the Cardex records to
This procedure contains several steps to accomplish exporting the Cardex records to a text file and merging the exported Cardex data to Microsoft Word for address labels. Exporting the Cardex records to
Information Technology Paul Kronberger, Chief Information Officer
 Paul Kronberger, Chief Information Officer City-County Building, Room 500 210 Martin Luther King, Jr. Boulevard Madison, Wisconsin 53703-3349 May 11, 2016 David Schmiedicke Finance Director City of Madison
Paul Kronberger, Chief Information Officer City-County Building, Room 500 210 Martin Luther King, Jr. Boulevard Madison, Wisconsin 53703-3349 May 11, 2016 David Schmiedicke Finance Director City of Madison
Independent Contractor Questionnaire
 Independent Contractor Questionnaire Instructional Guide 5/1/17 Independent Contractor Questionnaire The Independent Contractor Questionnaire (ICQ) is completed by the buyer in cooperation with the vendor
Independent Contractor Questionnaire Instructional Guide 5/1/17 Independent Contractor Questionnaire The Independent Contractor Questionnaire (ICQ) is completed by the buyer in cooperation with the vendor
Sage Financial Reporter User's Guide. May 2017
 Sage 300 2018 Financial Reporter User's Guide May 2017 This is a publication of Sage Software, Inc. 2017 The Sage Group plc or its licensors. All rights reserved. Sage, Sage logos, and Sage product and
Sage 300 2018 Financial Reporter User's Guide May 2017 This is a publication of Sage Software, Inc. 2017 The Sage Group plc or its licensors. All rights reserved. Sage, Sage logos, and Sage product and
CenturyLink for Microsoft
 Strategic Partner Alliances CenturyLink for Microsoft EMPOWER REACH AGILITY 2017 CenturyLink. All Rights Reserved. The CenturyLink mark, pathways logo and certain CenturyLink product names are the property
Strategic Partner Alliances CenturyLink for Microsoft EMPOWER REACH AGILITY 2017 CenturyLink. All Rights Reserved. The CenturyLink mark, pathways logo and certain CenturyLink product names are the property
"Charting the Course... Certified Information Systems Auditor (CISA) Course Summary
 Course Summary Description In this course, you will perform evaluations of organizational policies, procedures, and processes to ensure that an organization's information systems align with overall business
Course Summary Description In this course, you will perform evaluations of organizational policies, procedures, and processes to ensure that an organization's information systems align with overall business
Business Model for Global Platform for Big Data for Official Statistics in support of the 2030 Agenda for Sustainable Development
 Business Model for Global Platform for Big Data for Official Statistics in support of the 2030 Agenda for Sustainable Development Introduction This note sets out a business model for a Global Platform
Business Model for Global Platform for Big Data for Official Statistics in support of the 2030 Agenda for Sustainable Development Introduction This note sets out a business model for a Global Platform
Government of India R F D. (Results-Framework Document) for. Education and Research Network (ERNET) ( )
 Government of India R F D (Results-Framework Document) for Education and Research Network (ERNET) (2013-2014) Page : 2 of 14 Results-Framework Document (RFD) for Education and Research Network (ERNET)
Government of India R F D (Results-Framework Document) for Education and Research Network (ERNET) (2013-2014) Page : 2 of 14 Results-Framework Document (RFD) for Education and Research Network (ERNET)
CENTRAL SUSQUEHANNA INTERMEDIATE UNIT Application: Security. Fund Accounting: Security Learning Guide
 CENTRAL SUSQUEHANNA INTERMEDIATE UNIT Application: Security Fund Accounting: Security Learning Guide 2009 Central Susquehanna Intermediate Unit, USA Table of Contents INTRODUCTION...3 Tools:...4 User Maintenance...4
CENTRAL SUSQUEHANNA INTERMEDIATE UNIT Application: Security Fund Accounting: Security Learning Guide 2009 Central Susquehanna Intermediate Unit, USA Table of Contents INTRODUCTION...3 Tools:...4 User Maintenance...4
A1 ASSIGNMENT TERMINOLOGY.
 A1 ASSIGNMENT TERMINOLOGY. Emma Ziolkowski Term Definition Image blog a web page or site that speaks to an audience of readers informally about opinionated topics. a blog is a website on which the author
A1 ASSIGNMENT TERMINOLOGY. Emma Ziolkowski Term Definition Image blog a web page or site that speaks to an audience of readers informally about opinionated topics. a blog is a website on which the author
Brief on ecourts Project
 Brief on ecourts Project A. ecourts Integrated Mission Mode Project (Phase-I): The ecourts Integrated Mission Mode Project is one of the national egovernance projects being implemented in High Courts and
Brief on ecourts Project A. ecourts Integrated Mission Mode Project (Phase-I): The ecourts Integrated Mission Mode Project is one of the national egovernance projects being implemented in High Courts and
INSTRUCTIONS for PLANNING RECOMMENDATIONS in TracDat Program Level
 INSTRUCTIONS for PLANNING RECOMMENDATIONS in TracDat Program Level Table of Contents Introduction to TracDat... 2 Background... 2 Logging into TracDat... 2 Definitions... 2 Recommendations... 3 TracDat
INSTRUCTIONS for PLANNING RECOMMENDATIONS in TracDat Program Level Table of Contents Introduction to TracDat... 2 Background... 2 Logging into TracDat... 2 Definitions... 2 Recommendations... 3 TracDat
Campus IT Modernization OPERATIONAL CONTINUITY FLEXIBLE TECHNOLOGY MODERNIZED SYSTEMS
 Campus IT Modernization OPERATIONAL CONTINUITY FLEXIBLE TECHNOLOGY MODERNIZED SYSTEMS Managing the Complexity of IT Modernization Constructing and modernizing a new campus is a complex undertaking, requiring
Campus IT Modernization OPERATIONAL CONTINUITY FLEXIBLE TECHNOLOGY MODERNIZED SYSTEMS Managing the Complexity of IT Modernization Constructing and modernizing a new campus is a complex undertaking, requiring
CErtifi TM TimeClock In/Out User Manual
 CErtifi TM TimeClock In/Out User Manual Controlled Efficiencies, LLC 110 Glancy Street, Suite 202, Goodlettsville, TN 37072 T: 615.206.8765 E: info@cesimplify.com CESimplify.com I. Overview Our software
CErtifi TM TimeClock In/Out User Manual Controlled Efficiencies, LLC 110 Glancy Street, Suite 202, Goodlettsville, TN 37072 T: 615.206.8765 E: info@cesimplify.com CESimplify.com I. Overview Our software
REPORT 2015/186 INTERNAL AUDIT DIVISION
 INTERNAL AUDIT DIVISION REPORT 2015/186 Audit of information and communications technology operations in the Secretariat of the United Nations Joint Staff Pension Fund Overall results relating to the effective
INTERNAL AUDIT DIVISION REPORT 2015/186 Audit of information and communications technology operations in the Secretariat of the United Nations Joint Staff Pension Fund Overall results relating to the effective
ITG. Information Security Management System Manual
 ITG Information Security Management System Manual This manual describes the ITG Information Security Management system and must be followed closely in order to ensure compliance with the ISO 27001:2005
ITG Information Security Management System Manual This manual describes the ITG Information Security Management system and must be followed closely in order to ensure compliance with the ISO 27001:2005
Voluntary Product Accessibility Template QuickBooks 2016 Pro, Premiere and Enterprise
 Voluntary Product Accessibility Template QuickBooks 2016 Pro, Premiere and Enterprise The purpose of this Voluntary Product Accessibility Template ( VPAT ) is to assist Federal contracting officials and
Voluntary Product Accessibility Template QuickBooks 2016 Pro, Premiere and Enterprise The purpose of this Voluntary Product Accessibility Template ( VPAT ) is to assist Federal contracting officials and
UNIVERSITY OF VIRGINIA BOARD OF VISITORS MEETING OF THE AUDIT, COMPLIANCE, AND RISK COMMITTEE DECEMBER 9, 2016
 UNIVERSITY OF VIRGINIA BOARD OF VISITORS MEETING OF THE AUDIT, COMPLIANCE, AND RISK COMMITTEE DECEMBER 9, 2016 AUDIT, COMPLIANCE, AND RISK COMMITTEE (Open Session) Friday, December 9, 2016 12:45-1:45 p.m.
UNIVERSITY OF VIRGINIA BOARD OF VISITORS MEETING OF THE AUDIT, COMPLIANCE, AND RISK COMMITTEE DECEMBER 9, 2016 AUDIT, COMPLIANCE, AND RISK COMMITTEE (Open Session) Friday, December 9, 2016 12:45-1:45 p.m.
LTI Security Services. Intelligent & integrated Approach to Cyber & Digital Security
 LTI Security Intelligent & integrated Approach to Cyber & Digital Security Overview As businesses are expanding globally into new territories, propelled and steered by digital disruption and technological
LTI Security Intelligent & integrated Approach to Cyber & Digital Security Overview As businesses are expanding globally into new territories, propelled and steered by digital disruption and technological
ITG. Information Security Management System Manual
 ITG Information Security Management System Manual This manual describes the ITG Information Security Management system and must be followed closely in order to ensure compliance with the ISO 27001:2005
ITG Information Security Management System Manual This manual describes the ITG Information Security Management system and must be followed closely in order to ensure compliance with the ISO 27001:2005
COMPUTER INFORMATION SYSTEMS
 A Course of Study for COMPUTER INFORMATION SYSTEMS Computer Information Systems managers oversee a variety of administrative, clerical, and accounting functions necessary to efficiently run and maintain
A Course of Study for COMPUTER INFORMATION SYSTEMS Computer Information Systems managers oversee a variety of administrative, clerical, and accounting functions necessary to efficiently run and maintain
Compton College Department Plan Step-by-Step
 Compton College 2019-20 Department Plan Step-by-Step This document provides the step by step instructions to complete your 2019-20 department plan and submit the information into the Nuventive site (formerly
Compton College 2019-20 Department Plan Step-by-Step This document provides the step by step instructions to complete your 2019-20 department plan and submit the information into the Nuventive site (formerly
Oracle Taleo Services Descriptions and Metrics December 21, 2017
 Oracle Taleo Services Descriptions and Metrics December 21, 2017 Table of Contents Metric Definitions... 3 Hosted Named User... 3 Hosted Employee... 3 Hosted Trainee... 3 Per Posting... 3 New Customer
Oracle Taleo Services Descriptions and Metrics December 21, 2017 Table of Contents Metric Definitions... 3 Hosted Named User... 3 Hosted Employee... 3 Hosted Trainee... 3 Per Posting... 3 New Customer
COMPTIA CLO-001 EXAM QUESTIONS & ANSWERS
 COMPTIA CLO-001 EXAM QUESTIONS & ANSWERS Number: CLO-001 Passing Score: 800 Time Limit: 120 min File Version: 39.7 http://www.gratisexam.com/ COMPTIA CLO-001 EXAM QUESTIONS & ANSWERS Exam Name: CompTIA
COMPTIA CLO-001 EXAM QUESTIONS & ANSWERS Number: CLO-001 Passing Score: 800 Time Limit: 120 min File Version: 39.7 http://www.gratisexam.com/ COMPTIA CLO-001 EXAM QUESTIONS & ANSWERS Exam Name: CompTIA
Strategic Technology Trends for Digital Government
 - 2 - Strategic Technology Trends for Digital Government Strategic Technology Trends for Digital Government Virtual Reality / Augmented Reality Application of Virtual Reality (VR) and Augmented Reality
- 2 - Strategic Technology Trends for Digital Government Strategic Technology Trends for Digital Government Virtual Reality / Augmented Reality Application of Virtual Reality (VR) and Augmented Reality
NASA Policy Directive
 NASA Policy Directive NPD 8820.2D Effective Date: July 02, 2013 Expiration Date: July 02, 2018 COMPLIANCE IS MANDATORY Subject: Design and Construction of Facilities Responsible Office: Facilities Engineering
NASA Policy Directive NPD 8820.2D Effective Date: July 02, 2013 Expiration Date: July 02, 2018 COMPLIANCE IS MANDATORY Subject: Design and Construction of Facilities Responsible Office: Facilities Engineering
Oregon Health & Science University
 1A Pres, VP, Provost, Deans, Institute Director, Hospital Director EVP & CFO - 7102S 1 1B 1B Upper Management Chairs & SR+ Upper Management Chairs & SR+ VP & Chief Information Officer - 7118S 1 VP & Comptroller
1A Pres, VP, Provost, Deans, Institute Director, Hospital Director EVP & CFO - 7102S 1 1B 1B Upper Management Chairs & SR+ Upper Management Chairs & SR+ VP & Chief Information Officer - 7118S 1 VP & Comptroller
Desktop Virtualization for Higher Education. The Virtual Lab
 Desktop Virtualization for Higher Education The Virtual Lab What is the Virtual Lab? WHAT IS THE VIRTUAL LAB? Transformational technology for Higher Ed labs collaboration between Dell & VMware Virtualize
Desktop Virtualization for Higher Education The Virtual Lab What is the Virtual Lab? WHAT IS THE VIRTUAL LAB? Transformational technology for Higher Ed labs collaboration between Dell & VMware Virtualize
Sage 300 ERP Financial Reporter User's Guide
 Sage 300 ERP 2012 Financial Reporter User's Guide This is a publication of Sage Software, Inc. Version 2012 Copyright 2013. Sage Software, Inc. All rights reserved. Sage, the Sage logos, and the Sage product
Sage 300 ERP 2012 Financial Reporter User's Guide This is a publication of Sage Software, Inc. Version 2012 Copyright 2013. Sage Software, Inc. All rights reserved. Sage, the Sage logos, and the Sage product
Lecture Outline. Requirements Analysis I. Defining Requirements Analysis. Network Design: A Systems Approach. Jeremiah Deng.
 Lecture Outline TELE302 Lecture 15 Requirements Analysis I Jeremiah Deng TELE / InfoSci, University of Otago 31 August 2015 1 2 Starting from the Top 3 4 Other Requirements 5 TELE302 Lecture 15 2 / 30
Lecture Outline TELE302 Lecture 15 Requirements Analysis I Jeremiah Deng TELE / InfoSci, University of Otago 31 August 2015 1 2 Starting from the Top 3 4 Other Requirements 5 TELE302 Lecture 15 2 / 30
Geog 469 GIS Workshop. System Requirements
 Geog 469 GIS Workshop System Requirements Outline 1. What are some fundamental issues associated with system requirements? 2. What are your GIS data requirements? 3. What are your GIS software requirements?
Geog 469 GIS Workshop System Requirements Outline 1. What are some fundamental issues associated with system requirements? 2. What are your GIS data requirements? 3. What are your GIS software requirements?
Project DCOM. For municipalities, for the people - cloud in reality. René Kubiš, PosAm CSMO Deutsche Telekom Group
 Project DCOM For municipalities, for the people - cloud in reality René Kubiš, PosAm CSMO Deutsche Telekom Group Agenda /Municipalities of Slovakia overview /Stakeholders and financing /Scope of DCOM project
Project DCOM For municipalities, for the people - cloud in reality René Kubiš, PosAm CSMO Deutsche Telekom Group Agenda /Municipalities of Slovakia overview /Stakeholders and financing /Scope of DCOM project
Sage Financial Reporter User's Guide
 Sage 300 2017 Financial Reporter User's Guide This is a publication of Sage Software, Inc. Copyright 2016. Sage Software, Inc. All rights reserved. Sage, the Sage logos, and the Sage product and service
Sage 300 2017 Financial Reporter User's Guide This is a publication of Sage Software, Inc. Copyright 2016. Sage Software, Inc. All rights reserved. Sage, the Sage logos, and the Sage product and service
IBM MERVA ESA Version 4 and MERVA ESA Components Version 4 Begin a New Era for Financial Message Processing
 Software Announcement May 4, 1999 IBM MERVA ESA Version 4 and MERVA ESA Components Version 4 Begin a New Era for Financial Message Processing Overview A Strategic Solution for Connecting Financial Institutions
Software Announcement May 4, 1999 IBM MERVA ESA Version 4 and MERVA ESA Components Version 4 Begin a New Era for Financial Message Processing Overview A Strategic Solution for Connecting Financial Institutions
Design Checklist. Application Architecture. Initial cost and Total Cost of Ownership (TCO) Enterprise Resource Planning (ERP) Peter Lo
 Design Checklist Application Architecture Peter Lo Before selecting application architecture, the analyst must consider the following issues: Enterprise resource planning Initial cost and Total Cost of
Design Checklist Application Architecture Peter Lo Before selecting application architecture, the analyst must consider the following issues: Enterprise resource planning Initial cost and Total Cost of
COMPLIANCE BRIEF: HOW VARONIS HELPS WITH PCI DSS 3.1
 COMPLIANCE BRIEF: HOW VARONIS HELPS WITH OVERVIEW The Payment Card Industry Data Security Standard (PCI-DSS) 3.1 is a set of regulations that govern how firms that process credit card and other similar
COMPLIANCE BRIEF: HOW VARONIS HELPS WITH OVERVIEW The Payment Card Industry Data Security Standard (PCI-DSS) 3.1 is a set of regulations that govern how firms that process credit card and other similar
ORGANIGRAMME FONCTIONNEL au 31/12/2017
 ORGANIGRAMME FONCTIONNEL au 31/12/2017 D.G. D.G.A. 18 EXECUTIVE ADMINISTRATION OFFICE 8 6 Instances Legal 3 7 1 1 3 1 1 Secrétariat de Direction Administration Suivi des instances Contact communes Assurances
ORGANIGRAMME FONCTIONNEL au 31/12/2017 D.G. D.G.A. 18 EXECUTIVE ADMINISTRATION OFFICE 8 6 Instances Legal 3 7 1 1 3 1 1 Secrétariat de Direction Administration Suivi des instances Contact communes Assurances
Application of GIS to Cybersecurity. Brian Biesecker Ken Mitchell
 Application of GIS to Cybersecurity Brian Biesecker Ken Mitchell Fundamental Problems that GIS can help you solve What are the impacts to your mission, operations, business activities, critical systems,
Application of GIS to Cybersecurity Brian Biesecker Ken Mitchell Fundamental Problems that GIS can help you solve What are the impacts to your mission, operations, business activities, critical systems,
HRSD Position Description: UNIX Systems Administrator
 HRSD Position Description: UNIX Systems Administrator Section I. Section II. Section III. Position Reference Information a. Department Finance and Administration b. Division Information Technology c. Position
HRSD Position Description: UNIX Systems Administrator Section I. Section II. Section III. Position Reference Information a. Department Finance and Administration b. Division Information Technology c. Position
C106: DEMO OF THE INFORMATION SECURITY MANAGEMENT SYSTEM - ISO: 27001:2005 AWARENESS TRAINING PRESENTATION KIT
 C106: DEMO OF THE INFORMATION SECURITY MANAGEMENT SYSTEM - ISO: 27001:2005 AWARENESS TRAINING PRESENTATION KIT Buy: http://www.globalmanagergroup.com/iso27001training.htm Chapter-1.0 CONTENTS OF ISO 27001-2005
C106: DEMO OF THE INFORMATION SECURITY MANAGEMENT SYSTEM - ISO: 27001:2005 AWARENESS TRAINING PRESENTATION KIT Buy: http://www.globalmanagergroup.com/iso27001training.htm Chapter-1.0 CONTENTS OF ISO 27001-2005
Campus Network Design. 2003, Cisco Systems, Inc. All rights reserved. 2-1
 Campus Network Design 2003, Cisco Systems, Inc. All rights reserved. 2-1 Design Objective Business Requirement Why do you want to build a network? Too often people build networks based on technological,
Campus Network Design 2003, Cisco Systems, Inc. All rights reserved. 2-1 Design Objective Business Requirement Why do you want to build a network? Too often people build networks based on technological,
CLOUD COMPUTING READINESS CHECKLIST
 CLOUD COMPUTING READINESS DAVE WILLIS STEPHEN GOLDSMITH SUBJECT MATTER EXPERTS, CLOUD COMPUTING DENOVO DAVE WILLIS STEPHEN GOLDSMITH SUBJECT MATTER EXPERTS, CLOUD COMPUTING DENOVO 1 CONTENTS INTRODUCTION
CLOUD COMPUTING READINESS DAVE WILLIS STEPHEN GOLDSMITH SUBJECT MATTER EXPERTS, CLOUD COMPUTING DENOVO DAVE WILLIS STEPHEN GOLDSMITH SUBJECT MATTER EXPERTS, CLOUD COMPUTING DENOVO 1 CONTENTS INTRODUCTION
SAVANNAH LAKES VILLAGE PROPERTY OWNERS ASSOCIATION, INC. JOB DESCRIPTION
 SAVANNAH LAKES VILLAGE PROPERTY OWNERS ASSOCIATION, INC. JOB DESCRIPTION POSITION: CHIEF OPERATING OFFICER FUNCTION: Responsible for all aspects of the SLV POA day-to-day operations. In this capacity,
SAVANNAH LAKES VILLAGE PROPERTY OWNERS ASSOCIATION, INC. JOB DESCRIPTION POSITION: CHIEF OPERATING OFFICER FUNCTION: Responsible for all aspects of the SLV POA day-to-day operations. In this capacity,
DATA STEWARDSHIP STANDARDS
 DATA STEWARDSHIP STANDARDS Policy: Enterprise Data Stewardship Policy Document: Data Stewardship Standards Campus: MSU-Billings (MSUB) Revision: 01-08-18 Contact: Michael Barber, Chief Information Officer
DATA STEWARDSHIP STANDARDS Policy: Enterprise Data Stewardship Policy Document: Data Stewardship Standards Campus: MSU-Billings (MSUB) Revision: 01-08-18 Contact: Michael Barber, Chief Information Officer
Polycom RealAccess, Cloud Edition
 ADMINISTRATOR GUIDE January 2018 3725-47131-001E Polycom RealAccess, Cloud Edition Copyright 2017, Polycom, Inc. All rights reserved. No part of this document may be reproduced, translated into another
ADMINISTRATOR GUIDE January 2018 3725-47131-001E Polycom RealAccess, Cloud Edition Copyright 2017, Polycom, Inc. All rights reserved. No part of this document may be reproduced, translated into another
