CS121: Our Digital World
|
|
|
- Bathsheba Melanie Bishop
- 5 years ago
- Views:
Transcription
1 + CS121: Our Digital World
2 + Redacted Documents 2
3 + Activity: Badly Redacted 3 Documents Download the following file: Can you find the secret message?
4 + Electronically Redacted Document 4 Examples TSA: Screening Management Standard Operating Procedure Two examples: 2009 and 2010 US Military Washington Post What went wrong? WYSIWYG
5 + Number Systems ASCII, binary, decimal, hex 5
6 + ASCII 6 In text files, each character is represented as an ASCII character ASCII Table: So, the letter a is represented as: Decimal: 097 Binary: Hex: 061 A is represented as: Decimal: 065 Binary: Hex: 041
7 + Decimal Numbers 7 Start counting: 0, 1, 2, 3, 4, 5, 6, 7, 8, 9 Oops! We ve ran out of digits Add a second column: 10, 11, 12,., 19, 20, 21,, 98, 99 Oops! We ve ran out of digits Add a third column and so on
8 + Decimal Numbers 8 Another way: 365 is: 3 x x x 1 Or 3 x x x 10 0
9 + Binary Numbers 9 Start counting 0, 1 Oops, we ve run out of digits Add a column: 00, 01, 10, 11 Oops, we ve run out of digits Add another column: 000, 001, 010, 011, 100, 101, 110, 111 And so on.
10 + Binary Numbers 10 Another way: 1010 is: 0 x x x x 2 0
11 + Activity: Binary Numbers 11 Convert these numbers from binary to decimal Represent the following decimals in binary
12 + Track Changes & Metadata 12
13 + Changes that can be Traced 13 Track Changes Metadata Which also can be forged
14 + Track Changes Embarrassment 14 UN document on the assassination of Lebanese Prime Minister Rafiq hariri Dodgy Dossier used by British government to justify their 2003 entry into the war on Iraq
15 + Representation 15 ASCII vs. raster What are the pros and cons of each? Example: Book of Kells
16 + Compression 16 Compression is necessary sometimes due to the size of the original image or file Two kinds of compression: Lossless Lossy Raster example:
17 + Hiding Things 17
18 + Photo Editing 18 Microsoft edited a photo advertisement
19 + Steganography 19 It is the art and science of writing a message in a way to where the only the recipient knows of its existence. The word Steganography is of Greek origin and means covered, or hidden writing. Steganographic messages will generally appear as something else such as a picture or a text file. Provide security over insecure channel
20 + Steganography 20
21 + Watermarked pdf Example 21
22 + Activity: Watermarked PDFs 22 Download the pdf file to the desktop Open it and view it in Preview. Open Terminal and type the following: cd Desktop head -2 mad-men-denouement.pdf What did you notice?
23 + Watermarked PDFs 23 Download the python script ( ) Type the following in Terminal: python sign-pdf.py mad-men-denouement.pdf JaneDoe ls *.pdf tail -2 JaneDoe.pdf Repeat the process above using a different name
24 + Watermarked PDFs 24 Okay, the files look identical, but can we tell the difference at the bit level? Yes. There is a way of boiling down a file (of any length) down to a 128 bit signature. The technique is called MD5 (the MD stands for Message Digest ). The digest goes by several names, such as checksum (since it's very often used to check the integrity of a file: is a copy correct?). Download the python file ( ) then type in the following in the terminal: python md5.py *.pdf Notice that each file has been boiled down to a signature or checksum. In this case, it's 128 bits long, and the bits are described by a string of hexadecimal digits. This allows us to detect any tampering with the file, as well as being able to ascertain identity.
25 + Activity: Hard Disks 25 How do they work? How can hard disks be truly sanitized? Conduct a little research and come up with three techniques:
26 + References /12/the-tsa-makes-another-stupid-move/ publicexamplesoftrackchanges.html topic=core-pre-algebra
Social Issues. spam Espionage forgery access to your data years from today destroying old records/ data
 CS Concepts document formats interpreting bits ascii, jpg, mp3, meta data representing digital images modeling vs rendering ocr sampling rate cloud computing data compression spatial coherence temporal
CS Concepts document formats interpreting bits ascii, jpg, mp3, meta data representing digital images modeling vs rendering ocr sampling rate cloud computing data compression spatial coherence temporal
15110 PRINCIPLES OF COMPUTING SAMPLE EXAM 2
 15110 PRINCIPLES OF COMPUTING SAMPLE EXAM 2 Name Section Directions: Answer each question neatly in the space provided. Please read each question carefully. You have 50 minutes for this exam. No electronic
15110 PRINCIPLES OF COMPUTING SAMPLE EXAM 2 Name Section Directions: Answer each question neatly in the space provided. Please read each question carefully. You have 50 minutes for this exam. No electronic
Running head: FTK IMAGER 1
 Running head: FTK IMAGER 1 FTK Imager Jean-Raymond Ducasse CSOL-590 June 26, 2017 Thomas Plunkett FTK IMAGER 2 FTK Imager Outline Process for Adding Individual Files & Folders as Evidence Items Although
Running head: FTK IMAGER 1 FTK Imager Jean-Raymond Ducasse CSOL-590 June 26, 2017 Thomas Plunkett FTK IMAGER 2 FTK Imager Outline Process for Adding Individual Files & Folders as Evidence Items Although
GCSE Computing. Revision Pack TWO. Data Representation Questions. Name: /113. Attempt One % Attempt Two % Attempt Three %
 GCSE Computing Revision Pack TWO Data Representation Questions Name: /113 Attempt One % Attempt Two % Attempt Three % Areas of Strength Areas for Development 1. Explain how ASCII is used to represent text
GCSE Computing Revision Pack TWO Data Representation Questions Name: /113 Attempt One % Attempt Two % Attempt Three % Areas of Strength Areas for Development 1. Explain how ASCII is used to represent text
UNIT 7A Data Representation: Numbers and Text. Digital Data
 UNIT 7A Data Representation: Numbers and Text 1 Digital Data 10010101011110101010110101001110 What does this binary sequence represent? It could be: an integer a floating point number text encoded with
UNIT 7A Data Representation: Numbers and Text 1 Digital Data 10010101011110101010110101001110 What does this binary sequence represent? It could be: an integer a floating point number text encoded with
Open source for securing data with advanced Crypto-Steganography technology. 5th, 6th & 7th December, 2009 Pune, INDIA.
 Open source for securing data with advanced Crypto-Steganography technology 5th, 6th & 7th December, 2009 Pune, INDIA Suhas Desai Suhas_Desai/ClubHack2009 1 About me Security analyst. Contributing writer
Open source for securing data with advanced Crypto-Steganography technology 5th, 6th & 7th December, 2009 Pune, INDIA Suhas Desai Suhas_Desai/ClubHack2009 1 About me Security analyst. Contributing writer
Computing in the Modern World
 Computing in the Modern World BCS-CMW-7: Data Representation Wayne Summers Marion County October 25, 2011 There are 10 kinds of people in the world: those who understand binary and those who don t. Pre-exercises
Computing in the Modern World BCS-CMW-7: Data Representation Wayne Summers Marion County October 25, 2011 There are 10 kinds of people in the world: those who understand binary and those who don t. Pre-exercises
Enter the site Title: Student Name s eportfolio Choose your Website Domain: Use a Subdomain of Weebly.com
 Weebly Tutorial Tutorial #1: Signing Up: Welcome to this tutorial. I m going to show you how to sign up for an account with Weebly so you can start building your eportfolio. Go to www.weebly.com. You can
Weebly Tutorial Tutorial #1: Signing Up: Welcome to this tutorial. I m going to show you how to sign up for an account with Weebly so you can start building your eportfolio. Go to www.weebly.com. You can
Analysis of Steganography as a Security Technique
 Analysis of Steganography as a Security Technique Anirudh Sohil Department of Information Technology BVCOE, New Delhi Abstract: Application developers faces many challenges while creating an application
Analysis of Steganography as a Security Technique Anirudh Sohil Department of Information Technology BVCOE, New Delhi Abstract: Application developers faces many challenges while creating an application
Redaction of PDF Files Using Adobe Acrobat Professional X
 Redaction of PDF Files Using Adobe Acrobat Professional X Enterprise Applications Division of the Systems and Network Analysis Center (SNAC) Information Assurance Directorate National Security Agency 9800
Redaction of PDF Files Using Adobe Acrobat Professional X Enterprise Applications Division of the Systems and Network Analysis Center (SNAC) Information Assurance Directorate National Security Agency 9800
Jeff Hinson CS525, Spring 2010
 DIGITAL WATERMARKING Jeff Hinson CS525, Spring 2010 Outline Introduction Challenges Algorithms / Methods Detection Existing Programs Lessons Learned / Conclusion Questions Jeff Hinson CS525 Slide #1 Introduction
DIGITAL WATERMARKING Jeff Hinson CS525, Spring 2010 Outline Introduction Challenges Algorithms / Methods Detection Existing Programs Lessons Learned / Conclusion Questions Jeff Hinson CS525 Slide #1 Introduction
1. Consider the following code snippet. Describe what the user will see when it is executed.
 These are some practice problems for your final. These problems only cover the "new" material we have covered since the last exam. However, your final will be cumulative, with approximately 50% on the
These are some practice problems for your final. These problems only cover the "new" material we have covered since the last exam. However, your final will be cumulative, with approximately 50% on the
Hiding of Random Permutated Encrypted Text using LSB Steganography with Random Pixels Generator
 Hiding of Random Permutated Encrypted Text using LSB Steganography with Random Pixels Generator Noor Kareem Jumaa Department of Computer Technology Engineering Al-Mansour University College, Iraq ABSTRACT
Hiding of Random Permutated Encrypted Text using LSB Steganography with Random Pixels Generator Noor Kareem Jumaa Department of Computer Technology Engineering Al-Mansour University College, Iraq ABSTRACT
And program Office to FlipBook Pro is powerful enough to convert your DOCs to such kind of ebooks with ease.
 Note: This product is distributed on a try-before-you-buy basis. All features described in this documentation are enabled. The unregistered version will be added a demo watermark. About Office to FlipBook
Note: This product is distributed on a try-before-you-buy basis. All features described in this documentation are enabled. The unregistered version will be added a demo watermark. About Office to FlipBook
Overview. Finding information and help Adobe Acrobat. Where to find it and why to use it. When converting from Word to Acrobat
 Formatting 101: Adobe Acrobat October 2017 Overview 2 Finding information and help Adobe Acrobat Where to find it and why to use it How to embed fonts When converting from Word to Acrobat Using the grid
Formatting 101: Adobe Acrobat October 2017 Overview 2 Finding information and help Adobe Acrobat Where to find it and why to use it How to embed fonts When converting from Word to Acrobat Using the grid
CSC 170 Introduction to Computers and Their Applications. Lecture #1 Digital Basics. Data Representation
 CSC 170 Introduction to Computers and Their Applications Lecture #1 Digital Basics Data Representation Data refers to the symbols that represent people, events, things, and ideas. Data can be a name, a
CSC 170 Introduction to Computers and Their Applications Lecture #1 Digital Basics Data Representation Data refers to the symbols that represent people, events, things, and ideas. Data can be a name, a
OCR J276 GCSE Computer Science
 Name: Class Teacher: Date: OCR J276 GCSE Computer Science REVISION BOOKLET 2.6 DATA REPRESENTATION Content in J276 GCSE Computer Science: 1.1 Systems Architecture 1.2 Memory 1.3 Storage 1.4 Wireless and
Name: Class Teacher: Date: OCR J276 GCSE Computer Science REVISION BOOKLET 2.6 DATA REPRESENTATION Content in J276 GCSE Computer Science: 1.1 Systems Architecture 1.2 Memory 1.3 Storage 1.4 Wireless and
umber Systems bit nibble byte word binary decimal
 umber Systems Inside today s computers, data is represented as 1 s and 0 s. These 1 s and 0 s might be stored magnetically on a disk, or as a state in a transistor. To perform useful operations on these
umber Systems Inside today s computers, data is represented as 1 s and 0 s. These 1 s and 0 s might be stored magnetically on a disk, or as a state in a transistor. To perform useful operations on these
Encryption and Forensics/Data Hiding
 Encryption and Forensics/Data Hiding 1 Cryptography Background See: http://www.cacr.math.uwaterloo.ca/hac/ For more information 2 Security Objectives Confidentiality (Secrecy): Prevent/Detect/Deter improper
Encryption and Forensics/Data Hiding 1 Cryptography Background See: http://www.cacr.math.uwaterloo.ca/hac/ For more information 2 Security Objectives Confidentiality (Secrecy): Prevent/Detect/Deter improper
OVERVIEW... 1 WHAT IS A BAG?... 1 BAGGING...
 Bagger OVERVIEW... 1 WHAT IS A BAG?... 1 BAGGING... 3 WHICH WAY IS BETTER?... 3 BAG A COPY... 4 BAG IN PLACE... 12 VALIDATING... 14 APPENDIX A: INSTALLING & RUNNING BAGGER... 16 INSTALLING THE APPLICATION...
Bagger OVERVIEW... 1 WHAT IS A BAG?... 1 BAGGING... 3 WHICH WAY IS BETTER?... 3 BAG A COPY... 4 BAG IN PLACE... 12 VALIDATING... 14 APPENDIX A: INSTALLING & RUNNING BAGGER... 16 INSTALLING THE APPLICATION...
CS Lab 8. Part 1 - Basics of File I/O
 CS 105 - Lab 8 Today, you will be doing a lot with files! We will start with the basics of reading and writing and then expand upon the pixel value work that you did in a previous lab by working on image
CS 105 - Lab 8 Today, you will be doing a lot with files! We will start with the basics of reading and writing and then expand upon the pixel value work that you did in a previous lab by working on image
Memory Addressing, Binary, and Hexadecimal Review
 C++ By A EXAMPLE Memory Addressing, Binary, and Hexadecimal Review You do not have to understand the concepts in this appendix to become well-versed in C++. You can master C++, however, only if you spend
C++ By A EXAMPLE Memory Addressing, Binary, and Hexadecimal Review You do not have to understand the concepts in this appendix to become well-versed in C++. You can master C++, however, only if you spend
Data Representation From 0s and 1s to images CPSC 101
 Data Representation From 0s and 1s to images CPSC 101 Learning Goals After the Data Representation: Images unit, you will be able to: Recognize and translate between binary and decimal numbers Define bit,
Data Representation From 0s and 1s to images CPSC 101 Learning Goals After the Data Representation: Images unit, you will be able to: Recognize and translate between binary and decimal numbers Define bit,
Unit 2 Digital Information. Chapter 1 Study Guide
 Unit 2 Digital Information Chapter 1 Study Guide 2.5 Wrap Up Other file formats Other file formats you may have encountered or heard of include:.doc,.docx,.pdf,.mp4,.mov The file extension you often see
Unit 2 Digital Information Chapter 1 Study Guide 2.5 Wrap Up Other file formats Other file formats you may have encountered or heard of include:.doc,.docx,.pdf,.mp4,.mov The file extension you often see
Digital Data. 10/11/2011 Prepared by: Khuzaima Jallad
 Chapter 2 Digital Data Elements of Digital Data Digital Codes Files Digitization File Compression Advantages of Digital Information Challenges of Digital Information 2 Digital Data ELEMENTS OF DIGITAL
Chapter 2 Digital Data Elements of Digital Data Digital Codes Files Digitization File Compression Advantages of Digital Information Challenges of Digital Information 2 Digital Data ELEMENTS OF DIGITAL
DATA HIDING IN PDF FILES AND APPLICATIONS BY IMPERCEIVABLE MODIFICATIONS OF PDF OBJECT PARAMETERS
 DATA HIDING IN PDF FILES AND APPLICATIONS BY IMPERCEIVABLE MODIFICATIONS OF PDF OBJECT PARAMETERS 1 Jiun-Tsung Wang ( 王竣聰 ) and 2 Wen-Hsiang Tsai ( 蔡文祥 ) 1 Institute of Multimedia Eng., National Chiao
DATA HIDING IN PDF FILES AND APPLICATIONS BY IMPERCEIVABLE MODIFICATIONS OF PDF OBJECT PARAMETERS 1 Jiun-Tsung Wang ( 王竣聰 ) and 2 Wen-Hsiang Tsai ( 蔡文祥 ) 1 Institute of Multimedia Eng., National Chiao
OTP-Steg. One-Time Pad Image Steganography Using OTP-Steg V.1.0 Software October 2015 Dr. Michael J. Pelosi
 OTP-Steg One-Time Pad Image Steganography Using OTP-Steg V.1.0 Software October 2015 Dr. Michael J. Pelosi What is Steganography? Steganography literally means covered writing Encompasses methods of transmitting
OTP-Steg One-Time Pad Image Steganography Using OTP-Steg V.1.0 Software October 2015 Dr. Michael J. Pelosi What is Steganography? Steganography literally means covered writing Encompasses methods of transmitting
Introduction to Cryptography. Vasil Slavov William Jewell College
 Introduction to Cryptography Vasil Slavov William Jewell College Crypto definitions Cryptography studies how to keep messages secure Cryptanalysis studies how to break ciphertext Cryptology branch of mathematics,
Introduction to Cryptography Vasil Slavov William Jewell College Crypto definitions Cryptography studies how to keep messages secure Cryptanalysis studies how to break ciphertext Cryptology branch of mathematics,
ASCII Art. Introduction: Python
 Python 1 ASCII Art All Code Clubs must be registered. Registered clubs appear on the map at codeclub.org.uk - if your club is not on the map then visit jumpto.cc/18cplpy to find out what to do. Introduction:
Python 1 ASCII Art All Code Clubs must be registered. Registered clubs appear on the map at codeclub.org.uk - if your club is not on the map then visit jumpto.cc/18cplpy to find out what to do. Introduction:
Steganography. Brent McClain Rob Carey
 Steganography Brent McClain Rob Carey What is Steganography Greek Origin Steganos means covered Graph means writing Hiding information in plain sight Cover Image Another image hidden in the picture Created
Steganography Brent McClain Rob Carey What is Steganography Greek Origin Steganos means covered Graph means writing Hiding information in plain sight Cover Image Another image hidden in the picture Created
CPSC 301: Computing in the Life Sciences Lecture Notes 16: Data Representation
 CPSC 301: Computing in the Life Sciences Lecture Notes 16: Data Representation George Tsiknis University of British Columbia Department of Computer Science Winter Term 2, 2015-2016 Last updated: 04/04/2016
CPSC 301: Computing in the Life Sciences Lecture Notes 16: Data Representation George Tsiknis University of British Columbia Department of Computer Science Winter Term 2, 2015-2016 Last updated: 04/04/2016
2nd Paragraph should make a point (could be an advantage or disadvantage) and explain the point fully giving an example where necessary.
 STUDENT TEACHER WORKING AT GRADE TERM TARGET CLASS YEAR TARGET The long answer questions in this booklet are designed to stretch and challenge you. It is important that you understand how they should be
STUDENT TEACHER WORKING AT GRADE TERM TARGET CLASS YEAR TARGET The long answer questions in this booklet are designed to stretch and challenge you. It is important that you understand how they should be
Clemens H. Cap Universität Rostock clemens.cap (at) uni-rostock (dot) de STEGANOGRAPHY. BaSoTI 2012, Tartu
 Clemens H. Cap Universität Rostock clemens.cap (at) uni-rostock (dot) de STEGANOGRAPHY BaSoTI 2012, Tartu Question Definition Can we send hidden information? Steganography is the art of transmitting information
Clemens H. Cap Universität Rostock clemens.cap (at) uni-rostock (dot) de STEGANOGRAPHY BaSoTI 2012, Tartu Question Definition Can we send hidden information? Steganography is the art of transmitting information
Conventional Protection Mechanisms in File Systems
 Steganographic File Systems 1 Conventional Protection Mechanisms in File Systems User Access Control The operating system is fully trusted to enforce the security policy. Is it good enough? Operating System
Steganographic File Systems 1 Conventional Protection Mechanisms in File Systems User Access Control The operating system is fully trusted to enforce the security policy. Is it good enough? Operating System
STEGANOGRAPHY Question Definition. Historical Cases of Steganography. Can we send hidden information?
 Clemens H. Cap Universität Rostock clemens.cap (at) uni rostock (dot) de STEGANOGRAPHY Question Definition Can we send hidden information? Steganography is the art of transmitting information but hiding
Clemens H. Cap Universität Rostock clemens.cap (at) uni rostock (dot) de STEGANOGRAPHY Question Definition Can we send hidden information? Steganography is the art of transmitting information but hiding
Chapter 2 Number Systems and Codes Dr. Xu
 Chapter 2 Number Systems and Codes Dr. Xu Chapter 2 Objectives Selected areas covered in this chapter: Converting between number systems. Decimal, binary, hexadecimal. Advantages of the hexadecimal number
Chapter 2 Number Systems and Codes Dr. Xu Chapter 2 Objectives Selected areas covered in this chapter: Converting between number systems. Decimal, binary, hexadecimal. Advantages of the hexadecimal number
Search Engines. Information Retrieval in Practice
 Search Engines Information Retrieval in Practice All slides Addison Wesley, 2008 Web Crawler Finds and downloads web pages automatically provides the collection for searching Web is huge and constantly
Search Engines Information Retrieval in Practice All slides Addison Wesley, 2008 Web Crawler Finds and downloads web pages automatically provides the collection for searching Web is huge and constantly
EIDR: ID FORMAT. Ver January 2012
 EIDR: ID FORMAT Ver. 1.02 30 January 2012 Copyright 2012 by the Entertainment ID Registry Association EIDR: ID Format. The content of this manual is furnished for information use only and is subject to
EIDR: ID FORMAT Ver. 1.02 30 January 2012 Copyright 2012 by the Entertainment ID Registry Association EIDR: ID Format. The content of this manual is furnished for information use only and is subject to
15-110: Principles of Computing, Spring Problem Set 6 (PS6) Due: Friday, March 2 by 2:30PM via Gradescope Hand-in
 15-110: Principles of Computing, Spring 2018 Problem Set 6 (PS6) Due: Friday, March 2 by 2:30PM via Gradescope Hand-in HANDIN INSTRUCTIONS Download a copy of this PDF file. You have two ways to fill in
15-110: Principles of Computing, Spring 2018 Problem Set 6 (PS6) Due: Friday, March 2 by 2:30PM via Gradescope Hand-in HANDIN INSTRUCTIONS Download a copy of this PDF file. You have two ways to fill in
Image Processor. Copyright 18/04/2018 by clive homewood. All Rights Reserved.
 Copyright 18/04/2018 by clive homewood. All Rights Reserved. Table of contents Introduction... 3 Getting Started... 3 System requirements... 3 Application Layout... 3 Area Description... 4 Login... 7 Step
Copyright 18/04/2018 by clive homewood. All Rights Reserved. Table of contents Introduction... 3 Getting Started... 3 System requirements... 3 Application Layout... 3 Area Description... 4 Login... 7 Step
2. Opening, Editing and Saving Documents
 55 2. Opening, Editing and Saving Documents It is very easy to edit text on a computer. This is one of the reasons why computers have become so popular. No endless re-typing, no correction fluid or tape
55 2. Opening, Editing and Saving Documents It is very easy to edit text on a computer. This is one of the reasons why computers have become so popular. No endless re-typing, no correction fluid or tape
But I know what most of you will do: use a calculator to convert; that's fine, IF you understand the theory.
 Numbers After you have read this, the next section will show how to use a This and other videos related to numbers and colors are available on the class web site. Why are there different numbering systems?
Numbers After you have read this, the next section will show how to use a This and other videos related to numbers and colors are available on the class web site. Why are there different numbering systems?
A Study Of Steganography And The Art Of Hiding Information. Alain C. Brainos II. East Carolina University
 A Study Of Steganography 1 STEGANOGRAPHY STUDY A Study Of Steganography And The Art Of Hiding Information Alain C. Brainos II East Carolina University A Study Of Steganography 2 Abstract The recently created
A Study Of Steganography 1 STEGANOGRAPHY STUDY A Study Of Steganography And The Art Of Hiding Information Alain C. Brainos II East Carolina University A Study Of Steganography 2 Abstract The recently created
Administrative Notes February 9, 2017
 Administrative Notes February 9, 2017 Feb 10: Project proposal resubmission (optional) Feb 13: Art and Images reading quiz Feb 17: In the News call #2 Data Representation: Part 2 Text representation Colour
Administrative Notes February 9, 2017 Feb 10: Project proposal resubmission (optional) Feb 13: Art and Images reading quiz Feb 17: In the News call #2 Data Representation: Part 2 Text representation Colour
The inspection tool lets you inspect a document for metadata, like author information, headers and footers, and other information that may be hidden
 7 8 The inspection tool lets you inspect a document for metadata, like author information, headers and footers, and other information that may be hidden in your document before you post it in a public
7 8 The inspection tool lets you inspect a document for metadata, like author information, headers and footers, and other information that may be hidden in your document before you post it in a public
Desktop Crawls. Document Feeds. Document Feeds. Information Retrieval
 Information Retrieval INFO 4300 / CS 4300! Web crawlers Retrieving web pages Crawling the web» Desktop crawlers» Document feeds File conversion Storing the documents Removing noise Desktop Crawls! Used
Information Retrieval INFO 4300 / CS 4300! Web crawlers Retrieving web pages Crawling the web» Desktop crawlers» Document feeds File conversion Storing the documents Removing noise Desktop Crawls! Used
GCSE Computer Science Component 02
 GCSE Computer Science Component 02 Revision Computational Thinking ABSTRACTION Making a problem simpler by removing unnecessary details. This is important when coding as it: Makes it easier to code! Means
GCSE Computer Science Component 02 Revision Computational Thinking ABSTRACTION Making a problem simpler by removing unnecessary details. This is important when coding as it: Makes it easier to code! Means
Operating Systems. Engr. Abdul-Rahman Mahmood MS, PMP, MCP, QMR(ISO9001:2000) alphapeeler.sf.net/pubkeys/pkey.htm
 Operating Systems Engr. Abdul-Rahman Mahmood MS, PMP, MCP, QMR(ISO9001:2000) armahmood786@yahoo.com alphasecure@gmail.com alphapeeler.sf.net/pubkeys/pkey.htm http://alphapeeler.sourceforge.net pk.linkedin.com/in/armahmood
Operating Systems Engr. Abdul-Rahman Mahmood MS, PMP, MCP, QMR(ISO9001:2000) armahmood786@yahoo.com alphasecure@gmail.com alphapeeler.sf.net/pubkeys/pkey.htm http://alphapeeler.sourceforge.net pk.linkedin.com/in/armahmood
Dissecting Files. Endianness. So Many Bytes. Big Endian vs. Little Endian. Example Number. The "proper" order of things. Week 6
 Dissecting Files Endianness Week 6 The "proper" order of things So Many Bytes So Many Bytes On a 32-bit system, each word consists of 4 bytes So, when any 32-bit value is stored in memory, each of those
Dissecting Files Endianness Week 6 The "proper" order of things So Many Bytes So Many Bytes On a 32-bit system, each word consists of 4 bytes So, when any 32-bit value is stored in memory, each of those
Unit 10: Data Structures CS 101, Fall 2018
 Unit 10: Data Structures CS 101, Fall 2018 Learning Objectives After completing this unit, you should be able to: Define and give everyday examples of arrays, stacks, queues, and trees. Explain what a
Unit 10: Data Structures CS 101, Fall 2018 Learning Objectives After completing this unit, you should be able to: Define and give everyday examples of arrays, stacks, queues, and trees. Explain what a
CS Final Exam. Stanford University Computer Science Department. June 5, 2012 !!!!! SKIP 15 POINTS WORTH OF QUESTIONS.!!!!!
 CS 240 - Final Exam Stanford University Computer Science Department June 5, 2012!!!!! SKIP 15 POINTS WORTH OF QUESTIONS.!!!!! This is an open-book (but closed-laptop) exam. You have 75 minutes. Cross out
CS 240 - Final Exam Stanford University Computer Science Department June 5, 2012!!!!! SKIP 15 POINTS WORTH OF QUESTIONS.!!!!! This is an open-book (but closed-laptop) exam. You have 75 minutes. Cross out
Continental Mathematics League
 Continental Mathematics League 2015-2016 Computer Science Contest Grades 3-5 The contest consists of three meets. Each meet has six questions for 30 minutes. Note: Some questions have multiple answers.
Continental Mathematics League 2015-2016 Computer Science Contest Grades 3-5 The contest consists of three meets. Each meet has six questions for 30 minutes. Note: Some questions have multiple answers.
Quantum Encryption Keys
 Quantum Technology PROGRAMME ACTIVITY SHEETS Quantum Encryption Keys SHARING DECRYPTION KEYS AND DECODING MESSAGES Every time you send an email or you pay for something online, or with your debit card,
Quantum Technology PROGRAMME ACTIVITY SHEETS Quantum Encryption Keys SHARING DECRYPTION KEYS AND DECODING MESSAGES Every time you send an email or you pay for something online, or with your debit card,
Security+ Guide to Network Security Fundamentals, Third Edition. Chapter 11 Basic Cryptography
 Security+ Guide to Network Security Fundamentals, Third Edition Chapter 11 Basic Cryptography Objectives Define cryptography Describe hashing List the basic symmetric cryptographic algorithms 2 Objectives
Security+ Guide to Network Security Fundamentals, Third Edition Chapter 11 Basic Cryptography Objectives Define cryptography Describe hashing List the basic symmetric cryptographic algorithms 2 Objectives
Data Storage. Slides derived from those available on the web site of the book: Computer Science: An Overview, 11 th Edition, by J.
 Data Storage Slides derived from those available on the web site of the book: Computer Science: An Overview, 11 th Edition, by J. Glenn Brookshear Copyright 2012 Pearson Education, Inc. Data Storage Bits
Data Storage Slides derived from those available on the web site of the book: Computer Science: An Overview, 11 th Edition, by J. Glenn Brookshear Copyright 2012 Pearson Education, Inc. Data Storage Bits
LSB Based Audio Steganography Using Pattern Matching
 ISSN: 359-0040 Vol 2 Issue, November - 205 LSB Based Audio Steganography Using Pattern Matching Mr Ratul Choudhury Student, Dept of Computer Sc & Engg Dept University of Calcutta Kolkata, India ratulchowdhury@iemcalcom
ISSN: 359-0040 Vol 2 Issue, November - 205 LSB Based Audio Steganography Using Pattern Matching Mr Ratul Choudhury Student, Dept of Computer Sc & Engg Dept University of Calcutta Kolkata, India ratulchowdhury@iemcalcom
Compression-Compatible Fragile and Semi-Fragile Tamper Detection
 Compression-Compatible Fragile and Semi-Fragile Tamper Detection Lisa M. Marvel George W. Hartwig, Jr. Charles Boncelet, Jr. Presentation by Peter Macko Motivation Direct Applications Establishing credibility
Compression-Compatible Fragile and Semi-Fragile Tamper Detection Lisa M. Marvel George W. Hartwig, Jr. Charles Boncelet, Jr. Presentation by Peter Macko Motivation Direct Applications Establishing credibility
A Detailed look of Audio Steganography Techniques using LSB and Genetic Algorithm Approach
 www.ijcsi.org 402 A Detailed look of Audio Steganography Techniques using LSB and Genetic Algorithm Approach Gunjan Nehru 1, Puja Dhar 2 1 Department of Information Technology, IEC-Group of Institutions
www.ijcsi.org 402 A Detailed look of Audio Steganography Techniques using LSB and Genetic Algorithm Approach Gunjan Nehru 1, Puja Dhar 2 1 Department of Information Technology, IEC-Group of Institutions
MAIL MERGE MARKETING WITH CARDEX
 This procedure contains several steps to accomplish exporting the Cardex records to a text file and merging the exported Cardex data to Microsoft Word for address labels. Exporting the Cardex records to
This procedure contains several steps to accomplish exporting the Cardex records to a text file and merging the exported Cardex data to Microsoft Word for address labels. Exporting the Cardex records to
Packet Trace Simulation. School Scavenger Hunt Style Activity
 Packet Trace Simulation School Scavenger Hunt Style Activity Objective Students will simulate packet transfer to better understand process and procedures in data transmission including parts of a header,
Packet Trace Simulation School Scavenger Hunt Style Activity Objective Students will simulate packet transfer to better understand process and procedures in data transmission including parts of a header,
Reference Services Division Presents. Saving & Printing
 Reference Services Division Presents Saving & Printing Welcome to Saving & Printing. In this class, we will learn how to save and print in a Windows-based PC environment. Basic computer skills, including
Reference Services Division Presents Saving & Printing Welcome to Saving & Printing. In this class, we will learn how to save and print in a Windows-based PC environment. Basic computer skills, including
Midterm Exam 2A Principles of Computing Fall November 10, 2014
 Midterm Exam 2A 15110 Principles of Computing Fall 2014 November 10, 2014 Name: Andrew ID: Lab section: Instructions Answer each question neatly in the space provided. There are 6 questions totaling 28
Midterm Exam 2A 15110 Principles of Computing Fall 2014 November 10, 2014 Name: Andrew ID: Lab section: Instructions Answer each question neatly in the space provided. There are 6 questions totaling 28
Should you know scanf and printf?
 C-LANGUAGE INPUT & OUTPUT C-Language Output with printf Input with scanf and gets_s and Defensive Programming Copyright 2016 Dan McElroy Should you know scanf and printf? scanf is only useful in the C-language,
C-LANGUAGE INPUT & OUTPUT C-Language Output with printf Input with scanf and gets_s and Defensive Programming Copyright 2016 Dan McElroy Should you know scanf and printf? scanf is only useful in the C-language,
DATA REPRESENTATION. By- Neha Tyagi PGT CS KV 5 Jaipur II Shift, Jaipur Region. Based on CBSE curriculum Class 11. Neha Tyagi, KV 5 Jaipur II Shift
 DATA REPRESENTATION Based on CBSE curriculum Class 11 By- Neha Tyagi PGT CS KV 5 Jaipur II Shift, Jaipur Region Neha Tyagi, KV 5 Jaipur II Shift Introduction As we know that computer system stores any
DATA REPRESENTATION Based on CBSE curriculum Class 11 By- Neha Tyagi PGT CS KV 5 Jaipur II Shift, Jaipur Region Neha Tyagi, KV 5 Jaipur II Shift Introduction As we know that computer system stores any
Stonelaw High School. Computing Science. BGE - Computer Systems
 Stonelaw High School Computing Science BGE - Computer Systems Contents Computer Systems... 3 Computer Systems... 3 Hardware & Software... 3 Data Representation... 3 Representing Positive Integers... 3
Stonelaw High School Computing Science BGE - Computer Systems Contents Computer Systems... 3 Computer Systems... 3 Hardware & Software... 3 Data Representation... 3 Representing Positive Integers... 3
Digital Media. Daniel Fuller ITEC 2110
 Digital Media Daniel Fuller ITEC 2110 Daily Question: Which statement is True? 5 + 5 = 10 1 + 1 = 10 F + 1 = 10 Email answer to DFullerDailyQuestion@gmail.com Subject Line: ITEC2110-26 First, some mac
Digital Media Daniel Fuller ITEC 2110 Daily Question: Which statement is True? 5 + 5 = 10 1 + 1 = 10 F + 1 = 10 Email answer to DFullerDailyQuestion@gmail.com Subject Line: ITEC2110-26 First, some mac
CS 100 Spring Lecture Notes 3/8/05 Review for Exam 2
 CS 100 Spring 2005 Lecture Notes 3/8/05 Review for Exam 2 The second exam is Thursday, March 10. It will cover topics from Homework 2 through Homework 4, including anything pertaining to binary representation.
CS 100 Spring 2005 Lecture Notes 3/8/05 Review for Exam 2 The second exam is Thursday, March 10. It will cover topics from Homework 2 through Homework 4, including anything pertaining to binary representation.
Name EGR 2131 Lab #6 Number Representation and Arithmetic Circuits
 Name EGR 2131 Lab #6 Number Representation and Arithmetic Circuits Equipment and Components Quartus software and Altera DE2-115 board PART 1: Number Representation in Microsoft Calculator. First, let s
Name EGR 2131 Lab #6 Number Representation and Arithmetic Circuits Equipment and Components Quartus software and Altera DE2-115 board PART 1: Number Representation in Microsoft Calculator. First, let s
Example 1: Denary = 1. Answer: Binary = (1 * 1) = 1. Example 2: Denary = 3. Answer: Binary = (1 * 1) + (2 * 1) = 3
 1.1.1 Binary systems In mathematics and digital electronics, a binary number is a number expressed in the binary numeral system, or base-2 numeral system, which represents numeric values using two different
1.1.1 Binary systems In mathematics and digital electronics, a binary number is a number expressed in the binary numeral system, or base-2 numeral system, which represents numeric values using two different
Introduction. You might be interested in the system requirements, the installation, payment and registration procedures.
 Introduction Contenta NEF Converter is a simple and powerful tool to convert your NEF photos. It does support a very wide range of Nikon cameras. It is simple to use because of its intuitive interface
Introduction Contenta NEF Converter is a simple and powerful tool to convert your NEF photos. It does support a very wide range of Nikon cameras. It is simple to use because of its intuitive interface
Lab 5: Ciphers and Crypto Fundamentals
 Lab 5: Ciphers and Crypto Fundamentals Aim: Bill, Richard, Charley The aim of this lab is to give an introduction to ciphers, basic encoding/decoding techniques and frequency analysis, as to provide some
Lab 5: Ciphers and Crypto Fundamentals Aim: Bill, Richard, Charley The aim of this lab is to give an introduction to ciphers, basic encoding/decoding techniques and frequency analysis, as to provide some
intergraded format for quickly viewing, "Burn to CD" to output your digital books directly on CD ROM.
 Note: This product is distributed on a try-before-you-buy basis. All features described in this documentation are enabled. The registered version does not insert a watermark in your generated Flash Flip
Note: This product is distributed on a try-before-you-buy basis. All features described in this documentation are enabled. The registered version does not insert a watermark in your generated Flash Flip
15110 Principles of Computing, Carnegie Mellon University - CORTINA. Digital Data
 UNIT 7A Data Representa1on: Numbers and Text 1 Digital Data 10010101011110101010110101001110 What does this binary sequence represent? It could be: an integer a floa1ng point number text encoded with ASCII
UNIT 7A Data Representa1on: Numbers and Text 1 Digital Data 10010101011110101010110101001110 What does this binary sequence represent? It could be: an integer a floa1ng point number text encoded with ASCII
Experiments in Mathematical Web Animation
 Experiments in Mathematical Web Animation Steven Bellenot Mathematics Florida State University bellenot@math.fsu.edu http://www.math.fsu.edu/ bellenot/class/f0/web/anim.pdf Mathematics and the Web Sep,
Experiments in Mathematical Web Animation Steven Bellenot Mathematics Florida State University bellenot@math.fsu.edu http://www.math.fsu.edu/ bellenot/class/f0/web/anim.pdf Mathematics and the Web Sep,
A Guide to using Social Media (Facebook and Twitter)
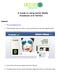 A Guide to using Social Media (Facebook and Twitter) Facebook 1. Visit www.facebook.com 2. Click the green Sign up button on the top left-hand corner (see diagram below) 3. Enter all the information required
A Guide to using Social Media (Facebook and Twitter) Facebook 1. Visit www.facebook.com 2. Click the green Sign up button on the top left-hand corner (see diagram below) 3. Enter all the information required
A Data Hiding Model for Image Steganography Using Primes: Towards Data Security
 International Journal of Computational Engineering & Management, Vol. 15 Issue 3, May 2012 www..org 1 A Data Hiding Model for Image Steganography Using Primes: Towards Data Security Mamatha.T Assistant
International Journal of Computational Engineering & Management, Vol. 15 Issue 3, May 2012 www..org 1 A Data Hiding Model for Image Steganography Using Primes: Towards Data Security Mamatha.T Assistant
CS107, Lecture 3 Bits and Bytes; Bitwise Operators
 CS107, Lecture 3 Bits and Bytes; Bitwise Operators reading: Bryant & O Hallaron, Ch. 2.1 This document is copyright (C) Stanford Computer Science and Nick Troccoli, licensed under Creative Commons Attribution
CS107, Lecture 3 Bits and Bytes; Bitwise Operators reading: Bryant & O Hallaron, Ch. 2.1 This document is copyright (C) Stanford Computer Science and Nick Troccoli, licensed under Creative Commons Attribution
COMPSCI 120 Fall 2017 Review Questions for Midterm #2 Professor William T. Verts
 COMPSCI 120 Fall 2017 Review Questions for Midterm #2 Professor William T. Verts UNIX What do the 9 permission letters represent (rwxrwxrwx)? How do you know if you have the permission or not? What is
COMPSCI 120 Fall 2017 Review Questions for Midterm #2 Professor William T. Verts UNIX What do the 9 permission letters represent (rwxrwxrwx)? How do you know if you have the permission or not? What is
A New Symmetric Key Algorithm for Modern Cryptography Rupesh Kumar 1 Sanjay Patel 2 Purushottam Patel 3 Rakesh Patel 4
 IJSRD - International Journal for Scientific Research & Development Vol. 2, Issue 08, 2014 ISSN (online): 2321-0613 A New Symmetric Key Algorithm for Modern Cryptography Rupesh Kumar 1 Sanjay Patel 2 Purushottam
IJSRD - International Journal for Scientific Research & Development Vol. 2, Issue 08, 2014 ISSN (online): 2321-0613 A New Symmetric Key Algorithm for Modern Cryptography Rupesh Kumar 1 Sanjay Patel 2 Purushottam
DIGITAL STEGANOGRAPHY 1 DIGITAL STEGANOGRAPHY
 DIGITAL STEGANOGRAPHY 1 DIGITAL STEGANOGRAPHY DIGITAL STEGANOGRAPHY 2 Abstract Steganography derives from a Greek word and means covered writing. It is a sector of computer information security. Cryptography
DIGITAL STEGANOGRAPHY 1 DIGITAL STEGANOGRAPHY DIGITAL STEGANOGRAPHY 2 Abstract Steganography derives from a Greek word and means covered writing. It is a sector of computer information security. Cryptography
Flipping Book Publisher for Image also provides different output methods for you to publish your
 Note: This product is distributed on a try-before-you-buy basis. All features described in this documentation are enabled. The unregistered version will be added a demo watermark. About Flipping Book Publisher
Note: This product is distributed on a try-before-you-buy basis. All features described in this documentation are enabled. The unregistered version will be added a demo watermark. About Flipping Book Publisher
Technical concepts. Some basics of computers today. Comp 399
 Technical concepts Some basics of computers today. Comp 399 Admin Anyone new?. http://www.cnn.com/2013/07/12/tech/social-media http://tv.msnbc.com/2013/08/13/pre-trial-hearings- Locard's Exchange Principle
Technical concepts Some basics of computers today. Comp 399 Admin Anyone new?. http://www.cnn.com/2013/07/12/tech/social-media http://tv.msnbc.com/2013/08/13/pre-trial-hearings- Locard's Exchange Principle
FLIP BOOK MAKER FOR EPUB. Flip Book Maker for epub Create Amazing Page-flipping ebooks with EPUB. User Documentation
 WWW.FLIPBOOKMAKER.COM FLIP BOOK MAKER FOR EPUB Page 1 of 33 Create your flipping book from EPUB files Note: This product is distributed on a try-before-you-buy basis. All features described in this documentation
WWW.FLIPBOOKMAKER.COM FLIP BOOK MAKER FOR EPUB Page 1 of 33 Create your flipping book from EPUB files Note: This product is distributed on a try-before-you-buy basis. All features described in this documentation
Flip Book Maker for Image Scan files into Page-flipping ebooks directly. User Documentation. About Flip Book Maker for Image. Detail features include:
 Note: This product is distributed on a try-before-you-buy basis. All features described in this documentation are enabled. The unregistered version will be added a demo watermark. About Flip Book Maker
Note: This product is distributed on a try-before-you-buy basis. All features described in this documentation are enabled. The unregistered version will be added a demo watermark. About Flip Book Maker
Using BBC Raw
 Electronic mail, or email is a quick way of sending messages to people using the internet. As with a postal address, an email address is made up of different parts, for example: tom@bbc.co.uk tom is your
Electronic mail, or email is a quick way of sending messages to people using the internet. As with a postal address, an email address is made up of different parts, for example: tom@bbc.co.uk tom is your
Electronic mail, or is a quick way of sending messages to people using the internet.
 Using email Electronic mail, or email is a quick way of sending messages to people using the internet. As with a postal address, an email address is made up of different parts, for example: tom@bbc.co.uk
Using email Electronic mail, or email is a quick way of sending messages to people using the internet. As with a postal address, an email address is made up of different parts, for example: tom@bbc.co.uk
Project 3: RPN Calculator
 ECE267 @ UIC, Spring 2012, Wenjing Rao Project 3: RPN Calculator What to do: Ask the user to input a string of expression in RPN form (+ - * / ), use a stack to evaluate the result and display the result
ECE267 @ UIC, Spring 2012, Wenjing Rao Project 3: RPN Calculator What to do: Ask the user to input a string of expression in RPN form (+ - * / ), use a stack to evaluate the result and display the result
A Novel Information Security Scheme using Cryptic Steganography
 A Novel Information Security Scheme using Cryptic Steganography B.RAJA RAO Associate Professor, E.C.E Dept raja_rao_b@ yahoo.com P.ANIL KUMAR Assistant Professor, I.T Dept anilkumar_pallikonda@yahoo.co.in
A Novel Information Security Scheme using Cryptic Steganography B.RAJA RAO Associate Professor, E.C.E Dept raja_rao_b@ yahoo.com P.ANIL KUMAR Assistant Professor, I.T Dept anilkumar_pallikonda@yahoo.co.in
Digital Fundamentals. CHAPTER 2 Number Systems, Operations, and Codes
 Digital Fundamentals CHAPTER 2 Number Systems, Operations, and Codes Decimal Numbers The decimal number system has ten digits: 0, 1, 2, 3, 4, 5, 6, 7, 8, and 9 The decimal numbering system has a base of
Digital Fundamentals CHAPTER 2 Number Systems, Operations, and Codes Decimal Numbers The decimal number system has ten digits: 0, 1, 2, 3, 4, 5, 6, 7, 8, and 9 The decimal numbering system has a base of
IPSec. Slides by Vitaly Shmatikov UT Austin. slide 1
 IPSec Slides by Vitaly Shmatikov UT Austin slide 1 TCP/IP Example slide 2 IP Security Issues Eavesdropping Modification of packets in transit Identity spoofing (forged source IP addresses) Denial of service
IPSec Slides by Vitaly Shmatikov UT Austin slide 1 TCP/IP Example slide 2 IP Security Issues Eavesdropping Modification of packets in transit Identity spoofing (forged source IP addresses) Denial of service
UWDCC Case Study. Supplementing DPOE Workshop 6 June Steven Dast Digital Asset Librarian UW Digital Collections Center
 UWDCC Case Study Supplementing DPOE Workshop 6 June 2016 Steven Dast Digital Asset Librarian UW Digital Collections Center 2,175,000 page images 225,000 multimedia files 2.4 million digital objects
UWDCC Case Study Supplementing DPOE Workshop 6 June 2016 Steven Dast Digital Asset Librarian UW Digital Collections Center 2,175,000 page images 225,000 multimedia files 2.4 million digital objects
Bits and Bit Patterns
 Bits and Bit Patterns Bit: Binary Digit (0 or 1) Bit Patterns are used to represent information. Numbers Text characters Images Sound And others 0-1 Boolean Operations Boolean Operation: An operation that
Bits and Bit Patterns Bit: Binary Digit (0 or 1) Bit Patterns are used to represent information. Numbers Text characters Images Sound And others 0-1 Boolean Operations Boolean Operation: An operation that
Bits, bytes, binary numbers, and the representation of information
 Bits, bytes, binary numbers, and the representation of information computers represent, process, store, copy, and transmit everything as numbers hence "digital computer" the numbers can represent anything
Bits, bytes, binary numbers, and the representation of information computers represent, process, store, copy, and transmit everything as numbers hence "digital computer" the numbers can represent anything
Image Types Vector vs. Raster
 Image Types Have you ever wondered when you should use a JPG instead of a PNG? Or maybe you are just trying to figure out which program opens an INDD? Unless you are a graphic designer by training (like
Image Types Have you ever wondered when you should use a JPG instead of a PNG? Or maybe you are just trying to figure out which program opens an INDD? Unless you are a graphic designer by training (like
Chapter 1. Getting Started
 Chapter 1. Hey, Logy, whatcha doing? What s it look like I m doing. I m cleaning the windows so we can get started on our new adventure. Can t you leave the housekeeping until later. We ve got Logo work
Chapter 1. Hey, Logy, whatcha doing? What s it look like I m doing. I m cleaning the windows so we can get started on our new adventure. Can t you leave the housekeeping until later. We ve got Logo work
Chapter 1. Data Storage Pearson Addison-Wesley. All rights reserved
 Chapter 1 Data Storage 2007 Pearson Addison-Wesley. All rights reserved Chapter 1: Data Storage 1.1 Bits and Their Storage 1.2 Main Memory 1.3 Mass Storage 1.4 Representing Information as Bit Patterns
Chapter 1 Data Storage 2007 Pearson Addison-Wesley. All rights reserved Chapter 1: Data Storage 1.1 Bits and Their Storage 1.2 Main Memory 1.3 Mass Storage 1.4 Representing Information as Bit Patterns
Data Hiding on Text Using Big-5 Code
 Data Hiding on Text Using Big-5 Code Jun-Chou Chuang 1 and Yu-Chen Hu 2 1 Department of Computer Science and Communication Engineering Providence University 200 Chung-Chi Rd., Shalu, Taichung 43301, Republic
Data Hiding on Text Using Big-5 Code Jun-Chou Chuang 1 and Yu-Chen Hu 2 1 Department of Computer Science and Communication Engineering Providence University 200 Chung-Chi Rd., Shalu, Taichung 43301, Republic
Image Steganography (cont.)
 Image Steganography (cont.) 2.2) Image Steganography: Use of Discrete Cosine Transform (DCT) DCT is one of key components of JPEG compression JPEG algorithm: (1) algorithm is split in 8x8 pixel squares
Image Steganography (cont.) 2.2) Image Steganography: Use of Discrete Cosine Transform (DCT) DCT is one of key components of JPEG compression JPEG algorithm: (1) algorithm is split in 8x8 pixel squares
Data Representation. Types of data: Numbers Text Audio Images & Graphics Video
 Data Representation Data Representation Types of data: Numbers Text Audio Images & Graphics Video Analog vs Digital data How is data represented? What is a signal? Transmission of data Analog vs Digital
Data Representation Data Representation Types of data: Numbers Text Audio Images & Graphics Video Analog vs Digital data How is data represented? What is a signal? Transmission of data Analog vs Digital
Practical Aspects of Modern Cryptography
 Practical Aspects of Modern Cryptography Lecture 3: Symmetric s and Hash Functions Josh Benaloh & Brian LaMacchia Meet Alice and Bob Alice Bob Message Modern Symmetric s Setup: Alice wants to send a private
Practical Aspects of Modern Cryptography Lecture 3: Symmetric s and Hash Functions Josh Benaloh & Brian LaMacchia Meet Alice and Bob Alice Bob Message Modern Symmetric s Setup: Alice wants to send a private
