Php-Brute-Force-Attack-Detector
|
|
|
- Alexandrina Roberts
- 6 years ago
- Views:
Transcription
1 Defeating scanners Php-Brute-Force-Attack-Detector By Aung Khant (d0ubl3_h3lix) Version: Beta Date: Saturday, June 28, 2008 URL: Overview Nowadays, in web application mapping, attackers use brute force tools in finding default files, hidden directories and known vulnerabilities as well as fingerprinting third-party components, web server backend components and alike. Almost all web hacking and security assessment tools such as famous Nikto, Nessus, JBroFuzz, OWASP DirBuster, WFuzz, and W3Af have built-in flat databases for relatively comprehensive footprinting web applications. At some time, developers may tend to use flawed third-party components without checking their vulnerabilities which may have been mentioned in milw0rm.com. Knowing someone is attacking your application is a sound alarm for waking up your security sense. You can proactively watch their tracks or you can stop their activities before they can mess up your critical applications. How it works Php-Brute-Attack-Detector notifies you in event of brute forcing attacks by looking at 404 errors per 5 minute routine. During that 5-minute period, there must be no more than 100 requests for is maximum request limit which you can change via config.php. It doesn t look for IP address which attackers can easily spoof and iterate using lists of public proxy servers. It looks only for how many 404 requests have been made. Notification can be achieved via methods 1) ing, 2) file logging, 3) logging in system log server. Option 1 and 2 are enabled by default. The third option forces system security auditor notice attack logs and to carry out appropriate actions. The first and the third one take place only once per day no matter how many there are flooded requests. This is to prevent mail bombing and messing up system log servers.
2 Unpredictable file names are used in file logging so that attackers cannot retrieve files by other means. For example, the log file name will be like: That means: Note: 24-Hour format is used. To fool most brute-force tools, I applied 200: header("http/ OK"); In addition, the size and contents of generated page are intentionally randomized to defeat tools like WFuzz which can provide the number of lines and words for assisting attackers in differentiating existent and non-existent stuffs. This would give attackers a heap of false positives. For defensive purpose, the application can sleep for several minutes, causing some of attackers' tools timing out. Upon notification and knowing attacks, you SHOULD deny attackers IPs via.htaccess. You can hack the code if you want to change the logic. For example, you can also implement it for 403 error. Objectives To detect as many web hacking tools processing as possible To give false positives to attackers in web application mapping phase To lengthen attackers web application mapping time To deter attackers before they go any further
3 Requirements PHP 5 MySQL 4 > Installation Guide Pretty easy. 1) Extract, Upload to your root folder 2) In.htaccess, - Comment/Remove line like the following: ErrorDocument 404 /missing.html - Write ErrorDocument 404 /yehgdetect/index.php Note: If you rename yehgdetect to something you want, change it accordingly. 3) Open PhpMyAdmin, Export yehgdetect.sql, Then Delete yehgdetect.sql. 4) In yehgdetect/db_info.php - Modify the following according to your database server, username, password, database name, database table name $db_server = 'localhost'; $db_user_login = 'username'; $db_user_pass = 'password'; $db_name = 'test'; $db_table = 'yehgdetect';
4 5) In yehgdetect/config.php - Modify Maximum request according to your will. It means that if BruteForce requests are above max_request number, then notify you or your web server 22 $max_request = 100; // per 5 minutes - Modify your/your web server admin's 29 $to = 'your @yourdomain.net,yourwebserveradmin@yourdomain.net ; - Modify notify 35 // 0 to no ing $ notify = 1; // Log attacks in file, 1 to yes, 0 to no $logfile = 1; // Log attacks in system log mechanism or server, 1 to yes, // 0 to no // You should discuss with your server admin to enable $logsys = 0; - Enable anti_attack or 48
5 // if set to 1, sleep the application for several minutes, causing attackers' tools timing out $anti_attack = 0; $sleep_time = 5; // minute Time-out value in some tools can be configured easily but it takes much longer time to complete the scan and make you take defensive measures in advance. But be careful with this option. It may cause DOS to your web server. 7) Make l0gz folder writable (Chmod 777) Warning As a possible counter-attack, attackers can flood the database within minutes. You need to take immediate action by denying their IPs in.htaccess at least. Attackers can fool search engines to attack your web sites by listing non-existent links of your site in their sites. That way, search engines see those lists of links pointing to your site and start indexing; hence they may get banned. That is why, before banning certain IPs, be sure to look them up in whois database such as If the IPs belong to trustworthy corporations like Google, Yahoo...etc., don t do banning. However, the countermeasure for this attack is to frequently check in google like link:yoursite.com. Regularly you need to clean up logs (after backing them up) as Php-Brute-Force-Attack Detector doesn t automate cleaning process after the records reach to certain number. Although it aims to defeat scanning, it is not suitable for all situations. Don t forget to disable it during valid (in-house) security assessment by setting $isdisable to 1 at line 18 of config.php. Further Help Send help, bugs, suggestions, and comments to yehg.org[xat]gmail[d0t]c0m. Thanks for downloading.
Web Application Penetration Testing
 Web Application Penetration Testing COURSE BROCHURE & SYLLABUS Course Overview Web Application penetration Testing (WAPT) is the Security testing techniques for vulnerabilities or security holes in corporate
Web Application Penetration Testing COURSE BROCHURE & SYLLABUS Course Overview Web Application penetration Testing (WAPT) is the Security testing techniques for vulnerabilities or security holes in corporate
Admin Login Log. User Guide. Compatibility: 1.5, 1.6, 1.7, 1.8, 1.9. Official Extension Page: Admin Login Log. User Guide: Admin Login Log Page 1
 Admin Login Log User Guide Compatibility: 1.5, 1.6, 1.7, 1.8, 1.9 Official Extension Page: Admin Login Log User Guide: Admin Login Log Page 1 Table of contents: 1. Introduction.3 2.Extension Configuration..5
Admin Login Log User Guide Compatibility: 1.5, 1.6, 1.7, 1.8, 1.9 Official Extension Page: Admin Login Log User Guide: Admin Login Log Page 1 Table of contents: 1. Introduction.3 2.Extension Configuration..5
SO, ARE YOU READY? HERE WE GO:
 Date: 28/09/2012 Procedure: How To Move WordPress To A New Server Or Host Source: LINK Permalink: LINK Created by: HeelpBook Staff Document Version: 1.0 HOW TO MOVE WORDPRESS TO A NEW SERVER OR HOST It
Date: 28/09/2012 Procedure: How To Move WordPress To A New Server Or Host Source: LINK Permalink: LINK Created by: HeelpBook Staff Document Version: 1.0 HOW TO MOVE WORDPRESS TO A NEW SERVER OR HOST It
MageFence User manual
 MageFence User manual Table of contents 1. Overview 1.1 General information 1.2 Key features 1.3 About this manual 2. Installation 2.1 Installation requirements 2.2 Installation instructions 3.MageFence
MageFence User manual Table of contents 1. Overview 1.1 General information 1.2 Key features 1.3 About this manual 2. Installation 2.1 Installation requirements 2.2 Installation instructions 3.MageFence
Mobile Login extension User Manual
 extension User Manual Magento 2 allows your customers convenience and security of login through mobile number and OTP. Table of Content 1. Extension Installation Guide 2. Configuration 3. API Settings
extension User Manual Magento 2 allows your customers convenience and security of login through mobile number and OTP. Table of Content 1. Extension Installation Guide 2. Configuration 3. API Settings
K-RATE INSTALLATION MANUAL
 K-RATE INSTALLATION MANUAL K-Rate Installation Manual Contents SYSTEM REQUIREMENTS... 3 1. DOWNLOADING K-RATE... 4 STEP 1: LOGIN TO YOUR MEMBER ACCOUNT... 4 STEP 2: ENTER DOMAIN NAME... 5 STEP 3: DOWNLOAD
K-RATE INSTALLATION MANUAL K-Rate Installation Manual Contents SYSTEM REQUIREMENTS... 3 1. DOWNLOADING K-RATE... 4 STEP 1: LOGIN TO YOUR MEMBER ACCOUNT... 4 STEP 2: ENTER DOMAIN NAME... 5 STEP 3: DOWNLOAD
TWO-FACTOR AUTHENTICATION Version 1.1.0
 TWO-FACTOR AUTHENTICATION Version 1.1.0 User Guide for Magento 1.9 Table of Contents 1..................... The MIT License 2.................... About JetRails 2FA 4................. Installing JetRails
TWO-FACTOR AUTHENTICATION Version 1.1.0 User Guide for Magento 1.9 Table of Contents 1..................... The MIT License 2.................... About JetRails 2FA 4................. Installing JetRails
Website Backend Manual
 Website Backend Manual Page Table of Contents Introduction Introduction to Drupal CMS User Login Content Management Content Overview Adding New Content Editing Homepage Slider Translating Content Blocks
Website Backend Manual Page Table of Contents Introduction Introduction to Drupal CMS User Login Content Management Content Overview Adding New Content Editing Homepage Slider Translating Content Blocks
Quick Start Manual for Mechanical TA
 Quick Start Manual for Mechanical TA Chris Thornton cwthornt@cs.ubc.ca August 18, 2013 Contents 1 Quick Install 1 2 Creating Courses 2 3 User Management 2 4 Assignment Management 3 4.1 Peer Review Assignment
Quick Start Manual for Mechanical TA Chris Thornton cwthornt@cs.ubc.ca August 18, 2013 Contents 1 Quick Install 1 2 Creating Courses 2 3 User Management 2 4 Assignment Management 3 4.1 Peer Review Assignment
How to create a secure WordPress install v1.1
 Table of Contents: Table of Contents:... 1 Introduction... 2 Installing WordPress... 2 Accessing your WordPress tables... 2 Changing your WordPress Table Prefix... 3 Before Installation... 3 Manually Change...
Table of Contents: Table of Contents:... 1 Introduction... 2 Installing WordPress... 2 Accessing your WordPress tables... 2 Changing your WordPress Table Prefix... 3 Before Installation... 3 Manually Change...
1 TABLE OF CONTENT. User Manual v0.4
 User Manual v0.4 1 TABLE OF CONTENT 2 Install your addressbook... 2 2.1 Quick installation... 2 2.2 Manual installation... 2 2.3 Setup user and passwords... 2 2.3.1 Setup User with passwords... 2 2.3.2
User Manual v0.4 1 TABLE OF CONTENT 2 Install your addressbook... 2 2.1 Quick installation... 2 2.2 Manual installation... 2 2.3 Setup user and passwords... 2 2.3.1 Setup User with passwords... 2 2.3.2
PHPBasket 4 Administrator Documentation
 PHPBasket 4 Please ensure you have the latest version of this document from http://www.phpbasket.com Contents CONTENTS 2 REQUIREMENTS 3 INSTALLATION 4 PREPARATION 4 UPLOAD 4 INSTALLATION 4 ADMINISTRATOR
PHPBasket 4 Please ensure you have the latest version of this document from http://www.phpbasket.com Contents CONTENTS 2 REQUIREMENTS 3 INSTALLATION 4 PREPARATION 4 UPLOAD 4 INSTALLATION 4 ADMINISTRATOR
ESET REMOTE ADMINISTRATOR PLUG-IN FOR KASEYA. Technical Setup and User Guide
 ESET REMOTE ADMINISTRATOR PLUG-IN FOR KASEYA Technical Setup and User Guide ESET REMOTE ADMINISTRATOR PLUG-INFOR KASEYA Copyright 2014 by ESET, spol. s r.o. ESET REMOTE ADMINISTRATOR Plug-in FOR KASEYA
ESET REMOTE ADMINISTRATOR PLUG-IN FOR KASEYA Technical Setup and User Guide ESET REMOTE ADMINISTRATOR PLUG-INFOR KASEYA Copyright 2014 by ESET, spol. s r.o. ESET REMOTE ADMINISTRATOR Plug-in FOR KASEYA
Installing Dolphin on Your PC
 Installing Dolphin on Your PC Note: When installing Dolphin as a test platform on the PC there are a few things you can overlook. Thus, this installation guide won t help you with installing Dolphin on
Installing Dolphin on Your PC Note: When installing Dolphin as a test platform on the PC there are a few things you can overlook. Thus, this installation guide won t help you with installing Dolphin on
WORDPRESS SECURITY HOUSTON WORDPRESS MEETUP.
 WORDPRESS SECURITY HOUSTON WORDPRESS MEETUP SCHEDULE 11:00 NETWORKING 11:30 SECURITY DISCUSSION 12:30 NETWORKING AGENDA Why WordPress Security is Important The Role of Web Hosting The Role of Core, Themes,
WORDPRESS SECURITY HOUSTON WORDPRESS MEETUP SCHEDULE 11:00 NETWORKING 11:30 SECURITY DISCUSSION 12:30 NETWORKING AGENDA Why WordPress Security is Important The Role of Web Hosting The Role of Core, Themes,
Database connection 1
 Database connection 1 Table of Contents 1 General Information... 3 2 Installing XAMPP... 4 3 Configuring the eibport database connection... 5 3.1 Creating a new database connection...6 3.2 Creation of
Database connection 1 Table of Contents 1 General Information... 3 2 Installing XAMPP... 4 3 Configuring the eibport database connection... 5 3.1 Creating a new database connection...6 3.2 Creation of
Certified Secure Web Application Engineer
 Certified Secure Web Application Engineer ACCREDITATIONS EXAM INFORMATION The Certified Secure Web Application Engineer exam is taken online through Mile2 s Assessment and Certification System ( MACS ),
Certified Secure Web Application Engineer ACCREDITATIONS EXAM INFORMATION The Certified Secure Web Application Engineer exam is taken online through Mile2 s Assessment and Certification System ( MACS ),
Jackson State University Department of Computer Science CSC / Advanced Information Security Spring 2013 Lab Project # 3
 Jackson State University Department of Computer Science CSC 439-01/539-02 Advanced Information Security Spring 2013 Lab Project # 3 Use of CAPTCHA (Image Identification Strategy) to Prevent XSRF Attacks
Jackson State University Department of Computer Science CSC 439-01/539-02 Advanced Information Security Spring 2013 Lab Project # 3 Use of CAPTCHA (Image Identification Strategy) to Prevent XSRF Attacks
CSWAE Certified Secure Web Application Engineer
 CSWAE Certified Secure Web Application Engineer Overview Organizations and governments fall victim to internet based attacks every day. In many cases, web attacks could be thwarted but hackers, organized
CSWAE Certified Secure Web Application Engineer Overview Organizations and governments fall victim to internet based attacks every day. In many cases, web attacks could be thwarted but hackers, organized
5/15/2009. Introduction
 Part 1: Cyber-Graffiti You know, I don t know what I hate more, wearing your face, or wearing your body. Look, why don t we just give them back to each other and call it even, okay? Castor Troy (Nicolas
Part 1: Cyber-Graffiti You know, I don t know what I hate more, wearing your face, or wearing your body. Look, why don t we just give them back to each other and call it even, okay? Castor Troy (Nicolas
Joomla! Security: Avoid Getting Hacked
 Joomla! Security: Avoid Getting Hacked Northern Virginia Joomla Users Group April 21, 2016 Dorothy Firsching, Ursa Major Consulting, LLC dfirsching@ursamajorconsulting.com Agenda Joomla! News and Plans
Joomla! Security: Avoid Getting Hacked Northern Virginia Joomla Users Group April 21, 2016 Dorothy Firsching, Ursa Major Consulting, LLC dfirsching@ursamajorconsulting.com Agenda Joomla! News and Plans
CCMS Installation Instructions
 CCMS Installation Instructions August 2012 Rev. 1.8.0 Ceedo Technologies, Ltd. 21 Hamelacha St. P.O. Box 11695 Park Afek, Rosh-Haayin, Israel 48091 T +972-7-322-322-00 www.ceedo.com 2012 Ceedo Technologies,
CCMS Installation Instructions August 2012 Rev. 1.8.0 Ceedo Technologies, Ltd. 21 Hamelacha St. P.O. Box 11695 Park Afek, Rosh-Haayin, Israel 48091 T +972-7-322-322-00 www.ceedo.com 2012 Ceedo Technologies,
Curso: Ethical Hacking and Countermeasures
 Curso: Ethical Hacking and Countermeasures Module 1: Introduction to Ethical Hacking Who is a Hacker? Essential Terminologies Effects of Hacking Effects of Hacking on Business Elements of Information Security
Curso: Ethical Hacking and Countermeasures Module 1: Introduction to Ethical Hacking Who is a Hacker? Essential Terminologies Effects of Hacking Effects of Hacking on Business Elements of Information Security
Dammit Jim, I m a Mac Admin, not a Web Developer
 Dammit Jim, I m a Mac Admin, not a Web Developer WordPress Basics for Mac Admins PSU Mac Admins Conference July 11, 2018 Tiffany Bridge Baxbridge Digital 1 WordPress Bridge Wi-Fi Bridge Who am I? The Best
Dammit Jim, I m a Mac Admin, not a Web Developer WordPress Basics for Mac Admins PSU Mac Admins Conference July 11, 2018 Tiffany Bridge Baxbridge Digital 1 WordPress Bridge Wi-Fi Bridge Who am I? The Best
Facebook Pixel for Remarketing for Magento 2
 Facebook Pixel for Remarketing for Magento 2 Facebook Pixel for Remarketing can be configured in few simple steps. We will guide through each step in this document. Installation Instructions Manual Installation
Facebook Pixel for Remarketing for Magento 2 Facebook Pixel for Remarketing can be configured in few simple steps. We will guide through each step in this document. Installation Instructions Manual Installation
Wordpress Security. GIMPA, November
 Wordpress Security GIMPA, November 2018 By: @niiankrah What is Wordpress? WordPress is a free and open-source content management system based on PHP and MySQL. It uses a plugin architecture and a template
Wordpress Security GIMPA, November 2018 By: @niiankrah What is Wordpress? WordPress is a free and open-source content management system based on PHP and MySQL. It uses a plugin architecture and a template
Module 1: Penetration Testing Planning and Scoping. Module 2: Basic Usage of Linux and its services
 Following topics will be covered: Module 1: Penetration Testing Planning and Scoping - Types of penetration testing and ethical hacking projects - Penetration testing methodology - Limitations and benefits
Following topics will be covered: Module 1: Penetration Testing Planning and Scoping - Types of penetration testing and ethical hacking projects - Penetration testing methodology - Limitations and benefits
CyberP3i Hands-on Lab Series
 CyberP3i Hands-on Lab Series Lab Series using NETLAB Designer: Dr. Lixin Wang, Associate Professor Hands-On Lab for Application Attacks The NDG Security+ Pod Topology Is Used 1. Introduction In this lab,
CyberP3i Hands-on Lab Series Lab Series using NETLAB Designer: Dr. Lixin Wang, Associate Professor Hands-On Lab for Application Attacks The NDG Security+ Pod Topology Is Used 1. Introduction In this lab,
How to perform the DDoS Testing of Web Applications
 How to perform the DDoS Testing of Web Applications Peerlyst November 02, 2017 Nasrumminallah Zeeshan (zeeshan@nzwriter.com) A Denial of Service (DoS) attack is consisted of carrying out traffic flooding
How to perform the DDoS Testing of Web Applications Peerlyst November 02, 2017 Nasrumminallah Zeeshan (zeeshan@nzwriter.com) A Denial of Service (DoS) attack is consisted of carrying out traffic flooding
INSTALLING RACHEL ON SYNOLOGY GIAKONDA IT
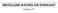 INSTALLING RACHEL ON SYNOLOGY GIAKONDA IT To add RACHEL to a Synology server there are a few stages to go through. First we need to ready the server for web use. Then we have to obtain a copy of the RACHEL
INSTALLING RACHEL ON SYNOLOGY GIAKONDA IT To add RACHEL to a Synology server there are a few stages to go through. First we need to ready the server for web use. Then we have to obtain a copy of the RACHEL
XML Sitemap Splitter for Magento 2. User Guide
 XML Sitemap Splitter for Magento 2 User Guide Table of Contents 1. XML Sitemap Splitter Configuration 1.1. Accessing the Extension Main Setting 1.2. General 1.3. Categories 1.4. Products In Stock 1.5.
XML Sitemap Splitter for Magento 2 User Guide Table of Contents 1. XML Sitemap Splitter Configuration 1.1. Accessing the Extension Main Setting 1.2. General 1.3. Categories 1.4. Products In Stock 1.5.
Web server reconnaissance
 Web server reconnaissance Reconnaissance and fingerprinting Finding information about a target web server/web site May be illegal to perform reconnaissance on a web server and web site without prior approval/permission.
Web server reconnaissance Reconnaissance and fingerprinting Finding information about a target web server/web site May be illegal to perform reconnaissance on a web server and web site without prior approval/permission.
K-SEARCH TRIAL INSTALLATION MANUAL
 K-SEARCH TRIAL INSTALLATION MANUAL Qsoft Inc, 2006-2009, All Rights Reserved Page 1 of 32 K-Search Trial Installation Manual Contents SYSTEM REQUIREMENTS... 3 1. DOWNLOADING K-SEARCH 15 DAYS TRIAL... 4
K-SEARCH TRIAL INSTALLATION MANUAL Qsoft Inc, 2006-2009, All Rights Reserved Page 1 of 32 K-Search Trial Installation Manual Contents SYSTEM REQUIREMENTS... 3 1. DOWNLOADING K-SEARCH 15 DAYS TRIAL... 4
5. A small dialog window appears; enter a new password twice (this is different from Dori!) and hit Go.
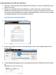 Installing Wordpress from JMA Lab to JMA Server 1. Take note these instructions are streamlined for the JMA lab they can t be performed in this fashion from home! 2. Wordpress is a database driven web
Installing Wordpress from JMA Lab to JMA Server 1. Take note these instructions are streamlined for the JMA lab they can t be performed in this fashion from home! 2. Wordpress is a database driven web
OWASP Broken Web Application Project. When Bad Web Apps are Good
 OWASP Broken Web Application Project When Bad Web Apps are Good About Me Mordecai (Mo) Kraushar Director of Audit, CipherTechs OWASP Project Lead, Vicnum OWASP New York City chapter member Assessing the
OWASP Broken Web Application Project When Bad Web Apps are Good About Me Mordecai (Mo) Kraushar Director of Audit, CipherTechs OWASP Project Lead, Vicnum OWASP New York City chapter member Assessing the
Courtesy of Clayton Fyfe. Lab 2 Runthrough
 Courtesy of Clayton Fyfe Lab 2 Runthrough Highlights 1. Accessing and Using phpmyadmin 2. CRUD for phpmyadmin 3. Microsoft expression WEB 3 Overview 4. CRUD for PHP 5. Adding Files to the playground Accessing
Courtesy of Clayton Fyfe Lab 2 Runthrough Highlights 1. Accessing and Using phpmyadmin 2. CRUD for phpmyadmin 3. Microsoft expression WEB 3 Overview 4. CRUD for PHP 5. Adding Files to the playground Accessing
GUI based and very easy to use, no security expertise required. Reporting in both HTML and RTF formats - Click here to view the sample report.
 Report on IRONWASP Software Product: IronWASP Description of the Product: IronWASP (Iron Web application Advanced Security testing Platform) is an open source system for web application vulnerability testing.
Report on IRONWASP Software Product: IronWASP Description of the Product: IronWASP (Iron Web application Advanced Security testing Platform) is an open source system for web application vulnerability testing.
CS 410/510: Web Security X1: Labs Setup WFP1, WFP2, and Kali VMs on Google Cloud
 CS 410/510: Web Security X1: Labs Setup WFP1, WFP2, and Kali VMs on Google Cloud Go to Google Cloud Console => Compute Engine => VM instances => Create Instance For the Boot Disk, click "Change", then
CS 410/510: Web Security X1: Labs Setup WFP1, WFP2, and Kali VMs on Google Cloud Go to Google Cloud Console => Compute Engine => VM instances => Create Instance For the Boot Disk, click "Change", then
Using PHPMyAdmin with WordPress
 Using PHPMyAdmin with WordPress A basic run-down of some of the things you may want to do manually on your WordPress database. (Using PHPMyAdmin) Kenneth Hargis Managing Partner ken@orphicworkshop.com
Using PHPMyAdmin with WordPress A basic run-down of some of the things you may want to do manually on your WordPress database. (Using PHPMyAdmin) Kenneth Hargis Managing Partner ken@orphicworkshop.com
Please post bugs on our forum on or us on
 JHacker Watch system plug-in - Trial Edition 2012-2017 INNATO BV - www.innato.nl license - http://www.gnu.org/licenses/gpl-2.0.html GNU/GPL **************************************************************************
JHacker Watch system plug-in - Trial Edition 2012-2017 INNATO BV - www.innato.nl license - http://www.gnu.org/licenses/gpl-2.0.html GNU/GPL **************************************************************************
Install WordPress 3.X In Multi Blog / Multi user mode On localhost
 Install WordPress 3.X In Multi Blog / Multi user mode On localhost In this tutorial, we will cover how to setup WordPress as a Multi User /Multi Blog. We ll start by downloading and installing a new version
Install WordPress 3.X In Multi Blog / Multi user mode On localhost In this tutorial, we will cover how to setup WordPress as a Multi User /Multi Blog. We ll start by downloading and installing a new version
Incident Response Tools
 Incident Response Tools James Madison University Dept. of Computer Science June 13, 2013 1 Introduction Being successfully attacked is inevitable. A determined hacker WILL be able to penetrate your network.
Incident Response Tools James Madison University Dept. of Computer Science June 13, 2013 1 Introduction Being successfully attacked is inevitable. A determined hacker WILL be able to penetrate your network.
Lecture 7: Web hacking 3, SQL injection, Xpath injection, Server side template injection, File inclusion
 IN5290 Ethical Hacking Lecture 7: Web hacking 3, SQL injection, Xpath injection, Server side template injection, File inclusion Universitetet i Oslo Laszlo Erdödi Lecture Overview What is SQL injection
IN5290 Ethical Hacking Lecture 7: Web hacking 3, SQL injection, Xpath injection, Server side template injection, File inclusion Universitetet i Oslo Laszlo Erdödi Lecture Overview What is SQL injection
TIMING-BASED ATTACKS IN WEB APPLICATIONS
 TIMING-BASED ATTACKS IN WEB APPLICATIONS ABOUT ME Ahmad Ashraff @Yappare Before : Chemical Engineer Current : Pentester @ Aura Information Security Hobbies : Backpacking, Watching Animes Member Of OWASP
TIMING-BASED ATTACKS IN WEB APPLICATIONS ABOUT ME Ahmad Ashraff @Yappare Before : Chemical Engineer Current : Pentester @ Aura Information Security Hobbies : Backpacking, Watching Animes Member Of OWASP
Here's how we are going to Supercharge WordPress.
 Here's how we are going to Supercharge WordPress. Fix the default WordPress settings. Optimize WordPress s operation. Correct the on-page SEO. Optimize our internal link juice. Upgrade the promotion engines.
Here's how we are going to Supercharge WordPress. Fix the default WordPress settings. Optimize WordPress s operation. Correct the on-page SEO. Optimize our internal link juice. Upgrade the promotion engines.
Running A MyDNS Name Server On OpenBSD (MySQL/PHP + MyDNS + MyDNSConfig)
 By ZcWorld (Shane Ebert) Published: 2008-03-31 18:28 Running A MyDNS Name Server On OpenBSD (MySQL/PHP + MyDNS + MyDNSConfig) This tutorial shows how to run a MyDNS name server on an OpenBSD server. It
By ZcWorld (Shane Ebert) Published: 2008-03-31 18:28 Running A MyDNS Name Server On OpenBSD (MySQL/PHP + MyDNS + MyDNSConfig) This tutorial shows how to run a MyDNS name server on an OpenBSD server. It
Jacksonville Linux User Group Presenter: Travis Phillips Date: 02/20/2013
 Jacksonville Linux User Group Presenter: Travis Phillips Date: 02/20/2013 Welcome Back! A Quick Recap of the Last Presentation: Overview of web technologies. What it is. How it works. Why it s attractive
Jacksonville Linux User Group Presenter: Travis Phillips Date: 02/20/2013 Welcome Back! A Quick Recap of the Last Presentation: Overview of web technologies. What it is. How it works. Why it s attractive
Protegent Total Security Solution USER GUIDE Unistal Systems Pvt. Ltd. All rights Reserved Page 1
 Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
5 Must-Have Magento Security Plugins
 5 Must-Have Magento Security Plugins http://beacon.by/magazine/pdf/serverguy/5-must-have-magento-security-plugins?type=print 1/16 Table of Contents 1. About ServerGuy 2. WatchLog 3. Amasty s Admin Login
5 Must-Have Magento Security Plugins http://beacon.by/magazine/pdf/serverguy/5-must-have-magento-security-plugins?type=print 1/16 Table of Contents 1. About ServerGuy 2. WatchLog 3. Amasty s Admin Login
Joomla 3.X Global Settings Part III Server Settings
 Joomla 3.X Global Settings Part III Server Settings Diagram 1 Path to Temp Folder: This is a text box adjacent to this prompt which holds the path to Joomla s temp folder on the web server. This is the
Joomla 3.X Global Settings Part III Server Settings Diagram 1 Path to Temp Folder: This is a text box adjacent to this prompt which holds the path to Joomla s temp folder on the web server. This is the
How To Clone, Backup & Move Your WordPress Blog! Step By Step Guide by Marian Krajcovic
 How To Clone, Backup & Move Your WordPress Blog! Step By Step Guide by Marian Krajcovic 2010 Marian Krajcovic You may NOT resell or giveaway this ebook! 1 If you have many WordPress blogs and especially
How To Clone, Backup & Move Your WordPress Blog! Step By Step Guide by Marian Krajcovic 2010 Marian Krajcovic You may NOT resell or giveaway this ebook! 1 If you have many WordPress blogs and especially
Migration Tool. User Guide. SHOPIFY to MAGENTO. Copyright 2014 LitExtension.com. All Rights Reserved.
 SHOPIFY to MAGENTO Migration Tool User Guide Copyright 2014 LitExtension.com. All Rights Reserved. Shopify to Magento Migration Tool: User Guide Page 1 Contents 1. Preparation... 3 2. Set-up... 3 3. Set-up...
SHOPIFY to MAGENTO Migration Tool User Guide Copyright 2014 LitExtension.com. All Rights Reserved. Shopify to Magento Migration Tool: User Guide Page 1 Contents 1. Preparation... 3 2. Set-up... 3 3. Set-up...
Web Penetration Testing
 Web Penetration Testing What is a Website How to hack a Website? Computer with OS and some servers. Apache, MySQL...etc Contains web application. PHP, Python...etc Web application is executed here and
Web Penetration Testing What is a Website How to hack a Website? Computer with OS and some servers. Apache, MySQL...etc Contains web application. PHP, Python...etc Web application is executed here and
DreamFactory Security Guide
 DreamFactory Security Guide This white paper is designed to provide security information about DreamFactory. The sections below discuss the inherently secure characteristics of the platform and the explicit
DreamFactory Security Guide This white paper is designed to provide security information about DreamFactory. The sections below discuss the inherently secure characteristics of the platform and the explicit
Kollaborate Server. Installation Guide
 1 Kollaborate Server Installation Guide Kollaborate Server is a local implementation of the Kollaborate cloud workflow system that allows you to run the service in-house on your own server and storage.
1 Kollaborate Server Installation Guide Kollaborate Server is a local implementation of the Kollaborate cloud workflow system that allows you to run the service in-house on your own server and storage.
SOFTWARE INSTALLATION README
 SOFTWARE INSTALLATION README This software uses two directories for its installation. One is a public directory, and one is a private, or secure directory. Kryptronic software installs in two different
SOFTWARE INSTALLATION README This software uses two directories for its installation. One is a public directory, and one is a private, or secure directory. Kryptronic software installs in two different
CNIT 129S: Securing Web Applications. Ch 4: Mapping the Application
 CNIT 129S: Securing Web Applications Ch 4: Mapping the Application Mapping Enumerate application's content and functionality Some is hidden, requiring guesswork and luck to discover Examine every aspect
CNIT 129S: Securing Web Applications Ch 4: Mapping the Application Mapping Enumerate application's content and functionality Some is hidden, requiring guesswork and luck to discover Examine every aspect
Locate your Advanced Tools and Applications
 . phpmyadmin is a web-based application used to manage a MySQL database. It is free and open-source software. We have modified phpmyadmin so that it functions without errors on a shared hosting platform.
. phpmyadmin is a web-based application used to manage a MySQL database. It is free and open-source software. We have modified phpmyadmin so that it functions without errors on a shared hosting platform.
MAGENTO Migration Tools
 MAGENTO Migration Tools User Guide Copyright 2014 LitExtension.com. All Rights Reserved. Magento Migration Tools: User Guide Page 1 Contents 1. Preparation... 3 2. Set-up... 4 3. Set-up... 5 4. License
MAGENTO Migration Tools User Guide Copyright 2014 LitExtension.com. All Rights Reserved. Magento Migration Tools: User Guide Page 1 Contents 1. Preparation... 3 2. Set-up... 4 3. Set-up... 5 4. License
Using.htaccess to Restrict OU Directory by Usernames and Passwords in an.htpasswd File
 Using.htaccess to Restrict OU Directory by Usernames and Passwords in an.htpasswd File (Last updated on 9/3/2015 by lucero@uark.edu) This method requires the management of three files,.htaccess,.htpasswd,
Using.htaccess to Restrict OU Directory by Usernames and Passwords in an.htpasswd File (Last updated on 9/3/2015 by lucero@uark.edu) This method requires the management of three files,.htaccess,.htpasswd,
PMI User Training 2016 JUNE
 PMI User Training 2016 JUNE Launching the system To access the system, please use the details provided to you. Your unique ELP username and password Access Details Navigate your internet browser to https://pmi.siyandza-elp.com
PMI User Training 2016 JUNE Launching the system To access the system, please use the details provided to you. Your unique ELP username and password Access Details Navigate your internet browser to https://pmi.siyandza-elp.com
Advanced Ethical Hacking & Penetration Testing. Ethical Hacking
 Summer Training Internship Program 2017 (STIP - 2017) is a practical oriented & industrial level training program for all students who have aspiration to work in the core technical industry domain. This
Summer Training Internship Program 2017 (STIP - 2017) is a practical oriented & industrial level training program for all students who have aspiration to work in the core technical industry domain. This
Tenable.sc-Tenable.io Upgrade Assistant Guide, Version 2.0. Last Revised: January 16, 2019
 Tenable.sc-Tenable.io Upgrade Assistant Guide, Version 2.0 Last Revised: January 16, 2019 Table of Contents Welcome to the Tenable.sc-Tenable.io Upgrade Assistant 3 Get Started 4 Environment Requirements
Tenable.sc-Tenable.io Upgrade Assistant Guide, Version 2.0 Last Revised: January 16, 2019 Table of Contents Welcome to the Tenable.sc-Tenable.io Upgrade Assistant 3 Get Started 4 Environment Requirements
Facebook Product Catalog Configuration Instructions
 Facebook Product Catalog Configuration Instructions Facebook Product Catalog can be configured in few simple steps. We will guide through each step in this document. First open your Admin Panel and go
Facebook Product Catalog Configuration Instructions Facebook Product Catalog can be configured in few simple steps. We will guide through each step in this document. First open your Admin Panel and go
TexSaw Penetration Te st in g
 TexSaw Penetration Te st in g What is penetration testing? The process of breaking something or using something for an unintended used case for the purpose of bettering the system or application. This
TexSaw Penetration Te st in g What is penetration testing? The process of breaking something or using something for an unintended used case for the purpose of bettering the system or application. This
Mobile Login Extension User Manual
 Extension User Manual Magento provides secured and convenient login to Magento stores through mobile number along with OTP. Table of Content 1. Extension Installation Guide 2. API Configuration 3. General
Extension User Manual Magento provides secured and convenient login to Magento stores through mobile number along with OTP. Table of Content 1. Extension Installation Guide 2. API Configuration 3. General
XAMPP Web Development Stack
 Overview @author R.L. Martinez, Ph.D. The steps below outline the processes for installing the XAMPP stack on a local machine. The XAMPP (pronounced Zamp) stack includes the following: Apache HTTP Server,
Overview @author R.L. Martinez, Ph.D. The steps below outline the processes for installing the XAMPP stack on a local machine. The XAMPP (pronounced Zamp) stack includes the following: Apache HTTP Server,
To check for an update outside of that, navigate to Utilities > Update WHMCS.
 UPDATING WHMCS Table of Contents Automatic Updates... 3 Checking for an update... 4 Configuring your Desired Update Channel... 6 How to resolve Unable to Perform Automatic Updates... 8 Configuring your
UPDATING WHMCS Table of Contents Automatic Updates... 3 Checking for an update... 4 Configuring your Desired Update Channel... 6 How to resolve Unable to Perform Automatic Updates... 8 Configuring your
A Guide to Finding the Best WordPress Backup Plugin: 10 Must-Have Features
 A Guide to Finding the Best WordPress Backup Plugin: 10 Must-Have Features \ H ow do you know if you re choosing the best WordPress backup plugin when it seems that all the plugins seem to do the same
A Guide to Finding the Best WordPress Backup Plugin: 10 Must-Have Features \ H ow do you know if you re choosing the best WordPress backup plugin when it seems that all the plugins seem to do the same
Installing Joomla
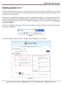 Installing Joomla 3.0.11 To start installing Joomla 3.X you have to copy the zipped file Joomla_3.0.1-Stable-Full_Package.zip to the folder in which you want to install Joomla 3.X. On a web host this is
Installing Joomla 3.0.11 To start installing Joomla 3.X you have to copy the zipped file Joomla_3.0.1-Stable-Full_Package.zip to the folder in which you want to install Joomla 3.X. On a web host this is
Quick Start Guide. Microsoft Windows Vista / XP / 2000 / 2003 / 2008
 Quick Start Guide Microsoft Windows Vista / XP / 2000 / 2003 / 2008 ESET NOD32 Antivirus provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning
Quick Start Guide Microsoft Windows Vista / XP / 2000 / 2003 / 2008 ESET NOD32 Antivirus provides state-of-the-art protection for your computer against malicious code. Based on the ThreatSense scanning
Spam Protection Guide
 Spam Email Protection Guide Version 1.0 Last Modified 5/29/2014 by Mike Copening Contents Overview of Spam at RTS... 1 Types of Spam... 1 Spam Tricks... 2 Imitation of 3 rd Party Email Template... 2 Spoofed
Spam Email Protection Guide Version 1.0 Last Modified 5/29/2014 by Mike Copening Contents Overview of Spam at RTS... 1 Types of Spam... 1 Spam Tricks... 2 Imitation of 3 rd Party Email Template... 2 Spoofed
Welcome To Account Manager 2.0
 Account Manager 2.0 Manage Unlimited FileMaker Servers, Databases, Privileges, and Users Effortlessly! The ultimate tool for FileMaker Database Administrators. Welcome To Account Manager 2.0 What Is Account
Account Manager 2.0 Manage Unlimited FileMaker Servers, Databases, Privileges, and Users Effortlessly! The ultimate tool for FileMaker Database Administrators. Welcome To Account Manager 2.0 What Is Account
ANTIVIRUS SITE PROTECTION (by SiteGuarding.com)
 ANTIVIRUS SITE PROTECTION (by SiteGuarding.com) USER GUIDE Version 1.0.0 Antivirus Site Protection (by SiteGuarding.com) 1.0.0 1 Table of content 1. INTRODUCTION. 3 2. HOW IT WORKS.... 6 3. HOW TO CONFIGURE..
ANTIVIRUS SITE PROTECTION (by SiteGuarding.com) USER GUIDE Version 1.0.0 Antivirus Site Protection (by SiteGuarding.com) 1.0.0 1 Table of content 1. INTRODUCTION. 3 2. HOW IT WORKS.... 6 3. HOW TO CONFIGURE..
ESET ENDPOINT SECURITY FOR ANDROID
 ESET ENDPOINT SECURITY FOR ANDROID Installation Manual and User Guide Click here to download the most recent version of this document Contents 1. Installation...3 of ESET Endpoint Security 1.1 Installation...3
ESET ENDPOINT SECURITY FOR ANDROID Installation Manual and User Guide Click here to download the most recent version of this document Contents 1. Installation...3 of ESET Endpoint Security 1.1 Installation...3
NET 311 INFORMATION SECURITY
 NET 311 INFORMATION SECURITY Networks and Communication Department Lec12: Software Security / Vulnerabilities lecture contents: o Vulnerabilities in programs Buffer Overflow Cross-site Scripting (XSS)
NET 311 INFORMATION SECURITY Networks and Communication Department Lec12: Software Security / Vulnerabilities lecture contents: o Vulnerabilities in programs Buffer Overflow Cross-site Scripting (XSS)
Migrating Data from Archivists Toolkit to ArchivesSpace Using the Migration Tool last updated December 19, 2017
 Migrating Data from Archivists Toolkit to ArchivesSpace Using the Migration Tool last updated December 19, 2017 These guidelines are for migrating data from Archivists Toolkit 2.0 Update 16 to all ArchivesSpace
Migrating Data from Archivists Toolkit to ArchivesSpace Using the Migration Tool last updated December 19, 2017 These guidelines are for migrating data from Archivists Toolkit 2.0 Update 16 to all ArchivesSpace
Admin console design changes
 Admin console design changes New icons and navigation for the toolbar Settings open in card view Managing your users Managing user accounts inline Managing multiple users Filtering your organization units
Admin console design changes New icons and navigation for the toolbar Settings open in card view Managing your users Managing user accounts inline Managing multiple users Filtering your organization units
ANTIVIRUS SITE PROTECTION (by SiteGuarding.com)
 ANTIVIRUS SITE PROTECTION (by SiteGuarding.com) USER GUIDE Version 0.1.0 1 Table of content 1. INTRODUCTION. 3 2. HOW IT WORKS.... 6 3. HOW TO CONFIGURE.. 7 2 1. INTRODUCTION Antivirus Site Protection
ANTIVIRUS SITE PROTECTION (by SiteGuarding.com) USER GUIDE Version 0.1.0 1 Table of content 1. INTRODUCTION. 3 2. HOW IT WORKS.... 6 3. HOW TO CONFIGURE.. 7 2 1. INTRODUCTION Antivirus Site Protection
Setting up Omeka on IU s Webserve
 Setting up Omeka on IU s Webserve Request Webserve Account Consult the "Getting Started" document before you request a Webserve account. The following steps are required: 1. Request a Group Account 1.
Setting up Omeka on IU s Webserve Request Webserve Account Consult the "Getting Started" document before you request a Webserve account. The following steps are required: 1. Request a Group Account 1.
Please post bugs on our forum on or us on
 Login One! authentication and user plug-in for Joomla! 3.x Trial Edition 2011-2018 INNATO BV - www.innato.nl - All rights reserved **************************************************************************
Login One! authentication and user plug-in for Joomla! 3.x Trial Edition 2011-2018 INNATO BV - www.innato.nl - All rights reserved **************************************************************************
Coordinated Disclosure of Vulnerabilities in AVG Antivirus Free Android
 Coordinated Disclosure of Vulnerabilities in AVG Antivirus Free Android 5.9.4.1 1 Executive summary Researchers of MRG Effitas tested the AVG AntiVirus Free Android application. During use, we came across
Coordinated Disclosure of Vulnerabilities in AVG Antivirus Free Android 5.9.4.1 1 Executive summary Researchers of MRG Effitas tested the AVG AntiVirus Free Android application. During use, we came across
Scanning-Less Scanning. Installation Guide
 Scanning-Less Scanning Installation Guide Last update: 9 February 2017 Table of Contents Scanning-Less Scanning Description... 3 1. A Traditional Approach... 3 2. Outpost24 s Unique Approach... 3 Enabling
Scanning-Less Scanning Installation Guide Last update: 9 February 2017 Table of Contents Scanning-Less Scanning Description... 3 1. A Traditional Approach... 3 2. Outpost24 s Unique Approach... 3 Enabling
Intrusion Attempt Who's Knocking Your Door
 10 Intrusion Attempt Who's Knocking Your Door By Kilausuria binti Abdullah Introduction: An intrusion attempt is a potential for a deliberate unauthorized attempt to enter either a computer, system or
10 Intrusion Attempt Who's Knocking Your Door By Kilausuria binti Abdullah Introduction: An intrusion attempt is a potential for a deliberate unauthorized attempt to enter either a computer, system or
Advanced Web Tutorial 10
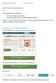 Advanced Web Tutorial 10 Editor Brackets / Visual Studio Code Goals Creating a blog with PHP and MySql. - Set up and configuration of Xampp - Learning Data flow using Create/Read/Update and Delete Things
Advanced Web Tutorial 10 Editor Brackets / Visual Studio Code Goals Creating a blog with PHP and MySql. - Set up and configuration of Xampp - Learning Data flow using Create/Read/Update and Delete Things
Coordinated Disclosure of Vulnerabilities in McAfee Security Android
 Coordinated Disclosure of Vulnerabilities in McAfee Security Android 4.8.0.370 1 Executive summary Researchers of MRG Effitas tested the McAfee Security Android application. During use, we came across
Coordinated Disclosure of Vulnerabilities in McAfee Security Android 4.8.0.370 1 Executive summary Researchers of MRG Effitas tested the McAfee Security Android application. During use, we came across
Ethical Hacking and Prevention
 Ethical Hacking and Prevention This course is mapped to the popular Ethical Hacking and Prevention Certification Exam from US-Council. This course is meant for those professionals who are looking for comprehensive
Ethical Hacking and Prevention This course is mapped to the popular Ethical Hacking and Prevention Certification Exam from US-Council. This course is meant for those professionals who are looking for comprehensive
FB Image Contest. Users Manual
 FB Image Contest Users Manual Table of contents Description.. 3 Step by step installation... 5 The administration interface.. 10 Creating a new contest... 13 Creating a Facebook Application.. 19 Adding
FB Image Contest Users Manual Table of contents Description.. 3 Step by step installation... 5 The administration interface.. 10 Creating a new contest... 13 Creating a Facebook Application.. 19 Adding
Change Management: DYNAMIC NETWORK MAPPING. LinuxWorld San Francisco Security Track. Presented by Joshua D. Abraham.
 Change Management: DYNAMIC NETWORK MAPPING LinuxWorld San Francisco Security Track Presented by Joshua D. Abraham August 16th 2006 jabra@ccs.neu.edu Northeastern University Agenda How do we scan? What
Change Management: DYNAMIC NETWORK MAPPING LinuxWorld San Francisco Security Track Presented by Joshua D. Abraham August 16th 2006 jabra@ccs.neu.edu Northeastern University Agenda How do we scan? What
Evaluating Website Security with Penetration Testing Methodology
 Evaluating Website Security with Penetration Testing Methodology D. Menoski, P. Mitrevski and T. Dimovski St. Clement of Ohrid University in Bitola/Faculty of Technical Sciences, Bitola, Republic of Macedonia
Evaluating Website Security with Penetration Testing Methodology D. Menoski, P. Mitrevski and T. Dimovski St. Clement of Ohrid University in Bitola/Faculty of Technical Sciences, Bitola, Republic of Macedonia
ADDING STAFF AS CONTACTS. DOCUMENT Here is a guide to Webdadi. WEBDADI Updated June 2015
 DOCUMENT Here is a guide to Webdadi WEBDADI Updated June 2015 ADDING STAFF AS CONTACTS How to add Internal staff and assign them their Webdadi User Rights ADDING INTERNAL STAFF IN WEBDADI: Adding staff
DOCUMENT Here is a guide to Webdadi WEBDADI Updated June 2015 ADDING STAFF AS CONTACTS How to add Internal staff and assign them their Webdadi User Rights ADDING INTERNAL STAFF IN WEBDADI: Adding staff
Monitoring Table of Contents:
 Table of Contents: Dashboard Status Edit Agent External SNMP Log 2 Chapter 6 - Sadjadi et al. Introduction Proactive and preventive system maintenance is only possible with accurate and easily accessible
Table of Contents: Dashboard Status Edit Agent External SNMP Log 2 Chapter 6 - Sadjadi et al. Introduction Proactive and preventive system maintenance is only possible with accurate and easily accessible
Offensive Countermeasures: The Art of Active Defense
 Offensive Countermeasures: The Art of Active Defense Prepared by Data Security Council of India A NASSCOM 1 Initiative YoungWallet is a recently launched mobile wallet company. They began their operations
Offensive Countermeasures: The Art of Active Defense Prepared by Data Security Council of India A NASSCOM 1 Initiative YoungWallet is a recently launched mobile wallet company. They began their operations
3. Apache Server Vulnerability Identification and Analysis
 1. Target Identification The pentester uses netdiscover to identify the target: root@kali:~# netdiscover -r 192.168.0.0/24 Target: 192.168.0.48 (Cadmus Computer Systems) Note: the victim IP address changes
1. Target Identification The pentester uses netdiscover to identify the target: root@kali:~# netdiscover -r 192.168.0.0/24 Target: 192.168.0.48 (Cadmus Computer Systems) Note: the victim IP address changes
Web Application & Web Server Vulnerabilities Assessment Pankaj Sharma
 Web Application & Web Server Vulnerabilities Assessment Pankaj Sharma Indian Computer Emergency Response Team ( CERT - IN ) Department Of Information Technology 1 Agenda Introduction What are Web Applications?
Web Application & Web Server Vulnerabilities Assessment Pankaj Sharma Indian Computer Emergency Response Team ( CERT - IN ) Department Of Information Technology 1 Agenda Introduction What are Web Applications?
Tenable.io User Guide. Last Revised: November 03, 2017
 Tenable.io User Guide Last Revised: November 03, 2017 Table of Contents Tenable.io User Guide 1 Getting Started with Tenable.io 10 Tenable.io Workflow 12 System Requirements 15 Scanners and Agents 16 Link
Tenable.io User Guide Last Revised: November 03, 2017 Table of Contents Tenable.io User Guide 1 Getting Started with Tenable.io 10 Tenable.io Workflow 12 System Requirements 15 Scanners and Agents 16 Link
PracticeDump. Free Practice Dumps - Unlimited Free Access of practice exam
 PracticeDump http://www.practicedump.com Free Practice Dumps - Unlimited Free Access of practice exam Exam : SY0-501 Title : CompTIA Security+ Certification Exam Vendor : CompTIA Version : DEMO Get Latest
PracticeDump http://www.practicedump.com Free Practice Dumps - Unlimited Free Access of practice exam Exam : SY0-501 Title : CompTIA Security+ Certification Exam Vendor : CompTIA Version : DEMO Get Latest
Cross Platform Penetration Testing Suite
 Cross Platform Penetration Testing Suite Ms. Shyaml Virnodkar, Rahul Gupta, Tejas Bharambe 1Asst Professor, Department of Computer Engineering, K J Somaiya Institute of Engineering and Information Technology,
Cross Platform Penetration Testing Suite Ms. Shyaml Virnodkar, Rahul Gupta, Tejas Bharambe 1Asst Professor, Department of Computer Engineering, K J Somaiya Institute of Engineering and Information Technology,
ForeScout Extended Module for Tenable Vulnerability Management
 ForeScout Extended Module for Tenable Vulnerability Management Version 2.7.1 Table of Contents About Tenable Vulnerability Management Module... 4 Compatible Tenable Vulnerability Products... 4 About Support
ForeScout Extended Module for Tenable Vulnerability Management Version 2.7.1 Table of Contents About Tenable Vulnerability Management Module... 4 Compatible Tenable Vulnerability Products... 4 About Support
Chapter. NagVis. Nagios, 2nd Edition (C) 2008 by Wolfgang Barth
 18 Chapter NagVis NagVis 1 is an addon for Nagios that displays host and service states against a background image selected by the user. This must be available in the PNG format; the choice is yours whether
18 Chapter NagVis NagVis 1 is an addon for Nagios that displays host and service states against a background image selected by the user. This must be available in the PNG format; the choice is yours whether
