Copyright
|
|
|
- Roland Carroll
- 5 years ago
- Views:
Transcription
1 This video looks at Claim Based/Identity Based systems using Active Directory Federation Services as an example. An example of a claim based system is where the user logs into a system like a web page using another system, for example a Facebook login.
2 Example In this fictional example, it shows the key points to a Federation Service. Federation Services work by a user wanting to access a system which belongs to a 3rd party. In order to do this, the first party needs to provide something the 3rd party can check to ensure the person is allowed access. It is still up to the 3rd party if they will allow them access or not. The point is that business B can check that the employee is a valid employee without having to contact business A to check.
3 In this example, an Active Directory Federation Services model would work the following way. 1) The user contacts the web server in business B in order to obtain access to a service. 2) The web server rejects the request as the web server does not know who they are. The web server refers them to Federation Server in business B in order to get a claim in order to access the web server. 3) The user then contacts the Federation Server in the business B network. 4) The Federation Server does not know who the user is, so it says to get authorization first. 5) The user contacts the Federation Server in its DMZ and requests to be authenticated. 6) The Federation Server will pass the username and password the user provided to a Domain Controller. 7) The Domain Controller will respond back to the Federation Server that they have been authenticated. 8) The Federation Server will give the user a claim. This claim contains information indicating the user has been authenticated. 9) This claim is presented to the Federation Server in business B. 10) The Federation Server will accept the claim. Although not shown in this video, the Federation Server will often create a new claim that would be given to the user to grant them access services. 11) The user will use the claim with the web server. 12) The web server will accept the claim and connect to a file server. 13) The file server will give the information to the web server. 14) The web server will then present the information to the user.
4 AD Example In order to have authentication occur between two businesses using Active Directory, a trust relationship needs to be created between the two businesses. In order for this to occur, firewall changes need to made. An Active Directory trust is also connection based, which means a direct connection between the two businesses must also be present. If you want to allow services like file transfers you also need to make additional changes to the firewall. Companies often do not want to make changes to their firewall and do not want to establish direct permanent connections between different businesses.
5 Advantages of Federation Services Federation Services does not require a connection style trust in order to work. It only requires a certificate to be exported and imported on the other side before the trust can be configured. Federation Services also uses standard HTTP and HTTPS protocols and thus these ports are most likely already open on the companies file firewall. Companies are more likely to agree to open these ports than open less commonly used ports. Federation Services uses standard protocols and thus can work with other systems. For example, a Windows based Federation Server can also work with a Linux based Federation Server.
6 Example Of Online Services In this example, a mobile user requires access to Exchange Services stored in the cloud using Microsoft Outlook as the client. 1) The user contacts the online Exchange Server in the cloud. 2) The server responds back that it needs a claim in order to access the service. 3) The user contacts that Federation Server. 4) The Federation Server responds back saying it will not issue a claim until they have been given a claim showing they are allow access. 5) The user contacts the Federation Service on their network with their username and password. Any authentication system could be used here. Even a system that only requires the user to present an address could be used. 6) The Federation Server contacts a Domain Controller to authenticate the user. 7) The Domain Controller responds back to the Federation Server that the user has been authenticated. 8) The Federation Server gives a claim to the user. 9) The user then gives the claim to a Federation Server. 10) The Federation Server accepts the claim and presents the user with another claim that the user can use with the online server to access the Exchange service. 11) The user then presents this claim to the online server and is now able to access the Exchange service in the cloud. The point to remember with claim based systems is that authentication is provided by a system that is separate from the system that is providing access. This means that the first system can add and remove users as required and thus indirectly be responsible for who has access.
7 Summary A Federation Service uses standard web protocols and does not require a connection style trust. For this reason these ports may already be open on the firewall and thus is generally easier to get management approval. Federation Services require many systems to work together and thus may not be that easy to get up and working. Microsoft cloud based systems are well documented. Other Federation Services solutions are not as well documented and thus may be harder to set up. Lastly a claim contains user information and what they would like access to. They use certificates to make sure the data is secure. In later videos claims will be covered in more detail. See or for our always free training videos. This is only one video from the many free courses available on YouTube. References Active Directory Federation Services Overview Federated identity
Copyright
 This video will look at the different Terminology that is used with Federation Services. This will give you a good indication of what components make up a Federation Service in Active Directory Federation
This video will look at the different Terminology that is used with Federation Services. This will give you a good indication of what components make up a Federation Service in Active Directory Federation
Copyright
 In Active Directory Federation Services there are two types of trusts. This video will look at the relying party trust which is configured on the account side. It essentially determines what information
In Active Directory Federation Services there are two types of trusts. This video will look at the relying party trust which is configured on the account side. It essentially determines what information
Microsoft ADFS Configuration
 Microsoft ADFS Configuration Side 1 af 12 1 Information 1.1 ADFS KMD Secure ISMS supports ADFS for integration with Microsoft Active Directory by implementing WS-Federation and SAML 2. The integration
Microsoft ADFS Configuration Side 1 af 12 1 Information 1.1 ADFS KMD Secure ISMS supports ADFS for integration with Microsoft Active Directory by implementing WS-Federation and SAML 2. The integration
SchoolBooking LDAP Integration Guide
 SchoolBooking LDAP Integration Guide Before you start This guide has been written to help you configure SchoolBooking to connect to your LDAP server. Please treat this document as a reference guide, your
SchoolBooking LDAP Integration Guide Before you start This guide has been written to help you configure SchoolBooking to connect to your LDAP server. Please treat this document as a reference guide, your
Architecture Assessment Case Study. Single Sign on Approach Document PROBLEM: Technology for a Changing World
 Technology for a Changing World Architecture Assessment Case Study Single Sign on Approach Document PROBLEM: Existing portal has Sign on Capabilities based on the SQL Server database and it s not having
Technology for a Changing World Architecture Assessment Case Study Single Sign on Approach Document PROBLEM: Existing portal has Sign on Capabilities based on the SQL Server database and it s not having
3.1 Getting Software and Certificates
 3 Configuring the Remote Client On the remote client you have to download the Sophos SSL VPN Client software including configuration data from the UTM User Portal. Then you install the software package
3 Configuring the Remote Client On the remote client you have to download the Sophos SSL VPN Client software including configuration data from the UTM User Portal. Then you install the software package
Use EMS to protect your mobile data and mobile app
 Use EMS to protect your mobile data and mobile app Peter Daalmans Senior Consultant, Enterprise Mobility MVP CTGlobal. pds@ctglobalservices.com PETER DAALMANS Enterprise Mobility MVP @ CTGlobal Blog: https://peterdaalmans.com
Use EMS to protect your mobile data and mobile app Peter Daalmans Senior Consultant, Enterprise Mobility MVP CTGlobal. pds@ctglobalservices.com PETER DAALMANS Enterprise Mobility MVP @ CTGlobal Blog: https://peterdaalmans.com
Copyright
 This video will look at the different components that make up Active Directory Certificate Services and which services you should look at installing these components on. Which components to install where?
This video will look at the different components that make up Active Directory Certificate Services and which services you should look at installing these components on. Which components to install where?
Enhancing cloud applications by using external authentication services. 2015, 2016 IBM Corporation
 Enhancing cloud applications by using external authentication services After you complete this section, you should understand: Terminology such as authentication, identity, and ID token The benefits of
Enhancing cloud applications by using external authentication services After you complete this section, you should understand: Terminology such as authentication, identity, and ID token The benefits of
Online Banking Initial Log In Instructions. Go to and enter your username: Ex JaneDoe
 Online Banking Initial Log In Instructions Go to www.riverbankandtrust.com and enter your username: Ex JaneDoe 1 Step 1: Enter your existing login ID: Step 2: Enter security code: username + last 4 of
Online Banking Initial Log In Instructions Go to www.riverbankandtrust.com and enter your username: Ex JaneDoe 1 Step 1: Enter your existing login ID: Step 2: Enter security code: username + last 4 of
Copyright
 This video will look at creating a relying party trust in Active Directory Federation Services. A relying party trust is required in order to create claims that will be used by the resource partner. In
This video will look at creating a relying party trust in Active Directory Federation Services. A relying party trust is required in order to create claims that will be used by the resource partner. In
Remotely auditing Check Point devices with Nipper Studio
 Remotely auditing Check Point devices with Nipper Studio Purpose: To explain how to audit a Check Point device using Nipper Studio remotely; Scope: This method will work with all Check Point devices and
Remotely auditing Check Point devices with Nipper Studio Purpose: To explain how to audit a Check Point device using Nipper Studio remotely; Scope: This method will work with all Check Point devices and
User Directories. Overview, Pros and Cons
 User Directories Overview, Pros and Cons Overview Secure ISMS can operate with one or more of the following user directories. Secure ISMS Users (ISMS) Internal users local to the Secure ISMS application
User Directories Overview, Pros and Cons Overview Secure ISMS can operate with one or more of the following user directories. Secure ISMS Users (ISMS) Internal users local to the Secure ISMS application
ArcGIS Server Components: An Introduction to Server IT
 ArcGIS Server Components: An Introduction to Server IT Outline Web Adaptors & Web Server Web Server Certificates Portal Security Settings SQL Server & Management Studio Platform Illustrated: Windows 2012
ArcGIS Server Components: An Introduction to Server IT Outline Web Adaptors & Web Server Web Server Certificates Portal Security Settings SQL Server & Management Studio Platform Illustrated: Windows 2012
Procedure for Connecting to OIL VPN
 Procedure for Connecting to OIL VPN Contents Introduction... 1 Pre-requisites... 1 How to Connect to OIL VPN... 1 Access using Checkpoint remote access client... 2 Note for macos users... 6 Accessing using
Procedure for Connecting to OIL VPN Contents Introduction... 1 Pre-requisites... 1 How to Connect to OIL VPN... 1 Access using Checkpoint remote access client... 2 Note for macos users... 6 Accessing using
RPC Award Program User Guide
 RPC Award Program User Guide This is a two-step application process: The applicant must first request access. It may take 1 to 3 days for access to be granted. Once granted access, the application can
RPC Award Program User Guide This is a two-step application process: The applicant must first request access. It may take 1 to 3 days for access to be granted. Once granted access, the application can
AMEC SCM USER MANUAL AMEC SCM USER MANUAL FOR SUPPLIER. 1 P a g e
 AMEC SCM USER MANUAL FOR SUPPLIER 1 P a g e 1. What is AMEC SCM? AMEC SCM is an application for manage a purchase order and claim slip document of Mitsubishi elevator Asia, co. ltd (AMEC). AMEC will issue
AMEC SCM USER MANUAL FOR SUPPLIER 1 P a g e 1. What is AMEC SCM? AMEC SCM is an application for manage a purchase order and claim slip document of Mitsubishi elevator Asia, co. ltd (AMEC). AMEC will issue
User Guide for the New Kofax Partner Portal
 User Guide for the New Kofax Partner Portal The purpose of this document is to better acquaint you with the basic features of the new Kofax Partner Portal being released in August 2012. Please note that
User Guide for the New Kofax Partner Portal The purpose of this document is to better acquaint you with the basic features of the new Kofax Partner Portal being released in August 2012. Please note that
ArcGIS Enterprise Administration
 TRAINING GUIDE ArcGIS Enterprise Administration Part 3 This session touches on key elements of Portal for ArcGIS setup, configuration and maintenance techniques. Table of Contents Portal for ArcGIS...
TRAINING GUIDE ArcGIS Enterprise Administration Part 3 This session touches on key elements of Portal for ArcGIS setup, configuration and maintenance techniques. Table of Contents Portal for ArcGIS...
Single Sign-On Showdown
 Single Sign-On Showdown ADFS vs Pass-Through Authentication Max Fritz Solutions Architect SADA Systems #ITDEVCONNECTIONS Azure AD Identity Sync & Auth Timeline 2009 2012 DirSync becomes Azure AD Sync 2013
Single Sign-On Showdown ADFS vs Pass-Through Authentication Max Fritz Solutions Architect SADA Systems #ITDEVCONNECTIONS Azure AD Identity Sync & Auth Timeline 2009 2012 DirSync becomes Azure AD Sync 2013
User guide NotifySCM Installer
 User guide NotifySCM Installer TABLE OF CONTENTS 1 Overview... 3 2 Office 365 Users synchronization... 3 3 Installation... 5 4 Starting the server... 17 2 P a g e 1 OVERVIEW This user guide provides instruction
User guide NotifySCM Installer TABLE OF CONTENTS 1 Overview... 3 2 Office 365 Users synchronization... 3 3 Installation... 5 4 Starting the server... 17 2 P a g e 1 OVERVIEW This user guide provides instruction
Help Document Series: Connecting to your Exchange mailbox via Outlook from off-campus
 Help Document Series: Connecting to your Exchange mailbox via Outlook from off-campus This document will take you through setting up your Clark Exchange mailbox in Outlook 2003 from off-campus. This will
Help Document Series: Connecting to your Exchange mailbox via Outlook from off-campus This document will take you through setting up your Clark Exchange mailbox in Outlook 2003 from off-campus. This will
Health Professional & ADFS Integration Guide
 Health Professional & ADFS Integration Guide Martyn Bradshaw, Sitekit Ltd 01/10/2014 09:48:23 Registered Office Company Department Author Document Type Document Title Version Number 1.1 Approved By Sitekit
Health Professional & ADFS Integration Guide Martyn Bradshaw, Sitekit Ltd 01/10/2014 09:48:23 Registered Office Company Department Author Document Type Document Title Version Number 1.1 Approved By Sitekit
Falcon. User Guide. EEG Enterprises, Inc. 586 Main Street Farmingdale, New York eegent.com (516)
 Falcon User Guide EEG Enterprises, Inc. 586 Main Street Farmingdale, New York 11735 eegent.com (516) 293-7472 Contents What is Falcon?... 2 RTMP vs. HTTP Uplink Only... 2 Creating an RTMP Falcon Stream...
Falcon User Guide EEG Enterprises, Inc. 586 Main Street Farmingdale, New York 11735 eegent.com (516) 293-7472 Contents What is Falcon?... 2 RTMP vs. HTTP Uplink Only... 2 Creating an RTMP Falcon Stream...
Using the New UCOP UAT Validation Reports for Graduate Admissions
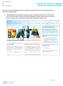 To access the new UAT validation reports in Cognos for Graduate Admissions data, please follow the instructions outlined below: 1. Copy and paste the following link into your browser - http://data.ucop.edu.
To access the new UAT validation reports in Cognos for Graduate Admissions data, please follow the instructions outlined below: 1. Copy and paste the following link into your browser - http://data.ucop.edu.
ADFS integration with Ibistic Commerce Platform A walkthrough of the feature and basic configuration
 IBISTIC TECHNOLOGIES ADFS integration with Ibistic Commerce Platform A walkthrough of the feature and basic configuration Magnus Akselvoll 19/02/2014 Change log 26/06/2012 Initial document 19/02/2014 Added
IBISTIC TECHNOLOGIES ADFS integration with Ibistic Commerce Platform A walkthrough of the feature and basic configuration Magnus Akselvoll 19/02/2014 Change log 26/06/2012 Initial document 19/02/2014 Added
DDS Identity Federation Service
 DDS Identity Federation Service Sharing Identity across Organisational Boundaries Executive Overview for UK Government Company Profile Daemon Directory Services Ltd. (DDS) is an application service provider
DDS Identity Federation Service Sharing Identity across Organisational Boundaries Executive Overview for UK Government Company Profile Daemon Directory Services Ltd. (DDS) is an application service provider
HOW TO SETUP CFS POLICIES WITH LDAP AND SSO TO RESTRICT INTERNET ACCESS ON CFS 3.0
 HOW TO SETUP CFS POLICIES WITH LDAP AND SSO TO RESTRICT INTERNET ACCESS ON CFS 3.0 DESCRIPTION This article explains about how to integrate Premium Content Filtering Service with LDAP (With Single Sign
HOW TO SETUP CFS POLICIES WITH LDAP AND SSO TO RESTRICT INTERNET ACCESS ON CFS 3.0 DESCRIPTION This article explains about how to integrate Premium Content Filtering Service with LDAP (With Single Sign
Education Data System (EDS) Administration Manual
 Education Data System (EDS) Administration Manual December 2017 Prepared by OSPI Customer Support Table of Contents Using Education Data System (EDS) Administration...2 Introduction...2 Overview of EDS
Education Data System (EDS) Administration Manual December 2017 Prepared by OSPI Customer Support Table of Contents Using Education Data System (EDS) Administration...2 Introduction...2 Overview of EDS
ESS Security Enhancements
 ESS Security Enhancements payentry.com Employee Self Service Enhancements 1 Table of Contents INTRODUCTION 3 EXISTING EMPLOYEES 3 Existing Employee -Email Address 4 Existing Employee - Username 4 Existing
ESS Security Enhancements payentry.com Employee Self Service Enhancements 1 Table of Contents INTRODUCTION 3 EXISTING EMPLOYEES 3 Existing Employee -Email Address 4 Existing Employee - Username 4 Existing
Cloud Access Manager Configuration Guide
 Cloud Access Manager 8.1.3 Configuration Guide Copyright 2017 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide
Cloud Access Manager 8.1.3 Configuration Guide Copyright 2017 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide
Actual4Test. Actual4test - actual test exam dumps-pass for IT exams
 Actual4Test http://www.actual4test.com Actual4test - actual test exam dumps-pass for IT exams Exam : 1z1-349 Title : Oracle Eloqua Marketing Cloud Service 2017 Implementation Essentials Vendor : Oracle
Actual4Test http://www.actual4test.com Actual4test - actual test exam dumps-pass for IT exams Exam : 1z1-349 Title : Oracle Eloqua Marketing Cloud Service 2017 Implementation Essentials Vendor : Oracle
Security Provider Integration Kerberos Authentication
 Security Provider Integration Kerberos Authentication 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are
Security Provider Integration Kerberos Authentication 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are
Massachusetts Registry of Motor Vehicles ATLAS. Insurance Company Help Documentation Version 1.0 3/22/2018
 ATLAS Version 1.0 3/22/2018 Last Modified: 03/22/2018 Contents General E-Services Information... 2 Access Type and Access Level... 2 First Time Logon... 2 Account Information... 3 Logon Profile Information...
ATLAS Version 1.0 3/22/2018 Last Modified: 03/22/2018 Contents General E-Services Information... 2 Access Type and Access Level... 2 First Time Logon... 2 Account Information... 3 Logon Profile Information...
Attachment 3 (B); Security Exhibit. As of March 29, 2016
 Attachment 3 (B); Security Exhibit As of March 29, 2016 UVA Medical Center (UVaMC) Security Requirements The term System shall mean computer equipment, peripheral equipment, system software, application
Attachment 3 (B); Security Exhibit As of March 29, 2016 UVA Medical Center (UVaMC) Security Requirements The term System shall mean computer equipment, peripheral equipment, system software, application
Microsoft MB Microsoft Dynamics CRM 2016 Installation. Download Full version :
 Microsoft MB2-711 Microsoft Dynamics CRM 2016 Installation Download Full version : https://killexams.com/pass4sure/exam-detail/mb2-711 Answer: D QUESTION: 87 Which two components are required to enable
Microsoft MB2-711 Microsoft Dynamics CRM 2016 Installation Download Full version : https://killexams.com/pass4sure/exam-detail/mb2-711 Answer: D QUESTION: 87 Which two components are required to enable
Account Set Up Guide
 Email Account Set Up Guide January 08. Webmail. Desktop Clients. Mobile Setup Account Set Up Details The following details are needed to set up your email account in desktop clients or mobile devices.
Email Account Set Up Guide January 08. Webmail. Desktop Clients. Mobile Setup Account Set Up Details The following details are needed to set up your email account in desktop clients or mobile devices.
Configuring Microsoft Outlook to Connect to Hosted Exchange Service
 Configuring Microsoft Outlook to Connect to Hosted Exchange Service Configuring Microsoft Outlook for Hosted Exchange Service Version: 1.0 Updated on: April 27, 2011 Page 1 of 7 TABLE OF CONTENTS Configuring
Configuring Microsoft Outlook to Connect to Hosted Exchange Service Configuring Microsoft Outlook for Hosted Exchange Service Version: 1.0 Updated on: April 27, 2011 Page 1 of 7 TABLE OF CONTENTS Configuring
Qualys SAML 2.0 Single Sign-On (SSO) Technical Brief
 Qualys SAML 2.0 Single Sign-On (SSO) Technical Brief Qualys provides its customers the option to use SAML 2.0 Single SignOn (SSO) authentication with their Qualys subscription. When implemented, Qualys
Qualys SAML 2.0 Single Sign-On (SSO) Technical Brief Qualys provides its customers the option to use SAML 2.0 Single SignOn (SSO) authentication with their Qualys subscription. When implemented, Qualys
LastPass Enterprise Recommended Policies Guide
 LastPass Enterprise Recommended Policies Guide This document will help guide you through common scenarios and selecting policies to enable on your LastPass Enterprise account. We will not cover all policies
LastPass Enterprise Recommended Policies Guide This document will help guide you through common scenarios and selecting policies to enable on your LastPass Enterprise account. We will not cover all policies
Quick Start: Permission requests and approvals
 Quick Start: Permission requests and approvals and approvals Microsoft Volume Licensing Field Center This guide shows field users the process for requesting access to the Volume Licensing Field Center
Quick Start: Permission requests and approvals and approvals Microsoft Volume Licensing Field Center This guide shows field users the process for requesting access to the Volume Licensing Field Center
Load Balancing Microsoft AD FS. Deployment Guide v Copyright Loadbalancer.org
 Load Balancing Microsoft AD FS Deployment Guide v1.3.1 Copyright Loadbalancer.org Table of Contents 1. About this Guide...4 2. Loadbalancer.org Appliances Supported...4 3. Loadbalancer.org Software Versions
Load Balancing Microsoft AD FS Deployment Guide v1.3.1 Copyright Loadbalancer.org Table of Contents 1. About this Guide...4 2. Loadbalancer.org Appliances Supported...4 3. Loadbalancer.org Software Versions
Passwordstate Mobile Client Manual Click Studios (SA) Pty Ltd
 2 Table of Contents Foreword 0 Part I Introduction 3 Part II User Preferences 3 Part III System Settings 4 Part IV Mobile Client Permissions 6 Part V Mobile Client Usage 8 Introduction 1 3 Introduction
2 Table of Contents Foreword 0 Part I Introduction 3 Part II User Preferences 3 Part III System Settings 4 Part IV Mobile Client Permissions 6 Part V Mobile Client Usage 8 Introduction 1 3 Introduction
FUJITSU Cloud Service S5 Setup and Configuration of the FTP Service under Windows 2008/2012 Server
 FUJITSU Cloud Service S5 Setup and Configuration of the FTP Service under Windows 2008/2012 Server This guide details steps required to install and configure a basic FTP server on a Windows 2008/2012 VM
FUJITSU Cloud Service S5 Setup and Configuration of the FTP Service under Windows 2008/2012 Server This guide details steps required to install and configure a basic FTP server on a Windows 2008/2012 VM
Revised: 08/02/ Click the Start button at bottom left, enter Server Manager in the search box, and select it in the list to open it.
 Mobile App Windows Authentication & SSL Config Revised: 08/02/2017 Job Aid This Job Aid is intended for agency IT staff and explains how to enable Windows Authentication and SSL for your mobile applications
Mobile App Windows Authentication & SSL Config Revised: 08/02/2017 Job Aid This Job Aid is intended for agency IT staff and explains how to enable Windows Authentication and SSL for your mobile applications
CUSTOMER CONTROL PANEL... 2 DASHBOARD... 3 HOSTING &
 Table of Contents CUSTOMER CONTROL PANEL... 2 LOGGING IN... 2 RESET YOUR PASSWORD... 2 DASHBOARD... 3 HOSTING & EMAIL... 4 WEB FORWARDING... 4 WEBSITE... 5 Usage... 5 Subdomains... 5 SSH Access... 6 File
Table of Contents CUSTOMER CONTROL PANEL... 2 LOGGING IN... 2 RESET YOUR PASSWORD... 2 DASHBOARD... 3 HOSTING & EMAIL... 4 WEB FORWARDING... 4 WEBSITE... 5 Usage... 5 Subdomains... 5 SSH Access... 6 File
TECHNICAL GUIDE SSO SAML. At 360Learning, we don t make promises about technical solutions, we make commitments.
 TECHNICAL GUIDE SSO SAML At 360Learning, we don t make promises about technical solutions, we make commitments. This technical guide is part of our Technical Documentation. 2 360Learning is a Leading European
TECHNICAL GUIDE SSO SAML At 360Learning, we don t make promises about technical solutions, we make commitments. This technical guide is part of our Technical Documentation. 2 360Learning is a Leading European
On-demand target, up and running
 On-demand target, up and running ii On-demand target, up and running Contents Chapter 1. Assumptions........ 1 Chapter 2. Overview......... 3 Chapter 3. Component purpose.... 5 Chapter 5. Starting a session
On-demand target, up and running ii On-demand target, up and running Contents Chapter 1. Assumptions........ 1 Chapter 2. Overview......... 3 Chapter 3. Component purpose.... 5 Chapter 5. Starting a session
Multi Factor Authentication & Self Password Reset
 Multi Factor Authentication & Self Password Reset Prepared by: Mohammad Asmayal Jawad https://ca.linkedin.com/in/asmayal August 14, 2017 Table of Contents Selectable Verification Methods... 2 Set up multi-factor
Multi Factor Authentication & Self Password Reset Prepared by: Mohammad Asmayal Jawad https://ca.linkedin.com/in/asmayal August 14, 2017 Table of Contents Selectable Verification Methods... 2 Set up multi-factor
Cloud Access Manager Overview
 Cloud Access Manager 8.1.3 Overview Copyright 2017 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished
Cloud Access Manager 8.1.3 Overview Copyright 2017 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished
Android Mobile Single Sign-On to VMware Workspace ONE. SEP 2018 VMware Workspace ONE VMware Identity Manager VMware Identity Manager 3.
 Android Mobile Single Sign-On to VMware Workspace ONE SEP 2018 VMware Workspace ONE VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on the VMware
Android Mobile Single Sign-On to VMware Workspace ONE SEP 2018 VMware Workspace ONE VMware Identity Manager VMware Identity Manager 3.3 You can find the most up-to-date technical documentation on the VMware
BSD-BSS system user guide
 The Bank hereby notifies, and the Client confirms that accepts all obligations to independently configure the RBS BSS system. At the same time, the Customer agrees that the Bank does not take any measures
The Bank hereby notifies, and the Client confirms that accepts all obligations to independently configure the RBS BSS system. At the same time, the Customer agrees that the Bank does not take any measures
Nuance. PowerMic Mobile. Installation and Administration Guide
 Nuance PowerMic Mobile Installation and Administration Guide Table of contents Welcome to PowerMic Mobile 3 System requirements 4 Hardware and software requirements 4 Network requirements 4 System sizing
Nuance PowerMic Mobile Installation and Administration Guide Table of contents Welcome to PowerMic Mobile 3 System requirements 4 Hardware and software requirements 4 Network requirements 4 System sizing
SAML-Based SSO Solution
 About SAML SSO Solution, page 1 SAML-Based SSO Features, page 2 Basic Elements of a SAML SSO Solution, page 2 SAML SSO Web Browsers, page 3 Cisco Unified Communications Applications that Support SAML SSO,
About SAML SSO Solution, page 1 SAML-Based SSO Features, page 2 Basic Elements of a SAML SSO Solution, page 2 SAML SSO Web Browsers, page 3 Cisco Unified Communications Applications that Support SAML SSO,
SAP Security in a Hybrid World. Kiran Kola
 SAP Security in a Hybrid World Kiran Kola Agenda Cybersecurity SAP Cloud Platform Identity Provisioning service SAP Cloud Platform Identity Authentication service SAP Cloud Connector & how to achieve Principal
SAP Security in a Hybrid World Kiran Kola Agenda Cybersecurity SAP Cloud Platform Identity Provisioning service SAP Cloud Platform Identity Authentication service SAP Cloud Connector & how to achieve Principal
The benefits of synchronizing G Suite and Active Directory passwords
 The benefits of synchronizing G Suite and Active Directory passwords www.adselfserviceplus.com Enterprises are adopting more and more applications to enhance productivity and improve employees' user experience.
The benefits of synchronizing G Suite and Active Directory passwords www.adselfserviceplus.com Enterprises are adopting more and more applications to enhance productivity and improve employees' user experience.
Holy Cross School Laptop Configuration Instructions for Students Grades 5 10 MAC OS
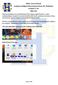 Holy Cross School Laptop Configuration Instructions for Students Grades 5 10 MAC OS This documentation is for students that will be using an Apple MacBook. A basic understanding of computers is assumed
Holy Cross School Laptop Configuration Instructions for Students Grades 5 10 MAC OS This documentation is for students that will be using an Apple MacBook. A basic understanding of computers is assumed
Qualys SAML & Microsoft Active Directory Federation Services Integration
 Qualys SAML & Microsoft Active Directory Federation Services Integration Microsoft Active Directory Federation Services (ADFS) is currently supported for authentication. The Qualys ADFS integration must
Qualys SAML & Microsoft Active Directory Federation Services Integration Microsoft Active Directory Federation Services (ADFS) is currently supported for authentication. The Qualys ADFS integration must
AFN Setup. If you have any trouble setting it up please contact the Help Desk by at Outlook 2007 and 2010
 AFN Email Setup Each version of Outlook is set up in the same general way. Some of the screens may have a few variations to them but they all should have the same options. Outlook 2007 and 2010 are very
AFN Email Setup Each version of Outlook is set up in the same general way. Some of the screens may have a few variations to them but they all should have the same options. Outlook 2007 and 2010 are very
Connect to Wireless, certificate install and setup Citrix Receiver
 Connect to Wireless, certificate install and setup Citrix Receiver This document explains how to connect to the Wireless Network, certificate and access applications using Citrix Receiver on a Bring Your
Connect to Wireless, certificate install and setup Citrix Receiver This document explains how to connect to the Wireless Network, certificate and access applications using Citrix Receiver on a Bring Your
Ramnish Singh IT Advisor Microsoft Corporation Session Code:
 Ramnish Singh IT Advisor Microsoft Corporation Session Code: Agenda Microsoft s Identity and Access Strategy Geneva Claims Based Access User access challenges Identity Metasystem and claims solution Introducing
Ramnish Singh IT Advisor Microsoft Corporation Session Code: Agenda Microsoft s Identity and Access Strategy Geneva Claims Based Access User access challenges Identity Metasystem and claims solution Introducing
Single Sign-On for PCF. User's Guide
 Single Sign-On for PCF Version 1.2 User's Guide 2018 Pivotal Software, Inc. Table of Contents Table of Contents Single Sign-On Overview Installation Getting Started with Single Sign-On Manage Service Plans
Single Sign-On for PCF Version 1.2 User's Guide 2018 Pivotal Software, Inc. Table of Contents Table of Contents Single Sign-On Overview Installation Getting Started with Single Sign-On Manage Service Plans
Configuring Alfresco Cloud with ADFS 3.0
 Configuring Alfresco Cloud with ADFS 3.0 Prerequisites: You have a working domain on your Windows Server 2012 and successfully installed ADFS. For these instructions, I created: alfresco.me as a domain
Configuring Alfresco Cloud with ADFS 3.0 Prerequisites: You have a working domain on your Windows Server 2012 and successfully installed ADFS. For these instructions, I created: alfresco.me as a domain
Adobe Document Cloud esign Services. for Salesforce Version 17 Upgrade Guide
 Adobe Document Cloud esign Services for Salesforce Version 17 Upgrade Guide 2015 Adobe Systems Incorporated. All Rights Reserved. Last Updated: August 25, 2015 Table of Contents Upgrading from a previous
Adobe Document Cloud esign Services for Salesforce Version 17 Upgrade Guide 2015 Adobe Systems Incorporated. All Rights Reserved. Last Updated: August 25, 2015 Table of Contents Upgrading from a previous
Step-by-step installation guide for monitoring untrusted servers using Operations Manager
 Step-by-step installation guide for monitoring untrusted servers using Operations Manager Most of the time through Operations Manager, you may require to monitor servers and clients that are located outside
Step-by-step installation guide for monitoring untrusted servers using Operations Manager Most of the time through Operations Manager, you may require to monitor servers and clients that are located outside
How to Set Up External CA VPN Certificates
 To configure a client-to-site, or site-to-site VPN using s created by External CA, you must create the following VPN s for the VPN service to be able to authenticate Before you begin Use an external CA
To configure a client-to-site, or site-to-site VPN using s created by External CA, you must create the following VPN s for the VPN service to be able to authenticate Before you begin Use an external CA
Remote Access via Cisco VPN Client
 Remote Access via Cisco VPN Client General Information This guide describes step by step the configuration of a remote access to the Astaro Security Gateway by using the Cisco VPN Client. The Cisco VPN
Remote Access via Cisco VPN Client General Information This guide describes step by step the configuration of a remote access to the Astaro Security Gateway by using the Cisco VPN Client. The Cisco VPN
Building Block Installation - Admins
 Building Block Installation - Admins Overview To use your Blackboard Server with Panopto, you first need to install the Panopto Building Block on your Blackboard server. You then need to add Blackboard
Building Block Installation - Admins Overview To use your Blackboard Server with Panopto, you first need to install the Panopto Building Block on your Blackboard server. You then need to add Blackboard
Sponsored Candidate Application Guide Voucher
 Sponsored Candidate Application Guide Voucher This guide will assist you through the Pharmacy Technician Certification Exam (PTCE) application process. Sponsored Candidate Application Guide Table of Contents
Sponsored Candidate Application Guide Voucher This guide will assist you through the Pharmacy Technician Certification Exam (PTCE) application process. Sponsored Candidate Application Guide Table of Contents
Setting Up Resources in VMware Identity Manager (On Premises) Modified on 30 AUG 2017 VMware AirWatch 9.1.1
 Setting Up Resources in VMware Identity Manager (On Premises) Modified on 30 AUG 2017 VMware AirWatch 9.1.1 Setting Up Resources in VMware Identity Manager (On Premises) You can find the most up-to-date
Setting Up Resources in VMware Identity Manager (On Premises) Modified on 30 AUG 2017 VMware AirWatch 9.1.1 Setting Up Resources in VMware Identity Manager (On Premises) You can find the most up-to-date
TRAINING GUIDE. Tablet: Cradle to Mobile Configuration and Setup
 TRAINING GUIDE Tablet: Cradle to Mobile Configuration and Setup Tablet Cradle to Mobile The Lucity Android Tablet and Lucity ios applications have been designed to work under the same framework as the
TRAINING GUIDE Tablet: Cradle to Mobile Configuration and Setup Tablet Cradle to Mobile The Lucity Android Tablet and Lucity ios applications have been designed to work under the same framework as the
CONNX SECURITY OVERVIEW
 CONNX SECURITY OVERVIEW ConnX is a web-based application which can be installed in a variety of technical environments. This purpose of this document is to advise you on the security aspects that are provided
CONNX SECURITY OVERVIEW ConnX is a web-based application which can be installed in a variety of technical environments. This purpose of this document is to advise you on the security aspects that are provided
Authentication. Katarina
 Authentication Katarina Valalikova @KValalikova k.valalikova@evolveum.com 1 Agenda History Multi-factor, adaptive authentication SSO, SAML, OAuth, OpenID Connect Federation 2 Who am I? Ing. Katarina Valaliková
Authentication Katarina Valalikova @KValalikova k.valalikova@evolveum.com 1 Agenda History Multi-factor, adaptive authentication SSO, SAML, OAuth, OpenID Connect Federation 2 Who am I? Ing. Katarina Valaliková
Configuration examples for the D-Link NetDefend Firewall series DFL-260/860
 Configuration examples for the D-Link NetDefend Firewall series DFL-260/860 Scenario: How to configure User Authentication for multiple groups Last update: 2008-04-29 Overview In this document, the notation
Configuration examples for the D-Link NetDefend Firewall series DFL-260/860 Scenario: How to configure User Authentication for multiple groups Last update: 2008-04-29 Overview In this document, the notation
SMS 2.0 SSO / LDAP Launch Kit
 SMS 2.0 SSO / LDAP Launch Kit Table of Contents What options are available in SMS 2.0 for Single Sign On?... 4 LDAP (Lightweight Directory Access Protocol)... 4 SkySSO (Skyward Single Sign On)... 4 SkySTS
SMS 2.0 SSO / LDAP Launch Kit Table of Contents What options are available in SMS 2.0 for Single Sign On?... 4 LDAP (Lightweight Directory Access Protocol)... 4 SkySSO (Skyward Single Sign On)... 4 SkySTS
Using the New UCOP UAT Validation Reports For Undergraduate Admissions
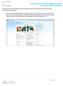 To access the new UAT validation reports in Cognos for Course Enrollment data, please follow the instructions outlined below: 1. Copy and paste the following link into your browser - http://data.ucop.edu.
To access the new UAT validation reports in Cognos for Course Enrollment data, please follow the instructions outlined below: 1. Copy and paste the following link into your browser - http://data.ucop.edu.
[Outlook Configuration Guide]
![[Outlook Configuration Guide] [Outlook Configuration Guide]](/thumbs/76/74367649.jpg) Prepared By: Sandeep Das Approved By: Effective From: October, 03, 2011 REVISION HISTORY S. N. Release Date Description Author Highlights 1 3 rd October 2011 First Release Sandeep Das First Release Copyright
Prepared By: Sandeep Das Approved By: Effective From: October, 03, 2011 REVISION HISTORY S. N. Release Date Description Author Highlights 1 3 rd October 2011 First Release Sandeep Das First Release Copyright
Online Fundraising Guide
 Online Fundraising Guide Step by Step Guide to Your Participant Center Learn How To: Access Your Participant Center Navigate Your Participant Center Home Page Update Your Fundraising Goal Send Emails From
Online Fundraising Guide Step by Step Guide to Your Participant Center Learn How To: Access Your Participant Center Navigate Your Participant Center Home Page Update Your Fundraising Goal Send Emails From
Do It Yourself Fundraising Guide
 Do It Yourself Fundraising Guide To Set Up a Do It Yourself (DIY) Fundraising Event: Step 1: Visit our website: http://www.nationalmssociety.org/chapters/mig/fundraisingevents/diy-event-information/index.aspx
Do It Yourself Fundraising Guide To Set Up a Do It Yourself (DIY) Fundraising Event: Step 1: Visit our website: http://www.nationalmssociety.org/chapters/mig/fundraisingevents/diy-event-information/index.aspx
IBM C Exam. Volume: 65 Questions
 Volume: 65 Questions Question No: 1 A customer has a requirement which is currently unavailable in an out-of-the-box product. Who would be able to assist in troubleshooting the customer when developing
Volume: 65 Questions Question No: 1 A customer has a requirement which is currently unavailable in an out-of-the-box product. Who would be able to assist in troubleshooting the customer when developing
Securing ArcGIS Services
 Federal GIS Conference 2014 February 10 11, 2014 Washington DC Securing ArcGIS Services James Cardona Agenda Security in the context of ArcGIS for Server Background concepts Access Securing web services
Federal GIS Conference 2014 February 10 11, 2014 Washington DC Securing ArcGIS Services James Cardona Agenda Security in the context of ArcGIS for Server Background concepts Access Securing web services
ISA 767, Secure Electronic Commerce Xinwen Zhang, George Mason University
 Identity Management and Federated ID (Liberty Alliance) ISA 767, Secure Electronic Commerce Xinwen Zhang, xzhang6@gmu.edu George Mason University Identity Identity is the fundamental concept of uniquely
Identity Management and Federated ID (Liberty Alliance) ISA 767, Secure Electronic Commerce Xinwen Zhang, xzhang6@gmu.edu George Mason University Identity Identity is the fundamental concept of uniquely
1 Installing KEEP is Easy
 Installing KEEP is Easy 1 Installing KEEP is Easy 1. Plug in the network cable to in Internet enabled port, either directly connected to the Internet or behind a router. 2. Connect the power supply to
Installing KEEP is Easy 1 Installing KEEP is Easy 1. Plug in the network cable to in Internet enabled port, either directly connected to the Internet or behind a router. 2. Connect the power supply to
Integration Guide. SafeNet Authentication Manager. Using SAM as an Identity Provider for SonicWALL Secure Remote Access
 SafeNet Authentication Manager Integration Guide Using SAM as an Identity Provider for SonicWALL Secure Remote Access Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright
SafeNet Authentication Manager Integration Guide Using SAM as an Identity Provider for SonicWALL Secure Remote Access Technical Manual Template Release 1.0, PN: 000-000000-000, Rev. A, March 2013, Copyright
SafeNet Authentication Manager
 SafeNet Authentication Manager INTEGRATION GUIDE Using SAM as an Identity Provider for Remedyforce Contents Support Contacts... 2 Description... 3 Single Sign-On Dataflow... 3 Configuring SAM as an Identity
SafeNet Authentication Manager INTEGRATION GUIDE Using SAM as an Identity Provider for Remedyforce Contents Support Contacts... 2 Description... 3 Single Sign-On Dataflow... 3 Configuring SAM as an Identity
CC Box Execution Page
 This article describes the functionalities of the Box Execution view of the Barracuda NG Control Center. Introduction The Barracuda NG Control Center control facility allows remote execution of scripts
This article describes the functionalities of the Box Execution view of the Barracuda NG Control Center. Introduction The Barracuda NG Control Center control facility allows remote execution of scripts
Importing Merit Calendar to Outlook 2010
 Page 1 of 12 Importing Merit Calendar to Outlook 2010 Transferring your calendar from the Merit Mail system to your new Outlook Exchange account is a quick and easy process. There are only two steps to
Page 1 of 12 Importing Merit Calendar to Outlook 2010 Transferring your calendar from the Merit Mail system to your new Outlook Exchange account is a quick and easy process. There are only two steps to
Tenable.io for Thycotic
 How-To Guide Tenable.io for Thycotic Introduction This document describes how to deploy Tenable.io for integration with Thycotic Secret Server. Please email any comments and suggestions to support@tenable.com.
How-To Guide Tenable.io for Thycotic Introduction This document describes how to deploy Tenable.io for integration with Thycotic Secret Server. Please email any comments and suggestions to support@tenable.com.
NetExtender for SSL-VPN
 NetExtender for SSL-VPN Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL-VPN Environment. This document contains the following
NetExtender for SSL-VPN Document Scope This document describes how to plan, design, implement, and manage the NetExtender feature in a SonicWALL SSL-VPN Environment. This document contains the following
Authentication CS 4720 Mobile Application Development
 Authentication Mobile Application Development System Security Human: social engineering attacks Physical: steal the server itself Network: treat your server like a 2 year old Operating System: the war
Authentication Mobile Application Development System Security Human: social engineering attacks Physical: steal the server itself Network: treat your server like a 2 year old Operating System: the war
Minimum requirements for Portal (on-premise version):
 Minimum requirements for Portal (on-premise version): Windows Server 2012 R2 Windows 10 (licensed) with the latest updates (64 bit only). All Windows applications must be licensed and activated. SQL Server
Minimum requirements for Portal (on-premise version): Windows Server 2012 R2 Windows 10 (licensed) with the latest updates (64 bit only). All Windows applications must be licensed and activated. SQL Server
Skandocs Installation and Connectivity Guide What you need to know to successfully utilise the Internet connectivity in Skandocs
 Skandocs Installation and Connectivity Guide What you need to know to successfully utilise the Internet connectivity in Skandocs Intended Audience This document is aimed at IT technical support professionals
Skandocs Installation and Connectivity Guide What you need to know to successfully utilise the Internet connectivity in Skandocs Intended Audience This document is aimed at IT technical support professionals
AvePoint Governance Automation 2. Release Notes
 AvePoint Governance Automation 2 Release Notes Service Pack 2, Cumulative Update 1 Release Date: June 2018 New Features and Improvements In the Create Office 365 Group/Team service > Governance Automation
AvePoint Governance Automation 2 Release Notes Service Pack 2, Cumulative Update 1 Release Date: June 2018 New Features and Improvements In the Create Office 365 Group/Team service > Governance Automation
User guide AppGate version 11.3-LTS-u1
 User guide AppGate version 11.3-LTS-u1 User guide Table of Contents 1. About this user guide... 1 1.1. Who should use this user guide... 1 2. What is AppGate security server... 2 2.1. User account... 2
User guide AppGate version 11.3-LTS-u1 User guide Table of Contents 1. About this user guide... 1 1.1. Who should use this user guide... 1 2. What is AppGate security server... 2 2.1. User account... 2
Configuring RentalPoint Web Services
 Table of Contents 1. What is RentalPoint Web Services? 2 2. How to Configure Your Server 2 2.1 Download and Install.NET Framework 4.5.1 2 2.2 Download and Install IIS 2 2.3 Download and Install RPWS Files
Table of Contents 1. What is RentalPoint Web Services? 2 2. How to Configure Your Server 2 2.1 Download and Install.NET Framework 4.5.1 2 2.2 Download and Install IIS 2 2.3 Download and Install RPWS Files
Identity Provider for SAP Single Sign-On and SAP Identity Management
 Implementation Guide Document Version: 1.0 2017-05-15 PUBLIC Identity Provider for SAP Single Sign-On and SAP Identity Management Content 1....4 1.1 What is SAML 2.0.... 5 SSO with SAML 2.0.... 6 SLO with
Implementation Guide Document Version: 1.0 2017-05-15 PUBLIC Identity Provider for SAP Single Sign-On and SAP Identity Management Content 1....4 1.1 What is SAML 2.0.... 5 SSO with SAML 2.0.... 6 SLO with
RNDC / NDC MicroStrategy Supplier Web Troubleshooting Guide
 RNDC / NDC MicroStrategy Supplier Web Troubleshooting Guide Where do I log into MicroStrategy for RNDC markets? 2 Where do I log into MicroStrategy for NDC markets? 3 Why can t I log in? Most common log
RNDC / NDC MicroStrategy Supplier Web Troubleshooting Guide Where do I log into MicroStrategy for RNDC markets? 2 Where do I log into MicroStrategy for NDC markets? 3 Why can t I log in? Most common log
Publishing Enterprise Web Applications to BYOD using a Granular. Trust Model. Shachaf Levi IT Client Security & Connectivity May 2013.
 Publishing Enterprise Web Applications to BYOD using a Granular Trust Model Shachaf Levi IT Client Security & Connectivity May 2013 Public Legal Notices This presentation is for informational purposes
Publishing Enterprise Web Applications to BYOD using a Granular Trust Model Shachaf Levi IT Client Security & Connectivity May 2013 Public Legal Notices This presentation is for informational purposes
DocAve. Release Notes. Governance Automation Service Pack 5 Cumulative Update 2. For Microsoft SharePoint
 DocAve Governance Automation Service Pack 5 Cumulative Update 2 Release Notes For Microsoft SharePoint Released March 10, 2015 Governance Automation SP5 CU2 Update Details Refer to the Updating Governance
DocAve Governance Automation Service Pack 5 Cumulative Update 2 Release Notes For Microsoft SharePoint Released March 10, 2015 Governance Automation SP5 CU2 Update Details Refer to the Updating Governance
Step-by-Step Guide to Ansur Executive 3.0 Installation With or without Electronic Signatures
 Step-by-Step Guide to Ansur Executive 3.0 Installation With or without Electronic Signatures Ansur with Electronic Signatures Background: Electronic signature is a new feature that is implemented in Ansur
Step-by-Step Guide to Ansur Executive 3.0 Installation With or without Electronic Signatures Ansur with Electronic Signatures Background: Electronic signature is a new feature that is implemented in Ansur
