User guide AppGate version 11.3-LTS-u1
|
|
|
- Bernadette James
- 5 years ago
- Views:
Transcription
1 User guide AppGate version 11.3-LTS-u1
2 User guide
3 Table of Contents 1. About this user guide Who should use this user guide What is AppGate security server User account Keep the password private Password quality User access Access from any device How to use the AppGate client Start the AppGate client Change password Log out... 4 iii
4 Chapter 1. About this user guide This guide describes how to use an AppGate client that interact with the AppGate security server. The function of the AppGate security server is to give access to company applications for authorized users Who should use this user guide This document is for general users who need to login through the AppGate security server to gain access to company applications. This login procedure is needed to secure the company resources from unathorized access. 1
5 Chapter 2. What is AppGate security server The AppGate security server protects the company applications and resources. It does so by giving access to authorized users only User account The user need to have an user account within the company organisation. The company have to decide which authentication method the user shall use. The AppGate security server supports a wide range of authentication methods. Some examples are Certificate, Public key, SecurId, SMS two factor authentication, any authentication method based on Radius and ordinary passwords Keep the password private It is important that the user understands that the security of the company resources is dependent on the user to keep the password or the pincode private Password quality The password quality is important and there may be an enforcement on how the password may be composed. An example of a password quality enforcement is that a password must be composed of at least 8 characters and of those at least 2 have to be non-alphanumeric and furthermore 2 have to be non-lowercase characters. There may be enforcement on how often a password may (or may not) be required to change User access The user can be granted access to different amount of the company resources or application. The amount of access a user can have is defined in a role. After the user is authenticated the user has to chose a role from the list of roles that the user has access to. It is the administrator of the AppGate security server that defines the roles and which users that shall have access to which roles Access from any device Since access to the company applications and resources are based on user access and not on machines or location, it is possible to securely access the company application from any location and any device. A user device can be a laptop, a mobile phone or an ordinary computer. The location can be anywhere the user can connect the device to the internet. Remote users may only run trusted software on their devices. The communication between the user device and the AppGate security server is encrypted. 2
6 Chapter 3. How to use the AppGate client AppGate security server protects the company resources. AppGate security server gives access to authorized users only. Since access is based on users it is important that the user understands that the security of the company resources is dependent on the user to keep the user password or pincode private Start the AppGate client The first step towards gaining access to the company applications is to launch the AppGate client. This is normally done through clicking on the AppGate icon. The user will be presented with a dialog to login to the AppGate security server. 1. Specify the name of the server to connect to. Previous servers will be listed in the drop-down list. Selecting a server from the drop-down list may fill in other fields as well. 2. Select which authentication method to use. 3. The other authentication fields depend on the selected authentication method. In the case of the password authentication it is the username and the password that should be applied by the user. When the user is authenticated a view is presented where the user has to chose which role to use. The different roles gives access to different amount of application or resources. For security reasons it is important to select the least privileged role possible for the task at hand, if there is several roles to chose from. It is possible to only have a single role. In that case the user will be logged in with this role, and will not be presented with the possibility to chose roles. If there are no role at all associated with the user, it is not possible to log in for the user. 3
7 How to use the AppGate client When the user are successfully logged in, the AppGate client will display the applications the user are athorized to use. To start an application the user has to doubleclick on the corresponding icon Change password 3.3. Log out If you are using password as authentication method you can easily change your password within the AppGate client. Since there are so many possible authentication methods a company may use together with the AppGate Security Server, it is advisable to refer to the local system administrator or company information of how to change password on other authentication methods than that of ordinary password. The AppGate security server supports a wide range of authentication methods. Some examples are Certificate, Public key, SecurId, SMS two factor authentication, any authentication method based on Radius and ordinary passwords. Authentication method password To change the password, the user first have to login to the AppGate client. Then the user will have to chose the "change password" alternative from the Connection menu in the AppGate client. If "change password" is greyed out and not possible to chose it means that the company uses another authentication method than ordinary password. Then the user has to contact the local system administrator to find out how to change the password. other authentication methods Refer to the local system administrator or company information of how to change password on other authentication methods than that of ordinary password. To log out of the AppGate client the user has to chose "Exit" from the Connection menu. This will log out the user and the company applications will be unavailable until the next time the user logs in to the AppGate client again. 4
Portwise support is not available on MAC computers.
 Informerande dokument Information Sida 1 (6) User manual Portwise Portwise is a product which you can connect from the Internet to NLLNET via an encrypted connection. The encrypted connection is required
Informerande dokument Information Sida 1 (6) User manual Portwise Portwise is a product which you can connect from the Internet to NLLNET via an encrypted connection. The encrypted connection is required
Connecting to the NJITSecure wireless network.
 Connecting to the NJITSecure wireless network. 1. Start by going to the Start menu and selecting Control Panel 2. Your control Panel will most likely be in Category view, you will need to change it to
Connecting to the NJITSecure wireless network. 1. Start by going to the Start menu and selecting Control Panel 2. Your control Panel will most likely be in Category view, you will need to change it to
Configuring Role-Based Access Control
 Configuring Role-Based Access Control This chapter includes the following sections: Role-Based Access Control, page 1 User Accounts for Cisco UCS Manager, page 1 User Roles, page 3 Privileges, page 4 User
Configuring Role-Based Access Control This chapter includes the following sections: Role-Based Access Control, page 1 User Accounts for Cisco UCS Manager, page 1 User Roles, page 3 Privileges, page 4 User
Connect to Wireless, certificate install and setup Citrix Receiver
 Connect to Wireless, certificate install and setup Citrix Receiver This document explains how to connect to the Wireless Network and access applications using Citrix Receiver on a Bring Your Own Device
Connect to Wireless, certificate install and setup Citrix Receiver This document explains how to connect to the Wireless Network and access applications using Citrix Receiver on a Bring Your Own Device
Manual for configuring VPN in Windows 7
 Manual for configuring VPN in Windows 7 A. Installing the User Digital Signing Certificate (DSC) 1. Once your receive the DSC, please acknowledge it by replying it to the same email address to get the
Manual for configuring VPN in Windows 7 A. Installing the User Digital Signing Certificate (DSC) 1. Once your receive the DSC, please acknowledge it by replying it to the same email address to get the
Securewireless Windows 7 Setup Guide
 Securewireless Windows 7 Setup Guide 1. Click on the wireless icon in the lower right-hand corner of the taskbar and then click on Open Network and Sharing Center. 2. From the Network and Sharing Center
Securewireless Windows 7 Setup Guide 1. Click on the wireless icon in the lower right-hand corner of the taskbar and then click on Open Network and Sharing Center. 2. From the Network and Sharing Center
Installing the WinSCP Secure FTP Client
 Draft 0.9 Page 1 of 6 Installing the WinSCP Secure FTP Client This document will instruct you to install the WinSCP application that will provide Secure FTP (SFTP) access to your website folder. So why
Draft 0.9 Page 1 of 6 Installing the WinSCP Secure FTP Client This document will instruct you to install the WinSCP application that will provide Secure FTP (SFTP) access to your website folder. So why
To Activate your Wireless Account
 To Activate your Wireless Account Access to the WVU Wireless network will require you to have an active WVU Active Directory account. Activation involves authenticating your account and setting a password.
To Activate your Wireless Account Access to the WVU Wireless network will require you to have an active WVU Active Directory account. Activation involves authenticating your account and setting a password.
FIPS Security Policy. for Marvell Semiconductor, Inc. Solaris 2 Cryptographic Module
 FIPS 140-2 Security Policy for Marvell Semiconductor, Inc. Solaris 2 Cryptographic Module Hardware Version: 88i8925, 88i8922, 88i8945, and 88i8946 Firmware Version: Solaris2-FIPS-FW-V1.0 Document Version:
FIPS 140-2 Security Policy for Marvell Semiconductor, Inc. Solaris 2 Cryptographic Module Hardware Version: 88i8925, 88i8922, 88i8945, and 88i8946 Firmware Version: Solaris2-FIPS-FW-V1.0 Document Version:
Connect to Wireless, certificate install and setup Citrix Receiver
 Connect to Wireless, certificate install and setup Citrix Receiver This document explains how to connect to the Wireless Network, certificate and access applications using Citrix Receiver on a Bring Your
Connect to Wireless, certificate install and setup Citrix Receiver This document explains how to connect to the Wireless Network, certificate and access applications using Citrix Receiver on a Bring Your
<Partner Name> <Partner Product> RSA SECURID ACCESS Authenticator Implementation Guide. Check Point SmartEndpoint Security
 RSA SECURID ACCESS Authenticator Implementation Guide Check Point SmartEndpoint Security Daniel R. Pintal, RSA Partner Engineering Last Modified: January 27, 2017 Solution
RSA SECURID ACCESS Authenticator Implementation Guide Check Point SmartEndpoint Security Daniel R. Pintal, RSA Partner Engineering Last Modified: January 27, 2017 Solution
SAFETICA INSTALLATION MANUAL
 SAFETICA INSTALLATION MANUAL SAFETICA INSTALLATION MANUAL for Safetica version 8.0.x Author: Safetica Technologies s.r.o. Safetica was developed by Safetica Technologies s.r.o. All rights reserved. No
SAFETICA INSTALLATION MANUAL SAFETICA INSTALLATION MANUAL for Safetica version 8.0.x Author: Safetica Technologies s.r.o. Safetica was developed by Safetica Technologies s.r.o. All rights reserved. No
Configuring 802.1X Settings on the WAP351
 Article ID: 5078 Configuring 802.1X Settings on the WAP351 Objective IEEE 802.1X authentication allows the WAP device to gain access to a secured wired network. You can configure the WAP device as an 802.1X
Article ID: 5078 Configuring 802.1X Settings on the WAP351 Objective IEEE 802.1X authentication allows the WAP device to gain access to a secured wired network. You can configure the WAP device as an 802.1X
Mac OS X version 10.6 and Below for Students
 Mac OS X version 10.6 and Below for Students The University Technology Services is privileged to offer a secure wifi network to the university community. Connecting to this network will provide you with
Mac OS X version 10.6 and Below for Students The University Technology Services is privileged to offer a secure wifi network to the university community. Connecting to this network will provide you with
Rev X 341. Table 111. Access Levels and Descriptions
 9424200994 Rev X 341 Multiple levels of security give personnel the level of access appropriate for the tasks they routinely perform while securing critical settings from unauthorized access. Access Levels
9424200994 Rev X 341 Multiple levels of security give personnel the level of access appropriate for the tasks they routinely perform while securing critical settings from unauthorized access. Access Levels
Remote Support Security Provider Integration: RADIUS Server
 Remote Support Security Provider Integration: RADIUS Server 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks
Remote Support Security Provider Integration: RADIUS Server 2003-2019 BeyondTrust Corporation. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust Corporation. Other trademarks
MyFloridaNet-2 (MFN-2) Customer Portal/ Password Management/ VPN Reference Guide
 MyFloridaNet-2 (MFN-2) Customer Portal/ Password Management/ VPN Reference Guide i VISION RECORDS REVISION DATE DESCRIPTION 0 27 September 2017 Initial Submittal. 1 Second Submittal. ii TABLE OF CONTENTS
MyFloridaNet-2 (MFN-2) Customer Portal/ Password Management/ VPN Reference Guide i VISION RECORDS REVISION DATE DESCRIPTION 0 27 September 2017 Initial Submittal. 1 Second Submittal. ii TABLE OF CONTENTS
SonicWall Global VPN Client Getting Started Guide
 SonicWall Global VPN Client 4.10 Getting Started Guide Copyright 2017 SonicWall Inc. All rights reserved. SonicWall is a trademark or registered trademark of SonicWall Inc. and/or its affiliates in the
SonicWall Global VPN Client 4.10 Getting Started Guide Copyright 2017 SonicWall Inc. All rights reserved. SonicWall is a trademark or registered trademark of SonicWall Inc. and/or its affiliates in the
SBCSC Staff BYOD (bring your own device) Instructions: 08/11/2016
 SBCSC Staff BYOD (bring your own device) Instructions: 08/11/2016 Teachers and staff, use these instructions to get a personal device of yours attached to the SBCSC BYOD wireless network. Once connected,
SBCSC Staff BYOD (bring your own device) Instructions: 08/11/2016 Teachers and staff, use these instructions to get a personal device of yours attached to the SBCSC BYOD wireless network. Once connected,
Configuring Funk Odyssey Software, Avaya AP-3 Access Point, and Avaya
 Configuring Funk Odyssey Software, Avaya AP-3 Access Point, and Avaya 802.11a/b Wireless Client for User Authentication (802.1x) and Data Encryption - Issue 1.0 Abstract These Application Notes describe
Configuring Funk Odyssey Software, Avaya AP-3 Access Point, and Avaya 802.11a/b Wireless Client for User Authentication (802.1x) and Data Encryption - Issue 1.0 Abstract These Application Notes describe
Managing Users and Configuring Role-Based Access Control
 Managing s and Configuring Role-Based Access Control This section describes how to manage users in Prime Central, including defining users and passwords and configuring role-based access control (RBAC).
Managing s and Configuring Role-Based Access Control This section describes how to manage users in Prime Central, including defining users and passwords and configuring role-based access control (RBAC).
Wireless for Windows 7
 Wireless for Windows 7 The new CWSL wireless network consists of three different wireless networks CWSL Faculty-Staff - This network is for faculty and staff only. (uses WPA2-Enterprise encryption) CWSL
Wireless for Windows 7 The new CWSL wireless network consists of three different wireless networks CWSL Faculty-Staff - This network is for faculty and staff only. (uses WPA2-Enterprise encryption) CWSL
Cryptzone AppGate. AX-V Virtual Appliance Getting Started Guide. Context Aware. Content Secure.
 AppGate AX-V Virtual Appliance Getting Started Guide Author: Malcolm Hamilton and Adam Rose Version: 2.3 Date: 12.8.2015 1 Table of Constance INTRODUCTION 3 PREREQUISITES 3 REQUIREMENTS 3 TECHNICAL SPECIFICATIONS
AppGate AX-V Virtual Appliance Getting Started Guide Author: Malcolm Hamilton and Adam Rose Version: 2.3 Date: 12.8.2015 1 Table of Constance INTRODUCTION 3 PREREQUISITES 3 REQUIREMENTS 3 TECHNICAL SPECIFICATIONS
TACACS Device Access Control with Cisco Active Network Abstraction
 TACACS Device Access Control with Cisco Active Network Abstraction Executive Summary Cisco Active Network Abstraction (ANA) is an extensible and scalable product suite that resides between the network
TACACS Device Access Control with Cisco Active Network Abstraction Executive Summary Cisco Active Network Abstraction (ANA) is an extensible and scalable product suite that resides between the network
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE. 31 January 2017
 BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
BitLocker Encryption for non-tpm laptops
 BitLocker Encryption for non-tpm laptops Contents 1.0 Introduction... 2 2.0 What is a TPM?... 2 3.0 Users of non-tpm University laptops... 2 3.1 Existing Windows 7 laptop users... 2 3.2 Existing Windows
BitLocker Encryption for non-tpm laptops Contents 1.0 Introduction... 2 2.0 What is a TPM?... 2 3.0 Users of non-tpm University laptops... 2 3.1 Existing Windows 7 laptop users... 2 3.2 Existing Windows
Atlantic Capital Exchange ACE Secure Browser Quick Start Guide
 Atlantic Capital Exchange ACE Secure Browser Quick Start Guide ACE Secure Browser is a user friendly, secure application that protects your company while accessing bank information and services. Early
Atlantic Capital Exchange ACE Secure Browser Quick Start Guide ACE Secure Browser is a user friendly, secure application that protects your company while accessing bank information and services. Early
The Reading Inventory Installation Guide
 The Reading Inventory Installation Guide For use with The Reading Inventory version 2.5 or later and Student Achievement Manager version 2.5 or later Table of Contents Introduction... 3 Getting Started...
The Reading Inventory Installation Guide For use with The Reading Inventory version 2.5 or later and Student Achievement Manager version 2.5 or later Table of Contents Introduction... 3 Getting Started...
Accessing Skyward Mobile Access App
 Accessing Skyward Mobile Access App Previous: Keyboard Shortcuts Parent: General Navigation Additional... The Skyward Mobile Access app is available for free download on Android and ios devices. Once you
Accessing Skyward Mobile Access App Previous: Keyboard Shortcuts Parent: General Navigation Additional... The Skyward Mobile Access app is available for free download on Android and ios devices. Once you
Installing and Connecting to the SOM VPN using the Cisco AnyConnect version 4.x Client (Windows)
 Installing and Connecting to the SOM VPN using the Cisco AnyConnect version 4.x Client (Windows) This document is for you if: - You connect to the SOM VPN via the Cisco AnyConnect Client - Your PC is running
Installing and Connecting to the SOM VPN using the Cisco AnyConnect version 4.x Client (Windows) This document is for you if: - You connect to the SOM VPN via the Cisco AnyConnect Client - Your PC is running
AAA and the Local Database
 This chapter describes authentication, authorization, and accounting (AAA, pronounced triple A ). AAA is a a set of services for controlling access to computer resources, enforcing policies, assessing
This chapter describes authentication, authorization, and accounting (AAA, pronounced triple A ). AAA is a a set of services for controlling access to computer resources, enforcing policies, assessing
NT 0018 Instructions for Setting Up UoE_Secure (XP)
 Academic Services Information & Computing Services Division Network Team NT 0018 Instructions for Setting Up UoE_Secure (XP) Document reference: Document type: Document status: Review period: NT0018 Network
Academic Services Information & Computing Services Division Network Team NT 0018 Instructions for Setting Up UoE_Secure (XP) Document reference: Document type: Document status: Review period: NT0018 Network
RSA Ready Implementation Guide for. Checkpoint Mobile VPN for ios v1.458
 RSA Ready Implementation Guide for v1.458 FAL, RSA Partner Engineering Last Modified: 7/22/16 Solution Summary The Check Point software solution is a comprehensive VPN
RSA Ready Implementation Guide for v1.458 FAL, RSA Partner Engineering Last Modified: 7/22/16 Solution Summary The Check Point software solution is a comprehensive VPN
Security Provider Integration RADIUS Server
 Security Provider Integration RADIUS Server 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property
Security Provider Integration RADIUS Server 2017 Bomgar Corporation. All rights reserved worldwide. BOMGAR and the BOMGAR logo are trademarks of Bomgar Corporation; other trademarks shown are the property
Web Intelligence Rich Client Getting Started Business Objects 4.1
 User Guide Web Intelligence Rich Client Getting Started Business Objects 4.1 Web Intelligence Rich Client Getting Started User Guide Contents Purpose of this Guide... 3 About Web Intelligence 4.1... 3
User Guide Web Intelligence Rich Client Getting Started Business Objects 4.1 Web Intelligence Rich Client Getting Started User Guide Contents Purpose of this Guide... 3 About Web Intelligence 4.1... 3
29 March 2017 SECURITY SERVER INSTALLATION GUIDE
 29 March 2017 SECURITY SERVER INSTALLATION GUIDE Contents 1. Introduction... 2 1.1 Assumptions... 2 1.2 Prerequisites... 2 2. Required setups prior the Security Server Installation... 3 1.1 Create domain
29 March 2017 SECURITY SERVER INSTALLATION GUIDE Contents 1. Introduction... 2 1.1 Assumptions... 2 1.2 Prerequisites... 2 2. Required setups prior the Security Server Installation... 3 1.1 Create domain
Contents. Windows 7 Instructions Windows 10 Instructions Android Instructions Mac OS Instructions ios Instructions...
 The following provides instructions on how to connect to the SJCD-Secure Wireless Network from a variety of operating systems and devices. If you experience any difficulty with these instructions, please
The following provides instructions on how to connect to the SJCD-Secure Wireless Network from a variety of operating systems and devices. If you experience any difficulty with these instructions, please
Reference Card: How to connect Windows 7 to UniWireless
 Reference Card: How to connect Windows 7 to UniWireless Important Information Windows 7 is not supported by ITS. These instructions provided are only a guide and do not provide any troubleshooting assistance.
Reference Card: How to connect Windows 7 to UniWireless Important Information Windows 7 is not supported by ITS. These instructions provided are only a guide and do not provide any troubleshooting assistance.
How to Configure Authentication and Access Control (AAA)
 How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
How to Configure Authentication and Access Control (AAA) Overview The Barracuda Web Application Firewall provides features to implement user authentication and access control. You can create a virtual
Best Practices Benchmarking Application
 1 1. Introduction For the purposes of this user manual, all menu items are visible in all screen shots. Depending upon the users privileges, the user s menu option may vary from what is shown in the screen
1 1. Introduction For the purposes of this user manual, all menu items are visible in all screen shots. Depending upon the users privileges, the user s menu option may vary from what is shown in the screen
VII. Corente Services SSL Client
 VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
VII. Corente Services SSL Client Corente Release 9.1 Manual 9.1.1 Copyright 2014, Oracle and/or its affiliates. All rights reserved. Table of Contents Preface... 5 I. Introduction... 6 Chapter 1. Requirements...
OT Message Center for Android Smartphone
 OT Message Center for Android Smartphone User Manual OpenTouch Message Center OpenTouch Business Edition OpenTouch Mutimedia Services R2.2 1646 1. INTRODUCTION 1-3 2. START THE APPLICATION 2-3 2.1 SIGN
OT Message Center for Android Smartphone User Manual OpenTouch Message Center OpenTouch Business Edition OpenTouch Mutimedia Services R2.2 1646 1. INTRODUCTION 1-3 2. START THE APPLICATION 2-3 2.1 SIGN
Configure Wireless for Windows 7
 Configure Wireless for Windows 7 There are two main procedures for configuring Windows 7 to access McGill's wireless network. You can also add the steps at the bottom if you don't want your username and
Configure Wireless for Windows 7 There are two main procedures for configuring Windows 7 to access McGill's wireless network. You can also add the steps at the bottom if you don't want your username and
msis Security Policy and Protocol
 msis Security Policy and Protocol Introduction This Policy details the secure use of msis as a tool for the capture and reporting of internet intelligence and investigations (i3). msis is a powerful i3
msis Security Policy and Protocol Introduction This Policy details the secure use of msis as a tool for the capture and reporting of internet intelligence and investigations (i3). msis is a powerful i3
Security Management System Central Monitoring Station with Push Mode Connectivity
 Security Management System Central Monitoring Station with Push Mode Connectivity Introduction Security Management System supports distributed deployment architecture, which involves (a) Central Monitoring
Security Management System Central Monitoring Station with Push Mode Connectivity Introduction Security Management System supports distributed deployment architecture, which involves (a) Central Monitoring
RSA Ready Implementation Guide for. GlobalSCAPE EFT Server 7.3
 RSA Ready Implementation Guide for GlobalSCAPE EFT Server 7.3 FAL, RSA Partner Engineering Last Modified: 5/19/2016 Solution Summary GlobalSCAPE Enhanced File Transfer (EFT) server can be configured to
RSA Ready Implementation Guide for GlobalSCAPE EFT Server 7.3 FAL, RSA Partner Engineering Last Modified: 5/19/2016 Solution Summary GlobalSCAPE Enhanced File Transfer (EFT) server can be configured to
Cisco s AnyConnect VPN Client (version 2.4)
 Table of Contents [TOC]: Introduction Getting Started Installation Overview Using the Softphone System Requirements Introduction: Valley City State University is deploying Cisco s AnyConnect Virtual Private
Table of Contents [TOC]: Introduction Getting Started Installation Overview Using the Softphone System Requirements Introduction: Valley City State University is deploying Cisco s AnyConnect Virtual Private
APSCN VPN Settings for Windows 7 2. APSCN VPN Settings for Windows XP 8. APSCN VPN Settings for MAC OS 15
 APSCN VPN Settings for Windows 7 2 1. Creating a VPN Connection 2 2. Disconnecting the VPN 6 3. Connecting to an existing VPN Connection 7 APSCN VPN Settings for Windows XP 8 1. Creating a VPN Connection
APSCN VPN Settings for Windows 7 2 1. Creating a VPN Connection 2 2. Disconnecting the VPN 6 3. Connecting to an existing VPN Connection 7 APSCN VPN Settings for Windows XP 8 1. Creating a VPN Connection
Log Server Configuration Utility
 Email Log Server Configuration Utility Email Log Server is the component that receives log records and processes them into the Log Database. During installation, you configure certain aspects of Log Server
Email Log Server Configuration Utility Email Log Server is the component that receives log records and processes them into the Log Database. During installation, you configure certain aspects of Log Server
Installing and Activating a Multi-User Network License for Statgraphics 18
 Installing and Activating a Multi-User Network License for Statgraphics 18 Step 1: Download and Install Statgraphics 18... 2 Step 2: Create a Statgraphics Registration Account... 2 Step 3: Register the
Installing and Activating a Multi-User Network License for Statgraphics 18 Step 1: Download and Install Statgraphics 18... 2 Step 2: Create a Statgraphics Registration Account... 2 Step 3: Register the
AppGate for AWS Step-by-Step Setup Guide. Last revised April 28, 2017
 AppGate for AWS Step-by-Step Setup Guide Last revised April 28, 2017 Contents Welcome & Overview... 2 Getting Started... 3 Pre-Requisites... 4 But what about Security Groups?... 5 Browser Compatibility:...
AppGate for AWS Step-by-Step Setup Guide Last revised April 28, 2017 Contents Welcome & Overview... 2 Getting Started... 3 Pre-Requisites... 4 But what about Security Groups?... 5 Browser Compatibility:...
Aventail Connect Client with Smart Tunneling
 Aventail Connect Client with Smart Tunneling User s Guide Windows v8.9.0 1996-2007 Aventail Corporation. All rights reserved. Aventail, Aventail Cache Control, Aventail Connect, Aventail Connect Mobile,
Aventail Connect Client with Smart Tunneling User s Guide Windows v8.9.0 1996-2007 Aventail Corporation. All rights reserved. Aventail, Aventail Cache Control, Aventail Connect, Aventail Connect Mobile,
Integrating IBM Security Privileged Identity Manager with ObserveIT Enterprise Session Recording
 Integrating IBM Security Privileged Identity Manager with ObserveIT Enterprise Session Recording Contents 1 About This Document... 2 2 Overview... 2 3 Before You Begin... 2 4 Deploying ObserveIT with IBM
Integrating IBM Security Privileged Identity Manager with ObserveIT Enterprise Session Recording Contents 1 About This Document... 2 2 Overview... 2 3 Before You Begin... 2 4 Deploying ObserveIT with IBM
learnpro Community User Manual
 learnpro Community User Manual Last Updated: December 2011 learnpro User Manual Page 1 Contents Contents... 2 1. Introduction... 3 1.1 Introduction to the system... 3 1.2 Help Icons... 3 1.3 Accessing
learnpro Community User Manual Last Updated: December 2011 learnpro User Manual Page 1 Contents Contents... 2 1. Introduction... 3 1.1 Introduction to the system... 3 1.2 Help Icons... 3 1.3 Accessing
Configuring WPA2 for Windows XP
 Configuring WPA2 for Windows XP Requirements for wireless using WPA2 on Windows XP Your wireless card must support 802.1x, AES, and WPA2. Your computer must have Windows XP service pack 2 installed and
Configuring WPA2 for Windows XP Requirements for wireless using WPA2 on Windows XP Your wireless card must support 802.1x, AES, and WPA2. Your computer must have Windows XP service pack 2 installed and
Develop Content SoftChalk Create
 \ Develop Content is a content authoring program that is easy to use (like a word processer) but allows you to make your lessons interactive for your students. You can put various activities and quiz groups
\ Develop Content is a content authoring program that is easy to use (like a word processer) but allows you to make your lessons interactive for your students. You can put various activities and quiz groups
User Manual. User Manual. Last Updated: August learnpro User Manual Page 1
 learnpro NHS User Manual Last Updated: August 2011 learnpro User Manual Page 1 Contents 1. Introduction... 3 1.1 Introduction to the system... 3 1.2 Help Icons... 3 1.3 Accessing learnpro NHS... 3 1.4
learnpro NHS User Manual Last Updated: August 2011 learnpro User Manual Page 1 Contents 1. Introduction... 3 1.1 Introduction to the system... 3 1.2 Help Icons... 3 1.3 Accessing learnpro NHS... 3 1.4
ConnectUPS-X / -BD /-E How to use and install SSL, SSH
 ConnectUPS-X /-BD /-E product family Root CA Certificate installation Rev. B Page 1/16 Index 1. How to use and install SSL (Secure Socket Layer)...3 1.1. General Certificate warning message if not installed...3
ConnectUPS-X /-BD /-E product family Root CA Certificate installation Rev. B Page 1/16 Index 1. How to use and install SSL (Secure Socket Layer)...3 1.1. General Certificate warning message if not installed...3
How to connect your device using eduroam
 How to connect your device using eduroam Banaras Hindu University is now fully covered under eduroam, a service with more than 70,000 member academic institutions worldwide. This service allows authorized
How to connect your device using eduroam Banaras Hindu University is now fully covered under eduroam, a service with more than 70,000 member academic institutions worldwide. This service allows authorized
Horizon Cloud with On-Premises Infrastructure Administration Guide. VMware Horizon Cloud Service Horizon Cloud with On-Premises Infrastructure 1.
 Horizon Cloud with On-Premises Infrastructure Administration Guide VMware Horizon Cloud Service Horizon Cloud with On-Premises Infrastructure 1.3 Horizon Cloud with On-Premises Infrastructure Administration
Horizon Cloud with On-Premises Infrastructure Administration Guide VMware Horizon Cloud Service Horizon Cloud with On-Premises Infrastructure 1.3 Horizon Cloud with On-Premises Infrastructure Administration
Hearing Care Dashboard
 Hearing Care Dashboard Registration & Management Hearing Care Dashboard: Register and Manage Your Organization Hearing Care Anywhere is Starkey s remote programming system. The Hearing Care Dashboard is
Hearing Care Dashboard Registration & Management Hearing Care Dashboard: Register and Manage Your Organization Hearing Care Anywhere is Starkey s remote programming system. The Hearing Care Dashboard is
Windows User Manual 1
 Windows User Manual 1 Creating and Installing a Dropbox Account... 3 How to Create a Dropbox Account... 3 How to Install Dropbox... 3 How to Register and Sign into Dropbox... 3 Install and Register for
Windows User Manual 1 Creating and Installing a Dropbox Account... 3 How to Create a Dropbox Account... 3 How to Install Dropbox... 3 How to Register and Sign into Dropbox... 3 Install and Register for
Configuring Role-Based Access Control
 Configuring Role-Based Access Control This chapter includes the following sections: Role-Based Access Control, page 1 User Accounts for Cisco UCS Manager, page 1 User Roles, page 4 User Locales, page 7
Configuring Role-Based Access Control This chapter includes the following sections: Role-Based Access Control, page 1 User Accounts for Cisco UCS Manager, page 1 User Roles, page 4 User Locales, page 7
Configuring and Using your Nationwide Extranet Virtual Machine
 Configuring and Using your Nationwide Extranet Virtual Machine V8.16.17 OVERVIEW To access your Nationwide email, you must configure your PC. This is required whenever you are accessing from a new machine
Configuring and Using your Nationwide Extranet Virtual Machine V8.16.17 OVERVIEW To access your Nationwide email, you must configure your PC. This is required whenever you are accessing from a new machine
Using TU Eindhoven s VPN with Ubuntu
 Using TU Eindhoven's VPN with Ubuntu 14.04 or 16.04 TU Eindhoven s Virtual Private Networking (VPN) service can be used on Linux computers. This document describes how to do it using Ubuntu 14.04 or 16.04
Using TU Eindhoven's VPN with Ubuntu 14.04 or 16.04 TU Eindhoven s Virtual Private Networking (VPN) service can be used on Linux computers. This document describes how to do it using Ubuntu 14.04 or 16.04
Aruba VIA Windows Edition
 Aruba VIA 3.0.0 Windows Edition a Hewlett Packard Enterprise company User Guide Copyright Information Copyright 2017 Hewlett Packard Enterprise Development LP. Open Source Code This product includes code
Aruba VIA 3.0.0 Windows Edition a Hewlett Packard Enterprise company User Guide Copyright Information Copyright 2017 Hewlett Packard Enterprise Development LP. Open Source Code This product includes code
User Guide. Version R92. English
 AuthAnvil User Guide Version R92 English October 9, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated from
AuthAnvil User Guide Version R92 English October 9, 2015 Agreement The purchase and use of all Software and Services is subject to the Agreement as defined in Kaseya s Click-Accept EULATOS as updated from
ClientNet. Portal Admin Guide
 ClientNet Portal Admin Guide Document Revision Date: June 5, 2013 ClientNet Portal Admin Guide i Contents Introduction to the Portal... 1 About the Portal... 1 Logging On and Off the Portal... 1 Language
ClientNet Portal Admin Guide Document Revision Date: June 5, 2013 ClientNet Portal Admin Guide i Contents Introduction to the Portal... 1 About the Portal... 1 Logging On and Off the Portal... 1 Language
External Authentication with Checkpoint R77.20 Authenticating Users Using SecurAccess Server by SecurEnvoy
 External Authentication with Checkpoint R77.20 Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 Merlin House Brunel Road Theale
External Authentication with Checkpoint R77.20 Authenticating Users Using SecurAccess Server by SecurEnvoy Contact information SecurEnvoy www.securenvoy.com 0845 2600010 Merlin House Brunel Road Theale
WDC RDS Connection for Android Users
 WDC RDS Connection for Android Users Introduction The WDC Remote Desktop Service (RDS) can be connected to most personal computer devices, including Android Smartphones and tablets, even though the RD
WDC RDS Connection for Android Users Introduction The WDC Remote Desktop Service (RDS) can be connected to most personal computer devices, including Android Smartphones and tablets, even though the RD
Advantage Cloud Two-Factor Security Process
 Advantage Cloud Two-Factor Security Process Advantage Cloud Two-Factor Security Process Table of Contents: 1. Why use Two-Factor Authentication? 2. Two-Factor Authentication Guide for Faculty Members 3.
Advantage Cloud Two-Factor Security Process Advantage Cloud Two-Factor Security Process Table of Contents: 1. Why use Two-Factor Authentication? 2. Two-Factor Authentication Guide for Faculty Members 3.
<Partner Name> <Partner Product> RSA SECURID ACCESS Authenticator Implementation Guide. Intel Security Drive Encryption 7.1.3
 RSA SECURID ACCESS Authenticator Implementation Guide Intel Security Daniel R. Pintal, RSA Partner Engineering Last Modified: December 12, 2016 Solution Summary Intel Security/McAfee
RSA SECURID ACCESS Authenticator Implementation Guide Intel Security Daniel R. Pintal, RSA Partner Engineering Last Modified: December 12, 2016 Solution Summary Intel Security/McAfee
User Account Manager
 CHAPTER 4 Note User accounts can be accessed only when operating in Internal Directory mode. To access User tasks, log in to the system (see Logging In section on page 2-1). Then, from the Home page, click
CHAPTER 4 Note User accounts can be accessed only when operating in Internal Directory mode. To access User tasks, log in to the system (see Logging In section on page 2-1). Then, from the Home page, click
Lab - Remote Desktop in Windows 8
 Lab - Remote Desktop in Windows 8 Introduction In this lab, you will remotely connect to another Windows 8 computer. Recommended Equipment The following equipment is required for this exercise: Two Windows
Lab - Remote Desktop in Windows 8 Introduction In this lab, you will remotely connect to another Windows 8 computer. Recommended Equipment The following equipment is required for this exercise: Two Windows
REMOTE ACCESS TO HUSKY S COMPUTER NETWORKS TWO WAYS TO CONNECT IN EUROPE
 REMOTE ACCESS TO HUSKY S COMPUTER NETWORKS TWO WAYS TO CONNECT IN EUROPE If you have access to the Internet (via net cable, wireless or phone line, hotel, airport, IPass), you need to change your proxy
REMOTE ACCESS TO HUSKY S COMPUTER NETWORKS TWO WAYS TO CONNECT IN EUROPE If you have access to the Internet (via net cable, wireless or phone line, hotel, airport, IPass), you need to change your proxy
Copyright
 This video looks at Claim Based/Identity Based systems using Active Directory Federation Services as an example. An example of a claim based system is where the user logs into a system like a web page
This video looks at Claim Based/Identity Based systems using Active Directory Federation Services as an example. An example of a claim based system is where the user logs into a system like a web page
Password Policy Best Practices
 Password Policy Best Practices 1.0 Overview Passwords are an important aspect of information security, and are the front line of protection for user accounts. A poorly chosen password may result in the
Password Policy Best Practices 1.0 Overview Passwords are an important aspect of information security, and are the front line of protection for user accounts. A poorly chosen password may result in the
TippingPoint Best Practice Guide. RADIUS PEAP Configuration for IPS Devices and Cisco ACS. Version:
 TippingPoint Best Practice Guide RADIUS PEAP Configuration for IPS Devices and Cisco ACS Version: 16.1.1 Copyright Statement Copyright 2016 Trend Micro. Trend Micro Incorporated ( Trend Micro ) makes no
TippingPoint Best Practice Guide RADIUS PEAP Configuration for IPS Devices and Cisco ACS Version: 16.1.1 Copyright Statement Copyright 2016 Trend Micro. Trend Micro Incorporated ( Trend Micro ) makes no
Unipass Secur Client User Guide v1.5
 Unipass Securemail Client User Guide v1.5 This document provides a step by step illustrated user guide for the Unipass Securemail desktop software client / plug-in. UIdP Project Team May 2018 Contents
Unipass Securemail Client User Guide v1.5 This document provides a step by step illustrated user guide for the Unipass Securemail desktop software client / plug-in. UIdP Project Team May 2018 Contents
FH Remote Access Last Updated: July 3, 2013
 FH Remote Access Last Updated: July 3, 2013 1. Remote Access at Fraser Health... 1 2. Cisco VPN Client Software on an FH Laptop... 1 3. Cisco VPN Client Software on a Non-FH Computer/Laptop... 1 1. Download
FH Remote Access Last Updated: July 3, 2013 1. Remote Access at Fraser Health... 1 2. Cisco VPN Client Software on an FH Laptop... 1 3. Cisco VPN Client Software on a Non-FH Computer/Laptop... 1 1. Download
PaperCut Student Guide
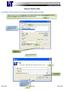 PaperCut Student Guide 1.0 Sending a Print Job directly from student workstations (Direct Printing) Students or Guest Users click the Printer icon on the standard toolbar or select the Print Command from
PaperCut Student Guide 1.0 Sending a Print Job directly from student workstations (Direct Printing) Students or Guest Users click the Printer icon on the standard toolbar or select the Print Command from
Excel-SMS Enotified. Excel-SMS Help Manual
 Enotified Help Manual 7/7/2012 Contents 1. What is the excel-sms User Guide?... 2 2. Getting Started with excel-sms... 2 3. About the excel-sms Interface... 3 4. How to Send an SMS... 4 4.1 Sending One
Enotified Help Manual 7/7/2012 Contents 1. What is the excel-sms User Guide?... 2 2. Getting Started with excel-sms... 2 3. About the excel-sms Interface... 3 4. How to Send an SMS... 4 4.1 Sending One
Lab - Remote Desktop in Windows 7 and Vista
 Lab - Remote Desktop in Windows 7 and Vista Introduction In this lab, you will remotely connect to another Windows 7 or Vista computer. Recommended Equipment The following equipment is required for this
Lab - Remote Desktop in Windows 7 and Vista Introduction In this lab, you will remotely connect to another Windows 7 or Vista computer. Recommended Equipment The following equipment is required for this
Table of Contents. Table of Figures. 2 Wave Systems Corp. Client User Guide
 2 Wave Systems Corp. Client User Guide Table of Contents Overview... 3 What is the Trusted Drive Manager?... 3 Key Features of Trusted Drive Manager... 3 Getting Started... 4 Required Components... 4 Configure
2 Wave Systems Corp. Client User Guide Table of Contents Overview... 3 What is the Trusted Drive Manager?... 3 Key Features of Trusted Drive Manager... 3 Getting Started... 4 Required Components... 4 Configure
Intel Security/McAfee Endpoint Encryption
 RSA Ready Implementation Guide for RSA SecurID Last Modified: March 13, 2015 Partner Information Product Information Partner Name Intel Security formerly McAfee Web Site www.mcafee.com Product Name for
RSA Ready Implementation Guide for RSA SecurID Last Modified: March 13, 2015 Partner Information Product Information Partner Name Intel Security formerly McAfee Web Site www.mcafee.com Product Name for
PS Suite EMR ASP Remote Access Setup Guide for Macintosh computers
 PS Suite EMR ASP Remote Access Setup Guide for Macintosh computers MDQS-6-3639 Rev 4.0 Revised June 13, 2017. PS Suite EMR software and related products and services are owned by TELUS. PS Suite EMR and
PS Suite EMR ASP Remote Access Setup Guide for Macintosh computers MDQS-6-3639 Rev 4.0 Revised June 13, 2017. PS Suite EMR software and related products and services are owned by TELUS. PS Suite EMR and
Hosted Microsoft Exchange Client Setup & Guide Book
 Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows 10 Mail App setup & configuration Section 3 Windows Mobile Phone ActiveSync
Hosted Microsoft Exchange Client Setup & Guide Book Section 1 Microsoft Outlook Web Access (OWA) access directions Section 2 Windows 10 Mail App setup & configuration Section 3 Windows Mobile Phone ActiveSync
Remote Access Installation
 Remote Access Installation Getting Started with Remote Access If you re on a desktop or laptop, open your browser and go to http://remote.palmettohealth.org. You may want to create an internet shortcut
Remote Access Installation Getting Started with Remote Access If you re on a desktop or laptop, open your browser and go to http://remote.palmettohealth.org. You may want to create an internet shortcut
OPC-UA Tutorial. A Guide to Configuring the TOP Server for OPC-UA
 OPC-UA Tutorial A Guide to Configuring the TOP Server for OPC-UA Page 2 of 40 Table of Contents INTRODUCTION 4 Introduction to OPC UA 4 Introduction to TOP Server 5 Intended Audience 5 Prerequisites 6
OPC-UA Tutorial A Guide to Configuring the TOP Server for OPC-UA Page 2 of 40 Table of Contents INTRODUCTION 4 Introduction to OPC UA 4 Introduction to TOP Server 5 Intended Audience 5 Prerequisites 6
Using the Subscriber Manager GUI Tool
 CHAPTER 11 Using the Subscriber Manager GUI Tool Published: December 23, 2013, Introduction This chapter describes how to use the Subscriber Manager (SM) graphical user interface (GUI) tool to configure
CHAPTER 11 Using the Subscriber Manager GUI Tool Published: December 23, 2013, Introduction This chapter describes how to use the Subscriber Manager (SM) graphical user interface (GUI) tool to configure
NTP Software File Reporter Analysis Server
 NTP Software File Reporter Analysis Server Installation Guide Version 8.2 This guide provides quick instructions for installing NTP Software File Reporter Analysis Server from an administrator s perspective.
NTP Software File Reporter Analysis Server Installation Guide Version 8.2 This guide provides quick instructions for installing NTP Software File Reporter Analysis Server from an administrator s perspective.
Configuring Microsoft Outlook to Connect to Hosted Exchange Service
 Configuring Microsoft Outlook to Connect to Hosted Exchange Service Configuring Microsoft Outlook for Hosted Exchange Service Version: 1.0 Updated on: April 27, 2011 Page 1 of 7 TABLE OF CONTENTS Configuring
Configuring Microsoft Outlook to Connect to Hosted Exchange Service Configuring Microsoft Outlook for Hosted Exchange Service Version: 1.0 Updated on: April 27, 2011 Page 1 of 7 TABLE OF CONTENTS Configuring
Multi-factor Authentication Instructions
 What is MFA? (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account. MFA authentication is typically
What is MFA? (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account. MFA authentication is typically
Cloud Access Manager Overview
 Cloud Access Manager 8.1.3 Overview Copyright 2017 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished
Cloud Access Manager 8.1.3 Overview Copyright 2017 One Identity LLC. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide is furnished
CITRIX REMOTE PC SKADDEN REMOTE ACCESS PAGE CONNECT TO SKADDEN SYSTEMS REMOTELY DOWNLOAD & INSTALL CITRIX LOG ON TO REMOTE DESKTOP
 CITRIX REMOTE PC SKADDEN REMOTE ACCESS PAGE Skadden Remote URL: http://skadlink.skadden.com Citrix Remote Desktop: Allows access to the Skadden network as if you were in the office. Outlook WebMail: Allows
CITRIX REMOTE PC SKADDEN REMOTE ACCESS PAGE Skadden Remote URL: http://skadlink.skadden.com Citrix Remote Desktop: Allows access to the Skadden network as if you were in the office. Outlook WebMail: Allows
Vemotion Streaming Server (VSS) Support Guide
 Vemotion Streaming Server (VSS) Support Guide 1 Table of Contents Change History... 4 Foreward... 4 How does Vemotion work?... 5 Vemotion Software... 5 Vemotion Video Server (VVS)... 5 Vemotion Encoder
Vemotion Streaming Server (VSS) Support Guide 1 Table of Contents Change History... 4 Foreward... 4 How does Vemotion work?... 5 Vemotion Software... 5 Vemotion Video Server (VVS)... 5 Vemotion Encoder
Ekran System v.6.0 Privileged User Accounts and Sessions (PASM)
 Ekran System v.6.0 Privileged User Accounts and Sessions (PASM) Table of Contents About... 3 Using Privileged User Accounts... 4 Password Vault Configuration... 5 Defining Domain Administrator Credentials...
Ekran System v.6.0 Privileged User Accounts and Sessions (PASM) Table of Contents About... 3 Using Privileged User Accounts... 4 Password Vault Configuration... 5 Defining Domain Administrator Credentials...
Comodo Endpoint Security Manager Professional Edition Software Version 3.3
 Comodo Endpoint Security Manager Professional Edition Software Version 3.3 Quick Start Guide Guide Version 3.2.022615 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo Endpoint Security
Comodo Endpoint Security Manager Professional Edition Software Version 3.3 Quick Start Guide Guide Version 3.2.022615 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Comodo Endpoint Security
Managing User Accounts
 Contents User Accounts 2 Passwords 3 Home Folders 4 The Anonymous User 5 User Accounts And The Web File Manager 5 Maxum Development Corp. ! Managing User Accounts The basic operation of a file transfer
Contents User Accounts 2 Passwords 3 Home Folders 4 The Anonymous User 5 User Accounts And The Web File Manager 5 Maxum Development Corp. ! Managing User Accounts The basic operation of a file transfer
PaperCut Student Guide
 5/2/2011 Technology Services PaperCut Student Guide Administrative Office Isaac Barbosa [Type text] [Type text] [Type text] Table of Contents: 1.0 Sending a Print Job directly from student workstations
5/2/2011 Technology Services PaperCut Student Guide Administrative Office Isaac Barbosa [Type text] [Type text] [Type text] Table of Contents: 1.0 Sending a Print Job directly from student workstations
