Refining SIRAP with a Dedicated Resource Ceiling for Self-Blocking
|
|
|
- Karin Hoover
- 6 years ago
- Views:
Transcription
1 Refining SIRAP with a Dedicated Reource Ceiling for Self-Blocking Mori Behnam, Thoma Nolte Mälardalen Real-Time Reearch Centre P.O. Box 883, SE Väterå, Sweden {mori.behnam,thoma.nolte}@mdh.e ABSTRACT In recent year, everal ynchronization protocol for reource haring have been preented for ue in a Hierarchical Scheduling Framework (HSF). An initial comparative aement of exiting protocol revealed that none of the protocol i uperior to the other and that the performance of a protocol heavily depend on ytem parameter. In thi paper, we aim at efficiency improvement of the ynchronization protocol SIRAP [?] and it aociated chedulability analyi, where efficiency refer to calculated CPU reource need. The contribution of the paper i threefold. Firtly, we preent an improvement of the chedulability analyi for SIRAP, which make SIRAP more efficient. Secondly, we generalize SIRAP by ditinguihing eparate reource ceiling for elf-blocking and reource acce. Uing a eparate reource ceiling for elf-blocking enable a reduction of the interference from lower priority tak, which can reult in efficiency improvement. The efficiency improvement depend on both ubytem characteritic and the value elected for the reource ceiling for elf-blocking, however. The third contribution of thi paper i therefore an algorithm that given a ubytem elect for each globally hared reource an optimal value in term of efficiency for it reource ceiling for elf-blocking. The efficiency improvement gained by the algorithm compared to the original SIRAP approach i evaluated by mean of imulation. Categorie and Subject Decriptor D.4.1 [OPERATING SYSTEMS]: Proce Management Scheduling; Synchronization; D.4.7 [OPERATING SYS- TEMS]: Organization and Deign Real-time ytem and embedded ytem. General Term Algorithm, Deign. The work in thi paper i upported by the Swedih Foundation for Strategic Reearch (SSF), via the reearch programme PROGRESS. EMSOFT 09, October 12 16, 2009, Grenoble, France. Reinder J. Bril Techniche Univeriteit Eindhoven (TU/e) Den Dolech 2, 5612 AZ Eindhoven, The Netherland r.j.bril@tue.nl Keyword Hierarchical cheduling, Real-time open ytem, Real-time ubytem integration, Reource-haring, SIRAP, Synchronization protocol. 1. INTRODUCTION The Hierarchical Scheduling Framework (HSF) ha been introduced to upport hierarchical CPU haring among application under different cheduling ervice [?]. The HSF can be repreented a a tree of node, where each node repreent an application with it own cheduler for cheduling internal workload (e.g., tak), and reource are allocated from a parent node to it children node. The HSF provide mean for decompoing a complex ytem into well-defined part called ubytem. In eence, the HSF provide a mechanim for timing-predictable compoition of coure-grained ubytem. In the HSF a ubytem provide an intropective interface that pecifie the timing propertie of the ubytem preciely [?]. Thi mean that ubytem can be independently developed and teted, and later aembled without introducing unwanted temporal interference. Temporal iolation between ubytem i provided through budget which are allocated to ubytem. Motivation: Reearch on HSF tarted with the aumption that ubytem are independent, i.e., inter-ubytem reource haring other than the CPU fell outide their cope. In ome cae [?,?], intra-ubytem reource haring i addreed uing exiting ynchronization protocol for reource haring between tak, e.g., the Stack Reource Policy (SRP) [?]. Recently, three SRP-baed ynchronization protocol for inter-ubytem reource haring have been preented, i.e., HSRP [?], BROE [?], and SIRAP [?]. Although all three protocol are SRP-baed, they rely on different mechanim to deal with inter-ubytem reource haring and depletion of budget. In particular, HSRP i baed on a o-called overrun mechanim, wherea both BROE and SIRAP are baed on a o-called kipping approach. Moreover, their contituting framework are baed on different aumption. A an example, cheduling (of ubytem a well a of tak) in the framework of HSRP and SIRAP i baed on FPPS, wherea it i baed on EDF for BROE. Finally, unlike BROE and SIRAP, HSRP doe not upport local chedulability analyi, and the local chedulability analyi in BROE a decribed in [?] i incomplete. An initial comparative aement of thee three ynchronization protocol [?] revealed that none of them wa uperior to the
2 other and that the performance of a protocol heavily depend on the ytem parameter. A comparative evaluation of the mechanim overrun and kipping uing a ingle framework can be found in [?]. In thi paper, we focu on SIRAP and aim at improving the efficiency of the protocol and it aociated chedulability analyi, where efficiency refer to calculated CPU reource need of a ubytem. SIRAP i baed on a kipping mechanim to prevent depletion of a ubytem budget during global hared reource acce. That i, whenever a tak trie to lock a global hared reource and the remaining budget i inufficient to complete the acce, the tak experience elf-blocking during the remainder of the current budget period and i guaranteed to acce the reource during the next budget period. The contribution of thi paper i threefold. Firtly, we remove ome peimim from SIRAP by improving it aociated chedulability analyi. Secondly, we generalize SIRAP by ditinguihing eparate reource ceiling for elfblocking and reource acce. Uing a dedicated reource ceiling for elf-blocking enable a reduction of the interference from lower priority tak which may reduce the calculated reource need of the ubytem whilt guaranteeing the chedulability of all it internal tak. Thirdly, we propoe an algorithm to elect the optimal value per global hared reource for thi novel reource ceiling for a ubytem with given characteritic, reulting in the lowet calculated reource need for that ubytem. The efficiency of the algorithm i evaluated by comparing it calculated reource need with thoe of the original SIRAP protocol in a imulation. 2. RELATED WORK Over the year, there ha been a growing attention to hierarchical cheduling of real-time ytem [?,?,?,?,?,?,?,?,?,?]. Deng and Liu [?] propoed a two-level HSF for open ytem, where ubytem may be developed and validated independently. Kuo and Li [?] preented chedulability analyi technique for uch a two-level framework with the Fixed-Priority Scheduling (FPS) global cheduler. Lipari and Baruah [?,?] preented chedulability analyi technique for Earliet Deadline Firt (EDF) global cheduler. Mok et al. [?,?] propoed the bounded-delay virtual proceor model to achieve a clean eparation in a multi-level HSF. In addition, Shin and Lee [?] introduced the periodic virtual proceor model (to characterize the periodic CPU allocation behaviour), and many tudie have been propoed on chedulability analyi with thi model under FPS [?,?,?] and under EDF cheduling [?,?]. However, a common aumption hared by all above tudie i that tak are independent. Recently, three SRP-baed ynchronization protocol for interubytem reource haring have been preented, i.e., HSRP [?], BROE [?], and SIRAP [?]. A comparative aement of thee three ynchronization protocol [?] revealed that none of them wa uperior to the other and that the performance of a protocol heavily depend on ytem parameter. 3. SYSTEM MODEL AND BACKGROUND Thi paper focue on cheduling of a ingle node or a ingle network link, where each node (or link) i modeled a a ytem S coniting of one or more ubytem S S. The ytem i cheduled by a two-level HSF a hown in Figure??. During runtime, the ytem level cheduler (global cheduler) elect, at all time, which ubytem will acce the common (hared) CPU reource. Sytem Subytem 1 Subytem 2 Subytem n Local Shared Reource SRP Tak Set Local FPS Scheduler Global Shared Reource SIRAP Local Shared Reource SRP Tak Set Local FPS Scheduler Global FPS Scheduler CPU Local Shared Reource SRP Tak Set Local FPS Scheduler Figure 1: HSF with reource haring. Subytem model. A ubytem S conit of a et T of n tak and a local cheduler. Once a ubytem i aigned the proceor (CPU), it cheduler will elect which of it tak will be executed. With each ubytem S, a ubytem timing interface S (P, Q, X ) i aociated, where Q i the ubytem budget that the ubytem S will receive every ubytem period P, and X i the maximum time that a ubytem internal tak may lock a hared reource. Finally, both the local cheduler of a ubytem S a well a the global cheduler of the ytem S i aumed to implement the fixed priority preemptive cheduling policy. Let R be the et of m global hared reource acceed by S. Tak model. The tak model conidered in thi paper i the deadline-contrained poradic hard real-time tak model τ i(t i, C i, D i, {c i,j}), where T i i a minimum eparation time between arrival of ucceive job of τ i, C i i their wortcae execution-time, and D i i an arrival-relative deadline (0 < C i D i T i) before which the execution of a job mut be completed. Each tak i allowed to acce one or more hared logical reource, and each element c i,j {c i,j} i a critical ection execution time that repreent a wortcae execution-time requirement within a critical ection of a global hared reource R j. It i aumed that all tak belonging to the ame ubytem are aigned unique tatic prioritie and are orted according to their prioritie in the order of increaing priority. Without lo of generality, it i aumed that the priority of a tak i equal to the tak ID number after orting, and the greater a tak ID number i, the higher it priority i. The ame aumption i made for
3 Notation S S T n P Q X R R j m τ i T i C i D i c i,j Decription Sytem Subytem Sporadic tak et Number of local tak. Subytem period Subytem budget Maximum time that S lock a global hared reource. Set of global hared reource acceed by S Global hared reource Cardinality of R Sporadic tak Period of τ i Wort cae execution time of τ i Relative deadline of τ i Critical ection execution time of τ i acceing R j {c i,j} Set of critical ection execution time of τ i acceing R j {R i } Set of hared reource acceed by τ i hp(i) lp(i) rc j RX j SC c rc LWB j RX LWB j bf (t) rbf FP (i, t) I S(i) I H(i, t) I L(i) rc j Set of local tak with prioritie higher than that of τ i Set of local tak with prioritie lower than that of τ i Internal reource ceiling of R j External reource ceiling Sytem ceiling Subytem ceiling Lower bound for rc j Lower bound for RX j Supply bound function Requet bound function of τ i Self blocking of τ i Interference from tak with priority higher than that of τ i Interference from tak, with priority lower than that of τ i Self blocking ceiling of R j Table 1: Summary of notation. the ubytem. The et of hared reource acceed by τ i i denoted {R i }. Let hp(i) return the et of local tak that belong to a ubytem with prioritie higher than that of τ i and lp(i) return the et of local tak with prioritie lower than that of tak τ i. Table?? how the ummary of the notation ued in thi paper. For each ubytem, we aume that the ubytem period i elected uch that 2P T min, where τ min i the tak with the hortet period. The motivation for thi aumption i that higher P will require more CPU reource [?]. In addition, thi aumption implifie the preentation of the paper (evaluating X ). Shared reource. The preented HSF allow for haring of logical reource between arbitrary tak, located in arbitrary ubytem, in a mutually excluive manner. To acce a reource R j, a tak mut firt lock the reource, and when the tak no longer need the reource it i unlocked. The time during which a tak hold a lock i called a critical ection. A reource that i ued by tak in more than one ubytem i denoted a global hared reource. The work in thi paper target managing global hared reource, and throughout the remainder of the paper thee are imply denoted a hared reource. To be able to ue SRP in a HSF for ynchronizing global hared reource, it aociated term reource, ytem and ubytem ceiling are extended a follow: Reource ceiling: Each global hared reource R j i aociated with two type of reource ceiling; an internal reource ceiling (rc j) for local cheduling and an external reource ceiling (RX j) for global cheduling. Lower bound for rc j and RX j are defined a rc LWB j = max{i τ i T accee R j} and RXj LWB = max{ S accee R j}, repectively. Sytem/ubytem ceiling: The ytem/ubytem ceiling (SC/c ) are dynamic parameter that change during execution. The ytem/ubytem ceiling i equal to the highet external/internal reource ceiling of a currently locked reource in the ytem/ubytem. Under SRP, a tak τ k can preempt the currently executing tak τ i (even inide a critical ection) within the ame ubytem, only if the priority of τ k i greater than it correponding ubytem ceiling. The ame reaoning applie for ubytem from a global cheduling point of view. An attractive property of SRP i that it allow tak within a ubytem to hare a common tack. 4. SIRAP The SIRAP [?] protocol can be ued for independent development of ubytem and it upport ubytem integration in the preence of globally hared logical reource. It ue a periodic reource model [?] to abtract the timing requirement of each ubytem. SIRAP ue the SRP protocol to ynchronize acce to global hared reource in both local and global cheduling. SIRAP applie a kipping approach to prevent the budget expiration inide critical ection problem. The mechanim work a follow; when a job want to enter a critical ection, it enter the critical ection at the earliet intant uch that it can complete the critical ection execution before the ubytem budget expire. Thi can be achieved by checking the remaining budget before granting the acce to globally hared reource; if there i ufficient remaining budget then the job enter the critical ection, and if there i inufficient remaining budget, the local cheduler delay the critical ection entering of the job (i.e., the job block itelf and it tate become elf blocking) until the next ubytem budget replenihment and guarantee acce to the reource during the next ubytem budget period. In addition, it et the ubytem ceiling equal to the internal reource ceiling of the reource that the elf blocked job wanted to acce, to prevent the execution of all tak that have a priority at mot equal to the ceiling of the reource until the job releae the reource. Local chedulability analyi. The local chedulability analyi under FPS i a follow [?,?]:
4 τ i t : 0 < t D i, rbf FP (i, t) bf (t), (1) where bf (t) i the upply bound function baed on the periodic reource model preented in [?] that compute the minimum poible CPU upply to S for every interval length t, and rbf FP (i, t) denote the requet bound function of a tak τ i. bf (t) can be calculated a follow: { t (k + 1)(P Q bf (t) = ) if t V (k) (k 1)Q otherwie, ( (t where k = max (P Q ) ) ) /P, 1 and V (k) denote an interval [(k + 1)P 2Q, (k + 1)P Q ]. Note that, for Eq. (??), t can be elected within a finite et of cheduling point [?]. The requet bound function rbf FP (i, t) of a tak τ i i given by: (2) rbf FP (i, t) = C i + I S(i) + I H(i, t) + I L(i), (3) I H(i, t) = I L(i) = I S(i) = τ j hp(i) R k {R i } t T j (C j + X i,k, (4) R k {R j } X j,k ), (5) max (2 max (X f,j )), (6) τ f lp(i) R j rc j i where I S(i) i the elf blocking of tak τ i, I H(i, t) i the interference from tak with priority higher than that of τ i, and I L(i) i the interference from tak, with priority lower than that of τ i, that acce hared reource. Subytem budget. In thi paper, it i aumed that the ubytem period i given while the minimum ubytem budget hould be computed o that the ytem will require lower CPU reource. Given a ubytem S, and P, let calculatebudget(s, P ) denote a function that calculate the mallet ubytem budget Q that atifie Eq. (??) (the function i imilar to the one preented in [?]). Hence, Q = calculatebudget(s, P ). (7) Calculating X. Given a ubytem S, it critical ection execution time X repreent the maximum time that a ubytem internal tak may lock a hared reource. Note that any tak τ i acceing a reource R j can be preempted by tak with priority higher than rc j. Note that SIRAP prevent ubytem budget expiration inide a critical ection of a global hared reource. When a tak experience elfblocking during a ubytem budget period it i guaranteed acce to the reource during the next period. A ufficient condition to provide thi guarantee i Q X. (8) We now derive X Q < P and ince we aume that 2P T min then all tak that are allowed to preempt while τ i accee R j will be activated at mot one time from the time that elf blocking happen until the end of the next ubytem period. Then X i,j which repreent the maximum time that τ i lock R j, can be computed a follow, X i,j = c i,j + n k=rc j +1 C k. (9) Let X j = max{x i,j for all τ i T acceing R j}, then X = max{x j for all R j R }. Internal reource ceiling. Looking at Eq. (??), aigning internal reource ceiling according to SRP may make the value of X very high which caue the ubytem to require more CPU reource. One way to handle thi problem i by preventing the preemption inide the ubytem when a tak i acceing a hared reource a propoed in [?] o X i,j = c i,j. It can be implemented uing SRP by aigning the reource ceiling of all reource equal to the maximum tak priority rc j = n where n i the tak ID number of the highet priority tak. However, Bertogna et al. [?] howed that preventing preemption while acceing a global hared reource may violate the local chedulability of the ubytem and propoed an algorithm baed on increaing the ceiling of all reource in tep a much a poible without violating the local chedulability. Finally, Shin et al. [?] howed that there i a tradeoff between decreaing the value of X and the minimum ubytem budget required to guarantee the chedulability of the ubytem. The reult of thi paper doe not depend on any of the dicued method to et the internal reource ceiling. So we aume that the internal ceiling of reource R j can be elected within the following range n rc j rc LWB j. 5. IMPROVED SIRAP ANALYSIS In thi ection we will how that Eq. (??) i peimitic and can be improved uch that the ubytem budget may decreae. Each tak τ i that hare a global reource R j with a lower priority tak τ f can be blocked by τ f due to (i) elf blocking of τ f and in addition due to (ii) acce of R j by τ f. The maximum blocking time of (i) and (ii) are given by the elf blocking time X f,j, and the maximum execution time c f,j of τ f inide a critical ection of R j, repectively. Note that preemption of tak with priority higher than rc j can be excluded from the reource acce of R j by τ f, becaue thoe preemption are already incorporated in I H(i, t) (in Eq. (??)). The wort-cae blocking i the ummation of the blocking from thee two cenario, a hown in Eq. (??).
5 I L(i) = max ( max (X f,j + c f,j )). (10) τ f lp(i) R j rc j i Since c f,j X f,j, the interference I L(i) of tak with a priority lower than that of tak τ i, baed on (8), i at mot equal to that of (6). A a reult, rbf FP (i, t) may decreae, and the correponding ubytem budget Q may therefore decreae a well. 6. IMPROVED SIRAP PROTOCOL In thi ection, we preent a generalization of SIRAP, providing option for efficiency improvement of the protocol. Firt, we conider a dedicated etting for the ubytem ceiling during elf-blocking. Next, we how that the efficiency of the protocol depend on both that etting and the ubytem parameter. Selecting an optimal etting i the topic of the next ection. 6.1 Subytem ceiling for elf-blocking Looking at Eq. (??), one way to reduce the ubytem budget Q i by decreaing rbf FP (i, t) for tak that require highet ubytem budget. In Section??, we have decribed one way to decreae rbf FP (i, t) for higher priority tak that hare reource by decreaing I L(i). In thi ection we propoe a method that allow for a further reduction of I L(i). According to SIRAP, when a tak τ i want to enter a critical ection of R j it firt check if the remaining budget i enough to releae the hared reource before the budget expiration. If there i not enough budget remaining, then the tak τ i block itelf and change only the ubytem ceiling to be equal to rc j. Thi prevent the execution of all tak {τ k } that have priority higher than that of τ i and at mot equal to the ceiling of R j (i.e., rc j k > i) that will be releaed after the elf blocking intance. The new method called E-SIRAP i baed on allowing tak in {τ k } to execute during the elf blocking time of τ i. Thi can be achieved by etting the ubytem ceiling equal to the priority of τ i upon elf blocking of tak τ i and raiing the ubytem ceiling to the reource ceiling when τ i actually accee the reource. The main difference between SIRAP and E-SIRAP i the etting of ubytem ceiling when a tak τ i enter elf blocking (want to acce a hared reource R j and there i not enough budget left). In SIRAP, the ubytem ceiling i et to rc j, i.e., the reource ceiling of R j (the reource that caued the elf blocking). While uing E-SIRAP the ubytem ceiling i et to i, i.e., the priority of τ i, which i at mot equal to rc j. By chooing i during elfblocking, we allow a maximum number of tak to execute while preerving the attractive property of SRP that we can ue a ingle tack for all tak of a ubytem. When uing E-SIRAP, the maximum interference from lower priority tak I L(i) will be decreaed compared to Eq. (??), and can be calculated a; I L(i) = max ( max (c f,j )). (11) τ f lp(i) R j rc j i According to the original SIRAP approach, if τ i block itelf, it hould enter the critical ection at the next ubytem budget replenihment. However, uing E-SIRAP there i no guarantee that τ i will enter the critical ection at the next ubytem activation, ince tak with priority higher than that of τ i and le than or equal to the ceiling of R j are alo allowed to execute in the next ubytem activation. To guarantee that τ i will enter it critical ection at the next ubytem budget replenihment, the ubytem budget hould be big enough to include the execution of thoe tak. When uing E-SIRAP, the ufficient condition (??) ha to be revied to: Q X i,j + k {i+1,...,rc j } C k. (12) Hence, the minimum amount of budget needed for E-SIRAP may increae compared to SIRAP. Since we aume that 2P T min then all higher priority tak will be activated at mot one time during the time t [t rep, t rep+p ] where t rep i the ubytem replenihment time after elf blocking of tak τ i. Note that to evaluate X i,j, Eq. (??) can be ued without modification ince E-SIRAP change the behavior of SIRAP only within the elf blocking time, and during the elf blocking the tak that caued elf blocking i not allowed to acce the hared reource. The only effect of uing E-SIRAP i on the ubytem budget, hence efficiency can be defined excluively in term of Q. Comparing Eq. (??) with Eq. (??), I L(i) may decreae ignificantly and that may decreae the ubytem budget. However, Eq. (??) i a tronger condition than Eq. (??), which may require a higher ubytem budget. Given thee oppoite force, we conclude that E-SIRAP will not alway decreae the minimum ubytem budget and therefore will not alway give better reult than the original SIRAP. We will illutrate thi by the following example. Example 1: Conider a ubytem S that ha three tak and two of them hare reource R 1 a hown in Table??. T C i T i R j c i,j τ τ R 1 1 τ R 1 4 Table 2: Tak et parameter of Example 1. Let the ubytem period be equal to P = 15. Uing the original SIRAP, we derive X = X 1,1 = 6 and Q = Uing E-SIRAP, we derive X = X 1,1 = 6 and Q = 7. Thi latter value atifie Eq. (??), i.e., Q X 1,1 + C 2 = 7. In thi cae, E-SIRAP decreae the ubytem budget, hence require le CPU reource. Converely, for C 2 = 5, we derive Q = for the original SIRAP and derive Q X 1,1 + C 2 = 11 by applying Eq. (??) for E-SIRAP. In thi cae, the original SIRAP outperform E-SIRAP. 6.2 Subytem ceiling upon elf-blocking A decribed in the previou ection, the ubytem ceiling uing E-SIRAP i equal to the priority of the tak that enter
6 elf blocking tate during the elf blocking time. However, uing thi etting for all hared reource during the elf blocking of tak may limit the performance improvement of E-SIRAP in term of decreaing the ubytem budget a hown in the following example. Example 2: Conider a ubytem S that ha four tak a hown in Table?? and the ubytem period P = 50. T C i T i R j c i,j τ R 1, R 2, R 3 0.1, 0.1, 0.1 τ R 3 4 τ R 2 3 τ R Table 3: Tak et parameter of Example 2. Uing original SIRAP, Q = 23, X = X 3 = 4 and rc 1 = rc 2 = rc 3 = 4. Uing E-SIRAP the minimum budget that atifie Eq. (??) i Q = 19, however, to atify the condition in Eq. (??) when τ 1 acce R 1, the ubytem budget hould be Q X 1,1 + C 2 + C 3 + C 4 = 24.8, when τ 2 acce R 2 then Q 22.7 and for τ 3 acce R 3 then Q Thi mean that the ubytem budget hould be Q = If we ue SIRAP etting for R 1 and E-SIRAP etting for the other hared reource then Q = 19 to atify Eq. (??), and to atify the condition in Eq. (??) for τ 1 acce R 1, then Q = 0.1, when τ 2 acce R 2 then Q 22.7 and for τ 3 acce R 3 then Q Thi mean that the ubytem budget hould be Q = Finally, if we et the ubytem ceiling equal to 3 when τ 2 block itelf after trying to lock R 2 then Q = 19 to atify Eq. (??), and to atify the condition in Eq. (??) for for τ 3 acce R 3 hould be Q 18.7 and τ 2 the ubytem budget hould be Q The ubytem budget for thi cae hould be Q = 19. It i clear that combining SIRAP and E-SIRAP give better reult than each alone but the lat etting give even better reult (lowet ubytem budget) which i the combination of SIRAP (for τ 1 acce R 1) and E-SIRAP (for τ 3 acce R 3) and in between (for τ 2 acce R 2). However, there are two problem aociated with thi approach. Firt, each tak acce a hared reource hould have it own etting for ubytem ceiling during the elf blocking time and that mean we need n m extra memory pace to ave thee value a a wort cae. The econd problem i finding the bet etting of ubytem ceiling for each tak acce a global hared reource. In Section?? we preent an algorithm that find the bet etting of the ubytem ceiling to decreae the ubytem budget Q. To olve the firt problem, we introduce elf blocking ceiling rc j a the ceiling of a global hared reource R j during the elf blocking time of all tak that acce thi reource. The value of the elf blocking ceiling hould be within rc j [k, rc j] where k i the index of the lowet priority tak that acce R j i.e., k = min{v τ v T accee R j}. The elf blocking ceiling will be ued in aigning the ubytem ceiling c value during the elf blocking, e.g., when τ i block itelf after failing to lock R j, the following aignment take place: c = max(rc j, i). (13) The max function in Eq. (??) i ued to prevent all lower priority tak τ k that have rc j k < i, from being executed during the elf blocking of τ i. One of the advantage of uing elf blocking ceiling i that it decreae the memory pace required to ave the etting during the elf blocking of tak to m, however, it increae the runtime overhead ince it ue the max function. Note that if it i required to ue SIRAP etting for R j then it i imply achieved by etting rc j = rc j and if it i required to ue E-SIRAP intead then rc j = k, o uing elf blocking ceiling generalize thi verion of SIRAP to include original SIRAP, firt E-SIRAP and in between. Eq. (??) and (??) hould be changed to include the elf blocking ceiling which ha a great effect on them. The interference from lower priority tak on τ i depend on rc j. During elf-blocking of a lower priority tak τ f that tried to acce R j, tak τ i i allowed to execute if rc j < i. Hence, τ i will not be blocked during the elf blocking of τ f on R j when rc j < i. The interference from lower priority tak can be calculated a follow; where I L(i) = max ( max (A(i, j) X f,j + c f,j )), (14) τ f lp(i) R j rc j i A(i, j) = { 0 if rcj < i 1 otherwie. rc j hould alo be included in Eq. (??) a hown below; Q X i,j + k {max(i,rc j )+1,...,rc j } (15) C k. (16) 7. SELECTION ALGORITHM In thi ection, we will preent an algorithm that find the bet etting of the elf blocking ceiling that minimize the ubytem budget Q. The algorithm earche for the bet value for {rc j}, R j R through iteration tep (ee Figure??). The algorithm i explained a follow; Input and output. S, R and {rc j}, R j R are the input to the algorithm, and the output from the algorithm are Q and {rc j}. Initialization. In the beginning, the algorithm et the elf blocking ceiling of reource equal to the reource ceiling (line 1 in Figure (??)) which i equivalent to SIRAP. In thi cae, the interference from lower priority tak will be the highet and i counted uing Eq (??).
7 Iteration tep. In line 4, the algorithm calculate the ubytem budget Q and it check the condition in Eq. (??) to guarantee the correctne of SIRAP/E-SIRAP (line 5 6). In line 14 it find the tak τ h that require the highet CPU reource, that the value of Q wa elected according to the CPU reource demand of thi tak. Then the algorithm find the reource R b that caue the maximum blocking on tak τ h (line 15). Finally, it et the rc b to be le than the priority of τ h in line 19 (rc b = h 1). The interference from lower priority tak that acce R b, on tak τ h will be lower and will be computed according to Eq. (??) (with A(h, b) = 0) which decreae rbf FP (h, t) and can decreae the ubytem budget Q. Finally, the algorithm compute the ubytem budget after the change of the elf blocking ceiling and repeat the operation. Iteration termination. The algorithm terminate if one of the following condition become true: 1. The elf blocking ceiling of the reource R b i lower than the priority of the tak τ h (line 16). In thi cae, lowering the elf blocking ceiling will not decreae Q becaue the maximum blocking on τ h can not be decreaed, i.e., maximum doe not contain the term X h,b in Eq. (??). 2. If there i not a reource that block the tak τ h, i.e., I L(h) = 0 in Eq. (??) (for example the lowet priority tak). 3. If the current budget i greater than the one that i evaluated in the previou iteration (line 8, 12). Note that the budget may increae only due to the condition in Eq. (??). The reaon i that in each iteration the elf blocking ceiling of R b i decreaed which can decreae the required Q that chedule τ h. On the other hand, decreaing rc b will increae the right hand ide of Eq. (??) which may require higher Q, and continuing to decreae rc b will increae Q even more. Complexity and runtime overhead. During an i-th iteration, the algorithm only decreae the elf blocking ceiling of R b. Then, it can repeat at mot O(n m ) iteration for a ubytem that it lowet priority tak accee all hared reource and the algorithm decreaed the elf blocking ceiling of the hared reource to the priority of that tak. During runtime, the improved E-SIRAP add ome runtime overhead compared with the original SIRAP ince it ue a max function in Eq. (??) when aigning the value of the ubytem ceiling when entering elf blocking tate. In addition, it require more memory to ave the elf blocking ceiling of hared reource compared with SIRAP a explained in ection??. Improvement compared to SIRAP. The reulting Q when uing thi algorithm i alway le than or equal to the ubytem budget when uing the original SIRAP. The algorithm initialize the elf blocking ceiling according to SIRAP (i.e., rc j = rc j) and it will continue iterating a long a there i a poibility to decreae Q. It top if the value of Q tart to increae or the algorithm can not decreae it anymore. Then we can conclude that the algorithm will give ame or better reult compared with SIRAP. Algorithm function The findtakmaxq function return the index of one tak. In cae there are more than one tak that require at leat Q then the algorithm will handle one ubytem at each iteration and the order of handling them doe not affect the reult of the algorithm. The ame hold for the function findreourcemaxb where it return the index of one reource and it might happen that more than one hared reource caue the maximum blocking. We will explain the function findtakmaxq ; for each tak τ i, let define lack i a the maximum poitive difference between the upply bound function and the requet bound function of τ i, lack i = max t [0,Di ](bf (t) rbf FP (i, t)) where t can be elected within a finite et of point [?]. Then the function findtakmaxq = i uch that lack i = min τk T (lack k ). Example. We will explain the operation of the algorithm uing the example in Table??. 1. Firt, the algorithm initialize the value of elf blocking uch that rc 1 = rc 2 = rc 3 = 4, then it find the minimum budget required to guarantee the chedulability Q = 23. At line 14, it find the tak that require maximum CPU reource which i τ 4. It trie to decreae the rbf FP (4, t) by decreaing the interference from lower priority tak, looking at Eq. (??) at thi tep, A(4, 1) = A(4, 2) = A(4, 3) = 1, i.e., the maximum blocking from each hared reource. At line 15 the algorithm find R 3 a the hared reource that impoe the maximum blocking on τ 4 o it decreae the elf blocking ceiling of R 3 uch that rc 3 = 3 which make A(4, 3) = The algorithm calculate the new budget Q = 21 and check the condition in Eq. (??) which i Q 18.7 o finalq = 21. It find the tak that require maximum CPU reource, and it i tak τ 4. After that it find the reource that impoe maximum blocking which i R 2. Then it et rc 2 = 3 and by thi A(4, 2) = 0 in Eq. (??). 3. The new ubytem budget will be Q = 19 and the condition in Eq. (??) then Q 18.7, finalq = 19. After that the algorithm find the tak that require maximum CPU, and it i till tak τ 4, and it find that R 3 i impoing the maximum blocking. But rc 3 < 4 (at line 16) the blocking from thi reource i the minimum and can not be minimized more (cae 1 in the iteration termination). So the algorithm top and return the ubytem budget finalq = 19 and the
8 - calculatebudget(s, P, RC, SRC ) return the mallet ubytem budget that atify (??). - findtakmaxq(s, P, Q, RC ) return the tak index of the tak that require at leat Q to be cheduled. - findreourcemaxb(s, P, RC, h) return the reource number that impoe the maximum blocking on τ h - SIRAPCondition(S, SRC ) return the value of budget that atify Eq. (??). - Pri(τ h ) return the priority of the tak τ h. 1: RC = finalsrc = SRC = {rc 1,, rc m } 2: finalq = calculatebudget(s, P, RC, SRC ) 3: do 4: Q = calculatebudget(s, P, RC, SRC ) 5: if (SIRAPCondition(S, SRC ) > Q ) 6: Q = SIRAPCondition(S, SRC ) 7: end if 8: if (Q finalq ) 9: finalq = Q 10: finalsrc = SRC 11: ele 12: return finalq, finalsrc 13: end if 14: h = findtakmaxq(s, P, Q, RC ) 15: b = findreourcemaxb(s, P, RC, h) 16: if (R b / R ) OR (SRC [b] < Pri(τ h )) 17: return finalq, finalsrc 18: ele 19: SRC [b] = Pri(τ h ) 1 20: end if 21: while (true) Figure 2: The election algorithm. elf blocking ceiling of the hared reource rc 1 = 4, rc 2 = 3, rc 3 = ALGORITHM EVALUATION In thi ection, we evaluate the performance of the preented algorithm, in term of requiring le CPU reource than uing original SIRAP. Baed on Eq. (??), (??), (??) and (??), we can ditinguih two parameter that have great effect on the performance of the algorithm: X i,j ince the algorithm decreae the interference of the lower priority tak by X i,j compared with SIRAP (ee Eq. (??)) then higher value of X i,j can decreae the ubytem budget more. The difference between P and T min the lower the difference i the better reult the algorithm will give. The reaon behind thi i that if P i much lower than T min, then the ubytem budget uing SIRAP will be lower and becaue of the condition in Eq. (??) the algorithm may not be able to decreae the ubytem budget. We will explain the effect of the mentioned parameter by mean of the imulation in the following ection. 8.1 Simulation etting The imulation i performed by applying the algorithm on 1000 different randomly generated ubytem where each ubytem conit of 5 tak, and then we have increaed the number of tak to 8 tak to invetigate the effect of changing the number of tak on the algorithm performance. The internal reource ceiling of the globally hared reource are aumed to be equal to the highet tak priority in each ubytem (i.e., rc j = n ) and we aume that T i = D i for all tak. For the ubytem that contain 8 tak, 2-6 tak acce globally hared reource and 1-4 tak acce global hared reource for the ubytem that contain 5 tak. The wort-cae critical ection execution time of a tak τ i i et to a value between 0.3C i and 0.8C i. A tak i aumed to acce at mot one globally hared reource. For each imulation tudy the following etting are changed and a new 1000 ubytem i generated except when changing the ubytem period where the ame ubytem are ued: 1. Number of tak the number of tak in ubytem. 2. Tak et utilization U T the tak et utilization i the ummation of the utilization of all tak in the ubytem, i pecified to a deired value. 3. The ubytem period the ubytem period i pecified to a deired value. The tak et utilization i divided randomly among the tak that belong to that ubytem. Tak period are elected within the range of 200 to Since the tak period i generated to a value within the interval a pecified, the execution time i derived from the deired tak utilization. All randomized ubytem parameter are generated following uniform ditribution. 8.2 Simulation reult Table??-?? how the reult of 3 different imulation tudie performed to meaure the performance of the algorithm. The table preent four main meaure. Firtly, the percentage of ubytem for which the ubytem budget decreaed when the algorithm wa applied i preented in the row labeled by Improve. Secondly, the abolute improvement, i.e. decrement, Q Dec of the ubytem budget i computed, which i defined a Q Dec = Q SIRAP Q alg, where Q SIRAP and Q alg are the ubytem budget uing SIRAP and uing the election algorithm, repectively. The table preent both the average decrement and the maximum decrement in row labeled by Avg. Q Dec and Max. Q Dec, repectively. Thirdly, the relative improvement of the ubytem utilization U Imp i computed, which i defined a U Imp where U SIRAP = (U SIRAP = Q SIRAP U alg )/U SIRAP, (17) /P and U alg = Q alg /P denote the ubytem utilization uing SIRAP and uing the election algorithm, repectively. Similar to the improvement of the ubytem budget, the table preent both the average decrement ( Avg. U Imp ) and maximum decrement ( Max. ) of the ubytem utilization. Finally, the maximum U Imp
9 number of iteration that the algorithm needed to find the lowet ubytem budget i determined and preented in the row labeled by Max. iteration. Study 1 i pecified having tak utilization U T of 5%, 10% and 20%, number of tak n equal to 5, tak period between 200 and 1000, and ubytem period P i 100. Study 2 change the ubytem period P (compared to Study 1) to 75, 70 and 65 and keep U T = 5%. A mentioned previouly we ue the ame 1000 ubytem in Study 1 that have U T = 5% and only change the ubytem period. Study 3 increae the number of tak (compared to Study 1) to 8 tak. Looking at the reult in Table??, it i clear that for ome ubytem the algorithm can decreae the required budget ignificantly (a maximum decreae Max. Q Dec of 17,4 and maximum relative ubytem utilization improvement Max.U Imp of 35%). It alo how that increaing U T decreae the number of ubytem for which the algorithm can improve their budget compared with SIRAP. The reaon i that increaing U T will increae C i of the tak and will increae the required budget that atify Eq. (??). However, it will alo increae c i,j which i clear from oberving the Avg. and Max. row in the table. Looking at Table??, it i clear that when the ubytem period i decreaed, the number of the ubytem that the algorithm can improve will be decreaed. However, the decrement in the ubytem budget will be more ignificant for the ubytem utilization when the ubytem period i lower ince U = Q /P (ee the Ave. and Max. row in Table?? for the cae P = 75). When P = 65 T min/3 then the algorithm can not improve any ubytem a explained in the beginning of thi ection. Thi can be een a a limitation of the algorithm and it could be better to decreae the ubytem period intead of uing the algorithm to decreae the ubytem utilization U = Q /P. However, thi i not alway true, firt, from the imulation reult we have compared the ubytem utilization U when P = 100 and P = 65 and we have found that when P = 100, 97 out of 410 ubytem that the algorithm improved, require le or equal ubytem U than when uing only SIRAP with P = 65. The reaon i that when the algorithm i able to improve the ubytem budget, then the requet bound function of the tak that need maximum CPU reource will be lower than the cae when uing original SIRAP with lower ubytem period, and thi affect Eq. (??). The econd iue of reducing the ubytem budget i that it increae the context witch overhead becaue the ubytem budget will be lower. Finally, a howed in [?] decreaing the ubytem period may increae U to atify the condition Q X of SIRAP. In Study 3 we have increaed the number of tak to 8 tak in each ubytem, and the reult in Table?? how that increaing the number of tak doe not change the effect of U T. However, increaing the number of tak will increae the number of ubytem that the algorithm can improve (compare the Improve row in Table?? and Table??). The reaon i that there are more tak and more hared reource in each ubytem o the algorithm can improve the ubytem more before it top. The maximum number of iteration for 8 tak i 6 iteration while for 5 tak it i 4. In addition, increaing the number of tak and keeping U T the ame, decreae the utilization of each tak which improve the algorithm performance in term of the number of the ubytem that the algorithm can improve a explained previouly. U T =5% U T =10% U T =20% Improve 41% 34, 1% 26% Avg. Q Dec 2 3, 70 5, 3 Avg. U Imp 16, 4% 15, 3% 12, 4% Max. Q Dec , 4 Max. U Imp 36, 6% 37, 2% 35% Max. iteration Table 4: Meaured reult of Study 1. P =75 P =70 P =65 Improve 19, 5% 5, 4% 0% Avg. Q Dec 1, 9 0, 55 0 Avg. U Imp 20% 8% 0% Max. Q Dec 5 1, 2 0 Max. U Imp 41, 9% 16, 6% 0% Max. iteration Table 5: Meaured reult of Study 2. U T =5% U T =10% U T =20% Improve 47, 6% 43, 4% 32, 3% Avg. Q Dec 2 3, 3 5 Avg. U Imp 14, 3% 13, 6% 11% Max. Q Dec , 6 Max. U Imp 34, 5% 35, 4% 33, 5% Max. iteration Table 6: Meaured reult of Study SUMMARY In thi paper, we preented an improved chedulability analyi for the ynchronization protocol SIRAP. The improved analyi may decreae the minimum ubytem budget while till guaranteeing the chedulability of all tak in a ubytem. We alo preented a generalization of SIRAP, which ditinguihe eparate reource ceiling for elf blocking and for actual reource acce, with the aim to reduce the required CPU reource for each ubytem by reducing the interference from lower priority tak. Becaue the efficiency of the protocol depend on both the etting of the reource ceiling and the ubytem parameter, we preented an algorithm that find the bet etting for reource ceiling during the elf blocking for each hared reource in order to minimize the required ubytem budget. The imulation reult how that the algorithm can ignificantly reduce the CPU reource need of a ubytem, but that the effectivene of the algorithm heavily depend on the tak parameter and the ubytem period.
10 Our future work include further improvement of SIRAP in two direction: I) Applying runtime mechanim to decreae the value of X i,j that i ued to check if there i enough remaining budget before acceing a hared reource, baed on the arrival time of the higher priority tak, in order to improve the average repone time of tak. II) Invetigating the cae of allowing lower priority tak to execute during the elf blocking in order to reduce the interference from higher priority tak. For thi improvement, a runtime mechanim may be required to decide the correct execution order of tak during the next activation ubytem period. III) Finally, howing the advantage of the propoed algorithm on real indutrial ytem.
Lecture 14: Minimum Spanning Tree I
 COMPSCI 0: Deign and Analyi of Algorithm October 4, 07 Lecture 4: Minimum Spanning Tree I Lecturer: Rong Ge Scribe: Fred Zhang Overview Thi lecture we finih our dicuion of the hortet path problem and introduce
COMPSCI 0: Deign and Analyi of Algorithm October 4, 07 Lecture 4: Minimum Spanning Tree I Lecturer: Rong Ge Scribe: Fred Zhang Overview Thi lecture we finih our dicuion of the hortet path problem and introduce
Analyzing Hydra Historical Statistics Part 2
 Analyzing Hydra Hitorical Statitic Part Fabio Maimo Ottaviani EPV Technologie White paper 5 hnode HSM Hitorical Record The hnode i the hierarchical data torage management node and ha to perform all the
Analyzing Hydra Hitorical Statitic Part Fabio Maimo Ottaviani EPV Technologie White paper 5 hnode HSM Hitorical Record The hnode i the hierarchical data torage management node and ha to perform all the
Performance of a Robust Filter-based Approach for Contour Detection in Wireless Sensor Networks
 Performance of a Robut Filter-baed Approach for Contour Detection in Wirele Senor Network Hadi Alati, William A. Armtrong, Jr., and Ai Naipuri Department of Electrical and Computer Engineering The Univerity
Performance of a Robut Filter-baed Approach for Contour Detection in Wirele Senor Network Hadi Alati, William A. Armtrong, Jr., and Ai Naipuri Department of Electrical and Computer Engineering The Univerity
Key Terms - MinMin, MaxMin, Sufferage, Task Scheduling, Standard Deviation, Load Balancing.
 Volume 3, Iue 11, November 2013 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Tak Aignment in
Volume 3, Iue 11, November 2013 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Tak Aignment in
A Practical Model for Minimizing Waiting Time in a Transit Network
 A Practical Model for Minimizing Waiting Time in a Tranit Network Leila Dianat, MASc, Department of Civil Engineering, Sharif Univerity of Technology, Tehran, Iran Youef Shafahi, Ph.D. Aociate Profeor,
A Practical Model for Minimizing Waiting Time in a Tranit Network Leila Dianat, MASc, Department of Civil Engineering, Sharif Univerity of Technology, Tehran, Iran Youef Shafahi, Ph.D. Aociate Profeor,
Keywords Cloud Computing, Service Level Agreements (SLA), CloudSim, Monitoring & Controlling SLA Agent, JADE
 Volume 5, Iue 8, Augut 2015 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Verification of Agent
Volume 5, Iue 8, Augut 2015 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Verification of Agent
Laboratory Exercise 6
 Laboratory Exercie 6 Adder, Subtractor, and Multiplier The purpoe of thi exercie i to examine arithmetic circuit that add, ubtract, and multiply number. Each type of circuit will be implemented in two
Laboratory Exercie 6 Adder, Subtractor, and Multiplier The purpoe of thi exercie i to examine arithmetic circuit that add, ubtract, and multiply number. Each type of circuit will be implemented in two
DAROS: Distributed User-Server Assignment And Replication For Online Social Networking Applications
 DAROS: Ditributed Uer-Server Aignment And Replication For Online Social Networking Application Thuan Duong-Ba School of EECS Oregon State Univerity Corvalli, OR 97330, USA Email: duongba@eec.oregontate.edu
DAROS: Ditributed Uer-Server Aignment And Replication For Online Social Networking Application Thuan Duong-Ba School of EECS Oregon State Univerity Corvalli, OR 97330, USA Email: duongba@eec.oregontate.edu
Edits in Xylia Validity Preserving Editing of XML Documents
 dit in Xylia Validity Preerving diting of XML Document Pouria Shaker, Theodore S. Norvell, and Denni K. Peter Faculty of ngineering and Applied Science, Memorial Univerity of Newfoundland, St. John, NFLD,
dit in Xylia Validity Preerving diting of XML Document Pouria Shaker, Theodore S. Norvell, and Denni K. Peter Faculty of ngineering and Applied Science, Memorial Univerity of Newfoundland, St. John, NFLD,
Routing Definition 4.1
 4 Routing So far, we have only looked at network without dealing with the iue of how to end information in them from one node to another The problem of ending information in a network i known a routing
4 Routing So far, we have only looked at network without dealing with the iue of how to end information in them from one node to another The problem of ending information in a network i known a routing
Distributed Packet Processing Architecture with Reconfigurable Hardware Accelerators for 100Gbps Forwarding Performance on Virtualized Edge Router
 Ditributed Packet Proceing Architecture with Reconfigurable Hardware Accelerator for 100Gbp Forwarding Performance on Virtualized Edge Router Satohi Nihiyama, Hitohi Kaneko, and Ichiro Kudo Abtract To
Ditributed Packet Proceing Architecture with Reconfigurable Hardware Accelerator for 100Gbp Forwarding Performance on Virtualized Edge Router Satohi Nihiyama, Hitohi Kaneko, and Ichiro Kudo Abtract To
1 The secretary problem
 Thi i new material: if you ee error, pleae email jtyu at tanford dot edu 1 The ecretary problem We will tart by analyzing the expected runtime of an algorithm, a you will be expected to do on your homework.
Thi i new material: if you ee error, pleae email jtyu at tanford dot edu 1 The ecretary problem We will tart by analyzing the expected runtime of an algorithm, a you will be expected to do on your homework.
The Association of System Performance Professionals
 The Aociation of Sytem Performance Profeional The Computer Meaurement Group, commonly called CMG, i a not for profit, worldwide organization of data proceing profeional committed to the meaurement and
The Aociation of Sytem Performance Profeional The Computer Meaurement Group, commonly called CMG, i a not for profit, worldwide organization of data proceing profeional committed to the meaurement and
Service and Network Management Interworking in Future Wireless Systems
 Service and Network Management Interworking in Future Wirele Sytem V. Tountopoulo V. Stavroulaki P. Demeticha N. Mitrou and M. Theologou National Technical Univerity of Athen Department of Electrical Engineering
Service and Network Management Interworking in Future Wirele Sytem V. Tountopoulo V. Stavroulaki P. Demeticha N. Mitrou and M. Theologou National Technical Univerity of Athen Department of Electrical Engineering
See chapter 8 in the textbook. Dr Muhammad Al Salamah, Industrial Engineering, KFUPM
 Goal programming Objective of the topic: Indentify indutrial baed ituation where two or more objective function are required. Write a multi objective function model dla a goal LP Ue weighting um and preemptive
Goal programming Objective of the topic: Indentify indutrial baed ituation where two or more objective function are required. Write a multi objective function model dla a goal LP Ue weighting um and preemptive
SLA Adaptation for Service Overlay Networks
 SLA Adaptation for Service Overlay Network Con Tran 1, Zbigniew Dziong 1, and Michal Pióro 2 1 Department of Electrical Engineering, École de Technologie Supérieure, Univerity of Quebec, Montréal, Canada
SLA Adaptation for Service Overlay Network Con Tran 1, Zbigniew Dziong 1, and Michal Pióro 2 1 Department of Electrical Engineering, École de Technologie Supérieure, Univerity of Quebec, Montréal, Canada
Increasing Throughput and Reducing Delay in Wireless Sensor Networks Using Interference Alignment
 Int. J. Communication, Network and Sytem Science, 0, 5, 90-97 http://dx.doi.org/0.436/ijcn.0.50 Publihed Online February 0 (http://www.scirp.org/journal/ijcn) Increaing Throughput and Reducing Delay in
Int. J. Communication, Network and Sytem Science, 0, 5, 90-97 http://dx.doi.org/0.436/ijcn.0.50 Publihed Online February 0 (http://www.scirp.org/journal/ijcn) Increaing Throughput and Reducing Delay in
A Multi-objective Genetic Algorithm for Reliability Optimization Problem
 International Journal of Performability Engineering, Vol. 5, No. 3, April 2009, pp. 227-234. RAMS Conultant Printed in India A Multi-objective Genetic Algorithm for Reliability Optimization Problem AMAR
International Journal of Performability Engineering, Vol. 5, No. 3, April 2009, pp. 227-234. RAMS Conultant Printed in India A Multi-objective Genetic Algorithm for Reliability Optimization Problem AMAR
On successive packing approach to multidimensional (M-D) interleaving
 On ucceive packing approach to multidimenional (M-D) interleaving Xi Min Zhang Yun Q. hi ankar Bau Abtract We propoe an interleaving cheme for multidimenional (M-D) interleaving. To achieved by uing a
On ucceive packing approach to multidimenional (M-D) interleaving Xi Min Zhang Yun Q. hi ankar Bau Abtract We propoe an interleaving cheme for multidimenional (M-D) interleaving. To achieved by uing a
Topics. Lecture 37: Global Optimization. Issues. A Simple Example: Copy Propagation X := 3 B > 0 Y := 0 X := 4 Y := Z + W A := 2 * 3X
 Lecture 37: Global Optimization [Adapted from note by R. Bodik and G. Necula] Topic Global optimization refer to program optimization that encompa multiple baic block in a function. (I have ued the term
Lecture 37: Global Optimization [Adapted from note by R. Bodik and G. Necula] Topic Global optimization refer to program optimization that encompa multiple baic block in a function. (I have ued the term
Universität Augsburg. Institut für Informatik. Approximating Optimal Visual Sensor Placement. E. Hörster, R. Lienhart.
 Univerität Augburg à ÊÇÅÍÆ ËÀǼ Approximating Optimal Viual Senor Placement E. Hörter, R. Lienhart Report 2006-01 Januar 2006 Intitut für Informatik D-86135 Augburg Copyright c E. Hörter, R. Lienhart Intitut
Univerität Augburg à ÊÇÅÍÆ ËÀǼ Approximating Optimal Viual Senor Placement E. Hörter, R. Lienhart Report 2006-01 Januar 2006 Intitut für Informatik D-86135 Augburg Copyright c E. Hörter, R. Lienhart Intitut
An Approach to a Test Oracle for XML Query Testing
 An Approach to a Tet Oracle for XML Query Teting Dae S. Kim-Park, Claudio de la Riva, Javier Tuya Univerity of Oviedo Computing Department Campu of Vieque, /n, 33204 (SPAIN) kim_park@li.uniovi.e, claudio@uniovi.e,
An Approach to a Tet Oracle for XML Query Teting Dae S. Kim-Park, Claudio de la Riva, Javier Tuya Univerity of Oviedo Computing Department Campu of Vieque, /n, 33204 (SPAIN) kim_park@li.uniovi.e, claudio@uniovi.e,
Hassan Ghaziri AUB, OSB Beirut, Lebanon Key words Competitive self-organizing maps, Meta-heuristics, Vehicle routing problem,
 COMPETITIVE PROBABIISTIC SEF-ORGANIZING MAPS FOR ROUTING PROBEMS Haan Ghaziri AUB, OSB Beirut, ebanon ghaziri@aub.edu.lb Abtract In thi paper, we have applied the concept of the elf-organizing map (SOM)
COMPETITIVE PROBABIISTIC SEF-ORGANIZING MAPS FOR ROUTING PROBEMS Haan Ghaziri AUB, OSB Beirut, ebanon ghaziri@aub.edu.lb Abtract In thi paper, we have applied the concept of the elf-organizing map (SOM)
Operational Semantics Class notes for a lecture given by Mooly Sagiv Tel Aviv University 24/5/2007 By Roy Ganor and Uri Juhasz
 Operational emantic Page Operational emantic Cla note for a lecture given by Mooly agiv Tel Aviv Univerity 4/5/7 By Roy Ganor and Uri Juhaz Reference emantic with Application, H. Nielon and F. Nielon,
Operational emantic Page Operational emantic Cla note for a lecture given by Mooly agiv Tel Aviv Univerity 4/5/7 By Roy Ganor and Uri Juhaz Reference emantic with Application, H. Nielon and F. Nielon,
Aspects of Formal and Graphical Design of a Bus System
 Apect of Formal and Graphical Deign of a Bu Sytem Tiberiu Seceleanu Univerity of Turku, Dpt. of Information Technology Turku, Finland tiberiu.eceleanu@utu.fi Tomi Weterlund Turku Centre for Computer Science
Apect of Formal and Graphical Deign of a Bu Sytem Tiberiu Seceleanu Univerity of Turku, Dpt. of Information Technology Turku, Finland tiberiu.eceleanu@utu.fi Tomi Weterlund Turku Centre for Computer Science
SIMIT 7. Profinet IO Gateway. User Manual
 SIMIT 7 Profinet IO Gateway Uer Manual Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult are only non-binding uggetion
SIMIT 7 Profinet IO Gateway Uer Manual Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult are only non-binding uggetion
Chapter 13 Non Sampling Errors
 Chapter 13 Non Sampling Error It i a general aumption in the ampling theory that the true value of each unit in the population can be obtained and tabulated without any error. In practice, thi aumption
Chapter 13 Non Sampling Error It i a general aumption in the ampling theory that the true value of each unit in the population can be obtained and tabulated without any error. In practice, thi aumption
A SIMPLE IMPERATIVE LANGUAGE THE STORE FUNCTION NON-TERMINATING COMMANDS
 A SIMPLE IMPERATIVE LANGUAGE Eventually we will preent the emantic of a full-blown language, with declaration, type and looping. However, there are many complication, o we will build up lowly. Our firt
A SIMPLE IMPERATIVE LANGUAGE Eventually we will preent the emantic of a full-blown language, with declaration, type and looping. However, there are many complication, o we will build up lowly. Our firt
Modeling and Analysis of Slow CW Decrease for IEEE WLAN
 Modeling and Analyi of Slow CW Decreae for IEEE 82. WLAN Qiang Ni, Imad Aad 2, Chadi Barakat, and Thierry Turletti Planete Group 2 Planete Group INRIA Sophia Antipoli INRIA Rhône-Alpe Sophia Antipoli,
Modeling and Analyi of Slow CW Decreae for IEEE 82. WLAN Qiang Ni, Imad Aad 2, Chadi Barakat, and Thierry Turletti Planete Group 2 Planete Group INRIA Sophia Antipoli INRIA Rhône-Alpe Sophia Antipoli,
CENTER-POINT MODEL OF DEFORMABLE SURFACE
 CENTER-POINT MODEL OF DEFORMABLE SURFACE Piotr M. Szczypinki Iintitute of Electronic, Technical Univerity of Lodz, Poland Abtract: Key word: Center-point model of deformable urface for egmentation of 3D
CENTER-POINT MODEL OF DEFORMABLE SURFACE Piotr M. Szczypinki Iintitute of Electronic, Technical Univerity of Lodz, Poland Abtract: Key word: Center-point model of deformable urface for egmentation of 3D
MAT 155: Describing, Exploring, and Comparing Data Page 1 of NotesCh2-3.doc
 MAT 155: Decribing, Exploring, and Comparing Data Page 1 of 8 001-oteCh-3.doc ote for Chapter Summarizing and Graphing Data Chapter 3 Decribing, Exploring, and Comparing Data Frequency Ditribution, Graphic
MAT 155: Decribing, Exploring, and Comparing Data Page 1 of 8 001-oteCh-3.doc ote for Chapter Summarizing and Graphing Data Chapter 3 Decribing, Exploring, and Comparing Data Frequency Ditribution, Graphic
LinkGuide: Towards a Better Collection of Hyperlinks in a Website Homepage
 Proceeding of the World Congre on Engineering 2007 Vol I LinkGuide: Toward a Better Collection of Hyperlink in a Webite Homepage A. Ammari and V. Zharkova chool of Informatic, Univerity of Bradford anammari@bradford.ac.uk,
Proceeding of the World Congre on Engineering 2007 Vol I LinkGuide: Toward a Better Collection of Hyperlink in a Webite Homepage A. Ammari and V. Zharkova chool of Informatic, Univerity of Bradford anammari@bradford.ac.uk,
Modelling the impact of cyber attacks on the traffic control centre of an urban automobile transport system by means of enhanced cybersecurity
 Modelling the impact of cyber attack on the traffic control centre of an urban automobile tranport ytem by mean of enhanced cyberecurity Yoana Ivanova 1,* 1 Bulgarian Academy of Science, Intitute of ICT,
Modelling the impact of cyber attack on the traffic control centre of an urban automobile tranport ytem by mean of enhanced cyberecurity Yoana Ivanova 1,* 1 Bulgarian Academy of Science, Intitute of ICT,
xy-monotone path existence queries in a rectilinear environment
 CCCG 2012, Charlottetown, P.E.I., Augut 8 10, 2012 xy-monotone path exitence querie in a rectilinear environment Gregory Bint Anil Mahehwari Michiel Smid Abtract Given a planar environment coniting of
CCCG 2012, Charlottetown, P.E.I., Augut 8 10, 2012 xy-monotone path exitence querie in a rectilinear environment Gregory Bint Anil Mahehwari Michiel Smid Abtract Given a planar environment coniting of
Analytical Redundancy and Fuzzy Inference in AUV Fault Detection and Compensation
 Analytical Redundancy and Fuzzy Inference in AUV Fault Detection and Compenation A. J. Healey Profeor and Director Center for AUV Reearch Naval Potgraduate School Monterey, CA 93953 healey@me.np.navy.mil
Analytical Redundancy and Fuzzy Inference in AUV Fault Detection and Compenation A. J. Healey Profeor and Director Center for AUV Reearch Naval Potgraduate School Monterey, CA 93953 healey@me.np.navy.mil
Policy-based Injection of Private Traffic into a Public SDN Testbed
 Intitut für Techniche Informatik und Kommunikationnetze Adrian Friedli Policy-baed Injection of Private Traffic into a Public SDN Tetbed Mater Thei MA-2013-12 Advior: Dr. Bernhard Ager, Vaileio Kotroni
Intitut für Techniche Informatik und Kommunikationnetze Adrian Friedli Policy-baed Injection of Private Traffic into a Public SDN Tetbed Mater Thei MA-2013-12 Advior: Dr. Bernhard Ager, Vaileio Kotroni
AUTOMATIC TEST CASE GENERATION USING UML MODELS
 Volume-2, Iue-6, June-2014 AUTOMATIC TEST CASE GENERATION USING UML MODELS 1 SAGARKUMAR P. JAIN, 2 KHUSHBOO S. LALWANI, 3 NIKITA K. MAHAJAN, 4 BHAGYASHREE J. GADEKAR 1,2,3,4 Department of Computer Engineering,
Volume-2, Iue-6, June-2014 AUTOMATIC TEST CASE GENERATION USING UML MODELS 1 SAGARKUMAR P. JAIN, 2 KHUSHBOO S. LALWANI, 3 NIKITA K. MAHAJAN, 4 BHAGYASHREE J. GADEKAR 1,2,3,4 Department of Computer Engineering,
A Linear Interpolation-Based Algorithm for Path Planning and Replanning on Girds *
 Advance in Linear Algebra & Matrix Theory, 2012, 2, 20-24 http://dx.doi.org/10.4236/alamt.2012.22003 Publihed Online June 2012 (http://www.scirp.org/journal/alamt) A Linear Interpolation-Baed Algorithm
Advance in Linear Algebra & Matrix Theory, 2012, 2, 20-24 http://dx.doi.org/10.4236/alamt.2012.22003 Publihed Online June 2012 (http://www.scirp.org/journal/alamt) A Linear Interpolation-Baed Algorithm
Multicast with Network Coding in Application-Layer Overlay Networks
 IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS, VOL. 22, NO. 1, JANUARY 2004 1 Multicat with Network Coding in Application-Layer Overlay Network Ying Zhu, Baochun Li, Member, IEEE, and Jiang Guo Abtract
IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS, VOL. 22, NO. 1, JANUARY 2004 1 Multicat with Network Coding in Application-Layer Overlay Network Ying Zhu, Baochun Li, Member, IEEE, and Jiang Guo Abtract
Performance Evaluation of search engines via user efforts measures
 IJCSI International Journal of Computer Science Iue, Vol. 9, Iue 4, No, July 01 www.ijcsi.org 437 Performance Evaluation of earch engine via uer effort meaure Raeh Kumar Goutam 1 and Sanay K. Dwivedi 1
IJCSI International Journal of Computer Science Iue, Vol. 9, Iue 4, No, July 01 www.ijcsi.org 437 Performance Evaluation of earch engine via uer effort meaure Raeh Kumar Goutam 1 and Sanay K. Dwivedi 1
A Hybrid Deployable Dynamic Traffic Assignment Framework for Robust Online Route Guidance
 A Hybrid Deployable Dynamic Traffic Aignment Framework for Robut Online Route Guidance Sriniva Peeta School of Civil Engineering, Purdue Univerity Chao Zhou Sabre, Inc. Sriniva Peeta School of Civil Engineering
A Hybrid Deployable Dynamic Traffic Aignment Framework for Robut Online Route Guidance Sriniva Peeta School of Civil Engineering, Purdue Univerity Chao Zhou Sabre, Inc. Sriniva Peeta School of Civil Engineering
Performance Evaluation of an Advanced Local Search Evolutionary Algorithm
 Anne Auger and Nikolau Hanen Performance Evaluation of an Advanced Local Search Evolutionary Algorithm Proceeding of the IEEE Congre on Evolutionary Computation, CEC 2005 c IEEE Performance Evaluation
Anne Auger and Nikolau Hanen Performance Evaluation of an Advanced Local Search Evolutionary Algorithm Proceeding of the IEEE Congre on Evolutionary Computation, CEC 2005 c IEEE Performance Evaluation
Karen L. Collins. Wesleyan University. Middletown, CT and. Mark Hovey MIT. Cambridge, MA Abstract
 Mot Graph are Edge-Cordial Karen L. Collin Dept. of Mathematic Weleyan Univerity Middletown, CT 6457 and Mark Hovey Dept. of Mathematic MIT Cambridge, MA 239 Abtract We extend the definition of edge-cordial
Mot Graph are Edge-Cordial Karen L. Collin Dept. of Mathematic Weleyan Univerity Middletown, CT 6457 and Mark Hovey Dept. of Mathematic MIT Cambridge, MA 239 Abtract We extend the definition of edge-cordial
Lecture Outline. Global flow analysis. Global Optimization. Global constant propagation. Liveness analysis. Local Optimization. Global Optimization
 Lecture Outline Global flow analyi Global Optimization Global contant propagation Livene analyi Adapted from Lecture by Prof. Alex Aiken and George Necula (UCB) CS781(Praad) L27OP 1 CS781(Praad) L27OP
Lecture Outline Global flow analyi Global Optimization Global contant propagation Livene analyi Adapted from Lecture by Prof. Alex Aiken and George Necula (UCB) CS781(Praad) L27OP 1 CS781(Praad) L27OP
An Intro to LP and the Simplex Algorithm. Primal Simplex
 An Intro to LP and the Simplex Algorithm Primal Simplex Linear programming i contrained minimization of a linear objective over a olution pace defined by linear contraint: min cx Ax b l x u A i an m n
An Intro to LP and the Simplex Algorithm Primal Simplex Linear programming i contrained minimization of a linear objective over a olution pace defined by linear contraint: min cx Ax b l x u A i an m n
Analysis of the results of analytical and simulation With the network model and dynamic priority Unchecked Buffer
 International Reearch Journal of Applied and Baic Science 218 Available online at www.irjab.com ISSN 2251-838X / Vol, 12 (1): 49-53 Science Explorer Publication Analyi of the reult of analytical and imulation
International Reearch Journal of Applied and Baic Science 218 Available online at www.irjab.com ISSN 2251-838X / Vol, 12 (1): 49-53 Science Explorer Publication Analyi of the reult of analytical and imulation
A Load Balancing Model based on Load-aware for Distributed Controllers. Fengjun Shang, Wenjuan Gong
 4th International Conference on Machinery, Material and Computing Technology (ICMMCT 2016) A Load Balancing Model baed on Load-aware for Ditributed Controller Fengjun Shang, Wenjuan Gong College of Compute
4th International Conference on Machinery, Material and Computing Technology (ICMMCT 2016) A Load Balancing Model baed on Load-aware for Ditributed Controller Fengjun Shang, Wenjuan Gong College of Compute
A note on degenerate and spectrally degenerate graphs
 A note on degenerate and pectrally degenerate graph Noga Alon Abtract A graph G i called pectrally d-degenerate if the larget eigenvalue of each ubgraph of it with maximum degree D i at mot dd. We prove
A note on degenerate and pectrally degenerate graph Noga Alon Abtract A graph G i called pectrally d-degenerate if the larget eigenvalue of each ubgraph of it with maximum degree D i at mot dd. We prove
A System Dynamics Model for Transient Availability Modeling of Repairable Redundant Systems
 International Journal of Performability Engineering Vol., No. 3, May 05, pp. 03-. RAMS Conultant Printed in India A Sytem Dynamic Model for Tranient Availability Modeling of Repairable Redundant Sytem
International Journal of Performability Engineering Vol., No. 3, May 05, pp. 03-. RAMS Conultant Printed in India A Sytem Dynamic Model for Tranient Availability Modeling of Repairable Redundant Sytem
The Data Locality of Work Stealing
 The Data Locality of Work Stealing Umut A. Acar School of Computer Science Carnegie Mellon Univerity umut@c.cmu.edu Guy E. Blelloch School of Computer Science Carnegie Mellon Univerity guyb@c.cmu.edu Robert
The Data Locality of Work Stealing Umut A. Acar School of Computer Science Carnegie Mellon Univerity umut@c.cmu.edu Guy E. Blelloch School of Computer Science Carnegie Mellon Univerity guyb@c.cmu.edu Robert
Distributed Partial Information Management (DPIM) Schemes for Survivable Networks - Part II
 IEEE INFOCO 2002 1 Ditributed Partial Information anagement (DPI) Scheme for Survivable Network - Part II Dahai Xu Chunming Qiao Department of Computer Science and Engineering State Univerity of New York
IEEE INFOCO 2002 1 Ditributed Partial Information anagement (DPI) Scheme for Survivable Network - Part II Dahai Xu Chunming Qiao Department of Computer Science and Engineering State Univerity of New York
SIMIT 7. Component Type Editor (CTE) User manual. Siemens Industrial
 SIMIT 7 Component Type Editor (CTE) Uer manual Siemen Indutrial Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult
SIMIT 7 Component Type Editor (CTE) Uer manual Siemen Indutrial Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult
A Local Mobility Agent Selection Algorithm for Mobile Networks
 A Local Mobility Agent Selection Algorithm for Mobile Network Yi Xu Henry C. J. Lee Vrizlynn L. L. Thing Intitute for Infocomm Reearch, 21 Heng Mui Keng Terrace, Singapore 119613 Email: {yxu, hlee, vriz}@i2r.a-tar.edu.g
A Local Mobility Agent Selection Algorithm for Mobile Network Yi Xu Henry C. J. Lee Vrizlynn L. L. Thing Intitute for Infocomm Reearch, 21 Heng Mui Keng Terrace, Singapore 119613 Email: {yxu, hlee, vriz}@i2r.a-tar.edu.g
On Peer-to-Peer Media Streaming Λ
 On eer-to-eer Media Streaming Λ Dongyan Xu y, Mohamed Hefeeda, Suanne Hambruch, Bharat Bhargava Department of Computer Science urdue Univerity, Wet Lafayette, IN 797 fdxu, hefeeda, eh, bbg@c.purdue.edu
On eer-to-eer Media Streaming Λ Dongyan Xu y, Mohamed Hefeeda, Suanne Hambruch, Bharat Bhargava Department of Computer Science urdue Univerity, Wet Lafayette, IN 797 fdxu, hefeeda, eh, bbg@c.purdue.edu
mapping reult. Our experiment have revealed that for many popular tream application, uch a networking and multimedia application, the number of VC nee
 Reolving Deadlock for Pipelined Stream Application on Network-on-Chip Xiaohang Wang 1,2, Peng Liu 1 1 Department of Information Science and Electronic Engineering, Zheiang Univerity Hangzhou, Zheiang,
Reolving Deadlock for Pipelined Stream Application on Network-on-Chip Xiaohang Wang 1,2, Peng Liu 1 1 Department of Information Science and Electronic Engineering, Zheiang Univerity Hangzhou, Zheiang,
Task-based Adaptation for Ubiquitous Computing
 IEEE Tranaction on Sytem, Man, and Cybernetic, Part C: Application and Review Special Iue on Engineering Autonomic Sytem, to appear Tak-baed Adaptation for Ubiquitou Computing João Pedro Soua, Vahe Poladian,
IEEE Tranaction on Sytem, Man, and Cybernetic, Part C: Application and Review Special Iue on Engineering Autonomic Sytem, to appear Tak-baed Adaptation for Ubiquitou Computing João Pedro Soua, Vahe Poladian,
Localized Minimum Spanning Tree Based Multicast Routing with Energy-Efficient Guaranteed Delivery in Ad Hoc and Sensor Networks
 Localized Minimum Spanning Tree Baed Multicat Routing with Energy-Efficient Guaranteed Delivery in Ad Hoc and Senor Network Hanne Frey Univerity of Paderborn D-3398 Paderborn hanne.frey@uni-paderborn.de
Localized Minimum Spanning Tree Baed Multicat Routing with Energy-Efficient Guaranteed Delivery in Ad Hoc and Senor Network Hanne Frey Univerity of Paderborn D-3398 Paderborn hanne.frey@uni-paderborn.de
Minimum congestion spanning trees in bipartite and random graphs
 Minimum congetion panning tree in bipartite and random graph M.I. Otrovkii Department of Mathematic and Computer Science St. John Univerity 8000 Utopia Parkway Queen, NY 11439, USA e-mail: otrovm@tjohn.edu
Minimum congetion panning tree in bipartite and random graph M.I. Otrovkii Department of Mathematic and Computer Science St. John Univerity 8000 Utopia Parkway Queen, NY 11439, USA e-mail: otrovm@tjohn.edu
Shortest Paths Problem. CS 362, Lecture 20. Today s Outline. Negative Weights
 Shortet Path Problem CS 6, Lecture Jared Saia Univerity of New Mexico Another intereting problem for graph i that of finding hortet path Aume we are given a weighted directed graph G = (V, E) with two
Shortet Path Problem CS 6, Lecture Jared Saia Univerity of New Mexico Another intereting problem for graph i that of finding hortet path Aume we are given a weighted directed graph G = (V, E) with two
Shortest Paths with Single-Point Visibility Constraint
 Shortet Path with Single-Point Viibility Contraint Ramtin Khoravi Mohammad Ghodi Department of Computer Engineering Sharif Univerity of Technology Abtract Thi paper tudie the problem of finding a hortet
Shortet Path with Single-Point Viibility Contraint Ramtin Khoravi Mohammad Ghodi Department of Computer Engineering Sharif Univerity of Technology Abtract Thi paper tudie the problem of finding a hortet
Domain-Specific Modeling for Rapid System-Wide Energy Estimation of Reconfigurable Architectures
 Domain-Specific Modeling for Rapid Sytem-Wide Energy Etimation of Reconfigurable Architecture Seonil Choi 1,Ju-wookJang 2, Sumit Mohanty 1, Viktor K. Praanna 1 1 Dept. of Electrical Engg. 2 Dept. of Electronic
Domain-Specific Modeling for Rapid Sytem-Wide Energy Etimation of Reconfigurable Architecture Seonil Choi 1,Ju-wookJang 2, Sumit Mohanty 1, Viktor K. Praanna 1 1 Dept. of Electrical Engg. 2 Dept. of Electronic
Stress-Blended Eddy Simulation (SBES) - A new Paradigm in hybrid RANS-LES Modeling
 Stre-Blended Eddy Simulation (SBES) - A new Paradigm in hybrid RANS-LES Modeling Menter F.R. ANSYS Germany GmbH Introduction It i oberved in many CFD imulation that RANS model how inherent technology limitation
Stre-Blended Eddy Simulation (SBES) - A new Paradigm in hybrid RANS-LES Modeling Menter F.R. ANSYS Germany GmbH Introduction It i oberved in many CFD imulation that RANS model how inherent technology limitation
Source Code (C) Phantom Support Sytem Generic Front-End Compiler BB CFG Code Generation ANSI C Single-threaded Application Phantom Call Identifier AEB
 Code Partitioning for Synthei of Embedded Application with Phantom André C. Nácul, Tony Givargi Department of Computer Science Univerity of California, Irvine {nacul, givargi@ic.uci.edu ABSTRACT In a large
Code Partitioning for Synthei of Embedded Application with Phantom André C. Nácul, Tony Givargi Department of Computer Science Univerity of California, Irvine {nacul, givargi@ic.uci.edu ABSTRACT In a large
ES205 Analysis and Design of Engineering Systems: Lab 1: An Introductory Tutorial: Getting Started with SIMULINK
 ES05 Analyi and Deign of Engineering Sytem: Lab : An Introductory Tutorial: Getting Started with SIMULINK What i SIMULINK? SIMULINK i a oftware package for modeling, imulating, and analyzing dynamic ytem.
ES05 Analyi and Deign of Engineering Sytem: Lab : An Introductory Tutorial: Getting Started with SIMULINK What i SIMULINK? SIMULINK i a oftware package for modeling, imulating, and analyzing dynamic ytem.
arxiv: v1 [cs.ds] 27 Feb 2018
![arxiv: v1 [cs.ds] 27 Feb 2018 arxiv: v1 [cs.ds] 27 Feb 2018](/thumbs/94/118997120.jpg) Incremental Strong Connectivity and 2-Connectivity in Directed Graph Louka Georgiadi 1, Giueppe F. Italiano 2, and Niko Parotidi 2 arxiv:1802.10189v1 [c.ds] 27 Feb 2018 1 Univerity of Ioannina, Greece.
Incremental Strong Connectivity and 2-Connectivity in Directed Graph Louka Georgiadi 1, Giueppe F. Italiano 2, and Niko Parotidi 2 arxiv:1802.10189v1 [c.ds] 27 Feb 2018 1 Univerity of Ioannina, Greece.
Stochastic Search and Graph Techniques for MCM Path Planning Christine D. Piatko, Christopher P. Diehl, Paul McNamee, Cheryl Resch and I-Jeng Wang
 Stochatic Search and Graph Technique for MCM Path Planning Chritine D. Piatko, Chritopher P. Diehl, Paul McNamee, Cheryl Rech and I-Jeng Wang The John Hopkin Univerity Applied Phyic Laboratory, Laurel,
Stochatic Search and Graph Technique for MCM Path Planning Chritine D. Piatko, Chritopher P. Diehl, Paul McNamee, Cheryl Rech and I-Jeng Wang The John Hopkin Univerity Applied Phyic Laboratory, Laurel,
Planning of scooping position and approach path for loading operation by wheel loader
 22 nd International Sympoium on Automation and Robotic in Contruction ISARC 25 - September 11-14, 25, Ferrara (Italy) 1 Planning of cooping poition and approach path for loading operation by wheel loader
22 nd International Sympoium on Automation and Robotic in Contruction ISARC 25 - September 11-14, 25, Ferrara (Italy) 1 Planning of cooping poition and approach path for loading operation by wheel loader
ETSI TS V ( )
 TS 122 153 V14.4.0 (2017-05) TECHNICAL SPECIFICATION Digital cellular telecommunication ytem (Phae 2+) (GSM); Univeral Mobile Telecommunication Sytem (UMTS); LTE; Multimedia priority ervice (3GPP TS 22.153
TS 122 153 V14.4.0 (2017-05) TECHNICAL SPECIFICATION Digital cellular telecommunication ytem (Phae 2+) (GSM); Univeral Mobile Telecommunication Sytem (UMTS); LTE; Multimedia priority ervice (3GPP TS 22.153
Modeling the Effect of Mobile Handoffs on TCP and TFRC Throughput
 Modeling the Effect of Mobile Handoff on TCP and TFRC Throughput Antonio Argyriou and Vijay Madietti School of Electrical and Computer Engineering Georgia Intitute of Technology Atlanta, Georgia 3332 25,
Modeling the Effect of Mobile Handoff on TCP and TFRC Throughput Antonio Argyriou and Vijay Madietti School of Electrical and Computer Engineering Georgia Intitute of Technology Atlanta, Georgia 3332 25,
Today s Outline. CS 561, Lecture 23. Negative Weights. Shortest Paths Problem. The presence of a negative cycle might mean that there is
 Today Outline CS 56, Lecture Jared Saia Univerity of New Mexico The path that can be trodden i not the enduring and unchanging Path. The name that can be named i not the enduring and unchanging Name. -
Today Outline CS 56, Lecture Jared Saia Univerity of New Mexico The path that can be trodden i not the enduring and unchanging Path. The name that can be named i not the enduring and unchanging Name. -
Modeling of underwater vehicle s dynamics
 Proceeding of the 11th WEA International Conference on YTEM, Agio Nikolao, Crete Iland, Greece, July 23-25, 2007 44 Modeling of underwater vehicle dynamic ANDRZEJ ZAK Department of Radiolocation and Hydrolocation
Proceeding of the 11th WEA International Conference on YTEM, Agio Nikolao, Crete Iland, Greece, July 23-25, 2007 44 Modeling of underwater vehicle dynamic ANDRZEJ ZAK Department of Radiolocation and Hydrolocation
Diverse: Application-Layer Service Differentiation in Peer-to-Peer Communications
 Divere: Application-Layer Service Differentiation in Peer-to-Peer Communication Chuan Wu, Student Member, IEEE, Baochun Li, Senior Member, IEEE Department of Electrical and Computer Engineering Univerity
Divere: Application-Layer Service Differentiation in Peer-to-Peer Communication Chuan Wu, Student Member, IEEE, Baochun Li, Senior Member, IEEE Department of Electrical and Computer Engineering Univerity
Hierarchical Real-Time Scheduling and Synchronization
 Mälardalen University Press Licentiate Thesis No.94 Hierarchical Real-Time Scheduling and Synchronization Moris Behnam October 2008 School of Innovation, Design and Engineering Mälardalen University Västerås,
Mälardalen University Press Licentiate Thesis No.94 Hierarchical Real-Time Scheduling and Synchronization Moris Behnam October 2008 School of Innovation, Design and Engineering Mälardalen University Västerås,
Laboratory Exercise 2
 Laoratory Exercie Numer and Diplay Thi i an exercie in deigning cominational circuit that can perform inary-to-decimal numer converion and inary-coded-decimal (BCD) addition. Part I We wih to diplay on
Laoratory Exercie Numer and Diplay Thi i an exercie in deigning cominational circuit that can perform inary-to-decimal numer converion and inary-coded-decimal (BCD) addition. Part I We wih to diplay on
Nearly Constant Approximation for Data Aggregation Scheduling in Wireless Sensor Networks
 Nearly Contant Approximation for Data Aggregation Scheduling in Wirele Senor Network Scott C.-H. Huang, Peng-Jun Wan, Chinh T. Vu, Yinghu Li and France Yao Computer Science Department, City Univerity of
Nearly Contant Approximation for Data Aggregation Scheduling in Wirele Senor Network Scott C.-H. Huang, Peng-Jun Wan, Chinh T. Vu, Yinghu Li and France Yao Computer Science Department, City Univerity of
(12) Patent Application Publication (10) Pub. No.: US 2011/ A1
 (19) United State US 2011 0316690A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0316690 A1 Siegman (43) Pub. Date: Dec. 29, 2011 (54) SYSTEMAND METHOD FOR IDENTIFYING ELECTRICAL EQUIPMENT
(19) United State US 2011 0316690A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0316690 A1 Siegman (43) Pub. Date: Dec. 29, 2011 (54) SYSTEMAND METHOD FOR IDENTIFYING ELECTRICAL EQUIPMENT
Cutting Stock by Iterated Matching. Andreas Fritsch, Oliver Vornberger. University of Osnabruck. D Osnabruck.
 Cutting Stock by Iterated Matching Andrea Fritch, Oliver Vornberger Univerity of Onabruck Dept of Math/Computer Science D-4909 Onabruck andy@informatikuni-onabrueckde Abtract The combinatorial optimization
Cutting Stock by Iterated Matching Andrea Fritch, Oliver Vornberger Univerity of Onabruck Dept of Math/Computer Science D-4909 Onabruck andy@informatikuni-onabrueckde Abtract The combinatorial optimization
Shortest Path Routing in Arbitrary Networks
 Journal of Algorithm, Vol 31(1), 1999 Shortet Path Routing in Arbitrary Network Friedhelm Meyer auf der Heide and Berthold Vöcking Department of Mathematic and Computer Science and Heinz Nixdorf Intitute,
Journal of Algorithm, Vol 31(1), 1999 Shortet Path Routing in Arbitrary Network Friedhelm Meyer auf der Heide and Berthold Vöcking Department of Mathematic and Computer Science and Heinz Nixdorf Intitute,
Motion Control (wheeled robots)
 3 Motion Control (wheeled robot) Requirement for Motion Control Kinematic / dynamic model of the robot Model of the interaction between the wheel and the ground Definition of required motion -> peed control,
3 Motion Control (wheeled robot) Requirement for Motion Control Kinematic / dynamic model of the robot Model of the interaction between the wheel and the ground Definition of required motion -> peed control,
Advanced Encryption Standard and Modes of Operation
 Advanced Encryption Standard and Mode of Operation G. Bertoni L. Breveglieri Foundation of Cryptography - AES pp. 1 / 50 AES Advanced Encryption Standard (AES) i a ymmetric cryptographic algorithm AES
Advanced Encryption Standard and Mode of Operation G. Bertoni L. Breveglieri Foundation of Cryptography - AES pp. 1 / 50 AES Advanced Encryption Standard (AES) i a ymmetric cryptographic algorithm AES
Semi-Distributed Load Balancing for Massively Parallel Multicomputer Systems
 Syracue Univerity SUFAC lectrical ngineering and Computer Science echnical eport College of ngineering and Computer Science 8-1991 Semi-Ditributed Load Balancing for aively Parallel ulticomputer Sytem
Syracue Univerity SUFAC lectrical ngineering and Computer Science echnical eport College of ngineering and Computer Science 8-1991 Semi-Ditributed Load Balancing for aively Parallel ulticomputer Sytem
Multi-Target Tracking In Clutter
 Multi-Target Tracking In Clutter John N. Sander-Reed, Mary Jo Duncan, W.B. Boucher, W. Michael Dimmler, Shawn O Keefe ABSTRACT A high frame rate (0 Hz), multi-target, video tracker ha been developed and
Multi-Target Tracking In Clutter John N. Sander-Reed, Mary Jo Duncan, W.B. Boucher, W. Michael Dimmler, Shawn O Keefe ABSTRACT A high frame rate (0 Hz), multi-target, video tracker ha been developed and
Variable Resolution Discretization in the Joint Space
 Variable Reolution Dicretization in the Joint Space Chritopher K. Monon, David Wingate, and Kevin D. Seppi {c,wingated,keppi}@c.byu.edu Computer Science, Brigham Young Univerity Todd S. Peteron peterto@uvc.edu
Variable Reolution Dicretization in the Joint Space Chritopher K. Monon, David Wingate, and Kevin D. Seppi {c,wingated,keppi}@c.byu.edu Computer Science, Brigham Young Univerity Todd S. Peteron peterto@uvc.edu
Kinematics Programming for Cooperating Robotic Systems
 Kinematic Programming for Cooperating Robotic Sytem Critiane P. Tonetto, Carlo R. Rocha, Henrique Sima, Altamir Dia Federal Univerity of Santa Catarina, Mechanical Engineering Department, P.O. Box 476,
Kinematic Programming for Cooperating Robotic Sytem Critiane P. Tonetto, Carlo R. Rocha, Henrique Sima, Altamir Dia Federal Univerity of Santa Catarina, Mechanical Engineering Department, P.O. Box 476,
New Structural Decomposition Techniques for Constraint Satisfaction Problems
 New Structural Decompoition Technique for Contraint Satifaction Problem Yaling Zheng and Berthe Y. Choueiry Contraint Sytem Laboratory Univerity of Nebraka-Lincoln Email: yzheng choueiry@ce.unl.edu Abtract.
New Structural Decompoition Technique for Contraint Satifaction Problem Yaling Zheng and Berthe Y. Choueiry Contraint Sytem Laboratory Univerity of Nebraka-Lincoln Email: yzheng choueiry@ce.unl.edu Abtract.
Representations and Transformations. Objectives
 Repreentation and Tranformation Objective Derive homogeneou coordinate tranformation matrice Introduce tandard tranformation - Rotation - Tranlation - Scaling - Shear Scalar, Point, Vector Three baic element
Repreentation and Tranformation Objective Derive homogeneou coordinate tranformation matrice Introduce tandard tranformation - Rotation - Tranlation - Scaling - Shear Scalar, Point, Vector Three baic element
Contents. shortest paths. Notation. Shortest path problem. Applications. Algorithms and Networks 2010/2011. In the entire course:
 Content Shortet path Algorithm and Network 21/211 The hortet path problem: Statement Verion Application Algorithm (for ingle ource p problem) Reminder: relaxation, Dijktra, Variant of Dijktra, Bellman-Ford,
Content Shortet path Algorithm and Network 21/211 The hortet path problem: Statement Verion Application Algorithm (for ingle ource p problem) Reminder: relaxation, Dijktra, Variant of Dijktra, Bellman-Ford,
An efficient resource allocation algorithm for OFDMA cooperative relay networks with fairness and QoS guaranteed
 Univerity of Wollongong Reearch Online Faculty of Informatic - Paper (Archive) Faculty of Engineering and Information Science 200 An efficient reource allocation algorithm for OFDMA cooperative relay network
Univerity of Wollongong Reearch Online Faculty of Informatic - Paper (Archive) Faculty of Engineering and Information Science 200 An efficient reource allocation algorithm for OFDMA cooperative relay network
A Study of a Variable Compression Ratio and Displacement Mechanism Using Design of Experiments Methodology
 A Study of a Variable Compreion Ratio and Diplacement Mechanim Uing Deign of Experiment Methodology Shugang Jiang, Michael H. Smith, Maanobu Takekohi Abtract Due to the ever increaing requirement for engine
A Study of a Variable Compreion Ratio and Diplacement Mechanim Uing Deign of Experiment Methodology Shugang Jiang, Michael H. Smith, Maanobu Takekohi Abtract Due to the ever increaing requirement for engine
Implementation of a momentum-based distance metric for motion graphs. Student: Alessandro Di Domenico (st.no ), Supervisor: Nicolas Pronost
 Implementation of a momentum-baed ditance metric for motion graph Student: Aleandro Di Domenico (t.no 3775682), Supervior: Nicola Pronot April 3, 2014 Abtract Thi report preent the procedure and reult
Implementation of a momentum-baed ditance metric for motion graph Student: Aleandro Di Domenico (t.no 3775682), Supervior: Nicola Pronot April 3, 2014 Abtract Thi report preent the procedure and reult
Floating Point CORDIC Based Power Operation
 Floating Point CORDIC Baed Power Operation Kazumi Malhan, Padmaja AVL Electrical and Computer Engineering Department School of Engineering and Computer Science Oakland Univerity, Rocheter, MI e-mail: kmalhan@oakland.edu,
Floating Point CORDIC Baed Power Operation Kazumi Malhan, Padmaja AVL Electrical and Computer Engineering Department School of Engineering and Computer Science Oakland Univerity, Rocheter, MI e-mail: kmalhan@oakland.edu,
Multiclass Road Sign Detection using Multiplicative Kernel
 Proceeding of the Croatian Computer Viion Workhop, Year 1 Multicla Road Sign Detection uing Multiplicative Kernel Valentina Zadrija Mireo d. d. Zagreb, Croatia valentina.zadrija@mireo.hr Siniša Šegvić
Proceeding of the Croatian Computer Viion Workhop, Year 1 Multicla Road Sign Detection uing Multiplicative Kernel Valentina Zadrija Mireo d. d. Zagreb, Croatia valentina.zadrija@mireo.hr Siniša Šegvić
Computer Arithmetic Homework Solutions. 1 An adder for graphics. 2 Partitioned adder. 3 HDL implementation of a partitioned adder
 Computer Arithmetic Homework 3 2016 2017 Solution 1 An adder for graphic In a normal ripple carry addition of two poitive number, the carry i the ignal for a reult exceeding the maximum. We ue thi ignal
Computer Arithmetic Homework 3 2016 2017 Solution 1 An adder for graphic In a normal ripple carry addition of two poitive number, the carry i the ignal for a reult exceeding the maximum. We ue thi ignal
Maneuverable Relays to Improve Energy Efficiency in Sensor Networks
 Maneuverable Relay to Improve Energy Efficiency in Senor Network Stephan Eidenbenz, Luka Kroc, Jame P. Smith CCS-5, MS M997; Lo Alamo National Laboratory; Lo Alamo, NM 87545. Email: {eidenben, kroc, jpmith}@lanl.gov
Maneuverable Relay to Improve Energy Efficiency in Senor Network Stephan Eidenbenz, Luka Kroc, Jame P. Smith CCS-5, MS M997; Lo Alamo National Laboratory; Lo Alamo, NM 87545. Email: {eidenben, kroc, jpmith}@lanl.gov
On combining Learning Vector Quantization and the Bayesian classifiers for natural textured images
 On combining Learning Vector Quantization and the Bayeian claifier for natural textured image María Guiarro Dept. Ingeniería del Software e Inteligencia Artificial Facultad Informática Univeridad Complutene
On combining Learning Vector Quantization and the Bayeian claifier for natural textured image María Guiarro Dept. Ingeniería del Software e Inteligencia Artificial Facultad Informática Univeridad Complutene
Delaunay Triangulation: Incremental Construction
 Chapter 6 Delaunay Triangulation: Incremental Contruction In the lat lecture, we have learned about the Lawon ip algorithm that compute a Delaunay triangulation of a given n-point et P R 2 with O(n 2 )
Chapter 6 Delaunay Triangulation: Incremental Contruction In the lat lecture, we have learned about the Lawon ip algorithm that compute a Delaunay triangulation of a given n-point et P R 2 with O(n 2 )
Joint Congestion Control and Media Access Control Design for Ad Hoc Wireless Networks
 Joint Congetion Control and Media Acce Control Deign for Ad Hoc Wirele Network Lijun Chen, Steven H. Low and John C. Doyle Engineering & Applied Science Diviion, California Intitute of Technology Paadena,
Joint Congetion Control and Media Acce Control Deign for Ad Hoc Wirele Network Lijun Chen, Steven H. Low and John C. Doyle Engineering & Applied Science Diviion, California Intitute of Technology Paadena,
The norm Package. November 15, Title Analysis of multivariate normal datasets with missing values
 The norm Package November 15, 2003 Verion 1.0-9 Date 2002/05/06 Title Analyi of multivariate normal dataet with miing value Author Ported to R by Alvaro A. Novo . Original by Joeph
The norm Package November 15, 2003 Verion 1.0-9 Date 2002/05/06 Title Analyi of multivariate normal dataet with miing value Author Ported to R by Alvaro A. Novo . Original by Joeph
999 Computer System Network. (12) Patent Application Publication (10) Pub. No.: US 2006/ A1. (19) United States
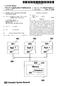 (19) United State US 2006O1296.60A1 (12) Patent Application Publication (10) Pub. No.: Mueller et al. (43) Pub. Date: Jun. 15, 2006 (54) METHOD AND COMPUTER SYSTEM FOR QUEUE PROCESSING (76) Inventor: Wolfgang
(19) United State US 2006O1296.60A1 (12) Patent Application Publication (10) Pub. No.: Mueller et al. (43) Pub. Date: Jun. 15, 2006 (54) METHOD AND COMPUTER SYSTEM FOR QUEUE PROCESSING (76) Inventor: Wolfgang
3D SMAP Algorithm. April 11, 2012
 3D SMAP Algorithm April 11, 2012 Baed on the original SMAP paper [1]. Thi report extend the tructure of MSRF into 3D. The prior ditribution i modified to atify the MRF property. In addition, an iterative
3D SMAP Algorithm April 11, 2012 Baed on the original SMAP paper [1]. Thi report extend the tructure of MSRF into 3D. The prior ditribution i modified to atify the MRF property. In addition, an iterative
