Keywords Cloud Computing, Service Level Agreements (SLA), CloudSim, Monitoring & Controlling SLA Agent, JADE
|
|
|
- Christian Allison
- 5 years ago
- Views:
Transcription
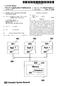
1 Volume 5, Iue 8, Augut 2015 ISSN: X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: Verification of Agent Baed Sytem for Monitoring and Controlling SLA in CloudSim Sarwan Singh Reearch Scholar, Sai Nath Univerity, Jharkhand, India Manih Arora Joint Director (Sytem) NIELIT, Chandigarh, India Abtract Cloud computing i an on-demand computing model where Cloud uer pay in per uage mode. Cloud uer avail ervice and Cloud ervice provider provide ervice. The ervice are provided on mutually agreed term and condition called Service Level Agreement (SLA). Thee term and condition are to be monitored during runtime to avoid any breach of trut between Cloud uer and Cloud ervice provider. A oftware agent baed monitoring tool i implemented and verified to monitor the SLA parameter that include reource being allocated during runtime and compare runtime value with the agreed parameter value. Thi paper preent the verification agent developed for Monitoring and controlling SLA, MACSLA. The working of agent i verified uing CloudSim where three virtual machine run. The agent generate alert in cae of any violation of reource allocation. Thi will help both Cloud Service Provider and Cloud uer in maintaining trut in the Cloud ervice being offered. Keyword Cloud Computing, Service Level Agreement (SLA), CloudSim, Monitoring & Controlling SLA Agent, JADE I. INTRODUCTION Cloud computing i an eential utility in today computing world. In thi on-demand computing model reource are made available on pay per ue bai, where trut between the Cloud uer and Cloud ervice provider i maintained by Service Level Agreement (SLA). Any violation in SLA parameter will impact the trut between the two. At runtime variou SLA parameter like RAM, Bandwidth MIPS, etc. aigned to Virtual Machine (VM) are monitored by a dynamic agent baed ytem [1] and alert are generated for any violation noted during run time. The agent baed ytem for monitoring and controlling SLA i implemented uing JADE and CloudSim with back end upport databae, MySQL. It i difficult to analye the performance of agent in actual environment, a it involve uage of hared reource with lot of Hardware. Thu imulation tool are becoming important and neceary for evaluation of Cloud computing model and agent baed model for calculating efficiency, reliability and performance. The verification of an agent i very important to acertain that the deign of agent i a per the requirement and it i performing the deired tak optimally. The verification proce of the agent require different tet cae. In view of thi, different tet cae have been identified and ued in verifying the working of agent for the purpoe of monitoring and controlling Multi level SLA. The paper ha been organized into five ection; ection II review the background and related reearch, ection III brief the verification approach, ection IV doe the analyi of output, followed by the concluion and cope for future work in ection V. II. BACKGROUND & RELATED RESEARCH a) Monitoring and Controlling SLA uing Agent Service Level Agreement (SLA) i an important document of agreement which maintain the trut relationhip between Cloud ervice provider and Cloud uer. Thi not only decribe variou SLA parameter wherea guarantee them with remedial action in cae of violation. For thi caue a oftware Agent baed methodology prove beneficial, and hence agent baed Monitoring and Controlling SLA (MACSLA) i modelled [2] [3]. The Monitoring and Controlling Agent (MCA) which orchetrate the whole proce and provide graphical interface to Cloud Adminitrator/Uer. The MCA ha two main procee underneath i.e. Term Collector (TC) and Term Monitor(TM). The main job of Term Collector (TC) i to collect agreed SLA parameter and their predeigned value from the databae. On the other hand, Term Monitor(TM) will collect SLA parameter value while Virtual Machine (VM) i running. The MCA will compare the value collected by TC & TM and generate alert accordingly. The databae which tore the pre-deigned/prenegotiated SLA parameter value i implemented uing MySQL databae [4]. b) Implementation of MACSLA Agent MACSLA agent i implemented uing Cloud imulation tool, CloudSim. CloudSim i a framework which allow, modelling, imulation and experimentation with the Cloud computing infratructure model [5]. The high level architecture of variou entitie involved in CloudSim i hown in Figure 1. The Cloud uer end the ervice requet to 2015, IJARCSSE All Right Reerved Page 926
2 Singh et al., International Journal of Advanced Reearch in Computer Science and Software Engineering 5(8), Augut- 2015, pp Data Center Borker which coordinate with Cloud Controller to create intance of Hot in DataCenter. Cloud Controller may coordinate more than one Data Center. Hot ha multiple VM running over it with different number of Cloudlet. Figure 1 : Architecture of variou entitie in CloudSim There are many clae like Cloudlet, Hot, Virtual Machine, etc. in CloudSim which erve a building block of CloudSim imulator. In MACSLA, clae available with CloudSim imulator are extended to experiment the violation of SLA. Commonly ued clae are dicued below: 1) Cloudlet: Thi cla model the Cloud-baed application, repreenting pre-aigned intruction length and amount of data tranfer. According to the load aigned to Cloudlet, it take time to complete it computational tak. 2) Data Centre: In a Cloud computing environment the infratructure level ervice offered by Cloud ervice provider are modelled by thi cla. Thi cla i ued to implement variou policie for allocation of bandwidth, memory, and torage device. 3) Data Center Broker: Thi cla mediate between uer and Cloud ervice provider depending on uer Quality of Service (QoS) requirement. Thi cla i ued to experiment application placement policie. 4) Hot: Thi cla repreent a phyical machine with memory, torage, number of core, etc. 5) Virtual Machine: Thi cla model an intance of a VM, which run on Hot, along with other VM (i any). Every VM ha it own memory, torage, proceor, etc along with proviioning policie. III. VERIFICATION OF MACSLA The implemented MACSLA i required to be verified for it functionality. The verification include identification of tet cae, generation of tet data and verification the functionality of agent implemented. The implemented agent i verified by integrating in imulator, CloudSim. The verification tep are detailed below : i) Identification of Tet Cae For the verification purpoe three Virtual Machine (VM) are created and deployed on two Hot. The configuration of VM and Hot are decribed in Table 1. Table 1: configuration detail of Virtual Machine and Hot Hot1 VM1 VM2 VM3 RAM (MB) Core MIPS Bandwidth 1,00,000 1,00,000 1,00,000 Hot2 RAM (MB) Core 2 2 MIPS Bandwidth 10,00,000 10,00,000 Baed on VM and Hot, eight tet cae are identified to verify MACSLA. The outcome of each tet cae would be either no violation or violation. The load i varied in each tet cae to know the outcome. The eight different tet cae and their outcome decribed in Table 2: Table 2 : Tet cae for three Virtual Machine Tet Cae VM1 VM2 VM3 1 Normal Load Normal Load Normal Load No SLA Violation No SLA Violation No SLA Violation 2 Over Load Normal Load Normal Load SLA Violation No SLA Violation No SLA Violation 2015, IJARCSSE All Right Reerved Page 927
3 Singh et al., International Journal of Advanced Reearch in Computer Science and Software Engineering 5(8), Augut- 2015, pp Normal Load Over Load Normal Load 3 No SLA Violation SLA Violation No SLA Violation Normal Load Normal Load Over Load 4 No SLA Violation No SLA Violation SLA Violation Over Load Over Load Normal Load 5 SLA Violation SLA Violation No SLA Violation Over Load Normal Load Over Load 6 SLA Violation No SLA Violation SLA Violation Normal Load Over Load Over Load 7 No SLA Violation SLA Violation SLA Violation Over Load Over Load Over Load 8 SLA Violation SLA Violation SLA Violation ii) Tet Data The tet data i generated in view of tet cae identified and deired outcome. The tet data i generated i uch a way that it hould fall in one of tet cae identified. The tet data generated (randomly) hown in Table 3 including the load on each virtual machine in the form of cloudlet. Table 3 : Tet data for each VM in different Tet Cae Tet Cae VM1 VM2 VM3 Remark (cloudlet count) (cloudlet count) (cloudlet count) No violation Violation in VM Violation in VM Violation in VM Violation in VM1 and VM Violation in VM1 and VM Violation in VM2 and VM Violation in VM1, VM2 & VM3 iii) Verifying Functionality of Agent The MACSLA agent [6] during runtime aign the Cloudlet to the Virtual Machine(VM).The code nippet to aign cloudlet to VM i given in Table 4. Table 4: java code nippet to aign cloudlet to VM // etcloudlettovm(cloudletlit, VMID, tart offet in cloudletlit, // end offet in cloudletlit); etcloudlettovm(cloudletlit, 1, 1, 7); etcloudlettovm(cloudletlit, 3, 8, 12); etcloudlettovm(cloudletlit, 2, 13, 15); The load on VM 1 i increaed by aigning more than 7 cloudlet a hown in the code nippet in Table 5. Table 5: java code nippet to aign cloudlet to VM // etcloudlettovm(cloudletlit, VMID, tart offet in cloudletlit, // end offet in cloudletlit); etcloudlettovm(cloudletlit, 1, 1, 7); etcloudlettovm(cloudletlit, 3, 8, 12); etcloudlettovm(cloudletlit, 2, 13, 15); etcloudlettovm(cloudletlit, 1, 16, 24); IV. ANALYZING THE OUTPUT The output after applying tet data for Tet Cae 1 i analyed. The cloudlet aigned to each of the VM are given in Figure 2. Under thi cenario, none of the VM violate the agreed SLA parameter. The Figure 2 ha three graph w.r.t time for each VM. The firt graph i for RAM v Timetamp, econd i for Mip v Timetamp and third i Bw v Timetamp. Each graph ha two parameter plotted, one repreenting agreed SLA parameter and other for SLA parameter being allocated to VM on runtime. 2015, IJARCSSE All Right Reerved Page 928
4 Singh et al., International Journal of Advanced Reearch in Computer Science and Software Engineering 5(8), Augut- 2015, pp Virtual Machine 1 Virtual Machine 2 Virtual Machine 3 No. Of cloudlet aigned 7 No. of cloudlet aigned 3 No. of cloudlet aigned 5 Figure 2 : Tet cae 1- VM1, VM2,VM3 are not violating SLA Later, the load in VM1 i increaed to verify Tet Cae 2. The effect of aigning 9 more cloudlet are depicted in Figure 3. The VM2 and VM3 ha ame load/cloudlet running on them, therefore SLA i not violated and remain a before. Figure 3 : Tet cae 2 VM1 violate the SLA Similarly, load on VM are increaed a per the Tet Cae and further reult are analyed a hown in the Figure 4. All the VM tart violating the SLA. Virtual Machine 1 No. Of cloudlet aigned 13 Virtual Machine 2 No. of cloudlet aigned 12 Virtual Machine 3 No. of cloudlet aigned , IJARCSSE All Right Reerved Page 929
5 Load / Cloudl et Load / Cloudl et Load / Cloudl et Singh et al., International Journal of Advanced Reearch in Computer Science and Software Engineering 5(8), Augut- 2015, pp Figure 4 : Tet cae 8-VM1, VM2,VM3 are violating SLA The uer interface created in JADE [7] a hown in Figure 5 prompt the variou SLA parameter value being collected by Term Monitor(TM) and compare it with deired value aved in databae by Term Collector (TC). The column howing Required Value i aved in databae by TC, the Demanded Value i aved in databae by TM and if any violation the third column how true along with background color changing to red, otherwie it how fale with white background. Figure 5 : Agent UI developed in JADE The eight tet cae identified are verified in the imulated environment uing CloudSim. It i found that the SLA violation take place with increae in load on Virtual Machine in context to parameter under obervation like RAM, MIPS, and Bandwidth. The complete reult for all the tet cae with load/cloudlet being aigned to each VM i hown in Table 6. Tet Cae Table 6 : Reult of SLA violation in different tet cae for three Virtual Machine VM1 VM2 VM3 SLA Violation SLA Violation SLA Violation RAM MIPS Bandwidth RAM MIPS Bandwidth RAM MIPS Bandwidth 1 7 No No No 3 No No No 5 No No No No No No 5 No No No 3 7 No No No No No No 3 No No No , IJARCSSE All Right Reerved Page No No No No No No No No No 5 No No No 12 10
6 Singh et al., International Journal of Advanced Reearch in Computer Science and Software Engineering 5(8), Augut- 2015, pp V. CONCLUSION The Monitoring And Controlling SLA (MACSLA) ha proved that any violation in SLA i highlighted a well a recorded in databae which aure Cloud uer that he i getting what ha been demanded and maintain trut relationhip between Cloud uer and Cloud ervice provider. REFERENCES [1] Sarwan Singh, Manih Arora, Implementation of Agent Baed Sytem for Monitoring and Controlling SLA in Cloud Environment, IJEBEA, Augut 2015 [2] Sarwan Singh, Manih Arora, Deign of Agent Baed Sytem for Monitoring and Controlling SLA in Cloud Environment, IJATES, Volume No 03, Special Iue No. 01, March 2015 [3] L. Taquier, S. Venticinque, R. Avera, and B. Di, Agent Baed Application Tool for Cloud Proviioning and Management, 3rd International Conference on Cloud Computing (CLOUDCOMP 2012), Wien, Autria, September 24 26, 2012 [4] MySQL, Available at acceed on Augut 16, 2015 [5] Rajkumar Buyya, Rajiv Ranjan, Rodrigo N. Calheiro Modeling and Simulation of Scalable Cloud Computing Environment and the CloudSim Toolkit: Challenge and Opportunitie, {raj, rodrigoc}@ce.unimelb.edu.au, rajiv@unw.edu.au [6] K. M. Sim, Agent-baed Cloud Computing, IEEE Tranaction On Service Computing, Vol.5, No.4, pp.564,577, Fourth Quarter [7] Java Agent Development Framework, Available at acceed on Augut 16, , IJARCSSE All Right Reerved Page 931
International Association of Scientific Innovation and Research (IASIR) (An Association Unifying the Sciences, Engineering, and Applied Research)
 International Association of Scientific Innovation and Research (IASIR) (An Association Unifying the Sciences, Engineering, and Applied Research) International Journal of Engineering, Business and Enterprise
International Association of Scientific Innovation and Research (IASIR) (An Association Unifying the Sciences, Engineering, and Applied Research) International Journal of Engineering, Business and Enterprise
Laboratory Exercise 6
 Laboratory Exercie 6 Adder, Subtractor, and Multiplier The purpoe of thi exercie i to examine arithmetic circuit that add, ubtract, and multiply number. Each type of circuit will be implemented in two
Laboratory Exercie 6 Adder, Subtractor, and Multiplier The purpoe of thi exercie i to examine arithmetic circuit that add, ubtract, and multiply number. Each type of circuit will be implemented in two
Key Terms - MinMin, MaxMin, Sufferage, Task Scheduling, Standard Deviation, Load Balancing.
 Volume 3, Iue 11, November 2013 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Tak Aignment in
Volume 3, Iue 11, November 2013 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Tak Aignment in
Analyzing Hydra Historical Statistics Part 2
 Analyzing Hydra Hitorical Statitic Part Fabio Maimo Ottaviani EPV Technologie White paper 5 hnode HSM Hitorical Record The hnode i the hierarchical data torage management node and ha to perform all the
Analyzing Hydra Hitorical Statitic Part Fabio Maimo Ottaviani EPV Technologie White paper 5 hnode HSM Hitorical Record The hnode i the hierarchical data torage management node and ha to perform all the
Distributed Packet Processing Architecture with Reconfigurable Hardware Accelerators for 100Gbps Forwarding Performance on Virtualized Edge Router
 Ditributed Packet Proceing Architecture with Reconfigurable Hardware Accelerator for 100Gbp Forwarding Performance on Virtualized Edge Router Satohi Nihiyama, Hitohi Kaneko, and Ichiro Kudo Abtract To
Ditributed Packet Proceing Architecture with Reconfigurable Hardware Accelerator for 100Gbp Forwarding Performance on Virtualized Edge Router Satohi Nihiyama, Hitohi Kaneko, and Ichiro Kudo Abtract To
DAROS: Distributed User-Server Assignment And Replication For Online Social Networking Applications
 DAROS: Ditributed Uer-Server Aignment And Replication For Online Social Networking Application Thuan Duong-Ba School of EECS Oregon State Univerity Corvalli, OR 97330, USA Email: duongba@eec.oregontate.edu
DAROS: Ditributed Uer-Server Aignment And Replication For Online Social Networking Application Thuan Duong-Ba School of EECS Oregon State Univerity Corvalli, OR 97330, USA Email: duongba@eec.oregontate.edu
AUTOMATIC TEST CASE GENERATION USING UML MODELS
 Volume-2, Iue-6, June-2014 AUTOMATIC TEST CASE GENERATION USING UML MODELS 1 SAGARKUMAR P. JAIN, 2 KHUSHBOO S. LALWANI, 3 NIKITA K. MAHAJAN, 4 BHAGYASHREE J. GADEKAR 1,2,3,4 Department of Computer Engineering,
Volume-2, Iue-6, June-2014 AUTOMATIC TEST CASE GENERATION USING UML MODELS 1 SAGARKUMAR P. JAIN, 2 KHUSHBOO S. LALWANI, 3 NIKITA K. MAHAJAN, 4 BHAGYASHREE J. GADEKAR 1,2,3,4 Department of Computer Engineering,
Service and Network Management Interworking in Future Wireless Systems
 Service and Network Management Interworking in Future Wirele Sytem V. Tountopoulo V. Stavroulaki P. Demeticha N. Mitrou and M. Theologou National Technical Univerity of Athen Department of Electrical Engineering
Service and Network Management Interworking in Future Wirele Sytem V. Tountopoulo V. Stavroulaki P. Demeticha N. Mitrou and M. Theologou National Technical Univerity of Athen Department of Electrical Engineering
SLA Adaptation for Service Overlay Networks
 SLA Adaptation for Service Overlay Network Con Tran 1, Zbigniew Dziong 1, and Michal Pióro 2 1 Department of Electrical Engineering, École de Technologie Supérieure, Univerity of Quebec, Montréal, Canada
SLA Adaptation for Service Overlay Network Con Tran 1, Zbigniew Dziong 1, and Michal Pióro 2 1 Department of Electrical Engineering, École de Technologie Supérieure, Univerity of Quebec, Montréal, Canada
Architecture and grid application of cluster computing system
 Architecture and grid application of cluter computing ytem Yi Lv*, Shuiqin Yu, Youju Mao Intitute of Optical Fiber Telecom, Chongqing Univ. of Pot & Telecom, Chongqing, 400065, P.R.China ABSTRACT Recently,
Architecture and grid application of cluter computing ytem Yi Lv*, Shuiqin Yu, Youju Mao Intitute of Optical Fiber Telecom, Chongqing Univ. of Pot & Telecom, Chongqing, 400065, P.R.China ABSTRACT Recently,
The Association of System Performance Professionals
 The Aociation of Sytem Performance Profeional The Computer Meaurement Group, commonly called CMG, i a not for profit, worldwide organization of data proceing profeional committed to the meaurement and
The Aociation of Sytem Performance Profeional The Computer Meaurement Group, commonly called CMG, i a not for profit, worldwide organization of data proceing profeional committed to the meaurement and
Laboratory Exercise 6
 Laboratory Exercie 6 Adder, Subtractor, and Multiplier a a The purpoe of thi exercie i to examine arithmetic circuit that add, ubtract, and multiply number. Each b c circuit will be decribed in Verilog
Laboratory Exercie 6 Adder, Subtractor, and Multiplier a a The purpoe of thi exercie i to examine arithmetic circuit that add, ubtract, and multiply number. Each b c circuit will be decribed in Verilog
A Basic Prototype for Enterprise Level Project Management
 A Baic Prototype for Enterprie Level Project Management Saurabh Malgaonkar, Abhay Kolhe Computer Engineering Department, Mukeh Patel School of Technology Management & Engineering, NMIMS Univerity, Mumbai,
A Baic Prototype for Enterprie Level Project Management Saurabh Malgaonkar, Abhay Kolhe Computer Engineering Department, Mukeh Patel School of Technology Management & Engineering, NMIMS Univerity, Mumbai,
ISSN: (Online) Volume 3, Issue 4, April 2015 International Journal of Advance Research in Computer Science and Management Studies
 ISSN: 2321-7782 (Online) Volume 3, Iue 4, April 2015 International Journal Advance Reearch in Computer Science and Management Studie Reearch Article / Survey Paper / Cae Study Available online at: www.ijarcm.com
ISSN: 2321-7782 (Online) Volume 3, Iue 4, April 2015 International Journal Advance Reearch in Computer Science and Management Studie Reearch Article / Survey Paper / Cae Study Available online at: www.ijarcm.com
ESRP Storage Program EMC VNXe3100 (500 User) Mailbox Resiliency Storage Solution for Microsoft Exchange 2010
 ESRP Stor Program EMC VNXe31 (5 Uer) Mailbox Reilie Stor Solution for Microoft Exchan 21 Teted with: ESRP Stor Verion 3. Teted Date: 4/25/211 EMC Corporation Corporate Headquarter Hopkinton, MA 1748-913
ESRP Stor Program EMC VNXe31 (5 Uer) Mailbox Reilie Stor Solution for Microoft Exchan 21 Teted with: ESRP Stor Verion 3. Teted Date: 4/25/211 EMC Corporation Corporate Headquarter Hopkinton, MA 1748-913
Floating Point CORDIC Based Power Operation
 Floating Point CORDIC Baed Power Operation Kazumi Malhan, Padmaja AVL Electrical and Computer Engineering Department School of Engineering and Computer Science Oakland Univerity, Rocheter, MI e-mail: kmalhan@oakland.edu,
Floating Point CORDIC Baed Power Operation Kazumi Malhan, Padmaja AVL Electrical and Computer Engineering Department School of Engineering and Computer Science Oakland Univerity, Rocheter, MI e-mail: kmalhan@oakland.edu,
ETSI TS V ( )
 TS 122 153 V14.4.0 (2017-05) TECHNICAL SPECIFICATION Digital cellular telecommunication ytem (Phae 2+) (GSM); Univeral Mobile Telecommunication Sytem (UMTS); LTE; Multimedia priority ervice (3GPP TS 22.153
TS 122 153 V14.4.0 (2017-05) TECHNICAL SPECIFICATION Digital cellular telecommunication ytem (Phae 2+) (GSM); Univeral Mobile Telecommunication Sytem (UMTS); LTE; Multimedia priority ervice (3GPP TS 22.153
mapping reult. Our experiment have revealed that for many popular tream application, uch a networking and multimedia application, the number of VC nee
 Reolving Deadlock for Pipelined Stream Application on Network-on-Chip Xiaohang Wang 1,2, Peng Liu 1 1 Department of Information Science and Electronic Engineering, Zheiang Univerity Hangzhou, Zheiang,
Reolving Deadlock for Pipelined Stream Application on Network-on-Chip Xiaohang Wang 1,2, Peng Liu 1 1 Department of Information Science and Electronic Engineering, Zheiang Univerity Hangzhou, Zheiang,
SCHEDULE DOCUMENT CONNECT MPLS SERVICES PUBLIC NODE4 LIMITED 17/07/2017
 SCHEDULE DOCUMENT CONNECT MPLS SERVICES PUBLIC NODE4 LIMITED 17/07/017 SCHEDULE DOCUMENT CONNECT MPLS SERVICES Additional term, Service Decription & Service Level Agreement for ConnectMPLS Service 1. SERVICE
SCHEDULE DOCUMENT CONNECT MPLS SERVICES PUBLIC NODE4 LIMITED 17/07/017 SCHEDULE DOCUMENT CONNECT MPLS SERVICES Additional term, Service Decription & Service Level Agreement for ConnectMPLS Service 1. SERVICE
999 Computer System Network. (12) Patent Application Publication (10) Pub. No.: US 2006/ A1. (19) United States
 (19) United State US 2006O1296.60A1 (12) Patent Application Publication (10) Pub. No.: Mueller et al. (43) Pub. Date: Jun. 15, 2006 (54) METHOD AND COMPUTER SYSTEM FOR QUEUE PROCESSING (76) Inventor: Wolfgang
(19) United State US 2006O1296.60A1 (12) Patent Application Publication (10) Pub. No.: Mueller et al. (43) Pub. Date: Jun. 15, 2006 (54) METHOD AND COMPUTER SYSTEM FOR QUEUE PROCESSING (76) Inventor: Wolfgang
Universität Augsburg. Institut für Informatik. Approximating Optimal Visual Sensor Placement. E. Hörster, R. Lienhart.
 Univerität Augburg à ÊÇÅÍÆ ËÀǼ Approximating Optimal Viual Senor Placement E. Hörter, R. Lienhart Report 2006-01 Januar 2006 Intitut für Informatik D-86135 Augburg Copyright c E. Hörter, R. Lienhart Intitut
Univerität Augburg à ÊÇÅÍÆ ËÀǼ Approximating Optimal Viual Senor Placement E. Hörter, R. Lienhart Report 2006-01 Januar 2006 Intitut für Informatik D-86135 Augburg Copyright c E. Hörter, R. Lienhart Intitut
Refining SIRAP with a Dedicated Resource Ceiling for Self-Blocking
 Refining SIRAP with a Dedicated Reource Ceiling for Self-Blocking Mori Behnam, Thoma Nolte Mälardalen Real-Time Reearch Centre P.O. Box 883, SE-721 23 Väterå, Sweden {mori.behnam,thoma.nolte}@mdh.e ABSTRACT
Refining SIRAP with a Dedicated Reource Ceiling for Self-Blocking Mori Behnam, Thoma Nolte Mälardalen Real-Time Reearch Centre P.O. Box 883, SE-721 23 Väterå, Sweden {mori.behnam,thoma.nolte}@mdh.e ABSTRACT
Laboratory Exercise 1
 Laboratory Eercie Switche, Light, and Multipleer The purpoe of thi eercie i to learn how to connect iple input and output device to an FPGA chip and ipleent a circuit that ue thee device. We will ue the
Laboratory Eercie Switche, Light, and Multipleer The purpoe of thi eercie i to learn how to connect iple input and output device to an FPGA chip and ipleent a circuit that ue thee device. We will ue the
Laboratory Exercise 6
 Laboratory Exercie 6 Adder, Subtractor, and Multiplier The purpoe of thi exercie i to examine arithmetic circuit that add, ubtract, and multiply number. Each circuit will be decribed in Verilog and implemented
Laboratory Exercie 6 Adder, Subtractor, and Multiplier The purpoe of thi exercie i to examine arithmetic circuit that add, ubtract, and multiply number. Each circuit will be decribed in Verilog and implemented
Laboratory Exercise 6
 Laboratory Exercie 6 Adder, Subtractor, and Multiplier The purpoe of thi exercie i to examine arithmetic circuit that add, ubtract, and multiply number. Each circuit will be decribed in VHL and implemented
Laboratory Exercie 6 Adder, Subtractor, and Multiplier The purpoe of thi exercie i to examine arithmetic circuit that add, ubtract, and multiply number. Each circuit will be decribed in VHL and implemented
Dynamically Reconfigurable Neuron Architecture for the Implementation of Self- Organizing Learning Array
 Dynamically Reconfigurable Neuron Architecture for the Implementation of Self- Organizing Learning Array Januz A. Starzyk,Yongtao Guo, and Zhineng Zhu School of Electrical Engineering & Computer Science
Dynamically Reconfigurable Neuron Architecture for the Implementation of Self- Organizing Learning Array Januz A. Starzyk,Yongtao Guo, and Zhineng Zhu School of Electrical Engineering & Computer Science
Image authentication and tamper detection using fragile watermarking in spatial domain
 International Journal of Advanced Reearch in Computer Engineering & Technology (IJARCET) Volume 6, Iue 7, July 2017, ISSN: 2278 1323 Image authentication and tamper detection uing fragile watermarking
International Journal of Advanced Reearch in Computer Engineering & Technology (IJARCET) Volume 6, Iue 7, July 2017, ISSN: 2278 1323 Image authentication and tamper detection uing fragile watermarking
SIMIT 7. Component Type Editor (CTE) User manual. Siemens Industrial
 SIMIT 7 Component Type Editor (CTE) Uer manual Siemen Indutrial Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult
SIMIT 7 Component Type Editor (CTE) Uer manual Siemen Indutrial Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult
Edits in Xylia Validity Preserving Editing of XML Documents
 dit in Xylia Validity Preerving diting of XML Document Pouria Shaker, Theodore S. Norvell, and Denni K. Peter Faculty of ngineering and Applied Science, Memorial Univerity of Newfoundland, St. John, NFLD,
dit in Xylia Validity Preerving diting of XML Document Pouria Shaker, Theodore S. Norvell, and Denni K. Peter Faculty of ngineering and Applied Science, Memorial Univerity of Newfoundland, St. John, NFLD,
Integration of Digital Test Tools to the Internet-Based Environment MOSCITO
 Integration of Digital Tet Tool to the Internet-Baed Environment MOSCITO Abtract Current paper decribe a new environment MOSCITO for providing acce to tool over the internet. The environment i built according
Integration of Digital Tet Tool to the Internet-Baed Environment MOSCITO Abtract Current paper decribe a new environment MOSCITO for providing acce to tool over the internet. The environment i built according
Laboratory Exercise 2
 Laoratory Exercie Numer and Diplay Thi i an exercie in deigning cominational circuit that can perform inary-to-decimal numer converion and inary-coded-decimal (BCD) addition. Part I We wih to diplay on
Laoratory Exercie Numer and Diplay Thi i an exercie in deigning cominational circuit that can perform inary-to-decimal numer converion and inary-coded-decimal (BCD) addition. Part I We wih to diplay on
(12) Patent Application Publication (10) Pub. No.: US 2003/ A1
 US 2003O196031A1 (19) United State (12) Patent Application Publication (10) Pub. No.: US 2003/0196031 A1 Chen (43) Pub. Date: Oct. 16, 2003 (54) STORAGE CONTROLLER WITH THE DISK Related U.S. Application
US 2003O196031A1 (19) United State (12) Patent Application Publication (10) Pub. No.: US 2003/0196031 A1 Chen (43) Pub. Date: Oct. 16, 2003 (54) STORAGE CONTROLLER WITH THE DISK Related U.S. Application
ESRP Storage Program EMC Celerra NX4 (500 User) Mailbox Resiliency Storage Solution for Microsoft Exchange 2010
 ESRP Stor Program EMC Celerra NX4 (5 Uer) Mailbox Reilie Stor Solution for Microoft Exchan 21 Teted with: ESRP Stor Verion. Teted Date: 6/25/21 EMC Corporation Corporate Headquarter Hopkinton, MA 1748-91
ESRP Stor Program EMC Celerra NX4 (5 Uer) Mailbox Reilie Stor Solution for Microoft Exchan 21 Teted with: ESRP Stor Verion. Teted Date: 6/25/21 EMC Corporation Corporate Headquarter Hopkinton, MA 1748-91
Kinematics Programming for Cooperating Robotic Systems
 Kinematic Programming for Cooperating Robotic Sytem Critiane P. Tonetto, Carlo R. Rocha, Henrique Sima, Altamir Dia Federal Univerity of Santa Catarina, Mechanical Engineering Department, P.O. Box 476,
Kinematic Programming for Cooperating Robotic Sytem Critiane P. Tonetto, Carlo R. Rocha, Henrique Sima, Altamir Dia Federal Univerity of Santa Catarina, Mechanical Engineering Department, P.O. Box 476,
The development of the South African ehealth Strategy assessed against the recommendations of the WHO/ITU ehealth Strategy Toolkit
 The development of the South African ehealth Strategy aeed againt the recommendation of the WHO/ITU ehealth Strategy Toolkit Roemary Foter PhD a,b a ehealth Strategy and Policy Diviion, Medical Reearch
The development of the South African ehealth Strategy aeed againt the recommendation of the WHO/ITU ehealth Strategy Toolkit Roemary Foter PhD a,b a ehealth Strategy and Policy Diviion, Medical Reearch
Modeling of underwater vehicle s dynamics
 Proceeding of the 11th WEA International Conference on YTEM, Agio Nikolao, Crete Iland, Greece, July 23-25, 2007 44 Modeling of underwater vehicle dynamic ANDRZEJ ZAK Department of Radiolocation and Hydrolocation
Proceeding of the 11th WEA International Conference on YTEM, Agio Nikolao, Crete Iland, Greece, July 23-25, 2007 44 Modeling of underwater vehicle dynamic ANDRZEJ ZAK Department of Radiolocation and Hydrolocation
LinkGuide: Towards a Better Collection of Hyperlinks in a Website Homepage
 Proceeding of the World Congre on Engineering 2007 Vol I LinkGuide: Toward a Better Collection of Hyperlink in a Webite Homepage A. Ammari and V. Zharkova chool of Informatic, Univerity of Bradford anammari@bradford.ac.uk,
Proceeding of the World Congre on Engineering 2007 Vol I LinkGuide: Toward a Better Collection of Hyperlink in a Webite Homepage A. Ammari and V. Zharkova chool of Informatic, Univerity of Bradford anammari@bradford.ac.uk,
How to. write a paper. The basics writing a solid paper Different communities/different standards Common errors
 How to write a paper The baic writing a olid paper Different communitie/different tandard Common error Reource Raibert eay My grammar point Article on a v. the Bug in writing Clarity Goal Conciene Calling
How to write a paper The baic writing a olid paper Different communitie/different tandard Common error Reource Raibert eay My grammar point Article on a v. the Bug in writing Clarity Goal Conciene Calling
Performance of a Robust Filter-based Approach for Contour Detection in Wireless Sensor Networks
 Performance of a Robut Filter-baed Approach for Contour Detection in Wirele Senor Network Hadi Alati, William A. Armtrong, Jr., and Ai Naipuri Department of Electrical and Computer Engineering The Univerity
Performance of a Robut Filter-baed Approach for Contour Detection in Wirele Senor Network Hadi Alati, William A. Armtrong, Jr., and Ai Naipuri Department of Electrical and Computer Engineering The Univerity
Modelling the impact of cyber attacks on the traffic control centre of an urban automobile transport system by means of enhanced cybersecurity
 Modelling the impact of cyber attack on the traffic control centre of an urban automobile tranport ytem by mean of enhanced cyberecurity Yoana Ivanova 1,* 1 Bulgarian Academy of Science, Intitute of ICT,
Modelling the impact of cyber attack on the traffic control centre of an urban automobile tranport ytem by mean of enhanced cyberecurity Yoana Ivanova 1,* 1 Bulgarian Academy of Science, Intitute of ICT,
Course Project: Adders, Subtractors, and Multipliers a
 In the name Allah Department of Computer Engineering 215 Spring emeter Computer Architecture Coure Intructor: Dr. Mahdi Abbai Coure Project: Adder, Subtractor, and Multiplier a a The purpoe of thi p roject
In the name Allah Department of Computer Engineering 215 Spring emeter Computer Architecture Coure Intructor: Dr. Mahdi Abbai Coure Project: Adder, Subtractor, and Multiplier a a The purpoe of thi p roject
A Practical Model for Minimizing Waiting Time in a Transit Network
 A Practical Model for Minimizing Waiting Time in a Tranit Network Leila Dianat, MASc, Department of Civil Engineering, Sharif Univerity of Technology, Tehran, Iran Youef Shafahi, Ph.D. Aociate Profeor,
A Practical Model for Minimizing Waiting Time in a Tranit Network Leila Dianat, MASc, Department of Civil Engineering, Sharif Univerity of Technology, Tehran, Iran Youef Shafahi, Ph.D. Aociate Profeor,
DWH Performance Tuning For Better Reporting
 DWH Performance Tuning For Better Sandeep Bhargava Reearch Scholar Naveen Hemrajani Aociate Profeor Dineh Goyal Aociate Profeor Subhah Gander IT Profeional ABSTRACT: The concept of data warehoue deal in
DWH Performance Tuning For Better Sandeep Bhargava Reearch Scholar Naveen Hemrajani Aociate Profeor Dineh Goyal Aociate Profeor Subhah Gander IT Profeional ABSTRACT: The concept of data warehoue deal in
SIMIT 7. Profinet IO Gateway. User Manual
 SIMIT 7 Profinet IO Gateway Uer Manual Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult are only non-binding uggetion
SIMIT 7 Profinet IO Gateway Uer Manual Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult are only non-binding uggetion
Analysis of the results of analytical and simulation With the network model and dynamic priority Unchecked Buffer
 International Reearch Journal of Applied and Baic Science 218 Available online at www.irjab.com ISSN 2251-838X / Vol, 12 (1): 49-53 Science Explorer Publication Analyi of the reult of analytical and imulation
International Reearch Journal of Applied and Baic Science 218 Available online at www.irjab.com ISSN 2251-838X / Vol, 12 (1): 49-53 Science Explorer Publication Analyi of the reult of analytical and imulation
CLOUD computing is considered a big step towards the
 IEEE TRANSACTIONS ON SUSTAINABLE COMPUTING, VOL. 2, NO. 2, APRIL-JUNE 2017 183 Dynamic VM Placement Method for Minimizing Energy and Carbon Cot in Geographically Ditributed Cloud Data Center Atefeh Khoravi,
IEEE TRANSACTIONS ON SUSTAINABLE COMPUTING, VOL. 2, NO. 2, APRIL-JUNE 2017 183 Dynamic VM Placement Method for Minimizing Energy and Carbon Cot in Geographically Ditributed Cloud Data Center Atefeh Khoravi,
Resource Auto-Scaling and Sparse Content Replication for Video Storage Systems
 1 Reource Auto-Scaling and Spare Content Replication for Video Storage Sytem DI NIU 1, HONG XU 2 and BAOCHUN LI 3, Univerity of Alberta 1, City Univerity of Hong Kong 2, Univerity of Toronto 3 Many video-on-demand
1 Reource Auto-Scaling and Spare Content Replication for Video Storage Sytem DI NIU 1, HONG XU 2 and BAOCHUN LI 3, Univerity of Alberta 1, City Univerity of Hong Kong 2, Univerity of Toronto 3 Many video-on-demand
ANALYSIS OF THE FIRST LAYER IN WEIGHTLESS NEURAL NETWORKS FOR 3_DIMENSIONAL PATTERN RECOGNITION
 ANALYSIS OF THE FIRST LAYER IN WEIGHTLESS NEURAL NETWORKS FOR 3_DIMENSIONAL PATTERN RECOGNITION A. Váque-Nava * Ecuela de Ingeniería. CENTRO UNIVERSITARIO MEXICO. DIVISION DE ESTUDIOS SUPERIORES J. Figueroa
ANALYSIS OF THE FIRST LAYER IN WEIGHTLESS NEURAL NETWORKS FOR 3_DIMENSIONAL PATTERN RECOGNITION A. Váque-Nava * Ecuela de Ingeniería. CENTRO UNIVERSITARIO MEXICO. DIVISION DE ESTUDIOS SUPERIORES J. Figueroa
Software Agent (SA) to guarantee QoS for multi constrain applications in all-ip networks
 Software Agent (SA) to guarantee QoS for multi contrain application in all-ip network Kazi Khaled Al-Zahid and Mituji Matumoto GITS, Waeda Univerity 94 Waeda Univ. Bldg. A-308, 1011Okuboyama Nihitomida
Software Agent (SA) to guarantee QoS for multi contrain application in all-ip network Kazi Khaled Al-Zahid and Mituji Matumoto GITS, Waeda Univerity 94 Waeda Univ. Bldg. A-308, 1011Okuboyama Nihitomida
Laboratory Exercise 2
 Laoratory Exercie Numer and Diplay Thi i an exercie in deigning cominational circuit that can perform inary-to-decimal numer converion and inary-coded-decimal (BCD) addition. Part I We wih to diplay on
Laoratory Exercie Numer and Diplay Thi i an exercie in deigning cominational circuit that can perform inary-to-decimal numer converion and inary-coded-decimal (BCD) addition. Part I We wih to diplay on
A Fast Association Rule Algorithm Based On Bitmap and Granular Computing
 A Fat Aociation Rule Algorithm Baed On Bitmap and Granular Computing T.Y.Lin Xiaohua Hu Eric Louie Dept. of Computer Science College of Information Science IBM Almaden Reearch Center San Joe State Univerity
A Fat Aociation Rule Algorithm Baed On Bitmap and Granular Computing T.Y.Lin Xiaohua Hu Eric Louie Dept. of Computer Science College of Information Science IBM Almaden Reearch Center San Joe State Univerity
ESRP Storage Program EMC Celerra NS-120 (1,500 User) Mailbox Resiliency Storage Solution for Microsoft Exchange 2010
 ESRP Stora Program EMC Celerra NS-12 (1, Uer) Mailbox Reilien Stora Solution for Microoft Exchan 21 Teted with: ESRP Stora Verion 3. Teted Date: 3/2/21 EMC Corporation Corporate Headquarter Hopkinton,
ESRP Stora Program EMC Celerra NS-12 (1, Uer) Mailbox Reilien Stora Solution for Microoft Exchan 21 Teted with: ESRP Stora Verion 3. Teted Date: 3/2/21 EMC Corporation Corporate Headquarter Hopkinton,
A Multi-objective Genetic Algorithm for Reliability Optimization Problem
 International Journal of Performability Engineering, Vol. 5, No. 3, April 2009, pp. 227-234. RAMS Conultant Printed in India A Multi-objective Genetic Algorithm for Reliability Optimization Problem AMAR
International Journal of Performability Engineering, Vol. 5, No. 3, April 2009, pp. 227-234. RAMS Conultant Printed in India A Multi-objective Genetic Algorithm for Reliability Optimization Problem AMAR
An Approach to a Test Oracle for XML Query Testing
 An Approach to a Tet Oracle for XML Query Teting Dae S. Kim-Park, Claudio de la Riva, Javier Tuya Univerity of Oviedo Computing Department Campu of Vieque, /n, 33204 (SPAIN) kim_park@li.uniovi.e, claudio@uniovi.e,
An Approach to a Tet Oracle for XML Query Teting Dae S. Kim-Park, Claudio de la Riva, Javier Tuya Univerity of Oviedo Computing Department Campu of Vieque, /n, 33204 (SPAIN) kim_park@li.uniovi.e, claudio@uniovi.e,
A SIMPLE IMPERATIVE LANGUAGE THE STORE FUNCTION NON-TERMINATING COMMANDS
 A SIMPLE IMPERATIVE LANGUAGE Eventually we will preent the emantic of a full-blown language, with declaration, type and looping. However, there are many complication, o we will build up lowly. Our firt
A SIMPLE IMPERATIVE LANGUAGE Eventually we will preent the emantic of a full-blown language, with declaration, type and looping. However, there are many complication, o we will build up lowly. Our firt
On successive packing approach to multidimensional (M-D) interleaving
 On ucceive packing approach to multidimenional (M-D) interleaving Xi Min Zhang Yun Q. hi ankar Bau Abtract We propoe an interleaving cheme for multidimenional (M-D) interleaving. To achieved by uing a
On ucceive packing approach to multidimenional (M-D) interleaving Xi Min Zhang Yun Q. hi ankar Bau Abtract We propoe an interleaving cheme for multidimenional (M-D) interleaving. To achieved by uing a
A METHOD OF REAL-TIME NURBS INTERPOLATION WITH CONFINED CHORD ERROR FOR CNC SYSTEMS
 Vietnam Journal of Science and Technology 55 (5) (017) 650-657 DOI: 10.1565/55-518/55/5/906 A METHOD OF REAL-TIME NURBS INTERPOLATION WITH CONFINED CHORD ERROR FOR CNC SYSTEMS Nguyen Huu Quang *, Banh
Vietnam Journal of Science and Technology 55 (5) (017) 650-657 DOI: 10.1565/55-518/55/5/906 A METHOD OF REAL-TIME NURBS INTERPOLATION WITH CONFINED CHORD ERROR FOR CNC SYSTEMS Nguyen Huu Quang *, Banh
PERFORMANCE EVALUATION ISSUES OF QUERY PROCESSING THROUGH CLIENT SERVER ARCHITECTURE
 Manih Srivatava et al./ International Journal of Comuter Science & Engineering Technology (IJCSET) PERFORMANCE EVALUATION ISSUES OF QUERY PROCESSING THROUGH CLIENT SERVER ARCHITECTURE Mr. Manih Srivatava
Manih Srivatava et al./ International Journal of Comuter Science & Engineering Technology (IJCSET) PERFORMANCE EVALUATION ISSUES OF QUERY PROCESSING THROUGH CLIENT SERVER ARCHITECTURE Mr. Manih Srivatava
Aspects of Formal and Graphical Design of a Bus System
 Apect of Formal and Graphical Deign of a Bu Sytem Tiberiu Seceleanu Univerity of Turku, Dpt. of Information Technology Turku, Finland tiberiu.eceleanu@utu.fi Tomi Weterlund Turku Centre for Computer Science
Apect of Formal and Graphical Deign of a Bu Sytem Tiberiu Seceleanu Univerity of Turku, Dpt. of Information Technology Turku, Finland tiberiu.eceleanu@utu.fi Tomi Weterlund Turku Centre for Computer Science
Ethernet Peer-To-Peer Communication With Model 353 And Procidia i pac Controllers
 iemen Energy & utomation pplication ata Ethernet Peer-To-Peer Communication With odel 353 nd Procidia ipac Controller 353-113 Rev. 1 July Ethernet i a leading form of network communication that i often
iemen Energy & utomation pplication ata Ethernet Peer-To-Peer Communication With odel 353 nd Procidia ipac Controller 353-113 Rev. 1 July Ethernet i a leading form of network communication that i often
Figure 1: Virtualization
 Volume 6, Issue 9, September 2016 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com A Profitable
Volume 6, Issue 9, September 2016 ISSN: 2277 128X International Journal of Advanced Research in Computer Science and Software Engineering Research Paper Available online at: www.ijarcsse.com A Profitable
Automated Usability Evaluation during Model-based Interactive System Development
 Automated Uability Evaluation during -baed Interactive Sytem Development Sebatian Feuertack 1, Marco Blumendorf 1, Maximilian Kern 1, Michael Kruppa 2, Michael Quade 1, Mathia Runge 1 and Sahin Albayrak
Automated Uability Evaluation during -baed Interactive Sytem Development Sebatian Feuertack 1, Marco Blumendorf 1, Maximilian Kern 1, Michael Kruppa 2, Michael Quade 1, Mathia Runge 1 and Sahin Albayrak
ES205 Analysis and Design of Engineering Systems: Lab 1: An Introductory Tutorial: Getting Started with SIMULINK
 ES05 Analyi and Deign of Engineering Sytem: Lab : An Introductory Tutorial: Getting Started with SIMULINK What i SIMULINK? SIMULINK i a oftware package for modeling, imulating, and analyzing dynamic ytem.
ES05 Analyi and Deign of Engineering Sytem: Lab : An Introductory Tutorial: Getting Started with SIMULINK What i SIMULINK? SIMULINK i a oftware package for modeling, imulating, and analyzing dynamic ytem.
An Improved Implementation of Elliptic Curve Digital Signature by Using Sparse Elements
 The International Arab Journal of Information Technology, Vol. 1, No., July 004 0 An Improved Implementation of Elliptic Curve Digital Signature by Uing Spare Element Eam Al-Daoud Computer Science Department,
The International Arab Journal of Information Technology, Vol. 1, No., July 004 0 An Improved Implementation of Elliptic Curve Digital Signature by Uing Spare Element Eam Al-Daoud Computer Science Department,
Software Shaders in Interactive Environments Using Relief Impostors
 Software Shader in Interactive Environment Uing Relief Impotor ESTEBAN WALTER GONZALEZ CLUA BRUNO FEIJÓ MARCELO DREUX, FRANCISCO FONSECA ICAD/IGame/ViionLab, Department of Computer Science, PUC-Rio {eteban,
Software Shader in Interactive Environment Uing Relief Impotor ESTEBAN WALTER GONZALEZ CLUA BRUNO FEIJÓ MARCELO DREUX, FRANCISCO FONSECA ICAD/IGame/ViionLab, Department of Computer Science, PUC-Rio {eteban,
Data Mining with Linguistic Thresholds
 Int. J. Contemp. Math. Science, Vol. 7, 22, no. 35, 7-725 Data Mining with Linguitic Threhold Tzung-Pei Hong Department of Electrical Engineering National Univerity of Kaohiung Kaohiung, Taiwan, R.O.C.
Int. J. Contemp. Math. Science, Vol. 7, 22, no. 35, 7-725 Data Mining with Linguitic Threhold Tzung-Pei Hong Department of Electrical Engineering National Univerity of Kaohiung Kaohiung, Taiwan, R.O.C.
(12) Patent Application Publication (10) Pub. No.: US 2013/ A1. Dhar et al. (43) Pub. Date: Jun. 6, 2013 NY (US) (57) ABSTRACT
 (19) United State US 2013 0145314A1 (12) Patent Application Publication (10) Pub. No.: US 2013/0145314 A1 Dhar et al. (43) Pub. Date: Jun. 6, 2013 (54) SYSTEMAND METHOD FORCHANGEABLE (52) U.S. Cl. FOCUS
(19) United State US 2013 0145314A1 (12) Patent Application Publication (10) Pub. No.: US 2013/0145314 A1 Dhar et al. (43) Pub. Date: Jun. 6, 2013 (54) SYSTEMAND METHOD FORCHANGEABLE (52) U.S. Cl. FOCUS
A Load Balancing Model based on Load-aware for Distributed Controllers. Fengjun Shang, Wenjuan Gong
 4th International Conference on Machinery, Material and Computing Technology (ICMMCT 2016) A Load Balancing Model baed on Load-aware for Ditributed Controller Fengjun Shang, Wenjuan Gong College of Compute
4th International Conference on Machinery, Material and Computing Technology (ICMMCT 2016) A Load Balancing Model baed on Load-aware for Ditributed Controller Fengjun Shang, Wenjuan Gong College of Compute
PERFORMANCE EVALUATION OF TRANSMISSION DISTANCE AND BIT RATES IN INTER-SATELLITE OPTICAL WIRELESS COMMUNICATION SYSTEM
 PERFORMANCE EVALUATION OF TRANSMISSION DISTANCE AND BIT RATES IN INTER-SATELLITE OPTICAL WIRELESS COMMUNICATION SYSTEM Rohni Joy 1, Ami Lavingia 2, Prof. Kruti Lavingia 3 1 Electronic and Communication
PERFORMANCE EVALUATION OF TRANSMISSION DISTANCE AND BIT RATES IN INTER-SATELLITE OPTICAL WIRELESS COMMUNICATION SYSTEM Rohni Joy 1, Ami Lavingia 2, Prof. Kruti Lavingia 3 1 Electronic and Communication
A System Dynamics Model for Transient Availability Modeling of Repairable Redundant Systems
 International Journal of Performability Engineering Vol., No. 3, May 05, pp. 03-. RAMS Conultant Printed in India A Sytem Dynamic Model for Tranient Availability Modeling of Repairable Redundant Sytem
International Journal of Performability Engineering Vol., No. 3, May 05, pp. 03-. RAMS Conultant Printed in India A Sytem Dynamic Model for Tranient Availability Modeling of Repairable Redundant Sytem
Domain-Specific Modeling for Rapid System-Wide Energy Estimation of Reconfigurable Architectures
 Domain-Specific Modeling for Rapid Sytem-Wide Energy Etimation of Reconfigurable Architecture Seonil Choi 1,Ju-wookJang 2, Sumit Mohanty 1, Viktor K. Praanna 1 1 Dept. of Electrical Engg. 2 Dept. of Electronic
Domain-Specific Modeling for Rapid Sytem-Wide Energy Etimation of Reconfigurable Architecture Seonil Choi 1,Ju-wookJang 2, Sumit Mohanty 1, Viktor K. Praanna 1 1 Dept. of Electrical Engg. 2 Dept. of Electronic
Building a Compact On-line MRF Recognizer for Large Character Set using Structured Dictionary Representation and Vector Quantization Technique
 202 International Conference on Frontier in Handwriting Recognition Building a Compact On-line MRF Recognizer for Large Character Set uing Structured Dictionary Repreentation and Vector Quantization Technique
202 International Conference on Frontier in Handwriting Recognition Building a Compact On-line MRF Recognizer for Large Character Set uing Structured Dictionary Repreentation and Vector Quantization Technique
Parameters, UVM, Coverage & Emulation Take Two and Call Me in the Morning
 Parameter, UVM, Coverage & Emulation Take Two and Call Me in the Morning Michael Horn Mentor Graphic Corporation Colorado, USA Mike_Horn@mentor.com Bryan Ramirez Mentor Graphic Corporation Colorado, USA
Parameter, UVM, Coverage & Emulation Take Two and Call Me in the Morning Michael Horn Mentor Graphic Corporation Colorado, USA Mike_Horn@mentor.com Bryan Ramirez Mentor Graphic Corporation Colorado, USA
Copyright Warning & Restrictions
 Copyright Warning & Retriction The copyright law of the United State (Title 17, United State Code) govern the making of photocopie or other reproduction of copyrighted material. Under certain condition
Copyright Warning & Retriction The copyright law of the United State (Title 17, United State Code) govern the making of photocopie or other reproduction of copyrighted material. Under certain condition
A Survey on CloudSim Toolkit for Implementing Cloud Infrastructure
 IJSTE - International Journal of Science Technology & Engineering Volume 1 Issue 12 June 2015 ISSN (online): 2349-784X A Survey on CloudSim Toolkit for Implementing Cloud Infrastructure Harsha Amipara
IJSTE - International Journal of Science Technology & Engineering Volume 1 Issue 12 June 2015 ISSN (online): 2349-784X A Survey on CloudSim Toolkit for Implementing Cloud Infrastructure Harsha Amipara
Digifort Standard. Architecture
 Digifort Standard Intermediate olution for intalling up to 32 camera The Standard verion provide the ideal reource for local and remote monitoring of up to 32 camera per erver and a the intermediate verion
Digifort Standard Intermediate olution for intalling up to 32 camera The Standard verion provide the ideal reource for local and remote monitoring of up to 32 camera per erver and a the intermediate verion
(12) United States Patent
 U009250939B2 (12) United tate Patent Odaira (54) INFORMATION PROCEING DEVICE, PROFILE TARGET DETERMINING PROGRAM, AND METHOD (71) Applicant: International Buine Machine Corporation, Armonk, NY (U) (72)
U009250939B2 (12) United tate Patent Odaira (54) INFORMATION PROCEING DEVICE, PROFILE TARGET DETERMINING PROGRAM, AND METHOD (71) Applicant: International Buine Machine Corporation, Armonk, NY (U) (72)
AN INTELLIGENT SCHEME FOR FACIAL EXPRESSION RECOGNITION
 AN INTELLIGENT SCHEME FOR FACIAL EXPRESSION RECOGNITION A. Raouzaiou, S. Ioannou, K. Karpouzi, N. Tapatouli, S. Kollia 1, R. Cowie 2 1 Department of Electrical and Computer Engineering National Technical
AN INTELLIGENT SCHEME FOR FACIAL EXPRESSION RECOGNITION A. Raouzaiou, S. Ioannou, K. Karpouzi, N. Tapatouli, S. Kollia 1, R. Cowie 2 1 Department of Electrical and Computer Engineering National Technical
Keywords: Defect detection, linear phased array transducer, parameter optimization, phased array ultrasonic B-mode imaging testing.
 Send Order for Reprint to reprint@benthamcience.ae 488 The Open Automation and Control Sytem Journal, 2014, 6, 488-492 Open Acce Parameter Optimization of Linear Phaed Array Tranducer for Defect Detection
Send Order for Reprint to reprint@benthamcience.ae 488 The Open Automation and Control Sytem Journal, 2014, 6, 488-492 Open Acce Parameter Optimization of Linear Phaed Array Tranducer for Defect Detection
Efficient Technique for Allocation of Processing Elements to Virtual Machines in Cloud Environment
 IJCSNS International Journal of Computer Science and Network Security, VOL.16 No.8, August 216 17 Efficient Technique for Allocation of Processing Elements to Virtual Machines in Cloud Environment Puneet
IJCSNS International Journal of Computer Science and Network Security, VOL.16 No.8, August 216 17 Efficient Technique for Allocation of Processing Elements to Virtual Machines in Cloud Environment Puneet
(12) Patent Application Publication (10) Pub. No.: US 2011/ A1
 (19) United State US 2011 0316690A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0316690 A1 Siegman (43) Pub. Date: Dec. 29, 2011 (54) SYSTEMAND METHOD FOR IDENTIFYING ELECTRICAL EQUIPMENT
(19) United State US 2011 0316690A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0316690 A1 Siegman (43) Pub. Date: Dec. 29, 2011 (54) SYSTEMAND METHOD FOR IDENTIFYING ELECTRICAL EQUIPMENT
Lecture 14: Minimum Spanning Tree I
 COMPSCI 0: Deign and Analyi of Algorithm October 4, 07 Lecture 4: Minimum Spanning Tree I Lecturer: Rong Ge Scribe: Fred Zhang Overview Thi lecture we finih our dicuion of the hortet path problem and introduce
COMPSCI 0: Deign and Analyi of Algorithm October 4, 07 Lecture 4: Minimum Spanning Tree I Lecturer: Rong Ge Scribe: Fred Zhang Overview Thi lecture we finih our dicuion of the hortet path problem and introduce
Integrated Single-arm Assembly and Manipulation Planning using Dynamic Regrasp Graphs
 Proceeding of The 2016 IEEE International Conference on Real-time Computing and Robotic June 6-9, 2016, Angkor Wat, Cambodia Integrated Single-arm Aembly and Manipulation Planning uing Dynamic Regrap Graph
Proceeding of The 2016 IEEE International Conference on Real-time Computing and Robotic June 6-9, 2016, Angkor Wat, Cambodia Integrated Single-arm Aembly and Manipulation Planning uing Dynamic Regrap Graph
The Performance Evaluation of Qos in Wireless Personal Area Network (WPAN) on Impact of Bluetooth Worms
 Journal of Wirele Networking and Communication 2012, 2(5): 111-116 DOI: 10.5923/j.jwnc.20120205.05 The Performance Evaluation of Qo in Wirele Peronal Area Network (WPAN) on Impact of Bluetooth Worm M.
Journal of Wirele Networking and Communication 2012, 2(5): 111-116 DOI: 10.5923/j.jwnc.20120205.05 The Performance Evaluation of Qo in Wirele Peronal Area Network (WPAN) on Impact of Bluetooth Worm M.
Task-based Adaptation for Ubiquitous Computing
 IEEE Tranaction on Sytem, Man, and Cybernetic, Part C: Application and Review Special Iue on Engineering Autonomic Sytem, to appear Tak-baed Adaptation for Ubiquitou Computing João Pedro Soua, Vahe Poladian,
IEEE Tranaction on Sytem, Man, and Cybernetic, Part C: Application and Review Special Iue on Engineering Autonomic Sytem, to appear Tak-baed Adaptation for Ubiquitou Computing João Pedro Soua, Vahe Poladian,
An Approach to Buffer Management in Java HPC Messaging
 An Approach to Buer Management in Java HPC Meaging Mark Baker, Bryan Carpenter, and Aamir Shai Ditributed Sytem Group, Univerity o Portmouth Abtract. One o the mot challenging apect to deigning a Java
An Approach to Buer Management in Java HPC Meaging Mark Baker, Bryan Carpenter, and Aamir Shai Ditributed Sytem Group, Univerity o Portmouth Abtract. One o the mot challenging apect to deigning a Java
AN ALGORITHM FOR RESTRICTED NORMAL FORM TO SOLVE DUAL TYPE NON-CANONICAL LINEAR FRACTIONAL PROGRAMMING PROBLEM
 RAC Univerity Journal, Vol IV, No, 7, pp 87-9 AN ALGORITHM FOR RESTRICTED NORMAL FORM TO SOLVE DUAL TYPE NON-CANONICAL LINEAR FRACTIONAL PROGRAMMING PROLEM Mozzem Hoain Department of Mathematic Ghior Govt
RAC Univerity Journal, Vol IV, No, 7, pp 87-9 AN ALGORITHM FOR RESTRICTED NORMAL FORM TO SOLVE DUAL TYPE NON-CANONICAL LINEAR FRACTIONAL PROGRAMMING PROLEM Mozzem Hoain Department of Mathematic Ghior Govt
A Test Bed for Multi-Agent Control Systems in Road Traffic Management
 van Katwijk, van Koningbruggen, De Schutter, Hellendoorn 1 A Tet Bed for Multi-Agent Control Sytem in Road Traffic Management Submiion date: July 29th, 2004 Etimated word count: 4500 + 8 (figure) * 250
van Katwijk, van Koningbruggen, De Schutter, Hellendoorn 1 A Tet Bed for Multi-Agent Control Sytem in Road Traffic Management Submiion date: July 29th, 2004 Etimated word count: 4500 + 8 (figure) * 250
Topics. Lecture 37: Global Optimization. Issues. A Simple Example: Copy Propagation X := 3 B > 0 Y := 0 X := 4 Y := Z + W A := 2 * 3X
 Lecture 37: Global Optimization [Adapted from note by R. Bodik and G. Necula] Topic Global optimization refer to program optimization that encompa multiple baic block in a function. (I have ued the term
Lecture 37: Global Optimization [Adapted from note by R. Bodik and G. Necula] Topic Global optimization refer to program optimization that encompa multiple baic block in a function. (I have ued the term
MAT 155: Describing, Exploring, and Comparing Data Page 1 of NotesCh2-3.doc
 MAT 155: Decribing, Exploring, and Comparing Data Page 1 of 8 001-oteCh-3.doc ote for Chapter Summarizing and Graphing Data Chapter 3 Decribing, Exploring, and Comparing Data Frequency Ditribution, Graphic
MAT 155: Decribing, Exploring, and Comparing Data Page 1 of 8 001-oteCh-3.doc ote for Chapter Summarizing and Graphing Data Chapter 3 Decribing, Exploring, and Comparing Data Frequency Ditribution, Graphic
Modeling Throughput and Delay in Infrastructure Mode Networks with QoS Support from the Point Coordination Function
 Proceeding of the World Congre on Engineering and Computer Science 2012 Vol II, October 24-26, 2012, San Francico, USA Modeling Throughput and Delay in 802.11 Infratructure Mode Network with QoS Support
Proceeding of the World Congre on Engineering and Computer Science 2012 Vol II, October 24-26, 2012, San Francico, USA Modeling Throughput and Delay in 802.11 Infratructure Mode Network with QoS Support
Performance Evaluation of search engines via user efforts measures
 IJCSI International Journal of Computer Science Iue, Vol. 9, Iue 4, No, July 01 www.ijcsi.org 437 Performance Evaluation of earch engine via uer effort meaure Raeh Kumar Goutam 1 and Sanay K. Dwivedi 1
IJCSI International Journal of Computer Science Iue, Vol. 9, Iue 4, No, July 01 www.ijcsi.org 437 Performance Evaluation of earch engine via uer effort meaure Raeh Kumar Goutam 1 and Sanay K. Dwivedi 1
Semi-Distributed Load Balancing for Massively Parallel Multicomputer Systems
 Syracue Univerity SUFAC lectrical ngineering and Computer Science echnical eport College of ngineering and Computer Science 8-1991 Semi-Ditributed Load Balancing for aively Parallel ulticomputer Sytem
Syracue Univerity SUFAC lectrical ngineering and Computer Science echnical eport College of ngineering and Computer Science 8-1991 Semi-Ditributed Load Balancing for aively Parallel ulticomputer Sytem
Computer Arithmetic Homework Solutions. 1 An adder for graphics. 2 Partitioned adder. 3 HDL implementation of a partitioned adder
 Computer Arithmetic Homework 3 2016 2017 Solution 1 An adder for graphic In a normal ripple carry addition of two poitive number, the carry i the ignal for a reult exceeding the maximum. We ue thi ignal
Computer Arithmetic Homework 3 2016 2017 Solution 1 An adder for graphic In a normal ripple carry addition of two poitive number, the carry i the ignal for a reult exceeding the maximum. We ue thi ignal
Testing Structural Properties in Textual Data: Beyond Document Grammars
 Teting Structural Propertie in Textual Data: Beyond Document Grammar Felix Saaki and Jen Pönninghau Univerity of Bielefeld, Germany Abtract Schema language concentrate on grammatical contraint on document
Teting Structural Propertie in Textual Data: Beyond Document Grammar Felix Saaki and Jen Pönninghau Univerity of Bielefeld, Germany Abtract Schema language concentrate on grammatical contraint on document
On combining Learning Vector Quantization and the Bayesian classifiers for natural textured images
 On combining Learning Vector Quantization and the Bayeian claifier for natural textured image María Guiarro Dept. Ingeniería del Software e Inteligencia Artificial Facultad Informática Univeridad Complutene
On combining Learning Vector Quantization and the Bayeian claifier for natural textured image María Guiarro Dept. Ingeniería del Software e Inteligencia Artificial Facultad Informática Univeridad Complutene
ENERGY EFFICIENT VIRTUAL MACHINE INTEGRATION IN CLOUD COMPUTING
 ENERGY EFFICIENT VIRTUAL MACHINE INTEGRATION IN CLOUD COMPUTING Mrs. Shweta Agarwal Assistant Professor, Dept. of MCA St. Aloysius Institute of Technology, Jabalpur(India) ABSTRACT In the present study,
ENERGY EFFICIENT VIRTUAL MACHINE INTEGRATION IN CLOUD COMPUTING Mrs. Shweta Agarwal Assistant Professor, Dept. of MCA St. Aloysius Institute of Technology, Jabalpur(India) ABSTRACT In the present study,
Aalborg Universitet. Published in: Proceedings of the Working Conference on Advanced Visual Interfaces
 Aalborg Univeritet Software-Baed Adjutment of Mobile Autotereocopic Graphic Uing Static Parallax Barrier Paprocki, Martin Marko; Krog, Kim Srirat; Kritofferen, Morten Bak; Krau, Martin Publihed in: Proceeding
Aalborg Univeritet Software-Baed Adjutment of Mobile Autotereocopic Graphic Uing Static Parallax Barrier Paprocki, Martin Marko; Krog, Kim Srirat; Kritofferen, Morten Bak; Krau, Martin Publihed in: Proceeding
A Sparse Shared-Memory Multifrontal Solver in SCAD Software
 Proceeding of the International Multiconference on ISBN 978-83-6080--9 Computer Science and Information echnology, pp. 77 83 ISSN 896-709 A Spare Shared-Memory Multifrontal Solver in SCAD Software Sergiy
Proceeding of the International Multiconference on ISBN 978-83-6080--9 Computer Science and Information echnology, pp. 77 83 ISSN 896-709 A Spare Shared-Memory Multifrontal Solver in SCAD Software Sergiy
Global Journal of Engineering Science and Research Management
 ENHANCED MULTI OBJECTIVE TASK SCHEDULING FOR CLOUD ENVIRONMENT USING TASK GROUPING Mohana. R. S *, Thangaraj. P, Kalaiselvi. S, Krishnakumar. B * Assistant Professor (SRG), Department of Computer Science,
ENHANCED MULTI OBJECTIVE TASK SCHEDULING FOR CLOUD ENVIRONMENT USING TASK GROUPING Mohana. R. S *, Thangaraj. P, Kalaiselvi. S, Krishnakumar. B * Assistant Professor (SRG), Department of Computer Science,
