TREND MICRO Mobile Security 9.0 for Android Product Guide
|
|
|
- Hugo Gilbert
- 6 years ago
- Views:
Transcription
1 H TREND MICRO Mobile Security 9.0 for Android Product Guide V1.0 Trend Micro, Incorporated US Headquarters 224 E. John Carpenter Freeway, Suite 1500 Irving, Texas U.S.A. Phone: +1 (817) Toll-free: (888)
2 Trend Micro Incorporated reserves the right to make changes to this document and to the service described herein without notice. Before implementing the service, please review the readme file and the latest version of the applicable user documentation. Trend Micro and the Trend Micro t-ball logo are trademarks or registered trademarks of Trend Micro, Incorporated. All other product or company names may be trademarks or registered trademarks of their owners. Copyright 2017 Trend Micro Incorporated, Consumer Technical Product Marketing. All rights reserved. Trend Micro Mobile Security 9.0 for Android Product Guide provides help for analysts, reviewers, potential customers, and users who are evaluating, reviewing, or using Trend Micro Mobile Security for Android. At Trend Micro, we are always seeking to improve our documentation. If you have questions, comments, or suggestions about this or any Trend Micro documents, please contact us at For support regarding Trend Micro Mobile Security for Android, go to: DOCUMENT PROFILE: Product Name: Trend Micro Mobile Security 9.0 for Android Document Title: Trend Micro Mobile Security 9.0 for Android - Product Guide Document Filename: PG - TM Mobile Security 9 for Android - Product Guide v1.0.docx Document Release Date: September 12, 2017 Team: Consumer Technical Product Marketing 2
3 Contents Trend Micro Mobile Security Quick Overview... 4 Chapter 1: Introducing Trend Micro Mobile Security... 5 Key Features... 6 System Requirements... 8 Incompatible Software... 8 Internet 3G-4G Connection... 8 Recommended Environment... 8 Target Market... 8 Availability... 8 Contacting Trend Micro... 9 Consumer Support Line and Chat Support... 9 Premium Services... 9 Chapter 2: Getting Started with Trend Micro Mobile Security Download and Install Trend Micro Mobile Security Chapter 3: Exploring Trend Micro Mobile Security Overview of the Mobile Security Console Security Scan Messenger Protection System Tuner App Manager Network Protection Parental Controls Uninstall Protection Lost Device Protection Lost Device Protection Portal Social Network Privacy Call Blocking Settings Mobile Security on Your Android Tablet About Trend Micro
4 Trend Micro Mobile Security Quick Overview Trend Micro Mobile Security for Android (v9.0) provides comprehensive protection for smartphones and tablets so you can enjoy your digital life safely. It safeguards against malicious apps, fraudulent websites, and identity theft, and includes performance-boosting tools. Also, it secures your data by allowing you to find, lock, or erase your device if it s lost or stolen. Installing easily from the Google Play Store onto your Android smartphone or tablet, Trend Micro Mobile Security provides the following essential features (Red = updated or new): Mobile Security Console. Refreshed User Interface. Provides easy access to all functions. (Free = F; Paid = P): Security Scan. Remove apps with security, vulnerability, or privacy issues. Stop installation of fake banking apps and install the real ones. Pre- Installation Scan blocks bad apps and malware on Google Play before they re installed. (F, P) Messenger Protection. Get alerts to dangerous links in Line or WhatsApp messages. (P) System Tuner. Optimize your device s Battery and Memory use. Just-a-Phone Mode and Smart Power Saver. Shortcut for quick tuning. (F, P) App Manager. Save valuable storage space by viewing Apps by usage, uninstalling rarely used and unused Apps and Setup Files. (P) Network Protection. Block malicious websites when browsing; block unsecured Wi-Fi hotspots. (P) Parental Controls. Lock Apps from kids use or filter inappropriate websites. Uninstall protection protects Mobile Security from unauthorized uninstallation. (P) Lost Device Protection. Using the online portal, locate a lost device, trigger an alarm, remotely lock it, or even wipe the device to protect your personal information. New! Secret Snap takes a photo of whoever s found or stolen your device after a specified number of failed attempts to log into it. (P) Social Network Privacy. Fix your Facebook privacy settings and protect from ID or data theft. (F, P) Call Blocking. Block and disconnect annoying calls from unknown numbers. (P) Figure 1. Console Scrolled Up Figure 2. Console Scrolled Down 4
5 Chapter 1: Introducing Trend Micro Mobile Security This chapter introduces you to Trend Micro Mobile Security 9.0 for Android. The topics discussed in this chapter include: Key Features System Requirements Incompatible Software Internet 3-G-4G Connection Recommended Environment Target Market Availability Contacting Trend Micro 5
6 Key Features All features of Trend Micro Mobile Security for Android are available during the 7-day Free Trial. When the Trial has expired, you can use it for Free, but you must buy a subscription (Paid) to re-enable the full feature set. 1-year Subscription: USD $ year Subscription: USD $ Monthly Subscription (Auto-renew): USD $2.99 Yearly Subscription (Auto-renew): USD $ (Red = updated or new) Table 1. Trend Micro Mobile Security (9.0) for Android (1 of 2) Android Security Features Free Paid Security Console: Refreshed User Interface Provides easy access to all functions Security Scan: Enhanced Scanning Engine - Enhanced scanning engine provides superior virus, vulnerability, and privacy protection for your device. Security Scan: Real-time Scan - Scans apps you download and install to filter out viruses and malware that can steal your information and cost you money. Security Scan: Pre-Installation Scan - Simplified Pre-installation Scan blocks viruses and malware before they re downloaded and installed. Security Scan: Updates - Unlimited updates to virus protection files. Security Scan: Cloud Cloud scan connection ensures continuous protection. Security Scan: Fake Banking Apps - Mobile App Reputation helps you stop the installation of fake banking apps and install the real ones instead. Security Scan: Malware / Ransomware Cleaner - Removes malware and ransomware from your device Security Scan: Privacy Scanner - Detects spyware by scanning all apps with Mobile App Reputation to identify ones that collect and potentially steal private information. Messenger Protection - Protects messages from bad links in LINE and WhatsApp messengers System Tuner: Memory Status and Optimizer - Helps free up memory and CPU to maximize performance. Shortcut for quick tuning. System Tuner: Battery Optimizer - Maximizes your battery s life. System Tuner: Just-a-Phone - Turns off power-draining features and apps. System Tuner: Auto Just-a-Phone - Turns off power-draining features and apps automatically. 6
7 Table 2. Trend Micro Mobile Security (9.0) for Android (2 of 2) Android Security Features Free Paid System Tuner: Smart Power Saver - Intelligently manages and disables the network connection when it is not in use to maximize the battery life. App Manager - Saves valuable storage space by showing you Apps by usage and size, letting you uninstall rarely used and unused Apps and Setup Files Network Protection: Safe Surfing - Uses the Trend Micro Smart Protection Network to block malicious websites. Network Protection: Wi-Fi Checker - Checks and notifies users of unsecured Wi-Fi Networks Parental Controls: App Lock - Locks Apps from use, requiring password, pattern, or PIN to open Parental Controls: Wi-Fi Filter - Filters inappropriate websites with agebased restrictions. Lost Device Protection: Remote Locate / Alarm - Helps you find your devices on a Google map using GPS, cell towers, or Wi-Fi / Enables you to trigger an alarm on your device even if it is in silent mode. Lost Device Protection: Remote Lock / Wipe - Remotely lock your device (accessing the phone again will require that you insert your Trend Micro password or a unique unlock code). Perform a factory reset of the device from the web portal to erase all your personal data. Lost Device Protection: Secret Snap - Takes a photo of whoever s found or stolen your device after a specified number of failed attempts to log into it. Lost Device Protection: SIM Card Protection - Automatically locks your device if the SIM card is removed (Accessing the phone again will require that you insert your Trend Micro password or a unique unlock code). Automatically locates your device when the following actions take place: SIM removal, SIM replacement, Phone Restart. Lost Device Protection: Last Known Location - Automatically locates your device when the following actions take place: SIM removal, SIM replacement, Phone Restart. Lost Device Protection: Low Power Location - Records the location of your device just before it runs out of power. Scan Facebook: Social Networking Protection - Scan your Facebook privacy settings to protect you from spying and identity theft. Call Blocking - Filters unknown callers with whitelist and blacklist. Uninstall Protection - Prevents unauthorized removal of the app. Online Technical Support - Offers support provided via online forums, knowledgebase, and . 7
8 System Requirements Table 3. Trend Micro Mobile Security 9 for Android - System Requirements Requirements Description Operating Systems Device Space Memory Other Android OS 4.0 and above 50MB (minimum) 40MB-100MB Android (varies by device) 3G/4G (LTE) Wi-Fi Internet Connection Incompatible Software To identify software that you should remove from the device before installing Trend Micro Mobile Security, please refer to the following Web site: Internet 3G-4G Connection Trend Micro Mobile Security uses a Wi-Fi Internet or 3G-4G connection for activating the program online, checking the expiration date, downloading updates, sending Trend Micro URL/web queries and logs to the portal, logging into the management portal, and browsing knowledge-based pages on the Trend Micro Web site. 3G-4G data connections fees are usually charged on a monthly basis, using a fixed allocation with an upper limit. If you exceed this limit, you will be charged additional fees for the amount of time connected or for the amount of data downloaded. Testers are therefore encouraged to use a Wi-Fi router-based connection to the Internet whenever possible. Recommended Environment This Product Guide assumes that you are using Trend Micro Mobile Security in conjunction with a PC or Mac, so you can log in to the Trend Micro Mobile Security Portal easily at and review your Lost Device Protection settings and execute certain actions. Target Market Trend Micro Mobile Security is targeted to mobile users who wish to secure their Android and ios smart phones and tablets from malicious applications, web threats to them and their family, unwanted calls and messages, and device loss. Availability September 12, 2017 Google Play Store 8
9 Contacting Trend Micro Trend Micro Incorporated 225 E. John Carpenter Freeway, Suite 1500 Irving, Texas U.S.A. Phone: +1 (817) Toll-free: (888) Consumer Support Line (800) Monday - Friday, 5:00AM - 8:00PM Pacific and Chat Support Paid users of Mobile Security may obtain free , chat, and community forum support. For more information, contact esupport at: Premium Services Trend Micro offers Premium Services for a wide variety of technical issues including installation, virus and spyware removal, PC Tune-ups, and more. For more information, visit 9
10 Chapter 2: Getting Started with Trend Micro Mobile Security This chapter gets you started with Trend Micro Mobile Security. Topics discussed in this chapter include: Downloading and Installing Trend Micro Mobile Security Registering to / Creating a Trend Micro Account Using an Activation Code Buying / Activating a License Transferring an Existing License Note: Trend Micro Mobile Security is included with Trend Micro Maximum Security and Premium Security. To download the bundled software, users of these editions can simply launch the Trend Micro Security Console. A Protect Another Device link to the Mobile Security download is available in the Console. Download and Install Trend Micro Mobile Security To download and install Trend Micro Mobile Security: 1. Open your browser on your Android device and type ecuritydownload. 2. This takes you directly to the Google Play Store page for Trend Micro Mobile Security & Antivirus. 3. Alternately, tap the Google Play Store icon on your Android device to load it. The Google Play Store screen appears. 4. Search for Trend Micro Mobile Security in the Google Play search field. Figure 3. Google Play Store Figure 4. Search Google Play 10
11 5. Trend Micro Mobile Security & Antivirus will appear at the top of the Apps list. 6. Tap it to load the app. The Trend Micro Mobile Security & Antivirus install screen appears. 7. Tap Install. The App Permissions screen appears, indicating the access permissions Trend Micro Mobile Security & Antivirus needs on your device. 8. If you accept, tap Accept. Trend Micro Mobile Security & Antivirus downloads and installs. 9. When installation is complete, you re presented with a screen to Open or Uninstall the app. Tap Open. A Welcome - License Agreement screen appears. Figure 5. Trend Micro Mobile Security Figure 6. Install Figure 7. Accept Figure 8. Open 11
12 10. The Welcome screen appears with the Trend Micro License Agreement. 11. Read the License Agreement by tapping the link. If you accept the terms of the agreement, tap Accept and Continue. A screen appears, asking you to Help Make Mobile Security Better by tapping Join to send anonymous data to Trend Micro to improve the program. Alternately, tape Skip. 12. A Welcome demo screen appears. Tap Close to close the demo screen. 13. A Set Up Account screen appears, letting you Sign In to a Trend Micro Account you already have, or to Create an Account. Option 1: If You Have An Account 14. Tap the first option Sign In. The Sign In screen appears. Figure 9. Welcome Figure 10. Help Make Mobile Security Better Figure 11. Welcome Demo Figure 12. Set Up Account 12
13 15. Enter the address and password for your Trend Micro account and tap Sign In. You re signed into your account and the Trial or Paid status of your install of Mobile Security is shown in the Console. Option 2: To Create an Account 16. Alternately, tap Create an Account. The Create an Account screen appears. 17. Enter your preferred address, your first and last name, choose your location from the drop-down menu, and tap Next. 18. Confirm your chosen address, then enter a password and confirm it for your new Trend Micro Account. 19. If you wish, check Receive the latest news and offers from Trend Micro, and tap Done. 20. Trend Micro Mobile Security is activated and registered to your account and the Console opens. The activation can be as a 7-day Trial subscription, or an expired or new subscription, showing the past or future expiration date. You have several options to upgrade Trial or Expired subscriptions: Option 1: If you already have an Activation Code, you may apply it to this device. Option 2: You may Purchase a subscription. Option 3: You may Transfer another license you own to this device. Figure 13. Sign In Figure 15. Create an Account (2) Figure 14. Create an Account Figure 16. Trend Micro Mobile Security Console 13
14 To apply the Options to Trial or Expired Subscriptions: 1. Tap the Buy / Activate link in the Console. The Buy / Activate screen appears Option 1 - Activate 2. Tap Use an Activation Code. 3. In the screen that appears, enter the Activation Code you received in your confirmation mail or in your retail box and tap OK. Your subscription is activated. Figure 17. Expired Subscription Figure 18. Buy / Activate: Use an Activation Code Option 2 - Purchase 4. Tap a Purchase option in the Buy / Activate screen. The subscription popup appears. 5. Tap Subscribe. The card you registered with your Google Account will be charged and your subscription will be activated. Figure 19. Enter Activation Code Figure 20. Subscribe: Yearly Subscription 14
15 Option 3 - Transfer: 6. With the Console visible, tap the Options menu on your device, then the Settings menu in the Options popup. The Settings screen appears. 7. In the Settings screen, tap Transfer a subscription to this device. The Transfer Subscription screen appears. 8. Scroll down to locate a viable subscription; e.g., Not Yet Installed or one that is already installed, and tap it. 9. A popup appears, asking if you wish to Switch to Another Subscription. 10. Tap OK to make the switch. If it s a new installation, the subscription will immediately be activated on this device. If it s already activated on another device, it will be deactivated on that device and transferred to this one. Figure 21. Options > Settings Figure 23. Transfer Subscription Figure 22. Transfer a subscription to this device Figure 24. Switch to Another Subscription 15
16 11. The Console will indicate Your subscription has been updated and your new expiration date will be applied to the installation. 12. You re now ready to use Trend Micro Mobile Security on your Android device! See the sections following for instructions. Figure 25. Updated Subscription 16
17 Chapter 3: Exploring Trend Micro Mobile Security This chapter provides an overview of Trend Micro Mobile Security (TMMS). Topics discussed in this chapter include: Overview of the Mobile Security Console Security Scan (Includes Pre-Installation Scan) Messenger Protection System Tuner App Manager Network Protection Parental Controls Lost Device Protection Secret Snap Social Network Privacy Call Blocking Settings Mobile Security on your Android Tablet 17
18 Overview of the Mobile Security Console Once installed, Trend Micro Mobile Security (TMMS) appears in your Applications list on your Android mobile device and a shortcut appears on the desktop of your device. To use the Mobile Security Console: 1. Tap the Trend Micro Mobile Security icon on your mobile device and the Mobile Security Console appears. 2. Simply tap a button or panel to access the Console functions. Tap, hold and scroll to see panels lower down in the Console function list. 3. For example, tap the Scan wheel to do a Device Scan. Figure 26. Console Figure 27. Device Scan 4. Or tap the [X] things to fix in the Status Banner; then tap the alert panel to remove a threat. The Security Scan screen appears. 5. In the Security Scan screen, tap the Apps: Removal Recommended panel to view apps you may want to Remove from device or add to the Trusted Apps list. 6. Tap a panel in the scrolling Console, e.g., Messenger Protection (Figure 26), to execute the function or configure its settings. More details below. Figure 28. Things to Fix Figure 29. Apps Removal Recommended 18
19 Security Scan To use the Security Scan: 1. Tap the Security Scan panel in the Console. The Security Scan settings screen appears, with the Settings tab active by default. 2. Tap Scan Now to conduct a security scan. The Security Scan performs a combination security, vulnerability, and privacy scan and returns the result. 3. In the example shown, Citibank has been detected as a fake banking app, (present on the device before Mobile Security was installed.) Apps are also recommended for removal (or to trust). 4. Tap Uninstall to uninstall the fake app. A Details screen defines the security threats. 5. Tap Uninstall again. A popup will ask if you want to uninstall the app; tap Uninstall once more to uninstall it. Figure 30. Security Scan Figure 31. Scan Now Figure 32. Device Scan Results Figure 33. Fake App Details Figure 34. Uninstall App 19
20 6. Back in the Security Scan > Settings screen, tap the Settings options to configure them. These include: Protection Strength. Choose the level for alerts: Low. Receive alerts only for apps confirmed as fraudulent or dangerous. Normal. Receive alerts for regular daily use, without notifications about minor risks. High. Receive alerts for apps that show any signs of fraud or danger. Real-Time Scan. Option is checked by default and provides a real-time scan of all downloaded apps. Pre-Installation Scan. Disabled by default. Blocks malware from Google Play before it s installed. To enable, see the following section. Scan Memory Card. This option, unchecked by default, checks the memory card for security threats. >Scan Option. Scan only apps (default) or Scan all files. Trusted Apps. Tap Trusted Apps > App then Remove from the Trusted List to remove an app from the list. Figure 35. Scan Now Figure 37. Trusted Apps Figure 36. Scan Option Figure 38. Remove from the Trusted List 20
21 To enable the Pre-installation Scan: 1. Tap the Pre-installation Scan panel in the Security Scan > Settings screen. The Pre-installation Scan toggle screen appears. 2. Note that the Pre- Installation Scan requires the Accessibility permission for Mobile Security to be turned on. 3. Tap the Pre-installation Scan toggle from Off to On. The demo screen for turning on Accessibility appears. 4. Tap Turn On Now. The Accessibility screen appears. 5. Scroll down the screen and tap the panel for Mobile Security. The screen to enable Mobile Security accessibility appears. Figure 39. Security Scan > Settings Figure 40. Pre-Installation Scan Figure 32. Demo: Turn On Accessibility Figure 33. Accessibility 21
22 6. Note that Accessibility Permission is needed for SafeSurfing, Messenger Protection, the Preinstallation Scan and App Freeze. 7. Tap the toggle from Off to On. 8. If your device has Secure Startup turned on in Android, a popup will appear to turn it off. Mobile Security wants permission to monitor your actions and retrieve window content. 9. Tap OK. Your PIN window appears. 10. Enter your PIN and tap Done. 11. Mobile Security s Accessibility permission is turned on. 12. Tap the back-arrow. The Pre-Installation Scan toggle is now On. Figure 43. Mobile Security > Accessibility Figure 44. Turns Off Android Secure Startup Figure 45. Enter PIN Figure 46. Mobile Security Accessibility On 22
23 13. Now all apps downloaded from Google Play will be scanned for malware before they re installed. 14. Test the Pre-Installation Scan by downloading an Antivirus Test app from Google Play. 15. Enter Antivirus Test into the Google Play Search field. 16. When the search results appear, pick an antivirus test for download. 17. For example, tap Test your antivirus. 18. Mobile Security s Pre- Installation Scan presents a popup saying Test your antivirus is dangerous. 19. Do not install the app, as it presents dangers to your device. 20. Use the back-arrow on your device to back out of the Install screen. Figure 47. Pre-Installation Scan On Figure 48. Antivirus Test Figure 49. Test Your Antivirus is dangerous 23
24 Updates and History: 1. Tap the Update tab in the Virus Scanner screen. The Update options appear. 2. Tap the Update button to manually update the pattern file. Mobile Security updates. If Automatic Scan is checked, a scan is conducted after an update. 3. Variously check Auto Update, Auto Updates require Wi-Fi. 4. Tap Auto Update Schedule and a popup appears, letting you choose your Update Interval: Daily, Weekly, or Monthly. 5. Tap the History tab, then the Security Scan or Updates panels to obtain a history of threats found or updates conducted. 6. Tap the Trashcan in the individual History panels if you wish to delete the history. Figure 50. Updates Figure 51. History Figure 52. Update Interval Figure 53. Security Scan History 24
25 Messenger Protection Mobile Security s Messenger Protection alerts you to dangerous links when you use Line and/or WhatsApp on your mobile device. To use the function, you need to first install Line or WhatsApp and enable the Accessibility option for Mobile Security in your phone settings. (See previous section.) In this example, Line has also been previously installed. To use Messenger Protection: 1. Tap Messenger Protection in the Mobile Security Console. The Messenger Protection screen appears, with the function turned Off by default. 2. Tap the toggle from Off to On. You re now protected from dangerous links in LINE and WhatsApp. 3. Tap Settings to set your Protection Level. Low. Blocks only sites confirmed as fraudulent or dangerous. Normal. Provides balanced protection without blocking minor risks. High. Blocks sites showing any signs of fraud or malicious software. Note: The level you select here will also be used for SafeSurfing. Figure 54. Messenger Protection Figure 55. Messenger Protection > Applications Figure 56. Messenger Protection > Settings 25
26 System Tuner Mobile Security s System Tuner lets you optimize the battery and memory settings on your device, as well as to clean up your clipboard data, web browser and Google Play search histories. Battery optimization tools include Just-a-Phone Mode, to manually or automatically turn off many settings to save battery power when it s especially low; and the Smart Power Saver, to automatically change Wi-Fi, 3G/4G, and Bluetooth connections upon idle to also save power. To use System Tuner: 1. Tap System Tuner in the Mobile Security Console. The System Tuner screen appears. 2. Tap Add a shortcut to homescreen to add a shortcut for future quick optimization of your phone, saving memory and battery. 3. Note the popup banner at the top telling you that Mobile Security needs more permissions before you can use all of the System Tuner features. 4. Tap the popup. The Allow Permissions popup appears. Figure 57. System Tuner Figure 58. System Tuner Screen 26
27 5. Depending on your configuration, different permission options will be highlighted as needed. 6. In this example, tap Apps with usage access. A demo screen appears, suggesting you tap Turn On Now. 7. When the Usage Data Access screen appears, tap Mobile Security to turn on usage data access for the app. The Usage Data Access screen for Mobile Security appears. 8. Tap the toggle Allow usage tracking from Off to On. 9. When you re done, tap the back arrow to return to the Allow Permissions screen. Figure 59. Allow Permissions Figure 60. Turn On Now Figure 61. Usage Data Access Figure 62. Usage Data Access > Mobile Security 27
28 10. Tap Phone permission. The demo screen appears, asking you to tap Turn On Now. Note: The permissions screen can be accessed through your phone Settings > Apps > App manager > Mobile Security > App Settings > Permissions. 11. Tap Turn on Now. The App Info screen for Mobile Security appears. 12. Tap Permissions for Mobile Security. The App Permissions screen appears. 13. Toggle on each of the App Permissions in turn. Figure 63. Allow Permissions Figure 64. Turn On Now Figure 65. App Info Figure 66. App Permissions > Mobile Security 28
29 14. When you ve finished turning on the permissions you ve chosen, tap your device back-arrow to return to the Permissions popup, then tap OK to complete the process. System Tuner is now set up to maximally optimize your system. 15. To optimize your system, do one of two things: Tap Optimize for a quick optimization. Tap Apps in Use, check those apps you wish to keep running, then tap Optimize. 16. Mobile Security optimizes your system. Figure 67. Permissions Figure 68. Optimize Apps in Use Figure 69. Apps in Use Figure 70. Optimizing 29
30 17. When it s done, you re presented with a Device Optimized screen that calculates the extra memory and battery time saved. 18. To further optimize your system by doing a Force Stop on selected apps, tap Open App Freeze. The App Freeze screen opens. 19. Check apps you want to freeze, then tap Stop Apps. 20. Selected apps will be force stopped, optimizing memory and battery. Reopen the app to restart all of its functions at any time. 21. Note that you cannot multi-task while this operation is in progress; i.e., when Mobile Security is freezing a number of apps. Tap Cancel to back out, if so desired. 22. When the App Freeze is complete, tap Close to close the screen. Figure 71. Open App Freeze Figure 72. Stop Apps Figure 73. Stopping Apps Figure 74. App Freeze Complete 30
31 To use Just-a-Phone Mode: 1. Tap the Just-a-Phone Mode toggle to the right to turn it on. The Ready for Just-a-Phone Mode screen appears. 2. Tap Turn On to enable Just-a-Phone Mode. The Just-a-Phone Mode is enabled according to the default Just-a-Phone Options. 3. To adjust those options, tap Auto Justa-Phone. The Auto Just-a-Phone screen appears. 4. Tap Auto Activate and Auto Activate Threshold to enable those auto-activate functions. 5. Tap Set Schedule to adjust the schedule Start and Stop times, and tap OK. Figure 75. Just-a-Phone Mode Figure 76. Ready for Just-a- Phone Mode Figure 77. Auto Just-a-Phone Figure 78. Set Schedule Time 31
32 6. Tap Set Threshold to set the battery power threshold at which Auto Just-a-Phone is activated. 7. By default, the Just-a- Phone Options section shows all four items checked: Switch off 3G/4G Switch off Wi-Fi Switch off Bluetooth Stop any running apps 8. Uncheck any options you wish to keep active during Just-a-Phone, whether on-demand or auto-activated, and tap Save. Figure 79. Battery Power Threshold Figure 80. Just-a-Phone Options To enable Smart Power Saver: 1. Tap the Smart Power Saver panel to access its settings. 2. Check Turn on Smart Power Saver to turn it on. 3. The option to maintain your 3G/4G connection, so you can receive instant messages and , is checked by default. Uncheck it if you wish. 4. Check/uncheck the various settings in Smart Standby and Smart Wi-Fi to enable the changes to W-Fi, 3G/4G, and Bluetooth to save power. Figure 81. Battery > Smart Power Saver Figure 82. Turn On Smart Power Saver 32
33 5. For Smart Standby, set how long after the screen darkens to switch-off 3G/4G and Bluetooth. 6. Also for Smart Standby, set at what intervals 3G/4G will switch on again to make a connection for /text messages. 7. For Smart Wi-Fi, set the interval to switch off Wi-Fi. 8. Again, for Smart Wi-Fi, set the interval when it will switch on again to make a connection. Figure 83. Switch off 3G/4G and Bluetooth Figure 84. Switch On 3G/4G Figure 85. Switch off Wi-Fi Figure 86. Switch on Wi-Fi 33
34 App Manager App Manager lets you remove unwanted files and apps, including setup files, which can take up unnecessary memory and space on your device. To use App Manager: 1. Tap App Manager to manage your apps. A demo screen appears, showing you how to change your sorting options. 2. Tap Ok to close the demo screen. The App Manager Uninstall tab displays. 3. Using the Sort menu in the upper right, sort by Size, Date, Name, or Last used, if you wish. 4. Scroll down to view apps you might want to uninstall; or tap Preinstalled apps and check the checkbox for an app to uninstall. Figure 87. App Manager Figure 88. App Manager > Uninstall 5. Tap Uninstall. A screen or popup appears, asking Do you want to uninstall this app? 6. Tap OK to uninstall the app(s). The app is uninstalled. 7. Tap Setup Files to delete APK files. Lists of Installed and Not Installed APK files appear. 8. Check those you wish to delete, then tap Delete to delete the setup files. The files are deleted. Figure 89. Uninstall App Figure 90. Setup Files 34
35 Network Protection Network Protection enables two types of protection on your mobile device: SafeSurfing provides web threat protection when you re surfing the net; and Wi-Fi Checker checks for unsecured Wi-Fi hotspots and notifies you when your mobile device provides an offer to connect to it. You can accept or reject the connection and add the Wi-Fi network to your list of Trusted or Blocked Wi-Fi hotspots. To use Network Protection: 1. Tap Network Protection in the Mobile Security Console. The Network Protection settings screen appears. 2. SafeSurfing and the Wi-Fi Checker are turned on by default and the SafeSurfing Protection Level tab is pre-selected. 3. Use the selection slider to set the strength of your SafeSurfing Protection. The level you set will also be applied to Messenger Protection. Low. Blocks sites confirmed as fraudulent or dangerous. Normal. Provides balanced protection without blocking minor risks. High. Blocks sites showing any signs of fraud or malicious software. Figure 91. Network Protection Figure 92. Network Protection > SafeSurfing 35
36 4. When you browse to a dangerous website in your browser, Mobile Security blocks it and gives you a Dangerous Page message, as shown in this test site. 5. To add a URL to the SafeSurfing Blocked or Approved Lists, tap the name of the respective list from the settings page or the drop-down menu; e.g., Blocked List. The Add screen appears. 6. Tap Add. A popup appears. Type the name the item and the URL and tap Save. The URL is added to the Blocked or Approved List. Figure 93. Dangerous Page Figure 94. Add URL to Blocked List Figure 95. Add Specific URL 36
37 7. If it s in the Blocked List, SafeSurfing will block it if you try to go to the website. 8. Similarly, the Wi-Fi Checker will notify you with a popup if you if your mobile device is connected or tries to connect to an unsecured Wi-Fi network. 9. Tap Settings to forget the unsecured Wi-Fi network in the future; or tap Trust Wi-Fi to add it to the Trusted Wi-Fi List. 10. To view trusted Wi-Fi hotspots, tap the Wi-Fi Checker tab. The Trusted Wi-Fi List appears. 11. Tap the Trusted Wi-Fi List to view the list; then if you wish, select any Wi-Fi network and tap Trashcan to remove it from the list. Figure 96. Suspicious Page Figure 97. Connection Not Secure Figure 98. Wi-FI Checker Figure 99. Trusted Wi-Fi List 37
38 12. Tap the History tab to view your SafeSurfing History; then tap the SafeSurfing panel to show the history of all sites blocked by SafeSurfing. 13. Once you see the list, tap-hold the item(s), then tap the Trashcan to delete all selected SafeSurfing events; or tap a specific event, then the Trashcan to delete the history. Figure 100. History Figure 101. SafeSurfing History 38
39 Parental Controls Mobile Security s Parental Controls lets you lock apps and block inappropriate websites to help protect your kids. To use Parental Controls: 1. Tap Parental Controls to access its settings. The Password screen appears. 2. The first time you enter Parental Controls or Lost Device Protection settings, the Unlock screen defaults to requiring your Trend Micro Account Password. 3. Enter your Trend Micro Account Password to unlock the Parental Control settings screens. The App Lock screen appears, with the toggle turned Off. 4. If you wish, tap the Lock Settings icon in the upper right corner of the screen to change your Password to a Pattern or a PIN, which may be easier to remember. The Lock Settings screen appears. 5. Tap Pattern if you wish to create a Pattern Lock. Figure 102. Parental Controls Figure 103. Enter Password Figure 104. App Lock Figure 105. Lock Settings 39
40 6. Draw a Pattern and when prompted, draw it again to confirm it and tap OK. NOTE: Use a less obvious, more complicated pattern than the one shown, to increase your protection. Your password changes to the unlock pattern you ve specified. 7. Similarly, tap PIN if you wish to use a 4-digit PIN. The Set PIN screen appears. 8. Type in a 4-digit PIN, then enter it again to confirm it, and tap OK. Your PIN is created successfully. 9. You ll use the Pattern or PIN when you want to make non-critical changes to your Mobile Security settings. For changes Trend Micro deems critical, you ll still need your Trend Micro Account Password. Figure 106. Set Pattern Figure 108. Set Up a 4-digit PIN Figure 107. Pattern Created Successfully Figure 109. PIN Created Successfully 40
41 To configure App Lock: 1. Tap the App Lock toggle to turn the function On. A demo screen appears; tap OK to close it. App Lock is turned on and your device Settings app is locked by default. 2. Tap Apps you wish to lock. The apps you add to the App Lock list will prompt you to enter the unlock key when you open them for use. 3. Note the Lock icon below the App Lock On/Off toggle. When selected, those apps you ve locked appear at the top, sorted alphabetically. Tap the lock Off to return to a basic alphabetical sort ordered by all the apps on your device. Figure 110. App Lock > Lock Sort Figure 111. Apps Locked > Alphabetical Sort 41
42 To configure Website Filter: 1. Tap the Website Filter toggle to turn it On. A demo screen appears; tap Close to close it. The Protection Level is Teen by default. 2. Set your Protection Level by tapping the selection button for the preferred level: Child. Provides filtering for children 9 or younger. Pre-teen. Provides filtering for children between 10 and 13. Teen. Provides filtering for young adults between 14 and Tap Blocked List to add a website you wish to block. The Blocked List appears. 4. Tap Add. The Lock screen appears. 5. Enter your Trend Micro Account Password and tap OK. The Add popup appears. 6. Type a Name for the website block, then enter the actual URL for the Website and tap Save. The website is added to the Blocked List. 7. You can now test for web threats and filtered websites. (The settings apply to your Native Android browser and Chrome only.) Figure 112. Website Filter Figure 114. Password Required Figure 113. Website Filter Demo Figure 115. Blocked List 42
43 8. Enter a URL into your browser s search field that you know or suspect is dangerous. 9. OR: Enter a URL that is inappropriate for the Protection Level you ve designated for your children. 10. OR: Enter a URL you ve put on the Blocked List. 11. In each case, Mobile Security will block the website and display a warning. 12. Tap Approved List to add a website to the Approved List; then repeat the instructions given above for adding the URL. 13. Tap History to view a history of blocked webpages. Figure 116. Dangerous Page Figure 117. Off Limits Figure 118. Approved List Figure 119. Parental Controls History 43
44 Uninstall Protection To enable Uninstall Protection: 1. Back in the main Parental Controls screen, toggle Uninstall Protection On to protect Mobile Security from unauthorized uninstallation and to keep your kids protected with Parental Controls. A screen appears, explaining how to use Uninstall Protection and to turn it off, if you wish to uninstall Mobile Security 2. Tap Ok. A screen appears for you to Activate Phone Administrator. 3. Review the operations allowed when you activate the phone administrator, then tap Activate. A screen appears for you to provide your password, PIN, or pattern. 4. In this example, Provide your PIN. A popup screen appears, indicating Device Administrator Activated. Figure 120. Uninstall Protection Figure 121. Using Uninstall Protection Figure 122. Activate Phone Administrator Figure 123. Provide your PIN 44
45 5. Tap OK to close the popup. Uninstall Protection is on. Figure 124. Device Administrator Activated Figure 125. Uninstall Protection On Lost Device Protection To enable Lost Device Protection: 1. Back in the main Console, tap Lost Device Protection. The login screen appears. 2. Enter your Password, Pattern, or PIN. The Lost Device Protection screen appears, with the Find My Android tab selected by default and three options displayed: SIM Card Lock. Lock this device if the SIM card is changed or removed. Device Name. Click the Edit icon to change the device name. Remote Lock. Display this message after locking the device. Figure 126. Lost Device Protection Figure 127. Password, Pattern, or PIN 45
46 Remote Wipe. Allows you to do a partial or full wipe of your device remotely. 3. Tap SIM Card Lock if you wish to lock your device when the SIM card is changed or removed. A Password Required screen appears. 4. Enter your Trend Micro Account password and tap OK. SIM Card Lock is enabled. 5. Tap the Device Name panel edit pencil to change your device s name, make your changes in the edit window, and tap Save. 6. Tap the Remote Lock panel edit pencil to display the message after locking the device, make your changes in the Edit Message screen, and tap Save. Your message changes are saved. Figure 128. Protection Figure 129. Password Required 7. Tap the Remote Wipe tab to access the feature. The Remote Wipe screen appears, with Full Remote Wipe selected. This lets you delete all content from the Lost Device Protection website in the event your device is lost or stolen. Figure 130. Edit Message Figure 131. Change Remote Wipe 46
47 Note: Full Remote Wipe is selected if you ve turned on Uninstall Protection, as given in the previous section. Otherwise, Partial Remote Wipe will be selected. 8. If you wish, tap Partial Remote Wipe to change to the partial wipe. The Password Required screen appears. 9. Enter your password and tap OK. 10. The option switches to Partial Remote Wipe and turns off the Uninstall Protection of Mobile Security. Turning Uninstall Protection back on will revert the wipe function to Full Remote Wipe. 11. Manage your protection in the Lost Device Protection Portal. See below for details. Figure 132. Password Required Figure 133. Partial Remote Wipe 47
48 To Use Secret Snap: 1. Tap Secret Snap to set your device to take a photo after a number of incorrect attempts to unlock your device. The Secret Snap editor appears. 2. Tap the toggle to turn Secret Snap from Off to On. The Activate Phone Administrator screen appears. 3. Tap Activate to activate the administrator. The Password/PIN/Pattern screen appears. 4. In this example, provide your PIN. Figure 134. Secret Snap Figure 135. Activate Phone Administrator Figure 136. Provide your PIN 48
49 5. Secret Snap is turned on. 6. Tap the panel to set the number of incorrect attempts to access your device before a photo is taken. 7. Choose 3, 5, or 7 attempts and tap Save. 8. Tap the Notification pencil to change the address where the photo notification will be sent, then tap Save. You ll be able to view the photos taken in this After you ve recovered your phone, you can review any photos stored on your device by tapping the Secret Snap Photos panel. The photo list appears. Figure 137. Secret Snap Figure 138. Incorrect Attempts Figure for Notification Figure 140. Secret Snap Photos 49
50 10. Tap a photo to view it, or tap the Trashcan to delete it. 11. As mentioned, you can also view the photo in the notification sent to you by Mobile Security. This can be used with the Lost Device Protection Portal s location feature to help locate the person who has found or stolen your device. 12. Click the link To Locate Your Device using the Lost Device Protection Portal. 13. To obtain assistance, visit obilehelp. Figure 141. Secret Snap Photos List Figure 142. Individual Secret Snap Photo Figure 34. Secret Snap Notification with Photo 50
51 Lost Device Protection Portal To access the Lost Device Protection Portal: 1. Launch your browser on your PC and type endmicro.com/ into the search field, and hit Enter. The Lost Device Protection Portal webpage appears. 2. Tap Find Now or Sign in to sign into your Trend Micro account. The Sign In page appears. 3. Type the address and password you used to create your Trend Micro account and click Sign in. The Lost Device Protection Portal appears. 4. You re presented with a Device List on the left, a Bing Map on the right with a GPS/Bing estimate of your location, and a toolbox to perform various operations regarding your lost or stolen device. Figure 144. Lost Device Protection Portal Sign In Figure 145. Sign In 51
52 5. In the Device List, click Hide to hide any device in the main list. Click the down-arrow to see Hidden Devices. 6. Click Share to share the device s location with a trusted friend. 7. Click Alarm to sound a one-minute alarm on your missing mobile device, even if it has been set to silent mode. 8. Click Locate to locate the phone on the map. 9. Click Reset to force stop apps and to Reset the Lock Screen Password. 10. Click Lock to stop anyone from using your missing mobile device. When you recover your device, click Unlock to unlock it, then use the Unlock Key provided or your Trend Micro password to complete the unlock. 11. Click Device Detail (below the device icon in the list) to view the unlock code that can be entered into the device interface to unlock the device instead of the master account password. This key can also be ed to you at your account address by taping Yourself an Unlock Key on the device once it s found. Figure 146. Lost Device Protection Options 12. Click Wipe to permanently delete all Figure 147. Unlock Figure 148. Device Unlock 52
53 the data stored on your missing mobile device. 13. A warning appears. If you wish to wipe your device, click OK. Warning: Using this feature will perform a factory reset of your device. For testing or review purposes, please ensure you are using a test device or have a complete backup of your information. Once reset, TMMS will be removed from the device and the location feature will no longer function. Figure 149. Wipe Warning 53
54 Social Network Privacy Trend Micro Mobile Security also includes Social Network Privacy scanner to help edit your Facebook Privacy Settings. To access Facebook Privacy Scanner: 1. Tap Social Network Privacy in the main Mobile Security Console. The Remove Privacy Risks screen appears. 2. Tap Sign into Facebook to check your privacy settings. The Facebook Login screen appears. 3. Enter the address and password you use to sign into Facebook and tap Log In. Facebook Privacy Scanner checks your privacy settings. 4. When it s done checking, it presents you with the analysis. Figure 150. Scan Facebook Figure 151. Facebook Privacy Scanner Figure 152. Enter Facebook Address and Password Figure 153. Checking Your Privacy Settings 54
55 5. Tap each item in the list to reset it to the recommended setting. A popup appears, letting you make the change. 6. Check the recommended Privacy Setting. In this case, change the setting from Friends of friends to just Friends, to increase your privacy, and tap OK. 7. Privacy Scanner makes the change, saying Great! Issue Fixed. 8. Since Facebook periodically changes its privacy policies or adds new features to the social network, you should periodically rescan your privacy settings to ensure your privacy. Figure 154. Two Privacy Concerns Figure 155. Editing Privacy Setting Figure 156. Great! Issue Fixed 55
56 Call Blocking To block unwanted calls: 1. Back in the main TMMS Console screen, tap Call Blocking. The Call Blocking screen displays, with the Call tab selected by default and Call Blocking enabled. Tap the slider to the left to disable the function. 2. Tap Filtering Method to change the filtering option in the popup: Stop only blocked callers Allow only approved callers Allow approved and anonymous callers 3. Tap Action to change the action to be performed in the popup. Reject call Silence device Reject call + send reply 4. Tap Reject call + send reply and you re given three preset options for Automatic Reply. Figure 157. Call Blocking Figure 158. Call Figure 159. Filtering Method Figure 160. Action 56
57 5. Check Block Annoying Calls from unknown numbers to disconnect them within three seconds. 6. Tap the Blocked / Approved lists to add a number to either list. The List tool at the top of the screen also gives access to the lists. 7. Tap the Plus (+) tool to add the number; you can also use the drop-down to switch easily between lists. 8. Tap History > Blocked Call History to review your Blocked Call History. Figure 161. Block Annoying Calls Figure 162. Blocked / Approved Lists Figure 163. Blocked Call History 57
58 Settings Trend Micro Mobile Security provides system settings for app management. 1. Tap Mobile Security on your device to open the Console. 2. Tap the Settings menu on your device to open the popup. 3. Here, you have access to various options. Settings. Access various system-level settings. Share. Send friends or associates a recommendation to use Trend Micro Mobile Security. Send Feedback. Provide a rating and review on Google Play and send feedback to Trend Micro. Renew / Activate. Renew or activate a subscription. Help. Get Online Help with Mobile Security. 4. Tap Settings to access system-level options. The Settings screen appears, with the list of options available. Scroll down to view the options. Trend Micro Account. Account you re registered to. Expiration Date. Date your subscription expires. Serial Number. 20- character serial number Renew / Activate. Purchase/renew or activate a subscription. Sign Out. Disconnect your Trend Micro account. Check your Trend Micro Account. Manage your account and subscriptions. Set up alternate addresses. Send from an unlock key from the lock screen to your Trend Micro account and the address you set up here. Display the app icon on the status bar. Check here to show Mobile Security on the status bar. Figure 164. Settings Popup Menu (Device) Figure 165. Settings (1) 58
59 Settings (continued) Uninstall. Uninstall Mobile Security with your Trend Micro Account password when Uninstall Protection is turned on. Low Power Alert. Send a notification when the battery is less than 50%. Low Memory Alert. Send a notification when the memory usage is over 80% About. Product details and version number. Help. Access Online Help. Collect logs. Collect logs to send to Trend Micro. Log history. Logs sent to Trend Micro. Help make Mobile Security better. Anonymously share device information with Trend Micro. Figure 166. Settings (2) Figure 167. Settings (3) 59
TREND MICRO Mobile Security 10.0 for Android Product Guide
 H TREND MICRO Mobile Security 10.0 for Android Product Guide V1.0 Trend Micro, Incorporated US Headquarters 224 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 U.S.A. Phone: +1 (817) 569-8900
H TREND MICRO Mobile Security 10.0 for Android Product Guide V1.0 Trend Micro, Incorporated US Headquarters 224 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 U.S.A. Phone: +1 (817) 569-8900
TREND MICRO Mobile Security 2.0 for ios Product Guide
 H TREND MICRO Mobile Security 2.0 for ios Product Guide (QR Code: US, CAN, AU, NZ) V1.0 Trend Micro, Incorporated US Headquarters 224 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 U.S.A Phone:
H TREND MICRO Mobile Security 2.0 for ios Product Guide (QR Code: US, CAN, AU, NZ) V1.0 Trend Micro, Incorporated US Headquarters 224 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 U.S.A Phone:
TREND MICRO Mobile Security 6.0 for Android Product Guide
 H TREND MICRO Mobile Security 6.0 for Android Product Guide QR Code: TMMS 6.0 GLOBAL (US, ANZ, Canada, Mexico, Brazil, Taiwan) V1.0 Trend Micro, Incorporated US Headquarters 224 E. John Carpenter Freeway,
H TREND MICRO Mobile Security 6.0 for Android Product Guide QR Code: TMMS 6.0 GLOBAL (US, ANZ, Canada, Mexico, Brazil, Taiwan) V1.0 Trend Micro, Incorporated US Headquarters 224 E. John Carpenter Freeway,
TREND MICRO Mobile Security 6.0 for ios - Product Guide
 H TREND MICRO Mobile Security 6.0 for ios - Product Guide V1.0 Trend Micro, Incorporated US Headquarters 224 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 - USA Phone: +1 (817) 569-8900 Toll-free:
H TREND MICRO Mobile Security 6.0 for ios - Product Guide V1.0 Trend Micro, Incorporated US Headquarters 224 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 - USA Phone: +1 (817) 569-8900 Toll-free:
Trend Micro Antivirus for Mac 2015
 H Trend Micro Antivirus for Mac 2015 Product Guide V1.2 Trend Micro Incorporated 225 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 U.S.A. Phone: +1 (817) 569-8900 Toll-free: (888) 762-8763
H Trend Micro Antivirus for Mac 2015 Product Guide V1.2 Trend Micro Incorporated 225 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 U.S.A. Phone: +1 (817) 569-8900 Toll-free: (888) 762-8763
Password Manager Product Guide for Mac and ios
 H Password Manager Product Guide for Mac and ios Trend Micro Incorporated 225 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 U.S.A. Phone: +1 (817) 569-8900 Toll-free: (888) 762-8763 www.trendmicro.com
H Password Manager Product Guide for Mac and ios Trend Micro Incorporated 225 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 U.S.A. Phone: +1 (817) 569-8900 Toll-free: (888) 762-8763 www.trendmicro.com
Password Manager. Product Guide. for PC (v3.8) and Android (v5.0) V1.0
 H Password Manager for PC (v3.8) and Android (v5.0) Product Guide V1.0 Trend Micro Inc. 225 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 U.S.A. Phone: +1 (817) 569-8900 Toll-free: (888) 762-8763
H Password Manager for PC (v3.8) and Android (v5.0) Product Guide V1.0 Trend Micro Inc. 225 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 U.S.A. Phone: +1 (817) 569-8900 Toll-free: (888) 762-8763
Password Manager. Product Guide. for PC (3.7) and Android (3.8) V1.0
 H Password Manager for PC (3.7) and Android (3.8) Product Guide V1.0 Trend Micro Inc. 225 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 U.S.A. Phone: +1 (817) 569-8900 Toll-free: (888) 762-8763
H Password Manager for PC (3.7) and Android (3.8) Product Guide V1.0 Trend Micro Inc. 225 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 U.S.A. Phone: +1 (817) 569-8900 Toll-free: (888) 762-8763
Quick Heal Mobile Security. Free protection for your Android phone against virus attacks, unwanted calls, and theft.
 Quick Heal Mobile Security Free protection for your Android phone against virus attacks, unwanted calls, and theft. Product Highlights Complete protection for your Android device that simplifies security
Quick Heal Mobile Security Free protection for your Android phone against virus attacks, unwanted calls, and theft. Product Highlights Complete protection for your Android device that simplifies security
Features. Product Highlights. Not just an app, but a friend for your phone. Optimization. Speed. Battery. Storage. Data Usage
 PRO Not just an app, but a friend for your phone. Product Highlights Fonetastic is an all-in-one app for Android devices. Built with multiple productivity and security features, it enhances your device
PRO Not just an app, but a friend for your phone. Product Highlights Fonetastic is an all-in-one app for Android devices. Built with multiple productivity and security features, it enhances your device
Mobile Security for Android devices
 Mobile Security for Android 2.2 3.2 devices 1 Swisscom Mobile Security for Android 2.2 3.2 devices This guide covers mobile devices (smartphones, tablets) that use the Android operating system (version
Mobile Security for Android 2.2 3.2 devices 1 Swisscom Mobile Security for Android 2.2 3.2 devices This guide covers mobile devices (smartphones, tablets) that use the Android operating system (version
Quick Heal Total Security for Android. Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping.
 Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Password Manager. Product Guide. for Mac (3.8) and ios (5.0) V1.0
 H Password Manager for Mac (3.8) and ios (5.0) Product Guide V1.0 Trend Micro Incorporated 225 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 U.S.A. Phone: +1 (817) 569-8900 Toll-free: (888)
H Password Manager for Mac (3.8) and ios (5.0) Product Guide V1.0 Trend Micro Incorporated 225 E. John Carpenter Freeway, Suite 1500 Irving, Texas 75062 U.S.A. Phone: +1 (817) 569-8900 Toll-free: (888)
DirectPass Password Manager for PC
 H Trend Micro DirectPass Password Manager for PC Product Guide Trend Micro, Inc. 10101 N. De Anza Blvd. Cupertino, CA 95014 T 800.228.5651 / 408.257.1500 F 408.257.2003 www.trendmicro.com Trend Micro Incorporated
H Trend Micro DirectPass Password Manager for PC Product Guide Trend Micro, Inc. 10101 N. De Anza Blvd. Cupertino, CA 95014 T 800.228.5651 / 408.257.1500 F 408.257.2003 www.trendmicro.com Trend Micro Incorporated
Quick Heal Mobile Security. Free protection for your Android phone against virus attacks, unwanted calls, and theft.
 Free protection for your Android phone against virus attacks, unwanted calls, and theft. Product Highlights With an easy-to-update virus protection and a dynamic yet simple interface, virus removal from
Free protection for your Android phone against virus attacks, unwanted calls, and theft. Product Highlights With an easy-to-update virus protection and a dynamic yet simple interface, virus removal from
Quick Heal Total Security for Android. Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping.
 Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that simplifies security and significantly
Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that simplifies security and significantly
Multi device User Guide
 Multi device User Guide Version 1.03 Quick Heal Technologies Ltd. www.quickheal.com Fonetastic-Multi device User guide Version 1.03 Copyright & License Information Copyright 2017 Quick Heal Technologies
Multi device User Guide Version 1.03 Quick Heal Technologies Ltd. www.quickheal.com Fonetastic-Multi device User guide Version 1.03 Copyright & License Information Copyright 2017 Quick Heal Technologies
3CX Mobile Device Manager
 3CX Mobile Device Manager Manual 1 Copyright 2013, 3CX Ltd. http://www.3cx.com E-mail: info@3cx.com Information in this document is subject to change without notice. Companies names and data used in examples
3CX Mobile Device Manager Manual 1 Copyright 2013, 3CX Ltd. http://www.3cx.com E-mail: info@3cx.com Information in this document is subject to change without notice. Companies names and data used in examples
Quick Heal AntiVirus for Mobile User Guide
 Quick Heal AntiVirus for Mobile User Guide Version 1.0 Quick Heal Technologies Ltd. www.quickheal.com Copyright & License Information Copyright & License Information Copyright 2018 Quick Heal Technologies
Quick Heal AntiVirus for Mobile User Guide Version 1.0 Quick Heal Technologies Ltd. www.quickheal.com Copyright & License Information Copyright & License Information Copyright 2018 Quick Heal Technologies
Trend Micro Security 2015 Product Guide
 H Trend Micro Security 2015 Product Guide Trend Micro Antivirus+ Security Trend Micro Internet Security Trend Micro Maximum Security Trend Micro Premium Security Trend Micro Incorporated 225 E. John Carpenter
H Trend Micro Security 2015 Product Guide Trend Micro Antivirus+ Security Trend Micro Internet Security Trend Micro Maximum Security Trend Micro Premium Security Trend Micro Incorporated 225 E. John Carpenter
WiFi Security User Guide
 WiFi Security User Guide Copyright Copyright 2018 Webroot. All rights reserved. Webroot WiFi Security User Guide Information in this document is subject to change without notice. The software described
WiFi Security User Guide Copyright Copyright 2018 Webroot. All rights reserved. Webroot WiFi Security User Guide Information in this document is subject to change without notice. The software described
Quick Heal Mobile Security. Anti-Theft Security. Real-Time Protection. Safe Online Banking & Shopping.
 Anti-Theft Security. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights With an easy-to-update virus protection and a dynamic yet simple interface, virus removal from your mobile
Anti-Theft Security. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights With an easy-to-update virus protection and a dynamic yet simple interface, virus removal from your mobile
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme files,
FAQ for KULT Basic. Connections. Settings. Calls. Apps. Media
 FAQ for KULT Basic 1. What do the Icons mean that can be found in notifications bar at the top of my screen? 2. How can I move an item on the home screen? 3. How can I switch between home screens? 4. How
FAQ for KULT Basic 1. What do the Icons mean that can be found in notifications bar at the top of my screen? 2. How can I move an item on the home screen? 3. How can I switch between home screens? 4. How
Kaspersky Mobile Security 9. Reviewer s Guide
 Kaspersky Mobile Security 9 Reviewer s Guide The purpose of this document is to provide an introduction to Kaspersky Mobile Security 9 (KMS 9). KMS 9 is a product that has been designed to protect the
Kaspersky Mobile Security 9 Reviewer s Guide The purpose of this document is to provide an introduction to Kaspersky Mobile Security 9 (KMS 9). KMS 9 is a product that has been designed to protect the
Quick Start Guide. PC, Mac, Android & ios
 Quick Start Guide PC, Mac, Android & ios Installation for PC Please refer to the ReadMe file on the installation disc or to the Trend Micro website for detailed system requirements. If you encounter difficulties
Quick Start Guide PC, Mac, Android & ios Installation for PC Please refer to the ReadMe file on the installation disc or to the Trend Micro website for detailed system requirements. If you encounter difficulties
Comodo Mobile Security for Android Software Version 2.5
 Comodo Mobile Security for Android Software Version 2.5 User Guide Guide Version 2.5.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Mobile
Comodo Mobile Security for Android Software Version 2.5 User Guide Guide Version 2.5.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1.Introduction to Comodo Mobile
College of Pharmacy Windows 10
 College of Pharmacy Windows 10 Windows 10 is the version of Microsoft s flagship operating system that follows Windows 8; the OS was released in July 2015. Windows 10 is designed to address common criticisms
College of Pharmacy Windows 10 Windows 10 is the version of Microsoft s flagship operating system that follows Windows 8; the OS was released in July 2015. Windows 10 is designed to address common criticisms
Bitdefender Antivirus Plus 2018 User's Guide
 USER'S GUIDE Bitdefender Antivirus Plus 2018 User's Guide Publication date 07/03/2017 Copyright 2017 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced or transmitted
USER'S GUIDE Bitdefender Antivirus Plus 2018 User's Guide Publication date 07/03/2017 Copyright 2017 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced or transmitted
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
ESET ENDPOINT SECURITY FOR ANDROID
 ESET ENDPOINT SECURITY FOR ANDROID Installation Manual and User Guide Click here to download the most recent version of this document Contents 1. Installation...3 of ESET Endpoint Security 1.1 Installation...3
ESET ENDPOINT SECURITY FOR ANDROID Installation Manual and User Guide Click here to download the most recent version of this document Contents 1. Installation...3 of ESET Endpoint Security 1.1 Installation...3
Review Kaspersky Internet Security - multi-device 2015 online software downloader ]
![Review Kaspersky Internet Security - multi-device 2015 online software downloader ] Review Kaspersky Internet Security - multi-device 2015 online software downloader ]](/thumbs/72/67088147.jpg) Review Kaspersky Internet Security - multi-device 2015 online software downloader ] Description: Benefits Protecting all your connected devices the one-licence, easy-touse solution Kaspersky Internet Security
Review Kaspersky Internet Security - multi-device 2015 online software downloader ] Description: Benefits Protecting all your connected devices the one-licence, easy-touse solution Kaspersky Internet Security
Junos Pulse for Google Android
 Junos Pulse for Google Android User Guide Release 2.1 November 2011 R3 Copyright 2011, Juniper Networks, Inc. Juniper Networks, Junos, Steel-Belted Radius, NetScreen, and ScreenOS are registered trademarks
Junos Pulse for Google Android User Guide Release 2.1 November 2011 R3 Copyright 2011, Juniper Networks, Inc. Juniper Networks, Junos, Steel-Belted Radius, NetScreen, and ScreenOS are registered trademarks
CleanMyPC User Guide
 CleanMyPC User Guide Copyright 2017 MacPaw Inc. All rights reserved. macpaw.com CONTENTS Overview 3 About CleanMyPC... 3 System requirements... 3 Download and installation 4 Activation and license reset
CleanMyPC User Guide Copyright 2017 MacPaw Inc. All rights reserved. macpaw.com CONTENTS Overview 3 About CleanMyPC... 3 System requirements... 3 Download and installation 4 Activation and license reset
Bitdefender Mobile Security & Antivirus User's Guide
 USER'S GUIDE Bitdefender Mobile Security & Antivirus User's Guide Publication date 01/30/2018 Copyright 2018 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced or transmitted
USER'S GUIDE Bitdefender Mobile Security & Antivirus User's Guide Publication date 01/30/2018 Copyright 2018 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced or transmitted
Table of Contents... ii. GO AHEAD BRING YOUR OWN DEVICE TO WORK... 1 Requirements... 1
 Table of Contents... ii GO AHEAD BRING YOUR OWN DEVICE TO WORK... 1 Requirements... 1 1: Start Using Toggle... 1 Personal... 2 ToggleHub... 2 AT&T Toggle Browser... 2 Downloads... 2 Media... 3 AT&T Toggle
Table of Contents... ii GO AHEAD BRING YOUR OWN DEVICE TO WORK... 1 Requirements... 1 1: Start Using Toggle... 1 Personal... 2 ToggleHub... 2 AT&T Toggle Browser... 2 Downloads... 2 Media... 3 AT&T Toggle
Qustodio. User Guide. Copyright Qustodio Technologies S.L. All rights reserved. Revised on June 2017.
 Qustodio User Guide Copyright Qustodio Technologies S.L. All rights reserved. Revised on June 2017. Table of Contents 1. INTRODUCTION... 3 1.1. WHAT IS QUSTODIO?... 3 1.2. FEATURES AND BENEFITS... 4 2.
Qustodio User Guide Copyright Qustodio Technologies S.L. All rights reserved. Revised on June 2017. Table of Contents 1. INTRODUCTION... 3 1.1. WHAT IS QUSTODIO?... 3 1.2. FEATURES AND BENEFITS... 4 2.
ESET Mobile Security for Windows Mobile. Installation Manual and User Guide - Public Beta
 ESET Mobile Security for Windows Mobile Installation Manual and User Guide - Public Beta Contents...3 1. Installation of ESET Mobile Security 1.1 Minimum...3 system requirements 1.2 Installation...3 1.2.1
ESET Mobile Security for Windows Mobile Installation Manual and User Guide - Public Beta Contents...3 1. Installation of ESET Mobile Security 1.1 Minimum...3 system requirements 1.2 Installation...3 1.2.1
AT&T Toggle. 2/3/2014 Page i
 Page i GO AHEAD BRING YOUR OWN DEVICE TO WORK... 1 Requirements... 1 1: Toggle Overview... 1 Personal Icon... 2 ToggleHub... 2 AT&T Toggle Browser... 2 Downloads... 2 Data Usage App... 3 Media... 4 AT&T
Page i GO AHEAD BRING YOUR OWN DEVICE TO WORK... 1 Requirements... 1 1: Toggle Overview... 1 Personal Icon... 2 ToggleHub... 2 AT&T Toggle Browser... 2 Downloads... 2 Data Usage App... 3 Media... 4 AT&T
IdeaTab A1000L-F. User Guide V1.0. Please read the Important safety and handling information in the supplied manuals before use.
 IdeaTab A1000L - UserGuide IdeaTab A1000L-F User Guide V1.0 Please read the Important safety and handling information in the supplied manuals before use. file:///c /Users/xieqy1/Desktop/EN UG/index.html[2013/8/14
IdeaTab A1000L - UserGuide IdeaTab A1000L-F User Guide V1.0 Please read the Important safety and handling information in the supplied manuals before use. file:///c /Users/xieqy1/Desktop/EN UG/index.html[2013/8/14
Bitdefender Antivirus Plus 2016 User's Guide
 USER'S GUIDE Bitdefender Antivirus Plus 2016 User's Guide Publication date 09/05/2015 Copyright 2015 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced or transmitted
USER'S GUIDE Bitdefender Antivirus Plus 2016 User's Guide Publication date 09/05/2015 Copyright 2015 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced or transmitted
Sophos Mobile Security
 Help Product Version: 8.5 Contents About Sophos Mobile Security...1 Dashboard... 2 Scanner... 3 Web Filtering... 4 App Protection...5 Call Blocking...6 Loss & Theft...7 Configure Loss & Theft... 8 Wi-Fi
Help Product Version: 8.5 Contents About Sophos Mobile Security...1 Dashboard... 2 Scanner... 3 Web Filtering... 4 App Protection...5 Call Blocking...6 Loss & Theft...7 Configure Loss & Theft... 8 Wi-Fi
The best for everyday PC users
 The best for everyday PC users 2019 ESET Internet Security delivers rock-solid protection for everyday web users, built on ESET s trademark best mix of detection, speed and usability. Legendary antivirus
The best for everyday PC users 2019 ESET Internet Security delivers rock-solid protection for everyday web users, built on ESET s trademark best mix of detection, speed and usability. Legendary antivirus
AT&T Toggle. 12/12/2013 Page i
 Page i GO AHEAD BRING YOUR OWN DEVICE TO WORK... 1 Requirements... 1 1: Toggle Overview... 1 Personal Icon... 2 ToggleHub... 2 AT&T Toggle Browser... 2 Downloads... 2 Media... 3 AT&T Toggle Messaging...
Page i GO AHEAD BRING YOUR OWN DEVICE TO WORK... 1 Requirements... 1 1: Toggle Overview... 1 Personal Icon... 2 ToggleHub... 2 AT&T Toggle Browser... 2 Downloads... 2 Media... 3 AT&T Toggle Messaging...
Bitdefender Internet Security 2017 User's Guide
 USER'S GUIDE Bitdefender Internet Security 2017 User's Guide Publication date 05/03/2017 Copyright 2017 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced or transmitted
USER'S GUIDE Bitdefender Internet Security 2017 User's Guide Publication date 05/03/2017 Copyright 2017 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced or transmitted
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Quick Heal Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac.
 Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to
Total Security Multi-Device (Mac) Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to
Built without compromise for users who want it all
 Built without compromise for users who want it all 2019 Enjoy your digital life, secured by ESET s ultimate multilayered antimalware protection for all internet users, built on ESET s trademark best mix
Built without compromise for users who want it all 2019 Enjoy your digital life, secured by ESET s ultimate multilayered antimalware protection for all internet users, built on ESET s trademark best mix
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice.
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
ANDROID PRIVACY & SECURITY GUIDE ANDROID DEVICE SETTINGS
 ANDROID PRIVACY & SECURITY GUIDE WESNET The Women s Services Network Smartphones store a lot of personal information, including email or social media accounts, reminders and notes, the number of steps
ANDROID PRIVACY & SECURITY GUIDE WESNET The Women s Services Network Smartphones store a lot of personal information, including email or social media accounts, reminders and notes, the number of steps
Bitdefender Antivirus Plus 2017 User's Guide
 USER'S GUIDE Bitdefender Antivirus Plus 2017 User's Guide Publication date 09/15/2016 Copyright 2016 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced or transmitted
USER'S GUIDE Bitdefender Antivirus Plus 2017 User's Guide Publication date 09/15/2016 Copyright 2016 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced or transmitted
Auslogics BOOSTSPEED USER MANUAL. auslogics.
 Auslogics BOOSTSPEED 10 USER MANUAL www..com TABLE OF CONTENTS: Welcome Installation Guide Registering Auslogics BoostSpeed 10 Backing up with the Rescue Center Your First Scan Navigation Panel Navigation
Auslogics BOOSTSPEED 10 USER MANUAL www..com TABLE OF CONTENTS: Welcome Installation Guide Registering Auslogics BoostSpeed 10 Backing up with the Rescue Center Your First Scan Navigation Panel Navigation
Quick Start Guide U.S. Cellular Customer Service
 Quick Start Guide U.S. Cellular Customer Service 1-888-944-9400 LEGAL INFORMATION Copyright 2017 ZTE CORPORATION. All rights reserved. No part of this publication may be quoted, reproduced, translated
Quick Start Guide U.S. Cellular Customer Service 1-888-944-9400 LEGAL INFORMATION Copyright 2017 ZTE CORPORATION. All rights reserved. No part of this publication may be quoted, reproduced, translated
owncloud Android App Manual
 owncloud Android App Manual Release 2.7.0 The owncloud developers October 30, 2018 CONTENTS 1 Release Notes 1 1.1 Changes in 2.7.0............................................. 1 1.2 Changes in 2.6.0.............................................
owncloud Android App Manual Release 2.7.0 The owncloud developers October 30, 2018 CONTENTS 1 Release Notes 1 1.1 Changes in 2.7.0............................................. 1 1.2 Changes in 2.6.0.............................................
The Smart Prime 6 Frequently Asked Questions. The Smart Prime 6 handset
 The Smart Prime 6 handset How do I answer a call? When you receive a call, touch Slide the icon right to answer the call; Slide the icon left to reject the call; Slide the icon up to reject the call by
The Smart Prime 6 handset How do I answer a call? When you receive a call, touch Slide the icon right to answer the call; Slide the icon left to reject the call; Slide the icon up to reject the call by
owncloud Android App Manual
 owncloud Android App Manual Release 2.0.0 The owncloud developers December 14, 2017 CONTENTS 1 Using the owncloud Android App 1 1.1 Getting the owncloud Android App...................................
owncloud Android App Manual Release 2.0.0 The owncloud developers December 14, 2017 CONTENTS 1 Using the owncloud Android App 1 1.1 Getting the owncloud Android App...................................
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, please review the readme files,
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, please review the readme files,
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
/ 1. Online Banking User Guide SouthStateBank.com / (800)
 / 1 Online Banking User Guide SouthStateBank.com / (800) 277-2175 06132017 Welcome Thank you for using South State s Online Banking. Whether you are a first time user or an existing user, this guide will
/ 1 Online Banking User Guide SouthStateBank.com / (800) 277-2175 06132017 Welcome Thank you for using South State s Online Banking. Whether you are a first time user or an existing user, this guide will
Safety and Security. April 2015
 Safety and Security April 2015 Protecting your smartphone and your data 2 Set a passcode on your smartphone For some smartphone models: 1. Go to Settings. 2. Tap ID & Passcode. 3. Set a 4-digit passcode.
Safety and Security April 2015 Protecting your smartphone and your data 2 Set a passcode on your smartphone For some smartphone models: 1. Go to Settings. 2. Tap ID & Passcode. 3. Set a 4-digit passcode.
Thank you for purchasing your new Moochies Watch. We hope you, and more importantly your kids will love it as much as we did creating it.
 www.moochies.com Thank you for purchasing your new Moochies Watch. We hope you, and more importantly your kids will love it as much as we did creating it. This manual will take you through all the steps
www.moochies.com Thank you for purchasing your new Moochies Watch. We hope you, and more importantly your kids will love it as much as we did creating it. This manual will take you through all the steps
Quick Heal AntiVirus Pro Advanced. Protects your computer from viruses, malware, and Internet threats.
 AntiVirus Pro Advanced Protects your computer from viruses, malware, and Internet threats. Features List Ransomware Protection anti-ransomware feature is more effective and advanced than other anti-ransomware
AntiVirus Pro Advanced Protects your computer from viruses, malware, and Internet threats. Features List Ransomware Protection anti-ransomware feature is more effective and advanced than other anti-ransomware
 Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Trend Micro Incorporated reserves the right to make changes to this document and to the products described herein without notice. Before installing and using the software, please review the readme file
Fix Three Common Accounting Firm Data Vulnerabilities
 Fix Three Common Accounting Firm Data Vulnerabilities Fix Three Common Accounting Firm Data Vulnerabilities Use these step-by-step guides to protect your business from data thieves Brought to you by: Encyro
Fix Three Common Accounting Firm Data Vulnerabilities Fix Three Common Accounting Firm Data Vulnerabilities Use these step-by-step guides to protect your business from data thieves Brought to you by: Encyro
User Guide PUSH TO TALK PLUS. For Android
 User Guide PUSH TO TALK PLUS For Android PUSH TO TALK PLUS For Android Contents Introduction and Key Features...4 PTT+ Calling to Individuals and Groups...4 Supervisory Override...4 Real-Time Presence...4
User Guide PUSH TO TALK PLUS For Android PUSH TO TALK PLUS For Android Contents Introduction and Key Features...4 PTT+ Calling to Individuals and Groups...4 Supervisory Override...4 Real-Time Presence...4
User Guide for Consumer & Business Clients
 Online Banking from Capital City Bank User Guide for Consumer & Business Clients Revised September 2015 www.ccbg.com/upgrade Contents Overview... 4 Exploring the Home Page... 5 Menu... 6 Accounts... 7
Online Banking from Capital City Bank User Guide for Consumer & Business Clients Revised September 2015 www.ccbg.com/upgrade Contents Overview... 4 Exploring the Home Page... 5 Menu... 6 Accounts... 7
F-Secure Mobile Security
 F-Secure Mobile Security for S60 User s Guide "F-Secure" and the triangle symbol are registered trademarks of F-Secure Corporation and F-Secure product names and symbols/logos are either trademarks or
F-Secure Mobile Security for S60 User s Guide "F-Secure" and the triangle symbol are registered trademarks of F-Secure Corporation and F-Secure product names and symbols/logos are either trademarks or
1. Introduction P Package Contents 1.
 1 Contents 1. Introduction ------------------------------------------------------------------------------- P. 3-5 1.1 Package Contents 1.2 Tablet Overview 2. Using the Tablet for the first time ---------------------------------------------------
1 Contents 1. Introduction ------------------------------------------------------------------------------- P. 3-5 1.1 Package Contents 1.2 Tablet Overview 2. Using the Tablet for the first time ---------------------------------------------------
Bitdefender Family Pack 2018 User's Guide
 USER'S GUIDE Bitdefender Family Pack 2018 User's Guide Publication date 09/28/2017 Copyright 2017 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced or transmitted in
USER'S GUIDE Bitdefender Family Pack 2018 User's Guide Publication date 09/28/2017 Copyright 2017 Bitdefender Legal Notice All rights reserved. No part of this book may be reproduced or transmitted in
Quick Heal Total Security for Mac. Simple, fast and seamless protection for Mac.
 Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth
Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth
Copyright 2018 PC Pitstop, Inc. User Guide v
 Copyright 2018 PC Pitstop, Inc User Guide v 3.0.2 2018 Table of Contents Introduction 1 Optimal System Requirements 1 Scan Components 1 Where to Purchase PC Matic 2 Installation Options 3 Launching PC
Copyright 2018 PC Pitstop, Inc User Guide v 3.0.2 2018 Table of Contents Introduction 1 Optimal System Requirements 1 Scan Components 1 Where to Purchase PC Matic 2 Installation Options 3 Launching PC
Kaspersky Mobile Security
 Kaspersky Mobile Security User Guide Dear User! Thank you for choosing our product. We hope that this documentation will help you in your work and will provide answers regarding this software product.
Kaspersky Mobile Security User Guide Dear User! Thank you for choosing our product. We hope that this documentation will help you in your work and will provide answers regarding this software product.
CCloud for ios Devices
 CCloud for ios Devices User Guide Guide Version 3.0.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. CCloud for ios - Introduction... 3 1.1.Starting Comodo Cloud...
CCloud for ios Devices User Guide Guide Version 3.0.010215 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1. CCloud for ios - Introduction... 3 1.1.Starting Comodo Cloud...
Avira Ultimate Protection Suite. Short guide
 Avira Ultimate Protection Suite Short guide 01 Trademarks and Copyright Trademarks Windows is a registered trademark of the Microsoft Corporation in the United States and other countries. All other brand
Avira Ultimate Protection Suite Short guide 01 Trademarks and Copyright Trademarks Windows is a registered trademark of the Microsoft Corporation in the United States and other countries. All other brand
Getting to know your ipad exploring the settings, App store, Mail
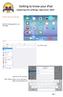 Getting to know your ipad exploring the settings, App store, Mail Exploring the settings Open the settings app from your homepage Wi-Fi Turn Wi-Fi on/off Add new Wi-Fi Connection Enter Network Name, any
Getting to know your ipad exploring the settings, App store, Mail Exploring the settings Open the settings app from your homepage Wi-Fi Turn Wi-Fi on/off Add new Wi-Fi Connection Enter Network Name, any
/ 1. Online Banking User Guide SouthStateBank.com / (800)
 / 1 Online Banking User Guide SouthStateBank.com / (800) 277-2175 01242018 Welcome Thank you for using South State s Online Banking. Whether you are a first time user or an existing user, this guide will
/ 1 Online Banking User Guide SouthStateBank.com / (800) 277-2175 01242018 Welcome Thank you for using South State s Online Banking. Whether you are a first time user or an existing user, this guide will
Android User Guide. Last Updated On: April 07, 2018
 Android User Guide Last Updated On: April 07, 2018 Copyright Notice Copyright 2018 ClickSoftware Technologies Ltd. All rights reserved. No part of this publication may be copied without the express written
Android User Guide Last Updated On: April 07, 2018 Copyright Notice Copyright 2018 ClickSoftware Technologies Ltd. All rights reserved. No part of this publication may be copied without the express written
 Trend Micro Incorporated reserves the right to make changes to this document and to the service described herein without notice. Before installing and using the service, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the service described herein without notice. Before installing and using the service, review the readme files, release
INTRODUCTION... 2 GETTING STARTED...
 Conventions used in this document: Keyboard keys that must be pressed will be shown as Enter or Ctrl. Controls to be activated with the mouse will be shown as Start button > Settings > System > About.
Conventions used in this document: Keyboard keys that must be pressed will be shown as Enter or Ctrl. Controls to be activated with the mouse will be shown as Start button > Settings > System > About.
 Trend Micro Incorporated reserves the right to make changes to this document and to the service described herein without notice. Before installing and using the service, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the service described herein without notice. Before installing and using the service, review the readme files, release
Setting Up KidiConnect : Unlock KidiConnect
 Setting Up KidiConnect : Unlock KidiConnect With KidiConnect, kids can use their KidiBuzz to send messages to a parent-approved list of contacts. But you have to unlock KidiConnect on your child's device
Setting Up KidiConnect : Unlock KidiConnect With KidiConnect, kids can use their KidiBuzz to send messages to a parent-approved list of contacts. But you have to unlock KidiConnect on your child's device
Version 5.0 September P Xerox App Gallery. App Gallery User Guide
 Version 5.0 September 2018 702P06709 Xerox App Gallery App Gallery User Guide 2018 Xerox Corporation. All rights reserved. Xerox, Xerox and Design, ConnectKey, VersaLink, AltaLink, Xerox Extensible Interface
Version 5.0 September 2018 702P06709 Xerox App Gallery App Gallery User Guide 2018 Xerox Corporation. All rights reserved. Xerox, Xerox and Design, ConnectKey, VersaLink, AltaLink, Xerox Extensible Interface
37 FAQs ABOUT CELLCONTROL ASKED BY PARENTS OF NEW DRIVERS
 37 FAQs ABOUT CELLCONTROL ASKED BY PARENTS OF NEW DRIVERS TABLE OF CONTENTS INTRODUCTION 3 QUESTIONS BEFORE YOU BUY 4 USING CELLCONTROL 9 iphone-specific QUESTIONS 14 ANDROID AND WINDOWS PHONE-SPECIFIC
37 FAQs ABOUT CELLCONTROL ASKED BY PARENTS OF NEW DRIVERS TABLE OF CONTENTS INTRODUCTION 3 QUESTIONS BEFORE YOU BUY 4 USING CELLCONTROL 9 iphone-specific QUESTIONS 14 ANDROID AND WINDOWS PHONE-SPECIFIC
Quick Heal AntiVirus Pro. Tough on malware, light on your PC.
 Tough on malware, light on your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware tools. Signature based detection Detects
Tough on malware, light on your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware tools. Signature based detection Detects
Notices. Third Party Project Usage. Sample Code in Documentation
 Malwarebytes for Mac User Guide Version 3.4.0 7 August 2018 Notices Malwarebytes products and related documentation are provided under a license agreement containing restrictions on use and disclosure
Malwarebytes for Mac User Guide Version 3.4.0 7 August 2018 Notices Malwarebytes products and related documentation are provided under a license agreement containing restrictions on use and disclosure
TABLE OF CONTENTS 1 INTRO
 TABLE OF CONTENTS 1 INTRO 4 2 GETTING STARTED 5 2.1 CREATING AN ACCOUNT 2.1.1 ENTERING ACCOUNT INFORMATION 2.1.2 SELECTING A PLAN 2.1.3 ENTERING PAYMENT INFORMATION 2.1.4 REVIEW AND CONFIRM 2.2 LOGGING
TABLE OF CONTENTS 1 INTRO 4 2 GETTING STARTED 5 2.1 CREATING AN ACCOUNT 2.1.1 ENTERING ACCOUNT INFORMATION 2.1.2 SELECTING A PLAN 2.1.3 ENTERING PAYMENT INFORMATION 2.1.4 REVIEW AND CONFIRM 2.2 LOGGING
Protegent Total Security Solution USER GUIDE Unistal Systems Pvt. Ltd. All rights Reserved Page 1
 Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
Protegent Total Security Solution USER GUIDE 2007-2017 Unistal Systems Pvt. Ltd. All rights Reserved Page 1 Table of Contents PROTEGENT TOTAL SECURITY...3 INSTALLATION...4 REGISTERING PROTEGENT TOTAL SECURITY...
CONTENTS I. DEVICE SETUP II. INSTALLATION III. UNINSTALL RETAIL MODE
 CONTENTS I. DEVICE SETUP SCENARIO A: New Device Setup SCENARIO B: Device Has Previous Retail Mode Installed 3 II. INSTALLATION 6 SCENARIO A: Download Installation (Device has access to Wi- Fi/4G Network)
CONTENTS I. DEVICE SETUP SCENARIO A: New Device Setup SCENARIO B: Device Has Previous Retail Mode Installed 3 II. INSTALLATION 6 SCENARIO A: Download Installation (Device has access to Wi- Fi/4G Network)
BlackVue C App Manual
 BlackVue C App Manual BlackVue C App Manual Contents Connecting to BLACKVUE CLOUD... 3 (A) Create an account... 3 (B) Register your dashcam with your account... 3 (C) Connect your BlackVue dashcam to a
BlackVue C App Manual BlackVue C App Manual Contents Connecting to BLACKVUE CLOUD... 3 (A) Create an account... 3 (B) Register your dashcam with your account... 3 (C) Connect your BlackVue dashcam to a
<,W,EϬϱ E USER MANUAL
 USER MANUAL GETTING STARTED To get started with the Agora handset, please take both the phone and the battery out of the box. On the rear of the phone you will find a plastic backing cover with a small
USER MANUAL GETTING STARTED To get started with the Agora handset, please take both the phone and the battery out of the box. On the rear of the phone you will find a plastic backing cover with a small
Consumer Technical Product Marketing. TREND MICRO Titanium 2013 Product Guide
 H Consumer Technical Product Marketing TREND MICRO Titanium 2013 Product Guide Titanium Antivirus+ Titanium Internet Security Titanium Maximum Security Titanium Premium Security US V1.2 Trend Micro, Inc.
H Consumer Technical Product Marketing TREND MICRO Titanium 2013 Product Guide Titanium Antivirus+ Titanium Internet Security Titanium Maximum Security Titanium Premium Security US V1.2 Trend Micro, Inc.
QUICK START GUIDE NTS HOSTED PBX CALL MANAGER. Welcome. Getting Oriented
 QUICK START GUIDE NTS HOSTED PBX Welcome Welcome to NTS Hosted PBX! This guide is intended to get you up and running with the basic features associated with the product. For more in-depth information,
QUICK START GUIDE NTS HOSTED PBX Welcome Welcome to NTS Hosted PBX! This guide is intended to get you up and running with the basic features associated with the product. For more in-depth information,
Installation guide Swisscom Mobile Security for Android Devices
 Security for 1 Installation of Mobile Security...2 1.1 operating system devices with preinstalled Mobile Security program...2 1.2 operating system devices with preinstalled Swisscom Security Launcher...2
Security for 1 Installation of Mobile Security...2 1.1 operating system devices with preinstalled Mobile Security program...2 1.2 operating system devices with preinstalled Swisscom Security Launcher...2
TABLE OF CONTENTS 1. SYSTEM REQUIREMENTS INSTALLATION ACCOUNT MANAGEMENT RAZER CORTEX GENERAL SETTINGS...
 Welcome to Razer Cortex, the nerve center of your entire gaming experience. From effortlessly finding the best deals on your games to launching and boosting them for peak pc performance while backing up
Welcome to Razer Cortex, the nerve center of your entire gaming experience. From effortlessly finding the best deals on your games to launching and boosting them for peak pc performance while backing up
2 User Guide. Contents
 E-mail User Guide 2 E-mail User Guide Contents Logging in to your web mail... 3 Changing your password... 5 Editing your signature... 6 Adding an e-mail account to Outlook 2010/2013/2016... 7 Adding an
E-mail User Guide 2 E-mail User Guide Contents Logging in to your web mail... 3 Changing your password... 5 Editing your signature... 6 Adding an e-mail account to Outlook 2010/2013/2016... 7 Adding an
Introduction. Package Checklist. Minimum System Requirements. Registering Your Product. More Help
 Introduction Keep a watch on your family, pet, home or office 24/7, even when you re not there. Creative Live! Cam IP SmartHD gives you a live update on your phone, wherever you are. Get activity alerts,
Introduction Keep a watch on your family, pet, home or office 24/7, even when you re not there. Creative Live! Cam IP SmartHD gives you a live update on your phone, wherever you are. Get activity alerts,
User s Guide. SingNet Desktop Security Copyright 2010 F-Secure Corporation. All rights reserved.
 User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
User s Guide SingNet Desktop Security 2011 Copyright 2010 F-Secure Corporation. All rights reserved. Table of Contents 1. Getting Started... 1 1.1. Installing SingNet Desktop Security... 1 1.1.1. System
 Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
Trend Micro Incorporated reserves the right to make changes to this document and to the product described herein without notice. Before installing and using the product, review the readme files, release
TABLE OF CONTENTS 1. SYSTEM REQUIREMENTS INSTALLATION ACCOUNT MANAGEMENT RAZER CORTEX GENERAL SETTINGS...
 Welcome to Razer Cortex, the nerve center of your entire gaming experience. From effortlessly finding the best deals on your games to launching and boosting them for peak pc performance while backing up
Welcome to Razer Cortex, the nerve center of your entire gaming experience. From effortlessly finding the best deals on your games to launching and boosting them for peak pc performance while backing up
