Modeling Processors. Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology
|
|
|
- Gabriel Gregory
- 6 years ago
- Views:
Transcription
1 Modeling Processors Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L08-1 Instruction set typedef enum {R0;R1;R2; ;R31} RName; typedef union tagged { struct {RName dst; RName src1; RName src2;} Add; struct {RName cond; RName addr;} Bz; struct {RName dst; RName addr;} Load; struct {RName value; RName addr;} Store } Instr deriving(bits, Eq); typedef Bit#(32) Iaddress; typedef Bit#(32) Daddress; typedef Bit#(32) Value; An instruction set can be implemented using many different microarchitectures L08-2 1
2 Deriving Bits typedef struct { } Foo deriving (Bits); To store datatypes in register, fifo, etc. we need to know how to represent them as bits (pack) and interpret their bit representation (unpack) Deriving annotation automatically generates the pack and unpack operations on the type (simple concatenation of bit representations of components) It is possible to customize the pack/unpack operations to any specific desired representation L08-3 Tagged Unions: Bit Representation typedef union tagged { struct {RName dst; RName src1; RName src2;} Add; struct {RName cond; RName addr;} Bz; struct {RName dst; RName addr;} Load; struct {RName dst; Immediate imm;} AddImm; } Instr deriving(bits, Eq); 00 dst src1 src2 01 cond addr 10 dst addr 11 dst imm Automatically derived representation; can be customized by the user written pack and unpack functions L08-4 2
3 The Plan Non-pipelined processor Two-stage Inelastic pipeline Two-stage Elastic pipeline next lecture Some understanding of simple processor pipelines is needed to follow this lecture L08-5 Non-pipelined Processor pc CPU rf fetch & execute imem dmem module mkcpu#(mem imem, Mem dmem)(); Reg#(Iaddress) pc <- mkreg(0); RegFile#(RName, Bit#(32)) rf <- mkregfilefull(); Instr instr = imem.read(pc); Iaddress predia = pc + 1; rule fetch_execute... endmodule L08-6 3
4 Non-pipelined processor rule rule fetch_execute (True); case (instr) matches tagged Add {dst:.rd,src1:.ra,src2:.rb}: begin rf.upd(rd, rf[ra]+rf[rb]); pc <= predia end tagged Bz {cond:.rc,addr:.ra}: begin pc <= (rf[rc]==0)? rf[ra] : predia; end tagged Load {dest:.rd,addr:.ra}: begin rf.upd(rd, dmem.read(rf[ra])); pc <= predia; end tagged Store {value:.rv,addr:.ra}: begin dmem.write(rf[ra],rf[rv]); pc <= predia; end endrule my syntax rf[r] rf.sub(r) Assume magic memory, i.e. responds to a read request in the same cycle and a write updates the memory at the end of the cycle L08-7 Register File How many read ports? How many write ports? Concurrency properties? L08-8 4
5 The Plan Non-pipelined processor Two-stage Inelastic pipeline Two-stage Elastic pipeline L08-9 Two-stage Inelastic Pipeline fetch & decode bureg execute pc rf dmem time t0 t1 t2 t3 t4 t5 t6 t7.... FDstage FD 1 FD 2 FD 3 FD 4 FD 5 EXstage EX 1 EX 2 EX 3 EX 4 EX 5 Actions to be performed in parallel every cycle: Fetch Action: Decodes the instruction at the current pc and fetches operands from the register file and stores the result in bureg Execute Action: Performs the action specified in bureg and updates the processor state (pc, rf, dmem) rule InelasticPipeline2(True); fetchaction; executeaction; endrule L
6 Instructions & Templates bureg contains instruction templates, i.e., decoded instructions typedef union tagged { struct {RName dst; RName src1; RName src2} Add; struct {RName cond; RName addr} Bz; struct {RName dst; RName addr} Load; struct {RName value; RName addr} Store; } Instr deriving(bits, Eq); typedef union tagged { struct {RName dst; Value op1; Value op2} EAdd; struct {Value cond; Iaddress taddr} EBz; struct {RName dst; Daddress addr} ELoad; struct {Value value; Daddress addr} EStore; } InstTemplate deriving(eq, Bits); L08-11 Fetch & Decode Action Fills the bureg with a decoded instruction bureg <= newit(instr); function InstrTemplate newit(instr instr); case (instr) matches tagged Add {dst:.rd,src1:.ra,src2:.rb}: return EAdd{dst:rd,op1:rf[ra],op2:rf[rb]}; tagged Bz {cond:.rc,addr:.addr}: return EBz{cond:rf[rc],addr:rf[addr]}; tagged Load {dst:.rd,addr:.addr}: return ELoad{dst:rd,addr:rf[addr]}; tagged Store{value:.v,addr:.addr}: return EStore{value:rf[v],addr:rf[addr]}; endfunction L
7 Execute Action: Reads bureg and modifies state (rf,dmem,pc) case (bureg) matches tagged EAdd{dst:.rd,src1:.va,src2:.vb}: begin rf.upd(rd, d va+vb); pc <= predia; end tagged ELoad{dst:.rd,addr:.av}: begin rf.upd(rd, dmem.read(av)); pc <= predia; end tagged EStore{value:.vv,addr:.av}: begin dmem.write(av, vv); pc <= predia; end tagged EBz {cond:.cv,addr:.av}: if (cv!= 0) then pc <= predia; else begin pc <= av; Invalidate bureg end What does this mean? L08-13 Issues with bureg fetch & decode bureg execute pc rf dmem bureg may not always contain an instruction. Why? start cycle Execute stage may kill the fetched instructions because of branch misprediction Can t update bureg in two concurrent actions fetchaction; executeaction L
8 Inelastic Pipeline first attempt rule SyncTwoStage (True); let instr = imem.read(pc); let predia = pc+1; pc fetch & decode CPU bureg rf execute Action fetchaction = action bureg <= Valid newit(instr); pc <= predia; endaction; case (bureg) matches each instruction execution calls fetchaction or puts Invalid in bureg endrule L08-15 Execute pc fetch & decode CPU rf execute bureg case (bureg) matches tagged Valid.it: case (it) matches tagged EAdd{dst:.rd,src1:.va,src2:.vb}: begin rf.upd(rd, va+vb); fetchaction; end tagged ELoad{dst:.rd,addr:.av}: begin rf.upd(rd, dmem.read(av)); fetchaction; end tagged EStore{value:.vv,addr:.av}: begin dmem.write(av, vv); fetchaction; end tagged EBz {cond:.cv,addr:.av}: if (cv!= 0) then fetchaction; else begin pc <= av; bureg <= Invalid; end tagged Invalid: fetchaction; L
9 Pipeline Hazards fetch & decode bureg execute pc rf dmem time t0 t1 t2 t3 t4 t5 t6 t7.... FDstage FD 1 FD 2 FD 3 FD 4 FD 5 EXstage EX 1 EX 2 EX 3 EX 4 EX 5 I 1 Add(R1,R2,R3) I 2 Add(R4,R1,R2) I 2 must be stalled until I 1 updates the register file time t0 t1 t2 t3 t4 t5 t6 t7.... FDstage FD 1 FD 2 FD 2 FD 3 FD 4 FD 5 EXstage EX 1 EX 2 EX 3 EX 4 EX 5 L08-17 Inelastic Pipeline corrected rule SyncTwoStage (True); let instr = imem.read(pc); let predia = pc+1; pc fetch & decode CPU bureg rf execute Action fetchaction = action if stallfunc(instr, bureg) then bureg <=Invalid else begin bureg <= Valid newit(instr); pc <= predia; end endaction; case (bureg) matches no change endrule How do we detect stalls? L
10 The Stall Function function Bool stallfunc (Instr instr, Maybe#(InstTemplate) mit); case (mit) matches tagged Invalid: return False; tagged Valid.it: case (instr) matches tagged Add {dst:.rd,src1:.ra,src2:.rb}: return (findf(ra,it) findf(rb,it)); tagged Bz {cond:.rc,addr:.addr}: return (findf(rc,it) findf(addr,it)); tagged Load {dst:.rd,addr:.addr}: return (findf(addr,it)); tagged Store {value:.v,addr:.addr}: return (findf(v,it) findf(addr,it)); endfunction L08-19 The findf function function Bool findf (RName r, InstrTemplate it); case (it) matches tagged EAdd{dst:.rd,op1:.v1,op2:.v2}: return (r == rd); tagged EBz {cond:.c,addr:.a}: return (False); tagged ELoad{dst:.rd,addr:.a}: return (r == rd); tagged EStore{value:.v,addr:.a}: return (False); endfunction L
11 Bypassing After decoding the newit function must read the new register values if available (i.e., the values that are still to be committed in the register file) We pass the value being written to decoding action (the newit function) L08-21 Updated newit function InstrTemplate newit(maybe#(rname) mrd, Value val, Instr instr); let nrf(a)=(valid a == mrd)? val: rf.sub(a); case (instr) matches tagged Add {dst:.rd,src1:.ra,src2:.rb}: return EAdd{dst:rd,op1:nrf(ra),op2:nrf(rb)}; tagged Bz {cond:.rc,addr:.addr}: return EBz{cond:nrf(rc),addr:nrf(addr)}; tagged Load {dst:.rd,addr:.addr}: return ELoad{dst:rd,addr:nrf(addr)}; tagged Store{value:.v,addr:.addr}: return EStore{value:nrf(v),addr:nrf(addr)}; endfunction L
12 New fetchaction function Action fetchaction(maybe#(rname) mrd, Value data); action if stallfunc(instr, bureg) then bureg <= Invalid; else begin bureg <= Valid newit(mrd, data, instr); pc <= predia; end endaction endfunction L08-23 New Execute Action case (bureg) matches tagged Valid.it: case (it) matches tagged EAdd{dst:.rd,src1:.va,src2:.vb}: begin rf.upd(rd, va+vb); fetchaction(valid rd, va+vb); end tagged ELoad{dst:.rd,addr:.av}: begin rf.upd(rd, dmem.read(av)); fetchaction(valid rd, dmem.read(av)); end tagged EStore{value:.vv,addr:.av}: begin dmem.write(av, vv); fetchaction(invalid,?); end tagged EBz {cond:.cv,addr:.av}: if (cv!= 0) then fetchaction(invalid,?); else begin pc <= av; bureg <= Invalid; end tagged Invalid: fetchaction(invalid,?); L
13 Bypassing Now that we ve correctly bypassed data, we do not have to stall as often The current stall function is correct, but inefficient Should not stall if the value is now being bypassed L08-25 The stall function for the Inelastic pipeline function Bool newstallfunc (Instr instr, Reg#(Maybe#(InstTemplate)) bureg); case (bureg) matches tagged Invalid: return False; tagged Valid.it: case (instr) matches tagged Add {dst:.rd,src1:.ra,src2:.rb}: return (findf(ra,it) findf(rb,it)); L
14 Inelastic Pipelines Notoriously difficult to get right Imagine the cases to be analyzed if it was a five stage pipeline Difficult to refine for better clock timing elastic pipelines L
Modeling Processors. Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology
 Modeling Processors Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L07-1 Instruction set typedef enum {R0;R1;R2; ;R31} RName; typedef union tagged { struct
Modeling Processors Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L07-1 Instruction set typedef enum {R0;R1;R2; ;R31} RName; typedef union tagged { struct
Modeling Processors. Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology
 Modeling Processors Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L07-1 The Plan Non-pipelined processor Two-stage synchronous pipeline Two-stage asynchronous
Modeling Processors Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L07-1 The Plan Non-pipelined processor Two-stage synchronous pipeline Two-stage asynchronous
Bluespec-5: Modeling Processors. Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology
 Bluespec-5: Modeling Processors (revised after the lecture) Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology Based on material prepared by Bluespec Inc, January
Bluespec-5: Modeling Processors (revised after the lecture) Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology Based on material prepared by Bluespec Inc, January
Bluespec-5: Modeling Processors. Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology
 Bluespec-5: Modeling Processors Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology Based on material prepared by Bluespec Inc, January 2005 L12-1 Some New Types
Bluespec-5: Modeling Processors Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology Based on material prepared by Bluespec Inc, January 2005 L12-1 Some New Types
Successive refinement & Modular Structure. Bluespec-8: Modules and Interfaces. Designing a 2-Stage Processor with GAA. A 2-Stage Processor in RTL
 Bluespec-8: Modules and Interfaces Successive refinement & Modular Structure rf fetch decode memory writeback Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology
Bluespec-8: Modules and Interfaces Successive refinement & Modular Structure rf fetch decode memory writeback Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology
Modular Refinement - 2. Successive refinement & Modular Structure
 Modular Refinement - 2 Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L10-1 Successive refinement & Modular Structure pc rf fetch decode execute memory writeback
Modular Refinement - 2 Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L10-1 Successive refinement & Modular Structure pc rf fetch decode execute memory writeback
Elastic Pipelines: Concurrency Issues
 Elastic Pipelines: Concurrency Issues Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L08-1 Inelastic vs Elastic Pipelines In a Inelastic pipeline: pp typically
Elastic Pipelines: Concurrency Issues Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L08-1 Inelastic vs Elastic Pipelines In a Inelastic pipeline: pp typically
Modular Refinement. Successive refinement & Modular Structure
 Modular Refinement Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L09-1 Successive refinement & Modular Structure pc rf fetch decode execute memory writeback
Modular Refinement Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L09-1 Successive refinement & Modular Structure pc rf fetch decode execute memory writeback
Elastic Pipelines: Concurrency Issues
 Elastic Pipelines: Concurrency Issues Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L09-1 Inelastic vs Elastic Pipelines In a Inelastic pipeline: pp typically
Elastic Pipelines: Concurrency Issues Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L09-1 Inelastic vs Elastic Pipelines In a Inelastic pipeline: pp typically
Non-pipelined Multicycle processors
 Non-pipelined Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology Code for the lecture is available on the course website under the code tab
Non-pipelined Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology Code for the lecture is available on the course website under the code tab
Performance Specifications. Simple processor pipeline
 Performance Specifications Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L11-1 Simple processor pipeline RF Bz? Bz? IF Dec Exe Mem Wb imem bf bd dmem Functional
Performance Specifications Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L11-1 Simple processor pipeline RF Bz? Bz? IF Dec Exe Mem Wb imem bf bd dmem Functional
Multicycle processors. Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology
 Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L12-1 Single-Cycle RISC Processor As an illustrative example, we use a subset of RISC-V
Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L12-1 Single-Cycle RISC Processor As an illustrative example, we use a subset of RISC-V
Control Unit. Main Memory. control. status. address instructions. address data. Internal storage Datapath
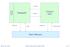 control Internal storage Datapath status Control Unit address data address instructions Main Memory March 20, 2018 http://csg.csail.mit.edu/6.s084 L11-1 Our interpreter is a Single-Cycle RISC-V Processor
control Internal storage Datapath status Control Unit address data address instructions Main Memory March 20, 2018 http://csg.csail.mit.edu/6.s084 L11-1 Our interpreter is a Single-Cycle RISC-V Processor
Implementing RISC-V Interpreter in Hardware
 Implementing RISC-V Interpreter in Hardware Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology October 16, 2018 MIT 6.004 Fall 2018 L11-1 Instruction interpreter
Implementing RISC-V Interpreter in Hardware Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology October 16, 2018 MIT 6.004 Fall 2018 L11-1 Instruction interpreter
Multicycle processors. Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology
 Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L14-1 Single-Cycle RISC Processor As an illustrative example, we use a subset of RISC-V
Multicycle processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L14-1 Single-Cycle RISC Processor As an illustrative example, we use a subset of RISC-V
Bluespec SystemVerilog TM Training. Lecture 05: Rules. Copyright Bluespec, Inc., Lecture 05: Rules
 Bluespec SystemVerilog Training Copyright Bluespec, Inc., 2005-2008 Rules: conditions, actions Rule Untimed Semantics Non-determinism Functional correctness: atomicity, invariants Examples Performance
Bluespec SystemVerilog Training Copyright Bluespec, Inc., 2005-2008 Rules: conditions, actions Rule Untimed Semantics Non-determinism Functional correctness: atomicity, invariants Examples Performance
Non-Pipelined Processors - 2
 Constructive Computer Architecture: Non-Pipelined Processors - 2 Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology October 4, 2017 http://csg.csail.mit.edu/6.175
Constructive Computer Architecture: Non-Pipelined Processors - 2 Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology October 4, 2017 http://csg.csail.mit.edu/6.175
Virtual Memory and Interrupts
 Constructive Computer Architecture Virtual Memory and Interrupts Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology November 13, 2015 http://csg.csail.mit.edu/6.175
Constructive Computer Architecture Virtual Memory and Interrupts Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology November 13, 2015 http://csg.csail.mit.edu/6.175
6.004 Recitation Problems L11 RISC-V Interpreter
 6.004 Recitation Problems L11 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. New Bluespec Constructs: Maybe Types // Maybe#() is a
6.004 Recitation Problems L11 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. New Bluespec Constructs: Maybe Types // Maybe#() is a
6.004 Recitation Problems L13 RISC-V Interpreter
 6.004 Recitation Problems L13 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. RISC-V Interpreter: Components Register File typedef Bit#(32)
6.004 Recitation Problems L13 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. RISC-V Interpreter: Components Register File typedef Bit#(32)
Bypassing and EHRs. Arvind Computer Science and Artificial Intelligence Laboratory M.I.T. L23-1
 Bypassing and EHRs Arvind Computer Science and Artificial Intelligence Laboratory M.I.T. L23-1 Bypassing F D RF bypass E/WB Bypassing is a technique to reduce the number of stalls (that is, the number
Bypassing and EHRs Arvind Computer Science and Artificial Intelligence Laboratory M.I.T. L23-1 Bypassing F D RF bypass E/WB Bypassing is a technique to reduce the number of stalls (that is, the number
6.004 Recitation Problems L13 RISC-V Interpreter
 6.004 Recitation Problems L13 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. RISC-V Interpreter: Components Register File typedef Bit#(32)
6.004 Recitation Problems L13 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. RISC-V Interpreter: Components Register File typedef Bit#(32)
6.004 Recitation Problems L11 RISC-V Interpreter
 6.004 Recitation Problems L11 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. New Bluespec Constructs: Maybe Types // Maybe#() is a
6.004 Recitation Problems L11 RISC-V Interpreter Refer to the 6.004 ISA Reference Tables (Website > Resources) for details about each instruction. New Bluespec Constructs: Maybe Types // Maybe#() is a
Contributors to the course material
 Constructive Computer Architecture: Data Hazards in Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology October 11, 2013 http://csg.csail.mit.edu/6.s195
Constructive Computer Architecture: Data Hazards in Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology October 11, 2013 http://csg.csail.mit.edu/6.s195
Bluespec for a Pipelined SMIPSv2 Processor
 Bluespec for a Pipelined SMIPSv2 Processor 6.375 Laboratory 2 February 14, 2008 The second laboratory assignment is to implement a pipelined SMIPSv2 in Bluespec SystemVerilog. As with Lab One, your deliverables
Bluespec for a Pipelined SMIPSv2 Processor 6.375 Laboratory 2 February 14, 2008 The second laboratory assignment is to implement a pipelined SMIPSv2 in Bluespec SystemVerilog. As with Lab One, your deliverables
Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology
 Constructive Computer Architecture: Data Hazards in Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology January 2, 2014 http://csg.csail.mit.edu/6.s195/cdac
Constructive Computer Architecture: Data Hazards in Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology January 2, 2014 http://csg.csail.mit.edu/6.s195/cdac
Announcements. ECE4750/CS4420 Computer Architecture L11: Speculative Execution I. Edward Suh Computer Systems Laboratory
 ECE4750/CS4420 Computer Architecture L11: Speculative Execution I Edward Suh Computer Systems Laboratory suh@csl.cornell.edu Announcements Lab3 due today 2 1 Overview Branch penalties limit performance
ECE4750/CS4420 Computer Architecture L11: Speculative Execution I Edward Suh Computer Systems Laboratory suh@csl.cornell.edu Announcements Lab3 due today 2 1 Overview Branch penalties limit performance
Background: Pipelining Basics. Instruction Scheduling. Pipelining Details. Idealized Instruction Data-Path. Last week Register allocation
 Instruction Scheduling Last week Register allocation Background: Pipelining Basics Idea Begin executing an instruction before completing the previous one Today Instruction scheduling The problem: Pipelined
Instruction Scheduling Last week Register allocation Background: Pipelining Basics Idea Begin executing an instruction before completing the previous one Today Instruction scheduling The problem: Pipelined
Sizhuo Zhang TA
 Constructive Computer Architecture Tutorial 2 Advanced BSV Sizhuo Zhang 6.175 TA T02-1 EHR and Scheduling Design example Up/down counter interface Counter; Bit#(8) read; Action increment(bit#(8) x); Action
Constructive Computer Architecture Tutorial 2 Advanced BSV Sizhuo Zhang 6.175 TA T02-1 EHR and Scheduling Design example Up/down counter interface Counter; Bit#(8) read; Action increment(bit#(8) x); Action
Pipelined RISC-V Processors
 Due date: Tuesday November 20th 11:59:59pm EST Getting started: To create your initial Lab 7 repository, please visit the repository creation page at https://6004.mit.edu/web/fall18/user/labs/lab7. Once
Due date: Tuesday November 20th 11:59:59pm EST Getting started: To create your initial Lab 7 repository, please visit the repository creation page at https://6004.mit.edu/web/fall18/user/labs/lab7. Once
Non-Pipelined Processors
 Constructive Computer Architecture: Non-Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology September 29, 2014 http://csg.csail.mit.edu/6.175
Constructive Computer Architecture: Non-Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology September 29, 2014 http://csg.csail.mit.edu/6.175
Realistic Memories and Caches
 Realistic Memories and Caches Li-Shiuan Peh Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L13-1 Three-Stage SMIPS Epoch Register File stall? PC +4 fr Decode Execute
Realistic Memories and Caches Li-Shiuan Peh Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L13-1 Three-Stage SMIPS Epoch Register File stall? PC +4 fr Decode Execute
Data Hazards in Pipelined Processors
 Data Hazards in Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology March 13, 2013 http://csg.csail.mit.edu/6.375 L11-1 A different 2-Stage
Data Hazards in Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology March 13, 2013 http://csg.csail.mit.edu/6.375 L11-1 A different 2-Stage
Non-Pipelined Processors
 Constructive Computer Architecture: Non-Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L10-1 Single-Cycle RISC Processor As an illustrative
Constructive Computer Architecture: Non-Pipelined Processors Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L10-1 Single-Cycle RISC Processor As an illustrative
3/12/2014. Single Cycle (Review) CSE 2021: Computer Organization. Single Cycle with Jump. Multi-Cycle Implementation. Why Multi-Cycle?
 CSE 2021: Computer Organization Single Cycle (Review) Lecture-10b CPU Design : Pipelining-1 Overview, Datapath and control Shakil M. Khan 2 Single Cycle with Jump Multi-Cycle Implementation Instruction:
CSE 2021: Computer Organization Single Cycle (Review) Lecture-10b CPU Design : Pipelining-1 Overview, Datapath and control Shakil M. Khan 2 Single Cycle with Jump Multi-Cycle Implementation Instruction:
Constructive Computer Architecture Tutorial 6: Discussion for lab6. October 7, 2013 T05-1
 Constructive Computer Architecture Tutorial 6: Discussion for lab6 October 7, 2013 T05-1 Introduction Lab 6 involves creating a 6 stage pipelined processor from a 2 stage pipeline This requires a lot of
Constructive Computer Architecture Tutorial 6: Discussion for lab6 October 7, 2013 T05-1 Introduction Lab 6 involves creating a 6 stage pipelined processor from a 2 stage pipeline This requires a lot of
Complex Pipelines and Branch Prediction
 Complex Pipelines and Branch Prediction Daniel Sanchez Computer Science & Artificial Intelligence Lab M.I.T. L22-1 Processor Performance Time Program Instructions Program Cycles Instruction CPI Time Cycle
Complex Pipelines and Branch Prediction Daniel Sanchez Computer Science & Artificial Intelligence Lab M.I.T. L22-1 Processor Performance Time Program Instructions Program Cycles Instruction CPI Time Cycle
Pipelining. CSC Friday, November 6, 2015
 Pipelining CSC 211.01 Friday, November 6, 2015 Performance Issues Longest delay determines clock period Critical path: load instruction Instruction memory register file ALU data memory register file Not
Pipelining CSC 211.01 Friday, November 6, 2015 Performance Issues Longest delay determines clock period Critical path: load instruction Instruction memory register file ALU data memory register file Not
Interrupts/Exceptions/Faults
 Constructive Computer Architecture Interrupts/Exceptions/Faults Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology November 6, 2013 http://csg.csail.mit.edu/6.s195
Constructive Computer Architecture Interrupts/Exceptions/Faults Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology November 6, 2013 http://csg.csail.mit.edu/6.s195
Need for a scheduler. Concurrent rule execution. L17/L18 Review- Rule Scheduling
 L17/L18 Review- Rule Scheduling Conflict Matri (CM) BSV compiler generates the pairwise conflict information Eample 1 rule ra;
L17/L18 Review- Rule Scheduling Conflict Matri (CM) BSV compiler generates the pairwise conflict information Eample 1 rule ra;
6.175: Constructive Computer Architecture. Tutorial 4 Epochs and Scoreboards
 6.175: Constructive Computer Architecture Tutorial 4 Epochs and Scoreboards Quan Nguyen (Hopes to help you avoid epoch fails) https://xkcd.com/376/ (not that kind of epoch) T04-1 Outline Epochs Scoreboards
6.175: Constructive Computer Architecture Tutorial 4 Epochs and Scoreboards Quan Nguyen (Hopes to help you avoid epoch fails) https://xkcd.com/376/ (not that kind of epoch) T04-1 Outline Epochs Scoreboards
CMSC 411 Computer Systems Architecture Lecture 6 Basic Pipelining 3. Complications With Long Instructions
 CMSC 411 Computer Systems Architecture Lecture 6 Basic Pipelining 3 Long Instructions & MIPS Case Study Complications With Long Instructions So far, all MIPS instructions take 5 cycles But haven't talked
CMSC 411 Computer Systems Architecture Lecture 6 Basic Pipelining 3 Long Instructions & MIPS Case Study Complications With Long Instructions So far, all MIPS instructions take 5 cycles But haven't talked
Lab 4 Overview: 6-stage SMIPS Pipeline
 Lab 4 Overview: 6-stage SMIPS Pipeline T05-1 Introduction Lab 4 involves creating a 6 stage pipelined SMIPS processor from a 2 stage pipeline This requires a lot of attention to architectural details of
Lab 4 Overview: 6-stage SMIPS Pipeline T05-1 Introduction Lab 4 involves creating a 6 stage pipelined SMIPS processor from a 2 stage pipeline This requires a lot of attention to architectural details of
CSE 490/590 Computer Architecture Homework 2
 CSE 490/590 Computer Architecture Homework 2 1. Suppose that you have the following out-of-order datapath with 1-cycle ALU, 2-cycle Mem, 3-cycle Fadd, 5-cycle Fmul, no branch prediction, and in-order fetch
CSE 490/590 Computer Architecture Homework 2 1. Suppose that you have the following out-of-order datapath with 1-cycle ALU, 2-cycle Mem, 3-cycle Fadd, 5-cycle Fmul, no branch prediction, and in-order fetch
VHDL vs. BSV: A case study on a Java-optimized processor
 VHDL vs. BSV: A case study on a Java-optimized processor April 18, 2007 Outline Introduction Goal Design parameters Goal Design parameters What are we trying to do? Compare BlueSpec SystemVerilog (BSV)
VHDL vs. BSV: A case study on a Java-optimized processor April 18, 2007 Outline Introduction Goal Design parameters Goal Design parameters What are we trying to do? Compare BlueSpec SystemVerilog (BSV)
BeiHang Short Course, Part 2: Description and Synthesis
 BeiHang Short Course, Part 2: Operation Centric Hardware Description and Synthesis J. C. Hoe, CMU/ECE/CALCM, 2014, BHSC L2 s1 James C. Hoe Department of ECE Carnegie Mellon University Collaborator: Arvind
BeiHang Short Course, Part 2: Operation Centric Hardware Description and Synthesis J. C. Hoe, CMU/ECE/CALCM, 2014, BHSC L2 s1 James C. Hoe Department of ECE Carnegie Mellon University Collaborator: Arvind
ECE 552 / CPS 550 Advanced Computer Architecture I. Lecture 6 Pipelining Part 1
 ECE 552 / CPS 550 Advanced Computer Architecture I Lecture 6 Pipelining Part 1 Benjamin Lee Electrical and Computer Engineering Duke University www.duke.edu/~bcl15 www.duke.edu/~bcl15/class/class_ece252fall12.html
ECE 552 / CPS 550 Advanced Computer Architecture I Lecture 6 Pipelining Part 1 Benjamin Lee Electrical and Computer Engineering Duke University www.duke.edu/~bcl15 www.duke.edu/~bcl15/class/class_ece252fall12.html
Memory System Implementation
 Memory System Implementation Silvina Hanono Wachman Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L14-1 Best Wishes from Japan October 25, 2018 MIT 6.004 Fall 2018
Memory System Implementation Silvina Hanono Wachman Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L14-1 Best Wishes from Japan October 25, 2018 MIT 6.004 Fall 2018
Pipeline Hazards. Midterm #2 on 11/29 5th and final problem set on 11/22 9th and final lab on 12/1. https://goo.gl/forms/hkuvwlhvuyzvdat42
 Pipeline Hazards https://goo.gl/forms/hkuvwlhvuyzvdat42 Midterm #2 on 11/29 5th and final problem set on 11/22 9th and final lab on 12/1 1 ARM 3-stage pipeline Fetch,, and Execute Stages Instructions are
Pipeline Hazards https://goo.gl/forms/hkuvwlhvuyzvdat42 Midterm #2 on 11/29 5th and final problem set on 11/22 9th and final lab on 12/1 1 ARM 3-stage pipeline Fetch,, and Execute Stages Instructions are
ECE 313 Computer Organization FINAL EXAM December 13, 2000
 This exam is open book and open notes. You have until 11:00AM. Credit for problems requiring calculation will be given only if you show your work. 1. Floating Point Representation / MIPS Assembly Language
This exam is open book and open notes. You have until 11:00AM. Credit for problems requiring calculation will be given only if you show your work. 1. Floating Point Representation / MIPS Assembly Language
EECS 151/251A Fall 2017 Digital Design and Integrated Circuits. Instructor: John Wawrzynek and Nicholas Weaver. Lecture 13 EE141
 EECS 151/251A Fall 2017 Digital Design and Integrated Circuits Instructor: John Wawrzynek and Nicholas Weaver Lecture 13 Project Introduction You will design and optimize a RISC-V processor Phase 1: Design
EECS 151/251A Fall 2017 Digital Design and Integrated Circuits Instructor: John Wawrzynek and Nicholas Weaver Lecture 13 Project Introduction You will design and optimize a RISC-V processor Phase 1: Design
EITF20: Computer Architecture Part2.2.1: Pipeline-1
 EITF20: Computer Architecture Part2.2.1: Pipeline-1 Liang Liu liang.liu@eit.lth.se 1 Outline Reiteration Pipelining Harzards Structural hazards Data hazards Control hazards Implementation issues Multi-cycle
EITF20: Computer Architecture Part2.2.1: Pipeline-1 Liang Liu liang.liu@eit.lth.se 1 Outline Reiteration Pipelining Harzards Structural hazards Data hazards Control hazards Implementation issues Multi-cycle
ECS 154B Computer Architecture II Spring 2009
 ECS 154B Computer Architecture II Spring 2009 Pipelining Datapath and Control 6.2-6.3 Partially adapted from slides by Mary Jane Irwin, Penn State And Kurtis Kredo, UCD Pipelined CPU Break execution into
ECS 154B Computer Architecture II Spring 2009 Pipelining Datapath and Control 6.2-6.3 Partially adapted from slides by Mary Jane Irwin, Penn State And Kurtis Kredo, UCD Pipelined CPU Break execution into
Constructive Computer Architecture Tutorial 6: Five Details of SMIPS Implementations
 Constructive Computer Architecture Tutorial 6: Five Details of SMIPS Implementations Andy Wright 6.S195 TA T05-1 Introduction Lab 6 involves creating a 6 stage pipelined SMIPS processor from a 2 stage
Constructive Computer Architecture Tutorial 6: Five Details of SMIPS Implementations Andy Wright 6.S195 TA T05-1 Introduction Lab 6 involves creating a 6 stage pipelined SMIPS processor from a 2 stage
Introduction to Pipelining. Silvina Hanono Wachman Computer Science & Artificial Intelligence Lab M.I.T.
 Introduction to Pipelining Silvina Hanono Wachman Computer Science & Artificial Intelligence Lab M.I.T. L15-1 Performance Measures Two metrics of interest when designing a system: 1. Latency: The delay
Introduction to Pipelining Silvina Hanono Wachman Computer Science & Artificial Intelligence Lab M.I.T. L15-1 Performance Measures Two metrics of interest when designing a system: 1. Latency: The delay
Constructive Computer Architecture. Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology
 Constructive Computer Architecture Caches-2 Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L18-1 Cache Interface req memreq mshr mreqq DRAM or Processor next
Constructive Computer Architecture Caches-2 Arvind Computer Science & Artificial Intelligence Lab. Massachusetts Institute of Technology L18-1 Cache Interface req memreq mshr mreqq DRAM or Processor next
CS152 Computer Architecture and Engineering March 13, 2008 Out of Order Execution and Branch Prediction Assigned March 13 Problem Set #4 Due March 25
 CS152 Computer Architecture and Engineering March 13, 2008 Out of Order Execution and Branch Prediction Assigned March 13 Problem Set #4 Due March 25 http://inst.eecs.berkeley.edu/~cs152/sp08 The problem
CS152 Computer Architecture and Engineering March 13, 2008 Out of Order Execution and Branch Prediction Assigned March 13 Problem Set #4 Due March 25 http://inst.eecs.berkeley.edu/~cs152/sp08 The problem
Chapter 4 The Processor 1. Chapter 4A. The Processor
 Chapter 4 The Processor 1 Chapter 4A The Processor Chapter 4 The Processor 2 Introduction CPU performance factors Instruction count Determined by ISA and compiler CPI and Cycle time Determined by CPU hardware
Chapter 4 The Processor 1 Chapter 4A The Processor Chapter 4 The Processor 2 Introduction CPU performance factors Instruction count Determined by ISA and compiler CPI and Cycle time Determined by CPU hardware
COSC 6385 Computer Architecture - Pipelining
 COSC 6385 Computer Architecture - Pipelining Fall 2006 Some of the slides are based on a lecture by David Culler, Instruction Set Architecture Relevant features for distinguishing ISA s Internal storage
COSC 6385 Computer Architecture - Pipelining Fall 2006 Some of the slides are based on a lecture by David Culler, Instruction Set Architecture Relevant features for distinguishing ISA s Internal storage
SI232 Set #20: Laundry, Co-dependency, and other Hazards of Modern (Architecture) Life. Chapter 6 ADMIN. Reading for Chapter 6: 6.1,
 SI232 Set #20: Laundry, Co-dependency, and other Hazards of Modern (Architecture) Life Chapter 6 ADMIN ing for Chapter 6: 6., 6.9-6.2 2 Midnight Laundry Task order A 6 PM 7 8 9 0 2 2 AM B C D 3 Smarty
SI232 Set #20: Laundry, Co-dependency, and other Hazards of Modern (Architecture) Life Chapter 6 ADMIN ing for Chapter 6: 6., 6.9-6.2 2 Midnight Laundry Task order A 6 PM 7 8 9 0 2 2 AM B C D 3 Smarty
E0-243: Computer Architecture
 E0-243: Computer Architecture L1 ILP Processors RG:E0243:L1-ILP Processors 1 ILP Architectures Superscalar Architecture VLIW Architecture EPIC, Subword Parallelism, RG:E0243:L1-ILP Processors 2 Motivation
E0-243: Computer Architecture L1 ILP Processors RG:E0243:L1-ILP Processors 1 ILP Architectures Superscalar Architecture VLIW Architecture EPIC, Subword Parallelism, RG:E0243:L1-ILP Processors 2 Motivation
Control Hazards - branching causes problems since the pipeline can be filled with the wrong instructions.
 Control Hazards - branching causes problems since the pipeline can be filled with the wrong instructions Stage Instruction Fetch Instruction Decode Execution / Effective addr Memory access Write-back Abbreviation
Control Hazards - branching causes problems since the pipeline can be filled with the wrong instructions Stage Instruction Fetch Instruction Decode Execution / Effective addr Memory access Write-back Abbreviation
CISC 662 Graduate Computer Architecture Lecture 6 - Hazards
 CISC 662 Graduate Computer Architecture Lecture 6 - Hazards Michela Taufer http://www.cis.udel.edu/~taufer/teaching/cis662f07 Powerpoint Lecture Notes from John Hennessy and David Patterson s: Computer
CISC 662 Graduate Computer Architecture Lecture 6 - Hazards Michela Taufer http://www.cis.udel.edu/~taufer/teaching/cis662f07 Powerpoint Lecture Notes from John Hennessy and David Patterson s: Computer
RTN (Register Transfer Notation)
 RTN (Register Transfer Notation) A formal means of describing machine structure & function. Is at the just right level for machine descriptions. Does not replace hardware description languages. RTN is
RTN (Register Transfer Notation) A formal means of describing machine structure & function. Is at the just right level for machine descriptions. Does not replace hardware description languages. RTN is
1 Hazards COMP2611 Fall 2015 Pipelined Processor
 1 Hazards Dependences in Programs 2 Data dependence Example: lw $1, 200($2) add $3, $4, $1 add can t do ID (i.e., read register $1) until lw updates $1 Control dependence Example: bne $1, $2, target add
1 Hazards Dependences in Programs 2 Data dependence Example: lw $1, 200($2) add $3, $4, $1 add can t do ID (i.e., read register $1) until lw updates $1 Control dependence Example: bne $1, $2, target add
Instruction Pipelining
 Instruction Pipelining Simplest form is a 3-stage linear pipeline New instruction fetched each clock cycle Instruction finished each clock cycle Maximal speedup = 3 achieved if and only if all pipe stages
Instruction Pipelining Simplest form is a 3-stage linear pipeline New instruction fetched each clock cycle Instruction finished each clock cycle Maximal speedup = 3 achieved if and only if all pipe stages
Instruction Pipelining
 Instruction Pipelining Simplest form is a 3-stage linear pipeline New instruction fetched each clock cycle Instruction finished each clock cycle Maximal speedup = 3 achieved if and only if all pipe stages
Instruction Pipelining Simplest form is a 3-stage linear pipeline New instruction fetched each clock cycle Instruction finished each clock cycle Maximal speedup = 3 achieved if and only if all pipe stages
Constructive Computer Architecture Tutorial 7: SMIPS Epochs. Andy Wright TA. October 7,
 Constructive Computer Architecture Tutorial 7: SMIPS Epochs Andy Wright 6.7 TA T0- drecirect erecirect N-Stage pipeline: Two predictors f fdepoch redirect depoch redirect d miss pred? miss pred? Fetch
Constructive Computer Architecture Tutorial 7: SMIPS Epochs Andy Wright 6.7 TA T0- drecirect erecirect N-Stage pipeline: Two predictors f fdepoch redirect depoch redirect d miss pred? miss pred? Fetch
EECS150 - Digital Design Lecture 10- CPU Microarchitecture. Processor Microarchitecture Introduction
 EECS150 - Digital Design Lecture 10- CPU Microarchitecture Feb 18, 2010 John Wawrzynek Spring 2010 EECS150 - Lec10-cpu Page 1 Processor Microarchitecture Introduction Microarchitecture: how to implement
EECS150 - Digital Design Lecture 10- CPU Microarchitecture Feb 18, 2010 John Wawrzynek Spring 2010 EECS150 - Lec10-cpu Page 1 Processor Microarchitecture Introduction Microarchitecture: how to implement
Week 11: Assignment Solutions
 Week 11: Assignment Solutions 1. Consider an instruction pipeline with four stages with the stage delays 5 nsec, 6 nsec, 11 nsec, and 8 nsec respectively. The delay of an inter-stage register stage of
Week 11: Assignment Solutions 1. Consider an instruction pipeline with four stages with the stage delays 5 nsec, 6 nsec, 11 nsec, and 8 nsec respectively. The delay of an inter-stage register stage of
Instruction Level Parallelism. Appendix C and Chapter 3, HP5e
 Instruction Level Parallelism Appendix C and Chapter 3, HP5e Outline Pipelining, Hazards Branch prediction Static and Dynamic Scheduling Speculation Compiler techniques, VLIW Limits of ILP. Implementation
Instruction Level Parallelism Appendix C and Chapter 3, HP5e Outline Pipelining, Hazards Branch prediction Static and Dynamic Scheduling Speculation Compiler techniques, VLIW Limits of ILP. Implementation
CS 152, Spring 2011 Section 2
 CS 152, Spring 2011 Section 2 Christopher Celio University of California, Berkeley About Me Christopher Celio celio @ eecs Office Hours: Tuesday 1-2pm, 751 Soda Agenda Q&A on HW1, Lab 1 Pipelining Questions
CS 152, Spring 2011 Section 2 Christopher Celio University of California, Berkeley About Me Christopher Celio celio @ eecs Office Hours: Tuesday 1-2pm, 751 Soda Agenda Q&A on HW1, Lab 1 Pipelining Questions
Pipelining: Hazards Ver. Jan 14, 2014
 POLITECNICO DI MILANO Parallelism in wonderland: are you ready to see how deep the rabbit hole goes? Pipelining: Hazards Ver. Jan 14, 2014 Marco D. Santambrogio: marco.santambrogio@polimi.it Simone Campanoni:
POLITECNICO DI MILANO Parallelism in wonderland: are you ready to see how deep the rabbit hole goes? Pipelining: Hazards Ver. Jan 14, 2014 Marco D. Santambrogio: marco.santambrogio@polimi.it Simone Campanoni:
Lecture: Out-of-order Processors. Topics: out-of-order implementations with issue queue, register renaming, and reorder buffer, timing, LSQ
 Lecture: Out-of-order Processors Topics: out-of-order implementations with issue queue, register renaming, and reorder buffer, timing, LSQ 1 An Out-of-Order Processor Implementation Reorder Buffer (ROB)
Lecture: Out-of-order Processors Topics: out-of-order implementations with issue queue, register renaming, and reorder buffer, timing, LSQ 1 An Out-of-Order Processor Implementation Reorder Buffer (ROB)
Lecture 7 Pipelining. Peng Liu.
 Lecture 7 Pipelining Peng Liu liupeng@zju.edu.cn 1 Review: The Single Cycle Processor 2 Review: Given Datapath,RTL -> Control Instruction Inst Memory Adr Op Fun Rt
Lecture 7 Pipelining Peng Liu liupeng@zju.edu.cn 1 Review: The Single Cycle Processor 2 Review: Given Datapath,RTL -> Control Instruction Inst Memory Adr Op Fun Rt
ECE473 Computer Architecture and Organization. Pipeline: Control Hazard
 Computer Architecture and Organization Pipeline: Control Hazard Lecturer: Prof. Yifeng Zhu Fall, 2015 Portions of these slides are derived from: Dave Patterson UCB Lec 15.1 Pipelining Outline Introduction
Computer Architecture and Organization Pipeline: Control Hazard Lecturer: Prof. Yifeng Zhu Fall, 2015 Portions of these slides are derived from: Dave Patterson UCB Lec 15.1 Pipelining Outline Introduction
CSE 533: Advanced Computer Architectures. Pipelining. Instructor: Gürhan Küçük. Yeditepe University
 CSE 533: Advanced Computer Architectures Pipelining Instructor: Gürhan Küçük Yeditepe University Lecture notes based on notes by Mark D. Hill and John P. Shen Updated by Mikko Lipasti Pipelining Forecast
CSE 533: Advanced Computer Architectures Pipelining Instructor: Gürhan Küçük Yeditepe University Lecture notes based on notes by Mark D. Hill and John P. Shen Updated by Mikko Lipasti Pipelining Forecast
Chapter 4. The Processor
 Chapter 4 The Processor Introduction CPU performance factors Instruction count Determined by ISA and compiler CPI and Cycle time Determined by CPU hardware We will examine two MIPS implementations A simplified
Chapter 4 The Processor Introduction CPU performance factors Instruction count Determined by ISA and compiler CPI and Cycle time Determined by CPU hardware We will examine two MIPS implementations A simplified
Lecture 9. Pipeline Hazards. Christos Kozyrakis Stanford University
 Lecture 9 Pipeline Hazards Christos Kozyrakis Stanford University http://eeclass.stanford.edu/ee18b 1 Announcements PA-1 is due today Electronic submission Lab2 is due on Tuesday 2/13 th Quiz1 grades will
Lecture 9 Pipeline Hazards Christos Kozyrakis Stanford University http://eeclass.stanford.edu/ee18b 1 Announcements PA-1 is due today Electronic submission Lab2 is due on Tuesday 2/13 th Quiz1 grades will
CS 152 Computer Architecture and Engineering
 CS 152 Computer Architecture and Engineering Lecture 18 Advanced Processors II 2006-10-31 John Lazzaro (www.cs.berkeley.edu/~lazzaro) Thanks to Krste Asanovic... TAs: Udam Saini and Jue Sun www-inst.eecs.berkeley.edu/~cs152/
CS 152 Computer Architecture and Engineering Lecture 18 Advanced Processors II 2006-10-31 John Lazzaro (www.cs.berkeley.edu/~lazzaro) Thanks to Krste Asanovic... TAs: Udam Saini and Jue Sun www-inst.eecs.berkeley.edu/~cs152/
ECE 313 Computer Organization FINAL EXAM December 11, Multicycle Processor Design 30 Points
 This exam is open book and open notes. Credit for problems requiring calculation will be given only if you show your work. 1. Multicycle Processor Design 0 Points In our discussion of exceptions in the
This exam is open book and open notes. Credit for problems requiring calculation will be given only if you show your work. 1. Multicycle Processor Design 0 Points In our discussion of exceptions in the
EITF20: Computer Architecture Part2.2.1: Pipeline-1
 EITF20: Computer Architecture Part2.2.1: Pipeline-1 Liang Liu liang.liu@eit.lth.se 1 Outline Reiteration Pipelining Harzards Structural hazards Data hazards Control hazards Implementation issues Multi-cycle
EITF20: Computer Architecture Part2.2.1: Pipeline-1 Liang Liu liang.liu@eit.lth.se 1 Outline Reiteration Pipelining Harzards Structural hazards Data hazards Control hazards Implementation issues Multi-cycle
1 /18 2 /16 3 /18 4 /26 5 /22
 M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.004 Computation Structures Fall 2018 Quiz #2 1 /18 2 /16 3 /18 4 /26 5 /22
M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.004 Computation Structures Fall 2018 Quiz #2 1 /18 2 /16 3 /18 4 /26 5 /22
The Processor. Z. Jerry Shi Department of Computer Science and Engineering University of Connecticut. CSE3666: Introduction to Computer Architecture
 The Processor Z. Jerry Shi Department of Computer Science and Engineering University of Connecticut CSE3666: Introduction to Computer Architecture Introduction CPU performance factors Instruction count
The Processor Z. Jerry Shi Department of Computer Science and Engineering University of Connecticut CSE3666: Introduction to Computer Architecture Introduction CPU performance factors Instruction count
CS 152 Computer Architecture and Engineering. Lecture 12 - Advanced Out-of-Order Superscalars
 CS 152 Computer Architecture and Engineering Lecture 12 - Advanced Out-of-Order Superscalars Dr. George Michelogiannakis EECS, University of California at Berkeley CRD, Lawrence Berkeley National Laboratory
CS 152 Computer Architecture and Engineering Lecture 12 - Advanced Out-of-Order Superscalars Dr. George Michelogiannakis EECS, University of California at Berkeley CRD, Lawrence Berkeley National Laboratory
LECTURE 3: THE PROCESSOR
 LECTURE 3: THE PROCESSOR Abridged version of Patterson & Hennessy (2013):Ch.4 Introduction CPU performance factors Instruction count Determined by ISA and compiler CPI and Cycle time Determined by CPU
LECTURE 3: THE PROCESSOR Abridged version of Patterson & Hennessy (2013):Ch.4 Introduction CPU performance factors Instruction count Determined by ISA and compiler CPI and Cycle time Determined by CPU
EITF20: Computer Architecture Part2.2.1: Pipeline-1
 EITF20: Computer Architecture Part2.2.1: Pipeline-1 Liang Liu liang.liu@eit.lth.se 1 Outline Reiteration Pipelining Harzards Structural hazards Data hazards Control hazards Implementation issues Multi-cycle
EITF20: Computer Architecture Part2.2.1: Pipeline-1 Liang Liu liang.liu@eit.lth.se 1 Outline Reiteration Pipelining Harzards Structural hazards Data hazards Control hazards Implementation issues Multi-cycle
ELE 655 Microprocessor System Design
 ELE 655 Microprocessor System Design Section 2 Instruction Level Parallelism Class 1 Basic Pipeline Notes: Reg shows up two places but actually is the same register file Writes occur on the second half
ELE 655 Microprocessor System Design Section 2 Instruction Level Parallelism Class 1 Basic Pipeline Notes: Reg shows up two places but actually is the same register file Writes occur on the second half
Simple Inelastic and
 Simple Inelastic and Folded Pipelines Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L04-1 Pipelining a block C f1 f2 f3 Combinational P f1 f2 f3 Pipeline FP
Simple Inelastic and Folded Pipelines Arvind Computer Science & Artificial Intelligence Lab Massachusetts Institute of Technology L04-1 Pipelining a block C f1 f2 f3 Combinational P f1 f2 f3 Pipeline FP
CS 252 Graduate Computer Architecture. Lecture 4: Instruction-Level Parallelism
 CS 252 Graduate Computer Architecture Lecture 4: Instruction-Level Parallelism Krste Asanovic Electrical Engineering and Computer Sciences University of California, Berkeley http://wwweecsberkeleyedu/~krste
CS 252 Graduate Computer Architecture Lecture 4: Instruction-Level Parallelism Krste Asanovic Electrical Engineering and Computer Sciences University of California, Berkeley http://wwweecsberkeleyedu/~krste
Lecture 4 - Pipelining
 CS 152 Computer Architecture and Engineering Lecture 4 - Pipelining John Wawrzynek Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~johnw
CS 152 Computer Architecture and Engineering Lecture 4 - Pipelining John Wawrzynek Electrical Engineering and Computer Sciences University of California at Berkeley http://www.eecs.berkeley.edu/~johnw
Pipelining concepts The DLX architecture A simple DLX pipeline Pipeline Hazards and Solution to overcome
 Thoai Nam Pipelining concepts The DLX architecture A simple DLX pipeline Pipeline Hazards and Solution to overcome Reference: Computer Architecture: A Quantitative Approach, John L Hennessy & David a Patterson,
Thoai Nam Pipelining concepts The DLX architecture A simple DLX pipeline Pipeline Hazards and Solution to overcome Reference: Computer Architecture: A Quantitative Approach, John L Hennessy & David a Patterson,
1 /15 2 /20 3 /20 4 /25 5 /20
 M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.S084 Computation Structures Spring 2018 1 /15 2 /20 3 /20 4 /25 5 /20 Quiz
M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.S084 Computation Structures Spring 2018 1 /15 2 /20 3 /20 4 /25 5 /20 Quiz
Four Steps of Speculative Tomasulo cycle 0
 HW support for More ILP Hardware Speculative Execution Speculation: allow an instruction to issue that is dependent on branch, without any consequences (including exceptions) if branch is predicted incorrectly
HW support for More ILP Hardware Speculative Execution Speculation: allow an instruction to issue that is dependent on branch, without any consequences (including exceptions) if branch is predicted incorrectly
Lecture 5: Instruction Pipelining. Pipeline hazards. Sequential execution of an N-stage task: N Task 2
 Lecture 5: Instruction Pipelining Basic concepts Pipeline hazards Branch handling and prediction Zebo Peng, IDA, LiTH Sequential execution of an N-stage task: 3 N Task 3 N Task Production time: N time
Lecture 5: Instruction Pipelining Basic concepts Pipeline hazards Branch handling and prediction Zebo Peng, IDA, LiTH Sequential execution of an N-stage task: 3 N Task 3 N Task Production time: N time
1 /18 2 /16 3 /18 4 /26 5 /22
 M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.004 Computation Structures Fall 2018 Quiz #2 1 /18 2 /16 3 /18 4 /26 5 /22
M A S S A C H U S E T T S I N S T I T U T E O F T E C H N O L O G Y DEPARTMENT OF ELECTRICAL ENGINEERING AND COMPUTER SCIENCE 6.004 Computation Structures Fall 2018 Quiz #2 1 /18 2 /16 3 /18 4 /26 5 /22
Computer Architecture Spring 2016
 Computer Architecture Spring 2016 Lecture 02: Introduction II Shuai Wang Department of Computer Science and Technology Nanjing University Pipeline Hazards Major hurdle to pipelining: hazards prevent the
Computer Architecture Spring 2016 Lecture 02: Introduction II Shuai Wang Department of Computer Science and Technology Nanjing University Pipeline Hazards Major hurdle to pipelining: hazards prevent the
Dynamic Branch Prediction
 Dynamic Branch Prediction Readings: 4.8 Branches introduce control hazards Determine the right next instruction in time for instruction fetch Previous solutions: Stall Statically predict not taken Branch
Dynamic Branch Prediction Readings: 4.8 Branches introduce control hazards Determine the right next instruction in time for instruction fetch Previous solutions: Stall Statically predict not taken Branch
CS 152 Computer Architecture and Engineering. Lecture 13 - Out-of-Order Issue and Register Renaming
 CS 152 Computer Architecture and Engineering Lecture 13 - Out-of-Order Issue and Register Renaming Krste Asanovic Electrical Engineering and Computer Sciences University of California at Berkeley http://wwweecsberkeleyedu/~krste
CS 152 Computer Architecture and Engineering Lecture 13 - Out-of-Order Issue and Register Renaming Krste Asanovic Electrical Engineering and Computer Sciences University of California at Berkeley http://wwweecsberkeleyedu/~krste
6.823 Computer System Architecture Datapath for DLX Problem Set #2
 6.823 Computer System Architecture Datapath for DLX Problem Set #2 Spring 2002 Students are allowed to collaborate in groups of up to 3 people. A group hands in only one copy of the solution to a problem
6.823 Computer System Architecture Datapath for DLX Problem Set #2 Spring 2002 Students are allowed to collaborate in groups of up to 3 people. A group hands in only one copy of the solution to a problem
