EE382V: System-on-a-Chip (SoC) Design
|
|
|
- Lorraine Ramsey
- 5 years ago
- Views:
Transcription
1 EE382V: System-on-a-Chip (SoC) Design Lecture 5 Performance Analysis Sources: Prof. Jacob Abraham, UT Austin Prof. Lothar Thiele, ETH Zurich Prof. Reinhard Wilhelm, Saarland Univ. Andreas Gerstlauer Electrical and Computer Engineering University of Texas at Austin gerstl@ece.utexas.edu Lecture 5: Outline SoC design flow Iterative design convergence Requirement & performance analysis Algorithm analysis Component-level estimation System-level estimation EE382V: SoC Design, Lecture A. Gerstlauer A. Gerstlauer 1
2 SoC Design Flow Start Analyze results Product Validation Loop No Modify Model? Yes MRD PRD Map, Model & Simulate in SPW or Matlab or C or C++ Functionality Met? Yes System BOM Costs Met? No No No Mapping to Platform or Components Complete? Yes Power Req. Met? No Design Convergence and Verification Loop No Yes Analyze results Metrics Met? Yes Schedule Req. Met? Yes No Yes Freeze Architecture Platform Req. Met? No No MRD Met? Yes Return Yes EE382V: SoC Design, Lecture 5 Done 2014 A. Gerstlauer 3 Design Convergence Front End Design Implementation Reduced convergence time due to minimal data Convergence time increases due to more design data # Optimization Solutions Reduced convergence time due to reduced solution space Convergence time increases due to transition phase Reduced convergence time due to reduced solution space Design Converges Rapid Exploration Rapid Traversal EE382V: SoC Design, Lecture A. Gerstlauer A. Gerstlauer 2
3 Performance of a System Depends on many factors System design (algorithms and data structures) Implementation (code) Execution platform architecture The workload to which it is subjected The metric used in the evaluation Interactions between these factors EE382V: SoC Design, Lecture A. Gerstlauer 5 Performance Analysis Predictability w.c. guarantee w.c. performance 0 Lower Best bound case Worst case Upper bound Variation of actual execution times Simulation (dynamic) vs. analysis (static) Tightness of bounds, under- vs. over-estimation EE382V: SoC Design, Lecture A. Gerstlauer A. Gerstlauer 3
4 Evaluating a Design Algorithm level Analysis of complexity Identify bottlenecks, evaluate tradeoffs Component level Software partition Profiling, measurement Simulation, tracing Power/performance/ estimation Hardware partition Modeling & estimation System level Virtual platform prototyping Physical prototyping EE382V: SoC Design, Lecture A. Gerstlauer 7 Algorithm Analysis Theoretical complexity analysis O() notation ( order-of ) Example: Sorting Bubble sort Merge sort Example: Fourier transform Discrete Fourier transform Fast Fourier transform Analysis of code Example: BCH * encoding Code in C Find the number of XOR and AND operations performed in the loop as a function of k Assume length is 1024, and in any bit position, 0 and 1 are equally likely * A BCH code is a multilevel, cyclic, error-correcting, variable-length digital code used to correct multiple random error patterns. BCH codes may also be used with multilevel phase-shift keying whenever the number of levels is a prime number or a power of a prime number. EE382V: SoC Design, Lecture A. Gerstlauer A. Gerstlauer 4
5 BCH Code encode_bch() { register int i, j; register int feedback; for (i = 0; i < length - k; i++) bb[i] = 0; for (i = k - 1; i >= 0; i--) { feedback = data[i] ^ bb[length - k - 1]; if (feedback!= 0) { for (j = length - k - 1; j > 0; j--) if (g[j]!= 0) bb[j] = bb[j - 1] ^ feedback; else bb[j] = bb[j - 1]; bb[0] = g[0] && feedback; } else { for (j = length - k - 1; j > 0; j--) bb[j] = bb[j - 1]; bb[0] = 0; } } } EE382V: SoC Design, Lecture A. Gerstlauer 9 Code Profiling Execute code on physical or simulated machine (Cross-)Compile down to binary Run on real processor or instruction-set simulator Benchmarks and input data test vectors Instrument code and collect metrics at runtime Include effect of processor instruction set and architecture For the given runtime platform (not necessarily the intended target) Many profiling tools for data gathering and analysis gprof, etc. Various interfaces, levels of automation, and approaches to information presentation A lot of work in the high performance computing community Effect of instrumentation on measured results? EE382V: SoC Design, Lecture A. Gerstlauer A. Gerstlauer 5
6 Instrumentation Techniques Program instrumentation techniques Manual: Programmer inserted directives Automatic: No direct user involvement Sampling [gprof] Binary rewriting [PIN] Dynamic Instrumentation Hardware instrumentation techniques Timers, memory system performance, processor usage, etc. Available mostly through special registers or memory mapped location Example: Pentium Pro MSRs (model (machine)-specific registers)» Counters for clock cycles, memory read/write, L1 cache misses, pipeline flushes, etc. Hardware assisted trace generation Operating system instrumentation techniques Behavior of virtual memory, file system, file cache, etc. Access via APIs Network instrumentation techniques Passive, e.g. RMON protocol packet header fields for monitoring Active, e.g. ping, NWS in grid style computing. EE382V: SoC Design, Lecture A. Gerstlauer 11 DRM Profiling PC-based reference code Designed to run in a Linux environment, but in this course, we are going to make it run on an embedded processor (ARM Cortex-A9) Profile in both Linux and (simulated) ARM environments Measure performance and identify bottlenecks Linux environment profiling gprof measures where program spends its time and which functions call other functions while it was executing Flat profile: total amount of time program spends executing each function Call graph: how much time was spent in each function and its children ARM environment profiling Run gprof in virtual platform prototype Flat and call graph profiles Timing accuracy of virtual platform? (QEMU timing model!) EE382V: SoC Design, Lecture A. Gerstlauer A. Gerstlauer 6
7 Component Simulation Cycle-accurate Describe micro-architecture/rtl in C Interpreted instruction-set simulation Cycle-accurate/-approximate Functionality/behavior only ISS Binary Arch. State App. RTOS HAL CPU I/O Compiled ISS Binary translation Offline vs. just-in-time (self-modifying code) Functional only (no/rough timing, e.g. CPI=1) Source-level/host-compiled simulation C model describing functionality/behavior Back-annotate with timing and other metrics EE382V: SoC Design, Lecture A. Gerstlauer 13 Quick EMUlator (QEMU) Open-source, binary-translating ISS [Ballard xx] Emulates a variety of architectures (x86, ARM, PowerPC) Stand-alone or full-system model (peripherals to boot OS) Source: M. Gilgor, N. Fournel, F. Pétrot, Using Binary Translation in Event Driven Simulation for Fast and Flexible MPSoC Simulation, CODES+ISSS'09 EE382V: SoC Design, Lecture A. Gerstlauer A. Gerstlauer 7
8 Estimation Static analysis and prediction of performance Need for hard guarantees in embedded space Reliability, safety, etc. Worst-Case Execution Time (WCET) estimation Tightness of bounds? Analysis of modern processors is very difficult Dynamic effects Pipeline introduces dependencies on input sequence (instructions) Cache effects Branch prediction Hazards lead to timing accidents & penalties Structural (resource being used by another) Data (dependence for data calculations) Control (calculating next address branches, interrupts) EE382V: SoC Design, Lecture A. Gerstlauer 15 Overall WCET Approach Compute upper bounds along the program structure Programs are hierarchically structured Compute the upper bound for a construct from the upper bounds of its constituents Basic blocks of code at the leaves of the hierarchy Micro-architecture analysis Abstract interpretation of code in basic blocks Determines WCET for each basic block (in contexts) Exclude as many timing accidents as possible Worst-case path determination Control flow graph (CFG) of basic blocks Map to an integer linear program Determines upper bound and associated path EE382V: SoC Design, Lecture 5 L. Thiele A. Gerstlauer 8
9 Conditional Statements A if B then A1 else A2 Constituents of A: 1. condition B 2. statements A1 and A2 yes B no wcet(a) = A1 A2 wcet(b) + max(wcet(a1), wcet(a2)) EE382V: SoC Design, Lecture 5 L. Thiele 17 Loops A for i 1 to 100 do A1 yes i 1 i 100 no wcet(a) = wcet(i 1) (wcet(i 100) + wcet(a1) ) + wcet( i 100) A1 EE382V: SoC Design, Lecture 5 L. Thiele A. Gerstlauer 9
10 ait Tool Executable program CFG Builder Control-Flow-Graph to improve WCET bounds for loops Loop Unfolding Static Analyses Path Analysis Value Analyzer Cache/Pipeline Analyzer Micro-architecture Analysis Micro- Architecture Timing Information ILP-Generator LP-Solver Evaluation Worst-case Path Determination Loop- Bounds WCET- Visualization EE382V: SoC Design, Lecture 5 L. Thiele 19 Program Path Analysis Program Path Analysis Which sequence of instructions is executed in the worstcase (longest runtime)? Problem: the number of possible program paths grows exponentially with the program length Model We know the upper bounds (number of cycles) for each basic block from static analysis Number of loop iterations must be bounded Concept Transform structure of CFG into a set of (integer) linear equations. Solution of the Integer Linear Program (ILP) yields bound on the WCET. EE382V: SoC Design, Lecture 5 L. Thiele A. Gerstlauer 10
11 Control Flow Graph (CFG) 1 what_is_this { 1 read (a,b); 2 done = FALSE; 3 repeat { 4 if (a>b) 5 a = a-b; 6 elseif (b>a) 7 b = b-a; 8 else done = TRUE; 9 } until done; 10 write (a); } a>b 5!done 2 4 a<b a<=b done 10 a=b EE382V: SoC Design, Lecture 5 L. Thiele 21 Control Flow Graph (CFG) The nodes are the basic blocks Single point of entry & exit Instructions in block always executed together i := 0 t2 := 0 L t2 := t2 + i i := i + 1 if i < 10 goto L x := t2 i < 10 i >= 10 EE382V: SoC Design, Lecture 5 L. Thiele A. Gerstlauer 11
12 Calculation of the WCET Definition: A program consists of N basic blocks, where each basic block B i has a worst-case execution time c i and is executed for exactly x i times. Then, the WCET is given by WCET N c i x i i 1 The c i values are determined using static analysis. How to determine x i? Structural constraints given by the program structure Additional constraints provided by the programmer (bounds for loop counters, etc.; based on knowledge of the program context) EE382V: SoC Design, Lecture 5 L. Thiele 23 Example B1 s = k; /* k >= 0 */ s = k; WHILE (k < 10) { IF (ok) j++; ELSE { j = 0; ok = true; } k ++; } r = j; B4 B2 j++; WHILE (k<10) B3 B6 if (ok) k++; B5 j = 0; ok = true; B7 r = j; EE382V: SoC Design, Lecture 5 L. Thiele A. Gerstlauer 12
13 Structural Constraints d1 B2 B1 s = k; d2 WHILE (k<10) 1 2 Flow equations: d1 = d2 = x 1 d2 + d8 = d3 + d9 = x 2 d3 d3 = d4 + d5 = x 3 B3 if (ok) 3 d4 = d6 = x 4 d4 d5 d5 = d7 = x 5 d9 B4 j++; 4 d6 B5 j 5 = 0; ok = true; d7 d6 + d7 = d8 = x 6 d9 = d10 = x 7 B6 k++; 6 d8 B7 r 7 = j; EE382V: SoC Design, Lecture 5 L. Thiele 25 d10 Additional Constraints d1 B1 s = k; d2 1 Loop is executed for at most 10 times: B2 WHILE (k<10) 2 x 3 <= 10 x 1 d3 B4 d9 j++; 4 B3 d6 d4 if (ok) B6 k++; 6 B5 3 d5 j 5 = 0; ok = true; d7 d8 B5 is executed for at most one time: x 5 <= 1 x 1 B7 r 7 = j; d10 L. Thiele A. Gerstlauer 13
14 Integer Linear Program (ILP) ILP with structural and additional constraints WCET max d j j in( B ) i... } { d k k out( B ) i i 1 c x 1 x, i 1... N Apply standard ILP solver NP-complete, i.e. exponential complexity! N i i i program is executed once d 1 structural constraints EE382V: SoC Design, Lecture 5 L. Thiele 27 Overview Executable program CFG Builder Control-Flow-Graph to improve WCET bounds for loops Loop Unfolding Static Analyses Path Analysis Value Analyzer Cache/Pipeline Analyzer Micro-architecture Analysis Micro- Architecture Timing Information ILP-Generator LP-Solver Evaluation Worst-case Path Determination Loop- Bounds WCET- Visualization EE382V: SoC Design, Lecture 5 L. Thiele A. Gerstlauer 14
15 Value Analysis Motivation: Provide access information to data-cache/pipeline analysis Detect infeasible paths Derive loop bounds Method: calculate intervals at all program points, i.e. lower and upper bounds for the set of possible values occurring in the machine program (addresses, register contents, local and global variables) Abstract interpretation (AI) Semantics-based method for static program analysis Perform the program's computations using value descriptions or abstract values in place of the concrete values, start with a description of all possible inputs Supports correctness proofs EE382V: SoC Design, Lecture 5 L. Thiele 29 Value Analysis move #4,D0 D1:[-4,4], A0:[0x1000,0x1000] D0:[4,4], D1:[-4,4], A0:[0x1000,0x1000] Intervals are computed along the CFG edges At joins, intervals are unioned add D1,D0 D0:[0,8], D1:[-4,4], A0:[0x1000,0x1000] move (A0,D0),D1 D1: [-2,+2] D1: [-4,0] D1: [-4,+2] Which address is accessed here? access [0x1000,0x1008] EE382V: SoC Design, Lecture 5 L. Thiele A. Gerstlauer 15
16 Caches Caches are used, because Speed gap between CPU and main memory Fast but expensive on-chip memory in between Every memory access goes through the cache Block m containing a is in the cache (hit): request for a is served in the next cycle. Block m is not in the cache (miss): m is transferred from main memory to the cache, m may replace some block in the cache, request for a is served ASAP while transfer still continues. Several replacement strategies: LRU, PLRU, FIFO,... determine which line to replace. EE382V: SoC Design, Lecture 5 L. Thiele 31 Static Cache Analysis Abstraction Sets of memory blocks in single cache lines From values to locations, ignoring arithmetic Must Analysis For each program point (and calling context), find out which blocks are in the cache Determines safe information about cache hits. Each predicted cache hit reduces WCET. May Analysis For each program point (and calling context), find out which blocks may be in the cache. Complement says what is not in the cache Determines safe information about cache misses. Each predicted cache miss increases BCET. EE382V: SoC Design, Lecture 5 L. Thiele A. Gerstlauer 16
17 Cache with LRU: Must Analysis concrete [ access s ] x y t z s x y t young old Age x t y s s x t y abstract [ access s ] { x } { } { y, t } { } { s } { x } { } {y, t} EE382V: SoC Design, Lecture 5 L. Thiele 33 Must Analysis: Join Join (must) { a } { } { c, f } { d } { c } { e } { a } { d } intersection + maximal age { } { } { a, c } { d } Interpretation: memory block a is definitively in the (concrete) cache => always hit EE382V: SoC Design, Lecture 5 L. Thiele A. Gerstlauer 17
18 Cache with LRU: May Analysis concrete [ access s ] x t z y s x t z young old Age t y x s s t y x abstract [ access s ] { x,t } { y,s } { z } { } { s } { x, t } { y, z } { } EE382V: SoC Design, Lecture 5 L. Thiele 35 May Analysis: Join Join (may) { a } { } { c, f } { d } { c } { e } { a } { d } union + minimal age { a, c } { e } { f } { d } Interpretation: all blocks may be in the cache; none is definitely not in the cache. EE382V: SoC Design, Lecture 5 L. Thiele A. Gerstlauer 18
19 Cache Analysis for WCET Information about cache contents sharpens timings. ref to s. t miss t hit if s is in must-cache: t WCET = t hit otherwise t WCET = t miss if s is in may-cache: t BCET = t hit otherwise t BCET = t miss EE382V: SoC Design, Lecture 5 L. Thiele 37 Cache Analysis Contexts Cache contents depends on the context Calls and loops First iteration loads the cache Intersection looses most of the information Distinguish as many contexts as useful 1 unrolling for caches 1 unrolling for branch prediction (pipeline) while cond do join (must) EE382V: SoC Design, Lecture 5 L. Thiele A. Gerstlauer 19
20 Overview Executable program CFG Builder Control-Flow-Graph to improve WCET bounds for loops Loop Unfolding Static Analyses Path Analysis Value Analyzer Cache/Pipeline Analyzer Micro-architecture Analysis Micro- Architecture Timing Information ILP-Generator LP-Solver Evaluation Worst-case Path Determination Loop- Bounds WCET- Visualization EE382V: SoC Design, Lecture 5 L. Thiele 39 Motorola ColdFire 5307 Pipeline set(a)/stop IAG cancel addr(a) wait fetch(a) IC1 hold await(a) wait cancel IC2 code(a) IED put(a) wait wait BUS UNIT instr wait IB next start EX read(a)/write(a) data/hold store wait SST EE382V: SoC Design, Lecture A. Gerstlauer A. Gerstlauer 20
21 Execution of Multiply Instruction Fetch Issue Execute Retire 1-Cache miss? Unit occupied? Multicycle? Pending instructions? No 30 Yes EE382V: SoC Design, Lecture A. Gerstlauer 41 Static Analysis of Hazards Cache analysis: prediction of cache hits on instruction or operand fetch or store lwz r4, 20(r1) Hit Dependency analysis: analysis of data/control hazards add r4, r5,r6 lwz r7, 10(r1) add r8, r4, r4 Operand ready Resource reservation tables: analysis of resource hazards IF EX M F EE382V: SoC Design, Lecture 5 L. Thiele A. Gerstlauer 21
22 Abstract Pipeline Execution exec (b : basic block, s : abstract pipeline state) t: trace Interprets instruction stream of b (annotated with cache information) starting in state s producing trace t length(t) gives number of cycles What is abstracted? Abstract states may lack information, e.g. about cache contents Assume local worst cases is safe (in the case of no timing anomalies) Traces may be longer (but never shorter) than in reality EE382V: SoC Design, Lecture 5 L. Thiele 43 Context Starting state for basic block? In particular, if there are several predecessor blocks? Solutions Sets of states Combine by assuming that local worst case is safe s 1 s? s 2 EE382V: SoC Design, Lecture 5 L. Thiele A. Gerstlauer 22
23 Summary of WCET Analysis Steps Value analysis Cache analysis using statically computed effective addresses and loop bounds Pipeline analysis Assume cache hits where predicted, Assume cache misses where predicted or not excluded. Only the worst result states of an instruction need to be considered as input states for successor instructions! Path analysis Compute final WCET estimate EE382V: SoC Design, Lecture 5 L. Thiele 45 Lecture 5: Outline SoC design flow Iterative design convergence Requirement & performance analysis Algorithm analysis Component-level estimation System-level estimation EE382V: SoC Design, Lecture A. Gerstlauer A. Gerstlauer 23
24 System Development Get the architecture right before implementation begins Best design for system performance and functionality Concept System Processor Addr Data RAM ROM System Development Interface The Intr Implementation Source: CoWare, Inc. EE382V: SoC Design, Lecture A. Gerstlauer 47 Virtual Platforms Software Startup code Device drivers RTOS Application code System Processor Addr Data RAM ROM Hardware Processors Bus Memory Peripherals Interfaces I/F Intr Analysis Simulation Virtual prototyping Instruction-set simulation in transaction-level model (TLM) Source: CoWare, Inc. EE382V: SoC Design, Lecture A. Gerstlauer A. Gerstlauer 24
25 Architecture Analysis Software ARM Core Instruction Data AHB Int. ROM Int. RAM Memory IRQ FIQ DMA Ctrl Slave Master1 APB APB_cfg AHB Custom Peripheral Hardware Master2 Bus Clock Gen. Reset Ctrl DMA_Int Intr. Ctrl. APB Input Device Source: CoWare, Inc. EE382V: SoC Design, Lecture A. Gerstlauer A. Gerstlauer 25
Hardware-Software Codesign. 9. Worst Case Execution Time Analysis
 Hardware-Software Codesign 9. Worst Case Execution Time Analysis Lothar Thiele 9-1 System Design Specification System Synthesis Estimation SW-Compilation Intellectual Prop. Code Instruction Set HW-Synthesis
Hardware-Software Codesign 9. Worst Case Execution Time Analysis Lothar Thiele 9-1 System Design Specification System Synthesis Estimation SW-Compilation Intellectual Prop. Code Instruction Set HW-Synthesis
HW/SW Codesign. WCET Analysis
 HW/SW Codesign WCET Analysis 29 November 2017 Andres Gomez gomeza@tik.ee.ethz.ch 1 Outline Today s exercise is one long question with several parts: Basic blocks of a program Static value analysis WCET
HW/SW Codesign WCET Analysis 29 November 2017 Andres Gomez gomeza@tik.ee.ethz.ch 1 Outline Today s exercise is one long question with several parts: Basic blocks of a program Static value analysis WCET
Design and Analysis of Real-Time Systems Microarchitectural Analysis
 Design and Analysis of Real-Time Systems Microarchitectural Analysis Jan Reineke Advanced Lecture, Summer 2013 Structure of WCET Analyzers Reconstructs a control-flow graph from the binary. Determines
Design and Analysis of Real-Time Systems Microarchitectural Analysis Jan Reineke Advanced Lecture, Summer 2013 Structure of WCET Analyzers Reconstructs a control-flow graph from the binary. Determines
EE382V: System-on-a-Chip (SoC) Design
 EE382V: System-on-a-Chip (SoC) Design Lecture 10 Task Partitioning Sources: Prof. Margarida Jacome, UT Austin Prof. Lothar Thiele, ETH Zürich Andreas Gerstlauer Electrical and Computer Engineering University
EE382V: System-on-a-Chip (SoC) Design Lecture 10 Task Partitioning Sources: Prof. Margarida Jacome, UT Austin Prof. Lothar Thiele, ETH Zürich Andreas Gerstlauer Electrical and Computer Engineering University
Previous Exam Questions System-on-a-Chip (SoC) Design
 Problem: Task Scheduling (20 Points) This is a simple single microprocessor core platform with a video coprocessor, which is configured to process 32 bytes of video data and produce a 1 byte result. Each
Problem: Task Scheduling (20 Points) This is a simple single microprocessor core platform with a video coprocessor, which is configured to process 32 bytes of video data and produce a 1 byte result. Each
ait: WORST-CASE EXECUTION TIME PREDICTION BY STATIC PROGRAM ANALYSIS
 ait: WORST-CASE EXECUTION TIME PREDICTION BY STATIC PROGRAM ANALYSIS Christian Ferdinand and Reinhold Heckmann AbsInt Angewandte Informatik GmbH, Stuhlsatzenhausweg 69, D-66123 Saarbrucken, Germany info@absint.com
ait: WORST-CASE EXECUTION TIME PREDICTION BY STATIC PROGRAM ANALYSIS Christian Ferdinand and Reinhold Heckmann AbsInt Angewandte Informatik GmbH, Stuhlsatzenhausweg 69, D-66123 Saarbrucken, Germany info@absint.com
Previous Exam Questions System-on-a-Chip (SoC) Design
 This image cannot currently be displayed. EE382V Problem: System Analysis (20 Points) This is a simple single microprocessor core platform with a video coprocessor, which is configured to process 32 bytes
This image cannot currently be displayed. EE382V Problem: System Analysis (20 Points) This is a simple single microprocessor core platform with a video coprocessor, which is configured to process 32 bytes
Timing analysis and timing predictability
 Timing analysis and timing predictability Architectural Dependences Reinhard Wilhelm Saarland University, Saarbrücken, Germany ArtistDesign Summer School in China 2010 What does the execution time depends
Timing analysis and timing predictability Architectural Dependences Reinhard Wilhelm Saarland University, Saarbrücken, Germany ArtistDesign Summer School in China 2010 What does the execution time depends
Timing Analysis. Dr. Florian Martin AbsInt
 Timing Analysis Dr. Florian Martin AbsInt AIT OVERVIEW 2 3 The Timing Problem Probability Exact Worst Case Execution Time ait WCET Analyzer results: safe precise (close to exact WCET) computed automatically
Timing Analysis Dr. Florian Martin AbsInt AIT OVERVIEW 2 3 The Timing Problem Probability Exact Worst Case Execution Time ait WCET Analyzer results: safe precise (close to exact WCET) computed automatically
Timing Analysis - timing guarantees for hard real-time systems- Reinhard Wilhelm Saarland University Saarbrücken
 Timing Analysis - timing guarantees for hard real-time systems- Reinhard Wilhelm Saarland University Saarbrücken Structure of the Lecture 1. Introduction 2. Static timing analysis 1. the problem 2. our
Timing Analysis - timing guarantees for hard real-time systems- Reinhard Wilhelm Saarland University Saarbrücken Structure of the Lecture 1. Introduction 2. Static timing analysis 1. the problem 2. our
Precise and Efficient FIFO-Replacement Analysis Based on Static Phase Detection
 Precise and Efficient FIFO-Replacement Analysis Based on Static Phase Detection Daniel Grund 1 Jan Reineke 2 1 Saarland University, Saarbrücken, Germany 2 University of California, Berkeley, USA Euromicro
Precise and Efficient FIFO-Replacement Analysis Based on Static Phase Detection Daniel Grund 1 Jan Reineke 2 1 Saarland University, Saarbrücken, Germany 2 University of California, Berkeley, USA Euromicro
Static WCET Analysis: Methods and Tools
 Static WCET Analysis: Methods and Tools Timo Lilja April 28, 2011 Timo Lilja () Static WCET Analysis: Methods and Tools April 28, 2011 1 / 23 1 Methods 2 Tools 3 Summary 4 References Timo Lilja () Static
Static WCET Analysis: Methods and Tools Timo Lilja April 28, 2011 Timo Lilja () Static WCET Analysis: Methods and Tools April 28, 2011 1 / 23 1 Methods 2 Tools 3 Summary 4 References Timo Lilja () Static
ELCT 912: Advanced Embedded Systems
 ELCT 912: Advanced Embedded Systems Lecture 2-3: Embedded System Hardware Dr. Mohamed Abd El Ghany, Department of Electronics and Electrical Engineering Embedded System Hardware Used for processing of
ELCT 912: Advanced Embedded Systems Lecture 2-3: Embedded System Hardware Dr. Mohamed Abd El Ghany, Department of Electronics and Electrical Engineering Embedded System Hardware Used for processing of
Evaluating Static Worst-Case Execution-Time Analysis for a Commercial Real-Time Operating System
 Evaluating Static Worst-Case Execution-Time Analysis for a Commercial Real-Time Operating System Daniel Sandell Master s thesis D-level, 20 credits Dept. of Computer Science Mälardalen University Supervisor:
Evaluating Static Worst-Case Execution-Time Analysis for a Commercial Real-Time Operating System Daniel Sandell Master s thesis D-level, 20 credits Dept. of Computer Science Mälardalen University Supervisor:
Towards Automation of Timing-Model Derivation. AbsInt Angewandte Informatik GmbH
 Towards Automation of Timing-Model Derivation Markus Pister Marc Schlickling AbsInt Angewandte Informatik GmbH Motivation Growing support of human life by complex embedded systems Safety-critical systems
Towards Automation of Timing-Model Derivation Markus Pister Marc Schlickling AbsInt Angewandte Informatik GmbH Motivation Growing support of human life by complex embedded systems Safety-critical systems
Approximation of the Worst-Case Execution Time Using Structural Analysis. Matteo Corti and Thomas Gross Zürich
 Approximation of the Worst-Case Execution Time Using Structural Analysis Matteo Corti and Thomas Gross Zürich Goal Worst-case execution time estimation of softreal time Java applications. We focus on semantic
Approximation of the Worst-Case Execution Time Using Structural Analysis Matteo Corti and Thomas Gross Zürich Goal Worst-case execution time estimation of softreal time Java applications. We focus on semantic
Evaluation and Validation
 12 Evaluation and Validation Peter Marwedel TU Dortmund, Informatik 12 Germany Graphics: Alexandra Nolte, Gesine Marwedel, 2003 2010 年 12 月 05 日 These slides use Microsoft clip arts. Microsoft copyright
12 Evaluation and Validation Peter Marwedel TU Dortmund, Informatik 12 Germany Graphics: Alexandra Nolte, Gesine Marwedel, 2003 2010 年 12 月 05 日 These slides use Microsoft clip arts. Microsoft copyright
ARM Processors for Embedded Applications
 ARM Processors for Embedded Applications Roadmap for ARM Processors ARM Architecture Basics ARM Families AMBA Architecture 1 Current ARM Core Families ARM7: Hard cores and Soft cores Cache with MPU or
ARM Processors for Embedded Applications Roadmap for ARM Processors ARM Architecture Basics ARM Families AMBA Architecture 1 Current ARM Core Families ARM7: Hard cores and Soft cores Cache with MPU or
General Purpose Signal Processors
 General Purpose Signal Processors First announced in 1978 (AMD) for peripheral computation such as in printers, matured in early 80 s (TMS320 series). General purpose vs. dedicated architectures: Pros:
General Purpose Signal Processors First announced in 1978 (AMD) for peripheral computation such as in printers, matured in early 80 s (TMS320 series). General purpose vs. dedicated architectures: Pros:
Computer and Hardware Architecture I. Benny Thörnberg Associate Professor in Electronics
 Computer and Hardware Architecture I Benny Thörnberg Associate Professor in Electronics Hardware architecture Computer architecture The functionality of a modern computer is so complex that no human can
Computer and Hardware Architecture I Benny Thörnberg Associate Professor in Electronics Hardware architecture Computer architecture The functionality of a modern computer is so complex that no human can
Memory Hierarchies 2009 DAT105
 Memory Hierarchies Cache performance issues (5.1) Virtual memory (C.4) Cache performance improvement techniques (5.2) Hit-time improvement techniques Miss-rate improvement techniques Miss-penalty improvement
Memory Hierarchies Cache performance issues (5.1) Virtual memory (C.4) Cache performance improvement techniques (5.2) Hit-time improvement techniques Miss-rate improvement techniques Miss-penalty improvement
Timing Analysis - timing guarantees for hard real-time systems- Reinhard Wilhelm Saarland University Saarbrücken
 Timing Analysis - timing guarantees for hard real-time systems- Reinhard Wilhelm Saarland University Saarbrücken Structure of the Lecture 1. 2. 1. 2. 3. 4. 5. 6. Introduction Static timing analysis the
Timing Analysis - timing guarantees for hard real-time systems- Reinhard Wilhelm Saarland University Saarbrücken Structure of the Lecture 1. 2. 1. 2. 3. 4. 5. 6. Introduction Static timing analysis the
HPC VT Machine-dependent Optimization
 HPC VT 2013 Machine-dependent Optimization Last time Choose good data structures Reduce number of operations Use cheap operations strength reduction Avoid too many small function calls inlining Use compiler
HPC VT 2013 Machine-dependent Optimization Last time Choose good data structures Reduce number of operations Use cheap operations strength reduction Avoid too many small function calls inlining Use compiler
DC57 COMPUTER ORGANIZATION JUNE 2013
 Q2 (a) How do various factors like Hardware design, Instruction set, Compiler related to the performance of a computer? The most important measure of a computer is how quickly it can execute programs.
Q2 (a) How do various factors like Hardware design, Instruction set, Compiler related to the performance of a computer? The most important measure of a computer is how quickly it can execute programs.
Pipelining, Branch Prediction, Trends
 Pipelining, Branch Prediction, Trends 10.1-10.4 Topics 10.1 Quantitative Analyses of Program Execution 10.2 From CISC to RISC 10.3 Pipelining the Datapath Branch Prediction, Delay Slots 10.4 Overlapping
Pipelining, Branch Prediction, Trends 10.1-10.4 Topics 10.1 Quantitative Analyses of Program Execution 10.2 From CISC to RISC 10.3 Pipelining the Datapath Branch Prediction, Delay Slots 10.4 Overlapping
CS 152 Computer Architecture and Engineering
 CS 152 Computer Architecture and Engineering Lecture 17 Advanced Processors I 2005-10-27 John Lazzaro (www.cs.berkeley.edu/~lazzaro) TAs: David Marquardt and Udam Saini www-inst.eecs.berkeley.edu/~cs152/
CS 152 Computer Architecture and Engineering Lecture 17 Advanced Processors I 2005-10-27 John Lazzaro (www.cs.berkeley.edu/~lazzaro) TAs: David Marquardt and Udam Saini www-inst.eecs.berkeley.edu/~cs152/
CS 152 Computer Architecture and Engineering
 CS 152 Computer Architecture and Engineering Lecture 20 Advanced Processors I 2005-4-5 John Lazzaro (www.cs.berkeley.edu/~lazzaro) TAs: Ted Hong and David Marquardt www-inst.eecs.berkeley.edu/~cs152/ Last
CS 152 Computer Architecture and Engineering Lecture 20 Advanced Processors I 2005-4-5 John Lazzaro (www.cs.berkeley.edu/~lazzaro) TAs: Ted Hong and David Marquardt www-inst.eecs.berkeley.edu/~cs152/ Last
Evaluation and Validation
 Springer, 2010 Evaluation and Validation Peter Marwedel TU Dortmund, Informatik 12 Germany 2013 年 12 月 02 日 These slides use Microsoft clip arts. Microsoft copyright restrictions apply. Application Knowledge
Springer, 2010 Evaluation and Validation Peter Marwedel TU Dortmund, Informatik 12 Germany 2013 年 12 月 02 日 These slides use Microsoft clip arts. Microsoft copyright restrictions apply. Application Knowledge
Embedded System Design
 Modeling, Synthesis, Verification Daniel D. Gajski, Samar Abdi, Andreas Gerstlauer, Gunar Schirner 9/29/2011 Outline System design trends Model-based synthesis Transaction level model generation Application
Modeling, Synthesis, Verification Daniel D. Gajski, Samar Abdi, Andreas Gerstlauer, Gunar Schirner 9/29/2011 Outline System design trends Model-based synthesis Transaction level model generation Application
Serial. Parallel. CIT 668: System Architecture 2/14/2011. Topics. Serial and Parallel Computation. Parallel Computing
 CIT 668: System Architecture Parallel Computing Topics 1. What is Parallel Computing? 2. Why use Parallel Computing? 3. Types of Parallelism 4. Amdahl s Law 5. Flynn s Taxonomy of Parallel Computers 6.
CIT 668: System Architecture Parallel Computing Topics 1. What is Parallel Computing? 2. Why use Parallel Computing? 3. Types of Parallelism 4. Amdahl s Law 5. Flynn s Taxonomy of Parallel Computers 6.
Recall from Pipelining Review. Lecture 16: Instruction Level Parallelism and Dynamic Execution #1: Ideas to Reduce Stalls
 CS252 Graduate Computer Architecture Recall from Pipelining Review Lecture 16: Instruction Level Parallelism and Dynamic Execution #1: March 16, 2001 Prof. David A. Patterson Computer Science 252 Spring
CS252 Graduate Computer Architecture Recall from Pipelining Review Lecture 16: Instruction Level Parallelism and Dynamic Execution #1: March 16, 2001 Prof. David A. Patterson Computer Science 252 Spring
In examining performance Interested in several things Exact times if computable Bounded times if exact not computable Can be measured
 System Performance Analysis Introduction Performance Means many things to many people Important in any design Critical in real time systems 1 ns can mean the difference between system Doing job expected
System Performance Analysis Introduction Performance Means many things to many people Important in any design Critical in real time systems 1 ns can mean the difference between system Doing job expected
Timing Analysis of Parallel Software Using Abstract Execution
 Timing Analysis of Parallel Software Using Abstract Execution Björn Lisper School of Innovation, Design, and Engineering Mälardalen University bjorn.lisper@mdh.se 2014-09-10 EACO Workshop 2014 Motivation
Timing Analysis of Parallel Software Using Abstract Execution Björn Lisper School of Innovation, Design, and Engineering Mälardalen University bjorn.lisper@mdh.se 2014-09-10 EACO Workshop 2014 Motivation
DEPARTMENT OF ELECTRONICS & COMMUNICATION ENGINEERING QUESTION BANK
 DEPARTMENT OF ELECTRONICS & COMMUNICATION ENGINEERING QUESTION BANK SUBJECT : CS6303 / COMPUTER ARCHITECTURE SEM / YEAR : VI / III year B.E. Unit I OVERVIEW AND INSTRUCTIONS Part A Q.No Questions BT Level
DEPARTMENT OF ELECTRONICS & COMMUNICATION ENGINEERING QUESTION BANK SUBJECT : CS6303 / COMPUTER ARCHITECTURE SEM / YEAR : VI / III year B.E. Unit I OVERVIEW AND INSTRUCTIONS Part A Q.No Questions BT Level
Multi-cycle Instructions in the Pipeline (Floating Point)
 Lecture 6 Multi-cycle Instructions in the Pipeline (Floating Point) Introduction to instruction level parallelism Recap: Support of multi-cycle instructions in a pipeline (App A.5) Recap: Superpipelining
Lecture 6 Multi-cycle Instructions in the Pipeline (Floating Point) Introduction to instruction level parallelism Recap: Support of multi-cycle instructions in a pipeline (App A.5) Recap: Superpipelining
Distributed Operation Layer Integrated SW Design Flow for Mapping Streaming Applications to MPSoC
 Distributed Operation Layer Integrated SW Design Flow for Mapping Streaming Applications to MPSoC Iuliana Bacivarov, Wolfgang Haid, Kai Huang, and Lothar Thiele ETH Zürich MPSoCs are Hard to program (
Distributed Operation Layer Integrated SW Design Flow for Mapping Streaming Applications to MPSoC Iuliana Bacivarov, Wolfgang Haid, Kai Huang, and Lothar Thiele ETH Zürich MPSoCs are Hard to program (
Lecture 8 Dynamic Branch Prediction, Superscalar and VLIW. Computer Architectures S
 Lecture 8 Dynamic Branch Prediction, Superscalar and VLIW Computer Architectures 521480S Dynamic Branch Prediction Performance = ƒ(accuracy, cost of misprediction) Branch History Table (BHT) is simplest
Lecture 8 Dynamic Branch Prediction, Superscalar and VLIW Computer Architectures 521480S Dynamic Branch Prediction Performance = ƒ(accuracy, cost of misprediction) Branch History Table (BHT) is simplest
Data-Flow Based Detection of Loop Bounds
 Data-Flow Based Detection of Loop Bounds Christoph Cullmann and Florian Martin AbsInt Angewandte Informatik GmbH Science Park 1, D-66123 Saarbrücken, Germany cullmann,florian@absint.com, http://www.absint.com
Data-Flow Based Detection of Loop Bounds Christoph Cullmann and Florian Martin AbsInt Angewandte Informatik GmbH Science Park 1, D-66123 Saarbrücken, Germany cullmann,florian@absint.com, http://www.absint.com
CS 5803 Introduction to High Performance Computer Architecture: RISC vs. CISC. A.R. Hurson 323 Computer Science Building, Missouri S&T
 CS 5803 Introduction to High Performance Computer Architecture: RISC vs. CISC A.R. Hurson 323 Computer Science Building, Missouri S&T hurson@mst.edu 1 Outline How to improve CPU time? Complex Instruction
CS 5803 Introduction to High Performance Computer Architecture: RISC vs. CISC A.R. Hurson 323 Computer Science Building, Missouri S&T hurson@mst.edu 1 Outline How to improve CPU time? Complex Instruction
Designing Predictable Real-Time and Embedded Systems
 Designing Predictable Real-Time and Embedded Systems Juniorprofessor Dr. Jian-Jia Chen Karlsruhe Institute of Technology (KIT), Germany 0 KIT Feb. University 27-29, 2012 of at thetu-berlin, State of Baden-Wuerttemberg
Designing Predictable Real-Time and Embedded Systems Juniorprofessor Dr. Jian-Jia Chen Karlsruhe Institute of Technology (KIT), Germany 0 KIT Feb. University 27-29, 2012 of at thetu-berlin, State of Baden-Wuerttemberg
Instruction Pipelining Review
 Instruction Pipelining Review Instruction pipelining is CPU implementation technique where multiple operations on a number of instructions are overlapped. An instruction execution pipeline involves a number
Instruction Pipelining Review Instruction pipelining is CPU implementation technique where multiple operations on a number of instructions are overlapped. An instruction execution pipeline involves a number
Computer System Overview OPERATING SYSTEM TOP-LEVEL COMPONENTS. Simplified view: Operating Systems. Slide 1. Slide /S2. Slide 2.
 BASIC ELEMENTS Simplified view: Processor Slide 1 Computer System Overview Operating Systems Slide 3 Main Memory referred to as real memory or primary memory volatile modules 2004/S2 secondary memory devices
BASIC ELEMENTS Simplified view: Processor Slide 1 Computer System Overview Operating Systems Slide 3 Main Memory referred to as real memory or primary memory volatile modules 2004/S2 secondary memory devices
Department of Computer Science, Institute for System Architecture, Operating Systems Group. Real-Time Systems '08 / '09. Hardware.
 Department of Computer Science, Institute for System Architecture, Operating Systems Group Real-Time Systems '08 / '09 Hardware Marcus Völp Outlook Hardware is Source of Unpredictability Caches Pipeline
Department of Computer Science, Institute for System Architecture, Operating Systems Group Real-Time Systems '08 / '09 Hardware Marcus Völp Outlook Hardware is Source of Unpredictability Caches Pipeline
Last Time. Response time analysis Blocking terms Priority inversion. Other extensions. And solutions
 Last Time Response time analysis Blocking terms Priority inversion And solutions Release jitter Other extensions Today Timing analysis Answers a question we commonly ask: At most long can this code take
Last Time Response time analysis Blocking terms Priority inversion And solutions Release jitter Other extensions Today Timing analysis Answers a question we commonly ask: At most long can this code take
NOW Handout Page 1. Review from Last Time #1. CSE 820 Graduate Computer Architecture. Lec 8 Instruction Level Parallelism. Outline
 CSE 820 Graduate Computer Architecture Lec 8 Instruction Level Parallelism Based on slides by David Patterson Review Last Time #1 Leverage Implicit Parallelism for Performance: Instruction Level Parallelism
CSE 820 Graduate Computer Architecture Lec 8 Instruction Level Parallelism Based on slides by David Patterson Review Last Time #1 Leverage Implicit Parallelism for Performance: Instruction Level Parallelism
Assembly Language. Lecture 2 - x86 Processor Architecture. Ahmed Sallam
 Assembly Language Lecture 2 - x86 Processor Architecture Ahmed Sallam Introduction to the course Outcomes of Lecture 1 Always check the course website Don t forget the deadline rule!! Motivations for studying
Assembly Language Lecture 2 - x86 Processor Architecture Ahmed Sallam Introduction to the course Outcomes of Lecture 1 Always check the course website Don t forget the deadline rule!! Motivations for studying
Computer System Overview
 Computer System Overview Operating Systems 2005/S2 1 What are the objectives of an Operating System? 2 What are the objectives of an Operating System? convenience & abstraction the OS should facilitate
Computer System Overview Operating Systems 2005/S2 1 What are the objectives of an Operating System? 2 What are the objectives of an Operating System? convenience & abstraction the OS should facilitate
Fast and Accurate Source-Level Simulation Considering Target-Specific Compiler Optimizations
 FZI Forschungszentrum Informatik at the University of Karlsruhe Fast and Accurate Source-Level Simulation Considering Target-Specific Compiler Optimizations Oliver Bringmann 1 RESEARCH ON YOUR BEHALF Outline
FZI Forschungszentrum Informatik at the University of Karlsruhe Fast and Accurate Source-Level Simulation Considering Target-Specific Compiler Optimizations Oliver Bringmann 1 RESEARCH ON YOUR BEHALF Outline
WCET-Aware C Compiler: WCC
 12 WCET-Aware C Compiler: WCC Jian-Jia Chen (slides are based on Prof. Heiko Falk) TU Dortmund, Informatik 12 2015 年 05 月 05 日 These slides use Microsoft clip arts. Microsoft copyright restrictions apply.
12 WCET-Aware C Compiler: WCC Jian-Jia Chen (slides are based on Prof. Heiko Falk) TU Dortmund, Informatik 12 2015 年 05 月 05 日 These slides use Microsoft clip arts. Microsoft copyright restrictions apply.
ECE332, Week 2, Lecture 3. September 5, 2007
 ECE332, Week 2, Lecture 3 September 5, 2007 1 Topics Introduction to embedded system Design metrics Definitions of general-purpose, single-purpose, and application-specific processors Introduction to Nios
ECE332, Week 2, Lecture 3 September 5, 2007 1 Topics Introduction to embedded system Design metrics Definitions of general-purpose, single-purpose, and application-specific processors Introduction to Nios
ECE332, Week 2, Lecture 3
 ECE332, Week 2, Lecture 3 September 5, 2007 1 Topics Introduction to embedded system Design metrics Definitions of general-purpose, single-purpose, and application-specific processors Introduction to Nios
ECE332, Week 2, Lecture 3 September 5, 2007 1 Topics Introduction to embedded system Design metrics Definitions of general-purpose, single-purpose, and application-specific processors Introduction to Nios
CSE 820 Graduate Computer Architecture. week 6 Instruction Level Parallelism. Review from Last Time #1
 CSE 820 Graduate Computer Architecture week 6 Instruction Level Parallelism Based on slides by David Patterson Review from Last Time #1 Leverage Implicit Parallelism for Performance: Instruction Level
CSE 820 Graduate Computer Architecture week 6 Instruction Level Parallelism Based on slides by David Patterson Review from Last Time #1 Leverage Implicit Parallelism for Performance: Instruction Level
Branch statistics. 66% forward (i.e., slightly over 50% of total branches). Most often Not Taken 33% backward. Almost all Taken
 Branch statistics Branches occur every 4-7 instructions on average in integer programs, commercial and desktop applications; somewhat less frequently in scientific ones Unconditional branches : 20% (of
Branch statistics Branches occur every 4-7 instructions on average in integer programs, commercial and desktop applications; somewhat less frequently in scientific ones Unconditional branches : 20% (of
Tutorial 11. Final Exam Review
 Tutorial 11 Final Exam Review Introduction Instruction Set Architecture: contract between programmer and designers (e.g.: IA-32, IA-64, X86-64) Computer organization: describe the functional units, cache
Tutorial 11 Final Exam Review Introduction Instruction Set Architecture: contract between programmer and designers (e.g.: IA-32, IA-64, X86-64) Computer organization: describe the functional units, cache
Embedded Systems. 7. System Components
 Embedded Systems 7. System Components Lothar Thiele 7-1 Contents of Course 1. Embedded Systems Introduction 2. Software Introduction 7. System Components 10. Models 3. Real-Time Models 4. Periodic/Aperiodic
Embedded Systems 7. System Components Lothar Thiele 7-1 Contents of Course 1. Embedded Systems Introduction 2. Software Introduction 7. System Components 10. Models 3. Real-Time Models 4. Periodic/Aperiodic
Embedded Systems Lecture 11: Worst-Case Execution Time. Björn Franke University of Edinburgh
 Embedded Systems Lecture 11: Worst-Case Execution Time Björn Franke University of Edinburgh Overview Motivation Worst-Case Execution Time Analysis Types of Execution Times Measuring vs. Analysing Flow
Embedded Systems Lecture 11: Worst-Case Execution Time Björn Franke University of Edinburgh Overview Motivation Worst-Case Execution Time Analysis Types of Execution Times Measuring vs. Analysing Flow
ECE 471 Embedded Systems Lecture 2
 ECE 471 Embedded Systems Lecture 2 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 7 September 2018 Announcements Reminder: The class notes are posted to the website. HW#1 will
ECE 471 Embedded Systems Lecture 2 Vince Weaver http://web.eece.maine.edu/~vweaver vincent.weaver@maine.edu 7 September 2018 Announcements Reminder: The class notes are posted to the website. HW#1 will
RISC & Superscalar. COMP 212 Computer Organization & Architecture. COMP 212 Fall Lecture 12. Instruction Pipeline no hazard.
 COMP 212 Computer Organization & Architecture Pipeline Re-Cap Pipeline is ILP -Instruction Level Parallelism COMP 212 Fall 2008 Lecture 12 RISC & Superscalar Divide instruction cycles into stages, overlapped
COMP 212 Computer Organization & Architecture Pipeline Re-Cap Pipeline is ILP -Instruction Level Parallelism COMP 212 Fall 2008 Lecture 12 RISC & Superscalar Divide instruction cycles into stages, overlapped
Next Generation Multi-Purpose Microprocessor
 Next Generation Multi-Purpose Microprocessor Presentation at MPSA, 4 th of November 2009 www.aeroflex.com/gaisler OUTLINE NGMP key requirements Development schedule Architectural Overview LEON4FT features
Next Generation Multi-Purpose Microprocessor Presentation at MPSA, 4 th of November 2009 www.aeroflex.com/gaisler OUTLINE NGMP key requirements Development schedule Architectural Overview LEON4FT features
LECTURE 10. Pipelining: Advanced ILP
 LECTURE 10 Pipelining: Advanced ILP EXCEPTIONS An exception, or interrupt, is an event other than regular transfers of control (branches, jumps, calls, returns) that changes the normal flow of instruction
LECTURE 10 Pipelining: Advanced ILP EXCEPTIONS An exception, or interrupt, is an event other than regular transfers of control (branches, jumps, calls, returns) that changes the normal flow of instruction
Page 1. Recall from Pipelining Review. Lecture 16: Instruction Level Parallelism and Dynamic Execution #1: Ideas to Reduce Stalls
 CS252 Graduate Computer Architecture Recall from Pipelining Review Lecture 16: Instruction Level Parallelism and Dynamic Execution #1: March 16, 2001 Prof. David A. Patterson Computer Science 252 Spring
CS252 Graduate Computer Architecture Recall from Pipelining Review Lecture 16: Instruction Level Parallelism and Dynamic Execution #1: March 16, 2001 Prof. David A. Patterson Computer Science 252 Spring
Computer Hardware Requirements for ERTSs: Microprocessors & Microcontrollers
 Lecture (4) Computer Hardware Requirements for ERTSs: Microprocessors & Microcontrollers Prof. Kasim M. Al-Aubidy Philadelphia University-Jordan DERTS-MSc, 2015 Prof. Kasim Al-Aubidy 1 Lecture Outline:
Lecture (4) Computer Hardware Requirements for ERTSs: Microprocessors & Microcontrollers Prof. Kasim M. Al-Aubidy Philadelphia University-Jordan DERTS-MSc, 2015 Prof. Kasim Al-Aubidy 1 Lecture Outline:
Embedded System Design Modeling, Synthesis, Verification
 Modeling, Synthesis, Verification Daniel D. Gajski, Samar Abdi, Andreas Gerstlauer, Gunar Schirner Chapter 4: System Synthesis Outline System design trends Model-based synthesis Transaction level model
Modeling, Synthesis, Verification Daniel D. Gajski, Samar Abdi, Andreas Gerstlauer, Gunar Schirner Chapter 4: System Synthesis Outline System design trends Model-based synthesis Transaction level model
Copyright 2016 Xilinx
 Zynq Architecture Zynq Vivado 2015.4 Version This material exempt per Department of Commerce license exception TSU Objectives After completing this module, you will be able to: Identify the basic building
Zynq Architecture Zynq Vivado 2015.4 Version This material exempt per Department of Commerce license exception TSU Objectives After completing this module, you will be able to: Identify the basic building
Assembly Language. Lecture 2 x86 Processor Architecture
 Assembly Language Lecture 2 x86 Processor Architecture Ahmed Sallam Slides based on original lecture slides by Dr. Mahmoud Elgayyar Introduction to the course Outcomes of Lecture 1 Always check the course
Assembly Language Lecture 2 x86 Processor Architecture Ahmed Sallam Slides based on original lecture slides by Dr. Mahmoud Elgayyar Introduction to the course Outcomes of Lecture 1 Always check the course
Lecture 2: Memory Systems
 Lecture 2: Memory Systems Basic components Memory hierarchy Cache memory Virtual Memory Zebo Peng, IDA, LiTH Many Different Technologies Zebo Peng, IDA, LiTH 2 Internal and External Memories CPU Date transfer
Lecture 2: Memory Systems Basic components Memory hierarchy Cache memory Virtual Memory Zebo Peng, IDA, LiTH Many Different Technologies Zebo Peng, IDA, LiTH 2 Internal and External Memories CPU Date transfer
Processor Architecture V! Wrap-Up!
 Processor Architecture V! Wrap-Up! Lecture 7, April 28 th 2011 Alexandre David Slides by Randal E. Bryant! Carnegie Mellon University! Overview! Wrap-Up of PIPE Design! n Performance analysis! n Fetch
Processor Architecture V! Wrap-Up! Lecture 7, April 28 th 2011 Alexandre David Slides by Randal E. Bryant! Carnegie Mellon University! Overview! Wrap-Up of PIPE Design! n Performance analysis! n Fetch
Performance Optimization for an ARM Cortex-A53 System Using Software Workloads and Cycle Accurate Models. Jason Andrews
 Performance Optimization for an ARM Cortex-A53 System Using Software Workloads and Cycle Accurate Models Jason Andrews Agenda System Performance Analysis IP Configuration System Creation Methodology: Create,
Performance Optimization for an ARM Cortex-A53 System Using Software Workloads and Cycle Accurate Models Jason Andrews Agenda System Performance Analysis IP Configuration System Creation Methodology: Create,
Instruction Level Parallelism. ILP, Loop level Parallelism Dependences, Hazards Speculation, Branch prediction
 Instruction Level Parallelism ILP, Loop level Parallelism Dependences, Hazards Speculation, Branch prediction Basic Block A straight line code sequence with no branches in except to the entry and no branches
Instruction Level Parallelism ILP, Loop level Parallelism Dependences, Hazards Speculation, Branch prediction Basic Block A straight line code sequence with no branches in except to the entry and no branches
Worst-Case Execution Time (WCET)
 Introduction to Cache Analysis for Real-Time Systems [C. Ferdinand and R. Wilhelm, Efficient and Precise Cache Behavior Prediction for Real-Time Systems, Real-Time Systems, 17, 131-181, (1999)] Schedulability
Introduction to Cache Analysis for Real-Time Systems [C. Ferdinand and R. Wilhelm, Efficient and Precise Cache Behavior Prediction for Real-Time Systems, Real-Time Systems, 17, 131-181, (1999)] Schedulability
Page # Let the Compiler Do it Pros and Cons Pros. Exploiting ILP through Software Approaches. Cons. Perhaps a mixture of the two?
 Exploiting ILP through Software Approaches Venkatesh Akella EEC 270 Winter 2005 Based on Slides from Prof. Al. Davis @ cs.utah.edu Let the Compiler Do it Pros and Cons Pros No window size limitation, the
Exploiting ILP through Software Approaches Venkatesh Akella EEC 270 Winter 2005 Based on Slides from Prof. Al. Davis @ cs.utah.edu Let the Compiler Do it Pros and Cons Pros No window size limitation, the
Worst Case Execution Time Analysis for Synthesized Hardware
 Worst Case Execution Time Analysis for Synthesized Hardware Jun-hee Yoo ihavnoid@poppy.snu.ac.kr Seoul National University, Seoul, Republic of Korea Xingguang Feng fengxg@poppy.snu.ac.kr Seoul National
Worst Case Execution Time Analysis for Synthesized Hardware Jun-hee Yoo ihavnoid@poppy.snu.ac.kr Seoul National University, Seoul, Republic of Korea Xingguang Feng fengxg@poppy.snu.ac.kr Seoul National
Introduction to Embedded Systems
 Introduction to Embedded Systems Edward A. Lee & Sanjit A. Seshia UC Berkeley EECS 124 Spring 2008 Copyright 2008, Edward A. Lee & Sanjit A. Seshia, All rights reserved Lecture 19: Execution Time Analysis
Introduction to Embedded Systems Edward A. Lee & Sanjit A. Seshia UC Berkeley EECS 124 Spring 2008 Copyright 2008, Edward A. Lee & Sanjit A. Seshia, All rights reserved Lecture 19: Execution Time Analysis
Compiler Design. Fall Control-Flow Analysis. Prof. Pedro C. Diniz
 Compiler Design Fall 2015 Control-Flow Analysis Sample Exercises and Solutions Prof. Pedro C. Diniz USC / Information Sciences Institute 4676 Admiralty Way, Suite 1001 Marina del Rey, California 90292
Compiler Design Fall 2015 Control-Flow Analysis Sample Exercises and Solutions Prof. Pedro C. Diniz USC / Information Sciences Institute 4676 Admiralty Way, Suite 1001 Marina del Rey, California 90292
CPE 631 Lecture 10: Instruction Level Parallelism and Its Dynamic Exploitation
 Lecture 10: Instruction Level Parallelism and Its Dynamic Exploitation Aleksandar Milenković, milenka@ece.uah.edu Electrical and Computer Engineering University of Alabama in Huntsville Outline Tomasulo
Lecture 10: Instruction Level Parallelism and Its Dynamic Exploitation Aleksandar Milenković, milenka@ece.uah.edu Electrical and Computer Engineering University of Alabama in Huntsville Outline Tomasulo
Test and Verification Solutions. ARM Based SOC Design and Verification
 Test and Verification Solutions ARM Based SOC Design and Verification 7 July 2008 1 7 July 2008 14 March 2 Agenda System Verification Challenges ARM SoC DV Methodology ARM SoC Test bench Construction Conclusion
Test and Verification Solutions ARM Based SOC Design and Verification 7 July 2008 1 7 July 2008 14 March 2 Agenda System Verification Challenges ARM SoC DV Methodology ARM SoC Test bench Construction Conclusion
Memory management units
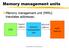 Memory management units Memory management unit (MMU) translates addresses: CPU logical address memory management unit physical address main memory Computers as Components 1 Access time comparison Media
Memory management units Memory management unit (MMU) translates addresses: CPU logical address memory management unit physical address main memory Computers as Components 1 Access time comparison Media
Exploiting ILP with SW Approaches. Aleksandar Milenković, Electrical and Computer Engineering University of Alabama in Huntsville
 Lecture : Exploiting ILP with SW Approaches Aleksandar Milenković, milenka@ece.uah.edu Electrical and Computer Engineering University of Alabama in Huntsville Outline Basic Pipeline Scheduling and Loop
Lecture : Exploiting ILP with SW Approaches Aleksandar Milenković, milenka@ece.uah.edu Electrical and Computer Engineering University of Alabama in Huntsville Outline Basic Pipeline Scheduling and Loop
Program verification. Generalities about software Verification Model Checking. September 20, 2016
 Program verification Generalities about software Verification Model Checking Laure Gonnord David Monniaux September 20, 2016 1 / 43 The teaching staff Laure Gonnord, associate professor, LIP laboratory,
Program verification Generalities about software Verification Model Checking Laure Gonnord David Monniaux September 20, 2016 1 / 43 The teaching staff Laure Gonnord, associate professor, LIP laboratory,
Static Memory and Timing Analysis of Embedded Systems Code
 Static Memory and Timing Analysis of Embedded Systems Code Christian Ferdinand Reinhold Heckmann Bärbel Franzen AbsInt Angewandte Informatik GmbH Science Park 1, D-66123 Saarbrücken, Germany Phone: +49-681-38360-0
Static Memory and Timing Analysis of Embedded Systems Code Christian Ferdinand Reinhold Heckmann Bärbel Franzen AbsInt Angewandte Informatik GmbH Science Park 1, D-66123 Saarbrücken, Germany Phone: +49-681-38360-0
Design and Analysis of Real-Time Systems Predictability and Predictable Microarchitectures
 Design and Analysis of Real-Time Systems Predictability and Predictable Microarcectures Jan Reineke Advanced Lecture, Summer 2013 Notion of Predictability Oxford Dictionary: predictable = adjective, able
Design and Analysis of Real-Time Systems Predictability and Predictable Microarcectures Jan Reineke Advanced Lecture, Summer 2013 Notion of Predictability Oxford Dictionary: predictable = adjective, able
Page 1 ILP. ILP Basics & Branch Prediction. Smarter Schedule. Basic Block Problems. Parallelism independent enough
 ILP ILP Basics & Branch Prediction Today s topics: Compiler hazard mitigation loop unrolling SW pipelining Branch Prediction Parallelism independent enough e.g. avoid s» control correctly predict decision
ILP ILP Basics & Branch Prediction Today s topics: Compiler hazard mitigation loop unrolling SW pipelining Branch Prediction Parallelism independent enough e.g. avoid s» control correctly predict decision
Chapter 2 Lecture 1 Computer Systems Organization
 Chapter 2 Lecture 1 Computer Systems Organization This chapter provides an introduction to the components Processors: Primary Memory: Secondary Memory: Input/Output: Busses The Central Processing Unit
Chapter 2 Lecture 1 Computer Systems Organization This chapter provides an introduction to the components Processors: Primary Memory: Secondary Memory: Input/Output: Busses The Central Processing Unit
What is Pipelining? RISC remainder (our assumptions)
 What is Pipelining? Is a key implementation techniques used to make fast CPUs Is an implementation techniques whereby multiple instructions are overlapped in execution It takes advantage of parallelism
What is Pipelining? Is a key implementation techniques used to make fast CPUs Is an implementation techniques whereby multiple instructions are overlapped in execution It takes advantage of parallelism
Worst-Case Execution Time (WCET)
 Introduction to Cache Analysis for Real-Time Systems [C. Ferdinand and R. Wilhelm, Efficient and Precise Cache Behavior Prediction for Real-Time Systems, Real-Time Systems, 17, 131-181, (1999)] Schedulability
Introduction to Cache Analysis for Real-Time Systems [C. Ferdinand and R. Wilhelm, Efficient and Precise Cache Behavior Prediction for Real-Time Systems, Real-Time Systems, 17, 131-181, (1999)] Schedulability
COMPUTER ORGANIZATION AND DESI
 COMPUTER ORGANIZATION AND DESIGN 5 Edition th The Hardware/Software Interface Chapter 4 The Processor 4.1 Introduction Introduction CPU performance factors Instruction count Determined by ISA and compiler
COMPUTER ORGANIZATION AND DESIGN 5 Edition th The Hardware/Software Interface Chapter 4 The Processor 4.1 Introduction Introduction CPU performance factors Instruction count Determined by ISA and compiler
ASSEMBLY LANGUAGE MACHINE ORGANIZATION
 ASSEMBLY LANGUAGE MACHINE ORGANIZATION CHAPTER 3 1 Sub-topics The topic will cover: Microprocessor architecture CPU processing methods Pipelining Superscalar RISC Multiprocessing Instruction Cycle Instruction
ASSEMBLY LANGUAGE MACHINE ORGANIZATION CHAPTER 3 1 Sub-topics The topic will cover: Microprocessor architecture CPU processing methods Pipelining Superscalar RISC Multiprocessing Instruction Cycle Instruction
Architectures & instruction sets R_B_T_C_. von Neumann architecture. Computer architecture taxonomy. Assembly language.
 Architectures & instruction sets Computer architecture taxonomy. Assembly language. R_B_T_C_ 1. E E C E 2. I E U W 3. I S O O 4. E P O I von Neumann architecture Memory holds data and instructions. Central
Architectures & instruction sets Computer architecture taxonomy. Assembly language. R_B_T_C_ 1. E E C E 2. I E U W 3. I S O O 4. E P O I von Neumann architecture Memory holds data and instructions. Central
COSC4201. Chapter 5. Memory Hierarchy Design. Prof. Mokhtar Aboelaze York University
 COSC4201 Chapter 5 Memory Hierarchy Design Prof. Mokhtar Aboelaze York University 1 Memory Hierarchy The gap between CPU performance and main memory has been widening with higher performance CPUs creating
COSC4201 Chapter 5 Memory Hierarchy Design Prof. Mokhtar Aboelaze York University 1 Memory Hierarchy The gap between CPU performance and main memory has been widening with higher performance CPUs creating
ARM CORTEX-R52. Target Audience: Engineers and technicians who develop SoCs and systems based on the ARM Cortex-R52 architecture.
 ARM CORTEX-R52 Course Family: ARMv8-R Cortex-R CPU Target Audience: Engineers and technicians who develop SoCs and systems based on the ARM Cortex-R52 architecture. Duration: 4 days Prerequisites and related
ARM CORTEX-R52 Course Family: ARMv8-R Cortex-R CPU Target Audience: Engineers and technicians who develop SoCs and systems based on the ARM Cortex-R52 architecture. Duration: 4 days Prerequisites and related
LRU. Pseudo LRU A B C D E F G H A B C D E F G H H H C. Copyright 2012, Elsevier Inc. All rights reserved.
 LRU A list to keep track of the order of access to every block in the set. The least recently used block is replaced (if needed). How many bits we need for that? 27 Pseudo LRU A B C D E F G H A B C D E
LRU A list to keep track of the order of access to every block in the set. The least recently used block is replaced (if needed). How many bits we need for that? 27 Pseudo LRU A B C D E F G H A B C D E
William Stallings Computer Organization and Architecture 8th Edition. Cache Memory
 William Stallings Computer Organization and Architecture 8th Edition Chapter 4 Cache Memory Characteristics Location Capacity Unit of transfer Access method Performance Physical type Physical characteristics
William Stallings Computer Organization and Architecture 8th Edition Chapter 4 Cache Memory Characteristics Location Capacity Unit of transfer Access method Performance Physical type Physical characteristics
ESE Back End 2.0. D. Gajski, S. Abdi. (with contributions from H. Cho, D. Shin, A. Gerstlauer)
 ESE Back End 2.0 D. Gajski, S. Abdi (with contributions from H. Cho, D. Shin, A. Gerstlauer) Center for Embedded Computer Systems University of California, Irvine http://www.cecs.uci.edu 1 Technology advantages
ESE Back End 2.0 D. Gajski, S. Abdi (with contributions from H. Cho, D. Shin, A. Gerstlauer) Center for Embedded Computer Systems University of California, Irvine http://www.cecs.uci.edu 1 Technology advantages
Page 1. Recall from Pipelining Review. Lecture 15: Instruction Level Parallelism and Dynamic Execution
 CS252 Graduate Computer Architecture Recall from Pipelining Review Lecture 15: Instruction Level Parallelism and Dynamic Execution March 11, 2002 Prof. David E. Culler Computer Science 252 Spring 2002
CS252 Graduate Computer Architecture Recall from Pipelining Review Lecture 15: Instruction Level Parallelism and Dynamic Execution March 11, 2002 Prof. David E. Culler Computer Science 252 Spring 2002
Embedded Computation
 Embedded Computation What is an Embedded Processor? Any device that includes a programmable computer, but is not itself a general-purpose computer [W. Wolf, 2000]. Commonly found in cell phones, automobiles,
Embedded Computation What is an Embedded Processor? Any device that includes a programmable computer, but is not itself a general-purpose computer [W. Wolf, 2000]. Commonly found in cell phones, automobiles,
Chapter 5 Memory Hierarchy Design. In-Cheol Park Dept. of EE, KAIST
 Chapter 5 Memory Hierarchy Design In-Cheol Park Dept. of EE, KAIST Why cache? Microprocessor performance increment: 55% per year Memory performance increment: 7% per year Principles of locality Spatial
Chapter 5 Memory Hierarchy Design In-Cheol Park Dept. of EE, KAIST Why cache? Microprocessor performance increment: 55% per year Memory performance increment: 7% per year Principles of locality Spatial
What is Pipelining? Time per instruction on unpipelined machine Number of pipe stages
 What is Pipelining? Is a key implementation techniques used to make fast CPUs Is an implementation techniques whereby multiple instructions are overlapped in execution It takes advantage of parallelism
What is Pipelining? Is a key implementation techniques used to make fast CPUs Is an implementation techniques whereby multiple instructions are overlapped in execution It takes advantage of parallelism
EE 3170 Microcontroller Applications
 EE 3170 Microcontroller Applications Lecture 4 : Processors, Computers, and Controllers - 1.2 (reading assignment), 1.3-1.5 Based on slides for ECE3170 by Profs. Kieckhafer, Davis, Tan, and Cischke Outline
EE 3170 Microcontroller Applications Lecture 4 : Processors, Computers, and Controllers - 1.2 (reading assignment), 1.3-1.5 Based on slides for ECE3170 by Profs. Kieckhafer, Davis, Tan, and Cischke Outline
Dissecting Execution Traces to Understand Long Timing Effects
 Dissecting Execution Traces to Understand Long Timing Effects Christine Rochange and Pascal Sainrat February 2005 Rapport IRIT-2005-6-R Contents 1. Introduction... 5 2. Long timing effects... 5 3. Methodology...
Dissecting Execution Traces to Understand Long Timing Effects Christine Rochange and Pascal Sainrat February 2005 Rapport IRIT-2005-6-R Contents 1. Introduction... 5 2. Long timing effects... 5 3. Methodology...
HY425 Lecture 05: Branch Prediction
 HY425 Lecture 05: Branch Prediction Dimitrios S. Nikolopoulos University of Crete and FORTH-ICS October 19, 2011 Dimitrios S. Nikolopoulos HY425 Lecture 05: Branch Prediction 1 / 45 Exploiting ILP in hardware
HY425 Lecture 05: Branch Prediction Dimitrios S. Nikolopoulos University of Crete and FORTH-ICS October 19, 2011 Dimitrios S. Nikolopoulos HY425 Lecture 05: Branch Prediction 1 / 45 Exploiting ILP in hardware
