3. Examine the importance of mobile systems and securing information and knowledge.
|
|
|
- Adam Payne
- 6 years ago
- Views:
Transcription
1 UNIT III STUDY GUIDE Collaboration Hardware, Software, and Mobile Systems; and Database Processing Course Learning Outcomes for Unit III Upon completion of this unit, students should be able to: 3. Examine the importance of mobile systems and securing information and knowledge. 5. Evaluate the approaches to developing organizational knowledge management strategies. 8. Identify major types of hardware and software used by organizations. Reading Assignment Chapter 4: Hardware, Software, and Mobile Systems Chapter 5: Database Processing Unit Lesson In Unit II, we investigated ways information systems can support collaboration and reviewed Porter s five forces model. In this unit, we will discuss the basic concepts of hardware and software. We will also discuss open source software development, database management systems, and compare the differences between native and thin-client applications. Lastly, we will explore mobile systems and the characteristics of quality mobile user experiences. It is important that business professionals understand hardware components, types of hardware, and computer data. We will start off with bits and bytes. Bits are used for computer data because they are easy to represent electronically. For example, you should know the differences between bits, bytes, kilobytes, megabytes, gigabyte, terabyte, petabyte, and exabyte (see Figure 1). Figure 1. Storage Capacity Terminology (Kroenke, 2015, p. 116) BBA 3551, Information Systems Management 1
2 A byte generally contains eight bits. A switch can be open or closed (see Figure 2). The author of your textbook describes the open switch represents zero and a closed switch represents one (Kroenke, 2015, p. 115). The zero and one also represent off and on respectively. He goes on to explain that all forms of computer data are represented by bits. The data can be numbers, characters, currency amounts, photos, recordings, or whatever. All are simply a string of bits specifications for size of main memory, disk, and other computer devices are expressed in bytes (Kroenke, 2015, pp ). Figure 2. Physical Representation of Bits (Kroenke, 2015, p. 115) The categories of computer software are clients and servers. Personal computers use non-mobile operating systems such as Windows and OSX. Remember that operating systems are developed for specific hardware and are often referred to as native applications. In other words, MS Windows was created specifically for PC hardware based systems so, you cannot install MS Windows on an Apple Macintosh as a base OS, nor can you install the Apple OS on a PC based system. Some version of Windows resides on more than 85% of the world s desktops, and, for business users, it is more than 95%. Other major operating systems are Unix and Linux. Be careful not to confuse operating systems with applications. MS Windows 8 is an operating system, while MS Office 365 is an application. Another application program, thin-client, are applications specifically designed for use within web browsers such as Firefox and Internet Explorer. Because these applications run within a browser, they can run on any type of computer with an internet connection and a browser. Thin-client applications vary considerably. Some are simply fancy Web-based brochures, while others are quite sophisticated. Which is best? Choice depends on strategy, particular goals, schedule, requirements for your application, budget, tolerance for managing technical projects, need for application revenue, and other factors. In general, thin-client applications are cheaper to develop and maintain, but may lack the wow factor. Let s take a look at Question 4-3, Using Your Knowledge, on page 151 (be sure to review the AllRoad Parts scenario on pages ) Suppose that you are Lucas at AllRoad Parts. List five criteria you would use in helping AllRoad Parts decide whether it should develop a native or a thin-client mobile application. Justify your criteria. There are a number of considerations that should be evaluated for this decision. Here is a partial list: Strategy for the mobile application: Are they just trying to create a mobile-device presence (browserbased) or are there very specific, complex elements to include in the application? Specific application requirements: What specific features and functions are to be included in the application? Budget: Native applications are much more costly to develop, requiring talented developers who will need to create a unique version of the application for every mobile operating system. BBA 3551, Information Systems Management 2
3 Schedule: Native applications will take much longer to develop. Ability to manage a technical project: Technical expertise to develop native applications is scarcer and will require more effort to acquire and manage. Need for application revenue: Native applications can potentially generate a revenue stream from royalties, while thin-client applications are made available for free. Kroenke defines virtualization as the process by which one computer hosts the appearance of many computers. One operating system, called the host operating system runs one or more operating systems as applications (2015, p. 120). Hosted operating systems are called virtual machines (vm). Each virtual machine has disk space and other resources allocated to it. Operates as if installed on own computer. Host operating system controls activities of virtual machines to prevent them from interfering with one another. An example is in the way Apple Macintoshes can take advantage of virtualization technology and run multiple operating systems (see Figure 3). Figure 3. Virtualization Example Own Versus License You do not actually own a program you own a license or right to use the program. When you buy a Windows license, Microsoft is selling you the right to use Windows. Microsoft continues to own the Windows program. Large organizations negotiate a site license that authorizes the company to install the product on all company computers or a specific site. Linux, no company can sell you a license to use it. It is owned by the Open Source Community. BBA 3551, Information Systems Management 3
4 What is Firmware? Software installed into special, read-only memory of a printer or other device and becomes part of the device s memory. Users do not need to load firmware into memory. It can be changed or upgraded, but normally, this is a task for IS professionals. Why do Programmers Volunteer Their Services to Open Source Projects? Programming is an intense combination of art and logic. Designing and writing a complicated computer program is exceedingly pleasurable (and addictive). Programmers can exercise creativity while working on projects they find interesting and fulfilling. Programmers can exhibit their skill, both for pride, finding a job or consulting employment, or start a business selling services to support an open source product. Open source involves: Collaboration of many programmers Examining source code and identifying a need, creating a new feature or redesigning an existing feature, or fixing a problem Code evaluated and extended by others Iteration, peer reviews, and well-managed projects yield high-quality code Mobile Information System In addition to computer operating systems, there are mobile client operating systems. The Apple iphone uses ios, and Motorola Android uses the Android OS. As of 2013, there are 6.8 billion wireless subscriptions. Onethird of those subscriptions involve smartphones or other mobile devices, meaning there are already 1.9 billion mobile system subscriptions worldwide. Mobile systems have a major impact on business and society today an impact forcing industry change while creating new career opportunities for mobile-is-savvy professionals and large numbers of new, interesting mobile-is-related jobs. What Characterizes Quality Mobile User Experiences? The primary emphasis is on users content, giving such content as much display as possible. Rather than show menus, toolbars, and heavy window borders, content should be shown cleanly and in center stage. Context-sensitive chrome pops up in the display when appropriate. Because mobile screen size is often limited, modern mobile applications eliminate it as much as possible. Touch-screen oriented, contextsensitive, pop-up menus are used with a mouse and keyboard. Characteristics that indicate quality mobile user experiences are: feature content, use context-sensitive chrome, provide animation and lively behavior, design to scale and share, and use the cloud. Application Scaling Mobile applications need to be designed to share data. For example, Windows 8 introduces a feature called charms, which are icons that slide in from the right of the display. One of the default charms is Share, and it is used to share data from one mobile application to another. BBA 3551, Information Systems Management 4
5 The Cloud Push data is data the server sends to or pushes onto the mobile device. Pull data is data the mobile device requests from the server. (Notice that those terms use the server s perspective.) Of the two types, push data is more impressive to users because they need to do nothing to receive it. On the other hand, excessive pushing is annoying. Let s take a look at question 4-4 Using Your Knowledge on page 152: 4-4. Describe how the class enrollment application at your university could benefit from a mobile application that uses the cloud. The class enrollment application could enable students to view course offerings, register for classes, view class waiting lists, change class registration, and view class schedules. Being able to do all of these things would be highly valued by students who can be anywhere and perform these registration-related tasks at any time. Challenges of personal mobile devices at work: Organizations have a love/hate relationship with their employees use of their own mobile devices at work. They love the cost-saving possibility of having employees buy their own hardware, but hate the increased vulnerability and loss of control. BYOD Policy: A BYOD (bring your own device) policy is a statement concerning employees permissions and responsibilities when they use their own device for organizational business. BYOD policies are rapidly evolving and many organizations have not yet determined what is best for them. If your employer has a committee to develop such policies, join it if you can. Doing so will provide a great way to gain exposure to the leading technology thinkers at your organization. As an example, an employer in recent years had a very restrictive policy on laptops any laptop in use on site that wanted access to the organization s WiFi services had to be physically registered with the central Information Technology Services organization. Although this policy has been relaxed, it had the advantage of forcing each user to have certain malware protection installed. BYOD policies will have to continue to relax and accommodate with wide array of devices and respond to user demands. Case Study 4 Apple Computers Apple tripled its market capitalization to become the second largest public company in the world. They pioneered well-engineered home computers and innovative interfaces with Apple II PC and Macintosh computer for students and knowledge workers. The succession of CEOs made numerous mistakes, such as not rewarding innovative engineering, creating too many products for too many market segments, and losing the respect of the retail computer stores. In 1996, Apple bought Job s NeXT Computing and gained technology that became the foundation of Mac OS X. Apple also soon created new markets with ipod, iphone, ipad, and Internet sales of music and apps. Apple encourages customer visits and earns loyalty with its open and inviting sales floor, Genius Bar help desk, and well-trained sales force. Apple shares its revenue with application developers who created 445,000 ios applications. Now, let s take a look at Apple s strategy and the future of Apple by discussing the questions on page 155, Apple without Steve Jobs Which of Porter s four competitive strategies does Apple engage in? Explain. Apple is pursuing a focused differentiation strategy. It is focused primarily on the mobile computing device market and is differentiating itself through its incredible engineering and huge array of applications for its devices. BBA 3551, Information Systems Management 5
6 4-8. What do you think are the three most important factors in Apple s past success? Justify your answer. Apple has demonstrated a capability of creating innovative new products successfully. Apple has also been able to keep that stream of innovations going and to enable the innovations to play off of each other. A culture that encourages and supports these engineering successes is obvious. Apple also has developed an ability to sell and market its new products successfully Steve Jobs passed away in October Until his death, he had been the heart and soul of Apple s innovation. Today, 35,000 Apple employees continue onward in his absence. A huge question facing many investors is whether the company can be successful without him. The current stock price would seem to indicate that the market does not. What do you think? What role did Jobs play? How can Apple respond to his loss? Would you be willing to invest in Apple without his leadership? Why or why not? Jobs had a very hands-on involvement in the business. He was the company s chief innovator. Of course, he did not do it all alone, but he seemed to set the direction for the business in a very effective way. He had the ability to be a visionary and send his company s engineers out to conquer challenges that paid off in big ways. The company then also had the ability to develop support systems for the new innovations. Another capability was to recover and move on from product failures, which Apple had its share of as well. Can this company continue its progress without Jobs? Obviously, only time will tell. Some students may feel that Apple will be unable to sustain its success without the unique vision and leadership style of Jobs and would, therefore, be unwilling to invest in Apple. Other students may feel that Apple s executives have been hand-picked and mentored by Jobs and are, therefore, capable of continuing to lead Apple effectively. There is no question that Apple will be a different place without Jobs influence, but it is not necessarily doomed Microsoft took an early lead in the development of slate devices (like the ipad), and it had the world s leading operating system and applications for more than 20 years. Provide five reasons why Microsoft was not able to achieve the same success that Apple has. Most industry analysts would agree that the skills and abilities of Microsoft s 88,000 employees are as good, on average, as Apple s. Here is a list of a few ideas to consider: Lack of a visionary leader since Gates has departed Very diffused focus many market niches pursued simultaneously Emphasis on acquiring new technologies rather than in-house development Strategy of maintaining edge through strategic manipulation rather than product enhancement Few products that are truly amazing, must-have products Considering your answers to the four questions above, if you had a spare $5,000 in your portfolio and wanted to buy an equity stock with it, would you buy AAPL (Apple)? Why, or why not? There may be different opinions on this, so ask and consider the following questions: Is it the best strategy to buy a stock with the price at record highs? Are you concerned about the loss of Steve Jobs on Apple s future? Do you believe in the company s ability to keep producing technical winners? On what do you base this opinion? In Chapter 5, we will discuss the why, what, and how of database processing. The purpose of a database is to keep track of things. A database contains a collection of tables (e.g., invoice, customers, etc.) and each record in the table contains a selection of fields or columns (e.g., invoice number, customer name, etc.). Relationships between tables help connect information such as the primary key. Primary keys are unique identifiers such as invoice numbers and customer numbers. These help make each record unique and also makes searching for a specific record much easier. For example, suppose you had four customers, each named Tom Jones; how do you find the right one? The primary key will help you differentiate one Tom Jones from the other. BBA 3551, Information Systems Management 6
7 A database management system (DBMS) is a program that provides you with the ability to create, process, and administer databases. Be careful not to confuse databases and DBMS; databases are a collection of tables, relationships, and metadata, while DBMS is the software that helps you manage the database. Database applications make databases more useful through: traditional forms, queries, reports, and applications; browser forms, reports, queries, and applications; and multi-user processing. Data models are a logical representation of what the database structure would look like. One such model is the entity-relationship model (ERM). This model is used as a tool for constructing data models. The ERM model assists developers in identifying the content of the database by defining things such as entities (what will be stored in the database) and the relationship among those entities. Entities are data that the user wants to track such as customer invoices, inventory, or contact. Entities have attributes that further define the entity such as invoice number, product description, number of units, and cost. Entities have an identifier that is associated with only one entity instance such as order number. Order number is an identifier because there can only be one order number. Figure 4. An entity-relationship diagram that shows the relationships among a database, database application, and users In logical database designs, database designers will use diagrams called entity-relationship diagrams or ERD. Relationships between entities in the diagram are represented with the use of crow s feet (see Figure 4). The forked lines indicate the type of relationship. Let s take a look at Figure 5-21 on page 177 of the textbook and consider the relationship between Adviser and Student. Below is an explanation of what it means if the maximum cardinality of this relationship is: a. N:1 An advisor is assigned many students; a student is assigned one advisor. b. 1:1 An advisor is assigned one student; a student is assigned one advisor. c. 5:1 An advisor is assigned no more than five students; a student is assigned one advisor. d. 1:5 An advisor is assigned one student; a student is assigned no more than five advisors. Next, let s look at Figure 5-28 on page 192 of your textbook. Now, let s identify two entities in the data entry form shown and the attributes shown for each as well as the identifiers: Entities: employee, class Employee attributes: employee number, first name, last name, Class attributes: course name, course date, instructor, remarks Employee identifier: employee number (also the primary key) Class identifier: course name, course date Data models are transformed into a database design through normalization and representing relationships. BBA 3551, Information Systems Management 7
8 Sometimes, tables are poorly designed and thus may suffer integrity problems. Normalization can be used to analyze the relationships between attributes within each entity and then determine if the structure needs improvement, usually by confirming that each table has only one theme. Let s take a look at Question 6 from, Using MIS InClass 5, on page Relate what you have learned in this exercise to the 3D printing discussion at AllRoad Parts. The opening case study vignette reveals how important AllRoad Parts database is in analyzing the 3D printing issue. Lucas says We know from our orders which parts each customer is most likely to order In other words, AllRoad Parts has extensive data on customer purchase history that it is using in formulating ideas for a customer-purchasing app for 3D printing designs. The database of customer purchasing history and the ability to query it enables AllRoad Parts to make an informed decision on the design of this potential new purchasing app, which will offer a cost-effective way of selling 3D printing designs to its customers. Let s also look at a few of the AllRoad Parts questions from Case Study 5 on page 195 of your textbook: 5-8. Given what you know about AllRoad Parts, should it use a relational DBMS, such as Oracle Database or MySQL, or should it use Cassandra? AllRoad Parts most likely can utilize a relational DBMS effectively and will not require a data management approach like Cassandra. AllRoad Parts probably does not have the volume of transactions or servers to justify a NoSQL approach Suppose that AllRoad Parts decides to use a NoSQL solution, but a battle emerges among the employees in the IT Department. One faction wants to use Cassandra, but another faction wants to use a different NoSQL data store, named MongoDB ( Assume that you re Kelly, and Lucas asks for your opinion about how he should proceed. How do you respond? Kelly should tell Lucas that the decision to use a specific NoSQL solution should be based on a careful analytical evaluation of AllRoad Parts requirements. There is no reason for this to become a factionalized debate. Determine exactly what AllRoad Parts needs are and then determine, analytically, how well Cassandra and MongoDB satisfy those requirements. Once each of the NoSQL s capabilities have been objectively researched and matched to the company s real requirements, the best fit should become apparent. Requirements should include technical feasibility, economic feasibility, and organizational feasibility issues in order to be complete. Let s also take a look at Question 5-11 of MyMISLab on page The partial E-R diagram in Figure 5-31 is for a sales order. Assume there is only one salesperson per sales order. a. Specify the maximum cardinalities for each relationship. State your assumptions, if necessary. A salesperson writes many sales orders; a sales order is written by one salesperson. (Assumes salespeople work alone and not in teams.) A customer places many sales orders; a sales order is placed by one customer. A sales order contains many line items; a line item is contained in one sales order. A line item contains one item; an item is contained in one line item. b. Specify the minimum cardinalities for each relationship. State your assumptions, if necessary. A salesperson may have zero sales orders; a sales order is written by one salesperson. (Assumes salespeople work alone and not in teams; assumes a sales order is not required for a salesperson to exist in the system.) A customer places at least one sales order; a sales order is placed by one and only one customer. (Assumes at least one sales order is required for a customer to exist in the system.) A sales order contains at least one line item; a line item is contained in one and only one sales order. A line item contains one and only one item; an item is contained in one and only one line item. BBA 3551, Information Systems Management 8
9 In closing, the AllRoad Parts operational database discussed at the beginning of the chapter has data that Drew and Addison need to determine which parts to consider for 3D printing. If Addison and Drew are dependent on Lucas (or the IT department) to produce the reports they need, they will (a) wait a long time and (b) probably not get what they want. Once they get the data, assuming that Addison knows how to create queries and reports, they can iterate on their own, without help from Lucas (or the IT department). They can produce their own reports, see the results, produce more reports, and so forth. Relying on their own skills will give them much more freedom and better results. At this point, relational database technology is not appropriate either for storing the 3D parts files or for supporting the graphics used for query-by-graphics. MongoDB would be a better choice. Reference Kroenke, D. (2015). Using MIS 2014 (7th ed.). Upper Saddle River, NJ: Prentice Hall. Suggested Reading Chapter 4 Presentation Chapter 5 Presentation Li, J., Moselhi, O., & Alkass, S. (2006). Internet-based database management system for project control. Retrieved from In order to access the resources below, you must first log into the mycsu Student Portal and access the ABI/INFORM Complete database within the CSU Online Library. Anjard, R. P., Sr. (1994). The basics of database management systems (DBMS). Industrial Management + Data Systems, 94(5), 11. Bass, L. J. (1987). Role of a historian in a database management system. IEEE Software, 4(2), Learning Activities (Non-Graded) Course Flashcards: From the Textbook: Using MIS InClass 4, Place Your Bets Now! pp Using MIS InClass 5, How Much Is a Database Worth? p. 167 Ethics Guide, Showrooming: The Consequences, pp Ethics Guide, Querying Inequality? pp Security Guide, Because It s Where the Money is, pp Security guide, No, Thanks, I ll Use a Spreadsheet, pp Guide, Keeping up to Speed, pp Guide, Immanuel Kant, Data Modeler, pp Using Your Knowledge, pp Using Your Knowledge, pp Case Study 4, The Apple of Your i, pp Case Study 5, Fail Away with Dynamo, Bigtable, and Cassandra, pp Non-graded Learning Activities are provided to aid students in their course of study. You do not have to submit them. If you have questions, contact your instructor for further guidance and information. BBA 3551, Information Systems Management 9
Chapter 5. Database Processing
 Chapter 5 Database Processing No, Drew, You Don t Know Anything About Creating Queries." AllRoad Parts operational database used to determine which parts to consider for 3D printing. If Addison and Drew
Chapter 5 Database Processing No, Drew, You Don t Know Anything About Creating Queries." AllRoad Parts operational database used to determine which parts to consider for 3D printing. If Addison and Drew
Chapter 5. Database Processing
 Chapter 5 Database Processing We Don t Have a Way to Track the Data About the Videos. Falcon Security stores sequentially numbered digital video files in separated directories for each client. Tracking
Chapter 5 Database Processing We Don t Have a Way to Track the Data About the Videos. Falcon Security stores sequentially numbered digital video files in separated directories for each client. Tracking
Why This Fifth Edition, Now?
 Why This Fifth Edition, Now? The past 12 months have been one of the most exciting years for MIS in memory. You probably know about Apple s icloud, Lion, and new software versions for the ipad and iphone.
Why This Fifth Edition, Now? The past 12 months have been one of the most exciting years for MIS in memory. You probably know about Apple s icloud, Lion, and new software versions for the ipad and iphone.
Chapter 4. Hardware, Software, and Mobile Systems
 Chapter 4 Hardware, Software, and Mobile Systems 3D Printing Our Own Drones Isn t Going to Save Us Enough Money. Investigating using 3D-printed parts to make drones in-house. Cost-savings, greater flexibility
Chapter 4 Hardware, Software, and Mobile Systems 3D Printing Our Own Drones Isn t Going to Save Us Enough Money. Investigating using 3D-printed parts to make drones in-house. Cost-savings, greater flexibility
Using MIS. Chapter 5. Database Processing. Tenth Edition
 Using MIS Tenth Edition Chapter 5 Database Processing Slides in this presentation contain hyperlinks. JAWS users should be able to get a list of links by using INSERT+F7 We Don t Have a Way to Track the
Using MIS Tenth Edition Chapter 5 Database Processing Slides in this presentation contain hyperlinks. JAWS users should be able to get a list of links by using INSERT+F7 We Don t Have a Way to Track the
FOUNDATIONS OF INFORMATION SYSTEMS MIS 2749 COURSE SYLLABUS Fall, Course Title and Description
 FOUNDATIONS OF INFORMATION SYSTEMS MIS 2749 COURSE SYLLABUS Fall, 2013 Instructor s Name: Vicki Robertson E-mail: vrobrtsn@memphis.edu Course Title and Description Foundations of Information Systems. (3
FOUNDATIONS OF INFORMATION SYSTEMS MIS 2749 COURSE SYLLABUS Fall, 2013 Instructor s Name: Vicki Robertson E-mail: vrobrtsn@memphis.edu Course Title and Description Foundations of Information Systems. (3
Predictive Insight, Automation and Expertise Drive Added Value for Managed Services
 Sponsored by: Cisco Services Author: Leslie Rosenberg December 2017 Predictive Insight, Automation and Expertise Drive Added Value for Managed Services IDC OPINION Competitive business leaders are challenging
Sponsored by: Cisco Services Author: Leslie Rosenberg December 2017 Predictive Insight, Automation and Expertise Drive Added Value for Managed Services IDC OPINION Competitive business leaders are challenging
Computer Software A computer contains two major sets of tools, software and hardware. Software is generally divided into Systems software and
 Computer Software A computer contains two major sets of tools, software and hardware. Software is generally divided into Systems software and Applications software. Systems software provides infrastructure
Computer Software A computer contains two major sets of tools, software and hardware. Software is generally divided into Systems software and Applications software. Systems software provides infrastructure
DATA Data and information are used in our daily life. Each type of data has its own importance that contribute toward useful information.
 INFORMATION SYSTEM LESSON 41 DATA, INFORMATION AND INFORMATION SYSTEM SMK Sultan Yahya Petra 1 DATA Data and information are used in our daily life. Each type of data has its own importance that contribute
INFORMATION SYSTEM LESSON 41 DATA, INFORMATION AND INFORMATION SYSTEM SMK Sultan Yahya Petra 1 DATA Data and information are used in our daily life. Each type of data has its own importance that contribute
SHORT ANSWER. Write the word or phrase that best completes each statement or answers the question.
 Exam Name SHORT ANSWER. Write the word or phrase that best completes each statement or answers the question. 1) (3) Identify 3 factors that affect data quality and drive information quality. 1) 2) (3)
Exam Name SHORT ANSWER. Write the word or phrase that best completes each statement or answers the question. 1) (3) Identify 3 factors that affect data quality and drive information quality. 1) 2) (3)
Inspire Education Program
 Inspire Education Program infocus.com Effective, Affordable Technology for Tomorrow InFocus Education Solutions For 30 years, InFocus has been a leader in educational technology that makes learning more
Inspire Education Program infocus.com Effective, Affordable Technology for Tomorrow InFocus Education Solutions For 30 years, InFocus has been a leader in educational technology that makes learning more
RELATIONSHIP WITH KONICA MINOLTA
 JOHN ENJOY DOE A FLEXIBLE INC. ENJOYS MOBILE TRUSTFUL WORKSTYLE RELATIONSHIP WITH KONICA MINOLTA Global technology leader profits from document security, lower costs, greener printing and the same level
JOHN ENJOY DOE A FLEXIBLE INC. ENJOYS MOBILE TRUSTFUL WORKSTYLE RELATIONSHIP WITH KONICA MINOLTA Global technology leader profits from document security, lower costs, greener printing and the same level
KONICA MINOLTA MOBILE PRINTING SOLUTIONS
 JOHN ENJOY DOE A FLEXIBLE INC. ENJOYS WORKSTYLE TRUSTFUL WITH RELATIONSHIP MOBILE PRINTING WITH KONICA MINOLTA Global technology leader profits from document security, lower costs, greener printing and
JOHN ENJOY DOE A FLEXIBLE INC. ENJOYS WORKSTYLE TRUSTFUL WITH RELATIONSHIP MOBILE PRINTING WITH KONICA MINOLTA Global technology leader profits from document security, lower costs, greener printing and
Welcome to Windows 10. Love it or Avoid it
 1 Welcome to Windows 10 Love it or Avoid it 2 What is an OPERATING SYSTEM??? 1) It s a set of programs that control the computer and make the components work together 2) It provides a interface between
1 Welcome to Windows 10 Love it or Avoid it 2 What is an OPERATING SYSTEM??? 1) It s a set of programs that control the computer and make the components work together 2) It provides a interface between
The Rise of Open Source Software
 14 October 2017 The Rise of Open Source Software Tony Wasserman Presented at Open Source India 2017 cmu.edu/iii 2017 Integrated Innovation Institute From Linux Asia to Open Source India Huge changes in
14 October 2017 The Rise of Open Source Software Tony Wasserman Presented at Open Source India 2017 cmu.edu/iii 2017 Integrated Innovation Institute From Linux Asia to Open Source India Huge changes in
Vendor: Cisco. Exam Code: Exam Name: Advanced Collaboration Architecture Sales Engineer. Version: Demo
 Vendor: Cisco Exam Code: 700-039 Exam Name: Advanced Collaboration Architecture Sales Engineer Version: Demo QUESTION 1 Which three statements are reasons why customers consider Cisco as their collaboration
Vendor: Cisco Exam Code: 700-039 Exam Name: Advanced Collaboration Architecture Sales Engineer Version: Demo QUESTION 1 Which three statements are reasons why customers consider Cisco as their collaboration
Cloud Computing. January 2012 CONTENT COMMUNITY CONVERSATION CONVERSION
 Cloud Computing January 2012 CONTENT COMMUNITY CONVERSATION CONVERSION Purpose and Methodology Survey Sample Field Work December 20, 2011 January 9, 2012 Total Respondents 554 Margin of Error +/- 4.2%
Cloud Computing January 2012 CONTENT COMMUNITY CONVERSATION CONVERSION Purpose and Methodology Survey Sample Field Work December 20, 2011 January 9, 2012 Total Respondents 554 Margin of Error +/- 4.2%
 Mobile Application Development by Lynn Rosier TEA 126.39 http://ritter.tea.state.tx.us/rules/tac/chapter126/ch126c.html#126.39 9-11:15 Mobile apps overview, software, possible projects, and an intro to
Mobile Application Development by Lynn Rosier TEA 126.39 http://ritter.tea.state.tx.us/rules/tac/chapter126/ch126c.html#126.39 9-11:15 Mobile apps overview, software, possible projects, and an intro to
Why is Office 365 the right choice?
 Why is Office 365 the right choice? People today want to be productive wherever they go. They want to work faster and smarter across their favorite devices, while staying current and connected. Simply
Why is Office 365 the right choice? People today want to be productive wherever they go. They want to work faster and smarter across their favorite devices, while staying current and connected. Simply
Economics: Principles in Action 2005 Correlated to: Indiana Family and Consumer Sciences Education, Consumer Economics (High School, Grades 9-12)
 Indiana Family and Consumer Sciences Education, Consumer Economics Consumer Economics 1.0 PROCESSES: Explain, demonstrate, and integrate processes of thinking, communication, leadership, and management
Indiana Family and Consumer Sciences Education, Consumer Economics Consumer Economics 1.0 PROCESSES: Explain, demonstrate, and integrate processes of thinking, communication, leadership, and management
Discovering Computers 2016
 Discovering Computers 2016 Tools, Apps, Devices, and the Impact of Technology Chapter 9 Operating Systems Objectives Overview Explain the purpose of an operating system Describe the start-up process and
Discovering Computers 2016 Tools, Apps, Devices, and the Impact of Technology Chapter 9 Operating Systems Objectives Overview Explain the purpose of an operating system Describe the start-up process and
QM Chapter 1 Database Fundamentals Version 10 th Ed. Prepared by Dr Kamel Rouibah / Dept QM & IS
 QM 433 - Chapter 1 Database Fundamentals Version 10 th Ed Prepared by Dr Kamel Rouibah / Dept QM & IS www.cba.edu.kw/krouibah Dr K. Rouibah / dept QM & IS Chapter 1 (433) Database fundamentals 1 Objectives
QM 433 - Chapter 1 Database Fundamentals Version 10 th Ed Prepared by Dr Kamel Rouibah / Dept QM & IS www.cba.edu.kw/krouibah Dr K. Rouibah / dept QM & IS Chapter 1 (433) Database fundamentals 1 Objectives
Appendix F Course codes, descriptions, units, lecture/lab
 Appendix F Course codes, descriptions, units, lecture/lab CIS 003 Introduction to Microsoft Word Units: 1 Students will learn the basics of Windows and Microsoft Word. Specific topics covered include:
Appendix F Course codes, descriptions, units, lecture/lab CIS 003 Introduction to Microsoft Word Units: 1 Students will learn the basics of Windows and Microsoft Word. Specific topics covered include:
DIABLO VALLEY COLLEGE CATALOG
 COMPUTER INFORMATION SYSTEMS CIS Mike Holtzclaw, Senior Dean San Ramon Campus Division San Ramon Campus Possible career opportunities Training in computer information systems prepares students for a broad
COMPUTER INFORMATION SYSTEMS CIS Mike Holtzclaw, Senior Dean San Ramon Campus Division San Ramon Campus Possible career opportunities Training in computer information systems prepares students for a broad
Business & Technology Department
 Accounting & Management Introduction to Business Personal Finance+ Microsoft Office+ Accounting 1 Accounting 2+ Accounting 3*+ Business Management Entrepreneurship: Virtual Enterprise International** Business
Accounting & Management Introduction to Business Personal Finance+ Microsoft Office+ Accounting 1 Accounting 2+ Accounting 3*+ Business Management Entrepreneurship: Virtual Enterprise International** Business
Choices when it comes to your communications infrastructure A BUYER S GUIDE TO IP-BASED SOLUTIONS
 Choices when it comes to your communications infrastructure A BUYER S GUIDE TO IP-BASED SOLUTIONS Introduction A small business has many priorities. With so much on your mind, your phone system might be
Choices when it comes to your communications infrastructure A BUYER S GUIDE TO IP-BASED SOLUTIONS Introduction A small business has many priorities. With so much on your mind, your phone system might be
requirements of Section 10 of the U.S. Securities Act of 1933, as amended, and otherwise in accordance with applicable law.
 Greg Kleiner, Twilio VP of Investor Relations & Treasurer Thank you. Good afternoon everyone and thank you for joining us on such short notice. As you ve seen by now, we ve announced the signing today
Greg Kleiner, Twilio VP of Investor Relations & Treasurer Thank you. Good afternoon everyone and thank you for joining us on such short notice. As you ve seen by now, we ve announced the signing today
Set your office free.
 Set your office free. Microsoft Office 365 offered by BT. Anywhere access. Stay connected on the go. Look professional. Make the best impression. Easy-to-manage IT. Big business benefits without big business
Set your office free. Microsoft Office 365 offered by BT. Anywhere access. Stay connected on the go. Look professional. Make the best impression. Easy-to-manage IT. Big business benefits without big business
Reinvent learning HP Education Solutions
 Reinvent learning HP Education Solutions 2018 1 HP EDUCATION HP Education solutions are designed to deliver meaningful outcomes for students, schools, and communities. They inspire students to learn everywhere,
Reinvent learning HP Education Solutions 2018 1 HP EDUCATION HP Education solutions are designed to deliver meaningful outcomes for students, schools, and communities. They inspire students to learn everywhere,
App Development. Quick Guides for Masterminds. J.D Gauchat Cover Illustration by Patrice Garden
 App Development Quick Guides for Masterminds J.D Gauchat www.jdgauchat.com Cover Illustration by Patrice Garden www.smartcreativz.com Quick Guides for Masterminds Copyright 2018 by John D Gauchat All Rights
App Development Quick Guides for Masterminds J.D Gauchat www.jdgauchat.com Cover Illustration by Patrice Garden www.smartcreativz.com Quick Guides for Masterminds Copyright 2018 by John D Gauchat All Rights
E-Commerce Business Technology Society Chapter 04
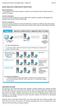 SIMPLE VERSUS MULTI-TIERED WEB SITE ARCHITECTURE System Architecture The arrangement of soft-ware, machinery, and tasks in an information system needed to achieve a specific functionality Two-Tier Architecture
SIMPLE VERSUS MULTI-TIERED WEB SITE ARCHITECTURE System Architecture The arrangement of soft-ware, machinery, and tasks in an information system needed to achieve a specific functionality Two-Tier Architecture
Communicate anywhere, anytime, on any device
 Hosted Voice Phone calls, instant messaging, web conferencing and team collaboration in one amazing Unified Communication platform, powered by market leader, Mitel. All the benefits of the latest technology
Hosted Voice Phone calls, instant messaging, web conferencing and team collaboration in one amazing Unified Communication platform, powered by market leader, Mitel. All the benefits of the latest technology
february 2013 part 1 of 3
 february 2013 part 1 of 3 contents hardware 3 software 10 hardware Microsoft Surface Pro Tablet Initial Reviews Mixed http://bit.ly/129hdn4 http://bit.ly/129hsrr http://nyti.ms/129hv6z -Laptop/Tablet Hybrid
february 2013 part 1 of 3 contents hardware 3 software 10 hardware Microsoft Surface Pro Tablet Initial Reviews Mixed http://bit.ly/129hdn4 http://bit.ly/129hsrr http://nyti.ms/129hv6z -Laptop/Tablet Hybrid
Fundamental Shift: A LOOK INSIDE THE RISING ROLE OF IT IN PHYSICAL ACCESS CONTROL
 Fundamental Shift: A LOOK INSIDE THE RISING ROLE OF IT IN PHYSICAL ACCESS CONTROL Shifting budgets and responsibilities require IT and physical security teams to consider fundamental change in day-to-day
Fundamental Shift: A LOOK INSIDE THE RISING ROLE OF IT IN PHYSICAL ACCESS CONTROL Shifting budgets and responsibilities require IT and physical security teams to consider fundamental change in day-to-day
Work-ready skills in Business, Administration and IT
 Work-ready skills in Business, Administration and IT A guide for centres We believe in learning At the core of everything we do is the desire to make a measurable impact on improving people s lives through
Work-ready skills in Business, Administration and IT A guide for centres We believe in learning At the core of everything we do is the desire to make a measurable impact on improving people s lives through
Collaboration Technical Consultant
 Brochure Collaboration Technical Consultant February, 2012 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 1 of 7 Cisco Support Center in Krakow To
Brochure Collaboration Technical Consultant February, 2012 2012 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public Information. Page 1 of 7 Cisco Support Center in Krakow To
Hybrid IT for SMBs. HPE addressing SMB and channel partner Hybrid IT demands ANALYST ANURAG AGRAWAL REPORT : HPE. October 2018
 V REPORT : HPE Hybrid IT for SMBs HPE addressing SMB and channel partner Hybrid IT demands October 2018 ANALYST ANURAG AGRAWAL Data You Can Rely On Analysis You Can Act Upon HPE addressing SMB and partner
V REPORT : HPE Hybrid IT for SMBs HPE addressing SMB and channel partner Hybrid IT demands October 2018 ANALYST ANURAG AGRAWAL Data You Can Rely On Analysis You Can Act Upon HPE addressing SMB and partner
Developing Applications for ios
 Developing Applications for ios Lecture 1: Mobile Applications Development Radu Ionescu raducu.ionescu@gmail.com Faculty of Mathematics and Computer Science University of Bucharest Evaluation Individual
Developing Applications for ios Lecture 1: Mobile Applications Development Radu Ionescu raducu.ionescu@gmail.com Faculty of Mathematics and Computer Science University of Bucharest Evaluation Individual
WANGANUI HIGH SCHOOL. Bring your own Technology. E-LIFE Steps to e-learning
 WANGANUI HIGH SCHOOL Bring your own Technology E-LIFE Steps to e-learning BRING YOUR OWN TECHNOLOGY At Wanganui High School we want every student to have the best learning opportunities possible. We want
WANGANUI HIGH SCHOOL Bring your own Technology E-LIFE Steps to e-learning BRING YOUR OWN TECHNOLOGY At Wanganui High School we want every student to have the best learning opportunities possible. We want
CREATIVITY MAKES THE DIFFERENCE
 CREATIVITY MAKES THE DIFFERENCE Your school has a big challenge: preparing Generation Z for a rapidly changing world and jobs that don t yet exist. Along with learning digital skills, your students need
CREATIVITY MAKES THE DIFFERENCE Your school has a big challenge: preparing Generation Z for a rapidly changing world and jobs that don t yet exist. Along with learning digital skills, your students need
communications and software
 1 Computer systems, communications and software 1.1 Components of a computer system and modes of use A computer system is made up of hardware and flow of data and information. The storage device is both
1 Computer systems, communications and software 1.1 Components of a computer system and modes of use A computer system is made up of hardware and flow of data and information. The storage device is both
Tennessee. Business Technology Course Code Web Design Essentials. HTML Essentials, Second Edition 2010
 Tennessee Business Technology Course Code 6501240 Web Design Essentials HTML Essentials, Second Edition 2010 Notation Key SE Student Edition LE Learning Expectation Standard 1.0 Demonstrate knowledge of
Tennessee Business Technology Course Code 6501240 Web Design Essentials HTML Essentials, Second Edition 2010 Notation Key SE Student Edition LE Learning Expectation Standard 1.0 Demonstrate knowledge of
Adobe Spark. Schools and Educators. A Guide for. spark.adobe.com
 Adobe Spark A Guide for Schools and Educators spark.adobe.com CONTENTS 1: What Is Adobe Spark?... 3 2: How Much Does Adobe Spark Cost?... 4 3: Is Adobe Spark A Web Application Or An App?... 4 4: Three
Adobe Spark A Guide for Schools and Educators spark.adobe.com CONTENTS 1: What Is Adobe Spark?... 3 2: How Much Does Adobe Spark Cost?... 4 3: Is Adobe Spark A Web Application Or An App?... 4 4: Three
Mac Five reasons to offer OS X now
 An Executive Guide to Mac Five reasons to offer OS X now An Executive Guide to Mac There s a new way to work. It s mobile. It s collaborative. It s fast. And it s why more organizations are offering Mac.
An Executive Guide to Mac Five reasons to offer OS X now An Executive Guide to Mac There s a new way to work. It s mobile. It s collaborative. It s fast. And it s why more organizations are offering Mac.
VISUAL SUMMARY SYSTEM SOFTWARE OPERATING SYSTEMS. System Software
 Rev.Confirming Pages VISUAL SUMMARY System Software SYSTEM SOFTWARE System software works with end users, application programs, and computer hardware to handle many details relating to computer operations.
Rev.Confirming Pages VISUAL SUMMARY System Software SYSTEM SOFTWARE System software works with end users, application programs, and computer hardware to handle many details relating to computer operations.
Special Edition: Tablet Tuesday. Droid Goes Turbo. Windows comes to the HTC One (M8) Meet the iphone 6
 ISSUE 01:31 7:22:15 One Year of Geekly! Today marks the one-year anniversary of Geekly:Weekly, and if there s one thing we ve learned from manufacturers, software creators, and innovators is that this
ISSUE 01:31 7:22:15 One Year of Geekly! Today marks the one-year anniversary of Geekly:Weekly, and if there s one thing we ve learned from manufacturers, software creators, and innovators is that this
GET CLOUD EMPOWERED. SEE HOW THE CLOUD CAN TRANSFORM YOUR BUSINESS.
 GET CLOUD EMPOWERED. SEE HOW THE CLOUD CAN TRANSFORM YOUR BUSINESS. Cloud computing is as much a paradigm shift in data center and IT management as it is a culmination of IT s capacity to drive business
GET CLOUD EMPOWERED. SEE HOW THE CLOUD CAN TRANSFORM YOUR BUSINESS. Cloud computing is as much a paradigm shift in data center and IT management as it is a culmination of IT s capacity to drive business
Cambridge Nationals R001. Revision help (LO1)
 Cambridge Nationals R001 Revision help (LO1) Portable devices These are electronic devices that can be carried easily. Examples include: Laptops Netbooks Mobile phones Tablets (Ipad, Android Tablet) handheld
Cambridge Nationals R001 Revision help (LO1) Portable devices These are electronic devices that can be carried easily. Examples include: Laptops Netbooks Mobile phones Tablets (Ipad, Android Tablet) handheld
InTact Technology : Cutting the Last Tie Holding the Wireless Office to the Desktop. October 2006
 InTact Technology : Cutting the Last Tie Holding the Wireless Office to the Desktop October 2006 Executive Summary Handheld mobile devices have gone a long way to liberate workers from trips back to the
InTact Technology : Cutting the Last Tie Holding the Wireless Office to the Desktop October 2006 Executive Summary Handheld mobile devices have gone a long way to liberate workers from trips back to the
The Rise and Fall of a Tech Leader Nokia Source Texts
 Name :... ID :. Section The Rise and Fall of a Tech Leader Nokia Source Texts Analytical/Descriptive Report Module 1 Report Prompt: Describe the situation and two reasons for the failure of Nokia. 1 Text
Name :... ID :. Section The Rise and Fall of a Tech Leader Nokia Source Texts Analytical/Descriptive Report Module 1 Report Prompt: Describe the situation and two reasons for the failure of Nokia. 1 Text
2018 Texas Focus: On the Move! Accessing Information Anywhere / Anytime! Shedding Light on Cloud Computing Friday, March 2, :30-5:00 PM
 Texas School for the Blind & Visually Impaired Outreach Programs www.tsbvi.edu 512-454-8631 1100 W. 45 th St. Austin, TX 78756 2018 Texas Focus: On the Move! Accessing Information Anywhere / Anytime! Shedding
Texas School for the Blind & Visually Impaired Outreach Programs www.tsbvi.edu 512-454-8631 1100 W. 45 th St. Austin, TX 78756 2018 Texas Focus: On the Move! Accessing Information Anywhere / Anytime! Shedding
UNDERSTAND THE OPPORTUNITY
 SALES GUIDE: seagate solid state hybrid drives (sshd) This interactive sales guide will provide insight into your customers computing challenges, and give you ideas on how to have a conversation that will
SALES GUIDE: seagate solid state hybrid drives (sshd) This interactive sales guide will provide insight into your customers computing challenges, and give you ideas on how to have a conversation that will
Masters of Computer Application (MCA) Entrance 2012 Computer Knowledge Paper I 1. All of the following are examples of real security and privacy
 Masters of Computer Application (MCA) Entrance 2012 Computer Knowledge Paper I 1. All of the following are examples of real security and privacy risks EXCEPT: A. hackers. B. spam. C. viruses. D. identity
Masters of Computer Application (MCA) Entrance 2012 Computer Knowledge Paper I 1. All of the following are examples of real security and privacy risks EXCEPT: A. hackers. B. spam. C. viruses. D. identity
Database Design. 1-4 Major Transformations in Computing. Copyright 2015, Oracle and/or its affiliates. All rights reserved.
 Database Design 1-4 Objectives This lesson covers the following objectives: List the major transformations in computing that have occurred since the 1970 s. Define and give an example of these terms: hardware,
Database Design 1-4 Objectives This lesson covers the following objectives: List the major transformations in computing that have occurred since the 1970 s. Define and give an example of these terms: hardware,
ITS310: Introduction to Computer Based Systems Credit Hours: 3
 ITS310: Introduction to Computer Based Systems Credit Hours: 3 Contact Hours: This is a 3 credit course, offered in accelerated format. This means that 16 weeks of material is covered in 8 weeks. The exact
ITS310: Introduction to Computer Based Systems Credit Hours: 3 Contact Hours: This is a 3 credit course, offered in accelerated format. This means that 16 weeks of material is covered in 8 weeks. The exact
APICS Certified Supply Chain Professional (CSCP)
 APICS Certified Supply Chain Professional (CSCP) LEARNING SYSTEM 2013 Preparation Overview TABLE OF CONTENTS APICS CSCP LEARNING SYSTEM OVERVIEW About the APICS CSCP Program 3 How Professionals Prepare
APICS Certified Supply Chain Professional (CSCP) LEARNING SYSTEM 2013 Preparation Overview TABLE OF CONTENTS APICS CSCP LEARNING SYSTEM OVERVIEW About the APICS CSCP Program 3 How Professionals Prepare
Strategic Information Systems Systems Development Life Cycle. From Turban et al. (2004), Information Technology for Management.
 Strategic Information Systems Systems Development Life Cycle Strategic Information System Any information system that changes the goals, processes, products, or environmental relationships to help an organization
Strategic Information Systems Systems Development Life Cycle Strategic Information System Any information system that changes the goals, processes, products, or environmental relationships to help an organization
E-Guide Server hardware purchasing considerations
 E-Guide Server hardware purchasing considerations Servers are expensive. When you re tasked with making a purchase of this size, you want to be sure you ve made the right choice especially as servers tend
E-Guide Server hardware purchasing considerations Servers are expensive. When you re tasked with making a purchase of this size, you want to be sure you ve made the right choice especially as servers tend
Accounting Ethics and Auditing
 Accounting Ethics and Auditing Only three percent of adults have career-boosting professional certifications you can be one of them. And you can earn while meeting Colorado CPA licensure requirements including
Accounting Ethics and Auditing Only three percent of adults have career-boosting professional certifications you can be one of them. And you can earn while meeting Colorado CPA licensure requirements including
SmarterMail v. Exchange: Admin Comparison
 SmarterMail v. Exchange: Admin Comparison Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2018 SmarterTools Inc. SmarterMail and Microsoft
SmarterMail v. Exchange: Admin Comparison Help Documentation This document was auto-created from web content and is subject to change at any time. Copyright (c) 2018 SmarterTools Inc. SmarterMail and Microsoft
a PennState A leader in online learning since 1998 Programs in Enterprise Architecture ~ World Campus A world of possibilities. Online.
 A leader in online learning since 1998 To learn more about programs in Enterprise Architecture, visit: worldcampus.psu.edu/psueabt Programs in Enterprise Architecture a PennState ~ World Campus A world
A leader in online learning since 1998 To learn more about programs in Enterprise Architecture, visit: worldcampus.psu.edu/psueabt Programs in Enterprise Architecture a PennState ~ World Campus A world
The office for the anywhere worker!!! Your LCB SOFTPHONE: A powerful new take on the all-in-one for a more immersive experience.
 The office for the anywhere worker!!! Your LCB SOFTPHONE: A powerful new take on the all-in-one for a more immersive experience. LCB SOFTPHONE FOR SALESFORCE Combine real-time communications and tracking
The office for the anywhere worker!!! Your LCB SOFTPHONE: A powerful new take on the all-in-one for a more immersive experience. LCB SOFTPHONE FOR SALESFORCE Combine real-time communications and tracking
HOW A CLOUD COMMUNICATIONS SYSTEM UNIQUELY SUPPORTS YOUR MOBILE WORKFORCE
 HOW A CLOUD COMMUNICATIONS SYSTEM UNIQUELY SUPPORTS YOUR MOBILE WORKFORCE Table of contents 3 How a UCaaS platform empowers your mobile workforce with a phone system and much more 4 6 11 A cloud phone
HOW A CLOUD COMMUNICATIONS SYSTEM UNIQUELY SUPPORTS YOUR MOBILE WORKFORCE Table of contents 3 How a UCaaS platform empowers your mobile workforce with a phone system and much more 4 6 11 A cloud phone
Announcement date: December 1, 2009 New program launch date: May 1, 2010
 Overview New Certified Management Accountant (CMA ) Certification Program Announcement date: December 1, 2009 New program launch date: May 1, 2010 Why did ICMA decide to update the curriculum and change
Overview New Certified Management Accountant (CMA ) Certification Program Announcement date: December 1, 2009 New program launch date: May 1, 2010 Why did ICMA decide to update the curriculum and change
BYOx at MacGregor SHS. Why Expand Digital Capabilities? Daymap
 BYOx - Information Handbook 2019 BYOx at MacGregor SHS BYOx is a program where students use a personally owned digital device within the MacGregor SHS network. The X stands for the device and all associated
BYOx - Information Handbook 2019 BYOx at MacGregor SHS BYOx is a program where students use a personally owned digital device within the MacGregor SHS network. The X stands for the device and all associated
WEB DESIGN SERVICES. Google Certified Partner. In-Studio Interactive CEO: Onan Bridgewater. instudiologic.com.
 In-Studio Interactive CEO: Onan Bridgewater instudiologic.com sales@instudiologic.com info@instudiologic.com WEB DESIGN SERVICES Google Certified Partner 1. Brand Building Engagements that Drive Sales
In-Studio Interactive CEO: Onan Bridgewater instudiologic.com sales@instudiologic.com info@instudiologic.com WEB DESIGN SERVICES Google Certified Partner 1. Brand Building Engagements that Drive Sales
IBM Security Systems. IBM X-Force 2012 & CISO Survey. Cyber Security Threat Landscape IBM Corporation IBM Corporation
 IBM X-Force 2012 & CISO Survey Cyber Security Threat Landscape 1 2012 IBM Corporation IBM X-Force 2011 Trend and Risk Report Highlights The mission of the IBM X-Force research and development team is to:
IBM X-Force 2012 & CISO Survey Cyber Security Threat Landscape 1 2012 IBM Corporation IBM X-Force 2011 Trend and Risk Report Highlights The mission of the IBM X-Force research and development team is to:
ROLE DESCRIPTION IT SPECIALIST
 ROLE DESCRIPTION IT SPECIALIST JOB IDENTIFICATION Job Title: Job Grade: Department: Location Reporting Line (This structure reports to?) Full-time/Part-time/Contract: IT Specialist D1 Finance INSETA Head
ROLE DESCRIPTION IT SPECIALIST JOB IDENTIFICATION Job Title: Job Grade: Department: Location Reporting Line (This structure reports to?) Full-time/Part-time/Contract: IT Specialist D1 Finance INSETA Head
Six steps to control the uncontrollable
 Six steps to control the uncontrollable Learn how to use Microsoft Enterprise Mobility Suite to protect cloud apps, manage devices, and guard against advanced threats today Introduction Employees today
Six steps to control the uncontrollable Learn how to use Microsoft Enterprise Mobility Suite to protect cloud apps, manage devices, and guard against advanced threats today Introduction Employees today
NEW ORLEANS, LOUISIANA MARCH 8-12, Employment Bureau Candidate Instructions
 NEW ORLEANS, LOUISIANA MARCH 8-12, 2015 Employment Bureau Candidate Instructions Welcome to the 2015 Employment Bureau (EB). Before you get started, please read the following important points. (This document
NEW ORLEANS, LOUISIANA MARCH 8-12, 2015 Employment Bureau Candidate Instructions Welcome to the 2015 Employment Bureau (EB). Before you get started, please read the following important points. (This document
Security Automation Best Practices
 WHITEPAPER Security Automation Best Practices A guide to making your security team successful with automation TABLE OF CONTENTS Introduction 3 What Is Security Automation? 3 Security Automation: A Tough
WHITEPAPER Security Automation Best Practices A guide to making your security team successful with automation TABLE OF CONTENTS Introduction 3 What Is Security Automation? 3 Security Automation: A Tough
The Value of Certification in the Wonderware Solution Provider Program. By Jay S. David, Senior Product Marketing Specialist
 The Value of Certification in the Wonderware Solution Provider Program By Jay S. David, Senior Product Marketing Specialist Table of Contents 1. The Advantages of Certification... 3 2. Demand for Wonderware
The Value of Certification in the Wonderware Solution Provider Program By Jay S. David, Senior Product Marketing Specialist Table of Contents 1. The Advantages of Certification... 3 2. Demand for Wonderware
A MODEL FOR COMPARATIVE ANALYSIS OF THE SIMILARITY BETWEEN ANDROID AND IOS OPERATING SYSTEMS
 Bulletin of the Transilvania University of Braşov Series V: Economic Sciences Vol. 7 (56) No. 2-2014 A MODEL FOR COMPARATIVE ANALYSIS OF THE SIMILARITY BETWEEN ANDROID AND IOS OPERATING SYSTEMS R. LIXĂNDROIU
Bulletin of the Transilvania University of Braşov Series V: Economic Sciences Vol. 7 (56) No. 2-2014 A MODEL FOR COMPARATIVE ANALYSIS OF THE SIMILARITY BETWEEN ANDROID AND IOS OPERATING SYSTEMS R. LIXĂNDROIU
Guide Series. How to upgrade to Microsoft Windows 10? Guide Series
 How to upgrade to Microsoft Windows 10? Acuutech All rights reserved 2016 1 Contents Introduction... 2 Why use Windows 10?... 3 What are the advantages of Windows 10?... 4 Windows 10 editions comparison...
How to upgrade to Microsoft Windows 10? Acuutech All rights reserved 2016 1 Contents Introduction... 2 Why use Windows 10?... 3 What are the advantages of Windows 10?... 4 Windows 10 editions comparison...
How Cisco IT Improved Development Processes with a New Operating Model
 How Cisco IT Improved Development Processes with a New Operating Model New way to manage IT investments supports innovation, improved architecture, and stronger process standards for Cisco IT By Patrick
How Cisco IT Improved Development Processes with a New Operating Model New way to manage IT investments supports innovation, improved architecture, and stronger process standards for Cisco IT By Patrick
Computer Information Systems
 Computer Information Systems Network Intranet, Local Area Networks (LANs), Wide Area Networks (WANs), Network Segments, Hardware, Software: Development Development Installation Testing Monitoring Maintenance
Computer Information Systems Network Intranet, Local Area Networks (LANs), Wide Area Networks (WANs), Network Segments, Hardware, Software: Development Development Installation Testing Monitoring Maintenance
BUSINESS 478. Section D400 CASE SYNOPSIS FOR: SAMSUNG
 BUSINESS 478 Section D400 CASE SYNOPSIS FOR: SAMSUNG Matthew Cheah Yu Liu Jacky Pan Louisa Qiu Date: March 21, 2013 INTRODUCTION History In 1938, Samsung was founded by Byung-Chull Lee as a small export
BUSINESS 478 Section D400 CASE SYNOPSIS FOR: SAMSUNG Matthew Cheah Yu Liu Jacky Pan Louisa Qiu Date: March 21, 2013 INTRODUCTION History In 1938, Samsung was founded by Byung-Chull Lee as a small export
Welcome to our Moodle site! What is Moodle?
 Welcome to our Moodle site! We are excited to introduce the use of this online e-learning platform in our "Get SMART FAST" Training Program! We believe the use of this virtual classroom and training format
Welcome to our Moodle site! We are excited to introduce the use of this online e-learning platform in our "Get SMART FAST" Training Program! We believe the use of this virtual classroom and training format
L E S S O N 1 Lesson objectives
 L E S S O N 1 Lesson objectives To gain an overview of the course and the topics to be covered To know how QuickBooks works and how you can get around in QuickBooks To learn common business terms used
L E S S O N 1 Lesson objectives To gain an overview of the course and the topics to be covered To know how QuickBooks works and how you can get around in QuickBooks To learn common business terms used
Debunking the Top 10 Cloud-Hosted Desktop Myths
 Debunking the Top 10 Cloud-Hosted Desktop Myths Page 1 Summary Desktops as a Service (DaaS) is the delivery of a virtual desktop offered as a hosted service by a service provider. DaaS has the potential
Debunking the Top 10 Cloud-Hosted Desktop Myths Page 1 Summary Desktops as a Service (DaaS) is the delivery of a virtual desktop offered as a hosted service by a service provider. DaaS has the potential
1. All of the following are examples of real security and privacy risks EXCEPT: A. hackers. B. spam. C. viruses. D. identity theft. 2.
 COMPUTER-BASED-OBJECTIVE-QUESTIONS www.mission2win.in 1. All of the following are examples of real security and privacy risks EXCEPT: A. hackers. B. spam. C. viruses. D. identity theft. 2. A process known
COMPUTER-BASED-OBJECTIVE-QUESTIONS www.mission2win.in 1. All of the following are examples of real security and privacy risks EXCEPT: A. hackers. B. spam. C. viruses. D. identity theft. 2. A process known
Agilent Connectivity Advances for Component Manufacturers. Product Note
 Agilent Connectivity Advances for Component Manufacturers Product Note Introduction Since the introduction of the IEEE 488 interface, computers have been used to control instrumentation and capture test
Agilent Connectivity Advances for Component Manufacturers Product Note Introduction Since the introduction of the IEEE 488 interface, computers have been used to control instrumentation and capture test
Lesson Plan. Course Title: Principles of Information Technology Session Title: Intro to Databases Lesson Duration: Varies dependent upon instructor
 Lesson Plan Course Title: Principles of Information Technology Session Title: Intro to Databases Lesson Duration: Varies dependent upon instructor Performance Objective: Upon completion of this lesson,
Lesson Plan Course Title: Principles of Information Technology Session Title: Intro to Databases Lesson Duration: Varies dependent upon instructor Performance Objective: Upon completion of this lesson,
Education and technology are two of our greatest social equalizers.
 Corporate Social Responsibility Education and technology are two of our greatest social equalizers. As the worldwide leader in networking, Cisco knows technology can be used to improve access to education.
Corporate Social Responsibility Education and technology are two of our greatest social equalizers. As the worldwide leader in networking, Cisco knows technology can be used to improve access to education.
CSC Introduction to Computers and Their Applications
 CSC 170 - Introduction to Computers and Their Applications Lecture 9 Software Essentials When searching for new software, it helps to have a framework of categories System Software Operating Systems For
CSC 170 - Introduction to Computers and Their Applications Lecture 9 Software Essentials When searching for new software, it helps to have a framework of categories System Software Operating Systems For
Intel (INTC) Analyst: Brian von Hein Jr. Fall Recommendation: SELL Target Price until (12/31/2015): $24.46
 Recommendation: SELL Target Price until (12/31/2015): $24.46 1. Reasons for the Recommendation Intel has been the markets leader in microprocessors for personal computers over the last decade. The industry
Recommendation: SELL Target Price until (12/31/2015): $24.46 1. Reasons for the Recommendation Intel has been the markets leader in microprocessors for personal computers over the last decade. The industry
WHOLESALE HOSTED CENTREX
 1 WE MAKE IT POSSIBLE CENTREX Taking communication into the cloud A complete, flexible hosted telephony and unified communications solution, helping you create a proposition that is unique. 2 CENTREX The
1 WE MAKE IT POSSIBLE CENTREX Taking communication into the cloud A complete, flexible hosted telephony and unified communications solution, helping you create a proposition that is unique. 2 CENTREX The
Presence and IM: Reduce Distractions and Increase Productivity
 Presence and IM: Reduce Distractions and Increase Productivity Table of Contents 1. Executive Summary... 1 2. Why Care About Presence and IM... 2 3. Avaya Presence and IM Strategy... 4 4. Avaya Presence
Presence and IM: Reduce Distractions and Increase Productivity Table of Contents 1. Executive Summary... 1 2. Why Care About Presence and IM... 2 3. Avaya Presence and IM Strategy... 4 4. Avaya Presence
Design Within Reach Re-Invents Its Digital Workplace with Egnyte
 Customer Success Design Within Reach Re-Invents Its Digital Workplace with Egnyte From Inspired Beginnings Design Within Reach (DWR) founder Rob Forbes started the company back in 1998 with a simple vision
Customer Success Design Within Reach Re-Invents Its Digital Workplace with Egnyte From Inspired Beginnings Design Within Reach (DWR) founder Rob Forbes started the company back in 1998 with a simple vision
Windows 7 Will Not Load On My Computer Says I'm
 Windows 7 Will Not Load On My Computer Says I'm There are various programs which will allow you to make a copy of your entire apply to my computer even though it does say it works for this issue in Windows
Windows 7 Will Not Load On My Computer Says I'm There are various programs which will allow you to make a copy of your entire apply to my computer even though it does say it works for this issue in Windows
SOFTWARE UNIT 1 PART B C O M P U T E R T E C H N O L O G Y ( S 1 O B J A N D O B J 3-2)
 SOFTWARE UNIT 1 PART B C O M P U T E R T E C H N O L O G Y ( S 1 O B J 2 2-3 A N D O B J 3-2) DIGITAL LITERACY STANDARD 1 OBJECTIVE 3 Explore and demonstrate understanding of managing operating systems
SOFTWARE UNIT 1 PART B C O M P U T E R T E C H N O L O G Y ( S 1 O B J 2 2-3 A N D O B J 3-2) DIGITAL LITERACY STANDARD 1 OBJECTIVE 3 Explore and demonstrate understanding of managing operating systems
Accountancy (ACCTCY) Accountancy (ACCTCY) 1
 Accountancy (ACCTCY) 1 Accountancy (ACCTCY) ACCTCY 2010: Introduction to Accounting Introduction to accounting for non-business majors. Emphasis on introducing students to business operations, as well
Accountancy (ACCTCY) 1 Accountancy (ACCTCY) ACCTCY 2010: Introduction to Accounting Introduction to accounting for non-business majors. Emphasis on introducing students to business operations, as well
Mobile Communication Device Contract Consolidation for State Agencies. Report to the Joint Legislative Oversight Committee on Information Technology
 Mobile Communication Device Contract Consolidation for State Agencies Report to the Joint Legislative Oversight Committee on Information Technology Chris Estes State Chief Information Officer November
Mobile Communication Device Contract Consolidation for State Agencies Report to the Joint Legislative Oversight Committee on Information Technology Chris Estes State Chief Information Officer November
2016 Summary Annual Report and Annual Meeting Documents
 2016 Summary Annual Report and 2017 Annual Meeting Documents To Our Shareholders We enter 2017 with confidence in a bright future ahead for CenturyLink. We are clear in our approach to the market: we
2016 Summary Annual Report and 2017 Annual Meeting Documents To Our Shareholders We enter 2017 with confidence in a bright future ahead for CenturyLink. We are clear in our approach to the market: we
CSC 170 Introduction to Computers and Their Applications. Computers
 CSC 170 Introduction to Computers and Their Applications Lecture #4 Digital Devices Computers At its core, a computer is a multipurpose device that accepts input, processes data, stores data, and produces
CSC 170 Introduction to Computers and Their Applications Lecture #4 Digital Devices Computers At its core, a computer is a multipurpose device that accepts input, processes data, stores data, and produces
7 Business Benefits of Moving from an On-Premise PBX to a Cloud Phone System
 White Paper 7 Business Benefits of Moving from an On-Premise PBX to a Cloud Phone System Tipping Points: Factors typically driving the transition from a legacy PBX to cloud VoIP For any number of reasons
White Paper 7 Business Benefits of Moving from an On-Premise PBX to a Cloud Phone System Tipping Points: Factors typically driving the transition from a legacy PBX to cloud VoIP For any number of reasons
Full file at
 Guide to MCSE 70-270, Second Edition, Enhanced 2-1 Chapter 2: Installing Windows XP Professional Objectives After reading this chapter and completing the exercises, you will be able to: Determine if an
Guide to MCSE 70-270, Second Edition, Enhanced 2-1 Chapter 2: Installing Windows XP Professional Objectives After reading this chapter and completing the exercises, you will be able to: Determine if an
Outline. Database Management Systems (DBMS) Database Management and Organization. IT420: Database Management and Organization
 Outline IT420: Database Management and Organization Dr. Crăiniceanu Capt. Balazs www.cs.usna.edu/~adina/teaching/it420/spring2007 Class Survey Why Databases (DB)? A Problem DB Benefits In This Class? Admin
Outline IT420: Database Management and Organization Dr. Crăiniceanu Capt. Balazs www.cs.usna.edu/~adina/teaching/it420/spring2007 Class Survey Why Databases (DB)? A Problem DB Benefits In This Class? Admin
LECTURE SCHEDULE 2. Units of Memory, Hardware, Software and Classification of Computers
 LECTURE SCHEDULE 2 Units of Memory, Hardware, Software and Classification of Computers Units of Memory The memory unit is the principal storage of the computer. All the data and instructions that the computer
LECTURE SCHEDULE 2 Units of Memory, Hardware, Software and Classification of Computers Units of Memory The memory unit is the principal storage of the computer. All the data and instructions that the computer
Murray Bridge High School Connecting to the BYOD Network Mac OS X Version 3 Amended 2/10/2014
 Murray Bridge High School Connecting to the BYOD Network Mac OS X 10.7 10.9 Version 3 Amended 2/10/2014 Use of the Murray Bridge High School BYOD (Bring Your Own Device) facilities and network is subject
Murray Bridge High School Connecting to the BYOD Network Mac OS X 10.7 10.9 Version 3 Amended 2/10/2014 Use of the Murray Bridge High School BYOD (Bring Your Own Device) facilities and network is subject
