APWG Global Phishing Survey 2H2010
|
|
|
- Carmella Ward
- 5 years ago
- Views:
Transcription
1 APWG Global Phishing Survey 2H2010 Rod Rasmussen Greg Aaron June 21, 2011
2 Goals Study domain names and URLs to: Provide a consistent benchmark for scope of phishing problems worldwide Understand what phishers are doing Identify new trends Find hot-spots and success stories Suggest anti-abuse measures
3 Data Set Comprehensive sources: APWG, phishing feeds, private sources, honeypots Millions of phishing URLs small number of domain names and attacks. Total of 205,715,855 domain names in the TLDs we have stats for ~ 99.5% of domain names in the world.
4 Basic Statistics 2H2010 1H2010 2H2009 1H2009 2H2008 Phishing domain names 42,624 28,646 28,775 30,131 30,454 Attacks 67,677 48, ,697 55,698 56,959 TLDs used IP-based phish (unique IPs) Maliciously registered domains 2,318 2,018 2,031 3,563 2,809 11,769 4,755 6,372 4,382 5,591 IDN domains
5 Phishing in China Data contribution from CNNIC and APAC (Anti- Phishing Alliance of China) Observers outside of China were detecting only about 20% of the phishing that targeted Chinese institutions. Attacks on Chinese banks, e-commerce sites. Lures: Chinese-language s, Chinese instant message services WHOIS: registrants often listed in China, and list Chinese fre services such as QQ.com
6 Phishing in China 2H2010: 12,282 attacks on Chinese institutions, using 6,382 unique domain names. (That s 18% of all attacks worldwide) 74% of those attacks targeted Taobao.com Few.CN names used. CN registration policy became very restrictive in December Only 278.CN names used in 2H2010, some hacked. Phishers simply switched to using other resources to phish Chinese targets: Used 4,737 free CO.CC subdomains Used large numbers of.com,.tk,.info,.us,.in domains Chinese phishers prefer to register domain names only 8% looked hacked.
7 84:00:00 Phishing Site Uptime 2H2010: 73 hours average, 15:19 hours median Phishing Site Uptimes (HH:MM:SS) 72:00:00 60:00:00 48:00:00 36:00:00 Average Median 24:00:00 12:00:00 0:00:00 1H2008 2H2008 1H2009 2H2009 1H2010 2H2010
8 Why So High? Absence of Avalanche domains There were 4,963 phishing attacks using free CO.CC subdomains. Their median uptime was almost 60 hours compared with 15:19 hours for all phish. Don t know the uptimes for the phish uniquely recorded by CNNIC/APAC
9 cctld Uptimes (HH:MM:SS) 216:00:00 cctlds Average Phishing Uptimes 2H2010 (HH:MM:SS) 192:00:00 168:00:00 144:00:00 120:00:00 96:00:00 72:00:00 48:00:00.CC.TK.BR.UK.RU.FR ALL TLDs 24:00:00 00:00:00 Jul Aug Sep Oct Nov Dec
10 gtld Uptimes (HH:MM:SS) 144:00:00 gtlds Average Phishing Uptimes 2H2010 (HH:MM:SS) 120:00:00 96:00:00 72:00:00 48:00:00.COM.NET.ORG.INFO.BIZ ALL TLDs 24:00:00 00:00:00 Jul Aug Sep Oct Nov Dec
11 Phishing Rates by TLD: roughly proportional by TLD size All Phishing Attacks, by TLD 2H2010.fr 1,4%.uk 2,5%.ru 1,6% Other (174) 20,9%.com 41,4%.info 2,8%.tk 3,7%.br 2,9%.net 7,2%.cc 7,3%.org 4,0% IP Based 4,5%
12 Phishing by TLD: Score Metric: Phishing Domains per 10,000 Measures prevalence of phishing in a TLD Median score: 3.2.COM score: 2.1 Scores between 2.1 and 3.2 are normal Scores skew higher for smaller TLDs. Metric: Attacks per 10,000 Domains
13 Top TLDs by Domain Score (minimum 30,000 domains and 25 phish) RANK TLD TLD Location # Unique Phishing attacks 2H2010 Unique Domain Names used for phishing 2H2010 Domains in registry Oct 2010 Score: Phish per 10,000 domains 2H2010 Score: Attacks per 10,000 domains 2H TH Thailand , IR Iran , MA Morocco , IE Ireland , TK Tokelau 2,533 2,429 4,030, (tie).kz Kazakhstan , (tie).cc Cocos (Keeling) Islands 4, ,000 (estimated) IN India , MY Malaysia , HU Hungary ,
14 Malicious Domain Registrations Of the 42,624 phishing domains: ~72% were compromised/hacked ~28% were registered by phishers (11,769). Most of those domains (6,382) were registered to attack Chinese targets. 9% of domains (1,503) contained a relevant brand name or brand misspelling. (Especially Taobao.com)
15 2,066 maliciously registered domains targeted WarCraft and Battle.net
16 Use of Subdomain Services <customer_name>.<provider>.tld Use of these services by phishers almost doubled in 2H2010, to 11,768 subdomains. If we counted these unique subdomains as regular domain names, they would represent 22% of all domains used for phishing. 40% of phishing subdomains were on CO.CC
17 Subdomain Service Phish Select Subdomain Reseller Phish, 2H ~ ~ Jul Aug Sep Oct Nov Dec co.cc t35.com 110mb.com altervista.org yourfreehosting.net hdfree.com.br tripod.com
18 Phish Count Jan '09 URL Shorteners URL Shortener Phish 1H2009-2H2010 Feb Mar Apr May Jun Jul Aug Sep Oct Nov Dec Jan '10 Unique Phish Feb Mar Apr May Jun Jul Aug Sep Oct Nov Dec
19 Virtual Hosts 600 Virtual Host Phish 1H2009-2H Phish Count Jan '09 Feb Mar Apr May Jun Jul Aug Sep Oct Nov Dec Jan '10 Feb Mar Apr May Jun Jul Aug Sep Oct Nov Dec Unique Phish
20 Internationalized Domain Names (IDNs) In last three years, we have only found two homographic attacks. July 12, 2010: = 36 new IDN TLDs have been approved Russian Federation:.РФ (.RF in Cyrillic,.xn--p1ai)
21 Conclusions Clamp down in one place and the problems simply move elsewhere. Free services like CO.CC and.tk are being abused heavily by phishers. Subdomain services are as big a problem as the registration of regular domain names. Uptimes got higher watch out!
22 APWG Global Phishing Survey 2H2010 Thank You! For more information or data for your TLD: Rod Rasmussen rod.rasmussen <at> internetidentity.co Greg Aaron gaaron <at> afilias.info
Global Phishing Survey 2H2009
 Global Phishing Survey 2H2009 Greg Aaron Rod Rasmussen Released May 11, 2010 http://apwg.org/reports/apwg_globalphishingsurvey_2h2009.pdf Goals Study domain names and URLs to: Provide a consistent benchmark
Global Phishing Survey 2H2009 Greg Aaron Rod Rasmussen Released May 11, 2010 http://apwg.org/reports/apwg_globalphishingsurvey_2h2009.pdf Goals Study domain names and URLs to: Provide a consistent benchmark
Global Phishing Survey: Trends and Domain Name Use in 1H2011
 Global Phishing Survey: Trends and Domain Name Use in January-June 2011 Unifying the Global Response To Cybercrime November 2011 An APWG Industry Advisory 1 Published November 7, 2011 Authors: Rod Rasmussen
Global Phishing Survey: Trends and Domain Name Use in January-June 2011 Unifying the Global Response To Cybercrime November 2011 An APWG Industry Advisory 1 Published November 7, 2011 Authors: Rod Rasmussen
Anti-Phishing Working Group
 Anti-Phishing Working Group www.antiphishing.org Fall 2008 Phishing Update ICANN ccnso Cairo, Egypt, November 5, 2008 Rod Rasmussen Co-Chair Internet Policy Committee of the APWG President & CTO, Internet
Anti-Phishing Working Group www.antiphishing.org Fall 2008 Phishing Update ICANN ccnso Cairo, Egypt, November 5, 2008 Rod Rasmussen Co-Chair Internet Policy Committee of the APWG President & CTO, Internet
Improving Domain Names Utilization
 Improving Domain Names Utilization Ning Kong June 27, 2017 Content Status Quo of Chinese Phishing Websites Anti-Phishing Alliance of China (APAC) Suggestions for Improving Domain Names Utilization Q &
Improving Domain Names Utilization Ning Kong June 27, 2017 Content Status Quo of Chinese Phishing Websites Anti-Phishing Alliance of China (APAC) Suggestions for Improving Domain Names Utilization Q &
RDAP Implementation. Francisco Arias & Gustavo Lozano 21 October 2015
 RDAP Implementation Francisco Arias & Gustavo Lozano 21 October 2015 Agenda 1 2 3 History of Replacing WHOIS protocol gtld RDAP Profile RDAP Profile Details 4 5 Open Issues gtld RDAP Profile Conclusion
RDAP Implementation Francisco Arias & Gustavo Lozano 21 October 2015 Agenda 1 2 3 History of Replacing WHOIS protocol gtld RDAP Profile RDAP Profile Details 4 5 Open Issues gtld RDAP Profile Conclusion
Briefing on Handling of Phishing Websites in November 2017
 Briefing on Handling of Phishing Websites in Secretariat of APAC December 2017 Contents 1 Overview... 3 2 Analysis of Handling Types... 3 2.1 Sources of reports about phishing websites... 3 2.2 Distribution
Briefing on Handling of Phishing Websites in Secretariat of APAC December 2017 Contents 1 Overview... 3 2 Analysis of Handling Types... 3 2.1 Sources of reports about phishing websites... 3 2.2 Distribution
August 2009 Report #22
 August 2009 Report #22 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This report
August 2009 Report #22 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This report
Report on Spamvertising and Phishing using.hk Domain Names and McAfee Report. ccnso Meeting June 24, 2008
 Report on Spamvertising and Phishing using.hk Domain Names and McAfee Report ccnso Meeting June 24, 2008 Agenda Introduction of HKIRC/HKDNR and.hk Domain Figure of Phishing and Spamvertising Common Patterns
Report on Spamvertising and Phishing using.hk Domain Names and McAfee Report ccnso Meeting June 24, 2008 Agenda Introduction of HKIRC/HKDNR and.hk Domain Figure of Phishing and Spamvertising Common Patterns
APTLD & MYNIC JOINT SURVEY
 INTERNET SECURITY & CCTLDS SURVEY RESULTS 24 th June 2008, Tuesday ccnso meeting, Paris, France Survey Objectives Survey Summary:- For APTLD members to examine the roles and responsibilities of cctlds
INTERNET SECURITY & CCTLDS SURVEY RESULTS 24 th June 2008, Tuesday ccnso meeting, Paris, France Survey Objectives Survey Summary:- For APTLD members to examine the roles and responsibilities of cctlds
COURSE LISTING. Courses Listed. with SAP Hybris Marketing Cloud. 24 January 2018 (23:53 GMT) HY760 - SAP Hybris Marketing Cloud
 with SAP Hybris Marketing Cloud Courses Listed HY760 - SAP Hybris Marketing Cloud C_HYMC_1702 - SAP Certified Technology Associate - SAP Hybris Marketing Cloud (1702) Implementation Page 1 of 12 All available
with SAP Hybris Marketing Cloud Courses Listed HY760 - SAP Hybris Marketing Cloud C_HYMC_1702 - SAP Certified Technology Associate - SAP Hybris Marketing Cloud (1702) Implementation Page 1 of 12 All available
Next Steps for WHOIS Accuracy Global Domains Division. ICANN June 2015
 Next Steps for WHOIS Accuracy Global Domains Division ICANN 53 24 June 2015 Agenda: Next Steps for WHOIS Accuracy Reporting System 1 2 3 Introduction and Implementation Approach Pilot Project and Lessons
Next Steps for WHOIS Accuracy Global Domains Division ICANN 53 24 June 2015 Agenda: Next Steps for WHOIS Accuracy Reporting System 1 2 3 Introduction and Implementation Approach Pilot Project and Lessons
ThaiCERT Incident Response & Phishing cases in Thailand. By Kitisak Jirawannakool Thai Computer Emergency Response team (ThaiCERT)
 ThaiCERT Incident Response & Phishing cases in Thailand By Kitisak Jirawannakool Thai Computer Emergency Response team (ThaiCERT) Agenda About ThaiCERT ThaiCERT IR Phishing in Thailand About ThaiCERT Ministry
ThaiCERT Incident Response & Phishing cases in Thailand By Kitisak Jirawannakool Thai Computer Emergency Response team (ThaiCERT) Agenda About ThaiCERT ThaiCERT IR Phishing in Thailand About ThaiCERT Ministry
Annex A to the DVD-R Disc and DVD-RW Disc Patent License Agreement Essential Sony Patents relevant to DVD-RW Disc
 Annex A to the DVD-R Disc and DVD-RW Disc Patent License Agreement Essential Sony Patents relevant to DVD-RW Disc AT-EP S95P0391 1103087.1 09-Feb-01 1126619 8/16 Modulation AT-EP S95P0391 1120568.9 29-Aug-01
Annex A to the DVD-R Disc and DVD-RW Disc Patent License Agreement Essential Sony Patents relevant to DVD-RW Disc AT-EP S95P0391 1103087.1 09-Feb-01 1126619 8/16 Modulation AT-EP S95P0391 1120568.9 29-Aug-01
December 2009 Report #26
 December 2009 Report #26 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This
December 2009 Report #26 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This
Monthly SEO Report. Example Client 16 November 2012 Scott Lawson. Date. Prepared by
 Date Monthly SEO Report Prepared by Example Client 16 November 212 Scott Lawson Contents Thanks for using TrackPal s automated SEO and Analytics reporting template. Below is a brief explanation of the
Date Monthly SEO Report Prepared by Example Client 16 November 212 Scott Lawson Contents Thanks for using TrackPal s automated SEO and Analytics reporting template. Below is a brief explanation of the
This report is based on sampled data. Jun 1 Jul 6 Aug 10 Sep 14 Oct 19 Nov 23 Dec 28 Feb 1 Mar 8 Apr 12 May 17 Ju
 0 - Total Traffic Content View Query This report is based on sampled data. Jun 1, 2009 - Jun 25, 2010 Comparing to: Site 300 Unique Pageviews 300 150 150 0 0 Jun 1 Jul 6 Aug 10 Sep 14 Oct 19 Nov 23 Dec
0 - Total Traffic Content View Query This report is based on sampled data. Jun 1, 2009 - Jun 25, 2010 Comparing to: Site 300 Unique Pageviews 300 150 150 0 0 Jun 1 Jul 6 Aug 10 Sep 14 Oct 19 Nov 23 Dec
Contractual Compliance Update. Contractual Compliance ICANN 57 5 November 2016
 Contractual Compliance Update Contractual Compliance ICANN 57 5 November 2016 Agenda Brief Update Since ICANN 55 Registrar Compliance Update Registry Compliance Update Contractual Compliance Audit Activities
Contractual Compliance Update Contractual Compliance ICANN 57 5 November 2016 Agenda Brief Update Since ICANN 55 Registrar Compliance Update Registry Compliance Update Contractual Compliance Audit Activities
TLD-OPS Standing Committee Meeting cctld Security and Stability Together
 Meeting cctld Security and Stability Together October 31, 2017 ICANN60, Abu Dhabi Jacques Latour,.ca (Chair) Agenda TLD-OPS Meeting @ ICANN60, Oct 29, 2017 1. Opening and welcome (Jacques) 2. TLD-OPS introduction
Meeting cctld Security and Stability Together October 31, 2017 ICANN60, Abu Dhabi Jacques Latour,.ca (Chair) Agenda TLD-OPS Meeting @ ICANN60, Oct 29, 2017 1. Opening and welcome (Jacques) 2. TLD-OPS introduction
Program Update. Contractual Compliance ICANN March 2017
 Program Update Contractual Compliance ICANN 58 13 March 2017 Agenda Brief Update Since ICANN 57 Registrar Compliance Update Registry Compliance Update Contractual Compliance Audit Update Questions & Answers
Program Update Contractual Compliance ICANN 58 13 March 2017 Agenda Brief Update Since ICANN 57 Registrar Compliance Update Registry Compliance Update Contractual Compliance Audit Update Questions & Answers
The Insider s Guide To Transfers. John Sweeting - Senior Director, Registration Services Cathy Clements Transfer Services Manager
 The Insider s Guide To Transfers John Sweeting - Senior Director, Registration Services Cathy Clements Transfer Services Manager Overview Transfer Basics M&A Transfer Procedure & Tips Specified Recipient
The Insider s Guide To Transfers John Sweeting - Senior Director, Registration Services Cathy Clements Transfer Services Manager Overview Transfer Basics M&A Transfer Procedure & Tips Specified Recipient
NOT PROTECTIVELY MARKED PHISHING. July 2016
 - PHISHING July 2016 1 Introduction: The purpose of this document is to provide an analysis of the most prevalent trends and characteristics of phishing campaigns in the UK in July 2016. The analysis is
- PHISHING July 2016 1 Introduction: The purpose of this document is to provide an analysis of the most prevalent trends and characteristics of phishing campaigns in the UK in July 2016. The analysis is
Intellectual Property Constituency (IPC)
 Contractual Compliance Intellectual Property Constituency (IPC) Tuesday, 14 October 2014 Agenda Registrar Related Update since ICANN 50 Registry Related Update since ICANN 50 Audit Programs Update Questions
Contractual Compliance Intellectual Property Constituency (IPC) Tuesday, 14 October 2014 Agenda Registrar Related Update since ICANN 50 Registry Related Update since ICANN 50 Audit Programs Update Questions
Anti-Phishing Working Group
 Anti-Phishing Working Group www.antiphishing.org DNS Policy Sub-Committee Overview Rod Rasmussen Rod.Rasmussen@InternetIdentity.com Anti-Phishing Working Group Launched in 2003 2600+ members 1600+ companies
Anti-Phishing Working Group www.antiphishing.org DNS Policy Sub-Committee Overview Rod Rasmussen Rod.Rasmussen@InternetIdentity.com Anti-Phishing Working Group Launched in 2003 2600+ members 1600+ companies
Bank of america report phishing
 Search Search pages & people Search Search Search pages & people Search Bank of america report phishing email We recently discovered a new phishing scam from a Bank of America spam email some reports that
Search Search pages & people Search Search Search pages & people Search Bank of america report phishing email We recently discovered a new phishing scam from a Bank of America spam email some reports that
All King County Summary Report
 September, 2016 MTD MARKET UPDATE Data Current Through: September, 2016 18,000 16,000 14,000 12,000 10,000 8,000 6,000 4,000 2,000 0 Active, Pending, & Months Supply of Inventory 15,438 14,537 6.6 6.7
September, 2016 MTD MARKET UPDATE Data Current Through: September, 2016 18,000 16,000 14,000 12,000 10,000 8,000 6,000 4,000 2,000 0 Active, Pending, & Months Supply of Inventory 15,438 14,537 6.6 6.7
WHOIS Accuracy Reporting System (ARS): Phase 2 Cycle 1 Results Webinar 12 January ICANN GDD Operations NORC at the University of Chicago
 WHOIS Accuracy Reporting System (ARS): Phase 2 Cycle 1 Results Webinar 12 January 2016 ICANN GDD Operations NORC at the University of Chicago Webinar Agenda 1 2 3 WHOIS ARS Background Phase 2 Cycle 1:
WHOIS Accuracy Reporting System (ARS): Phase 2 Cycle 1 Results Webinar 12 January 2016 ICANN GDD Operations NORC at the University of Chicago Webinar Agenda 1 2 3 WHOIS ARS Background Phase 2 Cycle 1:
Japan s Measures against Spam
 June 22, 2, 2006 Japan s Measures against Spam Yoshichika Imaizumi Telecommunications Bureau, Ministry of Internal Affairs and Communications (MIC), Japan Characteristics of spam in Japan 1.. Media 2004
June 22, 2, 2006 Japan s Measures against Spam Yoshichika Imaizumi Telecommunications Bureau, Ministry of Internal Affairs and Communications (MIC), Japan Characteristics of spam in Japan 1.. Media 2004
Computer
 2011-2014 Computer 2014.12. Contents 1. 2011-2013 China Computer Export Trend Analysis... 3 1.1. 2011-2013 China Computer Export Quantity Trend Analysis... 3 1.2. 2011-2013 China Computer Export Amount
2011-2014 Computer 2014.12. Contents 1. 2011-2013 China Computer Export Trend Analysis... 3 1.1. 2011-2013 China Computer Export Quantity Trend Analysis... 3 1.2. 2011-2013 China Computer Export Amount
Asia Key Economic and Financial Indicators
 ASEAN Brunei (BN) Cambodia (KH) Indonesia () Laos (LA) Malaysia () Myanmar (MM) Philippines () Singapore () Thailand () Vietnam () East Asia China (CN) Hong Kong (HK) Japan (JP) South Korea (KR) Taiw an
ASEAN Brunei (BN) Cambodia (KH) Indonesia () Laos (LA) Malaysia () Myanmar (MM) Philippines () Singapore () Thailand () Vietnam () East Asia China (CN) Hong Kong (HK) Japan (JP) South Korea (KR) Taiw an
Asia Key Economic and Financial Indicators
 ASEAN Brunei (BN) Cambodia (KH) Indonesia () Laos (LA) Malaysia () Myanmar (MM) Philippines () Singapore () Thailand () Vietnam () East Asia China (CN) Hong Kong (HK) Japan (JP) South Korea (KR) Taiw an
ASEAN Brunei (BN) Cambodia (KH) Indonesia () Laos (LA) Malaysia () Myanmar (MM) Philippines () Singapore () Thailand () Vietnam () East Asia China (CN) Hong Kong (HK) Japan (JP) South Korea (KR) Taiw an
October 2009 Report #24
 October 2009 Report #24 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This report
October 2009 Report #24 The data in this report is aggregated from a combination of sources including Symantec s Phish Report Network (PRN), strategic partners, customers and security solutions. This report
Asks for clarification of whether a GOP must communicate to a TOP that a generator is in manual mode (no AVR) during start up or shut down.
 # Name Duration 1 Project 2011-INT-02 Interpretation of VAR-002 for Constellation Power Gen 185 days Jan Feb Mar Apr May Jun Jul Aug Sep O 2012 2 Start Date for this Plan 0 days 3 A - ASSEMBLE SDT 6 days
# Name Duration 1 Project 2011-INT-02 Interpretation of VAR-002 for Constellation Power Gen 185 days Jan Feb Mar Apr May Jun Jul Aug Sep O 2012 2 Start Date for this Plan 0 days 3 A - ASSEMBLE SDT 6 days
THE AUSTRALIAN ONLINE LANDSCAPE REVIEW JULY 2015
 THE AUSTRALIAN ONLINE LANDSCAPE REVIEW JULY 2015 STATE OF THE ONLINE LANDSCAPE July 2015 Welcome to the July 2015 edition of Nielsen s Online Landscape Review. The online landscape in July saw Australians
THE AUSTRALIAN ONLINE LANDSCAPE REVIEW JULY 2015 STATE OF THE ONLINE LANDSCAPE July 2015 Welcome to the July 2015 edition of Nielsen s Online Landscape Review. The online landscape in July saw Australians
Korea Phishing Activity Trends Report
 Korea Phishing Activity Trends Report June, 2006 Issued by KrCERT/CC, Korea Internet Security Center Korea Phishing Activity Trends Report analyzes phishing attacks reported to KrCERT/CC via the organization
Korea Phishing Activity Trends Report June, 2006 Issued by KrCERT/CC, Korea Internet Security Center Korea Phishing Activity Trends Report analyzes phishing attacks reported to KrCERT/CC via the organization
Seattle (NWMLS Areas: 140, 380, 385, 390, 700, 701, 705, 710) Summary
 September, 2016 MTD MARKET UPDATE Data Current Through: September, 2016 (NWMLS Areas: 140, 380, 385, 390,, 701, 705, 710) Summary Active, Pending, & Months Supply of Inventory 5,000 4,500 4,000 3,500 4,091
September, 2016 MTD MARKET UPDATE Data Current Through: September, 2016 (NWMLS Areas: 140, 380, 385, 390,, 701, 705, 710) Summary Active, Pending, & Months Supply of Inventory 5,000 4,500 4,000 3,500 4,091
Compliance Outreach Wednesday, 26 March 2014
 ICANN Contractual Compliance Compliance Outreach Wednesday, 26 March 2014 1 Agenda General Update 2013 RAA Discussion and Clarification New Registry Agreement Update Question & Answer Session Contractual
ICANN Contractual Compliance Compliance Outreach Wednesday, 26 March 2014 1 Agenda General Update 2013 RAA Discussion and Clarification New Registry Agreement Update Question & Answer Session Contractual
software.sci.utah.edu (Select Visitors)
 software.sci.utah.edu (Select Visitors) Web Log Analysis Yearly Report 2002 Report Range: 02/01/2002 00:00:0-12/31/2002 23:59:59 www.webtrends.com Table of Contents Top Visitors...3 Top Visitors Over Time...5
software.sci.utah.edu (Select Visitors) Web Log Analysis Yearly Report 2002 Report Range: 02/01/2002 00:00:0-12/31/2002 23:59:59 www.webtrends.com Table of Contents Top Visitors...3 Top Visitors Over Time...5
Seattle (NWMLS Areas: 140, 380, 385, 390, 700, 701, 705, 710) Summary
 October, 2016 MTD MARKET UPDATE Data Current Through: October, 2016 (NWMLS Areas: 140, 380, 385, 390,, 701, 705, 710) Summary Active, Pending, & Months Supply of Inventory 4,500 4,000 3,500 4,197 4,128
October, 2016 MTD MARKET UPDATE Data Current Through: October, 2016 (NWMLS Areas: 140, 380, 385, 390,, 701, 705, 710) Summary Active, Pending, & Months Supply of Inventory 4,500 4,000 3,500 4,197 4,128
Security, For DNS and by DNS. ZHOU Yonglin Beijing, Nov 009
 Security, For DNS and by DNS ZHOU Yonglin Beijing, Nov 009 DNS and Security FOR DNS SECURITY BY DNS SECURITY, FOR DNS DNS attack Handling Vulnerability Handling DNS Monitoring 5.19 Storm Gate : Attack
Security, For DNS and by DNS ZHOU Yonglin Beijing, Nov 009 DNS and Security FOR DNS SECURITY BY DNS SECURITY, FOR DNS DNS attack Handling Vulnerability Handling DNS Monitoring 5.19 Storm Gate : Attack
ICANN PacNOG 11
 ICANN Update @ PacNOG 11 Savenaca Vocea Nadi, 2 June 2012 The mission of The Internet Corporation for Assigned Names and Numbers ("ICANN ) To coordinate, at the overall level, the global Internet's systems
ICANN Update @ PacNOG 11 Savenaca Vocea Nadi, 2 June 2012 The mission of The Internet Corporation for Assigned Names and Numbers ("ICANN ) To coordinate, at the overall level, the global Internet's systems
Contractual Compliance
 Contractual Compliance Registrars Outreach Thursday, 26 Jun 2014 Agenda General Update Quality process to periodically confirm compliance for suspended domains related to Whois Inaccuracy complaints Compliance
Contractual Compliance Registrars Outreach Thursday, 26 Jun 2014 Agenda General Update Quality process to periodically confirm compliance for suspended domains related to Whois Inaccuracy complaints Compliance
Seattle (NWMLS Areas: 140, 380, 385, 390, 700, 701, 705, 710) Summary
 November, 2016 MTD MARKET UPDATE Data Current Through: November, 2016 (NWMLS Areas: 140, 380, 385, 390,, 701, 705, 710) Summary 4,000 3,500 3,000 2,500 2,000 1,500 1,000 500 0 Active, Pending, & Months
November, 2016 MTD MARKET UPDATE Data Current Through: November, 2016 (NWMLS Areas: 140, 380, 385, 390,, 701, 705, 710) Summary 4,000 3,500 3,000 2,500 2,000 1,500 1,000 500 0 Active, Pending, & Months
New Listings. Bullock Russell Market Area. 300 Jan Feb Mar Apr May Jun Jul Aug Sep Oct Nov Dec
 New Listings Bullock Russell Market Area 1200 1100 1000 900 800 700 600 500 400 300 Jan Feb Mar Apr May Jun Jul Aug Sep Oct Nov Dec 2014 2015 2016 2017 2018 Closed Sales Bullock Russell Market Area 1000
New Listings Bullock Russell Market Area 1200 1100 1000 900 800 700 600 500 400 300 Jan Feb Mar Apr May Jun Jul Aug Sep Oct Nov Dec 2014 2015 2016 2017 2018 Closed Sales Bullock Russell Market Area 1000
CBERS-2. Attitude Control and its Effects on Image Geometric Correction. Follow up to TCM-06 INPE CBERS TEAM
 CBERS-2 Attitude Control and its Effects on Image Geometric Correction Follow up to TCM-06 INPE CBERS TEAM Topics for discussion Known issues about CBERS-2 attitude data Transmitted attitude angles are
CBERS-2 Attitude Control and its Effects on Image Geometric Correction Follow up to TCM-06 INPE CBERS TEAM Topics for discussion Known issues about CBERS-2 attitude data Transmitted attitude angles are
BANGLADESH UNIVERSITY OF PROFESSIONALS ACADEMIC CALENDAR FOR MPhil AND PHD PROGRAM 2014 (4 TH BATCH) PART I (COURSE WORK)
 BANGLADESH UNIVERSITY OF PROFESSIONALS ACADEMIC CALENDAR FOR MPhil AND PHD PROGRAM 2014 (4 TH BATCH) DAY Soci-Economic and Political History of Bangladesh PART I (COURSE WORK) 1 ST SEMESTER 2 ND SEMESTER
BANGLADESH UNIVERSITY OF PROFESSIONALS ACADEMIC CALENDAR FOR MPhil AND PHD PROGRAM 2014 (4 TH BATCH) DAY Soci-Economic and Political History of Bangladesh PART I (COURSE WORK) 1 ST SEMESTER 2 ND SEMESTER
DMARC Continuing to enable trust between brand owners and receivers
 DMARC Continuing to enable trust between brand owners and receivers February 2014 1 DMARC Defined DMARC stands for: Domain-based Message Authentication, Reporting & Conformance (pronounced dee-mark ) 2
DMARC Continuing to enable trust between brand owners and receivers February 2014 1 DMARC Defined DMARC stands for: Domain-based Message Authentication, Reporting & Conformance (pronounced dee-mark ) 2
Privacy and Proxy Service Provider Accreditation. ICANN58 Working Meeting 11 March 2017
 Privacy and Proxy Service Provider Accreditation ICANN58 Working Meeting 11 March 2017 Agenda 13:45-15:00 15:00-15:15 15:15-16:45 Timeline Check; Policy Document Update; Third- Party Requests Break PSWG
Privacy and Proxy Service Provider Accreditation ICANN58 Working Meeting 11 March 2017 Agenda 13:45-15:00 15:00-15:15 15:15-16:45 Timeline Check; Policy Document Update; Third- Party Requests Break PSWG
Update on ICANN Domain Name Registrant Work
 1 Update on ICANN Domain Name Registrant Work Brian Gutterman Registrant Program Manager GDD Strategic Programs ICANN60 1 November 2017 2 Agenda Focus on Registrants Service and Information Domain Name
1 Update on ICANN Domain Name Registrant Work Brian Gutterman Registrant Program Manager GDD Strategic Programs ICANN60 1 November 2017 2 Agenda Focus on Registrants Service and Information Domain Name
No domain left behind
 No domain left behind is Let s Encrypt democratizing encryption? M Aertsen 1, M Korzyński 2, G Moura 3 1 National Cyber Security Centre The Netherlands 2 Delft University of Technology The Netherlands
No domain left behind is Let s Encrypt democratizing encryption? M Aertsen 1, M Korzyński 2, G Moura 3 1 National Cyber Security Centre The Netherlands 2 Delft University of Technology The Netherlands
SURBL-Listed Domains And Their Registrars (In Just Seven or Eight Minutes)
 SURBL-Listed Domains And Their Registrars (In Just Seven or Eight Minutes) Joe St Sauver, Ph.D. (joe@uoregon.edu or joe@internet2.edu) Forum on DNS Abuse Grand Ballroom, 14 Mar 2011 11:30-13:00 ICANN 40,
SURBL-Listed Domains And Their Registrars (In Just Seven or Eight Minutes) Joe St Sauver, Ph.D. (joe@uoregon.edu or joe@internet2.edu) Forum on DNS Abuse Grand Ballroom, 14 Mar 2011 11:30-13:00 ICANN 40,
IDN query trends seen at JP and Root. Kazunori Fujiwara, JPRS 2016/4/3, IEPG meeting
 IDN query trends seen at JP and Root Kazunori Fujiwara, JPRS fujiwara@jprs.co.jp 2016/4/3, IEPG meeting Is IDN use increasing? It is said that IDN is important for non- English speakers IDN implementations
IDN query trends seen at JP and Root Kazunori Fujiwara, JPRS fujiwara@jprs.co.jp 2016/4/3, IEPG meeting Is IDN use increasing? It is said that IDN is important for non- English speakers IDN implementations
Phishing Activity Trends Report. 3 rd Quarter Unifying the. Global Response To Cybercrime. July September 2012
 3 rd Quarter 2012 Unifying the Global Response To Cybercrime July September 2012 Published February 1, 2013 , Phishing Report Scope The APWG analyzes phishing attacks reported to the APWG by its member
3 rd Quarter 2012 Unifying the Global Response To Cybercrime July September 2012 Published February 1, 2013 , Phishing Report Scope The APWG analyzes phishing attacks reported to the APWG by its member
Company Snapshot. $ million $2.46 billion 39% 52% $418.5 million
 Safe Harbor This presentation contains statements of a forward-looking nature. These statements are made under the safe harbor provisions of the U.S. Private Securities Litigation Reform Act of 1995. You
Safe Harbor This presentation contains statements of a forward-looking nature. These statements are made under the safe harbor provisions of the U.S. Private Securities Litigation Reform Act of 1995. You
Asia Key Economic and Financial Indicators
 Quarterly Yearly Quarterly Quarterly Month-End Quarter-End Monthly (USD) Monthly Monthly Monthly Monthly Interest Daily GDP GDP per BoP CA IR External Debt Import Trade Unemployment IPI PPI CPI Rates*
Quarterly Yearly Quarterly Quarterly Month-End Quarter-End Monthly (USD) Monthly Monthly Monthly Monthly Interest Daily GDP GDP per BoP CA IR External Debt Import Trade Unemployment IPI PPI CPI Rates*
Jordan Levesque Making sure your business is PCI compliant
 Jordan Levesque Making sure your business is PCI compliant Brief overview of PCIDSS What's new in PCI DSS 3.2 Why is PCI important? Dive in! Simple things you can do to be secure Tomorrows session: What
Jordan Levesque Making sure your business is PCI compliant Brief overview of PCIDSS What's new in PCI DSS 3.2 Why is PCI important? Dive in! Simple things you can do to be secure Tomorrows session: What
RIR Update. A Joint Presentation Prepared By APNIC, ARIN, RIPE NCC. 17 March 2002 IEPG - Minneapolis
 RIR Update A Joint Presentation Prepared By APNIC, ARIN, RIPE NCC Overview Joint Efforts RIR Specific Statistics Questions RIR Co-ordination IPv6 policy development Joint tutorial & presentation at AfNOG
RIR Update A Joint Presentation Prepared By APNIC, ARIN, RIPE NCC Overview Joint Efforts RIR Specific Statistics Questions RIR Co-ordination IPv6 policy development Joint tutorial & presentation at AfNOG
The Domain Abuse Activity Reporting System (DAAR)
 The Domain Abuse Activity Reporting System (DAAR) Dave Piscitello APWG EU October 2017 The Domain Abuse Activity Reporting system What is the Domain Abuse Activity Reporting system? A system for reporting
The Domain Abuse Activity Reporting System (DAAR) Dave Piscitello APWG EU October 2017 The Domain Abuse Activity Reporting system What is the Domain Abuse Activity Reporting system? A system for reporting
DAS LRS Monthly Service Report
 DAS LRS Monthly Service Report Customer Service Manager : Diploma Aggregation Service : Daniel Ward Project/document reference : DAS LRS 2010-12 Issue : 1.0 Issue date : 17 th January 2011 Reporting Period
DAS LRS Monthly Service Report Customer Service Manager : Diploma Aggregation Service : Daniel Ward Project/document reference : DAS LRS 2010-12 Issue : 1.0 Issue date : 17 th January 2011 Reporting Period
San Francisco Housing Authority (SFHA) Leased Housing Programs October 2015
 San Francisco Housing Authority (SFHA) Leased Housing Programs October 2015 Table of Contents Program Utilization Summary 3 PIC Reporting Rate 4-5 Operational Updates Recertifications and Inspections 6-7
San Francisco Housing Authority (SFHA) Leased Housing Programs October 2015 Table of Contents Program Utilization Summary 3 PIC Reporting Rate 4-5 Operational Updates Recertifications and Inspections 6-7
Universal Acceptance An Update
 Universal Acceptance An Update Don Hollander / GDD Summit / May 2016 Universal Acceptance Universal Acceptance Universal Acceptance is the state where all valid domain names and email addresses are accepted,
Universal Acceptance An Update Don Hollander / GDD Summit / May 2016 Universal Acceptance Universal Acceptance Universal Acceptance is the state where all valid domain names and email addresses are accepted,
Industrial Machinery. Search Marketing Case Study
 Industrial Machinery Search Marketing Case Study 2015-2016 A performance digital marketing consultancy & training academy. Our team comprises of digital researchers, strategists, consultants, usability
Industrial Machinery Search Marketing Case Study 2015-2016 A performance digital marketing consultancy & training academy. Our team comprises of digital researchers, strategists, consultants, usability
IoT - Next Wave of DDoS? IoT Sourced DDoS Attacks A Focus on Mirai Botnet and Best Practices in DDoS Defense
 IoT - Next Wave of DDoS? IoT Sourced DDoS Attacks A Focus on Mirai Botnet and Best Practices in DDoS Defense DDoS Attacks Increasing in Size, Frequency & Complexity Arbor Networks WISR XII Largest attack
IoT - Next Wave of DDoS? IoT Sourced DDoS Attacks A Focus on Mirai Botnet and Best Practices in DDoS Defense DDoS Attacks Increasing in Size, Frequency & Complexity Arbor Networks WISR XII Largest attack
Defending Against Known & Unknown Threats
 Defending Against Known & Unknown Threats Jack Walsh, New Initiatives & Mobility Programs Manager Copyright 2016 ICSA Labs Introducing ICSA Labs About ICSA Labs We re known for Providing independent 3
Defending Against Known & Unknown Threats Jack Walsh, New Initiatives & Mobility Programs Manager Copyright 2016 ICSA Labs Introducing ICSA Labs About ICSA Labs We re known for Providing independent 3
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
Phishing Activity Trends Report for the Month of September, 2007 Summarization of September Report Findings The total number of unique phishing reports submitted to APWG in September 2007 was 38,514, an
CIMA Asia. Interactive Timetable Live Online
 CIMA Asia Interactive Timetable 2018 Live Online Information version 8 last updated 04/05/18 Please note information and dates are subject to change. Premium Learning Partner 2018 CIMA Cert BA Course Overview
CIMA Asia Interactive Timetable 2018 Live Online Information version 8 last updated 04/05/18 Please note information and dates are subject to change. Premium Learning Partner 2018 CIMA Cert BA Course Overview
Instructor training course schedule v3 Confirmed courses due completion by 31 st July 2019
 Confirmed courses due completion by 31 st July 2019 Courses: 2 Orientation 2 IoT Fundamentals 2 Networking Essentials 2 Cybersecurity Essentials 2 IT Essentials: PC Hardware and Software 2 CCNA Routing
Confirmed courses due completion by 31 st July 2019 Courses: 2 Orientation 2 IoT Fundamentals 2 Networking Essentials 2 Cybersecurity Essentials 2 IT Essentials: PC Hardware and Software 2 CCNA Routing
Travellers reviews impact on destination brands. Jonathan Howlett VP Global Destination Marketing
 Travellers reviews impact on destination brands Jonathan Howlett VP Global Destination Marketing Evolution Of Travel The Users Take Control Advanced Discovery Plan & Have The Perfect Trip Source: Oyster.com
Travellers reviews impact on destination brands Jonathan Howlett VP Global Destination Marketing Evolution Of Travel The Users Take Control Advanced Discovery Plan & Have The Perfect Trip Source: Oyster.com
ICANN Contractual Compliance. ALAC Mee(ng. Sunday, 23 March 2014 #ICANN49
 ICANN Contractual Compliance ALAC Mee(ng Sunday, 23 March 2014 1 Agenda! Compliance General Update! Clarification of ALAC statement! Q&A session! Contractual Compliance Update! Ø Global presence in Singapore"
ICANN Contractual Compliance ALAC Mee(ng Sunday, 23 March 2014 1 Agenda! Compliance General Update! Clarification of ALAC statement! Q&A session! Contractual Compliance Update! Ø Global presence in Singapore"
ERS IT Portfolio Report
 Administration and Operations Committee ERS IT Portfolio Report January 21 st, 2014 1 Agenda Information Technology Projects Summary 2013 End of Year Metrics Project Management Office CMERS Website Applications
Administration and Operations Committee ERS IT Portfolio Report January 21 st, 2014 1 Agenda Information Technology Projects Summary 2013 End of Year Metrics Project Management Office CMERS Website Applications
Phishing Activity Trends Report. 4 th Quarter Unifying the. Global Response To Cybercrime. October December 2012
 4 th Quarter 2012 Unifying the Global Response To Cybercrime October December 2012 Published April 24, 2013 Phishing Report Scope The APWG analyzes phishing attacks reported to the APWG by its member companies,
4 th Quarter 2012 Unifying the Global Response To Cybercrime October December 2012 Published April 24, 2013 Phishing Report Scope The APWG analyzes phishing attacks reported to the APWG by its member companies,
Grade 4 Mathematics Pacing Guide
 Jul 2014 ~ August 2014 ~ Sep 2014 1 2 3 4 5 6 7 8 9 10 11 12 14 15 16 17 Routines 19 Routines 20 Routines BOY 22 BOY 23 24 11 12 14 29 15 30 31 Notes: Found Online @ wwweverydaymathonlinecom 1 More Calendars
Jul 2014 ~ August 2014 ~ Sep 2014 1 2 3 4 5 6 7 8 9 10 11 12 14 15 16 17 Routines 19 Routines 20 Routines BOY 22 BOY 23 24 11 12 14 29 15 30 31 Notes: Found Online @ wwweverydaymathonlinecom 1 More Calendars
Previous Intranet Initial intranet created in 2002 Created solely by Information Systems Very utilitarian i Created to permit people to access forms r
 ACHIEVA Cafe Steve McDonell Previous Intranet Initial intranet created in 2002 Created solely by Information Systems Very utilitarian i Created to permit people to access forms remotely Not much content
ACHIEVA Cafe Steve McDonell Previous Intranet Initial intranet created in 2002 Created solely by Information Systems Very utilitarian i Created to permit people to access forms remotely Not much content
In our Update this month
 In our Update this month Territory: UK Period: December/ January 2015 Key Reports: Top 20 Kids sites- 2015 in Review Top Kids Sites Insight Digital Download Disney to lead way in kids wearable market?
In our Update this month Territory: UK Period: December/ January 2015 Key Reports: Top 20 Kids sites- 2015 in Review Top Kids Sites Insight Digital Download Disney to lead way in kids wearable market?
CIMA Asia. Interactive Timetable Live Online
 CIMA Asia Interactive Timetable 2017 2018 Live Online Version 1 Information last updated 09 October 2017 Please note: Information and dates in this timetable are subject to change. CIMA Cert BA Course
CIMA Asia Interactive Timetable 2017 2018 Live Online Version 1 Information last updated 09 October 2017 Please note: Information and dates in this timetable are subject to change. CIMA Cert BA Course
Nigerian Telecommunications Sector
 Nigerian Telecommunications Sector SUMMARY REPORT: Q4 and full year 2015 NATIONAL BUREAU OF STATISTICS 26th April 2016 Telecommunications Data The telecommunications data used in this report were obtained
Nigerian Telecommunications Sector SUMMARY REPORT: Q4 and full year 2015 NATIONAL BUREAU OF STATISTICS 26th April 2016 Telecommunications Data The telecommunications data used in this report were obtained
CMR India Monthly Mobile Handset Market Report. June 2017
 CMR India Monthly Mobile Handset Market Report June 2017 Cyber Media Research Ltd. www.cmrindia.com Submitted by: Copyright 1 Copyright 2017 Cyber 2017 Cyber Media Media Research Research Ltd. Reproduction
CMR India Monthly Mobile Handset Market Report June 2017 Cyber Media Research Ltd. www.cmrindia.com Submitted by: Copyright 1 Copyright 2017 Cyber 2017 Cyber Media Media Research Research Ltd. Reproduction
Smart Protection Network. Raimund Genes, CTO
 Smart Protection Network Raimund Genes, CTO Overwhelmed by Volume of New Threats New unique samples added to AV-Test's malware repository (2000-2010) 20.000.000 18.000.000 16.000.000 14.000.000 12.000.000
Smart Protection Network Raimund Genes, CTO Overwhelmed by Volume of New Threats New unique samples added to AV-Test's malware repository (2000-2010) 20.000.000 18.000.000 16.000.000 14.000.000 12.000.000
Imputation for missing observation through Artificial Intelligence. A Heuristic & Machine Learning approach
 Imputation for missing observation through Artificial Intelligence A Heuristic & Machine Learning approach (Test case with macroeconomic time series from the BIS Data Bank) Byeungchun Kwon Bank for International
Imputation for missing observation through Artificial Intelligence A Heuristic & Machine Learning approach (Test case with macroeconomic time series from the BIS Data Bank) Byeungchun Kwon Bank for International
Practices on DNS Management and Domain Name Emerging Topics. Jirasak Jullawat July 14, 2016
 Practices on DNS Management and Domain Name Emerging Topics Jirasak Jullawat July 14, 2016 TABLE OF CONTENTS 1. Definition of Domain Name 2. Domain Name Structure 3. Why Domain Name? 4..th Management 5.
Practices on DNS Management and Domain Name Emerging Topics Jirasak Jullawat July 14, 2016 TABLE OF CONTENTS 1. Definition of Domain Name 2. Domain Name Structure 3. Why Domain Name? 4..th Management 5.
Budget Transfers. To initiate a budget transfer, go to FGAJVCM (Journal Voucher Mass Entry). FGAJVCM
 Budget Transfers To initiate a budget transfer, go to FGAJVCM (Journal Voucher Mass Entry). FGAJVCM 1 You don t need to enter a document number. It will auto-populate later. Continue on to the Next Block
Budget Transfers To initiate a budget transfer, go to FGAJVCM (Journal Voucher Mass Entry). FGAJVCM 1 You don t need to enter a document number. It will auto-populate later. Continue on to the Next Block
NCC Cable System Order
 Syscode 0081 Agency Beacon Media System Name Spectrum/Park Cities, TX Advertiser Ed Meier for Congress $2,421.00 Commission $363.15 Net $2,057.85 198 1 AEN VARIOUS 2/26/18 3/4/18 19:00 24:00 X X X X X
Syscode 0081 Agency Beacon Media System Name Spectrum/Park Cities, TX Advertiser Ed Meier for Congress $2,421.00 Commission $363.15 Net $2,057.85 198 1 AEN VARIOUS 2/26/18 3/4/18 19:00 24:00 X X X X X
Invincea Endpoint Protection Test
 Invincea Endpoint Protection Test A test commissioned by Invincea and performed by AV-TEST GmbH. Date of the report: May 2 nd, 2016 Executive Summary In April 2016, AV-TEST performed a review of the Invincea
Invincea Endpoint Protection Test A test commissioned by Invincea and performed by AV-TEST GmbH. Date of the report: May 2 nd, 2016 Executive Summary In April 2016, AV-TEST performed a review of the Invincea
Mobile Connect Driving Global Economic Growth Through Secure Mobile Identity
 Mobile Connect Driving Global Economic Growth Through Secure Mobile Identity Marta Ienco, Regulatory and Policy Director 21 st April 2016 UNCITRAL Colloquium on Legal issue Related to Identity Management
Mobile Connect Driving Global Economic Growth Through Secure Mobile Identity Marta Ienco, Regulatory and Policy Director 21 st April 2016 UNCITRAL Colloquium on Legal issue Related to Identity Management
New Concept for Article 36 Networking and Management of the List
 New Concept for Article 36 Networking and Management of the List Kerstin Gross-Helmert, AFSCO 28 th Meeting of the Focal Point Network EFSA, MTG SEAT 00/M08-09 THE PRESENTATION Why a new concept? What
New Concept for Article 36 Networking and Management of the List Kerstin Gross-Helmert, AFSCO 28 th Meeting of the Focal Point Network EFSA, MTG SEAT 00/M08-09 THE PRESENTATION Why a new concept? What
Contractual Compliance Update. Contractual Compliance ICANN 55 9 March 2016
 Contractual Compliance Update Contractual Compliance ICANN 55 9 March 2016 Agenda Brief Update Since ICANN 54 on: Contractual Compliance Campaign Policy Update & Continuous Improvement Update Contractual
Contractual Compliance Update Contractual Compliance ICANN 55 9 March 2016 Agenda Brief Update Since ICANN 54 on: Contractual Compliance Campaign Policy Update & Continuous Improvement Update Contractual
HPE Security Data Security. HPE SecureData. Product Lifecycle Status. End of Support Dates. Date: April 20, 2017 Version:
 HPE Security Data Security HPE SecureData Product Lifecycle Status End of Support Dates Date: April 20, 2017 Version: 1704-1 Table of Contents Table of Contents... 2 Introduction... 3 HPE SecureData Appliance...
HPE Security Data Security HPE SecureData Product Lifecycle Status End of Support Dates Date: April 20, 2017 Version: 1704-1 Table of Contents Table of Contents... 2 Introduction... 3 HPE SecureData Appliance...
Anti-Phishing Working Group
 Phishing Attack Trends Report April, 2004 Phishing attacks use spoofed e-mails and fraudulent websites designed to fool recipients into divulging personal financial data such as credit card numbers, account
Phishing Attack Trends Report April, 2004 Phishing attacks use spoofed e-mails and fraudulent websites designed to fool recipients into divulging personal financial data such as credit card numbers, account
Spiegel Research 3.0 The Mobile App Story
 Spiegel Research 3.0 The Mobile App Story The effects of adopting and using a brand s mobile application on purchase behaviors SU JUNG KIM THE PROJECT Smartphone penetration in the U.S. has reached 68
Spiegel Research 3.0 The Mobile App Story The effects of adopting and using a brand s mobile application on purchase behaviors SU JUNG KIM THE PROJECT Smartphone penetration in the U.S. has reached 68
Freedom of Information Act 2000 reference number RFI
 P. Norris By email to: xxxxxxxxxxxxxxxxxxxxxx@xxxxxxxxxxxxxx.xxm 02 November 2011 Dear P. Norris Freedom of Information Act 2000 reference number RFI20111218 Thank you for your request under the Freedom
P. Norris By email to: xxxxxxxxxxxxxxxxxxxxxx@xxxxxxxxxxxxxx.xxm 02 November 2011 Dear P. Norris Freedom of Information Act 2000 reference number RFI20111218 Thank you for your request under the Freedom
APNIC Status Report. ARIN VI Public Policy Meeting 2-44 October 2000
 APNIC Status Report ARIN VI Public Policy Meeting 2-44 October 2000 Overview News Membership Growth Statistics Activities Priorities Total number of medals won - top 5 USA 97 RUSSIA 88 CHINA 59 AUSTRALIA
APNIC Status Report ARIN VI Public Policy Meeting 2-44 October 2000 Overview News Membership Growth Statistics Activities Priorities Total number of medals won - top 5 USA 97 RUSSIA 88 CHINA 59 AUSTRALIA
AIMMS Function Reference - Date Time Related Identifiers
 AIMMS Function Reference - Date Time Related Identifiers This file contains only one chapter of the book. For a free download of the complete book in pdf format, please visit www.aimms.com Aimms 3.13 Date-Time
AIMMS Function Reference - Date Time Related Identifiers This file contains only one chapter of the book. For a free download of the complete book in pdf format, please visit www.aimms.com Aimms 3.13 Date-Time
CIMA Certificate BA Interactive Timetable
 CIMA Certificate BA Interactive Timetable 2018 Nottingham & Leicester Version 3.2 Information last updated 09/03/18 Please note: Information and dates in this timetable are subject to change. Introduction
CIMA Certificate BA Interactive Timetable 2018 Nottingham & Leicester Version 3.2 Information last updated 09/03/18 Please note: Information and dates in this timetable are subject to change. Introduction
Annex A to the MPEG Audio Patent License Agreement Essential Philips, France Telecom and IRT Patents relevant to DVD-Video Disc - MPEG Audio - general
 Essential Philips, France Telecom and IRT Patents relevant to DVD-Video Disc - MPEG Audio - general PUBLICATION AR N 013241-317015 04-Jun-90 11-Oct-96 250211 11-Oct-11 Universal subband coder format AT
Essential Philips, France Telecom and IRT Patents relevant to DVD-Video Disc - MPEG Audio - general PUBLICATION AR N 013241-317015 04-Jun-90 11-Oct-96 250211 11-Oct-11 Universal subband coder format AT
Phishing Activity Trends
 Phishing Activity Trends Report for the Month of July, 2007 Summarization of July Report Findings For the first time recorded by the APWG, China has surpassed the United States as the country hosting the
Phishing Activity Trends Report for the Month of July, 2007 Summarization of July Report Findings For the first time recorded by the APWG, China has surpassed the United States as the country hosting the
Detecting Abuse in TLDs
 Detecting Abuse in TLDs A NameSentry TM presentation by Greg Aaron and Michael Young ICANN Toronto: 15 October 2012 2012 Illumintel Inc. All rights reserved. 1 Defining Abuse Every service provider has
Detecting Abuse in TLDs A NameSentry TM presentation by Greg Aaron and Michael Young ICANN Toronto: 15 October 2012 2012 Illumintel Inc. All rights reserved. 1 Defining Abuse Every service provider has
Investigations Over Unfair Trade Practices Steel Products in Mexico
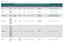 Investigations Over Unfair Trade Practices Steel Products in Mexico Product HTS Code Country Petitioner Start Preliminary Final Currents AD measures Status Rebar 7214.20.01 Brazil SICARTSA Nov 29, 1993
Investigations Over Unfair Trade Practices Steel Products in Mexico Product HTS Code Country Petitioner Start Preliminary Final Currents AD measures Status Rebar 7214.20.01 Brazil SICARTSA Nov 29, 1993
Town of Georgetown Comprehensive Plan
 Town of Georgetown Comprehensive Plan Town Council Kick-Off Meeting w/planning Commission August 24, 2016 Meeting Agenda Introductions Scope of Services Schedule Public Outreach Community Survey SWOT Analysis
Town of Georgetown Comprehensive Plan Town Council Kick-Off Meeting w/planning Commission August 24, 2016 Meeting Agenda Introductions Scope of Services Schedule Public Outreach Community Survey SWOT Analysis
Arabic Script IDN Working Group (ASIWG)
 Arabic Script IDN Working Group (ASIWG) ICANN Paris IDN Workshop 26 Jun08 Spot The Difference They Look The Same To Us But Not To A Computer When 1 is not 1 The Arabic Language is only a part of the Arabic
Arabic Script IDN Working Group (ASIWG) ICANN Paris IDN Workshop 26 Jun08 Spot The Difference They Look The Same To Us But Not To A Computer When 1 is not 1 The Arabic Language is only a part of the Arabic
No domain left behind:
 No domain left behind: is Let s Encrypt democratizing encryption? Maarten Aertsen 1, Maciej Korczyński 2, Giovane C. M. Moura 3, Samaneh Tajalizadehkhoob 2, Jan van den Berg 2 1 National Cyber Security
No domain left behind: is Let s Encrypt democratizing encryption? Maarten Aertsen 1, Maciej Korczyński 2, Giovane C. M. Moura 3, Samaneh Tajalizadehkhoob 2, Jan van den Berg 2 1 National Cyber Security
DATA FOR DEVELOPMENT June 13, 2017
 DATA FOR DEVELOPMENT June 13, 2017 1 Recent economic developments and outlook 2 Data for development Malaysia s development and its data ecosystem o Data and the public sector- public service delivery
DATA FOR DEVELOPMENT June 13, 2017 1 Recent economic developments and outlook 2 Data for development Malaysia s development and its data ecosystem o Data and the public sector- public service delivery
