Stream: Low Overhead Wireless Reprogramming for Sensor Networks
|
|
|
- Augustine Hardy
- 5 years ago
- Views:
Transcription
1 Thi full text paper wa peer reviewed at the direction of IEEE Communication Society ubject matter expert for publication in the IEEE INFOCOM 27 proceeding. : Low Overhead Wirele Reprogramming for Senor Network Rajeh Krihna Panta, Ia Khalil, Saurabh Bagchi Dependable Computing Sytem Lab, School of Electrical and Computer Engineering, Purdue Univerity 465 Northwetern Avenue,Wet Lafayette,IN {rpanta,ikhalil,bagchi}@purdue.edu Abtract Wirele reprogramming of a enor network i ueful for uploading new code or for changing the functionality of exiting code. Through the proce, a node hould remain receptive to future code update becaue reprogramming may be done multiple time during the node lifetime. Exiting reprogramming protocol, uch a, achieve thi by bundling the reprogramming protocol and the application a one program image, thereby increaing the overall ize of the image which i tranferred through the network. Thi increae both time and energy required for network reprogramming. We preent a protocol called that mitigate the problem by ignificantly reducing the ize of the program image. Uing the facility of having multiple code image on a node and witching between them, pre-intall the reprogramming protocol a one image and the application program equipped with the ability to liten to new code update a the econd image. For a ample application, reduce the ize of the program image by page (48 packet/page) compared to. i implemented on the Mica2 node and we conduct tetbed and imulation experiment to how the reduction in energy and reprogramming time of compared to. Index Term Network reprogramming, enor network,, three way handhake, mica2 mote. I. INTRODUCTION L ARGE cale enor network may be deployed for long period of time during which the requirement from the network or the environment in which the node are deployed may change. The change may neceitate uploading a new code or retaking the exiting code with different et of parameter. We will ue the term code upload for referring to both. A primary requirement i that the reprogramming be done while the node are embedded in their ening environment. Thi ha purred interet in multihop reprogramming protocol over the wirele link. For uch reprogramming, it i eential that the code update be % reliable and reach all the node that it i detined for. It i important to minimize the reource cot of the reprogramming energy pent in dieminating the code through the network and memory uage on each node. The code upload hould be fat ince the network functionality i likely degraded, if not reduced to zero, during the reprogramming period. While the cot of tranmitting code i high, the cot of periodically tranmitting meta-data about the code, to determine if an updated code i available, can alo be high. It i conceivable that the proce of code upload will be infrequent for many deployment and therefore it may appear that it reource conumption need not be optimized. However, conider that the enor network environment ha inherent unreliability in the wirele link that may have tranient failure. Thu the environment i dynamic with node coming in and out of period of diconnectedne. Alo, the network may have node added after the initial deployment while new code may be injected at arbitrary point in time. Since in mot deployment, the enor network i expected to operate over extended period of time, it i poible that the parameter for the application, uch a the monitoring period, change thereby neceitating retaking. The code diemination therefore cannot be conidered a one hot proce and thu, it become important to minimize the reource conumption ued in network reprogramming. Importantly, the reource cot which i incurred during the quiecent or teady tate of the network, due to keeping the code up-to-date mut be optimized ince that i the dominant phae in the network lifetime. A few reearcher have propoed protocol for reprogramming in enor network, the tate-of-the-art being defined by three protocol [], MNP [7], and Frehet [8]. Common to the three protocol i the notion of tranferring the code image in chunk of page on a hop-by-hop bai. Each node dieminate code to it immediate neighbor through a three-way handhake of advertiement, requet, and actual code tranfer. MNP and Frehet build on and optimize the tranfer for energy conumption repectively through judiciou ender election for dene network and leep-awake protocol for large network. The critical problem that beet all three protocol i what i tranferred. Common intuition would be to tranfer jut what i needed, in other word, the application image (or the image of the update to the application). However, each protocol tranfer the image of the entire reprogramming protocol together with the minimally neceary part. Since the reprogramming protocol are of coniderable complexity, the inflation in the program image ize 2 that get tranferred over the wirele medium increae greatly. The exact amount of increae i application pecific for a imple tand-alone application of page, the increae i 2 fold, while for a communicating application of the ame ize, the increae i fold. In a table environment, the increae would be problematic. In a enor network environment, thi poe an even bigger problem. Firt, the Quiecent doe not mean the node i idle. It mean there i no activity related to code upload, but the node i running it application and doing it normal activity, uch a monitoring. 2 We ue the term application image to refer to the uer application that need to run on the node, reprogramming protocol image to refer to the component for protocol, uch a, MNP, or Frehet, and program image to the combined image that get tranferred over the wirele medium X/7/$ IEEE 928
2 Thi full text paper wa peer reviewed at the direction of IEEE Communication Society ubject matter expert for publication in the IEEE INFOCOM 27 proceeding. network link are prone to tranient failure and yet, the code upload proce need to be % reliable. Second, the network are enviaged to be large and the cot of larger image i incurred at every hop and doe not get amortized. Third, it put preure on multiple carce reource of a node communication bandwidth, battery energy, and memory. Our approach i optimizing what need to be tranferred over the wirele medium and give rie to our protocol called. tranfer cloe to the minimally required image ize by egmenting the program image into an application image and the reprogramming protocol image. It tranfer over the wirele link the application image with minimal addition (typically page). It pre-intall in each node, before deployment, the reprogramming protocol image. utilize the ability to egment the Flah memory into multiple image and tore the two in two different image area. An application i modified by linking it to a mall component called ApplicationSupport (-AS) while ReprogrammingSupport (-RS) i pre-intalled in each node. -AS i generic and can be inerted in any TinyOS application through the inertion of jut two line of code. -RS build on and ue three-way handhake for hop-by-hop code diemination. Overall, deign principle i to limit the ize of -AS and providing it the facility to witch to -RS when triggered by a code update related meage. The advantage afforded by i demontrated over, though it can apply to any of the three protocol, ince the problem of code bloat i hared by each. A large part of the enor node lifetime i pent in the quiecent tate when it i not actively dieminating code. Hence, the energy expenditure due to exchanging control information during the teady-tate i of ignificance. optimize the teady-tate energy expenditure by witching from a puh-baed mechanim where the node periodically end advertiement to a pull-baed mechanim where a newly inerted node requet for the code. It i not poible for any puh-baed protocol to match the performance of in thi regard by imply reducing the frequency of advertiement, ince that will increae the time for newly introduced node to get the updated code. There are everal challenge to implementing the baic idea of in the Mica mote platform, the enor node platform of choice today. Firt, the node that ha been updated with the recent code need to remain receptive to future code update. Thu, it cannot be running jut the application. The mote platform doe not upport multi-taking and therefore the two program (reprogramming protocol and application) cannot be executing concurrently. A deign option we explored wa to pre-intall the reprogramming protocol component in the node and dynamically link it to the application to create a ingle executable image once the application i uploaded. However, the mote platform doe not provide a linking facility on the node itelf. Interetingly, thee contraint are alo found in other common enor node platform, uch a Senoria WINS and JPL enor node. Second, it i unreaonable to aume that the code update will alway occur according to a preet chedule in which cae the node could have queried the bae tation for it. Third, ha to conider the poibility that new node may be introduced into the network and may query a given node for coming up-to-date with the latet verion of the code. Thu a node cannot be content to handle jut it own need for taying up-to-date. The benefit of how up in fewer number of byte tranferred over the wirele medium leading to increaed energy aving and reduced delay for reprogramming. We demontrate thee claim by implementing in nec for the Mica2 mote platform. We conduct experiment with and on a real mall-ized tetbed (of up to 6 node) in linear and grid topologie. The output metric we meaure are number of byte tranferred (which relate to the energy pent) and the delay. We ee that achieve 63% to 98% reduction in reprogramming time and 75% to 32% reduction in the number of byte tranferred for the grid topologie. To evaluate for larger network, we ue the TOSSIM imulation environment. We preent a mathematical analyi to evaluate the performance of and compare it to the ideal cae when exactly the application image i tranferred. The ret of the paper i organized a follow. Section II urvey related work. Section III provide the detailed deign. Section IV preent the mathematical analyi. Section V explain the tetbed and the imulation etup and reult. Section VI conclude the paper. II. RELATED WORK Reliable multicat in unreliable environment, uch a ad-hoc network, can be achieved by epidemic multicat protocol baed on each node goiping the meage it received to a ubet of neighbor []. Thee protocol give probabilitic guarantee for the update to reach all the group member. The probability i monotonically increaing with the fanout of each node (the number of neighbor to goip to) and the quiecence threhold (the time after which a node will top goiping to it neighbor). By increaing the quiecence threhold, the reliability can be made to approach, which i the baic premie behind all the epidemic baed code update protocol in enor network, MNP, and Frehet. The puh-pull method for data diemination through the three way handhake of advertiement-requet-code ha been ued previouly in enor network with ened data taking the place of code. Protocol uch a SPIN [2] and SPMS [3] rely on the advertiement and the requet packet being much maller than the data packet and the redundancy in the network deployment which make everal node diintereted in any given advertiement. However, in the data diemination protocol, there i only uppreion of the requet and the data ize are much maller than the entire binary code image. The earliet network reprogramming protocol XNP [4] only operated over a ingle hop and did not provide incremental update of the code image. The Multihop Over the Air Programming (MOAP) protocol extended thi to multiple hop [5]. It introduced everal concept which are ued by later protocol, namely, local recovery uing unicat NACK and broadcat of the code, and liding window baed protocol for 929
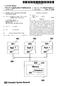
3 Thi full text paper wa peer reviewed at the direction of IEEE Communication Society ubject matter expert for publication in the IEEE INFOCOM 27 proceeding. receiving part of the code image. However, it did not leverage the pipelining effect with egment of the code image. The three protocol that are ubtantially more ophiticated than the ret and define the tate-of-the-art today are, MNP, and Frehet [6] wa the earliet and laid down ome deign principle ued by the other two. It ue a monotonically increaing verion number, egment the binary code image into page, and pipeline the different page acro the network. It build on top of Trickle [4], a protocol for a node to determine when to propagate code in a one hop cae. The code ditribution function through a three-way handhake protocol of advertiement, requet, and broadcat code. The operation of each node i periodic according to a fixed ize time window. The firt part of the window i for litening to advertiement and requet and ending advertiement. The econd part of the window i for tranmitting or receiving code correponding to the received requet. Within the firt part of the time window, a node randomly elect a time at which to end an advertiement with meta-data containing the verion number, the number of complete page it ha, and the total number of page in the image of thi verion. When the time to tranmit the advertiement come, the node ee whether it ha heard a advertiement with identical meta-data, and if o, it uppree the advertiement. When a node hear code that i newer than it own, it end a requet for that code and the lowet number page it need, to the node that advertied the new code. In the econd part of the periodic window, the node tranmit packet with the code image, correponding to the page for which it received requet. A receiving node only fill it page in monotonically increaing order thereby eliminating the need for maintaining large tate for miing hole in the code. For receiving the code, each node ue the hared broadcat medium that allow overhearing and can fill in a page requeted by a neighbor. The deign goal of MNP [7] i to chooe a local ource of the code which can atify the maximum number of node. They provide energy aving by turning off the radio of non-ender node. Frehet [8] aggreively optimize the energy conumption for reprogramming. During the initial phae in Frehet, information about the code and topology (primarily the number of hop a node i away from the wave front where the code i at) propagate through the network rapidly. Uing the topology information each node etimate when the code will arrive in it vicinity. Each node can go to leep till that time thereby aving energy. Frehet alo optimize the energy conumption by exponentially reducing the meta-data rate during the quiecent phae. III. STREAM DESIGN A. Deign Approach reduce the number of byte that need to be dieminated over the wirele medium o that intead of tranferring the entire reprogramming component along with the new application, only a mall ubet of reprogramming functionality i included in the program image. For the actual reprogramming protocol, build on the three-way handhake baed code ditribution een in exiting protocol. The idea i to have all node in the network be pre-intalled with the -RS (Figure ) component that include the complete functionality for network reprogramming. -RS i intalled a image. The application image augmented with the -AS component that provide minimal upport for network reprogramming i intalled a image. Henceforth, image mean -RS and image mean -AS plu application image. The addition to the ize of the program image over the application image ize with i ignificantly le than in the cae. When a new program image i to be injected into the network, all the node in the network running image reboot from image and the new image i injected into the network uing -RS. The new image again include -AS and we avoid the entire component from being tranferred to all the node each time the network need to be reprogrammed. Thi modification i that intead of adding the component, he add a much maller -AS component to her application. Both are localized two-line change to the application code. Bae node Code image in node Image: -RS Image:-AS+ uer application Circle are enor node Figure : Image in The aving in term of the number of page tranferred i quite ignificant. The exact figure depend on the application. Any application that ue radio communication will need to add about more page if i ued while -AS add only one more page. We tre that thi benefit i demontrated here for, but applie equally to all the current network reprogramming protocol ince each tranfer the entire protocol image along with the application image. B. Protocol Decription Conider that initially all node have -RS a image and the application with -AS a image. Each node i executing the image code. The node that initiate the reprogramming i attached to a computer through the erial port and i called the bae node. Following i the decription of how work when a new uer application plu - AS ha to be injected into the network.. In repone to the reboot command from the uer, all node in the network reboot from image. Thi i accomplihed a follow: a. The bae node executing image initiate the proce by generating a command to reboot from image. It broadcat the reboot command to it one hop neighbor and itelf reboot from image. b. When a node running the uer application receive the reboot command, it rebroadcat the reboot command and itelf reboot from image. 2. Once the reboot command reache all node, all node tart running -RS. Then the new uer application i injected into the network uing -RS. 93
4 Thi full text paper wa peer reviewed at the direction of IEEE Communication Society ubject matter expert for publication in the IEEE INFOCOM 27 proceeding. 3. -RS reprogram the network by uing the three way handhake method where each node broadcat the advertiement about the code page that it ha. When a node hear the advertiement of newer code than it currently ha, it end a requet to the advertiing node. Then the advertiing node broadcat the requeted code page. Each node maintain a et S containing the id of the node from which it ha received the requet for code. 4. Once the node download the new code completely, it perform a ingle-hop broadcat of an ACK indicating that it ha completed downloading. 5. When a node α receive the ACK from a node β, it remove the id of β from it et S. 6. When the et S i empty and all the image are complete (that i all page of all image have been downloaded), the node reboot from image. So, after ometime the entire network i reprogrammed and all node are execute image (-AS) which ha the uer application. Handling incremental node deployment. Let a node n having an older verion of application a image and running -RS join the network. n advertie the code it ha, uing -RS. When a neighbor n 2 of node n running image hear the advertiement, it reboot from it image if the advertiement from n i different from the code page poeed by n 2. Each neighbor of n that hear the advertiement perform thee action. Now uing tep 2 through 6, n download the new application from it neighbor. C. Deign of -AS The main goal of i to add little reprogramming functionality to the uer application intead of adding the entire reprogramming protocol (a in ) o that the code image that i tranferred over the wirele medium acro the network i a mall a poible. Thi i achieved by attaching the -AS component to the uer application. -AS hould be uch that the increae in the ize when it i attached to the uer application i minimum and at the ame time, the node hould be receptive to code update in the future. -AS provide the functionality to reboot from image when the uer give the reboot command. Thi reboot command i dieminated through the network according to tep and 2 in the Section Protocol Decription. The flooding technique ued to reboot all the node in the network doe not caue congetion becaue each node broadcat the reboot command only once and reboot from -RS immediately after. -AS alo provide functionality to reboot from image when new node are introduced to the network. When new node join the network, they periodically broadcat the advertiement. After one-hop neighbor of thee new node hear the advertiement, they reboot from image. Once a node reboot from image, -RS take care of dieminating the new application image. The time to reboot from one image to another i inconequential for the Mica mote (le than 5 econd). A mentioned above, -AS require minimal change in the uer application. In TinyOS, following i the nec code required to be added when i attached to the uer application: Component C; Main.StdControl C; To attach the uer application to -AS intead, replace C by ASC. Steady-tate behavior In, once a node reprogramming i over, it keep on advertiing the code image that it ha. Thi i to enure that the new node joining the network get the latet verion of the application image. A a reult, radio reource are continuouly ued by even in the teady tate. However, in, in the teady-tate, each node i running -AS, which doe not proactively advertie the code image that it ha. However, both new node joining the network and new code puhed in by the bae tation are handled. The node running uer application plu -AS in the teady tate receive the advertiement from the new node, reboot from -RS, and end the updated application to the new node. When the bae tation ha to puh an updated application image, the node running uer application plu -AS get the reboot command from the bae node, reboot from -RS, and download the new application. The teady-tate advertiement in mean that the uer application ha to hare the node radio reource with while thi i not the cae when i ued. Alo, the teady-tate RAM uage i much le for than for becaue of the maller ize of the uer application plu -AS compared to uer application plu. The cae where two partition of the network with different verion merge and the laggard one need to be updated i equivalent in and. In both, the reprogramming time of the laggard partition depend on the advertiement frequency from the node in thi partition. Source node Advertiement Requet Data Detination node. Figure 2: Three-way handhake for data diemination D. Deign of -RS -RS, preintalled in all node a image and executed during the reprogramming phae, i reponible for actual image tranfer among the node in the network. It i baed on with the ignificant change mentioned below. When new application image i to be injected into the network, all node reboot from -RS. Then, reprogramming i done by uing a three-way handhake (Figure 2) in which each node broadcat the advertiement about the code page that it currently ha. A node, upon hearing the advertiement of newer code than it currently ha, end a requet to the advertiing node. The advertiing node then broadcat the requeted code page. 93
5 Thi full text paper wa peer reviewed at the direction of IEEE Communication Society ubject matter expert for publication in the IEEE INFOCOM 27 proceeding. Change from Once reprogramming i done we want all the node to reboot from the new application automatically. One obviou approach would be to reboot each node from the uer application after it complete downloading the new application. But the flaw with thi approach i that even though a node ha completed downloading the new application, other node may till be dependant on it for getting the updated code image. Therefore the node need to continue to run -RS. To handle thi, when a node receive a requet for code, it put the node-id of the requeting node in the et S. When a node complete downloading the new application image, it broadcat an ACK. When a node receive an ACK from it neighbor, it remove the id of that node from the et S. So, the following invariant i maintained at all time for the et S of a node A: { } A. S = x REQ( x, A) = true ACK ( x, A) = fale Thi enure that the et S at a node A conit of the id of thoe node to which it i currently ending code fragment. The condition for a node A to reboot from image i a follow: A. S = φ A.# page = Total number of page The firt condition i that no neighbor i waiting on A to end it updated code and the econd condition i that A itelf ha downloaded all the page of the application. Eventually all node in the network download all the page of the new application and reboot from image. So in the teady tate all the node run the application attached with -AS. Thee change in enure that all node reboot from the uer application after reprogramming i done. In, in contrat to the automatic operation in, once all node complete downloading the new uer application, they reboot from the new application only after the uer give the reboot command manually from the bae node. IV. STREAM ANALYSIS A. Energy Cot Here we analyze the energy cot of uploading application uing three different protocol:, and an ideal protocol in which only the application need to be uploaded without any extra overhead. Let the application conit of N p page, each page ha N pkt packet and each packet ha N b byte. Let C be the energy cot of tranmitting and receiving a packet once and P be the probability of ucceful tranmiion of a packet over a ingle hop. Auming that retranmiion of a packet are independent, the probability that the number of retranmiion (N ret ) of a packet equal k i given by PN ( k) P( P) k The expected number of retranmiion K = E[N ret ] i ret = = () k = k K = E[ Nret ] = k ( P ( P ) ) = (2) k = P The energy cot of a node at h hop from the ource to completely download the application i given by h Np Npkt C Eh = K h Np Npkt C = (3) P The total energy overhead of uploading the application on all the node in a network in which each node i at mot h max hop from the ource i given by h= hmax h= hmax h Np Npkt C E = NNh Eh = NNh h= h= P (4) where N Nh i the number of node at hop h. N Nh depend on network topology and denity d. For a line topology, N Nh =. For a uniformly ditributed network on a dik with communication radiu r, N Nh = πdr 2 (2h-). For nxn grid, N Nh = h+ when h (n-) or N Nh = 2n-h- when n h (2n). For x grid, we calculate total energy E expended for (a) tandalone application (one that doe not perform radio communication) and (b) application that ue GenericComm component (provided by TinyOS) for communication. The application ize i taken to be,, or page. In cae (a), the increae in the ize of the program image (in unit of a page) are and 2, repectively, for and. In cae (b), thee increae are and, repectively, for and. We ue fixed energy cot a 5 nj/bit, P =.98, the variable (ditance dependent) energy cot i pj/bit r 2, for a tranmiion ditance of r, the receiving energy i equal to the fixed energy cot. Figure 3 how the ignificant difference in energy expended between and. Figure 4 reaffirm that for communicating application, energy cot of and the ideal cae are comparable. Energy in Joule (E) Ideal Figure 3: Total energy conumed in the grid topology with tandalone application B. Convergence Time In thi ection, we analyze the convergence time, i.e., the time to reprogram the entire network. Let P k = P(N r = k) be the probability that a whole page ha been uccefully ent in the k th round, where N r i the number of round. The probability that a given packet fail to be ent within k round i given by P f ( k) ( P ) k = (5) Then, the probability of uccefully ending the whole page in at mot k round (N r k) i k N pkt k ( ) (6) PN ( k) = P= P r i i= The expected number of round for uccefully ending a whole page i 932
6 Thi full text paper wa peer reviewed at the direction of IEEE Communication Society ubject matter expert for publication in the IEEE INFOCOM 27 proceeding. (7) E[ N ] = i P = i P( N = i) = P( N i) r i r r i= i= i= EN [ ] = PN ( < i) = PN ( i ) ( ) ( ) (8) r r r i= i= i = i ( P ) N pkt EN [ r] = ( ) (9) Since the page tranmiion i pipelined, the expected number of round it take to download the whole application at a node h-hop away i given by EN [ ] = ( N ) EN [ ] + h EN [ ] = ( N + h ) EN [ ] () rh, p r r p r The lat term i the time it take to download the firt page, and the firt term i the time it take to download the ret of the page. Plugging (9) into (), we get i ( ) N pkt EN [ ] = ( N + h ) ( P) () rh, p i= Auming maximum number of hop to be h max and the round time to be T r, the expected convergence time T conv i T = T E[ N ] conv r r, hmax i ( ) N pkt T = T ( N + h ) ( P) (2) conv r p max i= Energy in Joule (E) Ideal Figure 4: Total energy conumed in the grid topology with communicating application Convergence Time (econd) Ideal Figure 5: Convergence time for grid topology with tandalone application Convergence Time (econd) Ideal Figure 6: Convergence time for grid topology with communicating application Auming that P tay contant acro the three cae (Ideal,, and ), the time become directly proportional to the number of page (ince other factor are contant). Figure 5 and Figure 6 how the convergence time for the grid. In reality, ince put le preure on the bandwidth than, P will be higher for thu giving it additional advantage for convergence time. V. EXPERIMENTS AND RESULTS We implement uing the nec programming language in TinyOS [5]. In thi ection, we compare the performance of and for different network ize and node denitie. Both tetbed experiment uing Mica2 [4] mote and imulation uing TOSSIM [5] (a bit level imulator for TinyOS platform) are ued to demontrate the advantage of over. Tetbed experiment how the performance of and in realitic environment while imulation exhibit their calability. A. Evaluation Metric Any network reprogramming protocol mut enure that all node in the network receive the application image completely minimizing the time and the energy for the reprogramming. Both and are % reliable, i.e. all node in the network download every byte of the uer application. So, in the following ection, we focu on comparion in term of time to reprogram the network and the energy conumed during reprogramming. Though -RS ha more feature than, it i only one page larger in ize than and the increae in RAM uage i jut 74 byte. B. Tetbed decription and reult We perform the experiment uing Mica2 node having a 7.37 MHz, 8 bit microcontroller. Each Mica2 node i equipped with 28KB of program memory, 4KB of RAM and 52KB external flah which i ued for toring multiple code image. Thee node communicate via a 96 MHz radio tranceiver. The firt et of experiment i performed in 2x2, 3x3, and 4x4 quare grid network having a ditance of ft between adjacent node in each row and column. Experiment of network reprogramming uing are carried out by preintalling -RS a image and ame verion of application image plu -AS a image on all node in the network. A new application image plu -AS i injected into the ource node (ituated at one corner of the grid) via a computer attached to it. Then the ource node tart 933
7 Thi full text paper wa peer reviewed at the direction of IEEE Communication Society ubject matter expert for publication in the IEEE INFOCOM 27 proceeding. dieminating the new application image to the network. Experiment with are performed imilarly by intalling a image and the application image plu a image. A new application image plu i injected into the network. Time to reprogram the network i the time interval between the intant t when the ource node end the firt data packet to the intant t when the lat node (the one which take the longet time to download the new image) complete downloading the new application. Since clock maintained by the node in the network are not ynchronized, we cannot take the difference between the time intant t meaured by the lat node and t meaured by the ource node. Although a ynchronization protocol can be ued to olve thi iue, we do not ue it in our experiment becaue we do not want to add to the load in the network (due to ynchronization meage) or the node (due to the ynchronization protocol). Intead, once each node complete downloading the new image, it end a pecial packet to the ource node aying that it ha completed downloading the new application. The ource node meaure the time intant t when it receive uch packet, timetamp the packet with t and end the packet to the computer. If the network ha n node including the ource node, the computer attached to the ource node receive one t and (n-) number of t max. We take tprog = ( t' t ) a the reprogramming time. It t' hould be noted that the actual reprogramming time max i ( t' t td) where t d i the time required to end the t' pecial packet from the lat node to the ource node. Since t d i negligible compared to the reprogramming time, our formula i a reaonable approximation to the actual reprogramming time. Furthermore, ince we are intereted in the difference between the reprogramming time of and, the effect of t d cancel out. Among the variou factor that contribute to the energy ued during reprogramming, two important one are the amount of radio tranmiion in the network and the number of flahwrite (the downloaded application i written to the external flah a image ). Since the radio tranmiion are the major ource of energy conumption, we take the total number of byte tranmitted by all node in the network a the meaure of energy ued in reprogramming. In our experiment, each node count the number of byte it tranmit and log that data to it external flah. By umming the number of byte tranmitted by each node, we find the total number of byte tranmitted in the network for the purpoe of reprogramming. Since the amount of flah-write in i higher, the energy advantage will be increaed if we take that factor into account. A mentioned earlier, compared to the exact gain achieved by in term of number of page tranmitted depend on the uer application. In our experiment, we ue a imple application that perform radio communication but doe not write to external flah. The application image alone i page, application image plu -AS i 2 page and application image plu i 22 page. Time(econd) x2 3x3 4x4 Figure 7: Reprogramming time for grid network Number of byte (x 3 ) x2 3x3 4x4 Figure 8: Number of byte tranmitted in the network during reprogramming for grid network Figure 7 compare reprogramming time of and for 2x2, 3x3, and 4x4 grid network. Interetingly, we oberve from the experiment that the number of hop between two node i dependent on environmental condition and change during multiple run of the experiment. For example, a node i ometime able to communicate with a node eparated by more than one grid point. Expectedly, the experiment how that reduce the reprogramming time ignificantly. Thi i becaue need to tranfer only 2 page wherea ha to tranfer 22 page. The reduction in reprogramming time become more pronounced for larger network. Figure 8 how the total number of byte tranmitted in the network during the reprogramming period. Both data packet and control packet (requet and advertiement packet for and requet, advertiement and ACK packet for ) are conidered while calculating the number of byte. The reult indicate that depite the additional ACK traffic in, the reduction in data packet caue to outperform. We ee that achieve 63% to 98% reduction in reprogramming time and 75% to 32% reduction in the total number of byte tranferred for thee grid topologie. Next we performed the experiment for linear topologie with ft. eparation between adjacent node. Source node i ituated at one end of the line. Figure 9 and Figure provide the comparion of the reprogramming time and total number of byte tranmitted in the network repectively between and for different ize of the linear topologie. reduce reprogramming time by 58% to 9% and the total number of byte tranferred by 59% to 7% for different linear topologie. If we compare the reprogramming time of 2x2 grid with a 4 node linear network, we find that the latter take longer time to reprogram itelf becaue 2x2 network can 934
8 Thi full text paper wa peer reviewed at the direction of IEEE Communication Society ubject matter expert for publication in the IEEE INFOCOM 27 proceeding. involve at mot 2 hop communication (motly hop) while 4 linear node can have at mot 3 hop communication. Thee graph how only the number of byte that are tranmitted during the reprogramming period. In, each node keep on broadcating the advertiement packet even after the reprogramming period i over. A a reult, the node have to pend energy in advertiing even when reprogramming i not being done. doe not have thi problem becaue a oon a the reprogramming period i over, the node reboot from the application image plu -AS which doe not broadcat advertiement. A a reult, we oberve a monotonically increaing difference in the number of byte a the protocol are allowed to continue to run in the teady tate. Time (econd) node 3 node 4 node 5 node Figure 9: Reprogramming time for linear network Number of byte(x 3 ) node 3 node 4 node 5 node Figure : Number of byte tranmitted in the network during reprogramming for linear network C. Simulation Reult In order to demontrate the calability of and to compare it with for larger network ize, we performed imulation uing TOSSIM. Although TOSSIM doe not model TinyOS hardware preciely, it provide more accurate modeling of the phyical layer than many other imulator, uch a n-2. A TOSSIM doe not model execution time accurately, the imulation reult preented here only exhibit the overall behavior and trend and proper caling i required to give the abolute value for the Mica2 platform. A it take ten of hour to complete imulation for larger network, in our imulation, we reduce the number of packet per page from 48 to 24 packet. Thi i not of eriou concern becaue we are intereted in the comparion of performance of and and not on the abolute value. Effect of network ize We ue everal grid network ( ft ditance between adjacent node in any row and column) of varying ize (up to 6x6 grid) for our imulation. Source node i ituated at one corner of the grid. Like before, and need to tranfer 2 and 22 page repectively to all node in the network. Figure and Figure 2 compare the reprogramming time and number of byte tranmitted in the network between and for different grid ize. It how that both and are calable, at leat up to 256 node imulated. In our experiment, we found that compared to, reduce the reprogramming time by 4% to % for different network ize. We noticed that the reduction in the total number of byte tranmitted in the network wa between 75% to 2% for thee network ize. Time (econd) x2 4x4 6x6 8x8 x 2x2 4x4 6x6 Figure : Reprogramming time for nxn grid Number of byte(x 4 ) x2 4x4 6x6 8x8 x 2x2 4x4 6x6 Figure 2: Number of byte tranmitted in the network during reprogramming for nxn grid Effect of network denitie To compare the performance of and for different node denitie, we vary the number of node in a 9 ft by 9 ft area. For each node denity, the node are till arranged in grid fahion with uniform pacing between the adjacent node (jut the pacing decreae with increaing denity). Figure 3 how that reprogram the network much fater than for all network denitie and Figure 4 how that ue leer number of byte than. The increae in node denity increae the reprogramming time due to two reaon. Firt, there i an increae in the number of node in a given area reulting in more colliion of the tranmitted packet. Second, there are imply more node that need to download the new application. Thee figure how that for higher node denitie, the gap between reprogramming time a well a number of byte between and widen further. Thi can be explained by the fact that reduce colliion more effectively due to the reduced number of byte tranferred. From our experiment, we found that dieminate 935
9 Thi full text paper wa peer reviewed at the direction of IEEE Communication Society ubject matter expert for publication in the IEEE INFOCOM 27 proceeding. code approximately uniformly with hop ditance from the ource a oberved by the author in [6] for low denitie. Time (econd) Denity (node/q. ft) Figure 3: Reprogramming time (different node denitie) Number of byte(x 3 ) Denity(node/q. ft) Figure 4: Number of byte tranmitted in the network during reprogramming for different node denitie VI. CONCLUSION In thi paper, we preented a enor network reprogramming protocol called that greatly reduce the number of byte tranmitted over the wirele medium for reprogramming. It addree a fundamental problem in all exiting network reprogramming protocol, whereby the application image together with the reprogramming protocol image i tranferred. pre-intall the reprogramming protocol image in a node and tranfer the application image with a mall addition. Conequently, it reduce the reprogramming time, the number of byte tranferred, the energy expended, and the uage of program memory. i implemented on TinyOS for the Mica2 enor node. Experiment conducted on a tetbed of Mica2 mote demontrate up to 98% reduction in reprogramming time and up to 32% reduction in the number of byte tranferred compared to. Simulation experiment in TOSSIM how the increaing advantage of over with larger network ize. Further we are experimenting with making work with multiple ource node and integration with Frehet to provide a highly energy optimized protocol. ACKNOWLEDGMENT Thi material i baed upon work upported by the National Science Foundation under Grant No. ECS-336 and the Indiana 2 t Century Reearch & Technology Fund under Grant No Any opinion, finding, and concluion or recommendation expreed in thi material are thoe of the author and do not necearily reflect the view of the ponor. REFERENCES [] J. Luo, P. T. Eugter, and J. P. Hubaux, "Route driven goip: probabilitic reliable multicat in ad hoc network," at the Twenty- Second Annual Joint Conference of the IEEE Computer and Communication Societie (INFOCOM), pp , 23. [2] J. Kulik, W. Heinzelman, and H. Balakrihnan, "Negotiation-baed protocol for dieminating information in wirele enor network," Wirele Network, vol. 8, no. 2/3, pp , 22. [3] G. Khanna, S. Bagchi, and Y-S. Wu, "Fault tolerant energy aware data diemination protocol in enor network," at the International Conference on Dependable Sytem and Network, pp , 24. [4] Crobow Tech Inc., "Mote In-Network Programming Uer Reference," [5] T. Stathopoulo, J. Heidemann, and D. Etrin, "A remote code update mechanim for wirele enor network," Technical Report CENS Technical Report 3, no., 23. [6] J. W. Hui and D. Culler, "The dynamic behavior of a data diemination protocol for network programming at cale," at the Proceeding of the 2nd international conference on Embedded networked enor ytem, Baltimore, MD, USA, pp. 8-94, 24. [7] S. S. Kulkarni and W. Limin, "MNP: Multihop Network Reprogramming Service for Senor Network," at the 25th IEEE International Conference on Ditributed Computing Sytem, pp. 7-6, 25. [8] M. D. Kraniewki, R. Panta, S. Bagchi, C-L. Yang, W. J. Chappell, Energy-efficient, On-demand Reprogramming of Large-cale Senor Network, Under reviion to ACM TOSN. Available a Purdue ECE Technical Report TR-ECE-6-2, 26. [9] Univerity of California, Berkeley, TinyOS,at [] J. Heidemann, F. Silva, C. Intanagonwiwat, R. Govindan, D. Etrin, and D. Ganean, "Building efficient wirele enor network with low-level naming," at the Proceeding of the eighteenth ACM ympoium on Operating ytem principle, Banff, Alberta, Canada, pp , 2. [] P. Levi and D. Culler, "Maté: a tiny virtual machine for enor network," Proceeding of the th international conference on Architectural upport for programming language and operating ytem, no., pp , 22. [2] S. R. Madden, M. J. Franklin, J. M. Hellertein, and W. Hong, "TinyDB: an acquiitional query proceing ytem for enor network," ACM Tran. Databae Syt., vol. 3, no., pp , 25. [3] Crobow Technology, Inc., MPR/ MIB uer Manual at MIB_Serie_Uer_Manual.pdf. [4] P. Levi, N. Patel, S. Shenker, and D. Culler, "Trickle: A Self- Regulating Algorithm for Code Propogation and maintenance in Wirele Senor Network," Proceeding of the Firt USENIX/ACM Sympoium on Networked Sytem Deign and Implementation (NSDI 24), no., 24. [5] P. Levi, N. Lee, M. Welh, and D. Culler, TOSSIM: Accurate and calable imulation of entire tinyo application, Firt ACM Conference on Embedded Networked Senor Sytem (SenSy 23) 936
Stream: Low Overhead Wireless Reprogramming for Sensor Networks
 : Low Overhead Wireless Reprogramming for Sensor Networks Rajesh Krishna Panta, Issa Khalil, Saurabh Bagchi Dependable Computing Systems Lab, School of Electrical and Computer Engineering, Purdue University
: Low Overhead Wireless Reprogramming for Sensor Networks Rajesh Krishna Panta, Issa Khalil, Saurabh Bagchi Dependable Computing Systems Lab, School of Electrical and Computer Engineering, Purdue University
Performance of a Robust Filter-based Approach for Contour Detection in Wireless Sensor Networks
 Performance of a Robut Filter-baed Approach for Contour Detection in Wirele Senor Network Hadi Alati, William A. Armtrong, Jr., and Ai Naipuri Department of Electrical and Computer Engineering The Univerity
Performance of a Robut Filter-baed Approach for Contour Detection in Wirele Senor Network Hadi Alati, William A. Armtrong, Jr., and Ai Naipuri Department of Electrical and Computer Engineering The Univerity
DAROS: Distributed User-Server Assignment And Replication For Online Social Networking Applications
 DAROS: Ditributed Uer-Server Aignment And Replication For Online Social Networking Application Thuan Duong-Ba School of EECS Oregon State Univerity Corvalli, OR 97330, USA Email: duongba@eec.oregontate.edu
DAROS: Ditributed Uer-Server Aignment And Replication For Online Social Networking Application Thuan Duong-Ba School of EECS Oregon State Univerity Corvalli, OR 97330, USA Email: duongba@eec.oregontate.edu
Network Coding in Duty-Cycled Sensor Networks
 1 Network Coding in Duty-Cycled Senor Network Roja Chandanala, Radu Stoleru, Member, IEEE Abtract Network coding and duty-cycling are two popular technique for aving energy in wirele adhoc and enor network.
1 Network Coding in Duty-Cycled Senor Network Roja Chandanala, Radu Stoleru, Member, IEEE Abtract Network coding and duty-cycling are two popular technique for aving energy in wirele adhoc and enor network.
Nearly Constant Approximation for Data Aggregation Scheduling in Wireless Sensor Networks
 Nearly Contant Approximation for Data Aggregation Scheduling in Wirele Senor Network Scott C.-H. Huang, Peng-Jun Wan, Chinh T. Vu, Yinghu Li and France Yao Computer Science Department, City Univerity of
Nearly Contant Approximation for Data Aggregation Scheduling in Wirele Senor Network Scott C.-H. Huang, Peng-Jun Wan, Chinh T. Vu, Yinghu Li and France Yao Computer Science Department, City Univerity of
Laboratory Exercise 6
 Laboratory Exercie 6 Adder, Subtractor, and Multiplier The purpoe of thi exercie i to examine arithmetic circuit that add, ubtract, and multiply number. Each type of circuit will be implemented in two
Laboratory Exercie 6 Adder, Subtractor, and Multiplier The purpoe of thi exercie i to examine arithmetic circuit that add, ubtract, and multiply number. Each type of circuit will be implemented in two
Universität Augsburg. Institut für Informatik. Approximating Optimal Visual Sensor Placement. E. Hörster, R. Lienhart.
 Univerität Augburg à ÊÇÅÍÆ ËÀǼ Approximating Optimal Viual Senor Placement E. Hörter, R. Lienhart Report 2006-01 Januar 2006 Intitut für Informatik D-86135 Augburg Copyright c E. Hörter, R. Lienhart Intitut
Univerität Augburg à ÊÇÅÍÆ ËÀǼ Approximating Optimal Viual Senor Placement E. Hörter, R. Lienhart Report 2006-01 Januar 2006 Intitut für Informatik D-86135 Augburg Copyright c E. Hörter, R. Lienhart Intitut
Localized Minimum Spanning Tree Based Multicast Routing with Energy-Efficient Guaranteed Delivery in Ad Hoc and Sensor Networks
 Localized Minimum Spanning Tree Baed Multicat Routing with Energy-Efficient Guaranteed Delivery in Ad Hoc and Senor Network Hanne Frey Univerity of Paderborn D-3398 Paderborn hanne.frey@uni-paderborn.de
Localized Minimum Spanning Tree Baed Multicat Routing with Energy-Efficient Guaranteed Delivery in Ad Hoc and Senor Network Hanne Frey Univerity of Paderborn D-3398 Paderborn hanne.frey@uni-paderborn.de
Distributed Packet Processing Architecture with Reconfigurable Hardware Accelerators for 100Gbps Forwarding Performance on Virtualized Edge Router
 Ditributed Packet Proceing Architecture with Reconfigurable Hardware Accelerator for 100Gbp Forwarding Performance on Virtualized Edge Router Satohi Nihiyama, Hitohi Kaneko, and Ichiro Kudo Abtract To
Ditributed Packet Proceing Architecture with Reconfigurable Hardware Accelerator for 100Gbp Forwarding Performance on Virtualized Edge Router Satohi Nihiyama, Hitohi Kaneko, and Ichiro Kudo Abtract To
Increasing Throughput and Reducing Delay in Wireless Sensor Networks Using Interference Alignment
 Int. J. Communication, Network and Sytem Science, 0, 5, 90-97 http://dx.doi.org/0.436/ijcn.0.50 Publihed Online February 0 (http://www.scirp.org/journal/ijcn) Increaing Throughput and Reducing Delay in
Int. J. Communication, Network and Sytem Science, 0, 5, 90-97 http://dx.doi.org/0.436/ijcn.0.50 Publihed Online February 0 (http://www.scirp.org/journal/ijcn) Increaing Throughput and Reducing Delay in
Power Aware Location Aided Routing in Mobile Ad-hoc Networks
 International Journal of Scientific and Reearch Publication, Volume, Iue 1, December 01 1 Power Aware Location Aided Routing in Mobile Ad-hoc Network Anamika Computer Science, Inderprataha Engineering
International Journal of Scientific and Reearch Publication, Volume, Iue 1, December 01 1 Power Aware Location Aided Routing in Mobile Ad-hoc Network Anamika Computer Science, Inderprataha Engineering
Service and Network Management Interworking in Future Wireless Systems
 Service and Network Management Interworking in Future Wirele Sytem V. Tountopoulo V. Stavroulaki P. Demeticha N. Mitrou and M. Theologou National Technical Univerity of Athen Department of Electrical Engineering
Service and Network Management Interworking in Future Wirele Sytem V. Tountopoulo V. Stavroulaki P. Demeticha N. Mitrou and M. Theologou National Technical Univerity of Athen Department of Electrical Engineering
Analyzing Hydra Historical Statistics Part 2
 Analyzing Hydra Hitorical Statitic Part Fabio Maimo Ottaviani EPV Technologie White paper 5 hnode HSM Hitorical Record The hnode i the hierarchical data torage management node and ha to perform all the
Analyzing Hydra Hitorical Statitic Part Fabio Maimo Ottaviani EPV Technologie White paper 5 hnode HSM Hitorical Record The hnode i the hierarchical data torage management node and ha to perform all the
Key Terms - MinMin, MaxMin, Sufferage, Task Scheduling, Standard Deviation, Load Balancing.
 Volume 3, Iue 11, November 2013 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Tak Aignment in
Volume 3, Iue 11, November 2013 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Tak Aignment in
Advanced Encryption Standard and Modes of Operation
 Advanced Encryption Standard and Mode of Operation G. Bertoni L. Breveglieri Foundation of Cryptography - AES pp. 1 / 50 AES Advanced Encryption Standard (AES) i a ymmetric cryptographic algorithm AES
Advanced Encryption Standard and Mode of Operation G. Bertoni L. Breveglieri Foundation of Cryptography - AES pp. 1 / 50 AES Advanced Encryption Standard (AES) i a ymmetric cryptographic algorithm AES
Lecture 14: Minimum Spanning Tree I
 COMPSCI 0: Deign and Analyi of Algorithm October 4, 07 Lecture 4: Minimum Spanning Tree I Lecturer: Rong Ge Scribe: Fred Zhang Overview Thi lecture we finih our dicuion of the hortet path problem and introduce
COMPSCI 0: Deign and Analyi of Algorithm October 4, 07 Lecture 4: Minimum Spanning Tree I Lecturer: Rong Ge Scribe: Fred Zhang Overview Thi lecture we finih our dicuion of the hortet path problem and introduce
Minimum Energy Reliable Paths Using Unreliable Wireless Links
 Minimum Energy Reliable Path Uing Unreliable Wirele Link Qunfeng Dong Department of Computer Science Univerity of Wiconin-Madion Madion, Wiconin 53706 qunfeng@c.wic.edu Micah Adler Department of Computer
Minimum Energy Reliable Path Uing Unreliable Wirele Link Qunfeng Dong Department of Computer Science Univerity of Wiconin-Madion Madion, Wiconin 53706 qunfeng@c.wic.edu Micah Adler Department of Computer
Chapter 13 Non Sampling Errors
 Chapter 13 Non Sampling Error It i a general aumption in the ampling theory that the true value of each unit in the population can be obtained and tabulated without any error. In practice, thi aumption
Chapter 13 Non Sampling Error It i a general aumption in the ampling theory that the true value of each unit in the population can be obtained and tabulated without any error. In practice, thi aumption
Routing Definition 4.1
 4 Routing So far, we have only looked at network without dealing with the iue of how to end information in them from one node to another The problem of ending information in a network i known a routing
4 Routing So far, we have only looked at network without dealing with the iue of how to end information in them from one node to another The problem of ending information in a network i known a routing
A Load Balancing Model based on Load-aware for Distributed Controllers. Fengjun Shang, Wenjuan Gong
 4th International Conference on Machinery, Material and Computing Technology (ICMMCT 2016) A Load Balancing Model baed on Load-aware for Ditributed Controller Fengjun Shang, Wenjuan Gong College of Compute
4th International Conference on Machinery, Material and Computing Technology (ICMMCT 2016) A Load Balancing Model baed on Load-aware for Ditributed Controller Fengjun Shang, Wenjuan Gong College of Compute
ES205 Analysis and Design of Engineering Systems: Lab 1: An Introductory Tutorial: Getting Started with SIMULINK
 ES05 Analyi and Deign of Engineering Sytem: Lab : An Introductory Tutorial: Getting Started with SIMULINK What i SIMULINK? SIMULINK i a oftware package for modeling, imulating, and analyzing dynamic ytem.
ES05 Analyi and Deign of Engineering Sytem: Lab : An Introductory Tutorial: Getting Started with SIMULINK What i SIMULINK? SIMULINK i a oftware package for modeling, imulating, and analyzing dynamic ytem.
Chapter 7 Packet-Switching Networks. Chapter 7 Packet-Switching Networks. Packet Switching. Network Layer. Network Service
 Chapter 7 Packet-Switching etwork etwork Operation & Topology Datagram and Virtual Circuit Structure of a Packet Switch Routing in Packet etwork Shortet Path Routing etwork Chapter 7 Packet-Switching etwork
Chapter 7 Packet-Switching etwork etwork Operation & Topology Datagram and Virtual Circuit Structure of a Packet Switch Routing in Packet etwork Shortet Path Routing etwork Chapter 7 Packet-Switching etwork
Maneuverable Relays to Improve Energy Efficiency in Sensor Networks
 Maneuverable Relay to Improve Energy Efficiency in Senor Network Stephan Eidenbenz, Luka Kroc, Jame P. Smith CCS-5, MS M997; Lo Alamo National Laboratory; Lo Alamo, NM 87545. Email: {eidenben, kroc, jpmith}@lanl.gov
Maneuverable Relay to Improve Energy Efficiency in Senor Network Stephan Eidenbenz, Luka Kroc, Jame P. Smith CCS-5, MS M997; Lo Alamo National Laboratory; Lo Alamo, NM 87545. Email: {eidenben, kroc, jpmith}@lanl.gov
UC Berkeley International Conference on GIScience Short Paper Proceedings
 UC Berkeley International Conference on GIScience Short Paper Proceeding Title A novel method for probabilitic coverage etimation of enor network baed on 3D vector repreentation in complex urban environment
UC Berkeley International Conference on GIScience Short Paper Proceeding Title A novel method for probabilitic coverage etimation of enor network baed on 3D vector repreentation in complex urban environment
A Practical Model for Minimizing Waiting Time in a Transit Network
 A Practical Model for Minimizing Waiting Time in a Tranit Network Leila Dianat, MASc, Department of Civil Engineering, Sharif Univerity of Technology, Tehran, Iran Youef Shafahi, Ph.D. Aociate Profeor,
A Practical Model for Minimizing Waiting Time in a Tranit Network Leila Dianat, MASc, Department of Civil Engineering, Sharif Univerity of Technology, Tehran, Iran Youef Shafahi, Ph.D. Aociate Profeor,
See chapter 8 in the textbook. Dr Muhammad Al Salamah, Industrial Engineering, KFUPM
 Goal programming Objective of the topic: Indentify indutrial baed ituation where two or more objective function are required. Write a multi objective function model dla a goal LP Ue weighting um and preemptive
Goal programming Objective of the topic: Indentify indutrial baed ituation where two or more objective function are required. Write a multi objective function model dla a goal LP Ue weighting um and preemptive
Research Article Energy-Efficient Reservation-Based Medium Access Control Protocol for Wireless Sensor Networks
 Hindawi Publihing Corporation EUASIP Journal on Wirele Communication and Networking Volume 2010, Article ID 878412, 22 page doi:101155/2010/878412 eearch Article Energy-Efficient eervation-baed Medium
Hindawi Publihing Corporation EUASIP Journal on Wirele Communication and Networking Volume 2010, Article ID 878412, 22 page doi:101155/2010/878412 eearch Article Energy-Efficient eervation-baed Medium
SLA Adaptation for Service Overlay Networks
 SLA Adaptation for Service Overlay Network Con Tran 1, Zbigniew Dziong 1, and Michal Pióro 2 1 Department of Electrical Engineering, École de Technologie Supérieure, Univerity of Quebec, Montréal, Canada
SLA Adaptation for Service Overlay Network Con Tran 1, Zbigniew Dziong 1, and Michal Pióro 2 1 Department of Electrical Engineering, École de Technologie Supérieure, Univerity of Quebec, Montréal, Canada
Floating Point CORDIC Based Power Operation
 Floating Point CORDIC Baed Power Operation Kazumi Malhan, Padmaja AVL Electrical and Computer Engineering Department School of Engineering and Computer Science Oakland Univerity, Rocheter, MI e-mail: kmalhan@oakland.edu,
Floating Point CORDIC Baed Power Operation Kazumi Malhan, Padmaja AVL Electrical and Computer Engineering Department School of Engineering and Computer Science Oakland Univerity, Rocheter, MI e-mail: kmalhan@oakland.edu,
Modeling the Effect of Mobile Handoffs on TCP and TFRC Throughput
 Modeling the Effect of Mobile Handoff on TCP and TFRC Throughput Antonio Argyriou and Vijay Madietti School of Electrical and Computer Engineering Georgia Intitute of Technology Atlanta, Georgia 3332 25,
Modeling the Effect of Mobile Handoff on TCP and TFRC Throughput Antonio Argyriou and Vijay Madietti School of Electrical and Computer Engineering Georgia Intitute of Technology Atlanta, Georgia 3332 25,
1 The secretary problem
 Thi i new material: if you ee error, pleae email jtyu at tanford dot edu 1 The ecretary problem We will tart by analyzing the expected runtime of an algorithm, a you will be expected to do on your homework.
Thi i new material: if you ee error, pleae email jtyu at tanford dot edu 1 The ecretary problem We will tart by analyzing the expected runtime of an algorithm, a you will be expected to do on your homework.
Topics. Lecture 37: Global Optimization. Issues. A Simple Example: Copy Propagation X := 3 B > 0 Y := 0 X := 4 Y := Z + W A := 2 * 3X
 Lecture 37: Global Optimization [Adapted from note by R. Bodik and G. Necula] Topic Global optimization refer to program optimization that encompa multiple baic block in a function. (I have ued the term
Lecture 37: Global Optimization [Adapted from note by R. Bodik and G. Necula] Topic Global optimization refer to program optimization that encompa multiple baic block in a function. (I have ued the term
mapping reult. Our experiment have revealed that for many popular tream application, uch a networking and multimedia application, the number of VC nee
 Reolving Deadlock for Pipelined Stream Application on Network-on-Chip Xiaohang Wang 1,2, Peng Liu 1 1 Department of Information Science and Electronic Engineering, Zheiang Univerity Hangzhou, Zheiang,
Reolving Deadlock for Pipelined Stream Application on Network-on-Chip Xiaohang Wang 1,2, Peng Liu 1 1 Department of Information Science and Electronic Engineering, Zheiang Univerity Hangzhou, Zheiang,
A Local Mobility Agent Selection Algorithm for Mobile Networks
 A Local Mobility Agent Selection Algorithm for Mobile Network Yi Xu Henry C. J. Lee Vrizlynn L. L. Thing Intitute for Infocomm Reearch, 21 Heng Mui Keng Terrace, Singapore 119613 Email: {yxu, hlee, vriz}@i2r.a-tar.edu.g
A Local Mobility Agent Selection Algorithm for Mobile Network Yi Xu Henry C. J. Lee Vrizlynn L. L. Thing Intitute for Infocomm Reearch, 21 Heng Mui Keng Terrace, Singapore 119613 Email: {yxu, hlee, vriz}@i2r.a-tar.edu.g
Multi-Target Tracking In Clutter
 Multi-Target Tracking In Clutter John N. Sander-Reed, Mary Jo Duncan, W.B. Boucher, W. Michael Dimmler, Shawn O Keefe ABSTRACT A high frame rate (0 Hz), multi-target, video tracker ha been developed and
Multi-Target Tracking In Clutter John N. Sander-Reed, Mary Jo Duncan, W.B. Boucher, W. Michael Dimmler, Shawn O Keefe ABSTRACT A high frame rate (0 Hz), multi-target, video tracker ha been developed and
Shortest Paths Problem. CS 362, Lecture 20. Today s Outline. Negative Weights
 Shortet Path Problem CS 6, Lecture Jared Saia Univerity of New Mexico Another intereting problem for graph i that of finding hortet path Aume we are given a weighted directed graph G = (V, E) with two
Shortet Path Problem CS 6, Lecture Jared Saia Univerity of New Mexico Another intereting problem for graph i that of finding hortet path Aume we are given a weighted directed graph G = (V, E) with two
The Association of System Performance Professionals
 The Aociation of Sytem Performance Profeional The Computer Meaurement Group, commonly called CMG, i a not for profit, worldwide organization of data proceing profeional committed to the meaurement and
The Aociation of Sytem Performance Profeional The Computer Meaurement Group, commonly called CMG, i a not for profit, worldwide organization of data proceing profeional committed to the meaurement and
Computer Arithmetic Homework Solutions. 1 An adder for graphics. 2 Partitioned adder. 3 HDL implementation of a partitioned adder
 Computer Arithmetic Homework 3 2016 2017 Solution 1 An adder for graphic In a normal ripple carry addition of two poitive number, the carry i the ignal for a reult exceeding the maximum. We ue thi ignal
Computer Arithmetic Homework 3 2016 2017 Solution 1 An adder for graphic In a normal ripple carry addition of two poitive number, the carry i the ignal for a reult exceeding the maximum. We ue thi ignal
A Multi-objective Genetic Algorithm for Reliability Optimization Problem
 International Journal of Performability Engineering, Vol. 5, No. 3, April 2009, pp. 227-234. RAMS Conultant Printed in India A Multi-objective Genetic Algorithm for Reliability Optimization Problem AMAR
International Journal of Performability Engineering, Vol. 5, No. 3, April 2009, pp. 227-234. RAMS Conultant Printed in India A Multi-objective Genetic Algorithm for Reliability Optimization Problem AMAR
Minimum congestion spanning trees in bipartite and random graphs
 Minimum congetion panning tree in bipartite and random graph M.I. Otrovkii Department of Mathematic and Computer Science St. John Univerity 8000 Utopia Parkway Queen, NY 11439, USA e-mail: otrovm@tjohn.edu
Minimum congetion panning tree in bipartite and random graph M.I. Otrovkii Department of Mathematic and Computer Science St. John Univerity 8000 Utopia Parkway Queen, NY 11439, USA e-mail: otrovm@tjohn.edu
HAUSDORFF CLUSTERING AND MINIMUM ENERGY ROUTING FOR WIRELESS SENSOR NETWORKS
 The 8th Annual IEEE International Sympoium on Peronal, Indoor and Mobile Radio Communication (PIMRC'7) HAUSDORFF CLUSTERIG AD MIIMUM EERGY ROUTIG FOR WIRELESS SESOR ETWORKS Xiaorong ZHU Lianfeng SHE the
The 8th Annual IEEE International Sympoium on Peronal, Indoor and Mobile Radio Communication (PIMRC'7) HAUSDORFF CLUSTERIG AD MIIMUM EERGY ROUTIG FOR WIRELESS SESOR ETWORKS Xiaorong ZHU Lianfeng SHE the
Planning of scooping position and approach path for loading operation by wheel loader
 22 nd International Sympoium on Automation and Robotic in Contruction ISARC 25 - September 11-14, 25, Ferrara (Italy) 1 Planning of cooping poition and approach path for loading operation by wheel loader
22 nd International Sympoium on Automation and Robotic in Contruction ISARC 25 - September 11-14, 25, Ferrara (Italy) 1 Planning of cooping poition and approach path for loading operation by wheel loader
MAT 155: Describing, Exploring, and Comparing Data Page 1 of NotesCh2-3.doc
 MAT 155: Decribing, Exploring, and Comparing Data Page 1 of 8 001-oteCh-3.doc ote for Chapter Summarizing and Graphing Data Chapter 3 Decribing, Exploring, and Comparing Data Frequency Ditribution, Graphic
MAT 155: Decribing, Exploring, and Comparing Data Page 1 of 8 001-oteCh-3.doc ote for Chapter Summarizing and Graphing Data Chapter 3 Decribing, Exploring, and Comparing Data Frequency Ditribution, Graphic
SECTOR BASED MULTICAST ROUTING ALGORITHM FOR MOBILE AD-HOC NETWORKS
 SECTOR BASED MULTICAST ROUTING ALGORITHM OR MOBILE AD-HOC NETWORKS Murali Paramewaran 1 and Chittaranjan Hota 2 1 Department of Computer Science & Information Sytem, BITS-Pilani, Pilani, India 2 Department
SECTOR BASED MULTICAST ROUTING ALGORITHM OR MOBILE AD-HOC NETWORKS Murali Paramewaran 1 and Chittaranjan Hota 2 1 Department of Computer Science & Information Sytem, BITS-Pilani, Pilani, India 2 Department
How to Select Measurement Points in Access Point Localization
 Proceeding of the International MultiConference of Engineer and Computer Scientit 205 Vol II, IMECS 205, March 8-20, 205, Hong Kong How to Select Meaurement Point in Acce Point Localization Xiaoling Yang,
Proceeding of the International MultiConference of Engineer and Computer Scientit 205 Vol II, IMECS 205, March 8-20, 205, Hong Kong How to Select Meaurement Point in Acce Point Localization Xiaoling Yang,
Today s Outline. CS 561, Lecture 23. Negative Weights. Shortest Paths Problem. The presence of a negative cycle might mean that there is
 Today Outline CS 56, Lecture Jared Saia Univerity of New Mexico The path that can be trodden i not the enduring and unchanging Path. The name that can be named i not the enduring and unchanging Name. -
Today Outline CS 56, Lecture Jared Saia Univerity of New Mexico The path that can be trodden i not the enduring and unchanging Path. The name that can be named i not the enduring and unchanging Name. -
Compressed Sensing Image Processing Based on Stagewise Orthogonal Matching Pursuit
 Senor & randucer, Vol. 8, Iue 0, October 204, pp. 34-40 Senor & randucer 204 by IFSA Publihing, S. L. http://www.enorportal.com Compreed Sening Image Proceing Baed on Stagewie Orthogonal Matching Puruit
Senor & randucer, Vol. 8, Iue 0, October 204, pp. 34-40 Senor & randucer 204 by IFSA Publihing, S. L. http://www.enorportal.com Compreed Sening Image Proceing Baed on Stagewie Orthogonal Matching Puruit
CENTER-POINT MODEL OF DEFORMABLE SURFACE
 CENTER-POINT MODEL OF DEFORMABLE SURFACE Piotr M. Szczypinki Iintitute of Electronic, Technical Univerity of Lodz, Poland Abtract: Key word: Center-point model of deformable urface for egmentation of 3D
CENTER-POINT MODEL OF DEFORMABLE SURFACE Piotr M. Szczypinki Iintitute of Electronic, Technical Univerity of Lodz, Poland Abtract: Key word: Center-point model of deformable urface for egmentation of 3D
Modelling the impact of cyber attacks on the traffic control centre of an urban automobile transport system by means of enhanced cybersecurity
 Modelling the impact of cyber attack on the traffic control centre of an urban automobile tranport ytem by mean of enhanced cyberecurity Yoana Ivanova 1,* 1 Bulgarian Academy of Science, Intitute of ICT,
Modelling the impact of cyber attack on the traffic control centre of an urban automobile tranport ytem by mean of enhanced cyberecurity Yoana Ivanova 1,* 1 Bulgarian Academy of Science, Intitute of ICT,
(12) Patent Application Publication (10) Pub. No.: US 2011/ A1
 (19) United State US 2011 0316690A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0316690 A1 Siegman (43) Pub. Date: Dec. 29, 2011 (54) SYSTEMAND METHOD FOR IDENTIFYING ELECTRICAL EQUIPMENT
(19) United State US 2011 0316690A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0316690 A1 Siegman (43) Pub. Date: Dec. 29, 2011 (54) SYSTEMAND METHOD FOR IDENTIFYING ELECTRICAL EQUIPMENT
Multicast with Network Coding in Application-Layer Overlay Networks
 IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS, VOL. 22, NO. 1, JANUARY 2004 1 Multicat with Network Coding in Application-Layer Overlay Network Ying Zhu, Baochun Li, Member, IEEE, and Jiang Guo Abtract
IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS, VOL. 22, NO. 1, JANUARY 2004 1 Multicat with Network Coding in Application-Layer Overlay Network Ying Zhu, Baochun Li, Member, IEEE, and Jiang Guo Abtract
Diverse: Application-Layer Service Differentiation in Peer-to-Peer Communications
 Divere: Application-Layer Service Differentiation in Peer-to-Peer Communication Chuan Wu, Student Member, IEEE, Baochun Li, Senior Member, IEEE Department of Electrical and Computer Engineering Univerity
Divere: Application-Layer Service Differentiation in Peer-to-Peer Communication Chuan Wu, Student Member, IEEE, Baochun Li, Senior Member, IEEE Department of Electrical and Computer Engineering Univerity
Priority-Based Distribution Trees for Application-Level Multicast
 Priority-Baed Ditribution Tree for Application-Level Multicat Jürgen Vogel, Jörg Widmer, Dirk Farin, Martin Mauve, Wolfgang Effelberg Praktiche Informatik IV, Univerity of Mannheim, Germany vogel, widmer,
Priority-Baed Ditribution Tree for Application-Level Multicat Jürgen Vogel, Jörg Widmer, Dirk Farin, Martin Mauve, Wolfgang Effelberg Praktiche Informatik IV, Univerity of Mannheim, Germany vogel, widmer,
Modeling of underwater vehicle s dynamics
 Proceeding of the 11th WEA International Conference on YTEM, Agio Nikolao, Crete Iland, Greece, July 23-25, 2007 44 Modeling of underwater vehicle dynamic ANDRZEJ ZAK Department of Radiolocation and Hydrolocation
Proceeding of the 11th WEA International Conference on YTEM, Agio Nikolao, Crete Iland, Greece, July 23-25, 2007 44 Modeling of underwater vehicle dynamic ANDRZEJ ZAK Department of Radiolocation and Hydrolocation
Lecture Outline. Global flow analysis. Global Optimization. Global constant propagation. Liveness analysis. Local Optimization. Global Optimization
 Lecture Outline Global flow analyi Global Optimization Global contant propagation Livene analyi Adapted from Lecture by Prof. Alex Aiken and George Necula (UCB) CS781(Praad) L27OP 1 CS781(Praad) L27OP
Lecture Outline Global flow analyi Global Optimization Global contant propagation Livene analyi Adapted from Lecture by Prof. Alex Aiken and George Necula (UCB) CS781(Praad) L27OP 1 CS781(Praad) L27OP
Policy-based Injection of Private Traffic into a Public SDN Testbed
 Intitut für Techniche Informatik und Kommunikationnetze Adrian Friedli Policy-baed Injection of Private Traffic into a Public SDN Tetbed Mater Thei MA-2013-12 Advior: Dr. Bernhard Ager, Vaileio Kotroni
Intitut für Techniche Informatik und Kommunikationnetze Adrian Friedli Policy-baed Injection of Private Traffic into a Public SDN Tetbed Mater Thei MA-2013-12 Advior: Dr. Bernhard Ager, Vaileio Kotroni
Keywords Cloud Computing, Service Level Agreements (SLA), CloudSim, Monitoring & Controlling SLA Agent, JADE
 Volume 5, Iue 8, Augut 2015 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Verification of Agent
Volume 5, Iue 8, Augut 2015 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Verification of Agent
Refining SIRAP with a Dedicated Resource Ceiling for Self-Blocking
 Refining SIRAP with a Dedicated Reource Ceiling for Self-Blocking Mori Behnam, Thoma Nolte Mälardalen Real-Time Reearch Centre P.O. Box 883, SE-721 23 Väterå, Sweden {mori.behnam,thoma.nolte}@mdh.e ABSTRACT
Refining SIRAP with a Dedicated Reource Ceiling for Self-Blocking Mori Behnam, Thoma Nolte Mälardalen Real-Time Reearch Centre P.O. Box 883, SE-721 23 Väterå, Sweden {mori.behnam,thoma.nolte}@mdh.e ABSTRACT
Research Article Real-Time Communications in Large-Scale Wireless Networks
 Hindawi Publihing Corporation International Journal of Digital Multimedia Broadcating Volume 2008, Article ID 586067, 16 page doi:10.1155/2008/586067 eearch Article eal-time Communication in Large-Scale
Hindawi Publihing Corporation International Journal of Digital Multimedia Broadcating Volume 2008, Article ID 586067, 16 page doi:10.1155/2008/586067 eearch Article eal-time Communication in Large-Scale
(12) Patent Application Publication (10) Pub. No.: US 2003/ A1
 US 2003O196031A1 (19) United State (12) Patent Application Publication (10) Pub. No.: US 2003/0196031 A1 Chen (43) Pub. Date: Oct. 16, 2003 (54) STORAGE CONTROLLER WITH THE DISK Related U.S. Application
US 2003O196031A1 (19) United State (12) Patent Application Publication (10) Pub. No.: US 2003/0196031 A1 Chen (43) Pub. Date: Oct. 16, 2003 (54) STORAGE CONTROLLER WITH THE DISK Related U.S. Application
Analysis of the results of analytical and simulation With the network model and dynamic priority Unchecked Buffer
 International Reearch Journal of Applied and Baic Science 218 Available online at www.irjab.com ISSN 2251-838X / Vol, 12 (1): 49-53 Science Explorer Publication Analyi of the reult of analytical and imulation
International Reearch Journal of Applied and Baic Science 218 Available online at www.irjab.com ISSN 2251-838X / Vol, 12 (1): 49-53 Science Explorer Publication Analyi of the reult of analytical and imulation
Generic Traverse. CS 362, Lecture 19. DFS and BFS. Today s Outline
 Generic Travere CS 62, Lecture 9 Jared Saia Univerity of New Mexico Travere(){ put (nil,) in bag; while (the bag i not empty){ take ome edge (p,v) from the bag if (v i unmarked) mark v; parent(v) = p;
Generic Travere CS 62, Lecture 9 Jared Saia Univerity of New Mexico Travere(){ put (nil,) in bag; while (the bag i not empty){ take ome edge (p,v) from the bag if (v i unmarked) mark v; parent(v) = p;
Performance of Energy-Efficient TDMA Schemes in Data-Gathering Scenarios with Periodic Sources
 Performance of Energy-Efficient TDMA Scheme in Data-Gathering Scenario with Periodic Source Chritian Renner, Volker Turau, and Chritoph Weyer Abtract Energy-efficient tranportation of periodical enor reading
Performance of Energy-Efficient TDMA Scheme in Data-Gathering Scenario with Periodic Source Chritian Renner, Volker Turau, and Chritoph Weyer Abtract Energy-efficient tranportation of periodical enor reading
An Algebraic Approach to Adaptive Scalable Overlay Network Monitoring
 An Algebraic Approach to Adaptive Scalable Overlay Network Monitoring ABSTRACT Overlay network monitoring enable ditributed Internet application to detect and recover from path outage and period of degraded
An Algebraic Approach to Adaptive Scalable Overlay Network Monitoring ABSTRACT Overlay network monitoring enable ditributed Internet application to detect and recover from path outage and period of degraded
A Handover Scheme for Mobile WiMAX Using Signal Strength and Distance
 A Handover Scheme for Mobile WiMAX Uing Signal Strength and Ditance Mary Alatie, Mjumo Mzyece and Anih Kurien Department of Electrical Engineering/French South African Intitute of Technology (F SATI) Thwane
A Handover Scheme for Mobile WiMAX Uing Signal Strength and Ditance Mary Alatie, Mjumo Mzyece and Anih Kurien Department of Electrical Engineering/French South African Intitute of Technology (F SATI) Thwane
999 Computer System Network. (12) Patent Application Publication (10) Pub. No.: US 2006/ A1. (19) United States
 (19) United State US 2006O1296.60A1 (12) Patent Application Publication (10) Pub. No.: Mueller et al. (43) Pub. Date: Jun. 15, 2006 (54) METHOD AND COMPUTER SYSTEM FOR QUEUE PROCESSING (76) Inventor: Wolfgang
(19) United State US 2006O1296.60A1 (12) Patent Application Publication (10) Pub. No.: Mueller et al. (43) Pub. Date: Jun. 15, 2006 (54) METHOD AND COMPUTER SYSTEM FOR QUEUE PROCESSING (76) Inventor: Wolfgang
else end while End References
 621-630. [RM89] [SK76] Roenfeld, A. and Melter, R. A., Digital geometry, The Mathematical Intelligencer, vol. 11, No. 3, 1989, pp. 69-72. Sklanky, J. and Kibler, D. F., A theory of nonuniformly digitized
621-630. [RM89] [SK76] Roenfeld, A. and Melter, R. A., Digital geometry, The Mathematical Intelligencer, vol. 11, No. 3, 1989, pp. 69-72. Sklanky, J. and Kibler, D. F., A theory of nonuniformly digitized
Aspects of Formal and Graphical Design of a Bus System
 Apect of Formal and Graphical Deign of a Bu Sytem Tiberiu Seceleanu Univerity of Turku, Dpt. of Information Technology Turku, Finland tiberiu.eceleanu@utu.fi Tomi Weterlund Turku Centre for Computer Science
Apect of Formal and Graphical Deign of a Bu Sytem Tiberiu Seceleanu Univerity of Turku, Dpt. of Information Technology Turku, Finland tiberiu.eceleanu@utu.fi Tomi Weterlund Turku Centre for Computer Science
Optimal Gossip with Direct Addressing
 Optimal Goip with Direct Addreing Bernhard Haeupler Microoft Reearch 1065 La Avenida, Mountain View Mountain View, CA 94043 haeupler@c.cmu.edu Dahlia Malkhi Microoft Reearch 1065 La Avenida, Mountain View
Optimal Goip with Direct Addreing Bernhard Haeupler Microoft Reearch 1065 La Avenida, Mountain View Mountain View, CA 94043 haeupler@c.cmu.edu Dahlia Malkhi Microoft Reearch 1065 La Avenida, Mountain View
SIMIT 7. Component Type Editor (CTE) User manual. Siemens Industrial
 SIMIT 7 Component Type Editor (CTE) Uer manual Siemen Indutrial Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult
SIMIT 7 Component Type Editor (CTE) Uer manual Siemen Indutrial Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult
Optimization Coverage of Wireless Sensor Networks Based on Energy Saving. Technology, Luoyang , China. Xi an , China
 , pp.35-48 http://dx.doi.org/10.1457/ijfgcn.014.7.4.04 Optimization Coverage of Wirele Senor Network Baed on Energy Saving Zeyu Sun 1, Heng Li 1, Heng Chen and Wei Wei 3 1 Computer and Information Engineering,
, pp.35-48 http://dx.doi.org/10.1457/ijfgcn.014.7.4.04 Optimization Coverage of Wirele Senor Network Baed on Energy Saving Zeyu Sun 1, Heng Li 1, Heng Chen and Wei Wei 3 1 Computer and Information Engineering,
Shortest Path Routing in Arbitrary Networks
 Journal of Algorithm, Vol 31(1), 1999 Shortet Path Routing in Arbitrary Network Friedhelm Meyer auf der Heide and Berthold Vöcking Department of Mathematic and Computer Science and Heinz Nixdorf Intitute,
Journal of Algorithm, Vol 31(1), 1999 Shortet Path Routing in Arbitrary Network Friedhelm Meyer auf der Heide and Berthold Vöcking Department of Mathematic and Computer Science and Heinz Nixdorf Intitute,
Modeling and Analysis of Slow CW Decrease for IEEE WLAN
 Modeling and Analyi of Slow CW Decreae for IEEE 82. WLAN Qiang Ni, Imad Aad 2, Chadi Barakat, and Thierry Turletti Planete Group 2 Planete Group INRIA Sophia Antipoli INRIA Rhône-Alpe Sophia Antipoli,
Modeling and Analyi of Slow CW Decreae for IEEE 82. WLAN Qiang Ni, Imad Aad 2, Chadi Barakat, and Thierry Turletti Planete Group 2 Planete Group INRIA Sophia Antipoli INRIA Rhône-Alpe Sophia Antipoli,
A User-Attention Based Focus Detection Framework and Its Applications
 A Uer-Attention Baed Focu Detection Framework and It Application Chia-Chiang Ho, Wen-Huang Cheng, Ting-Jian Pan, Ja-Ling Wu Communication and Multimedia Laboratory, Department of Computer Science and Information
A Uer-Attention Baed Focu Detection Framework and It Application Chia-Chiang Ho, Wen-Huang Cheng, Ting-Jian Pan, Ja-Ling Wu Communication and Multimedia Laboratory, Department of Computer Science and Information
Through the Diversity of Bandwidth-Related Metrics, Estimation Techniques and Tools: An Overview
 I. J. Computer Network and Information Security, 08, 8, -6 Publihed Oine Augut 08 in MECS (http://www.mec-pre.org/) DOI: 0.585/icni.08.08.0 Through the Diverity of Bandwidth-Related Metric, Etimation Technique
I. J. Computer Network and Information Security, 08, 8, -6 Publihed Oine Augut 08 in MECS (http://www.mec-pre.org/) DOI: 0.585/icni.08.08.0 Through the Diverity of Bandwidth-Related Metric, Etimation Technique
SIMIT 7. Profinet IO Gateway. User Manual
 SIMIT 7 Profinet IO Gateway Uer Manual Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult are only non-binding uggetion
SIMIT 7 Profinet IO Gateway Uer Manual Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult are only non-binding uggetion
TFRC-CR: An Equation-based Transport Protocol for Cognitive Radio Networks
 213 International onference on omputing, Networking and ommunication (IN) Workhop on omputing, Networking and ommunication -R: An Equation-baed Tranport Protocol for ognitive Radio Network Abdulla K. Al-Ali
213 International onference on omputing, Networking and ommunication (IN) Workhop on omputing, Networking and ommunication -R: An Equation-baed Tranport Protocol for ognitive Radio Network Abdulla K. Al-Ali
Stochastic Search and Graph Techniques for MCM Path Planning Christine D. Piatko, Christopher P. Diehl, Paul McNamee, Cheryl Resch and I-Jeng Wang
 Stochatic Search and Graph Technique for MCM Path Planning Chritine D. Piatko, Chritopher P. Diehl, Paul McNamee, Cheryl Rech and I-Jeng Wang The John Hopkin Univerity Applied Phyic Laboratory, Laurel,
Stochatic Search and Graph Technique for MCM Path Planning Chritine D. Piatko, Chritopher P. Diehl, Paul McNamee, Cheryl Rech and I-Jeng Wang The John Hopkin Univerity Applied Phyic Laboratory, Laurel,
/06/$ IEEE 364
 006 IEEE International ympoium on ignal Proceing and Information Technology oie Variance Etimation In ignal Proceing David Makovoz IPAC, California Intitute of Technology, MC-0, Paadena, CA, 95 davidm@ipac.caltech.edu;
006 IEEE International ympoium on ignal Proceing and Information Technology oie Variance Etimation In ignal Proceing David Makovoz IPAC, California Intitute of Technology, MC-0, Paadena, CA, 95 davidm@ipac.caltech.edu;
An Approach to a Test Oracle for XML Query Testing
 An Approach to a Tet Oracle for XML Query Teting Dae S. Kim-Park, Claudio de la Riva, Javier Tuya Univerity of Oviedo Computing Department Campu of Vieque, /n, 33204 (SPAIN) kim_park@li.uniovi.e, claudio@uniovi.e,
An Approach to a Tet Oracle for XML Query Teting Dae S. Kim-Park, Claudio de la Riva, Javier Tuya Univerity of Oviedo Computing Department Campu of Vieque, /n, 33204 (SPAIN) kim_park@li.uniovi.e, claudio@uniovi.e,
DECENTRALIZED structured overlays and distributed. Distributed, Secure Load Balancing with Skew, Heterogeneity, and Churn
 Harvard Technical Report TR-3-4 Ditributed, Secure Load Balancing with Skew, Heterogeneity, and Churn Jonathan Ledlie and Margo Seltzer Abtract Numerou propoal exit for load balancing in peer-to-peer (pp)
Harvard Technical Report TR-3-4 Ditributed, Secure Load Balancing with Skew, Heterogeneity, and Churn Jonathan Ledlie and Margo Seltzer Abtract Numerou propoal exit for load balancing in peer-to-peer (pp)
A Linear Interpolation-Based Algorithm for Path Planning and Replanning on Girds *
 Advance in Linear Algebra & Matrix Theory, 2012, 2, 20-24 http://dx.doi.org/10.4236/alamt.2012.22003 Publihed Online June 2012 (http://www.scirp.org/journal/alamt) A Linear Interpolation-Baed Algorithm
Advance in Linear Algebra & Matrix Theory, 2012, 2, 20-24 http://dx.doi.org/10.4236/alamt.2012.22003 Publihed Online June 2012 (http://www.scirp.org/journal/alamt) A Linear Interpolation-Baed Algorithm
DWH Performance Tuning For Better Reporting
 DWH Performance Tuning For Better Sandeep Bhargava Reearch Scholar Naveen Hemrajani Aociate Profeor Dineh Goyal Aociate Profeor Subhah Gander IT Profeional ABSTRACT: The concept of data warehoue deal in
DWH Performance Tuning For Better Sandeep Bhargava Reearch Scholar Naveen Hemrajani Aociate Profeor Dineh Goyal Aociate Profeor Subhah Gander IT Profeional ABSTRACT: The concept of data warehoue deal in
Software Agent (SA) to guarantee QoS for multi constrain applications in all-ip networks
 Software Agent (SA) to guarantee QoS for multi contrain application in all-ip network Kazi Khaled Al-Zahid and Mituji Matumoto GITS, Waeda Univerity 94 Waeda Univ. Bldg. A-308, 1011Okuboyama Nihitomida
Software Agent (SA) to guarantee QoS for multi contrain application in all-ip network Kazi Khaled Al-Zahid and Mituji Matumoto GITS, Waeda Univerity 94 Waeda Univ. Bldg. A-308, 1011Okuboyama Nihitomida
LinkGuide: Towards a Better Collection of Hyperlinks in a Website Homepage
 Proceeding of the World Congre on Engineering 2007 Vol I LinkGuide: Toward a Better Collection of Hyperlink in a Webite Homepage A. Ammari and V. Zharkova chool of Informatic, Univerity of Bradford anammari@bradford.ac.uk,
Proceeding of the World Congre on Engineering 2007 Vol I LinkGuide: Toward a Better Collection of Hyperlink in a Webite Homepage A. Ammari and V. Zharkova chool of Informatic, Univerity of Bradford anammari@bradford.ac.uk,
Distributed Media-Aware Rate Allocation for Video Multicast over Wireless Networks
 Ditributed Media-Aware Rate Allocation for Video Multicat over Wirele Network Xiaoqing Zhu, Thoma Schierl, Thoma Wiegand, Senior Member, IEEE, and Bernd Girod, Fellow, IEEE Abtract A unified optimization
Ditributed Media-Aware Rate Allocation for Video Multicat over Wirele Network Xiaoqing Zhu, Thoma Schierl, Thoma Wiegand, Senior Member, IEEE, and Bernd Girod, Fellow, IEEE Abtract A unified optimization
Embedding Service Function Tree with Minimum Cost for NFV Enabled Multicast
 1 Embedding Service Function Tree with Minimum ot for NFV Enabled Multicat angbang Ren, Student Member, IEEE, eke Guo, Senior Member, IEEE, Yulong Shen, Member, IEEE, Guoming Tang, Member, IEEE, Xu Lin,
1 Embedding Service Function Tree with Minimum ot for NFV Enabled Multicat angbang Ren, Student Member, IEEE, eke Guo, Senior Member, IEEE, Yulong Shen, Member, IEEE, Guoming Tang, Member, IEEE, Xu Lin,
Efficient Data Forwarding in Mobile Social Networks with Diverse Connectivity Characteristics
 Efficient Data Forwarding in Mobile Social Network with Divere Connectivity Characteritic Xiaomei Zhang and Guohong Cao Department of Computer Science and Engineering The Pennylvania State Univerity, Univerity
Efficient Data Forwarding in Mobile Social Network with Divere Connectivity Characteritic Xiaomei Zhang and Guohong Cao Department of Computer Science and Engineering The Pennylvania State Univerity, Univerity
A New Approach to Pipeline FFT Processor
 A ew Approach to Pipeline FFT Proceor Shouheng He and Mat Torkelon Department of Applied Electronic, Lund Univerity S- Lund, SWEDE email: he@tde.lth.e; torkel@tde.lth.e Abtract A new VLSI architecture
A ew Approach to Pipeline FFT Proceor Shouheng He and Mat Torkelon Department of Applied Electronic, Lund Univerity S- Lund, SWEDE email: he@tde.lth.e; torkel@tde.lth.e Abtract A new VLSI architecture
Optimal Peer-to-Peer Technique for Massive Content Distribution
 1 Optimal Peer-to-Peer Technique for Maive Content Ditribution Xiaoying Zheng, Chunglae Cho and Ye Xia Computer and Information Science and Engineering Department Univerity of Florida Email: {xiazheng,
1 Optimal Peer-to-Peer Technique for Maive Content Ditribution Xiaoying Zheng, Chunglae Cho and Ye Xia Computer and Information Science and Engineering Department Univerity of Florida Email: {xiazheng,
Hassan Ghaziri AUB, OSB Beirut, Lebanon Key words Competitive self-organizing maps, Meta-heuristics, Vehicle routing problem,
 COMPETITIVE PROBABIISTIC SEF-ORGANIZING MAPS FOR ROUTING PROBEMS Haan Ghaziri AUB, OSB Beirut, ebanon ghaziri@aub.edu.lb Abtract In thi paper, we have applied the concept of the elf-organizing map (SOM)
COMPETITIVE PROBABIISTIC SEF-ORGANIZING MAPS FOR ROUTING PROBEMS Haan Ghaziri AUB, OSB Beirut, ebanon ghaziri@aub.edu.lb Abtract In thi paper, we have applied the concept of the elf-organizing map (SOM)
A note on degenerate and spectrally degenerate graphs
 A note on degenerate and pectrally degenerate graph Noga Alon Abtract A graph G i called pectrally d-degenerate if the larget eigenvalue of each ubgraph of it with maximum degree D i at mot dd. We prove
A note on degenerate and pectrally degenerate graph Noga Alon Abtract A graph G i called pectrally d-degenerate if the larget eigenvalue of each ubgraph of it with maximum degree D i at mot dd. We prove
xy-monotone path existence queries in a rectilinear environment
 CCCG 2012, Charlottetown, P.E.I., Augut 8 10, 2012 xy-monotone path exitence querie in a rectilinear environment Gregory Bint Anil Mahehwari Michiel Smid Abtract Given a planar environment coniting of
CCCG 2012, Charlottetown, P.E.I., Augut 8 10, 2012 xy-monotone path exitence querie in a rectilinear environment Gregory Bint Anil Mahehwari Michiel Smid Abtract Given a planar environment coniting of
Separation of Routing and Scheduling in Backpressure- Based Wireless Networks
 Separation of Routing and Scheduling in - Baed Wirele Network The MIT Faculty ha made thi article openly available. Pleae hare how thi acce benefit you. Your tory matter. Citation A Publihed Publiher Seferoglu,
Separation of Routing and Scheduling in - Baed Wirele Network The MIT Faculty ha made thi article openly available. Pleae hare how thi acce benefit you. Your tory matter. Citation A Publihed Publiher Seferoglu,
Lecture 6: Multicast. Multicast Motivation. Multicast Efficiency. Native IP Multicast Service Model. Native IP Multicast Service Model
 Lecture 6: Multicat Challene: how do we efficiently end meae to a roup of machine? Need to reviit all apect of networkin outin Autonomou ytem and admin control Addre allocation Conetion control eliable
Lecture 6: Multicat Challene: how do we efficiently end meae to a roup of machine? Need to reviit all apect of networkin outin Autonomou ytem and admin control Addre allocation Conetion control eliable
Karen L. Collins. Wesleyan University. Middletown, CT and. Mark Hovey MIT. Cambridge, MA Abstract
 Mot Graph are Edge-Cordial Karen L. Collin Dept. of Mathematic Weleyan Univerity Middletown, CT 6457 and Mark Hovey Dept. of Mathematic MIT Cambridge, MA 239 Abtract We extend the definition of edge-cordial
Mot Graph are Edge-Cordial Karen L. Collin Dept. of Mathematic Weleyan Univerity Middletown, CT 6457 and Mark Hovey Dept. of Mathematic MIT Cambridge, MA 239 Abtract We extend the definition of edge-cordial
A METHOD OF REAL-TIME NURBS INTERPOLATION WITH CONFINED CHORD ERROR FOR CNC SYSTEMS
 Vietnam Journal of Science and Technology 55 (5) (017) 650-657 DOI: 10.1565/55-518/55/5/906 A METHOD OF REAL-TIME NURBS INTERPOLATION WITH CONFINED CHORD ERROR FOR CNC SYSTEMS Nguyen Huu Quang *, Banh
Vietnam Journal of Science and Technology 55 (5) (017) 650-657 DOI: 10.1565/55-518/55/5/906 A METHOD OF REAL-TIME NURBS INTERPOLATION WITH CONFINED CHORD ERROR FOR CNC SYSTEMS Nguyen Huu Quang *, Banh
Joint Congestion Control and Media Access Control Design for Ad Hoc Wireless Networks
 Joint Congetion Control and Media Acce Control Deign for Ad Hoc Wirele Network Lijun Chen, Steven H. Low and John C. Doyle Engineering & Applied Science Diviion, California Intitute of Technology Paadena,
Joint Congetion Control and Media Acce Control Deign for Ad Hoc Wirele Network Lijun Chen, Steven H. Low and John C. Doyle Engineering & Applied Science Diviion, California Intitute of Technology Paadena,
AN ALGORITHM FOR RESTRICTED NORMAL FORM TO SOLVE DUAL TYPE NON-CANONICAL LINEAR FRACTIONAL PROGRAMMING PROBLEM
 RAC Univerity Journal, Vol IV, No, 7, pp 87-9 AN ALGORITHM FOR RESTRICTED NORMAL FORM TO SOLVE DUAL TYPE NON-CANONICAL LINEAR FRACTIONAL PROGRAMMING PROLEM Mozzem Hoain Department of Mathematic Ghior Govt
RAC Univerity Journal, Vol IV, No, 7, pp 87-9 AN ALGORITHM FOR RESTRICTED NORMAL FORM TO SOLVE DUAL TYPE NON-CANONICAL LINEAR FRACTIONAL PROGRAMMING PROLEM Mozzem Hoain Department of Mathematic Ghior Govt
Landmark Selection and Greedy Landmark-Descent Routing for Sensor Networks
 1 Landmark Selection and Greedy Landmark-Decent Routing for Senor Network An Nguyen Nikola Miloavljević Qing Fang Jie Gao Leonida J. Guiba Department of Computer Science, Stanford Univerity. {anguyen,nikolam,guiba}@c.tanford.edu
1 Landmark Selection and Greedy Landmark-Decent Routing for Senor Network An Nguyen Nikola Miloavljević Qing Fang Jie Gao Leonida J. Guiba Department of Computer Science, Stanford Univerity. {anguyen,nikolam,guiba}@c.tanford.edu
