Through the Diversity of Bandwidth-Related Metrics, Estimation Techniques and Tools: An Overview
|
|
|
- Spencer Butler
- 5 years ago
- Views:
Transcription
1 I. J. Computer Network and Information Security, 08, 8, -6 Publihed Oine Augut 08 in MECS ( DOI: 0.585/icni Through the Diverity of Bandwidth-Related Metric, Etimation Technique and Tool: An Overview Fatih Abut Adana Science and Technology Univerity, Dept. of Computer Engineering, Adana, 050, Turkey Received: 07 June 08; Accepted: 03 July 08; Publihed: 08 Augut 08 Abtract The knowledge of bandwidth in communication network can be ueful in variou application. Some popular example are validation of ervice level agreement, traffic engineering and capacity planning upport, detection of congeted or underutilized link, optimization of network route election, dynamic erver election for dowoad and viualizing network topologie, to name ut a few. Following thee variou motivation, a variety of bandwidth etimation technique and tool have been propoed in the lat decade and till, everal new one are currently being introduced. They all how a wide pectrum of different aumption, characteritic, advantage and limitation. In thi paper, the bandwidth etimation literature i reviewed, with focu on introducing four pecific bandwidth-related metric including capacity,, achievable throughput and bulk tranfer capacity (BTC); decribing the main characteritic, trength and weaknee of maor bandwidth etimation technique a well a claifying the repective tool implementation. Alo, the fundamental challenge, practical iue and difficultie faced by deigning and implementing bandwidth etimation technique are addreed. Index Term Capacity, Available Bandwidth, Throughput, Etimation Technique, Active Probing, Quality of Service. I. INTRODUCTION Bandwidth ha been a critical and preciou reource in variou kind of network. Having a good etimate of bandwidth i, for example, important for network error detection and diagnoi a well a for efficient operation of bandwidth dependent/data-intenive Internet application. Some popular example where knowledge of bandwidth can be valuable are validation of ervice level agreement, detection of congeted or underutilized link and capacity planning upport, admiion control policie at maively-acceed content erver, network tomography for tracking and viualizing Internet topology, dynamic erver election for dowoad, optimized congetion control for reliable tranport protocol (e.g. for TCP) and optimized network route election. Figure how an overview of maor bandwidth etimation technique and tool. They maiy etimate one of three related metric: capacity, available bandwidth and throughput. The latter can, in turn, be divided into achievable throughput and bulk tranfer capacity (BTC). The etimation of each metric i aociated at leat with one etimation technique wherea one and the ame metric can alo be etimated with everal and independent etimation technique in different way. Repreentative example of etimation technique ued by different etimation tool range from Packet Pair (PP) and Variable Packet Size (VPS) etimating the end-to-end and hop-by-hop capacity, repectively, to Probe Rate Model (PRM) and Probe Gap Model (PGM) etimating the end-to-end available bandwidth to TCP connection or emulation ued for meauring end-to-end achievable throughput and BTC metric. Etimation technique hown in Figure are repreented by everal variou tool implementation. They all how a wide pectrum of different aumption, characteritic, advantage and limitation: Active v. paive etimation tool Intruive v. lightweight etimation tool Single-ended v. double-ended etimation tool Offline v. oine (or real-time) etimation tool Ability to meaure aymmetric, wirele or highpeed link Different level of achievable etimation accuracy Difference in etimation time needed and probing overhead caued From the point of a uer view, the wihing lit for an ideal etimation technique and tool i long and manifold, and include requirement uch a accurate, conitent and reliable etimate; low overhead, fat and robut etimation procedure; reilience to both cro traffic and it rapid changing condition; independence of the meaurement end-hot performance and ytem capabilitie; and finally, applicability to mixed path coniting of wired, high-peed and/or wirele link. Copyright 08 MECS I.J. Computer Network and Information Security, 08, 8, -6
2 Through the Diverity of Bandwidth-Related Metric, Etimation Technique and Tool: An Overview metric Capacity Available Bandwidth Achievable Throughput Bulk Tranfer Capacity Implementation (tool) technique end-to-end Packet Pair / Train pathrate bprobe PPrate PBProbe AymProbe hop-by-hop Variable Packet Size clink nettimer CapProbe SProbe pathchar pchar Probe Rate Model end-to-end Probe Gap Model Delphi ABwProbe Spruce IGI end-to-end Parallel TCP / UDP Connection netperf iperf end-to-end TCP Connection or Emulation cap TReno pathload ASSOLO Yaz abget pathchirp Fig.. An Overview: Metric, Technique and Tool Current etimation technique and tool maiy uffer from two categorie of challenge that lead to untable and inaccurate etimate: Challenge that exit in Internet environment uch a route alternation, multichannel and aymmetric link, multiple exiting bottleneck, traffic haper or network component working with non-fifo queuing dicipline; or challenge which are related to end-hot performing the meaurement uch a interrupt coalecence, limited ytem I/O capability, limited ytem timer reolution, context witching and clock kew. The purpoe of thi paper i (a) to introduce pecific bandwidth-related metric, highlighting the cope and relevance of each; (b) to decribe the rationale of the maor exiting bandwidth etimation technique; and (c) to urvey and uniformly claify the variou exiting bandwidth etimation tool. Differently from the ret of urvey tudie in literature [ 3], the focu of thi work i to urvey and claify the more recent bandwidth etimation tool to comprehenively review and critically analyze the relevant characteritic, trength and weaknee of bandwidth etimation tool to give a detailed overview about the challenge, practical iue and difficultie faced by in deigning and implementing bandwidth etimation technique. The ret of the tudy i divided into the following ection. Section II decribe the four-pecific bandwidthrelated metric including capacity,, achievable throughput and BTC. Section III preent the working principle of maor bandwidth etimation technique along with their aumption. Section IV give a taxonomy of tool. Section V preent the fundamental challenge, practical iue and difficultie faced by deigning and implementing bandwidth etimation technique Finally, Section VI conclude the paper. II. BANDWIDTH-RELATED METRICS Baically, there exit three popular bandwidth-related metric: capacity, and throughput. The capacity of a ingle link i defined a the maximum number of bit thi link can tranfer per econd. If, on the other hand, a path coniting of everal link i conidered, the end-to-end capacity of thi path i given by C end toend min C () i... H wherea C i i the capacity of link i and H indicate the number of link along the path between the ender and the receiver. In other word, the end-to-end capacity pecifie the maximum capacity of the weaket link on the path between two hot. The capacity i a meaure of the bottleneck of a communication link, which i independent of the current load of the network. Figure illutrate a path coniting of three hop whoe end-toend capacity i 64 Kb/. i Copyright 08 MECS I.J. Computer Network and Information Security, 08, 8, -6
3 Through the Diverity of Bandwidth-Related Metric, Etimation Technique and Tool: An Overview 3 Fig.. Illutrating End-To-End Capacity of a Path Coniting of Three Hop C = 97.5 Mbit/ u = 0.05 (= 5 Mb/) C = 9.75 Mb/ A = 4.75 Mb/, u = 0.05 (= 5 Mb/) C3 = 97.5 Mb/ A = 9.5 Mb/ u3 = 0.05 (= 5 Mb/) A end toend 4.75 Mb / A3 = 9.5 Mb/ Sender Receiver Fig.3. Calculating Available Bandwidth Uing an Example Scenario at the IP Layer An intereting quetion when etimating the capacity i on which layer a tool meaure thi metric. A link on layer normally tranport the data at a contant rate. For example, with 0Bae-T Ethernet, thi contant tranmiion rate i 0 Mb/. Thi i the capacity of thi link on layer, alo referred to a nominal bandwidth. However, a compared to it nominal bandwidth thi link provide le capacity to the overlying IP layer becaue the overhead caued by layer ha a reducing effect on the capacity of layer 3. Let C be the capacity of a link L on layer. The tranmiion delay of an IP packet of ize L byte i calculated a follow: L3 L H L3 L L3 () CL where H L repreent the layer overhead in byte. The layer overhead i needed to encapulate the IP packet to be ent. The effective capacity of thi link on the IP layer i: C L3 L L L3 L3 3 L L H C L3 L It i to be noted that the maximum achievable capacity that i obtained on the IP layer trongly depend on the packet ize. Thu, for example, an IP packet with a larger payload ize lead to a correpondingly larger capacity, ince the overhead of layer ha a much greater impact on mall payload than on large payload. In thi repect, it i neceary to ue the maximum poible payload ize of an IP packet to determine the maximum capacity of the L (3) IP layer. The maximum poible payload ize of an IP packet including IP header i limited by the maximum tranmiion unit (MTU) for Ethernet. Thu, the capacity on the IP layer i defined a the maximum tranmiion rate on thi layer, which can be achieved uing the maximum poible payload ize limited by MTU []. The of a link can be coarely defined a the reidual capacity on that link during a time interval. The load of the network prevailing at the time of meaurement ha a coniderable influence on available bandwidth. The i determined by traffic from other ource. Let Ci be the capacity of link i and Cu i i the number of bit tranmitted via thi link during the time interval u with 0 T. The term i u i indicate the uage of the bandwidth of the link i during the time interval T. Then, the A of the link i during the time interval T i defined a the fraction of the capacity C which wa not ued during that time interval. i By extending thi concept to the entire path, the endto-end A during time i end to end interval T can be calculated a the minimum available bandwidth among all link, i.e. end toend i i i... H A min C u (4) The link with the minimum capacity determine the end-to-end capacity of the path, while the link where the proportion of the unued capacity i minimal limit the end-to-end. The link related to the firt and econd cae are referred to a narrow link and tight link, repectively. Copyright 08 MECS I.J. Computer Network and Information Security, 08, 8, -6
4 4 Through the Diverity of Bandwidth-Related Metric, Etimation Technique and Tool: An Overview Fig.4. The Rationale of PP Technique [4] Figure 3 illutrate an example in which the end-to-end i determined conidering the layer overhead. It how a path between a tranmitter and a receiver, where the firt and third link on the IP layer have an effective capacity of 97.5 Mb/. The econd link ha an effective bandwidth of 9.75 Mb/. The ue of thi path i contantly 5 Mb/ while meauring the available bandwidth. In thi cenario, the end-to-end available bandwidth available at the IP layer i 4.75 Mb/. There are two throughput-related metric, namely achievable throughput and BTC. Both metric are uually defined for end-to-end path and meaured at the tranport layer. Achievable throughput indicate the maximum amount of data that can be uccefully tranmitted between two hot over a network. Achievable throughput can be limited by many factor, including hardware propertie of the end computer, tranport protocol with which the data i tranmitted (e.g. TCP or UDP), the non-optimal etting of certain tranmiion parameter, e.g. for TCP, the ize of the buffer at the receiver or election of the initial ize of the overload window, ize of the data to be tranmitted and RTT of the communication link, to name ut a few. The achievable throughput thu indicate the number of bit that an application with thee pecific etting can maximally achieve. Conequently, it may occur that due to uch limitation factor, the achieved throughput of an application i maller than the actual in the path. In contrat to achievable throughput, BTC i defined a the maximum rate at which a ingle TCP connection can end over a given path. The connection hould carry out all TCP congetion control algorithm that conform to RFC 58. TCP throughput depend on variou parameter uch a congetion control algorithm (i.e. low-tart and congetion avoidance), RTT, nature of ide traffic (e.g. UDP and TCP) and flavor of TCP (e.g. Reno, new Reno, SACK). Differently from the achievable throughput which can be meaured uing different tranport protocol uch a UDP and TCP and parallel connection, BTC i a TCP-pecific metric exhibiting the maximal throughput attainable by a ingle TCP connection. III. BANDWIDTH ESTIMATION TECHNIQUES Thi ection preent the detail of PP, VPS, PGP, PRM, TCP connection and emulation technique along with the aumption each technique make. A. Packet Pair (PP) PP etimate the end-to-end capacity between two hot. Let P be the path between two hot coniting of n link. The link with the lowet capacity in P i referred to a narrow link, the capacity of which i ued ynonymouly for the end-to-end capacity. PP i baed on the fact that if two packet p and p of the ame ize are queued back-to-back at the narrow link of a path, they leave the link with a time difference of t, (5) where the ize of the econd packet i indicated by and the capacity of the narrow link i repreented by. Thi time difference, alo referred to a "diperion" can be meaured at the receiver by ubtracting the arrival n n t t t ). By changing time of the packet pair (i.e. the equation (5), the capacity of the narrow link of the path can be deduced, a given in (6). Figure 4 illutrate the rationale of PP technique. n n t t (6) For a correct etimation of the narrow link capacity, PP Copyright 08 MECS I.J. Computer Network and Information Security, 08, 8, -6
5 Through the Diverity of Bandwidth-Related Metric, Etimation Technique and Tool: An Overview 5 Sender Router Router Receiver A) Narrow Link B) Narrow Link C) Narrow Link D) Narrow Link Fig.5. Source of Error in the PP Etimate [4] aume that the two packet are queued back-to-back at the narrow link and that the caued time difference n n ( t t ) doe not change after leaving thi link, i.e. there i no queueing after the narrow link. Thi idealized proce i hown in Figure 5-A [4]. However, if the packet pair queued at the narrow link i eparated by one or more non-probe packet, the time difference i increaed by the ize of the additional packet (i.e. the diperion of the packet pair ample i extended), cauing the econd packet to fall farther behind than originally caued by the narrow link. In thi cae, the meaured narrow link capacity will reflect a lower value than the actual narrow link capacity. Thi cae i hown in Figure 5-B. Another error can occur if the firt packet p i delayed at the queue of a router after the narrow link by one or more other pre-queued packet, i.e. p mut wait longer than p in at leat one of the queue of a router after the narrow link, cauing the econd packet to follow the firt packet cloer o that the original time difference between the packet pair i reduced (i.e. the diperion of the packet pair ample i compreed). In thi cae, the etimated narrow link capacity will reflect a higher value than the actual narrow link capacity. Thi cae i hown in Figure 5-C. Finally, if the ender initially cannot end the packet cloe enough together o that they are not queued backto-back at the narrow link, the time difference between the packet will not clearly indicate the narrow link capacity. In thi cae, the etimated narrow link capacity will reflect a value lower than the actual narrow link capacity. Figure 5-D illutrate thi cae. Cae B through D repreent the maor ource of error that can occur in a packet pair meaurement. Although there are other poible cenario, thee are ut combination of thee three cae. Error of type B to D from Figure 5 caue ome noie in the meaurement reult and hould therefore be detected and eliminated. Several aumption made by the PP technique mut be fulfilled to correctly meaure the narrow link capacity of a path. Firt, the two packet, namely p and p, mut have the ame ize. If p i le than p, then the tranmiion delay of p would alway be maller than the tranmiion delay of p. Conequently, the packet p would travere the individual link in the path to the receiver fater than the packet p, and thu the time difference between the two packet would gradually decreae. If, on the other hand, p were maller than p, p would travere the individual link fater than becaue of the ame reaon. In thi cae, the time difference between the two packet would gradually increae. Second, the packet pair mut follow the ame path, i.e. no route alternation hould occur during the meaurement. Third, the router along the path mut proce the packet according to the FIFO principle. Finally, PP aume that the tranmiion delay i proportional to the packet ize and that the router operate according to the tore-and-forward principle. B. Variable Packet Size (VPS) VPS i ued to ae the capacity of each hop within a path between two hot. Thi technique tart by ending multiple packet of different ize to each hop in the path to the receiver and meaure the required Round Trip Time (RTT) baed on the incoming repone. To meaure the RTT, VPS ue the ICMP protocol and perform like the traceroute command, i.e. VPS end requet packet with an increaing TTL value. The tart i at TTL =. Thi value i then decremented by each intermediate node on the way between ender and receiver. If TTL = 0, the intermediate node that the packet lat reached end back an ICMP packet of type p Copyright 08 MECS I.J. Computer Network and Information Security, 08, 8, -6
6 6 Through the Diverity of Bandwidth-Related Metric, Etimation Technique and Tool: An Overview "Time Exceed" containing the IP addre of thi intermediate node. In thi way, VPS can ue the incrementing TTL value to find all intermediate node on the way to the detination and can calculate the required RTT of the packet up to each hop. According to the VPS technique, the RTT for a packet of ize from node n- to node n and back can be calculated a RTT q lat q forward icmp _ error _ ize q3 lat q4. The variable q through q4 repreent the random queuing time of a packet and forward indicate the time taken by the forwarding engine to proce the arrived packet. To implify the equation given in (0), VPS make three aumption: (i) The ize of the ICMP error packet i mall enough (56 byte) that it tranmiion delay of icmp _ error _ ize i negligible; (ii) the time taken by the forwarding engine to proce an incoming packet i negligible; and finally (iii) if the RTT for a packet ize i meaured everal time, VPS aume that at leat one of thee meaurement will be performed without queuing delay. In thi cae, the queuing time q through q4 can be neglected, too. The elimination of thee term from Eq. (0) yield: (7) It i obviou that the meaured RTT for packet with the ame ize can vary widely. Thi depend on how long the ent or received packet are delayed in the queue of the individual router. The hortet RTT for a packet of ize i referred to a Shortet Oberved RTT (SORTT). The SORTT for a packet of ize i given by SORTT lat. (9) Thi linear equation pecifie the hortet RTT needed to end a packet of ize to direct neighbor hop. Thi cenario i hown in Figure 6. However, ince the SORTT' of the different packet ize on a twodimenional coordinate ytem are uually not exactly aligned, the required linear function SORTT mut be approximated. The linear function to be approximated can be determined by uing linear regreion [6]. Once the optimal linear function SORTT lat ha been determined, the capacity from the firt hop can be determined by computing the invere of the lope of thi approximated linear function, a hown in Eq. (0), Slope SORTT SORTT SORTT SORTT (0) RTT lat lat lat. (8) Eq. (8) repreent a linear function with repect to the packet ize, where and lat indicate the lope and the y-intercept of thi function, repectively. The VPS method perform the RTT meaurement for each hop with different packet ize. The number of different packet ize depend on the correponding VPS implementation. For example, the pathchar [5] implementation end a total of MTU n different packet 3 ize. The MTU for Ethernet i 500 byte. Thu, tarting with 64 byte at a ditance of 3 byte, pathchar end a total of 45 different packet ize per hop. The RTT meaurement per packet ize and per hop i additionally repeated p time becaue of the aumption (iii). Thu, for each hop, pathchar perform a total of p * RTT meaurement. Fig.6. RTT Meaurement from Sender to Direct Neighbor Node SORTT SORTT and, where, are two point on the line approximated by conducting the linear regreion. The capacity of the firt hop i thu. () lope SORTT() Next, the RTT for a packet of ize i conidered from the ender to node 3 via an intermediate node. The cenario i hown in Figure 7. Copyright 08 MECS I.J. Computer Network and Information Security, 08, 8, -6
7 Through the Diverity of Bandwidth-Related Metric, Etimation Technique and Tool: An Overview 7 Fig.7. RTT Meaurement acro an Intermediate Node The SORTT for a packet of ize from the ender to node 3 i SORTT lat lat lat lat () A i een in Eq. (), the parameter including capacity, lope and latency of the ubpath between node through node 3 are formed by the um of value from each individual hop parameter. Thu, e.g. the term in () repreent the lope from the tranmitter to node 3. In the following, term of the type abbreviated by n are n. The bandwidth for the firt hop i given by. The bandwidth of the econd hop i then calculated from the invere of the difference between the two value and : By generalizing the Eq. (3), the capacity hop i calculated from:, n (3) for the (4) It hould be noted that the lope given in (4) i alo needed to calculate the capacity of the next hop, a for applie:, n (5) For thi reaon, an incorrect meaurement of will diturb not oy the capacity etimation of hop but alo the one of hop. For VPS, the algorithm mut oy be implemented on one hot, becaue the RTT of the ent requet are meaured by mean of repone at the ender. A in the cae of PP technique, VPS alo make a lot of aumption to deliver a valid etimate. Firt, it i required that the ICMP protocol i available on all router along the path between the ender and the receiver o that all intervening hop can be determined uing the TTL Time Exceeded mechanim. Ideally, each ent packet ize hould travere the entire path between the ender and receiver without queuing delay. Failure to meet thi requirement for multiple packet ize can caue the linear relationhip between RTT and different packet ize to be lot due to random queuing delay. VPS aume that the MTU of a link i not exceeded. A packet whoe ize exceed the MTU value i fragmented into a certain number of maller packet. The detination node end back the ICMP error packet a oon a it receive the firt packet of thi fragmented ICMP requet packet. Since thi principle i applied to all other packet whoe ize i above the MTU, the meaured RTT will be cloe to each other independent of the packet ize. A a reult, the determined line that optimally approximate thee point will not reflect the correct linear equation for the meaurement. In thi cae, VPS tend to overetimate the correponding hop capacity. Meaurement conducted by VPS can lead to a ignificant underetimation of the capacity if the meaurement path contain tore-and-forward witche. Such device caue additional tranmiion delay but do not generate ICMP TTL exceeded meage becaue they are "inviible" on layer 3. For thi reaon, thi extra tranmiion delay cannot be conidered in the VPS model. The equation given in (5) i oy valid for a direct connection between two layer 3 device. The impact of layer device on the accuracy of VPS ha been further invetigated in [7]. Another factor neglected in the model of VPS i the dynamic route change on the Internet. In packet-witched network, related data packet can reach the detination in different way. Thi can happen, for example, if a route i changed dynamically on the way depending on the load ituation. In a tudy conducted by Paxon [8] it ha been hown that dynamic route change on the Internet are very common. Such dynamic route change during a Copyright 08 MECS I.J. Computer Network and Information Security, 08, 8, -6
8 8 Through the Diverity of Bandwidth-Related Metric, Etimation Technique and Tool: An Overview Fig.8. Etimating Available Bandwidth Baed on OWD Analyi meaurement can caue VPS to provide fale etimate. For example, it i aumed that during the meaurement proce a route i contantly being changed between two poibilitie. Then it may happen that one part of the meaurement packet i tranmitted via the firt poible route and the econd part via thi econd poible route. Since the network interface of the two route can have different capacitie and characteritic, the complete meaurement of VPS will be falified. C. Probe Rate Model (PRM) PRM etimate the end-to-end between two hot. Thi technique require a cooperative environment to perform a meaurement, i.e. the ender and the receiver mut cooperate with each other, o the meaurement oftware mut be ued on both ide. Let P be the path between two hot coniting of n link. The link with the lowet in P i referred to a tight link, the of which i ued ynonymouly for the end-to-end available bandwidth. The ender begin by ending a equence of packet to the receiver. Thi packet equence conit of K-packet, where K i the length of thi equence. The ize of each packet in thi equence i L bit and i periodically ent every t econd. The tranmiion rate of thi packet equence i thu L R b /. (6) T The ender provide each packet i with a timetamp t before it tranmiion. Let a be the arrival timetamp i of packet i at the receiver. For each incoming packet i, the receiver firt calculate it relative one-way delay (OWD) D : i i Di ai ti (7) For a packet equence of length K, the receiver calculate a total of K OWD D, D,..., D. Afterward, the receiver check the equence of thee calculated OWD to deduce whether the tranmiion rate R of the packet equence i higher than the available bandwidth A of tight-link. The way in which the relation between R and A baed on thee calculated OWD i determined repreent the baic idea of thi etimation technique. Particularly, if the tranmiion rate R of the tranmitted packet equence i higher than the available bandwidth A of the tight-link, it caue a hort-term congetion on the tight link of the path. During thi hortterm overload, the tight link of the path to be meaured receive more traffic than what it can tranmit at maximum, o that the queue of that tight link i gradually filled with thee incoming packet. In thi cae, it i expected that the queuing time of the i th packet in thi queue i higher than the correponding queuing time of the th packet which wa placed in thi queue before the ith one. Thi i caued by the fact that the i th packet wait in the queue both the waiting time of the preceding th packet a well a hi own queueing time while the th packet mut oy wait it own queuing time. Conequently, it i expected that the OWD of the packet equence tend to increae. If, on the other hand, the tranmiion rate R i lower than the tight-link available bandwidth, no congetion i caued at the tight link. The tranmitted packet are thu not queued in the queue of the tight link, o in thi cae it i expected that the OWD of the tranmitted packet equence are not prone to increae. Figure 8 illutrate the baic principle of PRM for a packet equence of length K=4. The main purpoe of thi etimation procedure i to end the packet equence a fat a the weaket available bandwidth on a link (= tight-link ). If R A applie, the tranmiion rate of the next packet equence i decreaed. On the other hand, if R A applie, the tranmiion rate of the next packet equence i increaed. Thi iterative approach caue each time the K Copyright 08 MECS I.J. Computer Network and Information Security, 08, 8, -6
9 Through the Diverity of Bandwidth-Related Metric, Etimation Technique and Tool: An Overview 9 newly et tranmiion rate R to converge to the tightlink of the path. A maor problem aociated with PRM i that the tightlink to be meaured may vary during the meaurement. In uch cae, it can no longer be decided unambiguouly whether the meaured OWD of a tranmitted packet equence tend to increae. Two other aumption made by PRM are that neither context witching occur during the meaurement proce nor interrupt coalecence feature of the utilized network interface card (NIC ) i activated. The detail of context witching and interrupt coalecence are decribed in Section V. D. Probe Gap Model (PGM) Another technique for etimating the end-to-end available bandwidth between two hot i PGM which exploit the information in the time gap between the arrival of two ucceive probe at the receiver. A probe pair i ent with a time gap in, and reache the receiver with a time gap out. If the queue doe not become empty between the departure of the firt probe in the pair and the arrival of the econd probe, then out i the time taken by the bottleneck to tranmit the econd probe in the pair and the cro traffic that arrived during in, a hown in Figure 9. Thu, the time to tranmit the cro traffic i out in, and the rate of the cro-traffic i out in xc where C i the capacity of the bottleneck in [9]. The can be calculated a follow: out in A C x in (8) Fig.9. The Probe Gap Model for Etimating Available Bandwidth [9] PGM aume that all router along the path ue FIFO queuing; cro traffic follow a fluid model (i.e. crotraffic packet have an infinitely mall packet ize); average rate of cro traffic change lowly and i contant for the duration of a ingle meaurement; there i a ingle bottleneck which i both the narrow and tight link for that path; and finally, the capacity C of the bottleneck i known in advance. E. TCP Connection and Emulation Thi methodology i ued to meaure the throughputrelated metric (i.e. achievable throughput and BTC) by etablihing either a ingle or everal parallel TCP connection() to a elected hot and trying to end data a fat a poible. To gain an inight into the working principle, an undertanding of the TCP protocol i required. Particularly, a TCP connection tart with the low tart phae. During the low tart phae, the congetion window i doubled per RTT until the previouly et threhold i reached. Thi threhold value can be et arbitrarily high when the connection i etablihed. Often the value of "Advertied Window" i ued a it indicate the free pace in the buffer of the receiver. Since the ender double the congetion window per RTT, the congetion window increae exponentially. The exponential growth of the congetion window allow a TCP connection to quickly reach the o-called equilibrium [0]. The low tart algorithm can terminate in two poible way. Either the threhold i reached, or packet loe occur. If the threhold i reached, the congetion window i not further increaed and remain contant. If packet loe occur, the threhold i reduced to half the current congetion window. From thi halved place then begin the o-called congetion avoidance phae. Congetion avoidance aim to maximize the throughput while avoiding the congetion a much a poible. Therefore, in contrat to the low-tart phae, the congetion window oy increae linearly from thi halved point. More pecifically, for each RTT, the congetion window i increaed by one MSS. Thi procedure i referred to a "additive increae". A a reult of thi linear increae, more and more throughput i ued during the connection, and a oon a packet lo occur after a certain time, the additiveincreae phae i terminated and the threhold value i again et to half of the congetion window, i.e. the congetion window, which ha been linearly increaed by an MSS per RTT, i multiplicatively reduced in thi cae, which i why thi proce i alo referred to a "multiplicative decreae". Thi iterative additiveincreae/multiplicative-decreae paradigm allow the determine the throughput along a path between two hot. There are alo other algorithm, e.g. Fat Retranmit or Fat Recovery, which enure continuou and uninterrupted data flow during a TCP connection. For a detailed decription of the TCP proce, the intereted reader i referred to the related literature. TCP emulation i baed on the ame idea mentioned above, however in that cae the behavior of TCP i emulated by uing UDP or ICMP. For example, TReno emulate TCP by uing low TTL UDP or ICMP Echo packet: probe packet elicit TTL Expired ICMP packet from the receiving hot thu imulating TCP ACK. Cap alo ue UDP packet to emulate TCP but intead of uing ICMP to imulate ACK, it end UDP packet from the receiving end every time it receive a packet. TReno i a non-cooperative tool meaning that it doe not require oftware to be intalled to the receiving end. In contrat, cap i cooperative requiring oftware to be intalled on both end of the meaurement. IV. TAXONOMY OF BANDWIDTH ESTIMATION TOOLS Thi ection i divided into two part. In the firt, the tool characteritic are decribed, and in the econd the tool are claified baed on thee characteritic. Copyright 08 MECS I.J. Computer Network and Information Security, 08, 8, -6
10 0 Through the Diverity of Bandwidth-Related Metric, Etimation Technique and Tool: An Overview A. Tool Characteritic A illutrated in Figure, the broad urvey in thi reearch field revealed that there exit a variety of tool for etimating capacity, and throughput-related metric; and they all how a wide pectrum of different aumption, characteritic, advantage and limitation []. Bandwidth etimation tool can be claified a either active or paive. Active tool are baed on the inection of additional meaurement packet in the network. Paive tool, on the other hand, do not caue additional traffic, but oy capture and analyze the paing real traffic at an appropriate obervation point without perturbing the network traffic. Active meaurement method, in turn, differ in whether they meaure bandwidth in an intruive or non-intruive manner. An active meaurement method i intruive if it generate ignificant traffic load on the network, cauing high and peritent queue delay or packet lo, and thu affecting the throughput of other connection. Otherwie, the meaurement method i called non-intruive. A metric can be etimated on the entire path between two end-hot (i.e. at the end-to-end cope), on a ubpath coniting of many conecutive link of an end-to-end path, or hop-by-hop. Tool etimating end-to-end metric are able to oberve bottleneck viible at the end-to-endcope (e.g. pathload []). Tool etimating ubpathpecific metric can reveal characteritic on link which are not viible at end-to-end cope and allow identifying a portion of the end-to-end path containing the bottleneck link (e.g. cartouche [3]). Finally, hop-by-hop etimation tool allow meauring a metric for each hop along the path (e.g. pathchar [5]). One and the ame metric can be etimated at different layer of the TCP/IP model. A layer- link can normally tranfer data at a contant bit rate, which i alo called the nominal bandwidth of that link. However, from the ender point of view, thi nominal bandwidth cannot be completely ued for the raw data tranmiion, ince each layer in the TCP/IP model add it own header to the data received from the upper layer. Thu, the overhead caued by adding layer-pecific header information ha a reducing effect on the nominal bandwidth obtainable at layer. Uually, active tool perform the etimation at IP layer ince at layer the exact amount of overhead of protocol uch a Ethernet, ATM, PPPoE or PPPoA that carry the higher layer packet i unknown. Contrary, paive tool can take the meaurement at layer by imply capturing the incoming traffic. For example, the paive verion of nettimer attempt to etimate the capacity metric at the link layer (i.e. in cae of 00BASE- T Ethernet, the reference value i 00 Mb/) wherea pathrate [4] etimate it at IP layer (the reference value i 97.5 Mb/ []). Tool can be claified a ingle-ended or both-ended tool. A tool i claified a a ingle-ended tool, if it run oy at one hot on the entire path or a both-ended tool if it require acce to both end. Single-ended tool have the merit that the meaurement oftware i oy deployed locally on the meaurement hot and thu increaing the applicability of the tool ignificantly. Example for ingle-ended tool are SProbe [5], abget [6] and ABwProbe [7]. Single-ended tool are very flexible ince they enable meaurement of path from the ource to any arbitrary detination. Furthermore, ingle-ended tool don t need any ynchronization between the ender and receiver clock. Etimation tool able to work in uncooperative environment are all baed on the ame principle. They end pecial packet eliciting acknowledgement or repone from the receiver ide. Conequently, the meaurement packet travere the path twice, both in the forward and backward direction. However, thi principle alo entail the additional problem that cro traffic can affect the meaurement both in the forward and revere path. Thi i one of the main reaon why ingle-ended tool are uually le accurate than the both-ended tool. Both-ended tool require the cooperation of both the ource and the detination o a to their applicability i limited in ut a few path where the uer ha acce at both the ender and the receiver (e.g. CapProbe [8]). However, meauring in cooperative environment avoid the queuing in revere path leading to more accurate reult. It hould be noted that every both-ended tool i able to meaure aymmetric link by exchanging the ender and receiver component of that tool and applying the ame etimation technique to the revere path. The protocol ued by a tool i another important apect ince it can limit the applicability of the tool alo. ICMP packet, e.g., are often blocked by firewall, rate-limited or handled differently than normal network traffic (e.g. due to fat path / low path proceing mode in the router). Furthermore, the choice of the protocol determine whether a tool need the adminitrative right required to run the tool, e.g. ICMP on Linux/Unix uually require root privilege, wherea UDP and TCP protocol alo work with normal uer privilege. B. Tool Claification Thi ection introduce the claification of bandwidth etimation and meaurement tool baed on the claification criteria preented in Section IV A. Particularly, Table claifie the end-to-end and per-hop capacity etimation tool. Table claifie the end-toend-available bandwidth etimation tool. Finally, Table 3 claifie the end-to-end achievable throughput and BTC meaurement tool. V. CHALLENGES, PRACTICAL ISSUES AND DIFFICULTIES The broad urvey revealed that the current etimation technique and tool maiy uffer from two categorie of challenge that lead to untable and inaccurate etimate: Challenge that exit in Internet environment or thoe which are related to end-hot performing the meaurement. Figure 0 give an overview of claification of challenge, practical iue and difficultie affecting the accuracy of etimation technique and tool []. Copyright 08 MECS I.J. Computer Network and Information Security, 08, 8, -6
11 Through the Diverity of Bandwidth-Related Metric, Etimation Technique and Tool: An Overview Table. Claification of Tool for Etimating the End-To-End and Per-Hop Capacity Tool Metric Methodology Pathrate [3] PBProbe [3] CapProbe [8] AymProbe [33] SProbe [5] Nettimer[4] Bprobe [34] PPrate [35] capacity capacity capacity capacity capacity capacity capacity capacity Forward/ Revere Deployment Layer Active/ Paive Protocol PP Forward Double-ended 3 Active UDP PP Forward and Revere Double-ended 3 Active UDP PP Forward Single-ended 3 Active ICMP PP PP PP Forward and Revere Forward and Revere Forward and Revere Single-Ended 3 Active TCP Single-Ended 3 Active TCP On each obervation point Paive Layer protocol PP Forward Single-Ended 3 Active ICMP PP Forward and Revere From trace file Paive TCP Pathchar [5] Per-hop capacity VPS Forward Single-Ended 3 Active Clink [0] Per-hop capacity VPS Forward Single-Ended 3 Active UDP Pchar [36] Per-hop capacity VPS Forward Single-Ended 3 Active UDP; ICMP UDP; ICMP Table. Claification of Tool for Etimating the End-To-End Available Bandwidth Tool Metric Methodology ABwProbe [7] Abget [6] Pathload [] Yaz [37] ASSOLO [38] Pathchirp [39] Spruce [9] IGI [40] Delphi [4] Forward/ Revere Deployment Layer Active/ Paive Protocol PRM Revere Single-ended 3 Active TCP PRM Revere Single-Ended 3 Active TCP PRM Forward Both-Ended 3 Active UDP PRM Forward Both-Ended 3 Active UDP PRM Forward Both-Ended 3 Active UDP PRM Forward Both-Ended 3 Active UDP PGM Forward Both-Ended 3 Active UDP PGM Forward Both-Ended 3 Active UDP PGM Forward Both-Ended 3 Active UDP A. Challenge in Internet Environment One of the mot relevant property of an etimation tool i it reitance to cro traffic a Internet path almot alway contain cro traffic. To enhance the robutne of tool to cro traffic, everal technique have been propoed including confidence interval [9], kernel denity etimator and received/ent bandwidth ratio filtering technique [4], minimum delay um [8]. Unfortunately, there i no tandard tatitical approach that alway lead to correct etimate. The main reaon making the deal with the cro traffic difficult i that there exit everal type of cro traffic with different behavior (uch a contant cro traffic with different rate, burty cro traffic, elf-imilar cro traffic or cro traffic obeying to a ditribution like Poion or Pareto ditribution etc.) that interfere with an etimation procedure in different way. Alo, hop-peritent or pathperitent cro traffic pattern influence the etimation accuracy differently. In packet-witched network, data packet belonging together can reach their detination over different path. Thi could be caued, e.g., due to dynamic route alternation or load haring on a meaurement path. Route Copyright 08 MECS I.J. Computer Network and Information Security, 08, 8, -6
12 Through the Diverity of Bandwidth-Related Metric, Etimation Technique and Tool: An Overview Table 3. Claification of Tool for Meauring the End-To-End BTC and Achievable Throughput Tool Metric Methodology Forward/Revere Deployment Layer Active/ Paive Protocol Netperf [4] achievable throughput Parallel TCP Connection Forward and Revere Both-Ended 4 Active UDP; TCP Iperf [7] achievable throughput Parallel TCP Connection Forward and Revere Both-Ended 4 Active UDP; TCP Cap [43] BTC Emulated TCP Connection Forward Both-Ended 4 Active UDP TReno [44] BTC Emulated TCP Connection Forward Single-Ended 4 Active ICMP Cro Traffic Route Alternation and Load Balancing Multi-Channel Link Internet-Related Non-FIFO Queuing Multiple Bottleneck Link Challenge, Practical Iue and Difficultie in Etimating Bandwidth-Related Metric Traffic Shaper Interrupt Coalecence Limited Sytem I/O Capabilite End-Hot-Related Context Switching Limited Sytem Timer Reolution Clock Skew Fig.0. Overview of Claification of Challenge, Practical Iue and Difficultie Affecting the Accuracy of Etimation Technique and Tool alternation i the property of a path between two hot to change over time, uually between a mall et of poibilitie (e.g. in cae of node failure or load balancing). Note that in cae of route alternation, there i oy one poible route that a router can take at a given time. Contrary to route alternation, load haring can route the packet over two or more different interface. Aume that on a meaurement path, during the probing proce uch a route alternation or load haring occur. Then, the probe traffic will be tranmitted over different link/path which potentially will ugget different link/path characteritic (including different bandwidth peed) cauing ignificant etimation inaccuracie. Therefore, a robut tool hould characterize the meaurement path to be flexible to bandwidth and route change. For intance, when clink [0], a hop-by-hop capacity etimation tool, encounter a routing intability, it collect data for all the path it encounter, until one of the path generate enough data to yield an acceptable etimate. Along a path, a link can be multi-channeled which mean that it i made up of many parallel channel. If a link of total capacity C i made up of k channel, the individual channel forward packet in parallel at a rate of C/k. In uch a cae, a tool may incorrectly tend to etimate the capacity of a ingle channel, intead of the total capacity of that link. Pathrate, e.g., ue packet train of different length to detect and mitigate the effect of multi-channel bottleneck link uch a ISDN link. Copyright 08 MECS I.J. Computer Network and Information Security, 08, 8, -6
13 Through the Diverity of Bandwidth-Related Metric, Etimation Technique and Tool: An Overview 3 Several etimation methodologie and tool have the fundamental aumption that bottleneck router ue FIFO-queuing, i.e. what come in firt i handled firt. Other Non-FIFO queue proceing technique uch a prioritized or cla-baed queuing dicipline could ditort the meaurement proce. Ideally, the etimation methodology of a tool hould be independent of queuing dicipline of intermediate router to be uccefully ued for deployment on Internet path. The tudy in [], e.g., propoe a technique for etimation of end-to-end that i independent of the network queuing dicipline ued by intermediate router along a path. The etimation technique of a robut tool hould remain valid in the preence of multiple bottleneck link on a path. For example, PGM-baed tool like pruce [9] aume that there i oy a ingle bottleneck link which i both the narrow and tight link for that path. On the other ide, there are alo tool uch a MultiQ [] which are not oy robut to multiple bottleneck but alo able to etimate the bandwidth of multiple congeted bottleneck. In Internet, traffic haper are often employed to control the rate of the networking traffic to guarantee ome QoS parameter like latency, throughput and avoid burty traffic. In uch a cenario, the meaurement proce and reult of a tool may be affected if it probing rate i higher than the rate the traffic haper allow. Moreover, in cae of capacity etimation, the link on which traffic haping will be performed will have two different capacity metric, namely the uimited raw capacity and the utainable rate of the traffic haper. Thu, if a tool etimation methodology cannot overcome traffic haping limitation, it hould at leat clearly define, which capacity metric it intend to meaure for path with traffic haping node. B. End-Hot-Related Challenge Interrupt coalecence (IC) i a well-known and proven technique for reducing CPU utilization when proceing high packet arrival rate. Normally, a NIC without IC generate an interrupt for each incoming packet. Thi caue ignificant CPU load when packet arrival rate increae. By uing IC, the workload for the hot proceor can be reduced ignificantly by grouping multiple packet, received in a hort time interval, in a ingle interrupt. In thi way, the number of interrupt to be generated will be reduced ignificantly. However, lower CPU utilization i done at the cot of increaed network latency, ince the frame are firt buffered at the NIC before they are proceed by the operating ytem (the hot i not aware of the packet until the NIC generate an interrupt). Thu, the receiving timetamp for the packet ent by an etimation tool will be ditorted (in uch a cae, all incoming packet may have the ame timetamp) which may lead to erroneou etimation. To overcome IC, everal tool uch a IMR-Pathload [3] and ICIM [4] have been propoed, which incorporate robut IC detection algorithm to till enable reliable etimate of bandwidth metric under a wide range of interrupt delay. Much etimation tool fail to accurately etimate highpeed network bandwidth ince they do not take the capabilitie of the meaurement hot ytem into account (e.g. hot memory, I/O bu peed etc.). If end ytem capabilitie are involved, then the etimation will be of the end ytem throughput and will not indicate a correct aement of network bandwidth [5]. Thu, either the bandwidth etimation algorithm hould not be dependent on end hot performance (e.g. STAB [6]) or tool hould implement additional method to determine if the end hot can perform a proper meaurement. Mot etimation tool are baed on ending probing packet at a certain tranmiion rate, i.e. they mut end packet in regular interval to perform a proper meaurement (e.g. pathload, PBProbe and abget). Conider that a tool need to end packet at a tranmiion rate R with, i.e., every t time unit, a t packet of ize hould be ent. Two different approache can be taken to achieve the rate R. Firt, a tool could perform buy waiting by continuouly checking the ytem clock and end packet of ize every time when the clock reache the correponding value of t. Thi approach i, e.g., taken by Iperf [7] tool which intruively meaure the end-to-end achievable throughput of a network path. The maximum rate R obtainable with thi approach depend on the time which i required to perform the clock checking proce. Though the buy waiting mechanim allow achieving high tranmiion rate, it wate a lot of CPU cycle affecting the efficient proceing of tak from other application, epecially if the meaurement proce lat for everal econd which i typically the cae for mot of the tool. In the econd approach, an etimation tool aociate it action of ending probing packet with a ytem timer mechanim which i a recurring timeout proce in an OS. Every time when thi timer expire, and a timeout occur, the tool fire it probing packet. Conequently, creating a timeout event which end packet of ize with timeout value a t allow achieving the rate R. Thi approach avoid the problem of buy waiting ince the CPU i merely treed if and oy if a probing packet hould be ent. Due to thi ignificant advantage, almot all tool ue thi timing mechanim. Unfortunately, contrary to buy waiting mechanim, the maximum tranmiion rate obtainable uing thi approach i trongly limited by the inufficient ytem timer reolution. The current minimum ytem timer reolution among the common operating ytem i µ. By conidering the bigget ize of 500 Byte in claic Ethernet network, oy a tranmiion rate of R. Mb/ can be achieved. To overcome thi problem, the technique of packet train i propoed. For further information, we refer the reader to the repective publication [4]. Note that a clock reolution alo affect the preciene of packet timetamp. The higher the clock reolution i, the more accurate the timetamp on the packet. Copyright 08 MECS I.J. Computer Network and Information Security, 08, 8, -6
14 4 Through the Diverity of Bandwidth-Related Metric, Etimation Technique and Tool: An Overview Another challenge arie when a tool meaurement proce get interrupted by a context witch at the end hot. Aume that a probing tream with a pecified rate i tranmitted by an end hot, i.e. the probe packet are ent out periodically every time unit. If during thi tranmiion proce a context witch occur, the pecified rate can t be utained any more reducing the etimation accuracy. Thu, to avoid thi problem, a tool hould either detect the occurrence of context witching or elect the tranmiion period of it probing tream a hort a poible to complete before a context witch interruption occur. DIChirp [8] i, e.g., an end-to-end etimation tool which i deigned to minimize the impact of a context witching during a meaurement eion. Several both-ended tool rely on the aumption of a ynchronized clock between the endpoint. However, the clock on different machine are uually not ynchronized and the offet between two different clock uually change over time. To enure reaonable etimation accuracy, a tool hould be robut to thi clock kew problem. Example of tool that do not require any clock ynchronization between meaurement hot are Forecater [9] and Pathvar [30]. VI. CONCLUSION In principle, in bandwidth etimation reearch there are three popular metric: capacity, and throughput. PP meaure the end-to-end capacity of a path between two hot. In other word, the maximum bandwidth of the weaket link on the entire path between two hot i etimated. The diturbance of the normal network traffic caued by PP i relatively mall, ince few packet are ufficient for a good etimate and the probing duration i independent of the number of hop paed through. VPS aociate the RTT with everal packet of different ize. The capacity of each individual hop from a ender to a receiver i etimated. The diadvantage of thi technique are that the total duration of the meaurement i very high, and the generated meaurement traffic increae linearly with repect to the number of hop meaured. The baic idea in PRM i that the OWD of a periodic packet tream how an increaing trend when the tream rate i higher than the available bandwidth between two hot. Each tream rate teted require a large amount of data, but the hort duration of each burt doe not interfere with competing traffic. Another alternative end-to-end etimation technique i PGM which i characterized by it lightweight and fat etimation procedure. Compared to PRM that require multiple iteration with different probing rate, PGM ue a ingle probing rate and it infer the from a direct relation between the input and output rate of meaurement packet pair. Finally, throughput can, in turn, be divided into achievable throughput and BTC. Both metric are meaured by actively overloading TCP connection between two hot. Depite the highet level of meaurement accuracy, thi technique ha the demerit that it aturate the path, ignificantly increae the delay and itter, and potentially caue loe to other TCP flow. In addition to the etimation technique preented in thi tudy, there are everal other methodologie that were propoed and implemented in the related literature. It can be concluded that each methodology exhibit it own advantage and diadvantage, and there i no generalizable uperiority of one etimation technique over the other that conitently perform well over all network etting, cenario and condition. The bet deciion about the election of the more appropriated tool depend on both the network environment on which they are later deployed and their ue cae. Tool to be deployed on real Internet path mut be able to cope with aymmetric link. Moreover, due to limited acce to the remote Internet hot, ue of ingle-ended tool i needed which are oy deployed locally on the uer hot without requiring the cooperation from the other end of a meaurement path. However, for large cale tudie of Internet path characteritic, active tool become difficult becaue of the probe overhead they caue and the need to be deployed on each meaurement hot. In uch cae, paive tool demontrate their benefit which can be flexibly placed at a few appropriate obervation point to capture and analyze the paing real traffic. In cae of oy a few intereting path where the uer ha acce to both the ender and receiver hot, active and doubleended tool are more uitable ince in general, they achieve more accurate reult than ingle-ended or paive tool. Etimation in wirele network, on the other hand, require non-intruive and lightweight etimation procedure with fat convergence time wherea ue cae uch a dynamic erver election or congetion control upport require tool that can produce quick real-time etimation. Finally, depite the ignificant previou reearch on etimating bandwidth-related metric, it can be concluded that up to now the reearch community i till rather far from having conitently accurate and robut tool implementation. The broad urvey revealed that there are a variety of different challenge, practical iue and difficultie that can negatively affect an etimation procedure and lead to ignificant etimation error. Such challenge range from typical Internet-related iue uch a cro traffic diturbance, route alternation, multichannel and aymmetric link, traffic haper or network component working with non-fifo queuing dicipline to end-hot related challenge uch a NIC' IC mode, OS' limited ytem timer reolution, limited end-ytem capabilitie and the context witching problem. Thu, to have the capability to be deployed under real environment with uch network etting, a welletablihed etimation technique hould conider thee iue in it deign and implementation phae. Conideration in that context mean that it hould either attempt to overcome uch iue to till give acceptable accurate etimate or detect uch inconvenience and abort the etimation proce intead of reporting a potentially inaccurate etimate. Copyright 08 MECS I.J. Computer Network and Information Security, 08, 8, -6
15 Through the Diverity of Bandwidth-Related Metric, Etimation Technique and Tool: An Overview 5 ACKNOWLEDGEMENTS Thi work i upported by Adana Science and Technology Univerity Scientific Reearch Proect Center under grant no REFERENCES [] R. Proad et al., Bandwidth etimation: metric, meaurement technique, and tool, IEEE Netw., vol. 7, no. 6, pp. 7 35, 003. [] C. D. Guerrero and M. A. Labrador, On the applicability of etimation technique and tool, Comput. Commun., vol. 33, no., pp., 00. [3] A. S. Sairam, Survey of Bandwidth Etimation Technique, Wirel. Per. Commun., vol. 83, no., pp , 05. [4] K. Lai and M. Baker, Nettimer: A tool for meauring bottleneck link bandwidth, in Proceeding of the USENIX Sympoium on Internet Technologie and Sytem, 00, vol. 34, pp.. [5] A. B. Downey, Uing pathchar to etimate Internet link characteritic, ACM SIGCOMM Comput. Commun. Rev., vol. 9, no. 4, pp. 4 50, 999. [6] X. Su, X. Yan, and C.-L. Tai, Linear regreion, Wiley Interdicip. Rev. Comput. Stat., vol. 4, no. 3, pp , 0. [7] R. S. Praad, C. Dovroli, and B. A. Mah, The effect of layer- witche on pathchar-like tool, Proc. Second ACM SIGCOMM Work. Internet Mea. - IMW 0, no. 5, p. 3, 00. [8] V. Paxon, routing behavior in the internet, IEEE/ACM Tran. Netw., vol. 5, no. 5, pp , 997. [9] J. Strau, D. Katabi, and F. Kaahoek, A meaurement tudy of etimation tool, in Proceeding of the ACM SIGCOMM Internet Meaurement Conference, IMC, 003, pp [0] A. O. Tang, J. Wang, S. Hegde, and S. H. Low, Equilibrium and fairne of network hared by TCP Reno and Vega/FAST, Telecommun. Syt., vol. 30, no. 4 SPEC. ISS., pp , 005. [] F. Abut, Toward a Generic Claification and Evaluation Scheme for Bandwidth Meaurement Tool, Signal Telecommun. J., vol., pp , 0. [] M. Jain and C. Dovroli, Pathload: a meaurement tool for end-to-end, in Proceeding of the Paive and Active Meaurement (PAM) Workhop, 00, pp.. [3] K. Harfouh, A. Betavro, and J. Byer, Meauring capacity bandwidth of targeted path egment, IEEE/ACM Tran. Netw., vol. 7, no., pp. 80 9, 009. [4] C. Dovroli, P. Ramanathan, and D. Moore, What do packet diperion technique meaure?, in Proceeding of IEEE INFOCOM, vol., pp , 00. [5] S. Saroiu, P. Gummadi, and S. Gribble, Sprobe: A fat technique for meauring bottleneck bandwidth in uncooperative environment, in Proceeding of IEEE INFOCOM, pp., 00. [6] D. Antoniade, M. Athanato, and A. Papadogiannaki, Available bandwidth meaurement a imple a running wget, in Proceeding of Paive and Active Meaurement Conference (PAM), 006, pp [7] D. Croce, T. En-Naary, G. Urvoy-Keller, and E. W. Bierack, Non-cooperative etimation toward ADSL link, in Proceeding of IEEE INFOCOM, 008. [8] R. Kapoor, L. Chen, and M. Gerla, CapProbe : A Simple and Accurate Capacity Etimation Technique, in SIGCOMM 04 Proceeding of the 004 conference on Application, technologie, architecture, and protocol for computer communication, 004, pp [9] C. L. T. Man, G. Haegawa, and M. Murata, An Iine meaurement method for capacity of end-to-end network path, in 3rd IEEE/IFIP Workhop on End-to- End Monitoring Technique and Service, EEMON, 005, vol. 005, pp [0] A. B. Downey, Clink, 999. [Oine]. Available: downey/clink. [] M. Kazantzidi, D. Maggiorini, and M. Gerla, Network independent ampling and meaurement, Lect. NOTES Comput. Sci., vol. 60, pp. 7 30, 003. [] S. Katti, D. Katabi, C. Blake, E. Kohler, and J. Strau, MultiQ: automated detection of multiple bottleneck capacitie along a path, IMC 04 Proc. 4th ACM SIGCOMM Conf. Internet Mea., pp , 004. [3] S. R. Kang and D. Loguinov, IMR-Pathload: Robut etimation under end-hot interrupt delay, in Lecture Note in Computer Science, 008, vol LNCS, pp [4] C. L. T. Man, G. Haegawa, and M. Murata, ICIM: An Iine Network Meaurement Mechanim for Highpeed Network, in 006 4th IEEE/IFIP Workhop on Endto-End Monitoring Technique and Service, 006, pp [5] G. Jin and B. L. Tierney, Sytem Capability Effect on Algorithm for Network Bandwidth Meaurement, in Proceeding of 3rd ACM SIGCOMM Conf. Internet Mea., pp. 7 38, 003. [6] V. J. Ribeiro, R. H. Riedi, R. G. Baraniuk, and J. Navratil, Spatio-temporal etimation for high-peed network, in ISMA 003 Bandwidth Etimation Workhop, 003, pp [7] A. Tirumala, L. Cottrell, and T. Dunigan, Meauring end-to-end bandwidth with Iperf uing Web00, in Proceeding of Paiv. Act. Mea. Work., pp. 8, 003. [8] Y. Ozturk and M. Kulkarni, DIChirp: Direct inection bandwidth etimation, Int. J. Netw. Manag., vol. 8, no. 5, pp , 008. [9] M. Neginhal, K. Harfouh, and H. Perro, Meauring Bandwidth Signature of Network Path, Network, pp., 007. [30] M. Jain and C. Dovroli, etimation of the variation range, ACM SIGMETRICS Perform. Eval. Rev., vol. 33, no., p. 65, 005. [3] C. Dovroli, P. Ramanathan, and D. Moore, Packetdiperion technique and a capacity-etimation methodology, IEEE/ACM Tran. Netw., vol., no. 6, pp , 004. [3] L.-J. J. Chen, T.Sun, B.-C. C. Wang, M. Y. Y. Sanadidi, and M. Gerla, PBProbe: A capacity etimation tool for high peed network, vol. 3, no [33] L. Chen, T. Sun, G. Yang, M. Y. Sanadidi, and M. Gerla, End-to-End Aymmetric Link Capacity Etimation, in IFIP Networking, 005, pp [34] R. L. Carter and M. E. Crovella, Dynamic erver election uing bandwidth probing in wide-area network, in Proceeding of IEEE INFOCOM, 997. Copyright 08 MECS I.J. Computer Network and Information Security, 08, 8, -6
16 6 Through the Diverity of Bandwidth-Related Metric, Etimation Technique and Tool: An Overview [35] T. En-Naary and G. Urvoy-Keller, PPrate: A Paive Capacity Etimation Tool, in 006 4th IEEE/IFIP Workhop on End-to-End Monitoring Technique and Service, 006, pp [36] B. A. Mah, pchar: A Tool for Meauring Internet Path Characteritic, 00. [Oine]. Available: bmah/software/pchar/. [37] J. Sommer, P. Barford, and W. Willinger, Laboratorybaed calibration of etimation tool, Microproce. Microyt., vol. 3, no. 4 SPEC. ISS., pp. 35, 007. [38] E. Goldoni, G. Roi, and A. Torelli, Aolo, a New Method for Available Bandwidth Etimation, 009 Fourth Int. Conf. Internet Monit. Prot., pp , 009. [39] M. Ładyga, R. H. Riedi, R. G. Baraniuk, J. Navratil, and L. Cottrell, pathchirp: Efficient Available Bandwidth Etimation for Network Path, in Paive and Active Meaurement Workhop, 003. [40] N. Hu and P. Steenkite, Evaluation and characterization of probing technique, IEEE J. Sel. Area Commun., vol., no. 6, pp , 003. [4] V. Ribeiro, M. Coate, R. Riedi, S. Sarvotham, B. Hendrick, and R. Baraniuk, Multifractal cro-traffic etimation, ITC Spec. Semin. IP Traffic Mea., pp. 5, 000. [4] Netperf Homepage, 08. [Oine]. Available: [43] M. Allman, Meauring end-to-end bulk tranfer capacity, Proc. Firt ACM SIGCOMM Work. Internet Mea. Work. - IMW 0, no. November, p. 39, 00. [44] M. Mathi and J. Mahdav, Diagnoing internet congetion with a tranport layer performance tool, in INET 96, 996. Author Profile Fatih Abut received B.Sc. and M.Sc. degree in Computer Science from Bonn- Rhein-Sieg Univerity of Applied Science, Germany, in 008 and 00, repectively; and Ph.D. degree in Computer Engineering in the year 07 from Çukurova Univerity, Adana, Turkey. He i currently an Aitant Profeor in Department of Computer Engineering at Adana Science and Technology Univerity, Turkey. Hi reearch interet include wirele communication, network ecurity and IP network meaurement and characterization. How to cite thi paper: Fatih Abut,"Through the Diverity of Bandwidth-Related Metric, Etimation Technique and Tool: An Overview", International Journal of Computer Network and Information Security(IJCNIS), Vol.0, No.8, pp.-6, 08.DOI: 0.585/icni Copyright 08 MECS I.J. Computer Network and Information Security, 08, 8, -6
Performance of a Robust Filter-based Approach for Contour Detection in Wireless Sensor Networks
 Performance of a Robut Filter-baed Approach for Contour Detection in Wirele Senor Network Hadi Alati, William A. Armtrong, Jr., and Ai Naipuri Department of Electrical and Computer Engineering The Univerity
Performance of a Robut Filter-baed Approach for Contour Detection in Wirele Senor Network Hadi Alati, William A. Armtrong, Jr., and Ai Naipuri Department of Electrical and Computer Engineering The Univerity
Modeling the Effect of Mobile Handoffs on TCP and TFRC Throughput
 Modeling the Effect of Mobile Handoff on TCP and TFRC Throughput Antonio Argyriou and Vijay Madietti School of Electrical and Computer Engineering Georgia Intitute of Technology Atlanta, Georgia 3332 25,
Modeling the Effect of Mobile Handoff on TCP and TFRC Throughput Antonio Argyriou and Vijay Madietti School of Electrical and Computer Engineering Georgia Intitute of Technology Atlanta, Georgia 3332 25,
Distributed Packet Processing Architecture with Reconfigurable Hardware Accelerators for 100Gbps Forwarding Performance on Virtualized Edge Router
 Ditributed Packet Proceing Architecture with Reconfigurable Hardware Accelerator for 100Gbp Forwarding Performance on Virtualized Edge Router Satohi Nihiyama, Hitohi Kaneko, and Ichiro Kudo Abtract To
Ditributed Packet Proceing Architecture with Reconfigurable Hardware Accelerator for 100Gbp Forwarding Performance on Virtualized Edge Router Satohi Nihiyama, Hitohi Kaneko, and Ichiro Kudo Abtract To
The Association of System Performance Professionals
 The Aociation of Sytem Performance Profeional The Computer Meaurement Group, commonly called CMG, i a not for profit, worldwide organization of data proceing profeional committed to the meaurement and
The Aociation of Sytem Performance Profeional The Computer Meaurement Group, commonly called CMG, i a not for profit, worldwide organization of data proceing profeional committed to the meaurement and
Lecture 14: Minimum Spanning Tree I
 COMPSCI 0: Deign and Analyi of Algorithm October 4, 07 Lecture 4: Minimum Spanning Tree I Lecturer: Rong Ge Scribe: Fred Zhang Overview Thi lecture we finih our dicuion of the hortet path problem and introduce
COMPSCI 0: Deign and Analyi of Algorithm October 4, 07 Lecture 4: Minimum Spanning Tree I Lecturer: Rong Ge Scribe: Fred Zhang Overview Thi lecture we finih our dicuion of the hortet path problem and introduce
Measuring Link Bandwidths Using a Deterministic Model of Packet Delay
 Meauring Lin Bandwidth Uing a Determinitic Model of Pacet Delay Kevin Lai Stanford Univerity lai@c.tanford.edu Mary Baer Stanford Univerity mgbaer@c.tanford.edu ABSTRACT We decribe a determinitic model
Meauring Lin Bandwidth Uing a Determinitic Model of Pacet Delay Kevin Lai Stanford Univerity lai@c.tanford.edu Mary Baer Stanford Univerity mgbaer@c.tanford.edu ABSTRACT We decribe a determinitic model
Refining SIRAP with a Dedicated Resource Ceiling for Self-Blocking
 Refining SIRAP with a Dedicated Reource Ceiling for Self-Blocking Mori Behnam, Thoma Nolte Mälardalen Real-Time Reearch Centre P.O. Box 883, SE-721 23 Väterå, Sweden {mori.behnam,thoma.nolte}@mdh.e ABSTRACT
Refining SIRAP with a Dedicated Reource Ceiling for Self-Blocking Mori Behnam, Thoma Nolte Mälardalen Real-Time Reearch Centre P.O. Box 883, SE-721 23 Väterå, Sweden {mori.behnam,thoma.nolte}@mdh.e ABSTRACT
A Local Mobility Agent Selection Algorithm for Mobile Networks
 A Local Mobility Agent Selection Algorithm for Mobile Network Yi Xu Henry C. J. Lee Vrizlynn L. L. Thing Intitute for Infocomm Reearch, 21 Heng Mui Keng Terrace, Singapore 119613 Email: {yxu, hlee, vriz}@i2r.a-tar.edu.g
A Local Mobility Agent Selection Algorithm for Mobile Network Yi Xu Henry C. J. Lee Vrizlynn L. L. Thing Intitute for Infocomm Reearch, 21 Heng Mui Keng Terrace, Singapore 119613 Email: {yxu, hlee, vriz}@i2r.a-tar.edu.g
Analyzing Hydra Historical Statistics Part 2
 Analyzing Hydra Hitorical Statitic Part Fabio Maimo Ottaviani EPV Technologie White paper 5 hnode HSM Hitorical Record The hnode i the hierarchical data torage management node and ha to perform all the
Analyzing Hydra Hitorical Statitic Part Fabio Maimo Ottaviani EPV Technologie White paper 5 hnode HSM Hitorical Record The hnode i the hierarchical data torage management node and ha to perform all the
SLA Adaptation for Service Overlay Networks
 SLA Adaptation for Service Overlay Network Con Tran 1, Zbigniew Dziong 1, and Michal Pióro 2 1 Department of Electrical Engineering, École de Technologie Supérieure, Univerity of Quebec, Montréal, Canada
SLA Adaptation for Service Overlay Network Con Tran 1, Zbigniew Dziong 1, and Michal Pióro 2 1 Department of Electrical Engineering, École de Technologie Supérieure, Univerity of Quebec, Montréal, Canada
Modelling the impact of cyber attacks on the traffic control centre of an urban automobile transport system by means of enhanced cybersecurity
 Modelling the impact of cyber attack on the traffic control centre of an urban automobile tranport ytem by mean of enhanced cyberecurity Yoana Ivanova 1,* 1 Bulgarian Academy of Science, Intitute of ICT,
Modelling the impact of cyber attack on the traffic control centre of an urban automobile tranport ytem by mean of enhanced cyberecurity Yoana Ivanova 1,* 1 Bulgarian Academy of Science, Intitute of ICT,
DAROS: Distributed User-Server Assignment And Replication For Online Social Networking Applications
 DAROS: Ditributed Uer-Server Aignment And Replication For Online Social Networking Application Thuan Duong-Ba School of EECS Oregon State Univerity Corvalli, OR 97330, USA Email: duongba@eec.oregontate.edu
DAROS: Ditributed Uer-Server Aignment And Replication For Online Social Networking Application Thuan Duong-Ba School of EECS Oregon State Univerity Corvalli, OR 97330, USA Email: duongba@eec.oregontate.edu
(12) Patent Application Publication (10) Pub. No.: US 2011/ A1
 (19) United State US 2011 0316690A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0316690 A1 Siegman (43) Pub. Date: Dec. 29, 2011 (54) SYSTEMAND METHOD FOR IDENTIFYING ELECTRICAL EQUIPMENT
(19) United State US 2011 0316690A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0316690 A1 Siegman (43) Pub. Date: Dec. 29, 2011 (54) SYSTEMAND METHOD FOR IDENTIFYING ELECTRICAL EQUIPMENT
Chapter 13 Non Sampling Errors
 Chapter 13 Non Sampling Error It i a general aumption in the ampling theory that the true value of each unit in the population can be obtained and tabulated without any error. In practice, thi aumption
Chapter 13 Non Sampling Error It i a general aumption in the ampling theory that the true value of each unit in the population can be obtained and tabulated without any error. In practice, thi aumption
Chapter 7 Packet-Switching Networks. Chapter 7 Packet-Switching Networks. Packet Switching. Network Layer. Network Service
 Chapter 7 Packet-Switching etwork etwork Operation & Topology Datagram and Virtual Circuit Structure of a Packet Switch Routing in Packet etwork Shortet Path Routing etwork Chapter 7 Packet-Switching etwork
Chapter 7 Packet-Switching etwork etwork Operation & Topology Datagram and Virtual Circuit Structure of a Packet Switch Routing in Packet etwork Shortet Path Routing etwork Chapter 7 Packet-Switching etwork
Routing Definition 4.1
 4 Routing So far, we have only looked at network without dealing with the iue of how to end information in them from one node to another The problem of ending information in a network i known a routing
4 Routing So far, we have only looked at network without dealing with the iue of how to end information in them from one node to another The problem of ending information in a network i known a routing
Increasing Throughput and Reducing Delay in Wireless Sensor Networks Using Interference Alignment
 Int. J. Communication, Network and Sytem Science, 0, 5, 90-97 http://dx.doi.org/0.436/ijcn.0.50 Publihed Online February 0 (http://www.scirp.org/journal/ijcn) Increaing Throughput and Reducing Delay in
Int. J. Communication, Network and Sytem Science, 0, 5, 90-97 http://dx.doi.org/0.436/ijcn.0.50 Publihed Online February 0 (http://www.scirp.org/journal/ijcn) Increaing Throughput and Reducing Delay in
A Load Balancing Model based on Load-aware for Distributed Controllers. Fengjun Shang, Wenjuan Gong
 4th International Conference on Machinery, Material and Computing Technology (ICMMCT 2016) A Load Balancing Model baed on Load-aware for Ditributed Controller Fengjun Shang, Wenjuan Gong College of Compute
4th International Conference on Machinery, Material and Computing Technology (ICMMCT 2016) A Load Balancing Model baed on Load-aware for Ditributed Controller Fengjun Shang, Wenjuan Gong College of Compute
(12) Patent Application Publication (10) Pub. No.: US 2003/ A1
 US 2003O196031A1 (19) United State (12) Patent Application Publication (10) Pub. No.: US 2003/0196031 A1 Chen (43) Pub. Date: Oct. 16, 2003 (54) STORAGE CONTROLLER WITH THE DISK Related U.S. Application
US 2003O196031A1 (19) United State (12) Patent Application Publication (10) Pub. No.: US 2003/0196031 A1 Chen (43) Pub. Date: Oct. 16, 2003 (54) STORAGE CONTROLLER WITH THE DISK Related U.S. Application
Key Terms - MinMin, MaxMin, Sufferage, Task Scheduling, Standard Deviation, Load Balancing.
 Volume 3, Iue 11, November 2013 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Tak Aignment in
Volume 3, Iue 11, November 2013 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Tak Aignment in
Multi-Target Tracking In Clutter
 Multi-Target Tracking In Clutter John N. Sander-Reed, Mary Jo Duncan, W.B. Boucher, W. Michael Dimmler, Shawn O Keefe ABSTRACT A high frame rate (0 Hz), multi-target, video tracker ha been developed and
Multi-Target Tracking In Clutter John N. Sander-Reed, Mary Jo Duncan, W.B. Boucher, W. Michael Dimmler, Shawn O Keefe ABSTRACT A high frame rate (0 Hz), multi-target, video tracker ha been developed and
Localized Minimum Spanning Tree Based Multicast Routing with Energy-Efficient Guaranteed Delivery in Ad Hoc and Sensor Networks
 Localized Minimum Spanning Tree Baed Multicat Routing with Energy-Efficient Guaranteed Delivery in Ad Hoc and Senor Network Hanne Frey Univerity of Paderborn D-3398 Paderborn hanne.frey@uni-paderborn.de
Localized Minimum Spanning Tree Baed Multicat Routing with Energy-Efficient Guaranteed Delivery in Ad Hoc and Senor Network Hanne Frey Univerity of Paderborn D-3398 Paderborn hanne.frey@uni-paderborn.de
Keywords Cloud Computing, Service Level Agreements (SLA), CloudSim, Monitoring & Controlling SLA Agent, JADE
 Volume 5, Iue 8, Augut 2015 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Verification of Agent
Volume 5, Iue 8, Augut 2015 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Verification of Agent
An Algebraic Approach to Adaptive Scalable Overlay Network Monitoring
 An Algebraic Approach to Adaptive Scalable Overlay Network Monitoring ABSTRACT Overlay network monitoring enable ditributed Internet application to detect and recover from path outage and period of degraded
An Algebraic Approach to Adaptive Scalable Overlay Network Monitoring ABSTRACT Overlay network monitoring enable ditributed Internet application to detect and recover from path outage and period of degraded
Laboratory Exercise 6
 Laboratory Exercie 6 Adder, Subtractor, and Multiplier The purpoe of thi exercie i to examine arithmetic circuit that add, ubtract, and multiply number. Each type of circuit will be implemented in two
Laboratory Exercie 6 Adder, Subtractor, and Multiplier The purpoe of thi exercie i to examine arithmetic circuit that add, ubtract, and multiply number. Each type of circuit will be implemented in two
/06/$ IEEE 364
 006 IEEE International ympoium on ignal Proceing and Information Technology oie Variance Etimation In ignal Proceing David Makovoz IPAC, California Intitute of Technology, MC-0, Paadena, CA, 95 davidm@ipac.caltech.edu;
006 IEEE International ympoium on ignal Proceing and Information Technology oie Variance Etimation In ignal Proceing David Makovoz IPAC, California Intitute of Technology, MC-0, Paadena, CA, 95 davidm@ipac.caltech.edu;
The Implementation of an Adaptive Mechanism in the RTP Packet in Mobile Video Transmission
 2011 International Conference on Information Management and Engineering (ICIME 2011) IPCSIT vol. 52 (2012) (2012) IACSIT Pre, Singapore DOI: 10.7763/IPCSIT.2012.V52.91 The Implementation of an Adaptive
2011 International Conference on Information Management and Engineering (ICIME 2011) IPCSIT vol. 52 (2012) (2012) IACSIT Pre, Singapore DOI: 10.7763/IPCSIT.2012.V52.91 The Implementation of an Adaptive
Minimum Energy Reliable Paths Using Unreliable Wireless Links
 Minimum Energy Reliable Path Uing Unreliable Wirele Link Qunfeng Dong Department of Computer Science Univerity of Wiconin-Madion Madion, Wiconin 53706 qunfeng@c.wic.edu Micah Adler Department of Computer
Minimum Energy Reliable Path Uing Unreliable Wirele Link Qunfeng Dong Department of Computer Science Univerity of Wiconin-Madion Madion, Wiconin 53706 qunfeng@c.wic.edu Micah Adler Department of Computer
Performance Evaluation and Comparison of Westwood+, New Reno, and Vegas TCP Congestion Control
 Performance Evaluation and Comparion of,, and Vega TCP Congetion Control Luigi A. Grieco and Saverio Macolo Dipartimento di Elettrotecnica ed Elettronica, Politecnico di Bari, Italy {a.grieco,macolo}@poliba.it
Performance Evaluation and Comparion of,, and Vega TCP Congetion Control Luigi A. Grieco and Saverio Macolo Dipartimento di Elettrotecnica ed Elettronica, Politecnico di Bari, Italy {a.grieco,macolo}@poliba.it
SIMIT 7. Component Type Editor (CTE) User manual. Siemens Industrial
 SIMIT 7 Component Type Editor (CTE) Uer manual Siemen Indutrial Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult
SIMIT 7 Component Type Editor (CTE) Uer manual Siemen Indutrial Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult
New DSP to measure acoustic efficiency of road barriers. Part 2: Sound Insulation Index
 New DSP to meaure acoutic efficiency of road barrier. Part 2: Sound Inulation Index LAMBERTO TRONCHIN 1, KRISTIAN FABBRI 1, JELENA VASILJEVIC 2 1 DIENCA CIARM, Univerity of Bologna, Italy 2 Univerity of
New DSP to meaure acoutic efficiency of road barrier. Part 2: Sound Inulation Index LAMBERTO TRONCHIN 1, KRISTIAN FABBRI 1, JELENA VASILJEVIC 2 1 DIENCA CIARM, Univerity of Bologna, Italy 2 Univerity of
Service and Network Management Interworking in Future Wireless Systems
 Service and Network Management Interworking in Future Wirele Sytem V. Tountopoulo V. Stavroulaki P. Demeticha N. Mitrou and M. Theologou National Technical Univerity of Athen Department of Electrical Engineering
Service and Network Management Interworking in Future Wirele Sytem V. Tountopoulo V. Stavroulaki P. Demeticha N. Mitrou and M. Theologou National Technical Univerity of Athen Department of Electrical Engineering
A Practical Model for Minimizing Waiting Time in a Transit Network
 A Practical Model for Minimizing Waiting Time in a Tranit Network Leila Dianat, MASc, Department of Civil Engineering, Sharif Univerity of Technology, Tehran, Iran Youef Shafahi, Ph.D. Aociate Profeor,
A Practical Model for Minimizing Waiting Time in a Tranit Network Leila Dianat, MASc, Department of Civil Engineering, Sharif Univerity of Technology, Tehran, Iran Youef Shafahi, Ph.D. Aociate Profeor,
Aspects of Formal and Graphical Design of a Bus System
 Apect of Formal and Graphical Deign of a Bu Sytem Tiberiu Seceleanu Univerity of Turku, Dpt. of Information Technology Turku, Finland tiberiu.eceleanu@utu.fi Tomi Weterlund Turku Centre for Computer Science
Apect of Formal and Graphical Deign of a Bu Sytem Tiberiu Seceleanu Univerity of Turku, Dpt. of Information Technology Turku, Finland tiberiu.eceleanu@utu.fi Tomi Weterlund Turku Centre for Computer Science
How to Select Measurement Points in Access Point Localization
 Proceeding of the International MultiConference of Engineer and Computer Scientit 205 Vol II, IMECS 205, March 8-20, 205, Hong Kong How to Select Meaurement Point in Acce Point Localization Xiaoling Yang,
Proceeding of the International MultiConference of Engineer and Computer Scientit 205 Vol II, IMECS 205, March 8-20, 205, Hong Kong How to Select Meaurement Point in Acce Point Localization Xiaoling Yang,
Application of Social Relation Graphs for Early Detection of Transient Spammers
 Radolaw rendel and Henryk Krawczyk Application of Social Relation raph for Early Detection of Tranient Spammer RADOSLAW RENDEL and HENRYK KRAWCZYK Electronic, Telecommunication and Informatic Department
Radolaw rendel and Henryk Krawczyk Application of Social Relation raph for Early Detection of Tranient Spammer RADOSLAW RENDEL and HENRYK KRAWCZYK Electronic, Telecommunication and Informatic Department
LinkGuide: Towards a Better Collection of Hyperlinks in a Website Homepage
 Proceeding of the World Congre on Engineering 2007 Vol I LinkGuide: Toward a Better Collection of Hyperlink in a Webite Homepage A. Ammari and V. Zharkova chool of Informatic, Univerity of Bradford anammari@bradford.ac.uk,
Proceeding of the World Congre on Engineering 2007 Vol I LinkGuide: Toward a Better Collection of Hyperlink in a Webite Homepage A. Ammari and V. Zharkova chool of Informatic, Univerity of Bradford anammari@bradford.ac.uk,
Research Article Real-Time Communications in Large-Scale Wireless Networks
 Hindawi Publihing Corporation International Journal of Digital Multimedia Broadcating Volume 2008, Article ID 586067, 16 page doi:10.1155/2008/586067 eearch Article eal-time Communication in Large-Scale
Hindawi Publihing Corporation International Journal of Digital Multimedia Broadcating Volume 2008, Article ID 586067, 16 page doi:10.1155/2008/586067 eearch Article eal-time Communication in Large-Scale
CENTER-POINT MODEL OF DEFORMABLE SURFACE
 CENTER-POINT MODEL OF DEFORMABLE SURFACE Piotr M. Szczypinki Iintitute of Electronic, Technical Univerity of Lodz, Poland Abtract: Key word: Center-point model of deformable urface for egmentation of 3D
CENTER-POINT MODEL OF DEFORMABLE SURFACE Piotr M. Szczypinki Iintitute of Electronic, Technical Univerity of Lodz, Poland Abtract: Key word: Center-point model of deformable urface for egmentation of 3D
SIMIT 7. Profinet IO Gateway. User Manual
 SIMIT 7 Profinet IO Gateway Uer Manual Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult are only non-binding uggetion
SIMIT 7 Profinet IO Gateway Uer Manual Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult are only non-binding uggetion
Universität Augsburg. Institut für Informatik. Approximating Optimal Visual Sensor Placement. E. Hörster, R. Lienhart.
 Univerität Augburg à ÊÇÅÍÆ ËÀǼ Approximating Optimal Viual Senor Placement E. Hörter, R. Lienhart Report 2006-01 Januar 2006 Intitut für Informatik D-86135 Augburg Copyright c E. Hörter, R. Lienhart Intitut
Univerität Augburg à ÊÇÅÍÆ ËÀǼ Approximating Optimal Viual Senor Placement E. Hörter, R. Lienhart Report 2006-01 Januar 2006 Intitut für Informatik D-86135 Augburg Copyright c E. Hörter, R. Lienhart Intitut
Integration of Digital Test Tools to the Internet-Based Environment MOSCITO
 Integration of Digital Tet Tool to the Internet-Baed Environment MOSCITO Abtract Current paper decribe a new environment MOSCITO for providing acce to tool over the internet. The environment i built according
Integration of Digital Tet Tool to the Internet-Baed Environment MOSCITO Abtract Current paper decribe a new environment MOSCITO for providing acce to tool over the internet. The environment i built according
A METHOD OF REAL-TIME NURBS INTERPOLATION WITH CONFINED CHORD ERROR FOR CNC SYSTEMS
 Vietnam Journal of Science and Technology 55 (5) (017) 650-657 DOI: 10.1565/55-518/55/5/906 A METHOD OF REAL-TIME NURBS INTERPOLATION WITH CONFINED CHORD ERROR FOR CNC SYSTEMS Nguyen Huu Quang *, Banh
Vietnam Journal of Science and Technology 55 (5) (017) 650-657 DOI: 10.1565/55-518/55/5/906 A METHOD OF REAL-TIME NURBS INTERPOLATION WITH CONFINED CHORD ERROR FOR CNC SYSTEMS Nguyen Huu Quang *, Banh
Shortest Paths Problem. CS 362, Lecture 20. Today s Outline. Negative Weights
 Shortet Path Problem CS 6, Lecture Jared Saia Univerity of New Mexico Another intereting problem for graph i that of finding hortet path Aume we are given a weighted directed graph G = (V, E) with two
Shortet Path Problem CS 6, Lecture Jared Saia Univerity of New Mexico Another intereting problem for graph i that of finding hortet path Aume we are given a weighted directed graph G = (V, E) with two
Stream: Low Overhead Wireless Reprogramming for Sensor Networks
 Thi full text paper wa peer reviewed at the direction of IEEE Communication Society ubject matter expert for publication in the IEEE INFOCOM 27 proceeding. : Low Overhead Wirele Reprogramming for Senor
Thi full text paper wa peer reviewed at the direction of IEEE Communication Society ubject matter expert for publication in the IEEE INFOCOM 27 proceeding. : Low Overhead Wirele Reprogramming for Senor
Diverse: Application-Layer Service Differentiation in Peer-to-Peer Communications
 Divere: Application-Layer Service Differentiation in Peer-to-Peer Communication Chuan Wu, Student Member, IEEE, Baochun Li, Senior Member, IEEE Department of Electrical and Computer Engineering Univerity
Divere: Application-Layer Service Differentiation in Peer-to-Peer Communication Chuan Wu, Student Member, IEEE, Baochun Li, Senior Member, IEEE Department of Electrical and Computer Engineering Univerity
Stochastic Search and Graph Techniques for MCM Path Planning Christine D. Piatko, Christopher P. Diehl, Paul McNamee, Cheryl Resch and I-Jeng Wang
 Stochatic Search and Graph Technique for MCM Path Planning Chritine D. Piatko, Chritopher P. Diehl, Paul McNamee, Cheryl Rech and I-Jeng Wang The John Hopkin Univerity Applied Phyic Laboratory, Laurel,
Stochatic Search and Graph Technique for MCM Path Planning Chritine D. Piatko, Chritopher P. Diehl, Paul McNamee, Cheryl Rech and I-Jeng Wang The John Hopkin Univerity Applied Phyic Laboratory, Laurel,
A NEW APPROACH IN MEASURING OF THE ROUGHNESS FOR SURFACE CONSTITUTED WITH MACHINING PROCESS BY MATERIAL REMOVAL
 International Journal of Mechanical and Production Engineering Reearch and Development (IJMPERD) ISSN 49-689 Vol. 3, Iue, Mar 3, 4-5 TJPRC Pvt. Ltd. A NEW APPROACH IN MEASURING OF THE ROUGHNESS FOR SURFACE
International Journal of Mechanical and Production Engineering Reearch and Development (IJMPERD) ISSN 49-689 Vol. 3, Iue, Mar 3, 4-5 TJPRC Pvt. Ltd. A NEW APPROACH IN MEASURING OF THE ROUGHNESS FOR SURFACE
ETSI TS V ( )
 TS 122 153 V14.4.0 (2017-05) TECHNICAL SPECIFICATION Digital cellular telecommunication ytem (Phae 2+) (GSM); Univeral Mobile Telecommunication Sytem (UMTS); LTE; Multimedia priority ervice (3GPP TS 22.153
TS 122 153 V14.4.0 (2017-05) TECHNICAL SPECIFICATION Digital cellular telecommunication ytem (Phae 2+) (GSM); Univeral Mobile Telecommunication Sytem (UMTS); LTE; Multimedia priority ervice (3GPP TS 22.153
Focused Video Estimation from Defocused Video Sequences
 Focued Video Etimation from Defocued Video Sequence Junlan Yang a, Dan Schonfeld a and Magdi Mohamed b a Multimedia Communication Lab, ECE Dept., Univerity of Illinoi, Chicago, IL b Phyical Realization
Focued Video Etimation from Defocued Video Sequence Junlan Yang a, Dan Schonfeld a and Magdi Mohamed b a Multimedia Communication Lab, ECE Dept., Univerity of Illinoi, Chicago, IL b Phyical Realization
A Hybrid Deployable Dynamic Traffic Assignment Framework for Robust Online Route Guidance
 A Hybrid Deployable Dynamic Traffic Aignment Framework for Robut Online Route Guidance Sriniva Peeta School of Civil Engineering, Purdue Univerity Chao Zhou Sabre, Inc. Sriniva Peeta School of Civil Engineering
A Hybrid Deployable Dynamic Traffic Aignment Framework for Robut Online Route Guidance Sriniva Peeta School of Civil Engineering, Purdue Univerity Chao Zhou Sabre, Inc. Sriniva Peeta School of Civil Engineering
Maneuverable Relays to Improve Energy Efficiency in Sensor Networks
 Maneuverable Relay to Improve Energy Efficiency in Senor Network Stephan Eidenbenz, Luka Kroc, Jame P. Smith CCS-5, MS M997; Lo Alamo National Laboratory; Lo Alamo, NM 87545. Email: {eidenben, kroc, jpmith}@lanl.gov
Maneuverable Relay to Improve Energy Efficiency in Senor Network Stephan Eidenbenz, Luka Kroc, Jame P. Smith CCS-5, MS M997; Lo Alamo National Laboratory; Lo Alamo, NM 87545. Email: {eidenben, kroc, jpmith}@lanl.gov
Analytical Redundancy and Fuzzy Inference in AUV Fault Detection and Compensation
 Analytical Redundancy and Fuzzy Inference in AUV Fault Detection and Compenation A. J. Healey Profeor and Director Center for AUV Reearch Naval Potgraduate School Monterey, CA 93953 healey@me.np.navy.mil
Analytical Redundancy and Fuzzy Inference in AUV Fault Detection and Compenation A. J. Healey Profeor and Director Center for AUV Reearch Naval Potgraduate School Monterey, CA 93953 healey@me.np.navy.mil
A Handover Scheme for Mobile WiMAX Using Signal Strength and Distance
 A Handover Scheme for Mobile WiMAX Uing Signal Strength and Ditance Mary Alatie, Mjumo Mzyece and Anih Kurien Department of Electrical Engineering/French South African Intitute of Technology (F SATI) Thwane
A Handover Scheme for Mobile WiMAX Uing Signal Strength and Ditance Mary Alatie, Mjumo Mzyece and Anih Kurien Department of Electrical Engineering/French South African Intitute of Technology (F SATI) Thwane
Planning of scooping position and approach path for loading operation by wheel loader
 22 nd International Sympoium on Automation and Robotic in Contruction ISARC 25 - September 11-14, 25, Ferrara (Italy) 1 Planning of cooping poition and approach path for loading operation by wheel loader
22 nd International Sympoium on Automation and Robotic in Contruction ISARC 25 - September 11-14, 25, Ferrara (Italy) 1 Planning of cooping poition and approach path for loading operation by wheel loader
Frequency Table Computation on Dataflow Architecture
 Frequency Table Computation on Dataflow Architecture P. Škoda *, V. Sruk **, and B. Medved Rogina * * Ruđer Bošković Intitute, Zagreb, Croatia ** Faculty of Electrical Engineering and Computing, Univerity
Frequency Table Computation on Dataflow Architecture P. Škoda *, V. Sruk **, and B. Medved Rogina * * Ruđer Bošković Intitute, Zagreb, Croatia ** Faculty of Electrical Engineering and Computing, Univerity
MAT 155: Describing, Exploring, and Comparing Data Page 1 of NotesCh2-3.doc
 MAT 155: Decribing, Exploring, and Comparing Data Page 1 of 8 001-oteCh-3.doc ote for Chapter Summarizing and Graphing Data Chapter 3 Decribing, Exploring, and Comparing Data Frequency Ditribution, Graphic
MAT 155: Decribing, Exploring, and Comparing Data Page 1 of 8 001-oteCh-3.doc ote for Chapter Summarizing and Graphing Data Chapter 3 Decribing, Exploring, and Comparing Data Frequency Ditribution, Graphic
IMPROVED JPEG DECOMPRESSION OF DOCUMENT IMAGES BASED ON IMAGE SEGMENTATION. Tak-Shing Wong, Charles A. Bouman, and Ilya Pollak
 IMPROVED DECOMPRESSION OF DOCUMENT IMAGES BASED ON IMAGE SEGMENTATION Tak-Shing Wong, Charle A. Bouman, and Ilya Pollak School of Electrical and Computer Engineering Purdue Univerity ABSTRACT We propoe
IMPROVED DECOMPRESSION OF DOCUMENT IMAGES BASED ON IMAGE SEGMENTATION Tak-Shing Wong, Charle A. Bouman, and Ilya Pollak School of Electrical and Computer Engineering Purdue Univerity ABSTRACT We propoe
Distributed Partial Information Management (DPIM) Schemes for Survivable Networks - Part II
 IEEE INFOCO 2002 1 Ditributed Partial Information anagement (DPI) Scheme for Survivable Network - Part II Dahai Xu Chunming Qiao Department of Computer Science and Engineering State Univerity of New York
IEEE INFOCO 2002 1 Ditributed Partial Information anagement (DPI) Scheme for Survivable Network - Part II Dahai Xu Chunming Qiao Department of Computer Science and Engineering State Univerity of New York
On successive packing approach to multidimensional (M-D) interleaving
 On ucceive packing approach to multidimenional (M-D) interleaving Xi Min Zhang Yun Q. hi ankar Bau Abtract We propoe an interleaving cheme for multidimenional (M-D) interleaving. To achieved by uing a
On ucceive packing approach to multidimenional (M-D) interleaving Xi Min Zhang Yun Q. hi ankar Bau Abtract We propoe an interleaving cheme for multidimenional (M-D) interleaving. To achieved by uing a
Today s Outline. CS 561, Lecture 23. Negative Weights. Shortest Paths Problem. The presence of a negative cycle might mean that there is
 Today Outline CS 56, Lecture Jared Saia Univerity of New Mexico The path that can be trodden i not the enduring and unchanging Path. The name that can be named i not the enduring and unchanging Name. -
Today Outline CS 56, Lecture Jared Saia Univerity of New Mexico The path that can be trodden i not the enduring and unchanging Path. The name that can be named i not the enduring and unchanging Name. -
A User-Attention Based Focus Detection Framework and Its Applications
 A Uer-Attention Baed Focu Detection Framework and It Application Chia-Chiang Ho, Wen-Huang Cheng, Ting-Jian Pan, Ja-Ling Wu Communication and Multimedia Laboratory, Department of Computer Science and Information
A Uer-Attention Baed Focu Detection Framework and It Application Chia-Chiang Ho, Wen-Huang Cheng, Ting-Jian Pan, Ja-Ling Wu Communication and Multimedia Laboratory, Department of Computer Science and Information
999 Computer System Network. (12) Patent Application Publication (10) Pub. No.: US 2006/ A1. (19) United States
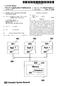 (19) United State US 2006O1296.60A1 (12) Patent Application Publication (10) Pub. No.: Mueller et al. (43) Pub. Date: Jun. 15, 2006 (54) METHOD AND COMPUTER SYSTEM FOR QUEUE PROCESSING (76) Inventor: Wolfgang
(19) United State US 2006O1296.60A1 (12) Patent Application Publication (10) Pub. No.: Mueller et al. (43) Pub. Date: Jun. 15, 2006 (54) METHOD AND COMPUTER SYSTEM FOR QUEUE PROCESSING (76) Inventor: Wolfgang
Policy-based Injection of Private Traffic into a Public SDN Testbed
 Intitut für Techniche Informatik und Kommunikationnetze Adrian Friedli Policy-baed Injection of Private Traffic into a Public SDN Tetbed Mater Thei MA-2013-12 Advior: Dr. Bernhard Ager, Vaileio Kotroni
Intitut für Techniche Informatik und Kommunikationnetze Adrian Friedli Policy-baed Injection of Private Traffic into a Public SDN Tetbed Mater Thei MA-2013-12 Advior: Dr. Bernhard Ager, Vaileio Kotroni
Modeling and Analysis of Slow CW Decrease for IEEE WLAN
 Modeling and Analyi of Slow CW Decreae for IEEE 82. WLAN Qiang Ni, Imad Aad 2, Chadi Barakat, and Thierry Turletti Planete Group 2 Planete Group INRIA Sophia Antipoli INRIA Rhône-Alpe Sophia Antipoli,
Modeling and Analyi of Slow CW Decreae for IEEE 82. WLAN Qiang Ni, Imad Aad 2, Chadi Barakat, and Thierry Turletti Planete Group 2 Planete Group INRIA Sophia Antipoli INRIA Rhône-Alpe Sophia Antipoli,
An Approach to a Test Oracle for XML Query Testing
 An Approach to a Tet Oracle for XML Query Teting Dae S. Kim-Park, Claudio de la Riva, Javier Tuya Univerity of Oviedo Computing Department Campu of Vieque, /n, 33204 (SPAIN) kim_park@li.uniovi.e, claudio@uniovi.e,
An Approach to a Tet Oracle for XML Query Teting Dae S. Kim-Park, Claudio de la Riva, Javier Tuya Univerity of Oviedo Computing Department Campu of Vieque, /n, 33204 (SPAIN) kim_park@li.uniovi.e, claudio@uniovi.e,
DECENTRALIZED structured overlays and distributed. Distributed, Secure Load Balancing with Skew, Heterogeneity, and Churn
 Harvard Technical Report TR-3-4 Ditributed, Secure Load Balancing with Skew, Heterogeneity, and Churn Jonathan Ledlie and Margo Seltzer Abtract Numerou propoal exit for load balancing in peer-to-peer (pp)
Harvard Technical Report TR-3-4 Ditributed, Secure Load Balancing with Skew, Heterogeneity, and Churn Jonathan Ledlie and Margo Seltzer Abtract Numerou propoal exit for load balancing in peer-to-peer (pp)
Ethernet Peer-To-Peer Communication With Model 353 And Procidia i pac Controllers
 iemen Energy & utomation pplication ata Ethernet Peer-To-Peer Communication With odel 353 nd Procidia ipac Controller 353-113 Rev. 1 July Ethernet i a leading form of network communication that i often
iemen Energy & utomation pplication ata Ethernet Peer-To-Peer Communication With odel 353 nd Procidia ipac Controller 353-113 Rev. 1 July Ethernet i a leading form of network communication that i often
Generic Traverse. CS 362, Lecture 19. DFS and BFS. Today s Outline
 Generic Travere CS 62, Lecture 9 Jared Saia Univerity of New Mexico Travere(){ put (nil,) in bag; while (the bag i not empty){ take ome edge (p,v) from the bag if (v i unmarked) mark v; parent(v) = p;
Generic Travere CS 62, Lecture 9 Jared Saia Univerity of New Mexico Travere(){ put (nil,) in bag; while (the bag i not empty){ take ome edge (p,v) from the bag if (v i unmarked) mark v; parent(v) = p;
Shortest Path Routing in Arbitrary Networks
 Journal of Algorithm, Vol 31(1), 1999 Shortet Path Routing in Arbitrary Network Friedhelm Meyer auf der Heide and Berthold Vöcking Department of Mathematic and Computer Science and Heinz Nixdorf Intitute,
Journal of Algorithm, Vol 31(1), 1999 Shortet Path Routing in Arbitrary Network Friedhelm Meyer auf der Heide and Berthold Vöcking Department of Mathematic and Computer Science and Heinz Nixdorf Intitute,
A Linear Interpolation-Based Algorithm for Path Planning and Replanning on Girds *
 Advance in Linear Algebra & Matrix Theory, 2012, 2, 20-24 http://dx.doi.org/10.4236/alamt.2012.22003 Publihed Online June 2012 (http://www.scirp.org/journal/alamt) A Linear Interpolation-Baed Algorithm
Advance in Linear Algebra & Matrix Theory, 2012, 2, 20-24 http://dx.doi.org/10.4236/alamt.2012.22003 Publihed Online June 2012 (http://www.scirp.org/journal/alamt) A Linear Interpolation-Baed Algorithm
Adaptive Beam Director for a Tiled Fiber Array
 Adaptive Beam Director for a Tiled Fiber Array Mikhail A. Vorontov Intelligent Optic Laboratory, Computational and Information Science Directorate, U.S. Army Reearch Laboratory, 2800 Powder Mill Road,
Adaptive Beam Director for a Tiled Fiber Array Mikhail A. Vorontov Intelligent Optic Laboratory, Computational and Information Science Directorate, U.S. Army Reearch Laboratory, 2800 Powder Mill Road,
1 The secretary problem
 Thi i new material: if you ee error, pleae email jtyu at tanford dot edu 1 The ecretary problem We will tart by analyzing the expected runtime of an algorithm, a you will be expected to do on your homework.
Thi i new material: if you ee error, pleae email jtyu at tanford dot edu 1 The ecretary problem We will tart by analyzing the expected runtime of an algorithm, a you will be expected to do on your homework.
Topics. Lecture 37: Global Optimization. Issues. A Simple Example: Copy Propagation X := 3 B > 0 Y := 0 X := 4 Y := Z + W A := 2 * 3X
 Lecture 37: Global Optimization [Adapted from note by R. Bodik and G. Necula] Topic Global optimization refer to program optimization that encompa multiple baic block in a function. (I have ued the term
Lecture 37: Global Optimization [Adapted from note by R. Bodik and G. Necula] Topic Global optimization refer to program optimization that encompa multiple baic block in a function. (I have ued the term
TFRC-CR: An Equation-based Transport Protocol for Cognitive Radio Networks
 213 International onference on omputing, Networking and ommunication (IN) Workhop on omputing, Networking and ommunication -R: An Equation-baed Tranport Protocol for ognitive Radio Network Abdulla K. Al-Ali
213 International onference on omputing, Networking and ommunication (IN) Workhop on omputing, Networking and ommunication -R: An Equation-baed Tranport Protocol for ognitive Radio Network Abdulla K. Al-Ali
Multicast with Network Coding in Application-Layer Overlay Networks
 IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS, VOL. 22, NO. 1, JANUARY 2004 1 Multicat with Network Coding in Application-Layer Overlay Network Ying Zhu, Baochun Li, Member, IEEE, and Jiang Guo Abtract
IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS, VOL. 22, NO. 1, JANUARY 2004 1 Multicat with Network Coding in Application-Layer Overlay Network Ying Zhu, Baochun Li, Member, IEEE, and Jiang Guo Abtract
Problem Set 2 (Due: Friday, October 19, 2018)
 Electrical and Computer Engineering Memorial Univerity of Newfoundland ENGI 9876 - Advanced Data Network Fall 2018 Problem Set 2 (Due: Friday, October 19, 2018) Quetion 1 Conider an M/M/1 model of a queue
Electrical and Computer Engineering Memorial Univerity of Newfoundland ENGI 9876 - Advanced Data Network Fall 2018 Problem Set 2 (Due: Friday, October 19, 2018) Quetion 1 Conider an M/M/1 model of a queue
ANALYSIS OF THE FIRST LAYER IN WEIGHTLESS NEURAL NETWORKS FOR 3_DIMENSIONAL PATTERN RECOGNITION
 ANALYSIS OF THE FIRST LAYER IN WEIGHTLESS NEURAL NETWORKS FOR 3_DIMENSIONAL PATTERN RECOGNITION A. Váque-Nava * Ecuela de Ingeniería. CENTRO UNIVERSITARIO MEXICO. DIVISION DE ESTUDIOS SUPERIORES J. Figueroa
ANALYSIS OF THE FIRST LAYER IN WEIGHTLESS NEURAL NETWORKS FOR 3_DIMENSIONAL PATTERN RECOGNITION A. Váque-Nava * Ecuela de Ingeniería. CENTRO UNIVERSITARIO MEXICO. DIVISION DE ESTUDIOS SUPERIORES J. Figueroa
Distributed Media-Aware Rate Allocation for Video Multicast over Wireless Networks
 Ditributed Media-Aware Rate Allocation for Video Multicat over Wirele Network Xiaoqing Zhu, Thoma Schierl, Thoma Wiegand, Senior Member, IEEE, and Bernd Girod, Fellow, IEEE Abtract A unified optimization
Ditributed Media-Aware Rate Allocation for Video Multicat over Wirele Network Xiaoqing Zhu, Thoma Schierl, Thoma Wiegand, Senior Member, IEEE, and Bernd Girod, Fellow, IEEE Abtract A unified optimization
Compressed Sensing Image Processing Based on Stagewise Orthogonal Matching Pursuit
 Senor & randucer, Vol. 8, Iue 0, October 204, pp. 34-40 Senor & randucer 204 by IFSA Publihing, S. L. http://www.enorportal.com Compreed Sening Image Proceing Baed on Stagewie Orthogonal Matching Puruit
Senor & randucer, Vol. 8, Iue 0, October 204, pp. 34-40 Senor & randucer 204 by IFSA Publihing, S. L. http://www.enorportal.com Compreed Sening Image Proceing Baed on Stagewie Orthogonal Matching Puruit
Stress-Blended Eddy Simulation (SBES) - A new Paradigm in hybrid RANS-LES Modeling
 Stre-Blended Eddy Simulation (SBES) - A new Paradigm in hybrid RANS-LES Modeling Menter F.R. ANSYS Germany GmbH Introduction It i oberved in many CFD imulation that RANS model how inherent technology limitation
Stre-Blended Eddy Simulation (SBES) - A new Paradigm in hybrid RANS-LES Modeling Menter F.R. ANSYS Germany GmbH Introduction It i oberved in many CFD imulation that RANS model how inherent technology limitation
Power Aware Location Aided Routing in Mobile Ad-hoc Networks
 International Journal of Scientific and Reearch Publication, Volume, Iue 1, December 01 1 Power Aware Location Aided Routing in Mobile Ad-hoc Network Anamika Computer Science, Inderprataha Engineering
International Journal of Scientific and Reearch Publication, Volume, Iue 1, December 01 1 Power Aware Location Aided Routing in Mobile Ad-hoc Network Anamika Computer Science, Inderprataha Engineering
Nearly Constant Approximation for Data Aggregation Scheduling in Wireless Sensor Networks
 Nearly Contant Approximation for Data Aggregation Scheduling in Wirele Senor Network Scott C.-H. Huang, Peng-Jun Wan, Chinh T. Vu, Yinghu Li and France Yao Computer Science Department, City Univerity of
Nearly Contant Approximation for Data Aggregation Scheduling in Wirele Senor Network Scott C.-H. Huang, Peng-Jun Wan, Chinh T. Vu, Yinghu Li and France Yao Computer Science Department, City Univerity of
else end while End References
 621-630. [RM89] [SK76] Roenfeld, A. and Melter, R. A., Digital geometry, The Mathematical Intelligencer, vol. 11, No. 3, 1989, pp. 69-72. Sklanky, J. and Kibler, D. F., A theory of nonuniformly digitized
621-630. [RM89] [SK76] Roenfeld, A. and Melter, R. A., Digital geometry, The Mathematical Intelligencer, vol. 11, No. 3, 1989, pp. 69-72. Sklanky, J. and Kibler, D. F., A theory of nonuniformly digitized
Gray-level histogram. Intensity (grey-level) transformation, or mapping. Use of intensity transformations:
 Faculty of Informatic Eötvö Loránd Univerity Budapet, Hungary Lecture : Intenity Tranformation Image enhancement by point proceing Spatial domain and frequency domain method Baic Algorithm for Digital
Faculty of Informatic Eötvö Loránd Univerity Budapet, Hungary Lecture : Intenity Tranformation Image enhancement by point proceing Spatial domain and frequency domain method Baic Algorithm for Digital
AUTOMATIC TEST CASE GENERATION USING UML MODELS
 Volume-2, Iue-6, June-2014 AUTOMATIC TEST CASE GENERATION USING UML MODELS 1 SAGARKUMAR P. JAIN, 2 KHUSHBOO S. LALWANI, 3 NIKITA K. MAHAJAN, 4 BHAGYASHREE J. GADEKAR 1,2,3,4 Department of Computer Engineering,
Volume-2, Iue-6, June-2014 AUTOMATIC TEST CASE GENERATION USING UML MODELS 1 SAGARKUMAR P. JAIN, 2 KHUSHBOO S. LALWANI, 3 NIKITA K. MAHAJAN, 4 BHAGYASHREE J. GADEKAR 1,2,3,4 Department of Computer Engineering,
Priority-Based Distribution Trees for Application-Level Multicast
 Priority-Baed Ditribution Tree for Application-Level Multicat Jürgen Vogel, Jörg Widmer, Dirk Farin, Martin Mauve, Wolfgang Effelberg Praktiche Informatik IV, Univerity of Mannheim, Germany vogel, widmer,
Priority-Baed Ditribution Tree for Application-Level Multicat Jürgen Vogel, Jörg Widmer, Dirk Farin, Martin Mauve, Wolfgang Effelberg Praktiche Informatik IV, Univerity of Mannheim, Germany vogel, widmer,
Software Agent (SA) to guarantee QoS for multi constrain applications in all-ip networks
 Software Agent (SA) to guarantee QoS for multi contrain application in all-ip network Kazi Khaled Al-Zahid and Mituji Matumoto GITS, Waeda Univerity 94 Waeda Univ. Bldg. A-308, 1011Okuboyama Nihitomida
Software Agent (SA) to guarantee QoS for multi contrain application in all-ip network Kazi Khaled Al-Zahid and Mituji Matumoto GITS, Waeda Univerity 94 Waeda Univ. Bldg. A-308, 1011Okuboyama Nihitomida
Advanced Encryption Standard and Modes of Operation
 Advanced Encryption Standard and Mode of Operation G. Bertoni L. Breveglieri Foundation of Cryptography - AES pp. 1 / 50 AES Advanced Encryption Standard (AES) i a ymmetric cryptographic algorithm AES
Advanced Encryption Standard and Mode of Operation G. Bertoni L. Breveglieri Foundation of Cryptography - AES pp. 1 / 50 AES Advanced Encryption Standard (AES) i a ymmetric cryptographic algorithm AES
On Peer-to-Peer Media Streaming Λ
 On eer-to-eer Media Streaming Λ Dongyan Xu y, Mohamed Hefeeda, Suanne Hambruch, Bharat Bhargava Department of Computer Science urdue Univerity, Wet Lafayette, IN 797 fdxu, hefeeda, eh, bbg@c.purdue.edu
On eer-to-eer Media Streaming Λ Dongyan Xu y, Mohamed Hefeeda, Suanne Hambruch, Bharat Bhargava Department of Computer Science urdue Univerity, Wet Lafayette, IN 797 fdxu, hefeeda, eh, bbg@c.purdue.edu
Tracking High Speed Skater by Using Multiple Model
 Vol. 2, No. 26 Tracing High Speed Sater by Uing Multiple Model Guojun Liu & Xianglong Tang School of Computer Science & Engineering Harbin Intitute of Technology Harbin 5000, China E-mail: hitliu@hit.edu.cn
Vol. 2, No. 26 Tracing High Speed Sater by Uing Multiple Model Guojun Liu & Xianglong Tang School of Computer Science & Engineering Harbin Intitute of Technology Harbin 5000, China E-mail: hitliu@hit.edu.cn
Hassan Ghaziri AUB, OSB Beirut, Lebanon Key words Competitive self-organizing maps, Meta-heuristics, Vehicle routing problem,
 COMPETITIVE PROBABIISTIC SEF-ORGANIZING MAPS FOR ROUTING PROBEMS Haan Ghaziri AUB, OSB Beirut, ebanon ghaziri@aub.edu.lb Abtract In thi paper, we have applied the concept of the elf-organizing map (SOM)
COMPETITIVE PROBABIISTIC SEF-ORGANIZING MAPS FOR ROUTING PROBEMS Haan Ghaziri AUB, OSB Beirut, ebanon ghaziri@aub.edu.lb Abtract In thi paper, we have applied the concept of the elf-organizing map (SOM)
Separation of Routing and Scheduling in Backpressure- Based Wireless Networks
 Separation of Routing and Scheduling in - Baed Wirele Network The MIT Faculty ha made thi article openly available. Pleae hare how thi acce benefit you. Your tory matter. Citation A Publihed Publiher Seferoglu,
Separation of Routing and Scheduling in - Baed Wirele Network The MIT Faculty ha made thi article openly available. Pleae hare how thi acce benefit you. Your tory matter. Citation A Publihed Publiher Seferoglu,
Performance Evaluation of an Advanced Local Search Evolutionary Algorithm
 Anne Auger and Nikolau Hanen Performance Evaluation of an Advanced Local Search Evolutionary Algorithm Proceeding of the IEEE Congre on Evolutionary Computation, CEC 2005 c IEEE Performance Evaluation
Anne Auger and Nikolau Hanen Performance Evaluation of an Advanced Local Search Evolutionary Algorithm Proceeding of the IEEE Congre on Evolutionary Computation, CEC 2005 c IEEE Performance Evaluation
Computer Arithmetic Homework Solutions. 1 An adder for graphics. 2 Partitioned adder. 3 HDL implementation of a partitioned adder
 Computer Arithmetic Homework 3 2016 2017 Solution 1 An adder for graphic In a normal ripple carry addition of two poitive number, the carry i the ignal for a reult exceeding the maximum. We ue thi ignal
Computer Arithmetic Homework 3 2016 2017 Solution 1 An adder for graphic In a normal ripple carry addition of two poitive number, the carry i the ignal for a reult exceeding the maximum. We ue thi ignal
Domain-Specific Modeling for Rapid System-Wide Energy Estimation of Reconfigurable Architectures
 Domain-Specific Modeling for Rapid Sytem-Wide Energy Etimation of Reconfigurable Architecture Seonil Choi 1,Ju-wookJang 2, Sumit Mohanty 1, Viktor K. Praanna 1 1 Dept. of Electrical Engg. 2 Dept. of Electronic
Domain-Specific Modeling for Rapid Sytem-Wide Energy Etimation of Reconfigurable Architecture Seonil Choi 1,Ju-wookJang 2, Sumit Mohanty 1, Viktor K. Praanna 1 1 Dept. of Electrical Engg. 2 Dept. of Electronic
Coordinated TCP Westwood Congestion Control for Multiple Paths over Wireless Networks
 Coordinated TCP Wetwood Congetion Control for Multiple Path over Wirele Network Tuan Anh Le, Choong eon Hong, and Eui-Nam Huh Department of Computer Engineering, Kyung Hee Univerity 1 eocheon, Giheung,
Coordinated TCP Wetwood Congetion Control for Multiple Path over Wirele Network Tuan Anh Le, Choong eon Hong, and Eui-Nam Huh Department of Computer Engineering, Kyung Hee Univerity 1 eocheon, Giheung,
Minimum congestion spanning trees in bipartite and random graphs
 Minimum congetion panning tree in bipartite and random graph M.I. Otrovkii Department of Mathematic and Computer Science St. John Univerity 8000 Utopia Parkway Queen, NY 11439, USA e-mail: otrovm@tjohn.edu
Minimum congetion panning tree in bipartite and random graph M.I. Otrovkii Department of Mathematic and Computer Science St. John Univerity 8000 Utopia Parkway Queen, NY 11439, USA e-mail: otrovm@tjohn.edu
Aalborg Universitet. Published in: Proceedings of the Working Conference on Advanced Visual Interfaces
 Aalborg Univeritet Software-Baed Adjutment of Mobile Autotereocopic Graphic Uing Static Parallax Barrier Paprocki, Martin Marko; Krog, Kim Srirat; Kritofferen, Morten Bak; Krau, Martin Publihed in: Proceeding
Aalborg Univeritet Software-Baed Adjutment of Mobile Autotereocopic Graphic Uing Static Parallax Barrier Paprocki, Martin Marko; Krog, Kim Srirat; Kritofferen, Morten Bak; Krau, Martin Publihed in: Proceeding
( ) subject to m. e (2) L are 2L+1. = s SEG SEG Las Vegas 2012 Annual Meeting Page 1
 A new imultaneou ource eparation algorithm uing frequency-divere filtering Ying Ji*, Ed Kragh, and Phil Chritie, Schlumberger Cambridge Reearch Summary We decribe a new imultaneou ource eparation algorithm
A new imultaneou ource eparation algorithm uing frequency-divere filtering Ying Ji*, Ed Kragh, and Phil Chritie, Schlumberger Cambridge Reearch Summary We decribe a new imultaneou ource eparation algorithm
