CS 528 Mobile and Ubiquitous Computing Lecture 11b: Mobile Security and Mobile Software Vulnerabilities Emmanuel Agu
|
|
|
- Marcia Perkins
- 5 years ago
- Views:
Transcription
1 CS 528 Mobile and Ubiquitous Computing Lecture 11b: Mobile Security and Mobile Software Vulnerabilities Emmanuel Agu
2 Authentication using Biometrics
3 Biometrics Passwords tough to remember, manage Many users have simple passwords (e.g. 1234) or do not change passwords Biometrics are unique physiological attributes of each person Fingerprint, voice, face Can be used to replace passwords No need to remember anything. Cool!!
4 Android Biometric Authentication: Fingerprints Fingerprint: On devices with fingerprint sensor, users can enroll multiple fingerprints for unlocking device
5 Samsung Pass: More Biometrics Samsung pass: Fingerprint + Iris scan + facial recognition Probably ok to use for facebook, social media Spanish bank BBVA s mobile app uses biometrics to allow login without username + password Bank of America: pilot testing iris authentication since August
6 Continuous Passive Authentication using Behavioral Biometrics
7 User Behavior as a Biometric User (micro-)behaviors are unique personal features. E.g Each person s daily location pattern (home, work, places, times) Walk pattern Phone tilt pattern General idea: Continuously authenticate user as long as they behave like themselves If we can measure user behavior at very fine granularity, this could enable passive authentication 7
8 BehavioMetrics Derived from Behavioral Biometrics Behavioral: the way a human subject behaves Biometrics: technologies and methods that measure and analyzes biological characteristics of the human body Fingerprints, eye retina, voice patterns BehavioMetrics: Measurable behavior to recognize or to verify identity of a human subject or subject s certain behaviors 8
9 Mobile Sensing BehavioMetrics Accelerometer activity, motion, hand trembling, driving style sleeping pattern inferred activity level, steps made per day, estimated calorie burned Motion sensors, WiFi, Bluetooth accurate indoor position and trace. GPS outdoor location, geo-trace, commuting pattern Microphone, camera From background noise: activity, type of location. From voice: stress level, emotion Video/audio: additional contexts 9 Keyboard, taps, swipes Specific tasks, user interactions,
10 BehavioMetrics Security Track smartphone user behavior using sensors Continuously extract and classify sensory traces + context = personal behavior features (pattern classification) Generate unique pattern for each user Trust score: How similar is today s behavior to user s typical behavior Trigger various authentication schemes when certain applications are launched
11 11
12 Continuous n-gram Model User activity at time i depends only on the last n-1 activities Sequence of activities can be predicted by n consecutive activities in the past Maximum Likelihood Estimation from training data by counting: MLE assign zero probability to unseen n-grams 12
13 Classification Build M BehavioMetrics models P 0, P 1, P 2,, P M-1 Genders, age groups, occupations Behaviors, activities, actions Health and mental status Classification problem formulated as 13
14 Anomaly Detection Threshold 14
15 Behavioral Biometrics Issues: Shared Devices
16 Multi-Person and -Device Use Many mobile devices are shared by multiple people Classifier trained using person A s data cannot detect Person B Question: How to distinguish different people s data (segment) on same device Many people have multiple mobile devices Classifier trained on device 1 (e.g. smartphone) may not detect behavior on device 2 (e.g. smartwatch) Question: How to match same user s session on multiple devices 16
17 2 Problems of Interest How to segment the activities on a single device to those of multiple users? User a User b User a User c User b How to match the activity segments on different devices e to a common user? Device 1 User a Device 2 User a Device 3 User a User a User a tim time 17
18 ActivPass
19 ActivPass S. Dandapat, S Pradhan, B Mitra, R Choudhury and N Ganguly, ActivPass: Your Daily Activity is Your Password, in Proc CHI 2015 Passwords are mostly secure, simple to use but have issues: Simple passwords (e.g. 1234): easy to crack Secure passwords hard to remember (e.g. $emime)$@(*$@)9) Remembering passwords for different websites even more challenging Many people use same password on different websites (dangerous!!)
20 ActivPass S. Dandapat, S Pradhan, B Mitra, R Choudhury and N Ganguly, ActivPass: Your Daily Activity is Your Password, in Proc CHI 2015 Unique human biometrics being explored Explicit biometrics: user actively makes input E.g. finger print, face print, retina scan, etc Implicit biometrics: works passively, user does nothing explicit to be authenticated. E.g. unique way of walk, typing, swiping on screen, locations visited daily This paper: smartphone soft sensors as biometrics: Specifically unique calls, SMS, contacts, etc Advantage of biometrics: simple, no need to remember anything
21 ActivPass Vision Observation: rare events are easy to remember, hard to guess E.g. Website visited this morning that user rarely visits. E.g User went to CNN.com today for the first time in 2 years! Got call from friend I haven t spoken to in 5 years for first time today Idea: Authenticate user by asking questions about user s outlier (rare) activities What is caller s name from first call you received today? Which news site did you not visit today? (CNN, CBS, BBC, Slashdot)?
22 ActivPass Vision Authentication questions based on outlier (rare) activities generated from: Call logs SMS logs Facebook activities Browser history
23 ActivPass Envisioned Usage Scenarios Prevent password sharing. E.g. Bob pays for Netflix, shares his login details with Alice Replace password hints with Activity questions when password lost Combine with regular password (soft authentication mechanism)
24 How ActivPass Works Activity Listener runs in background, logs Calls, SMS, web pages visited, etc When user launches an app: Password Generation Module (PGM) creates n password questions based on logged data If user can answer k of password questions correctly, app is launched!
25 ActivPass Vision User can customize Number of questions asked, what fraction must be answered correctly Question format Activity permissions Paper investigates ActivPass utility by conducting user studies
26 How ActivPass Works Periodically retrieves logs in order to classify them using Activity Categorization Module Tries to find outliers in the data. E.g. Frequently visited pages vs rarely visited web pages
27 ActivPass: Types of Questions Asked Vs Data Logged
28 ActivPass: Evaluation Over 50 volunteers given 20 questions: Average recall rate: 86.3% ± 9.5 Average guessability: 14.6% ± 5.7 Devised Bayesian estimate of challenge given n questions where k are required Optimal n, k Tested on 15 volunteers Authenticates correct user 95% Authenticates imposter 5.5% of the time (guessability) Maximize Minimize
29 Smartphones + IoT Security Risks
30 Cars + Smartphones? Many new vehicles come equipped with smartphone integration / capabilities in the infotainment system (Android Auto!)
31 Smartphones that Drive If a mobile app gets access to a vehicle s infotainment system, is it possible to get access to (or even to control) driving functionality? Body controls (lights, locks ) Airbag Control OBD Key access, anti-theft, etc. Telematics Engine Control Trans. Control TPMS HVAC Infotainment Steering & Brake Control 31
32 Smart Vehicle Risks Many of the risks and considerations that we discussed in this course can be applied to smart vehicles and smartphone interactions However, many more risks come into play because of the other functionality that a car has compared to a smartphone
33 Quiz 5
34 Quiz 5 In class next week Similar to other quizzes Covers lecture 10 (attention, energy efficient computing) and lecture 11 (today, security)
Copyright 2017, Zighra Inc.
 Zighra core AI based Adaptive Authentication Engine Patent (US Patent# - 9619852) 1. What does this cover? Zighra s patent answers the security question who is the real user behind a transaction or device?
Zighra core AI based Adaptive Authentication Engine Patent (US Patent# - 9619852) 1. What does this cover? Zighra s patent answers the security question who is the real user behind a transaction or device?
ANDROID PRIVACY & SECURITY GUIDE ANDROID DEVICE SETTINGS
 ANDROID PRIVACY & SECURITY GUIDE WESNET The Women s Services Network Smartphones store a lot of personal information, including email or social media accounts, reminders and notes, the number of steps
ANDROID PRIVACY & SECURITY GUIDE WESNET The Women s Services Network Smartphones store a lot of personal information, including email or social media accounts, reminders and notes, the number of steps
What is Authentication? All requests for resources have to be monitored. Every request must be authenticated and authorized to use the resource.
 P1L4 Authentication What is Authentication? All requests for resources have to be monitored. Every request must be authenticated and authorized to use the resource. Authentication: Who are you? Prove it.
P1L4 Authentication What is Authentication? All requests for resources have to be monitored. Every request must be authenticated and authorized to use the resource. Authentication: Who are you? Prove it.
Quick Heal Total Security for Android. Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping.
 Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Mobile and Ubiquitous Computing: Mobile Sensing
 Mobile and Ubiquitous Computing: Mobile Sensing Master studies, Winter 2015/2016 Dr Veljko Pejović Veljko.Pejovic@fri.uni-lj.si Based on: Mobile and Ubiquitous Computing Mirco Musolesi, University of Birmingham,
Mobile and Ubiquitous Computing: Mobile Sensing Master studies, Winter 2015/2016 Dr Veljko Pejović Veljko.Pejovic@fri.uni-lj.si Based on: Mobile and Ubiquitous Computing Mirco Musolesi, University of Birmingham,
In this unit we are continuing our discussion of IT security measures.
 1 In this unit we are continuing our discussion of IT security measures. 2 One of the best security practices in Information Security is that users should have access only to the resources and systems
1 In this unit we are continuing our discussion of IT security measures. 2 One of the best security practices in Information Security is that users should have access only to the resources and systems
User Manual Smartwatch SW15
 User Manual Smartwatch SW15! 1. Functions Health and exercise -Pedometer Built-in accelerometer checks and tracks your exercise time, fat burning, temperature, speed and distance. -Sleep Monitor Built-in
User Manual Smartwatch SW15! 1. Functions Health and exercise -Pedometer Built-in accelerometer checks and tracks your exercise time, fat burning, temperature, speed and distance. -Sleep Monitor Built-in
Privacy, Law, and Smartphones
 CyLab Privacy, Law, and Smartphones Engineering & Public Policy acy & Secur ity Priv e l :// C DU HT TP ratory bo La Oct. 29, 2015 CyLab U sab Rebecca Balebako U P S.C S.C M U.E 1 Agenda Quiz Reading discussion
CyLab Privacy, Law, and Smartphones Engineering & Public Policy acy & Secur ity Priv e l :// C DU HT TP ratory bo La Oct. 29, 2015 CyLab U sab Rebecca Balebako U P S.C S.C M U.E 1 Agenda Quiz Reading discussion
Quick Heal Mobile Security. Free protection for your Android phone against virus attacks, unwanted calls, and theft.
 Quick Heal Mobile Security Free protection for your Android phone against virus attacks, unwanted calls, and theft. Product Highlights Complete protection for your Android device that simplifies security
Quick Heal Mobile Security Free protection for your Android phone against virus attacks, unwanted calls, and theft. Product Highlights Complete protection for your Android device that simplifies security
Fingerprint Authentication Guide
 Fingerprint Authentication Guide What is fingerprint authentication? An electronic device is used to capture a digital image of a fingerprint pattern. This image is digitally processed to create a biometric
Fingerprint Authentication Guide What is fingerprint authentication? An electronic device is used to capture a digital image of a fingerprint pattern. This image is digitally processed to create a biometric
Hans Joachim Jelena Mirkovic Ivica Milanovic Øyvind Bakkeli
 Hans Joachim Jelena Mirkovic Ivica Milanovic Øyvind Bakkeli Introduction Research questions: What are most common and accepted authentication methods for mobile services? What are differences, opportunities
Hans Joachim Jelena Mirkovic Ivica Milanovic Øyvind Bakkeli Introduction Research questions: What are most common and accepted authentication methods for mobile services? What are differences, opportunities
Identification, authentication, authorisation. Identification and authentication. Authentication. Authentication. Three closely related concepts:
 Identification, authentication, authorisation Three closely related concepts: Identification and authentication WSPC, Chapter 6 Identification: associating an identity with a subject ( Who are you? ) Authentication:
Identification, authentication, authorisation Three closely related concepts: Identification and authentication WSPC, Chapter 6 Identification: associating an identity with a subject ( Who are you? ) Authentication:
NFC Identity and Access Control
 NFC Identity and Access Control Peter Cattaneo Vice President, Business Development Agenda Basics NFC User Interactions Architecture (F)ICAM Physical Access Logical Access Future Evolution 2 NFC Identity
NFC Identity and Access Control Peter Cattaneo Vice President, Business Development Agenda Basics NFC User Interactions Architecture (F)ICAM Physical Access Logical Access Future Evolution 2 NFC Identity
MOBILE COMPUTING 2/14/17. System Structure. Context as Implicit Input. explicit input. explicit output. explicit input.
 MOBILE COMPUTING CSE 40814/60814 Spring 2017 System Structure explicit input explicit output Context as Implicit Input explicit input explicit output Context: state of the user state of the physical environment
MOBILE COMPUTING CSE 40814/60814 Spring 2017 System Structure explicit input explicit output Context as Implicit Input explicit input explicit output Context: state of the user state of the physical environment
Integration tool user manual
 Integration tool user manual contact@ilocksystems.com www.ilocksystems.com tel.+ (48) 61 669 06 87 technical support: support@ilocksystems.com 1 P age Table of contents I. Basic information.... 2 1. What
Integration tool user manual contact@ilocksystems.com www.ilocksystems.com tel.+ (48) 61 669 06 87 technical support: support@ilocksystems.com 1 P age Table of contents I. Basic information.... 2 1. What
Version B Wi-Fi IP CAMERA
 HD Version B-1.0.0 Wi-Fi IP CAMERA Quick Start Guide Table of Contents Get Started... 1 Hardware Installation... 1 Live Video... 2 Live Video via Wi-Fi... 6 Camera Settings... 8 Change Password... 8 Alarm
HD Version B-1.0.0 Wi-Fi IP CAMERA Quick Start Guide Table of Contents Get Started... 1 Hardware Installation... 1 Live Video... 2 Live Video via Wi-Fi... 6 Camera Settings... 8 Change Password... 8 Alarm
StarryBay. User Guide
 StarryBay User Guide SW-08 Smart Watch 1 / 13 Contents 3 Chapter 1: Overview 3 External part & Internal part 3 Accessories 3 On screen keyboard 4 Basic gestures 5 Status icons 6 Three working modes 7 Chapter
StarryBay User Guide SW-08 Smart Watch 1 / 13 Contents 3 Chapter 1: Overview 3 External part & Internal part 3 Accessories 3 On screen keyboard 4 Basic gestures 5 Status icons 6 Three working modes 7 Chapter
Quick Heal Mobile Security. Anti-Theft Security. Real-Time Protection. Safe Online Banking & Shopping.
 Anti-Theft Security. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights With an easy-to-update virus protection and a dynamic yet simple interface, virus removal from your mobile
Anti-Theft Security. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights With an easy-to-update virus protection and a dynamic yet simple interface, virus removal from your mobile
WSD-F20 Quick Operation Guide Smart Outdoor Watch
 Smart Outdoor Watch WSD-F0 Getting Ready to Use the Product Depending on factors such as differences in product software versions, the screen displays and operations may differ from those shown in this.
Smart Outdoor Watch WSD-F0 Getting Ready to Use the Product Depending on factors such as differences in product software versions, the screen displays and operations may differ from those shown in this.
Google 2 factor authentication User Guide
 Google 2 factor authentication User Guide Description: Updated Date: This guide describes how to setup Two factor authentication for your Google account. March, 2018 Summary ITSC is pleased to launch Two
Google 2 factor authentication User Guide Description: Updated Date: This guide describes how to setup Two factor authentication for your Google account. March, 2018 Summary ITSC is pleased to launch Two
Quick Setup Guide. Tip: We recommend you use a Vodafone SIM card. SIM cards from other networks might not work!
 Owner s Manual Quick Setup Guide Insert the SIM card into the watch. The SIM slot is behind the rubber cover labelled SIM CARD on the left of the watch. Use a fingernail or other small item to prise open
Owner s Manual Quick Setup Guide Insert the SIM card into the watch. The SIM slot is behind the rubber cover labelled SIM CARD on the left of the watch. Use a fingernail or other small item to prise open
ECE 1160/2160 Embedded Systems Design. Projects and Demos. Wei Gao. ECE 1160/2160 Embedded Systems Design
 ECE 1160/2160 Embedded Systems Design Projects and Demos Wei Gao ECE 1160/2160 Embedded Systems Design 1 Project Group project 45% Proposal presentation 5% Midterm presentation/demo 10% Final presentation/demo
ECE 1160/2160 Embedded Systems Design Projects and Demos Wei Gao ECE 1160/2160 Embedded Systems Design 1 Project Group project 45% Proposal presentation 5% Midterm presentation/demo 10% Final presentation/demo
WELCOME : OVERVIEW Mobile Applications Testing. Copyright
 WELCOME : OVERVIEW Mobile Applications Testing Copyright NataliaS@portnov.com 1 INTRODUCTION: Mobile APP vs Desktop and WEB Ever since the first cell phone hit the commercial market in 1983, the mobile
WELCOME : OVERVIEW Mobile Applications Testing Copyright NataliaS@portnov.com 1 INTRODUCTION: Mobile APP vs Desktop and WEB Ever since the first cell phone hit the commercial market in 1983, the mobile
Now there is: Asignio web-based signature authentication.
 THE COST OF KYC AND AML Know Your Customer (KYC) technology and Anti-Money Laundering (AML) compliance are crucial elements of modern banking. Financial institutions are trusted to verify and authenticate
THE COST OF KYC AND AML Know Your Customer (KYC) technology and Anti-Money Laundering (AML) compliance are crucial elements of modern banking. Financial institutions are trusted to verify and authenticate
Technical White Paper. Behaviometrics. Measuring FAR/FRR/EER in Continuous Authentication
 Technical White Paper Behaviometrics Measuring FAR/FRR/EER in Continuous Authentication Draft version 12/22/2009 Table of Contents Background... 1 Calculating FAR/FRR/EER in the field of Biometrics...
Technical White Paper Behaviometrics Measuring FAR/FRR/EER in Continuous Authentication Draft version 12/22/2009 Table of Contents Background... 1 Calculating FAR/FRR/EER in the field of Biometrics...
User Guide LC4. Before using this product, please read the guide carefully to avoid any damage to the product.
 User Guide LC4 Before using this product, please read the guide carefully to avoid any damage to the product. 1. Product Description 1.1 Packing list IP Camera User Manual Before using this product, please
User Guide LC4 Before using this product, please read the guide carefully to avoid any damage to the product. 1. Product Description 1.1 Packing list IP Camera User Manual Before using this product, please
BIOMETRIC MECHANISM FOR ONLINE TRANSACTION ON ANDROID SYSTEM ENHANCED SECURITY OF. Anshita Agrawal
 BIOMETRIC MECHANISM FOR ENHANCED SECURITY OF ONLINE TRANSACTION ON ANDROID SYSTEM 1 Anshita Agrawal CONTENTS Introduction Biometric Authentication Fingerprints Proposed System Conclusion References 2 INTRODUCTION
BIOMETRIC MECHANISM FOR ENHANCED SECURITY OF ONLINE TRANSACTION ON ANDROID SYSTEM 1 Anshita Agrawal CONTENTS Introduction Biometric Authentication Fingerprints Proposed System Conclusion References 2 INTRODUCTION
Quick Heal Total Security for Android. Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping.
 Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that simplifies security and significantly
Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that simplifies security and significantly
Cybersecurity Challenges for Connected and Automated Vehicles. Robert W. Heller, Ph.D. Program Director R&D, Southwest Research Institute
 Cybersecurity Challenges for Connected and Automated Vehicles Robert W. Heller, Ph.D. Program Director R&D, Southwest Research Institute Cars are becoming complex (and CAV is only part of it) 1965: No
Cybersecurity Challenges for Connected and Automated Vehicles Robert W. Heller, Ph.D. Program Director R&D, Southwest Research Institute Cars are becoming complex (and CAV is only part of it) 1965: No
CHI Easy Access: Register From on the CHI Network
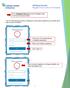 CHI Easy Access: Register From on the CHI Network Go to chieasyaccess.org and click "Register Now." You'll see the screen below. Your CHI Easy Access account is configured to use the same password you
CHI Easy Access: Register From on the CHI Network Go to chieasyaccess.org and click "Register Now." You'll see the screen below. Your CHI Easy Access account is configured to use the same password you
CS 528 Mobile and Ubiquitous Computing Lecture 7b: Smartphone Sensing. Emmanuel Agu
 CS 528 Mobile and Ubiquitous Computing Lecture 7b: Smartphone Sensing Emmanuel Agu Smartphone Sensors Typical smartphone sensors today accelerometer, compass, GPS, microphone, camera, proximity Use machine
CS 528 Mobile and Ubiquitous Computing Lecture 7b: Smartphone Sensing Emmanuel Agu Smartphone Sensors Typical smartphone sensors today accelerometer, compass, GPS, microphone, camera, proximity Use machine
POPA MOBILE BANKING USER GUIDE
 POPA MOBILE BANKING USER GUIDE 2 P OPA Federal Credit Union Safely Access your POPA Accounts At Your Fingertips. POPA Mobile Banking (MB) gives you the power to manage your accounts right from the palm
POPA MOBILE BANKING USER GUIDE 2 P OPA Federal Credit Union Safely Access your POPA Accounts At Your Fingertips. POPA Mobile Banking (MB) gives you the power to manage your accounts right from the palm
New Paradigms of Digital Identity:
 A Telefonica White Paper New Paradigms of Digital Identity: Authentication and Authorization as a Service (AuthaaS) February 2016 1. Introduction The concept of identity has always been the key factor
A Telefonica White Paper New Paradigms of Digital Identity: Authentication and Authorization as a Service (AuthaaS) February 2016 1. Introduction The concept of identity has always been the key factor
6.S062: Mobile and Sensor Computing aka IoT Systems
 6.S062: Mobile and Sensor Computing aka IoT Systems http://6s062.github.io/6mob Lecturers Hari Balakrishnan (hari@csail.mit.edu) Fadel Adib (fadel@mit.edu) TA Hyunjoon (Richard) Song (rsong@mit.edu) Course
6.S062: Mobile and Sensor Computing aka IoT Systems http://6s062.github.io/6mob Lecturers Hari Balakrishnan (hari@csail.mit.edu) Fadel Adib (fadel@mit.edu) TA Hyunjoon (Richard) Song (rsong@mit.edu) Course
How to install Internet Security for Android app
 How to install Internet Security for Android app 1. Go to Google Play Store app. 2. In the dialog window enter Kaspersky Mobile Antivirus: Web Security & AppLock. Tap INSTALL to allow the app to install
How to install Internet Security for Android app 1. Go to Google Play Store app. 2. In the dialog window enter Kaspersky Mobile Antivirus: Web Security & AppLock. Tap INSTALL to allow the app to install
Role of Biometrics in Cybersecurity. Sam Youness
 Role of Biometrics in Cybersecurity Sam Youness Agenda Biometrics basics How it works Biometrics applications and architecture Biometric devices Biometrics Considerations The road ahead The Basics Everyday
Role of Biometrics in Cybersecurity Sam Youness Agenda Biometrics basics How it works Biometrics applications and architecture Biometric devices Biometrics Considerations The road ahead The Basics Everyday
Qustodio. User Guide. Copyright Qustodio Technologies S.L. All rights reserved. Revised on June 2017.
 Qustodio User Guide Copyright Qustodio Technologies S.L. All rights reserved. Revised on June 2017. Table of Contents 1. INTRODUCTION... 3 1.1. WHAT IS QUSTODIO?... 3 1.2. FEATURES AND BENEFITS... 4 2.
Qustodio User Guide Copyright Qustodio Technologies S.L. All rights reserved. Revised on June 2017. Table of Contents 1. INTRODUCTION... 3 1.1. WHAT IS QUSTODIO?... 3 1.2. FEATURES AND BENEFITS... 4 2.
Volume UNCHAINED WARRIOR LIMITED UNCHAINED WARRIOR CHARGED UWTRK-007 QUICK START USER GUIDE 1.2. Charged: Smart Bracelet
 Volume 1 UNCHAINED WARRIOR LIMITED UNCHAINED WARRIOR CHARGED UWTRK-007 QUICK START USER GUIDE 1.2 Charged: Smart Bracelet U N C H A I N E D W A R R I O R L I M I T E D User Guide for Charged Smart Bracelet
Volume 1 UNCHAINED WARRIOR LIMITED UNCHAINED WARRIOR CHARGED UWTRK-007 QUICK START USER GUIDE 1.2 Charged: Smart Bracelet U N C H A I N E D W A R R I O R L I M I T E D User Guide for Charged Smart Bracelet
GeisingerConnect PingID Mobile App Enrollment Guide
 Purpose of this Guide This guide is intended for users who need to enroll in the PingID mobile device app to use PingID for logging into GeisingerConnect. If you replace your phone, please contact the
Purpose of this Guide This guide is intended for users who need to enroll in the PingID mobile device app to use PingID for logging into GeisingerConnect. If you replace your phone, please contact the
Hacking challenge: steal a car!
 Hacking challenge: steal a car! Your "local partner in crime" Sławomir Jasek IT security expert since 2005, and still loves this job Agenda BLE vs security How to hack the car New tool Vulnerabilities
Hacking challenge: steal a car! Your "local partner in crime" Sławomir Jasek IT security expert since 2005, and still loves this job Agenda BLE vs security How to hack the car New tool Vulnerabilities
ANZ FASTPAY USER GUIDE
 ANZ FASTPAY USER GUIDE WELCOME TO YOUR ANZ FASTPAY USER GUIDE CONTENTS What you need to set up ANZ FastPay 2 What s in your ANZ FastPay box? 2 Where else to find help and information 3 Get to know your
ANZ FASTPAY USER GUIDE WELCOME TO YOUR ANZ FASTPAY USER GUIDE CONTENTS What you need to set up ANZ FastPay 2 What s in your ANZ FastPay box? 2 Where else to find help and information 3 Get to know your
Sophos Mobile Security
 Help Product Version: 8.5 Contents About Sophos Mobile Security...1 Dashboard... 2 Scanner... 3 Web Filtering... 4 App Protection...5 Call Blocking...6 Loss & Theft...7 Configure Loss & Theft... 8 Wi-Fi
Help Product Version: 8.5 Contents About Sophos Mobile Security...1 Dashboard... 2 Scanner... 3 Web Filtering... 4 App Protection...5 Call Blocking...6 Loss & Theft...7 Configure Loss & Theft... 8 Wi-Fi
SMARTWATCH WITH ACTIVITY AND SLEEP TRACKER
 2 SMARTWATCH WITH ACTIVITY AND SLEEP TRACKER TIME CALLS ACTIVITY KEY FACTS UNIQUE SELLING POINTS PRICE 79,90 COMPATIBILITY ios, Android, Windows Phone, PC Windows, MAC DESIGN fashion and Swiss design Available
2 SMARTWATCH WITH ACTIVITY AND SLEEP TRACKER TIME CALLS ACTIVITY KEY FACTS UNIQUE SELLING POINTS PRICE 79,90 COMPATIBILITY ios, Android, Windows Phone, PC Windows, MAC DESIGN fashion and Swiss design Available
MOBILE COMPUTING 2/11/18. System Structure. Context as Implicit Input. explicit input. explicit output. explicit input.
 MOBILE COMPUTING CSE 40814/60814 Spring 2018 System Structure explicit input explicit output Context as Implicit Input explicit input explicit output Context: state of the user state of the physical environment
MOBILE COMPUTING CSE 40814/60814 Spring 2018 System Structure explicit input explicit output Context as Implicit Input explicit input explicit output Context: state of the user state of the physical environment
B.TECH/M.TECH MINOR/MAJOR PROJECT
 1 B.TECH/M.TECH MINOR/MAJOR PROJECT CSE/IT Project list of JAVA/ANDROID: New Patient Registry Management system MySQL Database Management Using Java Restaurant Billing Management System Library Management
1 B.TECH/M.TECH MINOR/MAJOR PROJECT CSE/IT Project list of JAVA/ANDROID: New Patient Registry Management system MySQL Database Management Using Java Restaurant Billing Management System Library Management
Quick Reference Guide
 Quick Reference Guide Unlocked ¹ Table of Contents 2 Samsung Care 3 Know your device 5 Device setup 9 Home screen 12 Volume and ringtones 13 Hello Bixby 14 Useful apps 15 Calls 16 Voicemail 17 Contacts
Quick Reference Guide Unlocked ¹ Table of Contents 2 Samsung Care 3 Know your device 5 Device setup 9 Home screen 12 Volume and ringtones 13 Hello Bixby 14 Useful apps 15 Calls 16 Voicemail 17 Contacts
User Guide (Android)
 Heart Foundation Walking App User Guide (Android) The Heart Foundation Walking app is a joint venture between the Australian Government and the National Heart Foundation Australia, looking to improve the
Heart Foundation Walking App User Guide (Android) The Heart Foundation Walking app is a joint venture between the Australian Government and the National Heart Foundation Australia, looking to improve the
Multi-Factor Authentication (MFA)
 What is it? Multi-Factor Authentication, or MFA, is a process that requires more than one type of authentication to gain access to a program. You have probably seen this with your bank or other secure
What is it? Multi-Factor Authentication, or MFA, is a process that requires more than one type of authentication to gain access to a program. You have probably seen this with your bank or other secure
Keystroke Dynamics: Low Impact Biometric Verification
 Keystroke Dynamics: Low Impact Biometric Verification Tom Olzak September 2006 Biometrics has long been one of the solutions touted by security vendors to meet multifactor authentication objectives. However,
Keystroke Dynamics: Low Impact Biometric Verification Tom Olzak September 2006 Biometrics has long been one of the solutions touted by security vendors to meet multifactor authentication objectives. However,
Quick Start Guide. This guide provides an overview of the basic functions of your devices and simple step-by-step installation instructions.
 Quick Start Guide This guide provides an overview of the basic functions of your devices and simple step-by-step installation instructions. W Welcome Welcome to In-Drive, an in-vehicle system that offers
Quick Start Guide This guide provides an overview of the basic functions of your devices and simple step-by-step installation instructions. W Welcome Welcome to In-Drive, an in-vehicle system that offers
User Guide Advanced Authentication - Smartphone Applications. Version 6.1
 User Guide Advanced Authentication - Smartphone Applications Version 6.1 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S.
User Guide Advanced Authentication - Smartphone Applications Version 6.1 Legal Notices For information about legal notices, trademarks, disclaimers, warranties, export and other use restrictions, U.S.
User Authentication and Human Factors
 CSE 484 / CSE M 584 (Autumn 2011) User Authentication and Human Factors Daniel Halperin Tadayoshi Kohno Thanks to Dan Boneh, Dieter Gollmann, John Manferdelli, John Mitchell, Vitaly Shmatikov, Bennet Yee,
CSE 484 / CSE M 584 (Autumn 2011) User Authentication and Human Factors Daniel Halperin Tadayoshi Kohno Thanks to Dan Boneh, Dieter Gollmann, John Manferdelli, John Mitchell, Vitaly Shmatikov, Bennet Yee,
Ctdigi.com. Instruction manual. Production by S & W Technology Labs
 Ctdigi.com Instruction manual Production by S & W Technology Labs I. Install app II. Guard camera Guard camera Introduction Accessory Sensor Scenario Guard 360 Introduction - Catalog - Install app Scenario
Ctdigi.com Instruction manual Production by S & W Technology Labs I. Install app II. Guard camera Guard camera Introduction Accessory Sensor Scenario Guard 360 Introduction - Catalog - Install app Scenario
37 FAQs ABOUT CELLCONTROL ASKED BY PARENTS OF NEW DRIVERS
 37 FAQs ABOUT CELLCONTROL ASKED BY PARENTS OF NEW DRIVERS TABLE OF CONTENTS INTRODUCTION 3 QUESTIONS BEFORE YOU BUY 4 USING CELLCONTROL 9 iphone-specific QUESTIONS 14 ANDROID AND WINDOWS PHONE-SPECIFIC
37 FAQs ABOUT CELLCONTROL ASKED BY PARENTS OF NEW DRIVERS TABLE OF CONTENTS INTRODUCTION 3 QUESTIONS BEFORE YOU BUY 4 USING CELLCONTROL 9 iphone-specific QUESTIONS 14 ANDROID AND WINDOWS PHONE-SPECIFIC
HKIoTDemo Documentation
 HKIoTDemo Documentation Release 1.0 Eric Tran, Tyler Freckmann October 12, 2016 Contents 1 Video of the Demo 3 2 About the project 5 3 Challenges we ran into 7 4 Architecture Overview 9 4.1 Architecture
HKIoTDemo Documentation Release 1.0 Eric Tran, Tyler Freckmann October 12, 2016 Contents 1 Video of the Demo 3 2 About the project 5 3 Challenges we ran into 7 4 Architecture Overview 9 4.1 Architecture
MOBILE INPUT LUKE WROBLEWSKI DESIGN FOR MOBILE
 MOBILE INPUT LUKE WROBLEWSKI DESIGN FOR MOBILE 2010 @LUKEW 1 MOBILE INPUT 1. Put in the effort where there s payoff. 2. Take the pain out of forms. Put it on yourself. 3. Look beyond forms for input. 2
MOBILE INPUT LUKE WROBLEWSKI DESIGN FOR MOBILE 2010 @LUKEW 1 MOBILE INPUT 1. Put in the effort where there s payoff. 2. Take the pain out of forms. Put it on yourself. 3. Look beyond forms for input. 2
CS 403X Mobile and Ubiquitous Computing Lecture 14: Google Places, Other Useful Android APIs and Cool Location Aware Apps Emmanuel Agu
 CS 403X Mobile and Ubiquitous Computing Lecture 14: Google Places, Other Useful Android APIs and Cool Location Aware Apps Emmanuel Agu Google Places Place: physical space that has a name (e.g. local businesses,
CS 403X Mobile and Ubiquitous Computing Lecture 14: Google Places, Other Useful Android APIs and Cool Location Aware Apps Emmanuel Agu Google Places Place: physical space that has a name (e.g. local businesses,
Tizen apps with. Context Awareness, powered by AI. by Shashwat Pradhan, CEO Emberify
 Tizen apps with 1 Context Awareness, powered by AI by Shashwat Pradhan, CEO Emberify Introduction Context refers to information that characterizes a situation, between: Apps People Surrounding environment
Tizen apps with 1 Context Awareness, powered by AI by Shashwat Pradhan, CEO Emberify Introduction Context refers to information that characterizes a situation, between: Apps People Surrounding environment
Stuart Hall ICTN /10/17 Advantages and Drawbacks to Using Biometric Authentication
 Stuart Hall ICTN 4040 601 04/10/17 Advantages and Drawbacks to Using Biometric Authentication As technology advances, so must the means of heightened information security. Corporate businesses, hospitals
Stuart Hall ICTN 4040 601 04/10/17 Advantages and Drawbacks to Using Biometric Authentication As technology advances, so must the means of heightened information security. Corporate businesses, hospitals
Authentication SPRING 2018: GANG WANG. Slides credit: Michelle Mazurek (U-Maryland) and Blase Ur (CMU)
 Authentication SPRING 2018: GANG WANG Slides credit: Michelle Mazurek (U-Maryland) and Blase Ur (CMU) Passwords, Hashes, Salt Password database Username Plaintext Password Not a good idea to store plaintext
Authentication SPRING 2018: GANG WANG Slides credit: Michelle Mazurek (U-Maryland) and Blase Ur (CMU) Passwords, Hashes, Salt Password database Username Plaintext Password Not a good idea to store plaintext
ITU-T SG 17 Q10/17. Trust Elevation Frameworks
 ITU-T SG 17 Q10/17 Trust Elevation Frameworks Abbie Barbir, Ph.D. ITU-T SG 17 Q10 Rapporteur Martin Euchner SG 17 Advisor ITU Workshop on "Future Trust and Knowledge Infrastructure July 1 2016 Contents
ITU-T SG 17 Q10/17 Trust Elevation Frameworks Abbie Barbir, Ph.D. ITU-T SG 17 Q10 Rapporteur Martin Euchner SG 17 Advisor ITU Workshop on "Future Trust and Knowledge Infrastructure July 1 2016 Contents
Using the Mobile App for Defense Connect Online
 Using the Mobile App for Defense Connect Online Conduct and Attend Meetings Virtually Anywhere AUTHOR Aaron W Wolf DCO Evangelist Carahsoft Technology Corp. 703.889.9781 aaron.w.wolf@carahsoft.com Defense
Using the Mobile App for Defense Connect Online Conduct and Attend Meetings Virtually Anywhere AUTHOR Aaron W Wolf DCO Evangelist Carahsoft Technology Corp. 703.889.9781 aaron.w.wolf@carahsoft.com Defense
Contents. Multi-Factor Authentication Overview. Available MFA Factors
 The purpose of this document is to provide National University student Single Sign-On users with instructions for how to configure and use Multi-Factor Authentication. Contents Multi-Factor Authentication
The purpose of this document is to provide National University student Single Sign-On users with instructions for how to configure and use Multi-Factor Authentication. Contents Multi-Factor Authentication
The Future of Authentication
 The Future of Authentication Table of Contents Introduction Facial Recognition Liveness Detection and Multimodal Biometrics FIDO: Standards-Based, Password-Free Authentication Biometric Authentication
The Future of Authentication Table of Contents Introduction Facial Recognition Liveness Detection and Multimodal Biometrics FIDO: Standards-Based, Password-Free Authentication Biometric Authentication
Quick Operation Guide
 Getting Ready to Use the Product This shows typical screen displays and operations. Procedures on the smartphone Important The Wear OS by Google app must be installed. Ensure that the watch is fully charged.
Getting Ready to Use the Product This shows typical screen displays and operations. Procedures on the smartphone Important The Wear OS by Google app must be installed. Ensure that the watch is fully charged.
CS 4518 Mobile and Ubiquitous Computing Lecture 15: Final Project Slides/Paper, Other Ubicomp Android APIs Emmanuel Agu
 CS 4518 Mobile and Ubiquitous Computing Lecture 15: Final Project Slides/Paper, Other Ubicomp Android APIs Emmanuel Agu The Rest of the Class The Rest of this class Part 1: Course and Android Introduction
CS 4518 Mobile and Ubiquitous Computing Lecture 15: Final Project Slides/Paper, Other Ubicomp Android APIs Emmanuel Agu The Rest of the Class The Rest of this class Part 1: Course and Android Introduction
Gurmeet Kaur 1, Parikshit 2, Dr. Chander Kant 3 1 M.tech Scholar, Assistant Professor 2, 3
 Volume 8 Issue 2 March 2017 - Sept 2017 pp. 72-80 available online at www.csjournals.com A Novel Approach to Improve the Biometric Security using Liveness Detection Gurmeet Kaur 1, Parikshit 2, Dr. Chander
Volume 8 Issue 2 March 2017 - Sept 2017 pp. 72-80 available online at www.csjournals.com A Novel Approach to Improve the Biometric Security using Liveness Detection Gurmeet Kaur 1, Parikshit 2, Dr. Chander
Frequently Asked Questions Retiro Móvil (Mobile Withdrawal)
 Frequently Asked Questions Retiro Móvil (Mobile Withdrawal) 1. What is Retiro Móvil (Mobile Withdrawal)? Retiro Móvil (Mobile Withdrawal) is a free service that allows you to schedule withdrawal requests
Frequently Asked Questions Retiro Móvil (Mobile Withdrawal) 1. What is Retiro Móvil (Mobile Withdrawal)? Retiro Móvil (Mobile Withdrawal) is a free service that allows you to schedule withdrawal requests
Do not place or mount Ocli 1 in an area where it will be exposed to water. Ocli 1 is designed for indoor use.
 1 Manual: Ocli 1 with Observeye Viewer App for Android Setting Up Ocli 1 Live Viewing with Ocli 1 Recording Video and Taking Snapshots Using Advanced Features Setting Up Ocli 1 Place or Mount the Camera
1 Manual: Ocli 1 with Observeye Viewer App for Android Setting Up Ocli 1 Live Viewing with Ocli 1 Recording Video and Taking Snapshots Using Advanced Features Setting Up Ocli 1 Place or Mount the Camera
Consumer Banking User Guide. Getting Started
 Consumer Banking User Guide Getting Started Contents About the platform... 3 Installing the mobile banking app... 4 Opening mobile banking... 4 Accessing the online banking site... 4 Browser requirements...
Consumer Banking User Guide Getting Started Contents About the platform... 3 Installing the mobile banking app... 4 Opening mobile banking... 4 Accessing the online banking site... 4 Browser requirements...
Markus Jakobsson Elaine Shi Philippe Golle Richard Chow (Palo Alto Research Center) Thanks to Yuan Niu (UC Davis)
 Implicit Authentication for Mobile Devices Markus Jakobsson Elaine Shi Philippe Golle Richard Chow (Palo Alto Research Center) Thanks to Yuan Niu (UC Davis) Authentication trends Increased demand for authentication
Implicit Authentication for Mobile Devices Markus Jakobsson Elaine Shi Philippe Golle Richard Chow (Palo Alto Research Center) Thanks to Yuan Niu (UC Davis) Authentication trends Increased demand for authentication
Tracking driver actions and guiding phone usage for safer driving. Hongyu Li Jan 25, 2018
 Tracking driver actions and guiding phone usage for safer driving Hongyu Li Jan 25, 2018 1 Smart devices risks and opportunities Phone in use 14% Other distractions 86% Distraction-Affected Fatalities
Tracking driver actions and guiding phone usage for safer driving Hongyu Li Jan 25, 2018 1 Smart devices risks and opportunities Phone in use 14% Other distractions 86% Distraction-Affected Fatalities
The 10 step communication plan
 The 10 step communication plan Follow these 10 suggested steps and you will be successful at launching the Specops password reset service. Step 1 Activity: Intranet texts explaining the service Suggested
The 10 step communication plan Follow these 10 suggested steps and you will be successful at launching the Specops password reset service. Step 1 Activity: Intranet texts explaining the service Suggested
Virtual Keypad App Help Last update: 2017/02/02
 Virtual Keypad App Help 16461 Last update: 2017/02/02 Table of Contents Virtual Keypad App Help Center... 1 Managing Your App Account... 2 Using Your App... 3 System in Alarm... 4 Contacting Your Security
Virtual Keypad App Help 16461 Last update: 2017/02/02 Table of Contents Virtual Keypad App Help Center... 1 Managing Your App Account... 2 Using Your App... 3 System in Alarm... 4 Contacting Your Security
9/27/15 MOBILE COMPUTING. CSE 40814/60814 Fall System Structure. explicit output. explicit input
 MOBILE COMPUTING CSE 40814/60814 Fall 2015 System Structure explicit input explicit output 1 Context as Implicit Input explicit input explicit output Context: state of the user state of the physical environment
MOBILE COMPUTING CSE 40814/60814 Fall 2015 System Structure explicit input explicit output 1 Context as Implicit Input explicit input explicit output Context: state of the user state of the physical environment
Quick Heal Mobile Security. Free protection for your Android phone against virus attacks, unwanted calls, and theft.
 Free protection for your Android phone against virus attacks, unwanted calls, and theft. Product Highlights With an easy-to-update virus protection and a dynamic yet simple interface, virus removal from
Free protection for your Android phone against virus attacks, unwanted calls, and theft. Product Highlights With an easy-to-update virus protection and a dynamic yet simple interface, virus removal from
More than time. Spring-Summer 2014 Collection
 T h e S m a r t w a t c h d e s i g n e d i n S w i t z e r l a n d More than time About Us MyKronoz Founded in January 2013, Kronoz LLC is a Swiss-based company that manufactures, designs and develops
T h e S m a r t w a t c h d e s i g n e d i n S w i t z e r l a n d More than time About Us MyKronoz Founded in January 2013, Kronoz LLC is a Swiss-based company that manufactures, designs and develops
Smartphone App User Guide
 Smartphone App User Guide Introduction The Buddy GPS Pet Tracker utilises a combination of location technologies to provide the best solution for keeping an eye on your pets. GPS, LBS (mobile tower triangulation)
Smartphone App User Guide Introduction The Buddy GPS Pet Tracker utilises a combination of location technologies to provide the best solution for keeping an eye on your pets. GPS, LBS (mobile tower triangulation)
TWO-STEP VERIFICATION USER GUIDE
 TWO-STEP VERIFICATION USER GUIDE TWO-STEP PROTECTS YOUR DATA EVEN IF YOUR PENNKEY PASSWORD IS COMPROMISED PROTECT YOUR PENN & PERSONAL DATA! Table of Contents Two-Step Verification User Guide... 2 1. Introduction...
TWO-STEP VERIFICATION USER GUIDE TWO-STEP PROTECTS YOUR DATA EVEN IF YOUR PENNKEY PASSWORD IS COMPROMISED PROTECT YOUR PENN & PERSONAL DATA! Table of Contents Two-Step Verification User Guide... 2 1. Introduction...
EMBEDDED SYSTEMS AND MOBILE SYSTEMS
 EMBEDDED SYSTEMS AND MOBILE SYSTEMS Embedded systems Sensors, actuators, devices 8-bit uc, sensors, actuators Mobile systems: Portable PC (powerfull, WiFi connected, heavy, cumbersome, about 4h of battery
EMBEDDED SYSTEMS AND MOBILE SYSTEMS Embedded systems Sensors, actuators, devices 8-bit uc, sensors, actuators Mobile systems: Portable PC (powerfull, WiFi connected, heavy, cumbersome, about 4h of battery
Passwords. EJ Jung. slide 1
 Passwords EJ Jung slide 1 Basic Problem? How do you prove to someone that you are who you claim to be? Any system with access control must solve this problem slide 2 Many Ways to Prove Who You Are What
Passwords EJ Jung slide 1 Basic Problem? How do you prove to someone that you are who you claim to be? Any system with access control must solve this problem slide 2 Many Ways to Prove Who You Are What
HSBC INTRODUCES A SOCIAL P2P PAYMENT APP TO HONG KONG Easy to use and available to everyone
 News Release 7 February 2017 HSBC INTRODUCES A SOCIAL P2P PAYMENT APP TO HONG KONG Easy to use and available to everyone HSBC today announced PayMe, a simple and secure social payment app that allows HSBC
News Release 7 February 2017 HSBC INTRODUCES A SOCIAL P2P PAYMENT APP TO HONG KONG Easy to use and available to everyone HSBC today announced PayMe, a simple and secure social payment app that allows HSBC
Information Security Identification and authentication. Advanced User Authentication II
 Information Security Identification and authentication Advanced User Authentication II 2016-01-29 Amund Hunstad Guest Lecturer, amund@foi.se Agenda for lecture I within this part of the course Background
Information Security Identification and authentication Advanced User Authentication II 2016-01-29 Amund Hunstad Guest Lecturer, amund@foi.se Agenda for lecture I within this part of the course Background
Overview. Background. Intelligence at the Edge. Learning at the Edge: Challenges and Brainstorming. Amazon Alexa Smart Home!
 Overview Background Intelligence at the Edge Samsung Research Learning at the Edge: Challenges and Brainstorming Amazon Alexa Smart Home! Background Ph.D. at UW CSE RFID, Mobile, Sensors, Data Nokia Research
Overview Background Intelligence at the Edge Samsung Research Learning at the Edge: Challenges and Brainstorming Amazon Alexa Smart Home! Background Ph.D. at UW CSE RFID, Mobile, Sensors, Data Nokia Research
GETTING STARTED HEALTH & SAFETY
 HEADSET USER MANUAL HEADPHONES 1. Pull out the 3.5 mm audio cable and insert the connector into the phone s headphone jack. Close the cover. iphone 7 users will need the adapter supplied with the phone.
HEADSET USER MANUAL HEADPHONES 1. Pull out the 3.5 mm audio cable and insert the connector into the phone s headphone jack. Close the cover. iphone 7 users will need the adapter supplied with the phone.
Volume UNCHAINED WARRIOR LIMITED. Quick Start User Guide 1.2. Smart Bracelet
 Volume 1 UNCHAINED WARRIOR LIMITED Quick Start User Guide 1.2 Smart Bracelet U N C H A I N E D W A R R I O R L I M I T E D User Guide for Smart Bracelet Version 1.2 Unchained Warrior Limited 2017 400 Pavilion
Volume 1 UNCHAINED WARRIOR LIMITED Quick Start User Guide 1.2 Smart Bracelet U N C H A I N E D W A R R I O R L I M I T E D User Guide for Smart Bracelet Version 1.2 Unchained Warrior Limited 2017 400 Pavilion
Thank you for purchasing your new Moochies Watch. We hope you, and more importantly your kids will love it as much as we did creating it.
 www.moochies.com Thank you for purchasing your new Moochies Watch. We hope you, and more importantly your kids will love it as much as we did creating it. This manual will take you through all the steps
www.moochies.com Thank you for purchasing your new Moochies Watch. We hope you, and more importantly your kids will love it as much as we did creating it. This manual will take you through all the steps
FAQ BlueWeigh Activity Tracker
 FAQ BlueWeigh Activity Tracker Before wearing your fitness activity tracker and hit the gym your device needs to be connected to your smartphone. To setup BlueWeigh Activity Tracker please follow the steps
FAQ BlueWeigh Activity Tracker Before wearing your fitness activity tracker and hit the gym your device needs to be connected to your smartphone. To setup BlueWeigh Activity Tracker please follow the steps
Charter Pacific Biometrics Acquisition
 Charter Pacific Biometrics Acquisition Charter Pacific Biometrics Acquisition Charter Pacific has executed a Share Purchase Agreement to acquire 100% of Microlatch. Charter Pacific/Microlatch has a patent
Charter Pacific Biometrics Acquisition Charter Pacific Biometrics Acquisition Charter Pacific has executed a Share Purchase Agreement to acquire 100% of Microlatch. Charter Pacific/Microlatch has a patent
EMBEDDED MAJOR PROJECTS LIST
 CODE PROJECT TITLE APPLICATION TECHNOLOGY /CORE KTEMB 01 KTEMB 02 KTEMB 03 A Location Aided Flooding Mechanism In Community Based Iot Networks An Iot Based Fire Alarming And Authentication System For Workhouse
CODE PROJECT TITLE APPLICATION TECHNOLOGY /CORE KTEMB 01 KTEMB 02 KTEMB 03 A Location Aided Flooding Mechanism In Community Based Iot Networks An Iot Based Fire Alarming And Authentication System For Workhouse
Simpli.Fi. App for wifi DK series cameras OWNER'S MANUAL. APP DSE Simpli.Fi for Wi-Fi DK series cameras. Product description. Download DSE Simpli.
 Page: 1 Simpli.Fi App for wifi DK series cameras Product description Simpli.Fi is THE app to control all our WIFI hidden cameras to investigate Series DK. Our investigation for cameras are IP cameras to
Page: 1 Simpli.Fi App for wifi DK series cameras Product description Simpli.Fi is THE app to control all our WIFI hidden cameras to investigate Series DK. Our investigation for cameras are IP cameras to
Mobile App User Guide
 Mobile App User Guide Introduction The Farmers Trust & Savings Bank Mobile Banking App is a downloadable application that is compatible with numerous mobile devices. These devices include Android phones,
Mobile App User Guide Introduction The Farmers Trust & Savings Bank Mobile Banking App is a downloadable application that is compatible with numerous mobile devices. These devices include Android phones,
STEALING PINS VIA MOBILE SENSORS: ACTUAL RISK VERSUS USER PERCEPTION
 STEALING PINS VIA MOBILE SENSORS: ACTUAL RISK VERSUS USER PERCEPTION Maryam Mehrnezhad Ehsan Toreini Siamak F. Shahandashti Feng Hao Newcastle University, UK At EuroUSEC, July 2016 JavaScript-based attack
STEALING PINS VIA MOBILE SENSORS: ACTUAL RISK VERSUS USER PERCEPTION Maryam Mehrnezhad Ehsan Toreini Siamak F. Shahandashti Feng Hao Newcastle University, UK At EuroUSEC, July 2016 JavaScript-based attack
Mobile Banking User Guide App for Android and iphone
 Downloading the App Simply open the App Store on your phone or device, search for Kansas State Bank or KS StateBank and select the App when it appears. Opening the App After you download the App, it will
Downloading the App Simply open the App Store on your phone or device, search for Kansas State Bank or KS StateBank and select the App when it appears. Opening the App After you download the App, it will
Reviewer s Guide. Ellipse is Simple to Use
 Reviewer s Guide Ellipse - A Smarter Bike Lock Retail price $199. Available for purchase on http://www.lattis.io/. Contact press@lattis.io or visit lattis.io for additional information Smart Keyless entry
Reviewer s Guide Ellipse - A Smarter Bike Lock Retail price $199. Available for purchase on http://www.lattis.io/. Contact press@lattis.io or visit lattis.io for additional information Smart Keyless entry
Congratulations! You just ordered IdentaMaster software package featuring Biometric login, File/Folder Encryption and Entire Drive Encryption.
 INSTALLATION Congratulations! You just ordered IdentaMaster software package featuring Biometric login, File/Folder Encryption and Entire Drive Encryption. From this point on, you may install any additional
INSTALLATION Congratulations! You just ordered IdentaMaster software package featuring Biometric login, File/Folder Encryption and Entire Drive Encryption. From this point on, you may install any additional
Survey Guide: Businesses Should Begin Preparing for the Death of the Password
 Survey Guide: Businesses Should Begin Preparing for the Death of the Password Survey Guide: Businesses Should Begin Preparing for the Death of the Password The way digital enterprises connect with their
Survey Guide: Businesses Should Begin Preparing for the Death of the Password Survey Guide: Businesses Should Begin Preparing for the Death of the Password The way digital enterprises connect with their
An Overview of Biometric Image Processing
 An Overview of Biometric Image Processing CHAPTER 2 AN OVERVIEW OF BIOMETRIC IMAGE PROCESSING The recognition of persons on the basis of biometric features is an emerging phenomenon in our society. Traditional
An Overview of Biometric Image Processing CHAPTER 2 AN OVERVIEW OF BIOMETRIC IMAGE PROCESSING The recognition of persons on the basis of biometric features is an emerging phenomenon in our society. Traditional
user guide AbiBird You will need The AbiBird Sensor and An iphone with ios 10+ OR A Smartphone with Android 5+
 AbiBird user guide AbiBird is an intelligent home activity sensor that connects to a smartphone App. Once set up, the free-standing AbiBird Sensor counts the movements of someone walking past and displays
AbiBird user guide AbiBird is an intelligent home activity sensor that connects to a smartphone App. Once set up, the free-standing AbiBird Sensor counts the movements of someone walking past and displays
Navi 900 IntelliLink, Touch R700 IntelliLink Frequently Asked Questions
 Index 1. Audio... 1 2. Navigation (only Navi 900 IntelliLink)... 2 3. Phone... 3 4. Apple CarPlay... 4 5. Android Auto... 6 6. Speech recognition... 8 7. Color instrument panel... 9 8. Favourites... 9
Index 1. Audio... 1 2. Navigation (only Navi 900 IntelliLink)... 2 3. Phone... 3 4. Apple CarPlay... 4 5. Android Auto... 6 6. Speech recognition... 8 7. Color instrument panel... 9 8. Favourites... 9
