2- Factor Authentication. Another layer of security Ron Brown
|
|
|
- Chloe Nelson
- 5 years ago
- Views:
Transcription
1 2- Factor Authentication Another layer of security Ron Brown
2 2FA HAS BEEN A COMPLETE FAILURE
3 Reason s for Failure Confusing terminology Lack of uniformity across Programs SMS Text vs Text Messaging Poor adoption over the past 7 years Not understanding the risks
4 Mobile Authentication Taskforce Better solution than SMS Text for 2018
5 Who's using 2FA? Usenix Enigma It has been nearly seven years since Google introduced two-factor authentication for Gmail accounts, but virtually no one is using it. In a presentation at Usenix's Enigma 2018 security conference in California, Google software engineer Grzegorz Milka today revealed that, right now, less than 10 per cent of active Google accounts use two-step authentication to lock down their services. 12 per cent of Americans have a password manager to protect their accounts, according to a 2016 Pew study. Google has tried to make the whole process easier to use, but it seems netizens just can t handle it. More than 10 per cent of those trying to use the defense mechanism had problems just inputting an access code sent via SMS.
6 WHAT WILL THE ATTACKER DO TO YOUR ACCOUNT? Once they access your account they will turn off notifications Ransack your InBox for stuff like Bitcoin Wallet Copy compromising pictures Copy Contact List Install a filter to mask their actions
7 Two-factor authentication (or 2FA) is one of the biggestbang-for-your-buck ways to improve the security of your online accounts Extra Security to your online accounts on top of your Password Your site will request something you know to log in ( Password) and something you have your phone or usb security key 1. 2FA is unique to every account 2. Setup process is different 3. Often confusing terminology 4. Recommend start with one accountgoogle
8 One million account logins and passwords are stolen every month, says Google Google has delved into the darker parts of the internet as part of a year-long research project analysing how cybercriminals manage to hijack user accounts by obtaining passwords and login codes. In collaboration with the University of California, Berkeley, Google s research examined three common ways hackers manage to hijack accounts between March 2016 and March 2017 Phishing and keylogging were used by cybercriminals to steal up to a staggering 250,000 account logins every week, Google found.
9 Delayed reporting for 6 weeks CEO-CFO-Director sold all shares CEO got 20M Bonus when fired
10 Equifax data breach was "entirely preventable," congressional report finds A scathing new report finds one of the largest data breaches in U.S. history was "entirely preventable." A 14-month congressional investigation slammed credit rating agency Equifax for lacking preventative measures in a data breach that exposed the personal information of 148 million Americans last year. Report just released December
11 Yahoo's Marissa Mayer Subpoenaed to Testify Before Senate, Says Report Verizon bought Yahoo for $4.48 billion in June 2017 Marissa Mayer- 5 Years with Yahoo and left with a 23M severance package Microsoft sees no reason to increase its bid for Yahoo, two months after it made a $44.6 billion offer to buy the Internet company, people familiar with Microsoft's plans said on Monday. (2010) Verizon reduced its acquisition offer by $350 million following the disclosure of the breaches, purchasing the site for $4.48 billion in cash.
12 Former White House communications director Hope Hicks the longtime Donald Trump aide who finally decided to leave the administration after a domestic abuse scandal involving now-former fellow aide and rumored boyfriend Rob Porter says she can t log into two of her accounts anymore because she was hacked. Hicks told members of Congress two of her accounts are inaccessible following a break-in by an unidentified third party.
13 SMS TEXTING VS TEXT MESSAGING TRUSTED SITE - COOKIES PASSWORDS
14 SENT VIA CELL PHONE NUMBER
15 SENT OVER INTERNET- MESSAGING APP
16 Google Microsoft Facebook Your Bank Last Pass Trusted Sites Browser Cookies C Cleaner
17 The Trick to get your Password Why are Passwords so insecure? Bryon s Story
18 Passwords should be changed every 3 months They should be complicated with upper and lower case They should be 8 characters or more
19 The man in question is Bill Burr, a former manager at the National Institute of Standards and Technology (NIST). In 2003, Burr drafted an eight-page guide on how to create secure passwords creatively called the NIST Special Publication Appendix A. This became the document that would go on to more or less dictate password requirements on everything from accounts to login pages to your online banking portal. All those rules about using uppercase letters and special characters and numbers those are all because of Bill. Much of what I did I now regret, Bill Burr told The Wall Street Journal This is why the latest set of NIST guidelines recommends that people create long passphrases rather than gobbledygook words like the ones Bill thought were secure.
20 Worst Passwords of 2017 SplashData has published its seventh annual "worst passwords" report, compiled from more than 5 million passwords leaked during the year, and there are some notable additions to the list. In anticipation of last weekend's premiere of Star Wars: The Last Jedi, many fans have clearly decided to express their excitement by making "starwars" one of their passwords. It joins the list at number 16, sandwiched between old favourite "abc123" and another new entry, "12312" (rank unchanged since 2016 list) password (unchanged) (up 1) qwerty (Up 2) (Down 2) (New) letmein (New) (Unchanged) football (Down 4) iloveyou (New) admin (Up 4) welcome (Unchanged) monkey (New) login (Down 3) abc123 (Down 1) starwars (New) (New) dragon (Up 1) passw0rd (Down 1) master (Up 1) hello (New) freedom (New) whatever (New) qazwsx (New)
21 Still require strong PW Passwords should withstand 100 guesses it shouldn t be tied to any public information about you or your family. Use a phrase Go long The new NIST guidelines suggest allowing users to create passwords up to 64 characters in length Don t change your password until you have to Choose something memorable Get creative with characters Use two-factor identification
22 5 2FA SMS 2FA Authenticator APP Google Prompt ( Push 2FA) Authenticator Dongle Google Advanced Protection Program Vip s, Politicians, Celebrities Must use Fido U2F YubiKey Cost $18-$25 Limited Apps
23 SMS 2FA Enable SMS 2FA - Provide SMS Phone number Next time you log in with your username and password, you ll also be asked to enter a short code (typically 5-6 digits) that gets texted to your phone. this is a very popular option for sites to implement, since many people have an SMS-capable phone number and it doesn t require installing an app. It provides a significant step up in account security relative to just a username and password.
24 Disadvantages of SMS 2FA Don t want to give out phone number- ( one more piece of personal info) May be used for Targeted advertising or Password Reset Attackers using phone number takeovers could get access to your account without even knowing your account Can t log in if your phone is dead or can not connect to a network Trick phone company to assign # to different SIM Card International Travel Don t own Smart Phone
25 Authenticator APP= Time based one time PW Another phone-based option for 2FA is to use an application that generates codes locally based on a secret key Google Authenticator is a very popular application for this If a site offers this style of 2FA, it will show you a QR code containing the secret key. You can scan that QR code into your application. If you have multiple phones you can scan it multiple times you can also save the image to a safe place or print it out if you need a backup
26 Authenticator App Once you ve scanned such a QR code, your application will produce a new 6-digit code every 30 seconds. Similar to SMS 2FA, you ll have to enter one of these codes in addition to your username and password in order to log in. this style of 2FA improves on SMS 2FA because you can use it even when your phone is not connected to a mobile network the secret key is stored physically on your phone
27 Disadvantages to Authenticator App If your phone dies or gets stolen, and you don t have printed backup codes or a saved copy of the original QR code, you can lose access to your account For this reason, many sites will encourage you to enable SMS 2FA as a backup if you log in frequently on different computers, it can be inconvenient to unlock your phone, open an app, and type in the code each time
28
29 All work the same with a TIME based six digit code Authy works on multiple devices - Android-IOS-Windows Authy works on Desktop Encrypted backup and restore on new phone Free up to 100 authentications/month then $0.09/authenticaton
30 Google Prompt - Push 2FA Google Prompt method, can send a prompt to one of your devices during login This prompt will indicate that someone (possibly you) is trying to log in, and an estimated location for the login attempt. You can then approve or deny the attempt.
31 Push Based 2FA Improves in Authenticator Apps in Two Ways acknowledging the prompt is slightly more convenient than typing in a code, and it is somewhat more resistant to phishing With SMS and authenticator apps, a phishing site can simply ask for your code in addition to your password, and pass that code along to the legitimate site when logging in as you this requires that you pay close attention to a subtle security indicator, IP address
32 It s not Standardized can t consolidate all your push-based credentials in a single app it requires a working data connection on your phone while Authenticator apps don t require any connection Disadvantages of push based 2FA
33 FIDO U2F / Security Keys Universal Second Factor (U2F) is a relatively new style of 2FA, typically using small USB, NFC or Bluetooth Low Energy (BTLE) devices often called security keys. Like push-based 2FA, this means you don t have to type any codes. U2F is also well-designed from a privacy perspective
34 Where do I buy Security Keys? USB security key with Bluetooth connectivity from Feitian standard USB key from Yubico
35 TITAN SECURITY BUNDLE $50 at Google Store
36 GOOGLE'S 'ADVANCED PROTECTION' LOCKS DOWN ACCOUNTS LIKE NEVER BEFORE October Google Advanced Protection Makes it harder than ever for hackers to break into your sensitive data on Gmail, Google Drive, YouTube or any other Google property. Logging in from a desktop will require a special USB key ($20) Accessing your data from a mobile device will similarly require a Bluetooth dongle ($25) The opt-in, ultra-secure mode is intended for truly high-risk users, including those who face the threat of state-sponsored, highly resourced cyberespionage
37
38 Thanks for coming Ron Brown Silvercomctc
39 The Demo
40
41
42
43 Why two-factor authentication is crucial for your Apple ID, and how to use it Access your Account 1. Apple ID 2. Your Password 3. Access to one of your devices Remember your Apple ID password. Use a device passcode on all your devices. Keep your trusted phone number(s) up to date. Keep your Apple devices physically secure.
44 When you sign into a new device for the first time a prompt will appear on your trusted device followed by a temporary code. You don t need to write this code down. Simply type the numbers from your trusted device onto the new device, and you re in. If you do not receive a code for whatever reason, don t worry. Simply hit didn t get code on the sign in screen and then you can text or call your trusted phone number to receive a code. If you re on a web browser, one last prompt may appear asking if you want to trust the new device. By selecting trust you will then no longer need any codes when signing into that browser again. It is important to take note that these verification codes that you are receiving are different from a passcode to get into your devices. This verification code is a one-time code that will not matter anymore after you ve used it.
45
46 LastPass reveals the threats posed by passwords in the workplace nearly everyone (91 percent) knows that it is dangerous to reuse passwords with 81 percent of data breaches attributable to "weak, reused, or stolen passwords more than half (61 percent) do reuse passwords 250-employee company, there are an average of 47,750 passwords in use LastPass found that people have nearly 200 passwords to remember LastPass estimates around 36 minutes a month is wasted typing out login credentials A worrying finding of the report is that many employees are using social media credentials to log into business systems and accounts -- something which is clearly undesirable.
47 Version 5.0 Google Authenticator ( New) The first new feature is experimental support for USB security keys (FIDO U2F) in Chrome. In other words, once you install the update, you should be able to use Yubikeys and similar devices to login to websites through Chrome (as well as Chrome Custom Tabs/WebViews).
48 2 FA
49 Apple s two-step authentication goes away with ios 11 and macos High Sierra Apple s original two-step system relied on its Apple ID site for set up and management, and could only send codes to ios devices and via SMS Its update in September 2015 left two-step in place for those who continued to want to use it, but the 2FA revision was far better. Enrollment happens via ios and macos
50 If you re still using two-step verification, when Apple converts your account to 2FA with ios 11 or High Sierra, here s what you need to know: Your Recovery Key is no longer needed, although you can opt into using it. If you don t opt in to retain a Recovery Key, you rely on Apple s account-recovery process. If you forget or lose your password and all your trusted devices and phone numbers, you can contact Apple, which has an intentionally slow process you have to go through to unlock and reclaim your account by proving your identity. You only use the Apple ID site to manage app-specific passwords for third-party calendar, contacts, and apps. These single-use passwords let you bypass authentication, and became mandatory in June for third-party icloud access. When you log in and Apple s system determines you re not on an already trusted machine or using a trusted browser, you ll get a location popup or dialog on every computer and ios device connected to the same icloud account. First, you click or tap Allow on the location. Then, on that device that you approved the location, you receive a six-digit code that you can enter in the browser, app, or OS component requesting it.
51 Apple continued1 If you can t get the location and code to arrive at an Apple device, Apple offers a backup method that lets you send a text message or have an automated voice system call you with the code. If you re using an OS that was released before Apple s 2FA support in 2015 or an older version of itunes for Windows, you may have to log in to an Apple ID account by using that account s password plus a six-digit verification code added to the password. If you don t receive a 2FA verification code for an older OS login or for a regular 2FA login, you can generate one instead. In ios go to Settings > account name > Password & Security and tap Get Verification Code. In macos, open the icloud system presence pane, and click Account Details, Security, and Get Verification Code.
52 Apple Continued 2 By default, 2FA-upgraded accounts rely on the accountrecovery process described above. But you can also regenerate a Recovery Key, in which case you must keep it safe and secure as a last-ditch way to recover your account.
53 Facebook
54 Yubico launches its smallest YubiKey yet Like all YubiKeys, the 4C Nano offers strong crypto and touch-to-sign and supports the FIDO U2F (Universal 2nd Factor), one-time password (OTP), OpenPGP and PIV smart card standards.
55 How to Set Up Google's Advanced Protection Program Security Keys ( Cost about $20) Biggest Change Login process Login with PW Insert security key Security Key generates code
56 Registering your Key An important note for ios users: You'll have to download an additional app to your device called Google Smart Lock in order to pair your Bluetooth-enabled security key with your Google account.
57
58 Protection On In your account settings, you can also add or revoke security keys and cut access to any Google sign-ons from other devices. Those options will come in handy if a security key is ever lost, or if your laptop gets stolen. There, you can also quit the Advanced Protection Program. Simply turn it off, and you'll revert back to Google's default login process.
59 How to Get Backup Codes Microsoft Visit your Microsoft Account page and hit the Security tab at the top. From there, you can change your password, add alternative addresses and phone numbers for account recovery, and keep an eye on your account s activity. Under those options, you ll find the link for additional security options, where that good good two-factor authentication information is hiding.
60 Apple When enabling two-factor authentication for your Apple ID account, Apple gives you the option of creating a recovery code. You should take the hint and generate a recovery code, both for security purposes and because losing it could lock you out of your Apple ID account for good. Generating a recovery key on your ios or macos device is pretty simple. Here are the instructions, according to Apple: Go to Settings > [your name] > Password & Security. You might need to enter your Apple ID password. Tap Recovery Key. Slide to turn on Recovery Key. Tap Use Recovery Key and enter your device passcode. Write down your recovery key and keep it in a safe place. Confirm your recovery key by entering it on the next screen. You can also get a recovery code using your Mac: Go to System Preferences > icloud > Account Details. You might need to enter your Apple ID password. Click Security. In the Recovery Key section, click Turn On. Click Use Recovery Key. Write down your recovery key and keep it in a safe place. Click Continue. Confirm your recovery key by entering it on the next screen.
61 Google Visit your Google Account page, and click Sign In & Security. In the Signing into Google section, select 2-Step Verification. Sign in again, and prepare to see all the ways you can keep prying eyes away from your Google account. Among the options to configure two-factor authentication via SMS or authenticator app, you ll see Backup Codes. Google presents you with the option to download or print out 10 recovery codes, or generate new ones (which renders your previous recovery codes inert). You can only use each recovery code once, so be sure to cross it out or delete it after you regain access your account. At least you ve got nine more.
62 Print Them Out, Keep Them Safe Also, Store Them Digitally Put Them In a Password Manager
63
2 Factor Authentication. By Ron Brown
 2 Factor Authentication By Ron Brown WHAT WILL THE ATTACKER DO TO YOUR ACCOUNT? Once they access your account they will turn off notifications and change your Password Ransack your InBox for stuff like
2 Factor Authentication By Ron Brown WHAT WILL THE ATTACKER DO TO YOUR ACCOUNT? Once they access your account they will turn off notifications and change your Password Ransack your InBox for stuff like
Multi-Factor Authentication (MFA)
 10.10.18 1 Multi-Factor Authentication (MFA) What is it? Why should I use it? CYBERSECURITY Tech Fair 2018 10.10.18 2 Recent Password Hacks PlayStation Network (2011) 77 Million accounts hacked Adobe (2013)
10.10.18 1 Multi-Factor Authentication (MFA) What is it? Why should I use it? CYBERSECURITY Tech Fair 2018 10.10.18 2 Recent Password Hacks PlayStation Network (2011) 77 Million accounts hacked Adobe (2013)
Take Control of Your Passwords
 Take Control of Your Passwords Joe Kissell Publisher, Take Control Books @joekissell takecontrolbooks.com The Password Problem Passwords are annoying! It s tempting to take the easy way out. There is an
Take Control of Your Passwords Joe Kissell Publisher, Take Control Books @joekissell takecontrolbooks.com The Password Problem Passwords are annoying! It s tempting to take the easy way out. There is an
Authentication Technology for a Smart eid Infrastructure.
 Authentication Technology for a Smart eid Infrastructure. www.aducid.com One app to access all public and private sector online services. One registration allows users to access all their online accounts
Authentication Technology for a Smart eid Infrastructure. www.aducid.com One app to access all public and private sector online services. One registration allows users to access all their online accounts
EXPERIENCE SIMPLER, STRONGER AUTHENTICATION
 1 EXPERIENCE SIMPLER, STRONGER AUTHENTICATION 2 Data Breaches are out of control 3 IN 2014... 708 data breaches 82 million personal records stolen $3.5 million average cost per breach 4 We have a PASSWORD
1 EXPERIENCE SIMPLER, STRONGER AUTHENTICATION 2 Data Breaches are out of control 3 IN 2014... 708 data breaches 82 million personal records stolen $3.5 million average cost per breach 4 We have a PASSWORD
Deprecating the Password: A Progress Report. Dr. Michael B. Jones Identity Standards Architect, Microsoft May 17, 2018
 Deprecating the Password: A Progress Report Dr. Michael B. Jones Identity Standards Architect, Microsoft May 17, 2018 The password problem Alpha-numeric passwords are hard for humans to remember and easy
Deprecating the Password: A Progress Report Dr. Michael B. Jones Identity Standards Architect, Microsoft May 17, 2018 The password problem Alpha-numeric passwords are hard for humans to remember and easy
COMPUTING FUNDAMENTALS I
 FALL 2017 / COMPUTER SCIENCE 105 COMPUTING FUNDAMENTALS I DAY 2 27 SEPTEMBER 2017 COURSE ADMIN COURSE ADMIN NOTECARDS - ATTENDANCE & FEEDBACK Name Student ID One of: What did you learn or find most interesting?
FALL 2017 / COMPUTER SCIENCE 105 COMPUTING FUNDAMENTALS I DAY 2 27 SEPTEMBER 2017 COURSE ADMIN COURSE ADMIN NOTECARDS - ATTENDANCE & FEEDBACK Name Student ID One of: What did you learn or find most interesting?
Stop sweating the password and learn to love public key cryptography. Chris Streeks Solutions Engineer, Yubico
 1 Stop sweating the password and learn to love public key cryptography Chris Streeks Solutions Engineer, Yubico Stop Sweating the Password! 2 Agenda Introduction The modern state of Phishing How to become
1 Stop sweating the password and learn to love public key cryptography Chris Streeks Solutions Engineer, Yubico Stop Sweating the Password! 2 Agenda Introduction The modern state of Phishing How to become
ANDROID PRIVACY & SECURITY GUIDE ANDROID DEVICE SETTINGS
 ANDROID PRIVACY & SECURITY GUIDE WESNET The Women s Services Network Smartphones store a lot of personal information, including email or social media accounts, reminders and notes, the number of steps
ANDROID PRIVACY & SECURITY GUIDE WESNET The Women s Services Network Smartphones store a lot of personal information, including email or social media accounts, reminders and notes, the number of steps
EXPERIENCE SIMPLER, STRONGER AUTHENTICATION
 1 EXPERIENCE SIMPLER, STRONGER AUTHENTICATION 2 Data Breaches are out of control 3 IN 2014... 783 data breaches >1 billion records stolen since 2012 $3.5 million average cost per breach 4 We have a PASSWORD
1 EXPERIENCE SIMPLER, STRONGER AUTHENTICATION 2 Data Breaches are out of control 3 IN 2014... 783 data breaches >1 billion records stolen since 2012 $3.5 million average cost per breach 4 We have a PASSWORD
INTRODUCTION TO CLOUD STORAGE
 INTRODUCTION TO CLOUD STORAGE GETTING STARTED PAGE 02 Class Overview What You Will Learn WHAT IS THE CLOUD? PAGE 03 Basic Vocabulary Advantages of the Cloud Disadvantages of the Cloud CLOUD STORAGE SERVICES
INTRODUCTION TO CLOUD STORAGE GETTING STARTED PAGE 02 Class Overview What You Will Learn WHAT IS THE CLOUD? PAGE 03 Basic Vocabulary Advantages of the Cloud Disadvantages of the Cloud CLOUD STORAGE SERVICES
Cybersecurity in 2016 and Lessons learned
 Cybersecurity in 2016 and Lessons learned Dr. Yu Cai Associate Professor Program Chair, Computer Network & System Administration School of Technology Michigan Technological University cai@mtu.edu A Quick
Cybersecurity in 2016 and Lessons learned Dr. Yu Cai Associate Professor Program Chair, Computer Network & System Administration School of Technology Michigan Technological University cai@mtu.edu A Quick
FACEBOOK SAFETY FOR JOURNALISTS. Thanks to these partners for reviewing these safety guidelines:
 FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
YubiKey Mac Operating System Login Guide
 YubiKey Mac Operating System Login Guide Using Yubico Pluggable Authentication Module (PAM) with Challenge-Response YubiKey Mac Login Guide 2017 Yubico. All rights reserved. Page 1 of 19 Copyright 2017
YubiKey Mac Operating System Login Guide Using Yubico Pluggable Authentication Module (PAM) with Challenge-Response YubiKey Mac Login Guide 2017 Yubico. All rights reserved. Page 1 of 19 Copyright 2017
Instructions I Lost My Iphone 4 Password Yahoo
 Instructions I Lost My Iphone 4 Password Yahoo Linux software Android Apps Blackberry Apps iphone Apps Windows Phone Apps Report Niash- Mar 4, 2014 02:48PM I have faced a problem. i forgot my yahoo id
Instructions I Lost My Iphone 4 Password Yahoo Linux software Android Apps Blackberry Apps iphone Apps Windows Phone Apps Report Niash- Mar 4, 2014 02:48PM I have faced a problem. i forgot my yahoo id
Password & Tutorials Packet
 & Tutorials Packet Print, staple, and use this & Tutorials Packet Sign up for Secure Backup Service: visit rowleyservices.com for a free trial & setup info Follow attached: Check iphone Camera Settings
& Tutorials Packet Print, staple, and use this & Tutorials Packet Sign up for Secure Backup Service: visit rowleyservices.com for a free trial & setup info Follow attached: Check iphone Camera Settings
The Lord of the Keys How two-part seed records solve all safety concerns regarding two-factor authentication
 White Paper The Lord of the Keys How two-part seed records solve all safety concerns regarding two-factor authentication Table of contents Introduction... 2 Password protection alone is no longer enough...
White Paper The Lord of the Keys How two-part seed records solve all safety concerns regarding two-factor authentication Table of contents Introduction... 2 Password protection alone is no longer enough...
Keeping Important Data Safe and Secure Online. Norm Kaufman
 Keeping Important Data Safe and Secure Online Norm Kaufman Examples of Important Data Passwords and Secret Answers Personal Documents (Licenses, Passports, Insurance Cards, Credit Cards) Social Security
Keeping Important Data Safe and Secure Online Norm Kaufman Examples of Important Data Passwords and Secret Answers Personal Documents (Licenses, Passports, Insurance Cards, Credit Cards) Social Security
Your . A setup guide. Last updated March 7, Kingsford Avenue, Glasgow G44 3EU
 fuzzylime WE KNOW DESIGN WEB DESIGN AND CONTENT MANAGEMENT 19 Kingsford Avenue, Glasgow G44 3EU 0141 416 1040 hello@fuzzylime.co.uk www.fuzzylime.co.uk Your email A setup guide Last updated March 7, 2017
fuzzylime WE KNOW DESIGN WEB DESIGN AND CONTENT MANAGEMENT 19 Kingsford Avenue, Glasgow G44 3EU 0141 416 1040 hello@fuzzylime.co.uk www.fuzzylime.co.uk Your email A setup guide Last updated March 7, 2017
User Help
 ginlo @work User Help 19 June 2018 Contents Get started... 5 System requirements for the ginlo @work app... 5 Recommended browsers for ginlo websites... 6 Supported languages... 6 Navigation in ginlo @work...
ginlo @work User Help 19 June 2018 Contents Get started... 5 System requirements for the ginlo @work app... 5 Recommended browsers for ginlo websites... 6 Supported languages... 6 Navigation in ginlo @work...
1Password for Mac. by Marcia Bolsinga for AshMUG 1/12/2019
 Why do we need passwords? First of all - why passwords? Passwords are one of the Primary Pain Points in our modern digital existence. Despite all the advances of our modern technology, we haven t managed
Why do we need passwords? First of all - why passwords? Passwords are one of the Primary Pain Points in our modern digital existence. Despite all the advances of our modern technology, we haven t managed
If your Mac keeps asking for the login keychain password
 If your Mac keeps asking for the login keychain password The password of your macos user account might not match the password of your login keychain. Either create a new login keychain or update it with
If your Mac keeps asking for the login keychain password The password of your macos user account might not match the password of your login keychain. Either create a new login keychain or update it with
How to Build a Culture of Security
 How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
Protect Yourself Against VPN-Based Attacks: Five Do s and Don ts
 White Paper Protect Yourself Against VPN-Based Attacks: Five Do s and Don ts Don t let stolen VPN credentials jeopardize your security March 2015 A TECHTARGET WHITE PAPER Most IT professionals take for
White Paper Protect Yourself Against VPN-Based Attacks: Five Do s and Don ts Don t let stolen VPN credentials jeopardize your security March 2015 A TECHTARGET WHITE PAPER Most IT professionals take for
Authentication Methods
 CERT-EU Security Whitepaper 16-003 Authentication Methods D.Antoniou, K.Socha ver. 1.0 20/12/2016 TLP: WHITE 1 Authentication Lately, protecting data has become increasingly difficult task. Cyber-attacks
CERT-EU Security Whitepaper 16-003 Authentication Methods D.Antoniou, K.Socha ver. 1.0 20/12/2016 TLP: WHITE 1 Authentication Lately, protecting data has become increasingly difficult task. Cyber-attacks
IT & DATA SECURITY BREACH PREVENTION
 IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
Would you bet your business on the strength of every employee s password?
 Would you bet your business on the strength of every employee s password? Table of Contents You re only one weak password away from a breach... 3 Think your passwords are strong? That won t stop hackers...
Would you bet your business on the strength of every employee s password? Table of Contents You re only one weak password away from a breach... 3 Think your passwords are strong? That won t stop hackers...
Managing IT Risk: What Now and What to Look For. Presented By Tina Bode IT Assurance Services
 Managing IT Risk: What Now and What to Look For Presented By Tina Bode IT Assurance Services Agenda 1 2 WHAT TOP TEN IT SECURITY RISKS YOU CAN DO 3 QUESTIONS 2 IT S ALL CONNECTED Introduction All of our
Managing IT Risk: What Now and What to Look For Presented By Tina Bode IT Assurance Services Agenda 1 2 WHAT TOP TEN IT SECURITY RISKS YOU CAN DO 3 QUESTIONS 2 IT S ALL CONNECTED Introduction All of our
Enterprise Mobile Management (EMM) Policies
 Enterprise Mobile Management (EMM) Policies Best Practices Guide Copyright 2016 Fiberlink, an IBM Company. All rights reserved. Information in this document is subject to change without notice. The software
Enterprise Mobile Management (EMM) Policies Best Practices Guide Copyright 2016 Fiberlink, an IBM Company. All rights reserved. Information in this document is subject to change without notice. The software
Help Desk Guide. Originally released June 22, 2016 Revised July 24, 2017
 Help Desk Guide Originally released June 22, 2016 Revised July 24, 2017 Table of Contents Commonly-used terms Part 1: Overview Why do I need this guide? Part 2: Enrollment and activation What will the
Help Desk Guide Originally released June 22, 2016 Revised July 24, 2017 Table of Contents Commonly-used terms Part 1: Overview Why do I need this guide? Part 2: Enrollment and activation What will the
Lecture 14 Passwords and Authentication
 Lecture 14 Passwords and Authentication Stephen Checkoway University of Illinois at Chicago CS 487 Fall 2017 Slides based on Bailey s ECE 422 Major Portions Courtesy Ryan Cunningham AUTHENTICATION Authentication
Lecture 14 Passwords and Authentication Stephen Checkoway University of Illinois at Chicago CS 487 Fall 2017 Slides based on Bailey s ECE 422 Major Portions Courtesy Ryan Cunningham AUTHENTICATION Authentication
SurePassID ServicePass User Guide. SurePassID Authentication Server 2017
 SurePassID ServicePass User Guide SurePassID Authentication Server 2017 Introduction This technical guide shows how users can manage their SurePassID security tokens that are compatible with SurePassID
SurePassID ServicePass User Guide SurePassID Authentication Server 2017 Introduction This technical guide shows how users can manage their SurePassID security tokens that are compatible with SurePassID
ios 12: Change these privacy and security settings now
 ios 12: Change these privacy and security settings now Published: October 4, 2018 -- 19:05 GMT (12:05 PDT) Caption by: Adrian Kingsley-Hughes - ZDNet Introduction Installed ios 12 or bought a new iphone
ios 12: Change these privacy and security settings now Published: October 4, 2018 -- 19:05 GMT (12:05 PDT) Caption by: Adrian Kingsley-Hughes - ZDNet Introduction Installed ios 12 or bought a new iphone
Password & Tutorials Packet
 & Tutorials Packet Print, staple, and use this & Tutorials Packet Sign up for Secure Backup Service: visit rowleyservices.com for a free trial & setup info Follow attached: Check iphone Camera Settings
& Tutorials Packet Print, staple, and use this & Tutorials Packet Sign up for Secure Backup Service: visit rowleyservices.com for a free trial & setup info Follow attached: Check iphone Camera Settings
2 User Guide. Contents
 E-mail User Guide 2 E-mail User Guide Contents Logging in to your web mail... 3 Changing your password... 5 Editing your signature... 6 Adding an e-mail account to Outlook 2010/2013/2016... 7 Adding an
E-mail User Guide 2 E-mail User Guide Contents Logging in to your web mail... 3 Changing your password... 5 Editing your signature... 6 Adding an e-mail account to Outlook 2010/2013/2016... 7 Adding an
Duo Travel Guide. duo.com
 Duo Travel Guide duo.com Overview As a member of an organization protected by Duo, you already have secure access to applications and assets. This guide is designed to help you maintain that trusted access
Duo Travel Guide duo.com Overview As a member of an organization protected by Duo, you already have secure access to applications and assets. This guide is designed to help you maintain that trusted access
Six steps to control the uncontrollable
 Six steps to control the uncontrollable Learn how to use Microsoft Enterprise Mobility Suite to protect cloud apps, manage devices, and guard against advanced threats today Introduction Employees today
Six steps to control the uncontrollable Learn how to use Microsoft Enterprise Mobility Suite to protect cloud apps, manage devices, and guard against advanced threats today Introduction Employees today
Welcome. Password Management & Public Wi-Fi Security. Hosted by: Content by:
 Welcome Password Management & Public Wi-Fi Security Hosted by: Content by: Presenter: Ray Cool, CEO PBSI Technology Solutions Webinar will begin at 1:00 Welcome Foster & Motley Clients to Security Education
Welcome Password Management & Public Wi-Fi Security Hosted by: Content by: Presenter: Ray Cool, CEO PBSI Technology Solutions Webinar will begin at 1:00 Welcome Foster & Motley Clients to Security Education
Enroll in Two factor Authentication - iphone
 OVERVIEW Passwords are increasingly easy to compromise. They can often be stolen, guessed, or hacked you might not even know someone is accessing your account. Two factor authentication adds a second layer
OVERVIEW Passwords are increasingly easy to compromise. They can often be stolen, guessed, or hacked you might not even know someone is accessing your account. Two factor authentication adds a second layer
Integrated Access Management Solutions. Access Televentures
 Integrated Access Management Solutions Access Televentures Table of Contents OVERCOMING THE AUTHENTICATION CHALLENGE... 2 1 EXECUTIVE SUMMARY... 2 2 Challenges to Providing Users Secure Access... 2 2.1
Integrated Access Management Solutions Access Televentures Table of Contents OVERCOMING THE AUTHENTICATION CHALLENGE... 2 1 EXECUTIVE SUMMARY... 2 2 Challenges to Providing Users Secure Access... 2 2.1
What is Authentication? All requests for resources have to be monitored. Every request must be authenticated and authorized to use the resource.
 P1L4 Authentication What is Authentication? All requests for resources have to be monitored. Every request must be authenticated and authorized to use the resource. Authentication: Who are you? Prove it.
P1L4 Authentication What is Authentication? All requests for resources have to be monitored. Every request must be authenticated and authorized to use the resource. Authentication: Who are you? Prove it.
Account Takeover: Why Payment Fraud Protection is Not Enough
 Cybercrime Protection Account Takeover: Why Payment Fraud Protection is Not Enough Mustafa Rassiwala, ThreatMetrix, Inc. April 2014 1 Agenda 1. Customer Accounts Blessing or Curse? 2. Passwords Weakest
Cybercrime Protection Account Takeover: Why Payment Fraud Protection is Not Enough Mustafa Rassiwala, ThreatMetrix, Inc. April 2014 1 Agenda 1. Customer Accounts Blessing or Curse? 2. Passwords Weakest
Rethinking Authentication. Steven M. Bellovin
 Rethinking Authentication Steven M. https://www.cs.columbia.edu/~smb Why? I don t think we understand the real security issues with authentication Our defenses are ad hoc I regard this as a step towards
Rethinking Authentication Steven M. https://www.cs.columbia.edu/~smb Why? I don t think we understand the real security issues with authentication Our defenses are ad hoc I regard this as a step towards
The purpose of this document is to help you to get started with your ipad to access Lilly resources such as , calendar, Lilly apps and more.
 The purpose of this document is to help you to get started with your ipad to access Lilly resources such as email, calendar, Lilly apps and more. The setup process will take about 30 minutes to complete
The purpose of this document is to help you to get started with your ipad to access Lilly resources such as email, calendar, Lilly apps and more. The setup process will take about 30 minutes to complete
Online Services USER GUIDE. First Time Log In
 Online Services USER GUIDE Welcome to online banking! Whether you re online or using a mobile device, access your accounts whenever and wherever it s convenient for you. First Time Log In Log In: BankMidwest.com
Online Services USER GUIDE Welcome to online banking! Whether you re online or using a mobile device, access your accounts whenever and wherever it s convenient for you. First Time Log In Log In: BankMidwest.com
SECURITY ON PUBLIC WI-FI New Zealand. A guide to help you stay safe online while using public Wi-Fi
 SECURITY ON PUBLIC WI-FI New Zealand A guide to help you stay safe online while using public Wi-Fi WHAT S YOUR WI-FI PASSWORD? Enter password for the COFFEE_TIME Wi-Fi network An all too common question
SECURITY ON PUBLIC WI-FI New Zealand A guide to help you stay safe online while using public Wi-Fi WHAT S YOUR WI-FI PASSWORD? Enter password for the COFFEE_TIME Wi-Fi network An all too common question
Restech. User Security AVOIDING LOSS GAINING CONFIDENCE IN THE FACE OF TODAY S THREATS
 Restech User Security AVOIDING LOSS GAINING CONFIDENCE IN THE FACE OF TODAY S THREATS Your presenter: Vince Gremillion, CISSP 30+ years technical and customer service experience Founder/Co-Owner RESTECH
Restech User Security AVOIDING LOSS GAINING CONFIDENCE IN THE FACE OF TODAY S THREATS Your presenter: Vince Gremillion, CISSP 30+ years technical and customer service experience Founder/Co-Owner RESTECH
Modern two-factor authentication: Easy. Affordable. Secure.
 Modern two-factor authentication: Easy. Affordable. Secure. www.duosecurity.com Your systems and users are under attack like never before The last few years have seen an unprecedented number of attacks
Modern two-factor authentication: Easy. Affordable. Secure. www.duosecurity.com Your systems and users are under attack like never before The last few years have seen an unprecedented number of attacks
Computer Security 4/12/19
 Authentication Computer Security 09. Authentication Identification: who are you? Authentication: prove it Authorization: you can do it Paul Krzyzanowski Protocols such as Kerberos combine all three Rutgers
Authentication Computer Security 09. Authentication Identification: who are you? Authentication: prove it Authorization: you can do it Paul Krzyzanowski Protocols such as Kerberos combine all three Rutgers
Welcome to United Bank - Mobile Banking!
 Questions Welcome to United Bank - Mobile Banking! General Questions How much does this service cost? Is it secure? Which wireless carriers are supported? Do I need a text message or data plan? I'm not
Questions Welcome to United Bank - Mobile Banking! General Questions How much does this service cost? Is it secure? Which wireless carriers are supported? Do I need a text message or data plan? I'm not
How. Biometrics. Expand the Reach of Mobile Banking ENTER
 How Biometrics Expand the Reach of Mobile Banking ENTER Table of Contents 01 The Mobile Banking Opportunity 02 What s Suppressing Mobile Adoption? 03 Onboarding Challenges: Proving One s Identity 04 Authentication
How Biometrics Expand the Reach of Mobile Banking ENTER Table of Contents 01 The Mobile Banking Opportunity 02 What s Suppressing Mobile Adoption? 03 Onboarding Challenges: Proving One s Identity 04 Authentication
Mobile Banking App Guide (ios and Android Apps) Mobile Banking App Guide (ios and Android)
 Mobile Banking App Guide (ios and Android) Page 1 A safe and efficient way of accessing your People s Choice Credit Union accounts, paying bills Contents. 1. Mobile Banking using the People s Choice iphone
Mobile Banking App Guide (ios and Android) Page 1 A safe and efficient way of accessing your People s Choice Credit Union accounts, paying bills Contents. 1. Mobile Banking using the People s Choice iphone
MFA Pilot Instructions
 MFA Pilot Instructions Getting Started You will need the following: Your smartphone, a computer, and Internet access. Before using MFA your computer will need to be running Office 2016. If you are still
MFA Pilot Instructions Getting Started You will need the following: Your smartphone, a computer, and Internet access. Before using MFA your computer will need to be running Office 2016. If you are still
Multi-Factor Authentication User Setup Guide
 Multi-Factor Authentication User Setup Guide This document is designed to provide assistance and guidance to someone setting up Multi-Factor Authentication in Office 365. Multi-factor, or 2 factor, authentication
Multi-Factor Authentication User Setup Guide This document is designed to provide assistance and guidance to someone setting up Multi-Factor Authentication in Office 365. Multi-factor, or 2 factor, authentication
SECURITY STORY WE NEVER SEE, TOUCH NOR HOLD YOUR DATA
 SECURITY STORY WE NEVER SEE, TOUCH NOR HOLD YOUR DATA CTO Office www.digi.me another Engineering Briefing digi.me keeping your data secure at all times ALL YOUR DATA IN ONE PLACE TO SHARE WITH PEOPLE WHO
SECURITY STORY WE NEVER SEE, TOUCH NOR HOLD YOUR DATA CTO Office www.digi.me another Engineering Briefing digi.me keeping your data secure at all times ALL YOUR DATA IN ONE PLACE TO SHARE WITH PEOPLE WHO
Manual Sync Contacts On My Iphone To Gmail Account Without Itunes
 Manual Sync Contacts On My Iphone To Gmail Account Without Itunes You can keep contacts from your Google account up to date on your ios device. Apple Store Mac iphone Watch ipad ipod itunes Support not
Manual Sync Contacts On My Iphone To Gmail Account Without Itunes You can keep contacts from your Google account up to date on your ios device. Apple Store Mac iphone Watch ipad ipod itunes Support not
The University of Toledo Intune End-User Enrollment Guide:
 The University of Toledo Intune End-User Enrollment Guide: Contents Enroll your Android device in Intune... 2 Enroll your ios device in Intune... 15 Enroll your Mac OS X device in Intune... 25 Enroll your
The University of Toledo Intune End-User Enrollment Guide: Contents Enroll your Android device in Intune... 2 Enroll your ios device in Intune... 15 Enroll your Mac OS X device in Intune... 25 Enroll your
Personal Internet Security Basics. Dan Ficker Twin Cities DrupalCamp 2018
 Personal Internet Security Basics Dan Ficker Twin Cities DrupalCamp 2018 Overview Security is an aspiration, not a state. Encryption is your friend. Passwords are very important. Make a back-up plan. About
Personal Internet Security Basics Dan Ficker Twin Cities DrupalCamp 2018 Overview Security is an aspiration, not a state. Encryption is your friend. Passwords are very important. Make a back-up plan. About
Instructions 1 Elevation of Privilege Instructions
 Instructions 1 Elevation of Privilege Instructions Draw a diagram of the system you want to threat model before you deal the cards. Deal the deck to 3-6 players. Play starts with the 3 of Tampering. Play
Instructions 1 Elevation of Privilege Instructions Draw a diagram of the system you want to threat model before you deal the cards. Deal the deck to 3-6 players. Play starts with the 3 of Tampering. Play
CS 161 Computer Security
 Popa & Weaver Fall 2016 CS 161 Computer Security 10/4 Passwords 1 Passwords are widely used for authentication, especially on the web. What practices should be used to make passwords as secure as possible?
Popa & Weaver Fall 2016 CS 161 Computer Security 10/4 Passwords 1 Passwords are widely used for authentication, especially on the web. What practices should be used to make passwords as secure as possible?
Password & Tutorials Packet
 & Tutorials Packet Print, staple, and use this & Tutorials Packet Sign up for Secure Backup Service: visit rowleyservices.com for a free trial & setup info Follow attached: iphone users that use a Windows
& Tutorials Packet Print, staple, and use this & Tutorials Packet Sign up for Secure Backup Service: visit rowleyservices.com for a free trial & setup info Follow attached: iphone users that use a Windows
Consumer Banking User Guide. Getting Started
 Consumer Banking User Guide Getting Started Contents About the platform... 3 Installing the mobile banking app... 4 Opening mobile banking... 4 Accessing the online banking site... 4 Browser requirements...
Consumer Banking User Guide Getting Started Contents About the platform... 3 Installing the mobile banking app... 4 Opening mobile banking... 4 Accessing the online banking site... 4 Browser requirements...
Cyber Security Guide. For Politicians and Political Parties
 Cyber Security Guide For Politicians and Political Parties Indian Election Integrity Initiative Design by ccm.design Cover Image by Paul Dufour Helping to Safeguard the Integrity of the Electoral Process
Cyber Security Guide For Politicians and Political Parties Indian Election Integrity Initiative Design by ccm.design Cover Image by Paul Dufour Helping to Safeguard the Integrity of the Electoral Process
Texas Division How to Login and Register for My IT Support and ServiceNow
 Texas Division How to Login and Register for My IT Support and ServiceNow Go to texas.mychiitsuppport.org. You'll see the screen below. My IT Support/ServiceNow is a national system and utilizes national
Texas Division How to Login and Register for My IT Support and ServiceNow Go to texas.mychiitsuppport.org. You'll see the screen below. My IT Support/ServiceNow is a national system and utilizes national
DER GOBBLE. Good Secure Crypto Wallet Practices. What is your wallet?
 DER GOBBLE Good Secure Crypto Wallet Practices When it comes to crypto currencies and securing your money, the absolute best 99% guaranteed security for your wallets is YOU. You are the one that will expose
DER GOBBLE Good Secure Crypto Wallet Practices When it comes to crypto currencies and securing your money, the absolute best 99% guaranteed security for your wallets is YOU. You are the one that will expose
DATA DISASTER AVERTED! HOW TO BACK UP YOUR ANDROID SMARTPHONE
 DATA DISASTER AVERTED! HOW TO BACK UP YOUR ANDROID SMARTPHONE Planning ahead is the easiest way to make sure your data isn t lost to the ether, even if your phone is destroyed. Luckily, Google automatically
DATA DISASTER AVERTED! HOW TO BACK UP YOUR ANDROID SMARTPHONE Planning ahead is the easiest way to make sure your data isn t lost to the ether, even if your phone is destroyed. Luckily, Google automatically
CNT4406/5412 Network Security
 CNT4406/5412 Network Security Authentication Zhi Wang Florida State University Fall 2014 Zhi Wang (FSU) CNT4406/5412 Network Security Fall 2014 1 / 43 Introduction Introduction Authentication is the process
CNT4406/5412 Network Security Authentication Zhi Wang Florida State University Fall 2014 Zhi Wang (FSU) CNT4406/5412 Network Security Fall 2014 1 / 43 Introduction Introduction Authentication is the process
Streamline IT with Secure Remote Connection and Password Management
 Streamline IT with Secure Remote Connection and Password Management Table of Contents Introduction Identifying IT pain points Selecting a secure remote connection and password management solution Turning
Streamline IT with Secure Remote Connection and Password Management Table of Contents Introduction Identifying IT pain points Selecting a secure remote connection and password management solution Turning
Google 2 factor authentication User Guide
 Google 2 factor authentication User Guide Description: Updated Date: This guide describes how to setup Two factor authentication for your Google account. March, 2018 Summary ITSC is pleased to launch Two
Google 2 factor authentication User Guide Description: Updated Date: This guide describes how to setup Two factor authentication for your Google account. March, 2018 Summary ITSC is pleased to launch Two
Remote Deposit Capture Member User Guide. RDC Brought to you by Sprig
 Remote Deposit Capture Member User Guide RDC Brought to you by Sprig This document will provide you the basic understanding of how to access the Sprig app, add accounts to your virtual wallet and utilize
Remote Deposit Capture Member User Guide RDC Brought to you by Sprig This document will provide you the basic understanding of how to access the Sprig app, add accounts to your virtual wallet and utilize
Attacking Your Two-Factor Authentication (PS: Use Two-Factor Authentication)
 Attacking Your Two-Factor Authentication (PS: Use Two-Factor Authentication) 08 Jun 2017 K-LUG Technical Meeting Rochester, MN Presented by: Vi Grey Independent Security Researcher https://vigrey.com Who
Attacking Your Two-Factor Authentication (PS: Use Two-Factor Authentication) 08 Jun 2017 K-LUG Technical Meeting Rochester, MN Presented by: Vi Grey Independent Security Researcher https://vigrey.com Who
FRONT USER GUIDE Getting Started with Front
 USER GUIDE USER GUIDE Getting Started with Front ESSENTIALS Teams That Use Front How To Roll Out Front Quick Start Productivity Tips Downloading Front Adding Your Team Inbox Add Your Own Work Email Update
USER GUIDE USER GUIDE Getting Started with Front ESSENTIALS Teams That Use Front How To Roll Out Front Quick Start Productivity Tips Downloading Front Adding Your Team Inbox Add Your Own Work Email Update
2-STEP AUTHENTICATION SETUP For Office 365
 2-STEP AUTHENTICATION SETUP For Office 365 Table of Contents 2-Step Authentication Introduction... 3 Section 1: Setup Process to Receive a Text on your Mobile Phone... 4 Section 1 Step 1... 4 Section 1
2-STEP AUTHENTICATION SETUP For Office 365 Table of Contents 2-Step Authentication Introduction... 3 Section 1: Setup Process to Receive a Text on your Mobile Phone... 4 Section 1 Step 1... 4 Section 1
BANKVIC APP FREQUENTLY ASKED QUESTIONS
 BANKVIC APP FREQUENTLY ASKED QUESTIONS TABLE OF CONTENTS TABLE OF CONTENTS... 1 ABOUT THE BANKVIC APP... 2 GETTING STARTED... 3 SECURITY... 4 FEATURES & FUNCTIONALITY... 5 PAYMENTS & TRANSFERS... 6 CARD
BANKVIC APP FREQUENTLY ASKED QUESTIONS TABLE OF CONTENTS TABLE OF CONTENTS... 1 ABOUT THE BANKVIC APP... 2 GETTING STARTED... 3 SECURITY... 4 FEATURES & FUNCTIONALITY... 5 PAYMENTS & TRANSFERS... 6 CARD
Instructions Hack Ipod Touch Password Without Losing Data
 Instructions Hack Ipod Touch Password Without Losing Data Apple has just released ios 8.4 for iphone, ipad and ipod touch, along with Apple with normal data, secure information like passwords etc. are
Instructions Hack Ipod Touch Password Without Losing Data Apple has just released ios 8.4 for iphone, ipad and ipod touch, along with Apple with normal data, secure information like passwords etc. are
Securing today s identity and transaction systems:! What you need to know! about two-factor authentication!
 Securing today s identity and transaction systems:! What you need to know! about two-factor authentication! 1 Today s Speakers! Alex Doll! CEO OneID Jim Fenton! Chief Security Officer OneID 2 Contents!
Securing today s identity and transaction systems:! What you need to know! about two-factor authentication! 1 Today s Speakers! Alex Doll! CEO OneID Jim Fenton! Chief Security Officer OneID 2 Contents!
Online Services User Guide
 Online Services User Guide Welcome to Online & Mobile Banking! Whether you re online or using a mobile device, manage your money whenever and wherever it s convenient for you. Access Visit BankMidwest.com
Online Services User Guide Welcome to Online & Mobile Banking! Whether you re online or using a mobile device, manage your money whenever and wherever it s convenient for you. Access Visit BankMidwest.com
Integrating Password Management with Enterprise Single Sign-On
 Integrating Password Management with Enterprise Single Sign-On 2016 Hitachi ID Systems, Inc. All rights reserved. Contents 1 Introduction 1 2 Background: one problem, two solutions 2 2.1 The Problem.............................................
Integrating Password Management with Enterprise Single Sign-On 2016 Hitachi ID Systems, Inc. All rights reserved. Contents 1 Introduction 1 2 Background: one problem, two solutions 2 2.1 The Problem.............................................
CHI Easy Access: Register From on the CHI Network
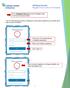 CHI Easy Access: Register From on the CHI Network Go to chieasyaccess.org and click "Register Now." You'll see the screen below. Your CHI Easy Access account is configured to use the same password you
CHI Easy Access: Register From on the CHI Network Go to chieasyaccess.org and click "Register Now." You'll see the screen below. Your CHI Easy Access account is configured to use the same password you
Frequently Asked Questions
 Frequently Asked Questions Contents Getting Started 3 Backup & Sync 7 Using NeatCloud on the Web 9 Using NeatMobile 9 Using NeatVerify 10 Adding files to my NeatCloud 10 Searching my NeatCloud files and
Frequently Asked Questions Contents Getting Started 3 Backup & Sync 7 Using NeatCloud on the Web 9 Using NeatMobile 9 Using NeatVerify 10 Adding files to my NeatCloud 10 Searching my NeatCloud files and
The security challenge in a mobile world
 The security challenge in a mobile world Contents Executive summary 2 Executive summary 3 Controlling devices and data from the cloud 4 Managing mobile devices - Overview - How it works with MDM - Scenario
The security challenge in a mobile world Contents Executive summary 2 Executive summary 3 Controlling devices and data from the cloud 4 Managing mobile devices - Overview - How it works with MDM - Scenario
Unlocking Office 365 without a password. How to Secure Access to Your Business Information in the Cloud without needing to remember another password.
 Unlocking Office 365 without a password How to Secure Access to Your Business Information in the Cloud without needing to remember another password. Introduction It is highly likely that if you have downloaded
Unlocking Office 365 without a password How to Secure Access to Your Business Information in the Cloud without needing to remember another password. Introduction It is highly likely that if you have downloaded
Progressive Authentication in ios
 Progressive Authentication in ios Genghis Chau, Denis Plotnikov, Edwin Zhang December 12 th, 2014 1 Overview In today s increasingly mobile-centric world, more people are beginning to use their smartphones
Progressive Authentication in ios Genghis Chau, Denis Plotnikov, Edwin Zhang December 12 th, 2014 1 Overview In today s increasingly mobile-centric world, more people are beginning to use their smartphones
WHAT IS GOOGLE+ AND WHY SHOULD I USE IT?
 CHAPTER ONE WHAT IS GOOGLE+ AND WHY SHOULD I USE IT? In this chapter: + Discovering Why Google+ Is So Great + What Is the Difference between Google+ and Other Social Networks? + Does It Cost Money to Use
CHAPTER ONE WHAT IS GOOGLE+ AND WHY SHOULD I USE IT? In this chapter: + Discovering Why Google+ Is So Great + What Is the Difference between Google+ and Other Social Networks? + Does It Cost Money to Use
IPHONE DEP REGISTRATION... 4 IPHONE DEP REGISTRATION... 3
 The purpose of this document is to help you to get started with your iphone facilitating DEP (Device Enrollment Program) Registration process to access Lilly resources such as email, calendar, Lilly apps
The purpose of this document is to help you to get started with your iphone facilitating DEP (Device Enrollment Program) Registration process to access Lilly resources such as email, calendar, Lilly apps
Yubico with Centrify for Mac - Deployment Guide
 CENTRIFY DEPLOYMENT GUIDE Yubico with Centrify for Mac - Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as a critical component
CENTRIFY DEPLOYMENT GUIDE Yubico with Centrify for Mac - Deployment Guide Abstract Centrify provides mobile device management and single sign-on services that you can trust and count on as a critical component
VBankWorks Frequently Asked Questions
 VBankWorks Frequently Asked Questions Please read these frequently asked questions for more details about this upgrade and what you can expect. Multifactor Authentication (MFA)/Enhanced Login Security
VBankWorks Frequently Asked Questions Please read these frequently asked questions for more details about this upgrade and what you can expect. Multifactor Authentication (MFA)/Enhanced Login Security
Quick recap on ing Security Recap on where to find things on Belvidere website & a look at the Belvidere Facebook page
 Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
Workshop #7 Email Security Previous workshops 1. Introduction 2. Smart phones & Tablets 3. All about WatsApp 4. More on WatsApp 5. Surfing the Internet 6. Emailing Quick recap on Emailing Email Security
Mobile App User Guide
 Download the Mobile App iphone and ipad To find our Freedom Credit Union Mobile App just scan the appropriate QR code to the right with your Apple device: iphone Download Or you can find it through the
Download the Mobile App iphone and ipad To find our Freedom Credit Union Mobile App just scan the appropriate QR code to the right with your Apple device: iphone Download Or you can find it through the
How NOT To Get Hacked
 How NOT To Get Hacked The right things to do so the bad guys can t do the wrong ones Mark Burnette Partner, LBMC -Risk Services October 25, 2016 Today s Agenda Protecting Against A Hack How should I start?
How NOT To Get Hacked The right things to do so the bad guys can t do the wrong ones Mark Burnette Partner, LBMC -Risk Services October 25, 2016 Today s Agenda Protecting Against A Hack How should I start?
10 Quick Tips to Mobile Security
 10 Quick Tips to Mobile Security 10 Quick Tips to Mobile Security contents 03 Introduction 05 Mobile Threats and Consequences 06 Important Mobile Statistics 07 Top 10 Mobile Safety Tips 19 Resources 22
10 Quick Tips to Mobile Security 10 Quick Tips to Mobile Security contents 03 Introduction 05 Mobile Threats and Consequences 06 Important Mobile Statistics 07 Top 10 Mobile Safety Tips 19 Resources 22
Multi-factor Authentication Instructions
 What is MFA? Multi-factor Authentication (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account.
What is MFA? Multi-factor Authentication (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account.
Who What Why
 Who What Why Board Members Sponsors Associates To Change Authentication Online by: (a) Developing unencumbered Specifications that define interoperable mechanisms that supplant reliance on passwords (b)
Who What Why Board Members Sponsors Associates To Change Authentication Online by: (a) Developing unencumbered Specifications that define interoperable mechanisms that supplant reliance on passwords (b)
Authentication KAMI VANIEA 1
 Authentication KAMI VANIEA FEBRUARY 1ST KAMI VANIEA 1 First, the news KAMI VANIEA 2 Today Basics of authentication Something you know passwords Something you have Something you are KAMI VANIEA 3 Most recommended
Authentication KAMI VANIEA FEBRUARY 1ST KAMI VANIEA 1 First, the news KAMI VANIEA 2 Today Basics of authentication Something you know passwords Something you have Something you are KAMI VANIEA 3 Most recommended
HBU Self Service Password Reset
 HBU Self Service Password Reset Houston Baptist University implemented self-service password reset in July 2014 to give end users/students a way to manage their own password resetting without relying upon
HBU Self Service Password Reset Houston Baptist University implemented self-service password reset in July 2014 to give end users/students a way to manage their own password resetting without relying upon
10 Hidden IT Risks That Might Threaten Your Business
 (Plus 1 Fast Way to Find Them) Your business depends on intelligence. But can you count on your technology? You may not be in the intelligence technology business, but it s probably impossible to imagine
(Plus 1 Fast Way to Find Them) Your business depends on intelligence. But can you count on your technology? You may not be in the intelligence technology business, but it s probably impossible to imagine
Maria Hishikawa MSIX Technical Lead Sarah Storms MSIX Contractor Security
 Migrant Student Information Exchange (MSIX) Security, Privacy and Account Management Webinar Deloitte Consulting LLP. February 22, 2018 Maria Hishikawa MSIX Technical Lead Sarah Storms MSIX Contractor
Migrant Student Information Exchange (MSIX) Security, Privacy and Account Management Webinar Deloitte Consulting LLP. February 22, 2018 Maria Hishikawa MSIX Technical Lead Sarah Storms MSIX Contractor
Best Practices Guide to Electronic Banking
 Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Common iphone problems, tips and tricks
 Common iphone problems, tips and tricks F. M. Spowart Upd April 2018 Page 2 of 9 Randomly losing contacts; iphone does this for some strange reason. The reason why numbers disappear unlike other phones,
Common iphone problems, tips and tricks F. M. Spowart Upd April 2018 Page 2 of 9 Randomly losing contacts; iphone does this for some strange reason. The reason why numbers disappear unlike other phones,
Welcome to Windows 10. Love it or Avoid it
 1 Welcome to Windows 10 Love it or Avoid it 2 What is an OPERATING SYSTEM??? 1) It s a set of programs that control the computer and make the components work together 2) It provides a interface between
1 Welcome to Windows 10 Love it or Avoid it 2 What is an OPERATING SYSTEM??? 1) It s a set of programs that control the computer and make the components work together 2) It provides a interface between
