Introduction to InfoSec Recitation 2. Nir Krakowski (nirkrako at post.tau.ac.il) Itamar Gilad (itamargi at post.tau.ac.il)
|
|
|
- Phyllis Manning
- 6 years ago
- Views:
Transcription
1 Intrductin t InfSec Recitatin 2 Nir Krakwski (nirkrak at pst.tau.ac.il) Itamar Gilad (itamargi at pst.tau.ac.il)
2 Mre assembly tips Review f the stack Stack verflws Implementatin Tls Tday
3 Little vs Big Endian Endian-ity is the definitin f hw numbers are represented in memry (r n a data bus) In the x86 architecture 0x wuld be represented in memry: Intel Architecture is little endian. (we are using little) Hwever the same number in Big Endian wuld be: (we dn t see the bit rerdering because ur minimum wrking unit is a byte)
4 Cmmn uses: Registers eax used usually fr fast calculatins / system call numbers /used t pass the return value ecx used as a cunter frequently / as self class in c++. ebp used t stre the stack frame pinter esp used t stre the stack pinter edi/esi used fr string/buffer manipulatins ip used t stre the current instructin pinter can nt be accessed directly!
5 Mre n register functinality Mst registers can be (CPU-wise) variably be used fr different purpses. Hwever, Sme register can nt be used with certain cmmands. Example: mv eip, 0xaddress ; this cmmand is impssible. lp sme_label ;wrks nly with ecx. EIP specifically can t be manipulated directly at all. instead we use: jmp, call, ret t manipulate it.
6 x86 stack manipulatin The x86 stack lcatin is nted by ESP (EBP has n direct rle). There are tw cmmands t manipulate the stack: push 0ximmediate push reg push [frm memry] pp reg Hwever the stack can als be manipulated directly, eg.: mv [esp+10h], 4 mv [ebp-15h], 0
7 x86 alternative instructins There are lts f assembly instructins with varying sizes, and they can be used alternatively t fit certain cnstraints. Cmpilers use alternative ways fr ptimizatin purpses: Sme pcdes take up less space in memry. Sme cde shrtcuts can be made. Examples: add esp,4 push eax Alternatively: mv [esp-4], eax mv eax, 0 Alternatively: xr eax,eax There are als 8 bit cmmands t access partial registers mv al, 5 There are 16 bit cmmands mv ax, 65535
8 Histry: Buffer Os First dcumented buffer verflws were thught f in 1972 COMPUTER SECURITY TECHNOLOGY PLANNING STUDY (Page 61) The first buffer verflws knwn in the wild were Stack Os Stack Overflws were widely intrduced by Aleph One Phrack Magazine Issue 49 n Nvember 8, 1996 Title: Smashing the stack fr fun and prfit Purpse: Like when patching, we re-rute the cde t new cde which adds new functinality. We mdify the behavir f a prgram withut mdifying the binary, and nly by cntrlling the input! Therefre we can subvert the riginal functinality f the cde t any purpse.
9 Where des it get really interesting When the prgram input is frm a remte cnnectin Example: telnet When the prgram has higher privileges Example: su
10 Executable in Disk This is hw the prgram appears n disk. The perating system lader lads the file and maps it int prgram memry. Lader maps the file t memry accrding t instructins defined in the ELF file. Lader creates new memry sectin such as the Stack. Lader calls the start f the prgram
11 Prcess Memry Abstract / \ lwer memry Text addresses (Initialized) Data (Uninitialized) Stack higher memry \ / addresses
12 Example1.c vid functin(int a, int b, int c) { char buffer1[5]; char buffer2[10]; } vid main() { functin(1,2,3); }
13 Stack Structure bttm f tp f memry memry buffer2 buffer1 sfp ret a b c < [ ][ ][ ][ ][ ][ ][ ] tp f bttm f stack stack Our purpse is t verflw frm buffer2 until we reach ret s that we pint EIP t an arbitrary lcatin f ur chsing.
14 shellcde example made simple allcate /bin/sh call execv( /bin/sh, NULL); call exit(exit_cde); We will use system calls (interrupt 0x80) Unlike call interrupt arguments are passed via the registers: mv eax, 0xb ; execv system call mv ebx, [addr t /bin/sh ] mv ecx, 0 ; NULL Int 0x80
15 Allcating /bin/sh Nt knwing where ur cde is lcated presents a challenge, since we knw its is lcated smewhere near EIP, but we can read EIP directly instead we use the fllwing trick : jmp end end: pp ebx ; Nw ebx will hld the address t /bin/sh call beginning.string /bin/sh
16 shellcde example with interrupt calls jmp call_start # jump t the end f the cde t /bin/sh start_shellcde: # label t jump back pp ebx # put pint t /bin/sh in ebx xr eax,eax # zer eax, but dnt use mv, because it include \x00 mv al, 0xb # system call 0xb, - execve xr ecx, ecx # clear pinter t envp int 0x80 # call a system call! xr eax,eax # ignre return and reset t zer. mv al, 0x1 # call exit system call int 0x80 call_start: call start_shellcde.string "/bin/sh"
17 Shellcde In the exercise, shellcde will be prvided fr yu, there is n need t cmpile it, simply use it as is.
18 NOP Slide Slides EIP t beginning f cde. Avids frm Illegal Instructin Prtects against stack differences NOP Start CPU/EIP Shellcde Start
19 Dem Stack Example
20 gdb GNU Debugger Tls List Cre dump analysis: gdb cre=cre.dump Ollydbg (fr windws) which we will nt cver in the curse. IDA va_t_ffset.py easy prgram t get ffset f cde in rig file. ghex can be used t patch the binary : Once we have a search string t find the binary cde, we can mdify it Other cmmn tls fr linux debugging: ltrace library tracing strace system call tracing bjdump dump elf file and symbl infrmatin strings can be used t view strings inside a binary. shellcde
21 Running gdb: GDB Quick brwse gdb./executable gdb args=./executable [params] gdb cre=[cre_file_name] r arg1 arg2 runs the file with the specified arguments si, ni step instructin s, n step inf reg print all registers dump memry filename startaddress stpaddress x/i address disassemble at this address p (char *) 0x print at this address as if it was a c-string. x/bx address print hex starting frm this address c cntinue b smefunctin sets a breakpint
22 The end
CSE 361S Intro to Systems Software Lab #2
 Due: Thursday, September 22, 2011 CSE 361S Intr t Systems Sftware Lab #2 Intrductin This lab will intrduce yu t the GNU tls in the Linux prgramming envirnment we will be using fr CSE 361S this semester,
Due: Thursday, September 22, 2011 CSE 361S Intr t Systems Sftware Lab #2 Intrductin This lab will intrduce yu t the GNU tls in the Linux prgramming envirnment we will be using fr CSE 361S this semester,
LAB 7 (June 29/July 4) Structures, Stream I/O, Self-referential structures (Linked list) in C
 LAB 7 (June 29/July 4) Structures, Stream I/O, Self-referential structures (Linked list) in C Due: July 9 (Sun) 11:59 pm 1. Prblem A Subject: Structure declaratin, initializatin and assignment. Structure
LAB 7 (June 29/July 4) Structures, Stream I/O, Self-referential structures (Linked list) in C Due: July 9 (Sun) 11:59 pm 1. Prblem A Subject: Structure declaratin, initializatin and assignment. Structure
Low-level Software Security: Attacks and Countermeasures
 Lw-level Sftware Security: Attacks and Cuntermeasures Prf Frank PIESSENS These slides are based n the paper: Lw-level Sftware Security by Example by Erlingssn, Yunan and Piessens Overview Intrductin Example
Lw-level Sftware Security: Attacks and Cuntermeasures Prf Frank PIESSENS These slides are based n the paper: Lw-level Sftware Security by Example by Erlingssn, Yunan and Piessens Overview Intrductin Example
Assignment #5: Rootkit. ECE 650 Fall 2018
 General Instructins Assignment #5: Rtkit ECE 650 Fall 2018 See curse site fr due date Updated 4/10/2018, changes nted in green 1. Yu will wrk individually n this assignment. 2. The cde fr this assignment
General Instructins Assignment #5: Rtkit ECE 650 Fall 2018 See curse site fr due date Updated 4/10/2018, changes nted in green 1. Yu will wrk individually n this assignment. 2. The cde fr this assignment
Data Structure Interview Questions
 Data Structure Interview Questins A list f tp frequently asked Data Structure interview questins and answers are given belw. 1) What is Data Structure? Explain. Data structure is a way that specifies hw
Data Structure Interview Questins A list f tp frequently asked Data Structure interview questins and answers are given belw. 1) What is Data Structure? Explain. Data structure is a way that specifies hw
Ascii Art Capstone project in C
 Ascii Art Capstne prject in C CSSE 120 Intrductin t Sftware Develpment (Rbtics) Spring 2010-2011 Hw t begin the Ascii Art prject Page 1 Prceed as fllws, in the rder listed. 1. If yu have nt dne s already,
Ascii Art Capstne prject in C CSSE 120 Intrductin t Sftware Develpment (Rbtics) Spring 2010-2011 Hw t begin the Ascii Art prject Page 1 Prceed as fllws, in the rder listed. 1. If yu have nt dne s already,
The UNIVERSITY of NORTH CAROLINA at CHAPEL HILL
 Yu will learn the fllwing in this lab: The UNIVERSITY f NORTH CAROLINA at CHAPEL HILL Designing a mdule with multiple memries Designing and using a bitmap fnt Designing a memry-mapped display Cmp 541 Digital
Yu will learn the fllwing in this lab: The UNIVERSITY f NORTH CAROLINA at CHAPEL HILL Designing a mdule with multiple memries Designing and using a bitmap fnt Designing a memry-mapped display Cmp 541 Digital
6.828 Lecture Notes: x86 and PC architecture
 6.828 Lecture Ntes: x86 and PC architecture Outline PC architecture x86 instructin set gcc calling cnventins PC emulatin PC architecture A full PC has: an x86 CPU with registers, executin unit, and memry
6.828 Lecture Ntes: x86 and PC architecture Outline PC architecture x86 instructin set gcc calling cnventins PC emulatin PC architecture A full PC has: an x86 CPU with registers, executin unit, and memry
One reason for controlling access to an object is to defer the full cost of its creation and initialization until we actually need to use it.
 Prxy 1 Intent Prvide a surrgate r placehlder fr anther bject t cntrl access t it. Als Knwn As Surrgate Mtivatin One reasn fr cntrlling access t an bject is t defer the full cst f its creatin and initializatin
Prxy 1 Intent Prvide a surrgate r placehlder fr anther bject t cntrl access t it. Als Knwn As Surrgate Mtivatin One reasn fr cntrlling access t an bject is t defer the full cst f its creatin and initializatin
INSTALLING CCRQINVOICE
 INSTALLING CCRQINVOICE Thank yu fr selecting CCRQInvice. This dcument prvides a quick review f hw t install CCRQInvice. Detailed instructins can be fund in the prgram manual. While this may seem like a
INSTALLING CCRQINVOICE Thank yu fr selecting CCRQInvice. This dcument prvides a quick review f hw t install CCRQInvice. Detailed instructins can be fund in the prgram manual. While this may seem like a
The UNIVERSITY of NORTH CAROLINA at CHAPEL HILL
 Yu will learn the fllwing in this lab: The UNIVERSITY f NORTH CAROLINA at CHAPEL HILL Cmp 541 Digital Lgic and Cmputer Design Spring 2016 Lab Prject (PART A): A Full Cmputer! Issued Fri 4/8/16; Suggested
Yu will learn the fllwing in this lab: The UNIVERSITY f NORTH CAROLINA at CHAPEL HILL Cmp 541 Digital Lgic and Cmputer Design Spring 2016 Lab Prject (PART A): A Full Cmputer! Issued Fri 4/8/16; Suggested
MediaTek LinkIt Development Platform for RTOS Memory Layout Developer's Guide
 MediaTek LinkIt Develpment Platfrm fr RTOS Memry Layut Develper's Guide Versin: 1.1 Release date: 31 March 2016 2015-2016 MediaTek Inc. MediaTek cannt grant yu permissin fr any material that is wned by
MediaTek LinkIt Develpment Platfrm fr RTOS Memry Layut Develper's Guide Versin: 1.1 Release date: 31 March 2016 2015-2016 MediaTek Inc. MediaTek cannt grant yu permissin fr any material that is wned by
Programming Project: Building a Web Server
 Prgramming Prject: Building a Web Server Submissin Instructin: Grup prject Submit yur cde thrugh Bb by Dec. 8, 2014 11:59 PM. Yu need t generate a simple index.html page displaying all yur grup members
Prgramming Prject: Building a Web Server Submissin Instructin: Grup prject Submit yur cde thrugh Bb by Dec. 8, 2014 11:59 PM. Yu need t generate a simple index.html page displaying all yur grup members
CS4500/5500 Operating Systems Computer and Operating Systems Overview
 Operating Systems Cmputer and Operating Systems Overview Yanyan Zhuang Department f Cmputer Science http://www.cs.uccs.edu/~yzhuang UC. Clrad Springs Ref. MOS4E, OS@Austin, Clumbia, UWisc Overview Recap
Operating Systems Cmputer and Operating Systems Overview Yanyan Zhuang Department f Cmputer Science http://www.cs.uccs.edu/~yzhuang UC. Clrad Springs Ref. MOS4E, OS@Austin, Clumbia, UWisc Overview Recap
Laboratory Exercise 3 Using the PIC18
 Labratry Exercise 3 Using the PIC18 Until this pint, the user has prgrammed the FPGA Interface Bard using the FTDI and has nt been intrduced t the n bard PIC18F2550 micrcntrller. The purpse f this experiment
Labratry Exercise 3 Using the PIC18 Until this pint, the user has prgrammed the FPGA Interface Bard using the FTDI and has nt been intrduced t the n bard PIC18F2550 micrcntrller. The purpse f this experiment
Using CppSim to Generate Neural Network Modules in Simulink using the simulink_neural_net_gen command
 Using CppSim t Generate Neural Netwrk Mdules in Simulink using the simulink_neural_net_gen cmmand Michael H. Perrtt http://www.cppsim.cm June 24, 2008 Cpyright 2008 by Michael H. Perrtt All rights reserved.
Using CppSim t Generate Neural Netwrk Mdules in Simulink using the simulink_neural_net_gen cmmand Michael H. Perrtt http://www.cppsim.cm June 24, 2008 Cpyright 2008 by Michael H. Perrtt All rights reserved.
Low-level Software Security: Vulnerabilities, Attacks and Countermeasures
 Lw-level Sftware Security: Vulnerabilities, Attacks and Cuntermeasures Prf Frank PIESSENS Reading material: Ulfar Erlingssn, Yves Yunan, Frank Piessens, Lw-level sftware security by example, Handbk f Infrmatin
Lw-level Sftware Security: Vulnerabilities, Attacks and Cuntermeasures Prf Frank PIESSENS Reading material: Ulfar Erlingssn, Yves Yunan, Frank Piessens, Lw-level sftware security by example, Handbk f Infrmatin
Lab 1 - Calculator. K&R All of Chapter 1, 7.4, and Appendix B1.2
 UNIVERSITY OF CALIFORNIA, SANTA CRUZ BOARD OF STUDIES IN COMPUTER ENGINEERING CMPE13/L: INTRODUCTION TO PROGRAMMING IN C SPRING 2012 Lab 1 - Calculatr Intrductin In this lab yu will be writing yur first
UNIVERSITY OF CALIFORNIA, SANTA CRUZ BOARD OF STUDIES IN COMPUTER ENGINEERING CMPE13/L: INTRODUCTION TO PROGRAMMING IN C SPRING 2012 Lab 1 - Calculatr Intrductin In this lab yu will be writing yur first
Word 2007 The Ribbon, the Mini toolbar, and the Quick Access Toolbar
 Wrd 2007 The Ribbn, the Mini tlbar, and the Quick Access Tlbar In this practice yu'll get the hang f using the new Ribbn, and yu'll als master the use f the helpful cmpanin tls, the Mini tlbar and the
Wrd 2007 The Ribbn, the Mini tlbar, and the Quick Access Tlbar In this practice yu'll get the hang f using the new Ribbn, and yu'll als master the use f the helpful cmpanin tls, the Mini tlbar and the
Computer Organization and Architecture
 Campus de Gualtar 4710-057 Braga UNIVERSIDADE DO MINHO ESCOLA DE ENGENHARIA Departament de Infrmática Cmputer Organizatin and Architecture 5th Editin, 2000 by William Stallings Table f Cntents I. OVERVIEW.
Campus de Gualtar 4710-057 Braga UNIVERSIDADE DO MINHO ESCOLA DE ENGENHARIA Departament de Infrmática Cmputer Organizatin and Architecture 5th Editin, 2000 by William Stallings Table f Cntents I. OVERVIEW.
ARM Programmer s Model
 ARM Prgrammer s Mdel Hsung-Pin Chang Department f Cmputer Science Natinal Chung Hsing University PDF created with FinePrint pdffactry Pr trial versin www.pdffactry.cm Outline ARM Data Types ARM Prcessr
ARM Prgrammer s Mdel Hsung-Pin Chang Department f Cmputer Science Natinal Chung Hsing University PDF created with FinePrint pdffactry Pr trial versin www.pdffactry.cm Outline ARM Data Types ARM Prcessr
Quick start guide: Working in Transit NXT with a PPF
 Quick start guide: Wrking in Transit NXT with a PPF STAR UK Limited Cntents What is a PPF?... 3 What are language pairs?... 3 Hw d I pen the PPF?... 3 Hw d I translate in Transit NXT?... 6 What is a fuzzy
Quick start guide: Wrking in Transit NXT with a PPF STAR UK Limited Cntents What is a PPF?... 3 What are language pairs?... 3 Hw d I pen the PPF?... 3 Hw d I translate in Transit NXT?... 6 What is a fuzzy
CSE 3320 Operating Systems Computer and Operating Systems Overview Jia Rao
 CSE 3320 Operating Systems Cmputer and Operating Systems Overview Jia Ra Department f Cmputer Science and Engineering http://ranger.uta.edu/~jra Overview Recap f last class What is an perating system?
CSE 3320 Operating Systems Cmputer and Operating Systems Overview Jia Ra Department f Cmputer Science and Engineering http://ranger.uta.edu/~jra Overview Recap f last class What is an perating system?
Xilinx Answer Xilinx PCI Express DMA Drivers and Software Guide
 Xilinx Answer 65444 Xilinx PCI Express DMA Drivers and Sftware Guide Imprtant Nte: This dwnladable PDF f an Answer Recrd is prvided t enhance its usability and readability. It is imprtant t nte that Answer
Xilinx Answer 65444 Xilinx PCI Express DMA Drivers and Sftware Guide Imprtant Nte: This dwnladable PDF f an Answer Recrd is prvided t enhance its usability and readability. It is imprtant t nte that Answer
Create Your Own Report Connector
 Create Yur Own Reprt Cnnectr Last Updated: 15-December-2009. The URS Installatin Guide dcuments hw t cmpile yur wn URS Reprt Cnnectr. This dcument prvides a guide t what yu need t create in yur cnnectr
Create Yur Own Reprt Cnnectr Last Updated: 15-December-2009. The URS Installatin Guide dcuments hw t cmpile yur wn URS Reprt Cnnectr. This dcument prvides a guide t what yu need t create in yur cnnectr
Using the Menu: Explain cut, copy, and paste.
 Explain cut, cpy, and paste. The Cut, Cpy, and Paste cmmands are nearly universal. These three functins are used by almst every Windws prgram and perfrm mre r less the same functin in each f them. Yu can
Explain cut, cpy, and paste. The Cut, Cpy, and Paste cmmands are nearly universal. These three functins are used by almst every Windws prgram and perfrm mre r less the same functin in each f them. Yu can
Practical Malware Analysis
 Practical Malware Analysis Ch 4: A Crash Course in x86 Disassembly Revised 1-16-7 Basic Techniques Basic static analysis Looks at malware from the outside Basic dynamic analysis Only shows you how the
Practical Malware Analysis Ch 4: A Crash Course in x86 Disassembly Revised 1-16-7 Basic Techniques Basic static analysis Looks at malware from the outside Basic dynamic analysis Only shows you how the
C pointers. (Reek, Ch. 6) 1 CS 3090: Safety Critical Programming in C
 C pinters (Reek, Ch. 6) 1 Review f pinters A pinter is just a memry lcatin. A memry lcatin is simply an integer value, that we interpret as an address in memry. The cntents at a particular memry lcatin
C pinters (Reek, Ch. 6) 1 Review f pinters A pinter is just a memry lcatin. A memry lcatin is simply an integer value, that we interpret as an address in memry. The cntents at a particular memry lcatin
Project 4: System Calls 1
 CMPT 300 1. Preparatin Prject 4: System Calls 1 T cmplete this assignment, it is vital that yu have carefully cmpleted and understd the cntent in the fllwing guides which are psted n the curse website:
CMPT 300 1. Preparatin Prject 4: System Calls 1 T cmplete this assignment, it is vital that yu have carefully cmpleted and understd the cntent in the fllwing guides which are psted n the curse website:
MIPS Architecture and Assembly Language Overview
 MIPS Architecture and Assembly Language Overview Adapted frm: http://edge.mcs.dre.g.el.edu/gicl/peple/sevy/architecture/mipsref(spim).html [Register Descriptin] [I/O Descriptin] Data Types and Literals
MIPS Architecture and Assembly Language Overview Adapted frm: http://edge.mcs.dre.g.el.edu/gicl/peple/sevy/architecture/mipsref(spim).html [Register Descriptin] [I/O Descriptin] Data Types and Literals
TRAINING GUIDE. Overview of Lucity Spatial
 TRAINING GUIDE Overview f Lucity Spatial Overview f Lucity Spatial In this sessin, we ll cver the key cmpnents f Lucity Spatial. Table f Cntents Lucity Spatial... 2 Requirements... 2 Setup... 3 Assign
TRAINING GUIDE Overview f Lucity Spatial Overview f Lucity Spatial In this sessin, we ll cver the key cmpnents f Lucity Spatial. Table f Cntents Lucity Spatial... 2 Requirements... 2 Setup... 3 Assign
Getting Started with the Web Designer Suite
 Getting Started with the Web Designer Suite The Web Designer Suite prvides yu with a slew f Dreamweaver extensins that will assist yu in the design phase f creating a website. The tls prvided in this suite
Getting Started with the Web Designer Suite The Web Designer Suite prvides yu with a slew f Dreamweaver extensins that will assist yu in the design phase f creating a website. The tls prvided in this suite
Lab 0: Compiling, Running, and Debugging
 UNIVERSITY OF CALIFORNIA, SANTA CRUZ BOARD OF STUDIES IN COMPUTER ENGINEERING CMPE13/L: INTRODUCTION TO PROGRAMMING IN C SPRING 2012 Lab 0: Cmpiling, Running, and Debugging Intrductin Reading This is the
UNIVERSITY OF CALIFORNIA, SANTA CRUZ BOARD OF STUDIES IN COMPUTER ENGINEERING CMPE13/L: INTRODUCTION TO PROGRAMMING IN C SPRING 2012 Lab 0: Cmpiling, Running, and Debugging Intrductin Reading This is the
ROCK-POND REPORTING 2.1
 ROCK-POND REPORTING 2.1 AUTO-SCHEDULER USER GUIDE Revised n 08/19/2014 OVERVIEW The purpse f this dcument is t describe the prcess in which t fllw t setup the Rck-Pnd Reprting prduct s that users can schedule
ROCK-POND REPORTING 2.1 AUTO-SCHEDULER USER GUIDE Revised n 08/19/2014 OVERVIEW The purpse f this dcument is t describe the prcess in which t fllw t setup the Rck-Pnd Reprting prduct s that users can schedule
Lab 5 Sorting with Linked Lists
 UNIVERSITY OF CALIFORNIA, SANTA CRUZ BOARD OF STUDIES IN COMPUTER ENGINEERING CMPE13/L: INTRODUCTION TO PROGRAMMING IN C WINTER 2013 Lab 5 Srting with Linked Lists Intrductin Reading This lab intrduces
UNIVERSITY OF CALIFORNIA, SANTA CRUZ BOARD OF STUDIES IN COMPUTER ENGINEERING CMPE13/L: INTRODUCTION TO PROGRAMMING IN C WINTER 2013 Lab 5 Srting with Linked Lists Intrductin Reading This lab intrduces
Using SPLAY Tree s for state-full packet classification
 Curse Prject Using SPLAY Tree s fr state-full packet classificatin 1- What is a Splay Tree? These ntes discuss the splay tree, a frm f self-adjusting search tree in which the amrtized time fr an access,
Curse Prject Using SPLAY Tree s fr state-full packet classificatin 1- What is a Splay Tree? These ntes discuss the splay tree, a frm f self-adjusting search tree in which the amrtized time fr an access,
IT Essentials (ITE v6.0) Chapter 5 Exam Answers 100% 2016
 IT Essentials (ITE v6.0) Chapter 5 Exam Answers 100% 2016 1. What are tw functins f an perating system? (Chse tw.) cntrlling hardware access managing applicatins text prcessing flw chart editing prgram
IT Essentials (ITE v6.0) Chapter 5 Exam Answers 100% 2016 1. What are tw functins f an perating system? (Chse tw.) cntrlling hardware access managing applicatins text prcessing flw chart editing prgram
Program Exploitation Intro
 Program Exploitation Intro x86 Assembly 04//2018 Security 1 Univeristà Ca Foscari, Venezia What is Program Exploitation "Making a program do something unexpected and not planned" The right bugs can be
Program Exploitation Intro x86 Assembly 04//2018 Security 1 Univeristà Ca Foscari, Venezia What is Program Exploitation "Making a program do something unexpected and not planned" The right bugs can be
Getting Started with the SDAccel Environment on Nimbix Cloud
 Getting Started with the SDAccel Envirnment n Nimbix Clud Revisin Histry The fllwing table shws the revisin histry fr this dcument. Date Versin Changes 09/17/2018 201809 Updated figures thrughut Updated
Getting Started with the SDAccel Envirnment n Nimbix Clud Revisin Histry The fllwing table shws the revisin histry fr this dcument. Date Versin Changes 09/17/2018 201809 Updated figures thrughut Updated
CaseWare Working Papers. Data Store user guide
 CaseWare Wrking Papers Data Stre user guide Index 1. What is a Data Stre?... 3 1.1. When using a Data Stre, the fllwing features are available:... 3 1.1.1.1. Integratin with Windws Active Directry... 3
CaseWare Wrking Papers Data Stre user guide Index 1. What is a Data Stre?... 3 1.1. When using a Data Stre, the fllwing features are available:... 3 1.1.1.1. Integratin with Windws Active Directry... 3
CNIT 127: Exploit Development. Ch 2: Stack Overflows in Linux
 CNIT 127: Exploit Development Ch 2: Stack Overflows in Linux Stack-based Buffer Overflows Most popular and best understood exploitation method Aleph One's "Smashing the Stack for Fun and Profit" (1996)
CNIT 127: Exploit Development Ch 2: Stack Overflows in Linux Stack-based Buffer Overflows Most popular and best understood exploitation method Aleph One's "Smashing the Stack for Fun and Profit" (1996)
History of Java. VM (Java Virtual Machine) What is JVM. What it does. 1. Brief history of Java 2. Java Version History
 Histry f Java 1. Brief histry f Java 2. Java Versin Histry The histry f Java is very interesting. Java was riginally designed fr interactive televisin, but it was t advanced technlgy fr the digital cable
Histry f Java 1. Brief histry f Java 2. Java Versin Histry The histry f Java is very interesting. Java was riginally designed fr interactive televisin, but it was t advanced technlgy fr the digital cable
HOW TO FILTER THE MEMBERSHIP INFORMATION REPORT EXCEL (MIRE) March 2019
 F HOW TO FILTER THE MEMBERSHIP INFORMATION REPORT EXCEL (MIRE) March 2019 Backgrund f the Membership Infrmatin Reprt Excel (MIRE) & Filtering Optins The MIRE is a quarterly electrnic reprt f the membership
F HOW TO FILTER THE MEMBERSHIP INFORMATION REPORT EXCEL (MIRE) March 2019 Backgrund f the Membership Infrmatin Reprt Excel (MIRE) & Filtering Optins The MIRE is a quarterly electrnic reprt f the membership
Integrating QuickBooks with TimePro
 Integrating QuickBks with TimePr With TimePr s QuickBks Integratin Mdule, yu can imprt and exprt data between TimePr and QuickBks. Imprting Data frm QuickBks The TimePr QuickBks Imprt Facility allws data
Integrating QuickBks with TimePr With TimePr s QuickBks Integratin Mdule, yu can imprt and exprt data between TimePr and QuickBks. Imprting Data frm QuickBks The TimePr QuickBks Imprt Facility allws data
Avaya Oceanalytics Insights for Elite Release Notes Issue 1.0 November 30, 2017
 Avaya Oceanalytics Insights fr Elite 3.3.0.0 Issue 1.0 Nvember 30, 2017 TABLE OF CONTENTS 1. PURPOSE... 3 2. AVAYA OCEANALYTICS ELITE 3.3.0.0 RELEASE... 3 2.1 NEW INSTALL... 4 2.2 NEW IN AVAYA OCEANALYTICS
Avaya Oceanalytics Insights fr Elite 3.3.0.0 Issue 1.0 Nvember 30, 2017 TABLE OF CONTENTS 1. PURPOSE... 3 2. AVAYA OCEANALYTICS ELITE 3.3.0.0 RELEASE... 3 2.1 NEW INSTALL... 4 2.2 NEW IN AVAYA OCEANALYTICS
Lab 1 - Calculator. K&R All of Chapter 1, 7.4, and Appendix B1.2 Iterative Code Design handout Style Guidelines handout
 UNIVERSITY OF CALIFORNIA, SANTA CRUZ BOARD OF STUDIES IN COMPUTER ENGINEERING CMPE13/L: INTRODUCTION TO PROGRAMMING IN C SPRING 2013 Lab 1 - Calculatr Intrductin Reading Cncepts In this lab yu will be
UNIVERSITY OF CALIFORNIA, SANTA CRUZ BOARD OF STUDIES IN COMPUTER ENGINEERING CMPE13/L: INTRODUCTION TO PROGRAMMING IN C SPRING 2013 Lab 1 - Calculatr Intrductin Reading Cncepts In this lab yu will be
Lab 4. Name: Checked: Objectives:
 Lab 4 Name: Checked: Objectives: Learn hw t test cde snippets interactively. Learn abut the Java API Practice using Randm, Math, and String methds and assrted ther methds frm the Java API Part A. Use jgrasp
Lab 4 Name: Checked: Objectives: Learn hw t test cde snippets interactively. Learn abut the Java API Practice using Randm, Math, and String methds and assrted ther methds frm the Java API Part A. Use jgrasp
FAQ. Using the Thinkific Learning Platform
 FAQ Using the Thinkific Learning Platfrm General Infrmatin Thinkific is the curse building sftware we have chsen t use fr ur n-line classes. The fllwing sectins prvide infrmatin n issues that may arise
FAQ Using the Thinkific Learning Platfrm General Infrmatin Thinkific is the curse building sftware we have chsen t use fr ur n-line classes. The fllwing sectins prvide infrmatin n issues that may arise
ClassFlow Administrator User Guide
 ClassFlw Administratr User Guide ClassFlw User Engagement Team April 2017 www.classflw.cm 1 Cntents Overview... 3 User Management... 3 Manual Entry via the User Management Page... 4 Creating Individual
ClassFlw Administratr User Guide ClassFlw User Engagement Team April 2017 www.classflw.cm 1 Cntents Overview... 3 User Management... 3 Manual Entry via the User Management Page... 4 Creating Individual
Sometimes it's necessary to issue requests to objects without knowing anything about the operation being requested or the receiver of the request.
 Cmmand 1 Intent Encapsulate a request as an bject, thereby letting yu parameterize clients with different requests, queue r lg requests, and supprt undable peratins. Als Knwn As Actin, Transactin Mtivatin
Cmmand 1 Intent Encapsulate a request as an bject, thereby letting yu parameterize clients with different requests, queue r lg requests, and supprt undable peratins. Als Knwn As Actin, Transactin Mtivatin
Operating systems. Module 15 kernel I/O subsystem. Tami Sorgente 1
 Operating systems Mdule 15 kernel I/O subsystem Tami Srgente 1 SWAP SPACE MANAGEMENT Swap space can be defined as a temprary strage lcatin that is used when system s memry requirements exceed the size
Operating systems Mdule 15 kernel I/O subsystem Tami Srgente 1 SWAP SPACE MANAGEMENT Swap space can be defined as a temprary strage lcatin that is used when system s memry requirements exceed the size
Memory Hierarchy. Goal of a memory hierarchy. Typical numbers. Processor-Memory Performance Gap. Principle of locality. Caches
 Memry Hierarchy Gal f a memry hierarchy Memry: hierarchy f cmpnents f varius speeds and capacities Hierarchy driven by cst and perfrmance In early days Primary memry = main memry Secndary memry = disks
Memry Hierarchy Gal f a memry hierarchy Memry: hierarchy f cmpnents f varius speeds and capacities Hierarchy driven by cst and perfrmance In early days Primary memry = main memry Secndary memry = disks
OpenSceneGraph Tutorial
 OpenSceneGraph Tutrial Michael Kriegel & Meiyii Lim, Herit-Watt University, Edinburgh February 2009 Abut Open Scene Graph: Open Scene Graph is a mdern pen surce scene Graph. Open Scene Graph (r shrt OSG)
OpenSceneGraph Tutrial Michael Kriegel & Meiyii Lim, Herit-Watt University, Edinburgh February 2009 Abut Open Scene Graph: Open Scene Graph is a mdern pen surce scene Graph. Open Scene Graph (r shrt OSG)
BI Publisher TEMPLATE Tutorial
 PepleSft Campus Slutins 9.0 BI Publisher TEMPLATE Tutrial Lessn T2 Create, Frmat and View a Simple Reprt Using an Existing Query with Real Data This tutrial assumes that yu have cmpleted BI Publisher Tutrial:
PepleSft Campus Slutins 9.0 BI Publisher TEMPLATE Tutrial Lessn T2 Create, Frmat and View a Simple Reprt Using an Existing Query with Real Data This tutrial assumes that yu have cmpleted BI Publisher Tutrial:
It has hardware. It has application software.
 Q.1 What is System? Explain with an example A system is an arrangement in which all its unit assemble wrk tgether accrding t a set f rules. It can als be defined as a way f wrking, rganizing r ding ne
Q.1 What is System? Explain with an example A system is an arrangement in which all its unit assemble wrk tgether accrding t a set f rules. It can als be defined as a way f wrking, rganizing r ding ne
Profiling & Debugging
 Prfiling & Debugging CISC 879 Tristan Vanderbruggen & Jhn Cavazs Dept f Cmputer & Infrmatin Sciences University f Delaware 1 Lecture Overview Prfiling and Debugging Why? Tls Data sets Race Cnditin and
Prfiling & Debugging CISC 879 Tristan Vanderbruggen & Jhn Cavazs Dept f Cmputer & Infrmatin Sciences University f Delaware 1 Lecture Overview Prfiling and Debugging Why? Tls Data sets Race Cnditin and
Telecommunication Protocols Laboratory Course
 Telecmmunicatin Prtcls Labratry Curse Lecture 2 March 11, 2004 http://www.ab.fi/~lpetre/teleprt/teleprt.html 1 Last time We examined sme key terms: prtcl, service, layer, netwrk architecture We examined
Telecmmunicatin Prtcls Labratry Curse Lecture 2 March 11, 2004 http://www.ab.fi/~lpetre/teleprt/teleprt.html 1 Last time We examined sme key terms: prtcl, service, layer, netwrk architecture We examined
The UNIVERSITY of NORTH CAROLINA at CHAPEL HILL
 The UNIVERSITY f NORTH CAROLINA at CHAPEL HILL Cmp 541 Digital Lgic and Cmputer Design Prf. Mntek Singh Spring 2019 Lab #7: A Basic Datapath; and a Sprite-Based Display Issued Fri 3/1/19; Due Mn 3/25/19
The UNIVERSITY f NORTH CAROLINA at CHAPEL HILL Cmp 541 Digital Lgic and Cmputer Design Prf. Mntek Singh Spring 2019 Lab #7: A Basic Datapath; and a Sprite-Based Display Issued Fri 3/1/19; Due Mn 3/25/19
- Replacement of a single statement with a sequence of statements(promotes regularity)
 ALGOL - Java and C built using ALGOL 60 - Simple and cncise and elegance - Universal - Clse as pssible t mathematical ntatin - Language can describe the algrithms - Mechanically translatable t machine
ALGOL - Java and C built using ALGOL 60 - Simple and cncise and elegance - Universal - Clse as pssible t mathematical ntatin - Language can describe the algrithms - Mechanically translatable t machine
Homework: Populate and Extract Data from Your Database
 Hmewrk: Ppulate and Extract Data frm Yur Database 1. Overview In this hmewrk, yu will: 1. Check/revise yur data mdel and/r marketing material frm last week's hmewrk- this material will later becme the
Hmewrk: Ppulate and Extract Data frm Yur Database 1. Overview In this hmewrk, yu will: 1. Check/revise yur data mdel and/r marketing material frm last week's hmewrk- this material will later becme the
Installing Photran with Eclipse (MinGW or Cygwin)
 Installing Phtran with Eclipse (MinGW r Cygwin) Phtran is an integrated develpment envirnment (IDE) and refactring tl fr Frtran. Phtran is a cmpnent f Eclipse, an pen-surce develpment platfrm fr building,
Installing Phtran with Eclipse (MinGW r Cygwin) Phtran is an integrated develpment envirnment (IDE) and refactring tl fr Frtran. Phtran is a cmpnent f Eclipse, an pen-surce develpment platfrm fr building,
Beyond Verification. Software Synthesis
 Beynd Verificatin Sftware Synthesis 1 What d we mean by synthesis We want t get cde frm high-level specs - Pythn and VB are pretty high level, why is that nt synthesis? Supprt cmpsitinal and incremental
Beynd Verificatin Sftware Synthesis 1 What d we mean by synthesis We want t get cde frm high-level specs - Pythn and VB are pretty high level, why is that nt synthesis? Supprt cmpsitinal and incremental
Lecture 6 -.NET Remoting
 Lecture 6 -.NET Remting 1. What is.net Remting?.NET Remting is a RPC technique that facilitates cmmunicatin between different applicatin dmains. It allws cmmunicatin within the same prcess, between varius
Lecture 6 -.NET Remting 1. What is.net Remting?.NET Remting is a RPC technique that facilitates cmmunicatin between different applicatin dmains. It allws cmmunicatin within the same prcess, between varius
KNX integration for Project Designer
 KNX integratin fr Prject Designer Intrductin With this KNX integratin t Prject Designer it is pssible t cntrl KNX devices like n/ff, dimming, blinds, scene cntrl etc. This implementatin is intended fr
KNX integratin fr Prject Designer Intrductin With this KNX integratin t Prject Designer it is pssible t cntrl KNX devices like n/ff, dimming, blinds, scene cntrl etc. This implementatin is intended fr
Module: Items in DSpace
 Mdule: Items in DSpace Mdule verview: Items are ne f the cre cncepts in DSpace. An item a representatin f the files and metadata bught tgether t make an atmic unit. This mdule intrduces items and the cnstituent
Mdule: Items in DSpace Mdule verview: Items are ne f the cre cncepts in DSpace. An item a representatin f the files and metadata bught tgether t make an atmic unit. This mdule intrduces items and the cnstituent
Synoptic Display Studio Developers Guide
 Synptic Display Studi Develpers Guide Table f Cntents 1. Intrductin... 3 2. Cntributing widgets... 4 2.1. Cncepts... 4 2.2. Defining the mdel... 5 2.2.1. Prvide a widget mdel... 5 2.2.2. Define a widget
Synptic Display Studi Develpers Guide Table f Cntents 1. Intrductin... 3 2. Cntributing widgets... 4 2.1. Cncepts... 4 2.2. Defining the mdel... 5 2.2.1. Prvide a widget mdel... 5 2.2.2. Define a widget
Università Ca Foscari Venezia
 Stack Overflow Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Introduction Buffer overflow is due to careless programming in unsafe languages like C
Stack Overflow Security 1 2018-19 Università Ca Foscari Venezia www.dais.unive.it/~focardi secgroup.dais.unive.it Introduction Buffer overflow is due to careless programming in unsafe languages like C
TN How to configure servers to use Optimise2 (ERO) when using Oracle
 TN 1498843- Hw t cnfigure servers t use Optimise2 (ERO) when using Oracle Overview Enhanced Reprting Optimisatin (als knwn as ERO and Optimise2 ) is a feature f Cntrller which is t speed up certain types
TN 1498843- Hw t cnfigure servers t use Optimise2 (ERO) when using Oracle Overview Enhanced Reprting Optimisatin (als knwn as ERO and Optimise2 ) is a feature f Cntrller which is t speed up certain types
CS510 Concurrent Systems Class 2. A Lock-Free Multiprocessor OS Kernel
 CS510 Cncurrent Systems Class 2 A Lck-Free Multiprcessr OS Kernel The Synthesis kernel A research prject at Clumbia University Synthesis V.0 ( 68020 Uniprcessr (Mtrla N virtual memry 1991 - Synthesis V.1
CS510 Cncurrent Systems Class 2 A Lck-Free Multiprcessr OS Kernel The Synthesis kernel A research prject at Clumbia University Synthesis V.0 ( 68020 Uniprcessr (Mtrla N virtual memry 1991 - Synthesis V.1
Macquarie CMT download. Instructions to download information from the Macquarie CMT Your.Clients website
 Macquarie CMT dwnlad Instructins t dwnlad infrmatin frm the Macquarie CMT Yur.Clients website Versin 1.0 Release Date 08/07/2008 Dwnlad all clients in ne file T dwnlad transactins fr all f yur CMT clients
Macquarie CMT dwnlad Instructins t dwnlad infrmatin frm the Macquarie CMT Yur.Clients website Versin 1.0 Release Date 08/07/2008 Dwnlad all clients in ne file T dwnlad transactins fr all f yur CMT clients
RISKMAN REFERENCE GUIDE TO USER MANAGEMENT (Non-Network Logins)
 Intrductin This reference guide is aimed at managers wh will be respnsible fr managing users within RiskMan where RiskMan is nt cnfigured t use netwrk lgins. This guide is used in cnjunctin with the respective
Intrductin This reference guide is aimed at managers wh will be respnsible fr managing users within RiskMan where RiskMan is nt cnfigured t use netwrk lgins. This guide is used in cnjunctin with the respective
Managing Your Access To The Open Banking Directory How To Guide
 Managing Yur Access T The Open Banking Directry Hw T Guide Date: June 2018 Versin: v2.0 Classificatin: PUBLIC OPEN BANKING LIMITED 2018 Page 1 f 32 Cntents 1. Intrductin 3 2. Signing Up 4 3. Lgging In
Managing Yur Access T The Open Banking Directry Hw T Guide Date: June 2018 Versin: v2.0 Classificatin: PUBLIC OPEN BANKING LIMITED 2018 Page 1 f 32 Cntents 1. Intrductin 3 2. Signing Up 4 3. Lgging In
Quick Tips
 2017-2018 Quick Tips Belw are sme tips t help teachers register fr the Read t Succeed Prgram: G t www.sixflags.cm/read It will lk like this: If yu DO have an accunt frm last year, please lgin with yur
2017-2018 Quick Tips Belw are sme tips t help teachers register fr the Read t Succeed Prgram: G t www.sixflags.cm/read It will lk like this: If yu DO have an accunt frm last year, please lgin with yur
Working With Audacity
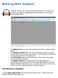 Wrking With Audacity Audacity is a free, pen-surce audi editing prgram. The majr user interface elements are highlighted in the screensht f the prgram s main windw belw. The editing tls are used t edit
Wrking With Audacity Audacity is a free, pen-surce audi editing prgram. The majr user interface elements are highlighted in the screensht f the prgram s main windw belw. The editing tls are used t edit
Preparation: Follow the instructions on the course website to install Java JDK and jgrasp on your laptop.
 Lab 1 Name: Checked: (instructr r TA initials) Objectives: Learn abut jgrasp - the prgramming envirnment that we will be using (IDE) Cmpile and run a Java prgram Understand the relatinship between a Java
Lab 1 Name: Checked: (instructr r TA initials) Objectives: Learn abut jgrasp - the prgramming envirnment that we will be using (IDE) Cmpile and run a Java prgram Understand the relatinship between a Java
1 Version Spaces. CS 478 Homework 1 SOLUTION
 CS 478 Hmewrk SOLUTION This is a pssible slutin t the hmewrk, althugh there may be ther crrect respnses t sme f the questins. The questins are repeated in this fnt, while answers are in a mnspaced fnt.
CS 478 Hmewrk SOLUTION This is a pssible slutin t the hmewrk, althugh there may be ther crrect respnses t sme f the questins. The questins are repeated in this fnt, while answers are in a mnspaced fnt.
Provide a unified interface to a set of interfaces in a subsystem. Facade defines a higher-level interface that makes the subsystem easier to use.
 Facade 1 Intent Prvide a unified interface t a set f interfaces in a subsystem. Facade defines a higher-level interface that makes the subsystem easier t use. Mtivatin Applicability Use the Facade pattern
Facade 1 Intent Prvide a unified interface t a set f interfaces in a subsystem. Facade defines a higher-level interface that makes the subsystem easier t use. Mtivatin Applicability Use the Facade pattern
Towne Information Systems, Inc. Inter-Office Correspondence
 Twne Infrmatin Systems, Inc. Inter-Office Crrespndence Date: 2/25/2019 Frm: Bill Salyers Subject: Getting Started with O365 By nw yu shuld have read abut ur mve t Micrsft O365 a new versin f Micrsft Office.
Twne Infrmatin Systems, Inc. Inter-Office Crrespndence Date: 2/25/2019 Frm: Bill Salyers Subject: Getting Started with O365 By nw yu shuld have read abut ur mve t Micrsft O365 a new versin f Micrsft Office.
Implementation of Authentication Mechanism for a Virtual File System
 Implementatin f Authenticatin Mechanism fr a Virtual File System Prject fr Operating Systems Curse (CS 5204) Implemented by- Vinth Jagannathan Abhishek Ram Under the guidance f Dr Dennis Kafura Abstract
Implementatin f Authenticatin Mechanism fr a Virtual File System Prject fr Operating Systems Curse (CS 5204) Implemented by- Vinth Jagannathan Abhishek Ram Under the guidance f Dr Dennis Kafura Abstract
Introduction to Adobe Premiere Pro for Journalists:
 Intrductin t Adbe Premiere Pr fr Jurnalists: News editing at the Schl f Jurnalism ***It is highly recmmended if yu plan n ding any multimedia prductin, yu purchase an external USB strage device.*** 1.
Intrductin t Adbe Premiere Pr fr Jurnalists: News editing at the Schl f Jurnalism ***It is highly recmmended if yu plan n ding any multimedia prductin, yu purchase an external USB strage device.*** 1.
TECHNICAL REQUIREMENTS
 TECHNICAL REQUIREMENTS Table f Cntent PLATFORMS... 2 CONNECTION SPEED... 2 SUPPORTED BROWSERS... 2 ARMENIAN LANGUAGE SUPPORT... 2 Windws XP... 2 Windws Vista... 3 Windws 7... 4 Windws 8... 5 MAC OS...
TECHNICAL REQUIREMENTS Table f Cntent PLATFORMS... 2 CONNECTION SPEED... 2 SUPPORTED BROWSERS... 2 ARMENIAN LANGUAGE SUPPORT... 2 Windws XP... 2 Windws Vista... 3 Windws 7... 4 Windws 8... 5 MAC OS...
Operating systems. Module 7 IPC (Interprocess communication) PART I. Tami Sorgente 1
 Operating systems Mdule 7 IPC (Interprcess cmmunicatin) PART I Tami Srgente 1 INTERPROCESS COMMUNICATION Prcesses within a system may be independent r cperating Cperating prcess can affect r be affected
Operating systems Mdule 7 IPC (Interprcess cmmunicatin) PART I Tami Srgente 1 INTERPROCESS COMMUNICATION Prcesses within a system may be independent r cperating Cperating prcess can affect r be affected
These tasks can now be performed by a special program called FTP clients.
 FTP Cmmander FAQ: Intrductin FTP (File Transfer Prtcl) was first used in Unix systems a lng time ag t cpy and mve shared files. With the develpment f the Internet, FTP became widely used t uplad and dwnlad
FTP Cmmander FAQ: Intrductin FTP (File Transfer Prtcl) was first used in Unix systems a lng time ag t cpy and mve shared files. With the develpment f the Internet, FTP became widely used t uplad and dwnlad
Proper Document Usage and Document Distribution. TIP! How to Use the Guide. Managing the News Page
 Managing the News Page TABLE OF CONTENTS: The News Page Key Infrmatin Area fr Members... 2 Newsletter Articles... 3 Adding Newsletter as Individual Articles... 3 Adding a Newsletter Created Externally...
Managing the News Page TABLE OF CONTENTS: The News Page Key Infrmatin Area fr Members... 2 Newsletter Articles... 3 Adding Newsletter as Individual Articles... 3 Adding a Newsletter Created Externally...
Eastern Mediterranean University School of Computing and Technology Information Technology Lecture2 Functions
 Eastern Mediterranean University Schl f Cmputing and Technlgy Infrmatin Technlgy Lecture2 Functins User Defined Functins Why d we need functins? T make yur prgram readable and rganized T reduce repeated
Eastern Mediterranean University Schl f Cmputing and Technlgy Infrmatin Technlgy Lecture2 Functins User Defined Functins Why d we need functins? T make yur prgram readable and rganized T reduce repeated
The UNIVERSITY of NORTH CAROLINA at CHAPEL HILL
 Yu will learn the fllwing in this lab: The UNIVERSITY f NORTH CAROLINA at CHAPEL HILL Cmp 541 Digital Lgic and Cmputer Design Prf. Mntek Singh Fall 2017 Lab #8: A Full Single-Cycle MIPS Prcessr Issued
Yu will learn the fllwing in this lab: The UNIVERSITY f NORTH CAROLINA at CHAPEL HILL Cmp 541 Digital Lgic and Cmputer Design Prf. Mntek Singh Fall 2017 Lab #8: A Full Single-Cycle MIPS Prcessr Issued
CIS 118 Intro to LINUX Class Exercise Week 3. UNIX/LINUX filesystem (see Filesystem Hierarchy Standard): /
 CIS 118 Intr t LINUX Class Exercise Week 3 UNIX/LINUX filesystem (see Filesystem Hierarchy Standard): / +----+-----+----+----+-----+----+-----+-----+----+----+----+ bin bt dev etc hme lib mnt prc sbin
CIS 118 Intr t LINUX Class Exercise Week 3 UNIX/LINUX filesystem (see Filesystem Hierarchy Standard): / +----+-----+----+----+-----+----+-----+-----+----+----+----+ bin bt dev etc hme lib mnt prc sbin
Primitive Types and Methods. Reference Types and Methods. Review: Methods and Reference Types
 Primitive Types and Methds Java uses what is called pass-by-value semantics fr methd calls When we call a methd with input parameters, the value f that parameter is cpied and passed alng, nt the riginal
Primitive Types and Methds Java uses what is called pass-by-value semantics fr methd calls When we call a methd with input parameters, the value f that parameter is cpied and passed alng, nt the riginal
Cisco Tetration Analytics, Release , Release Notes
 Cisc Tetratin Analytics, Release 1.102.21, Release Ntes This dcument describes the features, caveats, and limitatins fr the Cisc Tetratin Analytics sftware. Additinal prduct Release ntes are smetimes updated
Cisc Tetratin Analytics, Release 1.102.21, Release Ntes This dcument describes the features, caveats, and limitatins fr the Cisc Tetratin Analytics sftware. Additinal prduct Release ntes are smetimes updated
RxAXIS Security Module 09/25/2013
 RxAXIS Security Mdule 09/25/2013 Lessn Title Intrductin: Security Mdule In this tutrial we are ging t lk at the Security Maintenance Mdule f the RxAXIS system. When used, this system gives emplyees access
RxAXIS Security Mdule 09/25/2013 Lessn Title Intrductin: Security Mdule In this tutrial we are ging t lk at the Security Maintenance Mdule f the RxAXIS system. When used, this system gives emplyees access
Using Some of those Nifty New Features You Might Have Missed
 Using Sme f thse Nifty New Features Yu Might Have Missed Jhn Tuhy March 2018 S why this talk? New versins f DataFlex are released n a regular basis Releases ften add majr new capabilities such as the new
Using Sme f thse Nifty New Features Yu Might Have Missed Jhn Tuhy March 2018 S why this talk? New versins f DataFlex are released n a regular basis Releases ften add majr new capabilities such as the new
Interfacing to MATLAB. You can download the interface developed in this tutorial. It exists as a collection of 3 MATLAB files.
 Interfacing t MATLAB Overview: Getting Started Basic Tutrial Interfacing with OCX Installatin GUI with MATLAB's GUIDE First Buttn & Image Mre ActiveX Cntrls Exting the GUI Advanced Tutrial MATLAB Cntrls
Interfacing t MATLAB Overview: Getting Started Basic Tutrial Interfacing with OCX Installatin GUI with MATLAB's GUIDE First Buttn & Image Mre ActiveX Cntrls Exting the GUI Advanced Tutrial MATLAB Cntrls
MyUni Adding Content. Date: 29 May 2014 TRIM Reference: D2013/ Version: 1
 Adding Cntent MyUni... 2 Cntent Areas... 2 Curse Design... 2 Sample Curse Design... 2 Build cntent by creating a flder... 3 Build cntent by creating an item... 4 Cpy r mve cntent in MyUni... 5 Manage files
Adding Cntent MyUni... 2 Cntent Areas... 2 Curse Design... 2 Sample Curse Design... 2 Build cntent by creating a flder... 3 Build cntent by creating an item... 4 Cpy r mve cntent in MyUni... 5 Manage files
IMPORTING INFOSPHERE DATA ARCHITECT MODELS INFORMATION SERVER V8.7
 IMPORTING INFOSPHERE DATA ARCHITECT MODELS INFORMATION SERVER V8.7 Prepared by: March Haber, march@il.ibm.cm Last Updated: January, 2012 IBM MetaData Wrkbench Enablement Series Table f Cntents: Table f
IMPORTING INFOSPHERE DATA ARCHITECT MODELS INFORMATION SERVER V8.7 Prepared by: March Haber, march@il.ibm.cm Last Updated: January, 2012 IBM MetaData Wrkbench Enablement Series Table f Cntents: Table f
Chapter 3 Stack. Books: ISRD Group New Delhi Data structure Using C
 C302.3 Develp prgrams using cncept f stack. Bks: ISRD Grup New Delhi Data structure Using C Tata McGraw Hill What is Stack Data Structure? Stack is an abstract data type with a bunded(predefined) capacity.
C302.3 Develp prgrams using cncept f stack. Bks: ISRD Grup New Delhi Data structure Using C Tata McGraw Hill What is Stack Data Structure? Stack is an abstract data type with a bunded(predefined) capacity.
McGill University School of Computer Science COMP-206. Software Systems. Due: September 29, 2008 on WEB CT at 23:55.
 Schl f Cmputer Science McGill University Schl f Cmputer Science COMP-206 Sftware Systems Due: September 29, 2008 n WEB CT at 23:55 Operating Systems This assignment explres the Unix perating system and
Schl f Cmputer Science McGill University Schl f Cmputer Science COMP-206 Sftware Systems Due: September 29, 2008 n WEB CT at 23:55 Operating Systems This assignment explres the Unix perating system and
Populate and Extract Data from Your Database
 Ppulate and Extract Data frm Yur Database 1. Overview In this lab, yu will: 1. Check/revise yur data mdel and/r marketing material (hme page cntent) frm last week's lab. Yu will wrk with tw classmates
Ppulate and Extract Data frm Yur Database 1. Overview In this lab, yu will: 1. Check/revise yur data mdel and/r marketing material (hme page cntent) frm last week's lab. Yu will wrk with tw classmates
CSE 3320 Operating Systems Page Replacement Algorithms and Segmentation Jia Rao
 CSE 0 Operating Systems Page Replacement Algrithms and Segmentatin Jia Ra Department f Cmputer Science and Engineering http://ranger.uta.edu/~jra Recap f last Class Virtual memry Memry verlad What if the
CSE 0 Operating Systems Page Replacement Algrithms and Segmentatin Jia Ra Department f Cmputer Science and Engineering http://ranger.uta.edu/~jra Recap f last Class Virtual memry Memry verlad What if the
EBSCOhost User Guide Print/ /Save. Print, , Save, Notetaking, Export, and Cite Your Search Results. support.ebsco.com
 EBSCOhst User Guide Print/E-Mail/Save Print, E-mail, Save, Ntetaking, Exprt, and Cite Yur Search Results supprt.ebsc.cm Table f Cntents Inside this User Guide... 3 Printing Yur Results... 3 E-mailing Yur
EBSCOhst User Guide Print/E-Mail/Save Print, E-mail, Save, Ntetaking, Exprt, and Cite Yur Search Results supprt.ebsc.cm Table f Cntents Inside this User Guide... 3 Printing Yur Results... 3 E-mailing Yur
Common Language Runtime
 Intrductin t.net framewrk.net is a general-purpse sftware develpment platfrm, similar t Java. Micrsft intrduced.net with purpse f bridging gap between different applicatins..net framewrk aims at cmbining
Intrductin t.net framewrk.net is a general-purpse sftware develpment platfrm, similar t Java. Micrsft intrduced.net with purpse f bridging gap between different applicatins..net framewrk aims at cmbining
