INF204x Module 2 Lab 2: Using Encrypting File System (EFS) on Windows 10 Clients
|
|
|
- Henry Burns
- 6 years ago
- Views:
Transcription
1 INF204x Module 2 Lab 2: Using Encrypting File System (EFS) on Windows 10 Clients Estimated Time: 30 minutes You have a standalone Windows 10 client computer that you share with your colleagues. You plan to take advantage of the Encrypting File System to control access to selected files on the local computer. Objectives After completing this lab, students will be able to: Encrypt files and folders by using EFS Share access to encrypted files Lab Environment The lab consists of two virtual machines: LON-WIN10 - Windows 10 Enterprise client (Adatum.com Active Directory domain member) with IPv4 address of LON-DC1 Windows Server 2012 R2 Datacenter server (Adatum.com Active Directory domain controller) with IPv4 address of Exercise 1: Encrypt local files and folders by using EFS In this exercise, you will create two local user accounts on a Windows 10 computer, you will log on as the first user and encrypt a file by using EFS, and log on as the second user and ensure that the file is not accessible. The main tasks for this exercise are as follows: 1. Create two Windows 10 local user accounts 2. Encrypt a file by using EFS as the first user. 3. Attempt to access the encrypted file as the second user. Task 1: Create two Windows 10 local user accounts 1. Sign in to the lab virtual machine LON-WIN10 with the following credentials (note that these are local, rather than domain, credentials): USERNAME:.\Admin PASSWORD: Pa$$w0rd 2. On your lab virtual machine, click the Windows logo in the lower left corner and click Settings in the Start menu. 3. In the Settings app, click Accounts 4. Click Other users
2 5. Click Add someone else to this PC 6. On the Create an account for this PC page, specify the following information: User name: luser1 Enter password: luser1pa$$ Re-enter password: luser1pa$$ Password hint: Default 7. Click Next 8. Click again Add someone else to this PC 9. On the How will this person sign in? page, click I don t have this person s sign-in information 10. On the Let s create your account page, click Add a user without a Microsoft account. 11. On the Create an account for this PC page, specify the following information: User name: luser2 Enter password: luser2pa$$ Re-enter password: luser2pa$$ Password hint: Default 12. Click Next 13. Launch File Explorer 14. Create folder C:\Data 15. Sign out from the lab virtual machine. Task 2: Encrypt a file by using EFS as the first user 1. Sign in to the lab virtual machine (LON-WIN10) with the following credentials (note that these are local, rather than domain, credentials): USERNAME:.\luser1 PASSWORD: luser1pa$$ 2. Launch File Explorer and navigate to C:\Data folder. 3. Create a file named File1.txt, type a random text in it, and save it in the C:\Data folder. 4. Right-click on File1.txt and select Properties from the context-sensitive menu. 5. In the Properties dialog box, click Advanced. 6. In the Advanced Attributes dialog box, enable the checkbox next to Encrypt contents to secure data. 7. Click OK. 8. Back in the Properties dialog box, click OK.
3 9. When prompted with the Encryption Warning dialog box, select Encrypt the file only and click OK. Note that, in general, you should choose the option to Encrypt the file and its parent folder (recommended). In some cases, if the file is modified, the editing software might create a temporary, unencrypted copy of the file in the same folder. By using this option, you ensure that such files are also encrypted. We use the option to Encrypt the file only for demo purposes only. Keep in mind that you should back up encryption keys, so you can recover encrypted files if the encryption key stored in your user profile is lost or damaged. The encryption key is part of the EFS certificate and is generated automatically when you encrypt a file for the first time. You will receive at that point notification to Back up file encryption certificate and key giving you the option to back up certificate to removable media. Selecting this option will automatically trigger Certificate Export Wizard, guiding you through the process of exporting the certificate. Alternatively, you can also use the option to Back up keys appearing in the User Access to filename dialog box, accessible via Details command button on the Advanced Attributes dialog box of any encrypted file. 10. Note that the file is displayed in green color. Right-click on it again and select Properties from the context-sensitive menu. 11. In the Properties dialog box, click Advanced again. 12. In the Advanced Attributes dialog box, click Details next to Encrypt contents to secure data label. 13. In the User Access to File1.txt, note that the current user account (luser1) is the only one who can access this file. 14. Click Add. 15. In the Encrypting File System dialog box, you should see only the single certificate for luser1. Effectively, at this point, you cannot grant access to the encrypted file to other users. 16. Click Cancel three times to close all dialog boxes. Task 3: Attempt to access the encrypted file as the second user. 2. Sign in to the lab virtual machine with the following credentials (note that these are local, rather than domain, credentials): USERNAME:.\luser2 PASSWORD: luser2pa$$ 3. Launch File Explorer and navigate to C:\Data folder. 4. Double click the File1.txt file. 5. Verify that you get the Access is denied message.
4 6. Click OK and close Notepad. Results: After completing this exercise, you will have created two Windows 10 local user accounts, encrypted a file by using the first of them, and verified that the second one does not have access to the encrypted file. Exercise 2: Share access to encrypted files In this exercise, you will first encrypt a file as the second user, grant access to the previously encrypted file to the second user, and verify that the second user at that point can access the file. The main tasks for this exercise are as follows: 1. Encrypt a file by using EFS as the second user. 2. Grant shared access to the previously encrypted file. 3. Verify that the second user can access the shared encrypted file. Task 1: Encrypt a file by using EFS as the second user 1. While signed on as the second user, create a file named File2.txt, type a random text in it, and save it in the C:\Data folder. 2. Right-click on File2.txt and select Properties from the context-sensitive menu. 3. In the Properties dialog box, click Advanced. 4. In the Advanced Attributes dialog box, enable the checkbox next to Encrypt contents to secure data. 5. Click OK. 6. Back in the Properties dialog box, click OK. 7. When prompted with the Encryption Warning dialog box, select Encrypt the file only and click OK. By encrypting a file as the second user, you generate an EFS certificate that now can be used by the first use to provide shared access to File1.txt. Task 2: Grant shared access to the previously encrypted file. 2. Sign in to the lab virtual machine with the following credentials: USERNAME:.\luser1 PASSWORD: luser1pa$$ 3. In the File Explorer and navigate to C:\Data folder. 4. Right-click on File1.txt and select Properties from the context-sensitive menu. 5. In the Properties dialog box, click Advanced. 6. In the Advanced Attributes dialog box, click Details next to Encrypt contents to secure data label.
5 7. In the User Access to File1.txt, click Add. 8. Note that you can see at this point an additional EFS certificate for luser2. Make sure it is selected and click OK. 9. Back in the User Access to File1.txt dialog box, you should at this point see both luser1 and luser2 as the users who can access the file. 10. Click OK three times to close all dialog boxes. Task 3: Verify that the second user can access the shared encrypted file. 2. Sign in to the lab virtual machine with the following credentials: USERNAME:.\luser2 PASSWORD: luser2pa$$ 3. Launch File Explorer and navigate to C:\Data folder. 4. Double click the File1.txt file. 5. Verify that you can successfully open the file. 6. Click OK and close Notepad. Results: After completing this exercise, you will have encrypted a file as the second user to generate an EFS certificate, grant shared access to the previously encrypted file as the first user, and verify that you can access that file successfully as the second user.
INF204x Module 1, Lab 3 - Configure Windows 10 VPN
 INF204x Module 1, Lab 3 - Configure Windows 10 VPN Estimated Time: 40 minutes Your organization plans to allow Windows 10 users to connect to the internal network by using the VPN client built into the
INF204x Module 1, Lab 3 - Configure Windows 10 VPN Estimated Time: 40 minutes Your organization plans to allow Windows 10 users to connect to the internal network by using the VPN client built into the
INF204x Module 1 Lab 2: Configuring and Troubleshooting Networking Part 2
 INF204x Module 1 Lab 2: Configuring and Troubleshooting Networking Part 2 Estimated Time: 60 minutes Your organization plans to expand the use of IPv6 in its existing Windows Server 2012 R2 Active Directory
INF204x Module 1 Lab 2: Configuring and Troubleshooting Networking Part 2 Estimated Time: 60 minutes Your organization plans to expand the use of IPv6 in its existing Windows Server 2012 R2 Active Directory
Module 3 Remote Desktop Gateway Estimated Time: 90 minutes
 Module 3 Remote Desktop Gateway Estimated Time: 90 minutes A. Datum Corporation provided access to web intranet web applications by implementing Web Application Proxy. Now, IT management also wants to
Module 3 Remote Desktop Gateway Estimated Time: 90 minutes A. Datum Corporation provided access to web intranet web applications by implementing Web Application Proxy. Now, IT management also wants to
This course comes with a virtual lab environment where you can practice what you learn.
 INF220x Security Practical Exercises Overview This course comes with a virtual lab environment where you can practice what you learn. In most cases, the userid is Adatum\Administrator and the password
INF220x Security Practical Exercises Overview This course comes with a virtual lab environment where you can practice what you learn. In most cases, the userid is Adatum\Administrator and the password
INF204x Module 1 Lab 1: Configuring and Troubleshooting Networking Part 1
 INF204x Module 1 Lab 1: Configuring and Troubleshooting Networking Part 1 Estimated Time: 90 minutes Your organization plans to implement IPv6 in their existing Active Directory environment including Windows
INF204x Module 1 Lab 1: Configuring and Troubleshooting Networking Part 1 Estimated Time: 90 minutes Your organization plans to implement IPv6 in their existing Active Directory environment including Windows
LAB 5 IMPLEMENTING WINDOWS IN AN ENTERPRISE ENVIRONMENT
 LAB 5 IMPLEMENTING WINDOWS IN AN ENTERPRISE ENVIRONMENT THIS LAB CONTAINS THE FOLLOWING EXERCISES AND ACTIVITIES: Exercise 5.1 Exercise 5.2 Exercise 5.3 Lab Challenge Installing the Windows Assessment
LAB 5 IMPLEMENTING WINDOWS IN AN ENTERPRISE ENVIRONMENT THIS LAB CONTAINS THE FOLLOWING EXERCISES AND ACTIVITIES: Exercise 5.1 Exercise 5.2 Exercise 5.3 Lab Challenge Installing the Windows Assessment
Module 4 Network Controller Estimated Time: 90 minutes
 Module 4 Network Controller Estimated Time: 90 minutes A. Datum Corporation intends to deploy and use Network Controller to manage network services and devices. You need to test a deployment of Network
Module 4 Network Controller Estimated Time: 90 minutes A. Datum Corporation intends to deploy and use Network Controller to manage network services and devices. You need to test a deployment of Network
List of Virtual Machines Used in This Lab
 INF204x Module 3 Lab1: Deploying Windows 10 to a New Computer by Using Microsoft Deployment Toolkit Lab: Using Microsoft Deployment Toolkit 2013 Update 1 Preview to Deploy Operating Systems Overview of
INF204x Module 3 Lab1: Deploying Windows 10 to a New Computer by Using Microsoft Deployment Toolkit Lab: Using Microsoft Deployment Toolkit 2013 Update 1 Preview to Deploy Operating Systems Overview of
Student Lab Manual MS101.1x: Microsoft 365 Security Management
 Student Lab Manual MS101.1x: Microsoft 365 Security Management Lab Scenario You are the system administrator for Adatum Corporation, and you have Microsoft 365 deployed in a virtualized lab environment.
Student Lab Manual MS101.1x: Microsoft 365 Security Management Lab Scenario You are the system administrator for Adatum Corporation, and you have Microsoft 365 deployed in a virtualized lab environment.
20411D D Enayat Meer
 Lab A Module 8: Implementing Direct Access by Using the Getting Started Wizard Scenario: Recommended lab time is 240 Minutes {a complete class session is dedicated for this lab} Many users at A. Datum
Lab A Module 8: Implementing Direct Access by Using the Getting Started Wizard Scenario: Recommended lab time is 240 Minutes {a complete class session is dedicated for this lab} Many users at A. Datum
Module 1 Web Application Proxy (WAP) Estimated Time: 120 minutes
 Module 1 Web Application Proxy (WAP) Estimated Time: 120 minutes The remote access deployment is working well at A. Datum Corporation, but IT management also wants to enable access to some internal applications
Module 1 Web Application Proxy (WAP) Estimated Time: 120 minutes The remote access deployment is working well at A. Datum Corporation, but IT management also wants to enable access to some internal applications
Course CLD211.5x Microsoft SharePoint 2016: Search and Content Management
 Course CLD211.5x Microsoft SharePoint 2016: Search and Content Management Module 1 Lab - Configure Enterprise Search Introduction This document contains the detailed, step-by-step lab instructions for
Course CLD211.5x Microsoft SharePoint 2016: Search and Content Management Module 1 Lab - Configure Enterprise Search Introduction This document contains the detailed, step-by-step lab instructions for
DOCUMENT SECURITY IN WORD 2010
 DOCUMENT SECURITY IN WORD 2010 http://www.tutorialspoint.com/word/word_document_security.htm Copyright tutorialspoint.com Microsoft Word provides a high level of security for your word generated documents.
DOCUMENT SECURITY IN WORD 2010 http://www.tutorialspoint.com/word/word_document_security.htm Copyright tutorialspoint.com Microsoft Word provides a high level of security for your word generated documents.
BitLocker to Go: Encryption for personal USB
 BitLocker to Go: Encryption for personal USB [Windows 10] Encryption is an effective method of protecting data stored on portable USB devices such as flash drives and external hard drives. Encryption encodes
BitLocker to Go: Encryption for personal USB [Windows 10] Encryption is an effective method of protecting data stored on portable USB devices such as flash drives and external hard drives. Encryption encodes
Outlook Desktop Application for Windows
 Access Your Email There are two common ways to access your mail: via the Outlook Desktop Application and the Outlook Web Application. This document focuses on how to use the Outlook Desktop Application
Access Your Email There are two common ways to access your mail: via the Outlook Desktop Application and the Outlook Web Application. This document focuses on how to use the Outlook Desktop Application
Lab: Configuring and Troubleshooting DNS
 Lab: Configuring and Troubleshooting DNS A. Datum is a global engineering and manufacturing company with its head office in London, UK. An IT office and a data center are located in London to support the
Lab: Configuring and Troubleshooting DNS A. Datum is a global engineering and manufacturing company with its head office in London, UK. An IT office and a data center are located in London to support the
Lab - System Restore in Windows 8
 Lab - System Restore in Windows 8 Introduction In this lab, you will create a restore point and use it to restore your computer. Recommended Equipment A computer running Windows 8 Step 1: Create a restore
Lab - System Restore in Windows 8 Introduction In this lab, you will create a restore point and use it to restore your computer. Recommended Equipment A computer running Windows 8 Step 1: Create a restore
Using Attix5 Pro with EFS
 Using Attix5 Pro with EFS Windows has a built-in Encrypting File System (EFS), which is a component of NTFS. It allows users to encrypt files on disk, so that only they, and users who they provide keys
Using Attix5 Pro with EFS Windows has a built-in Encrypting File System (EFS), which is a component of NTFS. It allows users to encrypt files on disk, so that only they, and users who they provide keys
CLD206x Compliance in Office 365: Data Governance
 CLD206x Compliance in Office 365: Data Governance Student Lab Manual WARNING Be prepared for Office 365 UI changes Given the dynamic nature of Microsoft cloud tools, you may experience Office 365 user
CLD206x Compliance in Office 365: Data Governance Student Lab Manual WARNING Be prepared for Office 365 UI changes Given the dynamic nature of Microsoft cloud tools, you may experience Office 365 user
Lab - Share Resources in Windows
 Introduction In this lab, you will create and share a folder, set permissions for the shares, create a Homegroup and a Workgroup to share resources, and map a network drive. Due to Windows Vista lack of
Introduction In this lab, you will create and share a folder, set permissions for the shares, create a Homegroup and a Workgroup to share resources, and map a network drive. Due to Windows Vista lack of
8 MANAGING SHARED FOLDERS & DATA
 MANAGING SHARED FOLDERS & DATA STORAGE.1 Introduction to Windows XP File Structure.1.1 File.1.2 Folder.1.3 Drives.2 Windows XP files and folders Sharing.2.1 Simple File Sharing.2.2 Levels of access to
MANAGING SHARED FOLDERS & DATA STORAGE.1 Introduction to Windows XP File Structure.1.1 File.1.2 Folder.1.3 Drives.2 Windows XP files and folders Sharing.2.1 Simple File Sharing.2.2 Levels of access to
Course CLD221x: Enabling Office 365 Clients
 Course CLD221x: Enabling Office 365 Clients Student Lab Manual Lab Design There are five exercises in this lab, each of which contains one or more tasks. For a successful outcome to the lab, the exercises
Course CLD221x: Enabling Office 365 Clients Student Lab Manual Lab Design There are five exercises in this lab, each of which contains one or more tasks. For a successful outcome to the lab, the exercises
Installing the WinSCP Secure FTP Client
 Draft 0.9 Page 1 of 6 Installing the WinSCP Secure FTP Client This document will instruct you to install the WinSCP application that will provide Secure FTP (SFTP) access to your website folder. So why
Draft 0.9 Page 1 of 6 Installing the WinSCP Secure FTP Client This document will instruct you to install the WinSCP application that will provide Secure FTP (SFTP) access to your website folder. So why
IT Essentials v6.0 Windows 10 Software Labs
 IT Essentials v6.0 Windows 10 Software Labs 5.2.1.7 Install Windows 10... 1 5.2.1.10 Check for Updates in Windows 10... 10 5.2.4.7 Create a Partition in Windows 10... 16 6.1.1.5 Task Manager in Windows
IT Essentials v6.0 Windows 10 Software Labs 5.2.1.7 Install Windows 10... 1 5.2.1.10 Check for Updates in Windows 10... 10 5.2.4.7 Create a Partition in Windows 10... 16 6.1.1.5 Task Manager in Windows
Lab - Remote Assistance in Windows
 Lab - Remote Assistance in Windows Introduction In this lab, you will remotely connect to a computer, examine device drivers, and provide remote assistance. Recommended Equipment Two Windows 7, Windows
Lab - Remote Assistance in Windows Introduction In this lab, you will remotely connect to a computer, examine device drivers, and provide remote assistance. Recommended Equipment Two Windows 7, Windows
INF220x Security Practical Exercises
 INF220x Security Practical Exercises This course comes with a virtual lab environment where you can practice what you learn. In most cases, the userid is Adatum\Administrator and the password is Pa55w.rd,
INF220x Security Practical Exercises This course comes with a virtual lab environment where you can practice what you learn. In most cases, the userid is Adatum\Administrator and the password is Pa55w.rd,
Lab - System Restore in Windows 7 and Vista
 Lab - System Restore in Windows 7 and Vista Introduction In this lab, you will create a restore point and then use it to restore your computer. Recommended Equipment A computer running Windows 7 or Vista
Lab - System Restore in Windows 7 and Vista Introduction In this lab, you will create a restore point and then use it to restore your computer. Recommended Equipment A computer running Windows 7 or Vista
Aspera Connect Windows XP, 2003, Vista, 2008, 7. Document Version: 1
 Aspera Connect 2.6.3 Windows XP, 2003, Vista, 2008, 7 Document Version: 1 2 Contents Contents Introduction... 3 Setting Up... 4 Upgrading from a Previous Version...4 Installation... 4 Set Up Network Environment...
Aspera Connect 2.6.3 Windows XP, 2003, Vista, 2008, 7 Document Version: 1 2 Contents Contents Introduction... 3 Setting Up... 4 Upgrading from a Previous Version...4 Installation... 4 Set Up Network Environment...
Downloading & Installing Audacity
 Downloading Audacity 1. Open your web browser. 2. Navigate to the following URL: http://audacity.sourceforge.net/download/ 3. The system displays the Download page for Audacity. 4. Select your operating
Downloading Audacity 1. Open your web browser. 2. Navigate to the following URL: http://audacity.sourceforge.net/download/ 3. The system displays the Download page for Audacity. 4. Select your operating
Lab B: Configuring Disk Compression and Quotas
 Module 6: Managing Data by Using NTFS 33 Lab B: Configuring Disk Compression and Quotas Topic Objective To introduce the lab. Lead-in In this lab, you will configure disk compression and quotas. *****************************ILLEGAL
Module 6: Managing Data by Using NTFS 33 Lab B: Configuring Disk Compression and Quotas Topic Objective To introduce the lab. Lead-in In this lab, you will configure disk compression and quotas. *****************************ILLEGAL
Lab 11-1 Lab User Profiles and Tracking
 In the following lab instructions, you will be setting up groups, users, and passwords to require password-protected login to Kofax Capture modules. Rights will be assigned to the groups and users that
In the following lab instructions, you will be setting up groups, users, and passwords to require password-protected login to Kofax Capture modules. Rights will be assigned to the groups and users that
Student Lab Manual MS100.1x: Office 365 Management
 Student Lab Manual MS100.1x: Office 365 Management Lab Scenario You are the system administrator for Adatum Corporation, and you have Office 365 deployed in a virtualized lab environment. In this lab,
Student Lab Manual MS100.1x: Office 365 Management Lab Scenario You are the system administrator for Adatum Corporation, and you have Office 365 deployed in a virtualized lab environment. In this lab,
Lab 3-1 Lab Installing Kofax Capture 10
 In the following lab instructions, you re going to install and license Kofax Capture, turn on User Tracking, review the product documentation, and prepare your system for the lab exercises in this course.
In the following lab instructions, you re going to install and license Kofax Capture, turn on User Tracking, review the product documentation, and prepare your system for the lab exercises in this course.
8x8 Virtual Office Salesforce Call Center Interface User Guide
 8x8 Virtual Office User Guide August 2012 The Champion For Business Communications Table of Contents 8x8 Virtual Office Salesforce Call Center App... 3 System Requirements...3 Installation... 4 Uninstalling
8x8 Virtual Office User Guide August 2012 The Champion For Business Communications Table of Contents 8x8 Virtual Office Salesforce Call Center App... 3 System Requirements...3 Installation... 4 Uninstalling
VMware AirWatch - Workspace ONE, Single Sign-on and VMware Identity Manager
 VMware AirWatch - Workspace ONE, Single Sign-on and VMware Identity Table of Contents Lab Overview - HOL-1857-03-UEM - Workspace ONE UEM with App & Access Management... 2 Lab Guidance... 3 Module 1 - Workspace
VMware AirWatch - Workspace ONE, Single Sign-on and VMware Identity Table of Contents Lab Overview - HOL-1857-03-UEM - Workspace ONE UEM with App & Access Management... 2 Lab Guidance... 3 Module 1 - Workspace
Computer Setup Guide for SEC301
 Computer Setup Guide for SEC301 This document identifies the steps you need to take to make sure that your computer is ready for the lab exercises for SEC301. Prior to coming to class you need to ensure
Computer Setup Guide for SEC301 This document identifies the steps you need to take to make sure that your computer is ready for the lab exercises for SEC301. Prior to coming to class you need to ensure
Azure for On-Premises Administrators Practice Exercises
 Azure for On-Premises Administrators Practice Exercises Overview This course includes optional practical exercises where you can try out the techniques demonstrated in the course for yourself. This guide
Azure for On-Premises Administrators Practice Exercises Overview This course includes optional practical exercises where you can try out the techniques demonstrated in the course for yourself. This guide
Byte Classic Miracle Integration Guide 7/19/07
 Miracle Integration Guide 1 Byte Classic Miracle Integration Guide 7/19/07 Byte Classic interfaces data to Miracle Online using an application provided by MRG called MRGIFace. MRGIFace is available for
Miracle Integration Guide 1 Byte Classic Miracle Integration Guide 7/19/07 Byte Classic interfaces data to Miracle Online using an application provided by MRG called MRGIFace. MRGIFace is available for
File systems security: Shared folders & NTFS permissions, EFS Disk Quotas
 File systems security: Shared folders & NTFS permissions, EFS Disk Quotas (March 23, 2016) Abdou Illia, Spring 2016 1 Learning Objective Understand Shared Folders Assign Shared Folder permissions NTFS
File systems security: Shared folders & NTFS permissions, EFS Disk Quotas (March 23, 2016) Abdou Illia, Spring 2016 1 Learning Objective Understand Shared Folders Assign Shared Folder permissions NTFS
End User Manual. December 2014 V1.0
 End User Manual December 2014 V1.0 Contents Getting Started... 4 How to Log into the Web Portal... 5 How to Manage Account Settings... 6 The Web Portal... 8 How to Upload Files in the Web Portal... 9 How
End User Manual December 2014 V1.0 Contents Getting Started... 4 How to Log into the Web Portal... 5 How to Manage Account Settings... 6 The Web Portal... 8 How to Upload Files in the Web Portal... 9 How
1) Log on to the computer using your PU net ID and password.
 CS 150 Lab Logging on: 1) Log on to the computer using your PU net ID and password. Connecting to Winter: Winter is the computer science server where all your work will be stored. Remember, after you log
CS 150 Lab Logging on: 1) Log on to the computer using your PU net ID and password. Connecting to Winter: Winter is the computer science server where all your work will be stored. Remember, after you log
5. A small dialog window appears; enter a new password twice (this is different from Dori!) and hit Go.
 Installing Wordpress from JMA Lab to JMA Server 1. Take note these instructions are streamlined for the JMA lab they can t be performed in this fashion from home! 2. Wordpress is a database driven web
Installing Wordpress from JMA Lab to JMA Server 1. Take note these instructions are streamlined for the JMA lab they can t be performed in this fashion from home! 2. Wordpress is a database driven web
Manual UCSFwpa Configuration for Windows 7
 Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > Manual UCSFwpa Configuration for Windows 7 Manual UCSFwpa
Image not found https://it.ucsf.edu/sites/it.ucsf.edu/themes/custom/it_new/logo.png it.ucsf.edu Published on it.ucsf.edu (https://it.ucsf.edu) Home > Manual UCSFwpa Configuration for Windows 7 Manual UCSFwpa
Wireless Setup Instructions for Windows 7
 Wireless Setup Instructions for Windows 7 1. Make sure that your wireless feature is turned on. (You may need to flip a switch or press a button on your laptop.) On most laptops you should see a light
Wireless Setup Instructions for Windows 7 1. Make sure that your wireless feature is turned on. (You may need to flip a switch or press a button on your laptop.) On most laptops you should see a light
SharePoint General Instructions
 SharePoint General Instructions Table of Content What is GC Drive?... 2 Access GC Drive... 2 Navigate GC Drive... 2 View and Edit My Profile... 3 OneDrive for Business... 3 What is OneDrive for Business...
SharePoint General Instructions Table of Content What is GC Drive?... 2 Access GC Drive... 2 Navigate GC Drive... 2 View and Edit My Profile... 3 OneDrive for Business... 3 What is OneDrive for Business...
SIU s Secure App (XenMobile) Migration for Android
 SIU s Secure App (XenMobile) Migration for Android The version of the XenMobile we are currently using has reached its end of support lifespan. In order to maintain support for XenMobile and the associated
SIU s Secure App (XenMobile) Migration for Android The version of the XenMobile we are currently using has reached its end of support lifespan. In order to maintain support for XenMobile and the associated
SharePoint 2013 Power User EVALUATION COPY. (SHP version 1.0.1) Copyright Information. Copyright 2013 Webucator. All rights reserved.
 SharePoint 2013 Power User (SHP2013.2 version 1.0.1) Copyright Information Copyright 2013 Webucator. All rights reserved. The Authors Bruce Gordon Bruce Gordon has been a Microsoft Certified Trainer since
SharePoint 2013 Power User (SHP2013.2 version 1.0.1) Copyright Information Copyright 2013 Webucator. All rights reserved. The Authors Bruce Gordon Bruce Gordon has been a Microsoft Certified Trainer since
Status Web Evaluator s Guide Software Pursuits, Inc.
 Status Web Evaluator s Guide 2018 Table of Contents Introduction... 2 System Requirements... 2 Contact Information... 2 Installing Microsoft IIS... 2 Verifying Microsoft IIS Features... 9 Installing the
Status Web Evaluator s Guide 2018 Table of Contents Introduction... 2 System Requirements... 2 Contact Information... 2 Installing Microsoft IIS... 2 Verifying Microsoft IIS Features... 9 Installing the
Windows 2000 Disk Management
 LAB PROCEDURE 25 Windows 2000 Disk Management OBJECTIVES 1. Use Disk Cleanup. 2. Backup a file. 3. Restore a backup. 4. Compress a file. 5. Encrypt a file. Troubleshooting RESOURCES 1. Marcraft 8000 Trainer
LAB PROCEDURE 25 Windows 2000 Disk Management OBJECTIVES 1. Use Disk Cleanup. 2. Backup a file. 3. Restore a backup. 4. Compress a file. 5. Encrypt a file. Troubleshooting RESOURCES 1. Marcraft 8000 Trainer
Module 10: Denial of Service
 Module 10: Denial of Service Objective The objective of this lab is to help students learn to perform Denial of Service attacks and to test network for Denial of Service flaws. In this lab, you will: Create
Module 10: Denial of Service Objective The objective of this lab is to help students learn to perform Denial of Service attacks and to test network for Denial of Service flaws. In this lab, you will: Create
How to make a Work Profile for Windows 10
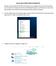 How to make a Work Profile for Windows 10 Setting up a new profile for Windows 10 requires you to navigate some screens that may lead you to create the wrong type of account. By following this guide, we
How to make a Work Profile for Windows 10 Setting up a new profile for Windows 10 requires you to navigate some screens that may lead you to create the wrong type of account. By following this guide, we
Azure 209x Practical Exercises Overview
 Azure 209x Practical Exercises Overview This course includes optional exercises where you can try out the techniques demonstrated in the course for yourself. This guide lists the steps for the individual
Azure 209x Practical Exercises Overview This course includes optional exercises where you can try out the techniques demonstrated in the course for yourself. This guide lists the steps for the individual
Getting Started with Cisco WebEx Meeting Applications
 CHAPTER 6 Getting Started with Cisco WebEx Meeting Applications Revised: September, 2010, Contents Modifying Your Provisioned Cisco WebEx Account, page 6-1 Setting Proxy Permissions, page 6-5 Productivity
CHAPTER 6 Getting Started with Cisco WebEx Meeting Applications Revised: September, 2010, Contents Modifying Your Provisioned Cisco WebEx Account, page 6-1 Setting Proxy Permissions, page 6-5 Productivity
VMware AirWatch: Directory and Certificate Authority
 Table of Contents Lab Overview - HOL-1857-06-UEM - VMware AirWatch: Directory and Certificate Authority Integration... 2 Lab Guidance... 3 Module 1 - Advanced AirWatch Configuration, AD Integration/Certificates
Table of Contents Lab Overview - HOL-1857-06-UEM - VMware AirWatch: Directory and Certificate Authority Integration... 2 Lab Guidance... 3 Module 1 - Advanced AirWatch Configuration, AD Integration/Certificates
Fleet Manager 2002 Professional Network Configuration Guide
 Handling a complex world. Fleet Manager 2002 Professional Network Configuration Guide Overview The VDO Fleet Manager Professional utilises an advanced three-tier client-server model and is designed to
Handling a complex world. Fleet Manager 2002 Professional Network Configuration Guide Overview The VDO Fleet Manager Professional utilises an advanced three-tier client-server model and is designed to
Abila MIP DrillPoint Reports. Installation Guide
 Abila MIP DrillPoint Reports This is a publication of Abila, Inc. Version 16.1 2015 Abila, Inc. and its affiliated entities. All rights reserved. Abila, the Abila logos, and the Abila product and service
Abila MIP DrillPoint Reports This is a publication of Abila, Inc. Version 16.1 2015 Abila, Inc. and its affiliated entities. All rights reserved. Abila, the Abila logos, and the Abila product and service
Module Overview. Instructor Notes (PPT Text)
 Module 12 - Deploying and Configuring SSIS Packages Page 1 Module Overview Instructor Notes (PPT Text) Microsoft SQL Server Integration Services (SSIS) provides tools that make it easy to deploy packages
Module 12 - Deploying and Configuring SSIS Packages Page 1 Module Overview Instructor Notes (PPT Text) Microsoft SQL Server Integration Services (SSIS) provides tools that make it easy to deploy packages
Pontem Check for Updates Guide
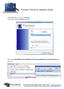 Pontem Check for Updates Guide STEP ONE: Back Up Your Database Log into your Pontem database as usual.. Next, select File Maintenance Backup for the Pontem application you wish to back up from the menu.
Pontem Check for Updates Guide STEP ONE: Back Up Your Database Log into your Pontem database as usual.. Next, select File Maintenance Backup for the Pontem application you wish to back up from the menu.
LAB MANUAL. Craig Zacker.
 Free ebooks ==> www.ebook777.com LAB MANUAL Craig Zacker www.ebook777.com Free ebooks ==> www.ebook777.com www.ebook777.com This page is intentionally left blank Free ebooks ==> www.ebook777.com Installing
Free ebooks ==> www.ebook777.com LAB MANUAL Craig Zacker www.ebook777.com Free ebooks ==> www.ebook777.com www.ebook777.com This page is intentionally left blank Free ebooks ==> www.ebook777.com Installing
MyNIC Team Site - Document Sharing
 Table of Contents Create a Document...2 Upload a Document...3 Rename Document...4 Edit a Document...6 Check-out a Document...6 Edit a Document...7 Check-in a Document...9 Check-in Someone Else s Document...
Table of Contents Create a Document...2 Upload a Document...3 Rename Document...4 Edit a Document...6 Check-out a Document...6 Edit a Document...7 Check-in a Document...9 Check-in Someone Else s Document...
You can also check the videos at the bottom of this page:
 This document is provided to give you an idea what R-Tag Version Control can do and how you can use it. If you decide that you need more information or you prefer to see a demo of the software please do
This document is provided to give you an idea what R-Tag Version Control can do and how you can use it. If you decide that you need more information or you prefer to see a demo of the software please do
Windows quick start instructions Pg. 1. OS X quick start instructions Pg. 4. ios quick start instructions Pg. 6
 Page 1 of 12 Windows quick start instructions Pg. 1 OS X quick start instructions Pg. 4 ios quick start instructions Pg. 6 Android quick start instructions Pg. 9 Windows Quick Start Instructions STEP 1
Page 1 of 12 Windows quick start instructions Pg. 1 OS X quick start instructions Pg. 4 ios quick start instructions Pg. 6 Android quick start instructions Pg. 9 Windows Quick Start Instructions STEP 1
PST for Outlook Admin Guide
 PST for Outlook 2013 Admin Guide Document Revision Date: Sept. 25, 2015 PST Admin for Outlook 2013 1 Populating Your Exchange Mailbox/Importing and Exporting.PST Files Use this guide to import data (Emails,
PST for Outlook 2013 Admin Guide Document Revision Date: Sept. 25, 2015 PST Admin for Outlook 2013 1 Populating Your Exchange Mailbox/Importing and Exporting.PST Files Use this guide to import data (Emails,
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE. 31 January 2017
 BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
BROWSER-BASED SUPPORT CONSOLE USER S GUIDE 31 January 2017 Contents 1 Introduction... 2 2 Netop Host Configuration... 2 2.1 Connecting through HTTPS using Certificates... 3 2.1.1 Self-signed certificate...
Demonstration Instructions
 Demonstration Instructions Digital Defence Ltd. Secure Mobile Version 10.2.1 19 th July 2010 Table of Contents TABLE OF CONTENTS... 2 1. DEMONSTRATION INSTRUCTIONS... 3 1.1 PREREQUISITES... 3 1.2 PROCEDURE...
Demonstration Instructions Digital Defence Ltd. Secure Mobile Version 10.2.1 19 th July 2010 Table of Contents TABLE OF CONTENTS... 2 1. DEMONSTRATION INSTRUCTIONS... 3 1.1 PREREQUISITES... 3 1.2 PROCEDURE...
Detailed Installation Guide
 Detailed Installation Guide ShopOps is a human resource, process management, and organizational system. As an easy to use web-based application, focused on the infrastructure of your business. ShopOps
Detailed Installation Guide ShopOps is a human resource, process management, and organizational system. As an easy to use web-based application, focused on the infrastructure of your business. ShopOps
In most cases, the userid is Adatum\Administrator and the password is Pa55w.rd, but read the instructions carefully.
 INF219x Advanced Virtualization Practical Exercises Overview This course comes with a virtual lab environment where you can practice what you learn. Launch the lab environment from the Welcome > Getting
INF219x Advanced Virtualization Practical Exercises Overview This course comes with a virtual lab environment where you can practice what you learn. Launch the lab environment from the Welcome > Getting
Connecting to the NJITSecure wireless network.
 Connecting to the NJITSecure wireless network. 1. Start by going to the Start menu and selecting Control Panel 2. Your control Panel will most likely be in Category view, you will need to change it to
Connecting to the NJITSecure wireless network. 1. Start by going to the Start menu and selecting Control Panel 2. Your control Panel will most likely be in Category view, you will need to change it to
Configuring File Server Resource Manager (FSRM)
 Configuring File Server Resource Manager (FSRM) LESSON 5 70-411 EXAM OBJECTIVE Objective 2.2 Configure File Server Resource Manager (FSRM). This objective may include but is not limited to: install the
Configuring File Server Resource Manager (FSRM) LESSON 5 70-411 EXAM OBJECTIVE Objective 2.2 Configure File Server Resource Manager (FSRM). This objective may include but is not limited to: install the
How to Install, Configure and Use sftp (Windows Version)
 How to Install, Configure and Use sftp (Windows Version) The sftp secure File Transfer Protocol allows you to transfer patient datasets to and from IDT s server securely. All data transfers are encrypted
How to Install, Configure and Use sftp (Windows Version) The sftp secure File Transfer Protocol allows you to transfer patient datasets to and from IDT s server securely. All data transfers are encrypted
Connect to Wireless, certificate install and setup Citrix Receiver
 Connect to Wireless, certificate install and setup Citrix Receiver This document explains how to connect to the Wireless Network and access applications using Citrix Receiver on a Bring Your Own Device
Connect to Wireless, certificate install and setup Citrix Receiver This document explains how to connect to the Wireless Network and access applications using Citrix Receiver on a Bring Your Own Device
KG-TOWER Software Download and Installation Instructions
 KG-TOWER Software Download and Installation Instructions Procedures are provided for three options to download and install KG-TOWER software version 5.1. Download to a temporary folder and install immediately.
KG-TOWER Software Download and Installation Instructions Procedures are provided for three options to download and install KG-TOWER software version 5.1. Download to a temporary folder and install immediately.
User Guide. BlackBerry Workspaces for Windows. Version 5.5
 User Guide BlackBerry Workspaces for Windows Version 5.5 Published: 2017-03-30 SWD-20170330110027321 Contents Introducing BlackBerry Workspaces for Windows... 6 Getting Started... 7 Setting up and installing
User Guide BlackBerry Workspaces for Windows Version 5.5 Published: 2017-03-30 SWD-20170330110027321 Contents Introducing BlackBerry Workspaces for Windows... 6 Getting Started... 7 Setting up and installing
Getting Started with BarTender
 Getting Started with BarTender MANUAL Contents Getting Started with BarTender 3 Installation 4 Choosing What to Install 4 Automation Editions (Automation and Enterprise Automation) 4 Installing BarTender
Getting Started with BarTender MANUAL Contents Getting Started with BarTender 3 Installation 4 Choosing What to Install 4 Automation Editions (Automation and Enterprise Automation) 4 Installing BarTender
Mobile Inventory Tracking & Sales Management Software. Installation Procedure
 Mobile Inventory Tracking & Sales Management Software Installation Procedure Tecom Group, Inc. 2016 Hello! Thank you for choosing HandiFox an award-winning Inventory Tracking and Sales Management solution.
Mobile Inventory Tracking & Sales Management Software Installation Procedure Tecom Group, Inc. 2016 Hello! Thank you for choosing HandiFox an award-winning Inventory Tracking and Sales Management solution.
APP NOTES Onsight Rugged Smart Camera Wireless Network Configuration
 APP NOTES Onsight Rugged Smart Camera Wireless Network Configuration July 2016 Table of Contents 1. Overview... 4 1.1 Onsight Setup Wizard... 4 1.2 Onsight Wireless Manual Setup... 4 1.3 Hotspot Login...
APP NOTES Onsight Rugged Smart Camera Wireless Network Configuration July 2016 Table of Contents 1. Overview... 4 1.1 Onsight Setup Wizard... 4 1.2 Onsight Wireless Manual Setup... 4 1.3 Hotspot Login...
ASSA ABLOY. CLIQ Connect PC Application User Manual
 ASSA ABLOY CLIQ Connect PC Application User Manual Table of Contents 1 INTRODUCTION... 3 2 VERSIONS... 3 2.1 CLIQ Web Manager/Remote... 3 2.2 Key Firmware... 3 2.3 Microsoft Windows... 3 3 INSTALLATION...
ASSA ABLOY CLIQ Connect PC Application User Manual Table of Contents 1 INTRODUCTION... 3 2 VERSIONS... 3 2.1 CLIQ Web Manager/Remote... 3 2.2 Key Firmware... 3 2.3 Microsoft Windows... 3 3 INSTALLATION...
Please click on the appropriate link to navigate through the available solutions:
 Error with your Java/UCF configuration: User Guide Updated: 08/11/2015 **NOTE: The limit is 8 Files/200MB for Import/Checkin and 20 Files/400MB for Export/Checkout. This File Transfer solution is Java-free
Error with your Java/UCF configuration: User Guide Updated: 08/11/2015 **NOTE: The limit is 8 Files/200MB for Import/Checkin and 20 Files/400MB for Export/Checkout. This File Transfer solution is Java-free
ms-help://ms.technet.2004apr.1033/win2ksrv/tnoffline/prodtechnol/win2ksrv/howto/efsguide.htm
 Page 1 of 14 Windows 2000 Server Step-by-Step Guide to Encrypting File System (EFS) Abstract This document provides sample procedures that demonstrate the end-user and administrative capabilities of the
Page 1 of 14 Windows 2000 Server Step-by-Step Guide to Encrypting File System (EFS) Abstract This document provides sample procedures that demonstrate the end-user and administrative capabilities of the
This course comes with a virtual lab environment where you can practice what you learn.
 INF220x Security Practical Exercises Overview This course comes with a virtual lab environment where you can practice what you learn. In most cases, the userid is Adatum\Administrator and the password
INF220x Security Practical Exercises Overview This course comes with a virtual lab environment where you can practice what you learn. In most cases, the userid is Adatum\Administrator and the password
DSS User Guide. End User Guide. - i -
 DSS User Guide End User Guide - i - DSS User Guide Table of Contents End User Guide... 1 Table of Contents... 2 Part 1: Getting Started... 1 How to Log in to the Web Portal... 1 How to Manage Account Settings...
DSS User Guide End User Guide - i - DSS User Guide Table of Contents End User Guide... 1 Table of Contents... 2 Part 1: Getting Started... 1 How to Log in to the Web Portal... 1 How to Manage Account Settings...
Windows Server 2012 Immersion Experience Enabling Secure Remote Users with RemoteApp, DirectAccess, and Dynamic Access Control
 Windows Server 2012 Immersion Experience Enabling Secure Remote Users with RemoteApp, DirectAccess, and Dynamic Access Control Windows Server 2012 Hands-on lab In this experience, you will configure a
Windows Server 2012 Immersion Experience Enabling Secure Remote Users with RemoteApp, DirectAccess, and Dynamic Access Control Windows Server 2012 Hands-on lab In this experience, you will configure a
OTC Student Wireless Network
 OTC Student Wireless Network (Connection Instructions for Windows 8, Windows 7, MAC OSX, ios and Kindle) Note: The OTC student wireless network conforms to the IEEE 802.11 a/b/g protocol and standards.
OTC Student Wireless Network (Connection Instructions for Windows 8, Windows 7, MAC OSX, ios and Kindle) Note: The OTC student wireless network conforms to the IEEE 802.11 a/b/g protocol and standards.
Installation Guide. Last Revision: Oct 03, Page 1-
 Installation Guide Last Revision: Oct 03, 2005 -Page 1- Contents Before You Begin... 2 Installation Overview... 2 Installation for Microsoft Windows 2000, Windows 2003, and Windows XP Professional... 3
Installation Guide Last Revision: Oct 03, 2005 -Page 1- Contents Before You Begin... 2 Installation Overview... 2 Installation for Microsoft Windows 2000, Windows 2003, and Windows XP Professional... 3
GIAC Introduction to Security Fundamentals. Laptop and External Drive Configuration Guide Version 1.1 SEC301
 GIAC Introduction to Security Fundamentals Laptop and External Drive Configuration Guide Version 1.1 SEC301 SEC301 - Hands-on Exercises Addendum Page 1 Table of Contents Background... 3 Create a local
GIAC Introduction to Security Fundamentals Laptop and External Drive Configuration Guide Version 1.1 SEC301 SEC301 - Hands-on Exercises Addendum Page 1 Table of Contents Background... 3 Create a local
Using Expressions Web to Edit an FCNet Department Web Site
 Using Expressions Web to Edit an FCNet Department Web Site Here are the steps to open and edit a site on the new FcWebDept shared department web site server using Microsoft Expression Web 4. The steps
Using Expressions Web to Edit an FCNet Department Web Site Here are the steps to open and edit a site on the new FcWebDept shared department web site server using Microsoft Expression Web 4. The steps
Pacific Premier Bank s Business e- Banking Getting Started Guide With QuickBooks for Mac
 Pacific Premier Bank s Business e- Banking Getting Started Guide With QuickBooks 2013-2015 for Mac Table of Contents SET UP AN ACCOUNT FOR ONLINE BANKING (DIRECT CONNECT)... 2 SET UP AN ACCOUNT FOR ONLINE
Pacific Premier Bank s Business e- Banking Getting Started Guide With QuickBooks 2013-2015 for Mac Table of Contents SET UP AN ACCOUNT FOR ONLINE BANKING (DIRECT CONNECT)... 2 SET UP AN ACCOUNT FOR ONLINE
Practice and Review Activities Software
 Practice and Review Activities Software Installation and Setup Procedure Reading Mastery Signature Edition Corrective Reading Installation Insert the Practice and Review Activities CD-ROM into the CD/DVD
Practice and Review Activities Software Installation and Setup Procedure Reading Mastery Signature Edition Corrective Reading Installation Insert the Practice and Review Activities CD-ROM into the CD/DVD
Storing Your Exercise Files
 Storing Your Exercise Files This appendix contains an overview for using this book with various file storage media, such as a USB flash drive or hard drive. Detailed instructions for downloading and unzipping
Storing Your Exercise Files This appendix contains an overview for using this book with various file storage media, such as a USB flash drive or hard drive. Detailed instructions for downloading and unzipping
Application Notes for Telephonetics IP Messaging Utility with Avaya IP Office 9.0 using Avaya Voic Pro Issue 1.0
 Avaya Solution & Interoperability Test Lab Application Notes for Telephonetics IP Messaging Utility with Avaya IP Office 9.0 using Avaya Voicemail Pro Issue 1.0 Abstract These Application Notes describe
Avaya Solution & Interoperability Test Lab Application Notes for Telephonetics IP Messaging Utility with Avaya IP Office 9.0 using Avaya Voicemail Pro Issue 1.0 Abstract These Application Notes describe
ms-help://ms.technet.2004apr.1033/ad/tnoffline/prodtechnol/ad/windows2000/howto/mapcerts.htm
 Page 1 of 8 Active Directory Step-by-Step Guide to Mapping Certificates to User Accounts Introduction The Windows 2000 operating system provides a rich administrative model for managing user accounts.
Page 1 of 8 Active Directory Step-by-Step Guide to Mapping Certificates to User Accounts Introduction The Windows 2000 operating system provides a rich administrative model for managing user accounts.
LiveNX Upgrade Guide from v5.1.2 to v Windows
 LIVEACTION, INC. LiveNX Upgrade Guide from v5.1.2 to v5.1.3 - Windows UPGRADE LiveAction, Inc. 3500 Copyright WEST BAYSHORE 2016 LiveAction, ROAD Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the
LIVEACTION, INC. LiveNX Upgrade Guide from v5.1.2 to v5.1.3 - Windows UPGRADE LiveAction, Inc. 3500 Copyright WEST BAYSHORE 2016 LiveAction, ROAD Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the
Implementing Messaging Security for Exchange Server Clients
 Implementing Messaging Security for Exchange Server Clients Objectives Scenario At the end of this lab, you will be able to: Protect e-mail messages using S/MIME signing and encryption Manage e-mail attachment
Implementing Messaging Security for Exchange Server Clients Objectives Scenario At the end of this lab, you will be able to: Protect e-mail messages using S/MIME signing and encryption Manage e-mail attachment
How to use Microsoft OneDrive
 How to use Microsoft OneDrive Instructions for Saint Paul College Students Table of Content What is OneDrive?... 2 How do I access OneDrive?... 2 How do I upload documents to OneDrive?... 3 How do I create
How to use Microsoft OneDrive Instructions for Saint Paul College Students Table of Content What is OneDrive?... 2 How do I access OneDrive?... 2 How do I upload documents to OneDrive?... 3 How do I create
Desktop & Laptop Edition
 Desktop & Laptop Edition USER MANUAL For Mac OS X Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Mac, Leopard, Snow Leopard, Lion and Mountain Lion
Desktop & Laptop Edition USER MANUAL For Mac OS X Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Mac, Leopard, Snow Leopard, Lion and Mountain Lion
Remote Deposit. Getting Started Guide
 Remote Deposit Getting Started Guide Table of Contents Introduction... 3 Minimum System Requirements... 3 Direct Merchant Smart Deposit Installation Instructions... 6 Multi-Factor Authentication Enrollment...
Remote Deposit Getting Started Guide Table of Contents Introduction... 3 Minimum System Requirements... 3 Direct Merchant Smart Deposit Installation Instructions... 6 Multi-Factor Authentication Enrollment...
Business Insights Dashboard
 Business Insights Dashboard Sage 500 ERP 2000-2013 Sage Software, Inc. All rights reserved. Sage, the Sage logos, and the Sage product and service names mentioned herein are registered trademarks or trademarks
Business Insights Dashboard Sage 500 ERP 2000-2013 Sage Software, Inc. All rights reserved. Sage, the Sage logos, and the Sage product and service names mentioned herein are registered trademarks or trademarks
Hill s Pet Nutrition Admin Center Guide
 Table of Contents 1 Introduction... 3 1.1 Background... 3 1.2 User Types/Roles... 3 1.3 General Navigation... 3 1.3.1 Sign In... 3 1.3.2 Sign Out... 5 1.3.3 Role Navigation... 5 2 Supervisor Role... 7
Table of Contents 1 Introduction... 3 1.1 Background... 3 1.2 User Types/Roles... 3 1.3 General Navigation... 3 1.3.1 Sign In... 3 1.3.2 Sign Out... 5 1.3.3 Role Navigation... 5 2 Supervisor Role... 7
Create MedicCoin Master Node Instruction Rev2
 Create MedicCoin Master Node Instruction Rev2 1. Download MedicCoin wallet using below link https://mediccoin.com/mediccoin-window.zip 2. Unzip/extract MedicCoin-Window.zip to C:\coins\MedicCoin folder.
Create MedicCoin Master Node Instruction Rev2 1. Download MedicCoin wallet using below link https://mediccoin.com/mediccoin-window.zip 2. Unzip/extract MedicCoin-Window.zip to C:\coins\MedicCoin folder.
Files.Kennesaw.Edu. Kennesaw State University Information Technology Services. Introduces. Presented by the ITS Technology Outreach Team
 Kennesaw State University Information Technology Services Introduces Files.Kennesaw.Edu Presented by the ITS Technology Outreach Team Last Updated 08/12/13 Powered by Xythos Copyright 2006, Xythos Software
Kennesaw State University Information Technology Services Introduces Files.Kennesaw.Edu Presented by the ITS Technology Outreach Team Last Updated 08/12/13 Powered by Xythos Copyright 2006, Xythos Software
