Data mining doesn t have official rules. You have tremendous flexibility
|
|
|
- Merryl Haynes
- 5 years ago
- Views:
Transcription
1 Chapter 5 Embracing the Data-Mining Process In This Chapter Establishing a framework for data mining Drilling into the CRISP-DM process Establishing good habits Data mining doesn t have official rules. You have tremendous flexibility to define and refine your own work methods. Still, you ll find benefits to understanding and following the approaches that work well for others. The Cross-Industry Standard Process for Data Mining (CRISP-DM) is the dominant process framework for data mining. It s an open standard; anyone may use it. This chapter explains each phase of the process. Whose Standard Is It, Anyway? The CRISP-DM process model is a step-by-step approach to data mining that was created by data miners for data miners. Participants from over 200 organizations (mainly a diverse group of businesses with an interest in using data mining internally or in promoting far-reaching use of data mining) provided input to develop the framework, which outlines key data-mining tasks in business terms and leaves users free to make their own choices about specific mathematical and computational approaches, and other technical matters. The explanation of the CRISP-DM process in this chapter follows the original published version very closely. However, differences exist, such as changes in terminology or a diagram, intended to make the information clearer for datamining novices. Also, the explanations in this book are briefer and lighter in style. If you would like to read the undiluted original (all 76 pages of it in small print), you can get it online (for free) at
2 74 Part II: Exploring Data-Mining Mantras and Methods ftp://ftp.software.ibm.com/software/analytics/spss/support/modeler/ Documentation/14/UserManual/CRISP-DM.pdf Approaching the process in phases The CRISP-DM process model has six primary phases. These are 1. Business understanding: Get a clear understanding of the problem you re out to solve, how it impacts your organization, and your goals for addressing it. 2. Data understanding: Review the data that you have, document it, and identify data management and data quality issues. 3. Data preparation: Get your data ready to use for modeling. 4. Modeling: Use mathematical techniques to identify patterns within your data. 5. Evaluation: Review the patterns you have discovered and assess their potential for business use. 6. Deployment: Put your discoveries to work in everyday business. Each of these phases involves several major tasks, and each task calls for several deliverables primarily reports that summarize the work done and the information learned in that phase of the data-mining process. However, CRISP-DM does not define templates for these deliverables. You must plan and create them to suit the specific needs and style of your own workplace. CRISP-DM defines the data-mining process primarily from a business standpoint. It tells you a lot about what you need to do, but it doesn t lay out all the technical details. Cycling through phases and projects Data mining is not something you do once and then forget. It s an ongoing cycle of activity. In any given project, you may address just a small element of a large and important problem, but you ll come back to that problem again and again with new projects. Because your work can also be applied to new projects, you ll revisit your past projects often, to see whether the models you developed in the past are still effective and to look for opportunities to improve on what you ve done. Recycling your work in this way minimizes effort and helps you avoid confusion.
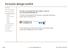
3 Chapter 5: Embracing the Data-Mining Process 75 The CRISP-DM process model (not a mathematical model, but a set of guidelines for data-mining work) is a cycle often represented by a diagram like the one shown in Figure 5-1. Each project begins with business understanding and steps through each of the five phases of the process. Within the cycle, you find smaller cycles, so you may make several passes back and forth as you work to understand the business and the data, or to prepare data and build models. The cycle repeats as your project evaluation and experience during deployment add to your understanding of the business and inspire new projects. Figure 5-1: The CRISP-DM process model. Documenting your work When you are in the midst of a project, deeply involved with your data and the issues you ve set out to address, you can easily get so familiar with the details that they seem obvious. You may not write things down because you
4 76 Part II: Exploring Data-Mining Mantras and Methods don t see any need. Later, though, when you ve moved on to other projects, spent time thinking about different datasets and different issues, and then returned to this project, you ll find that these details aren t obvious at all. You ll wonder what your sparse notes mean, be unsure of exactly where and how you got and prepared the data, and find other holes in your information. Inadequate documentation leads to many problems. You may end up repeating work, and making others repeat work as well. You may fail to detect errors in your work. Your management or coworkers may become frustrated (and even angry) if you haven t prepared the documentation that they need. Failure to document your reasons for making certain decisions, or the proof that you met data privacy obligations, may even have legal consequences. That s why much of the CRISP-DM process model is focused on reports and other documents that data miners create in the process of their work. These documents are your means of preserving information about what you ve done so that you and others won t have to wonder later. Business Understanding In the first phase of a data-mining project, before you approach data or tools, you define what you re out to accomplish and define the reasons for wanting to achieve this goal. The business understanding phase includes four tasks (primary activities, each of which may involve several smaller parts). These are Identifying your business goals Assessing your situation Defining your data-mining goals Producing your project plan Task: Identifying your business goals The first thing you must do in any project is to find out exactly what you re trying to accomplish! That s less obvious than it sounds. Many data miners have invested time on data analysis, only to find that their management wasn t particularly interested in the issue they were investigating. You must start with a clear understanding of A problem that your management wants to address The business goals
5 Chapter 5: Embracing the Data-Mining Process 77 Constraints (limitations on what you may do, the kinds of solutions that can be used, when the work must be completed, and so on) Impact (how the problem and possible solutions fit in with the business) Deliverables for this task include three items (usually brief reports focusing on just the main points): Background: Explain the business situation that drives the project. This item, like many that follow, amounts only to a few paragraphs. Here s an example of a Background item: Our client, a regional planning commission, seeks to influence property use to enhance the quality of life for local residents. The planning commission has a broad charter which allows it to consider wide-ranging issues including employment, recreation, environment, and many other aspects of community life; however, the commission s role is purely advisory. It has a great deal of latitude to select issues for study, conduct research, and make policy recommendations to local lawmakers and staff, but does not have independent power to set regulations or influence property owners. Commission members (and others in local government and civic organizations) believe the best opportunity to influence property use occurs when the property changes hands. This implies that local government planning efforts can achieve greatest impact by focusing on properties which are about to change ownership. This poses a problem: the best time to act is before property changes hands, but the local government doesn t have dependable information about which properties are likely to be transferred. (Commercial real estate listings may be useful, but they do not cover all property transfers, and the best time to act may be before the property is listed.) Earlier research has identified a number of factors believed to indicate impending change of ownership; these include nonlocal ownership, multiple building code violations, and foreclosure, among others. While commissioners have good reason to believe that these factors influence the likelihood of property to change hands, their effects have not been quantified. Business goals: Define what your organization intends to accomplish with the project. This is usually a broader goal than you, as a data miner, can accomplish independently. For example, the business goal might be to increase sales from a holiday ad campaign by 10 percent year over year. Business success criteria: Define how the results will be measured. Try to get clearly defined quantitative success criteria. If you must use subjective criteria (hint: terms like gain insight or get a handle on imply subjective criteria), at least get agreement on exactly who will judge whether or not those criteria have been fulfilled.
6 78 Part II: Exploring Data-Mining Mantras and Methods Task: Assessing your situation This is where you get into more detail on the issues associated with your business goals. Now you will go deeper into fact-finding, building out a much fleshier explanation of the issues outlined in the business goals task. Deliverables for this task include five in-depth reports: Inventory of resources: A list of all resources available for the project. These may include people (not just data miners, but also those with expert knowledge of the business problem, data managers, technical support, and others), data, hardware, and software. Requirements, assumptions, and constraints: Requirements will include a schedule for completion, legal and security obligations, and requirements for acceptable finished work. This is the point to verify that you ll have access to appropriate data! Risks and contingencies: Identify causes that could delay completion of the project, and prepare a contingency plan for each of them. For example, if an Internet outage in your office could pose a problem, perhaps your contingency could be to work at another office until the outage has ended. Terminology: Create a list of business terms and data-mining terms that are relevant to your project and write them down in a glossary with definitions (and perhaps examples), so that everyone involved in the project can have a common understanding of those terms. Costs and benefits: Prepare a cost-benefit analysis for the project. Try to state all costs and benefits in dollar (euro, pound, yen, and so on) terms. If the benefits don t significantly exceed the costs, stop and reconsider this analysis and your project. Decision makers often feel more comfortable allotting resources to projects that reduce costs than those that aim to increase revenue, so always look for cost-savings potential, and state savings opportunities first in your costs and benefits report. Task: Defining your data-mining goals Reaching the business goal often requires action from many people, not just the data miner. So now, you must define your little part within the bigger picture. If the business goal is to reduce customer attrition, for example, your data-mining goals might be to identify attrition rates for several customer segments, and develop models to predict which customers are at greatest risk.
7 Chapter 5: Embracing the Data-Mining Process 79 Deliverables for this task include two reports: Data-mining goals: Define data-mining deliverables, such as models, reports, presentations, and processed datasets. Data-mining success criteria: Define the data-mining technical criteria necessary to support the business success criteria. Try to define these in quantitative terms (such as model accuracy or predictive improvement compared to an existing method). If the criteria must be qualitative, identify the person who makes the assessment. Task: Producing your project plan Now you specify every step that you, the data miner, intend to take until the project is completed and the results are presented and reviewed. Deliverables for this task include two reports: Project plan: Outline your step-by-step action plan for the project. Expand the outline with a schedule for completion of each step, required resources, inputs (such as data or a meeting with a subject matter expert), and outputs (such as cleaned data, a model, or a report) for each step, and dependencies (steps that can t begin until this step is completed). Explicitly state that certain steps must be repeated (for example, modeling and evaluation usually call for several back-and-forth repetitions). Initial assessment of tools and techniques: Identify the required capabilities for meeting your data-mining goals and assess the tools and resources that you have. If something is missing, you have to address that concern very early in the process. Data Understanding In the second phase of a data-mining project, conducted after you have defined goals and made a plan, you obtain data and verify that it is appropriate for your needs. You might identify issues that cause you to return to business understanding and revise your plan. You may even discover flaws in your business understanding, another reason to rethink goals and plans. The data-understanding phase includes four tasks. These are Gathering data Describing data Exploring data Verifying data quality
8 80 Part II: Exploring Data-Mining Mantras and Methods Task: Gathering data You ve just set goals and defined a data-mining plan. Every step of the plan depends on having the right data. Better make sure that you really have that data! Just one deliverable exists for this task: the initial data collection report. In your report, you need to verify that you have acquired the data or at least gained access to the data, tested the data access process, and verified that the data exists. You ll also need to load data into any tools that you will be using for data mining to verify that the tools are compatible with the data. You may do a lot of work to assemble the data you need before you can write this report. First, you will make your plan, as follows: Outline data requirements: Create a list of the types of data necessary to address the data mining goals. Expand the list with details such as the required time range and data formats. Verify data availability: Confirm that the required data exists, and that you can use it. If some of the data you want is unavailable, decide how you will address that issue. Consider alternatives such as Substituting with an alternative data source Narrowing the scope of the project Gathering new data Define selection criteria: Identify the specific data sources (databases, files, documents, and so on.) you will use. Within those sources, specify the tables, fields, and case ranges that are relevant to this project. Once you ve gone through these steps, you must actually obtain the data. At this stage, import the data into the data-mining platform you ll be using for the project to confirm that it is possible to do so and that you understand the process. In the course of this trial you may discover software (or hardware) limitations you had not anticipated, such as Limits on the number of cases or fields, or on the amount of memory you may use Inability to read the data formats of your sources Difficulty dealing with imperfections in the data (for example, you might encounter products that won t import or analyze incomplete datasets) Finally, summarize the gathering process in a report. The report should describe your requirements, and explain in some detail exactly what data you have gathered and from what sources. Here you confirm that you have
9 Chapter 5: Embracing the Data-Mining Process 81 actually obtained the data and that it is compatible with your data-mining platform. If you have run into difficulties, you ll explain what they were and how you have addressed them (using alternative sources, revising plans, changing formats). The deliverable for this task is just a simple report, but the work that you need to do before you can write that report won t be simple! Data access can be one of the most challenging and frustrating parts of the data-mining process, rife with both technical and business challenges. Task: Describing data Now that you have data, prepare a general description of what you have. The deliverable for this task is the data description report. In it, you describe the source and formats of the data, the number of cases, the number and descriptions of the fields, and any other general information that may be important. You also make a brief evaluation of the suitability of the data for your data-mining goals. For example, verify that the data includes the fields that you expect and need to be there and sufficient cases for analysis. Task: Exploring data In this task, you examine the data more closely. For each variable, you look at the range of values and their distributions. You ll use simple data manipulation and basic statistical techniques for further checks into the data. Data exploration supports several purposes: Get familiar with the data. Spot signs of data quality problems. Set the stage for data preparation steps. The deliverable for this task is the data exploration report. It s the place to document any hypotheses or initial findings that you have developed during data exploration. This report should include a more detailed description of the data than the data description report, including distributions, summaries, and any signs of data quality problems. Task: Verifying data quality You have the data and you ve examined it, and now you have to determine whether it s good enough to support your goals. You will often have some quality problem to address yet still be able to move forward, but at times the data quality is so poor that it cannot support your plan and you ll have to look for alternatives. Some of the worst data problems would include The data you need doesn t exist. (Did it never exist, or was it discarded? Can this data be collected and saved for future use?)
10 82 Part II: Exploring Data-Mining Mantras and Methods It exists, but you can t have it. (Can this restriction be overcome?) You find severe data quality issues (lots of missing or incorrect values that can t be corrected). The deliverable for this task is the data quality report. This summarizes the data that you have, minor and major quality issues that you have found, and possible remedies for quality problems or alternatives (such as using an alternative data resource). If you are facing any really serious data quality issues and can t identify an adequate solution, you may have to recommend reconsidering goals or plans. Data Preparation Data miners spend most of their time on the third phase of the data-mining process: data preparation. Most data used for data mining was originally collected and preserved for other purposes and needs some refinement before it is ready to use for modeling. The data preparation phase includes five tasks. These are Selecting data Cleaning data Constructing data Integrating data Formatting data The CRISP-DM step-by-step guide does not explicitly mention datasets as deliverables for each of the data preparation tasks, but those datasets had darn well better exist and be properly archived and documented. Datasets won t correspond one-to-one with tasks, but information about the data used should be included in each deliverable report. Task: Selecting data Now you will decide which portion of the data that you have is actually going to be used for data mining. The deliverable for this task is the rationale for inclusion and exclusion. In it, you ll explain what data will, and will not, be used for further data-mining work. You ll explain the reasons for including or excluding each part of the data that you have, based on relevance to your goals, data quality, and technical issues such as limits to the number of fields or rows that your tools can handle, or the suitability of the data formats for your needs.
11 Chapter 5: Embracing the Data-Mining Process 83 Task: Cleaning data The data that you ve chosen to use is unlikely to be perfectly clean (errorfree). You ll make changes, perhaps tracking down sources to make specific data corrections, excluding some cases or individual cells (items of data), or replacing some items of data with default values or replacements selected by a more sophisticated modeling technique. You may choose to use only subsets of the data for all or some of your data-mining work. The deliverable for this task is the data-cleaning report, which documents, in excruciating detail, every decision and action used to clean your data. This report should cover and refer to each data quality problem that was identified in the verify data quality task in the data-understanding phase of the process. You report should also address the potential impact on results of the choices you have made during data cleaning. Task: Constructing data You may need to derive some new fields (for example, use the delivery date and the date when a customer placed an order to calculate how long the customer waited to receive an order), aggregate data, or otherwise create a new form of data. Deliverables for this task include two reports: Derived attributes: A report that describes what new fields (columns) you have constructed, how you did it, and why. Generated records: A report that describes what new cases (rows) you have constructed, how you did it, and why. Although the merge data and format data tasks are listed last in this phase of the process, they don t always come last, and they may not come up just once. You might have to do some merging or reformatting early in the data preparation phase. Task: Integrating data Your data may now be in several disparate datasets. You ll need to merge some or all of those disparate datasets together to get ready for the modeling phase. The deliverable for this task is the merged data. (And it would not hurt to document how the merge was performed.) Task: Formatting data Data often comes to you in formats other than the ones that are most convenient for modeling. (Format changes are usually driven by the design of your tools.) So convert those formats now.
12 84 Part II: Exploring Data-Mining Mantras and Methods The deliverable for this task is your reformatted data. (And a little report describing the changes you have made would be a smart thing to include.) You should end the data preparation phase of the data-mining process with a dataset ready for modeling and a thorough report describing the dataset. Modeling This is the part of the process that most data miners like best. Your data is already in good shape, and now you can search for useful patterns in your data. The modeling phase includes four tasks. These are Selecting modeling techniques Designing test(s) Building model(s) Assessing model(s) Task: Selecting modeling techniques The wonderful world of data mining offers oodles of modeling techniques, but not all of them will suit your needs. Narrow the list based on the kinds of variables involved, the selection of techniques available in your tools, and any business considerations that are important to you. (For example, many organizations favor methods with output that s easy to interpret, so decision trees or logistic regression might be acceptable, but neural networks would probably not be accepted.) Deliverables for this task include two reports: Modeling technique: Specify the technique(s) that you will use. Modeling assumptions: Many modeling techniques are based on certain assumptions. For example, a model type may be intended for use with data that has a specific type of distribution. Document these assumptions in this report. Statisticians are well-informed, strict, and fussy about assumptions. That s not necessarily true of data miners, and it s not a requirement to become a data miner. If you have deep statistical knowledge and understand the assumptions behind the models you select, you can be strict and fussy about assumptions. But many data miners, especially novice data miners, don t fuss much over assumptions. The alternative is testing lots and lots of testing of your models.
13 Chapter 5: Embracing the Data-Mining Process 85 Task: Designing tests The test in this task is the test that you ll use to determine how well your model works. It may be as simple as splitting your data into a group of cases for model training and another group for model testing. Training data is used to fit mathematical forms to the data model, and test data is used during the model-training process to avoid overfitting: making a model that s perfect for one dataset, but no other. You may also use holdout data, data that is not used during the model-training process, for an additional test. The deliverable for this task is your test design. It need not be elaborate, but you should at least take care that your training and test data are similar and that you avoid introducing any bias into the data. Task: Building model(s) Modeling is what many people imagine to be the whole job of the data miner, but it s just one task of dozens! Nonetheless, modeling to address specific business goals is the heart of the data-mining profession. Deliverables for this task include three items: Parameter settings: When building models, most tools give you the option of adjusting a variety of settings, and these settings have an impact on the structure of the final model. Document these settings in a report. Model descriptions: Describe your models. State the type of model (such as linear regression or neural network) and the variables used. Explain how the model is interpreted. Document any difficulties encountered in the modeling process. Models: This deliverable is the models themselves. Some model types can be easily defined with a simple equation; others are far too complex and must be transmitted in a more sophisticated format. Task: Assessing model(s) Now you will review the models that you ve created, from a technical standpoint and also from a business standpoint (often with input from business experts on your project team). Deliverables for this task include two reports: Model assessment: Summarizes the information developed in your model review. If you have created several models, you may rank them based on your assessment of their value for a specific application. Revised parameter settings: You may choose to fine-tune settings that were used to build the model and conduct another round of modeling and try to improve your results.
14 86 Part II: Exploring Data-Mining Mantras and Methods Data mining, like an onion, a Dobos torte, or a sedimentary rock, has lots of layers. When you are just getting started in data mining, you can start by leaving parameter settings at their default values (in fact, you might not even notice options unless you make an effort to look for them). As you get comfortable in your new data-mining career, it will make sense for you to find out about model parameters and know how you can use them. Your options will vary widely with the type of model and specific tool that you are using. The details are beyond the scope of this book, so when you are ready, refer to Chapter 19 for information about resources for discovering more about data mining. Evaluation You ve explored data and you ve found patterns, and now you have to ask: Are the results any good? You ll evaluate not just the models you create but also the process that you used to create them, and their potential for practical use. The data-understanding phase includes three tasks. These are Evaluating results Reviewing the process Determining the next steps Task: Evaluating results At this stage, you ll assess the value of your models for meeting the business goals that started the data-mining process. You ll look for any reasons why the model would not be satisfactory for business use. If possible, you ll test the model in a practical application, to determine whether it works as well in the workplace as it did in your tests. Deliverables for this task include two items: Assessment of results (for business goals): Summarize the results with respect to the business success criteria that you established in the business-understanding phase. Explicitly state whether you have reached the business goals defined at the start of the project. Approved models: These include any models that meet the business success criteria.
15 Chapter 5: Embracing the Data-Mining Process 87 Task: Reviewing the process Now that you have explored data and developed models, take time to review your process. This is an opportunity to spot issues that you might have overlooked and that might draw your attention to flaws in the work that you ve done while you still have time to correct the problem before deployment. Also consider ways that you might improve your process for future projects. The deliverable for this task is the review of process report. In it, you should outline your review process and findings and highlight any concerns that require immediate attention, such as steps that were overlooked or that should be revisited. Task: Determining the next steps The evaluation phase concludes with your recommendations for the next move. The model may be ready to deploy, or you may judge that it would be better to repeat some steps and try to improve it. Your findings may inspire new data-mining projects. Deliverables for this task include two items: List of possible actions: Describe each alternative action, along with the strongest reasons for and against it. Decision: State the final decision on each possible action, along with the reasoning behind the decision. Deployment Deployment is where data mining pays off. It doesn t matter how brilliant your discoveries may be, or how perfectly your models fit the data, if you don t actually use those things to improve the way that you do business. The deployment phase includes four tasks. These are Planning deployment (your methods for integrating data-mining discoveries into use) Planning monitoring and maintenance Reporting final results Reviewing final results
16 88 Part II: Exploring Data-Mining Mantras and Methods Task: Planning deployment When your model is ready to use, you will need a strategy for putting it to work in your business. The deliverable for this task is the deployment plan. This is a summary of your strategy for deployment, the steps required, and the instructions for carrying out those steps. Task: Planning monitoring and maintenance Data-mining work is a cycle, so expect to stay actively involved with your models as they are integrated into everyday use. The deliverable for this task is the monitoring and maintenance plan. This is a summary of your strategy for ongoing review of the model s performance. You ll need to assure that it is being used properly on an ongoing basis, and that any decline in model performance will be detected. Task: Reporting final results Deliverables for this task include two items: Final report: The final report summarizes the entire project by assembling all the reports created up to this point, and adding an overview summarizing the entire project and its results. Final presentation: A summary of the final report is presented in a meeting with management. This is also an opportunity to address any open questions. Task: Review project Finally, the data-mining team meets to discuss what worked and what didn t, what would be good to do again, and what should be avoided! This step, too, has a deliverable, although it is only for the use of the datamining team, not the manager (or client). It s the experience documentation report. This is where you should outline any work methods that worked particularly well, so that they are documented to use again in the future, and any improvements that might be made to your process. It s also the place to document problems and bad experiences, with your recommendations for avoiding similar problems in the future. Data mining is a team activity. So if this process seems to include a lot of steps, realize that it may not be your personal responsibility to do every one of them, and that it s always appropriate to ask for help from others when you need it. (At the start of the project, you made a list of people who are resources for the data-mining project. That s your little directory of helpers!)
The CRISP-DM Process Model
 CRISP-DM Discussion Paper March, 1999 The CRISP-DM Process Model Pete Chapman (NCR) Julian Clinton (SPSS) Thomas Khabaza (SPSS) Thomas Reinartz (DaimlerChrysler) Rüdiger Wirth (DaimlerChrysler) This discussion
CRISP-DM Discussion Paper March, 1999 The CRISP-DM Process Model Pete Chapman (NCR) Julian Clinton (SPSS) Thomas Khabaza (SPSS) Thomas Reinartz (DaimlerChrysler) Rüdiger Wirth (DaimlerChrysler) This discussion
Business Process Outsourcing
 Business Process Outsourcing Copyright 2012-2014, AdminBetter Inc. LIST BUILDING SERVICES Table of Contents Introduction To List Building Services... 3 A Note On Ballbark Pricing... 3 Types Of List Building
Business Process Outsourcing Copyright 2012-2014, AdminBetter Inc. LIST BUILDING SERVICES Table of Contents Introduction To List Building Services... 3 A Note On Ballbark Pricing... 3 Types Of List Building
The Data Center Migration Methodology Phase 2: Discovery
 White Paper The Data Center Migration Methodology Phase 2: Discovery The Manual for Successful Migrations 2011-2016 by David-Kenneth Group. All rights reserved Discovery is a challenging process in every
White Paper The Data Center Migration Methodology Phase 2: Discovery The Manual for Successful Migrations 2011-2016 by David-Kenneth Group. All rights reserved Discovery is a challenging process in every
ASTQB Advance Test Analyst Sample Exam Answer Key and Rationale
 ASTQB Advance Test Analyst Sample Exam Answer Key and Rationale Total number points = 120 points Total number points to pass = 78 points Question Answer Explanation / Rationale Learning 1 A A is correct.
ASTQB Advance Test Analyst Sample Exam Answer Key and Rationale Total number points = 120 points Total number points to pass = 78 points Question Answer Explanation / Rationale Learning 1 A A is correct.
VIDEO 1: WHY IS THE USER EXPERIENCE CRITICAL TO CONTEXTUAL MARKETING?
 VIDEO 1: WHY IS THE USER EXPERIENCE CRITICAL TO CONTEXTUAL MARKETING? Hello again! I m Angela with HubSpot Academy. In this class, you re going to learn about the user experience. Why is the user experience
VIDEO 1: WHY IS THE USER EXPERIENCE CRITICAL TO CONTEXTUAL MARKETING? Hello again! I m Angela with HubSpot Academy. In this class, you re going to learn about the user experience. Why is the user experience
Divisibility Rules and Their Explanations
 Divisibility Rules and Their Explanations Increase Your Number Sense These divisibility rules apply to determining the divisibility of a positive integer (1, 2, 3, ) by another positive integer or 0 (although
Divisibility Rules and Their Explanations Increase Your Number Sense These divisibility rules apply to determining the divisibility of a positive integer (1, 2, 3, ) by another positive integer or 0 (although
RightNow Technologies Best Practices Implementation Guide. RightNow Technologies, Inc.
 RightNow Technologies Best Practices Implementation Guide RightNow Technologies, Inc. www.rightnow.com http://rightnow.custhelp.com Welcome Welcome to the RightNow Technologies Best Practice Implementation
RightNow Technologies Best Practices Implementation Guide RightNow Technologies, Inc. www.rightnow.com http://rightnow.custhelp.com Welcome Welcome to the RightNow Technologies Best Practice Implementation
The data quality trends report
 Report The 2015 email data quality trends report How organizations today are managing and using email Table of contents: Summary...1 Research methodology...1 Key findings...2 Email collection and database
Report The 2015 email data quality trends report How organizations today are managing and using email Table of contents: Summary...1 Research methodology...1 Key findings...2 Email collection and database
Introduction to Software Testing
 Introduction to Software Testing Software Testing This paper provides an introduction to software testing. It serves as a tutorial for developers who are new to formal testing of software, and as a reminder
Introduction to Software Testing Software Testing This paper provides an introduction to software testing. It serves as a tutorial for developers who are new to formal testing of software, and as a reminder
Cognitive Walkthrough Evaluation
 Columbia University Libraries / Information Services Digital Library Collections (Beta) Cognitive Walkthrough Evaluation by Michael Benowitz Pratt Institute, School of Library and Information Science Executive
Columbia University Libraries / Information Services Digital Library Collections (Beta) Cognitive Walkthrough Evaluation by Michael Benowitz Pratt Institute, School of Library and Information Science Executive
CATCH ERRORS BEFORE THEY HAPPEN. Lessons for a mature data governance practice
 CATCH ERRORS BEFORE THEY HAPPEN Lessons for a mature data governance practice A guide to working with cross-departmental teams to establish proactive data governance for your website or mobile app. 2 Robust
CATCH ERRORS BEFORE THEY HAPPEN Lessons for a mature data governance practice A guide to working with cross-departmental teams to establish proactive data governance for your website or mobile app. 2 Robust
Special Report. What to test (and how) to increase your ROI today
 Special Report What to test (and how) to A well-designed test can produce an impressive return on investment. Of course, you may face several obstacles to producing that well-designed test to begin with.
Special Report What to test (and how) to A well-designed test can produce an impressive return on investment. Of course, you may face several obstacles to producing that well-designed test to begin with.
Up and Running Software The Development Process
 Up and Running Software The Development Process Success Determination, Adaptative Processes, and a Baseline Approach About This Document: Thank you for requesting more information about Up and Running
Up and Running Software The Development Process Success Determination, Adaptative Processes, and a Baseline Approach About This Document: Thank you for requesting more information about Up and Running
The power management skills gap
 The power management skills gap Do you have the knowledge and expertise to keep energy flowing around your datacentre environment? A recent survey by Freeform Dynamics of 320 senior data centre professionals
The power management skills gap Do you have the knowledge and expertise to keep energy flowing around your datacentre environment? A recent survey by Freeform Dynamics of 320 senior data centre professionals
. social? better than. 7 reasons why you should focus on . to GROW YOUR BUSINESS...
 Is EMAIL better than social? 7 reasons why you should focus on email to GROW YOUR BUSINESS... 1 EMAIL UPDATES ARE A BETTER USE OF YOUR TIME If you had to choose between sending an email and updating your
Is EMAIL better than social? 7 reasons why you should focus on email to GROW YOUR BUSINESS... 1 EMAIL UPDATES ARE A BETTER USE OF YOUR TIME If you had to choose between sending an email and updating your
Excel programmers develop two basic types of spreadsheets: spreadsheets
 Bonus Chapter 1 Creating Excel Applications for Others In This Chapter Developing spreadsheets for yourself and for other people Knowing what makes a good spreadsheet application Using guidelines for developing
Bonus Chapter 1 Creating Excel Applications for Others In This Chapter Developing spreadsheets for yourself and for other people Knowing what makes a good spreadsheet application Using guidelines for developing
COMP6471 WINTER User-Centered Design
 COMP6471 WINTER 2003 User-Centered Design Instructor: Shahriar Ameri, Ph.D. Student: Pedro Maroun Eid, ID# 5041872. Date of Submission: Monday, March 10, 2003. (Week 9) Outline Outline... 2 ABSTRACT...3
COMP6471 WINTER 2003 User-Centered Design Instructor: Shahriar Ameri, Ph.D. Student: Pedro Maroun Eid, ID# 5041872. Date of Submission: Monday, March 10, 2003. (Week 9) Outline Outline... 2 ABSTRACT...3
BETA DEMO SCENARIO - ATTRITION IBM Corporation
 BETA DEMO SCENARIO - ATTRITION 1 Please Note: IBM s statements regarding its plans, directions, and intent are subject to change or withdrawal without notice at IBM s sole discretion. Information regarding
BETA DEMO SCENARIO - ATTRITION 1 Please Note: IBM s statements regarding its plans, directions, and intent are subject to change or withdrawal without notice at IBM s sole discretion. Information regarding
Frequently Asked Questions about the NDIS
 Frequently Asked Questions about the NDIS Contents 3 4 5 5 5 5 6 6 7 7 8 8 8 8 8 9 9 9 9 9 10 10 10 10 11 11 11 11 12 12 12 12 13 13 13 14 14 What is the NDIS and how is it different to current funding
Frequently Asked Questions about the NDIS Contents 3 4 5 5 5 5 6 6 7 7 8 8 8 8 8 9 9 9 9 9 10 10 10 10 11 11 11 11 12 12 12 12 13 13 13 14 14 What is the NDIS and how is it different to current funding
IBM Atlas Suite Users Guide: Data Source Definition. for IBM Atlas Suite v6.0
 IBM Atlas Suite Users Guide: Data Source Definition for IBM Atlas Suite v6.0 IBM Atlas Suite Users Guide: Data Source Definition This edition applies to version 6.0 of IBM Atlas Suite (product numbers
IBM Atlas Suite Users Guide: Data Source Definition for IBM Atlas Suite v6.0 IBM Atlas Suite Users Guide: Data Source Definition This edition applies to version 6.0 of IBM Atlas Suite (product numbers
Note: In the presentation I should have said "baby registry" instead of "bridal registry," see
 Q-and-A from the Data-Mining Webinar Note: In the presentation I should have said "baby registry" instead of "bridal registry," see http://www.target.com/babyregistryportalview Q: You mentioned the 'Big
Q-and-A from the Data-Mining Webinar Note: In the presentation I should have said "baby registry" instead of "bridal registry," see http://www.target.com/babyregistryportalview Q: You mentioned the 'Big
Perfect Timing. Alejandra Pardo : Manager Andrew Emrazian : Testing Brant Nielsen : Design Eric Budd : Documentation
 Perfect Timing Alejandra Pardo : Manager Andrew Emrazian : Testing Brant Nielsen : Design Eric Budd : Documentation Problem & Solution College students do their best to plan out their daily tasks, but
Perfect Timing Alejandra Pardo : Manager Andrew Emrazian : Testing Brant Nielsen : Design Eric Budd : Documentation Problem & Solution College students do their best to plan out their daily tasks, but
Foundation Level Syllabus Usability Tester Sample Exam Answers
 Foundation Level Syllabus Usability Tester Sample Exam s Version 2017 Provided by German Testing Board Copyright Notice This document may be copied in its entirety, or extracts made, if the source is acknowledged.
Foundation Level Syllabus Usability Tester Sample Exam s Version 2017 Provided by German Testing Board Copyright Notice This document may be copied in its entirety, or extracts made, if the source is acknowledged.
THE CYBERSECURITY LITERACY CONFIDENCE GAP
 CONFIDENCE: SECURED WHITE PAPER THE CYBERSECURITY LITERACY CONFIDENCE GAP ADVANCED THREAT PROTECTION, SECURITY AND COMPLIANCE Despite the fact that most organizations are more aware of cybersecurity risks
CONFIDENCE: SECURED WHITE PAPER THE CYBERSECURITY LITERACY CONFIDENCE GAP ADVANCED THREAT PROTECTION, SECURITY AND COMPLIANCE Despite the fact that most organizations are more aware of cybersecurity risks
FIVE BEST PRACTICES FOR ENSURING A SUCCESSFUL SQL SERVER MIGRATION
 FIVE BEST PRACTICES FOR ENSURING A SUCCESSFUL SQL SERVER MIGRATION The process of planning and executing SQL Server migrations can be complex and risk-prone. This is a case where the right approach and
FIVE BEST PRACTICES FOR ENSURING A SUCCESSFUL SQL SERVER MIGRATION The process of planning and executing SQL Server migrations can be complex and risk-prone. This is a case where the right approach and
SAPtips. Journal. Creating a Well-Developed Master Data Management Solution in BW. August/September 2005 Volume III Issue 4. SAPtips.
 Page 1 Creating a Well-Developed Master Data Management Solution in BW By Arthur Pat Pesa, arthurpesa, inc Editor Note: Pat Pesa delivers another one-two-three punch with his discussion of developing,
Page 1 Creating a Well-Developed Master Data Management Solution in BW By Arthur Pat Pesa, arthurpesa, inc Editor Note: Pat Pesa delivers another one-two-three punch with his discussion of developing,
Business Requirements Document (BRD) Template
 Business Requirements Document (BRD) Template Following is a template for a business requirements document (BRD). The document includes many best practices in use today. Don t be limited by the template,
Business Requirements Document (BRD) Template Following is a template for a business requirements document (BRD). The document includes many best practices in use today. Don t be limited by the template,
WITH INTEGRITY
 EMAIL WITH INTEGRITY Reaching for inboxes in a world of spam a white paper by: www.oprius.com Table of Contents... Introduction 1 Defining Spam 2 How Spam Affects Your Earnings 3 Double Opt-In Versus Single
EMAIL WITH INTEGRITY Reaching for inboxes in a world of spam a white paper by: www.oprius.com Table of Contents... Introduction 1 Defining Spam 2 How Spam Affects Your Earnings 3 Double Opt-In Versus Single
MIS5206-Section Protecting Information Assets-Exam 1
 Your Name Date 1. Which of the following contains general approaches that also provide the necessary flexibility in the event of unforeseen circumstances? a. Policies b. Standards c. Procedures d. Guidelines
Your Name Date 1. Which of the following contains general approaches that also provide the necessary flexibility in the event of unforeseen circumstances? a. Policies b. Standards c. Procedures d. Guidelines
This PDF was generated from the Evaluate section of
 Toolkit home What is inclusive design? Why do inclusive design? How to design inclusively Overview Map of key activities Manage This PDF was generated from the Evaluate section of www.inclusivedesigntoolkit.com
Toolkit home What is inclusive design? Why do inclusive design? How to design inclusively Overview Map of key activities Manage This PDF was generated from the Evaluate section of www.inclusivedesigntoolkit.com
CPSC 444 Project Milestone III: Prototyping & Experiment Design Feb 6, 2018
 CPSC 444 Project Milestone III: Prototyping & Experiment Design Feb 6, 2018 OVERVIEW... 2 SUMMARY OF MILESTONE III DELIVERABLES... 2 1. Blog Update #3 - Low-fidelity Prototyping & Cognitive Walkthrough,
CPSC 444 Project Milestone III: Prototyping & Experiment Design Feb 6, 2018 OVERVIEW... 2 SUMMARY OF MILESTONE III DELIVERABLES... 2 1. Blog Update #3 - Low-fidelity Prototyping & Cognitive Walkthrough,
Introduction to Access 97/2000
 Introduction to Access 97/2000 PowerPoint Presentation Notes Slide 1 Introduction to Databases (Title Slide) Slide 2 Workshop Ground Rules Slide 3 Objectives Here are our objectives for the day. By the
Introduction to Access 97/2000 PowerPoint Presentation Notes Slide 1 Introduction to Databases (Title Slide) Slide 2 Workshop Ground Rules Slide 3 Objectives Here are our objectives for the day. By the
Introduction to Programming
 CHAPTER 1 Introduction to Programming Begin at the beginning, and go on till you come to the end: then stop. This method of telling a story is as good today as it was when the King of Hearts prescribed
CHAPTER 1 Introduction to Programming Begin at the beginning, and go on till you come to the end: then stop. This method of telling a story is as good today as it was when the King of Hearts prescribed
DISASTER RECOVERY PRIMER
 DISASTER RECOVERY PRIMER 1 Site Faliure Occurs Power Faliure / Virus Outbreak / ISP / Ransomware / Multiple Servers Sample Disaster Recovery Process Site Faliure Data Centre 1: Primary Data Centre Data
DISASTER RECOVERY PRIMER 1 Site Faliure Occurs Power Faliure / Virus Outbreak / ISP / Ransomware / Multiple Servers Sample Disaster Recovery Process Site Faliure Data Centre 1: Primary Data Centre Data
Good Technology State of BYOD Report
 Good Technology State of BYOD Report New data finds Finance and Healthcare industries dominate BYOD picture and that users are willing to pay device and service plan costs if they can use their own devices
Good Technology State of BYOD Report New data finds Finance and Healthcare industries dominate BYOD picture and that users are willing to pay device and service plan costs if they can use their own devices
One of the fundamental kinds of websites that SharePoint 2010 allows
 Chapter 1 Getting to Know Your Team Site In This Chapter Requesting a new team site and opening it in the browser Participating in a team site Changing your team site s home page One of the fundamental
Chapter 1 Getting to Know Your Team Site In This Chapter Requesting a new team site and opening it in the browser Participating in a team site Changing your team site s home page One of the fundamental
10 Tips For Effective Content
 10 Tips For Effective Email Content Nowadays when it comes to online marketing, and the Internet as a whole, so many people are being added to so many email lists. They're being bombarded constantly by
10 Tips For Effective Email Content Nowadays when it comes to online marketing, and the Internet as a whole, so many people are being added to so many email lists. They're being bombarded constantly by
Worksheet Answer Key: Scanning and Mapping Projects > Mine Mapping > Investigation 2
 Worksheet Answer Key: Scanning and Mapping Projects > Mine Mapping > Investigation 2 Ruler Graph: Analyze your graph 1. Examine the shape formed by the connected dots. i. Does the connected graph create
Worksheet Answer Key: Scanning and Mapping Projects > Mine Mapping > Investigation 2 Ruler Graph: Analyze your graph 1. Examine the shape formed by the connected dots. i. Does the connected graph create
QA Best Practices: A training that cultivates skills for delivering quality systems
 QA Best Practices: A training that cultivates skills for delivering quality systems Dixie Neilson QA Supervisor Lynn Worm QA Supervisor Maheen Imam QA Analyst Information Technology for Minnesota Government
QA Best Practices: A training that cultivates skills for delivering quality systems Dixie Neilson QA Supervisor Lynn Worm QA Supervisor Maheen Imam QA Analyst Information Technology for Minnesota Government
SharePoint 2010 Site Owner s Manual by Yvonne M. Harryman
 SharePoint 2010 Site Owner s Manual by Yvonne M. Harryman Chapter 9 Copyright 2012 Manning Publications Brief contents PART 1 GETTING STARTED WITH SHAREPOINT 1 1 Leveraging the power of SharePoint 3 2
SharePoint 2010 Site Owner s Manual by Yvonne M. Harryman Chapter 9 Copyright 2012 Manning Publications Brief contents PART 1 GETTING STARTED WITH SHAREPOINT 1 1 Leveraging the power of SharePoint 3 2
THE OFFICIAL (ISC)2 GUIDE TO THE CCSP CBK FROM SYBEX DOWNLOAD EBOOK : THE OFFICIAL (ISC)2 GUIDE TO THE CCSP CBK FROM SYBEX PDF
 Read Online and Download Ebook THE OFFICIAL (ISC)2 GUIDE TO THE CCSP CBK FROM SYBEX DOWNLOAD EBOOK : THE OFFICIAL (ISC)2 GUIDE TO THE CCSP CBK FROM Click link bellow and free register to download ebook:
Read Online and Download Ebook THE OFFICIAL (ISC)2 GUIDE TO THE CCSP CBK FROM SYBEX DOWNLOAD EBOOK : THE OFFICIAL (ISC)2 GUIDE TO THE CCSP CBK FROM Click link bellow and free register to download ebook:
The IDN Variant TLD Program: Updated Program Plan 23 August 2012
 The IDN Variant TLD Program: Updated Program Plan 23 August 2012 Table of Contents Project Background... 2 The IDN Variant TLD Program... 2 Revised Program Plan, Projects and Timeline:... 3 Communication
The IDN Variant TLD Program: Updated Program Plan 23 August 2012 Table of Contents Project Background... 2 The IDN Variant TLD Program... 2 Revised Program Plan, Projects and Timeline:... 3 Communication
Lecture 23: Domain-Driven Design (Part 1)
 1 Lecture 23: Domain-Driven Design (Part 1) Kenneth M. Anderson Object-Oriented Analysis and Design CSCI 6448 - Spring Semester, 2005 2 Goals for this lecture Introduce the main concepts of Domain-Driven
1 Lecture 23: Domain-Driven Design (Part 1) Kenneth M. Anderson Object-Oriented Analysis and Design CSCI 6448 - Spring Semester, 2005 2 Goals for this lecture Introduce the main concepts of Domain-Driven
Public Meeting Agenda Formatting Best Practices
 DEFINITIVE GUIDE Public Meeting Agenda Formatting Best Practices In this guide, we will first walk you through some best practices with text and images. Then, we will show you how to execute the best practices
DEFINITIVE GUIDE Public Meeting Agenda Formatting Best Practices In this guide, we will first walk you through some best practices with text and images. Then, we will show you how to execute the best practices
List Building Income
 List Building Income How to Build a Virtual Empire of Recurring Customers for Passive Income! Module 01: How to Create an Easy, Proven System to Suck in Leads Important Learning Advisory: To experience
List Building Income How to Build a Virtual Empire of Recurring Customers for Passive Income! Module 01: How to Create an Easy, Proven System to Suck in Leads Important Learning Advisory: To experience
WHITE PAPER. The General Data Protection Regulation: What Title It Means and How SAS Data Management Can Help
 WHITE PAPER The General Data Protection Regulation: What Title It Means and How SAS Data Management Can Help ii Contents Personal Data Defined... 1 Why the GDPR Is Such a Big Deal... 2 Are You Ready?...
WHITE PAPER The General Data Protection Regulation: What Title It Means and How SAS Data Management Can Help ii Contents Personal Data Defined... 1 Why the GDPR Is Such a Big Deal... 2 Are You Ready?...
Project Collaboration
 Bonus Chapter 8 Project Collaboration It s quite ironic that the last bonus chapter of this book contains information that many of you will need to get your first Autodesk Revit Architecture project off
Bonus Chapter 8 Project Collaboration It s quite ironic that the last bonus chapter of this book contains information that many of you will need to get your first Autodesk Revit Architecture project off
CHAPTER 18: CLIENT COMMUNICATION
 CHAPTER 18: CLIENT COMMUNICATION Chapter outline When to communicate with clients What modes of communication to use How much to communicate How to benefit from client communication Understanding your
CHAPTER 18: CLIENT COMMUNICATION Chapter outline When to communicate with clients What modes of communication to use How much to communicate How to benefit from client communication Understanding your
QUADCORECHAIN. White Paper ver.1
 QUADCORECHAIN White Paper ver.1 INTRO QuadCoreChain is designed to be a smart contract, crypto currency platform, decentralizing Live Streaming of Video. The platform ecosystem is to create favorable conditions
QUADCORECHAIN White Paper ver.1 INTRO QuadCoreChain is designed to be a smart contract, crypto currency platform, decentralizing Live Streaming of Video. The platform ecosystem is to create favorable conditions
OE-PM Project Charter Document
 Enter Project Name Here Enter Department Name OE-PM Project Charter Document Status: (Draft or Published) Version: (0.# or 1.#) Prepared by: Date Created: Date Last Revised: OE-PM Artifact ID: P01.00 Internal
Enter Project Name Here Enter Department Name OE-PM Project Charter Document Status: (Draft or Published) Version: (0.# or 1.#) Prepared by: Date Created: Date Last Revised: OE-PM Artifact ID: P01.00 Internal
2009 by Minitab Inc. All rights reserved. Release 3.1, January 2009 Minitab, Quality Companion by Minitab, the Minitab logo, and Quality Trainer by
 2009 by Minitab Inc. All rights reserved. Release 3.1, January 2009 Minitab, Quality Companion by Minitab, the Minitab logo, and Quality Trainer by Minitab are registered trademarks of Minitab, Inc. in
2009 by Minitab Inc. All rights reserved. Release 3.1, January 2009 Minitab, Quality Companion by Minitab, the Minitab logo, and Quality Trainer by Minitab are registered trademarks of Minitab, Inc. in
Topic C. Communicating the Precision of Measured Numbers
 Topic C. Communicating the Precision of Measured Numbers C. page 1 of 14 Topic C. Communicating the Precision of Measured Numbers This topic includes Section 1. Reporting measurements Section 2. Rounding
Topic C. Communicating the Precision of Measured Numbers C. page 1 of 14 Topic C. Communicating the Precision of Measured Numbers This topic includes Section 1. Reporting measurements Section 2. Rounding
Five Steps to Faster Data Classification
 CONTENTS OF THIS WHITE PAPER Unstructured Data Challenge... 1 Classifying Unstructured Data... 1 Faster, More Successful Data Classification... 2 Identify Data Owners... 2 Define Data of Interest... 3
CONTENTS OF THIS WHITE PAPER Unstructured Data Challenge... 1 Classifying Unstructured Data... 1 Faster, More Successful Data Classification... 2 Identify Data Owners... 2 Define Data of Interest... 3
ARCHIVE ESSENTIALS: Key Considerations When Moving to Office 365 DISCUSSION PAPER
 EMAIL ARCHIVE ESSENTIALS: Key Considerations When Moving to Office 365 DISCUSSION PAPER preface The last few years have seen significant changes in the way organisations conduct business. There has been
EMAIL ARCHIVE ESSENTIALS: Key Considerations When Moving to Office 365 DISCUSSION PAPER preface The last few years have seen significant changes in the way organisations conduct business. There has been
Usability Tests and Heuristic Reviews Planning and Estimation Worksheets
 For STC DC Usability SIG Planning and Estimation Worksheets Scott McDaniel Senior Interaction Designer 26 February, 2003 Eval_Design_Tool_Handout.doc Cognetics Corporation E-mail: info@cognetics.com! Web:
For STC DC Usability SIG Planning and Estimation Worksheets Scott McDaniel Senior Interaction Designer 26 February, 2003 Eval_Design_Tool_Handout.doc Cognetics Corporation E-mail: info@cognetics.com! Web:
Bring Your Own Device (BYOD)
 Bring Your Own Device (BYOD) An information security and ediscovery analysis A Whitepaper Call: +44 345 222 1711 / +353 1 210 1711 Email: cyber@bsigroup.com Visit: bsigroup.com Executive summary Organizations
Bring Your Own Device (BYOD) An information security and ediscovery analysis A Whitepaper Call: +44 345 222 1711 / +353 1 210 1711 Email: cyber@bsigroup.com Visit: bsigroup.com Executive summary Organizations
Request for Proposals for Data Assessment and Analysis
 Request for Proposals for Data Assessment and Analysis Introduction The Center for NYC Neighborhoods requires the services of a consultant to create a data architecture with the overall goal of assessing
Request for Proposals for Data Assessment and Analysis Introduction The Center for NYC Neighborhoods requires the services of a consultant to create a data architecture with the overall goal of assessing
Rowland s Motion Graphics Video Process
 Rowland s Motion Graphics Video Process You know it s essential to tell your story as clearly as possible. Getting it right isn t as easy as it sounds. There s always one more product spec or customer
Rowland s Motion Graphics Video Process You know it s essential to tell your story as clearly as possible. Getting it right isn t as easy as it sounds. There s always one more product spec or customer
Data Migration Plan (40) Fingrid Oyj
 1 (40) Fingrid Oyj FI10728943, VAT reg. 2 (40) Table of Contents Definitions... 5 1 Summary... 6 2 Introduction... 7 2.1 Datahub... 7 2.2 Members of the data migration plan... 8 2.3 Datahub's data migration
1 (40) Fingrid Oyj FI10728943, VAT reg. 2 (40) Table of Contents Definitions... 5 1 Summary... 6 2 Introduction... 7 2.1 Datahub... 7 2.2 Members of the data migration plan... 8 2.3 Datahub's data migration
Student Success Guide
 Student Success Guide Contents Like a web page, links in this document can be clicked and they will take you to where you want to go. Using a Mouse 6 The Left Button 6 The Right Button 7 The Scroll Wheel
Student Success Guide Contents Like a web page, links in this document can be clicked and they will take you to where you want to go. Using a Mouse 6 The Left Button 6 The Right Button 7 The Scroll Wheel
Guide to B2B Marketing Part four : Effective reporting
 Guide to B2B Email Marketing Part four : Effective email reporting Introduction One of the key attractions to email marketing is the speed with which you can reach a targeted audience with your message.
Guide to B2B Email Marketing Part four : Effective email reporting Introduction One of the key attractions to email marketing is the speed with which you can reach a targeted audience with your message.
3Lesson 3: Web Project Management Fundamentals Objectives
 3Lesson 3: Web Project Management Fundamentals Objectives By the end of this lesson, you will be able to: 1.1.11: Determine site project implementation factors (includes stakeholder input, time frame,
3Lesson 3: Web Project Management Fundamentals Objectives By the end of this lesson, you will be able to: 1.1.11: Determine site project implementation factors (includes stakeholder input, time frame,
Chapter 4. Fundamental Concepts and Models
 Chapter 4. Fundamental Concepts and Models 4.1 Roles and Boundaries 4.2 Cloud Characteristics 4.3 Cloud Delivery Models 4.4 Cloud Deployment Models The upcoming sections cover introductory topic areas
Chapter 4. Fundamental Concepts and Models 4.1 Roles and Boundaries 4.2 Cloud Characteristics 4.3 Cloud Delivery Models 4.4 Cloud Deployment Models The upcoming sections cover introductory topic areas
RED HAT ENTERPRISE LINUX. STANDARDIZE & SAVE.
 RED HAT ENTERPRISE LINUX. STANDARDIZE & SAVE. Is putting Contact us INTRODUCTION You know the headaches of managing an infrastructure that is stretched to its limit. Too little staff. Too many users. Not
RED HAT ENTERPRISE LINUX. STANDARDIZE & SAVE. Is putting Contact us INTRODUCTION You know the headaches of managing an infrastructure that is stretched to its limit. Too little staff. Too many users. Not
TDWI strives to provide course books that are content-rich and that serve as useful reference documents after a class has ended.
 Previews of TDWI course books are provided as an opportunity to see the quality of our material and help you to select the courses that best fit your needs. The previews can not be printed. TDWI strives
Previews of TDWI course books are provided as an opportunity to see the quality of our material and help you to select the courses that best fit your needs. The previews can not be printed. TDWI strives
1: Introduction to Object (1)
 1: Introduction to Object (1) 김동원 2003.01.20 Overview (1) The progress of abstraction Smalltalk Class & Object Interface The hidden implementation Reusing the implementation Inheritance: Reusing the interface
1: Introduction to Object (1) 김동원 2003.01.20 Overview (1) The progress of abstraction Smalltalk Class & Object Interface The hidden implementation Reusing the implementation Inheritance: Reusing the interface
Moving from FrameMaker to Blaze: Best Practices
 Moving from Adobe FrameMaker to MadCap Blaze is easy, although to get the best results you need to do some planning before you start. This document discusses suggestions and issues to make the import result
Moving from Adobe FrameMaker to MadCap Blaze is easy, although to get the best results you need to do some planning before you start. This document discusses suggestions and issues to make the import result
The first thing we ll need is some numbers. I m going to use the set of times and drug concentration levels in a patient s bloodstream given below.
 Graphing in Excel featuring Excel 2007 1 A spreadsheet can be a powerful tool for analyzing and graphing data, but it works completely differently from the graphing calculator that you re used to. If you
Graphing in Excel featuring Excel 2007 1 A spreadsheet can be a powerful tool for analyzing and graphing data, but it works completely differently from the graphing calculator that you re used to. If you
How Secure Do You Feel About Your HIPAA Compliance Plan? Daniel F. Shay, Esq.
 How Secure Do You Feel About Your HIPAA Compliance Plan? Daniel F. Shay, Esq. Word Count: 2,268 Physician practices have lived with the reality of HIPAA for over twenty years. In that time, it has likely
How Secure Do You Feel About Your HIPAA Compliance Plan? Daniel F. Shay, Esq. Word Count: 2,268 Physician practices have lived with the reality of HIPAA for over twenty years. In that time, it has likely
Landing Page Optimization What is Split Testing?... 13
 Table of Contents Introduction... 4 Types of Landing Pages... 5 Elements of Successful Landing Pages... 8 Creating Stunning Landing Pages... 10 WordPress Themes & Plugins... 10 Templates & Systems... 11
Table of Contents Introduction... 4 Types of Landing Pages... 5 Elements of Successful Landing Pages... 8 Creating Stunning Landing Pages... 10 WordPress Themes & Plugins... 10 Templates & Systems... 11
Chapter 8: SDLC Reviews and Audit Learning objectives Introduction Role of IS Auditor in SDLC
 Chapter 8: SDLC Reviews and Audit... 2 8.1 Learning objectives... 2 8.1 Introduction... 2 8.2 Role of IS Auditor in SDLC... 2 8.2.1 IS Auditor as Team member... 2 8.2.2 Mid-project reviews... 3 8.2.3 Post
Chapter 8: SDLC Reviews and Audit... 2 8.1 Learning objectives... 2 8.1 Introduction... 2 8.2 Role of IS Auditor in SDLC... 2 8.2.1 IS Auditor as Team member... 2 8.2.2 Mid-project reviews... 3 8.2.3 Post
Handling Your Data in SPSS. Columns, and Labels, and Values... Oh My! The Structure of SPSS. You should think about SPSS as having three major parts.
 Handling Your Data in SPSS Columns, and Labels, and Values... Oh My! You might think that simple intuition will guide you to a useful organization of your data. If you follow that path, you might find
Handling Your Data in SPSS Columns, and Labels, and Values... Oh My! You might think that simple intuition will guide you to a useful organization of your data. If you follow that path, you might find
Business Analysis for Practitioners - Requirements Elicitation and Analysis (Domain 3)
 Business Analysis for Practitioners - Requirements Elicitation and Analysis (Domain 3) COURSE STRUCTURE Introduction to Business Analysis Module 1 Needs Assessment Module 2 Business Analysis Planning Module
Business Analysis for Practitioners - Requirements Elicitation and Analysis (Domain 3) COURSE STRUCTURE Introduction to Business Analysis Module 1 Needs Assessment Module 2 Business Analysis Planning Module
Analytical model A structure and process for analyzing a dataset. For example, a decision tree is a model for the classification of a dataset.
 Glossary of data mining terms: Accuracy Accuracy is an important factor in assessing the success of data mining. When applied to data, accuracy refers to the rate of correct values in the data. When applied
Glossary of data mining terms: Accuracy Accuracy is an important factor in assessing the success of data mining. When applied to data, accuracy refers to the rate of correct values in the data. When applied
Contents at a Glance
 Contents at a Glance Introduction xvii Step 1 Step 2 Step 3 Step 4 Step 5 Step 6 Step 7 Step 8 Learn the Logic 1 Develop a Content Strategy 25 Lay a Foundation 47 Collect and Organize Your Content 71 Set
Contents at a Glance Introduction xvii Step 1 Step 2 Step 3 Step 4 Step 5 Step 6 Step 7 Step 8 Learn the Logic 1 Develop a Content Strategy 25 Lay a Foundation 47 Collect and Organize Your Content 71 Set
FUNCTIONAL BEST PRACTICES ORACLE USER PRODUCTIVITY KIT
 FUNCTIONAL BEST PRACTICES ORACLE USER PRODUCTIVITY KIT Purpose Oracle s User Productivity Kit (UPK) provides functionality that enables content authors, subject matter experts, and other project members
FUNCTIONAL BEST PRACTICES ORACLE USER PRODUCTIVITY KIT Purpose Oracle s User Productivity Kit (UPK) provides functionality that enables content authors, subject matter experts, and other project members
MARKETING VOL. 4. TITLE: Tips For Designing A Perfect Marketing Message. Author: Iris Carter-Collins
 TITLE: Tips For Designing A Perfect E-mail Marketing Message Author: Iris Carter-Collins Table Of Contents 1 Tips For Designing A Perfect E-mail Marketing Message 4 Are You Here To Learn About E-mail Marketing?
TITLE: Tips For Designing A Perfect E-mail Marketing Message Author: Iris Carter-Collins Table Of Contents 1 Tips For Designing A Perfect E-mail Marketing Message 4 Are You Here To Learn About E-mail Marketing?
[Compatibility Mode] Confusion in Office 2007
![[Compatibility Mode] Confusion in Office 2007 [Compatibility Mode] Confusion in Office 2007](/thumbs/74/70415826.jpg) [Compatibility Mode] Confusion in Office 2007 Confused by [Compatibility Mode] in Office 2007? You re Not Alone, and Here s Why Funnybroad@gmail.com 8/30/2007 This paper demonstrates how [Compatibility
[Compatibility Mode] Confusion in Office 2007 Confused by [Compatibility Mode] in Office 2007? You re Not Alone, and Here s Why Funnybroad@gmail.com 8/30/2007 This paper demonstrates how [Compatibility
<PROJECT NAME> IMPLEMENTATION PLAN
 IMPLEMENTATION PLAN Version VERSION HISTORY [Provide information on how the development and distribution of the Project Implementation Plan was controlled and tracked.
IMPLEMENTATION PLAN Version VERSION HISTORY [Provide information on how the development and distribution of the Project Implementation Plan was controlled and tracked.
The SD-WAN security guide
 The SD-WAN security guide How a flexible, software-defined WAN can help protect your network, people and data SD-WAN security: Separating fact from fiction For many companies, the benefits of SD-WAN are
The SD-WAN security guide How a flexible, software-defined WAN can help protect your network, people and data SD-WAN security: Separating fact from fiction For many companies, the benefits of SD-WAN are
Day in the Life of an SAP Consultant using IntelliCorp s LiveCompare Software
 Day in the Life of an SAP Consultant using IntelliCorp s LiveCompare Software Introduction Consultants use LiveCompare on a daily basis to help them deliver results to their clients more effectively and
Day in the Life of an SAP Consultant using IntelliCorp s LiveCompare Software Introduction Consultants use LiveCompare on a daily basis to help them deliver results to their clients more effectively and
ARCHIVE ESSENTIALS
 EMAIL ARCHIVE ESSENTIALS KEY CONSIDERATIONS WHEN MOVING TO OFFICE 365 DISCUSSION PAPER PREFACE The last few years have seen significant changes in the way that organisations conduct business. There has
EMAIL ARCHIVE ESSENTIALS KEY CONSIDERATIONS WHEN MOVING TO OFFICE 365 DISCUSSION PAPER PREFACE The last few years have seen significant changes in the way that organisations conduct business. There has
WHITE PAPER Application Performance Management. The Case for Adaptive Instrumentation in J2EE Environments
 WHITE PAPER Application Performance Management The Case for Adaptive Instrumentation in J2EE Environments Why Adaptive Instrumentation?... 3 Discovering Performance Problems... 3 The adaptive approach...
WHITE PAPER Application Performance Management The Case for Adaptive Instrumentation in J2EE Environments Why Adaptive Instrumentation?... 3 Discovering Performance Problems... 3 The adaptive approach...
Implementing ITIL v3 Service Lifecycle
 Implementing ITIL v3 Lifecycle WHITE PAPER introduction GSS INFOTECH IT services have become an integral means for conducting business for all sizes of businesses, private and public organizations, educational
Implementing ITIL v3 Lifecycle WHITE PAPER introduction GSS INFOTECH IT services have become an integral means for conducting business for all sizes of businesses, private and public organizations, educational
Excel Basics Rice Digital Media Commons Guide Written for Microsoft Excel 2010 Windows Edition by Eric Miller
 Excel Basics Rice Digital Media Commons Guide Written for Microsoft Excel 2010 Windows Edition by Eric Miller Table of Contents Introduction!... 1 Part 1: Entering Data!... 2 1.a: Typing!... 2 1.b: Editing
Excel Basics Rice Digital Media Commons Guide Written for Microsoft Excel 2010 Windows Edition by Eric Miller Table of Contents Introduction!... 1 Part 1: Entering Data!... 2 1.a: Typing!... 2 1.b: Editing
Six Sigma in the datacenter drives a zero-defects culture
 Six Sigma in the datacenter drives a zero-defects culture Situation Like many IT organizations, Microsoft IT wants to keep its global infrastructure available at all times. Scope, scale, and an environment
Six Sigma in the datacenter drives a zero-defects culture Situation Like many IT organizations, Microsoft IT wants to keep its global infrastructure available at all times. Scope, scale, and an environment
DEVELOPING DECISION SUPPORT SYSTEMS A MODERN APPROACH
 DEVELOPING DECISION SUPPORT SYSTEMS A MODERN APPROACH Ion Lungu PhD, Vlad Diaconiţa PhD Candidate Department of Economic Informatics Academy of Economic Studies Bucharest In today s economy access to quality
DEVELOPING DECISION SUPPORT SYSTEMS A MODERN APPROACH Ion Lungu PhD, Vlad Diaconiţa PhD Candidate Department of Economic Informatics Academy of Economic Studies Bucharest In today s economy access to quality
Summary of Consultation with Key Stakeholders
 Summary of Consultation with Key Stakeholders Technology and Communications Sector Electronic Manufacturing Services & Original Design Manufacturing Software & IT Services Hardware Semiconductors Telecommunication
Summary of Consultation with Key Stakeholders Technology and Communications Sector Electronic Manufacturing Services & Original Design Manufacturing Software & IT Services Hardware Semiconductors Telecommunication
E-COMMERCE HOMEPAGE UX DESIGN TIPS THESE TIPS WILL HELP YOU CREATE A USABLE E-COMMERCE WEBSITE AND TURN YOUR HOMEPAGE INTO A CONVERSION MAGNET
 E-COMMERCE HOMEPAGE UX DESIGN TIPS THESE TIPS WILL HELP YOU CREATE A USABLE E-COMMERCE WEBSITE AND TURN YOUR HOMEPAGE INTO A CONVERSION MAGNET Just imagine... You ve finished your work day and just completed
E-COMMERCE HOMEPAGE UX DESIGN TIPS THESE TIPS WILL HELP YOU CREATE A USABLE E-COMMERCE WEBSITE AND TURN YOUR HOMEPAGE INTO A CONVERSION MAGNET Just imagine... You ve finished your work day and just completed
A Working Paper of the EastWest Institute Breakthrough Group. Increasing the Global Availability and Use of Secure ICT Products and Services
 A Working Paper of the EastWest Institute Breakthrough Group Increasing the Global Availability and Use of Secure ICT Products and Services August 5, 2015 The EastWest Institute (EWI) is leading a Global
A Working Paper of the EastWest Institute Breakthrough Group Increasing the Global Availability and Use of Secure ICT Products and Services August 5, 2015 The EastWest Institute (EWI) is leading a Global
Extension Web Publishing 3 Lecture # 1. Chapter 6 Site Types and Architectures
 Chapter 6 Site Types and Architectures Site Types Definition: A public Web site, an Internet Web site, an external Web site or simply a Web site is one that is not explicitly restricted to a particular
Chapter 6 Site Types and Architectures Site Types Definition: A public Web site, an Internet Web site, an external Web site or simply a Web site is one that is not explicitly restricted to a particular
Order from Chaos. Nebraska Wesleyan University Mathematics Circle
 Order from Chaos Nebraska Wesleyan University Mathematics Circle Austin Mohr Department of Mathematics Nebraska Wesleyan University February 2, 20 The (, )-Puzzle Start by drawing six dots at the corners
Order from Chaos Nebraska Wesleyan University Mathematics Circle Austin Mohr Department of Mathematics Nebraska Wesleyan University February 2, 20 The (, )-Puzzle Start by drawing six dots at the corners
2016 All Rights Reserved
 2016 All Rights Reserved Table of Contents Chapter 1: The Truth About Safelists What is a Safelist Safelist myths busted Chapter 2: Getting Started What to look for before you join a Safelist Best Safelists
2016 All Rights Reserved Table of Contents Chapter 1: The Truth About Safelists What is a Safelist Safelist myths busted Chapter 2: Getting Started What to look for before you join a Safelist Best Safelists
Strategy. 1. You must do an internal needs analysis before looking at software or creating an ITT
 Strategy 1. You must do an internal needs analysis before looking at software or creating an ITT It is very easy to jump straight in and look at database software before considering what your requirements
Strategy 1. You must do an internal needs analysis before looking at software or creating an ITT It is very easy to jump straight in and look at database software before considering what your requirements
Content Strategy. A practical guide
 Content Strategy A practical guide 2 The basics So what is content strategy anyway? 3 We get that a lot Here s a good definition from the early days: Using words and data to create unambiguous content
Content Strategy A practical guide 2 The basics So what is content strategy anyway? 3 We get that a lot Here s a good definition from the early days: Using words and data to create unambiguous content
Introduction. A Brief Description of Our Journey
 Introduction If you still write RPG code as you did 20 years ago, or if you have ILE RPG on your resume but don t actually use or understand it, this book is for you. It will help you transition from the
Introduction If you still write RPG code as you did 20 years ago, or if you have ILE RPG on your resume but don t actually use or understand it, this book is for you. It will help you transition from the
Human Error Taxonomy
 Human Error Taxonomy The Human Error Taxonomy (HET) provides a structure for requirement errors made during the software development process. The HET can be employed during software inspection to help
Human Error Taxonomy The Human Error Taxonomy (HET) provides a structure for requirement errors made during the software development process. The HET can be employed during software inspection to help
SOME TYPES AND USES OF DATA MODELS
 3 SOME TYPES AND USES OF DATA MODELS CHAPTER OUTLINE 3.1 Different Types of Data Models 23 3.1.1 Physical Data Model 24 3.1.2 Logical Data Model 24 3.1.3 Conceptual Data Model 25 3.1.4 Canonical Data Model
3 SOME TYPES AND USES OF DATA MODELS CHAPTER OUTLINE 3.1 Different Types of Data Models 23 3.1.1 Physical Data Model 24 3.1.2 Logical Data Model 24 3.1.3 Conceptual Data Model 25 3.1.4 Canonical Data Model
Stop Scope Creep. Double Your Profit & Remove The Stress of Selling Websites
 Stop Scope Creep Double Your Profit & Remove The Stress of Selling Websites Why Do Projects Go Wrong? Imagine this: You ve agreed to do a specific project with a client. You start off well. But as the
Stop Scope Creep Double Your Profit & Remove The Stress of Selling Websites Why Do Projects Go Wrong? Imagine this: You ve agreed to do a specific project with a client. You start off well. But as the
Business Impacts of Poor Data Quality: Building the Business Case
 Business Impacts of Poor Data Quality: Building the Business Case David Loshin Knowledge Integrity, Inc. 1 Data Quality Challenges 2 Addressing the Problem To effectively ultimately address data quality,
Business Impacts of Poor Data Quality: Building the Business Case David Loshin Knowledge Integrity, Inc. 1 Data Quality Challenges 2 Addressing the Problem To effectively ultimately address data quality,
