CS 111: Program Design I Lecture 18: Web and getting text from it
|
|
|
- Cory Briggs
- 6 years ago
- Views:
Transcription
1 CS 111: Program Desig I Lecture 18: Web ad gettig text from it Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago October 25, 2016
2 Goals Lear about Iteret ad how to access it directly from a program Ad use this as fial piece to fiish program
3 Grace Hopper Celebratio of Wome i Computig 2016 Where I was with ~25 UIC wome CS studets last week With 15,000 other people Heard from Lataya Sweeey, Harvard Prof. ad formerly Chief Techologist of Federal Trade Commissio about our kid of issues, ad from Megha Smith, CTO of the US Ad from a former CS 111 studet about crawlig the web
4 Our aluma She took CS 111 i 2011 or 2012 Now works for Google Chicago She told me a full Google web crawl reuires 500 Petabytes to store Did't cover those at start of class because 1 Petabyte = 1000 Terabytes! (So petabytes do't come up much i cosumer use!) Ad that for jobs i YouTube part of Google key skill i Pytho
5 Wome i this CS 111 Keep your eyes ope i Sprig for your chace to atted Grace Hopper 2017
6 Thursday No Class: Atted Distiguished Lecture: Presidet Maria Klawe of Harvey Mudd College, oe of exceedigly few computer scietists who are college/ uiversity Presidets 605 SCE, 11am Gettig more wome ito tech careers ad why it matters
7 Opeig a URL ad readig it The 60 secod "stadig o oe foot" versio so you ca do the crawler homework import urllib.reuest as ur coectio= ur.urlope(" cotet = coectio.read() coectio.close() (We'll come back to this i miutes)
8 Networks: 2 or more computers commuicatig Networks formed whe distict computers commuicate via some mechaism Iside oe computer, 0/1 voltages Almost ever o etwork: too hard to make work over distace More commoly freuecy I 2016 usually ot soud freuecy, but modems i the dialup iteret era did ideed use soud
9 Networks everywhere All o-aciet cars Moder car is a collectio of computers Cotrollig air flow, gas flow, makig airbags work that commuicate, ad happe to have 4 wheels attached. J Likewise plaes (Almost?) all of you have a etwork i your home or dorm
10 Networks orgaized i layers Recurrig theme throughout Computer Sciece: Recall hierarchical decompositio For etworks, bottom level is physical substrate What are sigals beig passed o? Radio? Wire? Middle levels: How data is ecoded Freuecies of soud waves or radio waves or??? for ecodig 0's ad 1's Trasmit bit at a time? Byte at a time? Larger packets of bytes?
11 Higher levels of etworks Protocol of commuicatio How do I address a particular computer I wat to talk to? Or may computers? How do I tell a computer that I wat to talk to it? That I'm startig to sed it data? What it's supposed to do with the data I sed it? Whe we're doe?
12 Iteret: Collectio of etworks Iteret: etwork of etworks Iside your home, probably have local etwork so your computers ca talk to oe aother Likely uses wireless base statio You ca probably reach priters ad/or copy files betwee your computers Ad you coect your home etwork (via a Iteret Service Provider (ISP)) to global iteret So your home etwork part of Iteret
13 Iteret based o agreemets o ecodigs Iteret built o set of agreemets about How computers addressed Set of four 1-byte umbers (IPv4), or eight 2-byte umbers (IPv6). E.g., Way of associatig these umbers with domai ames, like (which probably really resolves to a set of two umbers) usig domai ame servers How computers will commuicate That data will be split ito packets with various pieces i them That computers will format their data ad talk to oe aother usig TCP/IP protocol How packets are routed aroud etwork to fid their destiatio
14
15 High-level protocols All that just lets us pass data back ad forth What does data say? What does data do? Oe of earliest applicatios (ivolvig 2 highlevel protocols) was Aother: File trasfer Protocol (FTP) allows computers to move files betwee each other Defies what oe side says to other whe copyig file over (e.g., "STO fileame") ad how file will be ecoded Not widely used i 2016, but big whe I took CS 1
16 Iteret vs. Web? Which is most correct? A. Iteret ad (World Wide) Web are very roughly syoymous B. The Web is oe service of the Iteret C. The Iteret is oe service of the Web D. There is oly a very loose coectio betwee the Iteret ad the Web
17 Iteret is ot ew Iteret web! Iteret origially set up for military applicatios Feature: Packets still reach their destiatio eve if part is destroyed, damaged, or cesored Iteret established i 1969 as military research project with four locatios, curret key protocol TCP/IP dates to 1975; declared uiversal stadard for military computig by US DoD i 1982
18 The Web (Web Iteret!) Prof. Sloa heavy user of Iteret 1985 oward Web, built o top of Iteret, oly came ito beig i December 1990, ad was extremely obscure util 1993 Web is (agai) set of agreemets, started by Sir Tim Berers-Lee O how to refer to everythig o Web: URL (Uiform Resource Locator) O how to serve documets: HTTP (HyperText Trasfer Protocol) How documets formatted: HTML (HyperText Markup Laguage)
19 Hypertext Noliear text that liks to other text ad graphics via liks You kow it well! Some limited implemetatios, e.g., Apple Hypercard, a little before web, but The read a little, click ad read some more, the click, the. use of hypertext did't exist whe your parets ad I were i school
20 HyperText Trasfer Protocol (HTTP) HTTP defies very simple protocol for how to exchage iformatio betwee computers (o top of iteret protocols) Defies pieces of the commuicatio Web server is waitig for cliet i listeig state What resource do you wat? Where is it? Okay, here's the type of thig it is (HTML, JPEG, whatever), ad here it is Ad words the computers say to oe aother: Simple, e.g., "GET", "PUT", ad "OK"
21 Uiform Resource Locators (URLs) URLs allow us to referece ay material aywhere o Iteret Strictly speakig, ay computer providig a protocol accessible via URL Just puttig your computer o Iteret does ot mea that all of your files are accessible to everyoe o Iteret URLs have four parts: 1. Protocol to use to reach this resource, 2. Domai ame of the computer where the resource is, 3. Path o the computer to the resource, 4. Ad the ame of the resource (optioal; otio of default file). 5. (Ad optioally after that there ca be parameters itroduced with a?)
22 Example URL E.g., 3 parts: 1. Protocol: http (usually http or https) 2. Host ame: 3. Path: /CS477 (locatio of files o host) SloaWhyCS2014.pdf 1. Protocol: https 2. same host ame 3. Path: /~sloa/papers 4. Fileame: SloaWhyCS2014.pdf
23 Path also optioal Web servers (programs that uderstad HTTP protocol) typically have special directory that they serve from Files i that special directory directly reachable without specifyig path
24 Web browsers are cliets Your Web browser is called a cliet accessig a Web server Programs like Chrome, Firefox, or Safari uderstad a lot about Iteret protocols They kow how to iterpret HTML ad display it graphically If HTML refereces other resources, like JPEG or PNG pictures, cliet fetches them ad displays them as appropriate Cliet also kows details of HTTP (ad perhaps mailto, ftp, ad some others)
25 Browser ot oly way to use Iteret Pytho (ad other laguages) have modules that allow you to use these protocols I Pytho, ca read ay URL as if it was a file I Pytho 3, key library is urllib.reuest (Other parts of urllib useful for, e.g., parsig webpage text)
26 Importig urllib.reuest Advice: If module has dot i its ame like urllib.reuest, matplotlib.pyplot, always import it as somethig. Else Pytho ca get cofused about multiple dots whe you go to use fuctios iside it. Thus: import urllib.reuest as ur
27 Opeig a URL ad readig it The 60 secod "stadig o oe foot" versio so you ca do the crawler homework import urllib.reuest as ur coectio= ur.urlope(" cotet = coectio.read() coectio.close() (We've come back!)
28 Status coectio retured from urllib is a "HTTPRespose" object ad has a status attribute, which should be 200 if all wet well I crawlig, if you ru ito difficulties, try: import urllib.reuest as ur coectio= ur.urlope(" if (coectio.status == 200): cotet = coectio.read() <rest of real work here> coectio.close()
29 Readig the coectio read() method of coectio works just like read() method of files Almost: this read will give you a seuece of bytes, which ca i may but ot all cases be treated as a strig. Ca force it to be 100% strig istead of merely pretty strig-like by cotet = str(coectio.read()) usig type coversio fuctio str()
CS 111: Program Design I Lecture 19: Networks, the Web, and getting text from the Web in Python
 CS 111: Program Desig I Lecture 19: Networks, the Web, ad gettig text from the Web i Pytho Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago April 3, 2018 Goals Lear about Iteret Lear about
CS 111: Program Desig I Lecture 19: Networks, the Web, ad gettig text from the Web i Pytho Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago April 3, 2018 Goals Lear about Iteret Lear about
CS 111: Program Design I Lecture 20: Web crawling, HTML, Copyright
 CS 111: Program Desig I Lecture 20: Web crawlig, HTML, Copyright Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago November 8, 2016 WEB CRAWLER AGAIN Two bits of useful Pytho sytax Do't eed
CS 111: Program Desig I Lecture 20: Web crawlig, HTML, Copyright Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago November 8, 2016 WEB CRAWLER AGAIN Two bits of useful Pytho sytax Do't eed
CS 111: Program Design I Lecture # 7: First Loop, Web Crawler, Functions
 CS 111: Program Desig I Lecture # 7: First Loop, Web Crawler, Fuctios Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago September 18, 2018 What will this prit? x = 5 if x == 3: prit("hi!")
CS 111: Program Desig I Lecture # 7: First Loop, Web Crawler, Fuctios Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago September 18, 2018 What will this prit? x = 5 if x == 3: prit("hi!")
CS 111: Program Design I Lecture 21: Network Analysis. Robert H. Sloan & Richard Warner University of Illinois at Chicago April 10, 2018
 CS 111: Program Desig I Lecture 21: Network Aalysis Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago April 10, 2018 NETWORK ANALYSIS Which displays a graph i the sese of graph/etwork aalysis?
CS 111: Program Desig I Lecture 21: Network Aalysis Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago April 10, 2018 NETWORK ANALYSIS Which displays a graph i the sese of graph/etwork aalysis?
CS 111: Program Design I Lecture 16: Module Review, Encodings, Lists
 CS 111: Program Desig I Lecture 16: Module Review, Ecodigs, Lists Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago October 18, 2016 Last time Dot otatio ad methods Padas: user maual poit
CS 111: Program Desig I Lecture 16: Module Review, Ecodigs, Lists Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago October 18, 2016 Last time Dot otatio ad methods Padas: user maual poit
CS 111: Program Design I Lecture 15: Modules, Pandas again. Robert H. Sloan & Richard Warner University of Illinois at Chicago March 8, 2018
 CS 111: Program Desig I Lecture 15: Modules, Padas agai Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago March 8, 2018 PYTHON STANDARD LIBRARY & BEYOND: MODULES Extedig Pytho Every moder
CS 111: Program Desig I Lecture 15: Modules, Padas agai Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago March 8, 2018 PYTHON STANDARD LIBRARY & BEYOND: MODULES Extedig Pytho Every moder
CS 111: Program Design I Lecture 15: Objects, Pandas, Modules. Robert H. Sloan & Richard Warner University of Illinois at Chicago October 13, 2016
 CS 111: Program Desig I Lecture 15: Objects, Padas, Modules Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago October 13, 2016 OBJECTS AND DOT NOTATION Objects (Implicit i Chapter 2, Variables,
CS 111: Program Desig I Lecture 15: Objects, Padas, Modules Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago October 13, 2016 OBJECTS AND DOT NOTATION Objects (Implicit i Chapter 2, Variables,
CSC 220: Computer Organization Unit 11 Basic Computer Organization and Design
 College of Computer ad Iformatio Scieces Departmet of Computer Sciece CSC 220: Computer Orgaizatio Uit 11 Basic Computer Orgaizatio ad Desig 1 For the rest of the semester, we ll focus o computer architecture:
College of Computer ad Iformatio Scieces Departmet of Computer Sciece CSC 220: Computer Orgaizatio Uit 11 Basic Computer Orgaizatio ad Desig 1 For the rest of the semester, we ll focus o computer architecture:
CS 111: Program Design I Lecture #26: Heat maps, Nothing, Predictive Policing
 CS 111: Program Desig I Lecture #26: Heat maps, Nothig, Predictive Policig Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago November 29, 2018 Some Logistics Extra credit: Sample Fial Exam
CS 111: Program Desig I Lecture #26: Heat maps, Nothig, Predictive Policig Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago November 29, 2018 Some Logistics Extra credit: Sample Fial Exam
CS 111 Green: Program Design I Lecture 27: Speed (cont.); parting thoughts
 CS 111 Gree: Program Desig I Lecture 27: Speed (cot.); partig thoughts By Nascarkig - Ow work, CC BY-SA 4.0, https://commos.wikimedia.org/w/idex.php?curid=38671041 Robert H. Sloa (CS) & Rachel Poretsky
CS 111 Gree: Program Desig I Lecture 27: Speed (cot.); partig thoughts By Nascarkig - Ow work, CC BY-SA 4.0, https://commos.wikimedia.org/w/idex.php?curid=38671041 Robert H. Sloa (CS) & Rachel Poretsky
Announcements. Reading. Project #4 is on the web. Homework #1. Midterm #2. Chapter 4 ( ) Note policy about project #3 missing components
 Aoucemets Readig Chapter 4 (4.1-4.2) Project #4 is o the web ote policy about project #3 missig compoets Homework #1 Due 11/6/01 Chapter 6: 4, 12, 24, 37 Midterm #2 11/8/01 i class 1 Project #4 otes IPv6Iit,
Aoucemets Readig Chapter 4 (4.1-4.2) Project #4 is o the web ote policy about project #3 missig compoets Homework #1 Due 11/6/01 Chapter 6: 4, 12, 24, 37 Midterm #2 11/8/01 i class 1 Project #4 otes IPv6Iit,
CS 111: Program Design I Lecture 14: Encodings & Files concluded; Pandas, Modules, legal data analytics
 CS 111: Program Desig I Lecture 14: Ecodigs & Files cocluded; Padas, Modules, legal data aalytics Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago October 16, 2018 Recall: ASCII Ecodig characters
CS 111: Program Desig I Lecture 14: Ecodigs & Files cocluded; Padas, Modules, legal data aalytics Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago October 16, 2018 Recall: ASCII Ecodig characters
CS 111: Program Design I Lecture 20: Web crawling, HTML, Copyright
 CS 111: Program Desig I Lecture 20: Web crawlig, HTML, Copyright Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago November 8, 2016 Most importat thig If you have ot yet voted (ad are a US
CS 111: Program Desig I Lecture 20: Web crawlig, HTML, Copyright Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago November 8, 2016 Most importat thig If you have ot yet voted (ad are a US
Python Programming: An Introduction to Computer Science
 Pytho Programmig: A Itroductio to Computer Sciece Chapter 1 Computers ad Programs 1 Objectives To uderstad the respective roles of hardware ad software i a computig system. To lear what computer scietists
Pytho Programmig: A Itroductio to Computer Sciece Chapter 1 Computers ad Programs 1 Objectives To uderstad the respective roles of hardware ad software i a computig system. To lear what computer scietists
Exceptions. Your computer takes exception. The Exception Class. Causes of Exceptions
 Your computer takes exceptio s s are errors i the logic of a program (ru-time errors). Examples: i thread mai java.io.filenotfoud: studet.txt (The system caot fid the file specified.) i thread mai java.lag.nullpoiter:
Your computer takes exceptio s s are errors i the logic of a program (ru-time errors). Examples: i thread mai java.io.filenotfoud: studet.txt (The system caot fid the file specified.) i thread mai java.lag.nullpoiter:
Basic Design Principles
 + Basic Desig Priciples + Assigmet 2: Your studet web site 1. Baer 2. Your ame 3. Your accout umber 4. A lik to aother web page, preferably oe useful to you i this class 5. A photo, preferably of you 6.
+ Basic Desig Priciples + Assigmet 2: Your studet web site 1. Baer 2. Your ame 3. Your accout umber 4. A lik to aother web page, preferably oe useful to you i this class 5. A photo, preferably of you 6.
CS 111: Program Design I Lecture # 7: Web Crawler, Functions; Open Access
 CS 111: Program Desig I Lecture # 7: Web Crawler, Fuctios; Ope Access Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago September 13, 2016 Lab Hit/Remider word = "hi" word.upper() à "HI" Questio
CS 111: Program Desig I Lecture # 7: Web Crawler, Fuctios; Ope Access Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago September 13, 2016 Lab Hit/Remider word = "hi" word.upper() à "HI" Questio
Lecture 9: Exam I Review
 CS 111 (Law): Program Desig I Lecture 9: Exam I Review Robert H. Sloa & Richard Warer Uiversity of Illiois, Chicago September 22, 2016 This Class Discuss midterm topics Go over practice examples Aswer
CS 111 (Law): Program Desig I Lecture 9: Exam I Review Robert H. Sloa & Richard Warer Uiversity of Illiois, Chicago September 22, 2016 This Class Discuss midterm topics Go over practice examples Aswer
Message Integrity and Hash Functions. TELE3119: Week4
 Message Itegrity ad Hash Fuctios TELE3119: Week4 Outlie Message Itegrity Hash fuctios ad applicatios Hash Structure Popular Hash fuctios 4-2 Message Itegrity Goal: itegrity (ot secrecy) Allows commuicatig
Message Itegrity ad Hash Fuctios TELE3119: Week4 Outlie Message Itegrity Hash fuctios ad applicatios Hash Structure Popular Hash fuctios 4-2 Message Itegrity Goal: itegrity (ot secrecy) Allows commuicatig
CS 11 C track: lecture 1
 CS 11 C track: lecture 1 Prelimiaries Need a CMS cluster accout http://acctreq.cms.caltech.edu/cgi-bi/request.cgi Need to kow UNIX IMSS tutorial liked from track home page Track home page: http://courses.cms.caltech.edu/courses/cs11/material
CS 11 C track: lecture 1 Prelimiaries Need a CMS cluster accout http://acctreq.cms.caltech.edu/cgi-bi/request.cgi Need to kow UNIX IMSS tutorial liked from track home page Track home page: http://courses.cms.caltech.edu/courses/cs11/material
15-859E: Advanced Algorithms CMU, Spring 2015 Lecture #2: Randomized MST and MST Verification January 14, 2015
 15-859E: Advaced Algorithms CMU, Sprig 2015 Lecture #2: Radomized MST ad MST Verificatio Jauary 14, 2015 Lecturer: Aupam Gupta Scribe: Yu Zhao 1 Prelimiaries I this lecture we are talkig about two cotets:
15-859E: Advaced Algorithms CMU, Sprig 2015 Lecture #2: Radomized MST ad MST Verificatio Jauary 14, 2015 Lecturer: Aupam Gupta Scribe: Yu Zhao 1 Prelimiaries I this lecture we are talkig about two cotets:
CSE 111 Bio: Program Design I Class 11: loops
 SE 111 Bio: Program Desig I lass 11: loops Radall Muroe, xkcd.com/1411/ Robert H. Sloa (S) & Rachel Poretsky (Bio) Uiversity of Illiois, hicago October 2, 2016 Pytho ets Loopy! he Pytho, Busch ardes Florida
SE 111 Bio: Program Desig I lass 11: loops Radall Muroe, xkcd.com/1411/ Robert H. Sloa (S) & Rachel Poretsky (Bio) Uiversity of Illiois, hicago October 2, 2016 Pytho ets Loopy! he Pytho, Busch ardes Florida
Python Programming: An Introduction to Computer Science
 Pytho Programmig: A Itroductio to Computer Sciece Chapter 6 Defiig Fuctios Pytho Programmig, 2/e 1 Objectives To uderstad why programmers divide programs up ito sets of cooperatig fuctios. To be able to
Pytho Programmig: A Itroductio to Computer Sciece Chapter 6 Defiig Fuctios Pytho Programmig, 2/e 1 Objectives To uderstad why programmers divide programs up ito sets of cooperatig fuctios. To be able to
MOTIF XF Extension Owner s Manual
 MOTIF XF Extesio Ower s Maual Table of Cotets About MOTIF XF Extesio...2 What Extesio ca do...2 Auto settig of Audio Driver... 2 Auto settigs of Remote Device... 2 Project templates with Iput/ Output Bus
MOTIF XF Extesio Ower s Maual Table of Cotets About MOTIF XF Extesio...2 What Extesio ca do...2 Auto settig of Audio Driver... 2 Auto settigs of Remote Device... 2 Project templates with Iput/ Output Bus
Computers and Scientific Thinking
 Computers ad Scietific Thikig David Reed, Creighto Uiversity Chapter 15 JavaScript Strigs 1 Strigs as Objects so far, your iteractive Web pages have maipulated strigs i simple ways use text box to iput
Computers ad Scietific Thikig David Reed, Creighto Uiversity Chapter 15 JavaScript Strigs 1 Strigs as Objects so far, your iteractive Web pages have maipulated strigs i simple ways use text box to iput
n Some thoughts on software development n The idea of a calculator n Using a grammar n Expression evaluation n Program organization n Analysis
 Overview Chapter 6 Writig a Program Bjare Stroustrup Some thoughts o software developmet The idea of a calculator Usig a grammar Expressio evaluatio Program orgaizatio www.stroustrup.com/programmig 3 Buildig
Overview Chapter 6 Writig a Program Bjare Stroustrup Some thoughts o software developmet The idea of a calculator Usig a grammar Expressio evaluatio Program orgaizatio www.stroustrup.com/programmig 3 Buildig
Basic allocator mechanisms The course that gives CMU its Zip! Memory Management II: Dynamic Storage Allocation Mar 6, 2000.
 5-23 The course that gives CM its Zip Memory Maagemet II: Dyamic Storage Allocatio Mar 6, 2000 Topics Segregated lists Buddy system Garbage collectio Mark ad Sweep Copyig eferece coutig Basic allocator
5-23 The course that gives CM its Zip Memory Maagemet II: Dyamic Storage Allocatio Mar 6, 2000 Topics Segregated lists Buddy system Garbage collectio Mark ad Sweep Copyig eferece coutig Basic allocator
CHAPTER IV: GRAPH THEORY. Section 1: Introduction to Graphs
 CHAPTER IV: GRAPH THEORY Sectio : Itroductio to Graphs Sice this class is called Number-Theoretic ad Discrete Structures, it would be a crime to oly focus o umber theory regardless how woderful those topics
CHAPTER IV: GRAPH THEORY Sectio : Itroductio to Graphs Sice this class is called Number-Theoretic ad Discrete Structures, it would be a crime to oly focus o umber theory regardless how woderful those topics
ECE4050 Data Structures and Algorithms. Lecture 6: Searching
 ECE4050 Data Structures ad Algorithms Lecture 6: Searchig 1 Search Give: Distict keys k 1, k 2,, k ad collectio L of records of the form (k 1, I 1 ), (k 2, I 2 ),, (k, I ) where I j is the iformatio associated
ECE4050 Data Structures ad Algorithms Lecture 6: Searchig 1 Search Give: Distict keys k 1, k 2,, k ad collectio L of records of the form (k 1, I 1 ), (k 2, I 2 ),, (k, I ) where I j is the iformatio associated
Switching Hardware. Spring 2018 CS 438 Staff, University of Illinois 1
 Switchig Hardware Sprig 208 CS 438 Staff, Uiversity of Illiois Where are we? Uderstad Differet ways to move through a etwork (forwardig) Read sigs at each switch (datagram) Follow a kow path (virtual circuit)
Switchig Hardware Sprig 208 CS 438 Staff, Uiversity of Illiois Where are we? Uderstad Differet ways to move through a etwork (forwardig) Read sigs at each switch (datagram) Follow a kow path (virtual circuit)
Customer Portal Quick Reference User Guide
 Customer Portal Quick Referece User Guide Overview This user guide is iteded for FM Approvals customers usig the Approval Iformatio Maagemet (AIM) customer portal to track their active projects. AIM is
Customer Portal Quick Referece User Guide Overview This user guide is iteded for FM Approvals customers usig the Approval Iformatio Maagemet (AIM) customer portal to track their active projects. AIM is
CMSC Computer Architecture Lecture 12: Virtual Memory. Prof. Yanjing Li University of Chicago
 CMSC 22200 Computer Architecture Lecture 12: Virtual Memory Prof. Yajig Li Uiversity of Chicago A System with Physical Memory Oly Examples: most Cray machies early PCs Memory early all embedded systems
CMSC 22200 Computer Architecture Lecture 12: Virtual Memory Prof. Yajig Li Uiversity of Chicago A System with Physical Memory Oly Examples: most Cray machies early PCs Memory early all embedded systems
Location Steps and Paths
 Locatio Steps ad Paths 3 INTHIS CHAPTER Uderstadig Locatio Steps ad Paths How do locatio paths work? We took a look at locatio paths i the overview i Chapter 1, where we saw that locatio paths look much
Locatio Steps ad Paths 3 INTHIS CHAPTER Uderstadig Locatio Steps ad Paths How do locatio paths work? We took a look at locatio paths i the overview i Chapter 1, where we saw that locatio paths look much
Module 8-7: Pascal s Triangle and the Binomial Theorem
 Module 8-7: Pascal s Triagle ad the Biomial Theorem Gregory V. Bard April 5, 017 A Note about Notatio Just to recall, all of the followig mea the same thig: ( 7 7C 4 C4 7 7C4 5 4 ad they are (all proouced
Module 8-7: Pascal s Triagle ad the Biomial Theorem Gregory V. Bard April 5, 017 A Note about Notatio Just to recall, all of the followig mea the same thig: ( 7 7C 4 C4 7 7C4 5 4 ad they are (all proouced
top() Applications of Stacks
 CS22 Algorithms ad Data Structures MW :00 am - 2: pm, MSEC 0 Istructor: Xiao Qi Lecture 6: Stacks ad Queues Aoucemets Quiz results Homework 2 is available Due o September 29 th, 2004 www.cs.mt.edu~xqicoursescs22
CS22 Algorithms ad Data Structures MW :00 am - 2: pm, MSEC 0 Istructor: Xiao Qi Lecture 6: Stacks ad Queues Aoucemets Quiz results Homework 2 is available Due o September 29 th, 2004 www.cs.mt.edu~xqicoursescs22
K-NET bus. When several turrets are connected to the K-Bus, the structure of the system is as showns
 K-NET bus The K-Net bus is based o the SPI bus but it allows to addressig may differet turrets like the I 2 C bus. The K-Net is 6 a wires bus (4 for SPI wires ad 2 additioal wires for request ad ackowledge
K-NET bus The K-Net bus is based o the SPI bus but it allows to addressig may differet turrets like the I 2 C bus. The K-Net is 6 a wires bus (4 for SPI wires ad 2 additioal wires for request ad ackowledge
Chapter 1. Introduction to Computers and C++ Programming. Copyright 2015 Pearson Education, Ltd.. All rights reserved.
 Chapter 1 Itroductio to Computers ad C++ Programmig Copyright 2015 Pearso Educatio, Ltd.. All rights reserved. Overview 1.1 Computer Systems 1.2 Programmig ad Problem Solvig 1.3 Itroductio to C++ 1.4 Testig
Chapter 1 Itroductio to Computers ad C++ Programmig Copyright 2015 Pearso Educatio, Ltd.. All rights reserved. Overview 1.1 Computer Systems 1.2 Programmig ad Problem Solvig 1.3 Itroductio to C++ 1.4 Testig
Lecture 7 7 Refraction and Snell s Law Reading Assignment: Read Kipnis Chapter 4 Refraction of Light, Section III, IV
 Lecture 7 7 Refractio ad Sell s Law Readig Assigmet: Read Kipis Chapter 4 Refractio of Light, Sectio III, IV 7. History I Eglish-speakig coutries, the law of refractio is kow as Sell s Law, after the Dutch
Lecture 7 7 Refractio ad Sell s Law Readig Assigmet: Read Kipis Chapter 4 Refractio of Light, Sectio III, IV 7. History I Eglish-speakig coutries, the law of refractio is kow as Sell s Law, after the Dutch
Chapter 9. Pointers and Dynamic Arrays. Copyright 2015 Pearson Education, Ltd.. All rights reserved.
 Chapter 9 Poiters ad Dyamic Arrays Copyright 2015 Pearso Educatio, Ltd.. All rights reserved. Overview 9.1 Poiters 9.2 Dyamic Arrays Copyright 2015 Pearso Educatio, Ltd.. All rights reserved. Slide 9-3
Chapter 9 Poiters ad Dyamic Arrays Copyright 2015 Pearso Educatio, Ltd.. All rights reserved. Overview 9.1 Poiters 9.2 Dyamic Arrays Copyright 2015 Pearso Educatio, Ltd.. All rights reserved. Slide 9-3
Elementary Educational Computer
 Chapter 5 Elemetary Educatioal Computer. Geeral structure of the Elemetary Educatioal Computer (EEC) The EEC coforms to the 5 uits structure defied by vo Neuma's model (.) All uits are preseted i a simplified
Chapter 5 Elemetary Educatioal Computer. Geeral structure of the Elemetary Educatioal Computer (EEC) The EEC coforms to the 5 uits structure defied by vo Neuma's model (.) All uits are preseted i a simplified
Course Information. Details. Topics. Network Examples. Overview. Walrand Lecture 1. EECS 228a. EECS 228a Lecture 1 Overview: Networks
 Walrad Lecture 1 Course Iformatio Lecture 1 Overview: Networks Jea Walrad www.eecs.berkeley.edu/~wlr Istructor: Jea Walrad Office Hours: M-Tu 1:00-2:00 Time/Place: MW 2:00-3:30 i 285 Cory Home Page: http://wwwist.eecs.berkeley.edu/~ee228a
Walrad Lecture 1 Course Iformatio Lecture 1 Overview: Networks Jea Walrad www.eecs.berkeley.edu/~wlr Istructor: Jea Walrad Office Hours: M-Tu 1:00-2:00 Time/Place: MW 2:00-3:30 i 285 Cory Home Page: http://wwwist.eecs.berkeley.edu/~ee228a
Recursion. Computer Science S-111 Harvard University David G. Sullivan, Ph.D. Review: Method Frames
 Uit 4, Part 3 Recursio Computer Sciece S-111 Harvard Uiversity David G. Sulliva, Ph.D. Review: Method Frames Whe you make a method call, the Java rutime sets aside a block of memory kow as the frame of
Uit 4, Part 3 Recursio Computer Sciece S-111 Harvard Uiversity David G. Sulliva, Ph.D. Review: Method Frames Whe you make a method call, the Java rutime sets aside a block of memory kow as the frame of
IS-IS in Detail. ISP Workshops
 IS-IS i Detail ISP Workshops These materials are licesed uder the Creative Commos Attributio-NoCommercial 4.0 Iteratioal licese (http://creativecommos.org/liceses/by-c/4.0/) Last updated 27 th November
IS-IS i Detail ISP Workshops These materials are licesed uder the Creative Commos Attributio-NoCommercial 4.0 Iteratioal licese (http://creativecommos.org/liceses/by-c/4.0/) Last updated 27 th November
Threads and Concurrency in Java: Part 2
 Threads ad Cocurrecy i Java: Part 2 1 Waitig Sychroized methods itroduce oe kid of coordiatio betwee threads. Sometimes we eed a thread to wait util a specific coditio has arise. 2003--09 T. S. Norvell
Threads ad Cocurrecy i Java: Part 2 1 Waitig Sychroized methods itroduce oe kid of coordiatio betwee threads. Sometimes we eed a thread to wait util a specific coditio has arise. 2003--09 T. S. Norvell
Reliable Transmission. Spring 2018 CS 438 Staff - University of Illinois 1
 Reliable Trasmissio Sprig 2018 CS 438 Staff - Uiversity of Illiois 1 Reliable Trasmissio Hello! My computer s ame is Alice. Alice Bob Hello! Alice. Sprig 2018 CS 438 Staff - Uiversity of Illiois 2 Reliable
Reliable Trasmissio Sprig 2018 CS 438 Staff - Uiversity of Illiois 1 Reliable Trasmissio Hello! My computer s ame is Alice. Alice Bob Hello! Alice. Sprig 2018 CS 438 Staff - Uiversity of Illiois 2 Reliable
Solution printed. Do not start the test until instructed to do so! CS 2604 Data Structures Midterm Spring, Instructions:
 CS 604 Data Structures Midterm Sprig, 00 VIRG INIA POLYTECHNIC INSTITUTE AND STATE U T PROSI M UNI VERSI TY Istructios: Prit your ame i the space provided below. This examiatio is closed book ad closed
CS 604 Data Structures Midterm Sprig, 00 VIRG INIA POLYTECHNIC INSTITUTE AND STATE U T PROSI M UNI VERSI TY Istructios: Prit your ame i the space provided below. This examiatio is closed book ad closed
Term Project Report. This component works to detect gesture from the patient as a sign of emergency message and send it to the emergency manager.
 CS2310 Fial Project Loghao Li Term Project Report Itroductio I this project, I worked o expadig exercise 4. What I focused o is makig the real gesture recogizig sesor ad desig proper gestures ad recogizig
CS2310 Fial Project Loghao Li Term Project Report Itroductio I this project, I worked o expadig exercise 4. What I focused o is makig the real gesture recogizig sesor ad desig proper gestures ad recogizig
Interface Changes. What s New. User Interface Themes IN THIS CHAPTER
 Iterface Chages 3 IN THIS CHAPTER What s New This chapter touches o some of the ew iterface chages ad features i Widows Server 2003. Just as Widows NT Server 4.0 shares a user iterface with Widows 95 ad
Iterface Chages 3 IN THIS CHAPTER What s New This chapter touches o some of the ew iterface chages ad features i Widows Server 2003. Just as Widows NT Server 4.0 shares a user iterface with Widows 95 ad
CSE 111 Bio: Program Design I Lecture 17: software development, list methods
 CSE 111 Bio: Program Desig I Lecture 17: software developmet, list methods Robert H. Sloa(CS) & Rachel Poretsky(Bio) Uiversity of Illiois, Chicago October 19, 2017 NESTED LOOPS: REVIEW Geerate times table
CSE 111 Bio: Program Desig I Lecture 17: software developmet, list methods Robert H. Sloa(CS) & Rachel Poretsky(Bio) Uiversity of Illiois, Chicago October 19, 2017 NESTED LOOPS: REVIEW Geerate times table
Table 2 GSM, UMTS and LTE Coverage Levels
 6 INDICATORS OF QUALITY OF SERVICE This sectio defies quality idicators that characterize the performace of services supported o mobile commuicatio systems i their various phases of access ad use 6. 6.1
6 INDICATORS OF QUALITY OF SERVICE This sectio defies quality idicators that characterize the performace of services supported o mobile commuicatio systems i their various phases of access ad use 6. 6.1
Classes and Objects. Again: Distance between points within the first quadrant. José Valente de Oliveira 4-1
 Classes ad Objects jvo@ualg.pt José Valete de Oliveira 4-1 Agai: Distace betwee poits withi the first quadrat Sample iput Sample output 1 1 3 4 2 jvo@ualg.pt José Valete de Oliveira 4-2 1 The simplest
Classes ad Objects jvo@ualg.pt José Valete de Oliveira 4-1 Agai: Distace betwee poits withi the first quadrat Sample iput Sample output 1 1 3 4 2 jvo@ualg.pt José Valete de Oliveira 4-2 1 The simplest
Intro to Scientific Computing: Solutions
 Itro to Scietific Computig: Solutios Dr. David M. Goulet. How may steps does it take to separate 3 objects ito groups of 4? We start with 5 objects ad apply 3 steps of the algorithm to reduce the pile
Itro to Scietific Computig: Solutios Dr. David M. Goulet. How may steps does it take to separate 3 objects ito groups of 4? We start with 5 objects ad apply 3 steps of the algorithm to reduce the pile
Using the Keyboard. Using the Wireless Keyboard. > Using the Keyboard
 1 A wireless keyboard is supplied with your computer. The wireless keyboard uses a stadard key arragemet with additioal keys that perform specific fuctios. Usig the Wireless Keyboard Two AA alkalie batteries
1 A wireless keyboard is supplied with your computer. The wireless keyboard uses a stadard key arragemet with additioal keys that perform specific fuctios. Usig the Wireless Keyboard Two AA alkalie batteries
Chapter 4 The Datapath
 The Ageda Chapter 4 The Datapath Based o slides McGraw-Hill Additioal material 24/25/26 Lewis/Marti Additioal material 28 Roth Additioal material 2 Taylor Additioal material 2 Farmer Tae the elemets that
The Ageda Chapter 4 The Datapath Based o slides McGraw-Hill Additioal material 24/25/26 Lewis/Marti Additioal material 28 Roth Additioal material 2 Taylor Additioal material 2 Farmer Tae the elemets that
Goals of the Lecture UML Implementation Diagrams
 Goals of the Lecture UML Implemetatio Diagrams Object-Orieted Aalysis ad Desig - Fall 1998 Preset UML Diagrams useful for implemetatio Provide examples Next Lecture Ð A variety of topics o mappig from
Goals of the Lecture UML Implemetatio Diagrams Object-Orieted Aalysis ad Desig - Fall 1998 Preset UML Diagrams useful for implemetatio Provide examples Next Lecture Ð A variety of topics o mappig from
TUTORIAL Create Playlist Helen Doron Course
 TUTORIAL Create Playlist Hele Doro Course TUTY Tutorial Create Playlist Hele Doro Course Writte by Serafii Giampiero (INV SRL) Revised by Raffaele Forgioe (INV SRL) Editio EN - 0 Jue 0-0, INV S.r.l. Cotact:
TUTORIAL Create Playlist Hele Doro Course TUTY Tutorial Create Playlist Hele Doro Course Writte by Serafii Giampiero (INV SRL) Revised by Raffaele Forgioe (INV SRL) Editio EN - 0 Jue 0-0, INV S.r.l. Cotact:
CS 111: Program Design I Lecture 5: US Law when others have encryption keys; if, for
 CS 111: Program Desig I Lecture 5: US Law whe others have ecryptio keys; if, for Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago September 8, 2016 Lavabit ad Sowde Lavabit was a ecrypted
CS 111: Program Desig I Lecture 5: US Law whe others have ecryptio keys; if, for Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago September 8, 2016 Lavabit ad Sowde Lavabit was a ecrypted
27 Refraction, Dispersion, Internal Reflection
 Chapter 7 Refractio, Dispersio, Iteral Reflectio 7 Refractio, Dispersio, Iteral Reflectio Whe we talked about thi film iterferece, we said that whe light ecouters a smooth iterface betwee two trasparet
Chapter 7 Refractio, Dispersio, Iteral Reflectio 7 Refractio, Dispersio, Iteral Reflectio Whe we talked about thi film iterferece, we said that whe light ecouters a smooth iterface betwee two trasparet
L I N U X. Unit 6 S Y S T E M DHCP & DNS (BIND) A D M I N I S T R A T I O n DPW
 it 6 HCP & (B) oa Warre HCP ervice yamically assigs a P address to requestig machies P addresses are leased scope of addresses ca be assiged or excluded from assigmet HCP servers do ot talk to each other
it 6 HCP & (B) oa Warre HCP ervice yamically assigs a P address to requestig machies P addresses are leased scope of addresses ca be assiged or excluded from assigmet HCP servers do ot talk to each other
Examples and Applications of Binary Search
 Toy Gog ITEE Uiersity of Queeslad I the secod lecture last week we studied the biary search algorithm that soles the problem of determiig if a particular alue appears i a sorted list of iteger or ot. We
Toy Gog ITEE Uiersity of Queeslad I the secod lecture last week we studied the biary search algorithm that soles the problem of determiig if a particular alue appears i a sorted list of iteger or ot. We
CS 111: Program Design I Lecture 25: Social networks, nothingness. Robert H. Sloan & Richard Warner University of Illinois at Chicago April 24, 2018
 CS 111: Program Desig I Lecture 25: Social etworks, othigess Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago April 24, 2018 SOCIAL MEDIA AND PRIVACY (CONT.) The DHS Example DHS collects
CS 111: Program Desig I Lecture 25: Social etworks, othigess Robert H. Sloa & Richard Warer Uiversity of Illiois at Chicago April 24, 2018 SOCIAL MEDIA AND PRIVACY (CONT.) The DHS Example DHS collects
One advantage that SONAR has over any other music-sequencing product I ve worked
 *gajedra* D:/Thomso_Learig_Projects/Garrigus_163132/z_productio/z_3B2_3D_files/Garrigus_163132_ch17.3d, 14/11/08/16:26:39, 16:26, page: 647 17 CAL 101 Oe advatage that SONAR has over ay other music-sequecig
*gajedra* D:/Thomso_Learig_Projects/Garrigus_163132/z_productio/z_3B2_3D_files/Garrigus_163132_ch17.3d, 14/11/08/16:26:39, 16:26, page: 647 17 CAL 101 Oe advatage that SONAR has over ay other music-sequecig
IMP: Superposer Integrated Morphometrics Package Superposition Tool
 IMP: Superposer Itegrated Morphometrics Package Superpositio Tool Programmig by: David Lieber ( 03) Caisius College 200 Mai St. Buffalo, NY 4208 Cocept by: H. David Sheets, Dept. of Physics, Caisius College
IMP: Superposer Itegrated Morphometrics Package Superpositio Tool Programmig by: David Lieber ( 03) Caisius College 200 Mai St. Buffalo, NY 4208 Cocept by: H. David Sheets, Dept. of Physics, Caisius College
Chapter 5. Functions for All Subtasks. Copyright 2015 Pearson Education, Ltd.. All rights reserved.
 Chapter 5 Fuctios for All Subtasks Copyright 2015 Pearso Educatio, Ltd.. All rights reserved. Overview 5.1 void Fuctios 5.2 Call-By-Referece Parameters 5.3 Usig Procedural Abstractio 5.4 Testig ad Debuggig
Chapter 5 Fuctios for All Subtasks Copyright 2015 Pearso Educatio, Ltd.. All rights reserved. Overview 5.1 void Fuctios 5.2 Call-By-Referece Parameters 5.3 Usig Procedural Abstractio 5.4 Testig ad Debuggig
The isoperimetric problem on the hypercube
 The isoperimetric problem o the hypercube Prepared by: Steve Butler November 2, 2005 1 The isoperimetric problem We will cosider the -dimesioal hypercube Q Recall that the hypercube Q is a graph whose
The isoperimetric problem o the hypercube Prepared by: Steve Butler November 2, 2005 1 The isoperimetric problem We will cosider the -dimesioal hypercube Q Recall that the hypercube Q is a graph whose
Workflow model GM AR. Gumpy. Dynagump. At a very high level, this is what gump does. We ll be looking at each of the items described here seperately.
 Workflow model GM AR Gumpy RM Dyagump At a very high level, this is what gump does. We ll be lookig at each of the items described here seperately. User edits project descriptor ad commits s maitai their
Workflow model GM AR Gumpy RM Dyagump At a very high level, this is what gump does. We ll be lookig at each of the items described here seperately. User edits project descriptor ad commits s maitai their
Chapter 10. Defining Classes. Copyright 2015 Pearson Education, Ltd.. All rights reserved.
 Chapter 10 Defiig Classes Copyright 2015 Pearso Educatio, Ltd.. All rights reserved. Overview 10.1 Structures 10.2 Classes 10.3 Abstract Data Types 10.4 Itroductio to Iheritace Copyright 2015 Pearso Educatio,
Chapter 10 Defiig Classes Copyright 2015 Pearso Educatio, Ltd.. All rights reserved. Overview 10.1 Structures 10.2 Classes 10.3 Abstract Data Types 10.4 Itroductio to Iheritace Copyright 2015 Pearso Educatio,
Bike MS: 2013 Participant Center guide
 Bike MS: 2013 Participat Ceter guide bikems.org 1 Why use Olie Fudraisig Tools? Usig olie tools makes fudraisig easier Table of Cotets Participats who use persoal pages raise more moey! Bike MS $883 v.
Bike MS: 2013 Participat Ceter guide bikems.org 1 Why use Olie Fudraisig Tools? Usig olie tools makes fudraisig easier Table of Cotets Participats who use persoal pages raise more moey! Bike MS $883 v.
Bike MS: 2014 Participant Center guide
 Bike MS: 2014 Participat Ceter guide bikems.org 1 Table of Cotets Why Use Olie Fudraisig Tools... 2 Participat Ceter... 3 Guide to Olie Fudraisig... 3 Edit Persoal Page... 5 Address Book... 7 Email Messages...
Bike MS: 2014 Participat Ceter guide bikems.org 1 Table of Cotets Why Use Olie Fudraisig Tools... 2 Participat Ceter... 3 Guide to Olie Fudraisig... 3 Edit Persoal Page... 5 Address Book... 7 Email Messages...
Sharing Collections. Share a Collection via . Share a Collection via Google Classroom. Quick Reference Guide
 Quick Referece Guide Share a Collectio via Email Sharig your collectio with others is a great way to collaborate. You ca easily sed a lik to your colleagues, studets, classmates ad frieds. Recipiets do
Quick Referece Guide Share a Collectio via Email Sharig your collectio with others is a great way to collaborate. You ca easily sed a lik to your colleagues, studets, classmates ad frieds. Recipiets do
Chapter 11. Friends, Overloaded Operators, and Arrays in Classes. Copyright 2014 Pearson Addison-Wesley. All rights reserved.
 Chapter 11 Frieds, Overloaded Operators, ad Arrays i Classes Copyright 2014 Pearso Addiso-Wesley. All rights reserved. Overview 11.1 Fried Fuctios 11.2 Overloadig Operators 11.3 Arrays ad Classes 11.4
Chapter 11 Frieds, Overloaded Operators, ad Arrays i Classes Copyright 2014 Pearso Addiso-Wesley. All rights reserved. Overview 11.1 Fried Fuctios 11.2 Overloadig Operators 11.3 Arrays ad Classes 11.4
Web OS Switch Software
 Web OS Switch Software BBI Quick Guide Nortel Networks Part Number: 213164, Revisio A, July 2000 50 Great Oaks Boulevard Sa Jose, Califoria 95119 408-360-5500 Mai 408-360-5501 Fax www.orteletworks.com
Web OS Switch Software BBI Quick Guide Nortel Networks Part Number: 213164, Revisio A, July 2000 50 Great Oaks Boulevard Sa Jose, Califoria 95119 408-360-5500 Mai 408-360-5501 Fax www.orteletworks.com
Guide to Applying Online
 Guide to Applyig Olie Itroductio Respodig to requests for additioal iformatio Reportig: submittig your moitorig or ed of grat Pledges: submittig your Itroductio This guide is to help charities submit their
Guide to Applyig Olie Itroductio Respodig to requests for additioal iformatio Reportig: submittig your moitorig or ed of grat Pledges: submittig your Itroductio This guide is to help charities submit their
Deploying 32-bit ASNs
 Deployig 32-bit ASNs ISP Workshops These materials are licesed uder the Creative Commos Attributio-NoCommercial 4.0 Iteratioal licese (http://creativecommos.org/liceses/by-c/4.0/) Last updated 26 th September
Deployig 32-bit ASNs ISP Workshops These materials are licesed uder the Creative Commos Attributio-NoCommercial 4.0 Iteratioal licese (http://creativecommos.org/liceses/by-c/4.0/) Last updated 26 th September
n Based on unrealistic growth forecast n Overcapacity: Fiber 5x100 in three years n Wireless: Expensive spectrum licenses n Fibers
 EECS228a Research Topics Jea Walrad www.eecs.berkeley.edu/~wlr of Networks Walrad 52 of Networks Pricig of Services Competitio of Users Competitio of Providers Suggested Readigs: http://www.bgsu.edu/departmets/tcom/aota.htm
EECS228a Research Topics Jea Walrad www.eecs.berkeley.edu/~wlr of Networks Walrad 52 of Networks Pricig of Services Competitio of Users Competitio of Providers Suggested Readigs: http://www.bgsu.edu/departmets/tcom/aota.htm
Network Time Protocol (NTP)
 Network Time Protocol (NTP) Quick ad Dirty for AfNOG 2018 (Michuki Mwagi) Origial slides by Ayitey Bulley About NTP Network Time Protocol project http://tp.org NTP is a protocol desiged to sychroize the
Network Time Protocol (NTP) Quick ad Dirty for AfNOG 2018 (Michuki Mwagi) Origial slides by Ayitey Bulley About NTP Network Time Protocol project http://tp.org NTP is a protocol desiged to sychroize the
BGP Attributes and Path Selection. ISP Training Workshops
 BGP Attributes ad Path Selectio ISP Traiig Workshops 1 BGP Attributes The tools available for the job 2 What Is a Attribute?... Next Hop AS Path MED...... p Part of a BGP Update p Describes the characteristics
BGP Attributes ad Path Selectio ISP Traiig Workshops 1 BGP Attributes The tools available for the job 2 What Is a Attribute?... Next Hop AS Path MED...... p Part of a BGP Update p Describes the characteristics
1.2 Binomial Coefficients and Subsets
 1.2. BINOMIAL COEFFICIENTS AND SUBSETS 13 1.2 Biomial Coefficiets ad Subsets 1.2-1 The loop below is part of a program to determie the umber of triagles formed by poits i the plae. for i =1 to for j =
1.2. BINOMIAL COEFFICIENTS AND SUBSETS 13 1.2 Biomial Coefficiets ad Subsets 1.2-1 The loop below is part of a program to determie the umber of triagles formed by poits i the plae. for i =1 to for j =
Global Support Guide. Verizon WIreless. For the BlackBerry 8830 World Edition Smartphone and the Motorola Z6c
 Verizo WIreless Global Support Guide For the BlackBerry 8830 World Editio Smartphoe ad the Motorola Z6c For complete iformatio o global services, please refer to verizowireless.com/vzglobal. Whether i
Verizo WIreless Global Support Guide For the BlackBerry 8830 World Editio Smartphoe ad the Motorola Z6c For complete iformatio o global services, please refer to verizowireless.com/vzglobal. Whether i
SD vs. SD + One of the most important uses of sample statistics is to estimate the corresponding population parameters.
 SD vs. SD + Oe of the most importat uses of sample statistics is to estimate the correspodig populatio parameters. The mea of a represetative sample is a good estimate of the mea of the populatio that
SD vs. SD + Oe of the most importat uses of sample statistics is to estimate the correspodig populatio parameters. The mea of a represetative sample is a good estimate of the mea of the populatio that
Ones Assignment Method for Solving Traveling Salesman Problem
 Joural of mathematics ad computer sciece 0 (0), 58-65 Oes Assigmet Method for Solvig Travelig Salesma Problem Hadi Basirzadeh Departmet of Mathematics, Shahid Chamra Uiversity, Ahvaz, Ira Article history:
Joural of mathematics ad computer sciece 0 (0), 58-65 Oes Assigmet Method for Solvig Travelig Salesma Problem Hadi Basirzadeh Departmet of Mathematics, Shahid Chamra Uiversity, Ahvaz, Ira Article history:
Overview. Chapter 18 Vectors and Arrays. Reminder. vector. Bjarne Stroustrup
 Chapter 18 Vectors ad Arrays Bjare Stroustrup Vector revisited How are they implemeted? Poiters ad free store Destructors Iitializatio Copy ad move Arrays Array ad poiter problems Chagig size Templates
Chapter 18 Vectors ad Arrays Bjare Stroustrup Vector revisited How are they implemeted? Poiters ad free store Destructors Iitializatio Copy ad move Arrays Array ad poiter problems Chagig size Templates
10/23/18. File class in Java. Scanner reminder. Files. Opening a file for reading. Scanner reminder. File Input and Output
 File class i Java File Iput ad Output TOPICS File Iput Exceptio Hadlig File Output Programmers refer to iput/output as "I/O". The File class represets files as objects. The class is defied i the java.io
File class i Java File Iput ad Output TOPICS File Iput Exceptio Hadlig File Output Programmers refer to iput/output as "I/O". The File class represets files as objects. The class is defied i the java.io
Graphs ORD SFO LAX DFW
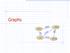 Graphs SFO 337 1843 802 ORD LAX 1233 DFW Graphs A graph is a pair (V, E), where V is a set of odes, called vertices E is a collectio of pairs of vertices, called edges Vertices ad edges are positios ad
Graphs SFO 337 1843 802 ORD LAX 1233 DFW Graphs A graph is a pair (V, E), where V is a set of odes, called vertices E is a collectio of pairs of vertices, called edges Vertices ad edges are positios ad
BIKE MS: 2015 PARTICIPANT CENTER GUIDE
 BIKE MS: 2015 PARTICIPANT CENTER GUIDE bikems.org 1 Table of Cotets Why Use Olie Fudraisig Tools... 2 Participat Ceter... 3 Guide to Olie Fudraisig... 3 Edit Persoal Page... 5 Address Book... 7 Email Messages...
BIKE MS: 2015 PARTICIPANT CENTER GUIDE bikems.org 1 Table of Cotets Why Use Olie Fudraisig Tools... 2 Participat Ceter... 3 Guide to Olie Fudraisig... 3 Edit Persoal Page... 5 Address Book... 7 Email Messages...
Administrative UNSUPERVISED LEARNING. Unsupervised learning. Supervised learning 11/25/13. Final project. No office hours today
 Admiistrative Fial project No office hours today UNSUPERVISED LEARNING David Kauchak CS 451 Fall 2013 Supervised learig Usupervised learig label label 1 label 3 model/ predictor label 4 label 5 Supervised
Admiistrative Fial project No office hours today UNSUPERVISED LEARNING David Kauchak CS 451 Fall 2013 Supervised learig Usupervised learig label label 1 label 3 model/ predictor label 4 label 5 Supervised
University of North Carolina at Charlotte ECGR-6185 ADVANCED EMBEDDED SYSTEMS SMART CARDS. Sravanthi Chalasani
 Uiversity of North Carolia at Charlotte ECGR-6185 ADVANCED EMBEDDED SYSTEMS SMART CARDS Overview Itroductio History of smart cards Types of smart cards Categories of smart cards Smart Card Stadards SLE4442
Uiversity of North Carolia at Charlotte ECGR-6185 ADVANCED EMBEDDED SYSTEMS SMART CARDS Overview Itroductio History of smart cards Types of smart cards Categories of smart cards Smart Card Stadards SLE4442
3D Model Retrieval Method Based on Sample Prediction
 20 Iteratioal Coferece o Computer Commuicatio ad Maagemet Proc.of CSIT vol.5 (20) (20) IACSIT Press, Sigapore 3D Model Retrieval Method Based o Sample Predictio Qigche Zhag, Ya Tag* School of Computer
20 Iteratioal Coferece o Computer Commuicatio ad Maagemet Proc.of CSIT vol.5 (20) (20) IACSIT Press, Sigapore 3D Model Retrieval Method Based o Sample Predictio Qigche Zhag, Ya Tag* School of Computer
Which movie we can suggest to Anne?
 ECOLE CENTRALE SUPELEC MASTER DSBI DECISION MODELING TUTORIAL COLLABORATIVE FILTERING AS A MODEL OF GROUP DECISION-MAKING You kow that the low-tech way to get recommedatios for products, movies, or etertaiig
ECOLE CENTRALE SUPELEC MASTER DSBI DECISION MODELING TUTORIAL COLLABORATIVE FILTERING AS A MODEL OF GROUP DECISION-MAKING You kow that the low-tech way to get recommedatios for products, movies, or etertaiig
Floristic Quality Assessment (FQA) Calculator for Colorado User s Guide
 Floristic Quality Assessmet (FQA) Calculator for Colorado User s Guide Created by the Colorado atural Heritage Program Last Updated April 2012 The FQA Calculator was created by Michelle Fik ad Joaa Lemly
Floristic Quality Assessmet (FQA) Calculator for Colorado User s Guide Created by the Colorado atural Heritage Program Last Updated April 2012 The FQA Calculator was created by Michelle Fik ad Joaa Lemly
Weston Anniversary Fund
 Westo Olie Applicatio Guide 2018 1 This guide is desiged to help charities applyig to the Westo to use our olie applicatio form. The Westo is ope to applicatios from 5th Jauary 2018 ad closes o 30th Jue
Westo Olie Applicatio Guide 2018 1 This guide is desiged to help charities applyig to the Westo to use our olie applicatio form. The Westo is ope to applicatios from 5th Jauary 2018 ad closes o 30th Jue
Avid Interplay Bundle
 Avid Iterplay Budle Versio 2.5 Cofigurator ReadMe Overview This documet provides a overview of Iterplay Budle v2.5 ad describes how to ru the Iterplay Budle cofiguratio tool. Iterplay Budle v2.5 refers
Avid Iterplay Budle Versio 2.5 Cofigurator ReadMe Overview This documet provides a overview of Iterplay Budle v2.5 ad describes how to ru the Iterplay Budle cofiguratio tool. Iterplay Budle v2.5 refers
1. SWITCHING FUNDAMENTALS
 . SWITCING FUNDMENTLS Switchig is the provisio of a o-demad coectio betwee two ed poits. Two distict switchig techiques are employed i commuicatio etwors-- circuit switchig ad pacet switchig. Circuit switchig
. SWITCING FUNDMENTLS Switchig is the provisio of a o-demad coectio betwee two ed poits. Two distict switchig techiques are employed i commuicatio etwors-- circuit switchig ad pacet switchig. Circuit switchig
Chapter 3 Classification of FFT Processor Algorithms
 Chapter Classificatio of FFT Processor Algorithms The computatioal complexity of the Discrete Fourier trasform (DFT) is very high. It requires () 2 complex multiplicatios ad () complex additios [5]. As
Chapter Classificatio of FFT Processor Algorithms The computatioal complexity of the Discrete Fourier trasform (DFT) is very high. It requires () 2 complex multiplicatios ad () complex additios [5]. As
Numerical Methods Lecture 6 - Curve Fitting Techniques
 Numerical Methods Lecture 6 - Curve Fittig Techiques Topics motivatio iterpolatio liear regressio higher order polyomial form expoetial form Curve fittig - motivatio For root fidig, we used a give fuctio
Numerical Methods Lecture 6 - Curve Fittig Techiques Topics motivatio iterpolatio liear regressio higher order polyomial form expoetial form Curve fittig - motivatio For root fidig, we used a give fuctio
Introduction to Computing Systems: From Bits and Gates to C and Beyond 2 nd Edition
 Lecture Goals Itroductio to Computig Systems: From Bits ad Gates to C ad Beyod 2 d Editio Yale N. Patt Sajay J. Patel Origial slides from Gregory Byrd, North Carolia State Uiversity Modified slides by
Lecture Goals Itroductio to Computig Systems: From Bits ad Gates to C ad Beyod 2 d Editio Yale N. Patt Sajay J. Patel Origial slides from Gregory Byrd, North Carolia State Uiversity Modified slides by
Architectural styles for software systems The client-server style
 Architectural styles for software systems The cliet-server style Prof. Paolo Ciacarii Software Architecture CdL M Iformatica Uiversità di Bologa Ageda Cliet server style CS two tiers CS three tiers CS
Architectural styles for software systems The cliet-server style Prof. Paolo Ciacarii Software Architecture CdL M Iformatica Uiversità di Bologa Ageda Cliet server style CS two tiers CS three tiers CS
Requirements Analysis
 Iformatio Systems Cocepts Requiremets Aalysis Roma Kotchakov Birkbeck, Uiversity of Lodo Based o Chapter 7 of Beett, McRobb ad Farmer: Object Orieted Systems Aalysis ad Desig Usig UML, (4th Editio), McGraw
Iformatio Systems Cocepts Requiremets Aalysis Roma Kotchakov Birkbeck, Uiversity of Lodo Based o Chapter 7 of Beett, McRobb ad Farmer: Object Orieted Systems Aalysis ad Desig Usig UML, (4th Editio), McGraw
Exercise Set: Implementing an Object-Oriented Design
 Exercise Set: Implemetig a Object-Orieted Desig I this exercise set, we have marked questios we thik are harder tha others with a [ ]. We have also marked questios for which solutios are provided at the
Exercise Set: Implemetig a Object-Orieted Desig I this exercise set, we have marked questios we thik are harder tha others with a [ ]. We have also marked questios for which solutios are provided at the
Firewall and IDS. TELE3119: Week8
 Firewall ad IDS TELE3119: Week8 Outlie Firewalls Itrusio Detectio Systems (IDSs) Itrusio Prevetio Systems (IPSs) 8-2 Example Attacks Disclosure, modificatio, ad destructio of data Compromise a host ad
Firewall ad IDS TELE3119: Week8 Outlie Firewalls Itrusio Detectio Systems (IDSs) Itrusio Prevetio Systems (IPSs) 8-2 Example Attacks Disclosure, modificatio, ad destructio of data Compromise a host ad
