Lab 1: OSPF With Three Routers
|
|
|
- Hugo Page
- 5 years ago
- Views:
Transcription
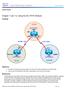
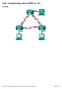
1 Lab 1: OSPF With Three Routers The physical topology is as shown in FIG Advanced OSPF Lab. FIG Advanced OSPF Lab Lab Exercise Your task is to configure the network in FIG Advanced OSPF Lab to allow full connectivity using OSPF. Router A should see routes for and be able to ping the loopback interface on router C and vice versa. Please feel free to try the lab without following the Lab Walk-Through section. Text written in courier new font indicates commands that can be entered on the router. Lab Objectives 1. Use the IP addressing scheme depicted in FIG X. 1. Set telnet access for the router to use the local login permissions of username banbury and the password ccna. 3. Configure the enable password to be cisco. 2. Configure IP addressing on all three routers. 3. Configure OSPF areas 0, 1, and Finally, test that the link is up and working by sending a ping across the link. Purpose Being able to configure and troubleshoot three routers will enable you to easily tackle issues that will arise in the lab. Lab Walk-Through 1. To set the IP addresses on an interface, you will need to do the following: Router#config t Router(config)#hostname RouterA RouterA(config)# RouterA(config)#interface serial 0/0 RouterA(config-if)#ip address RouterA(config-if)#no shutdown RouterA(config-if)#interface loopback 0 RouterA(config-if)#ip address RouterA(config-if)#^Z
2 RouterA# Router B: Router#config t Router(config)#hostname RouterB RouterB(config)# RouterB(config)#interface serial 0 RouterB(config-if)#ip address RouterB(config-if)#clock rate RouterB(config-if)#no shutdown RouterB(config-if)#interface serial 1 RouterB(config-if)#ip address RouterB(config-if)#clock rate RouterB(config-if)#no shutdown RouterB(config-if)#^Z RouterB# Router C: Router#config t Router#(config)#hostname RouterC RouterC(config)# RouterC(config)#interface serial 0/0 RouterC(config-if)#ip address RouterC(config-if)#no shutdown RouterC(config-if)#interface loopback 0 RouterC(config-if)#ip address RouterC(config-if)#^Z RouterC# Ping across the serial link now from A to B and then B to C. You will not be able to ping from A to C until you configure a routing protocol. 4. To set telnet access, you need to configure the VTY lines to allow telnet access. To do this, type (from configuration mode): RouterA(config)#line vty 0 4 RouterA(config-line)#login local RouterA(config-line)#exit RouterA(config)#username banbury password ccna Router B: RouterB(config)#line vty 0 4 RouterB(config-line)#login local RouterB(config-line)#exit RouterB(config)#username banbury password ccna Router C: RouterC(config)#line vty 0 4 RouterC(config-line)#login local RouterC(config-line)#exit RouterC(config)#username banbury password ccna 4. To set the enable password do the following: RouterA(config)#enable secret cisco Router B:
3 RouterB(config)#enable secret cisco Router C: RouterC(config)#enable secret cisco 5. To configure OSPF on a router, there are two steps: first, enable the routing protocol and second, specify the networks to be advertised by OSPF: RouterA(config)#router ospf 20 RouterA(config-router)#network area 0 RouterA(config-router)#network area 1 Router B: RouterB(config)#router ospf 20 RouterB(config-router)#network area 0 RouterB(config-router)#network area 0 Router C: RouterC(config)#router ospf 20 RouterC(config-router)#network area 0 RouterC(config-router)#network area 2 03:19:29: %OSPF-5-ADJCHG: Process 20, Nbr on Serial0 from LOADING to FULL, Loading Done 6. Make sure all the interfaces on the routers are up up with the show ip interface brief command. RouterA#show ip interface brief Interface IP-Address OK? Method Status Protocol Loopback YES manual up up Serial0/ YES manual up up Make sure you can see all of the networks including the loopback interfaces. RouterA#show ip route Codes: C - connected, S - static, I - IGRP, R - RIP, M - mobile, B - BGP D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2 E1 - OSPF external type 1, E2 - OSPF external type 2, E - EGP i - IS-IS, L1 - IS-IS level-1, L2 - IS-IS level-2, ia - IS-IS inter area * - candidate default, U - per-user static route, o - ODR P - periodic downloaded static route Gateway of last resort is not set
4 C /16 is directly connected, Loopback /32 is subnetted, 1 subnets O IA [110/129] via , 00:00:07, Serial0/0 C /30 is subnetted, 1 subnets is directly connected, Serial0/ /30 is subnetted, 1 subnets O [110/128] via ,00:00:07, Serial0/0 Check the protocol settings: RouterA#show ip protocols Routing Protocol is ospf 20 Outgoing update filter list for all interfaces is not set Incoming update filter list for all interfaces is not set Router ID It is an area border router Number of areas in this router is 2. 2 normal 0 stub 0 nssa Maximum path: 4 Routing for Networks: area area 0 Routing Information Sources: Gateway Distance Last Update :03: :03: :03:54 Distance: (default is 110) Ping the loopback interfaces: RouterA#ping Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds: Success rate is 100 percent (5/5), round-trip min/avg/max = 56/64/76 ms RouterA# 6. Now reload the routers. Show Runs RouterA#show run Building configuration... Current configuration : 697 bytes version 15.1 no service single-slot-reload-enable service timestamps debug uptime no service password-encryption hostname RouterA
5 enable secret 5 $1$SJxM$QL6.HXWDKQJBbfBa.tOg/0 username banbury password 0 ccna ip subnet-zero interface Loopback0 ip address interface Serial0/0 ip address router ospf 20 log-adjacency-changes network area 1 network area 0 ip classless no ip http server line con 0 line aux 0 line vty 0 4 login local end RouterB#show run Building configuration... version 15.1 no service single-slot-reload-enable service timestamps debug uptime no service password-encryption hostname RouterB enable secret 5 $1$C2Wp$S2ox/WQFXjyshkwnFX6Iu0 username banbury password 0 ccna ip subnet-zero interface Serial0 ip address clockrate interface Serial1 ip address clockrate 64000
6 router ospf 20 log-adjacency-changes network area 0 network area 0 line con 0 line aux 0 line vty 0 4 login local end RouterB# --- RouterC#show run Building configuration... Current configuration : 726 bytes version 15.1 service timestamps debug uptime no service password-encryption hostname RouterC enable secret 5 $1$1AZx$UzhYsYlIpc7I4vJI3ZI4U. username banbury password 0 cisco ip subnet-zero interface Loopback0 ip address interface Serial0/0 ip address router ospf 20 log-adjacency-changes network area 2 network area 0 ip classless no ip http server line con 0 line aux 0 line vty 0 4 login local end RouterC#
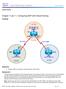
7 Lab 2: OSPF with Access-Lists Lab Exercise Your task is to configure the network in FIG OSPF with Access-list to allow full connectivity using OSPF. Router A is to block ICMP from Router C, and Router C is to deny any traffic on port 80. Please feel free to try the lab without following the Lab Walk-Through section. Router B Area 1 Loopback /16 Router A /30 S0.1 S0 (DCE) S1 (DCE).2.1 Area /30 Router C.2 S0 Loopback /16 Area 2 FIG OSPF with Access-lists Text written in courier new type indicates commands that can be entered on the router. Purpose A three-router lab is the typical scenario you will face in the CCNA exam. You must be comfortable with configuring three routers with a basic config and then applying a routing protocol and access-list. Lab Objectives 1. Use the IP-addressing scheme depicted in FIG OSPF with Access-list. 7. Set telnet access for the router to use the local login permissions of username banbury and the password ccna. 5. Configure the enable password to be cisco. 8. Configure IP addressing on all three routers. 9. Configure OSPF areas 0, 1, and Add an access-list on the serial interfaces of both routers A and C. Router A is to block all ping traffic from network Router C is to block all HTTP traffic from any network. Lab Walk-Through 1. Follow the configuration from the previous lab. 10. Configure the access-lists on both Routers A and C and apply them to the serial interfaces. RouterA(config)#access-list 100 deny icmp any RouterA(config)#access-list 100 permit ip any any RouterA(config)#interface serial 0/0 RouterA(config-if)#ip access-group 100 in
8 RouterC(config)#access-list 100 deny tcp any any eq 80 RouterC(config)#access-list 100 permit ip any any RouterC(config)#ip http server RouterC(config)#interface serial 0/0 RouterC(config-if)#ip access-group 100 in 6. Telnet from Router A to Router C. A normal telnet will work. However, a telnet on port 80 (HTTP) will fail. RouterA#telnet Trying Open User Access Verification Username: [EXIT BACK TO RouterA] RouterA#telnet Trying , Open exit HTTP/ Not Implemented Date: Mon, 01 Mar :22:17 UTC Content-type: text/html Expires: Thu, 16 Feb :00:00 GMT [H1]501 Not Implemented[/H1] [Connection to closed by foreign host] 11. Now ping Router A from Router C. The ping from the serial interface (the blocked network) will fail. A ping from loopback 0 ( ) will however, work. RouterC#ping Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds: U.U.U Success rate is 0 percent (0/5) RouterC#ping Protocol [ip]: Target IP address: Repeat count [5]: Datagram size [100]: Timeout in seconds [2]: Extended commands [n]: y Source address or interface: Type of service [0]: Set DF bit in IP header? [no]: Validate reply data? [no]: Data pattern [0xABCD]: Loose, Strict, Record, Timestamp, Verbose[none]: Sweep range of sizes [n]:
9 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds: Success rate is 100 percent (5/5), round-trip min/avg/max = 60/60/64 ms RouterC# Show Runs RouterA#show run Building configuration... Current configuration : 900 bytes version 15.1 no service single-slot-reload-enable service timestamps debug uptime no service password-encryption hostname RouterA enable secret 5 $1$rujI$BJ8GgiK8U9p5cdfXyApPr/ username banbury password 0 ccna interface Loopback0 ip address interface Serial0/0 ip address ip access-group 100 in router ospf 20 log-adjacency-changes network area 1 network area 0 ip classless no ip http server access-list 100 deny icmp any access-list 100 permit ip any any line con 0 password letmein login line 1 8 line aux 0 line vty 0 4 login local end
10 --- RouterB#show run Building configuration... Current configuration : 827 bytes version 15.1 no service single-slot-reload-enable service timestamps debug uptime no service password-encryption hostname RouterB enable secret 5 $1$oXft$UMJZc/BQzbfpeHVCApF3H0 username banbury password 0 ccna ip subnet-zero interface Serial0 ip address clockrate interface Serial1 ip address clockrate router ospf 20 log-adjacency-changes network area 0 network area 0 ip classless no ip http server line con 0 password letmein login line aux 0 line vty 0 4 login local end RouterB# --- RouterC#show run Building configuration... Current configuration: version 15.1
11 service timestamps debug uptime no service password-encryption hostname RouterC enable secret 5 $1$1AZx$UzhYsYlIpc7I4vJI3ZI4U. username banbury password 0 cisco ip subnet-zero interface Loopback0 ip address interface Serial0/0 ip address ip access-group 100 in no ip mroute-cache router ospf 20 network area 2 network area 0 ip classless access-list 100 deny tcp any any eq www access-list 100 permit ip any any line con 0 line 1 16 line aux 0 line vty 0 4 login local end RouterC# Lab 3: Multi-protocol Topology The physical topology is as shown in the figure below:
12 FIG Multi-Protocol Lab Lab Exercise This exercise will simulate a real word scenario in which a company might use two gateways to balance traffic going out into external networks (Internet for example). Your task is to configure the network in the diagram above to allow connectivity between PC1 and PC2 to the external network /32. PC1 will use Gateway 1 as the default gateway with Gateway 2 as secondary and PC2 will use Gateway 2 as the primary default gateway with Gateway 1 as secondary. PC1 will be located in VLAN 10, while PC2 will be located in VLAN20. HSRP will be configured for each VLAN between the two gateways. Gateway 1 will learn the external network through EIGRP, while Gateway 2 will learn about the external network through OSPF. The gateways will be configured with NAT. IP addressing details: External_router Fa0/0: /24 External_router Fa0/1: /24 Gateway1 Fa0/0: /24
13 Gateway1 Fa0/1.10: /24 Gateway1 Fa0/1.20: /24 Gateway2 Fa0/0: /24 Gateway2 Fa0/1.10: /24 Gateway2 Fa0/1.20: /24 VLAN 10 HSRP address: VLAN 20 HSRP address: PC1: /24, gateway: PC2: /24, gateway: VLAN 10 NAT Pool on Gateway1: VLAN 20 NAT Pool on Gateway1: VLAN 10 NAT Pool on Gateway2: VLAN 20 NAT Pool on Gateway2: Lab Objectives 1. Configure VLANs on the Switch; 2. Configure full Layer 3 addressing between the devices; 3. Configure EIGRP; 4. Configure OSPF; 5. Configure HSRP; 6. Configure NAT on the gateways; 7. Test connectivity. Purpose Practice the following technologies: OSPF EIGRP
14 VLANs HSRP Access-lists NAT Lab Walk-Through 1. Configure the necessary VLANs on the switch. We need trunk ports towards the gateways (carrying VLANs 10 and 20) and access ports towards the PCs. Switch(config)#int fa1/1 Switch(config)#sw mode trunk Switch(config)#sw trunk encapsulation dot Switch(config)#sw trunk all vlan 10,20 Switch(config)#no shut Switch(config)#int fa1/2 Switch(config)#sw mode trunk Switch(config)#sw trunk encapsulation dot Switch(config)#sw trunk all vlan 10,20 Switch(config)#no shut Switch(config)#int fa1/3 Switch(config)#sw mode access Switch(config)#sw access vlan 10 Switch(config)#no shut Switch(config)#int fa1/4 Switch(config)#sw mode access Switch(config)#sw access vlan 20 Switch(config)#no shut 2. Configure Layer 3 addressing on the devices. External_Router:
15 interface FastEthernet0/0 ip address interface FastEthernet0/1 ip address External_Router#sho ip int br Interface IP-Address OK? Method Status Protocol FastEthernet0/ YES manual up up Serial0/0 unassigned YES manual administratively down down FastEthernet0/ YES manual up up Serial0/1 unassigned YES manual administratively down down Loopback YES manual up up Gateway1: interface FastEthernet0/0 ip address interface FastEthernet0/1.10 encapsulation dot1q 10 ip address interface FastEthernet0/1.20 encapsulation dot1q 20 ip address Gateway1#sho ip int br
16 Any interface listed with OK? value NO does not have a valid configuration Interface IP-Address OK? Method Status Protocol FastEthernet0/ YES manual up up Serial0/0 unassigned YES manual administratively down down FastEthernet0/1 unassigned YES manual up up FastEthernet0/ YES manual up up FastEthernet0/ YES manual up up Serial0/1 unassigned YES manual administratively down down NVI0 unassigned NO unset up up Gateway2: interface FastEthernet0/0 ip address interface FastEthernet0/1.10 encapsulation dot1q 10 ip address interface FastEthernet0/1.20 encapsulation dot1q 20 ip address Gateway2#sho ip int br
17 Any interface listed with OK? value NO does not have a valid configuration Interface IP-Address OK? Method Status Protocol FastEthernet0/ YES manual up up Serial0/0 unassigned YES manual administratively down down FastEthernet0/1 unassigned YES manual up up FastEthernet0/ YES manual up up FastEthernet0/ YES manual up up Serial0/1 unassigned YES manual administratively down down NVI0 unassigned NO unset up up Note: you can use both real workstations or routers for PC1 and PC2. We have choosen to use routers for this exercise for simplicity. In order to configure a router to react as a workstation with 1 NIC, just disable IP routing, set the default gateway and the IP address on the interface. We will also configure the default gateway on PC1 and PC2. This is the HSRP address of VLAN10 for PC1 and the HSRP address of VLAN20 for PC2. PC1(config)#no ip routing PC1(config)#ip default-gateway PC1(config)#int fa0/0 PC1(config-if)#ip add PC2(config)#no ip routing
18 PC2(config)#ip default-gateway PC2(config)#int fa0/0 PC2(config-if)#ip add Configure EIGRP between the External_Router and Gateway1, advertise /32 towards the internal network via EIGRP. External_Router(config)#router eigrp 100 External_Router(config-router)#network External_Router(config-router)#network External_Router(config-router)#no auto-summary Gateway1(config)#router eigrp 100 Gateway1(config-router)#network Gateway1(config-router)#no auto-summary External_Router#show ip eigrp neighbors IP-EIGRP neighbors for process 100 H Address Interface Hold Uptime SRTT RTO Q Seq Cnt Num (sec) (ms) Fa0/ :10: Gateway1#show ip eigrp neighbors IP-EIGRP neighbors for process 100 H Address Interface Hold Uptime SRTT RTO Q Seq
19 Cnt Num (sec) (ms) Fa0/ :09: Gateway1#show ip route eigrp /32 is subnetted, 1 subnets D [90/409600] via , 01:10:24, FastEthernet0/0 We can see the /32 network is being learned by Gateway1 via EIGRP. 4. Configure OSPF between the External_Router and Gateway2, advertise /32 towards the internal network via OSPF. Yes, we will advertise the same subnet via both EIGRP and OSPF to different neighbors. This is possible in Cisco IOS. External_Router(config)#int fa0/1 External_Router(config-if)#ip ospf 1 area 0 External_Router(config-if)#lo0 External_Router(config-if)#ip ospf 1 area 0 Gateway2(config)#int fa0/1 Gateway2(config-if)#ip ospf 1 area 0 External_Router#show ip ospf nei Neighbor ID Pri State Dead Time Address Interface
20 FULL/DR 00:00: FastEthernet0/1 Gateway2#show ip ospf nei Neighbor ID Pri State Dead Time Address Interface FULL/BDR 00:00: FastEthernet0/0 Gateway2#show ip route ospf /32 is subnetted, 1 subnets O [110/11] via , 01:21:28, FastEthernet0/0 We can see the /32 network is being learned by Gateway2 via OSPF. 5. Configure HSRP for both VLANs. Gateway1 will be the primary gateway for VLAN10 and Gateway2 will be the primary gateway for VLAN20. If either of the routers fails, the other will assume default gateway functionality. We will configure Gateway1 with priority 110 for VLAN 10 and with priority 100 for VLAN 20 (default) and the other way around for Gateway 2. Gateway1(config)#int fa0/1.10 Gateway1(config-subif)#standby 10 ip Gateway1(config-subif)#standby 10 priority 110 Gateway1(config-subif)#standby 10 preempt Gateway1(config)#int fa0/1.20 Gateway1(config-subif)#standby 20 ip Gateway1(config-subif)#standby 20 preempt
21 Gateway2(config)#int fa0/1.10 Gateway2(config-subif)#standby 10 ip Gateway2(config-subif)#standby 10 preempt Gateway2(config)#int fa0/1.20 Gateway2(config-subif)#standby 20 ip Gateway2(config-subif)#standby 20 priority 110 Gateway2(config-subif)#standby 20 preempt Gateway1#show standby brief P indicates configured to preempt. Interface Grp Pri P State Active Standby Virtual IP Fa0/ P Active local Fa0/ P Standby local Gateway2#show standby brief P indicates configured to preempt. Interface Grp Pri P State Active Standby Virtual IP Fa0/ P Standby local Fa0/ P Active local
22 6. Configure NAT. On Gateway1 we want to translate the internal address for any packet sourced from VLAN 10 to In the same time, we want to translate the internal address for any packet souced from VLAN 20 to Even though traffic originated in VLAN 20 will not reach Gateway1 in a normal day of operations, this will happen if Gateway2 is down, as Gateway1 will assume the role of primary HSRP gateway. So we want to configure rules for both VLAN 10 and VLAN 20 on both routers. On Gateway2, we will assign an external IP address of for traffic sourced in VLAN 10 and of for traffic sourced in VLAN 20. We will also configure PAT (also known NAT overload) on both devices, so multiple internal sources in the same VLAN can share the same external IP address. Gateway1(config)#int fa0/0 Gateway1(config-if)#ip nat outside Gateway1(config)#int fa0/1.10 Gateway1(config-if)#ip nat inside Gateway1(config)#int fa0/1.20 Gateway1(config-if)#ip nat inside Gateway1(config)#ip nat inside source list VLAN10 pool VLAN10_OUT overload Gateway1(config)#ip nat inside source list VLAN20 pool VLAN20_OUT overload Gateway1(config)#ip nat pool VLAN10_OUT netmask Gateway1(config)#ip nat pool VLAN20_OUT netmask Gateway1(config)#ip access-list standard VLAN10 Gateway1(config-std-nacl)# permit Gateway1(config)#ip access-list standard VLAN20 Gateway1(config-std-nacl)# permit Gateway2(config)#int fa0/0 Gateway2(config-if)#ip nat outside
23 Gateway2(config)#int fa0/1.10 Gateway2(config-if)#ip nat inside Gateway2(config)#int fa0/1.20 Gateway2(config-if)#ip nat inside Gateway2(config)#ip nat inside source list VLAN10 pool VLAN10_OUT overload Gateway2(config)#ip nat inside source list VLAN20 pool VLAN20_OUT overload Gateway2(config)#ip nat pool VLAN10_OUT netmask Gateway2(config)#ip nat pool VLAN20_OUT netmask Gateway2(config)#ip access-list standard VLAN10 Gateway2(config-std-nacl)# permit Gateway2(config)#ip access-list standard VLAN20 Gateway2(config-std-nacl)# permit Test connectivity from PC1 and PC2 towards the external network. We will issue a ping both from PC1 and PC2 towards the external destination and we will then check traffic from each PC will hit a different gateway router. In this way traffic is load balanced toward the external networks. PC1#ping Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds:. Success rate is 80 percent (4/5), round-trip min/avg/max = 24/44/72 ms
24 PC2#ping Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to , timeout is 2 seconds:. Success rate is 80 percent (4/5), round-trip min/avg/max = 16/62/140 ms Gateway1#sho ip nat translations Pro Inside global Inside local Outside local Outside global icmp : : : :3 Gateway2#sho ip nat translations Pro Inside global Inside local Outside local Outside global icmp : : : :5 As you can see from the output of show ip nat translation, traffic sourced from (VLAN 10) is translated on Gateway1 and traffic sourced from (VLAN 20) is translated on Gateway2. Show Runs External_Router#show run Building configuration... Current configuration : 1305 bytes version 15.1 service timestamps debug datetime msec
25 service timestamps log datetime msec no service password-encryption hostname External_Router boot-start-marker boot-end-marker no aaa new-model memory-size iomem 5 no ip icmp rate-limit unreachable ip cef no ip domain lookup multilink bundle-name authenticated archive log config hidekeys ip tcp synwait-time 5 ip ssh version 1 interface Loopback0 ip address ip ospf 1 area 0 interface FastEthernet0/0 ip address duplex auto speed auto interface Serial0/0 no ip address shutdown clock rate interface FastEthernet0/1 ip address ip ospf 1 area 0 duplex auto speed auto interface Serial0/1 no ip address shutdown clock rate
26 router eigrp 100 network network no auto-summary router ospf 1 log-adjacency-changes ip forward-protocol nd no ip http server no ip http secure-server no cdp log mismatch duplex control-plane line con 0 exec-timeout 0 0 privilege level 15 logging synchronous line aux 0 exec-timeout 0 0 privilege level 15 logging synchronous line vty 0 4 login End Gateway1#show run Building configuration... Current configuration : 1907 bytes version 15.1 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption hostname Gateway1 boot-start-marker boot-end-marker
27 no aaa new-model memory-size iomem 5 no ip icmp rate-limit unreachable ip cef no ip domain lookup multilink bundle-name authenticated archive log config hidekeys ip tcp synwait-time 5 ip ssh version 1 interface FastEthernet0/0 ip address ip nat outside ip virtual-reassembly duplex auto speed auto interface Serial0/0 no ip address shutdown clock rate interface FastEthernet0/1 no ip address duplex auto speed auto interface FastEthernet0/1.10 encapsulation dot1q 10 ip address ip nat inside ip virtual-reassembly standby 10 ip standby 10 priority 110 standby 10 preempt interface FastEthernet0/1.20 encapsulation dot1q 20 ip address ip nat inside ip virtual-reassembly standby 20 ip
28 standby 20 preempt interface Serial0/1 no ip address shutdown clock rate router eigrp 100 network no auto-summary ip forward-protocol nd no ip http server no ip http secure-server ip nat pool VLAN10_OUT netmask ip nat pool VLAN20_OUT netmask ip nat inside source list VLAN10 pool VLAN10_OUT overload ip nat inside source list VLAN20 pool VLAN20_OUT overload ip access-list standard VLAN10 permit ip access-list standard VLAN20 permit no cdp log mismatch duplex control-plane line con 0 exec-timeout 0 0 privilege level 15 logging synchronous line aux 0 exec-timeout 0 0 privilege level 15 logging synchronous line vty 0 4 login End Gateway2#show run
29 Building configuration... Current configuration : 1907 bytes version 15.1 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption hostname Gateway2 boot-start-marker boot-end-marker no aaa new-model memory-size iomem 5 no ip icmp rate-limit unreachable ip cef no ip domain lookup multilink bundle-name authenticated archive log config hidekeys ip tcp synwait-time 5 ip ssh version 1 interface FastEthernet0/0 ip address ip nat outside ip virtual-reassembly ip ospf 1 area 0 duplex auto speed auto interface Serial0/0 no ip address shutdown clock rate interface FastEthernet0/1 no ip address duplex auto speed auto
30 interface FastEthernet0/1.10 encapsulation dot1q 10 ip address ip nat inside ip virtual-reassembly standby 10 ip standby 10 preempt interface FastEthernet0/1.20 encapsulation dot1q 20 ip address ip nat inside ip virtual-reassembly standby 20 ip standby 20 priority 110 standby 20 preempt interface Serial0/1 no ip address shutdown clock rate router ospf 1 log-adjacency-changes ip forward-protocol nd no ip http server no ip http secure-server ip nat pool VLAN20_OUT netmask ip nat pool VLAN10_OUT netmask ip nat inside source list VLAN10 pool VLAN10_OUT overload ip nat inside source list VLAN20 pool VLAN20_OUT overload ip access-list standard VLAN10 permit ip access-list standard VLAN20 permit no cdp log mismatch duplex control-plane line con 0 exec-timeout 0 0
31 privilege level 15 logging synchronous line aux 0 exec-timeout 0 0 privilege level 15 logging synchronous line vty 0 4 login End PC1#show run Building configuration... Current configuration : 1186 bytes version 15.1 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption hostname PC1 boot-start-marker boot-end-marker no aaa new-model memory-size iomem 5 no ip routing no ip icmp rate-limit unreachable no ip cef no ip domain lookup multilink bundle-name authenticated archive log config hidekeys ip tcp synwait-time 5 ip ssh version 1 interface FastEthernet0/0 ip address
32 no ip route-cache duplex auto speed auto interface Serial0/0 no ip address no ip route-cache shutdown clock rate interface FastEthernet0/1 no ip address no ip route-cache shutdown duplex auto speed auto interface Serial0/1 no ip address no ip route-cache shutdown clock rate ip default-gateway ip forward-protocol nd no ip http server no ip http secure-server no cdp log mismatch duplex control-plane line con 0 exec-timeout 0 0 privilege level 15 logging synchronous line aux 0 exec-timeout 0 0 privilege level 15 logging synchronous line vty 0 4 login end
33 PC2#show run Building configuration... Current configuration : 1208 bytes version 15.1 service timestamps debug datetime msec service timestamps log datetime msec no service password-encryption hostname PC2 boot-start-marker boot-end-marker no aaa new-model memory-size iomem 5 no ip routing no ip icmp rate-limit unreachable no ip cef no ip domain lookup multilink bundle-name authenticated ip tcp synwait-time 5 ip ssh version 1 interface FastEthernet0/0 ip address no ip route-cache duplex auto speed auto interface Serial0/0 no ip address no ip route-cache shutdown clock rate interface FastEthernet0/1 ip address no ip route-cache shutdown duplex auto speed auto interface Serial0/1
34 no ip address no ip route-cache shutdown clock rate ip default-gateway ip forward-protocol nd line con 0 exec-timeout 0 0 privilege level 15 logging synchronous line aux 0 exec-timeout 0 0 privilege level 15 logging synchronous line vty 0 4 login end
35
Lab Configuring and Verifying Standard IPv4 ACLs (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Lab Configuring Dynamic and Static NAT (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Lab Configuring Dynamic and Static NAT (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/1 209.165.201.18 255.255.255.252 N/A ISP S0/0/0 (DCE)
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/1 209.165.201.18 255.255.255.252 N/A ISP S0/0/0 (DCE)
Advanced IPv6 Training Course. Lab Manual. v1.3 Page 1
 Advanced IPv6 Training Course Lab Manual v1.3 Page 1 Network Diagram AS66 AS99 10.X.0.1/30 2001:ffXX:0:01::a/127 E0/0 R 1 E1/0 172.X.255.1 2001:ffXX::1/128 172.16.0.X/24 2001:ff69::X/64 E0/1 10.X.0.5/30
Advanced IPv6 Training Course Lab Manual v1.3 Page 1 Network Diagram AS66 AS99 10.X.0.1/30 2001:ffXX:0:01::a/127 E0/0 R 1 E1/0 172.X.255.1 2001:ffXX::1/128 172.16.0.X/24 2001:ff69::X/64 E0/1 10.X.0.5/30
Lab Configuring 802.1Q Trunk-Based Inter-VLAN Routing (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Lab Configuring Port Address Translation (PAT) (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
(Instructor Version) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
TELECOMMUNICATION MANAGEMENT AND NETWORKS
 QUAID-E-AWAM UNIVERSITY OF ENGINEERING SCIENCE AND TECHNOLOGY, NAWABSHAH TELECOMMUNICATION MANAGEMENT AND NETWORKS LAB # 3 CONFIGURING INTERFACES OF ROUTER AND SWITCH Topology Diagram Addressing Table
QUAID-E-AWAM UNIVERSITY OF ENGINEERING SCIENCE AND TECHNOLOGY, NAWABSHAH TELECOMMUNICATION MANAGEMENT AND NETWORKS LAB # 3 CONFIGURING INTERFACES OF ROUTER AND SWITCH Topology Diagram Addressing Table
Lab Configuring Per-Interface Inter-VLAN Routing (Instructor Version)
 (Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
(Instructor Version) Instructor Note: Red font color or Gray highlights indicate text that appears in the instructor copy only. Topology Addressing Table Objectives Device Interface IP Address Subnet Mask
Lab Configuring Per-Interface Inter-VLAN Routing (Solution)
 (Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
(Solution) Topology Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/0 192.168.20.1 255.255.255.0 N/A G0/1 192.168.10.1 255.255.255.0 N/A S1 VLAN 10 192.168.10.11
Lab Configuring IPv4 Static and Default Routes (Solution)
 (Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
(Solution) Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.0.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A R3 G0/1 192.168.1.1 255.255.255.0
Case Study 2: Frame Relay and OSPF Solution
 Case Study 2: Frame Relay and OSPF Solution Objective In this case study, you troubleshoot a complex scenario involving Frame Relay and Open Shortest Path First (OSPF). Figure 2-1 shows the topology for
Case Study 2: Frame Relay and OSPF Solution Objective In this case study, you troubleshoot a complex scenario involving Frame Relay and Open Shortest Path First (OSPF). Figure 2-1 shows the topology for
Basic Router Configuration
 This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
This section includes information about some basic router configuration, and contains the following sections: Default Configuration, on page 1 Configuring Global Parameters, on page 2 Configuring Gigabit
KIM DONNERBORG / RTS. Cisco Lab Øvelse Af Kim Donnerborg / RTS. Side 0 af 8
 KIM DONNERBORG / RTS Side 0 af 8 INDHOLDSFORTEGNELSE Lab: Basic Router Configuration... 2 Topology Diagram... 2 Addressing Table... 2 Learning Objectives... 2 Scenario... 2 Task 1: Cable the Network....
KIM DONNERBORG / RTS Side 0 af 8 INDHOLDSFORTEGNELSE Lab: Basic Router Configuration... 2 Topology Diagram... 2 Addressing Table... 2 Learning Objectives... 2 Scenario... 2 Task 1: Cable the Network....
Lab 8.5.2: Troubleshooting Enterprise Networks 2
 Lab 8.5.2: Troubleshooting Enterprise Networks 2 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 192.168.10.1 255.255.255.0 N/A R1 Fa0/1 192.168.11.1 255.255.255.0
Lab 8.5.2: Troubleshooting Enterprise Networks 2 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/0 192.168.10.1 255.255.255.0 N/A R1 Fa0/1 192.168.11.1 255.255.255.0
Lab Configuring and Verifying Standard IPv4 ACLs Topology
 Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 10 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Module 9, Assignment 7
 Module 9, Assignment 7 7.2.3 Control Router via Console (in Packet Tracer) 1. Prepare a Cisco 1841 Router (see figure 6-9). 2. Prepare a PC for administration. 3. Prepare a console cable and plug the serial
Module 9, Assignment 7 7.2.3 Control Router via Console (in Packet Tracer) 1. Prepare a Cisco 1841 Router (see figure 6-9). 2. Prepare a PC for administration. 3. Prepare a console cable and plug the serial
RR> RR> RR>en RR# RR# RR# RR# *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 RR#
 RR> RR> RR>en *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 term len 0 show run Building configuration... Current configuration : 2568 bytes version 15.4 service timestamps debug
RR> RR> RR>en *Oct 2 04:57:03.684: %AMDP2_FE-6-EXCESSCOLL: Ethernet0/2 TDR=0, TRC=0 term len 0 show run Building configuration... Current configuration : 2568 bytes version 15.4 service timestamps debug
CONFIGURATION DU SWITCH
 Current configuration : 2037 bytes version 12.2 no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption hostname Switch no aaa new-model ip subnet-zero
Current configuration : 2037 bytes version 12.2 no service pad service timestamps debug uptime service timestamps log uptime no service password-encryption hostname Switch no aaa new-model ip subnet-zero
CIS 83 LAB 3 - EIGRP Rich Simms September 23, Objective. Scenario. Topology
 CIS 83 LAB 3 - EIGRP Rich Simms September 23, 2006 Objective The objective of this lab is to become familiar setting up and configuring EIGRP on three routers. EIGRP is a Cisco proprietary distance-vector
CIS 83 LAB 3 - EIGRP Rich Simms September 23, 2006 Objective The objective of this lab is to become familiar setting up and configuring EIGRP on three routers. EIGRP is a Cisco proprietary distance-vector
Lab Configuring Basic RIPv2 (Solution)
 (Solution) Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 15 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway
(Solution) Topology 2017 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 15 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway
Chapter 6 Lab 6-3, Gateway Load Balancing Protocol (GLBP) INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 6 Lab 6-3, Gateway Load Balancing Protocol (GLBP) INSTRUCTOR VERSION Topology Objectives Configure trunking, VTP, and inter-vlan routing using router-on-a stick Configure GLBP Configure
CCNPv7.1 SWITCH Chapter 6 Lab 6-3, Gateway Load Balancing Protocol (GLBP) INSTRUCTOR VERSION Topology Objectives Configure trunking, VTP, and inter-vlan routing using router-on-a stick Configure GLBP Configure
Default Gateway Fa0/ N/A. Device Interface IP Address Subnet Mask
 Felix Rohrer Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/1 10.0.0.1 255.255.255.128 N/A S0/0/0 172.16.0.1 255.255.255.252 N/A S0/0/1 172.16.0.9 255.255.255.252
Felix Rohrer Topology Addressing Table Device Interface IP Address Subnet Mask Default Gateway Fa0/1 10.0.0.1 255.255.255.128 N/A S0/0/0 172.16.0.1 255.255.255.252 N/A S0/0/1 172.16.0.9 255.255.255.252
Adapted from the Synchronization example in g/case/studies/icsbgp4.html
 Adapted from the Synchronization example in http://www.cisco.com/en/us/docs/internetworkin g/case/studies/icsbgp4.html When an AS provides transit service to other ASs when there are non-bgp routers in
Adapted from the Synchronization example in http://www.cisco.com/en/us/docs/internetworkin g/case/studies/icsbgp4.html When an AS provides transit service to other ASs when there are non-bgp routers in
Lab Troubleshooting IPv4 and IPv6 Static Routes (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Lab Troubleshooting Using traceroute Instructor Version 2500
 Lab 9.3.4 Troubleshooting Using traceroute Instructor Version 2500 294-833 CCNA 2: Routers and Routing Basics v 3.1 - Lab 9.3.4 Copyright 2003, Cisco Systems, Inc. Objective Use the traceroute Cisco IOS
Lab 9.3.4 Troubleshooting Using traceroute Instructor Version 2500 294-833 CCNA 2: Routers and Routing Basics v 3.1 - Lab 9.3.4 Copyright 2003, Cisco Systems, Inc. Objective Use the traceroute Cisco IOS
Lab Configuring IGRP Instructor Version 2500
 Lab 7.3.5 Configuring IGRP Instructor Version 2500 Objective Setup IP an addressing scheme using class C networks. Configure IGRP on routers. Background/Preparation Cable a network similar to the one in
Lab 7.3.5 Configuring IGRP Instructor Version 2500 Objective Setup IP an addressing scheme using class C networks. Configure IGRP on routers. Background/Preparation Cable a network similar to the one in
Lab 2.8.1: Basic Static Route Configuration
 Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 Fa0/0 172.16.3.1 255.255.255.0 N/A S0/0/0 172.16.2.1 255.255.255.0 N/A Fa0/0 172.16.1.1 255.255.255.0 N/A R2
Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 Fa0/0 172.16.3.1 255.255.255.0 N/A S0/0/0 172.16.2.1 255.255.255.0 N/A Fa0/0 172.16.1.1 255.255.255.0 N/A R2
Lab Configuring OSPF Timers 2500 Series
 Lab 2.3.5 Configuring OSPF Timers 2500 Series Objective Setup an IP addressing scheme for OSPF area. Configure and verify OSPF routing. Modify OSPF interface timers to adjust efficiency of network. Background/Preparation
Lab 2.3.5 Configuring OSPF Timers 2500 Series Objective Setup an IP addressing scheme for OSPF area. Configure and verify OSPF routing. Modify OSPF interface timers to adjust efficiency of network. Background/Preparation
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and
 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
CIS 83 LAB 2 - Single Area OSPF Rich Simms September 12, Objective. Scenario. Topology
 CIS 83 LAB 2 - Single Area OSPF Rich Simms September 12, 2006 Objective The objective of this lab is to become familiar setting up and configuring OSPF on three routers for a single area. OSPF is our first
CIS 83 LAB 2 - Single Area OSPF Rich Simms September 12, 2006 Objective The objective of this lab is to become familiar setting up and configuring OSPF on three routers for a single area. OSPF is our first
Lab Configuring and Verifying Standard ACLs Topology
 Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 9 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Seattle Cisco Users Group
 Seattle Cisco Users Group CCNA Lab Project Joe Rinehart MBA, CCIE #14256 CCNP/DP/VP December 18, 2010 Table of Contents 1. Introduction... 3 1.1. The CCNA Certification... 3 1.2. Purpose of the Lab Project...
Seattle Cisco Users Group CCNA Lab Project Joe Rinehart MBA, CCIE #14256 CCNP/DP/VP December 18, 2010 Table of Contents 1. Introduction... 3 1.1. The CCNA Certification... 3 1.2. Purpose of the Lab Project...
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem
 How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
How to Configure a Cisco Router Behind a Non-Cisco Cable Modem Document ID: 19268 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations Verify
Seattle Cisco Users Group
 Seattle Cisco Users Group CCNA Lab Project #3 Joe Rinehart MBA, CCIE #14256 CCNP/DP/VP June 10, 2011 Table of Contents 1. Introduction... 3 1.1. The CCNA Certification... 3 1.2. Purpose of the Lab Project...
Seattle Cisco Users Group CCNA Lab Project #3 Joe Rinehart MBA, CCIE #14256 CCNP/DP/VP June 10, 2011 Table of Contents 1. Introduction... 3 1.1. The CCNA Certification... 3 1.2. Purpose of the Lab Project...
QUESTION/SOLUTION SET LAB 4
 QUESTION/SOLUTION SET LAB 4 CCIE lab Routing & Switching (v4.0) lab:4 Updated Testing Guidelines 1. The equipment on the rack assigned to you is physically Cabled and should not be tempered with. 2. Router
QUESTION/SOLUTION SET LAB 4 CCIE lab Routing & Switching (v4.0) lab:4 Updated Testing Guidelines 1. The equipment on the rack assigned to you is physically Cabled and should not be tempered with. 2. Router
Chapter 7 Lab 7-2, Using the AS_PATH Attribute
 Chapter 7 Topology Objectives Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter BGP routes based on their source AS numbers.
Chapter 7 Topology Objectives Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter BGP routes based on their source AS numbers.
Implementing EIGRP. Global Knowledge Training LLC L7-1
 L7 Implementing EIGRP Global Knowledge Training LLC L7-1 Objectives In this lab you will configure EIGRP on your pod routers. The core router is already configured for EIGRP. You will first remove the
L7 Implementing EIGRP Global Knowledge Training LLC L7-1 Objectives In this lab you will configure EIGRP on your pod routers. The core router is already configured for EIGRP. You will first remove the
Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION Topology Objectives Background Secure the server farm using private VLANs. Secure the staff VLAN from the student VLAN. Secure the
CCNPv7.1 SWITCH Chapter 10 Lab 10-2, Securing VLANs INSTRUCTOR VERSION Topology Objectives Background Secure the server farm using private VLANs. Secure the staff VLAN from the student VLAN. Secure the
Configuration and Management of Networks
 Configuring BGP using the AS_PATH attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter
Configuring BGP using the AS_PATH attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use the AS_PATH attribute to filter
Configuring GRE Tunnel Over Cable
 Configuring GRE Tunnel Over Cable Document ID: 12084 Introduction Before You Begin Conventions Prerequisites Components Used Background Theory Configure Network Diagram Configurations Verify Troubleshoot
Configuring GRE Tunnel Over Cable Document ID: 12084 Introduction Before You Begin Conventions Prerequisites Components Used Background Theory Configure Network Diagram Configurations Verify Troubleshoot
RealCiscoLAB.com. Chapter 6 Lab 6-2, Using the AS_PATH Attribute. Topology. Objectives. Background. CCNPv6 ROUTE
 RealCiscoLAB.com CCNPv6 ROUTE Chapter 6 Lab 6-2, Using the AS_PATH Attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use
RealCiscoLAB.com CCNPv6 ROUTE Chapter 6 Lab 6-2, Using the AS_PATH Attribute Topology Objectives Background Use BGP commands to prevent private AS numbers from being advertised to the outside world. Use
Lab Troubleshooting Routing Issues with show ip route and show ip protocols Instructor Version 2500
 Lab 9.3.5 Troubleshooting Routing Issues with show ip route and show ip protocols Instructor Version 2500 Objective Use the show ip route and show ip protocol commands to diagnose a routing configuration
Lab 9.3.5 Troubleshooting Routing Issues with show ip route and show ip protocols Instructor Version 2500 Objective Use the show ip route and show ip protocol commands to diagnose a routing configuration
Lab Configuring OSPF Authentication 2500 Series
 Lab 2.3.4 Configuring OSPF Authentication 2500 Series Objective Setup an IP addressing scheme for Open Shortest Path First (OSPF) area. Configure and verify OSPF routing. Introduce OSPF authentication
Lab 2.3.4 Configuring OSPF Authentication 2500 Series Objective Setup an IP addressing scheme for Open Shortest Path First (OSPF) area. Configure and verify OSPF routing. Introduce OSPF authentication
Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED
 Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED Topology Objectives Background For IBGP peers to correctly exchange routing information, use the next-hop-self command with
Chapter 6 Lab 6-3, Configuring IBGP and EBGP Sessions, Local Preference, and MED Topology Objectives Background For IBGP peers to correctly exchange routing information, use the next-hop-self command with
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and
 This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
This document is exclusive property of Cisco Systems, Inc. Permission is granted to print and copy this document for non-commercial distribution and exclusive use by instructors in the CCNA Exploration:
Configuring EtherChannel
 L4 Configuring EtherChannel Global Knowledge Training LLC L4-1 Objectives In this lab you will first verify that one of the parallel connections to the core switch is blocked by STP. You will then configure
L4 Configuring EtherChannel Global Knowledge Training LLC L4-1 Objectives In this lab you will first verify that one of the parallel connections to the core switch is blocked by STP. You will then configure
Lab b Simple DMZ Extended Access Lists Instructor Version 2500
 Lab 11.2.3b Simple DMZ Extended Access Lists Instructor Version 2500 Objective In this lab, the use of extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 372-833 CCNA 2:
Lab 11.2.3b Simple DMZ Extended Access Lists Instructor Version 2500 Objective In this lab, the use of extended access lists to create a simple DeMilitarized Zone (DMZ) will be learned. 372-833 CCNA 2:
Chapter 7 Lab 7-1, Configuring BGP with Default Routing
 Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
Chapter 7 Topology Objectives Configure BGP to exchange routing information with two ISPs. Background The International Travel Agency (ITA) relies extensively on the Internet for sales. For this reason,
Lab VTY Restriction Instructor Version 2500
 Lab 11.2.6 VTY Restriction Instructor Version 2500 NOTE: The loopback entry in this graphic is not required in the lab. Objective Scenario Use the access-class and line commands to control Telnet access
Lab 11.2.6 VTY Restriction Instructor Version 2500 NOTE: The loopback entry in this graphic is not required in the lab. Objective Scenario Use the access-class and line commands to control Telnet access
Troubleshooting VLANs and Trunks
 L2 Troubleshooting VLANs and Trunks Global Knowledge Training LLC L2-1 Objectives In this lab you will download configuration files into PxSW s running configuration to introduce VLAN and trunking issues
L2 Troubleshooting VLANs and Trunks Global Knowledge Training LLC L2-1 Objectives In this lab you will download configuration files into PxSW s running configuration to introduce VLAN and trunking issues
EIGRP Lab / lo1. .1 lo / /30
 EIGRP Lab 172,16,1.0/24.1 lo1 192.168.20.0/30.2.1 Merida fa0 fa0 Vargas lo2.1 lo2.5.1 lo1 192.168.30.0/24 172.16.2.0/24 192.168.20.4.0/30 Scenario: Loopback0 is used for RouterID Loopback1 is a virtual
EIGRP Lab 172,16,1.0/24.1 lo1 192.168.20.0/30.2.1 Merida fa0 fa0 Vargas lo2.1 lo2.5.1 lo1 192.168.30.0/24 172.16.2.0/24 192.168.20.4.0/30 Scenario: Loopback0 is used for RouterID Loopback1 is a virtual
Lab 1.1.4c Configuring Static NAT Addresses
 Lab 1.1.4c Configuring Static NAT Addresses Objective Configure a router to use network address translation (NAT) to convert internal IP addresses, typically private addresses, into outside public addresses.
Lab 1.1.4c Configuring Static NAT Addresses Objective Configure a router to use network address translation (NAT) to convert internal IP addresses, typically private addresses, into outside public addresses.
Study Guide. Using ACLs to Secure Networks
 CHAPTER 5 ACLs The Study Guide portion of this chapter uses a combination of matching, multiple-choice, and open-ended question exercises to test your knowledge of the various types of access control lists
CHAPTER 5 ACLs The Study Guide portion of this chapter uses a combination of matching, multiple-choice, and open-ended question exercises to test your knowledge of the various types of access control lists
Chapter 4 Lab 4-2, Redistribution Between EIGRP and OSPF
 Chapter 4 Lab 4-2, Redistribution Between EIGRP and OSPF Topology Objectives Review EIGRP and OSPF configuration. Redistribute into EIGRP. Redistribute into OSPF. Summarize routes in EIGRP. Filter routes
Chapter 4 Lab 4-2, Redistribution Between EIGRP and OSPF Topology Objectives Review EIGRP and OSPF configuration. Redistribute into EIGRP. Redistribute into OSPF. Summarize routes in EIGRP. Filter routes
Lab- Troubleshooting Basic EIGRP for 1Pv4
 Lab- Troubleshooting Basic EIGRP for 1Pv4 Topology G0/0 G0/0 PC-A PC-C 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 27 Addressing Table efault Gateway
Lab- Troubleshooting Basic EIGRP for 1Pv4 Topology G0/0 G0/0 PC-A PC-C 2013 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 27 Addressing Table efault Gateway
Configuring Redundant Routing on the VPN 3000 Concentrator
 Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
Configuring Redundant Routing on the VPN 3000 Concentrator Document ID: 13354 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Router Configurations
RealCiscoLAB.com. Chapter 2 Lab 2-2, EIGRP Load Balancing. Topology. Objectives. Background. CCNPv6 ROUTE
 RealCiscoLAB.com CCNPv6 ROUTE Chapter 2 Lab 2-2, EIGRP Load Balancing Topology Objectives Background Review a basic EIGRP configuration. Explore the EIGRP topology table. Identify successors, feasible
RealCiscoLAB.com CCNPv6 ROUTE Chapter 2 Lab 2-2, EIGRP Load Balancing Topology Objectives Background Review a basic EIGRP configuration. Explore the EIGRP topology table. Identify successors, feasible
Lab 5-1 Hot Standby Router Protocol
 Lab 5-1 Hot Standby Router Protocol Topology Diagram Objective Configure inter-vlan routing with HSRP to provide redundant, fault tolerant routing to the internal network. Scenario Step 1 HSRP provides
Lab 5-1 Hot Standby Router Protocol Topology Diagram Objective Configure inter-vlan routing with HSRP to provide redundant, fault tolerant routing to the internal network. Scenario Step 1 HSRP provides
Lab Configuring IPv6 Static and Default Routes (Solution)
 (Solution) Topology Addressing Table Device Interface IPv6 Address / Prefix Length Default Gateway R1 G0/1 2001:DB8:ACAD:A::/64 eui-64 N/A S0/0/1 FC00::1/64 N/A R3 G0/1 2001:DB8:ACAD:B::/64 eui-64 N/A
(Solution) Topology Addressing Table Device Interface IPv6 Address / Prefix Length Default Gateway R1 G0/1 2001:DB8:ACAD:A::/64 eui-64 N/A S0/0/1 FC00::1/64 N/A R3 G0/1 2001:DB8:ACAD:B::/64 eui-64 N/A
Scenario Labs NETSIM FOR CCNA LAB MANUAL. Scenario Labs. Boson NetSim for CCNA Lab Manual
 NETSIM FOR CCNA LAB MANUAL Welcome to the NetSim. The goal of these labs is to introduce you to the limited number of commands needed to enable a technology, without addressing extra commands that could
NETSIM FOR CCNA LAB MANUAL Welcome to the NetSim. The goal of these labs is to introduce you to the limited number of commands needed to enable a technology, without addressing extra commands that could
STUDENT LAB GUIDE CCNA ( )
 STUDENT LAB GUIDE CCNA (640-802) Developed By, Router Infotech Career Academy LAB: 09 Static Route Configuration Objective: To configure & implement Static Route successfully on said devices and test its
STUDENT LAB GUIDE CCNA (640-802) Developed By, Router Infotech Career Academy LAB: 09 Static Route Configuration Objective: To configure & implement Static Route successfully on said devices and test its
Building the Routing Table. Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles
 Building the Routing Table Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles Introducing the Routing Table R1# show ip route Codes: C - connected,
Building the Routing Table Introducing the Routing Table Directly Connected Networks Static Routing Dynamic Routing Routing Table Principles Introducing the Routing Table R1# show ip route Codes: C - connected,
IPv6 Tunnel through an IPv4 Network
 IPv6 Tunnel through an IPv4 Network Document ID: 25156 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations (Manual IPv6 Mode) Configurations
IPv6 Tunnel through an IPv4 Network Document ID: 25156 Contents Introduction Prerequisites Requirements Components Used Conventions Configure Network Diagram Configurations (Manual IPv6 Mode) Configurations
RealCiscoLAB.com. Configure inter-vlan routing with HSRP to provide redundant, fault-tolerant routing to the internal network.
 RealCiscoLAB.com CCNPv6 SWITCH Hot Standby Router Protocol Topology Objective Background Configure inter-vlan routing with HSRP to provide redundant, fault-tolerant routing to the internal network. Hot
RealCiscoLAB.com CCNPv6 SWITCH Hot Standby Router Protocol Topology Objective Background Configure inter-vlan routing with HSRP to provide redundant, fault-tolerant routing to the internal network. Hot
Configuring HSRP. Global Knowledge Training LLC L5-1
 L5 Configuring HSRP Global Knowledge Training LLC L5-1 Objectives In this lab you will examine the hot standby router protocol (HSRP). First you will configure PxR2 similar to PxR1, so they are both possible
L5 Configuring HSRP Global Knowledge Training LLC L5-1 Objectives In this lab you will examine the hot standby router protocol (HSRP). First you will configure PxR2 similar to PxR1, so they are both possible
Lab - Troubleshooting Connectivity Issues
 Lab - Troubleshooting Connectivity Issues Topology Addressing Table R1 ISP Objectives Device Interface IP Address Subnet Mask Default Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/0 10.1.1.1 255.255.255.252
Lab - Troubleshooting Connectivity Issues Topology Addressing Table R1 ISP Objectives Device Interface IP Address Subnet Mask Default Gateway G0/1 192.168.1.1 255.255.255.0 N/A S0/0/0 10.1.1.1 255.255.255.252
Lab Verifying NAT and PAT Configuration
 Lab 1.1.5 Verifying NAT and PAT Configuration Objective Configure a router for Network Address Translation (NAT) and Port Address Translation (PAT) Test the configuration and verify NAT/PAT statistics
Lab 1.1.5 Verifying NAT and PAT Configuration Objective Configure a router for Network Address Translation (NAT) and Port Address Translation (PAT) Test the configuration and verify NAT/PAT statistics
Lab Configuring Static Routes Instructor Version 2500
 Lab 6.1.6 Configuring Static Routes Instructor Version 2500 Objective Configure static routes between routers to allow data transfer between routers without the use of dynamic routing protocols. Background/Preparation
Lab 6.1.6 Configuring Static Routes Instructor Version 2500 Objective Configure static routes between routers to allow data transfer between routers without the use of dynamic routing protocols. Background/Preparation
Route between VLANs using a 3560 switch with an internal route processor using Cisco Express Forwarding (CEF).
 Lab 3- Part I Inter-VLAN routing with a Multilayer Switch Configuration and Management of Networks - 2014 Topology Objective Route between VLANs using a 3560 switch with an internal route processor using
Lab 3- Part I Inter-VLAN routing with a Multilayer Switch Configuration and Management of Networks - 2014 Topology Objective Route between VLANs using a 3560 switch with an internal route processor using
Chapter 6 Lab 6-1, First Hop Redundancy Protocols HSRP and VRRP INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 6 Lab 6-1, First Hop Redundancy Protocols HSRP and VRRP INSTRUCTOR VERSION Topology Objectives Configure inter-vlan routing with HSRP and load balancing Configure HSRP authentication
CCNPv7.1 SWITCH Chapter 6 Lab 6-1, First Hop Redundancy Protocols HSRP and VRRP INSTRUCTOR VERSION Topology Objectives Configure inter-vlan routing with HSRP and load balancing Configure HSRP authentication
VPN Connection through Zone based Firewall Router Configuration Example
 VPN Connection through Zone based Firewall Router Configuration Example Document ID: 112051 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
VPN Connection through Zone based Firewall Router Configuration Example Document ID: 112051 Contents Introduction Prerequisites Requirements Components Used Conventions Background Information Configure
IP NAT Troubleshooting. Solutions. Luke Bibby, CCIE #45527
 IP NAT Troubleshooting Solutions Luke Bibby, CCIE #45527 Quick Overview of Scenario Solutions Scenario #1 R2 s E0/0 should be NAT inside not NAT outside ACL 100 is configured incorrectly NAT policy missing
IP NAT Troubleshooting Solutions Luke Bibby, CCIE #45527 Quick Overview of Scenario Solutions Scenario #1 R2 s E0/0 should be NAT inside not NAT outside ACL 100 is configured incorrectly NAT policy missing
Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION
 CCNPv7.1 SWITCH Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION Topology Objectives Implement a Layer 3 EtherChannel Implement Static Routing Implement Inter-VLAN Routing Background Cisco's switching
CCNPv7.1 SWITCH Chapter 5 Lab 5-1 Inter-VLAN Routing INSTRUCTOR VERSION Topology Objectives Implement a Layer 3 EtherChannel Implement Static Routing Implement Inter-VLAN Routing Background Cisco's switching
Chapter 6: Network Layer
 Chapter 6: Network Layer Introduction to Networks Intro to Networks v5 Network Layer Intro to Networks v5 2 The Network Layer End to End Transport processes Addressing end devices Encapsulation of Packets
Chapter 6: Network Layer Introduction to Networks Intro to Networks v5 Network Layer Intro to Networks v5 2 The Network Layer End to End Transport processes Addressing end devices Encapsulation of Packets
Easy Virtual Network Configuration Example
 Easy Virtual Network Configuration Example Document ID: 117974 Contributed by Fabrice Ducomble, Cisco TAC Engineer. Aug 04, 2014 Contents Introduction Prerequisites Requirements Components Used Background
Easy Virtual Network Configuration Example Document ID: 117974 Contributed by Fabrice Ducomble, Cisco TAC Engineer. Aug 04, 2014 Contents Introduction Prerequisites Requirements Components Used Background
Lab Configuring Basic Router Settings with IOS CLI (Instructor Version Optional Lab)
 (Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
(Instructor Version Optional Lab) Instructor Note: Red font color or gray highlights indicate text that appears in the instructor copy only. Optional activities are designed to enhance understanding and/or
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only.
 Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
Support for policy-based routing applies to the Barracuda Web Security Gateway running version 6.x only. Transparently Routing Web Traffic to the Barracuda Web Security Gateway This article demonstrates
ROUTE Lab Guide Labs powered by
 OUTE Lab Guide 300-101 ii OUTE 300-101 Lab Guide LM20170908/BV1.0 iii 25 C e n tur y Blvd., S te. 5 0 0, N a s hvill e, T N 37214 B o s o n.c o m To perform the labs referenced in this book, please download
OUTE Lab Guide 300-101 ii OUTE 300-101 Lab Guide LM20170908/BV1.0 iii 25 C e n tur y Blvd., S te. 5 0 0, N a s hvill e, T N 37214 B o s o n.c o m To perform the labs referenced in this book, please download
Chapter 1 Lab 1-1, Basic RIPng and Default Gateway Configuration
 Chapter 1 Lab 1-1, Basic RIPng and Default Gateway Configuration Topology Objectives Configure IPv6 addressing. Configure and verify RIPng on R1 and R2. Configure IPv6 static routes between R2 and R3.
Chapter 1 Lab 1-1, Basic RIPng and Default Gateway Configuration Topology Objectives Configure IPv6 addressing. Configure and verify RIPng on R1 and R2. Configure IPv6 static routes between R2 and R3.
Distance vector Routing protocols. 2000, Cisco Systems, Inc. 9-1
 Distance vector Routing protocols 2000, Cisco Systems, Inc. 9-1 IP Routing Configuration Tasks Router configuration Select routing protocols Specify networks or interfaces RIP Network 172.16.0.0 IGRP,
Distance vector Routing protocols 2000, Cisco Systems, Inc. 9-1 IP Routing Configuration Tasks Router configuration Select routing protocols Specify networks or interfaces RIP Network 172.16.0.0 IGRP,
Lab Routing Between an External Router and an Internal Route Processor
 Lab 5.3.4.2 Routing Between an External Router and an Internal Route Processor Objective Scenario The purpose of this lab is to configure routing between an internal route processor and an external router.
Lab 5.3.4.2 Routing Between an External Router and an Internal Route Processor Objective Scenario The purpose of this lab is to configure routing between an internal route processor and an external router.
Lab Configuring and Verifying Extended ACLs Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway R1 G0/1 192.168.10.1
Lab Establishing and Verifying a Telnet Connection Instructor Version 2500
 Lab 4.2.2 Establishing and Verifying a Telnet Connection Instructor Version 2500 Objective Establish a Telnet connection to a remote router. Verify that the application layer between source and destination
Lab 4.2.2 Establishing and Verifying a Telnet Connection Instructor Version 2500 Objective Establish a Telnet connection to a remote router. Verify that the application layer between source and destination
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology
 Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab - Troubleshooting Standard IPv4 ACL Configuration and Placement Topology 2016 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives
Lab - Troubleshooting ACL Configuration and Placement Topology
 Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
Topology 2015 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. Page 1 of 8 Addressing Table Objectives Device Interface IP Address Subnet Mask Default Gateway HQ G0/1 192.168.1.1
Chapter 8 Lab 8-2, Using Manual IPv6 Tunnels with EIGRP for IPv6
 Chapter 8 Lab 8-2, Using Manual IPv6 Tunnels with EIGRP for IPv6 Topology Objectives Configure EIGRP for IPv4. Create a manual IPv6 tunnel. Configure EIGRP for IPv6 across the tunnel. Background In this
Chapter 8 Lab 8-2, Using Manual IPv6 Tunnels with EIGRP for IPv6 Topology Objectives Configure EIGRP for IPv4. Create a manual IPv6 tunnel. Configure EIGRP for IPv6 across the tunnel. Background In this
CCNA Semester 2 labs. Labs for chapters 2 10
 CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
CCNA Semester 2 labs Labs for chapters 2 10 2.2.2.5 Lab - Configuring IPv4 Static and Default Routes 2.3.2.4 Lab - Troubleshooting Static Routes 3.2.1.9 Lab - Configuring Basic RIPv2 5.2.2.9 Lab - Configuring
Configuring Network Access to the GGSN
 CHAPTER 7 This chapter describes how to configure access from the gateway GPRS support node (GGSN) to a serving GPRS support node (SGSN), public data network (PDN), and optionally to a Virtual Private
CHAPTER 7 This chapter describes how to configure access from the gateway GPRS support node (GGSN) to a serving GPRS support node (SGSN), public data network (PDN), and optionally to a Virtual Private
IOS Router : Easy VPN (EzVPN) in Network Extension Mode (NEM) with Split tunnelling Configuration Example
 IOS Router : Easy VPN (EzVPN) in Network Extension Mode (NEM) with Split tunnelling Configuration Example Document ID: 63098 Contents Introduction Prerequisites Requirements Components Used Conventions
IOS Router : Easy VPN (EzVPN) in Network Extension Mode (NEM) with Split tunnelling Configuration Example Document ID: 63098 Contents Introduction Prerequisites Requirements Components Used Conventions
L2TP IPsec Support for NAT and PAT Windows Clients
 L2TP IPsec Support for NAT and PAT Windows Clients The L2TP IPsec Support for NAT and PAT Windows Clients feature allows mulitple Windows client to connect to an IPsec-enabled Cisco IOS Layer 2 Tunneling
L2TP IPsec Support for NAT and PAT Windows Clients The L2TP IPsec Support for NAT and PAT Windows Clients feature allows mulitple Windows client to connect to an IPsec-enabled Cisco IOS Layer 2 Tunneling
Lab Designing and Implementing a VLSM Addressing Scheme. Topology. Objectives. Background / Scenario
 CSNB214 Packet Tracer Lab Designing and Implementing a VLSM Addressing Scheme Topology Objectives Part 1: Examine Network Requirements Part 2: Design the VLSM Address Scheme Part 3: Cable and Configure
CSNB214 Packet Tracer Lab Designing and Implementing a VLSM Addressing Scheme Topology Objectives Part 1: Examine Network Requirements Part 2: Design the VLSM Address Scheme Part 3: Cable and Configure
Chapter 2 Lab 2-1, EIGRP Configuration, Bandwidth, and Adjacencies
 Chapter 2 Lab 2-1, EIGRP Configuration, Bandwidth, and Adjacencies Topology Objectives Background Configure EIGRP on multiple routers. Configure the bandwidth command to modify the EIGRP metric. Verify
Chapter 2 Lab 2-1, EIGRP Configuration, Bandwidth, and Adjacencies Topology Objectives Background Configure EIGRP on multiple routers. Configure the bandwidth command to modify the EIGRP metric. Verify
Lab 5: Basic VLAN Configuration
 Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 172.17.99.11 255.255.255.0 N/A S2 VLAN 99 172.17.99.12 255.255.255.0 N/A S3 VLAN 99 172.17.99.13
Topology Diagram Addressing Table Device (Hostname) Interface IP Address Subnet Mask Default Gateway S1 VLAN 99 172.17.99.11 255.255.255.0 N/A S2 VLAN 99 172.17.99.12 255.255.255.0 N/A S3 VLAN 99 172.17.99.13
Cisco Press CCIE Practical Studies CCIE Practice Lab: Enchilada Solutions
 Cisco Press CCIE Practical Studies CCIE Practice Lab: Solutions Cisco Press CCIE Practical Studies CCIE Practice Lab: LAB Book Chapter Book Page The 18 1161 Overview... 3 Technical Details... 3 Table 54-1:
Cisco Press CCIE Practical Studies CCIE Practice Lab: Solutions Cisco Press CCIE Practical Studies CCIE Practice Lab: LAB Book Chapter Book Page The 18 1161 Overview... 3 Technical Details... 3 Table 54-1:
Troubleshooting Network analysis Software communication tests and development Education. Protocols used for communication (10 seconds capture)
 Lab 1 Wireshark Wireshark is an open source and free packet analyser used for many purposes, such as: Troubleshooting Network analysis Software communication tests and development Education This reports
Lab 1 Wireshark Wireshark is an open source and free packet analyser used for many purposes, such as: Troubleshooting Network analysis Software communication tests and development Education This reports
Lab 3.5.1: Basic Frame Relay
 Lab 3.5.1: Basic Frame Relay Topology Diagram Addressing Table Device Interface IP Address Subnet Mask R1 R2 Default Gateway Fa0/0 192.168.10.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A S0/0/1
Lab 3.5.1: Basic Frame Relay Topology Diagram Addressing Table Device Interface IP Address Subnet Mask R1 R2 Default Gateway Fa0/0 192.168.10.1 255.255.255.0 N/A S0/0/1 10.1.1.1 255.255.255.252 N/A S0/0/1
Lab: Basic Static Route Configuration
 Lab: Basic Static Route onfiguration Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 Fa0/0 172.16.3.1 255.255.255.0 N/A S0/0/0 172.16.2.1 255.255.255.0 N/A
Lab: Basic Static Route onfiguration Topology Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway R1 Fa0/0 172.16.3.1 255.255.255.0 N/A S0/0/0 172.16.2.1 255.255.255.0 N/A
CCNP TSHOOT. Quick Reference Sheet Exam
 CCNP TSHOOT Quick Reference Sheet Exam 300-135 Chapter 1. Network Principles Troubleshooting Steps Problem Identification Collection of Information Examination and Action Plan Verification Basic Troubleshooting
CCNP TSHOOT Quick Reference Sheet Exam 300-135 Chapter 1. Network Principles Troubleshooting Steps Problem Identification Collection of Information Examination and Action Plan Verification Basic Troubleshooting
Design and Implementation Plan for Network Based on the ALOHA Point of Sale System. Proposed by Jedadiah Casey. Introduction
 Design and Implementation Plan for Network Based on the ALOHA Point of Sale System Proposed by Jedadiah Casey Introduction The goal of this design document is to provide a framework of suggested implementation
Design and Implementation Plan for Network Based on the ALOHA Point of Sale System Proposed by Jedadiah Casey Introduction The goal of this design document is to provide a framework of suggested implementation
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM
 Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
Chapter 10 - Configure ASA Basic Settings and Firewall using ASDM This lab has been updated for use on NETLAB+ Topology Note: ISR G1 devices use FastEthernet interfaces instead of GigabitEthernet interfaces.
