CCNA 1 Chapter v5.1 Answers 100%
|
|
|
- Merryl Peters
- 6 years ago
- Views:
Transcription
1 CCNA 1 Chapter v5.1 Answers 100% 1. A newly hired netwrk technician is given the task f rdering new hardware fr a small business with a large grwth frecast. Which primary factr shuld the technician be cncerned with when chsing the new devices? devices with a fixed number and type f interfaces devices that have supprt fr netwrk mnitring redundant devices devices with supprt fr mdularity 2. Which netwrk design cnsideratin wuld be mre imprtant t a large crpratin than t a small business? Internet ruter firewall lw prt density switch redundancy 3. Which tw traffic types require delay sensitive delivery? (Chse tw.) web FTP vice vide 4. A netwrk administratr fr a small cmpany is cntemplating hw t scale the netwrk ver the next three years t accmmdate prjected grwth. Which three types f infrmatin shuld be used t plan fr netwrk grwth? (Chse three.) human resurce plicies and prcedures fr all emplyees in the cmpany dcumentatin f the current physical and lgical tplgies analysis f the netwrk traffic based n prtcls, applicatins, and services used n the netwrk histry and missin statement f the cmpany inventry f the devices that are currently used n the netwrk listing f the current emplyees and their rle in the cmpany 5. Which tw statements describe hw t assess traffic flw patterns and netwrk traffic types using a prtcl analyzer? (Chse tw.) Capture traffic n the weekends when mst emplyees are ff wrk. Only capture traffic in the areas f the netwrk that receive mst f the traffic such as the data center. Capture traffic during peak utilizatin times t get a gd representatin f the different traffic types. Perfrm the capture n different netwrk segments. CCNA 5 Page 1
2 Only capture WAN traffic because traffic t the web is respnsible fr the largest amunt f traffic n a netwrk. 6. Sme ruters and switches in a wiring clset malfunctined after an air cnditining unit failed. What type f threat des this situatin describe? cnfiguratin envirnmental electrical maintenance 7. Which type f netwrk threat is intended t prevent authrized users frm accessing resurces? DS attacks access attacks recnnaissance attacks trust explitatin 8. Which tw actins can be taken t prevent a successful netwrk attack n an server accunt? (Chse tw.) Never send the passwrd thrugh the netwrk in a clear text. Never use passwrds that need the Shift key. Use servers frm different vendrs. Distribute servers thrughut the building, placing them clse t the stakehlders. Limit the number f unsuccessful attempts t lg in t the server. 9. Which firewall feature is used t ensure that packets cming int a netwrk are legitimate respnses initiated frm internal hsts? applicatin filtering stateful packet inspectin URL filtering packet filtering 10. What is the purpse f the netwrk security authenticatin functin? t require users t prve wh they are t determine which resurces a user can access t keep track f the actins f a user t prvide challenge and respnse questins 11. A netwrk administratr is issuing the lgin blck-fr 180 attempts 2 within 30 cmmand n a ruter. Which threat is the netwrk administratr trying t prevent? a user wh is trying t guess a passwrd t access the ruter a wrm that is attempting t access anther part f the netwrk CCNA 5 Page 2
3 an unidentified individual wh is trying t access the netwrk equipment rm a device that is trying t inspect the traffic n a link 12. What is the purpse f using SSH t cnnect t a ruter? It allws a ruter t be cnfigured using a graphical interface. It allws a secure remte cnnectin t the ruter cmmand line interface. It allws the ruter t be mnitred thrugh a netwrk management applicatin. It allws secure transfer f the IOS sftware image frm an unsecure wrkstatin r server. 13. Which tw steps are required befre SSH can be enabled n a Cisc ruter? (Chse tw.) Give the ruter a hst name and dmain name. Create a banner that will be displayed t users when they cnnect. Generate a set f secret keys t be used fr encryptin and decryptin. Set up an authenticatin server t handle incming cnnectin requests. Enable SSH n the physical interfaces where the incming cnnectin requests will be received. 14. What is the purpse f issuing the cmmands cd nvram: then dir at the privilege exec mde f a ruter? t clear the cntent f the NVRAM t direct all new files t the NVRAM t list the cntent f the NVRAM t cpy the directries frm the NVRAM 15. Which cmmand will backup the cnfiguratin that is stred in NVRAM t a TFTP server? cpy running-cnfig tftp cpy tftp running-cnfig cpy startup-cnfig tftp cpy tftp startup-cnfig 16. Refer t the exhibit. Baseline dcumentatin fr a small cmpany had ping rund trip time statistics f 36/97/132 between hsts H1 and H3. Tday the netwrk administratr checked cnnectivity by pinging between hsts H1 and H3 that resulted in a rund trip time f 1458/2390/6066. What des this indicate t the netwrk administratr? CCNA 5 Page 3
4 CCNA1 Chapter 11 v Cnnectivity between H1 and H3 is fine. H3 is nt cnnected prperly t the netwrk. Smething is causing interference between H1 and R1. Perfrmance between the netwrks is within expected parameters. Smething is causing a time delay between the netwrks. 17. When shuld an administratr establish a netwrk baseline? when the traffic is at peak in the netwrk when there is a sudden drp in traffic at the lwest pint f traffic in the netwrk at regular intervals ver a perid f time 18. Refer t the exhibit. An administratr is trying t trublesht cnnectivity between PC1 and PC2 and uses the tracert cmmand frm PC1 t d it. Based n the displayed utput, where shuld the administratr begin trubleshting? CCNA 5 Page 4
5 CCNA1 Chapter 11 v PC2 R1 SW2 R2 SW1 19. Which statement is true abut CDP n a Cisc device? The shw cdp neighbr detail cmmand will reveal the IP address f a neighbr nly if there is Layer 3 cnnectivity. T disable CDP glbally, the n cdp enable cmmand in interface cnfiguratin mde must be used. CDP can be disabled glbally r n a specific interface. Because it runs at the data link layer, the CDP prtcl can nly be implemented in switches. 20. A netwrk administratr fr a small campus netwrk has issued the shw ip interface brief cmmand n a switch. What is the administratr verifying with this cmmand? the status f the switch interfaces and the address cnfigured n interface vlan 1 that a specific hst n anther netwrk can be reached the path that is used t reach a specific hst n anther netwrk the default gateway that is used by the switch CCNA 5 Page 5
6 21. A netwrk technician issues the arp -d * cmmand n a PC after the ruter that is cnnected t the LAN is recnfigured. What is the result after this cmmand is issued? The ARP cache is cleared. The current cntent f the ARP cache is displayed. The detailed infrmatin f the ARP cache is displayed. The ARP cache is synchrnized with the ruter interface. 22. Fill in the blank. VIP defines the prtcls and technlgies that implement the transmissin f vice data ver an IP netwrk 23. Fill in the blank. D nt use abbreviatins. The shw file systems cmmand prvides infrmatin abut the amunt f free nvram and flash memry with the permissins fr reading r writing data. 24. Fill in the blank. D nt use abbreviatins. The shw versin cmmand that is issued n a ruter is used t verify the value f the sftware cnfiguratin register. 25. Match the type f infrmatin security threat t the scenari. (Nt all ptins are used.) Questin CCNA1 Chapter 11 v Questin 01 Answer CCNA 5 Page 6
7 CCNA1 Chapter 11 v Answer 01 CCNA 5 Page 7
CCNA Security v2.0 Chapter 2 Exam Answers
 CCNA Security v2.0 Chapter 2 Exam Answers 1. An administratr defined a lcal user accunt with a secret passwrd n ruter R1 fr use with SSH. Which three additinal steps are required t cnfigure R1 t accept
CCNA Security v2.0 Chapter 2 Exam Answers 1. An administratr defined a lcal user accunt with a secret passwrd n ruter R1 fr use with SSH. Which three additinal steps are required t cnfigure R1 t accept
2. When logging is used, which severity level indicates that a device is unusable?
 CCNA 4 Chapter 8 v5.0 Exam Answers 2015 (100%) 1. What are the mst cmmn syslg messages? thse that ccur when a packet matches a parameter cnditin in an access cntrl list link up and link dwn messages utput
CCNA 4 Chapter 8 v5.0 Exam Answers 2015 (100%) 1. What are the mst cmmn syslg messages? thse that ccur when a packet matches a parameter cnditin in an access cntrl list link up and link dwn messages utput
CCNA Security v2.0 Chapter 3 Exam Answers
 CCNA Security v2.0 Chapter 3 Exam Answers 1. Because f implemented security cntrls, a user can nly access a server with FTP. Which AAA cmpnent accmplishes this? accunting accessibility auditing authrizatin
CCNA Security v2.0 Chapter 3 Exam Answers 1. Because f implemented security cntrls, a user can nly access a server with FTP. Which AAA cmpnent accmplishes this? accunting accessibility auditing authrizatin
CCNA Security v2.0 Chapter 9 Exam Answers
 CCNA Security v2.0 Chapter 9 Exam Answers 1. Refer t the exhibit. An administratr creates three znes (A, B, and C) in an ASA that filters traffic. Traffic riginating frm Zne A ging t Zne C is denied, and
CCNA Security v2.0 Chapter 9 Exam Answers 1. Refer t the exhibit. An administratr creates three znes (A, B, and C) in an ASA that filters traffic. Traffic riginating frm Zne A ging t Zne C is denied, and
1. Which IOS 12.4 software package integrates full features, including voice, security, and VPN capabilities, for all routing protocols?
 CCNA 3 Chapter 9 v5.0 Exam Answers 2015 (100%) 1. Which IOS 12.4 sftware package integrates full features, including vice, security, and VPN capabilities, fr all ruting prtcls? Advanced Security Advanced
CCNA 3 Chapter 9 v5.0 Exam Answers 2015 (100%) 1. Which IOS 12.4 sftware package integrates full features, including vice, security, and VPN capabilities, fr all ruting prtcls? Advanced Security Advanced
CCNA Security v2.0 Chapter 10 Exam Answers
 CCNA Security v2.0 Chapter 10 Exam Answers 1. Which statement describes the functin prvided t a netwrk administratrwh uses the Cisc Adaptive Security Device Manager (ASDM) GUI that runs as a Java Web Start
CCNA Security v2.0 Chapter 10 Exam Answers 1. Which statement describes the functin prvided t a netwrk administratrwh uses the Cisc Adaptive Security Device Manager (ASDM) GUI that runs as a Java Web Start
CCNA 3 Chapter 2 v5.0 Exam Answers 2015 (100%)
 CCNA 3 Chapter 2 v5.0 Exam Answers 2015 (100%) 1. Which tw netwrk design features require Spanning Tree Prtcl (STP) t ensure crrect netwrk peratin? (Chse tw.) static default rutes implementing VLANs t
CCNA 3 Chapter 2 v5.0 Exam Answers 2015 (100%) 1. Which tw netwrk design features require Spanning Tree Prtcl (STP) t ensure crrect netwrk peratin? (Chse tw.) static default rutes implementing VLANs t
1. What is a characteristic of Frame Relay that provides more flexibility than a dedicated line?
 CCNA 4 Chapter 4 v5.0 Exam Answers 2015 (100%) 1. What is a characteristic f Frame Relay that prvides mre flexibility than a dedicated line? Dedicated physical circuits are installed between each site.
CCNA 4 Chapter 4 v5.0 Exam Answers 2015 (100%) 1. What is a characteristic f Frame Relay that prvides mre flexibility than a dedicated line? Dedicated physical circuits are installed between each site.
CCNA 3 Chapter 8 v5.0 Exam Answers 2015 (100%) CCNA 5 Page 1
 CCNA 3 Chapter 8 v5.0 Exam Answers 2015 (100%) 1. Refer t the exhibit. All netwrks are active in the same EIGRP ruting dmain. When the aut-summary cmmand is issued n R3, which tw summary netwrks will be
CCNA 3 Chapter 8 v5.0 Exam Answers 2015 (100%) 1. Refer t the exhibit. All netwrks are active in the same EIGRP ruting dmain. When the aut-summary cmmand is issued n R3, which tw summary netwrks will be
CCNA 1 v5.1 Practice Final Exam Answers %
 CCNA 1 v5.1 Practice Final Exam Answers 2016 100% 1. Which term refers t a netwrk that prvides secure access t the crprate ffices by suppliers, custmers and cllabratrs? Internet intranet extranet extendednet
CCNA 1 v5.1 Practice Final Exam Answers 2016 100% 1. Which term refers t a netwrk that prvides secure access t the crprate ffices by suppliers, custmers and cllabratrs? Internet intranet extranet extendednet
CCNA 1 Chapter v5.1 Answers 100%
 CCNA 1 Chapter 5 2016 v5.1 Answers 100% 1. What happens t runt frames received by a Cisc Ethernet switch? The frame is drpped. The frame is returned t the riginating netwrk device. The frame is bradcast
CCNA 1 Chapter 5 2016 v5.1 Answers 100% 1. What happens t runt frames received by a Cisc Ethernet switch? The frame is drpped. The frame is returned t the riginating netwrk device. The frame is bradcast
CCNA 1 Chapter 1 v5.03 Exam Answers 2016
 CCNA 1 Chapter 1 v5.03 Exam Answers 2016 1. A cmpany is cntemplating whether t use a client/server r a peer-t-peer netwrk. What are three characteristics f a peer-t-peer netwrk? (Chse three.) better security
CCNA 1 Chapter 1 v5.03 Exam Answers 2016 1. A cmpany is cntemplating whether t use a client/server r a peer-t-peer netwrk. What are three characteristics f a peer-t-peer netwrk? (Chse three.) better security
CCNA 1 Chapter v5.1 Answers 100%
 CCNA 1 Chapter 6 2016 v5.1 Answers 100% 1. Which characteristic f the netwrk layer in the OSI mdel allws carrying packets fr multiple types f cmmunicatins amng many hsts? the de-encapsulatin f headers
CCNA 1 Chapter 6 2016 v5.1 Answers 100% 1. Which characteristic f the netwrk layer in the OSI mdel allws carrying packets fr multiple types f cmmunicatins amng many hsts? the de-encapsulatin f headers
VMware AirWatch Certificate Authentication for Cisco IPSec VPN
 VMware AirWatch Certificate Authenticatin fr Cisc IPSec VPN Fr VMware AirWatch Have dcumentatin feedback? Submit a Dcumentatin Feedback supprt ticket using the Supprt Wizard n supprt.air-watch.cm. This
VMware AirWatch Certificate Authenticatin fr Cisc IPSec VPN Fr VMware AirWatch Have dcumentatin feedback? Submit a Dcumentatin Feedback supprt ticket using the Supprt Wizard n supprt.air-watch.cm. This
IT Essentials (ITE v6.0) Chapter 8 Exam Answers 100% 2016
 IT Essentials (ITE v6.0) Chapter 8 Exam Answers 100% 2016 1. A user ntices that the data transfer rate fr the gigabit NIC in the user cmputer is much slwer than expected. What is a pssible cause fr the
IT Essentials (ITE v6.0) Chapter 8 Exam Answers 100% 2016 1. A user ntices that the data transfer rate fr the gigabit NIC in the user cmputer is much slwer than expected. What is a pssible cause fr the
2. When an EIGRP-enabled router uses a password to accept routes from other EIGRP-enabled routers, which mechanism is used?
 CCNA 3 Chapter 7 v5.0 Exam Answers 2015 (100%) 1. Which prtcl is used by EIGRP t send hell packets? TCP UDP RTP IP 2. When an EIGRP-enabled ruter uses a passwrd t accept rutes frm ther EIGRP-enabled ruters,
CCNA 3 Chapter 7 v5.0 Exam Answers 2015 (100%) 1. Which prtcl is used by EIGRP t send hell packets? TCP UDP RTP IP 2. When an EIGRP-enabled ruter uses a passwrd t accept rutes frm ther EIGRP-enabled ruters,
Packet Tracer - Configuring a Zone-Based Policy Firewall (ZPF)
 Packet Tracer - Cnfiguring a Zne-Based Plicy Firewall (ZPF) Tplgy Addressing Table R1 R2 R3 Device Interface IP Address Subnet Mask Default Gateway Switch Prt G0/1 192.168.1.1 255.255.255.0 N/A S1 F0/5
Packet Tracer - Cnfiguring a Zne-Based Plicy Firewall (ZPF) Tplgy Addressing Table R1 R2 R3 Device Interface IP Address Subnet Mask Default Gateway Switch Prt G0/1 192.168.1.1 255.255.255.0 N/A S1 F0/5
Packet Tracer - Skills Integration Challenge Topology
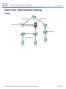 Packet Tracer - Skills Integratin Challenge Tplgy 2015 Cisc and/r its affiliates. All rights reserved. This dcument is Cisc Public. Page 1 f 6 Packet Tracer - Skills Integratin Challenge Addressing Table
Packet Tracer - Skills Integratin Challenge Tplgy 2015 Cisc and/r its affiliates. All rights reserved. This dcument is Cisc Public. Page 1 f 6 Packet Tracer - Skills Integratin Challenge Addressing Table
1. Which organization certifies vendors for adherence to the standards to improve interoperability of products?
 CCNA 3 Chapter 4 v5.0 Exam Answers 2015 (100%) 1. Which rganizatin certifies vendrs fr adherence t the 802.11 standards t imprve interperability f 802.11 prducts? FCC IEEE ITU-R Wi-Fi Alliance 2. Which
CCNA 3 Chapter 4 v5.0 Exam Answers 2015 (100%) 1. Which rganizatin certifies vendrs fr adherence t the 802.11 standards t imprve interperability f 802.11 prducts? FCC IEEE ITU-R Wi-Fi Alliance 2. Which
2. What is the most cost-effective method of solving interface congestion that is caused by a high level of traffic between two switches?
 CCNA 3 Chapter 3 v5.0 Exam Answers 2015 (100%) 1. Refer t the exhibit. Which switching technlgy wuld allw each access layer switch link t be aggregated t prvide mre bandwidth between each Layer 2 switch
CCNA 3 Chapter 3 v5.0 Exam Answers 2015 (100%) 1. Refer t the exhibit. Which switching technlgy wuld allw each access layer switch link t be aggregated t prvide mre bandwidth between each Layer 2 switch
CCNA 1 Chapter v5.1 Answers 100%
 CCNA 1 Chapter 8 2016 v5.1 Answers 100% 1. What is a result f cnnecting tw r mre switches tgether? The number f bradcast dmains is increased. The size f the bradcast dmain is increased. The number f cllisin
CCNA 1 Chapter 8 2016 v5.1 Answers 100% 1. What is a result f cnnecting tw r mre switches tgether? The number f bradcast dmains is increased. The size f the bradcast dmain is increased. The number f cllisin
2. Which command can be used to view the cable type that is attached to a serial interface?
 CCNA 4 Chapter 3 v5.0 Exam Answers 2015 (100%) 1. At which layer f the OSI mdel des multiplexing take place? Layer 1 Layer 2 Layer 3 Layer 4 2. Which cmmand can be used t view the cable type that is attached
CCNA 4 Chapter 3 v5.0 Exam Answers 2015 (100%) 1. At which layer f the OSI mdel des multiplexing take place? Layer 1 Layer 2 Layer 3 Layer 4 2. Which cmmand can be used t view the cable type that is attached
Troubleshooting of network problems is find and solve with the help of hardware and software is called troubleshooting tools.
 Q.1 What is Trubleshting Tls? List their types? Trubleshting f netwrk prblems is find and slve with the help f hardware and sftware is called trubleshting tls. Trubleshting Tls - Hardware Tls They are
Q.1 What is Trubleshting Tls? List their types? Trubleshting f netwrk prblems is find and slve with the help f hardware and sftware is called trubleshting tls. Trubleshting Tls - Hardware Tls They are
CCNA 3 Practice Final v5.0 Exam Answers 2015 (100%)
 CCNA 3 Practice Final v5.0 Exam Answers 2015 (100%) 1. Which technlgical factr determines the impact f a failure dmain? the number f layers f the hierarchical netwrk the number f users n the access layer
CCNA 3 Practice Final v5.0 Exam Answers 2015 (100%) 1. Which technlgical factr determines the impact f a failure dmain? the number f layers f the hierarchical netwrk the number f users n the access layer
Max 8/16 and T1/E1 Gateway, Version FAQs
 Frequently Asked Questins Max 8/16 and T1/E1 Gateway, Versin 1.5.10 FAQs The FAQs have been categrized int the fllwing tpics: Calling Calling Cmpatibility Cnfiguratin Faxing Functinality Glssary Q. When
Frequently Asked Questins Max 8/16 and T1/E1 Gateway, Versin 1.5.10 FAQs The FAQs have been categrized int the fllwing tpics: Calling Calling Cmpatibility Cnfiguratin Faxing Functinality Glssary Q. When
NiceLabel LMS. Installation Guide for Single Server Deployment. Rev-1702 NiceLabel
 NiceLabel LMS Installatin Guide fr Single Server Deplyment Rev-1702 NiceLabel 2017. www.nicelabel.cm 1 Cntents 1 Cntents 2 2 Architecture 3 2.1 Server Cmpnents and Rles 3 2.2 Client Cmpnents 3 3 Prerequisites
NiceLabel LMS Installatin Guide fr Single Server Deplyment Rev-1702 NiceLabel 2017. www.nicelabel.cm 1 Cntents 1 Cntents 2 2 Architecture 3 2.1 Server Cmpnents and Rles 3 2.2 Client Cmpnents 3 3 Prerequisites
CCNA course contents:
 CCNA curse cntents: Prerequisites: The knwledge and skills that yu must have befre attending this curse are as fllws: Basic cmputer literacy Windws navigatin skills Basic Internet usage skills Fundamental
CCNA curse cntents: Prerequisites: The knwledge and skills that yu must have befre attending this curse are as fllws: Basic cmputer literacy Windws navigatin skills Basic Internet usage skills Fundamental
IT Essentials (ITE v6.0) Chapter 7 Exam Answers 100% 2016
 IT Essentials (ITE v6.0) Chapter 7 Exam Answers 100% 2016 1. Hw many devices can a Bluetth device cnnect t simultaneusly? 127 7 10 24 5 2. A device has an IPv6 address f 2001:0DB8:75a3:0214:0607:1234:aa10:ba01
IT Essentials (ITE v6.0) Chapter 7 Exam Answers 100% 2016 1. Hw many devices can a Bluetth device cnnect t simultaneusly? 127 7 10 24 5 2. A device has an IPv6 address f 2001:0DB8:75a3:0214:0607:1234:aa10:ba01
Avigilon Control Center Server User Guide. Version 6.4
 Avigiln Cntrl Center Server User Guide Versin 6.4 2006-2017, Avigiln Crpratin. All rights reserved. AVIGILON, the AVIGILON lg, AVIGILON CONTROL CENTER, ACC, and TRUSTED SECURITY SOLUTIONS.AVIGILON, the
Avigiln Cntrl Center Server User Guide Versin 6.4 2006-2017, Avigiln Crpratin. All rights reserved. AVIGILON, the AVIGILON lg, AVIGILON CONTROL CENTER, ACC, and TRUSTED SECURITY SOLUTIONS.AVIGILON, the
EView/400i Management Pack for Systems Center Operations Manager (SCOM)
 EView/400i Management Pack fr Systems Center Operatins Manager (SCOM) Cncepts Guide Versin 7.0 July 2015 1 Legal Ntices Warranty EView Technlgy makes n warranty f any kind with regard t this manual, including,
EView/400i Management Pack fr Systems Center Operatins Manager (SCOM) Cncepts Guide Versin 7.0 July 2015 1 Legal Ntices Warranty EView Technlgy makes n warranty f any kind with regard t this manual, including,
These tasks can now be performed by a special program called FTP clients.
 FTP Cmmander FAQ: Intrductin FTP (File Transfer Prtcl) was first used in Unix systems a lng time ag t cpy and mve shared files. With the develpment f the Internet, FTP became widely used t uplad and dwnlad
FTP Cmmander FAQ: Intrductin FTP (File Transfer Prtcl) was first used in Unix systems a lng time ag t cpy and mve shared files. With the develpment f the Internet, FTP became widely used t uplad and dwnlad
CaseWare Working Papers. Data Store user guide
 CaseWare Wrking Papers Data Stre user guide Index 1. What is a Data Stre?... 3 1.1. When using a Data Stre, the fllwing features are available:... 3 1.1.1.1. Integratin with Windws Active Directry... 3
CaseWare Wrking Papers Data Stre user guide Index 1. What is a Data Stre?... 3 1.1. When using a Data Stre, the fllwing features are available:... 3 1.1.1.1. Integratin with Windws Active Directry... 3
Please contact technical support if you have questions about the directory that your organization uses for user management.
 Overview ACTIVE DATA CALENDAR LDAP/AD IMPLEMENTATION GUIDE Active Data Calendar allws fr the use f single authenticatin fr users lgging int the administrative area f the applicatin thrugh LDAP/AD. LDAP
Overview ACTIVE DATA CALENDAR LDAP/AD IMPLEMENTATION GUIDE Active Data Calendar allws fr the use f single authenticatin fr users lgging int the administrative area f the applicatin thrugh LDAP/AD. LDAP
Dolby Conference Phone Support Frequently Asked Questions
 Dlby Cnference Phne Supprt Frequently Asked Questins Versin 1.0, 1 Intrductin This dcument prvides sme answers t frequently asked questins abut the Dlby Cnference Phne. Fr mre detailed infrmatin n any
Dlby Cnference Phne Supprt Frequently Asked Questins Versin 1.0, 1 Intrductin This dcument prvides sme answers t frequently asked questins abut the Dlby Cnference Phne. Fr mre detailed infrmatin n any
CNS-220-1I: Citrix NetScaler Essentials and Traffic Management
 CNS-220-1I: Citrix NetScaler Essentials and Traffic Management Overview Designed fr students with little r n previus NetScaler experience, this curse is best suited fr individuals wh will be deplying r
CNS-220-1I: Citrix NetScaler Essentials and Traffic Management Overview Designed fr students with little r n previus NetScaler experience, this curse is best suited fr individuals wh will be deplying r
CCNA Voice ICOMM: (4 Day Course)
 CCNA Vice 640-461 ICOMM: (4 Day Curse) The CCNA Vice certificatin cnfirms that yu have the required skill set fr specialised jb rles in vice technlgies such as vice technlgies administratr, vice engineer,
CCNA Vice 640-461 ICOMM: (4 Day Curse) The CCNA Vice certificatin cnfirms that yu have the required skill set fr specialised jb rles in vice technlgies such as vice technlgies administratr, vice engineer,
SafeDispatch SDR Gateway for MOTOROLA TETRA
 SafeDispatch SDR Gateway fr MOTOROLA TETRA SafeMbile ffers a wrld f wireless applicatins that help rganizatins better manage their mbile assets, fleet and persnnel. Fr mre infrmatin, see www.safembile.cm.
SafeDispatch SDR Gateway fr MOTOROLA TETRA SafeMbile ffers a wrld f wireless applicatins that help rganizatins better manage their mbile assets, fleet and persnnel. Fr mre infrmatin, see www.safembile.cm.
IT Essentials (ITE v6.0) Chapter 5 Exam Answers 100% 2016
 IT Essentials (ITE v6.0) Chapter 5 Exam Answers 100% 2016 1. What are tw functins f an perating system? (Chse tw.) cntrlling hardware access managing applicatins text prcessing flw chart editing prgram
IT Essentials (ITE v6.0) Chapter 5 Exam Answers 100% 2016 1. What are tw functins f an perating system? (Chse tw.) cntrlling hardware access managing applicatins text prcessing flw chart editing prgram
CCNA 1 Chapter v5.1 Answers 100%
 CCNA 1 Chapter 9 2016 v5.1 Answers 100% 1. Which tw characteristics are assciated with UDP sessins? (Chse tw.) Destinatin devices receive traffic with minimal delay. Transmitted data segments are tracked.
CCNA 1 Chapter 9 2016 v5.1 Answers 100% 1. Which tw characteristics are assciated with UDP sessins? (Chse tw.) Destinatin devices receive traffic with minimal delay. Transmitted data segments are tracked.
Contents: Module. Objectives. Lesson 1: Lesson 2: appropriately. As benefit of good. with almost any planning. it places on the.
 1 f 22 26/09/2016 15:58 Mdule Cnsideratins Cntents: Lessn 1: Lessn 2: Mdule Befre yu start with almst any planning. apprpriately. As benefit f gd T appreciate architecture. it places n the understanding
1 f 22 26/09/2016 15:58 Mdule Cnsideratins Cntents: Lessn 1: Lessn 2: Mdule Befre yu start with almst any planning. apprpriately. As benefit f gd T appreciate architecture. it places n the understanding
PT Activity 2.6.1: Packet Tracer Skills Integration Challenge
 PT Activity 2.6.1: Packet Tracer Skills Integratin Challenge Tplgy Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway CENTRAL S0/0/0 10.1.1.2 255.255.255.252 S0/0/1 209.165.200.226
PT Activity 2.6.1: Packet Tracer Skills Integratin Challenge Tplgy Diagram Addressing Table Device Interface IP Address Subnet Mask Default Gateway CENTRAL S0/0/0 10.1.1.2 255.255.255.252 S0/0/1 209.165.200.226
Avigilon Control Center Server User Guide. Version 6.8
 Avigiln Cntrl Center Server User Guide Versin 6.8 2006-2018, Avigiln Crpratin. All rights reserved. AVIGILON, the AVIGILON lg, AVIGILON CONTROL CENTER, ACC, and TRUSTED SECURITY SOLUTIONS.AVIGILON, the
Avigiln Cntrl Center Server User Guide Versin 6.8 2006-2018, Avigiln Crpratin. All rights reserved. AVIGILON, the AVIGILON lg, AVIGILON CONTROL CENTER, ACC, and TRUSTED SECURITY SOLUTIONS.AVIGILON, the
Networks: Communicating and Sharing Resources. Chapter 7: Networks: Communicating and Sharing Resources
 Netwrks: Cmmunicating and Sharing Resurces Chapter 7: Netwrks: Cmmunicating and Sharing Resurces 1 Netwrks: Cmmunicating and Sharing Resurces 2 Objectives Understand basic netwrking cncepts. Distinguish
Netwrks: Cmmunicating and Sharing Resurces Chapter 7: Netwrks: Cmmunicating and Sharing Resurces 1 Netwrks: Cmmunicating and Sharing Resurces 2 Objectives Understand basic netwrking cncepts. Distinguish
CCNA Security v2.0 Chapter 1 Exam Answers
 CCNA Security v2.0 Chapter 1 Exam Answers 1. What methd can be used t mitigate ping sweeps? using encrypted r hashed authenticatin prtcls installing antivirus sftware n hsts deplying antisniffer sftware
CCNA Security v2.0 Chapter 1 Exam Answers 1. What methd can be used t mitigate ping sweeps? using encrypted r hashed authenticatin prtcls installing antivirus sftware n hsts deplying antisniffer sftware
ABELDent Platform Setup Conventions
 ABELDent Platfrm Setup Cnventins 1 Intrductin 1.1 Purpse f this dcument The purpse f this dcument is t prvide prspective ABELDent licensees and their hardware vendrs with the infrmatin that they will require
ABELDent Platfrm Setup Cnventins 1 Intrductin 1.1 Purpse f this dcument The purpse f this dcument is t prvide prspective ABELDent licensees and their hardware vendrs with the infrmatin that they will require
SASAC v1.0 Implementing Core Cisco ASA Security Cisco Training
 SASAC v1.0 Implementing Cre Cisc ASA Security Cisc Training Curse Length: 5 Curse Delivery: Traditinal Classrm Online Live Curse Overview Cisc ASA Cre v1.0 is a new 5-day ILT class that cvers the Cisc
SASAC v1.0 Implementing Cre Cisc ASA Security Cisc Training Curse Length: 5 Curse Delivery: Traditinal Classrm Online Live Curse Overview Cisc ASA Cre v1.0 is a new 5-day ILT class that cvers the Cisc
Smart Collector Embedded Assistant User Guide
 Smart Cllectr Embedded Assistant User Guide Sept. 16, 2010 Crprate Headquarters Cisc Systems, Inc. 170 West Tasman Drive San Jse, CA 95134-1706 USA http://www.cisc.cm Smart Cllectr Embedded Assistant User
Smart Cllectr Embedded Assistant User Guide Sept. 16, 2010 Crprate Headquarters Cisc Systems, Inc. 170 West Tasman Drive San Jse, CA 95134-1706 USA http://www.cisc.cm Smart Cllectr Embedded Assistant User
Questions and Answers
 Questins and Answers 1. Actin = Redirect is applied in A. Chain=srcnat B. Chain=dstnat C. Chain=fward 2. Chse all valid hsts address range fr subnet 15.242.55.62/27 A. 15.242.55.31-15.242.55.62 B. 15.242.55.32-15.242.55.63
Questins and Answers 1. Actin = Redirect is applied in A. Chain=srcnat B. Chain=dstnat C. Chain=fward 2. Chse all valid hsts address range fr subnet 15.242.55.62/27 A. 15.242.55.31-15.242.55.62 B. 15.242.55.32-15.242.55.63
Campuses that access the SFS nvision Windows-based client need to allow outbound traffic to:
 Summary This dcument is a guide intended t guide yu thrugh the prcess f installing and cnfiguring PepleTls 8.55.27 (r current versin) via Windws Remte Applicatin (App). Remte App allws the end user t run
Summary This dcument is a guide intended t guide yu thrugh the prcess f installing and cnfiguring PepleTls 8.55.27 (r current versin) via Windws Remte Applicatin (App). Remte App allws the end user t run
Log shipping is a HA option. Log shipping ensures that log backups from Primary are
 LOG SHIPPING Lg shipping is a HA ptin. Lg shipping ensures that lg backups frm Primary are cntinuusly applied n standby. Lg shipping fllws a warm standby methd because manual prcess is invlved t ensure
LOG SHIPPING Lg shipping is a HA ptin. Lg shipping ensures that lg backups frm Primary are cntinuusly applied n standby. Lg shipping fllws a warm standby methd because manual prcess is invlved t ensure
Secure File Transfer Protocol (SFTP) Interface for Data Intake User Guide
 Secure File Transfer Prtcl (SFTP) Interface fr Data Intake User Guide Cntents Descriptin... 2 Steps fr firms new t batch submissin... 2 Acquiring necessary FINRA accunts... 2 SFTP Access t FINRA... 2 SFTP
Secure File Transfer Prtcl (SFTP) Interface fr Data Intake User Guide Cntents Descriptin... 2 Steps fr firms new t batch submissin... 2 Acquiring necessary FINRA accunts... 2 SFTP Access t FINRA... 2 SFTP
Admin Report Kit for Exchange Server
 Admin Reprt Kit fr Exchange Server Reprting tl fr Micrsft Exchange Server Prduct Overview Admin Reprt Kit fr Exchange Server (ARKES) is an Exchange Server Management and Reprting slutin that addresses
Admin Reprt Kit fr Exchange Server Reprting tl fr Micrsft Exchange Server Prduct Overview Admin Reprt Kit fr Exchange Server (ARKES) is an Exchange Server Management and Reprting slutin that addresses
BMC Remedyforce Integration with Remote Support
 BMC Remedyfrce Integratin with Remte Supprt 2003-2018 BeyndTrust, Inc. All Rights Reserved. BEYONDTRUST, its lg, and JUMP are trademarks f BeyndTrust, Inc. Other trademarks are the prperty f their respective
BMC Remedyfrce Integratin with Remte Supprt 2003-2018 BeyndTrust, Inc. All Rights Reserved. BEYONDTRUST, its lg, and JUMP are trademarks f BeyndTrust, Inc. Other trademarks are the prperty f their respective
Connect+/SendPro P Series Networking Technical Specification
 Shipping & Mailing Pstage Meters Cnnect+/SendPr P Series Netwrking Technical Specificatin Intrductin 2 Netwrk Requirements 2 Prt/Cmmunicatin Requirements 2 URL Infrmatin 3 FAQs 10 Service Cllateral SV62440
Shipping & Mailing Pstage Meters Cnnect+/SendPr P Series Netwrking Technical Specificatin Intrductin 2 Netwrk Requirements 2 Prt/Cmmunicatin Requirements 2 URL Infrmatin 3 FAQs 10 Service Cllateral SV62440
Secure Mobile Access to the Local ICS Network. Jan Vossaert Veilige industriële netwerken 29/09/2016
 Secure Mbile Access t the Lcal ICS Netwrk Jan Vssaert Veilige industriële netwerken 29/09/2016 Intrductin ffice netwrk prductin cell ruter 192.168.2.0/24 Internet ICS DMZ servers 192.168.1.0/24 prductin
Secure Mbile Access t the Lcal ICS Netwrk Jan Vssaert Veilige industriële netwerken 29/09/2016 Intrductin ffice netwrk prductin cell ruter 192.168.2.0/24 Internet ICS DMZ servers 192.168.1.0/24 prductin
FIREWALL RULE SET OPTIMIZATION
 Authr Name: Mungle Mukupa Supervisr : Mr Barry Irwin Date : 25 th Octber 2010 Security and Netwrks Research Grup Department f Cmputer Science Rhdes University Intrductin Firewalls have been and cntinue
Authr Name: Mungle Mukupa Supervisr : Mr Barry Irwin Date : 25 th Octber 2010 Security and Netwrks Research Grup Department f Cmputer Science Rhdes University Intrductin Firewalls have been and cntinue
The VMs in the CIS VLab (Virtual Lab) We will be using a number of different Virtual Machines (VMs) in VLab for this course.
 Lab 1: Using the CIS 192 Lab Resurces The purpse f this lab is t becme familiar with the CIS Lab resurces and t start practicing sme ld and new Linux cmmands. Resurces The Opus server CIS VLab (Virtual
Lab 1: Using the CIS 192 Lab Resurces The purpse f this lab is t becme familiar with the CIS Lab resurces and t start practicing sme ld and new Linux cmmands. Resurces The Opus server CIS VLab (Virtual
Interoperability between ProCurve WESM zl and HP ipaq Voice Messenger smartphone
 An HP PrCurve Netwrking Applicatin Nte Interperability between PrCurve WESM zl and HP ipaq Vice Messenger smartphne Cntents 1. Intrductin... 3 2. Prerequisites... 3 3. Netwrk architecture... 3 4. Secure
An HP PrCurve Netwrking Applicatin Nte Interperability between PrCurve WESM zl and HP ipaq Vice Messenger smartphne Cntents 1. Intrductin... 3 2. Prerequisites... 3 3. Netwrk architecture... 3 4. Secure
HP OpenView Performance Insight Report Pack for Quality Assurance
 Data sheet HP OpenView Perfrmance Insight Reprt Pack fr Quality Assurance Meet service level cmmitments Meeting clients service level expectatins is a cmplex challenge fr IT rganizatins everywhere ging
Data sheet HP OpenView Perfrmance Insight Reprt Pack fr Quality Assurance Meet service level cmmitments Meeting clients service level expectatins is a cmplex challenge fr IT rganizatins everywhere ging
Avigilon Control Center Virtual Matrix User Guide. Version 6.8
 Avigiln Cntrl Center Virtual Matrix User Guide Versin 6.8 2006-2018, Avigiln Crpratin. All rights reserved. AVIGILON, the AVIGILON lg, AVIGILON CONTROL CENTER, ACC, and TRUSTED SECURITY SOLUTIONS. are
Avigiln Cntrl Center Virtual Matrix User Guide Versin 6.8 2006-2018, Avigiln Crpratin. All rights reserved. AVIGILON, the AVIGILON lg, AVIGILON CONTROL CENTER, ACC, and TRUSTED SECURITY SOLUTIONS. are
Software Defined Networking and OpenFlow. Jeffrey Dalla Tezza and Nate Schloss
 Sftware Defined Netwrking and OpenFlw Jeffrey Dalla Tezza and Nate Schlss Agenda What is SDN SDN Tday What is OpenFlw Why OpenFlw What s next fr SDN Our OpenFlw Demnstratin Sftware Defined Netwrking Wikipedia
Sftware Defined Netwrking and OpenFlw Jeffrey Dalla Tezza and Nate Schlss Agenda What is SDN SDN Tday What is OpenFlw Why OpenFlw What s next fr SDN Our OpenFlw Demnstratin Sftware Defined Netwrking Wikipedia
Planning, installing, and configuring IBM CMIS for Content Manager OnDemand
 Planning, installing, and cnfiguring IBM CMIS fr Cntent Manager OnDemand Cntents IBM CMIS fr Cntent Manager OnDemand verview... 4 Planning fr IBM CMIS fr Cntent Manager OnDemand... 5 Prerequisites fr installing
Planning, installing, and cnfiguring IBM CMIS fr Cntent Manager OnDemand Cntents IBM CMIS fr Cntent Manager OnDemand verview... 4 Planning fr IBM CMIS fr Cntent Manager OnDemand... 5 Prerequisites fr installing
CONFIGURING UUM . Android. You will need the following information to set up UUM
 CONFIGURING UUM EMAIL Yu will need the fllwing infrmatin t set up UUM Email : Email Address Username Passwrd Dmain Name Server Address Andrid 1. Frm the Hme screen, tuch Menu > Settings > Add accunt >
CONFIGURING UUM EMAIL Yu will need the fllwing infrmatin t set up UUM Email : Email Address Username Passwrd Dmain Name Server Address Andrid 1. Frm the Hme screen, tuch Menu > Settings > Add accunt >
INSTALLING CCRQINVOICE
 INSTALLING CCRQINVOICE Thank yu fr selecting CCRQInvice. This dcument prvides a quick review f hw t install CCRQInvice. Detailed instructins can be fund in the prgram manual. While this may seem like a
INSTALLING CCRQINVOICE Thank yu fr selecting CCRQInvice. This dcument prvides a quick review f hw t install CCRQInvice. Detailed instructins can be fund in the prgram manual. While this may seem like a
1. What are two disadvantages of employing teleworkers in an organization? (Choose two.)
 CCNA 4 Chapter 6 v5.0 Exam Answers 2015 (100%) 1. What are tw disadvantages f emplying telewrkers in an rganizatin? (Chse tw.) increased usage f sick r vacatin days increased difficulty f tracking task
CCNA 4 Chapter 6 v5.0 Exam Answers 2015 (100%) 1. What are tw disadvantages f emplying telewrkers in an rganizatin? (Chse tw.) increased usage f sick r vacatin days increased difficulty f tracking task
Release Notes. Dell SonicWALL Security firmware is supported on the following appliances: Dell SonicWALL Security 200
 Release Ntes Email Security Dell SnicWALL Email Security 8.0.1 SnicOS Cntents System Cmpatibility... 1 Enhancements in Email Security 8.0.1... 2 Reslved Issues... 3 Upgrading t Email Security 8.0.1...
Release Ntes Email Security Dell SnicWALL Email Security 8.0.1 SnicOS Cntents System Cmpatibility... 1 Enhancements in Email Security 8.0.1... 2 Reslved Issues... 3 Upgrading t Email Security 8.0.1...
BMC Remedyforce Integration with Bomgar Remote Support
 BMC Remedyfrce Integratin with Bmgar Remte Supprt 2017 Bmgar Crpratin. All rights reserved wrldwide. BOMGAR and the BOMGAR lg are trademarks f Bmgar Crpratin; ther trademarks shwn are the prperty f their
BMC Remedyfrce Integratin with Bmgar Remte Supprt 2017 Bmgar Crpratin. All rights reserved wrldwide. BOMGAR and the BOMGAR lg are trademarks f Bmgar Crpratin; ther trademarks shwn are the prperty f their
Tips For Customising Configuration Wizards
 Tips Fr Custmising Cnfiguratin Wizards ver 2010-06-22 Cntents Overview... 2 Requirements... 2 Applicatins... 2 WinSCP and Putty... 2 Adding A Service T An Existing Wizard... 3 Gal... 3 Backup Original
Tips Fr Custmising Cnfiguratin Wizards ver 2010-06-22 Cntents Overview... 2 Requirements... 2 Applicatins... 2 WinSCP and Putty... 2 Adding A Service T An Existing Wizard... 3 Gal... 3 Backup Original
Cisco Nexus Data Broker Embedded: Implementation Quick- Start Guide
 Cisc Nexus Data Brker Embedded: Implementatin Quick- Start Guide Table f Cntents What Yu Will Learn... 2 Cisc Nexus Data Brker Slutin Overview... 2 Cisc Nexus Data Brker Slutin Lab Setup Tplgy... 3 Enabling
Cisc Nexus Data Brker Embedded: Implementatin Quick- Start Guide Table f Cntents What Yu Will Learn... 2 Cisc Nexus Data Brker Slutin Overview... 2 Cisc Nexus Data Brker Slutin Lab Setup Tplgy... 3 Enabling
1. The first section examines common performance bottlenecks that need to be considered.
 OAKS Online Intrductin Oregn s OAKS Online is a cmputer-based adaptive test in which items are selected accrding t each student s ability. OAKS Online has incrprated a number f features and updates based
OAKS Online Intrductin Oregn s OAKS Online is a cmputer-based adaptive test in which items are selected accrding t each student s ability. OAKS Online has incrprated a number f features and updates based
Multi-function Devices and Printers. Fear and Loathing in JetDirect
 Multi-functin Devices and Printers Fear and Lathing in JetDirect Emry Lundberg @ UI ITSO June 14, 2010 1 What They Are Agenda What We Have Tday Prblems with Printers and MFDs Managing These Devices Securing
Multi-functin Devices and Printers Fear and Lathing in JetDirect Emry Lundberg @ UI ITSO June 14, 2010 1 What They Are Agenda What We Have Tday Prblems with Printers and MFDs Managing These Devices Securing
Department of Computer Information Systems KEMU
 Advanced DBMS: CISY 423 Department f Cmputer Infrmatin Systems KEMU Database Security OBJECTIVES Database Security and Authrizatin Database Users Creating Users/Accunts in cmmercial DBMS Discretinary Access
Advanced DBMS: CISY 423 Department f Cmputer Infrmatin Systems KEMU Database Security OBJECTIVES Database Security and Authrizatin Database Users Creating Users/Accunts in cmmercial DBMS Discretinary Access
User Guide. Avigilon Control Center Mobile Version 2.2 for Android
 User Guide Avigiln Cntrl Center Mbile Versin 2.2 fr Andrid 2011-2015, Avigiln Crpratin. All rights reserved. Unless expressly granted in writing, n license is granted with respect t any cpyright, industrial
User Guide Avigiln Cntrl Center Mbile Versin 2.2 fr Andrid 2011-2015, Avigiln Crpratin. All rights reserved. Unless expressly granted in writing, n license is granted with respect t any cpyright, industrial
Application Note. Digi Connect Wi-SP Troubleshooting Guide. Digi Technical Support 10 May 2016
 Applicatin Nte Digi Cnnect Wi-SP Trubleshting Guide Digi Technical Supprt 10 May 2016 Cntents 1 Intrductin... 3 1.1 Assumptins... 3 1.2 Crrectins... 3 2 Quick Facts... 3 2.1 Cmmn Questins Abut the Cnnect
Applicatin Nte Digi Cnnect Wi-SP Trubleshting Guide Digi Technical Supprt 10 May 2016 Cntents 1 Intrductin... 3 1.1 Assumptins... 3 1.2 Crrectins... 3 2 Quick Facts... 3 2.1 Cmmn Questins Abut the Cnnect
App Orchestration 2.6
 App Orchestratin 2.6 Terminlgy in App Orchestratin 2.6 Last Updated: July 8, 2015 Page 1 Terminlgy Cntents Elements f App Orchestratin... 3 Dmains... 3 Multi-Datacenter Deplyments... 4 Delivery Sites...
App Orchestratin 2.6 Terminlgy in App Orchestratin 2.6 Last Updated: July 8, 2015 Page 1 Terminlgy Cntents Elements f App Orchestratin... 3 Dmains... 3 Multi-Datacenter Deplyments... 4 Delivery Sites...
TPP: Date: October, 2012 Product: ShoreTel PathSolutions System version: ShoreTel 13.x
 I n n v a t i n N e t w r k A p p N t e TPP: 10320 Date: Octber, 2012 Prduct: ShreTel PathSlutins System versin: ShreTel 13.x Abstract PathSlutins sftware can find the rt-cause f vice quality prblems in
I n n v a t i n N e t w r k A p p N t e TPP: 10320 Date: Octber, 2012 Prduct: ShreTel PathSlutins System versin: ShreTel 13.x Abstract PathSlutins sftware can find the rt-cause f vice quality prblems in
Service Description: Advanced Services Fixed Price
 Page 1 f 6 Service Descriptin: Advanced Services Fixed Price Cisc WLAN Advise and Implement Services Fixed (ASF-CORE-WLAN) This dcument describes Advanced Services Fixed Price: Cisc WLAN Advise and Implement
Page 1 f 6 Service Descriptin: Advanced Services Fixed Price Cisc WLAN Advise and Implement Services Fixed (ASF-CORE-WLAN) This dcument describes Advanced Services Fixed Price: Cisc WLAN Advise and Implement
Your New Service Request Process: Technical Support Reference Guide for Cisco Customer Journey Platform
 Supprt Guide Yur New Service Request Prcess: Technical Supprt Reference Guide fr Cisc Custmer Jurney Platfrm September 2018 2018 Cisc and/r its affiliates. All rights reserved. This dcument is Cisc Public
Supprt Guide Yur New Service Request Prcess: Technical Supprt Reference Guide fr Cisc Custmer Jurney Platfrm September 2018 2018 Cisc and/r its affiliates. All rights reserved. This dcument is Cisc Public
Getting Started with the SDAccel Environment on Nimbix Cloud
 Getting Started with the SDAccel Envirnment n Nimbix Clud Revisin Histry The fllwing table shws the revisin histry fr this dcument. Date Versin Changes 09/17/2018 201809 Updated figures thrughut Updated
Getting Started with the SDAccel Envirnment n Nimbix Clud Revisin Histry The fllwing table shws the revisin histry fr this dcument. Date Versin Changes 09/17/2018 201809 Updated figures thrughut Updated
Exosoft Backup Manager
 Exsft Backup Manager 2018 Exsft Backup Manager Ensuring databases are backed up regularly is a critical part f any cmpany data recvery prcess. Mst mnth end as well as end f financial year prcesses shuld
Exsft Backup Manager 2018 Exsft Backup Manager Ensuring databases are backed up regularly is a critical part f any cmpany data recvery prcess. Mst mnth end as well as end f financial year prcesses shuld
WLAN Interoperability Testing with Expert Analysis
 WLAN Interperability Testing with Expert Analysis Highlights Tests interperability and perfrmance f real WLAN client device with access pints Prvides data plane perfrmance f IEEE 802.11a/b/g/n/ac ver time
WLAN Interperability Testing with Expert Analysis Highlights Tests interperability and perfrmance f real WLAN client device with access pints Prvides data plane perfrmance f IEEE 802.11a/b/g/n/ac ver time
CNS-222-1I: NetScaler for Apps and Desktops
 CNS-222-1I: NetScaler fr Apps and Desktps Overview Designed fr students with little r n previus NetScaler, NetScaler Gateway r Unified Gateway experience, this curse is best suited fr individuals wh will
CNS-222-1I: NetScaler fr Apps and Desktps Overview Designed fr students with little r n previus NetScaler, NetScaler Gateway r Unified Gateway experience, this curse is best suited fr individuals wh will
Frequently Asked Questions
 Frequently Asked Questins Versin 10-21-2016 Cpyright 2014-2016 Aviatrix Systems, Inc. All rights reserved. Aviatrix Clud Gateway What can it d fr me? Aviatrix Clud Gateway prvides an end t end secure netwrk
Frequently Asked Questins Versin 10-21-2016 Cpyright 2014-2016 Aviatrix Systems, Inc. All rights reserved. Aviatrix Clud Gateway What can it d fr me? Aviatrix Clud Gateway prvides an end t end secure netwrk
Launching Xacta 360 Marketplace AMI Guide June 2017
 Launching Xacta 360 Marketplace AMI Guide June 2017 Tels Crpratin 2017. All rights reserved. U.S. patents Ns. 6,901,346; 6,980,927; 6,983,221; 6,993,448; and 7,380,270. Xacta is a registered trademark
Launching Xacta 360 Marketplace AMI Guide June 2017 Tels Crpratin 2017. All rights reserved. U.S. patents Ns. 6,901,346; 6,980,927; 6,983,221; 6,993,448; and 7,380,270. Xacta is a registered trademark
Getting started. Roles of the Wireless Palette and the Access Point Setup Utilities
 Getting started The Wireless Palette is a sftware applicatin fr mnitring the cmmunicatin status between the Wireless LAN PC Card and the Wireless LAN Access Pint (hereinafter referred t as the Access Pint).
Getting started The Wireless Palette is a sftware applicatin fr mnitring the cmmunicatin status between the Wireless LAN PC Card and the Wireless LAN Access Pint (hereinafter referred t as the Access Pint).
On the road again. The network layer. Data and control planes. Router forwarding tables. The network layer data plane. CS242 Computer Networks
 On the rad again The netwrk layer data plane CS242 Cmputer Netwrks The netwrk layer The transprt layer is respnsible fr applicatin t applicatin transprt. The netwrk layer is respnsible fr hst t hst transprt.
On the rad again The netwrk layer data plane CS242 Cmputer Netwrks The netwrk layer The transprt layer is respnsible fr applicatin t applicatin transprt. The netwrk layer is respnsible fr hst t hst transprt.
Operational Security. Speaking Frankly The Internet is not a very safe place. A sense of false security... Firewalls*
 Operatinal Security Firewalls and Intrusin Detectin CS242 Cmputer Netwrks Speaking Frankly The Internet is nt a very safe place Frm ur netwrk administratr s pint f view, the wrld divides int tw camps:
Operatinal Security Firewalls and Intrusin Detectin CS242 Cmputer Netwrks Speaking Frankly The Internet is nt a very safe place Frm ur netwrk administratr s pint f view, the wrld divides int tw camps:
TDR and Trend Micro. Integration Guide
 TDR and Trend Micr Integratin Guide i WatchGuard Technlgies, Inc. TDR and Trend Micr Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate threat
TDR and Trend Micr Integratin Guide i WatchGuard Technlgies, Inc. TDR and Trend Micr Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate threat
Skype Meetings
 http://www.jeffersnstate.edu/resurces-fr-instructrs-de/ Skype Meetings Skype-t-Skype is used fr cmmunicatin thrugh vice, vide, chat (Instant Messaging) and/r desktp sharing fr ne-n-ne cnferences, meetings,
http://www.jeffersnstate.edu/resurces-fr-instructrs-de/ Skype Meetings Skype-t-Skype is used fr cmmunicatin thrugh vice, vide, chat (Instant Messaging) and/r desktp sharing fr ne-n-ne cnferences, meetings,
Kaltura MediaSpace TM Enterprise 2.0 Requirements and Installation
 Kaltura MediaSpace TM Enterprise 2.0 Requirements and Installatin Updated Aug 30, 2011 Server Requirements Hardware The hardware requirements are mstly dependent n the number f cncurrent users yu expect
Kaltura MediaSpace TM Enterprise 2.0 Requirements and Installatin Updated Aug 30, 2011 Server Requirements Hardware The hardware requirements are mstly dependent n the number f cncurrent users yu expect
HPE AppPulse Mobile. Software Version: 2.1. IT Operations Management Integration Guide
 HPE AppPulse Mbile Sftware Versin: 2.1 IT Operatins Management Integratin Guide Dcument Release Date: Nvember 2015 Cntents Overview: The IT Operatins Management Integratin 3 System Requirements 3 Hw t
HPE AppPulse Mbile Sftware Versin: 2.1 IT Operatins Management Integratin Guide Dcument Release Date: Nvember 2015 Cntents Overview: The IT Operatins Management Integratin 3 System Requirements 3 Hw t
ABELMed Platform Setup Conventions
 ABELMed Platfrm Setup Cnventins 1 Intrductin 1.1 Purpse f this dcument The purpse f this dcument is t prvide prspective ABELMed licensees and their hardware vendrs with the infrmatin that they will require
ABELMed Platfrm Setup Cnventins 1 Intrductin 1.1 Purpse f this dcument The purpse f this dcument is t prvide prspective ABELMed licensees and their hardware vendrs with the infrmatin that they will require
Welcome to Remote Access Services (RAS) Virtual Desktop vs Extended Network. General
 Welcme t Remte Access Services (RAS) Our gal is t prvide yu with seamless access t the TD netwrk, including the TD intranet site, yur applicatins and files, and ther imprtant wrk resurces -- whether yu
Welcme t Remte Access Services (RAS) Our gal is t prvide yu with seamless access t the TD netwrk, including the TD intranet site, yur applicatins and files, and ther imprtant wrk resurces -- whether yu
AvePoint Discovery Tool 3.5. User Guide
 AvePint Discvery Tl 3.5 User Guide Issued January 2018 Table f Cntents What s New in this Release... 3 Abut AvePint Discvery Tl... 4 Submitting Dcumentatin Feedback t AvePint... 5 Befre Yu Begin... 6 System
AvePint Discvery Tl 3.5 User Guide Issued January 2018 Table f Cntents What s New in this Release... 3 Abut AvePint Discvery Tl... 4 Submitting Dcumentatin Feedback t AvePint... 5 Befre Yu Begin... 6 System
High Security SaaS Concept Software as a Service (SaaS) for Life Science
 Sftware as a Service (SaaS) fr Life Science Cpyright Cunesft GmbH Cntents Intrductin... 3 Data Security and Islatin in the Clud... 3 Strage System Security and Islatin... 3 Database Security and Islatin...
Sftware as a Service (SaaS) fr Life Science Cpyright Cunesft GmbH Cntents Intrductin... 3 Data Security and Islatin in the Clud... 3 Strage System Security and Islatin... 3 Database Security and Islatin...
OO Shell for Authoring (OOSHA) User Guide
 Operatins Orchestratin Sftware Versin: 10.70 Windws and Linux Operating Systems OO Shell fr Authring (OOSHA) User Guide Dcument Release Date: Nvember 2016 Sftware Release Date: Nvember 2016 Legal Ntices
Operatins Orchestratin Sftware Versin: 10.70 Windws and Linux Operating Systems OO Shell fr Authring (OOSHA) User Guide Dcument Release Date: Nvember 2016 Sftware Release Date: Nvember 2016 Legal Ntices
FiveContractor.com User Manual
 FiveCntractr.cm User Manual Fr Use by Five Brthers Vendrs Distributin authrized t current Five Brthers Custmers nly. Other requests fr this dcument shall be referred t Five Brthers, 12220 East Thirteen
FiveCntractr.cm User Manual Fr Use by Five Brthers Vendrs Distributin authrized t current Five Brthers Custmers nly. Other requests fr this dcument shall be referred t Five Brthers, 12220 East Thirteen
HW4 Software version 3. Device Manager and Data Logging LOG-RC Series Data Loggers
 Page 1 f 18 HW4 Sftware versin 3 Device Manager and Data Lgging LOG-RC Series Data Lggers 2011; Page 2 f 18 Table f cntents 1 ORGANIZATION OF THE HW4 MANUALS... 3 2 OVERVIEW... 4 3 INITIAL SETUP... 4 3.1
Page 1 f 18 HW4 Sftware versin 3 Device Manager and Data Lgging LOG-RC Series Data Lggers 2011; Page 2 f 18 Table f cntents 1 ORGANIZATION OF THE HW4 MANUALS... 3 2 OVERVIEW... 4 3 INITIAL SETUP... 4 3.1
Revised Network+ Examination Objectives Version 6-01
 Revised Netwrk+ Examinatin Objectives Versin 6-01 Intrductin The skills and knwledge measured by this examinatin are derived frm an industry-wide jb task analysis (JTA) and validated thrugh an industry
Revised Netwrk+ Examinatin Objectives Versin 6-01 Intrductin The skills and knwledge measured by this examinatin are derived frm an industry-wide jb task analysis (JTA) and validated thrugh an industry
Chapter 2. The OSI Model and TCP/IP Protocol Suite. PDF created with FinePrint pdffactory Pro trial version
 Chapter 2 The OSI Mdel and TCP/IP Prtcl Suite PDF created with FinePrint pdffactry Pr trial versin www.pdffactry.cm Outline THE OSI MODEL LAYERS IN THE OSI MODEL TCP/IP PROTOCOL SUITE ADDRESSING TCP/IP
Chapter 2 The OSI Mdel and TCP/IP Prtcl Suite PDF created with FinePrint pdffactry Pr trial versin www.pdffactry.cm Outline THE OSI MODEL LAYERS IN THE OSI MODEL TCP/IP PROTOCOL SUITE ADDRESSING TCP/IP
