Transactions on Information and Communications Technologies vol 9, 1995 WIT Press, ISSN
|
|
|
- Jonas O’Brien’
- 5 years ago
- Views:
Transcription
1 A parallel approach to the extraction of boundary and shading information from digital images E. Ardizzone", A. Genco**, C. Lodato\ G. Lo Re\ R. Pirrone" "Dipartimento di Ingegneria Elettrica, Universita di Palermo, ^Centra Studi sulle Reti di Elaboratori, Consiglio Nazionale delle Ricerche, Viale delle Scienze, Palermo, Italy Abstract The Boundary Contour System (BCS) is a part of a computational model that is aimed to address the main issues in early vision processes, like boundary completion, grouping, brightness effects and so on. In this work we present a parallel implementation of the BCS carried out by means of a workstation network under the control of the PVM system. The obtained results are compared with those obtained in a previous sequential implementation of the model. The efficency of the distributed implementation is also discussed. 1 Introduction In this paper we propose a parallel implementation of an algorithm for the extraction of boundary and shading information from digital images, based on the Boundary Contour System (BCS). The BCS is a part of a larger computational model conceived by Grossberg and Mingolla [1][2] that is aimed to address the main issues in early vision processes, like boundary completion, grouping, brightness effects and so on. The model is based on a multi-layer architecture, with several stages cascaded in a loop way. The final result is a boundary detection and completion of regions present in the input scene and a computation of their brightness characteristics. We already built a non-parallel implementation of the BCS E.Ardizzone[3] and we also derived a set of suitable values for the parameters in the model equations. Since we are planning to apply the BCS model to real time applications with dynamic image acquisition, we designed a parallel implementation that will be capable of achieving the required performance.
2 316 High-Performance Computing in Engineering 2 Background: The Boundary Contour System The Boundary Contour System (BCS) is a part of a larger computational model conceived by Steven Grossberg and Ennio Mingolla that is aimed to address the main issues in early vision processes, like boundary completion, grouping, brightness effects and so on. This model is made up essentially by two neural architectures: the BCS and the PCS (Feature Contour System); the BCS is mainly responsible for boundary detection and completion in the input scene while the PCS computes the brightness characteristics of the perceived scene and fills the regions detected by the BCS with the correct colour. Both the BCS and the PCS take their input from a monocular preprocessing stage that acts as a retina. The retinal stage performs a centersurround filtering that is used for two purposes; it acts as a gain control over the true input signal and enhances image contrasts, while preserving contrasts ratios at the edges and suppressing uniform regions and noise. In this way the so called illuminant discounting is performed that is the computation of contrast ratios regardless of the illumination conditions. In this work we are concerned only in the BCS: the rest of this section is devoted to the description of the BCS structure. We have built a computer implementation of the BCS and we also derived a set of suitable values for the parameters in the model equations. In our work we followed the model description that is present in [1] and [2]. We first describe the preprocessing stage of the model that represents the true input to the BCS. The BCS/FCS theory defines this stage as a two channels filter with an ON channel and an OFF channel. The ON channel performs an on center-off surround filtering. Conversely the OFF channel performs an off center-on surround filtering. In our simulations we followed the work of Grossberg and his colleagues who didn't use the OFF channel so in our model the retinal stage acts only as a ON filter. The activation of this stage is obtained solving at equilibrium a classical shunting equation of the form: -=-Dx + (U-xCI-(x + LSI (1) where D is the decay rate of the activation while U and -L represent the bounding values of the range of variation of Xy. Ipq is the image intensity and Cpqij and Spqij are two bi-dimensional gaussian kernels centered in (ij). The solution of (lj has a bilinear form with a DoG in the numerator and a SoG in the denominator. The Boundary Comtour System has the structure of a multilayer feedback network made up by two main blocks: a feedforward block called OC Filter and the real feedback stage called CC Loop (see figure 1). All the neuron layers in the net are arranged as three-dimensional arrays of cells: the first two dimensions are for the spatial displacement of the cells over the input image while the third one indicates the orientation to which a single cell is sensible. In this way clusters of cells are regularly displaced all over the image plane and inside of each cluster the single cells span all possible orientations. Each cluster processes the output of the cluster in the same spatial position of the preceding layer. In our computer simulations we used N cells for each cluster with N= 1 2.
3 High-Performance Computing in Engineering 317 The Oriented Contrast (OC) Filter takes its input from the retinal stage and feeds it to N pairs of cells with elongated receptive fields that are sensible to the amount of contrast across their principal symmetry axis. These cells are called Simple Cells. The two cells of a pair are sensible to opposite directions of contrast along the same orientation; the output is computed summing the activations of each couple of cells. The Simple Cells feed their activation to the Complex Cells that have the same elongated receptive fields but are insensitive to the direction of contrast. Their activation is the output of the whole OC Filter. The BCS theory uses the OC Filter to roughly determine the orientation and position of the image contrasts, while the Cooperative-Competitive (CC) Loop is aimed to the detection, sharpening and completion of the image boundaries. The first stage of the CC Loop takes its input from the Complex Cells and performs a short-range competition between nearby cells with the same orientation: a cell in this layer sends inhibitory signals to the cells in its spatial neighborood that have the same orientation. ORIENTED COOPERATION ^ o o o o o o o o. o o o o 1. «. -h- \z> ^^ ^ ( 1 4 N 0 O o o (y) 00 o o (w) o o o o o o o o CC:LOOP OC"FILTER Fig. 1: The BCS structure The second stage is again a competitive one. In this case competition is a push-pull opponent process: couples of cells in the same position but with perpendicular orientation send inhibitory signals to each other. When an orientation is excited the perpendicular orientation is inhibited while when an orientation is inhibited the perpendicular one is excited via disinhibition. The two competitive stages have the task to eliminate the positional uncertainty of the edges. This positional uncertainty derives from the measurement errors that are present in the detection of the image contrasts by the OC Filter; an edge can fall everywhere within the receptive field of a Simple Cell and this gives rise to the uncertainty.
4 318 High-Performance Computing in Engineering The positional disambiguation is achieved in two steps. If we consider an edge in the image, first the competition 1 inhibits the weak activations of cells that are placed beyond the effective end of the edge, but partially overlap it with their receptive field. Second, the competition 2 enforces via disinhibition the activation near the end of the edge that are perpendicular to the edge itself. Such activations are called endcuts. The competitive processes give rise to boundary fragments that are not very sharp and can support completion within a band of orientations. To obtain correct completion a cooperative stage is employed. The cells in this stage are called Bipole Cells; they have very elongated receptive fields with two lobes along the orientation to which the cell is sensitive. A Bipole Cell takes the activations from the competitive cells in the neighborood of its position that are sensible to its orientation; it fires only if both sides of its receptive field receive a sufficient amount of activation. If there is an emergent contour along one orientation near the position of a Bipole Cell that is sensible to this orientation, then the cell fires and via the feedback path it enforces the activation of the competitive cell, in the first stage of the CC Loop, placed in the same position and sensitive to the same orientation. Along the feedback path, there is the last stage of the CC Loop that is the so called Feedback Competitive Stage. The kind of competition in this stage is quite the same as in the competition 1 stage; this stage has been introduced to disambiguate the boundary completion uncertainty; competition 2 generates in the same position different boundary fragments that are completed by the cooperative stage with variable intensity depending on the strength of their activation. A competitive mechanism is therefore necessary to ensure that only the strongest complete boundary can survive and the corresponding activation can be added to the competition 1 cell activity. Boundary completion requires some time to became stable due to its loop nature; the result of this process is an image segmentation in which several bounded regions are present. These regions are taken as input from the PCS that fills each region with a brightness value that is computed as a feature of the corresponding region in the input image. 3 The Parallel implementation The first step in trying problem decomposition was to evaluate the relative working load of each section of our BCS model implementation. As it can be seen in the flow chart of Fig. 2, the most relevant part is played by the cooperation module. It covers about the 80 % of the whole working load of the main loop, and therefore, we decided to investigate the parallelism of this part only. Furthermore, the intrinsic logic of this module appeared to be easily decomposable. The different orientations of contrast can be processed separately by means of co-operating processes.
5 High-Performance Computing in Engineering 319 FILE_LOADINq^ I SCREEN, _,. UNITIALIZE DEF_MASK ~~l COMPETITION 1st [COMPETITION 2nd CALC_KERNELI 80% 1 J_ I COOPERATION 10% [FEEDBACK I Fig. 2: The block diagram of the BCS algorithm 3.1 The distributed design We carried out the parallel implementation trying to distribute the working load among the available workstations connected into our Ethernet LAN. To this end we decided to exploit the features of the PVM (Parallel Virtual Machine) [4] environment. As it is well known, PVM is a free software that was developed by a group of researchers leaded by J. Dongarra at the Oak Ridge National Laboratory (Tennessee). It allows a master task to create new tasks to be run in selected workstations of the network. It also provides both synchronous and asynchronous communication primitives, synchronisation barriers, and many others language extensions to standard C, C++, and Fortran, to manage the distributed environment. We considered some different approaches to the parallel BCS implementation. One is based on the fact that this model is used for image recognition problems, where the object or the observer assume different positions. Under this hypothesis, a time parallelism schema could be considered between the image acquisition period, the initialisation phase and the elaboration code. Another option consists in partitioning the image matrix that sometimes can be a very large one. The last approach considers the different orientations of contrast of each point. They can be elaborated separately by different processes that are running in parallel. We chose this last strategy because it is the one that can be performed in any case: when the matrix is small or large, and when no dynamic acquisition has to be considered. However, this partial form of parallelism leaves a relevant part of sequential code. This affects the efficiency of the parallel solution that could be improved when the size of the problem and the application makes the first two approaches applicable. 3.2 Implementation notes When developing the distributed application in the PVM environment, we had to tackle the typical overhead factors of a distributed system. In particular the communication medium played a determinant role in time performances
6 320 High-Performance Computing in Engineering because the ethernet Ian is a shared-sequential medium and never allows two different communications to perform in parallel: their total completion time always results to be the sum of the two periods at least. An other aspect was the different data representation formats inside the different machines. This entails a conversion overhead if communication takes place between machines with different architectures. To this end, PVM adopts a common format, that is the XDR (external Data Representation) protocol by SUN Microsystems [5]. Our implementation follows the typical application structure of the PVM environment that is the master-slave schema. The master task (each process in the PVM terminology is a task) "spawns" the other tasks (slaves) allocating them in selected machines. The master task executes all the BCS modules sequentially, except for the co-operation module. For this step it creates a number of slaves equal to the number of the used machines. Then it assigns the calculations of the different orientations of contrast to each one, according to a suitable load distribution. In addition, the master task broadcasts the initial data, and collects the intermediate results of the co-operation at each iteration. 4 Experiments and results Our distributed environment consists of six workstations that are heterogeneous in terms of architecture and performance. Their hardware features are reported in Tab. 1. Tab. 1: hardware features of the workstations used workstation type processor RISC27 IBM RISC POWER 62 MHz CEREUX DEC 3000 ALPHA 175 MHz POWER RISC System/ POWER PC 66 MHz ALPHA DEC 3000 ALPHA 125 MHz SUNIPA SUN SPARC stat. 10 SPARC Supsc 50 MHz CUCAIX RISC System/ POWER 20 MHz mem. 64Mb 32Mb 32Mb 48%% 64Mb 32Mb In order to achieve an efficient load distribution, we firstly ran a benchmark that consisted in executing the same code on the different workstations. In particular, we used the co-operation module, once in its original sequential version and once in the multi-process version. This last test allowed us to evaluate a performance-index for each machine. These indexes were used to state the initial load distribution among the tasks running in the used workstations. Some adjustments were done considering other important aspects that affects the parallel performance, such as the communication medium and the different data representation adopted by the involved machines. Tab. 2 reports the execution times of the sequential code and Tab.3 the results of the benchmark in terms of the multi-process execution time and performance index of each workstation.
7 High-Performance Computing in Engineering 321 Tab. 2: sequential execution workstation RISC27 CEREUX POWER ALPHA SUNIPA CUCAIX cooperation Tab. 3: multi-process execution on a single workstation workstation cooperation peformance index RISC CEREUX POWER ALPHA SUNIPA CUCAIX As far as the efficiency evaluation is concerned, we should consider that the above workstations are heterogeneus, and therefore, we cannot correctly evaluate it as the ratio between the relative speedup and the number of used processor. Instead of this last quantity, we adopted a term that was evaluated as the ratio between the sum of the performance indexes of the used machines and the one of the workstation hosting the master task. Tab. 4: most representative results obtained allocating the master task in each workstation. master slaves 3 - CEREUX cooperation speedup efficiency RISC SUNIPA 5 - RISC RISC27 CEREUX 2 - ALPHA 4 - CEREUX 4 - CEREUX POWER 2 - SUNIPA 6 - RISC SUNIPA ALPHA 6-RISC CEREUX 3 - CEREUX 2 - POWER SUNIPA 2 - SUNIPA 5 - RISC POWER CUCAIX 4 - SUNIPA 5 - RISC As it can be observed, not all the configurations envolve all the workstations. This is due to the fact that, according to the performance indexes, the slowest machines should host a number of processes to low. In some cases this is not an effective option, and, generally speaking, it is better to restrict the configuration within a set of workstations not excessively different, especially when the master task runs on the fastest machine. It is relevant to observe that, while the efficiency value is roughly constant for all the configurations, the best speedup is relative to the configuration were the master task runs in the slowest machine. In this case the multi-process solution is four times faster than the sequential one.
8 322 High-Performance Computing in Engineering 5 Conclusions A parallel version of the BCS algorithm has been proposed. In particular an implementation of the cooperation module has been carried out distributing the computation of the possible orientations of the brightness gradient on different co-operating processes. A workstation network has been employed as a distributed system for the execution of the parallel experiments. The must relevant results have been reported that were obtained by trials with different configurations of the distributed system. The speed-up values rang from 1.58 to 4 in dependence of the processing rate of the involved machines. The paralellism degree has been bounded to twelve orientations, because these appeared to be sufficient for a good approximation of the actual direction of the brightness gradient. Nevertheless the model allows a larger number of directions to be evaluated. In this case the parallel implementation turns out to be more effective in reducing the processing time. References 1. Grossberg, S. & Mingolla, E. Neural dynamics of perceptual grouping: Textures, boundaries, and emergent segmentations, Perception & j,1985,38(2), Grossberg, S. & Mingolla, E. Neural dynamics of form perception: Boundary webs, illuminants, and shape-from-shading, Computer Vision, Graphics and Image Processing, 1987,37, E. Ardizzone, A. Chella, R. Pirrone, F. Sorbello: Recovering 3-D Form Features by a Connectionist Architecture, Pattern Recognition Letters, 15, (1994), G.A. Geist & V.S. Sunderam, Network-Based Concurrent Computing on the PVM System, Concurrency: Practice and Experience, 19924(4). 5. SunSoft, SunOS 5.3 Network Interfaces Programmer's Guide, XDR Protocol Specification, 1993 part number ,.261 -
Robust contour extraction and junction detection by a neural model utilizing recurrent long-range interactions
 Robust contour extraction and junction detection by a neural model utilizing recurrent long-range interactions Thorsten Hansen 1, 2 & Heiko Neumann 2 1 Abteilung Allgemeine Psychologie, Justus-Liebig-Universität
Robust contour extraction and junction detection by a neural model utilizing recurrent long-range interactions Thorsten Hansen 1, 2 & Heiko Neumann 2 1 Abteilung Allgemeine Psychologie, Justus-Liebig-Universität
A Resource Look up Strategy for Distributed Computing
 A Resource Look up Strategy for Distributed Computing F. AGOSTARO, A. GENCO, S. SORCE DINFO - Dipartimento di Ingegneria Informatica Università degli Studi di Palermo Viale delle Scienze, edificio 6 90128
A Resource Look up Strategy for Distributed Computing F. AGOSTARO, A. GENCO, S. SORCE DINFO - Dipartimento di Ingegneria Informatica Università degli Studi di Palermo Viale delle Scienze, edificio 6 90128
A Neural architecture for 3D Segmentation
 A Neural architecture for 3D Segmentation Antonio Chella 1,2, Umberto Maniscalco 2, and Roberto Pirrone 1,2 1 DINFO - University of Palermo Viale delle Scienze 90128 Palermo, Italy {chella,pirrone}@unipa.it
A Neural architecture for 3D Segmentation Antonio Chella 1,2, Umberto Maniscalco 2, and Roberto Pirrone 1,2 1 DINFO - University of Palermo Viale delle Scienze 90128 Palermo, Italy {chella,pirrone}@unipa.it
Feature Descriptors. CS 510 Lecture #21 April 29 th, 2013
 Feature Descriptors CS 510 Lecture #21 April 29 th, 2013 Programming Assignment #4 Due two weeks from today Any questions? How is it going? Where are we? We have two umbrella schemes for object recognition
Feature Descriptors CS 510 Lecture #21 April 29 th, 2013 Programming Assignment #4 Due two weeks from today Any questions? How is it going? Where are we? We have two umbrella schemes for object recognition
Lecture 6: Edge Detection
 #1 Lecture 6: Edge Detection Saad J Bedros sbedros@umn.edu Review From Last Lecture Options for Image Representation Introduced the concept of different representation or transformation Fourier Transform
#1 Lecture 6: Edge Detection Saad J Bedros sbedros@umn.edu Review From Last Lecture Options for Image Representation Introduced the concept of different representation or transformation Fourier Transform
NEURAL DYNAMICS OF 3-D SURFACE. March 7, Perception and Psychophysics, in press. The text and Paramter Table of this paper are available from
 NEURAL DYNAMICS OF 3-D SURFACE PERCEPTION: FIGURE-GROUND SEPARATION AND LIGHTNESS PERCEPTION Frank Kelly Stephen Grossberg March 7 000 Perception Psychophysics in press The text Paramter Table of this
NEURAL DYNAMICS OF 3-D SURFACE PERCEPTION: FIGURE-GROUND SEPARATION AND LIGHTNESS PERCEPTION Frank Kelly Stephen Grossberg March 7 000 Perception Psychophysics in press The text Paramter Table of this
LINUX. Benchmark problems have been calculated with dierent cluster con- gurations. The results obtained from these experiments are compared to those
 Parallel Computing on PC Clusters - An Alternative to Supercomputers for Industrial Applications Michael Eberl 1, Wolfgang Karl 1, Carsten Trinitis 1 and Andreas Blaszczyk 2 1 Technische Universitat Munchen
Parallel Computing on PC Clusters - An Alternative to Supercomputers for Industrial Applications Michael Eberl 1, Wolfgang Karl 1, Carsten Trinitis 1 and Andreas Blaszczyk 2 1 Technische Universitat Munchen
CHAPTER 6 PERCEPTUAL ORGANIZATION BASED ON TEMPORAL DYNAMICS
 CHAPTER 6 PERCEPTUAL ORGANIZATION BASED ON TEMPORAL DYNAMICS This chapter presents a computational model for perceptual organization. A figure-ground segregation network is proposed based on a novel boundary
CHAPTER 6 PERCEPTUAL ORGANIZATION BASED ON TEMPORAL DYNAMICS This chapter presents a computational model for perceptual organization. A figure-ground segregation network is proposed based on a novel boundary
Representation. and. Center for Adaptive Systems. Boston University. To appear in the 1995 Neural Networks special issue on
 Synthetic Aperture Radar Processing by a Multiple Scale Neural System for Boundary and Surface Representation Stephen Grossberg 1, Ennio Mingolla 2,andJames Williamson 3 Department of Cognitive and Neural
Synthetic Aperture Radar Processing by a Multiple Scale Neural System for Boundary and Surface Representation Stephen Grossberg 1, Ennio Mingolla 2,andJames Williamson 3 Department of Cognitive and Neural
Transactions on Information and Communications Technologies vol 15, 1997 WIT Press, ISSN
 Balanced workload distribution on a multi-processor cluster J.L. Bosque*, B. Moreno*", L. Pastor*" *Depatamento de Automdtica, Escuela Universitaria Politecnica de la Universidad de Alcald, Alcald de Henares,
Balanced workload distribution on a multi-processor cluster J.L. Bosque*, B. Moreno*", L. Pastor*" *Depatamento de Automdtica, Escuela Universitaria Politecnica de la Universidad de Alcald, Alcald de Henares,
Anno accademico 2006/2007. Davide Migliore
 Robotica Anno accademico 6/7 Davide Migliore migliore@elet.polimi.it Today What is a feature? Some useful information The world of features: Detectors Edges detection Corners/Points detection Descriptors?!?!?
Robotica Anno accademico 6/7 Davide Migliore migliore@elet.polimi.it Today What is a feature? Some useful information The world of features: Detectors Edges detection Corners/Points detection Descriptors?!?!?
Image Resizing Based on Gradient Vector Flow Analysis
 Image Resizing Based on Gradient Vector Flow Analysis Sebastiano Battiato battiato@dmi.unict.it Giovanni Puglisi puglisi@dmi.unict.it Giovanni Maria Farinella gfarinellao@dmi.unict.it Daniele Ravì rav@dmi.unict.it
Image Resizing Based on Gradient Vector Flow Analysis Sebastiano Battiato battiato@dmi.unict.it Giovanni Puglisi puglisi@dmi.unict.it Giovanni Maria Farinella gfarinellao@dmi.unict.it Daniele Ravì rav@dmi.unict.it
Three-Dimensional Computer Vision
 \bshiaki Shirai Three-Dimensional Computer Vision With 313 Figures ' Springer-Verlag Berlin Heidelberg New York London Paris Tokyo Table of Contents 1 Introduction 1 1.1 Three-Dimensional Computer Vision
\bshiaki Shirai Three-Dimensional Computer Vision With 313 Figures ' Springer-Verlag Berlin Heidelberg New York London Paris Tokyo Table of Contents 1 Introduction 1 1.1 Three-Dimensional Computer Vision
Point-to-Point Synchronisation on Shared Memory Architectures
 Point-to-Point Synchronisation on Shared Memory Architectures J. Mark Bull and Carwyn Ball EPCC, The King s Buildings, The University of Edinburgh, Mayfield Road, Edinburgh EH9 3JZ, Scotland, U.K. email:
Point-to-Point Synchronisation on Shared Memory Architectures J. Mark Bull and Carwyn Ball EPCC, The King s Buildings, The University of Edinburgh, Mayfield Road, Edinburgh EH9 3JZ, Scotland, U.K. email:
Parallel Implementation of a Unied Approach to. Image Focus and Defocus Analysis on the Parallel Virtual Machine
 Parallel Implementation of a Unied Approach to Image Focus and Defocus Analysis on the Parallel Virtual Machine Yen-Fu Liu, Nai-Wei Lo, Murali Subbarao, Bradley S. Carlson yiu@sbee.sunysb.edu, naiwei@sbee.sunysb.edu
Parallel Implementation of a Unied Approach to Image Focus and Defocus Analysis on the Parallel Virtual Machine Yen-Fu Liu, Nai-Wei Lo, Murali Subbarao, Bradley S. Carlson yiu@sbee.sunysb.edu, naiwei@sbee.sunysb.edu
CAP 5415 Computer Vision Fall 2012
 CAP 5415 Computer Vision Fall 01 Dr. Mubarak Shah Univ. of Central Florida Office 47-F HEC Lecture-5 SIFT: David Lowe, UBC SIFT - Key Point Extraction Stands for scale invariant feature transform Patented
CAP 5415 Computer Vision Fall 01 Dr. Mubarak Shah Univ. of Central Florida Office 47-F HEC Lecture-5 SIFT: David Lowe, UBC SIFT - Key Point Extraction Stands for scale invariant feature transform Patented
Unsupervised Learning
 Unsupervised Learning Learning without a teacher No targets for the outputs Networks which discover patterns, correlations, etc. in the input data This is a self organisation Self organising networks An
Unsupervised Learning Learning without a teacher No targets for the outputs Networks which discover patterns, correlations, etc. in the input data This is a self organisation Self organising networks An
Biometrics Technology: Image Processing & Pattern Recognition (by Dr. Dickson Tong)
 Biometrics Technology: Image Processing & Pattern Recognition (by Dr. Dickson Tong) References: [1] http://homepages.inf.ed.ac.uk/rbf/hipr2/index.htm [2] http://www.cs.wisc.edu/~dyer/cs540/notes/vision.html
Biometrics Technology: Image Processing & Pattern Recognition (by Dr. Dickson Tong) References: [1] http://homepages.inf.ed.ac.uk/rbf/hipr2/index.htm [2] http://www.cs.wisc.edu/~dyer/cs540/notes/vision.html
Comment on Numerical shape from shading and occluding boundaries
 Artificial Intelligence 59 (1993) 89-94 Elsevier 89 ARTINT 1001 Comment on Numerical shape from shading and occluding boundaries K. Ikeuchi School of Compurer Science. Carnegie Mellon dniversity. Pirrsburgh.
Artificial Intelligence 59 (1993) 89-94 Elsevier 89 ARTINT 1001 Comment on Numerical shape from shading and occluding boundaries K. Ikeuchi School of Compurer Science. Carnegie Mellon dniversity. Pirrsburgh.
100 Mbps DEC FDDI Gigaswitch
 PVM Communication Performance in a Switched FDDI Heterogeneous Distributed Computing Environment Michael J. Lewis Raymond E. Cline, Jr. Distributed Computing Department Distributed Computing Department
PVM Communication Performance in a Switched FDDI Heterogeneous Distributed Computing Environment Michael J. Lewis Raymond E. Cline, Jr. Distributed Computing Department Distributed Computing Department
Computational Foundations of Cognitive Science
 Computational Foundations of Cognitive Science Lecture 16: Models of Object Recognition Frank Keller School of Informatics University of Edinburgh keller@inf.ed.ac.uk February 23, 2010 Frank Keller Computational
Computational Foundations of Cognitive Science Lecture 16: Models of Object Recognition Frank Keller School of Informatics University of Edinburgh keller@inf.ed.ac.uk February 23, 2010 Frank Keller Computational
Parallel Program for Sorting NXN Matrix Using PVM (Parallel Virtual Machine)
 Parallel Program for Sorting NXN Matrix Using PVM (Parallel Virtual Machine) Ehab AbdulRazak Al-Asadi College of Science Kerbala University, Iraq Abstract The study will focus for analysis the possibilities
Parallel Program for Sorting NXN Matrix Using PVM (Parallel Virtual Machine) Ehab AbdulRazak Al-Asadi College of Science Kerbala University, Iraq Abstract The study will focus for analysis the possibilities
Edge and local feature detection - 2. Importance of edge detection in computer vision
 Edge and local feature detection Gradient based edge detection Edge detection by function fitting Second derivative edge detectors Edge linking and the construction of the chain graph Edge and local feature
Edge and local feature detection Gradient based edge detection Edge detection by function fitting Second derivative edge detectors Edge linking and the construction of the chain graph Edge and local feature
Using surface markings to enhance accuracy and stability of object perception in graphic displays
 Using surface markings to enhance accuracy and stability of object perception in graphic displays Roger A. Browse a,b, James C. Rodger a, and Robert A. Adderley a a Department of Computing and Information
Using surface markings to enhance accuracy and stability of object perception in graphic displays Roger A. Browse a,b, James C. Rodger a, and Robert A. Adderley a a Department of Computing and Information
Autoorganised Structures for Extraction of Perceptual Primitives
 Autoorganised Structures for Extraction of Perceptual Primitives M. Penas, M.G.Penedo Dept. Computer Science Univ. of A Coruña, SPAIN M.J.Carreira Dept. Electronics and Computer Science Univ. of Santiago
Autoorganised Structures for Extraction of Perceptual Primitives M. Penas, M.G.Penedo Dept. Computer Science Univ. of A Coruña, SPAIN M.J.Carreira Dept. Electronics and Computer Science Univ. of Santiago
Transactions on Information and Communications Technologies vol 20, 1998 WIT Press, ISSN
 A feed-forward neural network approach to edge detection L.X. Zhou & W.K. Gu Department of Information Science & Electronic Engineering, Zhejiang University, Hangzhou 3007, P.R. China EMail: zhoulx@isee.zju.edu.cn
A feed-forward neural network approach to edge detection L.X. Zhou & W.K. Gu Department of Information Science & Electronic Engineering, Zhejiang University, Hangzhou 3007, P.R. China EMail: zhoulx@isee.zju.edu.cn
PARALLEL VISUALIZATION OF LARGE-SCALE FINITE ELEMENT SOLUTIONS USING PC CLUSTER IN THE CABIN
 Annual Report of ADVENTURE Project ADV-99-1 (1999) PARALLEL VISUALIZATION OF LARGE-SCALE FINITE ELEMENT SOLUTIONS Izuru. SHIRAI *1, Shinobu. YOSHIMURA *1, and Genki. YAGAWA *2 *1 School of Frontier Science,
Annual Report of ADVENTURE Project ADV-99-1 (1999) PARALLEL VISUALIZATION OF LARGE-SCALE FINITE ELEMENT SOLUTIONS Izuru. SHIRAI *1, Shinobu. YOSHIMURA *1, and Genki. YAGAWA *2 *1 School of Frontier Science,
Practical Image and Video Processing Using MATLAB
 Practical Image and Video Processing Using MATLAB Chapter 14 Edge detection What will we learn? What is edge detection and why is it so important to computer vision? What are the main edge detection techniques
Practical Image and Video Processing Using MATLAB Chapter 14 Edge detection What will we learn? What is edge detection and why is it so important to computer vision? What are the main edge detection techniques
Detecting Salient Contours Using Orientation Energy Distribution. Part I: Thresholding Based on. Response Distribution
 Detecting Salient Contours Using Orientation Energy Distribution The Problem: How Does the Visual System Detect Salient Contours? CPSC 636 Slide12, Spring 212 Yoonsuck Choe Co-work with S. Sarma and H.-C.
Detecting Salient Contours Using Orientation Energy Distribution The Problem: How Does the Visual System Detect Salient Contours? CPSC 636 Slide12, Spring 212 Yoonsuck Choe Co-work with S. Sarma and H.-C.
Lecture 7: Most Common Edge Detectors
 #1 Lecture 7: Most Common Edge Detectors Saad Bedros sbedros@umn.edu Edge Detection Goal: Identify sudden changes (discontinuities) in an image Intuitively, most semantic and shape information from the
#1 Lecture 7: Most Common Edge Detectors Saad Bedros sbedros@umn.edu Edge Detection Goal: Identify sudden changes (discontinuities) in an image Intuitively, most semantic and shape information from the
COLOR FIDELITY OF CHROMATIC DISTRIBUTIONS BY TRIAD ILLUMINANT COMPARISON. Marcel P. Lucassen, Theo Gevers, Arjan Gijsenij
 COLOR FIDELITY OF CHROMATIC DISTRIBUTIONS BY TRIAD ILLUMINANT COMPARISON Marcel P. Lucassen, Theo Gevers, Arjan Gijsenij Intelligent Systems Lab Amsterdam, University of Amsterdam ABSTRACT Performance
COLOR FIDELITY OF CHROMATIC DISTRIBUTIONS BY TRIAD ILLUMINANT COMPARISON Marcel P. Lucassen, Theo Gevers, Arjan Gijsenij Intelligent Systems Lab Amsterdam, University of Amsterdam ABSTRACT Performance
SUPPLEMENTARY FILE S1: 3D AIRWAY TUBE RECONSTRUCTION AND CELL-BASED MECHANICAL MODEL. RELATED TO FIGURE 1, FIGURE 7, AND STAR METHODS.
 SUPPLEMENTARY FILE S1: 3D AIRWAY TUBE RECONSTRUCTION AND CELL-BASED MECHANICAL MODEL. RELATED TO FIGURE 1, FIGURE 7, AND STAR METHODS. 1. 3D AIRWAY TUBE RECONSTRUCTION. RELATED TO FIGURE 1 AND STAR METHODS
SUPPLEMENTARY FILE S1: 3D AIRWAY TUBE RECONSTRUCTION AND CELL-BASED MECHANICAL MODEL. RELATED TO FIGURE 1, FIGURE 7, AND STAR METHODS. 1. 3D AIRWAY TUBE RECONSTRUCTION. RELATED TO FIGURE 1 AND STAR METHODS
Chapter 7 Practical Considerations in Modeling. Chapter 7 Practical Considerations in Modeling
 CIVL 7/8117 1/43 Chapter 7 Learning Objectives To present concepts that should be considered when modeling for a situation by the finite element method, such as aspect ratio, symmetry, natural subdivisions,
CIVL 7/8117 1/43 Chapter 7 Learning Objectives To present concepts that should be considered when modeling for a situation by the finite element method, such as aspect ratio, symmetry, natural subdivisions,
Efficient Visual Coding: From Retina To V2
 Efficient Visual Coding: From Retina To V Honghao Shan Garrison Cottrell Computer Science and Engineering UCSD La Jolla, CA 9093-0404 shanhonghao@gmail.com, gary@ucsd.edu Abstract The human visual system
Efficient Visual Coding: From Retina To V Honghao Shan Garrison Cottrell Computer Science and Engineering UCSD La Jolla, CA 9093-0404 shanhonghao@gmail.com, gary@ucsd.edu Abstract The human visual system
Solution: filter the image, then subsample F 1 F 2. subsample blur subsample. blur
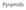 Pyramids Gaussian pre-filtering Solution: filter the image, then subsample blur F 0 subsample blur subsample * F 0 H F 1 F 1 * H F 2 { Gaussian pyramid blur F 0 subsample blur subsample * F 0 H F 1 F 1
Pyramids Gaussian pre-filtering Solution: filter the image, then subsample blur F 0 subsample blur subsample * F 0 H F 1 F 1 * H F 2 { Gaussian pyramid blur F 0 subsample blur subsample * F 0 H F 1 F 1
Perception. Autonomous Mobile Robots. Sensors Vision Uncertainties, Line extraction from laser scans. Autonomous Systems Lab. Zürich.
 Autonomous Mobile Robots Localization "Position" Global Map Cognition Environment Model Local Map Path Perception Real World Environment Motion Control Perception Sensors Vision Uncertainties, Line extraction
Autonomous Mobile Robots Localization "Position" Global Map Cognition Environment Model Local Map Path Perception Real World Environment Motion Control Perception Sensors Vision Uncertainties, Line extraction
Vivekananda. Collegee of Engineering & Technology. Question and Answers on 10CS762 /10IS762 UNIT- 5 : IMAGE ENHANCEMENT.
 Vivekananda Collegee of Engineering & Technology Question and Answers on 10CS762 /10IS762 UNIT- 5 : IMAGE ENHANCEMENT Dept. Prepared by Harivinod N Assistant Professor, of Computer Science and Engineering,
Vivekananda Collegee of Engineering & Technology Question and Answers on 10CS762 /10IS762 UNIT- 5 : IMAGE ENHANCEMENT Dept. Prepared by Harivinod N Assistant Professor, of Computer Science and Engineering,
Transactions on Information and Communications Technologies vol 9, 1995 WIT Press, ISSN
 Finite difference and finite element analyses using a cluster of workstations K.P. Wang, J.C. Bruch, Jr. Department of Mechanical and Environmental Engineering, q/ca/z/brm'a, 5Wa jbw6wa CW 937% Abstract
Finite difference and finite element analyses using a cluster of workstations K.P. Wang, J.C. Bruch, Jr. Department of Mechanical and Environmental Engineering, q/ca/z/brm'a, 5Wa jbw6wa CW 937% Abstract
Region-based Segmentation
 Region-based Segmentation Image Segmentation Group similar components (such as, pixels in an image, image frames in a video) to obtain a compact representation. Applications: Finding tumors, veins, etc.
Region-based Segmentation Image Segmentation Group similar components (such as, pixels in an image, image frames in a video) to obtain a compact representation. Applications: Finding tumors, veins, etc.
Moving Object Tracking in Video Using MATLAB
 Moving Object Tracking in Video Using MATLAB Bhavana C. Bendale, Prof. Anil R. Karwankar Abstract In this paper a method is described for tracking moving objects from a sequence of video frame. This method
Moving Object Tracking in Video Using MATLAB Bhavana C. Bendale, Prof. Anil R. Karwankar Abstract In this paper a method is described for tracking moving objects from a sequence of video frame. This method
Robotics Programming Laboratory
 Chair of Software Engineering Robotics Programming Laboratory Bertrand Meyer Jiwon Shin Lecture 8: Robot Perception Perception http://pascallin.ecs.soton.ac.uk/challenges/voc/databases.html#caltech car
Chair of Software Engineering Robotics Programming Laboratory Bertrand Meyer Jiwon Shin Lecture 8: Robot Perception Perception http://pascallin.ecs.soton.ac.uk/challenges/voc/databases.html#caltech car
Edge Detection for Dental X-ray Image Segmentation using Neural Network approach
 Volume 1, No. 7, September 2012 ISSN 2278-1080 The International Journal of Computer Science & Applications (TIJCSA) RESEARCH PAPER Available Online at http://www.journalofcomputerscience.com/ Edge Detection
Volume 1, No. 7, September 2012 ISSN 2278-1080 The International Journal of Computer Science & Applications (TIJCSA) RESEARCH PAPER Available Online at http://www.journalofcomputerscience.com/ Edge Detection
Evaluation of Parallel Application s Performance Dependency on RAM using Parallel Virtual Machine
 Evaluation of Parallel Application s Performance Dependency on RAM using Parallel Virtual Machine Sampath S 1, Nanjesh B R 1 1 Department of Information Science and Engineering Adichunchanagiri Institute
Evaluation of Parallel Application s Performance Dependency on RAM using Parallel Virtual Machine Sampath S 1, Nanjesh B R 1 1 Department of Information Science and Engineering Adichunchanagiri Institute
Three basic multiprocessing issues
 Three basic multiprocessing issues 1. artitioning. The sequential program must be partitioned into subprogram units or tasks. This is done either by the programmer or by the compiler. 2. Scheduling. Associated
Three basic multiprocessing issues 1. artitioning. The sequential program must be partitioned into subprogram units or tasks. This is done either by the programmer or by the compiler. 2. Scheduling. Associated
An Introduction to Content Based Image Retrieval
 CHAPTER -1 An Introduction to Content Based Image Retrieval 1.1 Introduction With the advancement in internet and multimedia technologies, a huge amount of multimedia data in the form of audio, video and
CHAPTER -1 An Introduction to Content Based Image Retrieval 1.1 Introduction With the advancement in internet and multimedia technologies, a huge amount of multimedia data in the form of audio, video and
What is Computer Vision?
 Perceptual Grouping in Computer Vision Gérard Medioni University of Southern California What is Computer Vision? Computer Vision Attempt to emulate Human Visual System Perceive visual stimuli with cameras
Perceptual Grouping in Computer Vision Gérard Medioni University of Southern California What is Computer Vision? Computer Vision Attempt to emulate Human Visual System Perceive visual stimuli with cameras
CONFIGR: A vision-based model for long-range figure completion
 Neural Networks 20 (2007) 1109 1131 www.elsevier.com/locate/neunet CONFIGR: A vision-based model for long-range figure completion Gail A. Carpenter, Chaitanya Sai Gaddam, Ennio Mingolla Department of Cognitive
Neural Networks 20 (2007) 1109 1131 www.elsevier.com/locate/neunet CONFIGR: A vision-based model for long-range figure completion Gail A. Carpenter, Chaitanya Sai Gaddam, Ennio Mingolla Department of Cognitive
Depth. Common Classification Tasks. Example: AlexNet. Another Example: Inception. Another Example: Inception. Depth
 Common Classification Tasks Recognition of individual objects/faces Analyze object-specific features (e.g., key points) Train with images from different viewing angles Recognition of object classes Analyze
Common Classification Tasks Recognition of individual objects/faces Analyze object-specific features (e.g., key points) Train with images from different viewing angles Recognition of object classes Analyze
A neural network for enhancing boundaries and surfaces in synthetic aperture radar images
 Neural Networks PERGAMON Neural Networks 12 (1999) 499 511 Contributed article A neural network for enhancing boundaries and surfaces in synthetic aperture radar images Ennio Mingolla, William Ross, Stephen
Neural Networks PERGAMON Neural Networks 12 (1999) 499 511 Contributed article A neural network for enhancing boundaries and surfaces in synthetic aperture radar images Ennio Mingolla, William Ross, Stephen
Part 3: Image Processing
 Part 3: Image Processing Image Filtering and Segmentation Georgy Gimel farb COMPSCI 373 Computer Graphics and Image Processing 1 / 60 1 Image filtering 2 Median filtering 3 Mean filtering 4 Image segmentation
Part 3: Image Processing Image Filtering and Segmentation Georgy Gimel farb COMPSCI 373 Computer Graphics and Image Processing 1 / 60 1 Image filtering 2 Median filtering 3 Mean filtering 4 Image segmentation
Arbib: Slides for TMB2 Section 7.2 1
 Arbib: Slides for TMB2 Section 7.2 1 Lecture 20: Optic Flow Reading assignment: TMB2 7.2 If, as we walk forward, we recognize that a tree appears to be getting bigger, we can infer that the tree is in
Arbib: Slides for TMB2 Section 7.2 1 Lecture 20: Optic Flow Reading assignment: TMB2 7.2 If, as we walk forward, we recognize that a tree appears to be getting bigger, we can infer that the tree is in
Massachusetts Institute of Technology. Department of Computer Science and Electrical Engineering /6.866 Machine Vision Quiz I
 Massachusetts Institute of Technology Department of Computer Science and Electrical Engineering 6.801/6.866 Machine Vision Quiz I Handed out: 2004 Oct. 21st Due on: 2003 Oct. 28th Problem 1: Uniform reflecting
Massachusetts Institute of Technology Department of Computer Science and Electrical Engineering 6.801/6.866 Machine Vision Quiz I Handed out: 2004 Oct. 21st Due on: 2003 Oct. 28th Problem 1: Uniform reflecting
THE CAMERA TRANSFORM
 On-Line Computer Graphics Notes THE CAMERA TRANSFORM Kenneth I. Joy Visualization and Graphics Research Group Department of Computer Science University of California, Davis Overview To understanding the
On-Line Computer Graphics Notes THE CAMERA TRANSFORM Kenneth I. Joy Visualization and Graphics Research Group Department of Computer Science University of California, Davis Overview To understanding the
Big Orange Bramble. August 09, 2016
 Big Orange Bramble August 09, 2016 Overview HPL SPH PiBrot Numeric Integration Parallel Pi Monte Carlo FDS DANNA HPL High Performance Linpack is a benchmark for clusters Created here at the University
Big Orange Bramble August 09, 2016 Overview HPL SPH PiBrot Numeric Integration Parallel Pi Monte Carlo FDS DANNA HPL High Performance Linpack is a benchmark for clusters Created here at the University
(Refer Slide Time 00:17) Welcome to the course on Digital Image Processing. (Refer Slide Time 00:22)
 Digital Image Processing Prof. P. K. Biswas Department of Electronics and Electrical Communications Engineering Indian Institute of Technology, Kharagpur Module Number 01 Lecture Number 02 Application
Digital Image Processing Prof. P. K. Biswas Department of Electronics and Electrical Communications Engineering Indian Institute of Technology, Kharagpur Module Number 01 Lecture Number 02 Application
Introduction to visual computation and the primate visual system
 Introduction to visual computation and the primate visual system Problems in vision Basic facts about the visual system Mathematical models for early vision Marr s computational philosophy and proposal
Introduction to visual computation and the primate visual system Problems in vision Basic facts about the visual system Mathematical models for early vision Marr s computational philosophy and proposal
Last update: May 4, Vision. CMSC 421: Chapter 24. CMSC 421: Chapter 24 1
 Last update: May 4, 200 Vision CMSC 42: Chapter 24 CMSC 42: Chapter 24 Outline Perception generally Image formation Early vision 2D D Object recognition CMSC 42: Chapter 24 2 Perception generally Stimulus
Last update: May 4, 200 Vision CMSC 42: Chapter 24 CMSC 42: Chapter 24 Outline Perception generally Image formation Early vision 2D D Object recognition CMSC 42: Chapter 24 2 Perception generally Stimulus
Topic 4 Image Segmentation
 Topic 4 Image Segmentation What is Segmentation? Why? Segmentation important contributing factor to the success of an automated image analysis process What is Image Analysis: Processing images to derive
Topic 4 Image Segmentation What is Segmentation? Why? Segmentation important contributing factor to the success of an automated image analysis process What is Image Analysis: Processing images to derive
(0, 1, 1) (0, 1, 1) (0, 1, 0) What is light? What is color? Terminology
 lecture 23 (0, 1, 1) (0, 0, 0) (0, 0, 1) (0, 1, 1) (1, 1, 1) (1, 1, 0) (0, 1, 0) hue - which ''? saturation - how pure? luminance (value) - intensity What is light? What is? Light consists of electromagnetic
lecture 23 (0, 1, 1) (0, 0, 0) (0, 0, 1) (0, 1, 1) (1, 1, 1) (1, 1, 0) (0, 1, 0) hue - which ''? saturation - how pure? luminance (value) - intensity What is light? What is? Light consists of electromagnetic
Edge Detection (with a sidelight introduction to linear, associative operators). Images
 Images (we will, eventually, come back to imaging geometry. But, now that we know how images come from the world, we will examine operations on images). Edge Detection (with a sidelight introduction to
Images (we will, eventually, come back to imaging geometry. But, now that we know how images come from the world, we will examine operations on images). Edge Detection (with a sidelight introduction to
Perception, Part 2 Gleitman et al. (2011), Chapter 5
 Perception, Part 2 Gleitman et al. (2011), Chapter 5 Mike D Zmura Department of Cognitive Sciences, UCI Psych 9A / Psy Beh 11A February 27, 2014 T. M. D'Zmura 1 Visual Reconstruction of a Three-Dimensional
Perception, Part 2 Gleitman et al. (2011), Chapter 5 Mike D Zmura Department of Cognitive Sciences, UCI Psych 9A / Psy Beh 11A February 27, 2014 T. M. D'Zmura 1 Visual Reconstruction of a Three-Dimensional
Visual object classification by sparse convolutional neural networks
 Visual object classification by sparse convolutional neural networks Alexander Gepperth 1 1- Ruhr-Universität Bochum - Institute for Neural Dynamics Universitätsstraße 150, 44801 Bochum - Germany Abstract.
Visual object classification by sparse convolutional neural networks Alexander Gepperth 1 1- Ruhr-Universität Bochum - Institute for Neural Dynamics Universitätsstraße 150, 44801 Bochum - Germany Abstract.
Local Features: Detection, Description & Matching
 Local Features: Detection, Description & Matching Lecture 08 Computer Vision Material Citations Dr George Stockman Professor Emeritus, Michigan State University Dr David Lowe Professor, University of British
Local Features: Detection, Description & Matching Lecture 08 Computer Vision Material Citations Dr George Stockman Professor Emeritus, Michigan State University Dr David Lowe Professor, University of British
CHAPTER 6 DETECTION OF MASS USING NOVEL SEGMENTATION, GLCM AND NEURAL NETWORKS
 130 CHAPTER 6 DETECTION OF MASS USING NOVEL SEGMENTATION, GLCM AND NEURAL NETWORKS A mass is defined as a space-occupying lesion seen in more than one projection and it is described by its shapes and margin
130 CHAPTER 6 DETECTION OF MASS USING NOVEL SEGMENTATION, GLCM AND NEURAL NETWORKS A mass is defined as a space-occupying lesion seen in more than one projection and it is described by its shapes and margin
Traffic Signs Recognition using HP and HOG Descriptors Combined to MLP and SVM Classifiers
 Traffic Signs Recognition using HP and HOG Descriptors Combined to MLP and SVM Classifiers A. Salhi, B. Minaoui, M. Fakir, H. Chakib, H. Grimech Faculty of science and Technology Sultan Moulay Slimane
Traffic Signs Recognition using HP and HOG Descriptors Combined to MLP and SVM Classifiers A. Salhi, B. Minaoui, M. Fakir, H. Chakib, H. Grimech Faculty of science and Technology Sultan Moulay Slimane
Outline 7/2/201011/6/
 Outline Pattern recognition in computer vision Background on the development of SIFT SIFT algorithm and some of its variations Computational considerations (SURF) Potential improvement Summary 01 2 Pattern
Outline Pattern recognition in computer vision Background on the development of SIFT SIFT algorithm and some of its variations Computational considerations (SURF) Potential improvement Summary 01 2 Pattern
Alpha AXP Workstation Family Performance Brief - OpenVMS
 DEC 3000 Model 500 AXP Workstation DEC 3000 Model 400 AXP Workstation INSIDE Digital Equipment Corporation November 20, 1992 Second Edition EB-N0102-51 Benchmark results: SPEC LINPACK Dhrystone X11perf
DEC 3000 Model 500 AXP Workstation DEC 3000 Model 400 AXP Workstation INSIDE Digital Equipment Corporation November 20, 1992 Second Edition EB-N0102-51 Benchmark results: SPEC LINPACK Dhrystone X11perf
Stereovision. Binocular disparity
 Stereovision Binocular disparity Retinal correspondence Uncrossed disparity Horoptor Crossed disparity Horoptor, crossed and uncrossed disparity Wheatsteone stereoscope (c. 1838) Red-green anaglyph How
Stereovision Binocular disparity Retinal correspondence Uncrossed disparity Horoptor Crossed disparity Horoptor, crossed and uncrossed disparity Wheatsteone stereoscope (c. 1838) Red-green anaglyph How
Structural Analysis of Aerial Photographs (HB47 Computer Vision: Assignment)
 Structural Analysis of Aerial Photographs (HB47 Computer Vision: Assignment) Xiaodong Lu, Jin Yu, Yajie Li Master in Artificial Intelligence May 2004 Table of Contents 1 Introduction... 1 2 Edge-Preserving
Structural Analysis of Aerial Photographs (HB47 Computer Vision: Assignment) Xiaodong Lu, Jin Yu, Yajie Li Master in Artificial Intelligence May 2004 Table of Contents 1 Introduction... 1 2 Edge-Preserving
CS4442/9542b Artificial Intelligence II prof. Olga Veksler
 CS4442/9542b Artificial Intelligence II prof. Olga Veksler Lecture 8 Computer Vision Introduction, Filtering Some slides from: D. Jacobs, D. Lowe, S. Seitz, A.Efros, X. Li, R. Fergus, J. Hayes, S. Lazebnik,
CS4442/9542b Artificial Intelligence II prof. Olga Veksler Lecture 8 Computer Vision Introduction, Filtering Some slides from: D. Jacobs, D. Lowe, S. Seitz, A.Efros, X. Li, R. Fergus, J. Hayes, S. Lazebnik,
NEURAL NETWORK VISUALIZATION
 Neural Network Visualization 465 NEURAL NETWORK VISUALIZATION Jakub Wejchert Gerald Tesauro IB M Research T.J. Watson Research Center Yorktown Heights NY 10598 ABSTRACT We have developed graphics to visualize
Neural Network Visualization 465 NEURAL NETWORK VISUALIZATION Jakub Wejchert Gerald Tesauro IB M Research T.J. Watson Research Center Yorktown Heights NY 10598 ABSTRACT We have developed graphics to visualize
Image Processing
 Image Processing 159.731 Canny Edge Detection Report Syed Irfanullah, Azeezullah 00297844 Danh Anh Huynh 02136047 1 Canny Edge Detection INTRODUCTION Edges Edges characterize boundaries and are therefore
Image Processing 159.731 Canny Edge Detection Report Syed Irfanullah, Azeezullah 00297844 Danh Anh Huynh 02136047 1 Canny Edge Detection INTRODUCTION Edges Edges characterize boundaries and are therefore
A New Technique of Extraction of Edge Detection Using Digital Image Processing
 International OPEN ACCESS Journal Of Modern Engineering Research (IJMER) A New Technique of Extraction of Edge Detection Using Digital Image Processing Balaji S.C.K 1 1, Asst Professor S.V.I.T Abstract:
International OPEN ACCESS Journal Of Modern Engineering Research (IJMER) A New Technique of Extraction of Edge Detection Using Digital Image Processing Balaji S.C.K 1 1, Asst Professor S.V.I.T Abstract:
DISTRIBUTED HIGH-SPEED COMPUTING OF MULTIMEDIA DATA
 DISTRIBUTED HIGH-SPEED COMPUTING OF MULTIMEDIA DATA M. GAUS, G. R. JOUBERT, O. KAO, S. RIEDEL AND S. STAPEL Technical University of Clausthal, Department of Computer Science Julius-Albert-Str. 4, 38678
DISTRIBUTED HIGH-SPEED COMPUTING OF MULTIMEDIA DATA M. GAUS, G. R. JOUBERT, O. KAO, S. RIEDEL AND S. STAPEL Technical University of Clausthal, Department of Computer Science Julius-Albert-Str. 4, 38678
Machine Learning 13. week
 Machine Learning 13. week Deep Learning Convolutional Neural Network Recurrent Neural Network 1 Why Deep Learning is so Popular? 1. Increase in the amount of data Thanks to the Internet, huge amount of
Machine Learning 13. week Deep Learning Convolutional Neural Network Recurrent Neural Network 1 Why Deep Learning is so Popular? 1. Increase in the amount of data Thanks to the Internet, huge amount of
An Adaptive Eigenshape Model
 An Adaptive Eigenshape Model Adam Baumberg and David Hogg School of Computer Studies University of Leeds, Leeds LS2 9JT, U.K. amb@scs.leeds.ac.uk Abstract There has been a great deal of recent interest
An Adaptive Eigenshape Model Adam Baumberg and David Hogg School of Computer Studies University of Leeds, Leeds LS2 9JT, U.K. amb@scs.leeds.ac.uk Abstract There has been a great deal of recent interest
CS4442/9542b Artificial Intelligence II prof. Olga Veksler
 CS4442/9542b Artificial Intelligence II prof. Olga Veksler Lecture 2 Computer Vision Introduction, Filtering Some slides from: D. Jacobs, D. Lowe, S. Seitz, A.Efros, X. Li, R. Fergus, J. Hayes, S. Lazebnik,
CS4442/9542b Artificial Intelligence II prof. Olga Veksler Lecture 2 Computer Vision Introduction, Filtering Some slides from: D. Jacobs, D. Lowe, S. Seitz, A.Efros, X. Li, R. Fergus, J. Hayes, S. Lazebnik,
Image enhancement for face recognition using color segmentation and Edge detection algorithm
 Image enhancement for face recognition using color segmentation and Edge detection algorithm 1 Dr. K Perumal and 2 N Saravana Perumal 1 Computer Centre, Madurai Kamaraj University, Madurai-625021, Tamilnadu,
Image enhancement for face recognition using color segmentation and Edge detection algorithm 1 Dr. K Perumal and 2 N Saravana Perumal 1 Computer Centre, Madurai Kamaraj University, Madurai-625021, Tamilnadu,
Parallel Architecture & Programing Models for Face Recognition
 Parallel Architecture & Programing Models for Face Recognition Submitted by Sagar Kukreja Computer Engineering Department Rochester Institute of Technology Agenda Introduction to face recognition Feature
Parallel Architecture & Programing Models for Face Recognition Submitted by Sagar Kukreja Computer Engineering Department Rochester Institute of Technology Agenda Introduction to face recognition Feature
An Introduction to Parallel Programming
 An Introduction to Parallel Programming Ing. Andrea Marongiu (a.marongiu@unibo.it) Includes slides from Multicore Programming Primer course at Massachusetts Institute of Technology (MIT) by Prof. SamanAmarasinghe
An Introduction to Parallel Programming Ing. Andrea Marongiu (a.marongiu@unibo.it) Includes slides from Multicore Programming Primer course at Massachusetts Institute of Technology (MIT) by Prof. SamanAmarasinghe
Comparison between Various Edge Detection Methods on Satellite Image
 Comparison between Various Edge Detection Methods on Satellite Image H.S. Bhadauria 1, Annapurna Singh 2, Anuj Kumar 3 Govind Ballabh Pant Engineering College ( Pauri garhwal),computer Science and Engineering
Comparison between Various Edge Detection Methods on Satellite Image H.S. Bhadauria 1, Annapurna Singh 2, Anuj Kumar 3 Govind Ballabh Pant Engineering College ( Pauri garhwal),computer Science and Engineering
The SIFT (Scale Invariant Feature
 The SIFT (Scale Invariant Feature Transform) Detector and Descriptor developed by David Lowe University of British Columbia Initial paper ICCV 1999 Newer journal paper IJCV 2004 Review: Matt Brown s Canonical
The SIFT (Scale Invariant Feature Transform) Detector and Descriptor developed by David Lowe University of British Columbia Initial paper ICCV 1999 Newer journal paper IJCV 2004 Review: Matt Brown s Canonical
CS 664 Segmentation. Daniel Huttenlocher
 CS 664 Segmentation Daniel Huttenlocher Grouping Perceptual Organization Structural relationships between tokens Parallelism, symmetry, alignment Similarity of token properties Often strong psychophysical
CS 664 Segmentation Daniel Huttenlocher Grouping Perceptual Organization Structural relationships between tokens Parallelism, symmetry, alignment Similarity of token properties Often strong psychophysical
Applying Synthetic Images to Learning Grasping Orientation from Single Monocular Images
 Applying Synthetic Images to Learning Grasping Orientation from Single Monocular Images 1 Introduction - Steve Chuang and Eric Shan - Determining object orientation in images is a well-established topic
Applying Synthetic Images to Learning Grasping Orientation from Single Monocular Images 1 Introduction - Steve Chuang and Eric Shan - Determining object orientation in images is a well-established topic
DD2423 Image Analysis and Computer Vision IMAGE FORMATION. Computational Vision and Active Perception School of Computer Science and Communication
 DD2423 Image Analysis and Computer Vision IMAGE FORMATION Mårten Björkman Computational Vision and Active Perception School of Computer Science and Communication November 8, 2013 1 Image formation Goal:
DD2423 Image Analysis and Computer Vision IMAGE FORMATION Mårten Björkman Computational Vision and Active Perception School of Computer Science and Communication November 8, 2013 1 Image formation Goal:
Digital Image Processing. Image Enhancement - Filtering
 Digital Image Processing Image Enhancement - Filtering Derivative Derivative is defined as a rate of change. Discrete Derivative Finite Distance Example Derivatives in 2-dimension Derivatives of Images
Digital Image Processing Image Enhancement - Filtering Derivative Derivative is defined as a rate of change. Discrete Derivative Finite Distance Example Derivatives in 2-dimension Derivatives of Images
CS4733 Class Notes, Computer Vision
 CS4733 Class Notes, Computer Vision Sources for online computer vision tutorials and demos - http://www.dai.ed.ac.uk/hipr and Computer Vision resources online - http://www.dai.ed.ac.uk/cvonline Vision
CS4733 Class Notes, Computer Vision Sources for online computer vision tutorials and demos - http://www.dai.ed.ac.uk/hipr and Computer Vision resources online - http://www.dai.ed.ac.uk/cvonline Vision
Chapter 4. Clustering Core Atoms by Location
 Chapter 4. Clustering Core Atoms by Location In this chapter, a process for sampling core atoms in space is developed, so that the analytic techniques in section 3C can be applied to local collections
Chapter 4. Clustering Core Atoms by Location In this chapter, a process for sampling core atoms in space is developed, so that the analytic techniques in section 3C can be applied to local collections
Types of Edges. Why Edge Detection? Types of Edges. Edge Detection. Gradient. Edge Detection
 Why Edge Detection? How can an algorithm extract relevant information from an image that is enables the algorithm to recognize objects? The most important information for the interpretation of an image
Why Edge Detection? How can an algorithm extract relevant information from an image that is enables the algorithm to recognize objects? The most important information for the interpretation of an image
SEMI-BLIND IMAGE RESTORATION USING A LOCAL NEURAL APPROACH
 SEMI-BLIND IMAGE RESTORATION USING A LOCAL NEURAL APPROACH Ignazio Gallo, Elisabetta Binaghi and Mario Raspanti Universitá degli Studi dell Insubria Varese, Italy email: ignazio.gallo@uninsubria.it ABSTRACT
SEMI-BLIND IMAGE RESTORATION USING A LOCAL NEURAL APPROACH Ignazio Gallo, Elisabetta Binaghi and Mario Raspanti Universitá degli Studi dell Insubria Varese, Italy email: ignazio.gallo@uninsubria.it ABSTRACT
Segmentation and Grouping
 Segmentation and Grouping How and what do we see? Fundamental Problems ' Focus of attention, or grouping ' What subsets of pixels do we consider as possible objects? ' All connected subsets? ' Representation
Segmentation and Grouping How and what do we see? Fundamental Problems ' Focus of attention, or grouping ' What subsets of pixels do we consider as possible objects? ' All connected subsets? ' Representation
An Algorithm for Blurred Thermal image edge enhancement for security by image processing technique
 An Algorithm for Blurred Thermal image edge enhancement for security by image processing technique Vinay Negi 1, Dr.K.P.Mishra 2 1 ECE (PhD Research scholar), Monad University, India, Hapur 2 ECE, KIET,
An Algorithm for Blurred Thermal image edge enhancement for security by image processing technique Vinay Negi 1, Dr.K.P.Mishra 2 1 ECE (PhD Research scholar), Monad University, India, Hapur 2 ECE, KIET,
Texture. Frequency Descriptors. Frequency Descriptors. Frequency Descriptors. Frequency Descriptors. Frequency Descriptors
 Texture The most fundamental question is: How can we measure texture, i.e., how can we quantitatively distinguish between different textures? Of course it is not enough to look at the intensity of individual
Texture The most fundamental question is: How can we measure texture, i.e., how can we quantitatively distinguish between different textures? Of course it is not enough to look at the intensity of individual
Optimal Grouping of Line Segments into Convex Sets 1
 Optimal Grouping of Line Segments into Convex Sets 1 B. Parvin and S. Viswanathan Imaging and Distributed Computing Group Information and Computing Sciences Division Lawrence Berkeley National Laboratory,
Optimal Grouping of Line Segments into Convex Sets 1 B. Parvin and S. Viswanathan Imaging and Distributed Computing Group Information and Computing Sciences Division Lawrence Berkeley National Laboratory,
Chapter 11 Representation & Description
 Chain Codes Chain codes are used to represent a boundary by a connected sequence of straight-line segments of specified length and direction. The direction of each segment is coded by using a numbering
Chain Codes Chain codes are used to represent a boundary by a connected sequence of straight-line segments of specified length and direction. The direction of each segment is coded by using a numbering
Feature Tracking and Optical Flow
 Feature Tracking and Optical Flow Prof. D. Stricker Doz. G. Bleser Many slides adapted from James Hays, Derek Hoeim, Lana Lazebnik, Silvio Saverse, who 1 in turn adapted slides from Steve Seitz, Rick Szeliski,
Feature Tracking and Optical Flow Prof. D. Stricker Doz. G. Bleser Many slides adapted from James Hays, Derek Hoeim, Lana Lazebnik, Silvio Saverse, who 1 in turn adapted slides from Steve Seitz, Rick Szeliski,
Fast Denoising for Moving Object Detection by An Extended Structural Fitness Algorithm
 Fast Denoising for Moving Object Detection by An Extended Structural Fitness Algorithm ALBERTO FARO, DANIELA GIORDANO, CONCETTO SPAMPINATO Dipartimento di Ingegneria Informatica e Telecomunicazioni Facoltà
Fast Denoising for Moving Object Detection by An Extended Structural Fitness Algorithm ALBERTO FARO, DANIELA GIORDANO, CONCETTO SPAMPINATO Dipartimento di Ingegneria Informatica e Telecomunicazioni Facoltà
Gauss-Sigmoid Neural Network
 Gauss-Sigmoid Neural Network Katsunari SHIBATA and Koji ITO Tokyo Institute of Technology, Yokohama, JAPAN shibata@ito.dis.titech.ac.jp Abstract- Recently RBF(Radial Basis Function)-based networks have
Gauss-Sigmoid Neural Network Katsunari SHIBATA and Koji ITO Tokyo Institute of Technology, Yokohama, JAPAN shibata@ito.dis.titech.ac.jp Abstract- Recently RBF(Radial Basis Function)-based networks have
FACE RECOGNITION USING INDEPENDENT COMPONENT
 Chapter 5 FACE RECOGNITION USING INDEPENDENT COMPONENT ANALYSIS OF GABORJET (GABORJET-ICA) 5.1 INTRODUCTION PCA is probably the most widely used subspace projection technique for face recognition. A major
Chapter 5 FACE RECOGNITION USING INDEPENDENT COMPONENT ANALYSIS OF GABORJET (GABORJET-ICA) 5.1 INTRODUCTION PCA is probably the most widely used subspace projection technique for face recognition. A major
Image Compression: An Artificial Neural Network Approach
 Image Compression: An Artificial Neural Network Approach Anjana B 1, Mrs Shreeja R 2 1 Department of Computer Science and Engineering, Calicut University, Kuttippuram 2 Department of Computer Science and
Image Compression: An Artificial Neural Network Approach Anjana B 1, Mrs Shreeja R 2 1 Department of Computer Science and Engineering, Calicut University, Kuttippuram 2 Department of Computer Science and
