Performance analysis of hybrid (M/M/1 and M/M/m) client server model using Queuing theory
|
|
|
- Ferdinand Bell
- 6 years ago
- Views:
Transcription
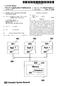
1 International Journal of Electronic and Couter cience Engineering vailable Online at wwwijeceorg IN erforance analyi of hybrid M/M/ and M/M/ client erver odel uing ueuing theory atarhi Guta, Dr Rajan John, Tannia Rubavathy Deartent of Electronic and Counication Engineering Deartent of Couter cience & Engineering ll Nation Univerity, Koforidua, Ghana, et frica Eail- btract- Internet ue acet witching and it i called delay yte hen any requet coe fro client ide, erver ay erve that requet iediately or it goe into queue for oe tie client i the couter, which requet the reource ail, audio, video etc, equied with a uer interface uually a web brower for reentation uroe DN Doain nae erver will a the web addre to it correonding Internet rotocol addre ll counication tae lace uing tranfer of acet acet arrive according to a oion roce with rate Router will route the requet to that articular Internet rotocol I of the alication erver The alication erver ta i to rovide the requeted reource ail, audio, video, authentication, but by calling on another erver Data erver, which rovide the alication erver with the data it require Thi aer deal with ingle erver and ultile erver queue Thi aer intend to find out the erforance average queue length, average reone tie, average waiting tie analyi of hybrid M/M/, M/M/ client erver odel uing queuing theory Keyword ueuing theory, Client erver odel, ingle erver queue, Multile erver queue I INTRODUCTION In -tier architecture, there i an interediary level, eaning the architecture i generally lit u between: a client, ie the couter, which requet the reource, equied with a uer interface uually a web brower for reentation uroe b The alication erver alo called iddleware, whoe ta it i to rovide the requeted reource, but by calling on another erver c The data erver, which rovide the alication erver with the data it require Figure Three-tier architecture of client erver odel ] IN 77-9/VN--0
2 IJECE,Volue,Nuber atarhi Guta et al In -tier architecture, each erver tier and erfor a ecialized ta a ervice erver can therefore ue ervice fro other erver in order to rovide own ervice a reult, -tier architecture i otentially an n-tiered architecture ] However, eb traffic i highly dynaic and volatile The data arrive and deart fro different node randoly Thu, we can enviage that, nuber of channel for arrival and nuber of channel for dearting ut be identical The incoing data can be tochatically treated a a roce and o will be the cae of dearting fro the eory of eb erver Thee ituation ae the woring of Meory of eb erver - a tyical cae of - ueuing roce ] It ha been ilicated that eory ae through divere ituation of ueue Model, ie, M/M/, M/M/ M/M/ odel i ot dicilined and can be analyzed analytically to etiate the queuing araeter ] The tandard queuing notation, /B/C, rereent the arrival ditribution, B the ervice ditribution, and C the nuber of erver For M/M/, odel nuber of erver i and for M/M/ odel denote ultile erver M ean eory le, which in thi context ilie oion ditribution for arrival rate and exonential ditribution for ervice tie ] II HYBRID UEUING RCHITECTURE FOR CLIENT ERVER MODEL Figure Hybrid queuing M/M/, M/M/ odel architecture client erver odel There are -inut in the queuing networ conidered in Figure with the arrival at the -inut being and The ervice rate are and The arrival rate at ource 0 i The robabilitie of arrival at ource inut 0 are, reectively Let be the arrival rate at firt queue, be the arrival at econd queue at the client brower Let the ervice rate of the erver and be and reectively Client brower will a the web addre to it correonding Internet rotocol addre fter getting erviced by erver and, the job arrive at queue Router Let be the arrival rate of the job at Router, o the arrival rate at i The ervice rate of the erver i Here, router chec the IN 77-9/VN--0
3 erforance analyi of hybrid M/M/ and M/M/ client erver odel uing ueuing theory I addre Internet rotocol addre of the articular alication erver which i aed by the DN Doain nae erver and the router forward that requet to that articular alication erver Uon getting erviced by erver, the job arrive at queue lication erver or lication erver Thi tranaction totally deend on the I addre of lication erver which ha been aed by the DN Doain nae erver Now, the job arrive at the queue, with robabilitie and, where o, the arrival rate at i, and that at i If the job arrive at with robability with the arrival rate then the arrival rate of will be becaue and are in erial connection The ervice rate of lication erver, and i and that of Databae erver 9, 0, i The ervice rate of lication erver, and are equal becaue they are M/M/ queue, Liewie the ervice rate of Databae erver 9, 0 and are equal becaue they are M/M/ queue a well Finally, job after ervice coletion at erver and arrive at the in databae, the databae erver, which rovide the alication erver with the data it require Here, lication erver act lie a web erver which erve age for viewing in a eb brower with the arrival rate then the arrival rate of will be If the job arrive at with robability becaue and are in erial connection The ervice rate of the lication erver, 7 and 8 i and the ervice rate of Databae erver,, i The ervice rate of lication erver, 7 and 8 are equal becaue they are M/M/ queue, liewie the ervice rate of Databae erver, and are equal becaue they are M/M/ queue a well Here i the nuber of erver Finally, job after ervice coletion at erver and arrive at in databae, the databae erver, which rovide the alication erver with the data it require Here, lication erver act lie a web erver which erve age for viewing in a eb brower erforance eaure for hybrid queuing client erver odel The erforance of the ingle and ultile erver i eaured by the average queue length, average waiting tie, average reone tie and the average no of job in the yte ] The queue in the odel are aued to be M/M/ and M/M/ Hybrid Here client brower and router are M/M/ tye lication erver and and databae erver and are M/M/ tye erforance eaure uch a a average queue length, b average reone tie, c average waiting tie are derived in thi ection verage queue length The average queue length in and client brower are E N ], E N ] iilarly, the average queue length in router i E N ] IN 77-9/VN--0
4 IJECE,Volue,Nuber atarhi Guta et al IN 77-9/VN--0 The average queue length in alication erver and databae erver,,, i EN ], where, robability that an arriving cutoer ha to wait in queue cutoer or ore in the yte i!- 0, and in the M/M/ cae, the robability of n cutoer in the yte i 0!! 0 ccording to Figure the alication erver and conit of ub erver each o here for each and fter ilification the average queue length for alication erver i EN ] here, robability that an arriving cutoer ha to wait in queue i 0, and in the M/M/ cae, the robability of n cutoer in the yte i 0 fter ilification the average queue length for alication erver i EN ] here, 0 and 0 ccording to Figure databae erver and conit of ub erver each o here for each and fter ilification the average queue length for databae erver i EN ] here, 0 and 0 fter ilification the average queue length for databae erver i EN ] here, 0 and 0 verage reone tie The average reone tie in and are ] R E ] E, ] R E ] E
5 erforance analyi of hybrid M/M/ and M/M/ client erver odel uing ueuing theory IN 77-9/VN--0 iilarly, the average reone tie in router i ] R E ] E The average reone tie in alication erver and databae erver,,, be ER], where, robability that an arriving cutoer ha to wait in queue cutoer or ore in the yte i!- 0, and in M/M/ cae robability of n cutoer in the yte i 0!! 0 ccording to Figure alication erver and conit of ub erver each o here for each and fter ilification the average reone tie for alication erver i ER ] 7 here, 0 and 0 fter ilification the average reone tie for alication erver i ER ] 8 here, 0 and 0 ccording to Figure the databae erver and conit of ub erver each o here for each and fter ilification the reone tie for databae erver i ER ] 9 here, 0 and 0 fter ilification the average reone tie for databae erver i ER ] 0 here, 0 and 0 verage waiting tie: The average waiting tie in and client brower are ] E ] N E, ] E ] N E
6 IJECE,Volue,Nuber atarhi Guta et al IN 77-9/VN--0 iilarly, the average waiting tie in router i ] E N E ] The average waiting tie in alication erver and databae erver,,, be E], where, robability that an arriving cutoer ha to wait in queue cutoer or ore in the yte i!- 0 and in M/M/ cae robability of n cutoer in the yte i 0!! 0 ccording to Figure the alication erver and conit of ub erver each o here for each and fter ilification the average waiting tie for alication erver i E ] here, 0 and 0 fter ilification the average waiting tie for alication erver i E ] here, 0 and 0 ccording to Figure the databae erver and conit of ub erver each o here for each and fter ilification the average waiting tie for databae erver i E ] here, 0 and 0 fter ilification the average waiting tie for databae erver i E ] here, 0 and 0 Total nuber of job, reone tie and waiting tie for different ath: For ath,,,, the total nuber of job fro t brower to data bae erver i E Nx] ] N E ] N E EN ] EN ] For ath,,,, the total reone tie fro t brower to data bae erver i
7 7 erforance analyi of hybrid M/M/ and M/M/ client erver odel uing ueuing theory IN 77-9/VN--0 E Rx] ] R E ] R E ER ] E R ] 7 For ath,,,, the total waiting tie fro t brower to data bae erver i E x] ] E ] E E ] E ] 8 For ath,,,, the total nuber of job fro nd brower to data bae erver i E Ny] ] N E ] N E EN ] E N ] 9 For ath,,,, the total reone tie fro nd brower to data bae erver i E Rx] ] R E ] R E ER ] E R ] 0 For ath,,,, the total waiting tie fro nd brower to data bae erver i E x] ] E ] E E ] E ] Nuerical reult for Hybrid queuing client erver odel ueue length v rrival rate for lin to and lin to
8 IJECE,Volue,Nuber atarhi Guta et al 8 Figure ueue length v rrival rate for lin to and lin to Let be the total nuber of arrival in the -inut queuing networ In the exale conidered in thi ection, the arrival rate,,,, 0 The other ecification include robability of arrival at queue and are 0 and 0 The ervice rate ecification of different erver in the networ are 78, 7, 7, 70,, 800, 07 robability of arrival at queue ', ' and ' and ', 7' and 8' are 0 and 0 For each value of, the average queue length in all node of the -inut queuing client erver networ i couted The average queue length in ath to and to are couted fro to The total queue length in ath to and to are couted in and 9 reectively The total queue length of lin to and lin to v different arrival rate are lotted in Figure Fro Figure it i found that a the arrival rate increae, the queue length of the lin to increae ore than the queue length of the lin to Becaue the ervice rate for erver and are ore than the ervice rate of and Reone tie v rrival rate for lin to and lin to IN 77-9/VN--0
9 erforance analyi of hybrid M/M/ and M/M/ client erver odel uing ueuing theory 9 Figure Reone tie v rrival rate for lin to and lin to For each value of, the utilization, average reone tie in all node of the -inut queuing client erver networ i couted The average reone tie in ath to and to are couted fro to 0 The total reone tie in ath to and to are couted in 7 and 0 The total reone tie of lin to and lin to v different arrival rate are lotted in Figure Fro Figure it i found that a the arrival rate increae, the reone tie of the lin to increae ore than the reone tie of the lin to Becaue the ervice rate for erver and are ore than the ervice rate of and, aiting tie v rrival rate for lin to and lin to Figure aiting tie v rrival rate for lin to and lin to IN 77-9/VN--0
10 IJECE,Volue,Nuber atarhi Guta et al 0 For each value of, the utilization, average waiting tie in all node of the -inut queuing client erver networ are couted The average waiting tie in ath to and to are couted fro to The total waiting tie in ath to and to are couted in 8 and The total waiting tie of lin to and lin to v different arrival rate are lotted in Figure Fro Figure it i found that a the arrival rate increae, the waiting tie of the lin to increae ore than the waiting tie of the lin to Becaue the ervice rate for erver and are ore than the ervice rate of and, IIICONCLUION In thi aer, erforance eaure for client erver odel uch a average queue length, average reone tie and average waiting tie are derived for M/M/ and M/M/ Hybrid tye odel and the reult how that reone tie i le Becaue of thi le reone tie robability of acet lo reduce and yte becoe fater The ervice rate of the equivalent erver i alo derived and couted nuerically ueue length v rrival rate, Reone tie v rrival rate, waiting tie v rrival rate are lotted uing MTLB 70 oftware Deciion for routing i ade at the lat node in each tage of the networ a to which ath to chooe for obtaining the leat reone tie IV REFERENCE ] htt://enioeanet/content/c/ctierh#qecurityinclient%ferverodel&cur&url%f ] Diitri Bertea, Robert Gallager, Data Networ, econd Edition, rentice Hall of India rivate Liited, 997 ] ingh, and rivatava, Meory Etiation of Internet erver Uing ueuing Theory: Coarative tudy between M/G/, G/M/ & G/G/ ueuing Model, orld cadey of cience, Engineering and Technology, ] Vidhyacharan Bhaar & atric Lalleent, ctivity routing in a ditributed uly chain: erforance evaluation with two inut Journal of Networ and Couter lication, cience Direct, IN 77-9/VN--0
PERFORMANCE EVALUATION ISSUES OF QUERY PROCESSING THROUGH CLIENT SERVER ARCHITECTURE
 Manih Srivatava et al./ International Journal of Comuter Science & Engineering Technology (IJCSET) PERFORMANCE EVALUATION ISSUES OF QUERY PROCESSING THROUGH CLIENT SERVER ARCHITECTURE Mr. Manih Srivatava
Manih Srivatava et al./ International Journal of Comuter Science & Engineering Technology (IJCSET) PERFORMANCE EVALUATION ISSUES OF QUERY PROCESSING THROUGH CLIENT SERVER ARCHITECTURE Mr. Manih Srivatava
On-Chip Interconnect Implications of Shared Memory Multicores
 On-Chi Interconnect Ilications of Shared Meory Multicores Srini Devadas Couter Science and Artificial Intelligence Laboratory (CSAIL) Massachusetts Institute of Technology 1 Prograing 1000 cores MPI has
On-Chi Interconnect Ilications of Shared Meory Multicores Srini Devadas Couter Science and Artificial Intelligence Laboratory (CSAIL) Massachusetts Institute of Technology 1 Prograing 1000 cores MPI has
Path Planning for Mine Countermeasures
 ath lanning for Mine Countereaure Cherl Rech *a Chritine iatko a Fernando J. ineda b Jeica itole a I-Jeng Wang a a John Hokin Univerit Alied hic Laborator Laurel Marland 073-6099 b John Hokin Blooberg
ath lanning for Mine Countereaure Cherl Rech *a Chritine iatko a Fernando J. ineda b Jeica itole a I-Jeng Wang a a John Hokin Univerit Alied hic Laborator Laurel Marland 073-6099 b John Hokin Blooberg
PERFORMANCE MEASUREMENT OF OEE USING DATA ENVELOPMENT ANALYSIS (DEA) Muhamad Arifpin Mansor 1 and Ario Ohsato 2
 National Conference in Mechanical Engineering Reearch and Potgraduate Student (1 t NCMER 2010) 26-27 MAY 2010, FKM Conference Hall, UMP, Kuantan, Pahang, Malayia; pp. 65-71 ISBN: 978-967-5080-9501 (CD
National Conference in Mechanical Engineering Reearch and Potgraduate Student (1 t NCMER 2010) 26-27 MAY 2010, FKM Conference Hall, UMP, Kuantan, Pahang, Malayia; pp. 65-71 ISBN: 978-967-5080-9501 (CD
Problem Set 2 (Due: Friday, October 19, 2018)
 Electrical and Computer Engineering Memorial Univerity of Newfoundland ENGI 9876 - Advanced Data Network Fall 2018 Problem Set 2 (Due: Friday, October 19, 2018) Quetion 1 Conider an M/M/1 model of a queue
Electrical and Computer Engineering Memorial Univerity of Newfoundland ENGI 9876 - Advanced Data Network Fall 2018 Problem Set 2 (Due: Friday, October 19, 2018) Quetion 1 Conider an M/M/1 model of a queue
Soft Output Decoding Algorithm for Turbo Codes Implementation in Mobile Wi-Max Environment.
 Available online at www.ciencedirect.com Procedia Technology 6 (202 ) 666 673 2nd International Conference on Communication, Comuting & Security [ICCCS-202] Soft Outut Decoding Algorithm for Turbo Code
Available online at www.ciencedirect.com Procedia Technology 6 (202 ) 666 673 2nd International Conference on Communication, Comuting & Security [ICCCS-202] Soft Outut Decoding Algorithm for Turbo Code
Distributed Packet Processing Architecture with Reconfigurable Hardware Accelerators for 100Gbps Forwarding Performance on Virtualized Edge Router
 Ditributed Packet Proceing Architecture with Reconfigurable Hardware Accelerator for 100Gbp Forwarding Performance on Virtualized Edge Router Satohi Nihiyama, Hitohi Kaneko, and Ichiro Kudo Abtract To
Ditributed Packet Proceing Architecture with Reconfigurable Hardware Accelerator for 100Gbp Forwarding Performance on Virtualized Edge Router Satohi Nihiyama, Hitohi Kaneko, and Ichiro Kudo Abtract To
PERFORMANCE MEASURES FOR INTERNET SERVER BY USING M/M/m QUEUEING MODEL
 IJRET: International Journal of Research in Engineering and Technology ISSN: 239-63 PERFORMANCE MEASURES FOR INTERNET SERVER BY USING M/M/ QUEUEING MODEL Raghunath Y. T. N. V, A. S. Sravani 2 Assistant
IJRET: International Journal of Research in Engineering and Technology ISSN: 239-63 PERFORMANCE MEASURES FOR INTERNET SERVER BY USING M/M/ QUEUEING MODEL Raghunath Y. T. N. V, A. S. Sravani 2 Assistant
Analysis of the results of analytical and simulation With the network model and dynamic priority Unchecked Buffer
 International Reearch Journal of Applied and Baic Science 218 Available online at www.irjab.com ISSN 2251-838X / Vol, 12 (1): 49-53 Science Explorer Publication Analyi of the reult of analytical and imulation
International Reearch Journal of Applied and Baic Science 218 Available online at www.irjab.com ISSN 2251-838X / Vol, 12 (1): 49-53 Science Explorer Publication Analyi of the reult of analytical and imulation
Transactions on the Multiversion B + -Tree
 Tranaction on the Multiverion B + -Tree Tuukka Haaaalo Helinki Univerity of Technology Eoo, Finland thaaaa@c.hut.fi Seo Siu Univerity of Helinki Helinki, Finland iu@c.helinki.fi Ibrahim Jaluta Helinki
Tranaction on the Multiverion B + -Tree Tuukka Haaaalo Helinki Univerity of Technology Eoo, Finland thaaaa@c.hut.fi Seo Siu Univerity of Helinki Helinki, Finland iu@c.helinki.fi Ibrahim Jaluta Helinki
Cisco VM-FEX Best Practices for VMware ESX Environment
 Deployent Guide Cico VM-FEX Bet Practice for VMware ESX Environent Deployent Guide Deceber 211 Content 1 Executive Suary... 3 1.1 Target Audience... 3 1.2 Introduction... 3 2 Cico CS VM-FEX Bet Practice...
Deployent Guide Cico VM-FEX Bet Practice for VMware ESX Environent Deployent Guide Deceber 211 Content 1 Executive Suary... 3 1.1 Target Audience... 3 1.2 Introduction... 3 2 Cico CS VM-FEX Bet Practice...
Keywords Cloud Computing, Service Level Agreements (SLA), CloudSim, Monitoring & Controlling SLA Agent, JADE
 Volume 5, Iue 8, Augut 2015 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Verification of Agent
Volume 5, Iue 8, Augut 2015 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Verification of Agent
Efficient Large-scale Content Distribution with Combination of CDN and P2P Networks
 Vol.2, No.2, Aril, 2009 Efficient Large-cale Content Ditribution with Combination of CDN and P2P Network Hai Jiang 1, 2, Jun Li 1, Zhongcheng Li 1, and Xiangyu Bai 1, 2 1 Intitute of Comuting Technology,
Vol.2, No.2, Aril, 2009 Efficient Large-cale Content Ditribution with Combination of CDN and P2P Network Hai Jiang 1, 2, Jun Li 1, Zhongcheng Li 1, and Xiangyu Bai 1, 2 1 Intitute of Comuting Technology,
ECE-320 Lab 2: Root Locus For Controller Design
 ECE-320 Lab 2: Root Locu For Controller Deign In thi Lab you will exlore the ue of the root locu technique in deigning controller. The root locu indicate the oible location of the cloed loo ole of a ytem
ECE-320 Lab 2: Root Locu For Controller Deign In thi Lab you will exlore the ue of the root locu technique in deigning controller. The root locu indicate the oible location of the cloed loo ole of a ytem
SLA Adaptation for Service Overlay Networks
 SLA Adaptation for Service Overlay Network Con Tran 1, Zbigniew Dziong 1, and Michal Pióro 2 1 Department of Electrical Engineering, École de Technologie Supérieure, Univerity of Quebec, Montréal, Canada
SLA Adaptation for Service Overlay Network Con Tran 1, Zbigniew Dziong 1, and Michal Pióro 2 1 Department of Electrical Engineering, École de Technologie Supérieure, Univerity of Quebec, Montréal, Canada
A Basic Prototype for Enterprise Level Project Management
 A Baic Prototype for Enterprie Level Project Management Saurabh Malgaonkar, Abhay Kolhe Computer Engineering Department, Mukeh Patel School of Technology Management & Engineering, NMIMS Univerity, Mumbai,
A Baic Prototype for Enterprie Level Project Management Saurabh Malgaonkar, Abhay Kolhe Computer Engineering Department, Mukeh Patel School of Technology Management & Engineering, NMIMS Univerity, Mumbai,
Hong Yao, Han Zhang, Changkai Zhang and Deze Zeng. Jie Wu* and Huanyang Zheng
 330 Int. J. Coputational Science and Engineering, Vol. 4, No. 4, 207 Data or index: a trade-off in obile delay tolerant network Hong Yao, Han Zhang, Changkai Zhang and Deze Zeng Hubei Key Laboratory of
330 Int. J. Coputational Science and Engineering, Vol. 4, No. 4, 207 Data or index: a trade-off in obile delay tolerant network Hong Yao, Han Zhang, Changkai Zhang and Deze Zeng Hubei Key Laboratory of
Analysis of slope stability
 Engineering manual No. 8 Updated: 02/2016 Analyi of lope tability Program: Slope tability File: Demo_manual_08.gt In thi engineering manual, we are going to how you how to verify the lope tability for
Engineering manual No. 8 Updated: 02/2016 Analyi of lope tability Program: Slope tability File: Demo_manual_08.gt In thi engineering manual, we are going to how you how to verify the lope tability for
Position Control of Manipulator s Links Using Artificial Neural Network with Backpropagation Training Algorithm
 Poition Control of Manipulator Link Uing Artificial Neural Network with Backpropagation Training Algorith Thiang, Handry Khowanto, Tan Hendra Sutanto Electrical Engineering Departent, Petra Chritian Univerity
Poition Control of Manipulator Link Uing Artificial Neural Network with Backpropagation Training Algorith Thiang, Handry Khowanto, Tan Hendra Sutanto Electrical Engineering Departent, Petra Chritian Univerity
DAROS: Distributed User-Server Assignment And Replication For Online Social Networking Applications
 DAROS: Ditributed Uer-Server Aignment And Replication For Online Social Networking Application Thuan Duong-Ba School of EECS Oregon State Univerity Corvalli, OR 97330, USA Email: duongba@eec.oregontate.edu
DAROS: Ditributed Uer-Server Aignment And Replication For Online Social Networking Application Thuan Duong-Ba School of EECS Oregon State Univerity Corvalli, OR 97330, USA Email: duongba@eec.oregontate.edu
Embedding Service Function Tree with Minimum Cost for NFV Enabled Multicast
 1 Embedding Service Function Tree with Minimum ot for NFV Enabled Multicat angbang Ren, Student Member, IEEE, eke Guo, Senior Member, IEEE, Yulong Shen, Member, IEEE, Guoming Tang, Member, IEEE, Xu Lin,
1 Embedding Service Function Tree with Minimum ot for NFV Enabled Multicat angbang Ren, Student Member, IEEE, eke Guo, Senior Member, IEEE, Yulong Shen, Member, IEEE, Guoming Tang, Member, IEEE, Xu Lin,
Modeling of communication complexity in parallel computing
 American Journal of Netork and Communication 2014; 3(5-1): 29-42 Publihed online July 30, 2014 (htt://.cienceublihinggrou.com/j/ajnc) doi: 10.11648/j.ajnc..2014030501.13 ISSN: 2326-893X (Print); ISSN:
American Journal of Netork and Communication 2014; 3(5-1): 29-42 Publihed online July 30, 2014 (htt://.cienceublihinggrou.com/j/ajnc) doi: 10.11648/j.ajnc..2014030501.13 ISSN: 2326-893X (Print); ISSN:
LinkGuide: Towards a Better Collection of Hyperlinks in a Website Homepage
 Proceeding of the World Congre on Engineering 2007 Vol I LinkGuide: Toward a Better Collection of Hyperlink in a Webite Homepage A. Ammari and V. Zharkova chool of Informatic, Univerity of Bradford anammari@bradford.ac.uk,
Proceeding of the World Congre on Engineering 2007 Vol I LinkGuide: Toward a Better Collection of Hyperlink in a Webite Homepage A. Ammari and V. Zharkova chool of Informatic, Univerity of Bradford anammari@bradford.ac.uk,
Laboratory Exercise 6
 Laboratory Exercie 6 Adder, Subtractor, and Multiplier The purpoe of thi exercie i to examine arithmetic circuit that add, ubtract, and multiply number. Each type of circuit will be implemented in two
Laboratory Exercie 6 Adder, Subtractor, and Multiplier The purpoe of thi exercie i to examine arithmetic circuit that add, ubtract, and multiply number. Each type of circuit will be implemented in two
Lecture 14: Minimum Spanning Tree I
 COMPSCI 0: Deign and Analyi of Algorithm October 4, 07 Lecture 4: Minimum Spanning Tree I Lecturer: Rong Ge Scribe: Fred Zhang Overview Thi lecture we finih our dicuion of the hortet path problem and introduce
COMPSCI 0: Deign and Analyi of Algorithm October 4, 07 Lecture 4: Minimum Spanning Tree I Lecturer: Rong Ge Scribe: Fred Zhang Overview Thi lecture we finih our dicuion of the hortet path problem and introduce
Performance Evaluation of Content Distribution in Hybrid CDN-P2P Network
 2008 Second International Conference on Future Generation Communication and Networking Performance Evaluation of Content Ditribution in Hybrid CDN-P2P Network Hai Jiang 1, 2, Jun Li 1, Zhongcheng Li 1,
2008 Second International Conference on Future Generation Communication and Networking Performance Evaluation of Content Ditribution in Hybrid CDN-P2P Network Hai Jiang 1, 2, Jun Li 1, Zhongcheng Li 1,
Topics. Lecture 37: Global Optimization. Issues. A Simple Example: Copy Propagation X := 3 B > 0 Y := 0 X := 4 Y := Z + W A := 2 * 3X
 Lecture 37: Global Optimization [Adapted from note by R. Bodik and G. Necula] Topic Global optimization refer to program optimization that encompa multiple baic block in a function. (I have ued the term
Lecture 37: Global Optimization [Adapted from note by R. Bodik and G. Necula] Topic Global optimization refer to program optimization that encompa multiple baic block in a function. (I have ued the term
EXTENDED SVD FLATNESS CONTROL. Per Erik Modén and Markus Holm ABB AB, Västerås, Sweden
 EXTENDED SVD FLATNESS CONTROL Per Erik Modén and Markus Hol ABB AB, Västerås, Sweden ABSTRACT Cold rolling ills soeties do not see able to control flatness as well as exected, taking into account the nuber
EXTENDED SVD FLATNESS CONTROL Per Erik Modén and Markus Hol ABB AB, Västerås, Sweden ABSTRACT Cold rolling ills soeties do not see able to control flatness as well as exected, taking into account the nuber
Homework 4 Due Thursday Oct 7. CLRS 12-4 (number of binary trees) CLRS (rb insert implementation)
 Homework 4 Due Thurday Oct 7 CLRS 12-4 (number of binary tree) CLRS 13.3-6 (rb inert imlementation) 1 Chater 13: Red-Black Tree A red-black tree i a node-colored BST. Each node i colored either black or
Homework 4 Due Thurday Oct 7 CLRS 12-4 (number of binary tree) CLRS 13.3-6 (rb inert imlementation) 1 Chater 13: Red-Black Tree A red-black tree i a node-colored BST. Each node i colored either black or
See chapter 8 in the textbook. Dr Muhammad Al Salamah, Industrial Engineering, KFUPM
 Goal programming Objective of the topic: Indentify indutrial baed ituation where two or more objective function are required. Write a multi objective function model dla a goal LP Ue weighting um and preemptive
Goal programming Objective of the topic: Indentify indutrial baed ituation where two or more objective function are required. Write a multi objective function model dla a goal LP Ue weighting um and preemptive
Performance Evaluation of TCP Implementations in OBS Networks
 Performance Evaluation of TCP Imlementation in OB Network iang Yu y, Chunming Qiao y, Yong Liu Λ and Don Towley Λ y Deartment of Comuter cience and Engineering, tate Univerity of New York at Buffalo Λ
Performance Evaluation of TCP Imlementation in OB Network iang Yu y, Chunming Qiao y, Yong Liu Λ and Don Towley Λ y Deartment of Comuter cience and Engineering, tate Univerity of New York at Buffalo Λ
Minimum congestion spanning trees in bipartite and random graphs
 Minimum congetion panning tree in bipartite and random graph M.I. Otrovkii Department of Mathematic and Computer Science St. John Univerity 8000 Utopia Parkway Queen, NY 11439, USA e-mail: otrovm@tjohn.edu
Minimum congetion panning tree in bipartite and random graph M.I. Otrovkii Department of Mathematic and Computer Science St. John Univerity 8000 Utopia Parkway Queen, NY 11439, USA e-mail: otrovm@tjohn.edu
Chapter 13 Non Sampling Errors
 Chapter 13 Non Sampling Error It i a general aumption in the ampling theory that the true value of each unit in the population can be obtained and tabulated without any error. In practice, thi aumption
Chapter 13 Non Sampling Error It i a general aumption in the ampling theory that the true value of each unit in the population can be obtained and tabulated without any error. In practice, thi aumption
A Study on Turbo Code Performance Based on AWGN Channel
 Proceeding of the 2nd International Conference on Comuter Science and Electronic Engineering (ICCSEE 2013 A Study on Turbo Code Performance Baed on AWGN Channel Peng Zhu, Jun Zhu, iang Liu Key Laboratory
Proceeding of the 2nd International Conference on Comuter Science and Electronic Engineering (ICCSEE 2013 A Study on Turbo Code Performance Baed on AWGN Channel Peng Zhu, Jun Zhu, iang Liu Key Laboratory
Karen L. Collins. Wesleyan University. Middletown, CT and. Mark Hovey MIT. Cambridge, MA Abstract
 Mot Graph are Edge-Cordial Karen L. Collin Dept. of Mathematic Weleyan Univerity Middletown, CT 6457 and Mark Hovey Dept. of Mathematic MIT Cambridge, MA 239 Abtract We extend the definition of edge-cordial
Mot Graph are Edge-Cordial Karen L. Collin Dept. of Mathematic Weleyan Univerity Middletown, CT 6457 and Mark Hovey Dept. of Mathematic MIT Cambridge, MA 239 Abtract We extend the definition of edge-cordial
Shortest Paths Problem. CS 362, Lecture 20. Today s Outline. Negative Weights
 Shortet Path Problem CS 6, Lecture Jared Saia Univerity of New Mexico Another intereting problem for graph i that of finding hortet path Aume we are given a weighted directed graph G = (V, E) with two
Shortet Path Problem CS 6, Lecture Jared Saia Univerity of New Mexico Another intereting problem for graph i that of finding hortet path Aume we are given a weighted directed graph G = (V, E) with two
I n many cases, the SPRT will come to a decision with fewer samples than would have been required for a fixed size test.
 STATGRAPHICS Rev. 9/6/3 Sequential Saling Suary... Data Inut... 3 Analysis Otions... 3 Analysis Suary... 5 Cuulative Plot... 6 Decision Nubers... 9 Test Perforance... O. C. Curve... ASN Function... Forulas...
STATGRAPHICS Rev. 9/6/3 Sequential Saling Suary... Data Inut... 3 Analysis Otions... 3 Analysis Suary... 5 Cuulative Plot... 6 Decision Nubers... 9 Test Perforance... O. C. Curve... ASN Function... Forulas...
Today s Outline. CS 561, Lecture 23. Negative Weights. Shortest Paths Problem. The presence of a negative cycle might mean that there is
 Today Outline CS 56, Lecture Jared Saia Univerity of New Mexico The path that can be trodden i not the enduring and unchanging Path. The name that can be named i not the enduring and unchanging Name. -
Today Outline CS 56, Lecture Jared Saia Univerity of New Mexico The path that can be trodden i not the enduring and unchanging Path. The name that can be named i not the enduring and unchanging Name. -
(12) Patent Application Publication (10) Pub. No.: US 2003/ A1
 US 2003O196031A1 (19) United State (12) Patent Application Publication (10) Pub. No.: US 2003/0196031 A1 Chen (43) Pub. Date: Oct. 16, 2003 (54) STORAGE CONTROLLER WITH THE DISK Related U.S. Application
US 2003O196031A1 (19) United State (12) Patent Application Publication (10) Pub. No.: US 2003/0196031 A1 Chen (43) Pub. Date: Oct. 16, 2003 (54) STORAGE CONTROLLER WITH THE DISK Related U.S. Application
A Model-Based Approach to Integrating Security Policies for Embedded Devices
 A Model-Baed Aroach to Integrating Security Policie for Embedded Device Michael McDougall mmcdouga@ci.uenn.edu Rajeev Alur alur@ci.uenn.edu Deartment of Comuter and Information Science Univerity of Pennylvania
A Model-Baed Aroach to Integrating Security Policie for Embedded Device Michael McDougall mmcdouga@ci.uenn.edu Rajeev Alur alur@ci.uenn.edu Deartment of Comuter and Information Science Univerity of Pennylvania
A Service with Bounded Degradation in Quality-of-Service. Networks. University of Virginia. Charlottesville, VA 22903
 To Aear: Proc. IEEE Infocom'95, Boton, Aril 1995. A Service with Bounded Degradation in Quality-of-Service Network Jorg Liebeherr Dongwei Liao Deartment of Comuter Science Univerity of Virginia Charlotteville,
To Aear: Proc. IEEE Infocom'95, Boton, Aril 1995. A Service with Bounded Degradation in Quality-of-Service Network Jorg Liebeherr Dongwei Liao Deartment of Comuter Science Univerity of Virginia Charlotteville,
Lecture Outline. Global flow analysis. Global Optimization. Global constant propagation. Liveness analysis. Local Optimization. Global Optimization
 Lecture Outline Global flow analyi Global Optimization Global contant propagation Livene analyi Adapted from Lecture by Prof. Alex Aiken and George Necula (UCB) CS781(Praad) L27OP 1 CS781(Praad) L27OP
Lecture Outline Global flow analyi Global Optimization Global contant propagation Livene analyi Adapted from Lecture by Prof. Alex Aiken and George Necula (UCB) CS781(Praad) L27OP 1 CS781(Praad) L27OP
Contents. shortest paths. Notation. Shortest path problem. Applications. Algorithms and Networks 2010/2011. In the entire course:
 Content Shortet path Algorithm and Network 21/211 The hortet path problem: Statement Verion Application Algorithm (for ingle ource p problem) Reminder: relaxation, Dijktra, Variant of Dijktra, Bellman-Ford,
Content Shortet path Algorithm and Network 21/211 The hortet path problem: Statement Verion Application Algorithm (for ingle ource p problem) Reminder: relaxation, Dijktra, Variant of Dijktra, Bellman-Ford,
How to protect from port scanning and smurf attack in Linux Server by iptables
 In thi pot I will hare the iptable cript in which we will learn How to protect from port canning and murf attack in Linux Server Feature Of Script : (1) When a attacker try to port can your erver, firt
In thi pot I will hare the iptable cript in which we will learn How to protect from port canning and murf attack in Linux Server Feature Of Script : (1) When a attacker try to port can your erver, firt
CHAPTER 4: INTERPROCESS COMMUNICATION AND COORDINATION
 CHAPTER : INTERPROCESS COMMUNICATION AND COORDINATION Chapter outline Dicu three level of communication: baic meage paing, requet/reply and tranaction communication baed on meage paing Dicu name ervice
CHAPTER : INTERPROCESS COMMUNICATION AND COORDINATION Chapter outline Dicu three level of communication: baic meage paing, requet/reply and tranaction communication baed on meage paing Dicu name ervice
An NoC Traffic Compiler for efficient FPGA implementation of Parallel Graph Applications
 An NoC Traffic Copiler for efficient FPGA ipleentation of Parallel Graph Application Nachiket Kapre California Intitute of Technology, Paadena, CA 9115 nachiket@caltech.edu André DeHon Univerity of Pennylvania
An NoC Traffic Copiler for efficient FPGA ipleentation of Parallel Graph Application Nachiket Kapre California Intitute of Technology, Paadena, CA 9115 nachiket@caltech.edu André DeHon Univerity of Pennylvania
A SIMPLE IMPERATIVE LANGUAGE THE STORE FUNCTION NON-TERMINATING COMMANDS
 A SIMPLE IMPERATIVE LANGUAGE Eventually we will preent the emantic of a full-blown language, with declaration, type and looping. However, there are many complication, o we will build up lowly. Our firt
A SIMPLE IMPERATIVE LANGUAGE Eventually we will preent the emantic of a full-blown language, with declaration, type and looping. However, there are many complication, o we will build up lowly. Our firt
Routing Definition 4.1
 4 Routing So far, we have only looked at network without dealing with the iue of how to end information in them from one node to another The problem of ending information in a network i known a routing
4 Routing So far, we have only looked at network without dealing with the iue of how to end information in them from one node to another The problem of ending information in a network i known a routing
Recap Consistent cuts. CS514: Intermediate Course in Operating Systems. What time is it? But what does time mean? Drawing time-line pictures:
 CS514: Interediate Course in Oerating Systes Professor Ken iran Vivek Vishnuurthy: T Reca Consistent cuts On Monday we saw that sily gathering the state of a syste isn t enough Often the state includes
CS514: Interediate Course in Oerating Systes Professor Ken iran Vivek Vishnuurthy: T Reca Consistent cuts On Monday we saw that sily gathering the state of a syste isn t enough Often the state includes
Anisotropy Estimation and Image Remapping Using Model Based Moveout
 Aniotropy Etiation and Iae Reappin Uin Model Baed Moveout Z. Liu* (PGS), N.D. Whitore (PGS) & C. Zhou (PGS) SUMMARY Typically odel paraeter etiation i achieved throuh ultiple iteration of linearized tooraphy
Aniotropy Etiation and Iae Reappin Uin Model Baed Moveout Z. Liu* (PGS), N.D. Whitore (PGS) & C. Zhou (PGS) SUMMARY Typically odel paraeter etiation i achieved throuh ultiple iteration of linearized tooraphy
ETSI TS V ( )
 TS 122 153 V14.4.0 (2017-05) TECHNICAL SPECIFICATION Digital cellular telecommunication ytem (Phae 2+) (GSM); Univeral Mobile Telecommunication Sytem (UMTS); LTE; Multimedia priority ervice (3GPP TS 22.153
TS 122 153 V14.4.0 (2017-05) TECHNICAL SPECIFICATION Digital cellular telecommunication ytem (Phae 2+) (GSM); Univeral Mobile Telecommunication Sytem (UMTS); LTE; Multimedia priority ervice (3GPP TS 22.153
Multi-Target Tracking In Clutter
 Multi-Target Tracking In Clutter John N. Sander-Reed, Mary Jo Duncan, W.B. Boucher, W. Michael Dimmler, Shawn O Keefe ABSTRACT A high frame rate (0 Hz), multi-target, video tracker ha been developed and
Multi-Target Tracking In Clutter John N. Sander-Reed, Mary Jo Duncan, W.B. Boucher, W. Michael Dimmler, Shawn O Keefe ABSTRACT A high frame rate (0 Hz), multi-target, video tracker ha been developed and
A MODULAR COMPOSABLE SOFTWARE ARCHITECTURE FOR THE SIMULATION OF MECHATRONIC SYSTEMS
 Proceeding of DETC 98 1998 ASME 18th Coputer in Engineering Conference Septeber 13-16, 1998, Atlanta, Georgia, USA DETC98/CIE-5704 A MODULAR COMPOSABLE SOFTWARE ARCHITECTURE FOR THE SIMULATION OF MECHATRONIC
Proceeding of DETC 98 1998 ASME 18th Coputer in Engineering Conference Septeber 13-16, 1998, Atlanta, Georgia, USA DETC98/CIE-5704 A MODULAR COMPOSABLE SOFTWARE ARCHITECTURE FOR THE SIMULATION OF MECHATRONIC
Performance Evaluation of search engines via user efforts measures
 IJCSI International Journal of Computer Science Iue, Vol. 9, Iue 4, No, July 01 www.ijcsi.org 437 Performance Evaluation of earch engine via uer effort meaure Raeh Kumar Goutam 1 and Sanay K. Dwivedi 1
IJCSI International Journal of Computer Science Iue, Vol. 9, Iue 4, No, July 01 www.ijcsi.org 437 Performance Evaluation of earch engine via uer effort meaure Raeh Kumar Goutam 1 and Sanay K. Dwivedi 1
Aspects of Formal and Graphical Design of a Bus System
 Apect of Formal and Graphical Deign of a Bu Sytem Tiberiu Seceleanu Univerity of Turku, Dpt. of Information Technology Turku, Finland tiberiu.eceleanu@utu.fi Tomi Weterlund Turku Centre for Computer Science
Apect of Formal and Graphical Deign of a Bu Sytem Tiberiu Seceleanu Univerity of Turku, Dpt. of Information Technology Turku, Finland tiberiu.eceleanu@utu.fi Tomi Weterlund Turku Centre for Computer Science
1 The secretary problem
 Thi i new material: if you ee error, pleae email jtyu at tanford dot edu 1 The ecretary problem We will tart by analyzing the expected runtime of an algorithm, a you will be expected to do on your homework.
Thi i new material: if you ee error, pleae email jtyu at tanford dot edu 1 The ecretary problem We will tart by analyzing the expected runtime of an algorithm, a you will be expected to do on your homework.
The Association of System Performance Professionals
 The Aociation of Sytem Performance Profeional The Computer Meaurement Group, commonly called CMG, i a not for profit, worldwide organization of data proceing profeional committed to the meaurement and
The Aociation of Sytem Performance Profeional The Computer Meaurement Group, commonly called CMG, i a not for profit, worldwide organization of data proceing profeional committed to the meaurement and
Drawing Lines in 2 Dimensions
 Drawing Line in 2 Dimenion Drawing a traight line (or an arc) between two end point when one i limited to dicrete pixel require a bit of thought. Conider the following line uperimpoed on a 2 dimenional
Drawing Line in 2 Dimenion Drawing a traight line (or an arc) between two end point when one i limited to dicrete pixel require a bit of thought. Conider the following line uperimpoed on a 2 dimenional
Optimizing Synchronous Systems for Multi-Dimensional. Notre Dame, IN Ames, Iowa computation is an optimization problem (b) circuit
 Optimizing Synchronou Sytem for ulti-imenional pplication Nelon L. Pao and Edwin H.-. Sha Liang-Fang hao ept. of omputer Science & Eng. ept. of Electrical & omputer Eng. Univerity of Notre ame Iowa State
Optimizing Synchronou Sytem for ulti-imenional pplication Nelon L. Pao and Edwin H.-. Sha Liang-Fang hao ept. of omputer Science & Eng. ept. of Electrical & omputer Eng. Univerity of Notre ame Iowa State
Distributed Partial Information Management (DPIM) Schemes for Survivable Networks - Part II
 IEEE INFOCO 2002 1 Ditributed Partial Information anagement (DPI) Scheme for Survivable Network - Part II Dahai Xu Chunming Qiao Department of Computer Science and Engineering State Univerity of New York
IEEE INFOCO 2002 1 Ditributed Partial Information anagement (DPI) Scheme for Survivable Network - Part II Dahai Xu Chunming Qiao Department of Computer Science and Engineering State Univerity of New York
Analyzing Hydra Historical Statistics Part 2
 Analyzing Hydra Hitorical Statitic Part Fabio Maimo Ottaviani EPV Technologie White paper 5 hnode HSM Hitorical Record The hnode i the hierarchical data torage management node and ha to perform all the
Analyzing Hydra Hitorical Statitic Part Fabio Maimo Ottaviani EPV Technologie White paper 5 hnode HSM Hitorical Record The hnode i the hierarchical data torage management node and ha to perform all the
A Fail-Aware Datagram Service
 A Fail-Aware Datagra Service Christof Fetzer and Flaviu Cristian christof@research.att.co, htt://www.christof.org Abstract In distributed real-tie systes it is often useful for a rocess to know that another
A Fail-Aware Datagra Service Christof Fetzer and Flaviu Cristian christof@research.att.co, htt://www.christof.org Abstract In distributed real-tie systes it is often useful for a rocess to know that another
Generic Traverse. CS 362, Lecture 19. DFS and BFS. Today s Outline
 Generic Travere CS 62, Lecture 9 Jared Saia Univerity of New Mexico Travere(){ put (nil,) in bag; while (the bag i not empty){ take ome edge (p,v) from the bag if (v i unmarked) mark v; parent(v) = p;
Generic Travere CS 62, Lecture 9 Jared Saia Univerity of New Mexico Travere(){ put (nil,) in bag; while (the bag i not empty){ take ome edge (p,v) from the bag if (v i unmarked) mark v; parent(v) = p;
Through the Diversity of Bandwidth-Related Metrics, Estimation Techniques and Tools: An Overview
 I. J. Computer Network and Information Security, 08, 8, -6 Publihed Oine Augut 08 in MECS (http://www.mec-pre.org/) DOI: 0.585/icni.08.08.0 Through the Diverity of Bandwidth-Related Metric, Etimation Technique
I. J. Computer Network and Information Security, 08, 8, -6 Publihed Oine Augut 08 in MECS (http://www.mec-pre.org/) DOI: 0.585/icni.08.08.0 Through the Diverity of Bandwidth-Related Metric, Etimation Technique
Policy-based Injection of Private Traffic into a Public SDN Testbed
 Intitut für Techniche Informatik und Kommunikationnetze Adrian Friedli Policy-baed Injection of Private Traffic into a Public SDN Tetbed Mater Thei MA-2013-12 Advior: Dr. Bernhard Ager, Vaileio Kotroni
Intitut für Techniche Informatik und Kommunikationnetze Adrian Friedli Policy-baed Injection of Private Traffic into a Public SDN Tetbed Mater Thei MA-2013-12 Advior: Dr. Bernhard Ager, Vaileio Kotroni
The norm Package. November 15, Title Analysis of multivariate normal datasets with missing values
 The norm Package November 15, 2003 Verion 1.0-9 Date 2002/05/06 Title Analyi of multivariate normal dataet with miing value Author Ported to R by Alvaro A. Novo . Original by Joeph
The norm Package November 15, 2003 Verion 1.0-9 Date 2002/05/06 Title Analyi of multivariate normal dataet with miing value Author Ported to R by Alvaro A. Novo . Original by Joeph
Modelling the impact of cyber attacks on the traffic control centre of an urban automobile transport system by means of enhanced cybersecurity
 Modelling the impact of cyber attack on the traffic control centre of an urban automobile tranport ytem by mean of enhanced cyberecurity Yoana Ivanova 1,* 1 Bulgarian Academy of Science, Intitute of ICT,
Modelling the impact of cyber attack on the traffic control centre of an urban automobile tranport ytem by mean of enhanced cyberecurity Yoana Ivanova 1,* 1 Bulgarian Academy of Science, Intitute of ICT,
Frequency Table Computation on Dataflow Architecture
 Frequency Table Computation on Dataflow Architecture P. Škoda *, V. Sruk **, and B. Medved Rogina * * Ruđer Bošković Intitute, Zagreb, Croatia ** Faculty of Electrical Engineering and Computing, Univerity
Frequency Table Computation on Dataflow Architecture P. Škoda *, V. Sruk **, and B. Medved Rogina * * Ruđer Bošković Intitute, Zagreb, Croatia ** Faculty of Electrical Engineering and Computing, Univerity
Laboratory Exercise 1
 Laboratory Eercie Switche, Light, and Multipleer The purpoe of thi eercie i to learn how to connect iple input and output device to an FPGA chip and ipleent a circuit that ue thee device. We will ue the
Laboratory Eercie Switche, Light, and Multipleer The purpoe of thi eercie i to learn how to connect iple input and output device to an FPGA chip and ipleent a circuit that ue thee device. We will ue the
(12) Patent Application Publication (10) Pub. No.: US 2011/ A1
 (19) United State US 2011 0316690A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0316690 A1 Siegman (43) Pub. Date: Dec. 29, 2011 (54) SYSTEMAND METHOD FOR IDENTIFYING ELECTRICAL EQUIPMENT
(19) United State US 2011 0316690A1 (12) Patent Application Publication (10) Pub. No.: US 2011/0316690 A1 Siegman (43) Pub. Date: Dec. 29, 2011 (54) SYSTEMAND METHOD FOR IDENTIFYING ELECTRICAL EQUIPMENT
Using the Spanning Tree of a Criminal Network for Identifying its Leaders
 Uing the Spanning Tree of a Criinal etwork for Identifying it Leader Kaal Taha, Senior Meber, IEEE and Paul D. Yoo, Senior Meber, IEEE Abtract We introduce a forenic analyi yte called that identifie the
Uing the Spanning Tree of a Criinal etwork for Identifying it Leader Kaal Taha, Senior Meber, IEEE and Paul D. Yoo, Senior Meber, IEEE Abtract We introduce a forenic analyi yte called that identifie the
Hassan Ghaziri AUB, OSB Beirut, Lebanon Key words Competitive self-organizing maps, Meta-heuristics, Vehicle routing problem,
 COMPETITIVE PROBABIISTIC SEF-ORGANIZING MAPS FOR ROUTING PROBEMS Haan Ghaziri AUB, OSB Beirut, ebanon ghaziri@aub.edu.lb Abtract In thi paper, we have applied the concept of the elf-organizing map (SOM)
COMPETITIVE PROBABIISTIC SEF-ORGANIZING MAPS FOR ROUTING PROBEMS Haan Ghaziri AUB, OSB Beirut, ebanon ghaziri@aub.edu.lb Abtract In thi paper, we have applied the concept of the elf-organizing map (SOM)
for Spectral and Glossiness Recording
 Imrovement in Accurac of Flat-bed Scanning Stem for Sectral and Gloine Recording Maki Yokoama a, Takahiro Takiguchi b, Keiichi Ochiai b, Norimichi Tumura b, Tohia Nakaguchi b, and Yoichi Miake c a Deartment
Imrovement in Accurac of Flat-bed Scanning Stem for Sectral and Gloine Recording Maki Yokoama a, Takahiro Takiguchi b, Keiichi Ochiai b, Norimichi Tumura b, Tohia Nakaguchi b, and Yoichi Miake c a Deartment
CLOUD computing is quickly becoming an effective and
 IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS, VOL. 24, NO. 6, JUNE 203 087 Otial Multiserver Configuration for Profit Maxiization in Cloud Couting Junwei Cao, Senior Meber, IEEE, Kai Hwang, Fellow,
IEEE TRANSACTIONS ON PARALLEL AND DISTRIBUTED SYSTEMS, VOL. 24, NO. 6, JUNE 203 087 Otial Multiserver Configuration for Profit Maxiization in Cloud Couting Junwei Cao, Senior Meber, IEEE, Kai Hwang, Fellow,
Multi-Sensor Data Fusion in Presence of Uncertainty and Inconsistency in Data
 3 Multi-Senor Data Fuion in Preence of Uncertainty and Inconitency in Data Manih Kumar and Devendra P. Garg Univerity of Cincinnati and Due Univerity USA Oen Acce Databae www.intechweb.org. Introduction
3 Multi-Senor Data Fuion in Preence of Uncertainty and Inconitency in Data Manih Kumar and Devendra P. Garg Univerity of Cincinnati and Due Univerity USA Oen Acce Databae www.intechweb.org. Introduction
Diverse: Application-Layer Service Differentiation in Peer-to-Peer Communications
 Divere: Application-Layer Service Differentiation in Peer-to-Peer Communication Chuan Wu, Student Member, IEEE, Baochun Li, Senior Member, IEEE Department of Electrical and Computer Engineering Univerity
Divere: Application-Layer Service Differentiation in Peer-to-Peer Communication Chuan Wu, Student Member, IEEE, Baochun Li, Senior Member, IEEE Department of Electrical and Computer Engineering Univerity
A Fail-Aware Datagram Service
 A Fail-Aware Datagra Service Christof Fetzer and Flaviu Cristian christof@research.att.co, htt://www.christof.org Abstract In distributed real-tie systes it is often useful for a rocess Ô to know that
A Fail-Aware Datagra Service Christof Fetzer and Flaviu Cristian christof@research.att.co, htt://www.christof.org Abstract In distributed real-tie systes it is often useful for a rocess Ô to know that
On Peer-to-Peer Media Streaming Λ
 On eer-to-eer Media Streaming Λ Dongyan Xu y, Mohamed Hefeeda, Suanne Hambruch, Bharat Bhargava Department of Computer Science urdue Univerity, Wet Lafayette, IN 797 fdxu, hefeeda, eh, bbg@c.purdue.edu
On eer-to-eer Media Streaming Λ Dongyan Xu y, Mohamed Hefeeda, Suanne Hambruch, Bharat Bhargava Department of Computer Science urdue Univerity, Wet Lafayette, IN 797 fdxu, hefeeda, eh, bbg@c.purdue.edu
999 Computer System Network. (12) Patent Application Publication (10) Pub. No.: US 2006/ A1. (19) United States
 (19) United State US 2006O1296.60A1 (12) Patent Application Publication (10) Pub. No.: Mueller et al. (43) Pub. Date: Jun. 15, 2006 (54) METHOD AND COMPUTER SYSTEM FOR QUEUE PROCESSING (76) Inventor: Wolfgang
(19) United State US 2006O1296.60A1 (12) Patent Application Publication (10) Pub. No.: Mueller et al. (43) Pub. Date: Jun. 15, 2006 (54) METHOD AND COMPUTER SYSTEM FOR QUEUE PROCESSING (76) Inventor: Wolfgang
Modeling the Effect of Mobile Handoffs on TCP and TFRC Throughput
 Modeling the Effect of Mobile Handoff on TCP and TFRC Throughput Antonio Argyriou and Vijay Madietti School of Electrical and Computer Engineering Georgia Intitute of Technology Atlanta, Georgia 3332 25,
Modeling the Effect of Mobile Handoff on TCP and TFRC Throughput Antonio Argyriou and Vijay Madietti School of Electrical and Computer Engineering Georgia Intitute of Technology Atlanta, Georgia 3332 25,
Advanced Encryption Standard and Modes of Operation
 Advanced Encryption Standard and Mode of Operation G. Bertoni L. Breveglieri Foundation of Cryptography - AES pp. 1 / 50 AES Advanced Encryption Standard (AES) i a ymmetric cryptographic algorithm AES
Advanced Encryption Standard and Mode of Operation G. Bertoni L. Breveglieri Foundation of Cryptography - AES pp. 1 / 50 AES Advanced Encryption Standard (AES) i a ymmetric cryptographic algorithm AES
JRes: A Resource Accounting Interface for Java
 JRe: A Reource Accounting Interface for Java Grzegorz Czajkowki and Thorten von Eicken Department of Computer Science Cornell Univerity {grze,tve@c.cornell.edu Abtract In order to better upport the Internet
JRe: A Reource Accounting Interface for Java Grzegorz Czajkowki and Thorten von Eicken Department of Computer Science Cornell Univerity {grze,tve@c.cornell.edu Abtract In order to better upport the Internet
Ethernet Peer-To-Peer Communication With Model 353 And Procidia i pac Controllers
 iemen Energy & utomation pplication ata Ethernet Peer-To-Peer Communication With odel 353 nd Procidia ipac Controller 353-113 Rev. 1 July Ethernet i a leading form of network communication that i often
iemen Energy & utomation pplication ata Ethernet Peer-To-Peer Communication With odel 353 nd Procidia ipac Controller 353-113 Rev. 1 July Ethernet i a leading form of network communication that i often
else end while End References
 621-630. [RM89] [SK76] Roenfeld, A. and Melter, R. A., Digital geometry, The Mathematical Intelligencer, vol. 11, No. 3, 1989, pp. 69-72. Sklanky, J. and Kibler, D. F., A theory of nonuniformly digitized
621-630. [RM89] [SK76] Roenfeld, A. and Melter, R. A., Digital geometry, The Mathematical Intelligencer, vol. 11, No. 3, 1989, pp. 69-72. Sklanky, J. and Kibler, D. F., A theory of nonuniformly digitized
3D SMAP Algorithm. April 11, 2012
 3D SMAP Algorithm April 11, 2012 Baed on the original SMAP paper [1]. Thi report extend the tructure of MSRF into 3D. The prior ditribution i modified to atify the MRF property. In addition, an iterative
3D SMAP Algorithm April 11, 2012 Baed on the original SMAP paper [1]. Thi report extend the tructure of MSRF into 3D. The prior ditribution i modified to atify the MRF property. In addition, an iterative
Monte-Carlo optimizations for resource allocation problems in stochastic network systems
 Monte-Carlo otimization for reource allocation roblem in tochatic network ytem Milo aukrecht Deartment of Comuter Science 5329 Sennott Square Univerity of Pittburgh milo@c.itt.edu Abtract Real-world ditributed
Monte-Carlo otimization for reource allocation roblem in tochatic network ytem Milo aukrecht Deartment of Comuter Science 5329 Sennott Square Univerity of Pittburgh milo@c.itt.edu Abtract Real-world ditributed
SIMIT 7. Profinet IO Gateway. User Manual
 SIMIT 7 Profinet IO Gateway Uer Manual Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult are only non-binding uggetion
SIMIT 7 Profinet IO Gateway Uer Manual Edition January 2013 Siemen offer imulation oftware to plan, imulate and optimize plant and machine. The imulation- and optimizationreult are only non-binding uggetion
The Data Locality of Work Stealing
 The Data Locality of Work Stealing Umut A. Acar School of Computer Science Carnegie Mellon Univerity umut@c.cmu.edu Guy E. Blelloch School of Computer Science Carnegie Mellon Univerity guyb@c.cmu.edu Robert
The Data Locality of Work Stealing Umut A. Acar School of Computer Science Carnegie Mellon Univerity umut@c.cmu.edu Guy E. Blelloch School of Computer Science Carnegie Mellon Univerity guyb@c.cmu.edu Robert
Edits in Xylia Validity Preserving Editing of XML Documents
 dit in Xylia Validity Preerving diting of XML Document Pouria Shaker, Theodore S. Norvell, and Denni K. Peter Faculty of ngineering and Applied Science, Memorial Univerity of Newfoundland, St. John, NFLD,
dit in Xylia Validity Preerving diting of XML Document Pouria Shaker, Theodore S. Norvell, and Denni K. Peter Faculty of ngineering and Applied Science, Memorial Univerity of Newfoundland, St. John, NFLD,
Delaunay Triangulation: Incremental Construction
 Chapter 6 Delaunay Triangulation: Incremental Contruction In the lat lecture, we have learned about the Lawon ip algorithm that compute a Delaunay triangulation of a given n-point et P R 2 with O(n 2 )
Chapter 6 Delaunay Triangulation: Incremental Contruction In the lat lecture, we have learned about the Lawon ip algorithm that compute a Delaunay triangulation of a given n-point et P R 2 with O(n 2 )
Software Agent (SA) to guarantee QoS for multi constrain applications in all-ip networks
 Software Agent (SA) to guarantee QoS for multi contrain application in all-ip network Kazi Khaled Al-Zahid and Mituji Matumoto GITS, Waeda Univerity 94 Waeda Univ. Bldg. A-308, 1011Okuboyama Nihitomida
Software Agent (SA) to guarantee QoS for multi contrain application in all-ip network Kazi Khaled Al-Zahid and Mituji Matumoto GITS, Waeda Univerity 94 Waeda Univ. Bldg. A-308, 1011Okuboyama Nihitomida
LJPS Gurgaon. Class XII- Physics - Assignment Topic: - Ray Optics
 LJPS Gurgaon 1. The refractive index of the ediu i 3. What i the angle of refraction, if the unpolaried light i incident on it at the polarizing angle of the ediu? [An : 30 degree] Cla XII- Phyic - Aignent
LJPS Gurgaon 1. The refractive index of the ediu i 3. What i the angle of refraction, if the unpolaried light i incident on it at the polarizing angle of the ediu? [An : 30 degree] Cla XII- Phyic - Aignent
Research on Target Detection based on moving Image
 International Journal of Science Vol.5 No.4 018 ISSN: 1813-4890 Reearch on Target Detection baed on moving Image Feiyan Wu 1, Xianwen Liao 1 Guangxi College and Univeritie Key Laboratory of Profeional
International Journal of Science Vol.5 No.4 018 ISSN: 1813-4890 Reearch on Target Detection baed on moving Image Feiyan Wu 1, Xianwen Liao 1 Guangxi College and Univeritie Key Laboratory of Profeional
Chapter 7 Packet-Switching Networks. Chapter 7 Packet-Switching Networks. Packet Switching. Network Layer. Network Service
 Chapter 7 Packet-Switching etwork etwork Operation & Topology Datagram and Virtual Circuit Structure of a Packet Switch Routing in Packet etwork Shortet Path Routing etwork Chapter 7 Packet-Switching etwork
Chapter 7 Packet-Switching etwork etwork Operation & Topology Datagram and Virtual Circuit Structure of a Packet Switch Routing in Packet etwork Shortet Path Routing etwork Chapter 7 Packet-Switching etwork
Architecture and grid application of cluster computing system
 Architecture and grid application of cluter computing ytem Yi Lv*, Shuiqin Yu, Youju Mao Intitute of Optical Fiber Telecom, Chongqing Univ. of Pot & Telecom, Chongqing, 400065, P.R.China ABSTRACT Recently,
Architecture and grid application of cluter computing ytem Yi Lv*, Shuiqin Yu, Youju Mao Intitute of Optical Fiber Telecom, Chongqing Univ. of Pot & Telecom, Chongqing, 400065, P.R.China ABSTRACT Recently,
RESEARCH ON A HEURISTIC SEARCHING ALGORITHM FOR ENERGY-AWARE ROUTING IN WIRELESS SENSOR NETWORKS
 RESEARCH ON A HEURISTIC SEARCHING ALGORITHM FOR ENERGY-AWARE ROUTING IN WIRELESS SENSOR NETWORKS 1 HONGWEI CHEN, CHUNHUA ZHANG, *3 CHUNZHI WANG 1 Aoc. Prof., School of Comuter Science, Hubei Univerity
RESEARCH ON A HEURISTIC SEARCHING ALGORITHM FOR ENERGY-AWARE ROUTING IN WIRELESS SENSOR NETWORKS 1 HONGWEI CHEN, CHUNHUA ZHANG, *3 CHUNZHI WANG 1 Aoc. Prof., School of Comuter Science, Hubei Univerity
Key Terms - MinMin, MaxMin, Sufferage, Task Scheduling, Standard Deviation, Load Balancing.
 Volume 3, Iue 11, November 2013 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Tak Aignment in
Volume 3, Iue 11, November 2013 ISSN: 2277 128X International Journal of Advanced Reearch in Computer Science and Software Engineering Reearch Paper Available online at: www.ijarce.com Tak Aignment in
The Performance Evaluation of Qos in Wireless Personal Area Network (WPAN) on Impact of Bluetooth Worms
 Journal of Wirele Networking and Communication 2012, 2(5): 111-116 DOI: 10.5923/j.jwnc.20120205.05 The Performance Evaluation of Qo in Wirele Peronal Area Network (WPAN) on Impact of Bluetooth Worm M.
Journal of Wirele Networking and Communication 2012, 2(5): 111-116 DOI: 10.5923/j.jwnc.20120205.05 The Performance Evaluation of Qo in Wirele Peronal Area Network (WPAN) on Impact of Bluetooth Worm M.
p done CPU p user p drivdone 1-p drivdone
 Approximate Analytical Performance Evaluation of a UNIX Baed Multiproceor Operating Sytem Stefan Greiner Duke Univerity Dept. of Electrical Engineering Durham, NC 2770-029, USA Box 9029 greiner@ee.duke.edu
Approximate Analytical Performance Evaluation of a UNIX Baed Multiproceor Operating Sytem Stefan Greiner Duke Univerity Dept. of Electrical Engineering Durham, NC 2770-029, USA Box 9029 greiner@ee.duke.edu
A Handover Scheme for Mobile WiMAX Using Signal Strength and Distance
 A Handover Scheme for Mobile WiMAX Uing Signal Strength and Ditance Mary Alatie, Mjumo Mzyece and Anih Kurien Department of Electrical Engineering/French South African Intitute of Technology (F SATI) Thwane
A Handover Scheme for Mobile WiMAX Uing Signal Strength and Ditance Mary Alatie, Mjumo Mzyece and Anih Kurien Department of Electrical Engineering/French South African Intitute of Technology (F SATI) Thwane
