OPERATIONS & MAINTENANCE MANUAL. Trivalent Management Service
|
|
|
- Kenneth Shepherd
- 6 years ago
- Views:
Transcription
1 OPERATIONS & MAINTENANCE MANUAL DECEMBER 2016
2 Table of Contents Table of Contents 1. Introduction Acronyms Scope of evaluation Installation Uninstalling Overview & Elements Home Screen (no configuration) Summary Elements Configuration Screen Summary Elements Home Screen Summary Elements Start Service Summary Elements Unlock Service Summary Elements Change Password Summary Elements Application Registration Summary Elements Extend Mission Summary Elements Operations Configure Integrated Apps Password Complexity Settings Mission Time To Live Authentication Settings Check Version Trivalent Proprietary Information i
3 Table of Contents 4.3. Start Service Lock Service Unlock Service Change Password Application Registration Extend Mission Clear Configuration Android API Calls - Introduction Scope Dependent Documents Android Data Protection SDK Overview Components Management Service Data Protection SDK Library Android Security API Reference Cryptographic Hashing FEKEK Generation Hardware-based RSA Key Pair Generation PBKDF2 Key Generation Key Wrapping and Unwrapping OAEP Keystores and Key Storage/Data Storage Data Protection SDK Library Cryptographic Hashing Hardware-based RSA Key Pair Generation Key Unwrapping Keystores and Key Storage Permissions Used Management Service Data Protection SDK Library Frequently Asked Questions Trivalent Proprietary Information ii
4 Table of Figures Table of Figures Figure 1: App icon... 1 Figure 2: Activate Device Administrator screen... 3 Figure 3: Confirmation of Device Administrator popup... 3 Figure 4: Deactivate Device Administrator screen... 4 Figure 5: Home Screen (no configuration)... 5 Figure 6: Configuration Screen... 6 Figure 7: Home Screen... 8 Figure 8: Start Service... 9 Figure 9: Unlock Service Figure 10: Change Password Figure 11: Application Registration Figure 12: Extend Mission Figure 13: Applications popup Figure 14: MTTL Expiration popup (1) Figure 15: MTTL Expiration popup (2) Figure 16: Check Version popup Figure 17: Android Notification Menu with Application Registration notification Figure 18: Clear Configuration popup Trivalent Proprietary Information iii
5 1. Introduction Introduction The Trivalent Data Protection solution is installed as an additional layer of security to protect sensitive data stored on mobile devices. The solution leverages a different approach to encryption by protecting files individually, first by encrypting the file, then by obfuscating the contents via a shredding and dispersal mechanism, storing files across the target storage media. This solution is compatible with additional encryption technologies that do Full Disk Encryption, Platform Encryption, or Hardware-Based Encryption. The solution is managed by the app. All graphics in this document relate to the. Below is the icon for the application: 1.1. Acronyms Figure 1: App icon ACRONYM DEFINITION AES Advanced Encryption Standard API Application Programming Interface APK Android application package CBC Cipher Block Chaining CTOR Object Constructor DAR Data-at-rest DIU Data-in-use/Data-in-process ECB Electronic Codebook (A type of block cipher) EUD End-user device FEKEK File Encryption Key Encryption Key HMAC Hashed Message Authentication Code I/O Input/Output MTTL Mission Time to Live OAEP Optimal Asymmetric Encryption Padding PBE Password-Based Encryption PBKDF(2) Password-Based Key Derivation Function PKCS Public Key Cryptography Standard Trivalent Proprietary Information 1
6 ACRONYM RSA SDK SHA SPXCORE TMS DEFINITION Rivest, Shamir & Adleman, a type of encryption algorithm Software Development Kit Secure Hash Algorithm An encryption engine Introduction 1.2. Scope of evaluation Version 2.13 of the application is being evaluated. Please see the Security Target document for further details of scope of evaluation. Trivalent Proprietary Information 2
7 2. Installation To install the APK, follow the steps below: Installation 1. Download the.apk file onto the device 2. Open the.apk file A prompt will appear asking if you wish to install this application 3. Tap the Install button Once installation is complete, open the. An Activate Device Administrator screen will appear. Figure 2: Activate Device Administrator screen 4. Tap the ACTIVATE button A confirmation popup will appear 5. Tap ALLOW Figure 3: Confirmation of Device Administrator popup Trivalent Proprietary Information 3
8 2.1. Uninstalling Installation To uninstall the, follow the steps below. All encrypted files will no longer be accessible once uninstallation is complete. 1. Navigate to Android s settings screen 2. Navigate to security settings 3. Look for the Device administrators setting (May be under other or advanced security settings) 4. On the Device administrators screen, locate the and slide the toggle to off A Deactivate device administrator screen will appear 5. Tap the DEACTIVATE button Figure 4: Deactivate Device Administrator screen The toggle will be set to off on the Device administrators screen 6. Return to Android s settings screen 7. Navigate to applications settings 8. Navigate to Application manager 9. Select the application info screen will appear 10. Tap UNINSTALL Confirmation popup will appear 11. Tap OK Trivalent Proprietary Information 4
9 3. Overview & Elements 3.1. Home Screen (no configuration) Summary Overview & Elements The Home Screen of the will present the user with multiple options. If there is no existing configuration on the device, the Home Screen will have a limited number of options available Elements 1 2 Figure 5: Home Screen (no configuration) Field Description Input Type 1 Configure Launches the Configuration Screen Button 2 Check Version Performs a version check of the Trivalent Management Service to determine if the installed version is the latest. Internet connection is required Button Trivalent Proprietary Information 5
10 3.2. Configuration Screen Summary Overview & Elements The Configuration Screen allows the user to set their encryption and password settings. Settings include integrated apps, password complexity, Mission Time to Live, and reauthentication rules. It is accessed from the Home Screen while the EUD has no configuration Elements Figure 6: Configuration Screen 19 Trivalent Proprietary Information 6
11 Overview & Elements Field Description Input Type 1 Apps to Encrypt 2 Enable Shredding 3 Minimum Password Length 4 Maximum Password Length 5 Minimum Uppercase 6 Minimum Lowercase 7 Minimum Digits 8 Minimum Symbols 9 Enable MTTL 10 Initial Expiration Time 11 Enable MTTL Extension 12 Extended Expiration Time 13 MTTL Password & Confirmation 14 Authentication Mechanism 15 Authentication Timeout 16 Maximum Attempts 17 Lockout Time 18 New Password & Confirmation Launches a popup for the user to select which applications installed on the EUD will be authorized to handle encrypted data Designates whether encrypted files will be shredded into four pieces or left whole Sets the minimum number of characters required for the user s password Sets the maximum number of characters allowed for the user s password Sets the minimum number of uppercase characters required in the user s password Sets the minimum number of lowercase characters required in the user s password Sets the minimum number of numbers (0-9) required in the user s password Sets the minimum number of special characters required in the user s password Enables/disables Mission Time to Live for the configuration being set up Launches a popup for the user to select how long their MTTL will be. Setting is disabled until Enable MTTL is checked Enables/disables an extendable MTTL for the current configuration Launches a popup for the user to select how long their extendable mission will be. Setting is disabled until Enable MTTL Extension is checked Password used to extend the MTTL. User will enter in the password in two separate textboxes. Sets how the user will use their password to authenticate. Device requires authentication every time the EUD is unlocked. Timer requires authentication after a certain duration of time Sets how long the EUD remains authenticated before requiring re-authentication. Setting is hidden unless Authentication Mechanism is set to Timer Sets the maximum number of consecutive incorrect password attempts before the user gets locked out Sets how long the EUD stays locked after too many incorrect password attempts have been made Password used for authentication. User will enter in the password in two separate textboxes Button Checkbox Slider Slider Slider Slider Slider Slider Checkbox Button Checkbox Button Textboxes Toggle Slider Slider Slider Textboxes 19 Build Applies all configuration settings Button Trivalent Proprietary Information 7
12 3.3. Home Screen Summary Overview & Elements The Home Screen of the will present the user with multiple options. Once a configuration has been set up, the Home Screen provides access to features such as changing the password and clearing the configuration Elements Figure 7: Home Screen Field Description Input Type 1 Start / Lock / Unlock Service Depending on the state of the TMS: Start Service launches the Start Service popup, Lock Service immediately unauthenticates the user, Unlock Service launches the Unlock Service popup Button 2 Change Password Launches a popup to change the user password Button 3 Clear Configuration 4 Check Version Launches a confirmation popup for the wiping of the keystore and configuration Performs a version check of the Trivalent Management Service to determine if the installed version is the latest. Internet connection is required Button Button Trivalent Proprietary Information 8
13 3.4. Start Service Summary Overview & Elements The Start Service popup functions similarly to the Unlock Service popup. It requires the user to enter in their password for authentication. Once the user submits their password, MTTL (if applicable) will begin. Starting the service needs to occur before the user can begin using their data. This popup will only appear one time per configuration Elements Figure 8: Start Service Field Description Input Type 1 Enter Password 2 Error field 3 Authenticate Current authentication password. Textbox border will turn red if the submitted password is incorrect Incorrect password will appear in the event of an incorrect password submission Submits the password entered for authentication. MTTL begins (if applicable) if the password is correct Textbox Label Button Trivalent Proprietary Information 9
14 3.5. Unlock Service Summary Overview & Elements The Unlock Service popup will appear when the Android device is not authenticated. The user password is needed to re-authenticate. This popup can also be launched from the Home Screen Elements Figure 9: Unlock Service Field Description Input Type 1 Enter Password 2 Error field Current authentication password. Textbox border will turn red if the submitted password is incorrect Incorrect password will appear in the event of an incorrect password submission Textbox Label 3 Authenticate Submits the password entered for authentication Button Trivalent Proprietary Information 10
15 3.6. Change Password Summary Overview & Elements The Change Password popup is used in the event the user needs to update their authentication password. This feature is available on-demand to the user from the Home Screen Elements Figure 10: Change Password Field Description Input Type 1 Current Password 2 New Password 3 Confirm New Password 4 Error field Current authentication password. Textbox border will turn red if submitted password is incorrect New password to be used for authentication. Textbox border will turn green when the password meets complexity requirements Re-entry of new authentication password. Textbox border will turn green when both textbox entries match Invalid password will appear if the password does not meet complexity requirements Password mismatch will appear in the event of unequal passwords Incorrect password will appear in this field in the event of an incorrect password submission Textbox Textbox Textbox Label 5 Cancel Returns the user to the Home Screen Button 6 Submit Submits the password entered for authentication and executes the password change request Button Trivalent Proprietary Information 11
16 3.7. Application Registration Summary Overview & Elements In order to ensure that only authorized applications have access to encrypted data, applications must be granted access to the via the Application Registration popup. Any applications selected during configuration will require registration the first time they are launched. Additionally, only applications with the Trivalent API embedded will work with the encryption solution Elements Figure 11: Application Registration Field Description Input Type 1 Enter Password 2 Error field Current authentication password. Textbox border will turn red if the submitted password is incorrect Incorrect password will appear in the event of an incorrect password submission Textbox Label 3 Authenticate Submits the password entered to register the application Button Trivalent Proprietary Information 12
17 3.8. Extend Mission Summary Overview & Elements The Extend Mission popup will appear when the configured MTTL is about to expire and if MTTL can be extended. The user will have a chance to extend their mission from the time the prompt appears until MTTL ends. Users can only extend their mission one time Elements Figure 12: Extend Mission Field Description Input Type 1 Mission Expiration Time Displays the MTTL expiration date and time Label 2 Possible Extension Time 3 Authentication Password 4 Mission Extension Password 5 Error field 6 Cancel Displays the MTTL expiration date and time if the mission were to be extended Current authentication password Password to extend the mission Incorrect password will appear in the event of an incorrect password submission. It does not indicate which password was incorrect, in order to circumvent hacking attempts Dismisses the Extend Mission popup into the Android Notification Menu Label Textbox Textbox Label Button 7 Extend Submits both passwords for MTTL extension Button Trivalent Proprietary Information 13
18 4. Operations 4.1. Configure Operations Setting up a new configuration can only be performed if there is no existing configuration residing on the EUD. See section 4.9 if there is an existing configuration that needs to be cleared first. 1. Open the Home Screen will be displayed 2. Tap Configure Configuration Screen will be displayed 3. Continue on to section Integrated Apps 4. Tap SELECT next to the Apps to Encrypt label Applications popup will appear 5. Tap on the desired applications to select them for integration 6. Tap ACCEPT Popup will disappear 7. Continue on to section Figure 13: Applications popup Trivalent Proprietary Information 14
19 Password Complexity Settings Operations Note: Settings in this section come pre-set with default values. This section is not mandatory. 8. Use the Min Password Length slider to set the minimum password length setting 9. Use the Max Password Length slider to set the maximum password length setting 10. Use the Min Uppercase slider to set the minimum number of uppercase characters required in the user password 11. Use the Min Lowercase slider to set the minimum number of lowercase characters required in the user password 12. Use the Min Digits slider to set the minimum number of numbers (0-9) required in the user password 13. Use the Min Symbols slider to set the minimum number of special characters required in the user password 14. Continue on to section Mission Time To Live Note: MTTL is not required and can be left unenabled. Continue on to section if MTTL is not needed. 15. Tap the Enable MTTL checkbox to enable MTTL for this configuration 16. Tap SELECT next to the Initial Expiration label MTTL Expiration popup will appear 17. Select a date for MTTL expiration Figure 14: MTTL Expiration popup (1) 18. Tap NEXT MTTL Expiration popup will display a clock 19. Select a time of day to end MTTL on the selected date Trivalent Proprietary Information 15
20 Operations 20. Tap ACCEPT Popup will disappear Figure 15: MTTL Expiration popup (2) Note: The following steps are optional. Continue on to section if MTTL extension is not needed. 21. Tap the Enable MTTL Extension checkbox to allow the configuration to have an extendable MTTL 22. Tap SELECT next to the Extended Expiration label MTTL Expiration popup will appear (Figure 14) 23. Select a date to end an extended MTTL on 24. Tap NEXT MTTL Expiration popup will display a clock (Figure 15) 25. Select a time of day to end an extended MTTL on the selected date 26. Tap ACCEPT Popup will disappear 27. Enter in a Mission Extension Password in the MTTL Password textbox 28. Confirm the password in the second textbox 29. Continue on to section Authentication Settings 30. Use the Auth Mechanism toggle to set how authentication will be used for this configuration Note: Device requires authentication every time the EUD is unlocked. Timer requires authentication after a given duration of time 31. (Only if Timer is selected above) Use the Auth Timeout slider to set how long the EUD remains authenticated before requiring re-authentication 32. Use the Max Attempts slider to set the maximum number of consecutive incorrect password attempts before the user gets locked out 33. Use the Lockout Time slider to set how long the EUD stays locked after too many incorrect password attempts have been made 34. Enter in the desired user password in the New Password textbox Trivalent Proprietary Information 16
21 35. Confirm the password in the second textbox 36. Tap BUILD to complete the configuration 4.2. Check Version Operations Note: The password must match the complexity settings defined in section It should be a strong passphrase; a passphrase with at least one uppercase letter, lowercase letter, special character, and number is recommended. Longer length passphrases provide increased security strength over shorter ones. Acceptable password strength should reflect the sensitivity of the data being encrypted. Higher data sensitivity should have increased password strength. Checking to see if all components of the are up to date can be performed regardless of if the EUD already has a configuration running. 1. Open the Home Screen will be displayed 2. Tap Check Version Check Version popup will appear, with one of the following messages: Up to date, Not up to date, Unable to connect Figure 16: Check Version popup 3. Tap OK to dismiss popup 4. If an update is available, please contact Trivalent at support@trivalent.us.com 4.3. Start Service Starting the service can only be performed once per configuration. Once the service is started, the mission will officially begin and the MTTL clock will start, if applicable. The service needs to be started in order to access encrypted content. 1. Open the Home Screen will be displayed 2. Tap Start Service Start Service popup will appear Note: If Start Service is not an option, this means the EUD already has a configuration or needs a new configuration. 3. In the Enter Password textbox, type in the user password 4. Tap AUTHENTICATE to submit the password Popup will disappear Trivalent Proprietary Information 17
22 4.4. Lock Service Operations In the event where a user needs to quickly un-authenticate themselves, they can do so by following the steps below. 1. Open the Home Screen will be displayed 2. Tap Lock Service Button should change to say Unlock Service 4.5. Unlock Service Depending on the configuration, authentication will be needed either after a certain amount of time or every time the EUD is unlocked. The Unlock Service popup will appear when authentication is needed. This popup can also be accessed via the Android notification menu or via the Home Screen. Once the popup appears, follow the steps below. 1. In the Enter Password textbox, type in the user password 2. Tap AUTHENTICATE to submit the password Popup will disappear 4.6. Change Password 1. Open the Home Screen will be displayed 2. Tap Change Password Change Password popup will appear 3. In the Current Password textbox, type in the current user password 4. In the New Password textbox, type in a new password The textbox border will turn green once the New Password meets the configured complexity requirements Note: The password must match the complexity settings defined in section It should be a strong passphrase; a passphrase with at least one uppercase letter, lowercase letter, special character, and number is recommended. Longer length passphrases provide increased security strength over shorter ones. Acceptable password strength should reflect the sensitivity of the data being encrypted. Higher data sensitivity should have increased password strength. 5. Re-type the new password in the Confirm New Password textbox The textbox border will turn green once the password matches the one typed in the New Password textbox 6. Tap the SUBMIT button to update the password Popup will disappear and a success message will briefly appear 4.7. Application Registration 1. While the EUD is currently authenticated, launch an integrated app Note: The integrated app should not be running before the mission starts. If already open, open the Android Task Manager and swipe the application closed. Do not use the app at all before registering. Trivalent Proprietary Information 18
23 Operations 2. Swipe down from the top of the screen to bring up the Android Notification Menu 3. Tap on the Application Registration notification for the integrated app Application Registration popup will appear Figure 17: Android Notification Menu with Application Registration notification 4. In the Enter Password textbox, type in the user password 5. Tap AUTHENTICATE to register the app Popup will disappear and a success message will briefly appear 6. Return to the app that was just integrated to begin use 4.8. Extend Mission The Extend Mission popup will appear when MTTL is approaching expiration. If the popup is accidently dismissed or missed, it can be found in the Android Notification Menu. Extending the mission is not mandatory. 1. In the Authentication Password textbox, type in the user password 2. In the Mission Extension Password textbox, type in the mission extension password 3. Tap the EXTEND button to extend the mission 4.9. Clear Configuration Clearing the configuration will wipe all key and configuration data. Encrypted files will no longer be accessible. 1. Open the Home Screen will be displayed 2. Tap Clear Configuration Clear Configuration popup will appear Figure 18: Clear Configuration popup Trivalent Proprietary Information 19
24 Operations 3. Read the warning message and tap YES to continue Home Screen (no configuration) will be displayed (section 3.1) Trivalent Proprietary Information 20
25 Android API Calls 1 Android API Calls - Introduction Scope Android API Calls - Introduction The scope of this document is to provide a complete list of the Android security API calls used by the Android Data Protection SDK encryption system. Note that details of the encryption system are not covered in this document. The Dependent Documents section lists any external documents that this document references content from. Dependent Documents The following documents contain information referenced by this document, but are outside the scope of this document. Android Data Protection SDK Key Management and Architecture (Android_DataProtectionSDK_KeyMgmt_and_Architecture.docx) Android Data Protection SDK SDS (Android_DataProtectionSDK_SDS.docx) 2 Android Data Protection SDK Overview Components A brief overview of the Android Data Protection SDK is provided for the reader s convenience. The major components of the Android Data Protection SDK system are: Data Protection SDK Library (used by Android applications) For more details regarding these components, refer to the documentation listed under the Dependent Documents section Management Service The is responsible for system configuration, initialization, authentication/de-authentication, FEKEK generation, centralized key management, and system finalization. Note that the itself is not responsible for encryption Data Protection SDK Library Android application developers that wish to use Trivalent s Data Protection SDK system can consume the library component, which allows access to the encryption APIs. The library is responsible for encryption and decryption. The library also allows an application to Trivalent Proprietary Information 21
26 Android Security API Reference communicate with the for key data, configuration information, and authentication state. 3 Android Security API Reference Cryptographic Hashing Constructors Called None Methods Called javax.crypto.mac.getinstance(string) javax.crypto.mac.getmaclength() javax.crypto.mac.getalgorithm() javax.crypto.mac.init(key) javax.crypto.mac.update(byte[]) javax.crypto.mac.dofinal(byte[], int) java.security.messagedigest.getinstance(string) java.security.messagedigest.digest(byte[]) android.content.pm.signature.tobytearray() java.security.cert.certificatefactory.getinstance(string) java.security.cert.certificatefactory.generatecertificate(byte[]) Objects Created javax.crypto.mac java.security.messagedigest android.content.pm.signature java.security.cert.certficatefactory java.security.cert.x509certificate Exceptions Handled java.security.nosuchalgorithmexception java.security.cert.certificateexception java.security.cert.certificateencodingexception Trivalent Proprietary Information 22
27 3.1.2 FEKEK Generation Constructors Called Android Security API Reference None Methods Called javax.crypto.keygenerator.getinstance(string) javax.crypto.keygenerator.init(int) javax.crypto.keygenerator.generatekey() Objects Created javax.crypto.keygenerator javax.crypto.secretkey Exceptions Handled java.security.nosuchalgorithmexception Hardware-based RSA Key Pair Generation Constructors Called android.security.keypairgeneratorspec.builder.ctor(context) javax.security.auth.x500.x500principal.ctor(string) Methods Called java.security.keystore.getinstance(string) java.security.keystore.load(inputstream, char[]) java.security.keystore.getentry(string, KeyStore.ProtectionParameter); java.security.keypairgenerator.getinstance(string, String) android.security.keypairgeneratorspec.builder.setalias(string) android.security.keypairgeneratorspec.builder.setstartdate(date) android.security.keypairgeneratorspec.builder.setenddate(date) android.security.keypairgeneratorspec.builder.setserialnumber(biginteger) android.security.keypairgeneratorspec.builder.setsubject(x500principal) android.security.keypairgeneratorspec.builder.build() java.security.keypairgenerator.initialize(algorithmparameterspec) java.security.keypairgenerator.generatekeypair() java.security.keystore.privatekeyentry.getcertificate() java.security.certificate.getpublickey() java.security.keystore.privatekeyentry.getprivatekey() Trivalent Proprietary Information 23
28 Objects Created Android Security API Reference java.security.keystore java.security.keystore.privatekeyentry java.security.keystore.entry java.security.keypairgenerator android.security.keypairgeneratorspec android.security.keypairgeneratorspec.builder javax.security.auth.x500.x500principal java.security.keypair java.security.publickey java.security.privatekey java.security.cert.certificate Exceptions Handled java.security.keystoreexception java.security.cert.certificateexception java.security.nosuchalgorithmexception java.security.unrecoverableentryexception java.security.nosuchproviderexception java.security.invalidalgorithmparameterexception PBKDF2 Key Generation Interfaces Implemented javax.crypto.secretkey o getalgorithm() o getformat() o getencoded() o hashcode() o equals(object) javax.crypto.interfaces.pbekey o getiterationcount() o getsalt() o getpassword() o hashcode() o equals(object) o finalize() Constructors Called java.security.securerandom.ctor() javax.crypto.spec.pbekeyspec.ctor(char[], byte[], int, int) java.security.keyrep.ctor(keyrep.type, String, String, byte[]) Methods Called java.security.securerandom.nextbytes(byte[]) javax.crypto.spec.pbekeyspec.getpassword() Trivalent Proprietary Information 24
29 javax.crypto.spec.pbekeyspec.getsalt() javax.crypto.spec.pbekeyspec.getiterationcount() javax.crypto.spec.pbekeyspec.getkeylength() javax.crypto.mac.getinstance(string) javax.crypto.mac.getmaclength() javax.crypto.mac.init(secretkey) javax.crypto.mac.update(byte[] salt) javax.crypto.mac.dofinal(byte[], int) Objects Created Android Security API Reference java.security.securerandom javax.crypto.spec.pbekeyspec javax.crypto.mac javax.crypto.secretkey javax.crypto.interfaces.pbekey java.security.keyrep Exceptions Handled java.security.spec.invalidkeyspecexception java.security.nosuchalgorithmexception java.security.generalsecurityexception Key Wrapping and Unwrapping Wrapping FEKEK with HWB_RSA_Mgmt Constructors Called javax.crypto.secretkeyspec.ctor(byte[], int, int, String) Methods Called java.security.key.getencoded() javax.crypto.cipher.getinstance(string) java.security.keystore.getinstance(string) java.security.keystore.load(keystore.loadstoreparameter) java.security.interfaces.rsapublickey.getmodulus() java.security.interfaces.rsakey.getmodulus() javax.crypto.cipher.init(int, Key) javax.crypto.cipher.dofinal(byte[]) Objects Created java.security.secretkey javax.crypto.cipher java.security.keystore Exceptions Handled java.security.keystoreexception Trivalent Proprietary Information 25
30 javax.crypto.nosuchpaddingexception java.security.nosuchalgorithmexception java.security.certificateexception javax.crypto.nosuchpaddingexception javax.crypto.illegalblocksizeexception java.security.invalidkeyexception Android Security API Reference Wrapping [FEKEK]HWB_RSA_Mgmt with PBKDF2 Key Constructors Called javax.crypto.secretkeyspec.ctor(byte[], int, int, String) Methods Called javax.crypto.cipher.getinstance(string) javax.crypto.cipher.init(int, Key) javax.crypto.cipher.wrap(key) Objects Created java.security.secretkey javax.crypto.cipher Exceptions Handled javax.crypto.nosuchpaddingexception java.security.nosuchalgorithmexception javax.crypto.nosuchpaddingexception javax.crypto.illegalblocksizeexception Unwrapping [[FEKEK]HWB_RSA_Mgmt]PBKDF2_Key (once) Constructors Called None Methods Called javax.crypto.cipher.getinstance(string) javax.crypto.cipher.init(int, Key) java.security.key.getencoded() javax.crypto.cipher.unwrap(key, String, int) Objects Created java.security.secretkey javax.crypto.cipher Exceptions Handled javax.crypto.nosuchpaddingexception Trivalent Proprietary Information 26
31 java.security.nosuchalgorithmexception javax.crypto.nosuchpaddingexception Android Security API Reference Unwrapping [FEKEK]HWB_RSA_Mgmt Constructors Called javax.crypto.spec.secretkeyspec.ctor(byte[], int, int, String) Methods Called java.security.messagedigest.getinstance(string) java.security.key.getencoded() javax.crypto.cipher.getinstance(string) java.security.keystore.getinstance(string) java.security.keystore.load(keystore.loadstoreparameter) java.security.interfaces.rsakey.getmodulus() javax.crypto.cipher.init(int, Key) javax.crypto.cipher.dofinal(byte[], int, int) Objects Created javax.crypto.cipher java.security.keystore java.security.secretkey java.security.privatekey java.security.interfaces.rsakey java.security.key Exceptions Handled java.security.nosuchalgorithmexception javax.crypto.nosuchpaddingexception java.security.keystoreexception java.security.certificateexception java.security.invalidkeyexception javax.crypto.illegalblocksizeexception javax.crypto.badpaddingexception Wrapping FEKEK with HWB_RSA_App Constructors Called javax.crypto.secretkeyspec.ctor(byte[], int, int, String) Methods Called java.security.key.getencoded() javax.crypto.cipher.getinstance(string) java.security.keystore.getinstance(string) Trivalent Proprietary Information 27
32 java.security.keystore.load(keystore.loadstoreparameter) java.security.interfaces.rsapublickey.getmodulus() java.security.interfaces.rsakey.getmodulus() javax.crypto.cipher.init(int, Key) javax.crypto.cipher.dofinal(byte[]) Android Security API Reference Objects Created java.security.secretkey javax.crypto.cipher java.security.keystore Exceptions Handled java.security.keystoreexception javax.crypto.nosuchpaddingexception java.security.nosuchalgorithmexception java.security.certificateexception javax.crypto.nosuchpaddingexception javax.crypto.illegalblocksizeexception java.security.invalidkeyexception OAEP For OAEP, the Android platform does not natively provide OAEP capabilities. An external Bouncy Castle library (v1.51) is utilized for OAEP. This external Bouncy Castle library is ONLY used for the padding piece. All other encryption and security functionality is executed using only Android platform security API calls. For reference, the external Bouncy Castle library API usage is also documented in this section Interfaces Implemented org.bouncycastle.crypto.asymmetricblockcipher o init(boolean, CipherParameters) o getinputblocksize() o getoutputblocksize() o processblock(byte[], int, int) Constructors Called org.bouncycastle.crypto.digests.sha512digest.ctor() org.bouncycastle.crypto.encodings.oaepencoding.ctor(asymmetricblockcipher, Digest, byte[]) Methods Called org.bouncycastle.crypto.encodings.oaepencoding.init(true, null) org.bouncycastle.crypto.encodings.oaepencoding.processblock(byte[], int, int) java.security.key.getencoded() Trivalent Proprietary Information 28
33 Objects Created Android Security API Reference org.bouncycastle.crypto.digest org.bouncycastle.crypto.digests.sha512digest org.bouncycastle.crypto.encodings.oaepencoding org.bouncycastle.crypto.asymmetricblockcipher java.security.key java.security.interfaces.rsapublickey java.security.privatekey org.bouncycastle.crypto.cipherparameters Exceptions Handled org.bouncycastle.crypto.invalidciphertextexception java.security.invalidkeyexception java.security.keystoreexception java.security.nosuchalgorithmexception java.security.cert.certificateexception javax.crypto.badpaddingexception javax.crypto.illegalblocksizeexception javax.crypto.nosuchpaddingexception Keystores and Key Storage/Data Storage Note that the Data Storage term describes a process where Trivalent stores semi-sensitive data in keystores. Semi-sensitive data that the stores include featurespecific secondary passwords not critical to system security (like MTTL password, NOT the user s primary password), and data hashes that are considered sensitive enough to be stored in a keystore rather than a normal file or SharedPreferences Hardware-Based Constructors Called None Methods Called java.security.keystore.getinstance(string) java.security.keystore.load(inputstream, char[]) java.security.keystore.getentry(string, null); java.security.keypairgenerator.getinstance(string, String) Objects Created java.security.keystore java.security.keystore.privatekeyentry java.security.keystore.entry java.security.publickey java.security.privatekey java.security.keypairgenerator Trivalent Proprietary Information 29
34 Exceptions Handled java.security.keystoreexception java.security.cert.certificateexception java.security.nosuchalgorithmexception java.security.unrecoverableentryexception java.security.nosuchproviderexception java.security.invalidalgorithmparameterexception File-Based Android Security API Reference Constructors Called java.security.spec.rsaprivatekeyspec.ctor(biginteger, BigInteger) java.security.spec.x509encodedkeyspec.ctor(byte[]) Methods Called java.security.keystore.getinstance(string, Provider) java.security.security.getprovider(string) java.security.keystore.load(inputstream, char[]) java.security.keystore.store(outputstream, char[]) java.security.keystore.aliases() java.security.keystore.getcertificate(string) java.security.keystore.setkeyentry(string, Key, char[], Certificate[]) java.security.keyfactory.getinstance(string, String) java.security.keyfactory.getinstance(string) java.security.keyfactory.generateprivate(keyspec) java.security.keyfactory.generatepublic(keyspec) javax.crypto.mac.getinstance(string) javax.crypto.mac.getmaclength() javax.crypto.mac.getalgorithm() javax.crypto.mac.init(key) javax.crypto.mac.update(byte[]) javax.crypto.mac.dofinal(byte[], int) java.security.messagedigest.getinstance(string) java.security.messagedigest.digest(byte[]) java.security.keystore.getkey(string, char[]) Objects Created java.security.keystore java.security.publickey java.security.privatekey java.security.keyfactory java.security.spec.rsaprivatekeyspec java.security.cert.x509certificate javax.crypto.mac java.security.messagedigest java.security.key java.security.secretkey Trivalent Proprietary Information 30
35 java.security.spec.x509encodedkeyspec Android Security API Reference Exceptions Handled java.security.keystoreexception java.security.cert.certificateexception java.security.nosuchalgorithmexception Data Protection SDK Library Cryptographic Hashing Constructors Called None Methods Called java.security.messagedigest.getinstance(string) java.security.messagedigest.digest(byte[]) android.content.pm.signature.tobytearray() java.security.cert.certificatefactory.getinstance(string) java.security.cert.certificatefactory.generatecertificate(byte[]) Objects Created java.security.messagedigest android.content.pm.signature java.security.cert.certficatefactory java.security.cert.x509certificate Exceptions Handled java.security.nosuchalgorithmexception java.security.cert.certificateexception java.security.cert.certificateencodingexception Hardware-based RSA Key Pair Generation Constructors Called android.security.keypairgeneratorspec.builder.ctor(context) javax.security.auth.x500.x500principal.ctor(string) Methods Called java.security.keystore.getinstance(string) java.security.keystore.load(inputstream, char[]) java.security.keystore.getentry(string, KeyStore.ProtectionParameter); Trivalent Proprietary Information 31
36 Android Security API Reference java.security.keypairgenerator.getinstance(string, String) android.security.keypairgeneratorspec.builder.setalias(string) android.security.keypairgeneratorspec.builder.setstartdate(date) android.security.keypairgeneratorspec.builder.setenddate(date) android.security.keypairgeneratorspec.builder.setserialnumber(biginteger) android.security.keypairgeneratorspec.builder.setsubject(x500principal) android.security.keypairgeneratorspec.builder.build() java.security.keypairgenerator.initialize(algorithmparameterspec) java.security.keypairgenerator.generatekeypair() java.security.keystore.privatekeyentry.getcertificate() java.security.certificate.getpublickey() java.security.keystore.privatekeyentry.getprivatekey() Objects Created java.security.keystore java.security.keystore.privatekeyentry java.security.keystore.entry java.security.keypairgenerator android.security.keypairgeneratorspec android.security.keypairgeneratorspec.builder javax.security.auth.x500.x500principal java.security.keypair java.security.publickey java.security.privatekey java.security.cert.certificate Exceptions Handled java.security.keystoreexception java.security.cert.certificateexception java.security.nosuchalgorithmexception java.security.unrecoverableentryexception java.security.nosuchproviderexception java.security.invalidalgorithmparameterexception Key Unwrapping Unwrapping [FEKEK]HWB_RSA_App Constructors Called javax.crypto.spec.secretkeyspec.ctor(byte[], int, int, String) Methods Called java.security.messagedigest.getinstance(string) java.security.key.getencoded() javax.crypto.cipher.getinstance(string) java.security.keystore.getinstance(string) java.security.keystore.load(keystore.loadstoreparameter) Trivalent Proprietary Information 32
37 java.security.interfaces.rsakey.getmodulus() javax.crypto.cipher.init(int, Key) javax.crypto.cipher.dofinal(byte[], int, int) Android Security API Reference Objects Created javax.crypto.cipher java.security.keystore java.security.secretkey java.security.privatekey java.security.interfaces.rsakey java.security.key Exceptions Handled java.security.nosuchalgorithmexception javax.crypto.nosuchpaddingexception java.security.keystoreexception java.security.certificateexception java.security.invalidkeyexception javax.crypto.illegalblocksizeexception javax.crypto.badpaddingexception Keystores and Key Storage Hardware-Based Constructors Called None Methods Called java.security.keystore.getinstance(string) java.security.keystore.load(inputstream, char[]) java.security.keystore.getentry(string, null); java.security.keypairgenerator.getinstance(string, String) Objects Created java.security.keystore java.security.keystore.privatekeyentry java.security.keystore.entry java.security.publickey java.security.privatekey java.security.keypairgenerator Exceptions Handled java.security.keystoreexception java.security.cert.certificateexception java.security.nosuchalgorithmexception java.security.unrecoverableentryexception java.security.nosuchproviderexception java.security.invalidalgorithmparameterexception Trivalent Proprietary Information 33
38 File-Based Permissions Used Constructors Called Nones Methods Called java.security.keystore.getinstance(string, Provider) java.security.security.getprovider(string) java.security.keystore.load(inputstream, char[]) java.security.keystore.aliases() java.security.keystore.getkey(string, char[]) Objects Created java.security.keystore java.security.key java.security.secretkey Exceptions Handled java.security.keystoreexception java.security.cert.certificateexception java.security.nosuchalgorithmexception 4 Permissions Used Management Service The Management Service uses the following Android permissions: WRITE_EXTERNAL_STORAGE READ_EXTERNAL_STORAGE READ_LOGS USE_CREDENTIALS WAKE_LOCK RECEIVE_BOOT_COMPLETED GET_TASKS REORDER_TASKS INTERNET Data Protection SDK Library The library component (that applications consume) uses the following Android permissions: WRITE_EXTERNAL_STORAGE READ_EXTERNAL_STORAGE READ_LOGS USE_CREDENTIALS Trivalent Proprietary Information 34
39 5. Frequently Asked Questions Question What types of Android devices is the TMS compatible with? How are my encrypted files stored? What is Mission Time to Live? Can I configure MTTL without having an extendable duration? Why is a password needed to extend MTTL? Why do I need to authenticate multiple times in a row after starting the Trivalent Management Service? I never received the Application Registration prompt after starting my integrated app. How do I get it? I unlocked my Android Device and did not get the authentication popup. How do I authenticate? If I do not enter my password then close the Authentication window, will I still be able to use my device? Answer Frequently Asked Questions Any Android device running Android 5.0, 5.1, or 6.0 is supported Files are first encrypted using AES 256 bit encryption. The encrypted file is then parsed using a proprietary Information Dispersal Algorithm to define shredding rules and to store the shreds securely. MTTL refers to a configurable timer for encrypted files. Once the timer expires, all encrypted files will become inaccessible. MTTL is set by an initial duration, and has the option to be extended once. Yes A password is needed in order to prevent unauthorized users of the EUD from having access to sensitive data if the device is lost. The first authentication starts the mission. Each integrated application also needs to be authenticated. The app-specific authentication only happens once per mission. After these steps in completing and validating the configuration, users will only be prompted to authenticate based on the configured parameters. You may need to close and restart the integrated app. Press and hold the device s home button until the app switcher appears. Next, locate the integrated app and swipe it left or right until it disappears. Next, reopen the integrated app and look for the Application Registration notification at the top (or swiping down to bring up the notification panel). If no message appears, try reconfiguring your device and repeating this process. If the authentication popup is accidently missed or dismissed, swipe down from the top of the Android device to reveal the Android Notification Menu. In the menu will be a notification reading Not Authenticated. Tap on this notification to bring back the authentication popup. Yes, but you will not be allowed to access encrypted files. Trivalent Proprietary Information 35
40 Question Will the TMS notify me when a lockout is over? When will I be able to extend my mission? Why do I keep getting a Password Mismatch when I try changing the password on my device? I just restarted my Android device and noticed the TMS notifications were gone. Did the service turn off? Where can I get additional Help Information? Answer No Frequently Asked Questions (If applicable) the option to extend a mission will be available once x% of the mission time remains. This is determined based upon the mission duration. Make sure the fields are an exact match. Remember that passwords are case sensitive. No, restarting the phone only clears the notifications. Launching the and authenticating will bring back the notifications. Trivalent Support can be contacted at support@trivalent.us.com or visit our website at Trivalent Proprietary Information 36
USER GUIDE. Trivalent Protect 2.6 for Android
 USER GUIDE NOVEMBER 2017 Table of Contents Table of Contents 1. General Information... 1 1.1. Introduction... 1 1.2. Description... 1 1.3. Benefits & Value... 1 1.4. Platform Requirements... 1 1.5. Application
USER GUIDE NOVEMBER 2017 Table of Contents Table of Contents 1. General Information... 1 1.1. Introduction... 1 1.2. Description... 1 1.3. Benefits & Value... 1 1.4. Platform Requirements... 1 1.5. Application
EasiShare ios User Guide
 Copyright 06 Inspire-Tech Pte Ltd. All Rights Reserved. Page of 44 Copyright 06 by Inspire-Tech Pte Ltd. All rights reserved. All trademarks or registered trademarks mentioned in this document are properties
Copyright 06 Inspire-Tech Pte Ltd. All Rights Reserved. Page of 44 Copyright 06 by Inspire-Tech Pte Ltd. All rights reserved. All trademarks or registered trademarks mentioned in this document are properties
Cipher Suite Configuration Mode Commands
 The Cipher Suite Configuration Mode is used to configure the building blocks for SSL cipher suites, including the encryption algorithm, hash function, and key exchange. Important The commands or keywords/variables
The Cipher Suite Configuration Mode is used to configure the building blocks for SSL cipher suites, including the encryption algorithm, hash function, and key exchange. Important The commands or keywords/variables
Defending Against the Sneakers Scenario. Bryan Sullivan, Security Program Manager, Microsoft SDL
 Defending Against the Sneakers Scenario Bryan Sullivan, Security Program Manager, Microsoft SDL Crypto systems get broken eh be sure vxuh to wr drink gulqn your brxu rydowlqh ovaltine Why assume that current
Defending Against the Sneakers Scenario Bryan Sullivan, Security Program Manager, Microsoft SDL Crypto systems get broken eh be sure vxuh to wr drink gulqn your brxu rydowlqh ovaltine Why assume that current
NotifySync 4.7. Notify Technology Corporation
 1 NotifySync 4.7 Notify Technology Corporation Device Requirements 2 BlackBerry OS 4.1 4.7 (5.0 coming soon) 4.5.0 and later Attachments can be downloaded and saved to the file system or SD Card. Any attachment
1 NotifySync 4.7 Notify Technology Corporation Device Requirements 2 BlackBerry OS 4.1 4.7 (5.0 coming soon) 4.5.0 and later Attachments can be downloaded and saved to the file system or SD Card. Any attachment
AT&T Global Network Client for Android
 Version 4.1.0 AT&T Global Network Client for Android 2016 AT&T Intellectual Property. All rights reserved. AT&T, the AT&T logo and all other AT&T marks contained herein are trademarks of AT&T Intellectual
Version 4.1.0 AT&T Global Network Client for Android 2016 AT&T Intellectual Property. All rights reserved. AT&T, the AT&T logo and all other AT&T marks contained herein are trademarks of AT&T Intellectual
Rev X 341. Table 111. Access Levels and Descriptions
 9424200994 Rev X 341 Multiple levels of security give personnel the level of access appropriate for the tasks they routinely perform while securing critical settings from unauthorized access. Access Levels
9424200994 Rev X 341 Multiple levels of security give personnel the level of access appropriate for the tasks they routinely perform while securing critical settings from unauthorized access. Access Levels
Salesforce1 Mobile Security White Paper. Revised: April 2014
 Salesforce1 Mobile Security White Paper Revised: April 2014 Table of Contents Introduction Salesforce1 Architecture Overview Authorization and Permissions Communication Security Authentication OAuth Pairing
Salesforce1 Mobile Security White Paper Revised: April 2014 Table of Contents Introduction Salesforce1 Architecture Overview Authorization and Permissions Communication Security Authentication OAuth Pairing
GigaCentral ios User Guide V2.0. For User and Storage Admin
 V2.0 For User and Storage Admin Copyright 2018 by Inspire-Tech Pte Ltd. All rights reserved. All trademarks or registered trademarks mentioned in this document are properties of their respective owners.
V2.0 For User and Storage Admin Copyright 2018 by Inspire-Tech Pte Ltd. All rights reserved. All trademarks or registered trademarks mentioned in this document are properties of their respective owners.
Progressive Authentication in ios
 Progressive Authentication in ios Genghis Chau, Denis Plotnikov, Edwin Zhang December 12 th, 2014 1 Overview In today s increasingly mobile-centric world, more people are beginning to use their smartphones
Progressive Authentication in ios Genghis Chau, Denis Plotnikov, Edwin Zhang December 12 th, 2014 1 Overview In today s increasingly mobile-centric world, more people are beginning to use their smartphones
Pass, No Record: An Android Password Manager
 Pass, No Record: An Android Password Manager Alex Konradi, Samuel Yeom December 4, 2015 Abstract Pass, No Record is an Android password manager that allows users to securely retrieve passwords from a server
Pass, No Record: An Android Password Manager Alex Konradi, Samuel Yeom December 4, 2015 Abstract Pass, No Record is an Android password manager that allows users to securely retrieve passwords from a server
EUCEG: Encryption process
 EUROPEAN COMMISSION DIRECTORATE-GENERAL FOR HEALTH AND FOOD SAFETY General Affairs Information systems EUCEG: Encryption process Document Control Information Settings Document Title: Project Title: Document
EUROPEAN COMMISSION DIRECTORATE-GENERAL FOR HEALTH AND FOOD SAFETY General Affairs Information systems EUCEG: Encryption process Document Control Information Settings Document Title: Project Title: Document
10.User Password and Object Security
 10-1 10.User Password and Object Security This chapter discusses the protection for operations provided by setting up user passwords and security classes. 10.1. Overview... 10-2 10.2. User Password and
10-1 10.User Password and Object Security This chapter discusses the protection for operations provided by setting up user passwords and security classes. 10.1. Overview... 10-2 10.2. User Password and
PayKings iprocess Setup Guide for Android Devices
 PayKings iprocess Setup Guide for Android Devices Contents: iprocess account setup 2 Installing iprocess on your Android device 3 Configuring the iprocess app 8 Attaching the iprocess card reader 10 Processing
PayKings iprocess Setup Guide for Android Devices Contents: iprocess account setup 2 Installing iprocess on your Android device 3 Configuring the iprocess app 8 Attaching the iprocess card reader 10 Processing
FIPS Non-Proprietary Security Policy. Level 1 Validation Version 1.2
 Oracle Solaris Kernel Cryptographic Framework with SPARC T4 and T5 Software Version: 1.0 and 1.1; Hardware Version: SPARC T4 (527-1437-01) and T5 (7043165) FIPS 140-2 Non-Proprietary Security Policy Level
Oracle Solaris Kernel Cryptographic Framework with SPARC T4 and T5 Software Version: 1.0 and 1.1; Hardware Version: SPARC T4 (527-1437-01) and T5 (7043165) FIPS 140-2 Non-Proprietary Security Policy Level
Oracle Solaris Kernel Cryptographic Framework Software Version 1.0 and 1.1
 Oracle Solaris Kernel Cryptographic Framework Software Version 1.0 and 1.1 FIPS 140-2 Non-Proprietary Security Policy Level 1 Validation Version 1.2 12/12/2013 Copyright 2013 Oracle Corporation Table of
Oracle Solaris Kernel Cryptographic Framework Software Version 1.0 and 1.1 FIPS 140-2 Non-Proprietary Security Policy Level 1 Validation Version 1.2 12/12/2013 Copyright 2013 Oracle Corporation Table of
IRONKEY D300S SECURE USB 3.0 FLASH DRIVE
 IRONKEY D300S SECURE USB 3.0 FLASH DRIVE User Guide Document No. 48000130-001.A01 D300S Page 1 of 27 Table of Contents About This Manual... 3 System Requirements...3 Recommendations...3 Setup (Windows
IRONKEY D300S SECURE USB 3.0 FLASH DRIVE User Guide Document No. 48000130-001.A01 D300S Page 1 of 27 Table of Contents About This Manual... 3 System Requirements...3 Recommendations...3 Setup (Windows
This Security Policy describes how this module complies with the eleven sections of the Standard:
 Vormetric, Inc Vormetric Data Security Server Module Firmware Version 4.4.1 Hardware Version 1.0 FIPS 140-2 Non-Proprietary Security Policy Level 2 Validation May 24 th, 2012 2011 Vormetric Inc. All rights
Vormetric, Inc Vormetric Data Security Server Module Firmware Version 4.4.1 Hardware Version 1.0 FIPS 140-2 Non-Proprietary Security Policy Level 2 Validation May 24 th, 2012 2011 Vormetric Inc. All rights
AT&T Business Messaging Account Management
 Account Management Administrator User Guide July 2016 1 Copyright 2016 AT&T Intellectual Property. All rights reserved. AT&T, the AT&T logo and all other AT&T marks contained herein are trademarks of AT&T
Account Management Administrator User Guide July 2016 1 Copyright 2016 AT&T Intellectual Property. All rights reserved. AT&T, the AT&T logo and all other AT&T marks contained herein are trademarks of AT&T
Android User Guide. for version 5.3
 Android User Guide for version 5.3 Contents 1. Installation... 3 1.1. How to install Babelnet... 3 1.2. Enter Babelnet in the search field.... 3 1.3. Safety precautions when using Babelnet on your Android...
Android User Guide for version 5.3 Contents 1. Installation... 3 1.1. How to install Babelnet... 3 1.2. Enter Babelnet in the search field.... 3 1.3. Safety precautions when using Babelnet on your Android...
Configuring SSL. SSL Overview CHAPTER
 7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
7 CHAPTER This topic describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section are:
Production Assistance for Cellular Therapies (PACT) PACT Application System User s Guide
 Production Assistance for Cellular Therapies (PACT) PACT Application System User s Guide Version 1.0 February 9, 2017 Version 1.0 TABLE OF CONTENTS 1.0 Getting Started... 1 1.1 Access to the Internet...
Production Assistance for Cellular Therapies (PACT) PACT Application System User s Guide Version 1.0 February 9, 2017 Version 1.0 TABLE OF CONTENTS 1.0 Getting Started... 1 1.1 Access to the Internet...
Once a USB drive has been inserted into an encrypted machine, the Dell Data Protection software will recognize the unencrypted device.
 Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
The question paper contains 40 multiple choice questions with four choices and students will have to pick the correct one (each carrying ½ marks.).
 Time: 3hrs BCA III Network security and Cryptography Examination-2016 Model Paper 2 M.M:50 The question paper contains 40 multiple choice questions with four choices and students will have to pick the
Time: 3hrs BCA III Network security and Cryptography Examination-2016 Model Paper 2 M.M:50 The question paper contains 40 multiple choice questions with four choices and students will have to pick the
IdeaTab A1000L-F. User Guide V1.0. Please read the Important safety and handling information in the supplied manuals before use.
 IdeaTab A1000L - UserGuide IdeaTab A1000L-F User Guide V1.0 Please read the Important safety and handling information in the supplied manuals before use. file:///c /Users/xieqy1/Desktop/EN UG/index.html[2013/8/14
IdeaTab A1000L - UserGuide IdeaTab A1000L-F User Guide V1.0 Please read the Important safety and handling information in the supplied manuals before use. file:///c /Users/xieqy1/Desktop/EN UG/index.html[2013/8/14
Beginner's Tutorial. How to Create and Use a TrueCrypt Container
 Beginner's Tutorial How to Create and Use a TrueCrypt Container This chapter contains step-by-step instructions on how to create, mount, and use a TrueCrypt volume. We strongly recommend that you also
Beginner's Tutorial How to Create and Use a TrueCrypt Container This chapter contains step-by-step instructions on how to create, mount, and use a TrueCrypt volume. We strongly recommend that you also
Configuring SSL. SSL Overview CHAPTER
 CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
CHAPTER 8 Date: 4/23/09 This topic describes the steps required to configure your ACE (both the ACE module and the ACE appliance) as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination.
Configuring the Cisco APIC-EM Settings
 Logging into the Cisco APIC-EM, page 1 Quick Tour of the APIC-EM Graphical User Interface (GUI), page 2 Configuring the Prime Infrastructure Settings, page 3 Discovery Credentials, page 4 Security, page
Logging into the Cisco APIC-EM, page 1 Quick Tour of the APIC-EM Graphical User Interface (GUI), page 2 Configuring the Prime Infrastructure Settings, page 3 Discovery Credentials, page 4 Security, page
CMS Enterprise Portal User Manual
 Centers for Medicare & Medicaid Services CMS expedited Life Cycle (XLC) 11/13/2017 Document Number: Enterprise_Portal_User_Manual_v6 Table of Contents Table of Contents 1. Introduction... 1 2. Overview...
Centers for Medicare & Medicaid Services CMS expedited Life Cycle (XLC) 11/13/2017 Document Number: Enterprise_Portal_User_Manual_v6 Table of Contents Table of Contents 1. Introduction... 1 2. Overview...
Secret-in.me. A pentester design of password secret manager
 Secret-in.me A pentester design of password secret manager Who am I? Security engineer Working at SCRT France! Password manager Password A string Secret Information shared by very few people You have to
Secret-in.me A pentester design of password secret manager Who am I? Security engineer Working at SCRT France! Password manager Password A string Secret Information shared by very few people You have to
The following device commands are used most frequently: Lock/Unlock device O - O O. Reset screen password O - O - Factory reset + Initialize SD Card
 10 Device management Administrators can install apps on an activated device using device commands and check the profiles settings. Moreover, they can update, delete, or re-install apps installed on users'
10 Device management Administrators can install apps on an activated device using device commands and check the profiles settings. Moreover, they can update, delete, or re-install apps installed on users'
Demonstration Instructions
 Demonstration Instructions Digital Defence Ltd. Secure Mobile Version 10.2.1 19 th July 2010 Table of Contents TABLE OF CONTENTS... 2 1. DEMONSTRATION INSTRUCTIONS... 3 1.1 PREREQUISITES... 3 1.2 PROCEDURE...
Demonstration Instructions Digital Defence Ltd. Secure Mobile Version 10.2.1 19 th July 2010 Table of Contents TABLE OF CONTENTS... 2 1. DEMONSTRATION INSTRUCTIONS... 3 1.1 PREREQUISITES... 3 1.2 PROCEDURE...
NotifyMDM Device Application User Guide Installation and Configuration for Android
 NotifyMDM Device Application User Guide Installation and Configuration for Android NotifyMDM for Android, Version 3.x NotifyMDM for Android 1 Table of Contents NotifyMDM for Android 3 Installation Instructions
NotifyMDM Device Application User Guide Installation and Configuration for Android NotifyMDM for Android, Version 3.x NotifyMDM for Android 1 Table of Contents NotifyMDM for Android 3 Installation Instructions
Configuring SSL CHAPTER
 7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
7 CHAPTER This chapter describes the steps required to configure your ACE appliance as a virtual Secure Sockets Layer (SSL) server for SSL initiation or termination. The topics included in this section
CardNav by CO-OP 3.0. Quick Reference Guide. CO-OP Financial Services
 CardNav by CO-OP 3.0 Quick Reference Guide CO-OP Financial Services TABLE OF CONTENTS Getting Started Installing and Upgrading Contents Logging in to the App Navigating the App Viewing Card Information
CardNav by CO-OP 3.0 Quick Reference Guide CO-OP Financial Services TABLE OF CONTENTS Getting Started Installing and Upgrading Contents Logging in to the App Navigating the App Viewing Card Information
BitLocker Group Policy Settings
 BitLocker Group Policy Settings Updated: September 13, 2013 Applies To: Windows 8, Windows 8.1, Windows Server 2012, Windows Server 2012 R2 This reference topic for the IT professional describes the function,
BitLocker Group Policy Settings Updated: September 13, 2013 Applies To: Windows 8, Windows 8.1, Windows Server 2012, Windows Server 2012 R2 This reference topic for the IT professional describes the function,
USER GUIDE GigaCentral Android User Guide
 USER GUIDE GigaCentral Android User Guide Copyright 2016 by Inspire-Tech Pte Ltd. All rights reserved. All trademarks or registered trademarks mentioned in this document are properties of their respective
USER GUIDE GigaCentral Android User Guide Copyright 2016 by Inspire-Tech Pte Ltd. All rights reserved. All trademarks or registered trademarks mentioned in this document are properties of their respective
Electronic Submission System User procedures document MAY 2018
 Electronic Submission System User procedures document MAY 2018 Electronic Submission System User Guide 1 What s new? This user guide was updated in May 2018 to include recent changes to the Electronic
Electronic Submission System User procedures document MAY 2018 Electronic Submission System User Guide 1 What s new? This user guide was updated in May 2018 to include recent changes to the Electronic
Barracuda Networks Android Mobile Application
 This article refers to the Barracuda Networks Android Mobile App version 1.2.0.0131 or greater, on an Android mobile phone devices running Android 4.1 or greater. Download the latest Barracuda Networks
This article refers to the Barracuda Networks Android Mobile App version 1.2.0.0131 or greater, on an Android mobile phone devices running Android 4.1 or greater. Download the latest Barracuda Networks
AT&T Global Network Client for Mac User s Guide Version 1.7.3
 Version 1.7.0 AT&T Global Network Client for Mac User s Guide Version 1.7.3 experience may vary. This document is not an offer, commitment, representation or warranty by AT&T and is subject to change..
Version 1.7.0 AT&T Global Network Client for Mac User s Guide Version 1.7.3 experience may vary. This document is not an offer, commitment, representation or warranty by AT&T and is subject to change..
Encrypt Data (QC3ENCDT, Qc3EncryptData) API
 Page 1 of 16 Encrypt Data (QC3ENCDT, Qc3EncryptData) API Required Parameter Group: 1 Clear data Input Char(*) 2 Length of clear data Input Binary(4) 3 Clear data format name Input Char(8) 4 Algorithm description
Page 1 of 16 Encrypt Data (QC3ENCDT, Qc3EncryptData) API Required Parameter Group: 1 Clear data Input Char(*) 2 Length of clear data Input Binary(4) 3 Clear data format name Input Char(8) 4 Algorithm description
Mobile Banking App User s Guide
 Mobile Banking App User s Guide Enrollment Enroll Using Online Banking 1. Log in to your Online Banking account at easternmichiganbank.com. 2. Go to Options > Mobile Settings > Web Mobile Settings. 3.
Mobile Banking App User s Guide Enrollment Enroll Using Online Banking 1. Log in to your Online Banking account at easternmichiganbank.com. 2. Go to Options > Mobile Settings > Web Mobile Settings. 3.
Registering a Card and Creating an Account on
 Installing MyCardRules The MyCardRules App is available for both iphones and Android phones. To install MyCardRules: 1. Search for the app in the App Store or on Google Play. 2. Follow the instructions
Installing MyCardRules The MyCardRules App is available for both iphones and Android phones. To install MyCardRules: 1. Search for the app in the App Store or on Google Play. 2. Follow the instructions
SecureDoc Disk Encryption Cryptographic Engine
 SecureDoc Disk Encryption Cryptographic Engine Security Policy Abstract: This document specifies Security Policy enforced by the SecureDoc Cryptographic Engine compliant with the requirements of FIPS 140-2
SecureDoc Disk Encryption Cryptographic Engine Security Policy Abstract: This document specifies Security Policy enforced by the SecureDoc Cryptographic Engine compliant with the requirements of FIPS 140-2
GEORGIA SOFTWORKS. February 15, GSW ConnectBot Android Client for SSH/Telnet. GSW ConnectBot. Users Guide
 GEORGIA SOFTWORKS February 15, 2018 GSW ConnectBot Android Client for SSH/Telnet GSW ConnectBot Users Guide THIS PAGE INTENTIONALLY LEFT BLANK ii GEORGIA SOFTWORKS February 15, 2018 Georgia SoftWorks Public
GEORGIA SOFTWORKS February 15, 2018 GSW ConnectBot Android Client for SSH/Telnet GSW ConnectBot Users Guide THIS PAGE INTENTIONALLY LEFT BLANK ii GEORGIA SOFTWORKS February 15, 2018 Georgia SoftWorks Public
Configuring Secure Socket Layer HTTP
 This feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS software. SSL provides server authentication, encryption, and message integrity
This feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS software. SSL provides server authentication, encryption, and message integrity
Refund Selection Single Sign On
 BankMobile Refund Selection Single Sign On OVERVIEW The BankMobile Refund Selection Single Sign-On (SSO) solution will offer an integrated user authentication system for students to make their initial
BankMobile Refund Selection Single Sign On OVERVIEW The BankMobile Refund Selection Single Sign-On (SSO) solution will offer an integrated user authentication system for students to make their initial
Configuring Secure Socket Layer HTTP
 This feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS software. SSL provides server authentication, encryption, and message integrity
This feature provides Secure Socket Layer (SSL) version 3.0 support for the HTTP 1.1 server and HTTP 1.1 client within Cisco IOS software. SSL provides server authentication, encryption, and message integrity
SECURE INTEGRATION OF CRYPTOGRAPHIC SOFTWARE
 SECURE INTEGRATION OF CRYPTOGRAPHIC SOFTWARE Speaker: Stefan Krüger Folie 1 When a Developer Uses a Crypto API Uses Electronic Codebook (ECB) Folie 2 The Average Developer is no Crypto Expert 88% of Android
SECURE INTEGRATION OF CRYPTOGRAPHIC SOFTWARE Speaker: Stefan Krüger Folie 1 When a Developer Uses a Crypto API Uses Electronic Codebook (ECB) Folie 2 The Average Developer is no Crypto Expert 88% of Android
DSS User Guide. End User Guide. - i -
 DSS User Guide End User Guide - i - DSS User Guide Table of Contents End User Guide... 1 Table of Contents... 2 Part 1: Getting Started... 1 How to Log in to the Web Portal... 1 How to Manage Account Settings...
DSS User Guide End User Guide - i - DSS User Guide Table of Contents End User Guide... 1 Table of Contents... 2 Part 1: Getting Started... 1 How to Log in to the Web Portal... 1 How to Manage Account Settings...
Calendar & Buttons Dashboard Menu Features My Profile My Favorites Watch List Adding a New Request...
 remitview User Guide 1 TABLE OF CONTENTS INTRODUCTION... 3 Calendar & Buttons... 3 GETTING STARTED.... 5 Dashboard.... 7 Menu Features... 8 PROFILE.... 10 My Profile... 10 My Favorites... 12 Watch List...
remitview User Guide 1 TABLE OF CONTENTS INTRODUCTION... 3 Calendar & Buttons... 3 GETTING STARTED.... 5 Dashboard.... 7 Menu Features... 8 PROFILE.... 10 My Profile... 10 My Favorites... 12 Watch List...
Payment Solutions MyCardRules. MyCardRules Mobile App. User Guide. Release 3.1
 Payment Solutions November 27, 2017 Installing MyCardRules... 2 Registering a Card and Creating an Account on MyCardRules... 2 Logging In to MyCardRules... 2 Registering a Card... 3 Creating an Account...
Payment Solutions November 27, 2017 Installing MyCardRules... 2 Registering a Card and Creating an Account on MyCardRules... 2 Logging In to MyCardRules... 2 Registering a Card... 3 Creating an Account...
Recipient USER GUIDE
 Recipient USER GUIDE General Information What is smartmail? smartmail is smartview s proprietary email encryption system used to protect your personal and transaction related information. What is smartportal?
Recipient USER GUIDE General Information What is smartmail? smartmail is smartview s proprietary email encryption system used to protect your personal and transaction related information. What is smartportal?
Salesforce Classic Guide for iphone
 Salesforce Classic Guide for iphone Version 35.0, Winter 16 @salesforcedocs Last updated: October 27, 2015 Copyright 2000 2015 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
Salesforce Classic Guide for iphone Version 35.0, Winter 16 @salesforcedocs Last updated: October 27, 2015 Copyright 2000 2015 salesforce.com, inc. All rights reserved. Salesforce is a registered trademark
Oracle Solaris Userland Cryptographic Framework Software Version 1.0 and 1.1
 Oracle Solaris Userland Cryptographic Framework Software Version 1.0 and 1.1 FIPS 140-2 Non-Proprietary Security Policy Level 1 Validation Version 1.3 2014-01-08 Copyright 2014 Oracle Corporation Table
Oracle Solaris Userland Cryptographic Framework Software Version 1.0 and 1.1 FIPS 140-2 Non-Proprietary Security Policy Level 1 Validation Version 1.3 2014-01-08 Copyright 2014 Oracle Corporation Table
Android U S E R M A N U A L
 Android USER MANUAL TABLE OF CONTENTS 1. SYSTEM REQUIREMENTS...1 2. GETTING STARTED...1 3. USING THE ACCESSIBILITY MODES...1 3.1. Using Hands-free Mode... 1 3.1.1 Performing Swipe Action... 2 3.1.2 Performing
Android USER MANUAL TABLE OF CONTENTS 1. SYSTEM REQUIREMENTS...1 2. GETTING STARTED...1 3. USING THE ACCESSIBILITY MODES...1 3.1. Using Hands-free Mode... 1 3.1.1 Performing Swipe Action... 2 3.1.2 Performing
Creating Trust in a Highly Mobile World
 Creating Trust in a Highly Mobile World Technical White Paper Oct, 2014 MobileCrypt with Hardware Strength Security MobileCrypt s solution leverages an Android based mobile application and a Hardware Security
Creating Trust in a Highly Mobile World Technical White Paper Oct, 2014 MobileCrypt with Hardware Strength Security MobileCrypt s solution leverages an Android based mobile application and a Hardware Security
TABLE OF CONTENTS 1 INTRO
 TABLE OF CONTENTS 1 INTRO 4 2 GETTING STARTED 5 2.1 CREATING AN ACCOUNT 2.1.1 ENTERING ACCOUNT INFORMATION 2.1.2 SELECTING A PLAN 2.1.3 ENTERING PAYMENT INFORMATION 2.1.4 REVIEW AND CONFIRM 2.2 LOGGING
TABLE OF CONTENTS 1 INTRO 4 2 GETTING STARTED 5 2.1 CREATING AN ACCOUNT 2.1.1 ENTERING ACCOUNT INFORMATION 2.1.2 SELECTING A PLAN 2.1.3 ENTERING PAYMENT INFORMATION 2.1.4 REVIEW AND CONFIRM 2.2 LOGGING
MarkzTools2 User Guide Markzware
 MarkzTools2 User Guide 2017 Markzware MarkzTools2 Table of Contents MarkzTools2 System Requirements... 3 MarkzTools2 Subscription License Model... 4 Installing MarkzTools2 on your Mac... 5 Running MarkzTools2
MarkzTools2 User Guide 2017 Markzware MarkzTools2 Table of Contents MarkzTools2 System Requirements... 3 MarkzTools2 Subscription License Model... 4 Installing MarkzTools2 on your Mac... 5 Running MarkzTools2
Regions OnePassSM USER GUIDE. It s time to expect more. Regions Bank Member FDIC Revised
 Regions OnePassSM USER GUIDE Regions Bank Member FDIC Revised 110614 It s time to expect more. Regions OnePass User Guide Table of Contents Section I. OnePass Basics 3 What Is OnePass? 3 Minimum Browser
Regions OnePassSM USER GUIDE Regions Bank Member FDIC Revised 110614 It s time to expect more. Regions OnePass User Guide Table of Contents Section I. OnePass Basics 3 What Is OnePass? 3 Minimum Browser
Salesforce Classic Mobile Guide for iphone
 Salesforce Classic Mobile Guide for iphone Version 41.0, Winter 18 @salesforcedocs Last updated: November 30, 2017 Copyright 2000 2017 salesforce.com, inc. All rights reserved. Salesforce is a registered
Salesforce Classic Mobile Guide for iphone Version 41.0, Winter 18 @salesforcedocs Last updated: November 30, 2017 Copyright 2000 2017 salesforce.com, inc. All rights reserved. Salesforce is a registered
MANAGING LOCAL AUTHENTICATION IN WINDOWS
 MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
MANAGING LOCAL AUTHENTICATION IN WINDOWS Credentials Manager Windows OS has a set of tools that help remedy some of the authentication challenges. For example, the Credential Manager in Windows 7 and newer
NOTE: This setting is applicable only for local users.
 How do I better user access security in NetScaler MAS? NetScaler Management and Analytics System is a centralized network management, analytics, and orchestration solution. From a single platform, administrators
How do I better user access security in NetScaler MAS? NetScaler Management and Analytics System is a centralized network management, analytics, and orchestration solution. From a single platform, administrators
The Linux Kernel Cryptographic API
 Published on Linux Journal (http://www.linuxjournal.com) The Linux Kernel Cryptographic API By James Morris Created 2003-04-01 02:00 This article provides a brief overview of the new cryptographic API
Published on Linux Journal (http://www.linuxjournal.com) The Linux Kernel Cryptographic API By James Morris Created 2003-04-01 02:00 This article provides a brief overview of the new cryptographic API
Frequently Asked Questions: Cisco Jabber Voice 9.1(4) for Android
 Frequently Asked Questions Frequently Asked Questions: Cisco Jabber Voice 9.1(4) for Android FAQs 2 Setup 2 Basics 4 Connectivity 8 Calls 9 Contacts and Directory Search 16 Voicemail 17 Recents 22 Feedback
Frequently Asked Questions Frequently Asked Questions: Cisco Jabber Voice 9.1(4) for Android FAQs 2 Setup 2 Basics 4 Connectivity 8 Calls 9 Contacts and Directory Search 16 Voicemail 17 Recents 22 Feedback
Smartphone App. Test Administrator Guide. Version 1.0
 Smartphone App Test Administrator Guide Version 1.0 1. Getting Started... 3 What is Versant?... 3 System Requirements... 3 Test Administrator Checklist... 3 Preparing for Test Administration... 3 Test
Smartphone App Test Administrator Guide Version 1.0 1. Getting Started... 3 What is Versant?... 3 System Requirements... 3 Test Administrator Checklist... 3 Preparing for Test Administration... 3 Test
BAE Systems employee app - installation Guide
 BAE Systems employee app - installation Guide The App was created for BAE Systems for distribution to employees in Saudi Arabia for the delivery of Company related news. It is a proprietary enterprise
BAE Systems employee app - installation Guide The App was created for BAE Systems for distribution to employees in Saudi Arabia for the delivery of Company related news. It is a proprietary enterprise
Juniper Network Connect Cryptographic Module Version 2.0 Security Policy Document Version 1.0. Juniper Networks, Inc.
 Juniper Network Connect Cryptographic Module Version 2.0 Security Policy Document Version 1.0 Juniper Networks, Inc. September 10, 2009 Copyright Juniper Networks, Inc. 2009. May be reproduced only in
Juniper Network Connect Cryptographic Module Version 2.0 Security Policy Document Version 1.0 Juniper Networks, Inc. September 10, 2009 Copyright Juniper Networks, Inc. 2009. May be reproduced only in
Multi-Factor Authentication (MFA)
 What is it? Multi-Factor Authentication, or MFA, is a process that requires more than one type of authentication to gain access to a program. You have probably seen this with your bank or other secure
What is it? Multi-Factor Authentication, or MFA, is a process that requires more than one type of authentication to gain access to a program. You have probably seen this with your bank or other secure
AT&T Global Network Client for Mac User s Guide Version 2.0.0
 Version 1.7.0 AT&T Global Network Client for Mac User s Guide Version 2.0.0 experience may vary. This document is not an offer, commitment, representation or warranty by AT&T and is subject to change..
Version 1.7.0 AT&T Global Network Client for Mac User s Guide Version 2.0.0 experience may vary. This document is not an offer, commitment, representation or warranty by AT&T and is subject to change..
PowerSchool 7.x Student Information System
 PowerSchool 7.x Student Information System Released May 2012 Document Owner: Documentation Services This edition applies to Release 7.2 of the PowerSchool software and to all subsequent releases and modifications
PowerSchool 7.x Student Information System Released May 2012 Document Owner: Documentation Services This edition applies to Release 7.2 of the PowerSchool software and to all subsequent releases and modifications
Application Note. Configuring SSH on Vocality units. Software From V07_04_01. Revision v1.5
 Application Note Configuring SSH on Vocality units Software From V07_04_01 Revision v1.5 Publish Date November 2017 AN309 CONFIGURING SSH SSH requires the Security software (RTUSEC) and a Feature Key on
Application Note Configuring SSH on Vocality units Software From V07_04_01 Revision v1.5 Publish Date November 2017 AN309 CONFIGURING SSH SSH requires the Security software (RTUSEC) and a Feature Key on
UCS Manager Communication Services
 Communication Protocols, page 1 Communication Services, page 1 Non-Secure Communication Services, page 3 Secure Communication Services, page 5 Network-Related Communication Services, page 12 Communication
Communication Protocols, page 1 Communication Services, page 1 Non-Secure Communication Services, page 3 Secure Communication Services, page 5 Network-Related Communication Services, page 12 Communication
Nextiva Drive The Setup Process Mobility & Storage Option
 Nextiva Drive The Setup Process The Setup Process Adding Users 1. Login to your account and click on the Account icon at the top of the page (this is only visible to the administrator). 2. Click Create
Nextiva Drive The Setup Process The Setup Process Adding Users 1. Login to your account and click on the Account icon at the top of the page (this is only visible to the administrator). 2. Click Create
Message Networking 5.2 Administration print guide
 Page 1 of 421 Administration print guide This print guide is a collection of system topics provided in an easy-to-print format for your convenience. Please note that the links shown in this document do
Page 1 of 421 Administration print guide This print guide is a collection of system topics provided in an easy-to-print format for your convenience. Please note that the links shown in this document do
Merchant Online Reporting System (MORS) Login with OTP
 Merchant Online Reporting System (MORS) Login with OTP How to download and use the OTP Generator upon first login 1. Log in to MORS by typing your User ID and Password on the Login page. 2. On the Navigate
Merchant Online Reporting System (MORS) Login with OTP How to download and use the OTP Generator upon first login 1. Log in to MORS by typing your User ID and Password on the Login page. 2. On the Navigate
Table of Contents. Overview. Installing and Using Afaria with your Motorola XOOM End User Document v0.3
 Overview This document will provide you instructions on how to install and use the Afaria client on your Motorola Xoom tablet. The Afaria client is designed to allow applications to be made available to
Overview This document will provide you instructions on how to install and use the Afaria client on your Motorola Xoom tablet. The Afaria client is designed to allow applications to be made available to
IBM Systems and Technology Group
 IBM Systems and Technology Group Encryption Facility for z/os Update Steven R. Hart srhart@us.ibm.com 2013 IBM Corporation Topics Encryption Facility for z/os EF OpenPGP Support X.509 vs. OpenPGP Certificates
IBM Systems and Technology Group Encryption Facility for z/os Update Steven R. Hart srhart@us.ibm.com 2013 IBM Corporation Topics Encryption Facility for z/os EF OpenPGP Support X.509 vs. OpenPGP Certificates
ECHA Accounts Manual for Industry Users
 1 ECHA Accounts Manual ECHA Accounts Manual for Industry Users 2 ECHA Accounts Manual Changes to this document Version Changes Date 1.0 First release September 2014 2.0 Update December 2014 3.0 Update
1 ECHA Accounts Manual ECHA Accounts Manual for Industry Users 2 ECHA Accounts Manual Changes to this document Version Changes Date 1.0 First release September 2014 2.0 Update December 2014 3.0 Update
CHI Easy Access: Register From on the CHI Network
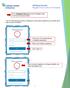 CHI Easy Access: Register From on the CHI Network Go to chieasyaccess.org and click "Register Now." You'll see the screen below. Your CHI Easy Access account is configured to use the same password you
CHI Easy Access: Register From on the CHI Network Go to chieasyaccess.org and click "Register Now." You'll see the screen below. Your CHI Easy Access account is configured to use the same password you
Enroll a New Student
 The txsuite How To Guide Series Connect tx Web-based Access for Teachers, Parents, and Students How to: Enroll a New Student Developed by the T E XA S CO M P U T E R CO O P E R AT I V E Business and Student
The txsuite How To Guide Series Connect tx Web-based Access for Teachers, Parents, and Students How to: Enroll a New Student Developed by the T E XA S CO M P U T E R CO O P E R AT I V E Business and Student
Welcome to ncrypted Cloud!... 4 Getting Started Register for ncrypted Cloud Getting Started Download ncrypted Cloud...
 Windows User Manual Welcome to ncrypted Cloud!... 4 Getting Started 1.1... 5 Register for ncrypted Cloud... 5 Getting Started 1.2... 7 Download ncrypted Cloud... 7 Getting Started 1.3... 9 Access ncrypted
Windows User Manual Welcome to ncrypted Cloud!... 4 Getting Started 1.1... 5 Register for ncrypted Cloud... 5 Getting Started 1.2... 7 Download ncrypted Cloud... 7 Getting Started 1.3... 9 Access ncrypted
DRACONEM RGB Touch ID Gaming Mouse Pad with Fingerprint Security
 Challenge Is The Game DRACONEM RGB Touch ID Gaming Mouse Pad with Fingerprint Security Software Guide 01 Index Challenge Is The Game Page 3 Page 7 Page 16 Page 22 Installing the software lregistering your
Challenge Is The Game DRACONEM RGB Touch ID Gaming Mouse Pad with Fingerprint Security Software Guide 01 Index Challenge Is The Game Page 3 Page 7 Page 16 Page 22 Installing the software lregistering your
How to Distribute a PDF File and ebook Securely Distribution Guide
 How to Distribute a PDF File and ebook Securely Distribution Guide This material is based on work supported by the National Science Foundation under Grant No. DUE 1205113 Contents Contents... 1 Secure
How to Distribute a PDF File and ebook Securely Distribution Guide This material is based on work supported by the National Science Foundation under Grant No. DUE 1205113 Contents Contents... 1 Secure
Table of Contents HOL-1757-MBL-5
 Table of Contents Lab Overview - - VMware AirWatch: Mobile App Management and App Development... 2 Lab Guidance... 3 Module 1 - Introduction to AppConfig (30 minutes)... 8 Login to the AirWatch Console...
Table of Contents Lab Overview - - VMware AirWatch: Mobile App Management and App Development... 2 Lab Guidance... 3 Module 1 - Introduction to AppConfig (30 minutes)... 8 Login to the AirWatch Console...
Security Service tools user IDs and passwords
 IBM Systems - iseries Security Service tools user IDs and passwords Version 5 Release 4 IBM Systems - iseries Security Service tools user IDs and passwords Version 5 Release 4 Note Before using this information
IBM Systems - iseries Security Service tools user IDs and passwords Version 5 Release 4 IBM Systems - iseries Security Service tools user IDs and passwords Version 5 Release 4 Note Before using this information
KYOCERA Device Manager User Guide
 KYOCERA Device Manager User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held
KYOCERA Device Manager User Guide Legal Notes Unauthorized reproduction of all or part of this guide is prohibited. The information in this guide is subject to change without notice. We cannot be held
Smart Lock Solution User Manual APP
 Smart Lock Solution User Manual APP Summary Set Owner Find Lock Lock & Unlock Menus Add User User Management Get Key Delete Key Recover Lock Lock Setting Update Lock Delete Lock Set App Code Reset App
Smart Lock Solution User Manual APP Summary Set Owner Find Lock Lock & Unlock Menus Add User User Management Get Key Delete Key Recover Lock Lock Setting Update Lock Delete Lock Set App Code Reset App
Tungsten Security Whitepaper
 Tungsten Labs UG (haftungsbeschränkt) Email: contact@tungsten-labs.com Web: http://tungsten-labs.com Monbijouplatz 5, 10178 Berlin Tungsten Security Whitepaper Berlin, May 2018 Version 1 Contents Introduction
Tungsten Labs UG (haftungsbeschränkt) Email: contact@tungsten-labs.com Web: http://tungsten-labs.com Monbijouplatz 5, 10178 Berlin Tungsten Security Whitepaper Berlin, May 2018 Version 1 Contents Introduction
3. Why should I use Samsung Pay instead of my physical cards?
 Overview 1. What is Samsung Pay? Samsung Pay is a secure and easy-to-use mobile payment service which can be used to make purchases almost anywhere. Leveraging a new proprietary technology called Magnetic
Overview 1. What is Samsung Pay? Samsung Pay is a secure and easy-to-use mobile payment service which can be used to make purchases almost anywhere. Leveraging a new proprietary technology called Magnetic
GET TO KNOW FEATURES THAT ANSWER THE CALL MANAGING VOIC WITH VOICEZONE
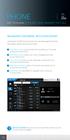 PHONE GET TO KNOW FEATURES THAT ANSWER THE CALL MANAGING VOICEMAIL WITH VOICEZONE Just sign in to My Account and you can manage Voicemail and more, online and on your time. Activate Voicemail. Use VoiceZone
PHONE GET TO KNOW FEATURES THAT ANSWER THE CALL MANAGING VOICEMAIL WITH VOICEZONE Just sign in to My Account and you can manage Voicemail and more, online and on your time. Activate Voicemail. Use VoiceZone
REACH Remote Deposit Capture
 REACH Remote Deposit Capture Company Administration CONTENTS Introduction to REACH... 1 Overview of Roles... 1 Session Timeouts and Maintenance... 1 User Login... 2 Login via Online Cash Management...
REACH Remote Deposit Capture Company Administration CONTENTS Introduction to REACH... 1 Overview of Roles... 1 Session Timeouts and Maintenance... 1 User Login... 2 Login via Online Cash Management...
Slides by Kent Seamons and Tim van der Horst Last Updated: Oct 7, 2013
 Digital Signatures Slides by Kent Seamons and Tim van der Horst Last Updated: Oct 7, 2013 Digital Signatures Diagram illustrating how to sign a message Why do we use a one-way hash? How does a collision
Digital Signatures Slides by Kent Seamons and Tim van der Horst Last Updated: Oct 7, 2013 Digital Signatures Diagram illustrating how to sign a message Why do we use a one-way hash? How does a collision
Windows quick start instructions Pg. 1. OS X quick start instructions Pg. 4. ios quick start instructions Pg. 6
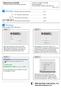 Page 1 of 12 Windows quick start instructions Pg. 1 OS X quick start instructions Pg. 4 ios quick start instructions Pg. 6 Android quick start instructions Pg. 9 Windows Quick Start Instructions STEP 1
Page 1 of 12 Windows quick start instructions Pg. 1 OS X quick start instructions Pg. 4 ios quick start instructions Pg. 6 Android quick start instructions Pg. 9 Windows Quick Start Instructions STEP 1
Texas Division How to Login and Register for My IT Support and ServiceNow
 Texas Division How to Login and Register for My IT Support and ServiceNow Go to texas.mychiitsuppport.org. You'll see the screen below. My IT Support/ServiceNow is a national system and utilizes national
Texas Division How to Login and Register for My IT Support and ServiceNow Go to texas.mychiitsuppport.org. You'll see the screen below. My IT Support/ServiceNow is a national system and utilizes national
FINANCIAL INFORMATION FORUM 5 Hanover Square New York, New York 10004
 FINANCIAL INFORMATION FORUM 5 Hanover Square New York, New York 10004 212-422-8568 Via Electronic Delivery August 3, 2018 Mr. Vas Rajan Chief Information Security Officer ThesysCAT, LLC 1740 Broadway New
FINANCIAL INFORMATION FORUM 5 Hanover Square New York, New York 10004 212-422-8568 Via Electronic Delivery August 3, 2018 Mr. Vas Rajan Chief Information Security Officer ThesysCAT, LLC 1740 Broadway New
ROAMpay TM. X4 User's Guide
 ROAMpay TM X4 User's Guide Last Modified: 06/14/2013 Contents 1 Activating ROAMpay X4 2 Using the System 2 Login 2 First-time Login 2 Default Settings 3 Retrieving Your Password 3 Online Sales 4 Saved
ROAMpay TM X4 User's Guide Last Modified: 06/14/2013 Contents 1 Activating ROAMpay X4 2 Using the System 2 Login 2 First-time Login 2 Default Settings 3 Retrieving Your Password 3 Online Sales 4 Saved
Zultys Mobile Communicator for iphone 4.0
 December 14 Zultys Mobile Communicator for iphone 4.0 Author: Zultys Technical Support Department This document covers basic use of the Zultys Mobile Communicator for iphone application. The Zultys Mobile
December 14 Zultys Mobile Communicator for iphone 4.0 Author: Zultys Technical Support Department This document covers basic use of the Zultys Mobile Communicator for iphone application. The Zultys Mobile
Android Rep Console
 Android Rep Console 2.2.10 2003-2018 BeyondTrust, Inc. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust, Inc. Other trademarks are the property of their respective owners.
Android Rep Console 2.2.10 2003-2018 BeyondTrust, Inc. All Rights Reserved. BEYONDTRUST, its logo, and JUMP are trademarks of BeyondTrust, Inc. Other trademarks are the property of their respective owners.
Guide Installation and User Guide - Mac
 Guide Installation and User Guide - Mac With Fujitsu mpollux DigiSign Client, you can use your smart card for secure access to electronic services or organization networks, as well as to digitally sign
Guide Installation and User Guide - Mac With Fujitsu mpollux DigiSign Client, you can use your smart card for secure access to electronic services or organization networks, as well as to digitally sign
