Encrypting Removable Media
|
|
|
- Quentin Greene
- 5 years ago
- Views:
Transcription
1 For security reasons all removable media must be encrypted with BitLocker to Go on Windows 7 workstations. The following will show you how to use a flash drive with BitLocker to Go. Please note that data on a drive encrypted with BitLocker to Go can only be modified on a Windows 7 workstation. On a Windows XP workstation, files can only be viewed. BitLocker encrypted drives are inaccessible in a Mac OS. Encrypting Removable Media BitLocker to Go Documentation When you plug in a flash drive or external hard drive you will be prompted with the following dialog box: If you click Don t encrypt this drive you will be able to immediately view the files on the drive, but you will not be able to save new files or modify existing files on the drive. You will need to click Encrypt this drive using BitLocker Drive Encryption to begin the encryption process. The encryption process must be performed on-campus with a network connection to the College domain. The above window appears for a few moments while the drive is being initialized. Once the drive is initialized, the above window appears. You are required to enter a password that meets password complexity requirements (at least one uppercase letter, one lower case letter, and one number or symbol). You may use the same password that you use to login. Once you ve typed and retyped your password, click Next
2 Are you ready to encrypt this drive? message appears. Click Start Encrypting The above window appears for a moment while the encryption process is being prepared to start. This above window appears while your dive is being encrypted. This process can take anywhere between 10 minutes and an hour depending on the size of your drive (external hard drives could take even longer). Be sure you allow ample time for this process to complete.
3 Once the encryption process is complete, the above window will display for a few moments, please wait for this window to disappear on its own. Once the encryption process is complete you can access your jump drive as normal from Windows Explorer or by double clicking the Computer icon on the desktop.
4 Using an Encrypted Drive in Windows 7 Each time you plug your jump drive into a Windows 7 workstation you will be prompted with the following dialog box: Type in the password that you used to encrypt the drive and click Unlock. Optionally, you have the option to Automatically unlock on this computer from now on, but this option should only be used on your workstation, and only if your workstation is not shared with others. In Windows Explorer (or double click the Computer icon on the desktop) it is very easy to tell whether a drive is locked or unlocked. When a drive is locked it will display a gold locked lock icon, and when the drive is unlocked it will display a silver unlocked lock icon. When you double click a drive with the gold locked lock icon, you will be automatically prompted with the dialog box to enter the password to unlock the drive.
5 Using an Encrypted Drive in Windows XP (Read Only!) When using your BitLocker to Go encrypted drive in Windows XP, it works a little differently than it does in Windows 7. You will not be able to make changes, or save new files, to the drive when connected to a Windows XP workstation. When you plug your drive into a Windows XP workstation, the drive will appear in My Computer with the gold locked lock icon indicating that the drive is encrypted with BitLocker to Go and you will only be able to view or copy files from the drive. When you double click the drive, you are not prompted to enter a password, but instead the drive is opened and all that you ll see is BitLockerToGo.exe and Read Me. Double click BitLockerToGo.exe to unlock the drive. The window above will appear. Type in the password that you used to encrypt the drive and click Unlock.
6 The BitLocker To Go Reader window opens, displaying the files saved on the drive. When double clicking a file in the BitLocker To Go Reader window, you will be prompted with the above message. Click Yes to make a copy of the file on the desktop. You can open, modify, and save the file located on the desktop, but you will not be able to move or copy this file back to the drive. If you attempt to copy a file into the BitLocker To Go Reader window, you will be prompted with the above message. Files on a BitLocker to Go encrypted drive can only be modified in Windows 7. BitLocker to Go Documentation Revision /29/2010
BitLocker to Go: Encryption for personal USB
 BitLocker to Go: Encryption for personal USB [Windows 10] Encryption is an effective method of protecting data stored on portable USB devices such as flash drives and external hard drives. Encryption encodes
BitLocker to Go: Encryption for personal USB [Windows 10] Encryption is an effective method of protecting data stored on portable USB devices such as flash drives and external hard drives. Encryption encodes
Configuring Microsoft Outlook to Connect to Hosted Exchange Service
 Configuring Microsoft Outlook to Connect to Hosted Exchange Service Configuring Microsoft Outlook for Hosted Exchange Service Version: 1.0 Updated on: April 27, 2011 Page 1 of 7 TABLE OF CONTENTS Configuring
Configuring Microsoft Outlook to Connect to Hosted Exchange Service Configuring Microsoft Outlook for Hosted Exchange Service Version: 1.0 Updated on: April 27, 2011 Page 1 of 7 TABLE OF CONTENTS Configuring
BitLocker Drive Encryption Guide
 BitLocker Drive Encryption Guide How to create a virtual hard drive and encrypt it with BitLocker... 2 How to Mount and Open your VHD after you restart your Computer... 11 Encrypting removable drives (Flash
BitLocker Drive Encryption Guide How to create a virtual hard drive and encrypt it with BitLocker... 2 How to Mount and Open your VHD after you restart your Computer... 11 Encrypting removable drives (Flash
WINDOWS 7 BITLOCKER DRIVE ENCRYPTION
 ComputerFixed.co.uk Page: 1 Email: info@computerfixed.co.uk WINDOWS 7 BITLOCKER DRIVE ENCRYPTION There are so many ways in which you can stop unauthorized access to your computer but what if someone steals
ComputerFixed.co.uk Page: 1 Email: info@computerfixed.co.uk WINDOWS 7 BITLOCKER DRIVE ENCRYPTION There are so many ways in which you can stop unauthorized access to your computer but what if someone steals
1. A broadband connection. 2. Windows Vista (for these instructions; other operating systems have other instructions).
 A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
SP LOCKER USER MANUAL. v1.0
 SP LOCKER USER MANUAL v1.0 Table of Contents 1 Introduction to the SP Locker Security Software... 2 2 Before You Get Started... 2 3 Features... 2 4 Public and Secured Partition... 3 5 How to use SP Locker...
SP LOCKER USER MANUAL v1.0 Table of Contents 1 Introduction to the SP Locker Security Software... 2 2 Before You Get Started... 2 3 Features... 2 4 Public and Secured Partition... 3 5 How to use SP Locker...
CIMS Login Quick Guide Your Guide to Login Procedures
 FDOE Bureau of School Improvement CIMS Login Quick Guide Your Guide to Login Procedures Welcome to the CIMS Login Quick Guide. The purpose of this guide is to provide step-by-step directions for logging
FDOE Bureau of School Improvement CIMS Login Quick Guide Your Guide to Login Procedures Welcome to the CIMS Login Quick Guide. The purpose of this guide is to provide step-by-step directions for logging
Using the Vita Group Citrix Portal
 Using the Vita Group Citrix Portal Using the Portal Summary This document is will step you through using the Vita Group Citrix portal. This portal allows you to reset your password if it is expired, unlock
Using the Vita Group Citrix Portal Using the Portal Summary This document is will step you through using the Vita Group Citrix portal. This portal allows you to reset your password if it is expired, unlock
Remote Access Instructions. remote.gpmlaw.com
 Remote Access Instructions Citrix XenApp 7.8 is the mostly widely-used solution to provide remote access to users while working out of the office. This latest version is more secure and optimized for a
Remote Access Instructions Citrix XenApp 7.8 is the mostly widely-used solution to provide remote access to users while working out of the office. This latest version is more secure and optimized for a
The tool can also be accessed by clicking the Self Service Password Manager icon on your desktop, or by visiting:
 Self Service Password Manager Last revised: April 2017 Last reviewed: April 2017 Information Technology Division Next review: September 2018 This guide should be used to learn how to set-up a Self Service
Self Service Password Manager Last revised: April 2017 Last reviewed: April 2017 Information Technology Division Next review: September 2018 This guide should be used to learn how to set-up a Self Service
Hitachi High Technologies America, Inc. Password Policy
 Hitachi High Technologies America, Inc. Password Policy Revision Date: 4/17/2015 Table of Contents Table of Contents...2 Overview...3 Scope. 3 Guidelines...3 A. General Password Construction Guidelines...3
Hitachi High Technologies America, Inc. Password Policy Revision Date: 4/17/2015 Table of Contents Table of Contents...2 Overview...3 Scope. 3 Guidelines...3 A. General Password Construction Guidelines...3
USER MANUAL SafeStick
 USER MANUAL SafeStick ------------------------ Sep 2017 ------------------------ Contents About this User Guide 3 System Requirements 4 Recommendations Setup 5 Setup- Windows 6 Setup- Mac 7 Device Initialization
USER MANUAL SafeStick ------------------------ Sep 2017 ------------------------ Contents About this User Guide 3 System Requirements 4 Recommendations Setup 5 Setup- Windows 6 Setup- Mac 7 Device Initialization
Multi-factor Authentication Instructions
 What is MFA? Multi-factor Authentication (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account.
What is MFA? Multi-factor Authentication (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account.
Imation Lock. Password Protection Software USER GUIDE. v1.1. (Mode 8)
 Imation Lock Password Protection Software USER GUIDE v1.1 (Mode 8) Table of Contents 1. Introduction to the Imation Lock Security Software....2 2. Before You Get Started...2 3. Features....2 4. Public
Imation Lock Password Protection Software USER GUIDE v1.1 (Mode 8) Table of Contents 1. Introduction to the Imation Lock Security Software....2 2. Before You Get Started...2 3. Features....2 4. Public
Connecting to the NMHU network and or your office PC using Microsoft VPN
 Connecting to the NMHU network and or your office PC using Microsoft VPN Before you can use the NMHU VPN server to connect to your office PC you must: Be running Windows XP on you office PC. Contact ITServices
Connecting to the NMHU network and or your office PC using Microsoft VPN Before you can use the NMHU VPN server to connect to your office PC you must: Be running Windows XP on you office PC. Contact ITServices
Multi-factor Authentication Instructions
 What is MFA? (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account. MFA authentication is typically
What is MFA? (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account. MFA authentication is typically
DropSend Getting Started Guide
 DropSend Getting Started Guide DropSend. 2016 Step 1: How to send a file without registration If you want to quickly send a large file, you can do it from the homepage in just a couple of clicks. Here
DropSend Getting Started Guide DropSend. 2016 Step 1: How to send a file without registration If you want to quickly send a large file, you can do it from the homepage in just a couple of clicks. Here
Ebrary User Guide. Downloading a Book: Reading ebrary books online: Accessing BookShelf: Using the Bookshelf:
 Ebrary User Guide Downloading a Book: Reading ebrary books online: Accessing BookShelf: Using the Bookshelf: ebrary Mobile App Installation and Sign in procedure: Using ebrary App in ipad iphone ipod:
Ebrary User Guide Downloading a Book: Reading ebrary books online: Accessing BookShelf: Using the Bookshelf: ebrary Mobile App Installation and Sign in procedure: Using ebrary App in ipad iphone ipod:
Logging into LTC Instant Access the First Time
 Logging into LTC Instant Access the First Time Access the Instant Access website at: https://mycampus.gotoltc.edu a. from the LTC website Current Students>Technology & Logins>LTC Instant Access Enter your
Logging into LTC Instant Access the First Time Access the Instant Access website at: https://mycampus.gotoltc.edu a. from the LTC website Current Students>Technology & Logins>LTC Instant Access Enter your
Once a USB drive has been inserted into an encrypted machine, the Dell Data Protection software will recognize the unencrypted device.
 Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
Dell Data Protection USB Drive Encryption Introduction To further protect PC s that have access to sensitive data, the Dell Data Protection (DDP) client detects and encrypts USB/Flash drives when they
VMware Horizon Client Installation Guide (Windows)
 VMware Horizon Client Installation Guide (Windows) (Please note: The steps in this document must be followed exactly as shown in order to ensure a proper installation.) Requirements: You must have an existing
VMware Horizon Client Installation Guide (Windows) (Please note: The steps in this document must be followed exactly as shown in order to ensure a proper installation.) Requirements: You must have an existing
UNIVERSITY OF EXETER BITLOCKER USER GUIDE
 Exeter IT Technical Planning & Development UNIVERSITY OF EXETER BITLOCKER USER GUIDE BitLocker is an encryption system which allows the University to secure sensitive information on University owned laptops,
Exeter IT Technical Planning & Development UNIVERSITY OF EXETER BITLOCKER USER GUIDE BitLocker is an encryption system which allows the University to secure sensitive information on University owned laptops,
Install New Java Client, Release GL 3.1 For Workstations Currently without Java
 Install New Java Client, For Workstations Currently without Java Following are instructions for installing the latest version of the Java client (GL3.1.3.228.5) on a workstation that does NOT currently
Install New Java Client, For Workstations Currently without Java Following are instructions for installing the latest version of the Java client (GL3.1.3.228.5) on a workstation that does NOT currently
REFWORKS STEP-BY-STEP
 REFWORKS STEP-BY-STEP HTTP://WWW.LIB.UMN.EDU/REFWORKS A. SETTING UP AN ACCOUNT 1. Go to / 2. Click on Set up a New RefWorks Account o If you are connecting from off-campus, you will be asked to login with
REFWORKS STEP-BY-STEP HTTP://WWW.LIB.UMN.EDU/REFWORKS A. SETTING UP AN ACCOUNT 1. Go to / 2. Click on Set up a New RefWorks Account o If you are connecting from off-campus, you will be asked to login with
SWCS 4.2 Backup Agent User s Guide Revision /20/2012 Solatech, Inc.
 SWCS 4.2 Backup Agent User s Guide Revision 24 11/20/2012 Solatech, Inc. Contents Introduction... 3 Installation... 3 Running the Backup Agent... 3 Using the Backup Agent... 3 Configuring the Backup...
SWCS 4.2 Backup Agent User s Guide Revision 24 11/20/2012 Solatech, Inc. Contents Introduction... 3 Installation... 3 Running the Backup Agent... 3 Using the Backup Agent... 3 Configuring the Backup...
Required software. Mac OS X In this section, you ll find instructions for downloading and configuring the Arduino IDE in Mac OS X.
 Required software You should be able to program your Arduino with just about any computer using a piece of software called an integrated development environment (IDE). To run this software, your computer
Required software You should be able to program your Arduino with just about any computer using a piece of software called an integrated development environment (IDE). To run this software, your computer
If your Mac keeps asking for the login keychain password
 If your Mac keeps asking for the login keychain password The password of your macos user account might not match the password of your login keychain. Either create a new login keychain or update it with
If your Mac keeps asking for the login keychain password The password of your macos user account might not match the password of your login keychain. Either create a new login keychain or update it with
Technology Services Group Procedures. IH Anywhere guide. 0 P a g e
 VDI Pilot Technology Services Group Procedures IH Anywhere guide 0 P a g e Installation Disable Apple Security Table of Contents IH Anywhere for Apple OSX (MAC)...2 1. Installation...2 Disable Apple Security...8
VDI Pilot Technology Services Group Procedures IH Anywhere guide 0 P a g e Installation Disable Apple Security Table of Contents IH Anywhere for Apple OSX (MAC)...2 1. Installation...2 Disable Apple Security...8
What is a Flash Drive?
 What is a Flash Drive? Flash drives, also called jump drives, pen drives, and thumb drives, are small flash memory drives with a USB (Universal Serial Bus) connection. Most computers have at least two
What is a Flash Drive? Flash drives, also called jump drives, pen drives, and thumb drives, are small flash memory drives with a USB (Universal Serial Bus) connection. Most computers have at least two
SWCS 4.2 Server Manager Users Guide Revision /22/2012 Solatech, Inc.
 SWCS 4.2 Server Manager Users Guide Revision 39 10/22/2012 Solatech, Inc. Contents Introduction... 5 Installation... 5 Installing on a server with the Solatech Window Covering Software... 5 Running the
SWCS 4.2 Server Manager Users Guide Revision 39 10/22/2012 Solatech, Inc. Contents Introduction... 5 Installation... 5 Installing on a server with the Solatech Window Covering Software... 5 Running the
Digital Content e-reader Features Overview
 Digital Content e-reader Features Overview Announcing the launch of our new digital content e-reader. This brief overview will demonstrate some of the most important features of our new e-reader. Once
Digital Content e-reader Features Overview Announcing the launch of our new digital content e-reader. This brief overview will demonstrate some of the most important features of our new e-reader. Once
CameraMate. Hi-Speed 10 in 1 Digital Media Reader/Writer User s Guide
 CameraMate Hi-Speed 10 in 1 Digital Media Reader/Writer User s Guide www.ziocorp.com Copyright Zio Corporation. All rights reserved. Trademarks are used for informational purposes, and remain the property
CameraMate Hi-Speed 10 in 1 Digital Media Reader/Writer User s Guide www.ziocorp.com Copyright Zio Corporation. All rights reserved. Trademarks are used for informational purposes, and remain the property
Job Aid: Citrix Receiver Upgrade
 January 3, 2018 Job Aid: Citrix Receiver Upgrade Overview We have upgraded the Citrix infrastructure that securely delivers your Citrix applications and desktops. While your applications and desktops are
January 3, 2018 Job Aid: Citrix Receiver Upgrade Overview We have upgraded the Citrix infrastructure that securely delivers your Citrix applications and desktops. While your applications and desktops are
Super USB. User Manual. 2007, March
 Super USB User Manual 2007, March Windows98 Driver Install/Uninstall Driver Install: 1. Execute Win 98 UFD driver, then restart PC. 2. Plug Super USB into an available USB port. A new Removable Disk drive
Super USB User Manual 2007, March Windows98 Driver Install/Uninstall Driver Install: 1. Execute Win 98 UFD driver, then restart PC. 2. Plug Super USB into an available USB port. A new Removable Disk drive
Step 1: Adding Darwin to your computer
 Step 1: Adding Darwin to your computer You MUST be on GoucherWIFI. If you receive any network connection problems at any point, double-check your WIFI connection. Remove/Move GoucherGuest and GoucherMultimedia
Step 1: Adding Darwin to your computer You MUST be on GoucherWIFI. If you receive any network connection problems at any point, double-check your WIFI connection. Remove/Move GoucherGuest and GoucherMultimedia
Introduction to Microsoft Windows
 Introduction to Microsoft Windows lab 1 Objectives: Upon successful completion of Lab 1, you will be able to Describe some of the basic functions of an operating system, and Windows in particular Describe
Introduction to Microsoft Windows lab 1 Objectives: Upon successful completion of Lab 1, you will be able to Describe some of the basic functions of an operating system, and Windows in particular Describe
Online Access: Login to The Media Audit
 Online Access: Login to The Media Audit Using The Media Audit online has never been easier! Simply open your web browser and follow the quick instructions below. app.themediaaudit.com Open your favorite
Online Access: Login to The Media Audit Using The Media Audit online has never been easier! Simply open your web browser and follow the quick instructions below. app.themediaaudit.com Open your favorite
Management Security Switch SGSD-1022 / SGSD-1022P SGSW-2840 / SGSW-2840P. Quick Installation Guide
 Management Security Switch SGSD-1022 / SGSD-1022P SGSW-2840 / SGSW-2840P Quick Installation Guide Table of Contents 1. Package Content... 3 2. Requirements... 4 3. Terminal Setup... 5 4. Logon to the Console...
Management Security Switch SGSD-1022 / SGSD-1022P SGSW-2840 / SGSW-2840P Quick Installation Guide Table of Contents 1. Package Content... 3 2. Requirements... 4 3. Terminal Setup... 5 4. Logon to the Console...
Remote Desktop Access
 Ready Reference 100208 Remote Desktop Access Introduction Remote Desktop Access for Windows XP Professional or Windows Vista Business provides access to a Windows session that is running on your computer
Ready Reference 100208 Remote Desktop Access Introduction Remote Desktop Access for Windows XP Professional or Windows Vista Business provides access to a Windows session that is running on your computer
Quick Guide to Installing and Setting Up MySQL Workbench
 Quick Guide to Installing and Setting Up MySQL Workbench If you want to install MySQL Workbench on your own computer: Go to: http://www.mysql.com/downloads/workbench/ Windows Users: 1) You will need to
Quick Guide to Installing and Setting Up MySQL Workbench If you want to install MySQL Workbench on your own computer: Go to: http://www.mysql.com/downloads/workbench/ Windows Users: 1) You will need to
Flash USB Drive. HwaZu Disk User Manual. Product Image File
 Flash USB Drive HwaZu Disk User Manual Product Image File Version 1.33 Table of Contents Introduction System Requirements Functions I. Install II. Formatting II-1 When Formatting II-2 Do Formatting III.
Flash USB Drive HwaZu Disk User Manual Product Image File Version 1.33 Table of Contents Introduction System Requirements Functions I. Install II. Formatting II-1 When Formatting II-2 Do Formatting III.
zspace 300 Windows 8.1 Configuration
 zspace 300 Windows 8.1 Configuration zspace 300 Windows 8.1 Configuration After you have set up your zspace hardware components you are ready to start up the zspace 300 for the first time. When the system
zspace 300 Windows 8.1 Configuration zspace 300 Windows 8.1 Configuration After you have set up your zspace hardware components you are ready to start up the zspace 300 for the first time. When the system
Faculty and Staff Instructions for connecting to the Hood College VPN to access your files on Blazer and/or your on-campus computer
 Faculty and Staff Instructions for connecting to the Hood College VPN to access your files on Blazer and/or your on-campus computer NOTE: These instructions were written for Windows XP. Also, please note
Faculty and Staff Instructions for connecting to the Hood College VPN to access your files on Blazer and/or your on-campus computer NOTE: These instructions were written for Windows XP. Also, please note
Setting Preferences. Setting Preferences. Setting up Parental Controls
 Setting Preferences Use the Settings application to set certain preferences for your account, such as parental controls and channel blocking settings. Note: You must enter your PIN every time you access
Setting Preferences Use the Settings application to set certain preferences for your account, such as parental controls and channel blocking settings. Note: You must enter your PIN every time you access
HOWTO Make an Initial Connection to the Office Anywhere Desktop using a Windows 7 based PC v1
 HOWTO Make an Initial Connection to the Office Anywhere Desktop using a Windows 7 based PC v1 1. Web browse to the Office Anywhere Portal: http://hosted.gg (as shown below) 2. Click the Access Office Anywhere
HOWTO Make an Initial Connection to the Office Anywhere Desktop using a Windows 7 based PC v1 1. Web browse to the Office Anywhere Portal: http://hosted.gg (as shown below) 2. Click the Access Office Anywhere
How to set up your wireless network
 How to set up your wireless network There are several steps involved in securing your wireless network. I recommend that you take these steps in order and only change one item at a time. While this may
How to set up your wireless network There are several steps involved in securing your wireless network. I recommend that you take these steps in order and only change one item at a time. While this may
Spec-ops Password Reset Enrollment and Usage
 ORIGINAL DOCUMENT DATE: 12/11/2015 LAST REVISION: 1/7/2016 Spec-ops Password Reset Enrollment and Usage Index Announcement... Page 1 Quick Links, Best Practices, and Enrollment... Page 2 Using the new
ORIGINAL DOCUMENT DATE: 12/11/2015 LAST REVISION: 1/7/2016 Spec-ops Password Reset Enrollment and Usage Index Announcement... Page 1 Quick Links, Best Practices, and Enrollment... Page 2 Using the new
Welcome to Learn. 1. Your first task is to log into Learn. a. (click this link or copy and paste it into your browser)
 Welcome to Learn 1. Your first task is to log into Learn. a. http://learn.gov.sk.ca (click this link or copy and paste it into your browser) b. You will see this at the bottom of your screen: Login. c.
Welcome to Learn 1. Your first task is to log into Learn. a. http://learn.gov.sk.ca (click this link or copy and paste it into your browser) b. You will see this at the bottom of your screen: Login. c.
Fair Isaac Product Name User s Guide ENHANCEMENT NOTIFICATION Fair Isaac LenStar. Security Requirements
 Fair Isaac Product Name User s Guide ENHANCEMENT NOTIFICATION 6.1.2 Fair Isaac LenStar Security Requirements This document is the confidential, unpublished property of Fair Isaac Corporation. Receipt or
Fair Isaac Product Name User s Guide ENHANCEMENT NOTIFICATION 6.1.2 Fair Isaac LenStar Security Requirements This document is the confidential, unpublished property of Fair Isaac Corporation. Receipt or
This is a GENERAL Servant Keeper Network Installation help sheet. If you need further assistance, please contact your network administrator.
 SK Help Network Help Sheets - Workstation Installation This is a GENERAL Servant Keeper Network Installation help sheet. If you need further assistance, please contact your network administrator. Due to
SK Help Network Help Sheets - Workstation Installation This is a GENERAL Servant Keeper Network Installation help sheet. If you need further assistance, please contact your network administrator. Due to
Opening and Saving Files using Minitab in Remote Applications using Macintosh
 Opening and Saving Files using Minitab in Remote Applications using Macintosh When using SU Remote Applications, the application accesses your P drive by default. But there may be some instances where
Opening and Saving Files using Minitab in Remote Applications using Macintosh When using SU Remote Applications, the application accesses your P drive by default. But there may be some instances where
JetFlash User s Manual
 JetFlash User s Manual ( Version 1.0 ) Table of Contents INTRODUCTION...1 PACKAGE CONTENTS...1 FEATURES...1 SYSTEM REQUIREMENTS...1 DRIVER INSTALLATION...2 DRIVER INSTALLATION FOR WINDOWS 98SE...2 DRIVER
JetFlash User s Manual ( Version 1.0 ) Table of Contents INTRODUCTION...1 PACKAGE CONTENTS...1 FEATURES...1 SYSTEM REQUIREMENTS...1 DRIVER INSTALLATION...2 DRIVER INSTALLATION FOR WINDOWS 98SE...2 DRIVER
Frequently Asked Technical Questions
 Frequently Asked Technical Questions The first step in resolving any technical problem is to make sure that you meet the technical requirements. A basic requirement for taking a PLS online course is to
Frequently Asked Technical Questions The first step in resolving any technical problem is to make sure that you meet the technical requirements. A basic requirement for taking a PLS online course is to
Join an OmniJoin Meeting as an Attendee (Mac and PC)
 Quickstart Guide Join an OmniJoin Meeting as an Attendee (Mac and PC) OmniJoin web conferencing from Brother delivers high quality, highly secure voice, video and collaboration through web meetings, in
Quickstart Guide Join an OmniJoin Meeting as an Attendee (Mac and PC) OmniJoin web conferencing from Brother delivers high quality, highly secure voice, video and collaboration through web meetings, in
Bridge Cable User s Guide
 Bridge Cable User s Guide Table of Contents Overview -------------------------------------------------------------------- 2 Driver Installation --------------------------------------------------------
Bridge Cable User s Guide Table of Contents Overview -------------------------------------------------------------------- 2 Driver Installation --------------------------------------------------------
USER MANUAL. DataLocker Sentry January
 USER MANUAL DataLocker Sentry ------------------------ January 2014 ------------------------ 1 Contents At a Glance 3 What is a secure USB drive? 3 Technical introduction Getting Started 4 Quick start
USER MANUAL DataLocker Sentry ------------------------ January 2014 ------------------------ 1 Contents At a Glance 3 What is a secure USB drive? 3 Technical introduction Getting Started 4 Quick start
Key File Generation. November 14, NATIONAL STUDENT CLEARINGHOUSE 2300 Dulles Station Blvd., Suite 220, Herndon, VA 20171
 Key File Generation NATIONAL STUDENT CLEARINGHOUSE 2300 Dulles Station Blvd., Suite 220, Herndon, VA 20171 Table of Contents Introduction... 2 PuTTY Installation... 2 Key Generation... 7 Configuring PuTTY
Key File Generation NATIONAL STUDENT CLEARINGHOUSE 2300 Dulles Station Blvd., Suite 220, Herndon, VA 20171 Table of Contents Introduction... 2 PuTTY Installation... 2 Key Generation... 7 Configuring PuTTY
Installing the WHI Virtual Private Network (VPN) for WHIX Users Updated 12/16/2016
 Installing the WHI Virtual Private Network (VPN) for WHIX Users Updated 12/16/2016 Note: Please read the FAQ section at the end of this document. I. Overview The way in which you connect to the WHI network
Installing the WHI Virtual Private Network (VPN) for WHIX Users Updated 12/16/2016 Note: Please read the FAQ section at the end of this document. I. Overview The way in which you connect to the WHI network
New Dropbox Users (don t have a Dropbox account set up with your Exeter account)
 The setup process will determine if you already have a Dropbox account associated with an Exeter email address, and if so, you'll be given a choice to move those contents to your Phillips Exeter Dropbox
The setup process will determine if you already have a Dropbox account associated with an Exeter email address, and if so, you'll be given a choice to move those contents to your Phillips Exeter Dropbox
Y115 Remote File Access. Use WebDav to Make Life Easier
 Y115 Remote File Access Use WebDav to Make Life Easier Introduction And Goals Of This Guide What Is Webdav? Webdav is a file sharing protocol that is used to transfer files between web devices using http.
Y115 Remote File Access Use WebDav to Make Life Easier Introduction And Goals Of This Guide What Is Webdav? Webdav is a file sharing protocol that is used to transfer files between web devices using http.
San Jacinto College. Secure SSL VPN Instruction Manual. Contents
 1 San Jacinto College Secure SSL VPN Instruction Manual The new Secure SSL VPN provides a more secure and convenient method of accessing San Jacinto College resources remotely. This document provides an
1 San Jacinto College Secure SSL VPN Instruction Manual The new Secure SSL VPN provides a more secure and convenient method of accessing San Jacinto College resources remotely. This document provides an
The manufacturer has released new improved firmware which upgrades your O2 USB Modem. To install it follow the instructions below.
 O2 USB Modem Firmware Upgrade. The manufacturer has released new improved firmware which upgrades your O2 USB Modem. To install it follow the instructions below. The upgrade will work on Microsoft Windows
O2 USB Modem Firmware Upgrade. The manufacturer has released new improved firmware which upgrades your O2 USB Modem. To install it follow the instructions below. The upgrade will work on Microsoft Windows
Encrypting external USB drive on Linux
 Encrypting external USB drive on Linux To prevent your important or personal information from falling into the wrong hands, you can easily encrypt the files on your USB-drive with a password. Windows,
Encrypting external USB drive on Linux To prevent your important or personal information from falling into the wrong hands, you can easily encrypt the files on your USB-drive with a password. Windows,
MSU Authorized User Campus Access Procedure, Campus VPN
 MSU Authorized User Campus Access Procedure, Campus VPN This document provides the requirements and procedures for access to the Campus Network for MSU Authorized Users. Access to the Campus Network is
MSU Authorized User Campus Access Procedure, Campus VPN This document provides the requirements and procedures for access to the Campus Network for MSU Authorized Users. Access to the Campus Network is
Version June 2016
 HOSTING GUIDE Version 3.2.3 June 2016 This guide is sold in conjunction with the VETtrak Hosting Serv ice and is current at the time of purchase. Later v ersions are av ailable for download from www.v
HOSTING GUIDE Version 3.2.3 June 2016 This guide is sold in conjunction with the VETtrak Hosting Serv ice and is current at the time of purchase. Later v ersions are av ailable for download from www.v
Table of Contents. A. Introduction...2. B. General Description...2. C. Features...3. D. Before Using the Security Application Program LOCK...
 v1.00 Table of Contents A. Introduction...2 B. General Description...2 C. Features...3 D. Before Using the Security Application Program LOCK...4 E. Introduction to the Security Application Program LOCK...5
v1.00 Table of Contents A. Introduction...2 B. General Description...2 C. Features...3 D. Before Using the Security Application Program LOCK...4 E. Introduction to the Security Application Program LOCK...5
Camera Control for Windows
 Camera Control for Windows 1910012275 REV1.1.0 Contents Chapter 1 Introduction... 1 1.1 Overview... 1 1.2 System Requirement... 1 Chapter 2 Software Installation... 2 Chapter 3 Quick Start... 5 3.1 Create
Camera Control for Windows 1910012275 REV1.1.0 Contents Chapter 1 Introduction... 1 1.1 Overview... 1 1.2 System Requirement... 1 Chapter 2 Software Installation... 2 Chapter 3 Quick Start... 5 3.1 Create
Outlook 2010 Setup Guide (POP3 Transmailaccess)
 Versions Addressed: Microsoft Office Outlook 2010 Document Updated: 7 /22/2013 Copyright 2012 Smarsh, Inc. All rights reserved. Purpose: This document will assist the end user in configuring Outlook 2010
Versions Addressed: Microsoft Office Outlook 2010 Document Updated: 7 /22/2013 Copyright 2012 Smarsh, Inc. All rights reserved. Purpose: This document will assist the end user in configuring Outlook 2010
Personal Fi. Personal Finance Quick Start Guide. Rev 3/18
 Personal Fi Personal Finance Quick Start Guide Rev 3/18 Welcome to Personal Finance. Use Personal Finance to view account balances and transactions from all your financial institutions. Get a complete
Personal Fi Personal Finance Quick Start Guide Rev 3/18 Welcome to Personal Finance. Use Personal Finance to view account balances and transactions from all your financial institutions. Get a complete
Updating Astea Mobile URLs
 Updating Astea Mobile URLs Table of Contents UPDATING THE ASTEA APPLICATION SERVER URL... 4 RESETTING YOUR PASSWORD UPON INITIAL LOGIN... 7 CHANGING YOUR PASSWORD... 10 ACCESSING THE UPDATED TRAINING MATERIALS...
Updating Astea Mobile URLs Table of Contents UPDATING THE ASTEA APPLICATION SERVER URL... 4 RESETTING YOUR PASSWORD UPON INITIAL LOGIN... 7 CHANGING YOUR PASSWORD... 10 ACCESSING THE UPDATED TRAINING MATERIALS...
Aqua Accelerated Protocol (AAP) User Manual
 Aqua Accelerated Protocol (AAP) User Manual Table of Contents About Aqua Accelerated Protocol...3 Features... 3 System Requirements... 4 Hardware... 4 Software (AAP Client)... 4 Software (Server Connecting
Aqua Accelerated Protocol (AAP) User Manual Table of Contents About Aqua Accelerated Protocol...3 Features... 3 System Requirements... 4 Hardware... 4 Software (AAP Client)... 4 Software (Server Connecting
Information Technology
 Information Technology Operations Team Instructional Sharing Protected Data Contents Introduction... 3 Procedure... 3 How to Password Protect a MS Word Document... 3 MS Word 2010/2013/2016... 3 Word 2007...
Information Technology Operations Team Instructional Sharing Protected Data Contents Introduction... 3 Procedure... 3 How to Password Protect a MS Word Document... 3 MS Word 2010/2013/2016... 3 Word 2007...
HealthyCT Online Member Bill Pay. User Guide For Enrollment and Online Payments
 HealthyCT Online Member Bill Pay User Guide For Enrollment and Online Payments Revised April 2016 Table of Contents I. Enrollment Process: Setting up Member Bill Pay... Page 2 II. Setting Up Your Payments...
HealthyCT Online Member Bill Pay User Guide For Enrollment and Online Payments Revised April 2016 Table of Contents I. Enrollment Process: Setting up Member Bill Pay... Page 2 II. Setting Up Your Payments...
CESecure Quick Start Guide
 CESecure Quick Start Guide Using CESecure Software CESecure software is pre-installed on CMS Products Flash or Hard Drives and does not require installation. The CESecure software moves with the encryption
CESecure Quick Start Guide Using CESecure Software CESecure software is pre-installed on CMS Products Flash or Hard Drives and does not require installation. The CESecure software moves with the encryption
Celadon Password Self-Service
 Celadon Password Self-Service Quest Password Manager is a facility that allows you to reset your Celadon Windows password as well as unlock the account without calling the Helpdesk to provide self-service
Celadon Password Self-Service Quest Password Manager is a facility that allows you to reset your Celadon Windows password as well as unlock the account without calling the Helpdesk to provide self-service
Commonfund Client Reporting Portal
 Commonfund Single Sign On Help Effective Tuesday, February 18, 2014, Commonfund has implemented a new, single sign-on login that provides enhanced security and flexibility in managing your login credentials.
Commonfund Single Sign On Help Effective Tuesday, February 18, 2014, Commonfund has implemented a new, single sign-on login that provides enhanced security and flexibility in managing your login credentials.
CIS 99 How to Purchase, Register and Navigate Myitlab
 CIS 99 How to Purchase, Register and Navigate Myitlab - Purchase Myitlab at the bookstore - (Option 1) Purchase these materials at the bookstore: Go to the bookstore and purchase the following textbook/registration-code:
CIS 99 How to Purchase, Register and Navigate Myitlab - Purchase Myitlab at the bookstore - (Option 1) Purchase these materials at the bookstore: Go to the bookstore and purchase the following textbook/registration-code:
Getting Started with VPN
 What is a VPN? VPN (Virtual Private Network) provides you with a way to connect to the HBU campus server securely over the internet in order to access your work computer and shared drives from home. VPN
What is a VPN? VPN (Virtual Private Network) provides you with a way to connect to the HBU campus server securely over the internet in order to access your work computer and shared drives from home. VPN
Enterprise Rights Management: Document Protection
 Enterprise Rights Management: Document Protection Intel Information Technology Job aid Revision Sep 16, 2011 Description Enterprise Rights Management (ERM) is used at Intel to protect classified content.
Enterprise Rights Management: Document Protection Intel Information Technology Job aid Revision Sep 16, 2011 Description Enterprise Rights Management (ERM) is used at Intel to protect classified content.
Citrix Desktop for Home Computers Mac OS Instructions
 Citrix Desktop for Home Computers Mac OS Instructions You can use Citrix to create and access a virtual work desktop from your home computer. Step 1 Uninstall: To install the newest version of Citrix on
Citrix Desktop for Home Computers Mac OS Instructions You can use Citrix to create and access a virtual work desktop from your home computer. Step 1 Uninstall: To install the newest version of Citrix on
The images shown below were taken on computers running Windows 8, but the general process should work on both Windows 7 and Windows 8 computers.
 GlobalProtect VPN VPN stands for "Virtual Private Network" which, in Carleton's context, allows you to access resources from off-campus, and provides secure, encrypted network access. The ability of VPNs
GlobalProtect VPN VPN stands for "Virtual Private Network" which, in Carleton's context, allows you to access resources from off-campus, and provides secure, encrypted network access. The ability of VPNs
L2+ Managed Gigabit Switch WGSW series
 L2+ Managed Gigabit Switch WGSW-24040 series Quick Installation Guide Table of Contents 1 Package Contents... 3 2. Requirements... 4 3. Terminal Setup... 5 3.1 Logon to Console... 6 3.2 Configuring IP
L2+ Managed Gigabit Switch WGSW-24040 series Quick Installation Guide Table of Contents 1 Package Contents... 3 2. Requirements... 4 3. Terminal Setup... 5 3.1 Logon to Console... 6 3.2 Configuring IP
SailPoint is accessible from both on and off of campus. Off campus users will need to verify their log in while on campus users may not need to.
 SailPoint SailPoint is a tool that Norwich University uses for Enterprise Single Sign-On, Password Management and Identity Management. It is a Software as a Service (SaaS) or cloud application. It will
SailPoint SailPoint is a tool that Norwich University uses for Enterprise Single Sign-On, Password Management and Identity Management. It is a Software as a Service (SaaS) or cloud application. It will
Contents. Getting Started...1. Managing Your Drives...9. Backing Up & Restoring Folders Synchronizing Folders...52
 Contents Getting Started.....................................................1 Installing the Software...........................................1 Using the Maxtor System Tray Icon................................6
Contents Getting Started.....................................................1 Installing the Software...........................................1 Using the Maxtor System Tray Icon................................6
BitLocker Encryption for non-tpm laptops
 BitLocker Encryption for non-tpm laptops Contents 1.0 Introduction... 2 2.0 What is a TPM?... 2 3.0 Users of non-tpm University laptops... 2 3.1 Existing Windows 7 laptop users... 2 3.2 Existing Windows
BitLocker Encryption for non-tpm laptops Contents 1.0 Introduction... 2 2.0 What is a TPM?... 2 3.0 Users of non-tpm University laptops... 2 3.1 Existing Windows 7 laptop users... 2 3.2 Existing Windows
L2+ Managed Metro Ethernet Switch MGSW / MGSD Series
 L2+ Managed Metro Ethernet Switch MGSW / MGSD Series Quick Installation Guide Table of Contents 1. Package Contents... 3 2. Requirements... 4 3. Wiring DC Power Inputs... 5 4. Terminal Setup... 6 5. Logon
L2+ Managed Metro Ethernet Switch MGSW / MGSD Series Quick Installation Guide Table of Contents 1. Package Contents... 3 2. Requirements... 4 3. Wiring DC Power Inputs... 5 4. Terminal Setup... 6 5. Logon
USBest Technology Inc.
 UT163 USB2.0 Flash Disk Controller Mass Production Tool User Manual Version 1.1 DECEMBER 25, 2006 Technical Marketing Dept. Page 1 of 13 Copyright by, all rights reserved. System Requirements: 1. OS: Windows
UT163 USB2.0 Flash Disk Controller Mass Production Tool User Manual Version 1.1 DECEMBER 25, 2006 Technical Marketing Dept. Page 1 of 13 Copyright by, all rights reserved. System Requirements: 1. OS: Windows
L2/L4 Managed Gigabit Ethernet Switch GS-4210 Ultra PoE Series
 L2/L4 Managed Gigabit Ethernet Switch GS-4210 Ultra PoE Series Quick Installation Guide Table of Contents 1. Introduction... 3 2. Package Contents... 4 3. Requirements... 5 4. Terminal Setup... 6 5. Logon
L2/L4 Managed Gigabit Ethernet Switch GS-4210 Ultra PoE Series Quick Installation Guide Table of Contents 1. Introduction... 3 2. Package Contents... 4 3. Requirements... 5 4. Terminal Setup... 6 5. Logon
How to Install Dawson Diagnostic Wizard A. Edit Your Mac System Preferences
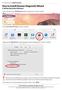 How to Install Dawson Diagnostic Wizard A. Edit Your Mac System Preferences 1. Open your Mac System Preferences under the apple menu, circled in red below. 2. Select Security & Privacy, circled in red
How to Install Dawson Diagnostic Wizard A. Edit Your Mac System Preferences 1. Open your Mac System Preferences under the apple menu, circled in red below. 2. Select Security & Privacy, circled in red
Using the Remote Desktop Portal
 Using the Remote Desktop Portal The Remote Desktop Portal The ICT Services team have implemented new software to provide staff greater access to College resources when away from the College. The new software
Using the Remote Desktop Portal The Remote Desktop Portal The ICT Services team have implemented new software to provide staff greater access to College resources when away from the College. The new software
VDI Users Guide. Mac OS X
 Mac OS X VDI Users Guide NOTICE: Access to electronic resources at Moraine Park Technical College is restricted to employees, students, or other individuals authorized by the College. By connecting to
Mac OS X VDI Users Guide NOTICE: Access to electronic resources at Moraine Park Technical College is restricted to employees, students, or other individuals authorized by the College. By connecting to
Format and Lock Utility User Manual (v2.0) USB 2.0 Flash Disk
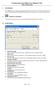 1. Introduction This FORMAT tool contains two programs: Format.exe and Lock.exe. The former (Format.exe) is used to format/partition the USB flash disk and the latter (Lock.exe) is for security disk function.
1. Introduction This FORMAT tool contains two programs: Format.exe and Lock.exe. The former (Format.exe) is used to format/partition the USB flash disk and the latter (Lock.exe) is for security disk function.
Edith Cowan University Information Technology Services Centre
 Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
Information There are three wireless networks on campus which give you access to the ECU website, the staff intranet, the internet and other ECU resources: ECU This is the easiest to use and safest wireless
Neehr Perfect Guide: Installing the Citrix Plugin
 Neehr Perfect Guide: Installing the Citrix Plugin Overview This guide covers how to install the Citrix plugin. The first time you log in to Neehr Perfect on any computer, you will be prompted to install
Neehr Perfect Guide: Installing the Citrix Plugin Overview This guide covers how to install the Citrix plugin. The first time you log in to Neehr Perfect on any computer, you will be prompted to install
This installation guide is intended for customers who are installing NMIS for the first time. Included are the recommended hardware specifications
 This installation guide is intended for customers who are installing NMIS for the first time. Included are the recommended hardware specifications and sample screens to guide you through the installation
This installation guide is intended for customers who are installing NMIS for the first time. Included are the recommended hardware specifications and sample screens to guide you through the installation
IT 341 Introduction to System Administration Project I Installing Ubuntu Server on a Virtual Machine
 IT 341 Introduction to System Administration Project I Installing Ubuntu Server on a Virtual Machine Here we create a new virtual machine and install Ubuntu 16.04 LTS Server on it. In this instance, we
IT 341 Introduction to System Administration Project I Installing Ubuntu Server on a Virtual Machine Here we create a new virtual machine and install Ubuntu 16.04 LTS Server on it. In this instance, we
Directions for Setting up Remote Desktop Connection for PC:
 Directions for Setting up Remote Desktop Connection for PC: BEFORE YOU BEGIN, MAKE SURE YOU HAVE: COMPUTER NAME USERNAME TEMPORARY PASSWORD 1 4/19/2016 Creating a Shortcut to your Concourse Hosting remote
Directions for Setting up Remote Desktop Connection for PC: BEFORE YOU BEGIN, MAKE SURE YOU HAVE: COMPUTER NAME USERNAME TEMPORARY PASSWORD 1 4/19/2016 Creating a Shortcut to your Concourse Hosting remote
48-Port 10/100/1000Base-T with 4 Shared SFP. Managed Gigabit Switch WGSW Quick Installation Guide
 48-Port 10/100/1000Base-T with 4 Shared SFP Managed Gigabit Switch WGSW-48000 Quick Installation Guide Table of Contents 1. Package Content... 3 2. Requirements... 4 3. Terminal Setup... 5 4. Logon to
48-Port 10/100/1000Base-T with 4 Shared SFP Managed Gigabit Switch WGSW-48000 Quick Installation Guide Table of Contents 1. Package Content... 3 2. Requirements... 4 3. Terminal Setup... 5 4. Logon to
<240mm> PANTONE Green C: For positional purposes only Do NOT Print <120mm> MF112 SUGuide aw.indd 1 08/06/ :05
 PANTONE Green C: For positional purposes only Do NOT Print Published by Hutchison 3G UK Limited, trading as Three. All rights in this publication are reserved and no part may be reproduced
PANTONE Green C: For positional purposes only Do NOT Print Published by Hutchison 3G UK Limited, trading as Three. All rights in this publication are reserved and no part may be reproduced
Connection Guide. Do this second:
 2 Do this second: Connection Guide 1 Install your lock. Use this Hardware Installation guide to get your lock hardware installed. Prefer a video? You are here. 2 Get connected. Use the Connection Guide
2 Do this second: Connection Guide 1 Install your lock. Use this Hardware Installation guide to get your lock hardware installed. Prefer a video? You are here. 2 Get connected. Use the Connection Guide
