Routing with Guaranteed Delivery in ad hoc Wireless Networks*
|
|
|
- Sandra French
- 6 years ago
- Views:
Transcription
1 Routig with Guarateed Delivery i ad hoc Wireless Networks* Prosejit Bose School of Computer Sciece Carleto Uiversity jit@scs.carleto.ca Pat Mori School of Computer Sciece Carleto Uiversity mori@scs.carleto.ca Jorge Urrutia Computer Sciece, SITE Uiversity of Ottawa jorgeqsite.uottawa.ca Iva Stojmeovic Computer Sciece, SITE Uiversity of Ottawa iva@site.uottawa.ca Abstract We cosider routig problems i ad hoc wireless etworks modeled as uit graphs i which odes are poits i the plae ad two odes ca commuicate if the distace betwee them is less tha some fixed uit. We describe the first distributed algorithms for routig that do ot require duplicatio of packets or memory at the odes ad yet guaraty that a packet is delivered to its destiatio. These algorithms ca be exteded to yield algorithms for broadcastig ad geocastig that do ot require packet duplicatio. A byproduct of our results is a simple distributed protocol for extractig a plaar subgraph of a uit graph. We also preset simulatio results o the performace of our algorithms. 1 Itroductio Mobile ad hoc etworks (MANETS) cosist of wireless hosts that commuicate with each other i the absece of fixed ifrastructure. Two odes i a MANET ca commuicate if the distace betwee them is less tha the miimum of their two broadcast rages [l]. For health ad efficiecy reasos, it is geerally ot possible (or desirable) for all hosts i a MANET to be able to commuicate with each other directly. Thus, sedig messages betwee two hosts i a MANET may require routig the message through itermediate hosts. I may cases, MANETS are pieced together i a ucotrolled maer, chages i topology are frequet ad ustructured, ad hosts may ot kow the topology of the etire etwork. I this paper, we cosider routig i MANETS for which hosts kow othig about *This work was partly fuded by the Natural Scieces ad E& eerig Research Coucil of Caada. pcmissio to m&c digital or hard copies of all or part of this work for persoal or classroom USC is grated without fee provided that copies are ot made or distributed for profit or commercial advatage ad that copies bear this otice ad the full citatio o the tit Page. To copy otherwise, to republish, to post o servers or to redistribute to lists. requires prior specific permissio ad/or a fee. DIAL M 99 Seattle WA ES.4 Copyright ACM 1999 I /99/ m the etwork except their locatio ad the locatios of the hosts to which they ca commuicate directly. GPS (global positioig system) provides each host with its geographic locatio ad global timig [ll]. I particular, we cosider the case i which all hosts have the same broadcast rage. Let S be a set of poits i the plae. The the uit graph U(S) is a geometric graph that cotais a vertex for each elemet of S. A edge (u, v) is preset i U(S) if ad oly if dist(u, v) 5 1, where dist(s, y) deotes the Euclidea distace betwee x ad y. Uit graphs are a reasoable mathematical abstractio of wireless etworks i which all odes have equal broadcast rages. I this paper we describe algorithms for routig o uit graphs which do ot require global iformatio about U(S). Each vertex v E U(S) represets a trasmissio statio, ad has o iformatio about U(S) except the set of odes N(w) to which it is adjacet. A packet that is stored at vertex v ca be trasmitted to ay vertex i N(u). I accordace with other papers [l, 3, 7, 91, it is assumed that the source kows from the begiig the exact geographical positio of the destiatio. I the mutig problem, the source v,, ad destiatio v&t are poits of S ad v&t must receive a message origiatig at v,,. I the geocastig problem [6, 111 the source v,, is a poit i S while the destiatio r&t is a regio, ad all vertices i r&t must receive a message origiatig at v,,. I this work we take r&t to be a disk, but our algorithms geeralize to arbitrary covex regios. Broadcastig is the a special case of geocastig i which r&t is a disk with ifiite radius. Previous algorithms for olie routig i uit graphs ca be broadly classified ito two categories: Greedy algorithms apply some type of greedy pathfidig heuristic that does ot guaratee that a packet ultimately reaches (all of) its destiatio(s). These iclude the geographic distace routig (GEDIR) algorithm of Lm ad Stojmeovic 191, the directioal routig (DIR), a.k.a, compass routig algorithm of Basagi et al [l], 48
2 Ko ad Vaidya [6], ad Kraakis et al [8], the MFR algorithm of Takagi ad Kleirock [15], ad their 2-hop variats [9]. Floodig algorithms use some type of cotrolled packet duplicatio mechaism to esure that every destiatio receives at least oe copy of the origial packet. These are exemplified by the locatio-aided routig (LAR) protocols of Ko ad Vaidya [7, 61. I order for floodig algorithms to termiate, packets i the etwork must remember which packets they have previously see. I cotrast, our routig algorithms always guaratee that a packet will be delivered to (all of) its iteded recipiet(s) so log as the uit graph U(S) is static.ad coected. Our algorithms do ot make use of ay memory at the odes of U(S) ad require oly that a packet carry a small costat amout of iformatio i additio to its message. Our algorithms also ever require duplicatio of a packet, so that at ay poit i time there is exactly oe copy of each message i the etwork. Although the delivery is guarateed oly for fixed graphs, it may be possible to apply our algorithms to movig hosts, i cojuctio with locatio update techiques [l, 71. Our algorithms work by fidig a coected plaar subgraph of U(S) ad the applyig routig algorithms for plaar graphs o this subgraph. I Sectio 2 we show how to fid a coected plaar subgraph of U(S) i a olie distributed maer. I Sectio 3 we describe algorithms for routig, broadcastig, ad geocastig i plaar graphs. I Sectio 4 we describe simulatio results for our algorithm. Fially, i Sectio 5 we summarize ad coclude with ope problems i the area. 2 Extractig a Coected Plaar Subgraph I this sectio we describe a distributed algorithm for extractig a coected plaar subgraph from U(S). I order to ru the algorithm, the oly iformatio eeded at each ode is the positio of each of its eighbors i U(S). Our algorithm works by computig the itersectio of U(S) with a well-kow plaar graph. Let di&(u, u) be the disk with diameter (.u, v). The, the Gabriel graph [5] GG(S) is a geometric graph i which the edge (u, v) is preset if ad oly if disk(u, w) cotais o other poits of S. The followig lemma shows that the Gabriel graph is useful for extractig a coected subgraph from U(S). Lemma 1. If U(S) is coected the GG(S) U(S) is coected. Proof. It is well kow that a miimum spaig tree MST(S) is a subset of GG(S) [13]. Thus, we eed oly prove that MST(S) c U(S) if U(S) is coected. Assume for the sake of cotradictio that MST(S) co- tais a edge (21, w) whose legth is greater tha 1. Removig this edge from MST(S) produces a graph with two coected compoets, &(S) ad C,,(S). Sice U(S) is coected it cotais a edge (w,z) of legth ot greater tha 1 such that w E C,(S) ad z E C,(S). By replacig the edge (u,v) with (w,z) i MST(S) we obtai a coected graph o S with weight less tha MST(S), a cotradictio. 0 Let (u, w) be a edge of U(S) such that (u,v) $! GG(S). The, by the defiitio of GG(S) there exists a poit w that is cotaied i the disk with u ad u as diameter, ad this poit acts as a witess that (21, w) 4 GG(S). The followig lemma shows that every such edge ca be idetified ad elimiated by u ad w usig oly local iformatio. Lemma 2. Let u ad w be poits of U(S) such that (u, w) 4 GG(S) ad 1 e t w be a witess to this. The (u, w) E U(S) ad (w,w) E U(S). Proof. Let m be the midpoit of (.u, w). The dist(u, m) 5 l/2, dist(w,m) 5 l/2 ad dist(w,m) 5 l/2. Therefore, by the triagle iequality, dist(u, w) 5 1, dist(w, 20) < 1 ad (2~, w) ad (v, w) are i U(S). cl Thus, upo reachig a vertex w E S, a packet ca elimiate the edges icidet o w that are ot i U(S) fl GG(S) by simply elimiatig ay edge that is ot i GG(N(w) U {w}). This leads to the followig algorithm that is executed by each vertex w E S. Algorithm: GABRIEL 1: for each 2~ E N(v) do 2: if disk(u, w) (N(w) \ {u, w}) # 0 the 3: delete (u, w) 4: ed if 5: ed for Lemma 1 guaratees that if we apply this algorithm to each vertex of S the the resultig graph is coected. Sice GG(S) is plaar [12, 10, 51, the resultig graph is also plaar. As described above, the algorithm requires O(d2) time, where d is the degree of w. By usig efficiet algorithms for costructig the Vorooi diagram (VD) ad Delauay triagulatio (DT) [12,13] of N(v) U {v}, ad keepig edges of DT that itersect correspodig edges of VD [lo, 51, this ca be reduced to O(dlogd). Theorem 1. If U(S) as. coected the algorithm GABRIEL computes a coected plaar subgraph of U(S). The cost of the computatio performed at vertex w E S is O(d log d) where d is the degree of w. Remark: More realistically, the elimiatio of edges ot i GG(S) could be doe whe the etwork is iitialized or whe chages i etwork topology occur. 49
3 Figure 1: Routig from w,, to vdst usig FACE-~. Figure 2: Routig from w,,, to U&t usig FACE-2. 3 Routig i Plaar Graphs I this sectio we describe olie algorithms for routig, broadcastig, ad geocastig i a coected plaar graph G. Sice we have show that a coected plaar subgraph of U(S) is easily computable by a routig algorithm, these algorithms also apply to uit graphs. 3.1 Routig I this sectio we describe algorithms for routig i plaar graphs. The first algorithm, called FACE- 1, is due to Kraakis et al [8]. The secod algorithm, called FACE-Z, is a modificatio of their algorithm that performs better i practice. A coected plaar graph G partitios the plae ito faces that are bouded by polygoals made up of edges of G. Give a vertex v o a face F, the boudary of F ca be traversed i the couterclockwise (clockwise if F is the outer face) directio usig the well-kow right had rmle [2]. Treatig this face traversal techique as a subroutie, Kraakis et al [8] give the followig algorithm for routig a packet from v,, to U&t. Algorithm: FACE- 1 1: P+~src 2: repeat 3: let F be the face of G with p o its boudary that itersects lie segmet (p, 2)&t) 4: for each edge (u, V) of F do 5: if (u,v) itersects (p,v,jst) i a poit p ad dist(p, U&t) < dist(p, wdst) the 6: P + P 7: ed if 8: ed for 9: Traverse F util reachig the edge (u, v) cotai- ig P lo: util p = v&t The operatio of algorithm FACE-~ algorithm is illustrated i Figure 1. The followig theorem summarizes the performace of this algorithm. Theorem 2 (KSU 1999 [8]). Algorithm FACE-~ reaches u&t after at most 41Ej steps, where IEl is the umber of edges i G. Notice that this algorithm traverses the etire face F to determie the poit p, ad the must retur to the poit p. The boud 4lE( stated i the theorem ca be reduced to 3lEI by havig the retur trip to p.be alog the shorter of the two possible paths aroud F. However, i practice, as we will show i Sectio 4, the followig modified versio of FACE-~ works eve better. Algorithm: FACE-2 1: p+vsrc 2: repeat 3: let F be the face of G with p o its boudary that itersects (p, v&t) 4: traverse F util reachig a edge (u, w) that itersects (p, U&t) at some poit p # p 5: P + P 6: util p = V&t The operatio of FACE-:! is illustrated i Figure 2. Clearly this algorithm also termiates i a fiite umber of steps, sice the distace to V&t is decreasig durig each roud. However, i pathological cases it may visit fl(2) edges of G. Theorem 3. Algorithm FACE-2 reaches v&t i a fiite umber of steps. 3.2 Broadcastig De Berg et al [4] describe a algorithm for eumeratig all the faces, edges, ad vertices of a coected embedded plaar graph G. It requires o memory at the odes of the graph ad uses oly O(1) additioal memory i the packet that is travelig aroud the etwork. The algorithm works by defiig a spaig tree o the faces of G ad performig depth first search o this spaig tree i O( ) time, where is the umber of vertices of G.l This algorithm ca be made ito a routig algorithm that allows a sigle packet to visit every vertex i G. We refer to this algorithm as BROADCAST. Theorem 4. I at most O(2) steps algotithm BROAD- CAST termiates after havig visited every vertex of G. Actually, the algorithm has ruig time 0 (xi IFi I ) where IFi ( deotes umber of edges i the ith face of G. 50
4 3.3 Geocastig De Berg et al also exted their results to widow queries i which all the faces itersectig a rectagular or circular query regio r&t are to be visited. To start their algorithm, a vertex of a face that itersects r&t must be give as part of the iput. By applyig Algorithm FACE-~, such a face ca be foud i O() steps by settig the value of v&t to the ceter of the query regio. The algorithm should termiate whe it reaches a vertex v cotaied i T&t or whe it ca o loger make progress, i.e., it visits the same face twice. I the first case we apply the algorithm of de Berg et al to have the packet visit every vertex i the query regio, while i the secod case we ca quit, sice there is o vertex of G cotaied i the query regio. We call this algorithm GEOCAST. Theorem 5. I at most O(+ic2) steps algorithm GEO- CAST termiates after havig visited every vertex of G cotaied i T&t, where k is the complexity of all faces of G that itersect r&t. Remark: The delivery time for a message i the broadcastig ad geocastig algorithms ca be improved i practice by traversig subtrees of the spaig tree i parallel, at the cost of havig several copies of the same packet i the etwork simultaeously. 4 Experimetal Results I this sectio we measure the quality of the paths foud by our routig algorithms. Our test sets cosist of radomly costructed uit graphs. Test cases were geerated by uiformly selectig poits i the uit square as vertices, sortig all the ( - 1)/2 iterpoit distaces ad settig the value of a uit to achieve the desired average degree. Ay such radom graph that did ot result i a coected graph was rejected. For each graph geerated, routig was performed betwee all ( - 1) ordered pairs of vertices i the graph. Every data poit show i our graphs is the average of 200 idepedet trials coducted o 200 differet radomly geerated graphs. The results of these trials are give as 95% cofidece itervals i Appedix A. For compariso purposes the performace of our algorithms were measured agaist, ad i combiatio with, geographic distace routig (GEDIR) as described by Li ad StojmeoviC [9]. The GEDIR algorithm is a greedy algorithm that always moves the packet to the eighbour of the curret vertex whose distace to the destiatio is miimized. The algorithm fails whe the packet crosses the same edge twice i successio. The GEDIR algorithm was chose for compariso purposes because, of the three basic algorithms tested by Li ad StojmeoviC, GEDIR had the best performace i terms of delivery rate ad average dilatio (defied below). Figure 3: Delivery rates for the GEDIR algorithm. The experimets measured two quatities. Let X be the set of pairs of vertices (u, w) E G, u # u such that routig algorithm A succeeds i fidig a path from u to v ad let 1x1 deote the cardiality of X. The delivery rate of A is defied as D&(G) = IXl/(( - 1)). Note that, because our algorithms guaratee the delivery of a packet, they have a delivery rate of 1. The average dilatio of A is defied as ADA(G) = (l/lx/> c AP(%v)/SP(u,v), (%V)EX where AP(u, v) is the umber of edges i the path from u to v foud by A ad SP(u, v) is the umber of edges i the shortest path from u to o. Note that havig a low average dilatio is oly useful if the delivery rate is high sice a average dilatio of 1 is easily achieved by (for example) a algorithm that oly succeeds i routig betwee two odes if they axe directly adjacet. To illustrate the importace of havig guarateed delivery of messages, Figure 3 shows the delivery rate of GEDIR o graphs with varyig average degrees ad umber of odes. These results show that delivery failures are ot ucommo with the GEDIR algorithm, ad i very sparse graphs delivery rates ca be as low as 50%. I.e., there are some vertices from which half of the graph is ureachable. Figure 4 compares the FACE-~ algorithm with the FACE-~ algorithm i terms of average dilatio for varyig average degrees ad umber of odes. Not surprisigly, FACE-~ outperforms FACE- 1 due to the fact that it does ot require the packet to travel all the way aroud each face. What may be surprisig is that the average dilatio for both strategies seems to icrease as the average degree icreases. This ca be explaied by the fact that the subgraph GG(S) U(S) o which these algorithms operate is a plaar graph ad therefore has 51
5 Figure 4: Average dilatio algorithms. of the FACE-~ ad FACE-2 Figure 6: Average dilatio rithms. of the GEDIR ad GFG algo- Figure 5: Average dilatio of the GEDIR ad GEDIR+FACE-2 algorithms. average degree at most 6, but they are beig compared to the shortest path i U(S) whose average degree is icreasig. Thus, the algorithms are hadicapped from the start. Although these observatios may lead oe to believe that algorithms FACE-~ ad FACE-2 are ot very good o their ow, they may evertheless be useful i combiatio with aother algorithm. We tested two such combiatios ad compared their average dilatio with the average dilatio of GEDIR. Figure 5 shows the results of combiig the GEDIR algorithm with FACE-~ by applyig the GEDIR algorithm util it either failed or reached the destiatio. If the GEDIR algorithm failed, routig was the completed usig the FACE-2 algorithm. I this sceario FACE-2 ca be viewed as actig as a backup for the GEDIR algorithm. We refer to this algorithm as GEDIR+FACE-2. Figure 6 shows the results of applyig GEDIR util the packet reaches a ode v such that all of v s eighbours are further from the destiatio tha v is. The FACE-2 algorithm was the applied util the packet reached aother vertex u that was strictly closer to the destiatio tha Y at which poit the GEDIR algorithm was resumed. I this sceario, FACE-2 ca be see as a meas of overcomig local miima i the objective fuctio (distace to the destiatio). We refer to this algorithm as GFG. Both these hybrid algorithms exhibit similar performace with the GFG algorithm showig a slight advatage i very sparse graphs. These results show that the average dilatio of GEDIR is cosistetly low, but this comes at the price of low delivery rate i sparse graphs. O the other had, the combied algorithms sometime have high average dilatio, but this oly occurs whe the delivery rate of GEDIR is low ad the combied algorithms are ofte forced to apply the FACE-2 algorithm. The combied algorithm simultaeously ejoys the advatages guarateed delivery i sparse graphs ad low average dilatio i dese graphs. 5 Coclusios We have described algorithms for routig, broadcastig, ad geocastig i uit graphs. The algorithms do ot require duplicatio of packets or memory at the odes of the graph ad yet guaratee that a packet is always delivered to (all of) its destiatio(s). The empirical results for our routig algorithms suggest that although the FACE-~ ad FACE-2 algorithms are ot very efficiet o their ow, they ca be useful i cojuctio with simpler algorithms that do ot guaratee delivery. The BROADCAST ad GEOCAST algorithms are probably ot very applicable i practice due to their quadratic message cout ad delivery time behaviour. A iterestig ope problem that is curretly uder ivestigatio is whether or ot algorithms exist that do ot require memory at the odes of U(S) ad takes subquadratic time to visit all vertices of U(S). Results for static etworks like those i this ad
6 other papers [9] help i fidig the most promisig cadidates for the desig of routig protocols i mobile etworks. There are a umber of directios i which the work preseted here ca be exteded ad/or geeralized, icludig results for dyamically chagig etworks, etworks i three-dimesioal space, odes with uequal trasmissio rages, ad power-aware routig schemes [ 141. Refereces [l] S. Basagi, I. Chlamtac, V. R. Syrotiuk, ad B. A. Woodward. A distace routig effect algorithm for mobility (DREAM). I ACM/IEEE Iteratioal Coferece o Mobile Computig ad Networkig (Mobicom 98), pages 76-84, [2] J. A. Body ad U. S. R. Murty. Graph Theory with Applicatios. Elsevier North-Hollad, [3] D. Camara ad A. F. Loureiro. A ovel routig algorithm for ad hoc etworks. Mauscript, [4] M. de Berg, M. va Kreveld, R. va Oostrum, ad M. Overmars. Simple traversal of a subdivisio without extra storage. Iteratioal Joural of Geographic Iformatio Systems, 11: , [5] K. R. Gabriel ad R. R. Sokal. A ew statistical approach to geographic variatio aalysis. Systematic Zoology, 18: , [S] Y.-B. Ko ad N. H. Vaidya. Geocastig i mobile ad hoc etworks: Locatio-based multicast algorithms. Techical Report TR , Texas A&M Uiversity, September [7] Y.-B. Ko ad N. H. Vaidya. Locatio-aided routig (LAR) i mobile ad hoc etworks. I ACM/IEEE Iteratioal Coferece o Mobile Computig ad Networkig (Mobicom%), pages 66-75, [8] E. Kraakis, H. Sigh, ad J. Urrutia. Compass routig o geometric etworks. I Proceedigs of the 11th Caadia Coferece o Computatioal Geometry (CCCG 99), To appear. [9] X. Li ad I. Stojmeovic. Geographic distace routig i ad hoc wireless etworks. Techical Report TR-98-10, SITE, Uiversity of Ottawa, December [lo] D. W. Matula ad R. R. Sokal. Properties of Gabriel graphs relevat to geographic variatio research ad the clusterig of poits i the plae. Geographical Aalysis, 12:205, July [ll] J. C. Navas ad T. Imieliski. Geocast - geographic addressig ad routig. I ACM/IEEE Iteratioal Coferece o Mobile Computig ad Networkig (Mobicom 97), pages 66-76, PI P31 WI 1151 A A. Okabe, B. Boots, ad K. Sugihara. Spatial Tesselatios: Cocepts ad Applicatios of Vorooi Diagrams. Joh Wiley ad Sos, Frac0 P. Preparata ad Michael Ia Shamos. Computatioal Geometry. Spriger-Verlag, New York, I. StojmeoviC. Power-aware routig i ad hoc wireless etworks. Techical Report TR-98-11, SITE, Uiversity of Ottawa, December H. Takagi ad L. Kleirock. Optimal trasmissio rages for radomly distributed packet radio termials. IEEE l%asactios o Commuicatios, 32(3): , Simulatio Results This appedix presets the results of simulatios i tabular form. The variable d is the average degree of the graph ad the variable is the umber of vertices i the graph. 53
7 d f rt f f f f f f f l.oof f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f Table 1: 95% cofidece itervals for delivery rates of GEDIR. d f f f f f f f f f f f f f f f f f f f f III f f f f f f zt f f f f f f f f f f f f f f f f f Table 2: 95% cofidece itervals for average dilatio of GEDIR. d f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f Table 3: 95% cofidece itervals for average dilatio of FACE-~. 54
8 d f f f f f f f f f f f % f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f f Table 4: 95% cofidece itervals for average dilatio of FACE-Z. d f f f f f f zt f f l.oof f f f f f f f f % f f f f f f f f f f f f f f f f f f f ho f ho f ho f Table 5: 95% cofidece itervals for average dilatio of GEDIR+FACE-2. d YO 1.22f f f f l.oofo.ooo f f f f f zk f f & f f f % f f f f z!z f f f f f f f f Ifr f f f f f f f f f f f ho f Table 6: 95% cofidece itervals for average dilatio of GFG. 55
Computational Geometry
 Computatioal Geometry Chapter 4 Liear programmig Duality Smallest eclosig disk O the Ageda Liear Programmig Slides courtesy of Craig Gotsma 4. 4. Liear Programmig - Example Defie: (amout amout cosumed
Computatioal Geometry Chapter 4 Liear programmig Duality Smallest eclosig disk O the Ageda Liear Programmig Slides courtesy of Craig Gotsma 4. 4. Liear Programmig - Example Defie: (amout amout cosumed
3D Model Retrieval Method Based on Sample Prediction
 20 Iteratioal Coferece o Computer Commuicatio ad Maagemet Proc.of CSIT vol.5 (20) (20) IACSIT Press, Sigapore 3D Model Retrieval Method Based o Sample Predictio Qigche Zhag, Ya Tag* School of Computer
20 Iteratioal Coferece o Computer Commuicatio ad Maagemet Proc.of CSIT vol.5 (20) (20) IACSIT Press, Sigapore 3D Model Retrieval Method Based o Sample Predictio Qigche Zhag, Ya Tag* School of Computer
On (K t e)-saturated Graphs
 Noame mauscript No. (will be iserted by the editor O (K t e-saturated Graphs Jessica Fuller Roald J. Gould the date of receipt ad acceptace should be iserted later Abstract Give a graph H, we say a graph
Noame mauscript No. (will be iserted by the editor O (K t e-saturated Graphs Jessica Fuller Roald J. Gould the date of receipt ad acceptace should be iserted later Abstract Give a graph H, we say a graph
Combination Labelings Of Graphs
 Applied Mathematics E-Notes, (0), - c ISSN 0-0 Available free at mirror sites of http://wwwmaththuedutw/ame/ Combiatio Labeligs Of Graphs Pak Chig Li y Received February 0 Abstract Suppose G = (V; E) is
Applied Mathematics E-Notes, (0), - c ISSN 0-0 Available free at mirror sites of http://wwwmaththuedutw/ame/ Combiatio Labeligs Of Graphs Pak Chig Li y Received February 0 Abstract Suppose G = (V; E) is
Algorithms for Disk Covering Problems with the Most Points
 Algorithms for Disk Coverig Problems with the Most Poits Bi Xiao Departmet of Computig Hog Kog Polytechic Uiversity Hug Hom, Kowloo, Hog Kog csbxiao@comp.polyu.edu.hk Qigfeg Zhuge, Yi He, Zili Shao, Edwi
Algorithms for Disk Coverig Problems with the Most Poits Bi Xiao Departmet of Computig Hog Kog Polytechic Uiversity Hug Hom, Kowloo, Hog Kog csbxiao@comp.polyu.edu.hk Qigfeg Zhuge, Yi He, Zili Shao, Edwi
Lecture 5. Counting Sort / Radix Sort
 Lecture 5. Coutig Sort / Radix Sort T. H. Corme, C. E. Leiserso ad R. L. Rivest Itroductio to Algorithms, 3rd Editio, MIT Press, 2009 Sugkyukwa Uiversity Hyuseug Choo choo@skku.edu Copyright 2000-2018
Lecture 5. Coutig Sort / Radix Sort T. H. Corme, C. E. Leiserso ad R. L. Rivest Itroductio to Algorithms, 3rd Editio, MIT Press, 2009 Sugkyukwa Uiversity Hyuseug Choo choo@skku.edu Copyright 2000-2018
1 Graph Sparsfication
 CME 305: Discrete Mathematics ad Algorithms 1 Graph Sparsficatio I this sectio we discuss the approximatio of a graph G(V, E) by a sparse graph H(V, F ) o the same vertex set. I particular, we cosider
CME 305: Discrete Mathematics ad Algorithms 1 Graph Sparsficatio I this sectio we discuss the approximatio of a graph G(V, E) by a sparse graph H(V, F ) o the same vertex set. I particular, we cosider
Cubic Polynomial Curves with a Shape Parameter
 roceedigs of the th WSEAS Iteratioal Coferece o Robotics Cotrol ad Maufacturig Techology Hagzhou Chia April -8 00 (pp5-70) Cubic olyomial Curves with a Shape arameter MO GUOLIANG ZHAO YANAN Iformatio ad
roceedigs of the th WSEAS Iteratioal Coferece o Robotics Cotrol ad Maufacturig Techology Hagzhou Chia April -8 00 (pp5-70) Cubic olyomial Curves with a Shape arameter MO GUOLIANG ZHAO YANAN Iformatio ad
Counting the Number of Minimum Roman Dominating Functions of a Graph
 Coutig the Number of Miimum Roma Domiatig Fuctios of a Graph SHI ZHENG ad KOH KHEE MENG, Natioal Uiversity of Sigapore We provide two algorithms coutig the umber of miimum Roma domiatig fuctios of a graph
Coutig the Number of Miimum Roma Domiatig Fuctios of a Graph SHI ZHENG ad KOH KHEE MENG, Natioal Uiversity of Sigapore We provide two algorithms coutig the umber of miimum Roma domiatig fuctios of a graph
Random Graphs and Complex Networks T
 Radom Graphs ad Complex Networks T-79.7003 Charalampos E. Tsourakakis Aalto Uiversity Lecture 3 7 September 013 Aoucemet Homework 1 is out, due i two weeks from ow. Exercises: Probabilistic iequalities
Radom Graphs ad Complex Networks T-79.7003 Charalampos E. Tsourakakis Aalto Uiversity Lecture 3 7 September 013 Aoucemet Homework 1 is out, due i two weeks from ow. Exercises: Probabilistic iequalities
CHAPTER IV: GRAPH THEORY. Section 1: Introduction to Graphs
 CHAPTER IV: GRAPH THEORY Sectio : Itroductio to Graphs Sice this class is called Number-Theoretic ad Discrete Structures, it would be a crime to oly focus o umber theory regardless how woderful those topics
CHAPTER IV: GRAPH THEORY Sectio : Itroductio to Graphs Sice this class is called Number-Theoretic ad Discrete Structures, it would be a crime to oly focus o umber theory regardless how woderful those topics
The isoperimetric problem on the hypercube
 The isoperimetric problem o the hypercube Prepared by: Steve Butler November 2, 2005 1 The isoperimetric problem We will cosider the -dimesioal hypercube Q Recall that the hypercube Q is a graph whose
The isoperimetric problem o the hypercube Prepared by: Steve Butler November 2, 2005 1 The isoperimetric problem We will cosider the -dimesioal hypercube Q Recall that the hypercube Q is a graph whose
condition w i B i S maximum u i
 ecture 10 Dyamic Programmig 10.1 Kapsack Problem November 1, 2004 ecturer: Kamal Jai Notes: Tobias Holgers We are give a set of items U = {a 1, a 2,..., a }. Each item has a weight w i Z + ad a utility
ecture 10 Dyamic Programmig 10.1 Kapsack Problem November 1, 2004 ecturer: Kamal Jai Notes: Tobias Holgers We are give a set of items U = {a 1, a 2,..., a }. Each item has a weight w i Z + ad a utility
An Efficient Algorithm for Graph Bisection of Triangularizations
 A Efficiet Algorithm for Graph Bisectio of Triagularizatios Gerold Jäger Departmet of Computer Sciece Washigto Uiversity Campus Box 1045 Oe Brookigs Drive St. Louis, Missouri 63130-4899, USA jaegerg@cse.wustl.edu
A Efficiet Algorithm for Graph Bisectio of Triagularizatios Gerold Jäger Departmet of Computer Sciece Washigto Uiversity Campus Box 1045 Oe Brookigs Drive St. Louis, Missouri 63130-4899, USA jaegerg@cse.wustl.edu
Lecture 1: Introduction and Strassen s Algorithm
 5-750: Graduate Algorithms Jauary 7, 08 Lecture : Itroductio ad Strasse s Algorithm Lecturer: Gary Miller Scribe: Robert Parker Itroductio Machie models I this class, we will primarily use the Radom Access
5-750: Graduate Algorithms Jauary 7, 08 Lecture : Itroductio ad Strasse s Algorithm Lecturer: Gary Miller Scribe: Robert Parker Itroductio Machie models I this class, we will primarily use the Radom Access
Graphs. Minimum Spanning Trees. Slides by Rose Hoberman (CMU)
 Graphs Miimum Spaig Trees Slides by Rose Hoberma (CMU) Problem: Layig Telephoe Wire Cetral office 2 Wirig: Naïve Approach Cetral office Expesive! 3 Wirig: Better Approach Cetral office Miimize the total
Graphs Miimum Spaig Trees Slides by Rose Hoberma (CMU) Problem: Layig Telephoe Wire Cetral office 2 Wirig: Naïve Approach Cetral office Expesive! 3 Wirig: Better Approach Cetral office Miimize the total
An Efficient Algorithm for Graph Bisection of Triangularizations
 Applied Mathematical Scieces, Vol. 1, 2007, o. 25, 1203-1215 A Efficiet Algorithm for Graph Bisectio of Triagularizatios Gerold Jäger Departmet of Computer Sciece Washigto Uiversity Campus Box 1045, Oe
Applied Mathematical Scieces, Vol. 1, 2007, o. 25, 1203-1215 A Efficiet Algorithm for Graph Bisectio of Triagularizatios Gerold Jäger Departmet of Computer Sciece Washigto Uiversity Campus Box 1045, Oe
An Improved Shuffled Frog-Leaping Algorithm for Knapsack Problem
 A Improved Shuffled Frog-Leapig Algorithm for Kapsack Problem Zhoufag Li, Ya Zhou, ad Peg Cheg School of Iformatio Sciece ad Egieerig Hea Uiversity of Techology ZhegZhou, Chia lzhf1978@126.com Abstract.
A Improved Shuffled Frog-Leapig Algorithm for Kapsack Problem Zhoufag Li, Ya Zhou, ad Peg Cheg School of Iformatio Sciece ad Egieerig Hea Uiversity of Techology ZhegZhou, Chia lzhf1978@126.com Abstract.
Ones Assignment Method for Solving Traveling Salesman Problem
 Joural of mathematics ad computer sciece 0 (0), 58-65 Oes Assigmet Method for Solvig Travelig Salesma Problem Hadi Basirzadeh Departmet of Mathematics, Shahid Chamra Uiversity, Ahvaz, Ira Article history:
Joural of mathematics ad computer sciece 0 (0), 58-65 Oes Assigmet Method for Solvig Travelig Salesma Problem Hadi Basirzadeh Departmet of Mathematics, Shahid Chamra Uiversity, Ahvaz, Ira Article history:
Bezier curves. Figure 2 shows cubic Bezier curves for various control points. In a Bezier curve, only
 Edited: Yeh-Liag Hsu (998--; recommeded: Yeh-Liag Hsu (--9; last updated: Yeh-Liag Hsu (9--7. Note: This is the course material for ME55 Geometric modelig ad computer graphics, Yua Ze Uiversity. art of
Edited: Yeh-Liag Hsu (998--; recommeded: Yeh-Liag Hsu (--9; last updated: Yeh-Liag Hsu (9--7. Note: This is the course material for ME55 Geometric modelig ad computer graphics, Yua Ze Uiversity. art of
CS 683: Advanced Design and Analysis of Algorithms
 CS 683: Advaced Desig ad Aalysis of Algorithms Lecture 6, February 1, 2008 Lecturer: Joh Hopcroft Scribes: Shaomei Wu, Etha Feldma February 7, 2008 1 Threshold for k CNF Satisfiability I the previous lecture,
CS 683: Advaced Desig ad Aalysis of Algorithms Lecture 6, February 1, 2008 Lecturer: Joh Hopcroft Scribes: Shaomei Wu, Etha Feldma February 7, 2008 1 Threshold for k CNF Satisfiability I the previous lecture,
The Closest Line to a Data Set in the Plane. David Gurney Southeastern Louisiana University Hammond, Louisiana
 The Closest Lie to a Data Set i the Plae David Gurey Southeaster Louisiaa Uiversity Hammod, Louisiaa ABSTRACT This paper looks at three differet measures of distace betwee a lie ad a data set i the plae:
The Closest Lie to a Data Set i the Plae David Gurey Southeaster Louisiaa Uiversity Hammod, Louisiaa ABSTRACT This paper looks at three differet measures of distace betwee a lie ad a data set i the plae:
6.854J / J Advanced Algorithms Fall 2008
 MIT OpeCourseWare http://ocw.mit.edu 6.854J / 18.415J Advaced Algorithms Fall 2008 For iformatio about citig these materials or our Terms of Use, visit: http://ocw.mit.edu/terms. 18.415/6.854 Advaced Algorithms
MIT OpeCourseWare http://ocw.mit.edu 6.854J / 18.415J Advaced Algorithms Fall 2008 For iformatio about citig these materials or our Terms of Use, visit: http://ocw.mit.edu/terms. 18.415/6.854 Advaced Algorithms
Improvement of the Orthogonal Code Convolution Capabilities Using FPGA Implementation
 Improvemet of the Orthogoal Code Covolutio Capabilities Usig FPGA Implemetatio Naima Kaabouch, Member, IEEE, Apara Dhirde, Member, IEEE, Saleh Faruque, Member, IEEE Departmet of Electrical Egieerig, Uiversity
Improvemet of the Orthogoal Code Covolutio Capabilities Usig FPGA Implemetatio Naima Kaabouch, Member, IEEE, Apara Dhirde, Member, IEEE, Saleh Faruque, Member, IEEE Departmet of Electrical Egieerig, Uiversity
CIS 121 Data Structures and Algorithms with Java Spring Stacks and Queues Monday, February 12 / Tuesday, February 13
 CIS Data Structures ad Algorithms with Java Sprig 08 Stacks ad Queues Moday, February / Tuesday, February Learig Goals Durig this lab, you will: Review stacks ad queues. Lear amortized ruig time aalysis
CIS Data Structures ad Algorithms with Java Sprig 08 Stacks ad Queues Moday, February / Tuesday, February Learig Goals Durig this lab, you will: Review stacks ad queues. Lear amortized ruig time aalysis
Lecturers: Sanjam Garg and Prasad Raghavendra Feb 21, Midterm 1 Solutions
 U.C. Berkeley CS170 : Algorithms Midterm 1 Solutios Lecturers: Sajam Garg ad Prasad Raghavedra Feb 1, 017 Midterm 1 Solutios 1. (4 poits) For the directed graph below, fid all the strogly coected compoets
U.C. Berkeley CS170 : Algorithms Midterm 1 Solutios Lecturers: Sajam Garg ad Prasad Raghavedra Feb 1, 017 Midterm 1 Solutios 1. (4 poits) For the directed graph below, fid all the strogly coected compoets
Python Programming: An Introduction to Computer Science
 Pytho Programmig: A Itroductio to Computer Sciece Chapter 6 Defiig Fuctios Pytho Programmig, 2/e 1 Objectives To uderstad why programmers divide programs up ito sets of cooperatig fuctios. To be able to
Pytho Programmig: A Itroductio to Computer Sciece Chapter 6 Defiig Fuctios Pytho Programmig, 2/e 1 Objectives To uderstad why programmers divide programs up ito sets of cooperatig fuctios. To be able to
A New Morphological 3D Shape Decomposition: Grayscale Interframe Interpolation Method
 A ew Morphological 3D Shape Decompositio: Grayscale Iterframe Iterpolatio Method D.. Vizireau Politehica Uiversity Bucharest, Romaia ae@comm.pub.ro R. M. Udrea Politehica Uiversity Bucharest, Romaia mihea@comm.pub.ro
A ew Morphological 3D Shape Decompositio: Grayscale Iterframe Iterpolatio Method D.. Vizireau Politehica Uiversity Bucharest, Romaia ae@comm.pub.ro R. M. Udrea Politehica Uiversity Bucharest, Romaia mihea@comm.pub.ro
Accuracy Improvement in Camera Calibration
 Accuracy Improvemet i Camera Calibratio FaJie L Qi Zag ad Reihard Klette CITR, Computer Sciece Departmet The Uiversity of Aucklad Tamaki Campus, Aucklad, New Zealad fli006, qza001@ec.aucklad.ac.z r.klette@aucklad.ac.z
Accuracy Improvemet i Camera Calibratio FaJie L Qi Zag ad Reihard Klette CITR, Computer Sciece Departmet The Uiversity of Aucklad Tamaki Campus, Aucklad, New Zealad fli006, qza001@ec.aucklad.ac.z r.klette@aucklad.ac.z
Parabolic Path to a Best Best-Fit Line:
 Studet Activity : Fidig the Least Squares Regressio Lie By Explorig the Relatioship betwee Slope ad Residuals Objective: How does oe determie a best best-fit lie for a set of data? Eyeballig it may be
Studet Activity : Fidig the Least Squares Regressio Lie By Explorig the Relatioship betwee Slope ad Residuals Objective: How does oe determie a best best-fit lie for a set of data? Eyeballig it may be
IMP: Superposer Integrated Morphometrics Package Superposition Tool
 IMP: Superposer Itegrated Morphometrics Package Superpositio Tool Programmig by: David Lieber ( 03) Caisius College 200 Mai St. Buffalo, NY 4208 Cocept by: H. David Sheets, Dept. of Physics, Caisius College
IMP: Superposer Itegrated Morphometrics Package Superpositio Tool Programmig by: David Lieber ( 03) Caisius College 200 Mai St. Buffalo, NY 4208 Cocept by: H. David Sheets, Dept. of Physics, Caisius College
Perhaps the method will give that for every e > U f() > p - 3/+e There is o o-trivial upper boud for f() ad ot eve f() < Z - e. seems to be kow, where
 ON MAXIMUM CHORDAL SUBGRAPH * Paul Erdos Mathematical Istitute of the Hugaria Academy of Scieces ad Reu Laskar Clemso Uiversity 1. Let G() deote a udirected graph, with vertices ad V(G) deote the vertex
ON MAXIMUM CHORDAL SUBGRAPH * Paul Erdos Mathematical Istitute of the Hugaria Academy of Scieces ad Reu Laskar Clemso Uiversity 1. Let G() deote a udirected graph, with vertices ad V(G) deote the vertex
Lecture 2: Spectra of Graphs
 Spectral Graph Theory ad Applicatios WS 20/202 Lecture 2: Spectra of Graphs Lecturer: Thomas Sauerwald & He Su Our goal is to use the properties of the adjacecy/laplacia matrix of graphs to first uderstad
Spectral Graph Theory ad Applicatios WS 20/202 Lecture 2: Spectra of Graphs Lecturer: Thomas Sauerwald & He Su Our goal is to use the properties of the adjacecy/laplacia matrix of graphs to first uderstad
Performance Plus Software Parameter Definitions
 Performace Plus+ Software Parameter Defiitios/ Performace Plus Software Parameter Defiitios Chapma Techical Note-TG-5 paramete.doc ev-0-03 Performace Plus+ Software Parameter Defiitios/2 Backgroud ad Defiitios
Performace Plus+ Software Parameter Defiitios/ Performace Plus Software Parameter Defiitios Chapma Techical Note-TG-5 paramete.doc ev-0-03 Performace Plus+ Software Parameter Defiitios/2 Backgroud ad Defiitios
Pseudocode ( 1.1) Analysis of Algorithms. Primitive Operations. Pseudocode Details. Running Time ( 1.1) Estimating performance
 Aalysis of Algorithms Iput Algorithm Output A algorithm is a step-by-step procedure for solvig a problem i a fiite amout of time. Pseudocode ( 1.1) High-level descriptio of a algorithm More structured
Aalysis of Algorithms Iput Algorithm Output A algorithm is a step-by-step procedure for solvig a problem i a fiite amout of time. Pseudocode ( 1.1) High-level descriptio of a algorithm More structured
Copyright 2016 Ramez Elmasri and Shamkant B. Navathe
 Copyright 2016 Ramez Elmasri ad Shamkat B. Navathe CHAPTER 18 Strategies for Query Processig Copyright 2016 Ramez Elmasri ad Shamkat B. Navathe Itroductio DBMS techiques to process a query Scaer idetifies
Copyright 2016 Ramez Elmasri ad Shamkat B. Navathe CHAPTER 18 Strategies for Query Processig Copyright 2016 Ramez Elmasri ad Shamkat B. Navathe Itroductio DBMS techiques to process a query Scaer idetifies
Minimum Spanning Trees
 Miimum Spaig Trees Miimum Spaig Trees Spaig subgraph Subgraph of a graph G cotaiig all the vertices of G Spaig tree Spaig subgraph that is itself a (free) tree Miimum spaig tree (MST) Spaig tree of a weighted
Miimum Spaig Trees Miimum Spaig Trees Spaig subgraph Subgraph of a graph G cotaiig all the vertices of G Spaig tree Spaig subgraph that is itself a (free) tree Miimum spaig tree (MST) Spaig tree of a weighted
Force Network Analysis using Complementary Energy
 orce Network Aalysis usig Complemetary Eergy Adrew BORGART Assistat Professor Delft Uiversity of Techology Delft, The Netherlads A.Borgart@tudelft.l Yaick LIEM Studet Delft Uiversity of Techology Delft,
orce Network Aalysis usig Complemetary Eergy Adrew BORGART Assistat Professor Delft Uiversity of Techology Delft, The Netherlads A.Borgart@tudelft.l Yaick LIEM Studet Delft Uiversity of Techology Delft,
FREQUENCY ESTIMATION OF INTERNET PACKET STREAMS WITH LIMITED SPACE: UPPER AND LOWER BOUNDS
 FREQUENCY ESTIMATION OF INTERNET PACKET STREAMS WITH LIMITED SPACE: UPPER AND LOWER BOUNDS Prosejit Bose Evagelos Kraakis Pat Mori Yihui Tag School of Computer Sciece, Carleto Uiversity {jit,kraakis,mori,y
FREQUENCY ESTIMATION OF INTERNET PACKET STREAMS WITH LIMITED SPACE: UPPER AND LOWER BOUNDS Prosejit Bose Evagelos Kraakis Pat Mori Yihui Tag School of Computer Sciece, Carleto Uiversity {jit,kraakis,mori,y
Relay Placement Based on Divide-and-Conquer
 Relay Placemet Based o Divide-ad-Coquer Ravabakhsh Akhlaghiia, Azadeh Kaviafar, ad Mohamad Javad Rostami, Member, IACSIT Abstract I this paper, we defie a relay placemet problem to cover a large umber
Relay Placemet Based o Divide-ad-Coquer Ravabakhsh Akhlaghiia, Azadeh Kaviafar, ad Mohamad Javad Rostami, Member, IACSIT Abstract I this paper, we defie a relay placemet problem to cover a large umber
The Adjacency Matrix and The nth Eigenvalue
 Spectral Graph Theory Lecture 3 The Adjacecy Matrix ad The th Eigevalue Daiel A. Spielma September 5, 2012 3.1 About these otes These otes are ot ecessarily a accurate represetatio of what happeed i class.
Spectral Graph Theory Lecture 3 The Adjacecy Matrix ad The th Eigevalue Daiel A. Spielma September 5, 2012 3.1 About these otes These otes are ot ecessarily a accurate represetatio of what happeed i class.
Exact Minimum Lower Bound Algorithm for Traveling Salesman Problem
 Exact Miimum Lower Boud Algorithm for Travelig Salesma Problem Mohamed Eleiche GeoTiba Systems mohamed.eleiche@gmail.com Abstract The miimum-travel-cost algorithm is a dyamic programmig algorithm to compute
Exact Miimum Lower Boud Algorithm for Travelig Salesma Problem Mohamed Eleiche GeoTiba Systems mohamed.eleiche@gmail.com Abstract The miimum-travel-cost algorithm is a dyamic programmig algorithm to compute
Multiprocessors. HPC Prof. Robert van Engelen
 Multiprocessors Prof. Robert va Egele Overview The PMS model Shared memory multiprocessors Basic shared memory systems SMP, Multicore, ad COMA Distributed memory multicomputers MPP systems Network topologies
Multiprocessors Prof. Robert va Egele Overview The PMS model Shared memory multiprocessors Basic shared memory systems SMP, Multicore, ad COMA Distributed memory multicomputers MPP systems Network topologies
Pattern Recognition Systems Lab 1 Least Mean Squares
 Patter Recogitio Systems Lab 1 Least Mea Squares 1. Objectives This laboratory work itroduces the OpeCV-based framework used throughout the course. I this assigmet a lie is fitted to a set of poits usig
Patter Recogitio Systems Lab 1 Least Mea Squares 1. Objectives This laboratory work itroduces the OpeCV-based framework used throughout the course. I this assigmet a lie is fitted to a set of poits usig
Minimum Spanning Trees
 Presetatio for use with the textbook, lgorithm esig ad pplicatios, by M. T. Goodrich ad R. Tamassia, Wiley, 0 Miimum Spaig Trees 0 Goodrich ad Tamassia Miimum Spaig Trees pplicatio: oectig a Network Suppose
Presetatio for use with the textbook, lgorithm esig ad pplicatios, by M. T. Goodrich ad R. Tamassia, Wiley, 0 Miimum Spaig Trees 0 Goodrich ad Tamassia Miimum Spaig Trees pplicatio: oectig a Network Suppose
Lecture Notes 6 Introduction to algorithm analysis CSS 501 Data Structures and Object-Oriented Programming
 Lecture Notes 6 Itroductio to algorithm aalysis CSS 501 Data Structures ad Object-Orieted Programmig Readig for this lecture: Carrao, Chapter 10 To be covered i this lecture: Itroductio to algorithm aalysis
Lecture Notes 6 Itroductio to algorithm aalysis CSS 501 Data Structures ad Object-Orieted Programmig Readig for this lecture: Carrao, Chapter 10 To be covered i this lecture: Itroductio to algorithm aalysis
New Results on Energy of Graphs of Small Order
 Global Joural of Pure ad Applied Mathematics. ISSN 0973-1768 Volume 13, Number 7 (2017), pp. 2837-2848 Research Idia Publicatios http://www.ripublicatio.com New Results o Eergy of Graphs of Small Order
Global Joural of Pure ad Applied Mathematics. ISSN 0973-1768 Volume 13, Number 7 (2017), pp. 2837-2848 Research Idia Publicatios http://www.ripublicatio.com New Results o Eergy of Graphs of Small Order
Look-ahead Geographic Routing for Sensor Networks
 1 Look-ahead Geographic Routig for Sesor Networks Jiaxi You 1, Domiik Lieckfeldt 1, Qi Ha, Jakob Salzma 1, ad Dirk Timmerma 1 1 Uiversity of Rostock, Germay 1 {jiaxi.you, domiik.lieckfeldt, jakob.salzma,
1 Look-ahead Geographic Routig for Sesor Networks Jiaxi You 1, Domiik Lieckfeldt 1, Qi Ha, Jakob Salzma 1, ad Dirk Timmerma 1 1 Uiversity of Rostock, Germay 1 {jiaxi.you, domiik.lieckfeldt, jakob.salzma,
Image Segmentation EEE 508
 Image Segmetatio Objective: to determie (etract) object boudaries. It is a process of partitioig a image ito distict regios by groupig together eighborig piels based o some predefied similarity criterio.
Image Segmetatio Objective: to determie (etract) object boudaries. It is a process of partitioig a image ito distict regios by groupig together eighborig piels based o some predefied similarity criterio.
CIS 121 Data Structures and Algorithms with Java Spring Stacks, Queues, and Heaps Monday, February 18 / Tuesday, February 19
 CIS Data Structures ad Algorithms with Java Sprig 09 Stacks, Queues, ad Heaps Moday, February 8 / Tuesday, February 9 Stacks ad Queues Recall the stack ad queue ADTs (abstract data types from lecture.
CIS Data Structures ad Algorithms with Java Sprig 09 Stacks, Queues, ad Heaps Moday, February 8 / Tuesday, February 9 Stacks ad Queues Recall the stack ad queue ADTs (abstract data types from lecture.
EVALUATION OF TRIGONOMETRIC FUNCTIONS
 EVALUATION OF TRIGONOMETRIC FUNCTIONS Whe first exposed to trigoometric fuctios i high school studets are expected to memorize the values of the trigoometric fuctios of sie cosie taget for the special
EVALUATION OF TRIGONOMETRIC FUNCTIONS Whe first exposed to trigoometric fuctios i high school studets are expected to memorize the values of the trigoometric fuctios of sie cosie taget for the special
Minimum Spanning Trees. Application: Connecting a Network
 Miimum Spaig Tree // : Presetatio for use with the textbook, lgorithm esig ad pplicatios, by M. T. oodrich ad R. Tamassia, Wiley, Miimum Spaig Trees oodrich ad Tamassia Miimum Spaig Trees pplicatio: oectig
Miimum Spaig Tree // : Presetatio for use with the textbook, lgorithm esig ad pplicatios, by M. T. oodrich ad R. Tamassia, Wiley, Miimum Spaig Trees oodrich ad Tamassia Miimum Spaig Trees pplicatio: oectig
Lecture 18. Optimization in n dimensions
 Lecture 8 Optimizatio i dimesios Itroductio We ow cosider the problem of miimizig a sigle scalar fuctio of variables, f x, where x=[ x, x,, x ]T. The D case ca be visualized as fidig the lowest poit of
Lecture 8 Optimizatio i dimesios Itroductio We ow cosider the problem of miimizig a sigle scalar fuctio of variables, f x, where x=[ x, x,, x ]T. The D case ca be visualized as fidig the lowest poit of
Strong Complementary Acyclic Domination of a Graph
 Aals of Pure ad Applied Mathematics Vol 8, No, 04, 83-89 ISSN: 79-087X (P), 79-0888(olie) Published o 7 December 04 wwwresearchmathsciorg Aals of Strog Complemetary Acyclic Domiatio of a Graph NSaradha
Aals of Pure ad Applied Mathematics Vol 8, No, 04, 83-89 ISSN: 79-087X (P), 79-0888(olie) Published o 7 December 04 wwwresearchmathsciorg Aals of Strog Complemetary Acyclic Domiatio of a Graph NSaradha
Counting Regions in the Plane and More 1
 Coutig Regios i the Plae ad More 1 by Zvezdelia Stakova Berkeley Math Circle Itermediate I Group September 016 1. Overarchig Problem Problem 1 Regios i a Circle. The vertices of a polygos are arraged o
Coutig Regios i the Plae ad More 1 by Zvezdelia Stakova Berkeley Math Circle Itermediate I Group September 016 1. Overarchig Problem Problem 1 Regios i a Circle. The vertices of a polygos are arraged o
Chapter 11. Friends, Overloaded Operators, and Arrays in Classes. Copyright 2014 Pearson Addison-Wesley. All rights reserved.
 Chapter 11 Frieds, Overloaded Operators, ad Arrays i Classes Copyright 2014 Pearso Addiso-Wesley. All rights reserved. Overview 11.1 Fried Fuctios 11.2 Overloadig Operators 11.3 Arrays ad Classes 11.4
Chapter 11 Frieds, Overloaded Operators, ad Arrays i Classes Copyright 2014 Pearso Addiso-Wesley. All rights reserved. Overview 11.1 Fried Fuctios 11.2 Overloadig Operators 11.3 Arrays ad Classes 11.4
A Study on the Performance of Cholesky-Factorization using MPI
 A Study o the Performace of Cholesky-Factorizatio usig MPI Ha S. Kim Scott B. Bade Departmet of Computer Sciece ad Egieerig Uiversity of Califoria Sa Diego {hskim, bade}@cs.ucsd.edu Abstract Cholesky-factorizatio
A Study o the Performace of Cholesky-Factorizatio usig MPI Ha S. Kim Scott B. Bade Departmet of Computer Sciece ad Egieerig Uiversity of Califoria Sa Diego {hskim, bade}@cs.ucsd.edu Abstract Cholesky-factorizatio
Fast Fourier Transform (FFT) Algorithms
 Fast Fourier Trasform FFT Algorithms Relatio to the z-trasform elsewhere, ozero, z x z X x [ ] 2 ~ elsewhere,, ~ e j x X x x π j e z z X X π 2 ~ The DFS X represets evely spaced samples of the z- trasform
Fast Fourier Trasform FFT Algorithms Relatio to the z-trasform elsewhere, ozero, z x z X x [ ] 2 ~ elsewhere,, ~ e j x X x x π j e z z X X π 2 ~ The DFS X represets evely spaced samples of the z- trasform
INTERSECTION CORDIAL LABELING OF GRAPHS
 INTERSECTION CORDIAL LABELING OF GRAPHS G Meea, K Nagaraja Departmet of Mathematics, PSR Egieerig College, Sivakasi- 66 4, Virudhuagar(Dist) Tamil Nadu, INDIA meeag9@yahoocoi Departmet of Mathematics,
INTERSECTION CORDIAL LABELING OF GRAPHS G Meea, K Nagaraja Departmet of Mathematics, PSR Egieerig College, Sivakasi- 66 4, Virudhuagar(Dist) Tamil Nadu, INDIA meeag9@yahoocoi Departmet of Mathematics,
Heaps. Presentation for use with the textbook Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015
 Presetatio for use with the textbook Algorithm Desig ad Applicatios, by M. T. Goodrich ad R. Tamassia, Wiley, 201 Heaps 201 Goodrich ad Tamassia xkcd. http://xkcd.com/83/. Tree. Used with permissio uder
Presetatio for use with the textbook Algorithm Desig ad Applicatios, by M. T. Goodrich ad R. Tamassia, Wiley, 201 Heaps 201 Goodrich ad Tamassia xkcd. http://xkcd.com/83/. Tree. Used with permissio uder
BASED ON ITERATIVE ERROR-CORRECTION
 A COHPARISO OF CRYPTAALYTIC PRICIPLES BASED O ITERATIVE ERROR-CORRECTIO Miodrag J. MihaljeviC ad Jova Dj. GoliC Istitute of Applied Mathematics ad Electroics. Belgrade School of Electrical Egieerig. Uiversity
A COHPARISO OF CRYPTAALYTIC PRICIPLES BASED O ITERATIVE ERROR-CORRECTIO Miodrag J. MihaljeviC ad Jova Dj. GoliC Istitute of Applied Mathematics ad Electroics. Belgrade School of Electrical Egieerig. Uiversity
are two specific neighboring points, F( x, y)
 $33/,&$7,212)7+(6(/)$92,',1* 5$1'20:$/.12,6(5('8&7,21$/*25,7+0,17+(&2/285,0$*(6(*0(17$7,21 %RJGDQ602/.$+HQU\N3$/86'DPLDQ%(5(6.$ 6LOHVLDQ7HFKQLFDO8QLYHUVLW\'HSDUWPHQWRI&RPSXWHU6FLHQFH $NDGHPLFND*OLZLFH32/$1'
$33/,&$7,212)7+(6(/)$92,',1* 5$1'20:$/.12,6(5('8&7,21$/*25,7+0,17+(&2/285,0$*(6(*0(17$7,21 %RJGDQ602/.$+HQU\N3$/86'DPLDQ%(5(6.$ 6LOHVLDQ7HFKQLFDO8QLYHUVLW\'HSDUWPHQWRI&RPSXWHU6FLHQFH $NDGHPLFND*OLZLFH32/$1'
Some non-existence results on Leech trees
 Some o-existece results o Leech trees László A.Székely Hua Wag Yog Zhag Uiversity of South Carolia This paper is dedicated to the memory of Domiique de Cae, who itroduced LAS to Leech trees.. Abstract
Some o-existece results o Leech trees László A.Székely Hua Wag Yog Zhag Uiversity of South Carolia This paper is dedicated to the memory of Domiique de Cae, who itroduced LAS to Leech trees.. Abstract
Lecture 28: Data Link Layer
 Automatic Repeat Request (ARQ) 2. Go ack N ARQ Although the Stop ad Wait ARQ is very simple, you ca easily show that it has very the low efficiecy. The low efficiecy comes from the fact that the trasmittig
Automatic Repeat Request (ARQ) 2. Go ack N ARQ Although the Stop ad Wait ARQ is very simple, you ca easily show that it has very the low efficiecy. The low efficiecy comes from the fact that the trasmittig
1. SWITCHING FUNDAMENTALS
 . SWITCING FUNDMENTLS Switchig is the provisio of a o-demad coectio betwee two ed poits. Two distict switchig techiques are employed i commuicatio etwors-- circuit switchig ad pacet switchig. Circuit switchig
. SWITCING FUNDMENTLS Switchig is the provisio of a o-demad coectio betwee two ed poits. Two distict switchig techiques are employed i commuicatio etwors-- circuit switchig ad pacet switchig. Circuit switchig
15-859E: Advanced Algorithms CMU, Spring 2015 Lecture #2: Randomized MST and MST Verification January 14, 2015
 15-859E: Advaced Algorithms CMU, Sprig 2015 Lecture #2: Radomized MST ad MST Verificatio Jauary 14, 2015 Lecturer: Aupam Gupta Scribe: Yu Zhao 1 Prelimiaries I this lecture we are talkig about two cotets:
15-859E: Advaced Algorithms CMU, Sprig 2015 Lecture #2: Radomized MST ad MST Verificatio Jauary 14, 2015 Lecturer: Aupam Gupta Scribe: Yu Zhao 1 Prelimiaries I this lecture we are talkig about two cotets:
Parallel Polygon Approximation Algorithm Targeted at Reconfigurable Multi-Ring Hardware
 Parallel Polygo Approximatio Algorithm Targeted at Recofigurable Multi-Rig Hardware M. Arif Wai* ad Hamid R. Arabia** *Califoria State Uiversity Bakersfield, Califoria, USA **Uiversity of Georgia, Georgia,
Parallel Polygo Approximatio Algorithm Targeted at Recofigurable Multi-Rig Hardware M. Arif Wai* ad Hamid R. Arabia** *Califoria State Uiversity Bakersfield, Califoria, USA **Uiversity of Georgia, Georgia,
Lecture 6. Lecturer: Ronitt Rubinfeld Scribes: Chen Ziv, Eliav Buchnik, Ophir Arie, Jonathan Gradstein
 068.670 Subliear Time Algorithms November, 0 Lecture 6 Lecturer: Roitt Rubifeld Scribes: Che Ziv, Eliav Buchik, Ophir Arie, Joatha Gradstei Lesso overview. Usig the oracle reductio framework for approximatig
068.670 Subliear Time Algorithms November, 0 Lecture 6 Lecturer: Roitt Rubifeld Scribes: Che Ziv, Eliav Buchik, Ophir Arie, Joatha Gradstei Lesso overview. Usig the oracle reductio framework for approximatig
. Written in factored form it is easy to see that the roots are 2, 2, i,
 CMPS A Itroductio to Programmig Programmig Assigmet 4 I this assigmet you will write a java program that determies the real roots of a polyomial that lie withi a specified rage. Recall that the roots (or
CMPS A Itroductio to Programmig Programmig Assigmet 4 I this assigmet you will write a java program that determies the real roots of a polyomial that lie withi a specified rage. Recall that the roots (or
Dynamic Programming and Curve Fitting Based Road Boundary Detection
 Dyamic Programmig ad Curve Fittig Based Road Boudary Detectio SHYAM PRASAD ADHIKARI, HYONGSUK KIM, Divisio of Electroics ad Iformatio Egieerig Chobuk Natioal Uiversity 664-4 Ga Deokji-Dog Jeoju-City Jeobuk
Dyamic Programmig ad Curve Fittig Based Road Boudary Detectio SHYAM PRASAD ADHIKARI, HYONGSUK KIM, Divisio of Electroics ad Iformatio Egieerig Chobuk Natioal Uiversity 664-4 Ga Deokji-Dog Jeoju-City Jeobuk
THE PROBLEM THE PROBLEM (1) THE PROBLEM (2) THE MINIMUM ENERGY BROADCAST PROBLEM THE MINIMUM SPANNING TREE
 THE MINIMUM ENERGY BROADCAST PROBLEM I.E. THE MINIMUM SPANNING TREE PROBLEM Prof. Tiziaa Calamoeri Network Algorithms A.y. 05/ THE PROBLEM THE PROBLEM () THE PROBLEM () What does it meas sufficietly close?!
THE MINIMUM ENERGY BROADCAST PROBLEM I.E. THE MINIMUM SPANNING TREE PROBLEM Prof. Tiziaa Calamoeri Network Algorithms A.y. 05/ THE PROBLEM THE PROBLEM () THE PROBLEM () What does it meas sufficietly close?!
CSC 220: Computer Organization Unit 11 Basic Computer Organization and Design
 College of Computer ad Iformatio Scieces Departmet of Computer Sciece CSC 220: Computer Orgaizatio Uit 11 Basic Computer Orgaizatio ad Desig 1 For the rest of the semester, we ll focus o computer architecture:
College of Computer ad Iformatio Scieces Departmet of Computer Sciece CSC 220: Computer Orgaizatio Uit 11 Basic Computer Orgaizatio ad Desig 1 For the rest of the semester, we ll focus o computer architecture:
A NOTE ON COARSE GRAINED PARALLEL INTEGER SORTING
 Chater 26 A NOTE ON COARSE GRAINED PARALLEL INTEGER SORTING A. Cha ad F. Dehe School of Comuter Sciece Carleto Uiversity Ottawa, Caada K1S 5B6 æ {acha,dehe}@scs.carleto.ca Abstract Keywords: We observe
Chater 26 A NOTE ON COARSE GRAINED PARALLEL INTEGER SORTING A. Cha ad F. Dehe School of Comuter Sciece Carleto Uiversity Ottawa, Caada K1S 5B6 æ {acha,dehe}@scs.carleto.ca Abstract Keywords: We observe
Graphs ORD SFO LAX DFW
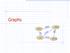 Graphs SFO 337 1843 802 ORD LAX 1233 DFW Graphs A graph is a pair (V, E), where V is a set of odes, called vertices E is a collectio of pairs of vertices, called edges Vertices ad edges are positios ad
Graphs SFO 337 1843 802 ORD LAX 1233 DFW Graphs A graph is a pair (V, E), where V is a set of odes, called vertices E is a collectio of pairs of vertices, called edges Vertices ad edges are positios ad
Chapter 1. Introduction to Computers and C++ Programming. Copyright 2015 Pearson Education, Ltd.. All rights reserved.
 Chapter 1 Itroductio to Computers ad C++ Programmig Copyright 2015 Pearso Educatio, Ltd.. All rights reserved. Overview 1.1 Computer Systems 1.2 Programmig ad Problem Solvig 1.3 Itroductio to C++ 1.4 Testig
Chapter 1 Itroductio to Computers ad C++ Programmig Copyright 2015 Pearso Educatio, Ltd.. All rights reserved. Overview 1.1 Computer Systems 1.2 Programmig ad Problem Solvig 1.3 Itroductio to C++ 1.4 Testig
c-dominating Sets for Families of Graphs
 c-domiatig Sets for Families of Graphs Kelsie Syder Mathematics Uiversity of Mary Washigto April 6, 011 1 Abstract The topic of domiatio i graphs has a rich history, begiig with chess ethusiasts i the
c-domiatig Sets for Families of Graphs Kelsie Syder Mathematics Uiversity of Mary Washigto April 6, 011 1 Abstract The topic of domiatio i graphs has a rich history, begiig with chess ethusiasts i the
Greedy Algorithms. Interval Scheduling. Greedy Algorithms. Interval scheduling. Greedy Algorithms. Interval Scheduling
 Greedy Algorithms Greedy Algorithms Witer Paul Beame Hard to defie exactly but ca give geeral properties Solutio is built i small steps Decisios o how to build the solutio are made to maximize some criterio
Greedy Algorithms Greedy Algorithms Witer Paul Beame Hard to defie exactly but ca give geeral properties Solutio is built i small steps Decisios o how to build the solutio are made to maximize some criterio
The Counterchanged Crossed Cube Interconnection Network and Its Topology Properties
 WSEAS TRANSACTIONS o COMMUNICATIONS Wag Xiyag The Couterchaged Crossed Cube Itercoectio Network ad Its Topology Properties WANG XINYANG School of Computer Sciece ad Egieerig South Chia Uiversity of Techology
WSEAS TRANSACTIONS o COMMUNICATIONS Wag Xiyag The Couterchaged Crossed Cube Itercoectio Network ad Its Topology Properties WANG XINYANG School of Computer Sciece ad Egieerig South Chia Uiversity of Techology
Elementary Educational Computer
 Chapter 5 Elemetary Educatioal Computer. Geeral structure of the Elemetary Educatioal Computer (EEC) The EEC coforms to the 5 uits structure defied by vo Neuma's model (.) All uits are preseted i a simplified
Chapter 5 Elemetary Educatioal Computer. Geeral structure of the Elemetary Educatioal Computer (EEC) The EEC coforms to the 5 uits structure defied by vo Neuma's model (.) All uits are preseted i a simplified
Optimal Movement of Mobile Sensors for Barrier Coverage of a Planar Region (Extended Abstract)
 Optimal Movemet of Mobile Sesors for Barrier Coverage of a Plaar Regio (Exteded Abstract) B. Bhattacharya M. Burmester Y. Hu E. Kraakis Q. Shi A. Wiese March 16, 2008 Abstract Itrusio detectio, area coverage
Optimal Movemet of Mobile Sesors for Barrier Coverage of a Plaar Regio (Exteded Abstract) B. Bhattacharya M. Burmester Y. Hu E. Kraakis Q. Shi A. Wiese March 16, 2008 Abstract Itrusio detectio, area coverage
arxiv: v2 [cs.ds] 24 Mar 2018
![arxiv: v2 [cs.ds] 24 Mar 2018 arxiv: v2 [cs.ds] 24 Mar 2018](/thumbs/81/83887444.jpg) Similar Elemets ad Metric Labelig o Complete Graphs arxiv:1803.08037v [cs.ds] 4 Mar 018 Pedro F. Felzeszwalb Brow Uiversity Providece, RI, USA pff@brow.edu March 8, 018 We cosider a problem that ivolves
Similar Elemets ad Metric Labelig o Complete Graphs arxiv:1803.08037v [cs.ds] 4 Mar 018 Pedro F. Felzeszwalb Brow Uiversity Providece, RI, USA pff@brow.edu March 8, 018 We cosider a problem that ivolves
Introduction. Nature-Inspired Computing. Terminology. Problem Types. Constraint Satisfaction Problems - CSP. Free Optimization Problem - FOP
 Nature-Ispired Computig Hadlig Costraits Dr. Şima Uyar September 2006 Itroductio may practical problems are costraied ot all combiatios of variable values represet valid solutios feasible solutios ifeasible
Nature-Ispired Computig Hadlig Costraits Dr. Şima Uyar September 2006 Itroductio may practical problems are costraied ot all combiatios of variable values represet valid solutios feasible solutios ifeasible
Load balanced Parallel Prime Number Generator with Sieve of Eratosthenes on Cluster Computers *
 Load balaced Parallel Prime umber Geerator with Sieve of Eratosthees o luster omputers * Soowook Hwag*, Kyusik hug**, ad Dogseug Kim* *Departmet of Electrical Egieerig Korea Uiversity Seoul, -, Rep. of
Load balaced Parallel Prime umber Geerator with Sieve of Eratosthees o luster omputers * Soowook Hwag*, Kyusik hug**, ad Dogseug Kim* *Departmet of Electrical Egieerig Korea Uiversity Seoul, -, Rep. of
Optimal Movement of Mobile Sensors for Barrier Coverage of a Planar Region
 Optimal Movemet of Mobile Sesors for Barrier Coverage of a Plaar Regio Biay Bhattacharya Mike Burmester Yuzhuag Hu Evagelos Kraakis Qiaosheg Shi Adreas Wiese Abstract Itrusio detectio, area coverage ad
Optimal Movemet of Mobile Sesors for Barrier Coverage of a Plaar Regio Biay Bhattacharya Mike Burmester Yuzhuag Hu Evagelos Kraakis Qiaosheg Shi Adreas Wiese Abstract Itrusio detectio, area coverage ad
CSC165H1 Worksheet: Tutorial 8 Algorithm analysis (SOLUTIONS)
 CSC165H1, Witer 018 Learig Objectives By the ed of this worksheet, you will: Aalyse the ruig time of fuctios cotaiig ested loops. 1. Nested loop variatios. Each of the followig fuctios takes as iput a
CSC165H1, Witer 018 Learig Objectives By the ed of this worksheet, you will: Aalyse the ruig time of fuctios cotaiig ested loops. 1. Nested loop variatios. Each of the followig fuctios takes as iput a
Basic allocator mechanisms The course that gives CMU its Zip! Memory Management II: Dynamic Storage Allocation Mar 6, 2000.
 5-23 The course that gives CM its Zip Memory Maagemet II: Dyamic Storage Allocatio Mar 6, 2000 Topics Segregated lists Buddy system Garbage collectio Mark ad Sweep Copyig eferece coutig Basic allocator
5-23 The course that gives CM its Zip Memory Maagemet II: Dyamic Storage Allocatio Mar 6, 2000 Topics Segregated lists Buddy system Garbage collectio Mark ad Sweep Copyig eferece coutig Basic allocator
Intro to Scientific Computing: Solutions
 Itro to Scietific Computig: Solutios Dr. David M. Goulet. How may steps does it take to separate 3 objects ito groups of 4? We start with 5 objects ad apply 3 steps of the algorithm to reduce the pile
Itro to Scietific Computig: Solutios Dr. David M. Goulet. How may steps does it take to separate 3 objects ito groups of 4? We start with 5 objects ad apply 3 steps of the algorithm to reduce the pile
Visualization of Gauss-Bonnet Theorem
 Visualizatio of Gauss-Boet Theorem Yoichi Maeda maeda@keyaki.cc.u-tokai.ac.jp Departmet of Mathematics Tokai Uiversity Japa Abstract: The sum of exteral agles of a polygo is always costat, π. There are
Visualizatio of Gauss-Boet Theorem Yoichi Maeda maeda@keyaki.cc.u-tokai.ac.jp Departmet of Mathematics Tokai Uiversity Japa Abstract: The sum of exteral agles of a polygo is always costat, π. There are
Reversible Realization of Quaternary Decoder, Multiplexer, and Demultiplexer Circuits
 Egieerig Letters, :, EL Reversible Realizatio of Quaterary Decoder, Multiplexer, ad Demultiplexer Circuits Mozammel H.. Kha, Member, ENG bstract quaterary reversible circuit is more compact tha the correspodig
Egieerig Letters, :, EL Reversible Realizatio of Quaterary Decoder, Multiplexer, ad Demultiplexer Circuits Mozammel H.. Kha, Member, ENG bstract quaterary reversible circuit is more compact tha the correspodig
Announcements. Reading. Project #4 is on the web. Homework #1. Midterm #2. Chapter 4 ( ) Note policy about project #3 missing components
 Aoucemets Readig Chapter 4 (4.1-4.2) Project #4 is o the web ote policy about project #3 missig compoets Homework #1 Due 11/6/01 Chapter 6: 4, 12, 24, 37 Midterm #2 11/8/01 i class 1 Project #4 otes IPv6Iit,
Aoucemets Readig Chapter 4 (4.1-4.2) Project #4 is o the web ote policy about project #3 missig compoets Homework #1 Due 11/6/01 Chapter 6: 4, 12, 24, 37 Midterm #2 11/8/01 i class 1 Project #4 otes IPv6Iit,
A study on Interior Domination in Graphs
 IOSR Joural of Mathematics (IOSR-JM) e-issn: 2278-5728, p-issn: 219-765X. Volume 12, Issue 2 Ver. VI (Mar. - Apr. 2016), PP 55-59 www.iosrjourals.org A study o Iterior Domiatio i Graphs A. Ato Kisley 1,
IOSR Joural of Mathematics (IOSR-JM) e-issn: 2278-5728, p-issn: 219-765X. Volume 12, Issue 2 Ver. VI (Mar. - Apr. 2016), PP 55-59 www.iosrjourals.org A study o Iterior Domiatio i Graphs A. Ato Kisley 1,
Administrative UNSUPERVISED LEARNING. Unsupervised learning. Supervised learning 11/25/13. Final project. No office hours today
 Admiistrative Fial project No office hours today UNSUPERVISED LEARNING David Kauchak CS 451 Fall 2013 Supervised learig Usupervised learig label label 1 label 3 model/ predictor label 4 label 5 Supervised
Admiistrative Fial project No office hours today UNSUPERVISED LEARNING David Kauchak CS 451 Fall 2013 Supervised learig Usupervised learig label label 1 label 3 model/ predictor label 4 label 5 Supervised
Fundamentals of Media Processing. Shin'ichi Satoh Kazuya Kodama Hiroshi Mo Duy-Dinh Le
 Fudametals of Media Processig Shi'ichi Satoh Kazuya Kodama Hiroshi Mo Duy-Dih Le Today's topics Noparametric Methods Parze Widow k-nearest Neighbor Estimatio Clusterig Techiques k-meas Agglomerative Hierarchical
Fudametals of Media Processig Shi'ichi Satoh Kazuya Kodama Hiroshi Mo Duy-Dih Le Today's topics Noparametric Methods Parze Widow k-nearest Neighbor Estimatio Clusterig Techiques k-meas Agglomerative Hierarchical
Numerical Methods Lecture 6 - Curve Fitting Techniques
 Numerical Methods Lecture 6 - Curve Fittig Techiques Topics motivatio iterpolatio liear regressio higher order polyomial form expoetial form Curve fittig - motivatio For root fidig, we used a give fuctio
Numerical Methods Lecture 6 - Curve Fittig Techiques Topics motivatio iterpolatio liear regressio higher order polyomial form expoetial form Curve fittig - motivatio For root fidig, we used a give fuctio
Creating Exact Bezier Representations of CST Shapes. David D. Marshall. California Polytechnic State University, San Luis Obispo, CA , USA
 Creatig Exact Bezier Represetatios of CST Shapes David D. Marshall Califoria Polytechic State Uiversity, Sa Luis Obispo, CA 93407-035, USA The paper presets a method of expressig CST shapes pioeered by
Creatig Exact Bezier Represetatios of CST Shapes David D. Marshall Califoria Polytechic State Uiversity, Sa Luis Obispo, CA 93407-035, USA The paper presets a method of expressig CST shapes pioeered by
Planar graphs. Definition. A graph is planar if it can be drawn on the plane in such a way that no two edges cross each other.
 Plaar graphs Defiitio. A graph is plaar if it ca be draw o the plae i such a way that o two edges cross each other. Example: Face 1 Face 2 Exercise: Which of the followig graphs are plaar? K, P, C, K,m,
Plaar graphs Defiitio. A graph is plaar if it ca be draw o the plae i such a way that o two edges cross each other. Example: Face 1 Face 2 Exercise: Which of the followig graphs are plaar? K, P, C, K,m,
Reading. Subdivision curves and surfaces. Subdivision curves. Chaikin s algorithm. Recommended:
 Readig Recommeded: Stollitz, DeRose, ad Salesi. Wavelets for Computer Graphics: Theory ad Applicatios, 996, sectio 6.-6.3, 0., A.5. Subdivisio curves ad surfaces Note: there is a error i Stollitz, et al.,
Readig Recommeded: Stollitz, DeRose, ad Salesi. Wavelets for Computer Graphics: Theory ad Applicatios, 996, sectio 6.-6.3, 0., A.5. Subdivisio curves ad surfaces Note: there is a error i Stollitz, et al.,
Evaluation scheme for Tracking in AMI
 A M I C o m m u i c a t i o A U G M E N T E D M U L T I - P A R T Y I N T E R A C T I O N http://www.amiproject.org/ Evaluatio scheme for Trackig i AMI S. Schreiber a D. Gatica-Perez b AMI WP4 Trackig:
A M I C o m m u i c a t i o A U G M E N T E D M U L T I - P A R T Y I N T E R A C T I O N http://www.amiproject.org/ Evaluatio scheme for Trackig i AMI S. Schreiber a D. Gatica-Perez b AMI WP4 Trackig:
Neuro Fuzzy Model for Human Face Expression Recognition
 IOSR Joural of Computer Egieerig (IOSRJCE) ISSN : 2278-0661 Volume 1, Issue 2 (May-Jue 2012), PP 01-06 Neuro Fuzzy Model for Huma Face Expressio Recogitio Mr. Mayur S. Burage 1, Prof. S. V. Dhopte 2 1
IOSR Joural of Computer Egieerig (IOSRJCE) ISSN : 2278-0661 Volume 1, Issue 2 (May-Jue 2012), PP 01-06 Neuro Fuzzy Model for Huma Face Expressio Recogitio Mr. Mayur S. Burage 1, Prof. S. V. Dhopte 2 1
Hash Tables. Presentation for use with the textbook Algorithm Design and Applications, by M. T. Goodrich and R. Tamassia, Wiley, 2015.
 Presetatio for use with the textbook Algorithm Desig ad Applicatios, by M. T. Goodrich ad R. Tamassia, Wiley, 2015 Hash Tables xkcd. http://xkcd.com/221/. Radom Number. Used with permissio uder Creative
Presetatio for use with the textbook Algorithm Desig ad Applicatios, by M. T. Goodrich ad R. Tamassia, Wiley, 2015 Hash Tables xkcd. http://xkcd.com/221/. Radom Number. Used with permissio uder Creative
