Making Name-Based Content Routing More Efficient than Link-State Routing
|
|
|
- Meryl Strickland
- 6 years ago
- Views:
Transcription
1 Makng Name-Based Content Routng More Effcent than Lnk-State Routng Ehsan Hemmat and J.J. Garca-Luna-Aceves, Comuter Engneerng Deartment, UC Santa Cruz, Santa Cruz, CA PARC, Palo Alto, CA { ehsan, jj }@soe.ucsc.edu arxv: v1 [cs.ni] 8 Ar 2018 Abstract The Dffusve Name-based Routng Protocol () s ntroduced for effcent name-based routng n nformatoncentrc networks (ICN). establshes and mantans multle loo-free routes to the nearest nstances of a name refx usng only dstance nformaton. elmnates the need for erodc udates, mantanng toology nformaton, storng comlete aths to content relcas, or knowng about all the stes storng relcas of named content. s sutable for large ICNs wth large numbers of refxes stored at multle stes. It s shown that rovdes loo-free routes to content ndeendently of the state of the toology, and that t converges wthn a fnte tme to correct routes to name refxes after arbtrary changes n the network toology or the lacement of refx nstances. The result of smulaton exerments llustrate that s more effcent than lnk-state routng aroaches. I. INTRODUCTION Several Informaton-Centrc Networkng (ICN) archtectures have been ntroduced to address the ncreasng demand of user-generated content [1], [3]. The goal of these archtectures s to rovde a cost-effcent, scalable, and moble access to content and servces by adotng a content-based model of communcaton. ICN archtectures seek to dssocate content and servces from ther roducers n such a way that the content can be retreved ndeendently of ts orgnal locaton or the locaton of consumers. The most romnent ICN archtectures can be characterzed as Interest-based archtectures, n whch locaton-ndeendent, self-defned, unque namng s used to retreve data. In ths aroach, messages flow from roducers to consumers based on the name of the content rather than the address of the senders or recevers exchangng such content. Content rovders or roducers create named data objects (NDOs), and advertse routable name refxes assocated wth the content objects whose own names are art of the name refxes. The only dentfer of an NDO s ts name. A consumer requests a ece of content by sendng an Interest (a request for the NDO) that s routed along content routers toward the roducer(s). Clearly, an effcent name-based content routng rotocol must be used for any ICN archtecture to succeed usng namebased forwardng of Interests and requested content. Secton II summarzes recent ror work n name-based content routng, and ths revew reveals that all ror roosals for name-based content routng rely on erodc transmssons of udate messages. Ths aer focuses on an aroach that avods the need c IFIP, 2018 Ths s the author s verson of the work. It s osted here by ermsson of IFIP for your ersonal use. Not for redstrbuton. ISBN , (2018) for erodc messagng by means of dffusng comutatons [5]. Secton III resents (Dffusve Name-based Routng Protocol), a name-based content routng rotocol for ICNs. rovdes multle loo-free routes to the nearest nstances of a named refx or to all nstances of a named refx usng only dstance nformaton and wthout requrng erodc udates, knowledge of the network toology, or the exchange of ath nformaton. Secton IV shows that revents routng-table loos even n the resence of toology changes as well as changes n the hostng of refxes, and converges wthn a fnte tme to correct mult-aths to name refxes. Secton V resents the results of smulaton exerments comarng wth an effcent lnk-state aroach smlar to NR [13]. The results show that roduces less communcaton and comutaton overhead n the case of toology changes as well as the addton of refxes. II. RELATED WORK Name-based content routng has been used n the ast n content-delvery networks (CDN) oeratng as overlay networks runnng on to of the Internet routng nfrastructure (e.g., [7], [16]). However, t has become more well known n the context of ICN archtectures, where t has been done tycally by adatng tradtonal routng algorthms desgned for networks n whch a destnaton has a sngle nstance [8]. Dstrbuted Hash Tables (DHT) are used n several archtectures as the name resoluton tool [11], [15], [18]. MobltyFrst [14] rely on an external and fast name resoluton system called Global Name Resoluton Servce (GNRS) that mas the data object names to network addresses. Some ICN archtectures use name resoluton mechansms to ma the name of the content to the content rovder. Data Orented Network Archtecture (DONA) [12] relaces DNS names wth flat, self-certfyng names and uses name resoluton to ma those flat names to corresondng IP addresses. DONA suorts host moblty and multhomng, and mroves servce access and data retreval. The Named-data Lnk State Routng rotocol (NR) [13] uses lnk state routng to rank the neghbors of a router for each name refx. Adjacency A and Prefx A, roagate toology and ublsher nformaton n the network resectvely. Each router uses toology nformaton and runs
2 an extenson of Djkstra s shortest-ath frst (SPF) algorthm to rank next hos for each router, then mas the refx to the name of the ublsher and creates routng table for each name refx. Lke most ror routng aroaches based on comlete or artal toology nformaton (e.g., [2], [6], [17]), NR uses sequence numbers to allow routers to determne whether the udates they receve have more recent nformaton than the data they currently store. As a consequence, these aroaches requre the use of erodc udates to ercolate throughout the network to ensure that all routers converge to consstent toology nformaton wthn a fnte tme. The Dstance-based Content Routng (DCR) [10] was the frst name-based content routng aroach for ICNs based on dstances to named content. DCR does not requre any nformaton about the network toology or knowledge about all the nstances of the same content. It enables routng to the nearest router announcng content from a name refx beng stored locally (called anchor), all anchors of a name refx, and subsets of anchors. Ths s attaned by means of multnstantated destnaton sannng trees (MIDST). Furthermore, DCR rovdes loo-free routes to reach any ece of named content even f dfferent content objects n the same refx are stored at dfferent stes. The lmtaton of DCR s that t requres erodc udates to be dssemnated through the network. III. fnds the shortest ath(s) to the nearest relca(s) of name refxes. To ensure that loo-free routes to named refxes are mantaned at every nstant ndeendently of the state of the network or refxes, establshes a lexcograhc orderng among the routes to refxes reorted and mantaned by routers. The lexcograhc orderng of routes s based on two suffcent condtons for loo freedom wth resect to a gven refx that allow for multle next hos to refxes along loo-free routes. dffuses the comutaton of new loofree routes when the loo-free condtons are not satsfed. The aroach used n s an extraolaton to the use of dffusng comutatons n [5]. Every ece of data n the network s a Named-Data Object (NDO), reresented by a name that belongs to a name refx or smly a refx advertsed by one or more roducer(s). Name refxes can be smle and human-readable or more comlcated and self certfyng, or may even be a crytograhc hash of the content. Content names can be flat or herarchcal. The namng schema deends on the system that runs and t s out of scoe of ths aer. A router attached to a roducer of content that advertses a name refx s called an anchor of that refx. At each router, calculates routes to the nearest anchor(s) of known name refxes, f there s any, and selects a subset of the neghbors of the router as vald next hos to reach name refxes, such that no routng-table loo s created at any router for any name refx. Cachng stes are not consdered content roducers and hence routes to cached content are not advertsed n. Our descrton assumes that routers rocess, store, and transfer nformaton correctly and that they rocess routng messages one at a tme wthn a fnte tme. Every router has a unque dentfer or a name that can be flat or herarchcal. The namng schema and name assgnment mechansm s out of scoe of ths aer. A. Messages and Data Structures Each router stores the lst of all actve neghbor routers (N ), and the cost of the lnk from the router to each such neghbor. The cost of the lnk from router to ts neghbor n s denoted by ln. Lnk costs can vary n tme but are always ostve. The lnk cost assgnment and metrc determnaton mechansms are beyond the scoe of ths aer. The routng nformaton reorted by each of the neghbors of router s stored n ts neghbor table (NT ). The entry of NT regardng neghbor n for refx s denoted by NTn and conssts of the name refx (), the dstance to refx reorted by neghbor n (d n), and the anchor of that refx reorted by neghbor n (a n). If router s the anchor of refx tself, then d = 0. Router stores routng nformaton for each known refx n ts routng table (RT ). The entry n RT for refx (RT) secfes: the name of the refx (); the dstance to the nearest nstance of that refx (d ); the feasble dstance to the refx (fd ); the neghbor that offers the shortest dstance to the refx (s ), whch we call the successor of the refx; the closest anchor to the refx (a ); the state mode (mf) regardng refx, whch can be PASSIVE or ACTIVE; the orgn state (o ) ndcatng whether router or a neghbor s the orgn of query n whch the router s actve; the udate flag lst (F L ); and the lst of all vald next hos (V ). F L conssts of four flags for each neghbor n. An udate flag (ufn) denotes whether or not the routng message should be sent to that neghbor. A tye flag (tfn) ndcates the tye of routng message the router has to send to neghbor n regardng refx (.e., whether t s an UPDATE, QUERY, or REPLY). A endng-rely flag (rfn) denotes whether the router has sent a QUERY to that neghbor and s watng for REPLY. A endng-query flag (qfn) s set f the router receved a QUERY from ts neghbor n and has not resonded to that QUERY yet. Router sends a routng message to each of ts neghbors contanng udates made to RT snce the tme t sent ts last udate message. A routng message from router to neghbor n conssts of one or more udates, each of whch carres nformaton regardng one refx that needs udatng. The udate nformaton for refx s denoted by U and states: (a) the name of the refx (); (b) the message tye (ut ) that ndcates f the message s an UPDATE, QUERY, or REPLY; (c) the dstance to ; and (d) the name of the closest anchor. The routng udate receved by router from neghbor n s denoted by Un. The udate nformaton of Un for refx, u n, secfes the refx name (), the dstance from n to that refx (ud n), the name of the anchor of that refx (ua n), and a message tye (ut n).
3 B. Suffcent Condtons for Loo Freedom The condtons for loo-free routng n are based on the feasble dstance mantaned at each router and the dstances reorted by ts neghbors for a name refx. One condton s used to determne the new shortest dstance through a loo-free ath to a name refx. The other s used to select a subset of neghbors as next hos to a name refx. Source Router Condton (SRC): Router can select neghbor n N as a new successor s for refx f: ( d n < ) ( d n < fd [d n = fd n < ] ) ( d n + l n = Mn{d v + l v v N } ). SRC smly states that router can select neghbor n as ts successor to refx f n reorts a fnte dstance to that refx, offers the smallest dstance to refx among all neghbors, and ether ts dstance to refx s less than the feasble dstance of router or ts dstance s equal to the feasble dstance of but n <. If two or more neghbors satsfy SRC, the neghbor that satsfes SRC and has the smallest dentfer s selected. If none of the neghbors satsfes SRC the router kees the current successor, f t has any. The dstance of router to refx, d, s defned by the dstance of the ath through the selected successor. A router that has a fnte feasble dstance (fd < ) selects a subset of neghbors as vald next hos at tme t f they have a fnte dstance to destnaton and are closer to destnaton. The followng condton s used for ths urose. Next-ho Selecton Condton (NSC): Router wth fd < adds neghbor n N to the set of vald next hos f: ( d n < ) ( d n < fd [d n = fd n < ] ). NSC states that router can select neghbor n as a next ho to refx f ether the dstance from n to refx s smaller than the feasble dstance of or ts dstance s equal to the feasble dstance and n <. NSC orders next hos lexcograhcally based on ther dstance to a refx and ther names. It s shown that no routng-table loos can be formed f NSC s used to select the next hos to refxes at each router. Note that the successor s also a vald next ho. The successor to a refx s a vald next ho that offers the smallest cost. SRC and NSC are suffcent condtons that, as we show subsequently, ensure loo-freedom at every nstance but do not guarantee shortest aths to destnatons. ntegrates these suffcent condtons wth nter-nodal synchronzaton sgnalng to acheve both loo freedom at every nstant and shortest aths for each destnaton. C. Oeraton A change n the network, such as a lnk-cost change, the addton or falure of a lnk, the addton or falure of a router, the addton or deleton of a refx, or the addton or deleton of a relca of a refx can cause one or more comutatons at each router for one or more refxes. A comutaton can be ether a local comutaton or a dffusng comutaton. In a local comutaton a router udates ts successor, dstance, next hos, and feasble dstance ndeendently of other routers n the network. On the other hand, n a dffusng comutaton a router orgnatng the comutaton must coordnate wth other routers before makng any changes n ts routng-table entry for a gven refx. allows a router to artcate n at most one dffusng comutaton er refx at any gven tme. A router can be n PASSIVE or ACTIVE mode wth resect to a gven refx ndeendently of other refxes. A router s PASSIVE wth resect to refx f t s not engaged n any dffusng comutaton regardng that refx. A router ntalzes tself n PASSIVE mode and wth a zero dstance to all the refxes for whch the router tself serves as an anchor. An nfnte dstance s assumed to any non-local (and hence unknown) name refx. Intally, no router s engaged n a dffusng comutaton (o = 0). When a PASSIVE router detects a change n a lnk or receves a QUERY or UPDATE from ts neghbor that does not affect the current successor or can fnd a feasble successor, t remans n PASSIVE mode. On the other hand, f the router cannot fnd a feasble successor then t enters the ACTIVE mode and kees the current successor, udates ts dstance, and sends QUERY to all ts neghbors. Table I shows the transt from one state to another. Neghbor k s a neghbor other than the successor s. Mode State Event Passve 0 Actve TABLE I STATE TRANSIT IN Events from a neghbor k, SRC satsfed 0 Events from a neghbor k, SRC not satsfed 1 QUERY from the Successor 3 Receves last REPLY 0 Change n dstance to Successor 2 QUERY from the Successor 4 Receves last REPLY, SRC satsfed 0 Receves last REPLY, SRC not satsfed 1 QUERY from the Successor 4 Receves last REPLY 0 Change n dstance to the Successor 4 Receves last REPLY, SRC satsfed 0 Receves last REPLY, SRC not satsfed 3 Next State Algorthm 1 shows the rocessng of messages by a router n PASSIVE mode. Algorthm 2 shows the stes taken n ACTIVE mode. Algorthm 3 shows the stes taken to rocess a routng udate. Handlng A Sngle Dffusng Comutaton: Routers are ntalzed n PASSIVE mode. Each router contnuously montors ts lnks and rocesses the routng messages receved from ts neghbors. When router detects a change n the cost or state of a lnk, or a change n ts neghbor table that causes a change n ts dstance to refx (d ), t frst tres to select a new successor that satsfes SRC. If such a successor exsts, the router carres out a local comutaton, udates ts dstance, successor, and closest anchor, and exts the comutaton. In a local comutaton, router comutes the mnmum cost to reach the destnaton and udates d = mn{d n + l n n
4 N }. If ts dstance changes, router sends a routng message wth ut = UPDATE. Router also udates ts feasble dstance to equal the smaller of ts value and the new dstance value,.e., fd (new) = mn{fd (old), d }. An UPDATE message from a neghbor s rocessed usng the same aroach stated above. If a router receves a QUERY from ts neghbor other than ts successor whle t s n PASSIVE mode, t udates the neghbor table, checks for a feasble successor accordng to SRC and reles wth d, f t succeeds. If router cannot fnd a neghbor that satsfes SRC after a change n a lnk or neghbor-table entry, then t starts out a dffusng comutaton by settng the new dstance as the dstance through ts current successor, enters the ACTIVE mode (mfj = ACTIVE) and sets the corresondng flag (rf n) for each neghbor n. After enterng the ACTIVE mode, router sets the new dstance as the cost of the ath through the current successor (d = d s + l s and sends a routng message ) wth ut = QUERY. Router uses the endng rely flag (rfn) to kee track of the neghbors from whch a REPLY has not been receved. When a router becomes ACTIVE t sets the udate flag (uf = 1), and also sets the tye flags (tf = QUERY n N ) and sends the routng messages to all ts neghbors. Algorthm 1 Processng routng messages n PASSIVE mode INPUT: RT, NT, ln, u n; [o] verfy u n; d n = ud n; d mn = ; for each k N {} do f (d k +lk < d mn) (d k +lk = d mn k < s new ) then s new = k; d mn = d k + lk; f (d s new < fd [d s new = fd s new < ]) then f s s new then s = s new; a = a s new f d d mn then d = d mn; fd = mn{fd, d }; V = φ; for each k N {} do ufk = 1; tfk =UPDATE; f (d k < fd [d k = fd k < ]) then V = V k; f ut n = QUERY then tf =REPLY; else mf = ACTIVE; d = d s + l s ; f (n = s ut n = QUERY) then o = 3; else o = 1; for each k N {} do uf = 1; tf =QUERY; When a router s n ACTIVE mode, t cannot change ts successor or fd untl t receves the reles to ts QUERY from all ts neghbors. After recevng all reles (.e. rf n = 0 n N ), router becomes PASSIVE by resettng ts feasble dstance. The router then selects the new successor and sends UPDATE messages to ts neghbors. More secfcally, router sets fd = whch nsures that the router can fnd a new successor that satsfes SRC and then sets fd = d = mn{d n + l n n N } and becomes PASSIVE. Algorthm 2 Processng routng messages n ACTIVE mode INPUT: RT, NT, u n; [o] verfy u n; d n = ud n; f ut n = REPLY then rf n = 0; lastrely = true; for each k N {} do f rf k = 0 then lastrely = false; f lastrely = true then f o = 1 o = 3 then fd = Execute Algorthm 3 else f ut n = QUERY then f (o = 1 o = 2) then f n s then uf n = 1; tf n =REPLY; else o = 4; f (o = 3 o = 4) then uf n = 1; tf n =REPLY; Algorthm 3 Udate RT INPUT: RT, NT, ln, u n; d mn = ; for each k N {} do f (d k +lk < d mn) (d k +lk = d mn k < s new ) then s new = k; d mn = d k + lk; f (d s new < fd [d s new = fd s new < ]) then o = 0; mf = P ASSIV E; f s s new then s = s new; f d d mn then d = d mn; fd = mn{fd, d }; V = φ; for each k N {} do ufk = 1; tfk =UPDATE; f (d k < fd [d k = fd k < ]) then V = V k; f qf s (old) = 1 then tf =REPLY; else f o = 2 then o = 1 else o = 3; for each k N {} do uf = 1; tf =QUERY; If router receves a QUERY from a neghbor other than ts successor whle t s ACTIVE, t smly reles to ts neghbor wth a REPLY message statng the current dstance to the destnaton. The case of a router recevng a QUERY from ts successor whle t s ACTIVE s descrbed subsequently n the context of multle dffusng comutatons. UPDATE messages are rocessed and neghbor tables are udated, but the successor or dstance s not changed untl the router receves all the reles t needs to transton to the PASSIVE mode. Whle a router s n ACTIVE mode, nether a QUERY nor an UPDATE can be sent.
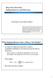
5 Fg. 1. Oeraton Examle Handlng Multle Dffusng Comutatons: Gven that a router executes each local comutaton to comleton, t handles multle local comutatons for the same refx one at a tme. Smlarly, a router handles multle dffusng comutaton for the same refx by rocessng one comutaton at a tme. An ACTIVE router can be n one of the followng four states: (1) router orgnated a dffusng comutaton (o = 1), (2) metrc ncrease detected durng ACTIVE mode (o = 2), (3) dffusng comutaton s relayed (o = 3), or (4) successor metrc changed durng ACTIVE mode (o = 4). If the router s n PASSIVE mode then ts state s 0 (.e., o = 0). Consder the case that a router s ACTIVE and n State 1 (o = 1). If the router receves the last REPLY to ts query, then t resets ts feasble dstance to nfnty, checks SRC to fnd the new successor, and sends an UPDATE to all ts neghbors. On the other hand, f router detects a change n the lnk to ts successor then t udates ts neghbor table and sets o = 2. If router s n State 2, receves the last REPLY, and can fnd a feasble successor usng SRC wth the current feasble dstance, then t becomes PASSIVE and sends an UPDATE to all ts neghbors(o = 0). Otherwse, t sends a QUERY wth the current dstance and sets o = 1. Router uses the endng query flag (qf n) to kee track of the reles that have been receved for ts QUERY regardng refx. If router s n ether State 1 or 2 and receves a QUERY from ts current successor to the refx, then t sets qf s =1 and transtons to State 4 (.e., t sets o = 4). If a router n PASSIVE mode receves a QUERY from ts successor, t searches for a new successor that satsfes SRC. If t cannot fnd such a successor then t kees the current successor, udates ts dstance, and becomes ACTIVE. Then, the router sends QUERY to all of ts neghbors and sets o = 3. When router n state 3 receves REPLY from all of ts neghbors, t resets ts feasble dstance, fd =, selects a new successor, udates the V and sends UPDATE to ts neghbors and REPLY to ts the revous successor. If the router detects a lnk falure or a cost ncrease n the lnk to ts current successor, the router sets o = 4 to ndcate that a toology change occurred whle the router s n ACTIVE mode. A router handles the case of the falure of the lnk wth ts successor as f t had receved a REPLY from ts successor wth d s =. If router s n State 4, (o = 4) and t receves reles from all ts neghbors, then t tres to fnd a feasble successor that satsfes SRC wth the current value of fd. If such a successor exsts, the router udates ts successor, dstance, and next hos for refx, and sends an UPDATE message to ts neghbors as well as REPLY to the revous successor. Otherwse, t sets o = 3 and sends a QUERY wth the new dstance. Whle router s n ACTIVE mode regardng a refx, f a QUERY s receved for the refx from a neghbor other than the current successor, the router udates the neghbor table and sends a REPLY to that neghbor. If a router n PASSIVE mode receves a QUERY from a neghbor other than the current successor, the router udates ts neghbor table. If the feasblty condton s not satsfed anymore, the router sends a REPLY to the neghbor that rovdes the current value d before t starts ts own comutaton. D. Examle of Oeraton Fgure 1 llustrates the oeraton of wth a smle examle. The fgure shows the routng nformaton used for a sngle refx when routers a and z advertse that refx and each lnk has unt cost. The tule next to each router states the dstance and the feasble dstance of the router for that refx. The red, blue, and green arrows reresent the QUERY, REPLY, and UPDATE messages resectvely and the number next to the arrow shows the tme sequence n whch that message s sent. Fgure 1 (a) shows the change n the cost of lnk (r, a). Router r detects ths change and becomes ACTIVE and sends QUERY to ts neghbors. Router q receves the QUERY from ts successor and cannot fnd a feasble successor (Fgure 1(b)). Therefore, t becomes ACTIVE and sends a QUERY to ts neghbors. Router r receves REPLY from a and t, and a QUERY from q. Gven that q s not a successor for router r, r sends REPLY to q. After recevng REPLY from routers r, s and t, router q becomes PASSIVE agan and sends ts REPLY to ts revous successor, r. In turn, ths means that r receves all the reles t needs, becomes PASSIVE, and resets ts feasble dstance. The oeraton of s such that only a orton of the routers are affected by the toology change.
6 E. Routng to all nstances of a refx enables routers to mantan multle loo-free routes to the nearest anchor of a name refx. In some ICN archtectures, such as NDN and CCNx, an anchor of a namerefx may have some but not necessarly all the content corresondng to a gven refx. Therefore, smly routng to nearest relca may cause some data to be unreachable, and the ablty to contact all anchors of a refx s needed. To address ths case, a mult-nstantated destnaton sannng tree (MIDST) can be used alongsde to suort routng to all anchors of the same refx. A MIDST s establshed n a dstrbuted manner. Routers that are aware of multle anchors for the same refx exchange routng udates to establsh the sannng tree between all anchors of a refx. Once the MIDST s formed for a gven refx, the frst router n the MIDST that receves a acket forwards t over the MIDST to all of the anchors. The detals of how a MIDST can be establshed n are omtted for brevty; however, the aroach s very much the same as that descrbed n [9]. IV. CORRECTNESS OF The followng theorems rove that s loo-free at every nstant and consders each comutaton ndvdually and n the roer sequence. From these results, the roof that converges to shortest aths to refxes s smlar to the roof resented n [4] and due to sace lmtaton s omtted. We assume that each router receves and rocesses all routng messages correctly. Ths mles that each router rocesses messages from each of ts neghbors n the correct order. Theorem 1: No routng-table loos can form n a network n whch routers use NSC to select ther next hos to refxes. Proof: Assume for the sake of contradcton that all routng tables are loo-free before tme t l but a routng-table loo s formed for refx at tme t l when router q adds ts neghbor n 1 to ts vald next-ho set V q. Because the successor s also a vald next ho, router q must ether choose a new successor or add a new neghbor other than ts current successor to ts vald next-ho set at tme t l. We must show that the exstence of a routng-table loo s a contradcton n ether case. Let L be the routng-table loo consstng of h hos startng at router q, (L = {q = n 0,new, n 1,new, n 2,new,..., n h,new }) where n h,new = q, n +1,new V n for 0 h. The tme router n udates ts vald next-ho set to nclude n +1,new s denoted by t new. Assume that the last tme router n sent an UPDATE that was rocessed by ts neghbor n 1, s t old. Router n revsts vald next hos after any changes n ts successor, dstance, or feasble dstance; therefore, t old t new t l and d n (t l ) = d n (t old ). Also, by defnton, at any tme t, fd (t ) d (t ), and fd (t 2 ) fd (t 1 ) f t 1 < t 2. Therefore, fd (t 2 ) d (t 1 ) such that t 1 < t 2 (1) If router n selects a new successor at tme t new then: d n 1 (t l ) = d n (t old ) fd n (t old ) fd n (t new ) (2) Usng NSC ensures that (fd n (t new ) > d n (t l )) (fd n (t new ) = d n (t l ) n > n +1 ) From Eqs. (2) and (3) we have: (d n 1 (t l ) > d n (t l )) (d n 1 (t l ) = d n (t l ) n > n +1 ) Therefore, for 0 k h n L t s true that: (d n0 n 1 (t l ) > d n k n k+1 (t l )) (d n0 n 1 (t l ) = d n k n k+1 (t l ) n 0 > n k ) If d n 1 (t l ) > d n (t l ) n at least one ho n L then t must be true that, for any gven k {1, 2,..., h}, d n k n k+1 (t l ) > d n k n k+1 (t l ), whch s a contradcton. If at any ho n the L t s true that d n 1 (t l ) = d n (t l ), then k > k, whch s also a contradcton. Therefore, no routngtable loo can be formed when routers use NSC to select ther next hos to refx. Lemma 2: A router that s not the orgn of a dffusng comutaton sends a REPLY to ts successor when t becomes PASSIVE. Proof: A router that runs can be n ether PASSIVE or ACTIVE mode for a refx when t receves a QUERY from ts successor regardng the refx. Assume that router s n PASSIVE mode when t receves a QUERY from ts successor. If router fnds a neghbor that satsfes SRC, then t sets ts new successor and sends a REPLY to ts old successor. Otherwse, t becomes ACTIVE, sets o = 3, and sends a QUERY to all ts neghbors. Router cannot receve a subsequent QUERY from ts successor regardng the same refx, untl t sends a REPLY back to ts successor. If the dstance does not ncrease whle router s ACTIVE then o remans the same (.e. o = 3). Otherwse, router must set o = 4. In both cases router must send a REPLY when t becomes PASSIVE. Assume that router s n ACTIVE mode when t receves a QUERY from ts successor s. Router s cannot send another QUERY untl t receves a REPLY from all ts neghbors to ts query, ncludng router. Hence, router must be the orgn of the dffusng comutaton for whch t s ACTIVE when t receves the QUERY from s, whch means that o = 1 or o = 2. In both cases router sets o = 4 when t receves a QUERY form ts successor s and s must send a REPLY n resonse to the QUERY from because, s not the successor for s. After recevng the last REPLY from ts neghbors, ether router fnds a feasble successor and sends a REPLY to s (o = 0) or t roagates the dffusng comutaton forwarded by s by sendng a QUERY to ts neghbors and settng o = 3. Router then must send a REPLY to s when t receves the last REPLY for the QUERY t forwarded from s. (3) (4) (5)
7 Hence, ndeendently of ts current mode, router must send a REPLY to a QUERY t receves from ts successor when t becomes PASSIVE. Lemma 3: Consder a network that s loo free before an arbtrary tme t and n whch a sngle dffusng comutaton takes lace. If node n s PASSIVE for refx at that tme, then t must be true that (dn n 1 (t) > d n (t)) (d n 1 (t) = d n (t) n > n +1 ) ndeendently of the state of other routers n the chan of vald next hos {n 1, n, n +1 } for refx. Proof: Assume that router n s PASSIVE and selects router n +1 as a vald next ho. Accordng to NSC t must be true that: (d n (t) < fd n (t) d n (t)) (d n (t) = fd n (t) d n (t) n +1 < n ) Assume that n dd not reset fd n the last tme t new < t when n became PASSIVE and selected ts successor s new and udated ts dstance d n (t new ) = d n (t). If router n 1 rocessed the message that router n sent after udatng ts dstance, then: dn n 1 (t) = d n (t new ). Substtutng ths equaton n 6 renders the result of ths lemma. On the other hand, If router n 1 dd not rocess the message that router n sent after udatng ts dstance and before t, then d n 1 (t) = d n (t old ). Based on the facts that router n dd not reset ts feasble dstance and Eq. 1 holds for ths case. Therefore: d n 1 (6) (t) = d n 1 (t old ) > fd n (t) (7) Now consder the case that n becomes PASSIVE at tme t new and changes ts successor from s old to s new by resetng ts feasble dstance. The case that n 1 rocessed the message that router n sent after becomng PASSIVE s the same as before. Assume that n 1 dd not rocess the message that n sent at tme t new. Furthermore, assume that router n becomes ACTIVE at tme t old, wth a dstance d n (t old ) = d n s old + ls n old. Router n cannot change ts successor or exerence any ncrement n ts dstance through s old ; hence, d n (t new ) d n (t old ). On the other hand, the dstance through the new successor must be the shortest and so d n (t new ) = d n s new + d n (t old ). Router n becomes PASSIVE f t receves a l n s new REPLY from each of ts neghbors ncludng n 1. Therefore, n 1 must be notfed about d n (t old ). Therefore: d n 1 (t) = d n (t old ) d n (t new ) = d n (t). (8) Substtutng ths equaton n 6 renders the result of ths lemma. Therefore, the lemma s true n all cases. Lemma 4: Consder a network that s loo free before an arbtrary tme t and n whch a sngle dffusng comutaton takes lace. Let two network nodes n and n +1 be such that n +1 V n. Indeendently of the state of these two nodes, t must be true that: (fd n (t) > fd n+1 (t)) (fd n (t) = fd n+1 (t) n > n +1 ) (9) Proof: Consder the case that router n s PASSIVE, then from Lemma 3 and the fact that routers select ther next hos based on NSC, t must be true that: (fd n (fd n > d n (t)) = d n (t) n > n +1 ) (10) Consder the case that router n +1 s ACTIVE. Router n +1 cannot change ts successor or ncrease ts feasble dstance. If router n rocessed the last message that router n +1 sent before tme t, then: d n (t) = fd n+1 (t) and the lemma s true. Assume router n dd not rocess the last message that router n +1 sent before tme t. Router n must send a REPLY to n +1 the last tme that router n +1 became PASSIVE at tme t reortng a dstance d n+1 (t old ) = d n+1 s old + ls n+1 old. If router n +1 dd not reset ts feasble dstance snce the last tme t became assve, fd n+1, then, d n+1 (t old ) fd n+1 (t). Consder the case that router n +1 resets fd n+1 the last tme before t that t becomes PASSIVE. Router n +1 cannot change ts successor or exerence any ncrement n ts dstance through ts old successor, s old. Hence, d n+1 (t new ) (t old ). On the other hand, the dstance through the new d n+1 successor must be the smallest among all neghbors ncludng the old successor and so d n+1 (t new ) = (d n+1 s new + ls n+1 new ) d n+1 (t old ). Router n +1 becomes PASSIVE f t receves a REPLY from each of ts neghbors, ncludng n. Therefore, n must be notfed about d n+1 (t old ). Therefore, d n (t) = d n+1 (t old ) d n+1 (t new ) fd n+1 (t new ) (11) The feasble dstance fd n+1 (t new ) wth t new < t cannot ncrease untl router n +1 becomes PASSIVE agan; therefore,fd n+1 (t new ) fd n (t). The result of the lemma follows n ths case by substtutng ths result n Eqs. (11) and Eq. (10). Now consder the case that router n +1 s PASSIVE. If router n rocessed the last message that router n +1 sent before tme t, then d n (t) = d n+1 (t) fd n+1 (t) and the lemma s true. Now consder the case that router n dd not rocess the last message router n +1 sent before tme t. If router n +1 dd not reset fd n+1 then d n+1 (t old ) fd n+1 (t). On the other hand, f router n +1 resets fd n+1 then we can conclude that fd n+1 (t new ) fd n (t) and n > n +1 usng an argument smlar to one we used for the ACTIVE mode. Hence, the lemma s true for all cases. NSC and SRC guarantees loo-freedom at every tme nstant. If we consder the lnk form router to ts vald next ho wth resect to a secfc refx as a drected edge, then the grah contanng all ths drected lnks s a drected acyclc grah (DAG) wth resect to that secfc refx. The DAG reresentng the relatonsh of vald next hos regardng refx s denoted by D. Lemma 5: If routers are nvolved n a sngle dffusng comutaton then D s loo-free at every nstant. Proof: Assume for the sake of contradcton that D s loo-free before an arbtrary tme t and a loo L consstng of h hos s created at tme t l > t when router q udates V q after
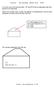
8 num. messages Add Prefx num. messages Delete Prefx num. messages Lnk Falure num. messages Lnk Recovery num. oeratons num. of relcas (a) Add Prefx num. oeratons num. of relcas (b) Delete Prefx num. oeratons num. of relcas (c) Lnk Falure num. oeratons num. of relcas (d) Lnk Recovery 10 0 num. of relcas (e) 10 0 num. of relcas (f) 10 0 num. of relcas (g) 10 0 num. of relcas (h) Fg. 2. Smulaton results showng average number of messages and average number of oeratons vs number of relcas rocessng an nut event. Assume that L = {n 1, n 2,..., n h } s the loo created, where n +1 V n for 1 h and n 1 V n h. If router n 1 changes ts next ho as a result of changng ts successor, t must be n PASSIVE mode at tme t l because an ACTIVE router cannot change ts successor or udate ts next-ho set. If all routers n L are PASSIVE at tme t l, ether all of them have always been PASSIVE at every nstant before t l, or at least one of them was ACTIVE for a whle and became PASSIVE before t l. If no router was ever ACTIVE before tme t l, t follows from Theorem 1 that udatng V n cannot create loo. Therefore, for router n 1 to create a loo, at least one of the routers must have been ACTIVE before tme t. If all routers are n PASSIVE mode at tme t, traversng L and alyng Theorem 10 leads to the erroneous concluson that ether d n1 > d n1 or n 1 > n 1. Therefore udatng V n1 cannot create a loo f all routers n the L are PASSIVE at tme t. Assume that only one dffusng comutaton s takng lace at tme t l. Based on Lemma 4 traversng loo L leads to the concluson that ether fd n > fd n or n > n, whch s a contradcton. Therefore, f only a sngle dffusng comutaton takes lace, then L cannot be formed when routers use SRC and NSC along wth dfusng comutatons to select next hos to reach the destnaton refx. At steady state, the grah contanng the successors and connected lnks between them, must create a tree. The tree contanng successors that are ACTIVE regardng refx and artcatng n a dffuson comutaton started form router at tme t are called dffusng tree (T (t)). Theorem 6: consders each comutaton ndvdually and n the roer sequence. Proof: Assume router s the only router that has started a dffusng comutaton u to tme t. If router generates a sngle dffuson comutaton, the roof s mmedate. Consder the case that router generates multle dffusng comutatons. Any router that s already artcatng n the current dffusng comutaton (routers n the T, ncludng the router ) cannot send a new QUERY untl t receves all the reles to the QUERY of the current comutaton and becomes PASSIVE. Note that each router rocesses each event n order. Also, when a router becomes PASSIVE, t must send a REPLY to ts successor, f t has any. Therefore, all the routers n T must rocess each dffusng comutaton ndvdually and n the roer sequence. Consder the case that multle sources of dffusng comutatons exst regardng refx n the network. Assume router s ACTIVE at tme t. Then ether router s the orgnator of the dffusng comutaton (o = 1 or 2), or receved a QUERY from ts successor (o = 3 or 4). If o = 1 or 3, the router must become PASSIVE before t can send another QUERY. If the router s the orgnator of the comutaton (o = 1 or 2) and receves a QUERY form ts successor, t holds that QUERY and sets o =4. Therefore, all the routers n the T reman n the same comutaton. Router can forward the new QUERY and become the art of the larger T s only after t receves a REPLY form each of ts neghbors for the current dffusng comutaton. If router a s ACTIVE and receves a QUERY from ts neghbor k s a, then t sends a REPLY to ts neghbor before creatng a dffusng comutaton, whch means that T a s not art of the ACTIVE T to whch k belongs. Therefore, any two ACTIVE T and T j have an emty ntersecton at any gven tme, t thus follows from the revous case that the Theorem s true. V. PERFORMANCE COMPARISON We comare wth a lnk-state routng rotocol gven that NR [13] s based on lnk states and s the routng rotocol advocated n NDN, one of the leadng ICN archtectures. We mlemented and an dealzed verson of NR, whch we smly call I (for deal lnk-state), n ns-3 usng the needed extensons to suort content-centrc networkng [19]. In the smulatons, I roagates udate messages usng the ntellgent floodng mechansm. There are two tyes of Lnk State Advertsements (A): An adjacency
9 A carres nformaton regardng a router, ts neghbors, and connected lnks; and a refx A advertses name refxes, as secfed n [13]. For convenence, sends HELLO messages between neghbors to detect changes n the sate of nodes and lnks. However, HELLO s can be omtted n a real mlementaton and detectng node adjacences can be done my montorng acket forwardng success n the data lane. The AT&T toology [20] s used because t s a realstc toology for smulatons that mmc art of the Internet toology. It has 154 nodes and 184 lnks. A node has 2.4 neghbors on average. In the smulatons, the cost of a lnk s set to one unt, and 30 nodes are selected as anchors that advertse 1200 unque name refxes. We generated test cases consstng of sngle lnk falure and recovery, and a sngle refx addton and deleton. To comare the comutaton and communcaton overhead of and I, we measured the number of routng messages transmtted over the network and the number of oeratons executed by each routng rotocol. The number of messages for I ncludes the number of HELLO messages, Adjacency As, and Prefx As. For, ths measurement ndcates the total number of all the routng messages transmtted as a result of any changes. The oeraton count s ncremented whenever an event occurs, and statements wthn a loo are executed. The smulaton results comarng wth I are dected n Fgure 2. In each grah, the horzontal axes s the average number of anchors er refx,.e., the number of anchors that advertse the same refx to the network. We consdered four scenaros: addng a new refx to the network; deletng one refx from one of the relcas; a sngle lnk falure; and a sngle lnk recovery. Hence, I ncurs the same sgnalng overhead ndeendently of how many A s are carred n an udate. Fgures (2a - 2d) showthe number of messages transmtted n the whole network whle Fgures (2e - 2h) show the number of oeratons each rotocol executed after the change. The number of oeratons n the fgure s n logarthmc scale. I advertses refxes from each of the relcas to the whole network. As the number of relcas ncreases, the number of messages ncreases, because each relca advertses ts own Prefx A. In, addng a new refx affects nodes n small regons and hence the number of messages and oeratons are fewer than n I. Deletng a refx from one of the relcas results n several dffusng comutatons n, whch results n more sgnalng. However, the number of messages decreases as the number of relcas ncreases, because the event affect fewer routers. In I one Prefx A wll be advertsed for each deleton. The comutaton of refx deleton s comarable; however, moses less comutaton overhead when the number of relcas reach 4. has less communcaton overhead comared to I after a lnk recovery or a lnk falure. The need to execute Djkstra s shortest-ath frst for each neghbor results n I requrng more comutatons than. outerforms NR for toology changes as well as addng a new refx. VI. CONCLUSION We ntroduced the frst name-based content routng rotocol based on dffusng comutatons () and roved that t rovdes loo-free mult-ath routes to mult-homed name refxes at every nstant. Routers that run do not requre to have knowledge about the network toology, use comlete aths to content relcas, know about all the stes storng relcas of named content, or use erodc udates. has better erformance comared to lnk-state routng rotocols when toology changes occur or new refxes are ntroduced to the network. A real mlementaton of would not requre the use of HELLO s used n our smulatons, and hence ts overhead s far less than routng rotocols that rely on A s valdated by sequence numbers, whch requre erodc udates to work correctly. VII. ACKNOWLEDGMENTS Ths work was suorted n art by the Baskn Char of Comuter Engneerng at UCSC. REFERENCES [1] M. Bar et al., A Survey of Namng and Routng n Informaton-Centrc Networks, IEEE Communcatons Magazne, vol. 50, no. 12, , Dec [2] J. Behrens and J.J. Garca-Luna-Aceves, Herarchcal Routng Usng Lnk Vectors, Proc. IEEE INFOCOM 98, March [3] J. Cho et al., A Survey on Content-Orented Networkng for Effcent Content Delvery, IEEE Communcatons Magazne, March [4] J. J. Garca-Luna-Aceves, A Dstrbuted, Loo-Free, Shortest-Path Routng Algorthm, Proc. IEEE INFOCOM 88, Mar [5] J. J. Garca-Luna-Aceves, Loo-Free Routng Usng Dffusng Comutatons, IEEE/ACM Transactons on Networkng, [6] J.J. Garca-Luna-Aceves and M. Sohn, Scalable Lnk-State Internet Routng, Proc. ICNP 98, Oct [7] J.J. Garca-Luna-Aceves, System and Method for Dscoverng Informaton Objects and Informaton Object Reostores n Comuter Networks, U.S. Patent 8,572,214, October 29, [8] J. J. Garca-Luna-Aceves, Name-Based Content Routng n Informaton Centrc Networks Usng Dstance Informaton, n Proc. ACM ICN 14, [9] J. J. Garca-Luna-Aceves, Routng to Mult-Instantated Destnatons: Prncles and Alcatons, Proc. IEEE ICNP 2014, [10] J. J. Garca-Luna-Aceves, A Fault-Tolerant Forwardng Strategy for Interest-Based Informaton Centrc Networks, Proc. IFIP Networkng 15, [11] K. V. Katsaros et al., On Inter-Doman Name Resoluton for Informaton-Centrc Networks, Proc. Networkng 2012, May [12] T. Koonen et al., A Data-Orented (and Beyond) Network Archtecture, Proc. ACM SIGCOMM 07, [13] V. Lehman et al., A Secure Lnk State Routng Protocol for NDN, IEEE Access, Jan [14] Moblty frst roject. [Onlne]. Avalable: htt://mobltyfrst.wnlab. rutgers.edu/ [15] Publsh subscrbe nternet technology (PURSUIT) roject. [Onlne]. Avalable: htt:// [16] J. Raju et al., System and Method for Informaton Object Routng n Comuter Networks, U.S. Patent 7,552,233, June 23, 2009 [17] M. Sohn and J.J. Garca-Luna-Aceves, Neghborhood Aware Source Routng, Proc. ACM MobHoc 2001, Oct [18] Scalable and adatve nternet solutons (SAIL) roject. [Onlne]. Avalable: htt:// [19] J. Mathewson et al., Sconet : Smulator content networkng, CCNxCon, [20] O. Heckmann et al., On realstc network toologes for smulaton MoMeTools 03, 2003.
Loop-Free Multipath Routing Using Generalized Diffusing Computations
 1 Loop-Free Multpath Routng Usng Generalzed Dffusng Computatons Wllam T. Zaumen J.J. Garca-Luna-Aceves Sun Mcrosystems, Inc. Computer Engneerng Department 901 San Antono Avenue School of Engneerng Palo
1 Loop-Free Multpath Routng Usng Generalzed Dffusng Computatons Wllam T. Zaumen J.J. Garca-Luna-Aceves Sun Mcrosystems, Inc. Computer Engneerng Department 901 San Antono Avenue School of Engneerng Palo
A Scheduling Algorithm of Periodic Messages for Hard Real-time Communications on a Switched Ethernet
 IJCSNS Internatonal Journal of Comuter Scence and Networ Securty VOL.6 No.5B May 26 A Schedulng Algorthm of Perodc Messages for Hard eal-tme Communcatons on a Swtched Ethernet Hee Chan Lee and Myung Kyun
IJCSNS Internatonal Journal of Comuter Scence and Networ Securty VOL.6 No.5B May 26 A Schedulng Algorthm of Perodc Messages for Hard eal-tme Communcatons on a Swtched Ethernet Hee Chan Lee and Myung Kyun
6.854 Advanced Algorithms Petar Maymounkov Problem Set 11 (November 23, 2005) With: Benjamin Rossman, Oren Weimann, and Pouya Kheradpour
 6.854 Advanced Algorthms Petar Maymounkov Problem Set 11 (November 23, 2005) Wth: Benjamn Rossman, Oren Wemann, and Pouya Kheradpour Problem 1. We reduce vertex cover to MAX-SAT wth weghts, such that the
6.854 Advanced Algorthms Petar Maymounkov Problem Set 11 (November 23, 2005) Wth: Benjamn Rossman, Oren Wemann, and Pouya Kheradpour Problem 1. We reduce vertex cover to MAX-SAT wth weghts, such that the
A note on Schema Equivalence
 note on Schema Equvalence.H.M. ter Hofstede and H.. Proer and Th.P. van der Wede E.Proer@acm.org PUBLISHED S:.H.M. ter Hofstede, H.. Proer, and Th.P. van der Wede. Note on Schema Equvalence. Techncal Reort
note on Schema Equvalence.H.M. ter Hofstede and H.. Proer and Th.P. van der Wede E.Proer@acm.org PUBLISHED S:.H.M. ter Hofstede, H.. Proer, and Th.P. van der Wede. Note on Schema Equvalence. Techncal Reort
Simulation Based Analysis of FAST TCP using OMNET++
 Smulaton Based Analyss of FAST TCP usng OMNET++ Umar ul Hassan 04030038@lums.edu.pk Md Term Report CS678 Topcs n Internet Research Sprng, 2006 Introducton Internet traffc s doublng roughly every 3 months
Smulaton Based Analyss of FAST TCP usng OMNET++ Umar ul Hassan 04030038@lums.edu.pk Md Term Report CS678 Topcs n Internet Research Sprng, 2006 Introducton Internet traffc s doublng roughly every 3 months
Evaluation of an Enhanced Scheme for High-level Nested Network Mobility
 IJCSNS Internatonal Journal of Computer Scence and Network Securty, VOL.15 No.10, October 2015 1 Evaluaton of an Enhanced Scheme for Hgh-level Nested Network Moblty Mohammed Babker Al Mohammed, Asha Hassan.
IJCSNS Internatonal Journal of Computer Scence and Network Securty, VOL.15 No.10, October 2015 1 Evaluaton of an Enhanced Scheme for Hgh-level Nested Network Moblty Mohammed Babker Al Mohammed, Asha Hassan.
Virtual Memory. Background. No. 10. Virtual Memory: concept. Logical Memory Space (review) Demand Paging(1) Virtual Memory
 Background EECS. Operatng System Fundamentals No. Vrtual Memory Prof. Hu Jang Department of Electrcal Engneerng and Computer Scence, York Unversty Memory-management methods normally requres the entre process
Background EECS. Operatng System Fundamentals No. Vrtual Memory Prof. Hu Jang Department of Electrcal Engneerng and Computer Scence, York Unversty Memory-management methods normally requres the entre process
Efficient Caching of Video Content to an Architecture of Proxies according to a Frequency-Based Cache Management Policy
 Effcent Cachng of Vdeo Content to an Archtecture of Proxes accordng to a Frequency-Based Cache Management Polcy Anna Satsou, Mchael Pateraks Laboratory of Informaton and Comuter Networks Deartment of Electronc
Effcent Cachng of Vdeo Content to an Archtecture of Proxes accordng to a Frequency-Based Cache Management Polcy Anna Satsou, Mchael Pateraks Laboratory of Informaton and Comuter Networks Deartment of Electronc
E-DEEC- Enhanced Distributed Energy Efficient Clustering Scheme for heterogeneous WSN
 21 1st Internatonal Conference on Parallel, Dstrbuted and Grd Comutng (PDGC - 21) E-DEEC- Enhanced Dstrbuted Energy Effcent Clusterng Scheme for heterogeneous WSN Parul San Deartment of Comuter Scence
21 1st Internatonal Conference on Parallel, Dstrbuted and Grd Comutng (PDGC - 21) E-DEEC- Enhanced Dstrbuted Energy Effcent Clusterng Scheme for heterogeneous WSN Parul San Deartment of Comuter Scence
MPATH: A Loop-free Multipath Routing Algorithm
 1 MPATH: A Loop-free Multpath Routng Algorthm SRINIVAS VUTUKURY vutukury@cse.ucsc.edu Computer Scences Department Unversty of Calforna Santa Cruz, CA 9564 J.J. GARCIA-LUNA-ACEVES jj@cse.ucsc.edu Computer
1 MPATH: A Loop-free Multpath Routng Algorthm SRINIVAS VUTUKURY vutukury@cse.ucsc.edu Computer Scences Department Unversty of Calforna Santa Cruz, CA 9564 J.J. GARCIA-LUNA-ACEVES jj@cse.ucsc.edu Computer
MOBILITY-BASED MULTICAST ROUTING ALGORITHM FOR WIRELESS MOBILE AD-HOC NETWORKS: A LEARNING AUTOMATA APPROACH
 بسم االله الرحمن الرحيم (الهي همه چيز را به تو مي سپارم ياريم كن) MOBILITY-BASED MULTICAST ROUTING ALGORITHM FOR WIRELESS MOBILE AD-HOC NETWORKS: A LEARNING AUTOMATA APPROACH JAVAD AKBARI TORKESTANI Deartment
بسم االله الرحمن الرحيم (الهي همه چيز را به تو مي سپارم ياريم كن) MOBILITY-BASED MULTICAST ROUTING ALGORITHM FOR WIRELESS MOBILE AD-HOC NETWORKS: A LEARNING AUTOMATA APPROACH JAVAD AKBARI TORKESTANI Deartment
Solving Optimization Problems on Orthogonal Ray Graphs
 Solvng Otmzaton Problems on Orthogonal Ray Grahs Steven Chalck 1, Phl Kndermann 2, Faban L 2, Alexander Wolff 2 1 Insttut für Mathematk, TU Berln, Germany chalck@math.tu-berln.de 2 Lehrstuhl für Informatk
Solvng Otmzaton Problems on Orthogonal Ray Grahs Steven Chalck 1, Phl Kndermann 2, Faban L 2, Alexander Wolff 2 1 Insttut für Mathematk, TU Berln, Germany chalck@math.tu-berln.de 2 Lehrstuhl für Informatk
THE CONDENSED FUZZY K-NEAREST NEIGHBOR RULE BASED ON SAMPLE FUZZY ENTROPY
 Proceedngs of the 20 Internatonal Conference on Machne Learnng and Cybernetcs, Guln, 0-3 July, 20 THE CONDENSED FUZZY K-NEAREST NEIGHBOR RULE BASED ON SAMPLE FUZZY ENTROPY JUN-HAI ZHAI, NA LI, MENG-YAO
Proceedngs of the 20 Internatonal Conference on Machne Learnng and Cybernetcs, Guln, 0-3 July, 20 THE CONDENSED FUZZY K-NEAREST NEIGHBOR RULE BASED ON SAMPLE FUZZY ENTROPY JUN-HAI ZHAI, NA LI, MENG-YAO
Transaction-Consistent Global Checkpoints in a Distributed Database System
 Proceedngs of the World Congress on Engneerng 2008 Vol I Transacton-Consstent Global Checkponts n a Dstrbuted Database System Jang Wu, D. Manvannan and Bhavan Thurasngham Abstract Checkpontng and rollback
Proceedngs of the World Congress on Engneerng 2008 Vol I Transacton-Consstent Global Checkponts n a Dstrbuted Database System Jang Wu, D. Manvannan and Bhavan Thurasngham Abstract Checkpontng and rollback
Advanced LEACH: A Static Clustering-based Heteroneous Routing Protocol for WSNs
 Advanced LEACH: A Statc Clusterng-based Heteroneous Routng Protocol for WSNs A. Iqbal 1, M. Akbar 1, N. Javad 1, S. H. Bouk 1, M. Ilah 1, R. D. Khan 2 1 COMSATS Insttute of Informaton Technology, Islamabad,
Advanced LEACH: A Statc Clusterng-based Heteroneous Routng Protocol for WSNs A. Iqbal 1, M. Akbar 1, N. Javad 1, S. H. Bouk 1, M. Ilah 1, R. D. Khan 2 1 COMSATS Insttute of Informaton Technology, Islamabad,
For instance, ; the five basic number-sets are increasingly more n A B & B A A = B (1)
 Secton 1.2 Subsets and the Boolean operatons on sets If every element of the set A s an element of the set B, we say that A s a subset of B, or that A s contaned n B, or that B contans A, and we wrte A
Secton 1.2 Subsets and the Boolean operatons on sets If every element of the set A s an element of the set B, we say that A s a subset of B, or that A s contaned n B, or that B contans A, and we wrte A
An Approach for Congestion Control in Sensor Network Using Priority Based Application*
 An Aroach for Congeston Control n Sensor Network Usng Prorty Based Alcaton* Md. Obadur Rahman Muhammad Mostafa Monowar Byung Goo Cho Choong Seon Hong Deartment of Comuter Engneerng, Kyung Hee Unversty
An Aroach for Congeston Control n Sensor Network Usng Prorty Based Alcaton* Md. Obadur Rahman Muhammad Mostafa Monowar Byung Goo Cho Choong Seon Hong Deartment of Comuter Engneerng, Kyung Hee Unversty
I 2 C: A Holistic Approach to Prolong the Sensor Network Lifetime
 : A Holstc Aroach to Prolong the Sensor Network Lfetme Yang Peng, Z L, Da Qao, and Wensheng Zhang Iowa State Unversty, Ames, IA 511 {yangeng, zl, da, wzhang}@astate.edu Abstract We resent a novel holstc
: A Holstc Aroach to Prolong the Sensor Network Lfetme Yang Peng, Z L, Da Qao, and Wensheng Zhang Iowa State Unversty, Ames, IA 511 {yangeng, zl, da, wzhang}@astate.edu Abstract We resent a novel holstc
Broadcast Time Synchronization Algorithm for Wireless Sensor Networks Chaonong Xu 1)2)3), Lei Zhao 1)2), Yongjun Xu 1)2) and Xiaowei Li 1)2)
 Broadcast Tme Synchronzaton Algorthm for Wreless Sensor Networs Chaonong Xu )2)3), Le Zhao )2), Yongun Xu )2) and Xaowe L )2) ) Key Laboratory of Comuter Archtecture, Insttute of Comutng Technology Chnese
Broadcast Tme Synchronzaton Algorthm for Wreless Sensor Networs Chaonong Xu )2)3), Le Zhao )2), Yongun Xu )2) and Xaowe L )2) ) Key Laboratory of Comuter Archtecture, Insttute of Comutng Technology Chnese
A Base Station-Coordinated Contention Resolution for IEEE PMP Networks
 A Base Staton-Coordnated Contenton Resoluton for IEEE 802.6 PMP Networks Wenyan Lu, Weja Ja,2, Wenfeng Du, and Ldong Ln 2 School of Informaton Scence & Engneerng, Central South Unversty, Changsha, 40083,
A Base Staton-Coordnated Contenton Resoluton for IEEE 802.6 PMP Networks Wenyan Lu, Weja Ja,2, Wenfeng Du, and Ldong Ln 2 School of Informaton Scence & Engneerng, Central South Unversty, Changsha, 40083,
The Greedy Method. Outline and Reading. Change Money Problem. Greedy Algorithms. Applications of the Greedy Strategy. The Greedy Method Technique
 //00 :0 AM Outlne and Readng The Greedy Method The Greedy Method Technque (secton.) Fractonal Knapsack Problem (secton..) Task Schedulng (secton..) Mnmum Spannng Trees (secton.) Change Money Problem Greedy
//00 :0 AM Outlne and Readng The Greedy Method The Greedy Method Technque (secton.) Fractonal Knapsack Problem (secton..) Task Schedulng (secton..) Mnmum Spannng Trees (secton.) Change Money Problem Greedy
Load-Balanced Anycast Routing
 Load-Balanced Anycast Routng Chng-Yu Ln, Jung-Hua Lo, and Sy-Yen Kuo Department of Electrcal Engneerng atonal Tawan Unversty, Tape, Tawan sykuo@cc.ee.ntu.edu.tw Abstract For fault-tolerance and load-balance
Load-Balanced Anycast Routng Chng-Yu Ln, Jung-Hua Lo, and Sy-Yen Kuo Department of Electrcal Engneerng atonal Tawan Unversty, Tape, Tawan sykuo@cc.ee.ntu.edu.tw Abstract For fault-tolerance and load-balance
Routing in Degree-constrained FSO Mesh Networks
 Internatonal Journal of Hybrd Informaton Technology Vol., No., Aprl, 009 Routng n Degree-constraned FSO Mesh Networks Zpng Hu, Pramode Verma, and James Sluss Jr. School of Electrcal & Computer Engneerng
Internatonal Journal of Hybrd Informaton Technology Vol., No., Aprl, 009 Routng n Degree-constraned FSO Mesh Networks Zpng Hu, Pramode Verma, and James Sluss Jr. School of Electrcal & Computer Engneerng
Bayesian Networks: Independencies and Inference. What Independencies does a Bayes Net Model?
 Bayesan Networks: Indeendences and Inference Scott Daves and Andrew Moore Note to other teachers and users of these sldes. Andrew and Scott would be delghted f you found ths source materal useful n gvng
Bayesan Networks: Indeendences and Inference Scott Daves and Andrew Moore Note to other teachers and users of these sldes. Andrew and Scott would be delghted f you found ths source materal useful n gvng
Load Balancing for Hex-Cell Interconnection Network
 Int. J. Communcatons, Network and System Scences,,, - Publshed Onlne Aprl n ScRes. http://www.scrp.org/journal/jcns http://dx.do.org/./jcns.. Load Balancng for Hex-Cell Interconnecton Network Saher Manaseer,
Int. J. Communcatons, Network and System Scences,,, - Publshed Onlne Aprl n ScRes. http://www.scrp.org/journal/jcns http://dx.do.org/./jcns.. Load Balancng for Hex-Cell Interconnecton Network Saher Manaseer,
An Optimal Algorithm for Prufer Codes *
 J. Software Engneerng & Applcatons, 2009, 2: 111-115 do:10.4236/jsea.2009.22016 Publshed Onlne July 2009 (www.scrp.org/journal/jsea) An Optmal Algorthm for Prufer Codes * Xaodong Wang 1, 2, Le Wang 3,
J. Software Engneerng & Applcatons, 2009, 2: 111-115 do:10.4236/jsea.2009.22016 Publshed Onlne July 2009 (www.scrp.org/journal/jsea) An Optmal Algorthm for Prufer Codes * Xaodong Wang 1, 2, Le Wang 3,
Research Article Energy Efficient Interest Forwarding in NDN-Based Wireless Sensor Networks
 Moble Informaton Systems Volume 2016, Artcle ID 3127029, 15 pages http://dx.do.org/10.1155/2016/3127029 Research Artcle Energy Effcent Interest Forwardng n NDN-Based Wreless Sensor Networks Shua Gao, 1
Moble Informaton Systems Volume 2016, Artcle ID 3127029, 15 pages http://dx.do.org/10.1155/2016/3127029 Research Artcle Energy Effcent Interest Forwardng n NDN-Based Wreless Sensor Networks Shua Gao, 1
Performance Improvement of Direct Diffusion Algorithm in Sensor Networks
 Mddle-East Journal of Scentfc Research 2 (): 566-574, 202 ISSN 990-9233 IDOSI Publcatons, 202 DOI: 0.5829/dos.mejsr.202.2..43 Performance Improvement of Drect Dffuson Algorthm n Sensor Networks Akbar Bemana
Mddle-East Journal of Scentfc Research 2 (): 566-574, 202 ISSN 990-9233 IDOSI Publcatons, 202 DOI: 0.5829/dos.mejsr.202.2..43 Performance Improvement of Drect Dffuson Algorthm n Sensor Networks Akbar Bemana
DEAR: A DEVICE AND ENERGY AWARE ROUTING PROTOCOL FOR MOBILE AD HOC NETWORKS
 DEAR: A DEVICE AND ENERGY AWARE ROUTING PROTOCOL FOR MOBILE AD HOC NETWORKS Arun Avudanayagam Yuguang Fang Wenjng Lou Department of Electrcal and Computer Engneerng Unversty of Florda Ganesvlle, FL 3261
DEAR: A DEVICE AND ENERGY AWARE ROUTING PROTOCOL FOR MOBILE AD HOC NETWORKS Arun Avudanayagam Yuguang Fang Wenjng Lou Department of Electrcal and Computer Engneerng Unversty of Florda Ganesvlle, FL 3261
Information Sciences
 Informaton Scences 79 (9) 369 367 ontents lsts avalable at ScenceDrect Informaton Scences ournal homepage: www.elsever.com/locate/ns Necessary and suffcent condtons for transacton-consstent global checkponts
Informaton Scences 79 (9) 369 367 ontents lsts avalable at ScenceDrect Informaton Scences ournal homepage: www.elsever.com/locate/ns Necessary and suffcent condtons for transacton-consstent global checkponts
Real-Time Guarantees. Traffic Characteristics. Flow Control
 Real-Tme Guarantees Requrements on RT communcaton protocols: delay (response s) small jtter small throughput hgh error detecton at recever (and sender) small error detecton latency no thrashng under peak
Real-Tme Guarantees Requrements on RT communcaton protocols: delay (response s) small jtter small throughput hgh error detecton at recever (and sender) small error detecton latency no thrashng under peak
Parallelism for Nested Loops with Non-uniform and Flow Dependences
 Parallelsm for Nested Loops wth Non-unform and Flow Dependences Sam-Jn Jeong Dept. of Informaton & Communcaton Engneerng, Cheonan Unversty, 5, Anseo-dong, Cheonan, Chungnam, 330-80, Korea. seong@cheonan.ac.kr
Parallelsm for Nested Loops wth Non-unform and Flow Dependences Sam-Jn Jeong Dept. of Informaton & Communcaton Engneerng, Cheonan Unversty, 5, Anseo-dong, Cheonan, Chungnam, 330-80, Korea. seong@cheonan.ac.kr
A Simple Approximation to Minimum-Delay Routing
 A Smple Approxmaton to Mnmum-Delay Routng Srnvas Vutukury Computer Scence Department J.J. Garca-Luna-Aceves Computer Engneerng Department Baskn School of Engneerng Unversty of Calforna, Santa Cruz, CA
A Smple Approxmaton to Mnmum-Delay Routng Srnvas Vutukury Computer Scence Department J.J. Garca-Luna-Aceves Computer Engneerng Department Baskn School of Engneerng Unversty of Calforna, Santa Cruz, CA
CMPS 10 Introduction to Computer Science Lecture Notes
 CPS 0 Introducton to Computer Scence Lecture Notes Chapter : Algorthm Desgn How should we present algorthms? Natural languages lke Englsh, Spansh, or French whch are rch n nterpretaton and meanng are not
CPS 0 Introducton to Computer Scence Lecture Notes Chapter : Algorthm Desgn How should we present algorthms? Natural languages lke Englsh, Spansh, or French whch are rch n nterpretaton and meanng are not
DESIGNING TRANSMISSION SCHEDULES FOR WIRELESS AD HOC NETWORKS TO MAXIMIZE NETWORK THROUGHPUT
 DESIGNING TRANSMISSION SCHEDULES FOR WIRELESS AD HOC NETWORKS TO MAXIMIZE NETWORK THROUGHPUT Bran J. Wolf, Joseph L. Hammond, and Harlan B. Russell Dept. of Electrcal and Computer Engneerng, Clemson Unversty,
DESIGNING TRANSMISSION SCHEDULES FOR WIRELESS AD HOC NETWORKS TO MAXIMIZE NETWORK THROUGHPUT Bran J. Wolf, Joseph L. Hammond, and Harlan B. Russell Dept. of Electrcal and Computer Engneerng, Clemson Unversty,
A Model for System Resources in Flexible Time-Triggered Middleware Architectures
 A Model for System Resources n Flexble Tme-Trggered Mddleware Archtectures Adran Noguero 1, Isdro Calvo 2, Lus Almeda 3, and Una Gangot 2 1 Tecnala, Software Systems Engneerng Unt, Parque Tecnológco de
A Model for System Resources n Flexble Tme-Trggered Mddleware Archtectures Adran Noguero 1, Isdro Calvo 2, Lus Almeda 3, and Una Gangot 2 1 Tecnala, Software Systems Engneerng Unt, Parque Tecnológco de
IP mobility support is becoming very important as the
 706 IEEE TRANSACTIONS ON COMPUTERS, VOL. 52, NO. 6, JUNE 2003 A New Scheme for Reducng Lnk and Sgnalng Costs n Moble IP Young J. Lee and Ian F. Akyldz, Fellow, IEEE Abstract IP moblty support s provded
706 IEEE TRANSACTIONS ON COMPUTERS, VOL. 52, NO. 6, JUNE 2003 A New Scheme for Reducng Lnk and Sgnalng Costs n Moble IP Young J. Lee and Ian F. Akyldz, Fellow, IEEE Abstract IP moblty support s provded
Optimal Fault-Tolerant Routing in Hypercubes Using Extended Safety Vectors
 Optmal Fault-Tolerant Routng n Hypercubes Usng Extended Safety Vectors Je Wu Department of Computer Scence and Engneerng Florda Atlantc Unversty Boca Raton, FL 3343 Feng Gao, Zhongcheng L, and Ynghua Mn
Optmal Fault-Tolerant Routng n Hypercubes Usng Extended Safety Vectors Je Wu Department of Computer Scence and Engneerng Florda Atlantc Unversty Boca Raton, FL 3343 Feng Gao, Zhongcheng L, and Ynghua Mn
A Binarization Algorithm specialized on Document Images and Photos
 A Bnarzaton Algorthm specalzed on Document mages and Photos Ergna Kavalleratou Dept. of nformaton and Communcaton Systems Engneerng Unversty of the Aegean kavalleratou@aegean.gr Abstract n ths paper, a
A Bnarzaton Algorthm specalzed on Document mages and Photos Ergna Kavalleratou Dept. of nformaton and Communcaton Systems Engneerng Unversty of the Aegean kavalleratou@aegean.gr Abstract n ths paper, a
Video Proxy System for a Large-scale VOD System (DINA)
 Vdeo Proxy System for a Large-scale VOD System (DINA) KWUN-CHUNG CHAN #, KWOK-WAI CHEUNG *# #Department of Informaton Engneerng *Centre of Innovaton and Technology The Chnese Unversty of Hong Kong SHATIN,
Vdeo Proxy System for a Large-scale VOD System (DINA) KWUN-CHUNG CHAN #, KWOK-WAI CHEUNG *# #Department of Informaton Engneerng *Centre of Innovaton and Technology The Chnese Unversty of Hong Kong SHATIN,
An efficient iterative source routing algorithm
 An effcent teratve source routng algorthm Gang Cheng Ye Tan Nrwan Ansar Advanced Networng Lab Department of Electrcal Computer Engneerng New Jersey Insttute of Technology Newar NJ 7 {gc yt Ansar}@ntedu
An effcent teratve source routng algorthm Gang Cheng Ye Tan Nrwan Ansar Advanced Networng Lab Department of Electrcal Computer Engneerng New Jersey Insttute of Technology Newar NJ 7 {gc yt Ansar}@ntedu
Analysis of Continuous Beams in General
 Analyss of Contnuous Beams n General Contnuous beams consdered here are prsmatc, rgdly connected to each beam segment and supported at varous ponts along the beam. onts are selected at ponts of support,
Analyss of Contnuous Beams n General Contnuous beams consdered here are prsmatc, rgdly connected to each beam segment and supported at varous ponts along the beam. onts are selected at ponts of support,
Contour Error of the 3-DoF Hydraulic Translational Parallel Manipulator. Ryszard Dindorf 1,a, Piotr Wos 2,b
 Advanced Materals Research Vol. 874 (2014) 57-62 Onlne avalable snce 2014/Jan/08 at www.scentfc.net (2014) rans ech Publcatons, Swtzerland do:10.4028/www.scentfc.net/amr.874.57 Contour Error of the 3-DoF
Advanced Materals Research Vol. 874 (2014) 57-62 Onlne avalable snce 2014/Jan/08 at www.scentfc.net (2014) rans ech Publcatons, Swtzerland do:10.4028/www.scentfc.net/amr.874.57 Contour Error of the 3-DoF
Hermite Splines in Lie Groups as Products of Geodesics
 Hermte Splnes n Le Groups as Products of Geodescs Ethan Eade Updated May 28, 2017 1 Introducton 1.1 Goal Ths document defnes a curve n the Le group G parametrzed by tme and by structural parameters n the
Hermte Splnes n Le Groups as Products of Geodescs Ethan Eade Updated May 28, 2017 1 Introducton 1.1 Goal Ths document defnes a curve n the Le group G parametrzed by tme and by structural parameters n the
IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS, VOL. 35, NO. 3, MARCH
 IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS, VOL. 35, NO. 3, MARCH 07 7 A Game Theoretc Aroach for Dstrbuted Resource Allocaton and Orchestraton of Softwarzed Networks Salvatore D Oro, Student Member,
IEEE JOURNAL ON SELECTED AREAS IN COMMUNICATIONS, VOL. 35, NO. 3, MARCH 07 7 A Game Theoretc Aroach for Dstrbuted Resource Allocaton and Orchestraton of Softwarzed Networks Salvatore D Oro, Student Member,
QoS-Based Service Provision Schemes and Plan Durability in Service Composition
 QoS-Based Servce Provson Schemes and Plan Durablty n Servce Comoston Koramt Pchanaharee and Twtte Senvongse Deartment of Comuter Engneerng, Faculty of Engneerng, Chulalongkorn Unversty Phyatha Road, Pathumwan,
QoS-Based Servce Provson Schemes and Plan Durablty n Servce Comoston Koramt Pchanaharee and Twtte Senvongse Deartment of Comuter Engneerng, Faculty of Engneerng, Chulalongkorn Unversty Phyatha Road, Pathumwan,
Analytical Performance Analysis of Network- Processor-Based Application Designs
 Analytcal Performance Analyss of Networ- Processor-Based Alcaton Desgns e Lu BMC Software Inc. Waltham, MA e Wang Unversty of Massachusetts Lowell, MA Abstract Networ rocessors (NP) are desgned to rovde
Analytcal Performance Analyss of Networ- Processor-Based Alcaton Desgns e Lu BMC Software Inc. Waltham, MA e Wang Unversty of Massachusetts Lowell, MA Abstract Networ rocessors (NP) are desgned to rovde
Overview. CSC 2400: Computer Systems. Pointers in C. Pointers - Variables that hold memory addresses - Using pointers to do call-by-reference in C
 CSC 2400: Comuter Systems Ponters n C Overvew Ponters - Varables that hold memory addresses - Usng onters to do call-by-reference n C Ponters vs. Arrays - Array names are constant onters Ponters and Strngs
CSC 2400: Comuter Systems Ponters n C Overvew Ponters - Varables that hold memory addresses - Usng onters to do call-by-reference n C Ponters vs. Arrays - Array names are constant onters Ponters and Strngs
Recognition of Identifiers from Shipping Container Images Using Fuzzy Binarization and Enhanced Fuzzy Neural Network
 Recognton of Identfers from Shng Contaner Images Usng uzzy Bnarzaton and Enhanced uzzy Neural Networ Kwang-Bae Km Det. of Comuter Engneerng, Slla Unversty, Korea gbm@slla.ac.r Abstract. In ths aer, we
Recognton of Identfers from Shng Contaner Images Usng uzzy Bnarzaton and Enhanced uzzy Neural Networ Kwang-Bae Km Det. of Comuter Engneerng, Slla Unversty, Korea gbm@slla.ac.r Abstract. In ths aer, we
Research Article QPRD: QoS-Aware Peering Routing Protocol for Delay-Sensitive Data in Hospital Body Area Network
 Moble Informaton Systems Volume 15, Artcle ID 153232, 16 pages http://dx.do.org/1.1155/15/153232 Research Artcle : QoS-Aware Peerng Routng Protocol for Delay-Senstve Data n Hosptal Body Area Network Zahoor
Moble Informaton Systems Volume 15, Artcle ID 153232, 16 pages http://dx.do.org/1.1155/15/153232 Research Artcle : QoS-Aware Peerng Routng Protocol for Delay-Senstve Data n Hosptal Body Area Network Zahoor
A Novel TCP with Dynamic Burst-Contention Loss Notification over OBS Networks
 A Novel TCP wth Dynamc Burst-Contenton Loss Notfcaton over OB Networks Basem hhada 1 and Pn-Han Ho 1, 1 D. R. Chraton chool of Comuter cence, Unversty of Waterloo, Waterloo, Canada Deartment of Electrcal
A Novel TCP wth Dynamc Burst-Contenton Loss Notfcaton over OB Networks Basem hhada 1 and Pn-Han Ho 1, 1 D. R. Chraton chool of Comuter cence, Unversty of Waterloo, Waterloo, Canada Deartment of Electrcal
Introduction. Leslie Lamports Time, Clocks & the Ordering of Events in a Distributed System. Overview. Introduction Concepts: Time
 Lesle Laports e, locks & the Orderng of Events n a Dstrbuted Syste Joseph Sprng Departent of oputer Scence Dstrbuted Systes and Securty Overvew Introducton he artal Orderng Logcal locks Orderng the Events
Lesle Laports e, locks & the Orderng of Events n a Dstrbuted Syste Joseph Sprng Departent of oputer Scence Dstrbuted Systes and Securty Overvew Introducton he artal Orderng Logcal locks Orderng the Events
A Novel Efficient Remote Data Possession Checking Protocol in Cloud Storage
 Ths artcle has been acceted for ublcaton n a future ssue of ths journal, but has not been fully edted. Content may change ror to fnal ublcaton. Ctaton nformaton: DOI 10.1109/TIFS.2016.2601070, IEEE Transactons
Ths artcle has been acceted for ublcaton n a future ssue of ths journal, but has not been fully edted. Content may change ror to fnal ublcaton. Ctaton nformaton: DOI 10.1109/TIFS.2016.2601070, IEEE Transactons
Problem Set 3 Solutions
 Introducton to Algorthms October 4, 2002 Massachusetts Insttute of Technology 6046J/18410J Professors Erk Demane and Shaf Goldwasser Handout 14 Problem Set 3 Solutons (Exercses were not to be turned n,
Introducton to Algorthms October 4, 2002 Massachusetts Insttute of Technology 6046J/18410J Professors Erk Demane and Shaf Goldwasser Handout 14 Problem Set 3 Solutons (Exercses were not to be turned n,
Performance Evaluation of Multicast Video Streaming via P2P Networking
 Secal Issue of Internatonal Journal of Comuter Alcatons (0975 8887) on Electroncs, Informaton and Communcaton Engneerng - ICEICE o.4, Dec 20 erformance Evaluaton of Multcast Vdeo Streamng va 2 etworkng
Secal Issue of Internatonal Journal of Comuter Alcatons (0975 8887) on Electroncs, Informaton and Communcaton Engneerng - ICEICE o.4, Dec 20 erformance Evaluaton of Multcast Vdeo Streamng va 2 etworkng
A New Transaction Processing Model Based on Optimistic Concurrency Control
 A New Transacton Processng Model Based on Optmstc Concurrency Control Wang Pedong,Duan Xpng,Jr. Abstract-- In ths paper, to support moblty and dsconnecton of moble clents effectvely n moble computng envronment,
A New Transacton Processng Model Based on Optmstc Concurrency Control Wang Pedong,Duan Xpng,Jr. Abstract-- In ths paper, to support moblty and dsconnecton of moble clents effectvely n moble computng envronment,
A Traffic Aware Routing Protocol for Congestion Avoidance in Content-Centric Network
 , pp.69-80 http://dx.do.org/10.14257/jmue.2014.9.9.08 A Traffc Aware Routng Protocol for Congeston Avodance n Content-Centrc Network Jung-Jae Km 1, Mn-Woo Ryu 2*, S-Ho Cha 3 and Kuk-Hyun Cho 1 1 Dept.
, pp.69-80 http://dx.do.org/10.14257/jmue.2014.9.9.08 A Traffc Aware Routng Protocol for Congeston Avodance n Content-Centrc Network Jung-Jae Km 1, Mn-Woo Ryu 2*, S-Ho Cha 3 and Kuk-Hyun Cho 1 1 Dept.
Available online at ScienceDirect. Procedia Computer Science 94 (2016 )
 Avalable onlne at www.scencedrect.com ScenceDrect Proceda Comuter Scence 94 (2016 ) 176 182 The 13th Internatonal Conference on Moble Systems and Pervasve Comutng (MobSPC 2016) An Effcent QoS-aware Web
Avalable onlne at www.scencedrect.com ScenceDrect Proceda Comuter Scence 94 (2016 ) 176 182 The 13th Internatonal Conference on Moble Systems and Pervasve Comutng (MobSPC 2016) An Effcent QoS-aware Web
RAP. Speed/RAP/CODA. Real-time Systems. Modeling the sensor networks. Real-time Systems. Modeling the sensor networks. Real-time systems:
 Speed/RAP/CODA Presented by Octav Chpara Real-tme Systems Many wreless sensor network applcatons requre real-tme support Survellance and trackng Border patrol Fre fghtng Real-tme systems: Hard real-tme:
Speed/RAP/CODA Presented by Octav Chpara Real-tme Systems Many wreless sensor network applcatons requre real-tme support Survellance and trackng Border patrol Fre fghtng Real-tme systems: Hard real-tme:
R s s f. m y s. SPH3UW Unit 7.3 Spherical Concave Mirrors Page 1 of 12. Notes
 SPH3UW Unt 7.3 Sphercal Concave Mrrors Page 1 of 1 Notes Physcs Tool box Concave Mrror If the reflectng surface takes place on the nner surface of the sphercal shape so that the centre of the mrror bulges
SPH3UW Unt 7.3 Sphercal Concave Mrrors Page 1 of 1 Notes Physcs Tool box Concave Mrror If the reflectng surface takes place on the nner surface of the sphercal shape so that the centre of the mrror bulges
Risk Assessment Using Functional Modeling based on Object Behavior and Interaction
 Rsk Assessment Usng Functonal Modelng based on Object Behavor and Interacton Akekacha Tangsuksant, Nakornth Promoon Software Engneerng Lab, Center of Ecellence n Software Engneerng Deartment of Comuter
Rsk Assessment Usng Functonal Modelng based on Object Behavor and Interacton Akekacha Tangsuksant, Nakornth Promoon Software Engneerng Lab, Center of Ecellence n Software Engneerng Deartment of Comuter
Optimized Query Planning of Continuous Aggregation Queries in Dynamic Data Dissemination Networks
 WWW 007 / Trac: Performance and Scalablty Sesson: Scalable Systems for Dynamc Content Otmzed Query Plannng of Contnuous Aggregaton Queres n Dynamc Data Dssemnaton Networs Rajeev Guta IBM Inda Research
WWW 007 / Trac: Performance and Scalablty Sesson: Scalable Systems for Dynamc Content Otmzed Query Plannng of Contnuous Aggregaton Queres n Dynamc Data Dssemnaton Networs Rajeev Guta IBM Inda Research
Synchronous Distributed Wireless Network Emulator for High-Speed Mobility: Implementation and Evaluation
 Synchronous Dstrbuted Wreless Network Emulator for Hgh-Speed Moblty: Implementaton and Evaluaton Mnoru Kozum, Tomoch Ebata Yokohama Research Laboratory, Htach, Ltd., 292 Yoshda-cho, Totsuka-ku, Yokohama,
Synchronous Dstrbuted Wreless Network Emulator for Hgh-Speed Moblty: Implementaton and Evaluaton Mnoru Kozum, Tomoch Ebata Yokohama Research Laboratory, Htach, Ltd., 292 Yoshda-cho, Totsuka-ku, Yokohama,
Constructing Minimum Connected Dominating Set: Algorithmic approach
 Constructng Mnmum Connected Domnatng Set: Algorthmc approach G.N. Puroht and Usha Sharma Centre for Mathematcal Scences, Banasthal Unversty, Rajasthan 304022 usha.sharma94@yahoo.com Abstract: Connected
Constructng Mnmum Connected Domnatng Set: Algorthmc approach G.N. Puroht and Usha Sharma Centre for Mathematcal Scences, Banasthal Unversty, Rajasthan 304022 usha.sharma94@yahoo.com Abstract: Connected
A RECONFIGURABLE ARCHITECTURE FOR MULTI-GIGABIT SPEED CONTENT-BASED ROUTING. James Moscola, Young H. Cho, John W. Lockwood
 A RECONFIGURABLE ARCHITECTURE FOR MULTI-GIGABIT SPEED CONTENT-BASED ROUTING James Moscola, Young H. Cho, John W. Lockwood Dept. of Computer Scence and Engneerng Washngton Unversty, St. Lous, MO {jmm5,
A RECONFIGURABLE ARCHITECTURE FOR MULTI-GIGABIT SPEED CONTENT-BASED ROUTING James Moscola, Young H. Cho, John W. Lockwood Dept. of Computer Scence and Engneerng Washngton Unversty, St. Lous, MO {jmm5,
kccvoip.com basic voip training NAT/PAT extract 2008
 kccvop.com basc vop tranng NAT/PAT extract 28 As we have seen n the prevous sldes, SIP and H2 both use addressng nsde ther packets to rely nformaton. Thnk of an envelope where we place the addresses of
kccvop.com basc vop tranng NAT/PAT extract 28 As we have seen n the prevous sldes, SIP and H2 both use addressng nsde ther packets to rely nformaton. Thnk of an envelope where we place the addresses of
Performance Comparison of a QoS Aware Routing Protocol for Wireless Sensor Networks
 Communcatons and Network, 2016, 8, 45-55 Publshed Onlne February 2016 n ScRes. http://www.scrp.org/journal/cn http://dx.do.org/10.4236/cn.2016.81006 Performance Comparson of a QoS Aware Routng Protocol
Communcatons and Network, 2016, 8, 45-55 Publshed Onlne February 2016 n ScRes. http://www.scrp.org/journal/cn http://dx.do.org/10.4236/cn.2016.81006 Performance Comparson of a QoS Aware Routng Protocol
Future Generation Computer Systems
 Future Generaton Computer Systems 29 (2013) 1631 1644 Contents lsts avalable at ScVerse ScenceDrect Future Generaton Computer Systems journal homepage: www.elsever.com/locate/fgcs Gosspng for resource
Future Generaton Computer Systems 29 (2013) 1631 1644 Contents lsts avalable at ScVerse ScenceDrect Future Generaton Computer Systems journal homepage: www.elsever.com/locate/fgcs Gosspng for resource
Using Particle Swarm Optimization for Enhancing the Hierarchical Cell Relay Routing Protocol
 2012 Thrd Internatonal Conference on Networkng and Computng Usng Partcle Swarm Optmzaton for Enhancng the Herarchcal Cell Relay Routng Protocol Hung-Y Ch Department of Electrcal Engneerng Natonal Sun Yat-Sen
2012 Thrd Internatonal Conference on Networkng and Computng Usng Partcle Swarm Optmzaton for Enhancng the Herarchcal Cell Relay Routng Protocol Hung-Y Ch Department of Electrcal Engneerng Natonal Sun Yat-Sen
UC Santa Cruz UC Santa Cruz Previously Published Works
 UC Santa Cruz UC Santa Cruz Previously Published Works Title CORD: Content Oriented Routing with Directories Permalink https://escholarship.org/uc/item/8g21p4hr Authors Garcia-Luna-Aceves, J.J. Li, Q.
UC Santa Cruz UC Santa Cruz Previously Published Works Title CORD: Content Oriented Routing with Directories Permalink https://escholarship.org/uc/item/8g21p4hr Authors Garcia-Luna-Aceves, J.J. Li, Q.
Pass by Reference vs. Pass by Value
 Pass by Reference vs. Pass by Value Most methods are passed arguments when they are called. An argument may be a constant or a varable. For example, n the expresson Math.sqrt(33) the constant 33 s passed
Pass by Reference vs. Pass by Value Most methods are passed arguments when they are called. An argument may be a constant or a varable. For example, n the expresson Math.sqrt(33) the constant 33 s passed
A Structure Preserving Database Encryption Scheme
 A Structure Preservng Database Encryton Scheme Yuval Elovc, Ronen Wasenberg, Erez Shmuel, and Ehud Gudes Ben-Guron Unversty of the Negev, Faculty of Engneerng, Deartment of Informaton Systems Engneerng,
A Structure Preservng Database Encryton Scheme Yuval Elovc, Ronen Wasenberg, Erez Shmuel, and Ehud Gudes Ben-Guron Unversty of the Negev, Faculty of Engneerng, Deartment of Informaton Systems Engneerng,
Priority-Based Scheduling Algorithm for Downlink Traffics in IEEE Networks
 Prorty-Based Schedulng Algorthm for Downlnk Traffcs n IEEE 80.6 Networks Ja-Mng Lang, Jen-Jee Chen, You-Chun Wang, Yu-Chee Tseng, and Bao-Shuh P. Ln Department of Computer Scence Natonal Chao-Tung Unversty,
Prorty-Based Schedulng Algorthm for Downlnk Traffcs n IEEE 80.6 Networks Ja-Mng Lang, Jen-Jee Chen, You-Chun Wang, Yu-Chee Tseng, and Bao-Shuh P. Ln Department of Computer Scence Natonal Chao-Tung Unversty,
such that is accepted of states in , where Finite Automata Lecture 2-1: Regular Languages be an FA. A string is the transition function,
 * Lecture - Regular Languages S Lecture - Fnte Automata where A fnte automaton s a -tuple s a fnte set called the states s a fnte set called the alphabet s the transton functon s the ntal state s the set
* Lecture - Regular Languages S Lecture - Fnte Automata where A fnte automaton s a -tuple s a fnte set called the states s a fnte set called the alphabet s the transton functon s the ntal state s the set
Maintaining temporal validity of real-time data on non-continuously executing resources
 Mantanng temporal valdty of real-tme data on non-contnuously executng resources Tan Ba, Hong Lu and Juan Yang Hunan Insttute of Scence and Technology, College of Computer Scence, 44, Yueyang, Chna Wuhan
Mantanng temporal valdty of real-tme data on non-contnuously executng resources Tan Ba, Hong Lu and Juan Yang Hunan Insttute of Scence and Technology, College of Computer Scence, 44, Yueyang, Chna Wuhan
IMRT workflow. Optimization and Inverse planning. Intensity distribution IMRT IMRT. Dose optimization for IMRT. Bram van Asselen
 IMRT workflow Otmzaton and Inverse lannng 69 Gy Bram van Asselen IMRT Intensty dstrbuton Webb 003: IMRT s the delvery of radaton to the atent va felds that have non-unform radaton fluence Purose: Fnd a
IMRT workflow Otmzaton and Inverse lannng 69 Gy Bram van Asselen IMRT Intensty dstrbuton Webb 003: IMRT s the delvery of radaton to the atent va felds that have non-unform radaton fluence Purose: Fnd a
UNIT 2 : INEQUALITIES AND CONVEX SETS
 UNT 2 : NEQUALTES AND CONVEX SETS ' Structure 2. ntroducton Objectves, nequaltes and ther Graphs Convex Sets and ther Geometry Noton of Convex Sets Extreme Ponts of Convex Set Hyper Planes and Half Spaces
UNT 2 : NEQUALTES AND CONVEX SETS ' Structure 2. ntroducton Objectves, nequaltes and ther Graphs Convex Sets and ther Geometry Noton of Convex Sets Extreme Ponts of Convex Set Hyper Planes and Half Spaces
Lecture Note 08 EECS 4101/5101 Instructor: Andy Mirzaian. All Nearest Neighbors: The Lifting Method
 Lecture Note 08 EECS 4101/5101 Instructor: Andy Mrzaan Introducton All Nearest Neghbors: The Lftng Method Suose we are gven aset P ={ 1, 2,..., n }of n onts n the lane. The gven coordnates of the -th ont
Lecture Note 08 EECS 4101/5101 Instructor: Andy Mrzaan Introducton All Nearest Neghbors: The Lftng Method Suose we are gven aset P ={ 1, 2,..., n }of n onts n the lane. The gven coordnates of the -th ont
Efficient Distributed File System (EDFS)
 Effcent Dstrbuted Fle System (EDFS) (Sem-Centralzed) Debessay(Debsh) Fesehaye, Rahul Malk & Klara Naherstedt Unversty of Illnos-Urbana Champagn Contents Problem Statement, Related Work, EDFS Desgn Rate
Effcent Dstrbuted Fle System (EDFS) (Sem-Centralzed) Debessay(Debsh) Fesehaye, Rahul Malk & Klara Naherstedt Unversty of Illnos-Urbana Champagn Contents Problem Statement, Related Work, EDFS Desgn Rate
Long Lifetime Routing in Unreliable Wireless Sensor Networks
 211 Internatonal Conference on Networkng, Sensng and Control Delft, the Netherlands, 11-13 Aprl 211 Long Lfetme Routng n Unrelable Wreless Sensor Networks Hamed Yousef, Mohammad Hossen Yeganeh, Al Movaghar
211 Internatonal Conference on Networkng, Sensng and Control Delft, the Netherlands, 11-13 Aprl 211 Long Lfetme Routng n Unrelable Wreless Sensor Networks Hamed Yousef, Mohammad Hossen Yeganeh, Al Movaghar
Connection-information-based connection rerouting for connection-oriented mobile communication networks
 Dstrb. Syst. Engng 5 (1998) 47 65. Prnted n the UK PII: S0967-1846(98)90513-7 Connecton-nformaton-based connecton reroutng for connecton-orented moble communcaton networks Mnho Song, Yanghee Cho and Chongsang
Dstrb. Syst. Engng 5 (1998) 47 65. Prnted n the UK PII: S0967-1846(98)90513-7 Connecton-nformaton-based connecton reroutng for connecton-orented moble communcaton networks Mnho Song, Yanghee Cho and Chongsang
Implement Public Audit ability and Data Dynamics with Security in Cloud Computing
 Internatonal Journal of Modern Engneerng Research (IJMER) www.jmer.com Vol. 3, Issue. 6, Nov - Dec. 203-3786-379 ISSN: 2249-6645 Imlement Publc Audt ablty and Data Dynamcs wth Securty n Cloud Comutng P.
Internatonal Journal of Modern Engneerng Research (IJMER) www.jmer.com Vol. 3, Issue. 6, Nov - Dec. 203-3786-379 ISSN: 2249-6645 Imlement Publc Audt ablty and Data Dynamcs wth Securty n Cloud Comutng P.
MobileGrid: Capacity-aware Topology Control in Mobile Ad Hoc Networks
 MobleGrd: Capacty-aware Topology Control n Moble Ad Hoc Networks Jle Lu, Baochun L Department of Electrcal and Computer Engneerng Unversty of Toronto {jenne,bl}@eecg.toronto.edu Abstract Snce wreless moble
MobleGrd: Capacty-aware Topology Control n Moble Ad Hoc Networks Jle Lu, Baochun L Department of Electrcal and Computer Engneerng Unversty of Toronto {jenne,bl}@eecg.toronto.edu Abstract Snce wreless moble
Avoiding congestion through dynamic load control
 Avodng congeston through dynamc load control Vasl Hnatyshn, Adarshpal S. Seth Department of Computer and Informaton Scences, Unversty of Delaware, Newark, DE 976 ABSTRACT The current best effort approach
Avodng congeston through dynamc load control Vasl Hnatyshn, Adarshpal S. Seth Department of Computer and Informaton Scences, Unversty of Delaware, Newark, DE 976 ABSTRACT The current best effort approach
Compiler Design. Spring Register Allocation. Sample Exercises and Solutions. Prof. Pedro C. Diniz
 Compler Desgn Sprng 2014 Regster Allocaton Sample Exercses and Solutons Prof. Pedro C. Dnz USC / Informaton Scences Insttute 4676 Admralty Way, Sute 1001 Marna del Rey, Calforna 90292 pedro@s.edu Regster
Compler Desgn Sprng 2014 Regster Allocaton Sample Exercses and Solutons Prof. Pedro C. Dnz USC / Informaton Scences Insttute 4676 Admralty Way, Sute 1001 Marna del Rey, Calforna 90292 pedro@s.edu Regster
On Selfishness, Local Information, and Network Optimality: A Topology Control Example
 On Selfshness, Local Informaton, and Network Optmalty: A Topology Control Example Ramakant S. Komal, Allen B. MacKenze, and Petr Mähönen Department of Wreless Networks, RWTH Aachen Unversty, 52072 Aachen
On Selfshness, Local Informaton, and Network Optmalty: A Topology Control Example Ramakant S. Komal, Allen B. MacKenze, and Petr Mähönen Department of Wreless Networks, RWTH Aachen Unversty, 52072 Aachen
Gentle Early Detection Algorithm
 Gentle Early etecton Algorthm Hussen Abdel-jaber 1, Mahmoud Abdeljaber 2, Hussen Abu Mansour 1, Malak El-Amr 1 1 Faculty of Comuter Studes, eartment of Informaton Technology and Comutng, Arab Oen Unversty,
Gentle Early etecton Algorthm Hussen Abdel-jaber 1, Mahmoud Abdeljaber 2, Hussen Abu Mansour 1, Malak El-Amr 1 1 Faculty of Comuter Studes, eartment of Informaton Technology and Comutng, Arab Oen Unversty,
Traffic Classification Method Based On Data Stream Fingerprint
 5th nternatonal Conference on Advanced Materals and Comuter Scence (CAMCS 6) Traffc Classfcaton Method Based On Data Stream Fngerrnt Kefe Cheng, a, Guohu We,b and Xangjun Ma3,c College of Comuter Scence
5th nternatonal Conference on Advanced Materals and Comuter Scence (CAMCS 6) Traffc Classfcaton Method Based On Data Stream Fngerrnt Kefe Cheng, a, Guohu We,b and Xangjun Ma3,c College of Comuter Scence
A new Algorithm for Lossless Compression applied to two-dimensional Static Images
 A new Algorthm for Lossless Comresson aled to two-dmensonal Statc Images JUAN IGNACIO LARRAURI Deartment of Technology Industral Unversty of Deusto Avda. Unversdades, 4. 48007 Blbao SPAIN larrau@deusto.es
A new Algorthm for Lossless Comresson aled to two-dmensonal Statc Images JUAN IGNACIO LARRAURI Deartment of Technology Industral Unversty of Deusto Avda. Unversdades, 4. 48007 Blbao SPAIN larrau@deusto.es
MASTER'S THESIS. Scalable Route Caching Methods for Networks with Many Mobile Nodes. by Theodoros Salonidis Advisor: Leandros Tassiulas
 MASTER'S THESIS Scalable Route Cachng Methods for Networks wth Many Moble Nodes by Theodoros Salonds Advsor: Leandros Tassulas CSHCN M.S. 99-8 (ISR M.S. 99-3) ABSTRACT Ttle of Thess: SCALABLE ROUTE CACHING
MASTER'S THESIS Scalable Route Cachng Methods for Networks wth Many Moble Nodes by Theodoros Salonds Advsor: Leandros Tassulas CSHCN M.S. 99-8 (ISR M.S. 99-3) ABSTRACT Ttle of Thess: SCALABLE ROUTE CACHING
Evaluation of Parallel Processing Systems through Queuing Model
 ISSN 2278-309 Vkas Shnde, Internatonal Journal of Advanced Volume Trends 4, n Computer No.2, March Scence - and Aprl Engneerng, 205 4(2), March - Aprl 205, 36-43 Internatonal Journal of Advanced Trends
ISSN 2278-309 Vkas Shnde, Internatonal Journal of Advanced Volume Trends 4, n Computer No.2, March Scence - and Aprl Engneerng, 205 4(2), March - Aprl 205, 36-43 Internatonal Journal of Advanced Trends
A Low-Overhead Routing Protocol for Ad Hoc Networks with selfish nodes
 A Low-Oerhead Routng Protocol for Ad Hoc Networks wth selfsh nodes Dongbn Wang 1, Xaofeng Wang 2, Xangzhan Yu 3, Kacheng Q 1, Zhbn Xa 1 1 School of Software Engneerng, Bejng Unersty of Posts and Telecommuncatons,100876,
A Low-Oerhead Routng Protocol for Ad Hoc Networks wth selfsh nodes Dongbn Wang 1, Xaofeng Wang 2, Xangzhan Yu 3, Kacheng Q 1, Zhbn Xa 1 1 School of Software Engneerng, Bejng Unersty of Posts and Telecommuncatons,100876,
Storage Data Security of Data in Cloud Computing
 IOSR Journal of Comuter Engneerng (IOSR-JCE) e-issn: 2278-066,-ISSN: 2278-8727, Volume 6, Issue 4, Ver. VI (Jul Aug. 204), PP 7-77 www.osrjournals.org Storage Data Securty of Data n Cloud Comutng Srnvasulu.B,
IOSR Journal of Comuter Engneerng (IOSR-JCE) e-issn: 2278-066,-ISSN: 2278-8727, Volume 6, Issue 4, Ver. VI (Jul Aug. 204), PP 7-77 www.osrjournals.org Storage Data Securty of Data n Cloud Comutng Srnvasulu.B,
A mathematical programming approach to the analysis, design and scheduling of offshore oilfields
 17 th European Symposum on Computer Aded Process Engneerng ESCAPE17 V. Plesu and P.S. Agach (Edtors) 2007 Elsever B.V. All rghts reserved. 1 A mathematcal programmng approach to the analyss, desgn and
17 th European Symposum on Computer Aded Process Engneerng ESCAPE17 V. Plesu and P.S. Agach (Edtors) 2007 Elsever B.V. All rghts reserved. 1 A mathematcal programmng approach to the analyss, desgn and
Distributed Grid based Robust Clustering Protocol for Mobile Sensor Networks
 414 The Internatonal Arab Journal of Informaton Technology, Vol. 8, No. 4, October 011 Dstrbuted Grd based Robust Clusterng Protocol for Moble Sensor Networks Shahzad Al and Sajjad Madan Department of
414 The Internatonal Arab Journal of Informaton Technology, Vol. 8, No. 4, October 011 Dstrbuted Grd based Robust Clusterng Protocol for Moble Sensor Networks Shahzad Al and Sajjad Madan Department of
Extending Network Life by Using Mobile Actors in Cluster-based Wireless Sensor and Actor Networks
 Extendng Networ Lfe by Usng Moble Actors n Cluster-based Wreless Sensor and Actor Networs Nauman Aslam, Wllam Phllps, Wllam Robertson and S. Svaumar Department of Engneerng Mathematcs & Internetworng Dalhouse
Extendng Networ Lfe by Usng Moble Actors n Cluster-based Wreless Sensor and Actor Networs Nauman Aslam, Wllam Phllps, Wllam Robertson and S. Svaumar Department of Engneerng Mathematcs & Internetworng Dalhouse
AMath 483/583 Lecture 21 May 13, Notes: Notes: Jacobi iteration. Notes: Jacobi with OpenMP coarse grain
 AMath 483/583 Lecture 21 May 13, 2011 Today: OpenMP and MPI versons of Jacob teraton Gauss-Sedel and SOR teratve methods Next week: More MPI Debuggng and totalvew GPU computng Read: Class notes and references
AMath 483/583 Lecture 21 May 13, 2011 Today: OpenMP and MPI versons of Jacob teraton Gauss-Sedel and SOR teratve methods Next week: More MPI Debuggng and totalvew GPU computng Read: Class notes and references
Bayesian Model for Mobility Prediction to Support Routing in Mobile Ad-Hoc Networks
 Bayesan Model for Moblty Predcton to Support Routng n Moble Ad-Hoc Networks Tran The Son, Hoa Le Mnh, Graham Sexton, Nauman Aslam, Zabh Ghassemlooy Northumbra Communcatons Research Laboratory (NCRLab Faculty
Bayesan Model for Moblty Predcton to Support Routng n Moble Ad-Hoc Networks Tran The Son, Hoa Le Mnh, Graham Sexton, Nauman Aslam, Zabh Ghassemlooy Northumbra Communcatons Research Laboratory (NCRLab Faculty
Outline. Self-Organizing Maps (SOM) US Hebbian Learning, Cntd. The learning rule is Hebbian like:
 Self-Organzng Maps (SOM) Turgay İBRİKÇİ, PhD. Outlne Introducton Structures of SOM SOM Archtecture Neghborhoods SOM Algorthm Examples Summary 1 2 Unsupervsed Hebban Learnng US Hebban Learnng, Cntd 3 A
Self-Organzng Maps (SOM) Turgay İBRİKÇİ, PhD. Outlne Introducton Structures of SOM SOM Archtecture Neghborhoods SOM Algorthm Examples Summary 1 2 Unsupervsed Hebban Learnng US Hebban Learnng, Cntd 3 A
A Topology-aware Random Walk
 A Topology-aware Random Walk Inkwan Yu, Rchard Newman Dept. of CISE, Unversty of Florda, Ganesvlle, Florda, USA Abstract When a graph can be decomposed nto clusters of well connected subgraphs, t s possble
A Topology-aware Random Walk Inkwan Yu, Rchard Newman Dept. of CISE, Unversty of Florda, Ganesvlle, Florda, USA Abstract When a graph can be decomposed nto clusters of well connected subgraphs, t s possble
