Security. Internet and Network Attacks. Computer Security Risks 1/23/2019
|
|
|
- Charleen Wilkins
- 5 years ago
- Views:
Transcription
1 Security Security refers to the steps a computer owner takes to prevent unauthorized use of or damage to the computer Malware Viruses Spyware Adware Firewall Phishing Pharming Antivirus software Internet and Network Attacks Users can take several precautions to protect their home and work computers and mobile devices from these malicious infections Pages Figure 10-4 Discovering Computers & Microsoft Office 2010: Discovering Computers Chapter 5 20 Computer Security Risks Pages Figure 10-1 Discovering Computers & Microsoft Office 2010: Discovering Computers Chapter
2 University of Memphis Network Network Login If you Bring your own device on campus, you will need to log into the network the network: Network Login On Windows and Mac machines you will need to follow instructions to install Safe Connect 2
3 iprint To facilitate students wishing to print from their own computers, ITD has given access to print via iprint to many of the printers in labs and other locations around campus. Instructions LiveSafe An emergency alert system on campus Informs you, via push message, of: University closings and delays Emergencies on campus Features Download Instructions Android Device ios UMWare UM Ware allows students to use SELECTED software from off campus 3
4 UMWare New in 2018 UMWare will also let you get the same desktop you get in ET216 if you click on the DESKTOPS Icon at the top of the screen and then select Virtual Lab Engineering Students have access to create WordPress Blogs on their University Account Blogs Your blog (if active) would be at Using MyMemphis 30 4
5 Go to mymemphis 31 Type name and password 32 A good place to start is UofMOnline 33 5
6 UMdrive (file space accessible from anywhere with internet access) 34 For UMdrive Help umservices/umdrive.php You can give access to files placed on UMDrive to individuals and groups Many faculty use UMDrive to give students access to files 35 Library Search 36 6
7 Identity Management 37 Free Microsoft Access Students have access to Microsoft Office 356 through your account Log into and click on upper left corner icon You also have a free OneDrive account /docs/onedrive.pdf 7
8 Free Software Microsoft Imagine Download Win8.1 and 10, Server, Project, Access, Visual Studio Enterprise, Visio and more. LINK (NOTE: this is impossible to find off of University website)! Free Software Autodesk, makers of Autocad and Inventor, allows free downloads of their products to students. LINK Campus 42 8
9 Etiquette Always include a subject line and include your name if you think the person might not know who you are from your account name. Remember, without facial expressions and body language, written comments may be taken the wrong way. Be careful in wording your s. Use standard fonts. Don t use all capital letters when typing; all caps is understood to be the equivalent of shouting. Do not send large attachments without permission. Special formatting such as centering, audio messages, tables, html, etc. should be avoided unless necessary to complete an assignment or other communication. Avoid using text messaging choppiness and use capital letters to start sentences. Other Notes Do not open attachments (especially from people you do not know) VIRUSES! Use appropriate account names (sending a resume via an account ilovegames@aol.com is a bad idea) When attaching a file, make sure the person you are sending has the program to open it (when in doubt PDF!) One Last Note Once you put something on the internet (via facebook, , etc) it is there forever do you really want an employer to see that picture of you at that party? 9
10 Bibliography New Perspectives on Microsoft Office 2007, First Course, Windows XP Edition Class Notes for CGS1100, Prof. Robert W Janson, Florida Community College University of Memphis - MyMemphis webpages 10
Networks and the Internet
 UofM Internet Concepts TECH 1010 Dan Kohn University of Memphis Engineering Technology Department Networks and the Internet A network is a collection of computers and devices connected together, often
UofM Internet Concepts TECH 1010 Dan Kohn University of Memphis Engineering Technology Department Networks and the Internet A network is a collection of computers and devices connected together, often
Networks and the Internet
 UofM Internet Concepts TECH 1010 Dan Kohn University of Memphis Engineering Technology Department 2018 v2.1 ed. Networks and the Internet A network is a collection of computers and devices connected together,
UofM Internet Concepts TECH 1010 Dan Kohn University of Memphis Engineering Technology Department 2018 v2.1 ed. Networks and the Internet A network is a collection of computers and devices connected together,
2 User Guide. Contents
 E-mail User Guide 2 E-mail User Guide Contents Logging in to your web mail... 3 Changing your password... 5 Editing your signature... 6 Adding an e-mail account to Outlook 2010/2013/2016... 7 Adding an
E-mail User Guide 2 E-mail User Guide Contents Logging in to your web mail... 3 Changing your password... 5 Editing your signature... 6 Adding an e-mail account to Outlook 2010/2013/2016... 7 Adding an
University of Tennessee at Chattanooga ARCS, Michael Ward, Basic Windows Security
 University of Tennessee at Chattanooga ARCS, Michael Ward, 2005-7-27 Basic Windows Security Nothing, besides turning off the power, can insure that your PC will be completely protected from hazards such
University of Tennessee at Chattanooga ARCS, Michael Ward, 2005-7-27 Basic Windows Security Nothing, besides turning off the power, can insure that your PC will be completely protected from hazards such
Chapter 10: Security. 2. What are the two types of general threats to computer security? Give examples of each.
 Name Date Chapter 10: Security After completion of this chapter, students should be able to: Explain why security is important and describe security threats. Explain social engineering, data wiping, hard
Name Date Chapter 10: Security After completion of this chapter, students should be able to: Explain why security is important and describe security threats. Explain social engineering, data wiping, hard
um Wireless Revised 8/17/18
 um Wireless Center for Teaching and Learning (CTL) 100 Administration Bldg., Memphis, TN 38152 Phone: 901.678.8888 Email: itstrainers@memphis.edu Center for Teaching and Learning Website Revised 8/17/18
um Wireless Center for Teaching and Learning (CTL) 100 Administration Bldg., Memphis, TN 38152 Phone: 901.678.8888 Email: itstrainers@memphis.edu Center for Teaching and Learning Website Revised 8/17/18
1/29/2019. Storage Media. Storage Media
 File Management TECH 1010 Dan Kohn University of Memphis Engineering Technology Department Last update 1/29/18 (WIN10) Storage Media A computer file is a named collection of stored data An executable file
File Management TECH 1010 Dan Kohn University of Memphis Engineering Technology Department Last update 1/29/18 (WIN10) Storage Media A computer file is a named collection of stored data An executable file
9/2/2016. Storage Media. Storage Media
 File Management TECH 1010 Dan Kohn University of Memphis Engineering Technology Department Last update 1/24/14 Storage Media A computer file is a named collection of stored data An executable file contains
File Management TECH 1010 Dan Kohn University of Memphis Engineering Technology Department Last update 1/24/14 Storage Media A computer file is a named collection of stored data An executable file contains
UofM Secure Wireless 2/14/2018. Brought to you by: umtech & The Center for Teaching & Learning
 UofM Secure Wireless Center for Teaching and Learning (CTL) 100 Administration Bldg., Memphis, TN 38152 Phone: 901.678.8888 Email: itstrainers@memphis.edu Center for Teaching and Learning Website 2/14/2018
UofM Secure Wireless Center for Teaching and Learning (CTL) 100 Administration Bldg., Memphis, TN 38152 Phone: 901.678.8888 Email: itstrainers@memphis.edu Center for Teaching and Learning Website 2/14/2018
Get Max Internet Security where to buy software for students ]
![Get Max Internet Security where to buy software for students ] Get Max Internet Security where to buy software for students ]](/thumbs/87/95239861.jpg) Get Max Internet Security where to buy software for students ] Description: Features of Max Secure Internet Security 2013 Exciting, Easy to understand GUI Easy, Quick installation Get immediate protection
Get Max Internet Security where to buy software for students ] Description: Features of Max Secure Internet Security 2013 Exciting, Easy to understand GUI Easy, Quick installation Get immediate protection
User Guide. This user guide explains how to use and update Max Secure Anti Virus Enterprise Client.
 User Guide This user guide explains how to use and update Max Secure Anti Virus Enterprise Client. Copyright 2002-2016 Max Secure Software. All rights reserved. Contents 2 Contents Introduction... 3 System
User Guide This user guide explains how to use and update Max Secure Anti Virus Enterprise Client. Copyright 2002-2016 Max Secure Software. All rights reserved. Contents 2 Contents Introduction... 3 System
What is VMware View. IMPORTANT: Connecting from Off-Campus. Connecting to View Desktops. Downloading the Client
 1. What is VMware View 2. Connecting from Off-Campus 3. Connecting to View Desktops 4. Extra View Tips 5. What to do if something is wrong What is VMware View VMware View is a technology that allows us
1. What is VMware View 2. Connecting from Off-Campus 3. Connecting to View Desktops 4. Extra View Tips 5. What to do if something is wrong What is VMware View VMware View is a technology that allows us
Airtel PC Secure Trouble Shooting Guide
 Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Airtel PC Secure Trouble Shooting Guide Table of Contents Questions before installing the software Q: What is required from my PC to be able to use the Airtel PC Secure? Q: Which operating systems does
Get BitDefender Security for File Servers 2 Years 5 PCs computer new software download ]
![Get BitDefender Security for File Servers 2 Years 5 PCs computer new software download ] Get BitDefender Security for File Servers 2 Years 5 PCs computer new software download ]](/thumbs/90/103076930.jpg) Get BitDefender Security for File Servers 2 Years 5 PCs computer new software download ] Description: FILE SERVERS - THE BACKBONE OF THE NETWORK File servers are not just a network repository for the company
Get BitDefender Security for File Servers 2 Years 5 PCs computer new software download ] Description: FILE SERVERS - THE BACKBONE OF THE NETWORK File servers are not just a network repository for the company
Multi-factor Authentication Instructions
 What is MFA? Multi-factor Authentication (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account.
What is MFA? Multi-factor Authentication (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account.
How to Create a Basic Webpage in WordPress
 By Debra McClure Intended Audience: WordPress is a free content management system (CMS) that is used to create blogs and websites. These instructions are for people who already have WordPress installed
By Debra McClure Intended Audience: WordPress is a free content management system (CMS) that is used to create blogs and websites. These instructions are for people who already have WordPress installed
Quick Start Guide. Kaspersky Total Security THE POWER OF PROTECTION. The license period starts when you activate the product on the first device.
 THE POWER OF PROTECTION 2014 Kaspersky Total Security Quick Start Guide The license period starts when you activate the product on the first device. The number of devices that can be protected varies according
THE POWER OF PROTECTION 2014 Kaspersky Total Security Quick Start Guide The license period starts when you activate the product on the first device. The number of devices that can be protected varies according
Encrypting Removable Media
 For security reasons all removable media must be encrypted with BitLocker to Go on Windows 7 workstations. The following will show you how to use a flash drive with BitLocker to Go. Please note that data
For security reasons all removable media must be encrypted with BitLocker to Go on Windows 7 workstations. The following will show you how to use a flash drive with BitLocker to Go. Please note that data
Free antivirus software download
 Cari untuk: Cari Cari Free antivirus software download 3-11-2015 Avast has one of the most popular antivirus apps around, due in part to offering a free version, and it's one that performs respectably.
Cari untuk: Cari Cari Free antivirus software download 3-11-2015 Avast has one of the most popular antivirus apps around, due in part to offering a free version, and it's one that performs respectably.
OFFICE 365 FOR STUDENTS O VERVIEW OF OFFICE 36 5 FOR STUDENTS. Passero, Denise Author. Overview
 O VERVIEW OF OFFICE 36 5 FOR STUDENTS Use this overview to get acquainted with Office 365 for students. Passero, Denise Author OFFICE 365 FOR STUDENTS Overview Overview of Office 365 for Students Downloading
O VERVIEW OF OFFICE 36 5 FOR STUDENTS Use this overview to get acquainted with Office 365 for students. Passero, Denise Author OFFICE 365 FOR STUDENTS Overview Overview of Office 365 for Students Downloading
Staying Safe Online. My Best Internet Safety Tips. and the AgeWell Computer Education Center.
 Staying Safe Online My Best Internet Safety Tips and the AgeWell Computer Education Center Welcome to our first Webinar of 2017! Agenda o How to use the Webinar Room o Upcoming CEC Classes o My tips for
Staying Safe Online My Best Internet Safety Tips and the AgeWell Computer Education Center Welcome to our first Webinar of 2017! Agenda o How to use the Webinar Room o Upcoming CEC Classes o My tips for
College of Pharmacy Windows 10
 College of Pharmacy Windows 10 Windows 10 is the version of Microsoft s flagship operating system that follows Windows 8; the OS was released in July 2015. Windows 10 is designed to address common criticisms
College of Pharmacy Windows 10 Windows 10 is the version of Microsoft s flagship operating system that follows Windows 8; the OS was released in July 2015. Windows 10 is designed to address common criticisms
ANTIVIRUS SITE PROTECTION (by SiteGuarding.com)
 ANTIVIRUS SITE PROTECTION (by SiteGuarding.com) USER GUIDE Version 0.1.0 1 Table of content 1. INTRODUCTION. 3 2. HOW IT WORKS.... 6 3. HOW TO CONFIGURE.. 7 2 1. INTRODUCTION Antivirus Site Protection
ANTIVIRUS SITE PROTECTION (by SiteGuarding.com) USER GUIDE Version 0.1.0 1 Table of content 1. INTRODUCTION. 3 2. HOW IT WORKS.... 6 3. HOW TO CONFIGURE.. 7 2 1. INTRODUCTION Antivirus Site Protection
How To Remove Virus From Computer Without Using Antivirus In Windows Xp
 How To Remove Virus From Computer Without Using Antivirus In Windows Xp How to remove a virus - how to clean PC and laptop of virus, spyware and other PC internet security software that includes up to
How To Remove Virus From Computer Without Using Antivirus In Windows Xp How to remove a virus - how to clean PC and laptop of virus, spyware and other PC internet security software that includes up to
FIT 100 LAB Activity 3: Constructing HTML Documents
 FIT 100 LAB Activity 3: Constructing HTML Documents Winter 2002.pdf version of this lab (may be better formatted) Required Reading for Lab 3 Chapter 4 of the FIT course pack Additional helpful references
FIT 100 LAB Activity 3: Constructing HTML Documents Winter 2002.pdf version of this lab (may be better formatted) Required Reading for Lab 3 Chapter 4 of the FIT course pack Additional helpful references
Quick Start Guide. Kaspersky Internet Security THE POWER OF PROTECTION. The license period starts when you activate the product on the first device.
 THE POWER OF PROTECTION 2014 Kaspersky Internet Security Quick Start Guide The license period starts when you activate the product on the first device. The number of devices that can be protected varies
THE POWER OF PROTECTION 2014 Kaspersky Internet Security Quick Start Guide The license period starts when you activate the product on the first device. The number of devices that can be protected varies
. Account & Google Message Center Guide. January Prepared by: Angela Mars IT Education and Training
 Email Account & Google Message Center Guide January 2019 Prepared by: Angela Mars IT Education and Training Table Of Contents Email Account Information Page 4 Safe Email Practices Page 5 Recommended Email
Email Account & Google Message Center Guide January 2019 Prepared by: Angela Mars IT Education and Training Table Of Contents Email Account Information Page 4 Safe Email Practices Page 5 Recommended Email
JCCC Virtual Labs. Click the link for more information on installing on that device type. Windows PC/laptop Apple imac or MacBook ipad Android Linux
 JCCC Virtual Labs Revision 9/21/2017 http://ats.web. Welcome to the JCCC Virtual Lab Environment. This system allows students to access campus software titles on their personal computers from almost anywhere.
JCCC Virtual Labs Revision 9/21/2017 http://ats.web. Welcome to the JCCC Virtual Lab Environment. This system allows students to access campus software titles on their personal computers from almost anywhere.
Text Only Version of Lessons
 Text Only Version of Lessons Introduction to Lessons Did you realize that creating web page is not much harder than creating word documents? Contrary to what you may believe, you do not need to know HTML,
Text Only Version of Lessons Introduction to Lessons Did you realize that creating web page is not much harder than creating word documents? Contrary to what you may believe, you do not need to know HTML,
ELLUCIAN GO HOW-TO GUIDE
 ELLUCIAN GO HOW-TO GUIDE 03.31.17 CONTENTS GET THE ELLUCIAN GO APP... CHOOSE ACM AS YOUR SCHOOL... SIGN IN... ELLUCIAN GO MENU... REGISTER FOR COURSES... MY SCHEDULE... MY GRADES... MY FINANCIALS... ACADEMICS
ELLUCIAN GO HOW-TO GUIDE 03.31.17 CONTENTS GET THE ELLUCIAN GO APP... CHOOSE ACM AS YOUR SCHOOL... SIGN IN... ELLUCIAN GO MENU... REGISTER FOR COURSES... MY SCHEDULE... MY GRADES... MY FINANCIALS... ACADEMICS
Data Warehouse: User Computer Configuration Guide
 University of Texas at San Antonio Data Warehouse: User Computer Configuration Guide Sponsored by the Vice Provost of Institutional Effectiveness DOCUMENT HISTORY This is an on-line document. Paper copies
University of Texas at San Antonio Data Warehouse: User Computer Configuration Guide Sponsored by the Vice Provost of Institutional Effectiveness DOCUMENT HISTORY This is an on-line document. Paper copies
1. A broadband connection. 2. Windows Vista (for these instructions; other operating systems have other instructions).
 A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
A VPN (Virtual Private Network) provides a secure, encrypted tunnel from your computer to UHCL's network when off campus. UHCL offers VPN software to allow authenticated, secure access to many UHCL resources
This guide will walk you through the steps to browse, access, and favorite VDIs and Applications through Citrix.
 April 3, 2018 Citrix Overview OVERVIEW This guide will walk you through the steps to browse, access, and favorite VDIs and Applications through Citrix. Note: ICIT technology training courses are only offered
April 3, 2018 Citrix Overview OVERVIEW This guide will walk you through the steps to browse, access, and favorite VDIs and Applications through Citrix. Note: ICIT technology training courses are only offered
Introduction to the Portal
 Introduction to the Portal Intro to the Portal Page 1 of 23 Table of Contents General Information... 4 Chapter 1: What is the Spectrum Portal... 5 Chapter 2: Tabs, Channels, and Columns... Introduction
Introduction to the Portal Intro to the Portal Page 1 of 23 Table of Contents General Information... 4 Chapter 1: What is the Spectrum Portal... 5 Chapter 2: Tabs, Channels, and Columns... Introduction
How To Remove Live Security Platinum Virus Using Mcafee
 How To Remove Live Security Platinum Virus Using Mcafee This article helps you determine what to do if you discover or suspect a virus For current information about viruses and threats, always use the
How To Remove Live Security Platinum Virus Using Mcafee This article helps you determine what to do if you discover or suspect a virus For current information about viruses and threats, always use the
Student Tech Guide. Get Help from the Information and Technology Solutions Center! link.mnsu.edu/studenttech. Big ideas. Real-world thinking.
 Student Tech Guide Get Help from the Information and Technology Solutions Center! Find this Student Tech Guide online at link.mnsu.edu/studenttech Big ideas. Real-world thinking. Get Started Your StarID
Student Tech Guide Get Help from the Information and Technology Solutions Center! Find this Student Tech Guide online at link.mnsu.edu/studenttech Big ideas. Real-world thinking. Get Started Your StarID
SUMMARIES OF INTERACTIVE MULTIMEDIA
 SUMMARIES OF INTERACTIVE MULTIMEDIA GRADE 10-12 INTERNET TECHNOLOGIES 1. Introduction to Electronic Communications Use this lesson to: Understand the differences between the various e-communications modes
SUMMARIES OF INTERACTIVE MULTIMEDIA GRADE 10-12 INTERNET TECHNOLOGIES 1. Introduction to Electronic Communications Use this lesson to: Understand the differences between the various e-communications modes
Microsoft Yammer Users Guide
 2017 Microsoft Yammer Users Guide This guide will assist you with using Microsoft Yammer. INFORMATION TECHNOLOGY SERVICES ITS TRAINING Table of Contents What is Yammer?... 2 Access... 2 Navigating Yammer...
2017 Microsoft Yammer Users Guide This guide will assist you with using Microsoft Yammer. INFORMATION TECHNOLOGY SERVICES ITS TRAINING Table of Contents What is Yammer?... 2 Access... 2 Navigating Yammer...
Manual Removal Norton Internet Security Won't Open Or
 Manual Removal Norton Internet Security Won't Open Or Dec 3, 2014. Finally during the reinstall - I had to delete a key to get a new key other wise I would I have it shown on the prgrams and features -
Manual Removal Norton Internet Security Won't Open Or Dec 3, 2014. Finally during the reinstall - I had to delete a key to get a new key other wise I would I have it shown on the prgrams and features -
Student Evaluation of Teaching (SET)
 Testing, Evaluation and Research Services Student Evaluation of Teaching (SET) A guide to retrieving your faculty longitudinal report online. FOR ADDITIONAL INFORMATION, PLEASE CONTACT THE SET HELPDESK
Testing, Evaluation and Research Services Student Evaluation of Teaching (SET) A guide to retrieving your faculty longitudinal report online. FOR ADDITIONAL INFORMATION, PLEASE CONTACT THE SET HELPDESK
Upgrading Your Home Network Security
 Upgrading Your Home Network Security For Free! Dr. Glen Sagers Illinois State University Outline Passwords & Passphrases Two-factor authentication Updates Viruses and Malware WiFi security Internet of
Upgrading Your Home Network Security For Free! Dr. Glen Sagers Illinois State University Outline Passwords & Passphrases Two-factor authentication Updates Viruses and Malware WiFi security Internet of
Getting started with. Windows 10 Desktop
 Getting started with the ITS Windows 10 Desktop Version 0.1 Release Date Status Draft Author Mark Miners Document ID ITS_Windows 10 user guide_v0.1.docx 1 Contents: Introduction...3 Concept....3 Logging
Getting started with the ITS Windows 10 Desktop Version 0.1 Release Date Status Draft Author Mark Miners Document ID ITS_Windows 10 user guide_v0.1.docx 1 Contents: Introduction...3 Concept....3 Logging
Internet and Mini.K.G Senior Scientist, FRAD, CMFRI
 Internet and E-Mail Mini.K.G Senior Scientist, FRAD, CMFRI Email: mini.anish02@gmail.com 28 Introduction to Internet Internet is a worldwide system of interconnected computer networks. It connects several
Internet and E-Mail Mini.K.G Senior Scientist, FRAD, CMFRI Email: mini.anish02@gmail.com 28 Introduction to Internet Internet is a worldwide system of interconnected computer networks. It connects several
Office 365 Instructions
 Office 365 Instructions What is Office 365? Office 365 includes a variety of Microsoft applications in addition to the standard Microsoft Office products. Most of the Office 365 applications (or apps)
Office 365 Instructions What is Office 365? Office 365 includes a variety of Microsoft applications in addition to the standard Microsoft Office products. Most of the Office 365 applications (or apps)
Keeping Your Computer Secure Quick Reference Guide
 Keeping Your Computer Secure Quick Reference Guide Created: 3/16/2010 Page 1 of 1 Table Of Contents 1. Introduction... 3 2. Keeping Your Computer Up to Date... 4 2.1 Windows... 4 2.2 Mac... 6 3. Malware
Keeping Your Computer Secure Quick Reference Guide Created: 3/16/2010 Page 1 of 1 Table Of Contents 1. Introduction... 3 2. Keeping Your Computer Up to Date... 4 2.1 Windows... 4 2.2 Mac... 6 3. Malware
Cracked BitDefender Client Security 2 Years 20 PCs lowest price software ]
![Cracked BitDefender Client Security 2 Years 20 PCs lowest price software ] Cracked BitDefender Client Security 2 Years 20 PCs lowest price software ]](/thumbs/96/128018846.jpg) Cracked BitDefender Client Security 2 Years 20 PCs lowest price software ] Description: The foundation of business security The security requirements for any new or existing company no matter how large
Cracked BitDefender Client Security 2 Years 20 PCs lowest price software ] Description: The foundation of business security The security requirements for any new or existing company no matter how large
TCC College WiFi and Printer Setup 07/11/2018 College WiFi and Printer Setup Guide
 College WiFi and Printer Setup Guide **Please note that the below instructions need to be followed by you only when you are at the college** 1 College WiFi and Printer Setup **Please note that the below
College WiFi and Printer Setup Guide **Please note that the below instructions need to be followed by you only when you are at the college** 1 College WiFi and Printer Setup **Please note that the below
Quick Heal Total Security for Mac. Simple, fast and seamless protection for Mac.
 Simple, fast and seamless protection for Mac. Product Highlights Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth email
Simple, fast and seamless protection for Mac. Product Highlights Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth email
NUIT Tech Talk: Agenda
 NUIT Tech Talk: May 14, 2008 Leigh Underwood NUIT Senior Consultant Agenda Tips for Staying Secure Tips for Staying Connected Forwarding E-mail Special Instructions for Graduates Where to Go for Help Keep
NUIT Tech Talk: May 14, 2008 Leigh Underwood NUIT Senior Consultant Agenda Tips for Staying Secure Tips for Staying Connected Forwarding E-mail Special Instructions for Graduates Where to Go for Help Keep
DEFENCE IN DEPTH HOW ANTIVIRUS, TRADITIONAL FIREWALLS, AND DNS FIREWALLS WORK TOGETHER
 DEFENCE IN DEPTH HOW ANTIVIRUS, TRADITIONAL FIREWALLS, AND DNS FIREWALLS WORK TOGETHER D-Zone DNS Firewall 18-10-20171 EXECUTIVE SUMMARY Cyber attacks continue to grow at an alarming rate with ransomware
DEFENCE IN DEPTH HOW ANTIVIRUS, TRADITIONAL FIREWALLS, AND DNS FIREWALLS WORK TOGETHER D-Zone DNS Firewall 18-10-20171 EXECUTIVE SUMMARY Cyber attacks continue to grow at an alarming rate with ransomware
Introduction to
 Introduction to Email Overview 1. What is Email?... 2 2. Creating an Email Account... 3 3. Managing Messages... 8 4. Sending and Replying to Emails... 9 5. Signing Out... 15 519-579-3800 * ConnectKW@waterlooregion.org
Introduction to Email Overview 1. What is Email?... 2 2. Creating an Email Account... 3 3. Managing Messages... 8 4. Sending and Replying to Emails... 9 5. Signing Out... 15 519-579-3800 * ConnectKW@waterlooregion.org
ThinkPrint a User Guide for Staff. The Latest Print Management System
 ThinkPrint a User Guide for Staff The Latest Print Management System 1 ThinkPrint Agenda What is ThinkPrint for Staff? Printing on Campus Resetting your password Features of your ThinkPrint account How
ThinkPrint a User Guide for Staff The Latest Print Management System 1 ThinkPrint Agenda What is ThinkPrint for Staff? Printing on Campus Resetting your password Features of your ThinkPrint account How
Quick Heal AntiVirus Pro Advanced. Protects your computer from viruses, malware, and Internet threats.
 AntiVirus Pro Advanced Protects your computer from viruses, malware, and Internet threats. Features List Ransomware Protection anti-ransomware feature is more effective and advanced than other anti-ransomware
AntiVirus Pro Advanced Protects your computer from viruses, malware, and Internet threats. Features List Ransomware Protection anti-ransomware feature is more effective and advanced than other anti-ransomware
Student Evaluation of Teaching (SET)
 Testing, Evaluation and Research Services Student Evaluation of Teaching (SET) A guide to retrieving your Chair administrative reports online. FOR ADDITIONAL INFORMATION, PLEASE CONTACT THE SET HELPDESK
Testing, Evaluation and Research Services Student Evaluation of Teaching (SET) A guide to retrieving your Chair administrative reports online. FOR ADDITIONAL INFORMATION, PLEASE CONTACT THE SET HELPDESK
Scheduling WebEx Meetings
 Scheduling WebEx Meetings Instructions for ConnSCU Faculty and Staff using ConnSCU WebEx Table of Contents How Can Faculty and Staff Use WebEx?... 2 Meeting Attendees... 2 Schedule WebEx Meetings from
Scheduling WebEx Meetings Instructions for ConnSCU Faculty and Staff using ConnSCU WebEx Table of Contents How Can Faculty and Staff Use WebEx?... 2 Meeting Attendees... 2 Schedule WebEx Meetings from
INFORMATION TECHNOLOGY DEPT (IT) EMPLOYEE QUICK GUIDE
 INFORMATION TECHNOLOGY DEPT (IT) EMPLOYEE QUICK GUIDE ABOUT US: The Information Technology Department provides students, faculty, and staff with computing and telecommunication based-resources for the
INFORMATION TECHNOLOGY DEPT (IT) EMPLOYEE QUICK GUIDE ABOUT US: The Information Technology Department provides students, faculty, and staff with computing and telecommunication based-resources for the
1 Introduction. Table of Contents. Manual for
 Manual for www.lornasixsmith.com Table of Contents 1Introduction...1 2Log in...2 3Users...2 4What is the difference between pages and posts?...2 5Adding Images to the Media Library...2 6Adding Text to
Manual for www.lornasixsmith.com Table of Contents 1Introduction...1 2Log in...2 3Users...2 4What is the difference between pages and posts?...2 5Adding Images to the Media Library...2 6Adding Text to
Duplication and/or selling of the i-safe copyrighted materials, or any other form of unauthorized use of this material, is against the law.
 Thank you for your interest in e-safety, and for teaching safe and responsible Internet use to your students. Educators are invited to access and download i-safe curriculum AT NO CHARGE under the following
Thank you for your interest in e-safety, and for teaching safe and responsible Internet use to your students. Educators are invited to access and download i-safe curriculum AT NO CHARGE under the following
How To Remove A Virus Manually Windows 7 Without Antivirus Security Pro
 How To Remove A Virus Manually Windows 7 Without Antivirus Security Pro Security Defender is a fake antivirus program, it should not be trusted, since it is a The program usually installs on PCs without
How To Remove A Virus Manually Windows 7 Without Antivirus Security Pro Security Defender is a fake antivirus program, it should not be trusted, since it is a The program usually installs on PCs without
Getting View Client File
 Getting View Client File 1. Launch Internet Explorer 2. At address bar enter this URL https://viewvdi.tp.edu.sg/ and press [Enter]. 3. Please click on More information and click on Go on to the webpage
Getting View Client File 1. Launch Internet Explorer 2. At address bar enter this URL https://viewvdi.tp.edu.sg/ and press [Enter]. 3. Please click on More information and click on Go on to the webpage
Quick Reference Guide for Students: Applying for Course or Campus Transfer
 Quick Reference Guide for Students: Applying for Course or Campus Transfer This guide contains information for current Monash students applying for a Course or Campus Transfer using a new online course
Quick Reference Guide for Students: Applying for Course or Campus Transfer This guide contains information for current Monash students applying for a Course or Campus Transfer using a new online course
Quick Heal AntiVirus Pro. Tough on malware, light on your PC.
 Tough on malware, light on your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware tools. Signature based detection Detects
Tough on malware, light on your PC. Features List Ransomware Protection Quick Heal anti-ransomware feature is more effective and advanced than other anti-ransomware tools. Signature based detection Detects
CMPSCI 120 Fall 2013 Lab #2 Professor William T. Verts
 CMPSCI 120 Fall 2013 Lab #2 Professor William T. Verts Setting Up (PC) Go to the link for the encrypted telnet program PuTTY (Simon Tatham s site in the UK at http://www.chiark.greenend.org.uk/~sgtatham/putty/).
CMPSCI 120 Fall 2013 Lab #2 Professor William T. Verts Setting Up (PC) Go to the link for the encrypted telnet program PuTTY (Simon Tatham s site in the UK at http://www.chiark.greenend.org.uk/~sgtatham/putty/).
Avira Ultimate Protection Suite. Short guide
 Avira Ultimate Protection Suite Short guide 01 Trademarks and Copyright Trademarks Windows is a registered trademark of the Microsoft Corporation in the United States and other countries. All other brand
Avira Ultimate Protection Suite Short guide 01 Trademarks and Copyright Trademarks Windows is a registered trademark of the Microsoft Corporation in the United States and other countries. All other brand
VDI User s Guide: Using VDI from a Web Browser
 Virtual Desktop Interface (VDI) allows Montgomery College students the ability to access College lab images from wherever and whenever they need to from multiple devices (computer, laptop, tablet, smart
Virtual Desktop Interface (VDI) allows Montgomery College students the ability to access College lab images from wherever and whenever they need to from multiple devices (computer, laptop, tablet, smart
Free antivirus software download windows 10
 Free antivirus software download windows 10 Search Free software download,the biggest software directory for freeware and shareware download at brothersoft.com. 2-3-2018 Protect your devices with the best
Free antivirus software download windows 10 Search Free software download,the biggest software directory for freeware and shareware download at brothersoft.com. 2-3-2018 Protect your devices with the best
How To Remove Personal Antivirus Security Pro Virus Manually
 How To Remove Personal Antivirus Security Pro Virus Manually Uninstall Antivirus Pro 2017 Virus (Manual Removal Guide) This type of virus uses false scan results and fake security alerts to scare computer
How To Remove Personal Antivirus Security Pro Virus Manually Uninstall Antivirus Pro 2017 Virus (Manual Removal Guide) This type of virus uses false scan results and fake security alerts to scare computer
INTERNET SAFETY IS IMPORTANT
 INTERNET SAFETY IS IMPORTANT Internet safety is not just the ability to avoid dangerous websites, scams, or hacking. It s the idea that knowledge of how the internet works is just as important as being
INTERNET SAFETY IS IMPORTANT Internet safety is not just the ability to avoid dangerous websites, scams, or hacking. It s the idea that knowledge of how the internet works is just as important as being
ANTIVIRUS SITE PROTECTION (by SiteGuarding.com)
 ANTIVIRUS SITE PROTECTION (by SiteGuarding.com) USER GUIDE Version 1.0.0 Antivirus Site Protection (by SiteGuarding.com) 1.0.0 1 Table of content 1. INTRODUCTION. 3 2. HOW IT WORKS.... 6 3. HOW TO CONFIGURE..
ANTIVIRUS SITE PROTECTION (by SiteGuarding.com) USER GUIDE Version 1.0.0 Antivirus Site Protection (by SiteGuarding.com) 1.0.0 1 Table of content 1. INTRODUCTION. 3 2. HOW IT WORKS.... 6 3. HOW TO CONFIGURE..
Multi-factor Authentication Instructions
 What is MFA? (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account. MFA authentication is typically
What is MFA? (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account. MFA authentication is typically
Chapter 12. Information Security Management
 Chapter 12 Information Security Management We Have to Design It for Privacy... and Security. Tension between Maggie and Ajit regarding terminology to use with Dr. Flores. Overly technical communication
Chapter 12 Information Security Management We Have to Design It for Privacy... and Security. Tension between Maggie and Ajit regarding terminology to use with Dr. Flores. Overly technical communication
How To Remove Virus Without Antivirus In >>>CLICK HERE<<<
 How To Remove Virus Without Antivirus In Windows 7 Pdf Remove virus without antivirus, Here I have all necessary things and also I have steps to Few Effective Steps To Remove Virus Without Antivirus In
How To Remove Virus Without Antivirus In Windows 7 Pdf Remove virus without antivirus, Here I have all necessary things and also I have steps to Few Effective Steps To Remove Virus Without Antivirus In
Quick Heal Total Security for Mac. Simple, fast and seamless protection for Mac.
 Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth
Simple, fast and seamless protection for Mac. Product Highlights Quick Heal Fast and highly responsive Virus Protection. Browsing Protection and Phishing Protection to keep malicious websites at bay. Smooth
Topic: Dropbox. Instructional Technology Services Dropbox Faculty Help. Dropbox Features: Minimum Requirements: Create a Dropbox Account
 Instructional Technology Services Dropbox Faculty Help Topic: Dropbox Dropbox is a free service that lets you save your documents, photos and videos. You can access your files anywhere using any computer,
Instructional Technology Services Dropbox Faculty Help Topic: Dropbox Dropbox is a free service that lets you save your documents, photos and videos. You can access your files anywhere using any computer,
Step 1: Syncing Your Library. After installing One Drive for Business, you will be prompted to Sync a library. NEXT: Select the Library URL
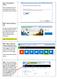 Step 1: Syncing Your Library After installing One Drive for Business, you will be prompted to Sync a library. NEXT: Select the Library URL For this, we want to choose the URL that connects to your Office
Step 1: Syncing Your Library After installing One Drive for Business, you will be prompted to Sync a library. NEXT: Select the Library URL For this, we want to choose the URL that connects to your Office
American Public Health Association s Affiliate Online Community User s Guide. October 2015 edition
 American Public Health Association s Affiliate Online Community User s Guide October 2015 edition TABLE OF CONTENTS Getting Started- Creating Your Account.3 Getting Started- Tips and Suggestions.4 Getting
American Public Health Association s Affiliate Online Community User s Guide October 2015 edition TABLE OF CONTENTS Getting Started- Creating Your Account.3 Getting Started- Tips and Suggestions.4 Getting
Introduction to MS Word XP 2002: An Overview
 Introduction to MS Word XP 2002: An Overview Sources Used: http://www.fgcu.edu/support/office2000/word/files.html Florida Gulf Coast University Technology Skills Orientation Word 2000 Tutorial The Computer
Introduction to MS Word XP 2002: An Overview Sources Used: http://www.fgcu.edu/support/office2000/word/files.html Florida Gulf Coast University Technology Skills Orientation Word 2000 Tutorial The Computer
The process by which a user can associate specific permissions to each username.
 Jargon Buster A Antispyware A program that detects and removes malicious programs on your computer called spyware. Once it is installed can collect information without the users consent, that can be almost
Jargon Buster A Antispyware A program that detects and removes malicious programs on your computer called spyware. Once it is installed can collect information without the users consent, that can be almost
IT & DATA SECURITY BREACH PREVENTION
 IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
IT & DATA SECURITY BREACH PREVENTION A PRACTICAL GUIDE Part 1: Reducing Employee and Application Risks CONTENTS EMPLOYEES: IT security hygiene best practice APPLICATIONS: Make patching a priority AS CORPORATE
Master Student IT Guidebook. Step by Step Guide to IT Success in Zayed University
 Master Student IT Guidebook Step by Step Guide to IT Success in Zayed University Contents Computing Services in Zayed University... 4 Configure Network Connection... 6 Window 7... 6 Mac... 14 ZU Network
Master Student IT Guidebook Step by Step Guide to IT Success in Zayed University Contents Computing Services in Zayed University... 4 Configure Network Connection... 6 Window 7... 6 Mac... 14 ZU Network
Activation Screen Virus
 How To Get Rid Of Spyware Windows Xp Activation Screen Virus Spyware Clear it's technically not a virus, but it does exhibit plenty of malicious To uninstall the Spyware Clear program from Windows XP,
How To Get Rid Of Spyware Windows Xp Activation Screen Virus Spyware Clear it's technically not a virus, but it does exhibit plenty of malicious To uninstall the Spyware Clear program from Windows XP,
Canon Multifunction Copier
 Canon Multifunction Copier FACULTY/STAFF Quick Guide Need help? Send text or email to ithelp@catawba.edu or call the IT Help Desk at 704-637-4666 1 You may use any copier on campus to copy, scan, fax or
Canon Multifunction Copier FACULTY/STAFF Quick Guide Need help? Send text or email to ithelp@catawba.edu or call the IT Help Desk at 704-637-4666 1 You may use any copier on campus to copy, scan, fax or
ONLINE LEARNING MOODLE INSTRUCTIONS FOR STUDENTS TAFENSW.EDU.AU
 ONLINE LEARNING MOODLE INSTRUCTIONS FOR STUDENTS TAFENSW.EDU.AU welcome CONTENTS TECHNICAL REQUIREMENTS FOR USING MOODLE 4 LOGGING INTO YOUR MOODLE COURSE 5 WELCOME TO YOUR STUDY EDITING YOUR MOODLE PROFILE
ONLINE LEARNING MOODLE INSTRUCTIONS FOR STUDENTS TAFENSW.EDU.AU welcome CONTENTS TECHNICAL REQUIREMENTS FOR USING MOODLE 4 LOGGING INTO YOUR MOODLE COURSE 5 WELCOME TO YOUR STUDY EDITING YOUR MOODLE PROFILE
Welcome! The Clarion University Libraries. In This Issue Welcome! CU Libraries Links: Inside The Clarion University Libraries
 August 27, 2013 The Clarion University Libraries Volume 9, Number 1 In This Issue Welcome! Libraries Services And Hours Carlson Lab S.W.A.T. Team Library Tip: ID Cards Faculty Tip: Library Staffing Update
August 27, 2013 The Clarion University Libraries Volume 9, Number 1 In This Issue Welcome! Libraries Services And Hours Carlson Lab S.W.A.T. Team Library Tip: ID Cards Faculty Tip: Library Staffing Update
Getting Started with Destiny Discover ebooks
 Getting Started with Destiny Discover ebooks Log in Access Destiny Discover from a link or widget on your library ebook page. Click on the Search ebooks widget Click Login. Students and staff will select
Getting Started with Destiny Discover ebooks Log in Access Destiny Discover from a link or widget on your library ebook page. Click on the Search ebooks widget Click Login. Students and staff will select
umapps Using umapps 6/13/2018 Brought to you by: umtech & The Center for Teaching & Learning
 umapps Using umapps Center for Teaching and Learning (CTL) 100 Administration Bldg., Memphis, TN 38152 Phone: 901.678.8888 Email: itstrainers@memphis.edu Center for Teaching and Learning Website 6/13/2018
umapps Using umapps Center for Teaching and Learning (CTL) 100 Administration Bldg., Memphis, TN 38152 Phone: 901.678.8888 Email: itstrainers@memphis.edu Center for Teaching and Learning Website 6/13/2018
Portrait Editor. to Portrait Flow
 Portrait Editor to Portrait Flow Portrait Editor is a Walsworth program that allows you to view and edit your portrait images, names and grades based on the photo DVD supplied by your photographer. The
Portrait Editor to Portrait Flow Portrait Editor is a Walsworth program that allows you to view and edit your portrait images, names and grades based on the photo DVD supplied by your photographer. The
CS 120 Digital Literacy, Chapter 5: p
 CS 120 Digital Literacy, Chapter 5: p. 287-344 CS 120, Digital Literacy, Ch 5, p.1 Browsing & Searching the Internet: Web browser a software program that is used to display web pages. IE, Safari, Firefox,
CS 120 Digital Literacy, Chapter 5: p. 287-344 CS 120, Digital Literacy, Ch 5, p.1 Browsing & Searching the Internet: Web browser a software program that is used to display web pages. IE, Safari, Firefox,
PROTECTING YOUR BUSINESS ASSETS
 PROTECTING YOUR BUSINESS ASSETS How to Spot Danger Before Your Computer Gets Infected, Your Site Hosts Malware, and Your Credit Card Number Gets Stolen A MyNAMS Presentation by Regina Smola @2012 Regina
PROTECTING YOUR BUSINESS ASSETS How to Spot Danger Before Your Computer Gets Infected, Your Site Hosts Malware, and Your Credit Card Number Gets Stolen A MyNAMS Presentation by Regina Smola @2012 Regina
LOGGING IN AND OUT OF YOUR ACCOUNT
 WELCOME TO EMAIL Email is one of the most important methods of communication in the world today. Not only does it allow you to contact one or more people almost instantly, but it also acts as your online
WELCOME TO EMAIL Email is one of the most important methods of communication in the world today. Not only does it allow you to contact one or more people almost instantly, but it also acts as your online
How do I access the wireless network using a laptop?
 Zane State College offers free computer software and software tools to help students achieve success. Below are instructions to install the many software applications offered at Zane State College. How
Zane State College offers free computer software and software tools to help students achieve success. Below are instructions to install the many software applications offered at Zane State College. How
Microsoft 365 Business FAQs
 Microsoft 365 Business FAQs Last updated April 27 th, 2018 Table of Contents General... 3 What is Microsoft 365 Business?... 3 Who should consider adopting Microsoft 365 Business?... 3 How can I get Microsoft
Microsoft 365 Business FAQs Last updated April 27 th, 2018 Table of Contents General... 3 What is Microsoft 365 Business?... 3 Who should consider adopting Microsoft 365 Business?... 3 How can I get Microsoft
EDUCATIONAL SERVICES. Parent Portal Contact Management Manual
 EDUCATIONAL SERVICES Parent Portal Contact Management Manual Introduction The Genesis Parent/Student Portal tool is a safe, secure way to view your child s school record and will give you access to the
EDUCATIONAL SERVICES Parent Portal Contact Management Manual Introduction The Genesis Parent/Student Portal tool is a safe, secure way to view your child s school record and will give you access to the
TUHSD ebook Shelf. Student/Staff Accounts: Student Accounts are the same as their district computer login accounts. To access from school:
 TUHSD ebook Shelf Student/Staff Accounts: To access from school: 1. Click on the TUHSD EBook icon on your desktop Student Accounts are the same as their district computer login accounts Username: ID #
TUHSD ebook Shelf Student/Staff Accounts: To access from school: 1. Click on the TUHSD EBook icon on your desktop Student Accounts are the same as their district computer login accounts Username: ID #
TUHSD ebook Shelf. Student/Staff Accounts: To access from school: Student Accounts are the same as their district computer login accounts
 TUHSD ebook Shelf Student/Staff Accounts: To access from school: 1. Click on the TUHSD EBook icon on your desktop Student Accounts are the same as their district computer login accounts Username: ID #
TUHSD ebook Shelf Student/Staff Accounts: To access from school: 1. Click on the TUHSD EBook icon on your desktop Student Accounts are the same as their district computer login accounts Username: ID #
stickapp anti-virus password manager vpn client free Security & Productivity Apps for SafeStick stickapps.co.uk
 Security & Productivity Apps for SafeStick StickApps are a collection of Security and Productivity apps - some free and some licenced - which have been selected, designed and tested to work on SafeStick
Security & Productivity Apps for SafeStick StickApps are a collection of Security and Productivity apps - some free and some licenced - which have been selected, designed and tested to work on SafeStick
ORU IT Oral Roberts University Information Technology Student Guide
 ORU IT 2017-18 Oral Roberts University Information Technology Student Guide August 2017 Contents Contacting ORU IT... 2 Accessing ORU-Student Wireless on Campus... 2 How to Log into the ORU Web Apps...
ORU IT 2017-18 Oral Roberts University Information Technology Student Guide August 2017 Contents Contacting ORU IT... 2 Accessing ORU-Student Wireless on Campus... 2 How to Log into the ORU Web Apps...
Client Computing Security Standard (CCSS)
 Client Computing Security Standard (CCSS) 1. Background The purpose of the Client Computing Security Standard (CCSS) is to (a) help protect each user s device from harm, (b) to protect other users devices
Client Computing Security Standard (CCSS) 1. Background The purpose of the Client Computing Security Standard (CCSS) is to (a) help protect each user s device from harm, (b) to protect other users devices
ELECTRONIC BANKING & ONLINE AUTHENTICATION
 ELECTRONIC BANKING & ONLINE AUTHENTICATION How Internet fraudsters are trying to trick you What you can do to stop them How multi-factor authentication and other new techniques can help HELPING YOU STAY
ELECTRONIC BANKING & ONLINE AUTHENTICATION How Internet fraudsters are trying to trick you What you can do to stop them How multi-factor authentication and other new techniques can help HELPING YOU STAY
Basics. IT services for postgraduate resarch students
 Basics IT services for postgraduate resarch students Get started Activate your computing account We re looking forward to welcoming you to the University of Liverpool! This guide will help you to understand
Basics IT services for postgraduate resarch students Get started Activate your computing account We re looking forward to welcoming you to the University of Liverpool! This guide will help you to understand
