Datto BDR Needs Assessment Module
|
|
|
- Jemimah Marshall
- 6 years ago
- Views:
Transcription
1 Datto BDR Needs Assessment Module Instructions to Perform the Full BDR Needs Assessment User Guide 2016 RapidFire Tools, Inc. All rights reserved. V Ver 4K
2 Contents Overview... 2 Performing the Full BDR Needs Assessment versus Quick Assessment... 3 Perform BDR Needs Assessment Project Initial Set-up... 4 Start an Active Full BDR Needs Assessment Project... 4 Perform the Full BDR Needs Assessment... 6 Step 1 Complete the BDR Needs Worksheet... 6 Step 2 Run BDR Data Collector using Network Scan and Import Scan... 7 Step 3 Run Push Deploy Tool Selecting the Local Collector to Scan Local Computers... 8 Step 4 Run Computer Data Collector on Computers that cannot be Scanned Remotely (Optional)... 8 Step 5 Confirm that Data Collection is Complete using the Scan Completion Confirmation Worksheet... 9 Step 6 Complete Critical System ID Worksheet Step 7 Complete Backup Volume Exclusion Worksheet Step 8 Complete Existing Backup Solution Backup Set ID Worksheet Step 9 Complete Backup Selection Preference Worksheet Generating Reports Appendix A Running the BDR Data Collector Steps to Perform the BDR Data Collection Process on the Network Importing the BDR Collector Generated Scan Data Appendix B Using the BDR Push Deploy Tool to Collect Local Computer Scan Data Running the BDR Push Deploy Tool to Perform Local Computer Scans Importing the Local Computer Scan Data into the BDR Needs Assessment Appendix C Using the Computer Data Collector to Scan Unreachable Computers Running the Computer Data Collector to Perform Local Computer Scans Importing the Local Computer Scan Data into the BDR Needs Assessment Appendix D - Time Savings Tip to Reduce Worksheet Data Input Time Saving Time Inputting Reponses in Worksheets Through the Use of Bulk Entry Option
3 Overview The BDR Needs Assessment is a powerful tool for much more than just sizing your customer s back-up requirements. Use it to get detailed information for upselling your services around the proper Datto solution, and to discover issues related to backups that could cause loss of data in the event of a disaster. You also get a recovery time calculator, and summary information on the servers and workstations on the network. The software includes the Network Detective Application, the BDR Data Collector, Worksheets used to collect Secondary Data, and the Push Deploy Tool used to collect detailed local computer data. The BDR Needs Assessment lets you: Quickly perform BDR Needs assessments to identify and expand BDR sales opportunities Identify the Risks associated with the prospect s current BDR solution that is in place to present the business impact of system downtime and recovery time Calculate Recovery Time Costs associated with prospect s current BDR to justify BDR system upgrades or improvements along with generating a BDR System Sizing specification The process to create a BDR needs assessment involves creating a Site and executing three major assessment steps using Network Detective: A) Network data collection, B) Collecting computer endpoint data, and C) Gathering secondary data necessary through the use of worksheets to further specify BDR needs. Steps of a BDR Needs Assessment Using Network Detective The BDR Needs Assessment is a complete assessment that includes automated data collection and worksheets. The Network Data Collector is wizard driven and takes just a few minutes of your time to set-up. The scan itself typically takes minutes on a 50-user network on a single subnet. You can run this from any windows system on the network. The collection runs automatically, so you don t you have to watch it the entire minutes. 2
4 The Push Deploy tool can be run at the same time as the Network Data Collector and is used to gather detailed information from each computer on the network. It is also wizard driven, takes only a few minutes to setup, and then will take about an hour to scan a 50 system network. (In the event that systems are not accessible via WMI, a local collection can be manually run on each system that you wish to include in the assessment.) You will also fill-out the BDR worksheets, which take 5-15 minutes depending on the size of the network. Performing the Full BDR Needs Assessment versus Quick Assessment This User Guide focuses on performing the Full BDR Needs Assessment which allows you to do a comprehensive sizing and needs exercise. For a less thorough and faster to perform BDR needs analysis, you can perform a Quick BDR Needs Assessment. The instructions for performing a Quick assessment are outlined in the BDR Needs Assessment Quick Start Guide available for download at The table below outlines the major differences between the Quick and Full assessment. Feature Quick Full Scan Types Network Only Network and Local Computer Cloud Storage Opportunity Detection Cloud Application Usage Detection Non-published Local Attached Storage Detection Existing Backup Solution Evaluation RTO Calculator Critical System Identification Exclude Individual Volumes from Assessment Requires Completion of InForm Worksheets Use default setting of servers as critical and workstations as not Allows you to hand pick which systems are critical It is recommended that a Full BDR Needs Assessment be performed in order to more closely align the customers actual business growth, Recovery Time Objective (RTO), and operational risk management needs with the available BDR solutions. 3
5 Perform BDR Needs Assessment Project Initial Set-up 1. Go to to download and install the Network Detective application. Then run Network Detective and login with your credentials. 2. Create a new Site by selecting the New Site option. Set the Site Name for the Site in Network Detective. Select the OK button to create the site. Start an Active Full BDR Needs Assessment Project 1. From within the Site Window, select the Start button that is located on the far right side of the window to start the Assessment. 2. Next, select the BDR Assessment option presented. 3. Select the Next button to continue. 4. In the Create New Assessment Window presented, use the default Label presented OR assign the Label (name) for your Assessment project by typing the name of your Assessment in the Label Name field. 5. Select the Next button to Start your Assessment. 6. Select the Finish button to complete the creation of your Assessment project. 7. Once the new BDR Assessment Project is started, a Checklist is displayed in the Assessment Window. 4
6 This Checklist presents the Required and Optional steps that are to be performed during the assessment process. Throughout the assessment process you will be required to Complete the Checklist Items, in the order presented in the Checklist. Note: The successful completion of your Assessment is dependent on the completion of each Checklist item in the numerical order as presented within the Checklist. DO NOT ATTEMPT TO COMPLETE CHECKLIST ITEMS OUT OF ORDER DOING SO WILL CAUSE YOU TO PRODUCE AN INVALID ASSESSMENT You may also print a copy of the Checklist for reference purposes by using the Printed Checklist feature. 5
7 Perform the Full BDR Needs Assessment Execute the following steps, IN THE EXACT ORDER DETAILED BELOW, to perform the Full BDR Needs Assessment. Step 1 Complete the BDR Needs Worksheet 1. To complete the BDR Needs Worksheet, click on the selector on the left side of the InForm Bar (located towards the bottom of the Assessment window) to display the BDR Needs Worksheet for selection. 2. Open the BDR Needs Worksheet listed under the InForm Bar by selecting the BDR Needs Worksheet s name label. The BDR Needs Worksheet window will be displayed. 3. Enter Responses in the Response Field for each Question Topic listed throughout the worksheet in order to document the BDR needs for your client. Next to some Topic Questions that must be answered is an indicator stating Required Remaining. The Required Remaining indicator is used to indicate that Responses are Required to the topics/questions posed. Topic Questions that do not have the Required Remaining Indicator present, are Questions where Responses are OPTIONAL. Worksheet Time Saving Tip: See Appendix D for Worksheet completion time saving tip using the Bulk Entry feature. To document the Responses to the Instructions/Questions presented in this worksheet: A. Select and Review the Topic Question. B. Review the Instructions. Instructions provide guidance and are not included in the reports. C. Enter the Response. The questions related to the Recovery Time Cost Calculator are Optional. FOR HOURLY WAGE, COST AND REVENUE 6
8 NUMBER RESPONSE INPUTS, DO NOT USE A $ IN THE VALUES INPUT INTO THE RESPONSE FIELD. D. Enter any Notes relevant to the topic s response by selecting the Notes icon. (OPTIONAL) E. Select the Respondent icon to enter the name of individual that provided the information necessary to document the response to the topic s question or requirement. (OPTIONAL) 4. After completing the BDR Needs Worksheet, select the Save button in the worksheet to save your responses. Then select the Close button to close the worksheet s window. 5. After the BDR Needs Worksheet has been completed, the Checklist will be updated to show that this worksheet has been Completed. Proceed to the next step below to start the BDR assessment s Network Data Collection process. Step 2 Run BDR Data Collector using Network Scan and Import Scan 1. Download, install, and run the BDR Data Collector from 2. Follow the steps outlined in Appendix A Running the BDR Data Collector to perform the BDR Network Data Collection. Note: To run this scan, WMI must be enabled within the network. 3. After the BDR Data Collector Scan is complete, select the Import Scan File option in the Assessment window to Import the Scan File into the Assessment. After the BDR Collector Data Scan is finished, select Import File within the Network Detective BDR Assessment Window to select the scan data file and Import the file into the Assessment 7
9 Step 3 Run Push Deploy Tool Selecting the Local Collector to Scan Local Computers 1. Visit to download, and install the BDR Push Deploy Tool on a computer within the Network you are assessing. 2. Run the BDR Push Deploy Tool to Initiate the BDR Push Local Computer Data Scan. Note: WMI must be enabled within the network to run this scan. 3. Follow the steps outlined in Appendix B Running the Push Deploy Tool to Collect Local Computer Data to perform scans and data collection on local computer endpoints and import the scan results into the Assessment. 4. After the Push Deploy Local Computer Data Scan is complete, select the Import Scan File option in the Assessment window to Import the scan results into the Assessment. After the Push Deploy Local Computer Scan is finished, select Import File within the Network Detective BDR Assessment Window to select the Local Computer Scan Data files and Import the files into the Assessment Step 4 Run Computer Data Collector on Computers that cannot be Scanned Remotely (Optional) 1. Download, install, and run the Computer Data Collector from 2. Run the Computer Data Collector Tool to Initiate a Local Computer Data Scan on a single computer. 3. Follow the steps outlined in Appendix C Running the Computer Data Collector to Scan Unreachable Computers to perform scans and data collection on local computer endpoints and import the scan results into the Assessment. 8
10 4. After the Computer Data Collector generated Local Computer Data Scan is complete, select the Import Scan File option in the Assessment window to Import the scan results into the Assessment. After the Computer Data Collector Local Computer Scan is finished, select Import File within the Network Detective BDR Assessment Window to select the Local Computer Scan Data file and Import the file into the Assessment Step 5 Confirm that Data Collection is Complete using the Scan Completion Confirmation Worksheet After you have performed all required data collection and are ready to move forward, open and mark this worksheet as complete. 1. To complete the Scan Completion Confirmation Worksheet, click on the selector on the left side of the InForm Bar located towards the bottom of the Assessment window to display the Worksheet for selection. 2. Open the Scan Completion Confirmation Worksheet listed under the InForm Bar by selecting the Scan Completion Confirmation Worksheet s name label. 3. The Scan Completion Confirmation Worksheet window will be displayed. 4. If the BDR Collector Scan and all local computer scans have been performed and Imported into the Assessment, then select the Yes Response to confirm that the scans are complete. 5. After completing the Scan Completion Confirmation Worksheet, select the Save button to save your response. Then select the Close button to close the worksheet s window. 6. After the Scan Completion Confirmation Worksheet has been completed, the Checklist will be updated to show that this worksheet has been Completed. After the completion of this worksheet, new steps will be added to the Checklist that require additional worksheets be 9
11 completed. These additional worksheets will be accessible for editing and completion in a list located under the InForm bar at the bottom of the Assessment Window. Step 6 Complete Critical System ID Worksheet The Critical Systems ID Worksheet shows all detected systems and allows you to mark them as critical to the operation of this business. These systems can be either servers or workstations. 1. To complete the Critical System ID Worksheet, open the Critical System ID Worksheet listed under the InForm Bar located towards the bottom of the Assessment window by selecting the Critical System ID Worksheet s name label. The Critical System ID Worksheet window will be displayed. 2. Enter Responses in the Response Field for each Topic Question listed throughout the worksheet s Category pages in order to document the BDR needs for your client. 3. Select each Category page within the worksheet to assign Responses all of the questions associated with the servers or workstations identified within the Network. To save time completing this worksheet, use the Bulk Data Entry feature detailed in Appendix D. Use the Bulk Data Entry feature to set all of the responses to Topic Questions in the worksheet s to the No Response. Then, one by one, set the Response to Yes only for the Computers that are deemed as Critical to the business. 10
12 4. After completing the Critical System ID Worksheet, select the Save button to save your responses. Then select the Close button to close the worksheet s window. 5. After the Critical System ID Worksheet has been completed, the Checklist will be updated to show that this worksheet is Complete. Step 7 Complete Backup Volume Exclusion Worksheet This worksheet lists all volumes by computer and allows you to identify volumes to exclude from the analysis. By default, no volumes are excluded, but you may use this worksheet to identify some volumes (such as backup file drives) that are not to be included. 1. Open the Backup Volume Exclusion Worksheet listed under the InForm Bar located towards the bottom of the Assessment window by selecting the Backup Volume Exclusion Worksheet s name label. The Backup Volume Exclusion Worksheet window will be displayed. 2. Select each available Category page within the worksheet to assign responses to the questions posed about the need to include identified drive volumes for each of the servers and workstations identified within the Network. 11
13 3. Enter Responses in the Response Field for each Topic Question listed throughout the worksheet in order to document the BDR needs for your client. The Default Responses in this worksheet are set to No in order to save you time in completing this worksheet. Select the Yes Response for computer volumes that are to be excluded. 4. After completing the Backup Volume Exclusion Worksheet, select the Save button to save your responses. Then select the Close button to close the worksheet s window. 5. After the Backup Volume Exclusion Worksheet has been completed, the Checklist will be updated to show that the worksheet has been Completed. Step 8 Complete Existing Backup Solution Backup Set ID Worksheet This worksheet allows you to identify which systems are in the current backup set within the existing backup solution that is in place. 1. To complete the Existing Backup Solution Backup Set ID Worksheet, open the Existing Backup Solution Backup Set ID Worksheet listed under the InForm Bar located towards the bottom of the Assessment window by selecting the Existing Backup Solution Backup Set ID Worksheet s name label. 2. The Existing Backup Solution Backup Set ID Worksheet window will be displayed. 3. Select each Category page within the worksheet to assign responses to the questions associated with the servers or workstations identified within the Network. Enter Responses in the Response Field for each Topic Question listed throughout the worksheet in order to document the BDR needs for your client. 12
14 ` To save time completing this worksheet, use the Bulk Data Entry feature detailed in Appendix D. Use the Bulk Data Entry feature to set all of the answers to Topic Questions in the worksheet s to the No Response. Then, one by one, set the Response to Yes only for the Computers that are included in the currently implemented backup solution s Backup Set. 4. After completing the Existing Backup Solution Backup Set ID Worksheet, select the Save button to save your responses. Then select the Close button to close the worksheet s window. 5. After the Existing Backup Solution Backup Set ID Worksheet has been completed, the Checklist will be updated to show that the Existing Backup Solution Backup Set ID Worksheet has been Completed. Step 9 Complete Backup Selection Preference Worksheet This worksheet allows you to override the suggested Datto Model. 1. To complete the Backup Selection Preference Worksheet, open the Backup Selection Preference Worksheet. The worksheet is listed under the InForm Bar located towards the bottom of the Assessment window. To open the worksheet select the Backup Selection Preference Worksheet s name label. 2. The Backup Selection Preference Worksheet window will be displayed. 3. In the Response field, select the Datto BDR Solution option override that you want to assign to this assessment. 4. After completing the Backup Selection Preference Worksheet, select the Save button to save your responses. Then select the Close button to close the worksheet s window. 13
15 5. After the Backup Selection Preference Worksheet has been completed, the Checklist will be updated to show that the worksheet has been Completed. Generating Reports NOTE: This step is NOT performed at the client site or network. The Network Detective application should be installed on your workstations or laptop. Install Network Detective from if you have not already done so. To incorporate your company s brand in the reports, use the custom Reporting Branding Preference features in Network Detective. To learn more about how to use the Report Branding Preference feature, refer to the Network Detective User Guide available at Follow these steps to run the BDR Analysis Reports 1. Run Network Detective and login with your credentials. 2. Then select the Site, go to the Active BDR Assessment, and then select the Reports link located in the center of the Assessment Window. The Create Reports window will be displayed. 3. Select the BBR Needs Assessment reports that you want to generate. 4. Select the Create Reports button and follow the prompts to generate the reports you selected. You may be prompted to add information to the report to include for whom the report is prepared. At the end of the report generation process, the generated reports will be made available for you to open and review. The BDR Needs Assessment module can generate the following reports and assessment worksheets: BDR Needs Analysis Report Reporting showing analysis of the Backup/Disaster Recovery needs for an environment. It includes both discovered information regarding the storage needs of an environment, along with analysis of both onsite and offsite backup requirements. BDR PowerPoint PowerPoint slide deck for use in presenting your finding from the BDR Needs Analysis with your client. BDR Needs Assessment Worksheets All of the worksheets that were completed during an assessment can be generated. The generated worksheets will contain the Response input that was placed into each worksheet during the assessment process. 14
16 Appendix A Running the BDR Data Collector Prerequisite: The BDR Data Collector scan depends on the availability of WMI within the network environment being scanned. Please verify that WMI is enabled before proceeding with the steps below. Steps to Perform the BDR Data Collection Process on the Network Step 1 - Launch the BDR Data Collector To perform a BDR Network scan, visit the RapidFire Tools software download website and download and run the BDR Data Collector named BDRDataCollector.exe at The BDR Data Collector is a self-extracting.zip file that does not install on the client computer. To start the BDR Data Collector, right-click on the BDRDataCollector.exe and run BDRDataCollector.exe using the RUN AS ADMINISTRATOR MENU option. Use the unzip option to unzip the files into a temporary location and start the collector. Step 2 Configure the BDR Data Collector Network Scan Starting the BDR Data Collector application will present the following screen. Select the Next button and the Credentials window will be presented. Step 3 Configure the BDR Data Collector Network Scan The Credentials window will be displayed to enable you to assign the required administrative credentials necessary to access the network environment during the scanning process. Enter the Credentials by performing these steps: 1. Enter a username and password with administrative rights to connect to a Domain Controller and Active Directory. If in a domain, clicking the Next button will test a connection to the a Domain Controller and Active Directory to verify your credentials. 2. Select the Next button. At this point in the process, the Local Domains window will be presented. 15
17 Step 4 Configure the Local Domains Select the Domains to gather information from by performing these steps: 1. Select to gather information from ALL domains detected OR from Domains and OUs you select. 2. Select the Next button. 3. If you selected the Gather Information from the Selected Domains and OUs Below option, you will then be requested to confirm the Domain and OU when the Domain and OU Confirmation window is presented. 4. Select the OK button to confirm the Domain and OUs you have selected. At this point in the process, the Network IP Address Range window will be presented. Step 5 Configure the Network IP Address Range to be Scanned You may use the default IP Range presented and select the Next button, or define an IP Range. You can specify an IP Range by clearing the default IP address range entry detected within the network by selecting the Clear All Entries option. Next, enter the Starting and Ending IP Addresses for the range(s) you want to scan in the IP range field using the following format: Starting Address of IP Range Address<hyphen>Ending Address of IP Range. Then select the Add link to add the IP Range you specified. Scans may affect network performance. Select Perform minimal impact scan if this is an issue. Then select the Next button. The Verify and Run window will be presented. Step 6 Verify and Run the Scan Select the folder that you want to store the scan data file in after the scan is completed. You may change the scan s Output Assessment File Folder location and Basename for the scan data. Enter any Comments and then select Start. The Collection Progress window will then be displayed as presented below. Note: Prior to performing Step 6 above, you can run the Pre-Scan Analyzer. The Pre-Scan Analyzer checks to verify that WMI is available. 16
18 The Pre-Scan Analyzer can also identify any unreachable computers that should be turned on to be made accessible before you start the BDR Collector Scan, or identify unreachable computers that you need to later scan with the Computer Data Collector. Step 7 Monitor the Network Scan s Collection Progress The Network Scan s status is detailed in the Collection Progress window. The Collection Progress window presents the progress status of a number of scanning processes that are undertaken. At any time you can Cancel Data Collection which will not save any data. By selecting Wrap It Up you can terminate the scan and generate reports using the incomplete data collected. Upon the completion of the scan, the Finish window will be displayed. Step 8 Complete the BDR Data Collector Network Scan Process The Finish window indicates that the scan is complete and enables you to review the scan output file s location and the scan s Results Summary. Click on Done button to close the BDR Data Collector window. Note the location where the scan s output file is stored. This information is necessary for the importing of the BDR Collector generated Scan Data. Importing the BDR Collector Generated Scan Data The final step in this process is to import the data collected during the BDR Network Scan into the Active BDR needs assessment. Perform the following steps to Import the Scan Data: 1. Click on the Import Scans File button in the Network Detective Assessment window. The Select the Scan Results window will be displayed thereby allowing you to import the.zip file produced by the BDR Network Data Scan into the Assessment. 2. Browse and Select the BDR Network Scan data file from the folder you selected during the Network Scan process. 17
19 3. Then click the Next button to import the scan data. 4. The Network Detective Merge window will be displayed. The success of the scan s import will be confirmed by the Scan Archive Created window being displayed. 5. Select the Finish button to complete the scan file import process. After the BDR Data Collector scan file is imported into the assessment, the Scans section of the Assessment Window will be updated to list the Network Scans files imported into the assessment as seen below. In addition, the Status and Check List information indicators will be updated to present the assessment s current status. Refer to the figure to the right. 18
20 Appendix B Using the BDR Push Deploy Tool to Collect Local Computer Scan Data Prerequisite: The BDR Push Deploy Tool scan depends on the availability of WMI within the network environment being scanned. Please verify that WMI is enabled before proceeding with the steps below. Running the BDR Push Deploy Tool to Perform Local Computer Scans The BDR Assessment Push Deploy Tool pushes the Local Data Collector to machines in a specified IP range, the local scans are executed on each computer, and then each computer scan file is saved to a specified directory (which can also be a network share). This directory (i.e. folder) is defined during the set-up of the Push Deploy Tool based scan. The benefit of the tool is that a local scan can be run simultaneously on each computer within the network from a centralized location. The Push Deploy Tool is used to reduce or eliminate the need you to spend time at each computer within the network to run a local computer scan. The output files (.CDF files) from the local scans can either be: 1. stored on a USB drive and taken off site to be imported into the active assessment within Network Detective. 2. automatically uploaded to the RapidFire Tools secure cloud storage area using the Client Connector (a Network Detective add-on) and later downloaded from the secure cloud storage area directly to the Network Detective application for use in report generation. To use the BDR Assessment Push Deploy Tool to perform local scans for computers within a network, please follow the steps detailed below. Step 1 Download and Run the BDR Needs Assessment Push Deploy Tool To perform a local computer scan, download the BDR Push Deploy Tool named BDRPushDeployTool.zip from the RapidFire Tools download page at Then extract the contents of the BDR Push Deploy Tool.ZIP file to any machine on the target network or to a USB drive for use. Within the folder named BDRPushDeployTool that was created by the.zip file extraction, right-click and run BDRPushDeployTool.exe using the RUN AS ADMINISTRATOR option. If you do not run the BDRPushDeployTool.exe as an administrator, you will see the following Warning message. 19
21 Step 2 Configure BDR Assessment Push Deploy Tool to Perform Local Computer Scan Starting the BDR Assessment Push Deploy Tool will present the following window. First, set the I want to collect option to be Computer Data (.CDF). Step 3 Set the Storage Folder Location for the Local Computer Scans Collected Set the Storage Folder location used to store the scan data collected from the computers scanned. Note: This Storage Folder location can be located on a network share drive to centralize scan file storage. If the individual performing the BDR Assessment Push Deploy Tool-based scans is logged into the network using Domain Administrator credentials, then the need to enter credentials as part of configuring the Push Deploy Tool scans is optional. Step 4 Enter User Name and Password Credentials If the entry of credentials is required, then type in the administrator level Username and Password Credentials necessary to access the local computers on the network to be scanned. Next, select the Computers and Collection Status tab. Step 5 Define the IP Address Range of the Computers to Scanned The Computers and Collection Status window allows you to: Add (computers) from IP Range that are to be scanned Add a Single Computer to be scanned Add (computers) from File that are to be scanned Or. to Save Computers to File in order to export a list of computers to be scanned again in future assessments Methods for the Set-up Process Used to Configure Computers to be Scanned As previously referenced, there are three methods to creating/adding a list of computers to be scanned by the Push Deploy tool. These methods are explained below. 20
22 Method 1 Add (computers) from IP Range that are to be Scanned A. Click on the Add from IP Range and to define the Starting and Ending computer IP addresses range that are to be included within the scanning process. B. When you have input the IP address range into the IP Range window, select the OK button. Method 2 - Add a Single Computer to be Scanned To use the Add Single Computer method to select computers to be scanned: A. Type in the computer s IP address as shown B. Next, click on the Add Single Computer link to the right of the IP address entry field. C. The single IP address to be scanned will be listed in the list of computers to be scanned in the Computers and Collection status window. Method 3 - Add (computers) from File that are to be Scanned A. Click on the Add from File link and select the text file that contains the computer IP addresses that are to be included within the scanning process. B. Select the file that contains the IP addresses to be scanned, and then click on the Open button. The file that contains the IP addresses can be created using the Push Deploy Tools Save Computers to File feature, or created manually with a text editor using the required text formatting structure so that the IP addresses are recognized by the BDR Needs Assessment Push Deploy Tool. Upon the file s selection and opening, the IP address and computer information will be imported into the BDR Needs Assessment Push Deploy Tool and presented in the Computers and Collection Status window for verification prior to starting the scan. After one or more of the abovementioned methods have been used to define the computer IP addresses to be scanned, the computer names and IP addresses will be listed in the Computer and Collection Status window. 21
23 Step 6 Initiating the Scan After creating/adding a list of one or more computers to scan, the scan can be initiated by selecting the Start Data Collection button. The status of each computer s scan activity will be highlighted within the Computers and Collection Status window as presented below. Upon the completion of all of the scheduled scans, the scan data collected is stored within the Storage Folder Location folder presented in the Collected Data Files window of the BDR Needs Assessment Push Deploy Tool. Step 7 Verify that the Local Computer Scan Data has been Collected To verify the inclusion of the scan data produced by the BDR Needs Assessment Push Deploy Tool within your assessment, select the Collected Data Files tab within the Push Deploy Tool. The Collected Data Files window will be displayed. Step 8 Verify that BDR Needs Assessment Local Computer Scan Files are Available from Scan Process Refresh the list of files presented by clicking on the Refresh Data Files link. This action will update the list of files available within the Current Storage Folder containing scan data. After all of the BDR Needs Assessment s Local Computer Scans are complete for the computers that were selected to undergo this scan, the next phase in the process is to import the scan data files produced by the Local Scans into the current BDR Needs Assessment. 22
24 Importing the Local Computer Scan Data into the BDR Needs Assessment The final step in this process is to import the Local Computer Scan data collected during the Push Deploy Tool Scan into the Active BDR needs assessment. Perform the following steps to Import the Local Computer Scan Data files: 1. Click on the Import Scans File button in the Network Detective Assessment window. The Select the Scan Results window will be displayed thereby allowing you to import the.cdf files produced by the Push Deploy Tools Local Computer Scans into the Assessment. 2. Browse and Select the Local Computer Scan data files from the Storage Folder location you selected during the setup of the Push Deploy Tool Scan process. 3. Then click the Next button to import the scan data. 4. The Network Detective Merge window will be displayed. The success of the scan s import will be confirmed by the Scan Archive Created window being displayed as presented below. 5. Select the Finish button to complete the scan file import process. 23
25 After the Local Computer scan files are imported into the assessment, the Scans section of the Assessment Window will be updated to list the Computer Scans files imported into the assessment. In addition, the Status and Check List information indicators will be updated to present the assessment s current status. Refer to the figure to the right. 24
26 Appendix C Using the Computer Data Collector to Scan Unreachable Computers Using the Computer Data Collector, run the local scan any computers that cannot be scanned remotely (i.e. blocked by a firewall, not connected to the domain, or otherwise inaccessible). Use the Computer Data Collector to run the Local Scan on selected computer systems manually. Running the Computer Data Collector to Perform Local Computer Scans For computers that were unreachable during the Local Scans that were to be performed using the Push Deploy Tool and still require scanning, you will need to download and run the Computer Data Collector from the RapidFire Tools software download website to a folder on a local computer or a USB drive. The Computer Data Collector is a self-extracting.zip file named NetworkDetectiveComputerDataCollector.exe that executes as an.exe and is completely noninvasive it is not installed on the local computer being scanned or any other machine on the client s network, and does not make any changes to the system. Step 1 Running the Computer Data Collector to Perform a Local Computer Scan Before starting the use of the Computer Data Collector, always download the latest version of the Computer Data Collector. Please follow these steps to download the run the Computer Data Collector. 1. Visit the RapidFire Tools software download website at and download to a Storage Folder and run the Computer Data Collector named NetworkDetectiveComputerDataCollector.exe This file is a self-extracting ZIP file that does not install on the client computer. 2. After download, run NetworkDetectiveComputerDataCollector.exe and use the Unzip option to unzip the files into a temporary location. The Computer Data Collector will automatically start running. Note: After the Computer Data Collector Scan is complete, the scan data file will be located in the Storage Folder you selected during the download and running of the Computer Data Collector. Note, that the Computer Data Collector will have to be downloaded and run on each local computer that is to be included in the Network Assessment that you are performing. 25
27 Step 2 Monitoring the Computer Data Collector Scan on a Local Computer Once you unzip the Computer Data Collector, the Computer Data Collector application in the Storage Folder you selected, the program will automatically start and you will be presented with the following window indicating that the Computer Data Collector is performing the local scan. Step 3 Review Local Scan File Location Upon completion of the Local Computer Scan using the Computer Data Collector, a window will be presented to you displaying the location of the scan output file that has a file extension of.cdf. This.CDF file should be retrieved and imported into your assessment. Importing the Local Computer Scan Data into the BDR Needs Assessment The final step in this process is to import the Local Computer Scan data collected during the Push Deploy Tool Scan into the Active BDR needs assessment. Perform the following steps to Import the Local Computer Scan Data files: 1. Click on the Import Scans File button in the Network Detective Assessment window. The Select the Scan Results window will be displayed thereby allowing you to import the.cdf file produced by the Computer Data Collector into the Assessment. 2. Browse and Select the Local Computer Scan data files from the Storage Folder location you selected during the setup of the Computer Data Collector installation process. 26
28 3. Then click the Next button to import the scan data. 4. The Network Detective Merge window will be displayed. The success of the scan s import will be confirmed by the Scan Archive Created window being displayed as presented below. 5. Select the Finish button to complete the scan file import process. After the Local Computer scan files are imported into the assessment, the Scans section of the Assessment Window will be updated to list the Computer Scans files imported into the assessment. Please note, the Status and Check List information indicators for this step will not be updated in the Checklist until you complete the Scan Completion Confirmation Worksheet. To verify that the scan file produced by the Computer Data Collector was imported into your assessment, view the Computer Scans file list located under the Scans Bar. 27
29 Appendix D - Time Savings Tip to Reduce Worksheet Data Input Time Saving Time Inputting Reponses in Worksheets Through the Use of Bulk Entry Option You can save time inputting multiple Responses to answer questions presented in a worksheet using the Bulk Response feature. For example, in the Critical Systems ID Worksheet, the same response needs to be applied to a number of Topics and Questions in the Server Category Worksheet. Follow these steps to use the Bulk Response feature: After opening the worksheet, select the Bulk Entry Option.Then follow the steps below to setup the Bulk Entry within the Worksheet you are updating: A. Select the worksheet s Category page that should be updated using the Bulk Entry feature. B. Select the Servers or Workstations questions that you want to assign a Response. C. Select the list of available responses that you want to use for your Response entry. D. Select the specific Response from the list that you want to enter for the selected Servers or Workstations. E. Enter in a Note that you would like to assign to your Response for the selected Server or Workstation related questions. F. Enter the name of the Respondent that provided the selected Response. G. Select the Apply to Selected button to assign your selected Response to the selected Server or Workstation questions. The Response, Note, and Respondent you defined will be applied to the selected Server or Workstation listed in the Worksheet. H. View the assigned responses to verify the bulk entries are correct. 28
30 After you have verified that all of the responses you assigned are correct, select the Save button to save the updated worksheet. Then select the Close button to close the Worksheet. 29
HIPAA Compliance Module. Using the HIPAA Module without Inspector Instructions. User Guide RapidFire Tools, Inc. All rights reserved.
 HIPAA Compliance Module Using the HIPAA Module without Inspector Instructions User Guide 2017 RapidFire Tools, Inc. All rights reserved. V20180216 Contents Purpose of this Guide... 4 About Network Detective
HIPAA Compliance Module Using the HIPAA Module without Inspector Instructions User Guide 2017 RapidFire Tools, Inc. All rights reserved. V20180216 Contents Purpose of this Guide... 4 About Network Detective
PCI Compliance Assessment Module
 User Guide PCI Compliance Assessment Module Instructions to Perform a PCI Compliance Assessment V20180316 Network Detective PCI Compliance Module without Inspector User Guide Contents About the Network
User Guide PCI Compliance Assessment Module Instructions to Perform a PCI Compliance Assessment V20180316 Network Detective PCI Compliance Module without Inspector User Guide Contents About the Network
HIPAA Compliance Assessment Module
 Quick Start Guide HIPAA Compliance Assessment Module Instructions to Perform a HIPAA Compliance Assessment Performing a HIPAA Compliance Assessment 2 HIPAA Compliance Assessment Overview 2 What You Will
Quick Start Guide HIPAA Compliance Assessment Module Instructions to Perform a HIPAA Compliance Assessment Performing a HIPAA Compliance Assessment 2 HIPAA Compliance Assessment Overview 2 What You Will
PCI Compliance Assessment Module with Inspector
 Quick Start Guide PCI Compliance Assessment Module with Inspector Instructions to Perform a PCI Compliance Assessment Performing a PCI Compliance Assessment (with Inspector) 2 PCI Compliance Assessment
Quick Start Guide PCI Compliance Assessment Module with Inspector Instructions to Perform a PCI Compliance Assessment Performing a PCI Compliance Assessment (with Inspector) 2 PCI Compliance Assessment
Reporter User Guide RapidFire Tools, Inc. All rights reserved Ver 4T
 Reporter User Guide 2017 RapidFire Tools, Inc. All rights reserved 20171102 Ver 4T Contents Overview... 3 Components of the Reporter... 3 Reporter Appliance... 3 Network Detective Application... 3 Diagnostic
Reporter User Guide 2017 RapidFire Tools, Inc. All rights reserved 20171102 Ver 4T Contents Overview... 3 Components of the Reporter... 3 Reporter Appliance... 3 Network Detective Application... 3 Diagnostic
Inspector Software Appliance User Guide
 User Guide 2017 RapidFire Tools, Inc. All rights reserved 20170804 Ver 3V Contents Overview... 3 Components of the... 3... 3 Inspector Diagnostic Tool... 3 Network Detective Application... 3 Features...
User Guide 2017 RapidFire Tools, Inc. All rights reserved 20170804 Ver 3V Contents Overview... 3 Components of the... 3... 3 Inspector Diagnostic Tool... 3 Network Detective Application... 3 Features...
Remote Data Collector Installation and User Guide
 Remote Data Collector Installation and User Guide 2017 RapidFire Tools, Inc. All rights reserved. V20170207 Ver 1F Contents Purpose of this Guide... 2 System Requirements... 2 Remote Data Collector installation
Remote Data Collector Installation and User Guide 2017 RapidFire Tools, Inc. All rights reserved. V20170207 Ver 1F Contents Purpose of this Guide... 2 System Requirements... 2 Remote Data Collector installation
QUICK START GUIDE. SQL Server Assessment Module. Instructions to Perform a SQL Server Assessment 8/22/2018 4:45 PM
 QUICK START GUIDE SQL Server Assessment Module Instructions to Perform a SQL Server Assessment 8/22/2018 4:45 PM Network Detective SQL Server Assessment Module Quick Start Guide Contents Performing a SQL
QUICK START GUIDE SQL Server Assessment Module Instructions to Perform a SQL Server Assessment 8/22/2018 4:45 PM Network Detective SQL Server Assessment Module Quick Start Guide Contents Performing a SQL
Detector Service Delivery System (SDS) Version 3.0
 Detector Service Delivery System (SDS) Version 3.0 Detecting and Responding to IT Security Policy Violations Quick Start Guide 2018 RapidFire Tools, Inc. All rights reserved. V20180112 Contents Overview
Detector Service Delivery System (SDS) Version 3.0 Detecting and Responding to IT Security Policy Violations Quick Start Guide 2018 RapidFire Tools, Inc. All rights reserved. V20180112 Contents Overview
INSTALLATION GUIDE. Virtual Appliance for Inspector and Reporter 9/20/2018 1:32 PM
 INSTALLATION GUIDE Virtual Appliance for Inspector and Reporter 9/20/2018 1:32 PM Network Detective Virtual Appliance for Inspector and Reporter Installation Guide Contents Purpose of this Guide 4 RapidFire
INSTALLATION GUIDE Virtual Appliance for Inspector and Reporter 9/20/2018 1:32 PM Network Detective Virtual Appliance for Inspector and Reporter Installation Guide Contents Purpose of this Guide 4 RapidFire
Virtual Appliance Installation Guide
 Virtual Appliance Installation Guide 2017 RapidFire Tools, Inc. All rights reserved. V20171027 Ver 2M Contents Purpose of this Guide...3 System Requirements...3 Hyper-V installation System Requirements...3
Virtual Appliance Installation Guide 2017 RapidFire Tools, Inc. All rights reserved. V20171027 Ver 2M Contents Purpose of this Guide...3 System Requirements...3 Hyper-V installation System Requirements...3
EntraPass Installation Guide Kantech-OnBoard systems
 EntraPass Installation Guide Overview Purpose ExacqVision recorders now include Kantech EntraPass Corporate Edition software. The purpose of this document is to guide the technician or installer through
EntraPass Installation Guide Overview Purpose ExacqVision recorders now include Kantech EntraPass Corporate Edition software. The purpose of this document is to guide the technician or installer through
Moving HRtrack to a new computer
 First Reference Moving HRtrack to a new computer Process at a Glance Confirm the location of your HRtrack data Install HRtrack on the new computer Copy the HRtrack data folder from the old computer to
First Reference Moving HRtrack to a new computer Process at a Glance Confirm the location of your HRtrack data Install HRtrack on the new computer Copy the HRtrack data folder from the old computer to
EntraPass (W10) Installation Guide Kantech-OnBoard systems
 Overview Purpose ExacqVision recorders now include Kantech EntraPass Corporate Edition software. The purpose of this document is to guide the technician or installer through the process of installing and
Overview Purpose ExacqVision recorders now include Kantech EntraPass Corporate Edition software. The purpose of this document is to guide the technician or installer through the process of installing and
1. ECI Hosted Clients Installing Release 6.3 for the First Time (ECI Hosted) Upgrading to Release 6.3SP2 (ECI Hosted)
 1. ECI Hosted Clients........................................................................................... 2 1.1 Installing Release 6.3 for the First Time (ECI Hosted)...........................................................
1. ECI Hosted Clients........................................................................................... 2 1.1 Installing Release 6.3 for the First Time (ECI Hosted)...........................................................
Silk Performance Manager Installation and Setup Help
 Silk Performance Manager 18.5 Installation and Setup Help Micro Focus The Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK http://www.microfocus.com Copyright 2004-2017 Micro Focus. All rights reserved.
Silk Performance Manager 18.5 Installation and Setup Help Micro Focus The Lawn 22-30 Old Bath Road Newbury, Berkshire RG14 1QN UK http://www.microfocus.com Copyright 2004-2017 Micro Focus. All rights reserved.
PCLaw Installation and Upgrade Guide
 PCLaw Installation and Upgrade Guide Version 14.1 2015 LexisNexis. All rights reserved. Copyright and trademark LexisNexis, Lexis, and the Knowledge Burst logo are registered trademarks of Reed Elsevier
PCLaw Installation and Upgrade Guide Version 14.1 2015 LexisNexis. All rights reserved. Copyright and trademark LexisNexis, Lexis, and the Knowledge Burst logo are registered trademarks of Reed Elsevier
Dell License Manager Version 1.2 User s Guide
 Dell License Manager Version 1.2 User s Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your computer. CAUTION: A CAUTION indicates either
Dell License Manager Version 1.2 User s Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your computer. CAUTION: A CAUTION indicates either
QUICK START GUIDE. Exchange Assessment Module. Instructions to Perform an Exchange Assessment 8/22/2018 4:37 PM
 QUICK START GUIDE Assessment Module Instructions to Perform an Assessment 8/22/2018 4:37 PM Network Detective Assessment Module Quick Start Guide Contents Performing an Assessment 3 Assessment Overview
QUICK START GUIDE Assessment Module Instructions to Perform an Assessment 8/22/2018 4:37 PM Network Detective Assessment Module Quick Start Guide Contents Performing an Assessment 3 Assessment Overview
<Partner Name> <Partner Product> RSA SECURID ACCESS Implementation Guide. Pulse Connect Secure 8.x
 RSA SECURID ACCESS Implementation Guide Pulse Connect Secure 8.x Daniel R. Pintal, RSA Partner Engineering Last Modified: January 24 th, 2018 Solution Summary The Pulse
RSA SECURID ACCESS Implementation Guide Pulse Connect Secure 8.x Daniel R. Pintal, RSA Partner Engineering Last Modified: January 24 th, 2018 Solution Summary The Pulse
XIA Configuration Server
 XIA Configuration Server XIA Configuration Server v6 Cloud Services Quick Start Guide Tuesday, 20 May 2014 1 P a g e X I A C o n f i g u r a t i o n C l o u d S e r v i c e s Contents Overview... 3 Creating
XIA Configuration Server XIA Configuration Server v6 Cloud Services Quick Start Guide Tuesday, 20 May 2014 1 P a g e X I A C o n f i g u r a t i o n C l o u d S e r v i c e s Contents Overview... 3 Creating
SC-T35/SC-T45/SC-T46/SC-T47 ViewSonic Device Manager User Guide
 SC-T35/SC-T45/SC-T46/SC-T47 ViewSonic Device Manager User Guide Copyright and Trademark Statements 2014 ViewSonic Computer Corp. All rights reserved. This document contains proprietary information that
SC-T35/SC-T45/SC-T46/SC-T47 ViewSonic Device Manager User Guide Copyright and Trademark Statements 2014 ViewSonic Computer Corp. All rights reserved. This document contains proprietary information that
Configuring the SMA 500v Virtual Appliance
 Using the SMA 500v Virtual Appliance Configuring the SMA 500v Virtual Appliance Registering Your Appliance Using the 30-day Trial Version Upgrading Your Appliance Configuring the SMA 500v Virtual Appliance
Using the SMA 500v Virtual Appliance Configuring the SMA 500v Virtual Appliance Registering Your Appliance Using the 30-day Trial Version Upgrading Your Appliance Configuring the SMA 500v Virtual Appliance
1. Initial Setting and Installation of ActiveVisor... 1
 ActiveVisor Startup Guide 1 st Edition August, 2018 Contents 1. Initial Setting and Installation of ActiveVisor... 1 1.1 System Requirements... 1 1.2 Installation of ActiveVisor... 2 1.3 Initial Settings
ActiveVisor Startup Guide 1 st Edition August, 2018 Contents 1. Initial Setting and Installation of ActiveVisor... 1 1.1 System Requirements... 1 1.2 Installation of ActiveVisor... 2 1.3 Initial Settings
AT&T Global Network Client for Mac User s Guide Version 2.0.0
 Version 1.7.0 AT&T Global Network Client for Mac User s Guide Version 2.0.0 experience may vary. This document is not an offer, commitment, representation or warranty by AT&T and is subject to change..
Version 1.7.0 AT&T Global Network Client for Mac User s Guide Version 2.0.0 experience may vary. This document is not an offer, commitment, representation or warranty by AT&T and is subject to change..
VMware Mirage Web Manager Guide
 Mirage 5.3 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this document,
Mirage 5.3 This document supports the version of each product listed and supports all subsequent versions until the document is replaced by a new edition. To check for more recent editions of this document,
Quick Start Guide TABLE OF CONTENTS COMMCELL ARCHITECTURE OVERVIEW COMMCELL SOFTWARE DEPLOYMENT INSTALL THE COMMSERVE SOFTWARE
 Page 1 of 35 Quick Start Guide TABLE OF CONTENTS This Quick Start Guide is designed to help you install and use a CommCell configuration to which you can later add other components. COMMCELL ARCHITECTURE
Page 1 of 35 Quick Start Guide TABLE OF CONTENTS This Quick Start Guide is designed to help you install and use a CommCell configuration to which you can later add other components. COMMCELL ARCHITECTURE
Oracle Eloqua Sales Tools for Microsoft Outlook. User Guide
 Oracle Eloqua Sales Tools for Microsoft Outlook User Guide 2018 Oracle Corporation. All rights reserved 21-Sep-2018 Contents 1 Oracle Eloqua Sales Tools for Microsoft Outlook 3 2 Frequently asked questions
Oracle Eloqua Sales Tools for Microsoft Outlook User Guide 2018 Oracle Corporation. All rights reserved 21-Sep-2018 Contents 1 Oracle Eloqua Sales Tools for Microsoft Outlook 3 2 Frequently asked questions
Upgrading Software and Firmware
 APPENDIXB This appendix describes how to upgrade or reinstall the Cisco PAM server software, desktop client software, and Gateway module firmware. Contents Upgrade Notes for Release 1.1.0, page B-2 Upgrading
APPENDIXB This appendix describes how to upgrade or reinstall the Cisco PAM server software, desktop client software, and Gateway module firmware. Contents Upgrade Notes for Release 1.1.0, page B-2 Upgrading
Interact2 Help and Support
 Exporting and Importing an Interact2 Site Best practice for transferring subject content into a new session subject site is: Export/Import process -> Publish Subject Outline -> Merging (only if required).
Exporting and Importing an Interact2 Site Best practice for transferring subject content into a new session subject site is: Export/Import process -> Publish Subject Outline -> Merging (only if required).
exacqvision-entrapass (W10) Installation Guide
 1 Overview Purpose ExacqVision recorders now include Kantech Entrapass CE software. The purpose of this document is to guide the technician or installer through the process of installing and registering
1 Overview Purpose ExacqVision recorders now include Kantech Entrapass CE software. The purpose of this document is to guide the technician or installer through the process of installing and registering
Dell Storage Compellent Integration Tools for VMware
 Dell Storage Compellent Integration Tools for VMware Version 4.0 Administrator s Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your
Dell Storage Compellent Integration Tools for VMware Version 4.0 Administrator s Guide Notes, Cautions, and Warnings NOTE: A NOTE indicates important information that helps you make better use of your
DataCollect Administrative Tools Supporting DataCollect (CMDT 3900) Version 3.0.0
 Administrator Manual DataCollect Administrative Tools Supporting DataCollect (CMDT 3900) Version 3.0.0 P/N 15V-090-00054-100 Revision A SKF is a registered trademark of the SKF Group. All other trademarks
Administrator Manual DataCollect Administrative Tools Supporting DataCollect (CMDT 3900) Version 3.0.0 P/N 15V-090-00054-100 Revision A SKF is a registered trademark of the SKF Group. All other trademarks
Anchor User Guide. Presented by: Last Revised: August 07, 2017
 Anchor User Guide Presented by: Last Revised: August 07, 2017 TABLE OF CONTENTS GETTING STARTED... 1 How to Log In to the Web Portal... 1 How to Manage Account Settings... 2 How to Configure Two-Step Authentication...
Anchor User Guide Presented by: Last Revised: August 07, 2017 TABLE OF CONTENTS GETTING STARTED... 1 How to Log In to the Web Portal... 1 How to Manage Account Settings... 2 How to Configure Two-Step Authentication...
Desktop & Laptop Edition
 Desktop & Laptop Edition USER MANUAL For Mac OS X Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Mac, Leopard, Snow Leopard, Lion and Mountain Lion
Desktop & Laptop Edition USER MANUAL For Mac OS X Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Mac, Leopard, Snow Leopard, Lion and Mountain Lion
Comodo One Software Version 3.26
 rat Comodo One Software Version 3.26 Network Assessment Tool Administrator Guide Guide Version 1.3.113018 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction
rat Comodo One Software Version 3.26 Network Assessment Tool Administrator Guide Guide Version 1.3.113018 Comodo Security Solutions 1255 Broad Street Clifton, NJ 07013 Table of Contents 1 Introduction
High Availability Enabling SSL Database Migration Auto Backup and Auto Update Mail Server and Proxy Settings Support...
 Quick Start Guide Table of Contents Overview... 4 Deployment... 4 System Requirements... 4 Installation... 6 Working with AD360... 8 Starting AD360... 8 Launching AD360 client... 9 Stopping AD360... 9
Quick Start Guide Table of Contents Overview... 4 Deployment... 4 System Requirements... 4 Installation... 6 Working with AD360... 8 Starting AD360... 8 Launching AD360 client... 9 Stopping AD360... 9
Symantec ediscovery Platform
 Symantec ediscovery Platform Native Viewer (ActiveX) Installation Guide 7.1.5 Symantec ediscovery Platform : Native Viewer (ActiveX) Installation Guide The software described in this book is furnished
Symantec ediscovery Platform Native Viewer (ActiveX) Installation Guide 7.1.5 Symantec ediscovery Platform : Native Viewer (ActiveX) Installation Guide The software described in this book is furnished
AT&T Global Network Client for Mac User s Guide Version 1.7.3
 Version 1.7.0 AT&T Global Network Client for Mac User s Guide Version 1.7.3 experience may vary. This document is not an offer, commitment, representation or warranty by AT&T and is subject to change..
Version 1.7.0 AT&T Global Network Client for Mac User s Guide Version 1.7.3 experience may vary. This document is not an offer, commitment, representation or warranty by AT&T and is subject to change..
Network DK2 DESkey Installation Guide
 VenturiOne Getting Started Network DK2 DESkey Installation Guide PD-061.2.306 DESkey Network Server Manual Rev A Applied Cytometry CONTENTS 1 DK2 Network Server Overview... 2 2 DK2 Network Server Installation...
VenturiOne Getting Started Network DK2 DESkey Installation Guide PD-061.2.306 DESkey Network Server Manual Rev A Applied Cytometry CONTENTS 1 DK2 Network Server Overview... 2 2 DK2 Network Server Installation...
UNICORN Administration and Technical Manual
 UNICORN 7.0.2 Administration and Technical Manual Table of Contents Table of Contents 1 Introduction... 1.1 Administrator functions overview... 1.2 Network terms and concepts... 1.3 Network environment...
UNICORN 7.0.2 Administration and Technical Manual Table of Contents Table of Contents 1 Introduction... 1.1 Administrator functions overview... 1.2 Network terms and concepts... 1.3 Network environment...
Backup everything to cloud / local storage. CloudBacko Home. Essential steps to get started
 CloudBacko Home Essential steps to get started Last update: December 2, 2016 Index Step 1). Installation Step 2). Configure a new backup set, trigger a backup manually Step 3). Configure other backup set
CloudBacko Home Essential steps to get started Last update: December 2, 2016 Index Step 1). Installation Step 2). Configure a new backup set, trigger a backup manually Step 3). Configure other backup set
Sync User Guide. Powered by Axient Anchor
 Sync Powered by Axient Anchor TABLE OF CONTENTS End... Error! Bookmark not defined. Last Revised: Wednesday, October 10, 2018... Error! Bookmark not defined. Table of Contents... 2 Getting Started... 7
Sync Powered by Axient Anchor TABLE OF CONTENTS End... Error! Bookmark not defined. Last Revised: Wednesday, October 10, 2018... Error! Bookmark not defined. Table of Contents... 2 Getting Started... 7
Dell EMC License Manager Version 1.5 User's Guide
 Dell EMC License Manager Version 1.5 User's Guide Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates
Dell EMC License Manager Version 1.5 User's Guide Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates
Installation Guide Worksoft Certify
 Installation Guide Worksoft Certify Worksoft, Inc. 15851 Dallas Parkway, Suite 855 Addison, TX 75001 www.worksoft.com 866-836-1773 Worksoft Certify Installation Guide Version 9.0.3 Copyright 2017 by Worksoft,
Installation Guide Worksoft Certify Worksoft, Inc. 15851 Dallas Parkway, Suite 855 Addison, TX 75001 www.worksoft.com 866-836-1773 Worksoft Certify Installation Guide Version 9.0.3 Copyright 2017 by Worksoft,
To upgrade to the i-vu v6.0 application
 i-vu Application Upgrade Guide to v6.0 CARRIER CORPORATION 2014 A member of the United Technologies Corporation family Stock symbol UTX Catalog No. 11-808-493-01 3/21/2014 Table of Contents To upgrade
i-vu Application Upgrade Guide to v6.0 CARRIER CORPORATION 2014 A member of the United Technologies Corporation family Stock symbol UTX Catalog No. 11-808-493-01 3/21/2014 Table of Contents To upgrade
Computer Based Examinations
 Computer Based Examinations CBE V24.0 Installation Instructions Existing CBE Centres This document is intended for existing CBE centres that currently have ACCA CBE software installed, and are installing
Computer Based Examinations CBE V24.0 Installation Instructions Existing CBE Centres This document is intended for existing CBE centres that currently have ACCA CBE software installed, and are installing
GRS Enterprise Synchronization Tool
 GRS Enterprise Synchronization Tool Last Revised: Thursday, April 05, 2018 Page i TABLE OF CONTENTS Anchor End User Guide... Error! Bookmark not defined. Last Revised: Monday, March 12, 2018... 1 Table
GRS Enterprise Synchronization Tool Last Revised: Thursday, April 05, 2018 Page i TABLE OF CONTENTS Anchor End User Guide... Error! Bookmark not defined. Last Revised: Monday, March 12, 2018... 1 Table
1 Overview. 2 Installation. exacqvision-entrapass Installation Guide.
 1 Overview Purpose ExacqVision recorders now include Kantech Entrapass CE software. The purpose of this document is to guide the technician or installer through the process of installing and registering
1 Overview Purpose ExacqVision recorders now include Kantech Entrapass CE software. The purpose of this document is to guide the technician or installer through the process of installing and registering
mce100+ getting started guide Install mce100+ The disc will run and display the below screen: Choose Install mce to continue
 content between two the phonebook records of a content from a 1. Insert the mce CD. 2. Choose the Run mce Setup button. The disc will run and display the below screen: Choose mce to continue 5. Ready to
content between two the phonebook records of a content from a 1. Insert the mce CD. 2. Choose the Run mce Setup button. The disc will run and display the below screen: Choose mce to continue 5. Ready to
ROCK-POND REPORTING 2.1
 ROCK-POND REPORTING 2.1 Installation and Setup Guide Revised on 09/25/2014 TABLE OF CONTENTS ROCK-POND REPORTING 2.1... 1 SUPPORT FROM ROCK-POND SOLUTIONS... 2 ROCK-POND REPORTING OVERVIEW... 2 INFRASTRUCTURE
ROCK-POND REPORTING 2.1 Installation and Setup Guide Revised on 09/25/2014 TABLE OF CONTENTS ROCK-POND REPORTING 2.1... 1 SUPPORT FROM ROCK-POND SOLUTIONS... 2 ROCK-POND REPORTING OVERVIEW... 2 INFRASTRUCTURE
LiveNX Upgrade Guide from v5.1.2 to v Windows
 LIVEACTION, INC. LiveNX Upgrade Guide from v5.1.2 to v5.1.3 - Windows UPGRADE LiveAction, Inc. 3500 Copyright WEST BAYSHORE 2016 LiveAction, ROAD Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the
LIVEACTION, INC. LiveNX Upgrade Guide from v5.1.2 to v5.1.3 - Windows UPGRADE LiveAction, Inc. 3500 Copyright WEST BAYSHORE 2016 LiveAction, ROAD Inc. All rights reserved. LiveAction, LiveNX, LiveUX, the
Rockfast Revelation Upgrade Procedure. (Rockfast Revelation version 547+)
 Rockfast Revelation Upgrade Procedure (Rockfast Revelation version 547+) August 2015 Pre-upgrade checklist Local administrator rights The user performing the upgrade has local administrator privileges
Rockfast Revelation Upgrade Procedure (Rockfast Revelation version 547+) August 2015 Pre-upgrade checklist Local administrator rights The user performing the upgrade has local administrator privileges
PAN 802.1x Connector Application Installation Guide
 PAN 802.1x Connector Application Installation Guide Version 1.2 "Copyright CodeCentrix. All rights reserved 2015. Version 1.2 Contact Information CodeCentrix www.codecentrix.co.za/contact Email: info@codecentrix.co.za
PAN 802.1x Connector Application Installation Guide Version 1.2 "Copyright CodeCentrix. All rights reserved 2015. Version 1.2 Contact Information CodeCentrix www.codecentrix.co.za/contact Email: info@codecentrix.co.za
Restore Online Backup Manager Guide
 Restore Online Backup Manager Guide To begin using your new Restore service you will need to install the client which can be downloaded via the links below: Windows - http://fastnet.co.uk/downloads/obm-win.exe
Restore Online Backup Manager Guide To begin using your new Restore service you will need to install the client which can be downloaded via the links below: Windows - http://fastnet.co.uk/downloads/obm-win.exe
enicq 5 Upgrade Guide
 Vermont Oxford Network enicq 5 Documentation enicq 5 Upgrade Guide Release 2.2 Published August 2016 2016 Vermont Oxford Network. All Rights Reserved. enicq 5 Upgrade Guide Introduction This document describes
Vermont Oxford Network enicq 5 Documentation enicq 5 Upgrade Guide Release 2.2 Published August 2016 2016 Vermont Oxford Network. All Rights Reserved. enicq 5 Upgrade Guide Introduction This document describes
SecureGuard VMS. SecureGuard All-In-One Quick Install Guide V. 2.5
 SecureGuard VMS Quick Install Guide V. 2.5 9/30/2018 2 Table of Contents Purpose... 3 Installation... 3 Setup... 4 Startup & Live View... 26 3 Purpose This is a step-by-step guide to installing the current
SecureGuard VMS Quick Install Guide V. 2.5 9/30/2018 2 Table of Contents Purpose... 3 Installation... 3 Setup... 4 Startup & Live View... 26 3 Purpose This is a step-by-step guide to installing the current
Client Installation and User's Guide
 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1.1 Client Installation and User's Guide SC27-2809-04 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1.1 Client Installation
IBM Tivoli Storage Manager FastBack for Workstations Version 7.1.1 Client Installation and User's Guide SC27-2809-04 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1.1 Client Installation
Equitrac Embedded for Kyocera Mita. Setup Guide Equitrac Corporation Equitrac Corporation
 Equitrac Embedded for Kyocera Mita 1.3 Setup Guide 2012 Equitrac Corporation 2012 Equitrac Corporation Equitrac Embedded for Kyocera Mita Setup Guide Document Revision History Revision Date Revision List
Equitrac Embedded for Kyocera Mita 1.3 Setup Guide 2012 Equitrac Corporation 2012 Equitrac Corporation Equitrac Embedded for Kyocera Mita Setup Guide Document Revision History Revision Date Revision List
This guide details the deployment and initial configuration necessary to maximize the value of JetAdvantage Insights.
 HP JetAdvantage Insights Deployment Guide This guide details the deployment and initial configuration necessary to maximize the value of JetAdvantage Insights. 1. Overview HP JetAdvantage Insights provides
HP JetAdvantage Insights Deployment Guide This guide details the deployment and initial configuration necessary to maximize the value of JetAdvantage Insights. 1. Overview HP JetAdvantage Insights provides
Server Edition USER MANUAL. For Mac OS X
 Server Edition USER MANUAL For Mac OS X Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Mac, Leopard, Snow Leopard, Lion and Mountain Lion are registered
Server Edition USER MANUAL For Mac OS X Copyright Notice & Proprietary Information Redstor Limited, 2016. All rights reserved. Trademarks - Mac, Leopard, Snow Leopard, Lion and Mountain Lion are registered
VMware AirWatch Database Migration Guide A sample procedure for migrating your AirWatch database
 VMware AirWatch Database Migration Guide A sample procedure for migrating your AirWatch database For multiple versions Have documentation feedback? Submit a Documentation Feedback support ticket using
VMware AirWatch Database Migration Guide A sample procedure for migrating your AirWatch database For multiple versions Have documentation feedback? Submit a Documentation Feedback support ticket using
User Agent Preparing the Windows Environment and Installing the User Agent. How-To
 User Agent 1.1.5 Preparing the Windows Environment and Installing the User Agent How-To CONTENTS Introduction to the User Agent... 2 Selecting the User Account to Run the User Agent... 3 Setting Access
User Agent 1.1.5 Preparing the Windows Environment and Installing the User Agent How-To CONTENTS Introduction to the User Agent... 2 Selecting the User Account to Run the User Agent... 3 Setting Access
Dell Storage Integration Tools for VMware
 Dell Storage Integration Tools for VMware Version 4.1 Administrator s Guide Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION:
Dell Storage Integration Tools for VMware Version 4.1 Administrator s Guide Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION:
License Manager Client
 License Manager Client Operations Guide NEC NEC Corporation of America November 2010 NDA-30899, Revision 6 Liability Disclaimer NEC Corporation of America reserves the right to change the specifications,
License Manager Client Operations Guide NEC NEC Corporation of America November 2010 NDA-30899, Revision 6 Liability Disclaimer NEC Corporation of America reserves the right to change the specifications,
efolder BDR for Veeam VMware Continuity Cloud Guide
 efolder BDR for Veeam VMware Continuity Cloud Guide Setup Continuity Cloud Import Backup Copy Job Restore Your VM Accessing the Continuity Cloud Host uh6 efolder BDR Guide for Veeam Page 1 of 36 INTRODUCTION
efolder BDR for Veeam VMware Continuity Cloud Guide Setup Continuity Cloud Import Backup Copy Job Restore Your VM Accessing the Continuity Cloud Host uh6 efolder BDR Guide for Veeam Page 1 of 36 INTRODUCTION
Quick Start Guide. Kaseya 2009
 Agent Configuration and Deployment Quick Start Guide Kaseya 2009 February 13, 2010 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector
Agent Configuration and Deployment Quick Start Guide Kaseya 2009 February 13, 2010 About Kaseya Kaseya is a global provider of IT automation software for IT Solution Providers and Public and Private Sector
Application Notes for Installing and Configuring Avaya Control Manager Enterprise Edition in a High Availability mode.
 Application Notes for Installing and Configuring Avaya Control Manager Enterprise Edition in a High Availability mode. Abstract This Application Note describes the steps required for installing and configuring
Application Notes for Installing and Configuring Avaya Control Manager Enterprise Edition in a High Availability mode. Abstract This Application Note describes the steps required for installing and configuring
Double click the downloaded installation file (MPMLink.exe) to initiate the installation.
 MPM Link Quick Start Installing MPM Link. Make sure your PC has an active Internet connection. MPMLink prerequisites may be required and those will be downloaded automatically from a Microsoft site. Double
MPM Link Quick Start Installing MPM Link. Make sure your PC has an active Internet connection. MPMLink prerequisites may be required and those will be downloaded automatically from a Microsoft site. Double
Features - SRM Windows File System Agent
 Page 1 of 53 Features - SRM Windows File System Agent Table of Contents Overview System Requirements - SRM Windows File System Agent Installation Install the SRM Windows File System Agent Install the SRM
Page 1 of 53 Features - SRM Windows File System Agent Table of Contents Overview System Requirements - SRM Windows File System Agent Installation Install the SRM Windows File System Agent Install the SRM
Enterprise Vault.cloud CloudLink Google Account Synchronization Guide. CloudLink to 4.0.3
 Enterprise Vault.cloud CloudLink Google Account Synchronization Guide CloudLink 4.0.1 to 4.0.3 Enterprise Vault.cloud: CloudLink Google Account Synchronization Guide Last updated: 2018-06-08. Legal Notice
Enterprise Vault.cloud CloudLink Google Account Synchronization Guide CloudLink 4.0.1 to 4.0.3 Enterprise Vault.cloud: CloudLink Google Account Synchronization Guide Last updated: 2018-06-08. Legal Notice
IQSweb Installation Instructions Version 5.0
 IQSweb Installation Instructions Version 5.0 Contents Additional References... 3 IQSweb ROSS Connection... 3 IQSweb V5.0 Install/Upgrade Scenarios... 4 IQSweb Configuration Options... 5 A. Single Computer/Server
IQSweb Installation Instructions Version 5.0 Contents Additional References... 3 IQSweb ROSS Connection... 3 IQSweb V5.0 Install/Upgrade Scenarios... 4 IQSweb Configuration Options... 5 A. Single Computer/Server
QSalesData User Guide
 QSalesData User Guide Updated: 11/10/11 Installing the QSalesData Software... 2 Licensing the QSalesData Product... 3 Build QSalesData fields in ACT Step 2 of Install Checklist... 4 Adding the QB Data
QSalesData User Guide Updated: 11/10/11 Installing the QSalesData Software... 2 Licensing the QSalesData Product... 3 Build QSalesData fields in ACT Step 2 of Install Checklist... 4 Adding the QB Data
1.0. Quest Enterprise Reporter Discovery Manager USER GUIDE
 1.0 Quest Enterprise Reporter Discovery Manager USER GUIDE 2012 Quest Software. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide
1.0 Quest Enterprise Reporter Discovery Manager USER GUIDE 2012 Quest Software. ALL RIGHTS RESERVED. This guide contains proprietary information protected by copyright. The software described in this guide
AccessData FTK Quick Installation Guide
 AccessData FTK Quick Installation Guide Document date: May 20, 2014 2014 AccessData Group, Inc. All rights reserved. No part of this publication may be reproduced, photocopied, stored on a retrieval system,
AccessData FTK Quick Installation Guide Document date: May 20, 2014 2014 AccessData Group, Inc. All rights reserved. No part of this publication may be reproduced, photocopied, stored on a retrieval system,
BEST PRACTICES. Checkpoint Engage with AdvanceFlow
 BEST PRACTICES Checkpoint Engage with AdvanceFlow Table of Contents Using Checkpoint Engage... 3 Add New Client Engagement... 4 Set up the New Customer Engagement... 6 Master Engagement Templates... 9
BEST PRACTICES Checkpoint Engage with AdvanceFlow Table of Contents Using Checkpoint Engage... 3 Add New Client Engagement... 4 Set up the New Customer Engagement... 6 Master Engagement Templates... 9
BackupVault Desktop & Laptop Edition. USER MANUAL For Microsoft Windows
 BackupVault Desktop & Laptop Edition USER MANUAL For Microsoft Windows Copyright Notice & Proprietary Information Blueraq Networks Ltd, 2017. All rights reserved. Trademarks - Microsoft, Windows, Microsoft
BackupVault Desktop & Laptop Edition USER MANUAL For Microsoft Windows Copyright Notice & Proprietary Information Blueraq Networks Ltd, 2017. All rights reserved. Trademarks - Microsoft, Windows, Microsoft
LDAP/AD v1.0 User Guide
 LDAP/AD v1.0 User Guide For v6.5 systems Catalog No. 11-808-615-01 Important changes are listed in Document revision history at the end of this document. UTC 2017. throughout the world. All trademarks
LDAP/AD v1.0 User Guide For v6.5 systems Catalog No. 11-808-615-01 Important changes are listed in Document revision history at the end of this document. UTC 2017. throughout the world. All trademarks
EN Engineering s File Transfer System Client User Manual
 EN Engineering s File Transfer System Client User Manual 05/30/2017 1 Contents 1. Introduction & Purpose... 3 2. User Access... 3 2.1. User Accounts... 3 2.2. Logging In to ENsured... 3 2.3. Changing a
EN Engineering s File Transfer System Client User Manual 05/30/2017 1 Contents 1. Introduction & Purpose... 3 2. User Access... 3 2.1. User Accounts... 3 2.2. Logging In to ENsured... 3 2.3. Changing a
BMS Managing Users in Modelpedia V1.1
 BMS 3.2.0 Managing Users in Modelpedia V1.1 Version Control Version Number Purpose/Change Author Date 1.0 Initial published version Gillian Dass 26/10/2017 1.1 Changes to User roles Gillian Dass 14/11/2017
BMS 3.2.0 Managing Users in Modelpedia V1.1 Version Control Version Number Purpose/Change Author Date 1.0 Initial published version Gillian Dass 26/10/2017 1.1 Changes to User roles Gillian Dass 14/11/2017
CDP Data Center Console User Guide CDP Data Center Console User Guide Version
 CDP Data Center Console User Guide CDP Data Center Console User Guide Version 3.18.2 1 README FIRST Welcome to the R1Soft CDP Data Center Console User Guide The purpose of this manual is to provide you
CDP Data Center Console User Guide CDP Data Center Console User Guide Version 3.18.2 1 README FIRST Welcome to the R1Soft CDP Data Center Console User Guide The purpose of this manual is to provide you
INSIGHT Installation Instructions
 This is the New Icon that will appear on your computer screen after the INSIGHT v8.1 software is installed. IMPORTANT: These instructions pertain to version 8.1.29. INSIGHT v8.1.29 requires Windows 8,
This is the New Icon that will appear on your computer screen after the INSIGHT v8.1 software is installed. IMPORTANT: These instructions pertain to version 8.1.29. INSIGHT v8.1.29 requires Windows 8,
Version 6.3 Upgrade Guide
 Version 6.3 Upgrade Guide Copyright 2016 Manufacturing Information Systems, Inc. 217-4 Maxham Meadow Way Woodstock, Vermont 05091 MISys and the MISys logo are registered trademarks of Manufacturing Information
Version 6.3 Upgrade Guide Copyright 2016 Manufacturing Information Systems, Inc. 217-4 Maxham Meadow Way Woodstock, Vermont 05091 MISys and the MISys logo are registered trademarks of Manufacturing Information
McAfee File and Removable Media Protection Product Guide
 McAfee File and Removable Media Protection 5.0.8 Product Guide COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator, McAfee
McAfee File and Removable Media Protection 5.0.8 Product Guide COPYRIGHT Copyright 2018 McAfee, LLC TRADEMARK ATTRIBUTIONS McAfee and the McAfee logo, McAfee Active Protection, epolicy Orchestrator, McAfee
penelope case management software AUTHENTICATION GUIDE v4.4 and higher
 penelope case management software AUTHENTICATION GUIDE v4.4 and higher Last modified: August 9, 2016 TABLE OF CONTENTS Authentication: The basics... 4 About authentication... 4 SSO authentication... 4
penelope case management software AUTHENTICATION GUIDE v4.4 and higher Last modified: August 9, 2016 TABLE OF CONTENTS Authentication: The basics... 4 About authentication... 4 SSO authentication... 4
Microsoft Office Groove Server Groove Manager. Domain Administrator s Guide
 Microsoft Office Groove Server 2007 Groove Manager Domain Administrator s Guide Copyright Information in this document, including URL and other Internet Web site references, is subject to change without
Microsoft Office Groove Server 2007 Groove Manager Domain Administrator s Guide Copyright Information in this document, including URL and other Internet Web site references, is subject to change without
Installation Manual. Fleet Maintenance Software. Version 6.4
 Fleet Maintenance Software Installation Manual Version 6.4 6 Terri Lane, Suite 700 Burlington, NJ 08016 (609) 747-8800 Fax (609) 747-8801 Dossier@dossiersystemsinc.com www.dossiersystemsinc.com Copyright
Fleet Maintenance Software Installation Manual Version 6.4 6 Terri Lane, Suite 700 Burlington, NJ 08016 (609) 747-8800 Fax (609) 747-8801 Dossier@dossiersystemsinc.com www.dossiersystemsinc.com Copyright
INSTALLATION GUIDE. Trimble PipeDesigner 3D Software
 INSTALLATION GUIDE Trimble PipeDesigner 3D Software Revision A May 2015 F Englewood Office Trimble Navigation Limited 116 Inverness Drive East, Suite 210 Englewood, Colorado 80112 (800) 234-3758 Copyright
INSTALLATION GUIDE Trimble PipeDesigner 3D Software Revision A May 2015 F Englewood Office Trimble Navigation Limited 116 Inverness Drive East, Suite 210 Englewood, Colorado 80112 (800) 234-3758 Copyright
Version 2.3 User Guide
 V Mware vcloud Usage Meter Version 2.3 User Guide 2012 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual property laws. This product is covered
V Mware vcloud Usage Meter Version 2.3 User Guide 2012 VMware, Inc. All rights reserved. This product is protected by U.S. and international copyright and intellectual property laws. This product is covered
Delphi Workstation Setup Instructions. June 3, 1009
 Delphi 9.5.2 Workstation Setup Instructions June 3, 1009 Copyright 2009 Newmarket International, Inc. All rights reserved. The information in this document is confidential and proprietary to Newmarket
Delphi 9.5.2 Workstation Setup Instructions June 3, 1009 Copyright 2009 Newmarket International, Inc. All rights reserved. The information in this document is confidential and proprietary to Newmarket
Multi-Sponsor Environment. SAS Clinical Trial Data Transparency User Guide
 Multi-Sponsor Environment SAS Clinical Trial Data Transparency User Guide Version 6.0 01 December 2017 Contents Contents 1 Overview...1 2 Setting up Your Account...3 2.1 Completing the Initial Email and
Multi-Sponsor Environment SAS Clinical Trial Data Transparency User Guide Version 6.0 01 December 2017 Contents Contents 1 Overview...1 2 Setting up Your Account...3 2.1 Completing the Initial Email and
Perceptive TransForm E-Forms Manager
 Perceptive TransForm E-Forms Manager Installation and Setup Guide Version: 8.x Date: February 2017 2016-2017 Lexmark. All rights reserved. Lexmark is a trademark of Lexmark International Inc., registered
Perceptive TransForm E-Forms Manager Installation and Setup Guide Version: 8.x Date: February 2017 2016-2017 Lexmark. All rights reserved. Lexmark is a trademark of Lexmark International Inc., registered
ForeScout Extended Module for Advanced Compliance
 ForeScout Extended Module for Advanced Compliance Version 1.2 Table of Contents About Advanced Compliance Integration... 4 Use Cases... 4 Additional Documentation... 6 About This Module... 6 About Support
ForeScout Extended Module for Advanced Compliance Version 1.2 Table of Contents About Advanced Compliance Integration... 4 Use Cases... 4 Additional Documentation... 6 About This Module... 6 About Support
Pontem Check for Updates Guide
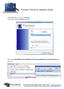 Pontem Check for Updates Guide STEP ONE: Back Up Your Database Log into your Pontem database as usual.. Next, select File Maintenance Backup for the Pontem application you wish to back up from the menu.
Pontem Check for Updates Guide STEP ONE: Back Up Your Database Log into your Pontem database as usual.. Next, select File Maintenance Backup for the Pontem application you wish to back up from the menu.
ForeScout Extended Module for Tenable Vulnerability Management
 ForeScout Extended Module for Tenable Vulnerability Management Version 2.7.1 Table of Contents About Tenable Vulnerability Management Module... 4 Compatible Tenable Vulnerability Products... 4 About Support
ForeScout Extended Module for Tenable Vulnerability Management Version 2.7.1 Table of Contents About Tenable Vulnerability Management Module... 4 Compatible Tenable Vulnerability Products... 4 About Support
BEST PRACTICES. Checkpoint Engage with AdvanceFlow
 BEST PRACTICES Checkpoint Engage with AdvanceFlow Table of Contents Table of Contents... 2 Using Checkpoint Engage... 3 Add New Client Engagement... 3 Set up the New Customer Engagement... 6 Master Engagement
BEST PRACTICES Checkpoint Engage with AdvanceFlow Table of Contents Table of Contents... 2 Using Checkpoint Engage... 3 Add New Client Engagement... 3 Set up the New Customer Engagement... 6 Master Engagement
DSS User Guide. End User Guide. - i -
 DSS User Guide End User Guide - i - DSS User Guide Table of Contents End User Guide... 1 Table of Contents... 2 Part 1: Getting Started... 1 How to Log in to the Web Portal... 1 How to Manage Account Settings...
DSS User Guide End User Guide - i - DSS User Guide Table of Contents End User Guide... 1 Table of Contents... 2 Part 1: Getting Started... 1 How to Log in to the Web Portal... 1 How to Manage Account Settings...
version 5.4 Installation Guide
 version 5.4 Installation Guide Document Release Date: February 9, 2012 www.phdvirtual.com Legal Notices PHD Virtual Backup for Citrix XenServer Installation Guide Copyright 2010-2012 PHD Virtual Technologies
version 5.4 Installation Guide Document Release Date: February 9, 2012 www.phdvirtual.com Legal Notices PHD Virtual Backup for Citrix XenServer Installation Guide Copyright 2010-2012 PHD Virtual Technologies
Client Installation and User's Guide
 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1 Client Installation and User's Guide SC27-2809-03 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1 Client Installation
IBM Tivoli Storage Manager FastBack for Workstations Version 7.1 Client Installation and User's Guide SC27-2809-03 IBM Tivoli Storage Manager FastBack for Workstations Version 7.1 Client Installation
NOTE: Single user and network installation is the same. Network users will only have to download and install the program once.
 Dear TaxTime USA Customer, Thank you for ordering TaxTime's 941/MI Unemployment Express 2013. Please print this for easy reference of download and program registration instructions. NOTE: Single user and
Dear TaxTime USA Customer, Thank you for ordering TaxTime's 941/MI Unemployment Express 2013. Please print this for easy reference of download and program registration instructions. NOTE: Single user and
