Computing Resources. at the University of Pittsburgh Tuesday, June 27, 2017
|
|
|
- Gavin Freeman
- 6 years ago
- Views:
Transcription
1 Computing Resources at the University of Pittsburgh Tuesday, June 27, 2017
2 Who We Are Computing Services & Systems Development (CSSD) provides computing resources at the University for students, faculty, and staff Technology Help Computer Accounts Software Network Access Security Services Telecommunications Services
3 Where to Find Us Information Technology Web site: technology.pitt.edu Learn about our services Submit a request for assistance Obtain security tools and information Review computing guidelines Obtain software
4 The Information Technology Web site technology.pitt.edu
5 Getting started for new Faculty and Staff How do I get my computer account? What about ? What s My Pitt? How can I get software? How do I protect my computer? How can I stay informed? Where can I find help?
6 New Faculty and Staff Information Technology Web site technology.pitt.edu/newstaff
7 How to Get Help Technology Help Desk Get answers to technology-related questions. Staffed 24 hours a day, 7 days a week. Phone: HELP (4357)
8 How to Get Help Technical Support Desk at the University Store on Fifth Get walk-in computer assistance: Connecting to PittNet. Configuring your mobile device for or Wireless PittNet. Software purchases and installations. Changing your password.
9 Your University Computing Account Automatically created when you are hired Your username and password provide access to University computing resources My Pitt PittNet and the Internet My Pitt (my.pitt.edu) Change your password immediately
10 Your University Computing Account Manage Your Account at My Pitt (my.pitt.edu) Manage your account password Set your preferences Edit your contact information
11 Managing Your Account Online at my.pitt.edu
12 Managing Your Account Online
13 Managing Your Account Online
14 Managing Your Account Online
15 Managing Your Account Online
16 Password Tips Protect Your Password Keep your password secret. Don t write down your password in an easy-to-find location. Change your password periodically. Use a strong password: Eight to 14 characters Combines letters, numbers, special characters Don t use guessable words
17 Password Tips Good passwords 4Pitt2Go# 444??141A 2Gud2BTru# Bad passwords Pittsburgh Panthers or Steelers Abc123 or asdfg July41966 Your Self-Service Password Reset at My Pitt (my.pitt.edu)
18 Multifactor Authentication at Pitt Protects Your Privacy Provides another layer of security to your online accounts when using Pitt Passport.
19 My Pitt Your University address: My Pitt . Access from your desktop, laptop, or smartphone. Preferences Change where you would like to receive your My Pitt . Create Aliases.
20 Setting Preferences
21 Setting Preferences
22 Setting Preferences
23 Software Distribution Services Software for Faculty and Staff More than 125 software packages are available at no cost or for purchase at reduced costs. View available software at technology.pitt.edu. Purchase select software at the Technical Support Desk at the University Store on Fifth. my.pitt.edu (click Software Downloads) Download free software. Symantec antivirus, software applications and security tools.
24 Network Access Gigabit Ethernet Network (PittNet) Provides access to University resources and the Internet. Wireless PittNet / Wireless PittNet Fast Available at locations across the Pittsburgh campus. Newer devices can take advantage of faster wireless speeds. Visit technology.pitt.edu for details. Secure Remote Access Service Provides secure access to restricted online services. Use the Pulse Secure client. Download it from my.pitt.edu.
25 Telecommunications Network Port Installation Telephone Service Migration to Skype for Business
26 Skype for Business Phones at Pitt
27 Skype for Business
28 My Pitt (my.pitt.edu) Access the information you use most from one location: University Resources Student Information such as: Grades, class schedule, ebill, CourseWeb
29 My Pitt (my.pitt.edu)
30 My Pitt
31 Ask Cathy
32 Emergency Notification Service ENS is used to communicate through , voice and text messages as deemed appropriate in the event of an emergency. You must subscribe to receive alerts. Subscribe at My Pitt (my.pitt.edu).
33 Emergency Notification Service
34 Read Green
35 Mobile Device Charging Stations Battery running low on your mobile devices? Get a quick boost. Charging Locations: University Store of Fifth William Pitt Union Towers Lobby CSSD Computing Labs
36 Technology Loaner Program for International Travel Offers loaner laptops, ipads, and smartphones to individuals traveling abroad to lessen the associated security risks while allowing full use of required software applications. Visit the Pitt Global web site for details.
37 Pitt App Store (appstore.pitt.edu) Your one-stop shop for University related apps: PeopleSoft Mobile Pitt Mobile CourseWeb pitt.box.com My Pitt Video Microsoft Outlook Lynda Microsoft Word, Excel, PowerPoint and More!
38 Box (pitt.box.com) Box is a secure cloud storage solution that provides unlimited file storage and access to your files from anywhere. You can invite others to collaborate with you or share files and folders through a simple Web link. Use Box on your computer, smartphone or tablet.
39 My Pitt Video My Pitt Video, powered by Panopto Video record and Webcast Capture presentations, online training, meetings, and lectures. Use from your desktop, laptop, smartphone, or tablet. Visit technology.pitt.edu for details.
40 Technology Workshops:
41 Technology Workshop
42 Online Technology Training Online training service that provides more than 3,000 business, creative, and technology courses. Learn what you want and when you want. Visit lynda.pitt.edu for details.
43 Information Security and Privacy Computer Security is everyone s responsibility. What you can do: Review our Security resources at technology.pitt.edu/security Information Security Awareness Training Security Alerts Secure Your Data
44 Information Security and Privacy Physical Security Precautions Keep your workspace and sensitive documents securely locked. Shred documents containing sensitive information. Protect laptops.
45 Responsible Computing Responsible Computing Means: Using resources for University-related activities. Protecting your password. Not sharing your computing account. Respecting copyright laws: Do not copy software. Do not download copyrighted music and movies.
46 Responsible Computing Walk away from Phishing scams Request personal information Contain poor spelling or grammar Call you to action Click or download No one legitimate will ask for your password Assume every is potentially fraudulent
47 Responsible Computing Computer Protection Don t Leave computer logged in or unlocked Accept or use unknown USB sticks Share your password or your PC Do Use Anti-Virus/Malware and local firewall Install updates to OS and Apps Only use trusted WiFi networks
48 Responsible Computing Mobile Device Protect Basic steps Lock it Don t hack it Trust, but verify apps No third-party site, android users!!! Update, update, update Find my device Bluetooth/WiFi off
49 Computer Privacy University owned computing equipment, networks, services and resources, including electronic mail, are provided for the purpose of conducting Universityrelated activities and are therefore considered University property. The University, as owner of such property, has the right to access information on the system stored, created or received by employees, including electronic mail messages, as it deems necessary and appropriate. As such, employees should not expect individual privacy in the system.
50 The Information Technology Web site technology.pitt.edu
51 Questions? Contact us Technology Web site: technology.pitt.edu Technology Help Desk: HELP facebook.com/pittcssd
52 Thank you
Ole Miss
 Technology @ Ole Miss ORIENTATION SPRING 2016 SUBTITLE WOULD GO HERE Online version available at: olemiss.edu/tech Official Ole Miss Mobile App Now available for ipad, iphone, Kindle Fire and Android devices.
Technology @ Ole Miss ORIENTATION SPRING 2016 SUBTITLE WOULD GO HERE Online version available at: olemiss.edu/tech Official Ole Miss Mobile App Now available for ipad, iphone, Kindle Fire and Android devices.
Katz IT Services Technology Resource Guide
 Katz IT Services Technology Resource Guide KITS: Katz IT Services 317 Mervis Hall kitsdesk@katz.pitt.edu 412-648-1601 Services: Network connection (wired and wireless) setup Secure Remote Access (SSLVPN)
Katz IT Services Technology Resource Guide KITS: Katz IT Services 317 Mervis Hall kitsdesk@katz.pitt.edu 412-648-1601 Services: Network connection (wired and wireless) setup Secure Remote Access (SSLVPN)
Skype for Business. Improve your team s productivity
 Skype for Business Improve your team s productivity Presented by Biren Shukla, President & CEO Forum Info-Tech About Forum Info-Tech Working as a trusted partner since 2005, Forum Info-Tech is a B2B company
Skype for Business Improve your team s productivity Presented by Biren Shukla, President & CEO Forum Info-Tech About Forum Info-Tech Working as a trusted partner since 2005, Forum Info-Tech is a B2B company
Lifespan Guide for installing and using Multi-Factor Authentication (MFA)
 Lifespan Guide for installing and using Multi-Factor Authentication (MFA) Registering for MFA for the First Time... 2 Using MFA... 7 Using one of your alternate MFA Methods... 7 Making an MFA response
Lifespan Guide for installing and using Multi-Factor Authentication (MFA) Registering for MFA for the First Time... 2 Using MFA... 7 Using one of your alternate MFA Methods... 7 Making an MFA response
Basics. IT services for postgraduate resarch students
 Basics IT services for postgraduate resarch students Get started Activate your computing account We re looking forward to welcoming you to the University of Liverpool! This guide will help you to understand
Basics IT services for postgraduate resarch students Get started Activate your computing account We re looking forward to welcoming you to the University of Liverpool! This guide will help you to understand
PharmD Class of 2020 IT Basics. Dave Nesmith and Wenqi Chen August 26, 2016 PharmD IT Committee
 PharmD Class of 2020 IT Basics Dave Nesmith and Wenqi Chen August 26, 2016 PharmD IT Committee David.Nesmith@pitt.edu Wenqi.Chen@pitt.edu Pitt Passport New single sign-on for all university services My
PharmD Class of 2020 IT Basics Dave Nesmith and Wenqi Chen August 26, 2016 PharmD IT Committee David.Nesmith@pitt.edu Wenqi.Chen@pitt.edu Pitt Passport New single sign-on for all university services My
Multi-Factor Authentication FAQs
 General FAQs What is Multi-factor Authentication (MFA)? Multi-factor authentication (MFA) seeks to decrease the likelihood that others can access your data. Specifically, it enhances the security of your
General FAQs What is Multi-factor Authentication (MFA)? Multi-factor authentication (MFA) seeks to decrease the likelihood that others can access your data. Specifically, it enhances the security of your
For Windows Microsoft Corporation. All rights reserved.
 For Windows 1 About Skype for Business... 4 Skype for Business Window... 5 Audio... 6 Set up your audio device... 6 Make a call... 6 Answer a call... 7 Use audio call controls... 7 Check voicemail... 8
For Windows 1 About Skype for Business... 4 Skype for Business Window... 5 Audio... 6 Set up your audio device... 6 Make a call... 6 Answer a call... 7 Use audio call controls... 7 Check voicemail... 8
Data Infrastructure Management 4/21/2017
 Data Infrastructure Management 4/21/2017 1 What is Box? When do I use Box? Creating your account Getting started with box Brown bag overview Box user guide Box university Box applications Box Edit Box
Data Infrastructure Management 4/21/2017 1 What is Box? When do I use Box? Creating your account Getting started with box Brown bag overview Box user guide Box university Box applications Box Edit Box
Lifespan Guide for installing and using Multi-Factor Authentication (MFA)
 Lifespan Guide for installing and using Multi-Factor Authentication (MFA) Registering for MFA for the First Time... 2 Using MFA... 7 Using one of your alternate MFA Methods... 7 Making an MFA response
Lifespan Guide for installing and using Multi-Factor Authentication (MFA) Registering for MFA for the First Time... 2 Using MFA... 7 Using one of your alternate MFA Methods... 7 Making an MFA response
Lifespan Guide for using your Lifespan Network Account
 Lifespan Guide for using your Lifespan Network Account Summary Instructions for setting up a new Lifespan network and Microsoft cloud account... 2 Set password... 2 Register for Self-Service Password Reset...
Lifespan Guide for using your Lifespan Network Account Summary Instructions for setting up a new Lifespan network and Microsoft cloud account... 2 Set password... 2 Register for Self-Service Password Reset...
Welcome to the UVU IT Service Desk
 Welcome to the UVU IT Service Desk Agenda 1. Procedures Getting Help 2. Network & Email 3. myuvu Portal 4. Security 5. Outages & Emergencies 6. Software 7. Miscellaneous Getting Help Phone 801-863-8888
Welcome to the UVU IT Service Desk Agenda 1. Procedures Getting Help 2. Network & Email 3. myuvu Portal 4. Security 5. Outages & Emergencies 6. Software 7. Miscellaneous Getting Help Phone 801-863-8888
2-STEP AUTHENTICATION SETUP For Office 365
 2-STEP AUTHENTICATION SETUP For Office 365 Table of Contents 2-Step Authentication Introduction... 3 Section 1: Setup Process to Receive a Text on your Mobile Phone... 4 Section 1 Step 1... 4 Section 1
2-STEP AUTHENTICATION SETUP For Office 365 Table of Contents 2-Step Authentication Introduction... 3 Section 1: Setup Process to Receive a Text on your Mobile Phone... 4 Section 1 Step 1... 4 Section 1
CaneNet_Wireless Documentation
 CaneNet_Wireless Documentation November 2018 Rev 1.0 CaneNet_Wireless Instructions What is CaneNet_Wireless? CaneNet_Wireless is a wireless network that provides encryption for your wireless communications
CaneNet_Wireless Documentation November 2018 Rev 1.0 CaneNet_Wireless Instructions What is CaneNet_Wireless? CaneNet_Wireless is a wireless network that provides encryption for your wireless communications
CaTS. Call: (937) Surf: Visit: 025 Library Annex
 CaTS CaTS is committed to providing high quality technology solutions and service that will help our students, faculty, and staff be successful in their endeavors while at Wright State. Call: (937) 775-4827
CaTS CaTS is committed to providing high quality technology solutions and service that will help our students, faculty, and staff be successful in their endeavors while at Wright State. Call: (937) 775-4827
Office365 & CANVAS. Quick Guide and Reference
 Office365 & CANVAS Quick Guide and Reference Office365 Office365 is a web or cloud-based subscription that can be accessed on multiple devices from anywhere with an online connection. It includes the most
Office365 & CANVAS Quick Guide and Reference Office365 Office365 is a web or cloud-based subscription that can be accessed on multiple devices from anywhere with an online connection. It includes the most
IT User accounts. IT resources for McGill students. McGill ID ( a 9 digit number) Minerva PIN - (yymmdd) First time login to Minerva
 IT resources for McGill students IT User accounts First time login to Minerva McGill ID - 260123456 ( a 9 digit number) Minerva PIN - (yymmdd) Will be prompted to change the initial Minerva PIN 1 IT User
IT resources for McGill students IT User accounts First time login to Minerva McGill ID - 260123456 ( a 9 digit number) Minerva PIN - (yymmdd) Will be prompted to change the initial Minerva PIN 1 IT User
utrgv.edu/it IT Services GETTING UTRGV
 IT Services GETTING CONNECTED @ UTRGV IT Service Desk www.youtube.com- @utrgvit Welcome to UTRGV video IT Service Desk Need Help? Request help or report an incident IT Service Desk Edinburg / McAllen /
IT Services GETTING CONNECTED @ UTRGV IT Service Desk www.youtube.com- @utrgvit Welcome to UTRGV video IT Service Desk Need Help? Request help or report an incident IT Service Desk Edinburg / McAllen /
Computing at MIT: Basics
 Computing at MIT: Basics Phyllis Galt and Stuart Peloquin Information Services and Technology August 2007 Key take-aways: Utilizing the MIT residential network Responsible network behavior Safe Computing
Computing at MIT: Basics Phyllis Galt and Stuart Peloquin Information Services and Technology August 2007 Key take-aways: Utilizing the MIT residential network Responsible network behavior Safe Computing
Student Tech Guide. Get Help from the Information and Technology Solutions Center! link.mnsu.edu/studenttech. Big ideas. Real-world thinking.
 Student Tech Guide Get Help from the Information and Technology Solutions Center! Find this Student Tech Guide online at link.mnsu.edu/studenttech Big ideas. Real-world thinking. Get Started Your StarID
Student Tech Guide Get Help from the Information and Technology Solutions Center! Find this Student Tech Guide online at link.mnsu.edu/studenttech Big ideas. Real-world thinking. Get Started Your StarID
Unified Communications Telephone Orientation
 Unified Communications Telephone Orientation http://ucsupport.kent.edu August 2016 Set up Voice Mailbox Press Messages Press * (star key) Enter your 5-digit extension, # (pound sign) Enter 2010, # (pound
Unified Communications Telephone Orientation http://ucsupport.kent.edu August 2016 Set up Voice Mailbox Press Messages Press * (star key) Enter your 5-digit extension, # (pound sign) Enter 2010, # (pound
Enviro Technology Services Ltd Data Protection Policy
 Enviro Technology Services Ltd Data Protection Policy 1. CONTEXT AND OVERVIEW 1.1 Key details Rev 1.0 Policy prepared by: Duncan Mounsor. Approved by board on: 23/03/2016 Policy became operational on:
Enviro Technology Services Ltd Data Protection Policy 1. CONTEXT AND OVERVIEW 1.1 Key details Rev 1.0 Policy prepared by: Duncan Mounsor. Approved by board on: 23/03/2016 Policy became operational on:
Multi-factor Authentication Instructions
 What is MFA? Multi-factor Authentication (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account.
What is MFA? Multi-factor Authentication (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account.
New Student Orientation. CaTS
 New Student Orientation CaTS Our Mission Provide computing resources, assistance, and direction to Wright State University s Faculty, Staff, and Students. Wright State Accounts Account Example Expiration
New Student Orientation CaTS Our Mission Provide computing resources, assistance, and direction to Wright State University s Faculty, Staff, and Students. Wright State Accounts Account Example Expiration
IT in St John s College
 IT in St John s College Welcome to St John s. Below is some information on the main IT systems you ll find in both St John s College and the University as well as some help to get you online. It will also
IT in St John s College Welcome to St John s. Below is some information on the main IT systems you ll find in both St John s College and the University as well as some help to get you online. It will also
Phish Alert Button How-To. Website:
 Phish Alert Button How-To Phishing Phishing is defined as the fraudulent practice of sending emails claiming to be from a reputable or known source in order to convince individuals to reveal personal information,
Phish Alert Button How-To Phishing Phishing is defined as the fraudulent practice of sending emails claiming to be from a reputable or known source in order to convince individuals to reveal personal information,
Network and Printing at Munich Business School
 Network and Printing at Munich Business School Dipl-Inf Frank Eyermann Frank.Eyermann@munichbusiness-school.de MBS IT resources Computers at the MBS premises WiFi at the MBS premises Printers MBS E-Mail
Network and Printing at Munich Business School Dipl-Inf Frank Eyermann Frank.Eyermann@munichbusiness-school.de MBS IT resources Computers at the MBS premises WiFi at the MBS premises Printers MBS E-Mail
Office365 & CANVAS. Quick Guide and Reference
 Office365 & CANVAS Quick Guide and Reference Office365 Office365 is a web or cloud-based subscription that can be accessed on multiple devices from anywhere with an online connection. It includes the most
Office365 & CANVAS Quick Guide and Reference Office365 Office365 is a web or cloud-based subscription that can be accessed on multiple devices from anywhere with an online connection. It includes the most
Full Disk Encryption. Larry Carson, Associate Director, Information Security Management
 Full Disk Encryption Larry Carson, Associate Director, Information Security Management What Security Really Looks Like at UBC News-worthy Security Incidents VGH Loss of 450 medical records via Resident
Full Disk Encryption Larry Carson, Associate Director, Information Security Management What Security Really Looks Like at UBC News-worthy Security Incidents VGH Loss of 450 medical records via Resident
Keeping Your Computer Secure Quick Reference Guide
 Keeping Your Computer Secure Quick Reference Guide Created: 3/16/2010 Page 1 of 1 Table Of Contents 1. Introduction... 3 2. Keeping Your Computer Up to Date... 4 2.1 Windows... 4 2.2 Mac... 6 3. Malware
Keeping Your Computer Secure Quick Reference Guide Created: 3/16/2010 Page 1 of 1 Table Of Contents 1. Introduction... 3 2. Keeping Your Computer Up to Date... 4 2.1 Windows... 4 2.2 Mac... 6 3. Malware
Data Protection Policy
 Data Protection Policy Status: Released Page 2 of 7 Introduction Our Data Protection policy indicates that we are dedicated to and responsible of processing the information of our employees, customers,
Data Protection Policy Status: Released Page 2 of 7 Introduction Our Data Protection policy indicates that we are dedicated to and responsible of processing the information of our employees, customers,
This handbook is designed to help you with all your Technology information.
 Berryville School Technology Assistance Handbook 2017-18 It's more fun to compute...kraftwerk 1981 This handbook is designed to help you with all your Technology information. P. 2 - Setting up your Classroom
Berryville School Technology Assistance Handbook 2017-18 It's more fun to compute...kraftwerk 1981 This handbook is designed to help you with all your Technology information. P. 2 - Setting up your Classroom
Infinite Campus Mobile App
 Infinite Campus Mobile App Requirements The following is required to view information on the Mobile Portal: The school district attended must use Infinite Campus as their student information system. You
Infinite Campus Mobile App Requirements The following is required to view information on the Mobile Portal: The school district attended must use Infinite Campus as their student information system. You
How to Build a Culture of Security
 How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
How to Build a Culture of Security March 2016 Table of Contents You are the target... 3 Social Engineering & Phishing and Spear-Phishing... 4 Browsing the Internet & Social Networking... 5 Bringing Your
Set up Voice Mailbox. Unified Communications Telephone Orientation. Support
 Unified Communications Telephone Orientation http://ucsupport.kent.edu August 2016 Set up Voice Mailbox Press Messages Press * (star key) Enter your 5 digit extension, # (pound sign) Enter 2010, # (pound
Unified Communications Telephone Orientation http://ucsupport.kent.edu August 2016 Set up Voice Mailbox Press Messages Press * (star key) Enter your 5 digit extension, # (pound sign) Enter 2010, # (pound
Security Awareness Training June 2016
 Security Awareness Training June 2016 What is Information Security Awareness? The University of North Carolina at Chapel Hill protects its data network from thousands of daily intrusion attempts, but technical
Security Awareness Training June 2016 What is Information Security Awareness? The University of North Carolina at Chapel Hill protects its data network from thousands of daily intrusion attempts, but technical
Members: Faculty: Christos Alexopoulos (IsyE); Lori Critz (Library); Hyesoon Kim (CS); Steve Potter (BME); Bruce Walker (Psych)
 Georgia Institute of Technology Student Computer Ownership Committee 2012 2013 Annual Report October 22, 2013 3 5:00 p.m. Student Center Theater Fall Meeting of the General Faculty, General Faculty Assembly,
Georgia Institute of Technology Student Computer Ownership Committee 2012 2013 Annual Report October 22, 2013 3 5:00 p.m. Student Center Theater Fall Meeting of the General Faculty, General Faculty Assembly,
Microsoft 365 Business FAQs
 Microsoft 365 Business FAQs Last updated April 27 th, 2018 Table of Contents General... 3 What is Microsoft 365 Business?... 3 Who should consider adopting Microsoft 365 Business?... 3 How can I get Microsoft
Microsoft 365 Business FAQs Last updated April 27 th, 2018 Table of Contents General... 3 What is Microsoft 365 Business?... 3 Who should consider adopting Microsoft 365 Business?... 3 How can I get Microsoft
imail Frequently Asked Questions (FAQs) 20 June 2014 Version 2.1
 imail Frequently Asked Questions (FAQs) 20 June 2014 Version 2.1 Owner: Cynthia Tan IT Services Table of Contents GENERAL FAQS... 1 1. How to access to Sunway imail account?... 1 2. I can t login to my
imail Frequently Asked Questions (FAQs) 20 June 2014 Version 2.1 Owner: Cynthia Tan IT Services Table of Contents GENERAL FAQS... 1 1. How to access to Sunway imail account?... 1 2. I can t login to my
Configuring Outlook from an Off-Campus Location to Use Enterprise Exchange
 Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Configuring Outlook from an Off-Campus Location to Use Enterprise Exchange Overview The easiest way to access your Enterprise Exchange
Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Configuring Outlook from an Off-Campus Location to Use Enterprise Exchange Overview The easiest way to access your Enterprise Exchange
UKIP needs to gather and use certain information about individuals.
 UKIP Data Protection Policy Context and overview Key details Policy Update Prepared by: D. Dennemarck / S. Turner Update approved by Management on: November 6, 2015 Policy update became operational on:
UKIP Data Protection Policy Context and overview Key details Policy Update Prepared by: D. Dennemarck / S. Turner Update approved by Management on: November 6, 2015 Policy update became operational on:
CHI Easy Access: Register From on the CHI Network
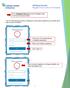 CHI Easy Access: Register From on the CHI Network Go to chieasyaccess.org and click "Register Now." You'll see the screen below. Your CHI Easy Access account is configured to use the same password you
CHI Easy Access: Register From on the CHI Network Go to chieasyaccess.org and click "Register Now." You'll see the screen below. Your CHI Easy Access account is configured to use the same password you
Magellan HUB: Making the Most of Our Collaboration Tools CAYLAN HORD DIRECTOR, END USER COMPUTE DAWN ROMBERG VP, CORPORATE COMMUNICATIONS
 Magellan HUB: Making the Most of Our Collaboration Tools CAYLAN HORD DIRECTOR, END USER COMPUTE DAWN ROMBERG VP, CORPORATE COMMUNICATIONS Agenda Magellan HUB: What does is it and what does it do? Live
Magellan HUB: Making the Most of Our Collaboration Tools CAYLAN HORD DIRECTOR, END USER COMPUTE DAWN ROMBERG VP, CORPORATE COMMUNICATIONS Agenda Magellan HUB: What does is it and what does it do? Live
Topic Course Activities
 The Absolute Basics What is a computer? 1. What is a computer? 2. What is a screen? 3. What is a keyboard? 4. What is a mouse? What is a laptop? 1. What is a laptop? 2. Using the touchpad 3. How to charge
The Absolute Basics What is a computer? 1. What is a computer? 2. What is a screen? 3. What is a keyboard? 4. What is a mouse? What is a laptop? 1. What is a laptop? 2. Using the touchpad 3. How to charge
Quick Heal Total Security for Android. Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping.
 Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Quick Heal Total Security for Android Anti-Theft Security. Web Security. Backup. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights Complete protection for your Android device that
Skype for Business 2016 For Windows Conferencing Quick Reference
 Skype for Business 2016 For Windows Conferencing Quick Reference 1 2 Contents Information for Skype for Business Meetings and Conference Calls... 3 Schedule a Phone Conference or Skype for Business Meeting...
Skype for Business 2016 For Windows Conferencing Quick Reference 1 2 Contents Information for Skype for Business Meetings and Conference Calls... 3 Schedule a Phone Conference or Skype for Business Meeting...
Model Numbers: DPC3939, TC8707C. Quick Start Guide. Wi-Fi Devices. Wireless Gateway 2
 Wireless Gateway 2 Model Numbers: DPC3939, TC8707C Quick Start Guide Wi-Fi Devices Wireless Gateway 2 ENG_WG2XB3_QSG_1013.indd 1 About the Wireless Gateway 2 (Model Numbers: DPC3939, TC8707C) The Wireless
Wireless Gateway 2 Model Numbers: DPC3939, TC8707C Quick Start Guide Wi-Fi Devices Wireless Gateway 2 ENG_WG2XB3_QSG_1013.indd 1 About the Wireless Gateway 2 (Model Numbers: DPC3939, TC8707C) The Wireless
PRACTICING SAFE COMPUTING AT HOME
 PRACTICING SAFE COMPUTING AT HOME WILLIAM (THE GONZ) FLINN M.S. INFORMATION SYSTEMS SECURITY MANAGEMENT; COMPTIA SECURITY+, I-NET+, NETWORK+; CERTIFIED PATCHLINK ENGINEER ENTERPRISE INFORMATION SYSTEMS
PRACTICING SAFE COMPUTING AT HOME WILLIAM (THE GONZ) FLINN M.S. INFORMATION SYSTEMS SECURITY MANAGEMENT; COMPTIA SECURITY+, I-NET+, NETWORK+; CERTIFIED PATCHLINK ENGINEER ENTERPRISE INFORMATION SYSTEMS
Windows ierīces Enterprise infrastruktūrā. Aris Dzērvāns Microsoft
 Windows ierīces Enterprise infrastruktūrā Aris Dzērvāns Microsoft Windows 8.1 Update the vision for everyone Designed for the way you live and work Brings together all you do On great devices Always business
Windows ierīces Enterprise infrastruktūrā Aris Dzērvāns Microsoft Windows 8.1 Update the vision for everyone Designed for the way you live and work Brings together all you do On great devices Always business
Course Outline (version 2)
 Course Outline (version 2) Page. 1 CERTIFIED SECURE COMPUTER USER This course is aimed at end users in order to educate them about the main threats to their data s security. It also equips the students
Course Outline (version 2) Page. 1 CERTIFIED SECURE COMPUTER USER This course is aimed at end users in order to educate them about the main threats to their data s security. It also equips the students
Data protection policy
 Data protection policy Context and overview Introduction The ASHA Centre needs to gather and use certain information about individuals. These can include customers, suppliers, business contacts, employees
Data protection policy Context and overview Introduction The ASHA Centre needs to gather and use certain information about individuals. These can include customers, suppliers, business contacts, employees
Office 365 Basics Training
 Office 365 Basics Table of Contents About Us... 3 Outlook Web App (OWA) vs. Outlook Client... 4 Accessing OWA Apps... 5 Mail (Outlook Web App)... 6 Adding/Removing Folders... 7 Adding/Removing Folders
Office 365 Basics Table of Contents About Us... 3 Outlook Web App (OWA) vs. Outlook Client... 4 Accessing OWA Apps... 5 Mail (Outlook Web App)... 6 Adding/Removing Folders... 7 Adding/Removing Folders
Initial Funding FY15 ETF Initial Funding FY17 ETF ESTIMATED AVAILABLE FUNDS 8,015,850 1,218,162 8,459,600 1,319,958 CAMPUS AND UNIT SUPPORT
 FY16 (June 15, 2015) DRAFT FY17 6/21/2016 $9,234,012 Cut $572,000 9,779,558 2015-16 2016-17 Initial Funding FY15 ETF Initial Funding FY17 ETF ESTIMATED AVAILABLE FUNDS 8,015,850 1,218,162 8,459,600 1,319,958
FY16 (June 15, 2015) DRAFT FY17 6/21/2016 $9,234,012 Cut $572,000 9,779,558 2015-16 2016-17 Initial Funding FY15 ETF Initial Funding FY17 ETF ESTIMATED AVAILABLE FUNDS 8,015,850 1,218,162 8,459,600 1,319,958
Quick Heal Mobile Security. Free protection for your Android phone against virus attacks, unwanted calls, and theft.
 Quick Heal Mobile Security Free protection for your Android phone against virus attacks, unwanted calls, and theft. Product Highlights Complete protection for your Android device that simplifies security
Quick Heal Mobile Security Free protection for your Android phone against virus attacks, unwanted calls, and theft. Product Highlights Complete protection for your Android device that simplifies security
Getting Started with Telecommunications Online Billing
 Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Getting Started with Telecommunications Online Billing The Departmental Online Phone Billing system allows you to view bills for your
Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Getting Started with Telecommunications Online Billing The Departmental Online Phone Billing system allows you to view bills for your
IT Help Desk/Technology Support website
 IT Help Desk/Technology Support website The IT Help Desk/Technology Support site has a wealth of information to use for troubleshooting common issues and tasks. Opening the IT Help Desk/Technology Support
IT Help Desk/Technology Support website The IT Help Desk/Technology Support site has a wealth of information to use for troubleshooting common issues and tasks. Opening the IT Help Desk/Technology Support
ANNUAL SECURITY AWARENESS TRAINING 2012
 UMW Information Technology Security Program Annual Security Awareness Training for UMW Faculty and Staff ANNUAL SECURITY AWARENESS TRAINING 2012 NETWORK AND COMPUTER USE POLICY Users of information technology
UMW Information Technology Security Program Annual Security Awareness Training for UMW Faculty and Staff ANNUAL SECURITY AWARENESS TRAINING 2012 NETWORK AND COMPUTER USE POLICY Users of information technology
College of Pharmacy Windows 10
 College of Pharmacy Windows 10 Windows 10 is the version of Microsoft s flagship operating system that follows Windows 8; the OS was released in July 2015. Windows 10 is designed to address common criticisms
College of Pharmacy Windows 10 Windows 10 is the version of Microsoft s flagship operating system that follows Windows 8; the OS was released in July 2015. Windows 10 is designed to address common criticisms
Allen University Microsoft Office 365
 Allen University Microsoft Office 365 Here's what you need to know to complete the transition On December 18 at 5:00pm, the University will complete the migration to Office 365, a new version of the hosted
Allen University Microsoft Office 365 Here's what you need to know to complete the transition On December 18 at 5:00pm, the University will complete the migration to Office 365, a new version of the hosted
commtech Online Holiday Shopping Tips A Guide Presented by: CommTech Industries
 Online Holiday Shopping Tips A Guide Presented by: CommTech Industries Holiday season is already upon us and that means high traffic for online shopping and higher risk for internet scams. The scammers
Online Holiday Shopping Tips A Guide Presented by: CommTech Industries Holiday season is already upon us and that means high traffic for online shopping and higher risk for internet scams. The scammers
ShareSync Get Started Guide for Mac
 ShareSync Get Started Guide for Mac ShareSync Overview ShareSync is a file backup and sharing service. It allows you to: Back up your files in real-time to protect against data loss from ransomware, accidental
ShareSync Get Started Guide for Mac ShareSync Overview ShareSync is a file backup and sharing service. It allows you to: Back up your files in real-time to protect against data loss from ransomware, accidental
a. UTRGV owned, leased or managed computers that fall within the regular UTRGV Computer Security Standard
 Kiosk Security Standard 1. Purpose This standard was created to set minimum requirements for generally shared devices that need to be easily accessible for faculty, staff, students, and the general public,
Kiosk Security Standard 1. Purpose This standard was created to set minimum requirements for generally shared devices that need to be easily accessible for faculty, staff, students, and the general public,
For Windows Users - Meetings Best Practice Guide
 For Windows Users - Meetings Best Practice Guide SKYPE FOR BUSINESS QUICK START GUIDE SKYPE FOR BUSINESS QUICK START GUIDE - WINDOWS USERS Contents On the Skype website, you ll find Quick Start Guides
For Windows Users - Meetings Best Practice Guide SKYPE FOR BUSINESS QUICK START GUIDE SKYPE FOR BUSINESS QUICK START GUIDE - WINDOWS USERS Contents On the Skype website, you ll find Quick Start Guides
Spirion Identity Finder Performing a Scan. Introduction. Conducting a Scan
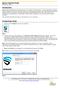 Spirion Identity Finder Performing a Scan Introduction Because data breaches are so prevalent and can be costly to the University, TU has made Spirion Identify Finder available to all faculty and staff.
Spirion Identity Finder Performing a Scan Introduction Because data breaches are so prevalent and can be costly to the University, TU has made Spirion Identify Finder available to all faculty and staff.
WELCOME TO PROGRAMMING
 WELCOME TO PROGRAMMING Course Navigation and information on Canvas Dan McElroy This video is offered under a Creative Commons Attribution Non-Commercial Share license. Content in this video can be considered
WELCOME TO PROGRAMMING Course Navigation and information on Canvas Dan McElroy This video is offered under a Creative Commons Attribution Non-Commercial Share license. Content in this video can be considered
How to access Launchpad and Textbooks online
 Quest Tech Tips Launchpad & Textbooks Online Directions (front and back) How to setup your mobile device to receive school/district notifications (front and back) Edline parent instructions Free Microsoft
Quest Tech Tips Launchpad & Textbooks Online Directions (front and back) How to setup your mobile device to receive school/district notifications (front and back) Edline parent instructions Free Microsoft
Why is Office 365 the right choice?
 Why is Office 365 the right choice? People today want to be productive wherever they go. They want to work faster and smarter across their favorite devices, while staying current and connected. Simply
Why is Office 365 the right choice? People today want to be productive wherever they go. They want to work faster and smarter across their favorite devices, while staying current and connected. Simply
Manually Configuring Windows 8 for Wireless PittNet
 Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 8 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Technology Help Desk 412 624-HELP [4357] http://technology.pitt.edu Manually Configuring Windows 8 for Wireless PittNet If you are not able to connect to Wireless PittNet using our automated wizard, you
Multi-factor Authentication Instructions
 What is MFA? (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account. MFA authentication is typically
What is MFA? (MFA) is a security measure to confirm your identity in addition to your username and password. It helps in the prevention of unauthorized access to your account. MFA authentication is typically
Best Practices Guide to Electronic Banking
 Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Best Practices Guide to Electronic Banking City Bank & Trust Company offers a variety of services to our customers. As these services have evolved over time, a much higher percentage of customers have
Campuswide the average is two devices per student
 Q1 Please enter the number of devices (laptop, smartphone, tablet, etc.) that you brought to campus and connect to the wireless network. Answered: 536 Skipped: 0 Campuswide the average is two devices per
Q1 Please enter the number of devices (laptop, smartphone, tablet, etc.) that you brought to campus and connect to the wireless network. Answered: 536 Skipped: 0 Campuswide the average is two devices per
Office 365 Faculty & Staff. Migration: June 26 th 30 th, 2017
 Office 365 Faculty & Staff Migration: June 26 th 30 th, 2017 What is Office 365? Outlook Web App Office Online Skype for Business OneDrive What is Office 365? Outlook Web App Updates existing OWA No change
Office 365 Faculty & Staff Migration: June 26 th 30 th, 2017 What is Office 365? Outlook Web App Office Online Skype for Business OneDrive What is Office 365? Outlook Web App Updates existing OWA No change
CERTIFIED SECURE COMPUTER USER COURSE OUTLINE
 CERTIFIED SECURE COMPUTER USER COURSE OUTLINE Page 1 TABLE OF CONTENT 1 COURSE DESCRIPTION... 3 2 MODULE-1: INTRODUCTION TO DATA SECURITY... 4 3 MODULE-2: SECURING OPERATING SYSTEMS... 6 4 MODULE-3: MALWARE
CERTIFIED SECURE COMPUTER USER COURSE OUTLINE Page 1 TABLE OF CONTENT 1 COURSE DESCRIPTION... 3 2 MODULE-1: INTRODUCTION TO DATA SECURITY... 4 3 MODULE-2: SECURING OPERATING SYSTEMS... 6 4 MODULE-3: MALWARE
POLICY 8200 NETWORK SECURITY
 POLICY 8200 NETWORK SECURITY Policy Category: Information Technology Area of Administrative Responsibility: Information Technology Services Board of Trustees Approval Date: April 17, 2018 Effective Date:
POLICY 8200 NETWORK SECURITY Policy Category: Information Technology Area of Administrative Responsibility: Information Technology Services Board of Trustees Approval Date: April 17, 2018 Effective Date:
Using the Vita Group Citrix Portal
 Using the Vita Group Citrix Portal Using the Portal Summary This document is will step you through using the Vita Group Citrix portal. This portal allows you to reset your password if it is expired, unlock
Using the Vita Group Citrix Portal Using the Portal Summary This document is will step you through using the Vita Group Citrix portal. This portal allows you to reset your password if it is expired, unlock
Corporate Information & Computing Services. IT Services For University Staff.
 Corporate Information & Computing Services. IT Services For University Staff. Working at the University of Sheffield This guide will help you get started with the key IT services provided by Corporate
Corporate Information & Computing Services. IT Services For University Staff. Working at the University of Sheffield This guide will help you get started with the key IT services provided by Corporate
FAQ: Privacy, Security, and Data Protection at Libraries
 FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
FAQ: Privacy, Security, and Data Protection at Libraries This FAQ was developed out of workshops and meetings connected to the Digital Privacy and Data Literacy Project (DPDL) and Brooklyn Public Library
STUDENT ACCEPTABLE USE OF IT SYSTEMS POLICY
 STUDENT ACCEPTABLE USE OF IT SYSTEMS POLICY Introduction The college offer an extensive range of IT systems across campuses and online for course related activities and drop-in purposes. This policy applies
STUDENT ACCEPTABLE USE OF IT SYSTEMS POLICY Introduction The college offer an extensive range of IT systems across campuses and online for course related activities and drop-in purposes. This policy applies
716 West Ave Austin, TX USA
 Fundamentals of Computer and Internet Fraud GLOBAL Headquarters the gregor building 716 West Ave Austin, TX 78701-2727 USA TABLE OF CONTENTS I. INTRODUCTION What Is Computer Crime?... 2 Computer Fraud
Fundamentals of Computer and Internet Fraud GLOBAL Headquarters the gregor building 716 West Ave Austin, TX 78701-2727 USA TABLE OF CONTENTS I. INTRODUCTION What Is Computer Crime?... 2 Computer Fraud
Quentin Burdick Building
 www.ndsu.edu/it Quentin Burdick Building IT Help Desk IT Training Room Software Licensing Technology Learning IT Security & Media Center and more! Thorson Maintenance Center Telecommunications Help with
www.ndsu.edu/it Quentin Burdick Building IT Help Desk IT Training Room Software Licensing Technology Learning IT Security & Media Center and more! Thorson Maintenance Center Telecommunications Help with
Your guide to Microsoft Lumia 950. The phone that works like your PC.
 Your guide to Microsoft Lumia 950. The phone that works like your PC. Microsoft Lumia 950 with Windows 0 Sleek and stylish, Microsoft Lumia 950 with Windows 0 enables you to access, share, create and edit
Your guide to Microsoft Lumia 950. The phone that works like your PC. Microsoft Lumia 950 with Windows 0 Sleek and stylish, Microsoft Lumia 950 with Windows 0 enables you to access, share, create and edit
Quick Heal Mobile Security. Anti-Theft Security. Real-Time Protection. Safe Online Banking & Shopping.
 Anti-Theft Security. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights With an easy-to-update virus protection and a dynamic yet simple interface, virus removal from your mobile
Anti-Theft Security. Real-Time Protection. Safe Online Banking & Shopping. Product Highlights With an easy-to-update virus protection and a dynamic yet simple interface, virus removal from your mobile
1) Are employees required to sign an Acceptable Use Policy (AUP)?
 Business ebanking Risk Assessment & Controls Evaluation As a business owner, you want to be sure you have a strong process in place for monitoring and managing who has access to your Business ebanking
Business ebanking Risk Assessment & Controls Evaluation As a business owner, you want to be sure you have a strong process in place for monitoring and managing who has access to your Business ebanking
Instruction How To Use Wifi In Mobile Phone Via Laptop >>>CLICK HERE<<<
 Instruction How To Use Wifi In Mobile Phone Via Laptop You could also just connect your phone to your laptop and draw power from of the Wi-Fi hotspot feature, but you can also tether via a USB cable or
Instruction How To Use Wifi In Mobile Phone Via Laptop You could also just connect your phone to your laptop and draw power from of the Wi-Fi hotspot feature, but you can also tether via a USB cable or
Prepared for: June 18, 2014
 Prepared for: June 18, 2014 Changing Student Expectations Innovative Technology Trends: BYOD Networks & Security Cloud Computing Video Network Security Design Guidelines Questions welcome throughout! Differing
Prepared for: June 18, 2014 Changing Student Expectations Innovative Technology Trends: BYOD Networks & Security Cloud Computing Video Network Security Design Guidelines Questions welcome throughout! Differing
US FOODS ONLINE 2015: Overview
 US FOODS ONLINE 2015: Overview 1 What s new in US Foods Online 2015? We re committed to Easy, Every Step of the Way. Easy and intuitive Help find the right products Faster, more reliable platform Continuous
US FOODS ONLINE 2015: Overview 1 What s new in US Foods Online 2015? We re committed to Easy, Every Step of the Way. Easy and intuitive Help find the right products Faster, more reliable platform Continuous
SecuriSync Get Started Guide for Windows
 SecuriSync Get Started Guide for Windows Intermedia Backup and File Sharing - SecuriSync SecuriSync is a file backup and sharing service. It allows you to: Back up your files in real-time to protect against
SecuriSync Get Started Guide for Windows Intermedia Backup and File Sharing - SecuriSync SecuriSync is a file backup and sharing service. It allows you to: Back up your files in real-time to protect against
An introduction to wireless security at home, on the road and on campus. Sherry Callahan and Kyle Crane
 Out of Thin Air! An introduction to wireless security at home, on the road and on campus Sherry Callahan and Kyle Crane University of Kansas Medical Center October 5, 2009 Wireless Networking at Home Sherry
Out of Thin Air! An introduction to wireless security at home, on the road and on campus Sherry Callahan and Kyle Crane University of Kansas Medical Center October 5, 2009 Wireless Networking at Home Sherry
Remote employee. / future ready / Remote employee
 Remote employee Business success is, literally, in your employees hands in the form of the IT they use every day. It s your choice: Equip employees with the solutions that will help your organization win,
Remote employee Business success is, literally, in your employees hands in the form of the IT they use every day. It s your choice: Equip employees with the solutions that will help your organization win,
Train employees to avoid inadvertent cyber security breaches
 Train employees to avoid inadvertent cyber security breaches TRAIN EMPLOYEES TO AVOID INADVERTENT CYBER SECURITY BREACHES PAGE 2 How much do you know about cyber security? Small business owners often lack
Train employees to avoid inadvertent cyber security breaches TRAIN EMPLOYEES TO AVOID INADVERTENT CYBER SECURITY BREACHES PAGE 2 How much do you know about cyber security? Small business owners often lack
Activate your computing account
 se nti als IT tau servic ght es f pos or u tgr nde adu rg ate radu stu den ate an ts 2 d 018 /19 Es Get started Activate your computing account We re looking forward to welcoming you to the University
se nti als IT tau servic ght es f pos or u tgr nde adu rg ate radu stu den ate an ts 2 d 018 /19 Es Get started Activate your computing account We re looking forward to welcoming you to the University
Data Protection in Practice
 ANNUAL CPD BOARD CONFERENCE Data Protection in Practice 6 & 13 DECEMBER 2016 There are only two types of companies: those that have been hacked, and those that will be. Robert Mueller, FBI Director There
ANNUAL CPD BOARD CONFERENCE Data Protection in Practice 6 & 13 DECEMBER 2016 There are only two types of companies: those that have been hacked, and those that will be. Robert Mueller, FBI Director There
VOA COMPUTER MIGRATION OCTOBER 21-24
 VOA COMPUTER MIGRATION OCTOBER 21-24 Over the weekend starting Friday, October 21 at 4:00 PM (Central) / 5:00 PM (Eastern) and concluding at 7:00 AM (local time) Monday, October 24 every VOA computer will
VOA COMPUTER MIGRATION OCTOBER 21-24 Over the weekend starting Friday, October 21 at 4:00 PM (Central) / 5:00 PM (Eastern) and concluding at 7:00 AM (local time) Monday, October 24 every VOA computer will
Monash technology essentials for students 2013
 Monash technology essentials for students 2013 Australia China India Italy Malaysia South Africa Contents Overview...1 Contacting esolutions...2 my.monash Portal...3 Free Wireless...5 Printing...5 Computer
Monash technology essentials for students 2013 Australia China India Italy Malaysia South Africa Contents Overview...1 Contacting esolutions...2 my.monash Portal...3 Free Wireless...5 Printing...5 Computer
BHIG - Mobile Devices Policy Version 1.0
 Version 1.0 Authorised by: CEO Endorsed By: Chief Operations Officer 1 Document Control Version Date Amended by Changes Made 0.1 20/01/2017 Lars Cortsen Initial document 0.2 29/03/2017 Simon Hahnel Incorporate
Version 1.0 Authorised by: CEO Endorsed By: Chief Operations Officer 1 Document Control Version Date Amended by Changes Made 0.1 20/01/2017 Lars Cortsen Initial document 0.2 29/03/2017 Simon Hahnel Incorporate
Part-Time Faculty Guide View and Print Roster, Online Grading, and Notify Button
 Faculty may access the system from the CLC Home page located at: http://www.clcillinois.edu On the CLC Home page use the Faculty/Staff link in the top navigation bar.. Under Resources for Faculty & Staff
Faculty may access the system from the CLC Home page located at: http://www.clcillinois.edu On the CLC Home page use the Faculty/Staff link in the top navigation bar.. Under Resources for Faculty & Staff
<Criminal Justice Agency Name> Personally Owned Device Policy. Allowed Personally Owned Device Policy
 Policy Title: Effective Date: Revision Date: Approval(s): LASO: CSO: Agency Head: Allowed Personally Owned Device Policy Every 2 years or as needed Purpose: A personally owned information system or device
Policy Title: Effective Date: Revision Date: Approval(s): LASO: CSO: Agency Head: Allowed Personally Owned Device Policy Every 2 years or as needed Purpose: A personally owned information system or device
Red Flags Program. Purpose
 Red Flags Program Purpose The purpose of this Red Flags Rules Program is to document the protocol adopted by the University of Memphis in compliance with the Red Flags Rules. Many offices at the University
Red Flags Program Purpose The purpose of this Red Flags Rules Program is to document the protocol adopted by the University of Memphis in compliance with the Red Flags Rules. Many offices at the University
FACEBOOK SAFETY FOR JOURNALISTS. Thanks to these partners for reviewing these safety guidelines:
 FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
FACEBOOK SAFETY FOR JOURNALISTS Thanks to these partners for reviewing these safety guidelines: 10 STEPS TO KEEP YOURSELF SAFE Journalists are using Facebook in innovative ways to do their jobs, tell stories,
Mobile Devices Manual. Revised July 2017 Robert C. Fisler School
 Mobile Devices Manual Revised July 2017 Robert C. Fisler School Contents Mobile Devices for Learning Overview Distribution and Return Mobile Devices Care Discipline with Mobile Device Use Managing Files
Mobile Devices Manual Revised July 2017 Robert C. Fisler School Contents Mobile Devices for Learning Overview Distribution and Return Mobile Devices Care Discipline with Mobile Device Use Managing Files
