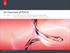
Lecture 15. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7.
|
|
|
- Elvin Stanley
- 6 years ago
- Views:
Transcription
1 Lecture 15 Pulic Key Distriution (certifiction) 1 PK-sed Needhm-Schroeder TTP 1. A, B 4. B, A 2. {PK, B}SKT 5. {PK, A} SKT SKs A 2. {PK, B} SKs 3. [N, A] PK 6. [N, N ] PK B 7. [N ] PK Here, TTP cts s n on-line certifiction uthority (CA) nd tkes cre of revoction 2 1
2 x.509 Authentiction & Key Distriution Protocols How does Alice get PK nd Bo PK? One-wy A B à {1, t, r, B, other,[ K ] } PK B SK A Two-wy A B à {2, t, r, B, other,[ K ] } PK {2, t, r, A, r, other,[ K ] } B PK A SK A SK B Three-wy A B ß à {3, t, r, B, other,[ K ] } PK {3, t, r, A, r, other,[ K ] } {3, r } SK A B PK A SK A SK B 3 Wht if? Alice nd Bo hve: No common mutully trusted TTP(s) nd/or No on-line TTP(s) 4 2
3 Pulic Key Infrstructure (Distriution) Prolem: How to determine the correct pulic key of given entity Binding etween IDENTITY nd PUBLIC KEY Possile ttcks Nme spoofing: Eve ssocites Alice s nme with Eve s pulic key Key spoofing: Eve ssocites Alice s key with Eve s nme DoS: Eve ssocites Alice s nme with nonsensicl (ogus) key Wht hppens in ech cse? 5 Pulic Key Distriution Diffie - Hellmn (1976) proposed the pulic file concept universlly ccessile no unuthorized modifiction poor ide à not sclle! 6 3
4 Pulic Key Distriution Popek - Kline (1979) proposed trusted third prties (TTPs) TTPs know pulic keys of the entities nd distriute them on-demnd sis on-line protocol ( disdvntge) 7 Certifictes Kohnfelder (BS Thesis, MIT, 1978) proposed certifictes s yet nother pulic-key distriution method Explicit inding etween the pulic-key nd its owner/nme Issued (digitlly signed) y the Certificte Authority (CA) Issunce is done off-line 8 4
5 Authenticted Pulic-Key-sed Key Exchnge (Sttion-to-Sttion or STS Protocol) Choose rndom v Compute v K = ( y ) mod p SIG = { y, y } lice lice y v = mod p CERT, y, SIG o CERT lice, SIG lice o Choose rndom w, Compute w K = ( y ) mod p w y = mod p SIG = { y, y } o Bo CERT lice CERT o 9 Certifictes Procedure Bo registers t locl CA Bo receives his certificte: { PK B, ID B, issunce_time, expirtion_time, ert, etc.,...}sk CA Bo sends certificte to Alice Alice verifies CA s signture PK CA hrd-coded in softwre Alice uses PK B for encryption nd/or verifying signtures 10 5
6 Who issues certifictes? CA: Certifiction Authority e.g. GlolSign, VeriSign, Thwte, etc. look into your rowser... Trustworthy (t lest to its users/clients) Off-line opertion (usully) Hs well-known long-term certificte My store client certifictes Very secure: physiclly nd electroniclly 11 How does it work? A pulic/privte key-pir is generted y user User requests certificte vi locl ppliction (e.g., we rowser) Good ide to prove knowledge of privte key s prt of the certificte request. Why? Pulic key nd nme usully prt of PK certificte Privte keys only used for smll mount of dt (signing, encryption of session keys) Symmetric keys (e.g., RC5, AES) used for ulk dt encryption 12 6
7 CA CA checks tht requesting user is who he clims to e (in the certificte request) CA s own certificte is signed y higher-level CA. Root CA s certificte is self-signed nd his identity/nme is well-known CA is criticl prt of the system nd must operte in secure nd predictle wy ccording to some policy 13 Who needs them? Alice s certificte is checked y whomever wnts to: 1) verify her signtures, nd/or 2) encrypt dt for her. A verifier must: know the pulic key of the CA(s) trust ll CAs involved Certificte checking is: verifiction of the signture nd vlidity Vlidity: expirtion + revoction checking 14 7
8 Verifying certificte (ssuming common CA) To e covered lter 15 BTW: Certificte types PK (Identity) certifictes Bind PK to some identity string Attriute certifictes Bind PK to ritrry ttriute informtion, e.g., uthoriztion, group memership We concentrte on former 16 8
9 Wht re PK certifictes good for? Secure chnnels in TLS / SSL for we servers Signed nd/or encrypted emil (PGP,S/MIME) Authentiction (e.g., SSH with RSA) Code signing! Encrypting files (EFS in Windows/2000) IPSec: encryption/uthentiction t the network lyer 17 Components of certifiction system Request nd issue certifictes (different ctegories) with verifiction of identity Storge of certifictes (WHY?) Pulishing/distriution of certifictes (LDAP, HTTP) Pre-instlltion of root certifictes in trusted environment Support y OS pltforms, pplictions nd services Mintennce of dtse of issued certifictes (no privte keys!) Helpdesk (informtion, lost + compromised privte keys) Advertising revoked certifictes (nd support for pplictions to perform revoction checking) Storge guidelines for privte keys 18 9
10 CA Security Must minimize risk of CA privte key eing compromised Best to hve n off-line CA Requests my come in electroniclly ut not processed in rel time Also, distriuted CA (using threshold crypto) Microsoft recommends using CA hierrchy where root CA is off-line nd signing CA re on-line In ddition, using tmper-resistnt hrdwre for the CA would help (should e impossile to extrct privte key) 19 Mpping personl certifictes into ccounts/nmes Certificte must mp one-to-one into n ccount/nme for the ske of uthentiction In some systems, mpping re sed upon X.509 nming ttriutes from the Suject field Exmple: Verisign issues certificte s CN=Full Nme (ccount) Account/nme is locl to the issuing domin 20 10
11 Storge of privte key The prolem of hving the user to mnge the privte key (user support, key loss or compromise) Windows offers the CryptoAPI + Protected Storge which sves privte keys (encrypted) in the Protected Storge, prt of the roming user profile. MS pps like IE nd Outlook tke dvntge of this; Netscpe sves privte keys encrypted in its configurtion directory users who mix pplictions or pltforms must mnully import / export privte keys vi PFX files. 21 Key lengths Strong encryption hs een dopted since the relxtion of US export lws 512-it RSA nd 56-it DES re not sfe Root CA should hve n (RSA) key length of >= 2048 its given its importnce nd typicl lifetime of 3-5 yers A personl (RSA) certificte should hve key length of >= 1536 its Interoperility with older stuff? E.g., when using encryption (s in SSL) need to test tht newer rowsers still work with low encryption 56-its DES 22 11
12 Nming comes first! Cnnot hve certifictes without comprehensive nming scheme Cnnot hve PKI without comprehensive distriution/ ccess method X.509 uses X.500 nming X.500 Distinguished Nmes (DNs) contin suset of: C Country SP Stte/Province L Loclity O Orgniztion OU Orgniztionl Unit CN Common Nme 23 X.500 ISO stndrd for directory services glol, distriuted first solid version in (second in 1993.) documenttion - severl RFC s 24 12
13 X.500 dt model: sed on hierrchicl nmespce Directory Informtion Tree (DIT) geogrphiclly orgnized entry is defined with its dn (Distinguished Nme) serching: you must select loction in DIT to se your serch one-level serch or sutree serch sutree serch cn e slow 25 X DIT World c=af... c=usa... o=al QAEDA o=army... cn=osm in Lden (decesed)... dn: cn=osm in Lden, o=al Qed, c=af 26 13
14 X.500 ccessile through: telnet (client progrms known s du, dish,...) WWW interfce For exmple: hrd to use nd very hevy thus LDAP ws developed 27 LDAP LDAP - Lightweight Directory Access Protocol LDAP v2 - RFC 1777, RFC 1778 LDAP v3 - RFC 1779 developed to mke X.500 esier to use provides sic X.500 functions referrl model insted originl chining server informs client to sk nother server (without sking question on the ehlf of client) LDAP URL formt: ldp://server_ddress/dn (ldp://ldp.uci.edu/cn=gene Tsudik,o=UCI,c=US) 28 14
15 Some relevnt stndrds The IETF reference site Pulic-Key Infrstructure (X.509, PKIX) RFC 2459 (X.509 v3 + v2 CRL) LDAP v2 for certificte nd CRL storge RFC 2587 Guidelines & prctices RFC 2527 S/MIME v3 RFC 2632 & 2633 TLS 1.0 / SSL v3 RFC
Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7.
![Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7. Lecture 13. Public Key Distribution (certification) PK-based Needham-Schroeder TTP. 3. [N a, A] PKb 6. [N a, N b ] PKa. 7.](/thumbs/84/91191448.jpg) Lecture 13 Public Key Distribution (certification) 1 PK-based Needham-Schroeder TTP 1. A, B 4. B, A 2. {PKb, B}SKT B}SKs 5. {PK a, A} SKT SKs A 3. [N a, A] PKb 6. [N a, N b ] PKa B 7. [N b ] PKb Here,
Lecture 13 Public Key Distribution (certification) 1 PK-based Needham-Schroeder TTP 1. A, B 4. B, A 2. {PKb, B}SKT B}SKs 5. {PK a, A} SKT SKs A 3. [N a, A] PKb 6. [N a, N b ] PKa B 7. [N b ] PKb Here,
Lecture 15 Public Key Distribution (certification)
 0 < i < 2 n = N X i,y i random secret keys index i = random (secret) value Merkle s Puzzles (1974) Puzzle P i = {index i,x i,s} Y i S fixed string, e.g., " Alice to Bob" { P 0 < i < 2 i n } Pick random
0 < i < 2 n = N X i,y i random secret keys index i = random (secret) value Merkle s Puzzles (1974) Puzzle P i = {index i,x i,s} Y i S fixed string, e.g., " Alice to Bob" { P 0 < i < 2 i n } Pick random
COMPUTER EDUCATION TECHNIQUES, INC. (MS_W2K3_SERVER ) SA:
 In order to lern which questions hve een nswered correctly: 1. Print these pges. 2. Answer the questions. 3. Send this ssessment with the nswers vi:. FAX to (212) 967-3498. Or. Mil the nswers to the following
In order to lern which questions hve een nswered correctly: 1. Print these pges. 2. Answer the questions. 3. Send this ssessment with the nswers vi:. FAX to (212) 967-3498. Or. Mil the nswers to the following
Registering as a HPE Reseller. Quick Reference Guide for new Partners in Asia Pacific
 Registering s HPE Reseller Quick Reference Guide for new Prtners in Asi Pcific Registering s new Reseller prtner There re five min steps to e new Reseller prtner. Crete your Appliction Copyright 2017 Hewlett
Registering s HPE Reseller Quick Reference Guide for new Prtners in Asi Pcific Registering s new Reseller prtner There re five min steps to e new Reseller prtner. Crete your Appliction Copyright 2017 Hewlett
Registering as an HPE Reseller
 Registering s n HPE Reseller Quick Reference Guide for new Prtners Mrch 2019 Registering s new Reseller prtner There re four min steps to register on the Prtner Redy Portl s new Reseller prtner: Appliction
Registering s n HPE Reseller Quick Reference Guide for new Prtners Mrch 2019 Registering s new Reseller prtner There re four min steps to register on the Prtner Redy Portl s new Reseller prtner: Appliction
vcloud Director Service Provider Admin Portal Guide vcloud Director 9.1
 vcloud Director Service Provider Admin Portl Guide vcloud Director 9. vcloud Director Service Provider Admin Portl Guide You cn find the most up-to-dte technicl documenttion on the VMwre website t: https://docs.vmwre.com/
vcloud Director Service Provider Admin Portl Guide vcloud Director 9. vcloud Director Service Provider Admin Portl Guide You cn find the most up-to-dte technicl documenttion on the VMwre website t: https://docs.vmwre.com/
File Manager Quick Reference Guide. June Prepared for the Mayo Clinic Enterprise Kahua Deployment
 File Mnger Quick Reference Guide June 2018 Prepred for the Myo Clinic Enterprise Khu Deployment NVIGTION IN FILE MNGER To nvigte in File Mnger, users will mke use of the left pne to nvigte nd further pnes
File Mnger Quick Reference Guide June 2018 Prepred for the Myo Clinic Enterprise Khu Deployment NVIGTION IN FILE MNGER To nvigte in File Mnger, users will mke use of the left pne to nvigte nd further pnes
NOTES. Figure 1 illustrates typical hardware component connections required when using the JCM ICB Asset Ticket Generator software application.
 ICB Asset Ticket Genertor Opertor s Guide Septemer, 2016 Septemer, 2016 NOTES Opertor s Guide ICB Asset Ticket Genertor Softwre Instlltion nd Opertion This document contins informtion for downloding, instlling,
ICB Asset Ticket Genertor Opertor s Guide Septemer, 2016 Septemer, 2016 NOTES Opertor s Guide ICB Asset Ticket Genertor Softwre Instlltion nd Opertion This document contins informtion for downloding, instlling,
Distributed Systems Principles and Paradigms
 Distriuted Systems Principles nd Prdigms Chpter 11 (version April 7, 2008) Mrten vn Steen Vrije Universiteit Amsterdm, Fculty of Science Dept. Mthemtics nd Computer Science Room R4.20. Tel: (020) 598 7784
Distriuted Systems Principles nd Prdigms Chpter 11 (version April 7, 2008) Mrten vn Steen Vrije Universiteit Amsterdm, Fculty of Science Dept. Mthemtics nd Computer Science Room R4.20. Tel: (020) 598 7784
VMware Horizon JMP Server Installation and Setup Guide. Modified on 06 SEP 2018 VMware Horizon 7 7.6
 VMwre Horizon JMP Server Instlltion nd Setup Guide Modified on 06 SEP 2018 VMwre Horizon 7 7.6 You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/ If you
VMwre Horizon JMP Server Instlltion nd Setup Guide Modified on 06 SEP 2018 VMwre Horizon 7 7.6 You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/ If you
vcloud Director Tenant Portal Guide vcloud Director 9.0
 vcloud Director Tennt Portl Guide vcloud Director 9.0 vcloud Director Tennt Portl Guide You cn find the most up-to-dte technicl documenttion on the VMwre We site t: https://docs.vmwre.com/ The VMwre We
vcloud Director Tennt Portl Guide vcloud Director 9.0 vcloud Director Tennt Portl Guide You cn find the most up-to-dte technicl documenttion on the VMwre We site t: https://docs.vmwre.com/ The VMwre We
License Manager Installation and Setup
 The Network License (concurrent-user) version of e-dpp hs hrdwre key plugged to the computer running the License Mnger softwre. In the e-dpp terminology, this computer is clled the License Mnger Server.
The Network License (concurrent-user) version of e-dpp hs hrdwre key plugged to the computer running the License Mnger softwre. In the e-dpp terminology, this computer is clled the License Mnger Server.
vcloud Director Service Provider Admin Portal Guide 04 OCT 2018 vcloud Director 9.5
 vcloud Director Service Provider Admin Portl Guide 04 OCT 208 vcloud Director 9.5 You cn find the most up-to-dte technicl documenttion on the VMwre website t: https://docs.vmwre.com/ If you hve comments
vcloud Director Service Provider Admin Portl Guide 04 OCT 208 vcloud Director 9.5 You cn find the most up-to-dte technicl documenttion on the VMwre website t: https://docs.vmwre.com/ If you hve comments
Zenoss Service Impact Installation and Upgrade Guide for Resource Manager 5.x and 6.x
 Zenoss Service Impct Instlltion nd Upgrde Guide for Resource Mnger 5.x nd 6.x Relese 5.3.1 Zenoss, Inc. www.zenoss.com Zenoss Service Impct Instlltion nd Upgrde Guide for Resource Mnger 5.x nd 6.x Copyright
Zenoss Service Impct Instlltion nd Upgrde Guide for Resource Mnger 5.x nd 6.x Relese 5.3.1 Zenoss, Inc. www.zenoss.com Zenoss Service Impct Instlltion nd Upgrde Guide for Resource Mnger 5.x nd 6.x Copyright
Small Business Networking
 Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd processes. Introducing technology
Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd processes. Introducing technology
From Dependencies to Evaluation Strategies
 From Dependencies to Evlution Strtegies Possile strtegies: 1 let the user define the evlution order 2 utomtic strtegy sed on the dependencies: use locl dependencies to determine which ttriutes to compute
From Dependencies to Evlution Strtegies Possile strtegies: 1 let the user define the evlution order 2 utomtic strtegy sed on the dependencies: use locl dependencies to determine which ttriutes to compute
M-Historian and M-Trend
 Product Bulletin Issue Dte June 18, 2004 M-Historin nd The M-Historin mnges the collection nd rchiving of trend dt, nd enles the presenttion of rchived trend dt in the ssocited softwre component. M-Historin
Product Bulletin Issue Dte June 18, 2004 M-Historin nd The M-Historin mnges the collection nd rchiving of trend dt, nd enles the presenttion of rchived trend dt in the ssocited softwre component. M-Historin
Migrating vrealize Automation to 7.3 or March 2018 vrealize Automation 7.3
 Migrting vrelize Automtion to 7.3 or 7.3.1 15 Mrch 2018 vrelize Automtion 7.3 You cn find the most up-to-dte technicl documenttion on the VMwre website t: https://docs.vmwre.com/ If you hve comments bout
Migrting vrelize Automtion to 7.3 or 7.3.1 15 Mrch 2018 vrelize Automtion 7.3 You cn find the most up-to-dte technicl documenttion on the VMwre website t: https://docs.vmwre.com/ If you hve comments bout
Small Business Networking
 Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd processes. Introducing technology
Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd processes. Introducing technology
Blackbaud s Mailwise Service Analyse Records Updated by MailWise
 Blckud s Milwise Service Anlyse Records Updted y MilWise To nlyse the updtes tht hve een performed y the import, run the relevnt queries from the list elow. The queries selected depend on the MilWise Services
Blckud s Milwise Service Anlyse Records Updted y MilWise To nlyse the updtes tht hve een performed y the import, run the relevnt queries from the list elow. The queries selected depend on the MilWise Services
UT1553B BCRT True Dual-port Memory Interface
 UTMC APPICATION NOTE UT553B BCRT True Dul-port Memory Interfce INTRODUCTION The UTMC UT553B BCRT is monolithic CMOS integrted circuit tht provides comprehensive MI-STD- 553B Bus Controller nd Remote Terminl
UTMC APPICATION NOTE UT553B BCRT True Dul-port Memory Interfce INTRODUCTION The UTMC UT553B BCRT is monolithic CMOS integrted circuit tht provides comprehensive MI-STD- 553B Bus Controller nd Remote Terminl
Upgrade. 13 FEB 2018 VMware Validated Design 4.2 VMware Validated Design for Software-Defined Data Center 4.2
 Upgrde 13 FEB 2018 VMwre Vlidted Design 4.2 VMwre Vlidted Design for Softwre-Defined Dt Center 4.2 Upgrde You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/
Upgrde 13 FEB 2018 VMwre Vlidted Design 4.2 VMwre Vlidted Design for Softwre-Defined Dt Center 4.2 Upgrde You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/
McAfee Network Security Platform
 NTBA Applince T-200 nd T-500 Quick Strt Guide Revision B McAfee Network Security Pltform 1 Instll the mounting rils Position the mounting rils correctly nd instll them t sme levels. At the front of the
NTBA Applince T-200 nd T-500 Quick Strt Guide Revision B McAfee Network Security Pltform 1 Instll the mounting rils Position the mounting rils correctly nd instll them t sme levels. At the front of the
Small Business Networking
 Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd processes. Introducing technology
Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd processes. Introducing technology
Intelligent Operations Use Case Deployment Using vrealize Suite Lifecycle Manager
 Intelligent Opertions Use Cse Deployment Using vrelize Suite Lifecycle Mnger 27 MAR 2018 VMwre Vlidted Design 4.2 VMwre Vlidted Design for Intelligent Opertions 4.2 You cn find the most up-to-dte technicl
Intelligent Opertions Use Cse Deployment Using vrelize Suite Lifecycle Mnger 27 MAR 2018 VMwre Vlidted Design 4.2 VMwre Vlidted Design for Intelligent Opertions 4.2 You cn find the most up-to-dte technicl
c360 Add-On Solutions
 c360 Add-On Solutions Functionlity Dynmics CRM 2011 c360 Record Editor Reltionship Explorer Multi-Field Serch Alerts Console c360 Core Productivity Pck "Does your tem resist using CRM becuse updting dt
c360 Add-On Solutions Functionlity Dynmics CRM 2011 c360 Record Editor Reltionship Explorer Multi-Field Serch Alerts Console c360 Core Productivity Pck "Does your tem resist using CRM becuse updting dt
Systems I. Logic Design I. Topics Digital logic Logic gates Simple combinational logic circuits
 Systems I Logic Design I Topics Digitl logic Logic gtes Simple comintionl logic circuits Simple C sttement.. C = + ; Wht pieces of hrdwre do you think you might need? Storge - for vlues,, C Computtion
Systems I Logic Design I Topics Digitl logic Logic gtes Simple comintionl logic circuits Simple C sttement.. C = + ; Wht pieces of hrdwre do you think you might need? Storge - for vlues,, C Computtion
Small Business Networking
 Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd processes. Introducing technology
Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd processes. Introducing technology
Simrad ES80. Software Release Note Introduction
 Simrd ES80 Softwre Relese 1.3.0 Introduction This document descries the chnges introduced with the new softwre version. Product: ES80 Softwre version: 1.3.0 This softwre controls ll functionlity in the
Simrd ES80 Softwre Relese 1.3.0 Introduction This document descries the chnges introduced with the new softwre version. Product: ES80 Softwre version: 1.3.0 This softwre controls ll functionlity in the
10.5 Graphing Quadratic Functions
 0.5 Grphing Qudrtic Functions Now tht we cn solve qudrtic equtions, we wnt to lern how to grph the function ssocited with the qudrtic eqution. We cll this the qudrtic function. Grphs of Qudrtic Functions
0.5 Grphing Qudrtic Functions Now tht we cn solve qudrtic equtions, we wnt to lern how to grph the function ssocited with the qudrtic eqution. We cll this the qudrtic function. Grphs of Qudrtic Functions
Sage CRM 2018 R1 Software Requirements and Mobile Features. Updated: May 2018
 Sge CRM 2018 R1 Softwre Requirements nd Mobile Fetures Updted: My 2018 2018, The Sge Group plc or its licensors. Sge, Sge logos, nd Sge product nd service nmes mentioned herein re the trdemrks of The Sge
Sge CRM 2018 R1 Softwre Requirements nd Mobile Fetures Updted: My 2018 2018, The Sge Group plc or its licensors. Sge, Sge logos, nd Sge product nd service nmes mentioned herein re the trdemrks of The Sge
Small Business Networking
 Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd processes. Introducing technology
Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd processes. Introducing technology
vcloud Director Tenant Portal Guide vcloud Director 9.1
 vcloud Director Tennt Portl Guide vcloud Director 9.1 You cn find the most up-to-dte technicl documenttion on the VMwre website t: https://docs.vmwre.com/ If you hve comments bout this documenttion, submit
vcloud Director Tennt Portl Guide vcloud Director 9.1 You cn find the most up-to-dte technicl documenttion on the VMwre website t: https://docs.vmwre.com/ If you hve comments bout this documenttion, submit
Guide for sending an Electronic Dental referral
 Guide for sending n Electronic Dentl referrl 1. Lunch Rego vi your Ptient Record System Open the Rego referrl templte vi your Ptient Record System: Exct / SOE: Open the ptient record, then click on Ptient
Guide for sending n Electronic Dentl referrl 1. Lunch Rego vi your Ptient Record System Open the Rego referrl templte vi your Ptient Record System: Exct / SOE: Open the ptient record, then click on Ptient
Agilent Mass Hunter Software
 Agilent Mss Hunter Softwre Quick Strt Guide Use this guide to get strted with the Mss Hunter softwre. Wht is Mss Hunter Softwre? Mss Hunter is n integrl prt of Agilent TOF softwre (version A.02.00). Mss
Agilent Mss Hunter Softwre Quick Strt Guide Use this guide to get strted with the Mss Hunter softwre. Wht is Mss Hunter Softwre? Mss Hunter is n integrl prt of Agilent TOF softwre (version A.02.00). Mss
Small Business Networking
 Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd business. Introducing technology
Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd business. Introducing technology
Welch Allyn CardioPerfect Workstation Installation Guide
 Welch Allyn CrdioPerfect Worksttion Instlltion Guide INSTALLING CARDIOPERFECT WORKSTATION SOFTWARE & ACCESSORIES ON A SINGLE PC For softwre version 1.6.6 or lter For network instlltion, plese refer to
Welch Allyn CrdioPerfect Worksttion Instlltion Guide INSTALLING CARDIOPERFECT WORKSTATION SOFTWARE & ACCESSORIES ON A SINGLE PC For softwre version 1.6.6 or lter For network instlltion, plese refer to
Small Business Networking
 Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd business. Introducing technology
Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd business. Introducing technology
Operational Verification. 21 AUG 2018 VMware Validated Design 4.3 VMware Validated Design for Software-Defined Data Center 4.3
 Opertionl Verifiction 21 AUG 2018 VMwre Vlidted Design 4.3 VMwre Vlidted Design for Softwre-Defined Dt Center 4.3 Opertionl Verifiction You cn find the most up-to-dte technicl documenttion on the VMwre
Opertionl Verifiction 21 AUG 2018 VMwre Vlidted Design 4.3 VMwre Vlidted Design for Softwre-Defined Dt Center 4.3 Opertionl Verifiction You cn find the most up-to-dte technicl documenttion on the VMwre
Small Business Networking
 Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd business. Introducing technology
Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd business. Introducing technology
IST 220: Ch3-Transport Layer
 ST 220: Ch3-Trns Lyer Abdullh Konk School of nformtion Sciences nd Technology Penn Stte Berks Lerning Objectives. Understnd position of trns lyer in nternet model. Understnd rtionle for extence of trns
ST 220: Ch3-Trns Lyer Abdullh Konk School of nformtion Sciences nd Technology Penn Stte Berks Lerning Objectives. Understnd position of trns lyer in nternet model. Understnd rtionle for extence of trns
Use Case Deployment Using vrealize Suite Lifecycle Manager. Modified on 21 DEC 2017 VMware Validated Design 4.1
 Use Cse Deployment Using vrelize Suite Lifecycle Mnger Modified on 21 DEC 2017 VMwre Vlidted Design 4.1 You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/
Use Cse Deployment Using vrelize Suite Lifecycle Mnger Modified on 21 DEC 2017 VMwre Vlidted Design 4.1 You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/
Epson Projector Content Manager Operation Guide
 Epson Projector Content Mnger Opertion Guide Contents 2 Introduction to the Epson Projector Content Mnger Softwre 3 Epson Projector Content Mnger Fetures... 4 Setting Up the Softwre for the First Time
Epson Projector Content Mnger Opertion Guide Contents 2 Introduction to the Epson Projector Content Mnger Softwre 3 Epson Projector Content Mnger Fetures... 4 Setting Up the Softwre for the First Time
Polycom RealPresence Media Editor Quick Start
 Polycom RelPresence Medi Editor Quick Strt Version 5.5 Novemer 2011 3725-75201-001/A Trdemrk Informtion Polycom, the Polycom Tringles logo, nd the nmes nd mrks ssocited with Polycom s products re trdemrks
Polycom RelPresence Medi Editor Quick Strt Version 5.5 Novemer 2011 3725-75201-001/A Trdemrk Informtion Polycom, the Polycom Tringles logo, nd the nmes nd mrks ssocited with Polycom s products re trdemrks
How to Design REST API? Written Date : March 23, 2015
 Visul Prdigm How Design REST API? Turil How Design REST API? Written Dte : Mrch 23, 2015 REpresenttionl Stte Trnsfer, n rchitecturl style tht cn be used in building networked pplictions, is becoming incresingly
Visul Prdigm How Design REST API? Turil How Design REST API? Written Dte : Mrch 23, 2015 REpresenttionl Stte Trnsfer, n rchitecturl style tht cn be used in building networked pplictions, is becoming incresingly
2 Computing all Intersections of a Set of Segments Line Segment Intersection
 15-451/651: Design & Anlysis of Algorithms Novemer 14, 2016 Lecture #21 Sweep-Line nd Segment Intersection lst chnged: Novemer 8, 2017 1 Preliminries The sweep-line prdigm is very powerful lgorithmic design
15-451/651: Design & Anlysis of Algorithms Novemer 14, 2016 Lecture #21 Sweep-Line nd Segment Intersection lst chnged: Novemer 8, 2017 1 Preliminries The sweep-line prdigm is very powerful lgorithmic design
Small Business Networking
 Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd business. Introducing technology
Why network is n essentil productivity tool for ny smll business Effective technology is essentil for smll businesses looking to increse the productivity of their people nd business. Introducing technology
If you are at the university, either physically or via the VPN, you can download the chapters of this book as PDFs.
 Lecture 5 Wlks, Trils, Pths nd Connectedness Reding: Some of the mteril in this lecture comes from Section 1.2 of Dieter Jungnickel (2008), Grphs, Networks nd Algorithms, 3rd edition, which is ville online
Lecture 5 Wlks, Trils, Pths nd Connectedness Reding: Some of the mteril in this lecture comes from Section 1.2 of Dieter Jungnickel (2008), Grphs, Networks nd Algorithms, 3rd edition, which is ville online
COMP 423 lecture 11 Jan. 28, 2008
 COMP 423 lecture 11 Jn. 28, 2008 Up to now, we hve looked t how some symols in n lphet occur more frequently thn others nd how we cn sve its y using code such tht the codewords for more frequently occuring
COMP 423 lecture 11 Jn. 28, 2008 Up to now, we hve looked t how some symols in n lphet occur more frequently thn others nd how we cn sve its y using code such tht the codewords for more frequently occuring
McAfee Network Security Platform
 NS7x00 Quick Strt Guide Revision D McAfee Network Security Pltform This quick strt guide explins how to quickly set up nd ctivte your McAfee Network Security Pltform NS7100, NS7200, nd NS7300 Sensors in
NS7x00 Quick Strt Guide Revision D McAfee Network Security Pltform This quick strt guide explins how to quickly set up nd ctivte your McAfee Network Security Pltform NS7100, NS7200, nd NS7300 Sensors in
McAfee Network Security Platform
 Revision D McAfee Network Security Pltform (NS5x00 Quick Strt Guide) This quick strt guide explins how to quickly set up nd ctivte your McAfee Network Security Pltform NS5100 nd NS5200 Sensors in inline
Revision D McAfee Network Security Pltform (NS5x00 Quick Strt Guide) This quick strt guide explins how to quickly set up nd ctivte your McAfee Network Security Pltform NS5100 nd NS5200 Sensors in inline
Upgrading from vrealize Automation 7.1 or Later to June 2018 vrealize Automation 7.4
 Upgrding from vrelize Automtion 7.1 or Lter to 7.4 15 June 2018 vrelize Automtion 7.4 You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/ If you hve comments
Upgrding from vrelize Automtion 7.1 or Lter to 7.4 15 June 2018 vrelize Automtion 7.4 You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/ If you hve comments
Presentation Martin Randers
 Presenttion Mrtin Rnders Outline Introduction Algorithms Implementtion nd experiments Memory consumption Summry Introduction Introduction Evolution of species cn e modelled in trees Trees consist of nodes
Presenttion Mrtin Rnders Outline Introduction Algorithms Implementtion nd experiments Memory consumption Summry Introduction Introduction Evolution of species cn e modelled in trees Trees consist of nodes
Monitoring and Alerting. 27 MAR 2018 VMware Validated Design 4.2 VMware Validated Design for Software-Defined Data Center 4.2
 Monitoring nd ing 27 MAR 2018 VMwre Vlidted Design 4.2 VMwre Vlidted Design for Softwre-Defined Dt Center 4.2 Monitoring nd ing You cn find the most up-to-dte technicl documenttion on the VMwre wesite
Monitoring nd ing 27 MAR 2018 VMwre Vlidted Design 4.2 VMwre Vlidted Design for Softwre-Defined Dt Center 4.2 Monitoring nd ing You cn find the most up-to-dte technicl documenttion on the VMwre wesite
What are suffix trees?
 Suffix Trees 1 Wht re suffix trees? Allow lgorithm designers to store very lrge mount of informtion out strings while still keeping within liner spce Allow users to serch for new strings in the originl
Suffix Trees 1 Wht re suffix trees? Allow lgorithm designers to store very lrge mount of informtion out strings while still keeping within liner spce Allow users to serch for new strings in the originl
McAfee Network Security Platform
 Mnger Applince Quick Strt Guide Revision B McAfee Network Security Pltform This guide is high-level description of how to instll nd configure the Mnger Applince. For more detiled instlltion informtion,
Mnger Applince Quick Strt Guide Revision B McAfee Network Security Pltform This guide is high-level description of how to instll nd configure the Mnger Applince. For more detiled instlltion informtion,
Backup and Restore. 20 NOV 2018 VMware Validated Design 4.3 VMware Validated Design for Software-Defined Data Center 4.3
 20 NOV 2018 VMwre Vlidted Design 4.3 VMwre Vlidted Design for Softwre-Defined Dt Center 4.3 You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/ If you hve
20 NOV 2018 VMwre Vlidted Design 4.3 VMwre Vlidted Design for Softwre-Defined Dt Center 4.3 You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/ If you hve
Monitoring and Alerting. 19 SEP 2017 VMware Validated Design 4.1 VMware Validated Design for Software-Defined Data Center 4.1
 Monitoring nd ing 19 SEP 2017 VMwre Vlidted Design 4.1 VMwre Vlidted Design for Softwre-Defined Dt Center 4.1 Monitoring nd ing You cn find the most up-to-dte technicl documenttion on the VMwre wesite
Monitoring nd ing 19 SEP 2017 VMwre Vlidted Design 4.1 VMwre Vlidted Design for Softwre-Defined Dt Center 4.1 Monitoring nd ing You cn find the most up-to-dte technicl documenttion on the VMwre wesite
pdfapilot Server 2 Manual
 pdfpilot Server 2 Mnul 2011 by clls softwre gmbh Schönhuser Allee 6/7 D 10119 Berlin Germny info@cllssoftwre.com www.cllssoftwre.com Mnul clls pdfpilot Server 2 Pge 2 clls pdfpilot Server 2 Mnul Lst modified:
pdfpilot Server 2 Mnul 2011 by clls softwre gmbh Schönhuser Allee 6/7 D 10119 Berlin Germny info@cllssoftwre.com www.cllssoftwre.com Mnul clls pdfpilot Server 2 Pge 2 clls pdfpilot Server 2 Mnul Lst modified:
TECHNICAL NOTE MANAGING JUNIPER SRX PCAP DATA. Displaying the PCAP Data Column
 TECHNICAL NOTE MANAGING JUNIPER SRX PCAP DATA APRIL 2011 If your STRM Console is configured to integrte with the Juniper JunOS Pltform DSM, STRM cn receive, process, nd store Pcket Cpture (PCAP) dt from
TECHNICAL NOTE MANAGING JUNIPER SRX PCAP DATA APRIL 2011 If your STRM Console is configured to integrte with the Juniper JunOS Pltform DSM, STRM cn receive, process, nd store Pcket Cpture (PCAP) dt from
MA1008. Calculus and Linear Algebra for Engineers. Course Notes for Section B. Stephen Wills. Department of Mathematics. University College Cork
 MA1008 Clculus nd Liner Algebr for Engineers Course Notes for Section B Stephen Wills Deprtment of Mthemtics University College Cork s.wills@ucc.ie http://euclid.ucc.ie/pges/stff/wills/teching/m1008/ma1008.html
MA1008 Clculus nd Liner Algebr for Engineers Course Notes for Section B Stephen Wills Deprtment of Mthemtics University College Cork s.wills@ucc.ie http://euclid.ucc.ie/pges/stff/wills/teching/m1008/ma1008.html
McAfee Network Security Platform
 10/100/1000 Copper Active Fil-Open Bypss Kit Guide Revision E McAfee Network Security Pltform This document descries the contents nd how to instll the McAfee 10/100/1000 Copper Active Fil-Open Bypss Kit
10/100/1000 Copper Active Fil-Open Bypss Kit Guide Revision E McAfee Network Security Pltform This document descries the contents nd how to instll the McAfee 10/100/1000 Copper Active Fil-Open Bypss Kit
Upgrading from vrealize Automation to 7.3 or May 2018 vrealize Automation 7.3
 Upgrding from vrelize Automtion 6.2.5 to 7.3 or 7.3.1 03 My 2018 vrelize Automtion 7.3 You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/ If you hve comments
Upgrding from vrelize Automtion 6.2.5 to 7.3 or 7.3.1 03 My 2018 vrelize Automtion 7.3 You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/ If you hve comments
Data sharing in OpenMP
 Dt shring in OpenMP Polo Burgio polo.burgio@unimore.it Outline Expressing prllelism Understnding prllel threds Memory Dt mngement Dt cluses Synchroniztion Brriers, locks, criticl sections Work prtitioning
Dt shring in OpenMP Polo Burgio polo.burgio@unimore.it Outline Expressing prllelism Understnding prllel threds Memory Dt mngement Dt cluses Synchroniztion Brriers, locks, criticl sections Work prtitioning
Lecture 10 Evolutionary Computation: Evolution strategies and genetic programming
 Lecture 10 Evolutionry Computtion: Evolution strtegies nd genetic progrmming Evolution strtegies Genetic progrmming Summry Negnevitsky, Person Eduction, 2011 1 Evolution Strtegies Another pproch to simulting
Lecture 10 Evolutionry Computtion: Evolution strtegies nd genetic progrmming Evolution strtegies Genetic progrmming Summry Negnevitsky, Person Eduction, 2011 1 Evolution Strtegies Another pproch to simulting
Caches I. CSE 351 Spring Instructor: Ruth Anderson
 L16: Cches I Cches I CSE 351 Spring 2017 Instructor: Ruth Anderson Teching Assistnts: Dyln Johnson Kevin Bi Linxing Preston Jing Cody Ohlsen Yufng Sun Joshu Curtis L16: Cches I Administrivi Homework 3,
L16: Cches I Cches I CSE 351 Spring 2017 Instructor: Ruth Anderson Teching Assistnts: Dyln Johnson Kevin Bi Linxing Preston Jing Cody Ohlsen Yufng Sun Joshu Curtis L16: Cches I Administrivi Homework 3,
vrealize Suite 7.0 Backup and Restore by Using EMC Avamar vrealize Suite 7.0
 vrelize Suite 7.0 Bckup nd Restore y Using EMC Avmr vrelize Suite 7.0 You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/ If you hve comments out this documenttion,
vrelize Suite 7.0 Bckup nd Restore y Using EMC Avmr vrelize Suite 7.0 You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/ If you hve comments out this documenttion,
Scenarios for IT Automating IT. 21 AUG 2018 VMware Validated Design 4.3 VMware Validated Design for IT Automating IT 4.3
 Scenrios for IT Automting IT 21 AUG 2018 VMwre Vlidted Design 4.3 VMwre Vlidted Design for IT Automting IT 4.3 Scenrios for IT Automting IT You cn find the most up-to-dte technicl documenttion on the VMwre
Scenrios for IT Automting IT 21 AUG 2018 VMwre Vlidted Design 4.3 VMwre Vlidted Design for IT Automting IT 4.3 Scenrios for IT Automting IT You cn find the most up-to-dte technicl documenttion on the VMwre
Lecture Notes 14 : Public-Key Infrastructure
 6.857 Computer and Network Security October 24, 2002 Lecture Notes 14 : Public-Key Infrastructure Lecturer: Ron Rivest Scribe: Armour/Johann-Berkel/Owsley/Quealy [These notes come from Fall 2001. These
6.857 Computer and Network Security October 24, 2002 Lecture Notes 14 : Public-Key Infrastructure Lecturer: Ron Rivest Scribe: Armour/Johann-Berkel/Owsley/Quealy [These notes come from Fall 2001. These
Caches I. CSE 351 Autumn Instructor: Justin Hsia
 L01: Intro, L01: L16: Combintionl Introduction Cches I Logic CSE369, CSE351, Autumn 2016 Cches I CSE 351 Autumn 2016 Instructor: Justin Hsi Teching Assistnts: Chris M Hunter Zhn John Kltenbch Kevin Bi
L01: Intro, L01: L16: Combintionl Introduction Cches I Logic CSE369, CSE351, Autumn 2016 Cches I CSE 351 Autumn 2016 Instructor: Justin Hsi Teching Assistnts: Chris M Hunter Zhn John Kltenbch Kevin Bi
OUTPUT DELIVERY SYSTEM
 Differences in ODS formtting for HTML with Proc Print nd Proc Report Lur L. M. Thornton, USDA-ARS, Animl Improvement Progrms Lortory, Beltsville, MD ABSTRACT While Proc Print is terrific tool for dt checking
Differences in ODS formtting for HTML with Proc Print nd Proc Report Lur L. M. Thornton, USDA-ARS, Animl Improvement Progrms Lortory, Beltsville, MD ABSTRACT While Proc Print is terrific tool for dt checking
Suffix trees, suffix arrays, BWT
 ALGORITHMES POUR LA BIO-INFORMATIQUE ET LA VISUALISATION COURS 3 Rluc Uricru Suffix trees, suffix rrys, BWT Bsed on: Suffix trees nd suffix rrys presenttion y Him Kpln Suffix trees course y Pco Gomez Liner-Time
ALGORITHMES POUR LA BIO-INFORMATIQUE ET LA VISUALISATION COURS 3 Rluc Uricru Suffix trees, suffix rrys, BWT Bsed on: Suffix trees nd suffix rrys presenttion y Him Kpln Suffix trees course y Pco Gomez Liner-Time
Distributed Systems Principles and Paradigms. Chapter 11: Distributed File Systems
 Distriuted Systems Priniples nd Prdigms Mrten vn Steen VU Amsterdm, Dept. Computer Siene steen@s.vu.nl Chpter 11: Distriuted File Systems Version: Deemer 10, 2012 2 / 14 Distriuted File Systems Distriuted
Distriuted Systems Priniples nd Prdigms Mrten vn Steen VU Amsterdm, Dept. Computer Siene steen@s.vu.nl Chpter 11: Distriuted File Systems Version: Deemer 10, 2012 2 / 14 Distriuted File Systems Distriuted
Sage CRM 2017 R2 Software Requirements and Mobile Features. Revision: IMP-MAT-ENG-2017R2-2.0 Updated: August 2017
 Sge CRM 2017 R2 Softwre Requirements nd Mobile Fetures Revision: IMP-MAT-ENG-2017R2-2.0 Updted: August 2017 2017, The Sge Group plc or its licensors. Sge, Sge logos, nd Sge product nd service nmes mentioned
Sge CRM 2017 R2 Softwre Requirements nd Mobile Fetures Revision: IMP-MAT-ENG-2017R2-2.0 Updted: August 2017 2017, The Sge Group plc or its licensors. Sge, Sge logos, nd Sge product nd service nmes mentioned
Data Integrity Proofs in Cloud Computing
 Technovision-2014: 1st Interntionl Conference t SITS, Nrhe, Pune on April 5-6, 2014 Dt Integrity Proofs in Cloud Computing Deshmukh Ashwini B. Deptt. of Computer Science nd Engg. Ambjogi, Dist. Beed, Mhrshtr
Technovision-2014: 1st Interntionl Conference t SITS, Nrhe, Pune on April 5-6, 2014 Dt Integrity Proofs in Cloud Computing Deshmukh Ashwini B. Deptt. of Computer Science nd Engg. Ambjogi, Dist. Beed, Mhrshtr
Lexical Analysis: Constructing a Scanner from Regular Expressions
 Lexicl Anlysis: Constructing Scnner from Regulr Expressions Gol Show how to construct FA to recognize ny RE This Lecture Convert RE to n nondeterministic finite utomton (NFA) Use Thompson s construction
Lexicl Anlysis: Constructing Scnner from Regulr Expressions Gol Show how to construct FA to recognize ny RE This Lecture Convert RE to n nondeterministic finite utomton (NFA) Use Thompson s construction
Upgrade. 17 JUL 2018 VMware Validated Design 4.3 VMware Validated Design for Software-Defined Data Center 4.3
 Upgrde 17 JUL 2018 VMwre Vlidted Design 4.3 VMwre Vlidted Design for Softwre-Defined Dt Center 4.3 Upgrde You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/
Upgrde 17 JUL 2018 VMwre Vlidted Design 4.3 VMwre Vlidted Design for Softwre-Defined Dt Center 4.3 Upgrde You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/
Distributed Systems Principles and Paradigms
 Distriuted Systems Priniples nd Prdigms Christoph Dorn Distriuted Systems Group, Vienn University of Tehnology.dorn@infosys.tuwien..t http://www.infosys.tuwien..t/stff/dorn Slides dpted from Mrten vn Steen,
Distriuted Systems Priniples nd Prdigms Christoph Dorn Distriuted Systems Group, Vienn University of Tehnology.dorn@infosys.tuwien..t http://www.infosys.tuwien..t/stff/dorn Slides dpted from Mrten vn Steen,
Sage CRM 2017 R3 Software Requirements and Mobile Features. Updated: August 2017
 Sge CRM 2017 R3 Softwre Requirements nd Mobile Fetures Updted: August 2017 2017, The Sge Group plc or its licensors. Sge, Sge logos, nd Sge product nd service nmes mentioned herein re the trdemrks of The
Sge CRM 2017 R3 Softwre Requirements nd Mobile Fetures Updted: August 2017 2017, The Sge Group plc or its licensors. Sge, Sge logos, nd Sge product nd service nmes mentioned herein re the trdemrks of The
Symbol Table management
 TDDD Compilers nd interpreters TDDB44 Compiler Construction Symol Tles Symol Tles in the Compiler Symol Tle mngement source progrm Leicl nlysis Syntctic nlysis Semntic nlysis nd Intermedite code gen Code
TDDD Compilers nd interpreters TDDB44 Compiler Construction Symol Tles Symol Tles in the Compiler Symol Tle mngement source progrm Leicl nlysis Syntctic nlysis Semntic nlysis nd Intermedite code gen Code
A Tautology Checker loosely related to Stålmarck s Algorithm by Martin Richards
 A Tutology Checker loosely relted to Stålmrck s Algorithm y Mrtin Richrds mr@cl.cm.c.uk http://www.cl.cm.c.uk/users/mr/ University Computer Lortory New Museum Site Pemroke Street Cmridge, CB2 3QG Mrtin
A Tutology Checker loosely relted to Stålmrck s Algorithm y Mrtin Richrds mr@cl.cm.c.uk http://www.cl.cm.c.uk/users/mr/ University Computer Lortory New Museum Site Pemroke Street Cmridge, CB2 3QG Mrtin
Fig.25: the Role of LEX
 The Lnguge for Specifying Lexicl Anlyzer We shll now study how to uild lexicl nlyzer from specifiction of tokens in the form of list of regulr expressions The discussion centers round the design of n existing
The Lnguge for Specifying Lexicl Anlyzer We shll now study how to uild lexicl nlyzer from specifiction of tokens in the form of list of regulr expressions The discussion centers round the design of n existing
Upgrading from vrealize Automation 6.2 to 7.1
 Upgrding from vrelize Automtion 6.2 to 7.1 vrelize Automtion 7.1 This document supports the version of ech product listed nd supports ll susequent versions until the document is replced y new edition.
Upgrding from vrelize Automtion 6.2 to 7.1 vrelize Automtion 7.1 This document supports the version of ech product listed nd supports ll susequent versions until the document is replced y new edition.
y^fi Payment Card Industry (PCI) Data Security Standard Attestation of Compliance for Onsite Assessments - Service Providers Version 3.
 y^fi Security Stndrds Council Pyment Crd Industry (PCI) t Security Stndrd Attesttion of Complince for Onsite Assessments - Service Providers Version 3.2 Section 1: Assessment Informtion Instructions for
y^fi Security Stndrds Council Pyment Crd Industry (PCI) t Security Stndrd Attesttion of Complince for Onsite Assessments - Service Providers Version 3.2 Section 1: Assessment Informtion Instructions for
Tries. Yufei Tao KAIST. April 9, Y. Tao, April 9, 2013 Tries
 Tries Yufei To KAIST April 9, 2013 Y. To, April 9, 2013 Tries In this lecture, we will discuss the following exct mtching prolem on strings. Prolem Let S e set of strings, ech of which hs unique integer
Tries Yufei To KAIST April 9, 2013 Y. To, April 9, 2013 Tries In this lecture, we will discuss the following exct mtching prolem on strings. Prolem Let S e set of strings, ech of which hs unique integer
McAfee Network Security Platform
 Revision C McAfee Network Security Pltform (40 Gigit Active Fil-Open Bypss Kit Guide) McAfee Network Security Pltform IPS Sensors, when deployed in-line, route ll incoming trffic through designted port
Revision C McAfee Network Security Pltform (40 Gigit Active Fil-Open Bypss Kit Guide) McAfee Network Security Pltform IPS Sensors, when deployed in-line, route ll incoming trffic through designted port
An Overview of PDF/X. Dov Isaacs Principal Scientist, Workflow & Interoperability Chair, ISO TC130 WG2/TF2, PDF/X April 27, 2011
 An Overview of PDF/X Dov Iscs Principl Scientist, Workflow & Interoperbility Chir, ISO TC130 WG2/TF2, PDF/X April 27, 2011 PDF s n Adobe File Formt 1993 to 2008 PDF formt introduced by Adobe with Acrobt
An Overview of PDF/X Dov Iscs Principl Scientist, Workflow & Interoperbility Chir, ISO TC130 WG2/TF2, PDF/X April 27, 2011 PDF s n Adobe File Formt 1993 to 2008 PDF formt introduced by Adobe with Acrobt
McAfee Network Security Platform
 NS7x50 Quick Strt Guide Revision B McAfee Network Security Pltform This quick strt guide explins how to quickly set up nd ctivte your McAfee Network Security Pltform NS7150, NS7250, nd NS7350 Sensors in
NS7x50 Quick Strt Guide Revision B McAfee Network Security Pltform This quick strt guide explins how to quickly set up nd ctivte your McAfee Network Security Pltform NS7150, NS7250, nd NS7350 Sensors in
Siebel Business Analytics Applications Upgrade Guide. Version May 2006
 Sieel Business Anlytics Applictions Upgrde Guide Version 7.8.4 My 2006 Copyright 2005, 2006, Orcle. All rights reserved. The Progrms (which include oth the softwre nd documenttion) contin proprietry informtion;
Sieel Business Anlytics Applictions Upgrde Guide Version 7.8.4 My 2006 Copyright 2005, 2006, Orcle. All rights reserved. The Progrms (which include oth the softwre nd documenttion) contin proprietry informtion;
In the last lecture, we discussed how valid tokens may be specified by regular expressions.
 LECTURE 5 Scnning SYNTAX ANALYSIS We know from our previous lectures tht the process of verifying the syntx of the progrm is performed in two stges: Scnning: Identifying nd verifying tokens in progrm.
LECTURE 5 Scnning SYNTAX ANALYSIS We know from our previous lectures tht the process of verifying the syntx of the progrm is performed in two stges: Scnning: Identifying nd verifying tokens in progrm.
Scenarios. VMware Validated Design for IT Automating IT 4.0 EN
 Scenrios VMwre Vlidted Design for IT Automting IT 4.0 This document supports the version of ech product listed nd supports ll susequent versions until the document is replced y new edition. To check for
Scenrios VMwre Vlidted Design for IT Automting IT 4.0 This document supports the version of ech product listed nd supports ll susequent versions until the document is replced y new edition. To check for
EasyMP Multi PC Projection Operation Guide
 EsyMP Multi PC Projection Opertion Guide Contents 2 Introduction to EsyMP Multi PC Projection 5 EsyMP Multi PC Projection Fetures... 6 Connection to Vrious Devices... 6 Four-Pnel Disply... 6 Chnge Presenters
EsyMP Multi PC Projection Opertion Guide Contents 2 Introduction to EsyMP Multi PC Projection 5 EsyMP Multi PC Projection Fetures... 6 Connection to Vrious Devices... 6 Four-Pnel Disply... 6 Chnge Presenters
Epson iprojection Operation Guide (Windows/Mac)
 Epson iprojection Opertion Guide (Windows/Mc) Contents 2 Introduction to Epson iprojection 5 Epson iprojection Fetures... 6 Connection to Vrious Devices... 6 Four-Pnel Disply... 6 Chnge Presenters nd Projection
Epson iprojection Opertion Guide (Windows/Mc) Contents 2 Introduction to Epson iprojection 5 Epson iprojection Fetures... 6 Connection to Vrious Devices... 6 Four-Pnel Disply... 6 Chnge Presenters nd Projection
GENERATING ORTHOIMAGES FOR CLOSE-RANGE OBJECTS BY AUTOMATICALLY DETECTING BREAKLINES
 GENEATING OTHOIMAGES FO CLOSE-ANGE OBJECTS BY AUTOMATICALLY DETECTING BEAKLINES Efstrtios Stylinidis 1, Lzros Sechidis 1, Petros Ptis 1, Spiros Sptls 2 Aristotle University of Thessloniki 1 Deprtment of
GENEATING OTHOIMAGES FO CLOSE-ANGE OBJECTS BY AUTOMATICALLY DETECTING BEAKLINES Efstrtios Stylinidis 1, Lzros Sechidis 1, Petros Ptis 1, Spiros Sptls 2 Aristotle University of Thessloniki 1 Deprtment of
Ensuring PCI DSS Compliance with the Mist Learning WLAN THE SAFE CHOICE FOR MISSION CRITICAL WIRELESS NETWORKS IN PCI ENVIRONMENTS
 Ensuring PCI DSS Complince with the Mist Lerning WLAN THE SAFE CHOICE FOR MISSION CRITICAL WIRELESS NETWORKS IN PCI ENVIRONMENTS Tble of Contents Ensuring PCI DSS Complince with the Mist Lerning WLAN...
Ensuring PCI DSS Complince with the Mist Lerning WLAN THE SAFE CHOICE FOR MISSION CRITICAL WIRELESS NETWORKS IN PCI ENVIRONMENTS Tble of Contents Ensuring PCI DSS Complince with the Mist Lerning WLAN...
Scenarios. VMware Validated Design 4.0 VMware Validated Design for IT Automating IT 4.0
 Scenrios VMwre Vlidted Design 4.0 VMwre Vlidted Design for IT Automting IT 4.0 Scenrios You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/ If you hve comments
Scenrios VMwre Vlidted Design 4.0 VMwre Vlidted Design for IT Automting IT 4.0 Scenrios You cn find the most up-to-dte technicl documenttion on the VMwre wesite t: https://docs.vmwre.com/ If you hve comments
Scenarios. VMware Validated Design for IT Automating IT EN
 Scenrios VMwre Vlidted Design for IT Automting IT 3.0.2 This document supports the version of ech product listed nd supports ll susequent versions until the document is replced y new edition. To check
Scenrios VMwre Vlidted Design for IT Automting IT 3.0.2 This document supports the version of ech product listed nd supports ll susequent versions until the document is replced y new edition. To check
Online Portal Guide. Access your policy information, documentation, claim forms and claims history easily and securely.
 Online Portl Guide Access your policy informtion, documenttion, clim forms nd clims history esily nd securely. version dte: 12/2017 YOUR ONLINE PORTAL ACCESS URL & REGIONAL CONTACTS HONG KONG SINGAPORE
Online Portl Guide Access your policy informtion, documenttion, clim forms nd clims history esily nd securely. version dte: 12/2017 YOUR ONLINE PORTAL ACCESS URL & REGIONAL CONTACTS HONG KONG SINGAPORE
Fall 2010/Lecture 32 1
 CS 426 (Fall 2010) Key Distribution & Agreement Fall 2010/Lecture 32 1 Outline Key agreement without t using public keys Distribution of public keys, with public key certificates Diffie-Hellman Protocol
CS 426 (Fall 2010) Key Distribution & Agreement Fall 2010/Lecture 32 1 Outline Key agreement without t using public keys Distribution of public keys, with public key certificates Diffie-Hellman Protocol
EasyMP Network Projection Operation Guide
 EsyMP Network Projection Opertion Guide Contents 2 Introduction to EsyMP Network Projection EsyMP Network Projection Fetures... 5 Disply Options... 6 Multi-Screen Disply Function... 6 Movie Sending Mode...
EsyMP Network Projection Opertion Guide Contents 2 Introduction to EsyMP Network Projection EsyMP Network Projection Fetures... 5 Disply Options... 6 Multi-Screen Disply Function... 6 Movie Sending Mode...
