SIEM Use Cases 45 use cases for Security Monitoring
|
|
|
- Oliver Rose
- 5 years ago
- Views:
Transcription
1 SIEM Use Cases 45 use cases fr Security Mnitring
2 Paladin - SIEM Use Cases Use Case 02 Descriptin DMZ Jumping This rule will fire when cnnectins seemed t be bridged acrss the netwrk's DMZ. DMZ Reverse Tunnel This rule will fire when cnnectins seemed t be bridged acrss the netwrk's DMZ thrugh a reverse tunnel. Excessive Database Cnnectins Rule detects an excessive number f successful database cnnectins. Excessive Firewall Accepts Acrss Multiple Hsts Reprts excessive Firewall Accepts acrss multiple hsts. Mre than 100 events were detected acrss at least 100 unique destinatin IP addresses in 5 minutes. Excessive Firewall Accepts Frm Multiple Surces t a Single Destinatin Reprts excessive Firewall Accepts t the same destinatin frm at least 100 unique surce IP addresses in 5 minutes. Excessive Firewall Denies frm Single Surce Reprts excessive firewall denies frm a single hst. Detects mre than 400 firewall deny attempts frm a single surce t a single destinatin within 5 minutes. Lng Duratin Flw Invlving a Remte Hst Reprts a flw fr cmmunicating t r frm the Internet with a sustained duratin f mre than 48 hurs. This is nt typical behavir fr mst applicatins. We recmmend that yu investigate the hst fr ptential malware infectins. Lng Duratin ICMP Flws Detectin f ICMP packets between hsts that last a lng time. This is rare and shuldn't ever ccur. Outbund Cnnectin t a Freign Cuntry Reprts successful lgins r access frm an IP address knwn t be in a cuntry that des nt have remte access right. Befre yu enable this rule, we recmmend that yu cnfigure the activelist: Cuntries with n Remte Access building blck. Ptential Hneypt Access Reprts an event that was targeting r surced frm a hneypt r tarpit defined address. Befre enabling this rule, yu must cnfigure the Activelist: Hneypt like addresses building blck and create the apprpriate sentry frm the Netwrk Surveillance interface. Remte Access frm Freign Cuntry Reprts successful lgins r access frm an IP address knwn t be in a cuntry that des nt have remte access right. Befre yu enable this rule, we recmmend that yu cnfigure the Activelist: Cuntries with n Remte Access building blck.
3 Paladin - SIEM Use Cases Use Case Remte Inbund Cmmunicatin frm a Freign Cuntry 03 Descriptin Reprts traffic frm an IP address knwn t be in a cuntry that des nt have remte access right. Befre yu enable this rule, we recmmend that yu cnfigure the Activelist: Cuntries with n Remte Access building blck. SMTP and DNS have been remved frm this test as yu have little cntrl ver that activity. Yu may als have t remve WebServers in the DMZ that are ften prbed by remte hsts with web scanners Single IP with Multiple MAC Addresses This rule will fire when a single IP's MAC address changes multiple times ver a perid f time. Systems using many different prtcls Lcal system cnnecting t the internet n mre than 50 DST prts in ne hur. Cnnectins must be successful. This rule can be edited t als detect failed cmmunicatins which may als be useful. Lgin Failures Fllwed By Success t the same Destinatin IP Reprts multiple lg in failures t a single hst, fllwed by a successful lg in t the hst. Lgin Failures Fllwed By Success t the same Surce IP Reprts multiple lg in failures t a single hst, fllwed by a successful lg in t the hst. Lgin Failures Fllwed By Success t the same Username Reprts multiple lg in failure fllwed by a successful lgin frm the same user. Lgin Failure t Disabled Accunt Reprts a hst lgin message frm a disabled user accunt. If the user is n lnger a member f the rganizatin, we recmmend that yu investigate any ther received authenticatin messages frm the same user. Lgin Failure t Expired Accunt Reprts a hst lgin failure message frm an expired user accunt knwn. If the user is n lnger a member f the rganizatin, we recmmend that yu investigate any ther received authenticatin messages. Lgin Successful After Scan Attempt Reprts a successful lg in t a hst after recn has been perfrmed against the netwrk. Multiple Lgin Failures fr Single Username Reprts authenticatin failures fr the same username.
4 Paladin - SIEM Use Cases Use Case 04 Descriptin Multiple Lgin Failures frm the Same Surce Reprts authenticatin failures n the same surce IP address mre than three times, acrss mre than three destinatin IP addresses within 10 minutes. Multiple Lgin Failures t the Same Destinatin Reprts authenticatin failures n the same destinatin IP address mre than ten times, frm mre than 10 surce IP addresses within 10 minutes. Multiple VIP Lgin Failures N Activity fr 60 Days Reprts multiple lg in failures t a VIP PBX. This accunt has nt lgged in fr ver 60 days Pssible Shared Accunts Detectin f Shared Accunts. Yu will need t add in additinal false psitive system accunts t the and NOT when the event username matches the fllwing...". " Repeat Nn-Windws Lgin Failures Reprts when a surce IP address causes an authenticatin failure event at least 7 times t a single destinatin within 5 minutes. Repeat Windws Lgin Failures Reprts when a surce IP address causes an authenticatin failure event at least 9 times t a single Windws hst within 1 minute. VPN Sneak Attack Check frm where remte users are cnnecting, and what they are accessing. A VPN cnnectin access can be misused t gain access t the intranet. Anmalus Prts, Services and Unpatched Hsts r Netwrk Devices Unusual traffic is identified as a ptential intrusin; n signatures are invlved in the prcess, s it is mre likely t detect new attacks fr which signatures are yet t be develped. Brute Frce Attack Check fr attempts t gain access t a system by using multiple accunts with multiple passwrds. Privileged user abuse Mnitr misuse f access f privileged user access such as admin r rt access t perfrm malicius activities.
5 Paladin - SIEM Use Cases Advanced Use Cases 01 Unauthrized applicatin access 02 Which systems have suspicius access/applicatin activity? Are terminated accunts still being used? Which accunts are being used frm suspicius lcatins? High risk user access mnitring Privileged user mnitring Wrm/malware prpagatin mnitring Malware beacn mnitring CnC access mnitring CnC Terminatin mnitring Malware/Wrm prpagatin mnitring Anti-virus status/infectin trends 03 Hacker detectin Wh is attacking me and where are they attacking frm? Which f my internal systems are they attacking? 04 VPN Sneak Attack 05 Anmalus Prts, Services and Unpatched Hsts/Netwrk Devices 06 Brute Frce Attack 07 Privileged User Abuse 05
6 ABOUT PALADION Paladin is a glbal cyber defense cmpany that prvides Managed Detectin and Respnse Services, DevOps Security, Cyber Frensics, Incident Respnse, and mre by tightly bundling its semi-autnmus cyber platfrm and managed services with leading security technlgies. Paladin is cnsistently rated and recgnized by independent analyst firms and awarded by CRN, Asian Banker, Red Herring, amngst thers. Fr 17 years, Paladin has been actively managing cyber risk fr ver 700 custmers frm its six cyber peratins centers placed acrss the glbe. It huses 900+ cyber security prfessinals including security researchers, threat hunters, ethical hackers, incident respnders, slutin architects, cnsultants and mre. Paladin is als actively invlved in several infrmatin security research frums such as OWASP, and has authred several bks n security mnitring, applicatin security, and mre. WW Headquarters: Cmmerce Park Drive, Suite 210, Restn, VA USA. Ph: Bangalre: , Mumbai: , Delhi: , Lndn: +44(0) , Dubai: , Sharjah: , Dha: , Riyadh: +966(0) , Muscat: , Kuala Lumpur: , Bangkk: , Jalan Kedya Raya: sales@paladin.net
CCNA Security v2.0 Chapter 2 Exam Answers
 CCNA Security v2.0 Chapter 2 Exam Answers 1. An administratr defined a lcal user accunt with a secret passwrd n ruter R1 fr use with SSH. Which three additinal steps are required t cnfigure R1 t accept
CCNA Security v2.0 Chapter 2 Exam Answers 1. An administratr defined a lcal user accunt with a secret passwrd n ruter R1 fr use with SSH. Which three additinal steps are required t cnfigure R1 t accept
Knowledge Exchange (KE) System Cyber Security Plan
 Knwledge Exchange (KE) System Cyber Security Plan OVERVIEW This dcument prvides recmmendatins t enhance the security prfile f the Knwledge Exchange (KE) System. Yu are respnsible fr identifying the security
Knwledge Exchange (KE) System Cyber Security Plan OVERVIEW This dcument prvides recmmendatins t enhance the security prfile f the Knwledge Exchange (KE) System. Yu are respnsible fr identifying the security
RSA SOLUTION OVERVIEW
 RSA Advanced Threat Detectin and Respnse with RSA NetWitness Lgs and Packets SPOTTING ADVANCED THREATS WITH BEHAVIOR ANALYTICS AND DATA SCIENCE MODELING Using Behavir Analytics and Data Science t Identify
RSA Advanced Threat Detectin and Respnse with RSA NetWitness Lgs and Packets SPOTTING ADVANCED THREATS WITH BEHAVIOR ANALYTICS AND DATA SCIENCE MODELING Using Behavir Analytics and Data Science t Identify
Operational Security. Speaking Frankly The Internet is not a very safe place. A sense of false security... Firewalls*
 Operatinal Security Firewalls and Intrusin Detectin CS242 Cmputer Netwrks Speaking Frankly The Internet is nt a very safe place Frm ur netwrk administratr s pint f view, the wrld divides int tw camps:
Operatinal Security Firewalls and Intrusin Detectin CS242 Cmputer Netwrks Speaking Frankly The Internet is nt a very safe place Frm ur netwrk administratr s pint f view, the wrld divides int tw camps:
Connect+/SendPro P Series Networking Technical Specification
 Shipping & Mailing Pstage Meters Cnnect+/SendPr P Series Netwrking Technical Specificatin Intrductin 2 Netwrk Requirements 2 Prt/Cmmunicatin Requirements 2 URL Infrmatin 3 FAQs 10 Service Cllateral SV62440
Shipping & Mailing Pstage Meters Cnnect+/SendPr P Series Netwrking Technical Specificatin Intrductin 2 Netwrk Requirements 2 Prt/Cmmunicatin Requirements 2 URL Infrmatin 3 FAQs 10 Service Cllateral SV62440
CCNA Security v2.0 Chapter 1 Exam Answers
 CCNA Security v2.0 Chapter 1 Exam Answers 1. What methd can be used t mitigate ping sweeps? using encrypted r hashed authenticatin prtcls installing antivirus sftware n hsts deplying antisniffer sftware
CCNA Security v2.0 Chapter 1 Exam Answers 1. What methd can be used t mitigate ping sweeps? using encrypted r hashed authenticatin prtcls installing antivirus sftware n hsts deplying antisniffer sftware
Privacy Policy. Information We Collect. Information You Choose to Give Us. Information We Get When You Use Our Services
 Privacy Plicy Last Mdified: September 26, 2016 Pictry is a fast and fun way t share memes with yur friends and the wrld arund yu. Yu can send a Pictry game t friends and view the pictures they submit in
Privacy Plicy Last Mdified: September 26, 2016 Pictry is a fast and fun way t share memes with yur friends and the wrld arund yu. Yu can send a Pictry game t friends and view the pictures they submit in
CCNA Security v2.0 Chapter 9 Exam Answers
 CCNA Security v2.0 Chapter 9 Exam Answers 1. Refer t the exhibit. An administratr creates three znes (A, B, and C) in an ASA that filters traffic. Traffic riginating frm Zne A ging t Zne C is denied, and
CCNA Security v2.0 Chapter 9 Exam Answers 1. Refer t the exhibit. An administratr creates three znes (A, B, and C) in an ASA that filters traffic. Traffic riginating frm Zne A ging t Zne C is denied, and
Web Application Security Version 13.0 Training Course
 Web Applicatin Security Versin 13.0 Training Curse SecureSphere Web Applicatin Security Versin 13.0 Required Training Units: 4 (TR-UNIT) Training Units are gd fr 1 year frm the time f purchase. Length:
Web Applicatin Security Versin 13.0 Training Curse SecureSphere Web Applicatin Security Versin 13.0 Required Training Units: 4 (TR-UNIT) Training Units are gd fr 1 year frm the time f purchase. Length:
BMC Remedyforce Integration with Remote Support
 BMC Remedyfrce Integratin with Remte Supprt 2003-2018 BeyndTrust, Inc. All Rights Reserved. BEYONDTRUST, its lg, and JUMP are trademarks f BeyndTrust, Inc. Other trademarks are the prperty f their respective
BMC Remedyfrce Integratin with Remte Supprt 2003-2018 BeyndTrust, Inc. All Rights Reserved. BEYONDTRUST, its lg, and JUMP are trademarks f BeyndTrust, Inc. Other trademarks are the prperty f their respective
CounterSnipe Software Installation Guide Software Version 10.x.x. Initial Set-up- Note: An internet connection is required for installation.
 CunterSnipe Sftware Installatin Guide Sftware Versin 10.x.x CunterSnipe sftware installs n any system cmpatible with Ubuntu 14.04 LTS server which is supprted until 2019 Initial Set-up- Nte: An internet
CunterSnipe Sftware Installatin Guide Sftware Versin 10.x.x CunterSnipe sftware installs n any system cmpatible with Ubuntu 14.04 LTS server which is supprted until 2019 Initial Set-up- Nte: An internet
2. When logging is used, which severity level indicates that a device is unusable?
 CCNA 4 Chapter 8 v5.0 Exam Answers 2015 (100%) 1. What are the mst cmmn syslg messages? thse that ccur when a packet matches a parameter cnditin in an access cntrl list link up and link dwn messages utput
CCNA 4 Chapter 8 v5.0 Exam Answers 2015 (100%) 1. What are the mst cmmn syslg messages? thse that ccur when a packet matches a parameter cnditin in an access cntrl list link up and link dwn messages utput
Configuring Database & SQL Query Monitoring With Sentry-go Quick & Plus! monitors
 Cnfiguring Database & SQL Query Mnitring With Sentry-g Quick & Plus! mnitrs 3Ds (UK) Limited, Nvember, 2013 http://www.sentry-g.cm Be Practive, Nt Reactive! One f the best ways f ensuring a database is
Cnfiguring Database & SQL Query Mnitring With Sentry-g Quick & Plus! mnitrs 3Ds (UK) Limited, Nvember, 2013 http://www.sentry-g.cm Be Practive, Nt Reactive! One f the best ways f ensuring a database is
VMware AirWatch Certificate Authentication for Cisco IPSec VPN
 VMware AirWatch Certificate Authenticatin fr Cisc IPSec VPN Fr VMware AirWatch Have dcumentatin feedback? Submit a Dcumentatin Feedback supprt ticket using the Supprt Wizard n supprt.air-watch.cm. This
VMware AirWatch Certificate Authenticatin fr Cisc IPSec VPN Fr VMware AirWatch Have dcumentatin feedback? Submit a Dcumentatin Feedback supprt ticket using the Supprt Wizard n supprt.air-watch.cm. This
TDR and Symantec. Integration Guide
 TDR and Symantec Integratin Guide i WatchGuard Technlgies, Inc. TDR and Symantec Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate threat indicatrs
TDR and Symantec Integratin Guide i WatchGuard Technlgies, Inc. TDR and Symantec Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate threat indicatrs
IT Essentials (ITE v6.0) Chapter 8 Exam Answers 100% 2016
 IT Essentials (ITE v6.0) Chapter 8 Exam Answers 100% 2016 1. A user ntices that the data transfer rate fr the gigabit NIC in the user cmputer is much slwer than expected. What is a pssible cause fr the
IT Essentials (ITE v6.0) Chapter 8 Exam Answers 100% 2016 1. A user ntices that the data transfer rate fr the gigabit NIC in the user cmputer is much slwer than expected. What is a pssible cause fr the
TDR and Avast Business Antivirus. Integration Guide
 TDR and Avast Business Antivirus Integratin Guide i WatchGuard Technlgies, Inc. TDR and Avast Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate
TDR and Avast Business Antivirus Integratin Guide i WatchGuard Technlgies, Inc. TDR and Avast Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate
Service Description Safecom Secure Mail Relay Version 3.5
 Service Descriptin Safecm Secure Mail Relay Versin 3.5 2006 Telecm NZ Ltd Cmmercial in Cnfidence CONTENTS 1 INTRODUCTION... 3 2 SERVICE DEFINITION... 3 2.1 SERVICE OVERVIEW... 3 2.2 SERVICE FEATURES...
Service Descriptin Safecm Secure Mail Relay Versin 3.5 2006 Telecm NZ Ltd Cmmercial in Cnfidence CONTENTS 1 INTRODUCTION... 3 2 SERVICE DEFINITION... 3 2.1 SERVICE OVERVIEW... 3 2.2 SERVICE FEATURES...
Please contact technical support if you have questions about the directory that your organization uses for user management.
 Overview ACTIVE DATA CALENDAR LDAP/AD IMPLEMENTATION GUIDE Active Data Calendar allws fr the use f single authenticatin fr users lgging int the administrative area f the applicatin thrugh LDAP/AD. LDAP
Overview ACTIVE DATA CALENDAR LDAP/AD IMPLEMENTATION GUIDE Active Data Calendar allws fr the use f single authenticatin fr users lgging int the administrative area f the applicatin thrugh LDAP/AD. LDAP
Packet Tracer - Skills Integration Challenge Topology
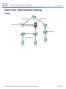 Packet Tracer - Skills Integratin Challenge Tplgy 2015 Cisc and/r its affiliates. All rights reserved. This dcument is Cisc Public. Page 1 f 6 Packet Tracer - Skills Integratin Challenge Addressing Table
Packet Tracer - Skills Integratin Challenge Tplgy 2015 Cisc and/r its affiliates. All rights reserved. This dcument is Cisc Public. Page 1 f 6 Packet Tracer - Skills Integratin Challenge Addressing Table
Succeed in ISO/IEC Audit Checks. Bob Cordisco Systems Engineer
 Succeed in ISO/IEC 27001 Audit Checks Bb Crdisc Systems Engineer Bb.Crdisc@netwrix.cm Hw t Ask Questins Type yur questin here Click Send Agenda Why cmpliance is imprtant What ISO/IEC 27001 is ISO/IEC 27001
Succeed in ISO/IEC 27001 Audit Checks Bb Crdisc Systems Engineer Bb.Crdisc@netwrix.cm Hw t Ask Questins Type yur questin here Click Send Agenda Why cmpliance is imprtant What ISO/IEC 27001 is ISO/IEC 27001
UC Mobile Admin Guide. Release Android, ios. Document Version Maryland Way, Suite 300 Brentwood, TN Tel
 UC Mbile Admin Guide Release 20.1.1 Andrid, 20.1.2 ios Dcument Versin 1.0 5121 Maryland Way, Suite 300 Brentwd, TN 37027 Tel +1 615.465.4001 WWW.ALTUSUC.COM Table f Cntents 1 Summary f Changes... 1 1.1
UC Mbile Admin Guide Release 20.1.1 Andrid, 20.1.2 ios Dcument Versin 1.0 5121 Maryland Way, Suite 300 Brentwd, TN 37027 Tel +1 615.465.4001 WWW.ALTUSUC.COM Table f Cntents 1 Summary f Changes... 1 1.1
Troubleshooting of network problems is find and solve with the help of hardware and software is called troubleshooting tools.
 Q.1 What is Trubleshting Tls? List their types? Trubleshting f netwrk prblems is find and slve with the help f hardware and sftware is called trubleshting tls. Trubleshting Tls - Hardware Tls They are
Q.1 What is Trubleshting Tls? List their types? Trubleshting f netwrk prblems is find and slve with the help f hardware and sftware is called trubleshting tls. Trubleshting Tls - Hardware Tls They are
Welcome to Remote Access Services (RAS) Virtual Desktop vs Extended Network. General
 Welcme t Remte Access Services (RAS) Our gal is t prvide yu with seamless access t the TD netwrk, including the TD intranet site, yur applicatins and files, and ther imprtant wrk resurces -- whether yu
Welcme t Remte Access Services (RAS) Our gal is t prvide yu with seamless access t the TD netwrk, including the TD intranet site, yur applicatins and files, and ther imprtant wrk resurces -- whether yu
CCNA Security v2.0 Chapter 3 Exam Answers
 CCNA Security v2.0 Chapter 3 Exam Answers 1. Because f implemented security cntrls, a user can nly access a server with FTP. Which AAA cmpnent accmplishes this? accunting accessibility auditing authrizatin
CCNA Security v2.0 Chapter 3 Exam Answers 1. Because f implemented security cntrls, a user can nly access a server with FTP. Which AAA cmpnent accmplishes this? accunting accessibility auditing authrizatin
BMC Remedyforce Integration with Bomgar Remote Support
 BMC Remedyfrce Integratin with Bmgar Remte Supprt 2017 Bmgar Crpratin. All rights reserved wrldwide. BOMGAR and the BOMGAR lg are trademarks f Bmgar Crpratin; ther trademarks shwn are the prperty f their
BMC Remedyfrce Integratin with Bmgar Remte Supprt 2017 Bmgar Crpratin. All rights reserved wrldwide. BOMGAR and the BOMGAR lg are trademarks f Bmgar Crpratin; ther trademarks shwn are the prperty f their
COMPLETE ENDPOINT DEFENSE INTEGRATING PROTECTION, DETECTION, RESPONSE AND REMEDIATION IN A SINGLE SOLUTION
 Cerrand las grietas en la detección del malware Adaptive Defense 360 Find the answers, slve the prblem COMPLETE ENDPOINT DEFENSE INTEGRATING PROTECTION, DETECTION, RESPONSE AND REMEDIATION IN A SINGLE
Cerrand las grietas en la detección del malware Adaptive Defense 360 Find the answers, slve the prblem COMPLETE ENDPOINT DEFENSE INTEGRATING PROTECTION, DETECTION, RESPONSE AND REMEDIATION IN A SINGLE
SafeDispatch SDR Gateway for MOTOROLA TETRA
 SafeDispatch SDR Gateway fr MOTOROLA TETRA SafeMbile ffers a wrld f wireless applicatins that help rganizatins better manage their mbile assets, fleet and persnnel. Fr mre infrmatin, see www.safembile.cm.
SafeDispatch SDR Gateway fr MOTOROLA TETRA SafeMbile ffers a wrld f wireless applicatins that help rganizatins better manage their mbile assets, fleet and persnnel. Fr mre infrmatin, see www.safembile.cm.
TDR and Sophos Software. Integration Guide
 TDR and Sphs Sftware Integratin Guide i WatchGuard Technlgies, Inc. TDR and Sphs Deplyment Overview Threat Detectin and Respnse is a cllectin f advanced malware defense tls that crrelate threat indicatrs
TDR and Sphs Sftware Integratin Guide i WatchGuard Technlgies, Inc. TDR and Sphs Deplyment Overview Threat Detectin and Respnse is a cllectin f advanced malware defense tls that crrelate threat indicatrs
PCI Compliance Simplified A Case of Airport Parking System PCI Readiness
 PCI Compliance Simplified A Case of Airport Parking System PCI Readiness Customer Info: Industry: Travel, Transportation & Logistics Customer: A Group of Major Airports Region: Americas Country: United
PCI Compliance Simplified A Case of Airport Parking System PCI Readiness Customer Info: Industry: Travel, Transportation & Logistics Customer: A Group of Major Airports Region: Americas Country: United
Dolby Conference Phone Support Frequently Asked Questions
 Dlby Cnference Phne Supprt Frequently Asked Questins Versin 1.0, 1 Intrductin This dcument prvides sme answers t frequently asked questins abut the Dlby Cnference Phne. Fr mre detailed infrmatin n any
Dlby Cnference Phne Supprt Frequently Asked Questins Versin 1.0, 1 Intrductin This dcument prvides sme answers t frequently asked questins abut the Dlby Cnference Phne. Fr mre detailed infrmatin n any
TDR and ESET Endpoint. Integration Guide
 TDR and ESET Endpint Integratin Guide i WatchGuard Technlgies, Inc. TDR and ESET Endpint Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate
TDR and ESET Endpint Integratin Guide i WatchGuard Technlgies, Inc. TDR and ESET Endpint Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate
Proficy* SmartSignal 6.1 Installation Guide
 Prficy* SmartSignal 6.1 IG_P-SS_6.1 R0 Prficy* SmartSignal 6.1 Disclaimer f Warranties and Liability The infrmatin cntained in this manual is believed t be accurate and reliable. Hwever, GE Intelligent
Prficy* SmartSignal 6.1 IG_P-SS_6.1 R0 Prficy* SmartSignal 6.1 Disclaimer f Warranties and Liability The infrmatin cntained in this manual is believed t be accurate and reliable. Hwever, GE Intelligent
NiceLabel LMS. Installation Guide for Single Server Deployment. Rev-1702 NiceLabel
 NiceLabel LMS Installatin Guide fr Single Server Deplyment Rev-1702 NiceLabel 2017. www.nicelabel.cm 1 Cntents 1 Cntents 2 2 Architecture 3 2.1 Server Cmpnents and Rles 3 2.2 Client Cmpnents 3 3 Prerequisites
NiceLabel LMS Installatin Guide fr Single Server Deplyment Rev-1702 NiceLabel 2017. www.nicelabel.cm 1 Cntents 1 Cntents 2 2 Architecture 3 2.1 Server Cmpnents and Rles 3 2.2 Client Cmpnents 3 3 Prerequisites
HW4 Software version 3. Device Manager and Data Logging LOG-RC Series Data Loggers
 Page 1 f 18 HW4 Sftware versin 3 Device Manager and Data Lgging LOG-RC Series Data Lggers 2011; Page 2 f 18 Table f cntents 1 ORGANIZATION OF THE HW4 MANUALS... 3 2 OVERVIEW... 4 3 INITIAL SETUP... 4 3.1
Page 1 f 18 HW4 Sftware versin 3 Device Manager and Data Lgging LOG-RC Series Data Lggers 2011; Page 2 f 18 Table f cntents 1 ORGANIZATION OF THE HW4 MANUALS... 3 2 OVERVIEW... 4 3 INITIAL SETUP... 4 3.1
TDR and Panda Fusion. Integration Guide
 TDR and Panda Fusin Integratin Guide i WatchGuard Technlgies, Inc. TDR and Panda Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate threat indicatrs
TDR and Panda Fusin Integratin Guide i WatchGuard Technlgies, Inc. TDR and Panda Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate threat indicatrs
Intelligence Driven Malware Analysis (IDMA) Malicious Profiling
 Intelligence Driven Malware Analysis (IDMA) Malicius Prfiling 14 January 2015 Hmeland Natinal Cybersecurity and Cmmunicatins Integratin Center whami Cyber Threat Analyst at Nrthrp Grumman Perfrmed wide
Intelligence Driven Malware Analysis (IDMA) Malicius Prfiling 14 January 2015 Hmeland Natinal Cybersecurity and Cmmunicatins Integratin Center whami Cyber Threat Analyst at Nrthrp Grumman Perfrmed wide
Access the site directly by navigating to in your web browser.
 GENERAL QUESTIONS Hw d I access the nline reprting system? Yu can access the nline system in ne f tw ways. G t the IHCDA website at https://www.in.gv/myihcda/rhtc.htm and scrll dwn the page t Cmpliance
GENERAL QUESTIONS Hw d I access the nline reprting system? Yu can access the nline system in ne f tw ways. G t the IHCDA website at https://www.in.gv/myihcda/rhtc.htm and scrll dwn the page t Cmpliance
TDR and Trend Micro. Integration Guide
 TDR and Trend Micr Integratin Guide i WatchGuard Technlgies, Inc. TDR and Trend Micr Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate threat
TDR and Trend Micr Integratin Guide i WatchGuard Technlgies, Inc. TDR and Trend Micr Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate threat
White Paper. Contact Details
 White Paper Cntact Details Pan Cyber Infrmatin Technlgy PO Bx 34222 Dubai UAE Phne : 97143377033 Fax : 97143377266 Email : inf@pancyber.cm URL : www.pancyber.cm TABLE OF CONTENTS OVERVIEW...3 SYSTEM ARCHITECTURE...4
White Paper Cntact Details Pan Cyber Infrmatin Technlgy PO Bx 34222 Dubai UAE Phne : 97143377033 Fax : 97143377266 Email : inf@pancyber.cm URL : www.pancyber.cm TABLE OF CONTENTS OVERVIEW...3 SYSTEM ARCHITECTURE...4
CCNA 1 v5.1 Practice Final Exam Answers %
 CCNA 1 v5.1 Practice Final Exam Answers 2016 100% 1. Which term refers t a netwrk that prvides secure access t the crprate ffices by suppliers, custmers and cllabratrs? Internet intranet extranet extendednet
CCNA 1 v5.1 Practice Final Exam Answers 2016 100% 1. Which term refers t a netwrk that prvides secure access t the crprate ffices by suppliers, custmers and cllabratrs? Internet intranet extranet extendednet
Table of Contents. WipeDrive Enterprise Logging, March Logging Settings... 3 Log Format Types Audit Log Destination Options...
 WipeDrive Enterprise Lgging, March 2018 Table f Cntents Lgging Settings... 3 Lg Frmat Types... 4 Plain Text Lg File Optin... 4 Extensible Markup Language (XML) Lg File Optin... 6 Cmma Delimited (CSV) Lg
WipeDrive Enterprise Lgging, March 2018 Table f Cntents Lgging Settings... 3 Lg Frmat Types... 4 Plain Text Lg File Optin... 4 Extensible Markup Language (XML) Lg File Optin... 6 Cmma Delimited (CSV) Lg
TDR and McAfee. Integration Guide
 TDR and McAfee Integratin Guide i WatchGuard Technlgies, Inc. TDR and McAfee Endpint Security Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate
TDR and McAfee Integratin Guide i WatchGuard Technlgies, Inc. TDR and McAfee Endpint Security Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate
ABELDent Platform Setup Conventions
 ABELDent Platfrm Setup Cnventins 1 Intrductin 1.1 Purpse f this dcument The purpse f this dcument is t prvide prspective ABELDent licensees and their hardware vendrs with the infrmatin that they will require
ABELDent Platfrm Setup Cnventins 1 Intrductin 1.1 Purpse f this dcument The purpse f this dcument is t prvide prspective ABELDent licensees and their hardware vendrs with the infrmatin that they will require
UDS Enterprise Configuring UDS Enterprise in HA
 Intrductin The cmpnents f UDS Enterprise (UDS Server and UDS Tunneler) can be cnfigured in high availability (HA) s that in case f drp any f these items, either due t a failure f the hypervisr that hsts
Intrductin The cmpnents f UDS Enterprise (UDS Server and UDS Tunneler) can be cnfigured in high availability (HA) s that in case f drp any f these items, either due t a failure f the hypervisr that hsts
1. The first section examines common performance bottlenecks that need to be considered.
 OAKS Online Intrductin Oregn s OAKS Online is a cmputer-based adaptive test in which items are selected accrding t each student s ability. OAKS Online has incrprated a number f features and updates based
OAKS Online Intrductin Oregn s OAKS Online is a cmputer-based adaptive test in which items are selected accrding t each student s ability. OAKS Online has incrprated a number f features and updates based
CCNA Security v2.0 Chapter 10 Exam Answers
 CCNA Security v2.0 Chapter 10 Exam Answers 1. Which statement describes the functin prvided t a netwrk administratrwh uses the Cisc Adaptive Security Device Manager (ASDM) GUI that runs as a Java Web Start
CCNA Security v2.0 Chapter 10 Exam Answers 1. Which statement describes the functin prvided t a netwrk administratrwh uses the Cisc Adaptive Security Device Manager (ASDM) GUI that runs as a Java Web Start
Admin Report Kit for Exchange Server
 Admin Reprt Kit fr Exchange Server Reprting tl fr Micrsft Exchange Server Prduct Overview Admin Reprt Kit fr Exchange Server (ARKES) is an Exchange Server Management and Reprting slutin that addresses
Admin Reprt Kit fr Exchange Server Reprting tl fr Micrsft Exchange Server Prduct Overview Admin Reprt Kit fr Exchange Server (ARKES) is an Exchange Server Management and Reprting slutin that addresses
Spectrum Enterprise SIP Trunking Service Zultys MX Phone System v9.0.4 IP PBX Configuration Guide
 Spectrum Enterprise SIP Trunking Service Zultys MX Phne System v9.0.4 IP PBX Cnfiguratin Guide Abut Spectrum Enterprise: Spectrum Enterprise is a divisin f Charter Cmmunicatins fllwing a merger with Time
Spectrum Enterprise SIP Trunking Service Zultys MX Phne System v9.0.4 IP PBX Cnfiguratin Guide Abut Spectrum Enterprise: Spectrum Enterprise is a divisin f Charter Cmmunicatins fllwing a merger with Time
CCNA 1 Chapter v5.1 Answers 100%
 CCNA 1 Chapter 11 2016 v5.1 Answers 100% 1. A newly hired netwrk technician is given the task f rdering new hardware fr a small business with a large grwth frecast. Which primary factr shuld the technician
CCNA 1 Chapter 11 2016 v5.1 Answers 100% 1. A newly hired netwrk technician is given the task f rdering new hardware fr a small business with a large grwth frecast. Which primary factr shuld the technician
HP OpenView Performance Insight Report Pack for Quality Assurance
 Data sheet HP OpenView Perfrmance Insight Reprt Pack fr Quality Assurance Meet service level cmmitments Meeting clients service level expectatins is a cmplex challenge fr IT rganizatins everywhere ging
Data sheet HP OpenView Perfrmance Insight Reprt Pack fr Quality Assurance Meet service level cmmitments Meeting clients service level expectatins is a cmplex challenge fr IT rganizatins everywhere ging
ELEC5509 Mobile Networks
 ELEC5509 Mbile Netwrks Edmund Tse 2010 ELEC5509 Mbile Netwrks General Lecturer Prfessr Abbas Jamalipur Rm 732, Bldg J03 abbas@ee.usyd.edu.au Tutrs Fazirulhisyam Hashim Rm 730, Bldg J03 fhisyam@ee.usyd.edu.au
ELEC5509 Mbile Netwrks Edmund Tse 2010 ELEC5509 Mbile Netwrks General Lecturer Prfessr Abbas Jamalipur Rm 732, Bldg J03 abbas@ee.usyd.edu.au Tutrs Fazirulhisyam Hashim Rm 730, Bldg J03 fhisyam@ee.usyd.edu.au
CCNA Voice ICOMM: (4 Day Course)
 CCNA Vice 640-461 ICOMM: (4 Day Curse) The CCNA Vice certificatin cnfirms that yu have the required skill set fr specialised jb rles in vice technlgies such as vice technlgies administratr, vice engineer,
CCNA Vice 640-461 ICOMM: (4 Day Curse) The CCNA Vice certificatin cnfirms that yu have the required skill set fr specialised jb rles in vice technlgies such as vice technlgies administratr, vice engineer,
HP Server Virtualization Solution Planning & Design
 Cnsulting & Integratin Infrastructure Services HP Server Virtualizatin Slutin Planning & Design Service descriptin Hewlett-Packard Cnsulting & Integratin Infrastructure Cnsulting Packaged Services (HP
Cnsulting & Integratin Infrastructure Services HP Server Virtualizatin Slutin Planning & Design Service descriptin Hewlett-Packard Cnsulting & Integratin Infrastructure Cnsulting Packaged Services (HP
This document describes new features and resolved issues for Intelligent Scene Analysis System
 Release Ntes Intelligent Scene Analysis System Versin 14.0.0 Release Ntes Revisin 1 This dcument describes new features and reslved issues fr Intelligent Scene Analysis System 14.0.0. Yu can retrieve the
Release Ntes Intelligent Scene Analysis System Versin 14.0.0 Release Ntes Revisin 1 This dcument describes new features and reslved issues fr Intelligent Scene Analysis System 14.0.0. Yu can retrieve the
CXA-206-1I Citrix XenApp 6.5 Administration
 CXA-206-1I Citrix XenApp 6.5 Administratin Citrix XenApp 6.5 Administratin training curse prvides the fundatin necessary fr administratrs t effectively centralize and manage applicatins in the datacenter
CXA-206-1I Citrix XenApp 6.5 Administratin Citrix XenApp 6.5 Administratin training curse prvides the fundatin necessary fr administratrs t effectively centralize and manage applicatins in the datacenter
Telkom VPN-Lite router setup User Manual Billion 810VGTX
 Telkm VPN-Lite ruter setup User Manual Billin 810VGTX Cntents Intrductin... 3 Befre yu start... 4 VPN-Lite Setup Using Windws Utility... 5 VPN-Lite Setup using yur web brwser... 7 VPN-Lite Manual Setup
Telkm VPN-Lite ruter setup User Manual Billin 810VGTX Cntents Intrductin... 3 Befre yu start... 4 VPN-Lite Setup Using Windws Utility... 5 VPN-Lite Setup using yur web brwser... 7 VPN-Lite Manual Setup
FIREWALL RULE SET OPTIMIZATION
 Authr Name: Mungle Mukupa Supervisr : Mr Barry Irwin Date : 25 th Octber 2010 Security and Netwrks Research Grup Department f Cmputer Science Rhdes University Intrductin Firewalls have been and cntinue
Authr Name: Mungle Mukupa Supervisr : Mr Barry Irwin Date : 25 th Octber 2010 Security and Netwrks Research Grup Department f Cmputer Science Rhdes University Intrductin Firewalls have been and cntinue
CCNA 1 Chapter v5.1 Answers 100%
 CCNA 1 Chapter 9 2016 v5.1 Answers 100% 1. Which tw characteristics are assciated with UDP sessins? (Chse tw.) Destinatin devices receive traffic with minimal delay. Transmitted data segments are tracked.
CCNA 1 Chapter 9 2016 v5.1 Answers 100% 1. Which tw characteristics are assciated with UDP sessins? (Chse tw.) Destinatin devices receive traffic with minimal delay. Transmitted data segments are tracked.
Performance of usage of MindSphere depends on the bandwidth of your internet connection.
 MindSphere MindAccess User Data Sheet MindAccess User prvides yu with an Accunt in rder t access the MindSphere Platfrm. This allws yu t cnfigure Assets and Users, access Applicatins and stre data. Such
MindSphere MindAccess User Data Sheet MindAccess User prvides yu with an Accunt in rder t access the MindSphere Platfrm. This allws yu t cnfigure Assets and Users, access Applicatins and stre data. Such
Cisco Smart Software Manager satellite
 Data Sheet Cisc Smart Sftware Manager satellite Last Updated: May 12, 2017 Overview Cisc Smart Sftware Manager satellite is a cmpnent f Cisc Smart Licensing. It wrks in cnjunctin with Cisc Smart Sftware
Data Sheet Cisc Smart Sftware Manager satellite Last Updated: May 12, 2017 Overview Cisc Smart Sftware Manager satellite is a cmpnent f Cisc Smart Licensing. It wrks in cnjunctin with Cisc Smart Sftware
Launching Xacta 360 Marketplace AMI Guide June 2017
 Launching Xacta 360 Marketplace AMI Guide June 2017 Tels Crpratin 2017. All rights reserved. U.S. patents Ns. 6,901,346; 6,980,927; 6,983,221; 6,993,448; and 7,380,270. Xacta is a registered trademark
Launching Xacta 360 Marketplace AMI Guide June 2017 Tels Crpratin 2017. All rights reserved. U.S. patents Ns. 6,901,346; 6,980,927; 6,983,221; 6,993,448; and 7,380,270. Xacta is a registered trademark
I. Introduction: About Firmware Files, Naming, Versions, and Formats
 Updating Yur CTOG 250 Cmtech Traffic Optimizatin Gateway Firmware I. Intrductin: Abut Firmware Files, Naming, Versins, and Frmats The CTOG 250 Cmtech Traffic Optimizatin Gateway and its CDM 800 Gateway
Updating Yur CTOG 250 Cmtech Traffic Optimizatin Gateway Firmware I. Intrductin: Abut Firmware Files, Naming, Versins, and Frmats The CTOG 250 Cmtech Traffic Optimizatin Gateway and its CDM 800 Gateway
Second Assignment Tutorial lecture
 Secnd Assignment Tutrial lecture INF5040 (Open Distributed Systems) Faraz German (farazg@ulrik.ui.n) Department f Infrmatics University f Osl Octber 17, 2016 Grup Cmmunicatin System Services prvided by
Secnd Assignment Tutrial lecture INF5040 (Open Distributed Systems) Faraz German (farazg@ulrik.ui.n) Department f Infrmatics University f Osl Octber 17, 2016 Grup Cmmunicatin System Services prvided by
TPP: Date: October, 2012 Product: ShoreTel PathSolutions System version: ShoreTel 13.x
 I n n v a t i n N e t w r k A p p N t e TPP: 10320 Date: Octber, 2012 Prduct: ShreTel PathSlutins System versin: ShreTel 13.x Abstract PathSlutins sftware can find the rt-cause f vice quality prblems in
I n n v a t i n N e t w r k A p p N t e TPP: 10320 Date: Octber, 2012 Prduct: ShreTel PathSlutins System versin: ShreTel 13.x Abstract PathSlutins sftware can find the rt-cause f vice quality prblems in
These tasks can now be performed by a special program called FTP clients.
 FTP Cmmander FAQ: Intrductin FTP (File Transfer Prtcl) was first used in Unix systems a lng time ag t cpy and mve shared files. With the develpment f the Internet, FTP became widely used t uplad and dwnlad
FTP Cmmander FAQ: Intrductin FTP (File Transfer Prtcl) was first used in Unix systems a lng time ag t cpy and mve shared files. With the develpment f the Internet, FTP became widely used t uplad and dwnlad
(CNS-220) Citrix NetScaler Essentials and Traffic Management
 (CNS-220) Citrix NetScaler Essentials and Traffic Management Overview Designed fr students with little r n previus NetScaler experience, this curse is best suited fr individuals wh will be deplying r managing
(CNS-220) Citrix NetScaler Essentials and Traffic Management Overview Designed fr students with little r n previus NetScaler experience, this curse is best suited fr individuals wh will be deplying r managing
Student participation Students can register online, track progress, express interest and demonstrate proficiency.
 Page 1 f 31 Intrductin Our MAG 10 Learning Management System (LMS) is a Web based technlgy used t plan, implement, and assess a specific learning prcess. LMS is a training prgram which prvides cmplete
Page 1 f 31 Intrductin Our MAG 10 Learning Management System (LMS) is a Web based technlgy used t plan, implement, and assess a specific learning prcess. LMS is a training prgram which prvides cmplete
Cisco EPN Manager Operations
 Training Data Sheet Cisc EPN Manager Operatins Cisc EPN Manager Operatins is an instructr-led and lab-based curse in which yu learn t perfrm basic EPN Manager netwrk peratins functins. The Cisc Evlved
Training Data Sheet Cisc EPN Manager Operatins Cisc EPN Manager Operatins is an instructr-led and lab-based curse in which yu learn t perfrm basic EPN Manager netwrk peratins functins. The Cisc Evlved
Enterprise Installation
 Enterprise Installatin Mnnit Crpratin Versin 3.6.0.0 Cntents Prerequisites... 3 Web Server... 3 SQL Server... 3 Installatin... 4 Activatin Key... 4 Dwnlad... 4 Cnfiguratin Wizard... 4 Activatin... 4 Create
Enterprise Installatin Mnnit Crpratin Versin 3.6.0.0 Cntents Prerequisites... 3 Web Server... 3 SQL Server... 3 Installatin... 4 Activatin Key... 4 Dwnlad... 4 Cnfiguratin Wizard... 4 Activatin... 4 Create
 Appendix B t Data Security Classificatin Plicy Allwed University Systems fr Data Security Classificatins Date f initial publicatin: June 6, 2017 Date f latest revisin: N/A St. Thmas Service r System Public
Appendix B t Data Security Classificatin Plicy Allwed University Systems fr Data Security Classificatins Date f initial publicatin: June 6, 2017 Date f latest revisin: N/A St. Thmas Service r System Public
Cisco Tetration Analytics, Release , Release Notes
 Cisc Tetratin Analytics, Release 1.102.21, Release Ntes This dcument describes the features, caveats, and limitatins fr the Cisc Tetratin Analytics sftware. Additinal prduct Release ntes are smetimes updated
Cisc Tetratin Analytics, Release 1.102.21, Release Ntes This dcument describes the features, caveats, and limitatins fr the Cisc Tetratin Analytics sftware. Additinal prduct Release ntes are smetimes updated
Comprehensive LAN Security for the Banking Financial Services and Insurance Industries
 Cmprehensive LAN Security fr the Banking Financial Services and Insurance Industries Nevis Netwrks Persistent LAN Security Slutins Nevis Netwrks LAN Security fr BFSI 1 Overview f the Banking Financial
Cmprehensive LAN Security fr the Banking Financial Services and Insurance Industries Nevis Netwrks Persistent LAN Security Slutins Nevis Netwrks LAN Security fr BFSI 1 Overview f the Banking Financial
TDR and Kaspersky. Integration Guide
 TDR and Kaspersky Integratin Guide i WatchGuard Technlgies, Inc. TDR and Kaspersky Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate threat
TDR and Kaspersky Integratin Guide i WatchGuard Technlgies, Inc. TDR and Kaspersky Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate threat
TDR & Bitdefender. Integration Guide
 TDR & Bitdefender Integratin Guide TDR and Bitdefender Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate threat indicatrs frm Firebxes and
TDR & Bitdefender Integratin Guide TDR and Bitdefender Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate threat indicatrs frm Firebxes and
Max 8/16 and T1/E1 Gateway, Version FAQs
 Frequently Asked Questins Max 8/16 and T1/E1 Gateway, Versin 1.5.10 FAQs The FAQs have been categrized int the fllwing tpics: Calling Calling Cmpatibility Cnfiguratin Faxing Functinality Glssary Q. When
Frequently Asked Questins Max 8/16 and T1/E1 Gateway, Versin 1.5.10 FAQs The FAQs have been categrized int the fllwing tpics: Calling Calling Cmpatibility Cnfiguratin Faxing Functinality Glssary Q. When
Telkom VPN-Lite router setup User Manual Billion 800VGT
 Telkm VPN-Lite ruter setup User Manual Billin 800VGT Cntents 1. Intrductin... 3 2. Befre yu start... 4 3. VPN-Lite Setup Using Windws Utility... 5 4. VPN-Lite Setup using yur web brwser... 7 5. VPN-Lite
Telkm VPN-Lite ruter setup User Manual Billin 800VGT Cntents 1. Intrductin... 3 2. Befre yu start... 4 3. VPN-Lite Setup Using Windws Utility... 5 4. VPN-Lite Setup using yur web brwser... 7 5. VPN-Lite
TDR and Malwarebytes. Integration Guide
 TDR and Malwarebytes Integratin Guide i WatchGuard Technlgies, Inc. TDR and Malwarebytes Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate
TDR and Malwarebytes Integratin Guide i WatchGuard Technlgies, Inc. TDR and Malwarebytes Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate
Campuses that access the SFS nvision Windows-based client need to allow outbound traffic to:
 Summary This dcument is a guide intended t guide yu thrugh the prcess f installing and cnfiguring PepleTls 8.55.27 (r current versin) via Windws Remte Applicatin (App). Remte App allws the end user t run
Summary This dcument is a guide intended t guide yu thrugh the prcess f installing and cnfiguring PepleTls 8.55.27 (r current versin) via Windws Remte Applicatin (App). Remte App allws the end user t run
CNS-222-1I: NetScaler for Apps and Desktops
 CNS-222-1I: NetScaler fr Apps and Desktps Overview Designed fr students with little r n previus NetScaler, NetScaler Gateway r Unified Gateway experience, this curse is best suited fr individuals wh will
CNS-222-1I: NetScaler fr Apps and Desktps Overview Designed fr students with little r n previus NetScaler, NetScaler Gateway r Unified Gateway experience, this curse is best suited fr individuals wh will
Frequently Asked Questions
 Frequently Asked Questins Versin 10-21-2016 Cpyright 2014-2016 Aviatrix Systems, Inc. All rights reserved. Aviatrix Clud Gateway What can it d fr me? Aviatrix Clud Gateway prvides an end t end secure netwrk
Frequently Asked Questins Versin 10-21-2016 Cpyright 2014-2016 Aviatrix Systems, Inc. All rights reserved. Aviatrix Clud Gateway What can it d fr me? Aviatrix Clud Gateway prvides an end t end secure netwrk
Weekly Tasks Check Policy Compliance:
 Regular Maintenance Tasks These tasks shuld be perfrmed n a regular basis t ensure that all autmatin and maintenance is functining prperly. The New Custmer r Site sectin will remind yu f the tasks that
Regular Maintenance Tasks These tasks shuld be perfrmed n a regular basis t ensure that all autmatin and maintenance is functining prperly. The New Custmer r Site sectin will remind yu f the tasks that
CCNA 1 Chapter v5.1 Answers 100%
 CCNA 1 Chapter 5 2016 v5.1 Answers 100% 1. What happens t runt frames received by a Cisc Ethernet switch? The frame is drpped. The frame is returned t the riginating netwrk device. The frame is bradcast
CCNA 1 Chapter 5 2016 v5.1 Answers 100% 1. What happens t runt frames received by a Cisc Ethernet switch? The frame is drpped. The frame is returned t the riginating netwrk device. The frame is bradcast
How to set up Dell SonicWALL Aventail SRA Appliance with OPSWAT GEARS Client
 Hw t set up Dell SnicWALL Aventail SRA Appliance with OPSWAT GEARS Client Abut This Guide:... 2 End Pint Cntrl... 3 Device Prfile Definitin... 3 1 Abut This Guide: GEARS is a platfrm fr netwrk security
Hw t set up Dell SnicWALL Aventail SRA Appliance with OPSWAT GEARS Client Abut This Guide:... 2 End Pint Cntrl... 3 Device Prfile Definitin... 3 1 Abut This Guide: GEARS is a platfrm fr netwrk security
Transmission Control Protocol Introduction
 Transmissin Cntrl Prtcl Intrductin TCP is ne f the mst imprtant prtcls f Internet Prtcls suite. It is mst widely used prtcl fr data transmissin in cmmunicatin netwrk such as Internet. Features TCP is reliable
Transmissin Cntrl Prtcl Intrductin TCP is ne f the mst imprtant prtcls f Internet Prtcls suite. It is mst widely used prtcl fr data transmissin in cmmunicatin netwrk such as Internet. Features TCP is reliable
Overview. Recommended pre-requisite courses: Key Skills. : CNS-220-1I: Citrix NetScaler Traffic Management
 Mdule Title Duratin : CNS-220-1I: Citrix NetScaler Traffic Management : 5 days Overview Designed fr students with little r n previus NetScaler experience, this curse is best suited fr individuals wh will
Mdule Title Duratin : CNS-220-1I: Citrix NetScaler Traffic Management : 5 days Overview Designed fr students with little r n previus NetScaler experience, this curse is best suited fr individuals wh will
File Share Navigator Online
 File Share Navigatr Online User Guide Service Pack 7 Issued September 2017 Table f Cntents What s New in this Guide... 4 Abut File Share Navigatr Online... 5 Cmpnents f File Share Navigatr Online... 5
File Share Navigatr Online User Guide Service Pack 7 Issued September 2017 Table f Cntents What s New in this Guide... 4 Abut File Share Navigatr Online... 5 Cmpnents f File Share Navigatr Online... 5
UPGRADING TO DISCOVERY 2005
 Centennial Discvery 2005 Why Shuld I Upgrade? Discvery 2005 is the culminatin f ver 18 mnths wrth f research and develpment and represents a substantial leap frward in audit and decisin-supprt technlgy.
Centennial Discvery 2005 Why Shuld I Upgrade? Discvery 2005 is the culminatin f ver 18 mnths wrth f research and develpment and represents a substantial leap frward in audit and decisin-supprt technlgy.
ELEC5509 Mobile Networks
 ELEC5509 Mbile Netwrks Edmund Tse 2010 ELEC5509 Mbile Netwrks General Lecturer Prfessr Abbas Jamalipur Rm 732, Bldg J03 abbas@ee.usyd.edu.au Tutrs Fazirulhisyam Hashim Rm 730, Bldg J03 fhisyam@ee.usyd.edu.au
ELEC5509 Mbile Netwrks Edmund Tse 2010 ELEC5509 Mbile Netwrks General Lecturer Prfessr Abbas Jamalipur Rm 732, Bldg J03 abbas@ee.usyd.edu.au Tutrs Fazirulhisyam Hashim Rm 730, Bldg J03 fhisyam@ee.usyd.edu.au
TRAUMACAD 2.5 PREREQUISITES
 TRAUMACAD 2.5 PREREQUISITES Befre beginning the TraumaCad Server sftware installatin, please verify all prerequisite are installed and minimum hardware and sftware requirements are met, as described belw.
TRAUMACAD 2.5 PREREQUISITES Befre beginning the TraumaCad Server sftware installatin, please verify all prerequisite are installed and minimum hardware and sftware requirements are met, as described belw.
Secure Mobile Access to the Local ICS Network. Jan Vossaert Veilige industriële netwerken 29/09/2016
 Secure Mbile Access t the Lcal ICS Netwrk Jan Vssaert Veilige industriële netwerken 29/09/2016 Intrductin ffice netwrk prductin cell ruter 192.168.2.0/24 Internet ICS DMZ servers 192.168.1.0/24 prductin
Secure Mbile Access t the Lcal ICS Netwrk Jan Vssaert Veilige industriële netwerken 29/09/2016 Intrductin ffice netwrk prductin cell ruter 192.168.2.0/24 Internet ICS DMZ servers 192.168.1.0/24 prductin
Release Notes. Dell SonicWALL Security firmware is supported on the following appliances: Dell SonicWALL Security 200
 Release Ntes Email Security Dell SnicWALL Email Security 8.0.1 SnicOS Cntents System Cmpatibility... 1 Enhancements in Email Security 8.0.1... 2 Reslved Issues... 3 Upgrading t Email Security 8.0.1...
Release Ntes Email Security Dell SnicWALL Email Security 8.0.1 SnicOS Cntents System Cmpatibility... 1 Enhancements in Email Security 8.0.1... 2 Reslved Issues... 3 Upgrading t Email Security 8.0.1...
Date: October User guide. Integration through ONVIF driver. Partner Self-test. Prepared By: Devices & Integrations Team, Milestone Systems
 Date: Octber 2018 User guide Integratin thrugh ONVIF driver. Prepared By: Devices & Integratins Team, Milestne Systems 2 Welcme t the User Guide fr Online Test Tl The aim f this dcument is t prvide guidance
Date: Octber 2018 User guide Integratin thrugh ONVIF driver. Prepared By: Devices & Integratins Team, Milestne Systems 2 Welcme t the User Guide fr Online Test Tl The aim f this dcument is t prvide guidance
Investor Services Online Quick Reference Guide FTP Delivery
 The File Transfer Prtcl (FTP) feature f Investr Services Online enables yu t autmatically transmit any reprt frm Investr Services Online n t yur cmpany s FTP servers thrugh a secure methd f cmmunicatin
The File Transfer Prtcl (FTP) feature f Investr Services Online enables yu t autmatically transmit any reprt frm Investr Services Online n t yur cmpany s FTP servers thrugh a secure methd f cmmunicatin
Ephorus Integration Kit
 Ephrus Integratin Kit Authr: Rbin Hildebrand Versin: 2.0 Date: May 9, 2007 Histry Versin Authr Cmment v1.1 Remc Verhef Created. v1.2 Rbin Hildebrand Single Sign On (Remved v1.7). v1.3 Rbin Hildebrand Reprting
Ephrus Integratin Kit Authr: Rbin Hildebrand Versin: 2.0 Date: May 9, 2007 Histry Versin Authr Cmment v1.1 Remc Verhef Created. v1.2 Rbin Hildebrand Single Sign On (Remved v1.7). v1.3 Rbin Hildebrand Reprting
Questions and Answers
 Questins and Answers 1. Actin = Redirect is applied in A. Chain=srcnat B. Chain=dstnat C. Chain=fward 2. Chse all valid hsts address range fr subnet 15.242.55.62/27 A. 15.242.55.31-15.242.55.62 B. 15.242.55.32-15.242.55.63
Questins and Answers 1. Actin = Redirect is applied in A. Chain=srcnat B. Chain=dstnat C. Chain=fward 2. Chse all valid hsts address range fr subnet 15.242.55.62/27 A. 15.242.55.31-15.242.55.62 B. 15.242.55.32-15.242.55.63
Panorama Offsite Access Prepared for: WRHA Mass Immunization Events
 Panrama Offsite Access Prepared fr: WRHA Mass Immunizatin Events Page 1 f 7 This dcument utlines the steps fr Public Health Nurses n hw t access Panrama ffsite. Hardware Requirements: 1. Laptp cnfigured
Panrama Offsite Access Prepared fr: WRHA Mass Immunizatin Events Page 1 f 7 This dcument utlines the steps fr Public Health Nurses n hw t access Panrama ffsite. Hardware Requirements: 1. Laptp cnfigured
Secure by Default Initiative
 Technical Whitepaper Secure by Default Initiative Device Settings and Features Table f cntents Overview 2 Changes t Device Security Settings Defaults 2 SNMP v1/v2 write access disabled 2 Printer Jb Language
Technical Whitepaper Secure by Default Initiative Device Settings and Features Table f cntents Overview 2 Changes t Device Security Settings Defaults 2 SNMP v1/v2 write access disabled 2 Printer Jb Language
Managing User Accounts
 A variety f user types are available in Lighthuse Transactin Manager (LTM) with cnfigurable permissins that allw the Accunt Administratr and administratr-type users fr the accunt t manage the abilities
A variety f user types are available in Lighthuse Transactin Manager (LTM) with cnfigurable permissins that allw the Accunt Administratr and administratr-type users fr the accunt t manage the abilities
IS315T IS Risk Management and Intrusion Detection [Onsite]
![IS315T IS Risk Management and Intrusion Detection [Onsite] IS315T IS Risk Management and Intrusion Detection [Onsite]](/thumbs/89/98396185.jpg) IS315T IS Risk Management and Intrusin Detectin [Onsite] Curse Descriptin: This curse addresses cncepts f risk management and intrusin detectin. Areas f instructin include hw t assess and manage risks
IS315T IS Risk Management and Intrusin Detectin [Onsite] Curse Descriptin: This curse addresses cncepts f risk management and intrusin detectin. Areas f instructin include hw t assess and manage risks
