|
|
|
- Christopher Ray
- 6 years ago
- Views:
Transcription
1
2
3
4
5
6
7 Appendix B t Data Security Classificatin Plicy Allwed University Systems fr Data Security Classificatins Date f initial publicatin: June 6, 2017 Date f latest revisin: N/A St. Thmas Service r System Public / Directry Inf Internal / Prpietary Prtected PII (SSN's & Bank Accunt#) ed Identifiable Human Subject esearch Credit Card Data HIPAA Data Persnal Strage: DrpBx r Other Persnal Strage Persnal G-mail, Htmail, etc. St. Thmas Website ( St. Thmas emvable Strage (Unencrypted) St. Thmas emvable Strage (Encrypted) St. Thmas Wrsktatin Lcal Strage (Unencrypted) St. Thmas Wrsktatin Lcal Strage (Encrypted) ITSM: Web Help Desk Calendar: Office365 Yammer: Office365 File Strage: MyStrage Office365 Dcument Management: SharePint Dcument Management: OneDrive St. Thmas Intranet: Unily File Strage: AcadStre File Strage: DeptStre1 CrashPlan POe LMS: Blackbard / Canvas Banner EP (Banner INB ) Dcument Management: Optix CM: Flatbridge CM: Salesfrce CM: eheer uffal Cdy TuchNet PayPath and Marketplace Authrize.net PyraMed
8 Appendix C t Data Security Classificatin Plicy Cntrls Standards fr Data Security Classificatins User Security Standards Prtect Passwrds Different Passwrds ecurring Task? What t D Users' passwrds and ther access credentials must never be shared. Different passwrds must be used fr St. Thmas and nn- St. Thmas accunts. Date f initial publicatin: June 6, 2017 Date f latest revisin: N/A ed Strng Passwrds Cmprmised Passwrds Accessing Cnfidential Infrmatin Sharing Cnfidential Infrmatin Lss f Cnfidential Infrmatin Dispsal f Cnfidential Infrmatin Payment Card Transactins Passwrds used fr St. Thmas business must be f sufficient length and cmplexity t reasnably prtect them frm being guessed by humans r cmputers. Passwrds must be changed immediately if there is a suspicin f cmprmise. Cnfidential infrmatin must nly be accessed fr authrized purpses. Cnfidential infrmatin must nly be shared with thse authrized t receive it. Any actual r suspected lss, theft, r imprper uses f r access t cnfidential infrmatin must be reprted prmptly. Cnfidential infrmatin in any frm must be apprpriately dispsed when it is n lnger needed. All users handling credit card r debit card transactins must cmply with University Payment Plicy requirements. End Pint Security Standards ecurring Task? What t D ed Patching Apply security patches within seven days f publish. Use a supprted OS versin. Whle Disk Encryptin Enable FileVault fr Mac, r BitLcker fr Windws. Malware Prtectin Install ITS apprved and supprted anti-virus slutin and cnfiguratins. Backup user data at least daily. University prvided Backups CrashPlan is the recmmended slutin. Ensure backups are encrypted in transit and at rest. Inventry All university end pints must be tracked in the ITS inventry. egulated Data Security Cntrls Implement hardened ITS PC standard cnfiguratin n device. Server Security Standards Patching ecurring Task? What t D Based n Natinal Vulnerability Database (NVD) ratings, apply high severity security patches within seven days f publish and all ther security patches within 90 days. Use a supprted OS versin. ed Vulnernability Management Perfrm a quarterly Nessus scan. emediate severity 4 and 5 vulnerabilities within seven days f discvery and severity 3 vulnerabilities within 90 days. Credentials & Access Cntrl Firewall eview existing accunts and privileges quarterly. Enfrce passwrd cmplexity. Enable hst-based firewall in default deny mde and permit the minimum necessary services. Inventry Physical Prtectin Multifactr Authenticatin Centralized Lgging All university servers must be tracked in the ITS inventry. Place system hardware in a secure data center r ITS apprved hsted lcatin. equire multifactr authenticatin fr all interactive user and administratr lgins. Frward security event lgs t a remte lg server. University IT Splunk service recmmended.
9 Malware Prtectin Install ITS apprved and supprted anti-virus slutin and cnfiguratins. Intrusin Detectin Enable firewall and IDS rules t allw nly required traffic. eview alerts as they are received. Sysadmin Training Attend ITS server admin security training annually. Dedicated Admin Wrkstatin Access administrative accunts and systems nly via a certified Priviledge Access Wrkstatin. Security, Privacy, and Legal eview equest a Security, Privacy, and Legal review and implement recmmendatins prir t deplyment. egulated Data Security Cntrls Implement PCI DSS, HIPAA, r exprt cntrls as applicable. Applicatin Security Standards ecurring Task? What t D ed isk Assessment Applicatin is put thrugh ITS risk assessment prcess prir t aquistin. All identified risks must be accespted by the Data Owner(s). EDUCAUSE HECVAT r HECVAT Lite are preferred assessement tls. Patching Based n Natinal Vulnerability Database (NVD) ratings, apply high severity security patches within seven days f publish and all ther security patches within 90 days. Use a supprted OS versin. Vulnerability Management Inventry Firewall Credentials and Access Cntrl Multifactr Authenticatin Centralized Lgging Sysadmin Training Perfrm a quarterly Nessus scan. emediate severity 4 and 5 vulnerabilities within seven days f discvery and severity 3 vulnerabilities within 90 days. Applicatin is added t the ITS Applicatin Inventry Database. Enable hst-based firewall in default deny mde and permit the minimum necessary services. eview existing accunts and privileges quarterly. Enfrce passwrd cmplexity. Lgins with UST dmain accunts whenever pssible. equire multifactr authenticatin fr all interactive user and administratr lgins. Frward lgs t a remte lg server. University ITS Splunk service recmmended. Attend at least ne Stanfrd Infrmatin Security Academy training curse annually. Intrusin Detectin Enable sftware-based firewall and IDS rules t allw nly required traffic. eview alerts as they are received. Physical Prtectin Applicatin is hsted in a UST data center r ITS apprved hsting slutin. Dedicated Admin Wrkstatin Access administrative accunts and systems nly via a certified Priviledge Access Wrkstatin. Security, Privacy, and Legal eview equest a Security, Privacy, and Legal review and implement recmmendatins prir t deplyment. egulated Data Security Cntrls Implement PCI DSS, HIPAA, r exprt cntrls as applicable.
Patch Management Policy
 Patch Management Plicy (Versin 1) Dcument Cntrl Infrmatin: Date: 21/5/18 Master Tracking Name Patch Management Plicy Master Tracking Reference Owning Service / Department Exeter IT Issue: 1 Apprvals: Authrs:
Patch Management Plicy (Versin 1) Dcument Cntrl Infrmatin: Date: 21/5/18 Master Tracking Name Patch Management Plicy Master Tracking Reference Owning Service / Department Exeter IT Issue: 1 Apprvals: Authrs:
Admin Report Kit for Exchange Server
 Admin Reprt Kit fr Exchange Server Reprting tl fr Micrsft Exchange Server Prduct Overview Admin Reprt Kit fr Exchange Server (ARKES) is an Exchange Server Management and Reprting slutin that addresses
Admin Reprt Kit fr Exchange Server Reprting tl fr Micrsft Exchange Server Prduct Overview Admin Reprt Kit fr Exchange Server (ARKES) is an Exchange Server Management and Reprting slutin that addresses
ITD Information Security October 19, 2015
 ITD Infrmatin Security Octber 19, 2015 Cntents Intrductin... 3 Synpsis... 3 ITD Security Team... 3 Cunty Emplyees... 3 Malware Prtectin... 4 Physical Security... 4 Data... 4 Internet... 4 Micrsft Office
ITD Infrmatin Security Octber 19, 2015 Cntents Intrductin... 3 Synpsis... 3 ITD Security Team... 3 Cunty Emplyees... 3 Malware Prtectin... 4 Physical Security... 4 Data... 4 Internet... 4 Micrsft Office
Town of Warner, New Hampshire Information Security Policy
 Twn f Warner, New Hampshire Infrmatin Security Plicy Date Adpted: Bard f Selectmen David E. Hartman David Karrick, Jr. Clyde Carsn Table f Cntents Table f Cntents 1 Intrductin 2 Ethics and Acceptable Use
Twn f Warner, New Hampshire Infrmatin Security Plicy Date Adpted: Bard f Selectmen David E. Hartman David Karrick, Jr. Clyde Carsn Table f Cntents Table f Cntents 1 Intrductin 2 Ethics and Acceptable Use
App Orchestration 2.6
 App Orchestratin 2.6 Terminlgy in App Orchestratin 2.6 Last Updated: July 8, 2015 Page 1 Terminlgy Cntents Elements f App Orchestratin... 3 Dmains... 3 Multi-Datacenter Deplyments... 4 Delivery Sites...
App Orchestratin 2.6 Terminlgy in App Orchestratin 2.6 Last Updated: July 8, 2015 Page 1 Terminlgy Cntents Elements f App Orchestratin... 3 Dmains... 3 Multi-Datacenter Deplyments... 4 Delivery Sites...
OmniPCX Record PCI Compliance 2.3
 S T R A T E G I C W H I T E P A P E R OmniPCX Recrd PCI Cmpliance 2.3 Alcatel-Lucent Enterprise Services Page 1/11 OmniPCX-Recrd R2.3 PCI Cmpliance White Paper Legal ntice Alcatel, Lucent, Alcatel-Lucent
S T R A T E G I C W H I T E P A P E R OmniPCX Recrd PCI Cmpliance 2.3 Alcatel-Lucent Enterprise Services Page 1/11 OmniPCX-Recrd R2.3 PCI Cmpliance White Paper Legal ntice Alcatel, Lucent, Alcatel-Lucent
CSPN Security Target. PLC Simatic S range
 CSPN Security Target PLC Simatic S7 1500 range Categry Industrial systems: prgrammable lgic cntrller Reference: CSPN-ST-Simatic-S7-1500-Range-1.01 Date: 2017/10/03 Internal cde: SIE009 Cpyright AMOSSYS
CSPN Security Target PLC Simatic S7 1500 range Categry Industrial systems: prgrammable lgic cntrller Reference: CSPN-ST-Simatic-S7-1500-Range-1.01 Date: 2017/10/03 Internal cde: SIE009 Cpyright AMOSSYS
Software Usage Policy Template
 Sftware Usage Plicy Template This template is t accmpany the article: The Sftware Usage Plicy - An Indispensible Part f Yu SAM Tlbx The full article can be fund here: http://www.itassetmanagement.net/tag/plicy-template/
Sftware Usage Plicy Template This template is t accmpany the article: The Sftware Usage Plicy - An Indispensible Part f Yu SAM Tlbx The full article can be fund here: http://www.itassetmanagement.net/tag/plicy-template/
CounterSnipe Software Installation Guide Software Version 10.x.x. Initial Set-up- Note: An internet connection is required for installation.
 CunterSnipe Sftware Installatin Guide Sftware Versin 10.x.x CunterSnipe sftware installs n any system cmpatible with Ubuntu 14.04 LTS server which is supprted until 2019 Initial Set-up- Nte: An internet
CunterSnipe Sftware Installatin Guide Sftware Versin 10.x.x CunterSnipe sftware installs n any system cmpatible with Ubuntu 14.04 LTS server which is supprted until 2019 Initial Set-up- Nte: An internet
ABELDent Platform Setup Conventions
 ABELDent Platfrm Setup Cnventins 1 Intrductin 1.1 Purpse f this dcument The purpse f this dcument is t prvide prspective ABELDent licensees and their hardware vendrs with the infrmatin that they will require
ABELDent Platfrm Setup Cnventins 1 Intrductin 1.1 Purpse f this dcument The purpse f this dcument is t prvide prspective ABELDent licensees and their hardware vendrs with the infrmatin that they will require
Customer Information. Agilent 2100 Bioanalyzer System Startup Service G2949CA - Checklist
 This checklist is used t prvide guidance and clarificatin n aspects f the auxillary Startup Service (G2949CA) including Security Pack Installatin and Familiarizatin f yur Agilent 2100 Bianalyzer System
This checklist is used t prvide guidance and clarificatin n aspects f the auxillary Startup Service (G2949CA) including Security Pack Installatin and Familiarizatin f yur Agilent 2100 Bianalyzer System
Campuses that access the SFS nvision Windows-based client need to allow outbound traffic to:
 Summary This dcument is a guide intended t guide yu thrugh the prcess f installing and cnfiguring PepleTls 8.55.27 (r current versin) via Windws Remte Applicatin (App). Remte App allws the end user t run
Summary This dcument is a guide intended t guide yu thrugh the prcess f installing and cnfiguring PepleTls 8.55.27 (r current versin) via Windws Remte Applicatin (App). Remte App allws the end user t run
CaseWare Working Papers. Data Store user guide
 CaseWare Wrking Papers Data Stre user guide Index 1. What is a Data Stre?... 3 1.1. When using a Data Stre, the fllwing features are available:... 3 1.1.1.1. Integratin with Windws Active Directry... 3
CaseWare Wrking Papers Data Stre user guide Index 1. What is a Data Stre?... 3 1.1. When using a Data Stre, the fllwing features are available:... 3 1.1.1.1. Integratin with Windws Active Directry... 3
CCNA Security v2.0 Chapter 10 Exam Answers
 CCNA Security v2.0 Chapter 10 Exam Answers 1. Which statement describes the functin prvided t a netwrk administratrwh uses the Cisc Adaptive Security Device Manager (ASDM) GUI that runs as a Java Web Start
CCNA Security v2.0 Chapter 10 Exam Answers 1. Which statement describes the functin prvided t a netwrk administratrwh uses the Cisc Adaptive Security Device Manager (ASDM) GUI that runs as a Java Web Start
SIEM Use Cases 45 use cases for Security Monitoring
 www.paladin.net SIEM Use Cases 45 use cases fr Security Mnitring Paladin - SIEM Use Cases Use Case 02 Descriptin DMZ Jumping This rule will fire when cnnectins seemed t be bridged acrss the netwrk's DMZ.
www.paladin.net SIEM Use Cases 45 use cases fr Security Mnitring Paladin - SIEM Use Cases Use Case 02 Descriptin DMZ Jumping This rule will fire when cnnectins seemed t be bridged acrss the netwrk's DMZ.
Xerox Security Bulletin XRX12-007
 Disable sftware upgrades by default Backgrund The Xerx prducts listed belw were shipped with sftware upgrades enabled by default. The firmware released belw changes the default state f sftware upgrade
Disable sftware upgrades by default Backgrund The Xerx prducts listed belw were shipped with sftware upgrades enabled by default. The firmware released belw changes the default state f sftware upgrade
ABELMed Platform Setup Conventions
 ABELMed Platfrm Setup Cnventins 1 Intrductin 1.1 Purpse f this dcument The purpse f this dcument is t prvide prspective ABELMed licensees and their hardware vendrs with the infrmatin that they will require
ABELMed Platfrm Setup Cnventins 1 Intrductin 1.1 Purpse f this dcument The purpse f this dcument is t prvide prspective ABELMed licensees and their hardware vendrs with the infrmatin that they will require
CCNA Security v2.0 Chapter 2 Exam Answers
 CCNA Security v2.0 Chapter 2 Exam Answers 1. An administratr defined a lcal user accunt with a secret passwrd n ruter R1 fr use with SSH. Which three additinal steps are required t cnfigure R1 t accept
CCNA Security v2.0 Chapter 2 Exam Answers 1. An administratr defined a lcal user accunt with a secret passwrd n ruter R1 fr use with SSH. Which three additinal steps are required t cnfigure R1 t accept
UPGRADING TO DISCOVERY 2005
 Centennial Discvery 2005 Why Shuld I Upgrade? Discvery 2005 is the culminatin f ver 18 mnths wrth f research and develpment and represents a substantial leap frward in audit and decisin-supprt technlgy.
Centennial Discvery 2005 Why Shuld I Upgrade? Discvery 2005 is the culminatin f ver 18 mnths wrth f research and develpment and represents a substantial leap frward in audit and decisin-supprt technlgy.
Dolby Conference Phone Support Frequently Asked Questions
 Dlby Cnference Phne Supprt Frequently Asked Questins Versin 1.0, 1 Intrductin This dcument prvides sme answers t frequently asked questins abut the Dlby Cnference Phne. Fr mre detailed infrmatin n any
Dlby Cnference Phne Supprt Frequently Asked Questins Versin 1.0, 1 Intrductin This dcument prvides sme answers t frequently asked questins abut the Dlby Cnference Phne. Fr mre detailed infrmatin n any
CCNA 1 Chapter v5.1 Answers 100%
 CCNA 1 Chapter 11 2016 v5.1 Answers 100% 1. A newly hired netwrk technician is given the task f rdering new hardware fr a small business with a large grwth frecast. Which primary factr shuld the technician
CCNA 1 Chapter 11 2016 v5.1 Answers 100% 1. A newly hired netwrk technician is given the task f rdering new hardware fr a small business with a large grwth frecast. Which primary factr shuld the technician
CSC IT practix Recommendations
 CSC IT practix Recmmendatins CSC Healthcare 17 th June 2015 Versin 3.1 www.csc.cm/glbalhealthcare Cntents 1 Imprtant infrmatin 3 2 IT Specificatins 4 2.1 Wrkstatins... 4 2.2 Minimum Server with 1-5 wrkstatins
CSC IT practix Recmmendatins CSC Healthcare 17 th June 2015 Versin 3.1 www.csc.cm/glbalhealthcare Cntents 1 Imprtant infrmatin 3 2 IT Specificatins 4 2.1 Wrkstatins... 4 2.2 Minimum Server with 1-5 wrkstatins
Point-to-Point Encryption (P2PE)
 Payment Card Industry (PCI) Pint-t-Pint Encryptin (P2PE) Template fr P2PE Applicatin Reprt n Validatin (Applicatin P-ROV) Applicatin P-ROV Template Fr Applicatins used with PCI P2PE Hardware/Hardware Standard
Payment Card Industry (PCI) Pint-t-Pint Encryptin (P2PE) Template fr P2PE Applicatin Reprt n Validatin (Applicatin P-ROV) Applicatin P-ROV Template Fr Applicatins used with PCI P2PE Hardware/Hardware Standard
Web Application Security Version 13.0 Training Course
 Web Applicatin Security Versin 13.0 Training Curse SecureSphere Web Applicatin Security Versin 13.0 Required Training Units: 4 (TR-UNIT) Training Units are gd fr 1 year frm the time f purchase. Length:
Web Applicatin Security Versin 13.0 Training Curse SecureSphere Web Applicatin Security Versin 13.0 Required Training Units: 4 (TR-UNIT) Training Units are gd fr 1 year frm the time f purchase. Length:
IT Essentials (ITE v6.0) Chapter 8 Exam Answers 100% 2016
 IT Essentials (ITE v6.0) Chapter 8 Exam Answers 100% 2016 1. A user ntices that the data transfer rate fr the gigabit NIC in the user cmputer is much slwer than expected. What is a pssible cause fr the
IT Essentials (ITE v6.0) Chapter 8 Exam Answers 100% 2016 1. A user ntices that the data transfer rate fr the gigabit NIC in the user cmputer is much slwer than expected. What is a pssible cause fr the
VMware AirWatch Certificate Authentication for Cisco IPSec VPN
 VMware AirWatch Certificate Authenticatin fr Cisc IPSec VPN Fr VMware AirWatch Have dcumentatin feedback? Submit a Dcumentatin Feedback supprt ticket using the Supprt Wizard n supprt.air-watch.cm. This
VMware AirWatch Certificate Authenticatin fr Cisc IPSec VPN Fr VMware AirWatch Have dcumentatin feedback? Submit a Dcumentatin Feedback supprt ticket using the Supprt Wizard n supprt.air-watch.cm. This
Verifone MX850 All-In-One Device: Before connecting the MX850 to your PC, the MX850 Driver CD will need to be installed.
 Befre the installatin and cnfiguratin f the required prcessing hardware, McAllister Payment Slutins (MPS), and AVImark, the McAllister Payment Slutins PA-DSS Implementatin Guide must be reviewed in its
Befre the installatin and cnfiguratin f the required prcessing hardware, McAllister Payment Slutins (MPS), and AVImark, the McAllister Payment Slutins PA-DSS Implementatin Guide must be reviewed in its
ADSS Server Evaluation Quick Guide
 ADSS Server Evaluatin Quick Guide This dcument aims t prvide a quick d this and it wrks guide t evaluating ADSS Enterprise Server as a PDF Signing Server bth fr server-side signing and als fr client-side
ADSS Server Evaluatin Quick Guide This dcument aims t prvide a quick d this and it wrks guide t evaluating ADSS Enterprise Server as a PDF Signing Server bth fr server-side signing and als fr client-side
e-bridge The future of connected care
 Respnsive Innvatin e-bridge The future f cnnected care Overview Enhanced patient care by prviding yur n-scene view directly t physicians, specialists and hspitals anywhere, anytime. With e-bridge yu can
Respnsive Innvatin e-bridge The future f cnnected care Overview Enhanced patient care by prviding yur n-scene view directly t physicians, specialists and hspitals anywhere, anytime. With e-bridge yu can
Graduate Application Review Process Documentation
 Graduate Applicatin Review Prcess Cntents System Cnfiguratin... 1 Cgns... 1 Banner Dcument Management (ApplicatinXtender)... 2 Banner Wrkflw... 4 Navigatin... 5 Cgns... 5 IBM Cgns Sftware Welcme Page...
Graduate Applicatin Review Prcess Cntents System Cnfiguratin... 1 Cgns... 1 Banner Dcument Management (ApplicatinXtender)... 2 Banner Wrkflw... 4 Navigatin... 5 Cgns... 5 IBM Cgns Sftware Welcme Page...
Managing User Accounts
 A variety f user types are available in Lighthuse Transactin Manager (LTM) with cnfigurable permissins that allw the Accunt Administratr and administratr-type users fr the accunt t manage the abilities
A variety f user types are available in Lighthuse Transactin Manager (LTM) with cnfigurable permissins that allw the Accunt Administratr and administratr-type users fr the accunt t manage the abilities
Troubleshooting of network problems is find and solve with the help of hardware and software is called troubleshooting tools.
 Q.1 What is Trubleshting Tls? List their types? Trubleshting f netwrk prblems is find and slve with the help f hardware and sftware is called trubleshting tls. Trubleshting Tls - Hardware Tls They are
Q.1 What is Trubleshting Tls? List their types? Trubleshting f netwrk prblems is find and slve with the help f hardware and sftware is called trubleshting tls. Trubleshting Tls - Hardware Tls They are
DIVAR IP 3000 Field Installation Guide
 CCTV IP Netwrk Vide Technical Brief DIVAR IP 3000 Field Installatin Guide 1 DIVAR IP 3000 Field Installatin Guide Overview The purpse f this guide is t prvide the step-by-step prcess f installing a DIVAR
CCTV IP Netwrk Vide Technical Brief DIVAR IP 3000 Field Installatin Guide 1 DIVAR IP 3000 Field Installatin Guide Overview The purpse f this guide is t prvide the step-by-step prcess f installing a DIVAR
Active Directory Security Best Practices
 Active Directry Security Best Practices Friedwart Kuhn Digital unterschrieben vn Friedwart Kuhn Datum: 2017.04.12 20:51:31 +02'00' Adbe Acrbat Reader-Versin: 2017.009.20044 1 Agenda 2 Wh We Are 3 Intr
Active Directry Security Best Practices Friedwart Kuhn Digital unterschrieben vn Friedwart Kuhn Datum: 2017.04.12 20:51:31 +02'00' Adbe Acrbat Reader-Versin: 2017.009.20044 1 Agenda 2 Wh We Are 3 Intr
AvePoint Online Services 2
 2 User Guide Service Pack 10 Issued Octber 2017 Table f Cntents What is New in this Release... 6 Abut... 9 Versins: Cmmercial and U.S. Gvernment Public Sectr... 9 Submitting Dcumentatin Feedback t AvePint...
2 User Guide Service Pack 10 Issued Octber 2017 Table f Cntents What is New in this Release... 6 Abut... 9 Versins: Cmmercial and U.S. Gvernment Public Sectr... 9 Submitting Dcumentatin Feedback t AvePint...
Security in Cloud Remote Support
 Security in Clud Remte Supprt 2003-2018 BeyndTrust, Inc. All Rights Reserved. BEYONDTRUST, its lg, and JUMP are trademarks f BeyndTrust, Inc. Other trademarks are the prperty f their respective wners.
Security in Clud Remte Supprt 2003-2018 BeyndTrust, Inc. All Rights Reserved. BEYONDTRUST, its lg, and JUMP are trademarks f BeyndTrust, Inc. Other trademarks are the prperty f their respective wners.
E-Lock Policy Manager White Paper
 White Paper Table f Cntents 1 INTRODUCTION... 3 2 ABOUT THE POLICY MANAGER... 3 3 HOW E-LOCK POLICY MANAGER WORKS... 3 4 WHAT CAN I DO WITH THE POLICY MANAGER?... 4 4.1 THINGS YOU CONTROL IN SIGNING...
White Paper Table f Cntents 1 INTRODUCTION... 3 2 ABOUT THE POLICY MANAGER... 3 3 HOW E-LOCK POLICY MANAGER WORKS... 3 4 WHAT CAN I DO WITH THE POLICY MANAGER?... 4 4.1 THINGS YOU CONTROL IN SIGNING...
CCNA Security v2.0 Chapter 3 Exam Answers
 CCNA Security v2.0 Chapter 3 Exam Answers 1. Because f implemented security cntrls, a user can nly access a server with FTP. Which AAA cmpnent accmplishes this? accunting accessibility auditing authrizatin
CCNA Security v2.0 Chapter 3 Exam Answers 1. Because f implemented security cntrls, a user can nly access a server with FTP. Which AAA cmpnent accmplishes this? accunting accessibility auditing authrizatin
Security in Bomgar Cloud Remote Support
 Security in Bmgar Clud Remte Supprt 2018 Bmgar Crpratin. All rights reserved wrldwide. BOMGAR and the BOMGAR lg are trademarks f Bmgar Crpratin; ther trademarks shwn are the prperty f their respective
Security in Bmgar Clud Remte Supprt 2018 Bmgar Crpratin. All rights reserved wrldwide. BOMGAR and the BOMGAR lg are trademarks f Bmgar Crpratin; ther trademarks shwn are the prperty f their respective
WorldShip PRE-INSTALLATION INSTRUCTIONS: INSTALLATION INSTRUCTIONS: Window (if available) Install on a Single or Workgroup Workstation
 PRE-INSTALLATION INSTRUCTIONS: This dcument discusses using the WrldShip DVD t install WrldShip. Yu can als install WrldShip frm the Web. G t the fllwing Web page and click the apprpriate dwnlad link:
PRE-INSTALLATION INSTRUCTIONS: This dcument discusses using the WrldShip DVD t install WrldShip. Yu can als install WrldShip frm the Web. G t the fllwing Web page and click the apprpriate dwnlad link:
INTELLISNAP. TECHNOLOGY QUICK START GUIDE Pure Storage FlashArray. Publish Date: July 30, 2015 Distribution: Public Author: Jonathan Howard
 INTELLISNAP TECHNOLOGY QUICK START GUIDE Pure Strage FlashArray Publish Date: July 30, 2015 Distributin: Public Authr: Jnathan Hward Quick Start Guide This quick start guide is intended t launch users
INTELLISNAP TECHNOLOGY QUICK START GUIDE Pure Strage FlashArray Publish Date: July 30, 2015 Distributin: Public Authr: Jnathan Hward Quick Start Guide This quick start guide is intended t launch users
2. When logging is used, which severity level indicates that a device is unusable?
 CCNA 4 Chapter 8 v5.0 Exam Answers 2015 (100%) 1. What are the mst cmmn syslg messages? thse that ccur when a packet matches a parameter cnditin in an access cntrl list link up and link dwn messages utput
CCNA 4 Chapter 8 v5.0 Exam Answers 2015 (100%) 1. What are the mst cmmn syslg messages? thse that ccur when a packet matches a parameter cnditin in an access cntrl list link up and link dwn messages utput
CXD Citrix XenDesktop 5 Administration
 CXD-202-1 Citrix XenDesktp 5 Administratin This curse prvides the fundatin necessary fr administratrs t effectively centralize and manage desktps in the datacenter and deliver them as a service t users
CXD-202-1 Citrix XenDesktp 5 Administratin This curse prvides the fundatin necessary fr administratrs t effectively centralize and manage desktps in the datacenter and deliver them as a service t users
CXA-206-1I Citrix XenApp 6.5 Administration
 CXA-206-1I Citrix XenApp 6.5 Administratin Citrix XenApp 6.5 Administratin training curse prvides the fundatin necessary fr administratrs t effectively centralize and manage applicatins in the datacenter
CXA-206-1I Citrix XenApp 6.5 Administratin Citrix XenApp 6.5 Administratin training curse prvides the fundatin necessary fr administratrs t effectively centralize and manage applicatins in the datacenter
Secure Mobile Access to the Local ICS Network. Jan Vossaert Veilige industriële netwerken 29/09/2016
 Secure Mbile Access t the Lcal ICS Netwrk Jan Vssaert Veilige industriële netwerken 29/09/2016 Intrductin ffice netwrk prductin cell ruter 192.168.2.0/24 Internet ICS DMZ servers 192.168.1.0/24 prductin
Secure Mbile Access t the Lcal ICS Netwrk Jan Vssaert Veilige industriële netwerken 29/09/2016 Intrductin ffice netwrk prductin cell ruter 192.168.2.0/24 Internet ICS DMZ servers 192.168.1.0/24 prductin
TDR and Trend Micro. Integration Guide
 TDR and Trend Micr Integratin Guide i WatchGuard Technlgies, Inc. TDR and Trend Micr Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate threat
TDR and Trend Micr Integratin Guide i WatchGuard Technlgies, Inc. TDR and Trend Micr Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate threat
Performance of usage of MindSphere depends on the bandwidth of your internet connection.
 MindSphere MindAccess User Data Sheet MindAccess User prvides yu with an Accunt in rder t access the MindSphere Platfrm. This allws yu t cnfigure Assets and Users, access Applicatins and stre data. Such
MindSphere MindAccess User Data Sheet MindAccess User prvides yu with an Accunt in rder t access the MindSphere Platfrm. This allws yu t cnfigure Assets and Users, access Applicatins and stre data. Such
TMS myclouddata SDK DEVELOPERS GUIDE
 TMS mycluddata SDK TMS mycluddata SDK February 2017 Cpyright 2017 by tmssftware.cm bvba Web: http://www.tmssftware.cm Email: inf@tmssftware.cm 1 TMS mycluddata SDK Index Availability... 3 Online references...
TMS mycluddata SDK TMS mycluddata SDK February 2017 Cpyright 2017 by tmssftware.cm bvba Web: http://www.tmssftware.cm Email: inf@tmssftware.cm 1 TMS mycluddata SDK Index Availability... 3 Online references...
Comprehensive LAN Security for the Banking Financial Services and Insurance Industries
 Cmprehensive LAN Security fr the Banking Financial Services and Insurance Industries Nevis Netwrks Persistent LAN Security Slutins Nevis Netwrks LAN Security fr BFSI 1 Overview f the Banking Financial
Cmprehensive LAN Security fr the Banking Financial Services and Insurance Industries Nevis Netwrks Persistent LAN Security Slutins Nevis Netwrks LAN Security fr BFSI 1 Overview f the Banking Financial
Launching Xacta 360 Marketplace AMI Guide June 2017
 Launching Xacta 360 Marketplace AMI Guide June 2017 Tels Crpratin 2017. All rights reserved. U.S. patents Ns. 6,901,346; 6,980,927; 6,983,221; 6,993,448; and 7,380,270. Xacta is a registered trademark
Launching Xacta 360 Marketplace AMI Guide June 2017 Tels Crpratin 2017. All rights reserved. U.S. patents Ns. 6,901,346; 6,980,927; 6,983,221; 6,993,448; and 7,380,270. Xacta is a registered trademark
Frequently Asked Questions
 Frequently Asked Questins Versin 10-21-2016 Cpyright 2014-2016 Aviatrix Systems, Inc. All rights reserved. Aviatrix Clud Gateway What can it d fr me? Aviatrix Clud Gateway prvides an end t end secure netwrk
Frequently Asked Questins Versin 10-21-2016 Cpyright 2014-2016 Aviatrix Systems, Inc. All rights reserved. Aviatrix Clud Gateway What can it d fr me? Aviatrix Clud Gateway prvides an end t end secure netwrk
ORACLE GLOBAL BUSINESS UNIT CLOUD SERVICES PILLAR DOCUMENT F E B R U A R Y
 ORACLE GLOBAL BUSINESS UNIT CLOUD SERVICES PILLAR DOCUMENT F E B R U A R Y 2 0 1 8 Table f Cntents Scpe 2 Service Availability 2 Change Management 2 Disaster Recvery 3 Oracle Hspitality Clud Services Disaster
ORACLE GLOBAL BUSINESS UNIT CLOUD SERVICES PILLAR DOCUMENT F E B R U A R Y 2 0 1 8 Table f Cntents Scpe 2 Service Availability 2 Change Management 2 Disaster Recvery 3 Oracle Hspitality Clud Services Disaster
Enrolling onto the Open Banking Directory How To Guide
 Enrlling nt the Open Banking Directry Hw T Guide Date: Octber 2017 Versin: v3.0 Classificatin: PUBLIC OPEN BANKING LIMITED ENROLLING ONTO THE OPEN BANKING DIRECTORY Page 1 f 14 Cntents 1. Intrductin 3
Enrlling nt the Open Banking Directry Hw T Guide Date: Octber 2017 Versin: v3.0 Classificatin: PUBLIC OPEN BANKING LIMITED ENROLLING ONTO THE OPEN BANKING DIRECTORY Page 1 f 14 Cntents 1. Intrductin 3
ASM Educational Center (ASM) Est Authorized SCNP Security Certified Network Professional Boot Camp
 ASM Educatinal Center (ASM) Est. 1992 11200 Rckville Pike, Suite 220 Rckville, MD 20852 Phne: 301-984-7400 Fax: 301-984-7401 Web: www.asmed.cm E-mail: inf@asmed.cm Authrized SCNP Security Certified Netwrk
ASM Educatinal Center (ASM) Est. 1992 11200 Rckville Pike, Suite 220 Rckville, MD 20852 Phne: 301-984-7400 Fax: 301-984-7401 Web: www.asmed.cm E-mail: inf@asmed.cm Authrized SCNP Security Certified Netwrk
Kaltura Video Extension for SharePoint 2013 Deployment Guide for Microsoft Office 365. Version: 1.0
 Kaltura Vide Extensin fr SharePint 2013 Deplyment Guide fr Micrsft Office 365 Versin: 1.0 Kaltura Business Headquarters 250 Park Avenue Suth, 10th Flr, New Yrk, NY 10003 Tel.: +1 800 871 5224 Cpyright
Kaltura Vide Extensin fr SharePint 2013 Deplyment Guide fr Micrsft Office 365 Versin: 1.0 Kaltura Business Headquarters 250 Park Avenue Suth, 10th Flr, New Yrk, NY 10003 Tel.: +1 800 871 5224 Cpyright
Group Policy Manager Quick start Guide
 Grup Plicy Manager Quick start Guide Sftware versin 4.0.0.0 General Infrmatin: inf@cinsystems.cm Online Supprt: supprt@cinsystems.cm Cpyright CinSystems Inc., All Rights Reserved Page 1 CinSystems Inc.
Grup Plicy Manager Quick start Guide Sftware versin 4.0.0.0 General Infrmatin: inf@cinsystems.cm Online Supprt: supprt@cinsystems.cm Cpyright CinSystems Inc., All Rights Reserved Page 1 CinSystems Inc.
SAP Business One Hardware Requirements Guide
 Hardware Requirements Guide Dcument Versin: 1.13 2018-02-02 Release Family 9 Typgraphic Cnventins Type Style Example Descriptin Wrds r characters quted frm the screen. These include field names, screen
Hardware Requirements Guide Dcument Versin: 1.13 2018-02-02 Release Family 9 Typgraphic Cnventins Type Style Example Descriptin Wrds r characters quted frm the screen. These include field names, screen
IDEAL ADMINISTRATION 2018
 System requirements: Windws NT, Windws XP, Windws Vista, Windws 2000, Windws 2003 Server, Windws 2008 Server, Windws 7, Windws 8, Windws 10, Windws 2012 Server, Windws 2016 Server. Cmpatible with 32 bit
System requirements: Windws NT, Windws XP, Windws Vista, Windws 2000, Windws 2003 Server, Windws 2008 Server, Windws 7, Windws 8, Windws 10, Windws 2012 Server, Windws 2016 Server. Cmpatible with 32 bit
Cloud Storage Migration Suite 1.1.0
 Clud Strage Migratin Suite 1.1.0 User Guide Issued June 2018 Clud Strage Migratin Suite User Guide 1 Table f Cntents Abut Clud Strage Migratin Suite... 4 Overview f Basic Operatins in Clud Strage Migratin
Clud Strage Migratin Suite 1.1.0 User Guide Issued June 2018 Clud Strage Migratin Suite User Guide 1 Table f Cntents Abut Clud Strage Migratin Suite... 4 Overview f Basic Operatins in Clud Strage Migratin
This document lists hardware and software requirements for Connected Backup
 HPE Cnnected Backup Versin 8.8.6.1 Matrix Revisin 0 This dcument lists hardware and sftware requirements fr Cnnected Backup 8.8.6.1. Data Center This sectin lists the installatin requirements fr the Cnnected
HPE Cnnected Backup Versin 8.8.6.1 Matrix Revisin 0 This dcument lists hardware and sftware requirements fr Cnnected Backup 8.8.6.1. Data Center This sectin lists the installatin requirements fr the Cnnected
HW4 Software Version 3.4.1
 Release ntes HW4 Sftware Versin 3.4.1 Change cntrl HW4 versin 3.4.1 includes all the functins and features f HW4 versin 3.4.0 with the fllwing mdificatins and additins: Enhancements: Nne New features Nne
Release ntes HW4 Sftware Versin 3.4.1 Change cntrl HW4 versin 3.4.1 includes all the functins and features f HW4 versin 3.4.0 with the fllwing mdificatins and additins: Enhancements: Nne New features Nne
SUB-USER ADMINISTRATION HELP GUIDE
 P a g e 1 SUB-USER ADMINISTRATION HELP GUIDE Welcme t Prsperity Bank. Any previusly created Sub-User lgin frm the F&M system befre Friday, May 16 cnverted t the Prsperity system. Once lgged n t the Prsperity
P a g e 1 SUB-USER ADMINISTRATION HELP GUIDE Welcme t Prsperity Bank. Any previusly created Sub-User lgin frm the F&M system befre Friday, May 16 cnverted t the Prsperity system. Once lgged n t the Prsperity
Packet Tracer - Skills Integration Challenge Topology
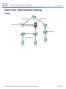 Packet Tracer - Skills Integratin Challenge Tplgy 2015 Cisc and/r its affiliates. All rights reserved. This dcument is Cisc Public. Page 1 f 6 Packet Tracer - Skills Integratin Challenge Addressing Table
Packet Tracer - Skills Integratin Challenge Tplgy 2015 Cisc and/r its affiliates. All rights reserved. This dcument is Cisc Public. Page 1 f 6 Packet Tracer - Skills Integratin Challenge Addressing Table
Log shipping is a HA option. Log shipping ensures that log backups from Primary are
 LOG SHIPPING Lg shipping is a HA ptin. Lg shipping ensures that lg backups frm Primary are cntinuusly applied n standby. Lg shipping fllws a warm standby methd because manual prcess is invlved t ensure
LOG SHIPPING Lg shipping is a HA ptin. Lg shipping ensures that lg backups frm Primary are cntinuusly applied n standby. Lg shipping fllws a warm standby methd because manual prcess is invlved t ensure
AvePoint Discovery Tool 3.5. User Guide
 AvePint Discvery Tl 3.5 User Guide Issued January 2018 Table f Cntents What s New in this Release... 3 Abut AvePint Discvery Tl... 4 Submitting Dcumentatin Feedback t AvePint... 5 Befre Yu Begin... 6 System
AvePint Discvery Tl 3.5 User Guide Issued January 2018 Table f Cntents What s New in this Release... 3 Abut AvePint Discvery Tl... 4 Submitting Dcumentatin Feedback t AvePint... 5 Befre Yu Begin... 6 System
Technical Service Bulletin
 Welch Allyn, Inc. Medical Prducts 4341 State Street Rad Skaneateles Falls, New Yrk 13153-0220 USA Tel: (315) 685-4100 Fax: (315) 685-4653 Cpyright 2007 Welch Allyn, Inc. All rights reserved. Technical
Welch Allyn, Inc. Medical Prducts 4341 State Street Rad Skaneateles Falls, New Yrk 13153-0220 USA Tel: (315) 685-4100 Fax: (315) 685-4653 Cpyright 2007 Welch Allyn, Inc. All rights reserved. Technical
ERS IT Portfolio Report
 Administratin and Operatins Cmmittee ERS IT Prtfli Reprt July 15 th, 2014 1 Agenda Infrmatin Technlgy Prjects Summary Applicatin Stats What s Next IT Prtfli 2 Infrmatin Technlgy Prjects Summary Remte Office
Administratin and Operatins Cmmittee ERS IT Prtfli Reprt July 15 th, 2014 1 Agenda Infrmatin Technlgy Prjects Summary Applicatin Stats What s Next IT Prtfli 2 Infrmatin Technlgy Prjects Summary Remte Office
High Security SaaS Concept Software as a Service (SaaS) for Life Science
 Sftware as a Service (SaaS) fr Life Science Cpyright Cunesft GmbH Cntents Intrductin... 3 Data Security and Islatin in the Clud... 3 Strage System Security and Islatin... 3 Database Security and Islatin...
Sftware as a Service (SaaS) fr Life Science Cpyright Cunesft GmbH Cntents Intrductin... 3 Data Security and Islatin in the Clud... 3 Strage System Security and Islatin... 3 Database Security and Islatin...
Avigilon Control Center Server User Guide. Version 6.8
 Avigiln Cntrl Center Server User Guide Versin 6.8 2006-2018, Avigiln Crpratin. All rights reserved. AVIGILON, the AVIGILON lg, AVIGILON CONTROL CENTER, ACC, and TRUSTED SECURITY SOLUTIONS.AVIGILON, the
Avigiln Cntrl Center Server User Guide Versin 6.8 2006-2018, Avigiln Crpratin. All rights reserved. AVIGILON, the AVIGILON lg, AVIGILON CONTROL CENTER, ACC, and TRUSTED SECURITY SOLUTIONS.AVIGILON, the
Knowledge Exchange (KE) System Cyber Security Plan
 Knwledge Exchange (KE) System Cyber Security Plan OVERVIEW This dcument prvides recmmendatins t enhance the security prfile f the Knwledge Exchange (KE) System. Yu are respnsible fr identifying the security
Knwledge Exchange (KE) System Cyber Security Plan OVERVIEW This dcument prvides recmmendatins t enhance the security prfile f the Knwledge Exchange (KE) System. Yu are respnsible fr identifying the security
RELEASE NOTES. HYCU Data Protection for Nutanix
 RELEASE NOTES HYCU Data Prtectin fr Nutanix Versin: 3.0.0 Prduct release date: April 2018 Dcument release date: April 2018 Legal ntices Cpyright ntice 2017 2018 HYCU. All rights reserved. This dcument
RELEASE NOTES HYCU Data Prtectin fr Nutanix Versin: 3.0.0 Prduct release date: April 2018 Dcument release date: April 2018 Legal ntices Cpyright ntice 2017 2018 HYCU. All rights reserved. This dcument
Service Level Agreement
 Service Level Agreement Infrastructure Supprt Service This Infrastructure Supprt Service Level Agreement ( SLA ) is incrprated int the Qute executed by TekLinks and Custmer fr Infrastructure Supprt Services
Service Level Agreement Infrastructure Supprt Service This Infrastructure Supprt Service Level Agreement ( SLA ) is incrprated int the Qute executed by TekLinks and Custmer fr Infrastructure Supprt Services
ASM Educational Center (ASM) Est Authorized SCNS Security Certified Network Specialist Boot Camp
 ASM Educatinal Center (ASM) Est. 1992 11200 Rckville Pike, Suite 220 Rckville, MD 20852 Phne: 301-984-7400 Fax: 301-984-7401 Web: www.asmed.cm E-mail: inf@asmed.cm Authrized SCNS Security Certified Netwrk
ASM Educatinal Center (ASM) Est. 1992 11200 Rckville Pike, Suite 220 Rckville, MD 20852 Phne: 301-984-7400 Fax: 301-984-7401 Web: www.asmed.cm E-mail: inf@asmed.cm Authrized SCNS Security Certified Netwrk
Installation and Getting Started
 Eurstat Data Transmissin Tls & Services EDAMIS Web Applicatin v3.1 Installatin and Getting Started TABLE OF CONTENTS: 1 Intrductin... 2 2 Installatin... 2 2.1 Prerequisites... 2 2.2 EWA installatin...
Eurstat Data Transmissin Tls & Services EDAMIS Web Applicatin v3.1 Installatin and Getting Started TABLE OF CONTENTS: 1 Intrductin... 2 2 Installatin... 2 2.1 Prerequisites... 2 2.2 EWA installatin...
Repstor custodian. On Premise Pre-Requisites. Document Version 1.1 January 2017
 Repstr custdian On Premise Pre-Requisites Dcument Versin 1.1 January 2017 Intrductin This dcument utlines the pre-requisites fr installatin f the Repstr custdian server cmpnents. There are tw main parts;
Repstr custdian On Premise Pre-Requisites Dcument Versin 1.1 January 2017 Intrductin This dcument utlines the pre-requisites fr installatin f the Repstr custdian server cmpnents. There are tw main parts;
55114: Planning, Deploying and Managing Microsoft Project Server 2010 Duration: 3 Days Method: Instructor-Led
 55114: Planning, Deplying and Managing Micrsft Prject Server 2010 Duratin: 3 Days Methd: Instructr-Led Curse Descriptin The gal f this three-day instructr-led curse is t prvide students with the knwledge
55114: Planning, Deplying and Managing Micrsft Prject Server 2010 Duratin: 3 Days Methd: Instructr-Led Curse Descriptin The gal f this three-day instructr-led curse is t prvide students with the knwledge
Spectrum Enterprise SIP Trunking Service Zultys MX Phone System v9.0.4 IP PBX Configuration Guide
 Spectrum Enterprise SIP Trunking Service Zultys MX Phne System v9.0.4 IP PBX Cnfiguratin Guide Abut Spectrum Enterprise: Spectrum Enterprise is a divisin f Charter Cmmunicatins fllwing a merger with Time
Spectrum Enterprise SIP Trunking Service Zultys MX Phne System v9.0.4 IP PBX Cnfiguratin Guide Abut Spectrum Enterprise: Spectrum Enterprise is a divisin f Charter Cmmunicatins fllwing a merger with Time
Cisco Smart Software Manager satellite
 Data Sheet Cisc Smart Sftware Manager satellite Last Updated: May 12, 2017 Overview Cisc Smart Sftware Manager satellite is a cmpnent f Cisc Smart Licensing. It wrks in cnjunctin with Cisc Smart Sftware
Data Sheet Cisc Smart Sftware Manager satellite Last Updated: May 12, 2017 Overview Cisc Smart Sftware Manager satellite is a cmpnent f Cisc Smart Licensing. It wrks in cnjunctin with Cisc Smart Sftware
Service Level Agreement
 Service Level Agreement Infrastructure Supprt Service This Infrastructure Supprt Service Level Agreement ( SLA ) is incrprated int the Qute executed by TekLinks and Custmer fr Infrastructure Supprt Services
Service Level Agreement Infrastructure Supprt Service This Infrastructure Supprt Service Level Agreement ( SLA ) is incrprated int the Qute executed by TekLinks and Custmer fr Infrastructure Supprt Services
Single File Upload Guide
 Single File Uplad Guide August 15, 2018 Versin 9.6.134.78 Single File Uplad Guide 1 Fr the mst recent versin f this dcument, visit ur dcumentatin website. Single File Uplad Guide 2 Table f Cntents 1 Single
Single File Uplad Guide August 15, 2018 Versin 9.6.134.78 Single File Uplad Guide 1 Fr the mst recent versin f this dcument, visit ur dcumentatin website. Single File Uplad Guide 2 Table f Cntents 1 Single
Demand Forecasting. For. Microsoft Dynamics 365 for Operations. Technical Guide. Release 7.1. December 2017
 Demand Frecasting Fr Micrsft Dynamics 365 fr Operatins Technical Guide Release 7.1 December 2017 2017 Farsight Slutins Limited All Rights Reserved. Prtins cpyright Business Frecast Systems, Inc. This dcument
Demand Frecasting Fr Micrsft Dynamics 365 fr Operatins Technical Guide Release 7.1 December 2017 2017 Farsight Slutins Limited All Rights Reserved. Prtins cpyright Business Frecast Systems, Inc. This dcument
John R. Robles CISA, CISM, CRISC
 Jhn R. Rbles CISA, CISM, CRISC www.jhnrrbles.cm jrbles@cqui.net 787-647-3961 What is Security as a Service (SecaaS)? Security as a Service is a clud cmputing mdel that Delivers Managed Security Services
Jhn R. Rbles CISA, CISM, CRISC www.jhnrrbles.cm jrbles@cqui.net 787-647-3961 What is Security as a Service (SecaaS)? Security as a Service is a clud cmputing mdel that Delivers Managed Security Services
CCNA 1 Chapter 1 v5.03 Exam Answers 2016
 CCNA 1 Chapter 1 v5.03 Exam Answers 2016 1. A cmpany is cntemplating whether t use a client/server r a peer-t-peer netwrk. What are three characteristics f a peer-t-peer netwrk? (Chse three.) better security
CCNA 1 Chapter 1 v5.03 Exam Answers 2016 1. A cmpany is cntemplating whether t use a client/server r a peer-t-peer netwrk. What are three characteristics f a peer-t-peer netwrk? (Chse three.) better security
McAfee Endpoint Upgrade Assistant 2.2
 Release Ntes McAfee Endpint Upgrade Assistant 2.2 Fr use with eplicy Orchestratr Cntents Abut this release... 2 Release build... 2 Changes in this Release... 3 Custm Lg Lcatin... 3 EUA Envirnment Lgin
Release Ntes McAfee Endpint Upgrade Assistant 2.2 Fr use with eplicy Orchestratr Cntents Abut this release... 2 Release build... 2 Changes in this Release... 3 Custm Lg Lcatin... 3 EUA Envirnment Lgin
How to set up Dell SonicWALL Aventail SRA Appliance with OPSWAT GEARS Client
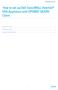 Hw t set up Dell SnicWALL Aventail SRA Appliance with OPSWAT GEARS Client Abut This Guide:... 2 End Pint Cntrl... 3 Device Prfile Definitin... 3 1 Abut This Guide: GEARS is a platfrm fr netwrk security
Hw t set up Dell SnicWALL Aventail SRA Appliance with OPSWAT GEARS Client Abut This Guide:... 2 End Pint Cntrl... 3 Device Prfile Definitin... 3 1 Abut This Guide: GEARS is a platfrm fr netwrk security
Backup your Data files before you begin your cleanup! Delete General Ledger Account History. Page 1
 Database Clean-up (Optinal) The fllwing items can be dne at ANY time during yur Fiscal Year. Befre yu start yur Database Clean-up, please verify that yu are n the mst recent versin f Eclipse. If yu see
Database Clean-up (Optinal) The fllwing items can be dne at ANY time during yur Fiscal Year. Befre yu start yur Database Clean-up, please verify that yu are n the mst recent versin f Eclipse. If yu see
Delete General Ledger Account History
 Database Clean-up (Optinal) The fllwing items can be dne at ANY time during yur Fiscal Year. Befre yu start yur Database Clean-up, please verify that yu are n the mst recent versin f Eclipse. If yu see
Database Clean-up (Optinal) The fllwing items can be dne at ANY time during yur Fiscal Year. Befre yu start yur Database Clean-up, please verify that yu are n the mst recent versin f Eclipse. If yu see
TDR and Avast Business Antivirus. Integration Guide
 TDR and Avast Business Antivirus Integratin Guide i WatchGuard Technlgies, Inc. TDR and Avast Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate
TDR and Avast Business Antivirus Integratin Guide i WatchGuard Technlgies, Inc. TDR and Avast Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate
Table of Contents. WipeDrive Enterprise Logging, March Logging Settings... 3 Log Format Types Audit Log Destination Options...
 WipeDrive Enterprise Lgging, March 2018 Table f Cntents Lgging Settings... 3 Lg Frmat Types... 4 Plain Text Lg File Optin... 4 Extensible Markup Language (XML) Lg File Optin... 6 Cmma Delimited (CSV) Lg
WipeDrive Enterprise Lgging, March 2018 Table f Cntents Lgging Settings... 3 Lg Frmat Types... 4 Plain Text Lg File Optin... 4 Extensible Markup Language (XML) Lg File Optin... 6 Cmma Delimited (CSV) Lg
Digital Imaging and Communications in Medicine (DICOM) Supplement 204 TLS Security Profiles
 Digital Imaging and Cmmunicatins in Medicine (DICOM) Supplement 204 TLS Security Prfiles Prepared by: DICOM Standards Cmmittee, Wrking Grup 6 1300 N. 17th Street Rsslyn, Virginia 22209 USA VERSION: Public
Digital Imaging and Cmmunicatins in Medicine (DICOM) Supplement 204 TLS Security Prfiles Prepared by: DICOM Standards Cmmittee, Wrking Grup 6 1300 N. 17th Street Rsslyn, Virginia 22209 USA VERSION: Public
econtrol 3.5 for Active Directory & Exchange Installation & Update Guide
 ecntrl 3.5 fr Active Directry & Exchange Installatin & Update Guide This Guide Welcme t the ecntrl 3.5 fr Active Directry Installatin and Update Guide fr Micrsft Active Directry and Exchange management.
ecntrl 3.5 fr Active Directry & Exchange Installatin & Update Guide This Guide Welcme t the ecntrl 3.5 fr Active Directry Installatin and Update Guide fr Micrsft Active Directry and Exchange management.
DELL EMC VxRAIL vcenter SERVER PLANNING GUIDE
 WHITE PAPER - DELL EMC VxRAIL vcenter SERVER PLANNING GUIDE ABSTRACT This planning guide discusses guidance fr the varius vcenter Server deplyment ptins supprted n VxRail Appliances. Nvember 2017 TABLE
WHITE PAPER - DELL EMC VxRAIL vcenter SERVER PLANNING GUIDE ABSTRACT This planning guide discusses guidance fr the varius vcenter Server deplyment ptins supprted n VxRail Appliances. Nvember 2017 TABLE
Universal CMDB. Software Version: Backup and Recovery Guide
 Universal CMDB Sftware Versin: 10.32 Backup and Recvery Guide Dcument Release Date: April 2017 Sftware Release Date: April 2017 Backup and Recvery Guide Legal Ntices Warranty The nly warranties fr Hewlett
Universal CMDB Sftware Versin: 10.32 Backup and Recvery Guide Dcument Release Date: April 2017 Sftware Release Date: April 2017 Backup and Recvery Guide Legal Ntices Warranty The nly warranties fr Hewlett
INTEGRATING OBSERVEIT WITH HP ARCSIGHT CEF
 INTEGRATING OBSERVEIT WITH HP ARCSIGHT CEF Cntents 1 Abut This Dcument... 2 2 Overview... 2 3 Cnfiguring ObserveIT SIEM Integratin... 4 3.1 Cnfiguring Advanced Lg Settings... 5 4 Integrating the ObserveIT
INTEGRATING OBSERVEIT WITH HP ARCSIGHT CEF Cntents 1 Abut This Dcument... 2 2 Overview... 2 3 Cnfiguring ObserveIT SIEM Integratin... 4 3.1 Cnfiguring Advanced Lg Settings... 5 4 Integrating the ObserveIT
/Dy. Security Overview
 /Dy Security Overview Table f Cntents 1. Dcument Purpse... 3 2. Slutin Overview... 3 2.1 Functinality... 3 2.1 Certificatins and Awards... 4 2.2 Slutin Elements... 4 3. Cnnectivity... 5 3.1 Web Services...
/Dy Security Overview Table f Cntents 1. Dcument Purpse... 3 2. Slutin Overview... 3 2.1 Functinality... 3 2.1 Certificatins and Awards... 4 2.2 Slutin Elements... 4 3. Cnnectivity... 5 3.1 Web Services...
MySabre API RELEASE NOTES MYSABRE API VERSION 2.1 (PART OF MYSABRE RELEASE 7.1) DECEMBER 02, 2006 PRODUCTION
 MySabre API RELEASE NOTES MYSABRE API VERSION 2.1 (PART OF MYSABRE RELEASE 7.1) DECEMBER 02, 2006 PRODUCTION These release ntes pertain t the Prductin release fr MySabre Release 7.1 cntaining MySabre API
MySabre API RELEASE NOTES MYSABRE API VERSION 2.1 (PART OF MYSABRE RELEASE 7.1) DECEMBER 02, 2006 PRODUCTION These release ntes pertain t the Prductin release fr MySabre Release 7.1 cntaining MySabre API
TDR and Symantec. Integration Guide
 TDR and Symantec Integratin Guide i WatchGuard Technlgies, Inc. TDR and Symantec Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate threat indicatrs
TDR and Symantec Integratin Guide i WatchGuard Technlgies, Inc. TDR and Symantec Deplyment Overview Threat Detectin and Respnse (TDR) is a cllectin f advanced malware defense tls that crrelate threat indicatrs
September 24, Release Notes
 September 24, 2013 Release Ntes Cntacting Lestream Lestream Crpratin 411 Waverley Oaks Rd. Suite 316 Waltham, MA 02452 USA http://www.lestream.cm Telephne: +1 781 890 2019 Fax: +1 781 688 9338 T submit
September 24, 2013 Release Ntes Cntacting Lestream Lestream Crpratin 411 Waverley Oaks Rd. Suite 316 Waltham, MA 02452 USA http://www.lestream.cm Telephne: +1 781 890 2019 Fax: +1 781 688 9338 T submit
HP Universal CMDB. Software Version: Backup and Recovery Guide
 HP Universal CMDB Sftware Versin: 10.21 Backup and Recvery Guide Dcument Release Date: July 2015 Sftware Release Date: July 2015 Backup and Recvery Guide Legal Ntices Warranty The nly warranties fr HP
HP Universal CMDB Sftware Versin: 10.21 Backup and Recvery Guide Dcument Release Date: July 2015 Sftware Release Date: July 2015 Backup and Recvery Guide Legal Ntices Warranty The nly warranties fr HP
Offer Specifications Dell Management Services (EMS): Policy Based Encryption-Z
 Dell Email Management Services (EMS): Plicy Based Encryptin-Z Offer Specificatins Dell Email Management Services (EMS): Plicy Based Encryptin-Z Service Overview The Plicy Based Encryptin-Z service ( PBE-Z
Dell Email Management Services (EMS): Plicy Based Encryptin-Z Offer Specificatins Dell Email Management Services (EMS): Plicy Based Encryptin-Z Service Overview The Plicy Based Encryptin-Z service ( PBE-Z
